#hackthissite
Explore tagged Tumblr posts
Text

With Firefox having AI added in the recent update. Here's how you can disable it.
Open about:config in your browser.Accept the Warning it gives.Search browser.ml and blank all values and set false where necessary as shown in the screenshot, anything that requires a numerical string can be set as 0 .Once you restart you should no longer see the Grey-ed out checkbox checked, and the AI chatbot disabled from ever functioning.
#mozilla#mozilla firefox#firefox#web browsers#pro tip#protips#anti ai#fuck ai#internet#how to#diy#do it yourself#artificial intelligence#signal boost#signal b00st#signal boooooost#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government
481 notes
·
View notes
Text
trying HackThisSite. honestly a lot of fun.
2 notes
·
View notes
Text
Hack This Site - Forensics #2
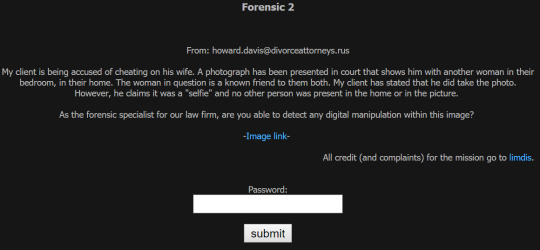
This one here is quite interesting in the sense that we have to determine if an image has been digitally modified. The image we’ve been given is below; looking at it from a distance nothing seems too obvious and stands out. If you zoom in on the edges of the woman they look a bit dodgy but we need to prove this more definitively.

I looked into some of the techniques you can use for determining modification of an image - one of them is known as “error level analysis”. The idea behind it is that if another object has been “photoshopped” into an image, there will be different compression artifacts in different sections of the image. For example, if the image of the woman was extracted from a higher resolution image, you would be able to distinguish this when it is compressed to be added to the selfie above. There is actually a pretty cool forensics tool online at www.fotoforensics.com to do this:

You can see in the ELA how she was clearly cropped into the image and conveniently enough the password appears to be written in the top left corner, “ELA4LIFE!!”
6 notes
·
View notes
Text
Hacking
There are servers people set up and allow anyone to hack - some are realistic, and some are more instructive in nature. HackThisSite may be the most famous - someone asked on r/asknetsec if it’s actually useful, and the top response was that the absolute worst-case scenario is that you learn something new, you have a lot of fun, and then you find out later that MAYBE the techniques you used are out of date.
That’s not the worst case scenario. A worse scenario I can think of is that one of their website admins tries your password on your email, and that’s not even the worst case scenario...but the site is fairly famous now.
You can pass the first few levels just by fiddling with “inspect element.” From there, things get more interesting. You can pass one level with a SQL injection, meaning you enter a login page and instead of entering something like “admin” and “secretpassword” you enter something like OR 1=1 -- ' . What you’ve just entered is additional text interpreted as part of a command, so that as long as 1 = 1 (which, by the laws of logic, is always true) the rest of the command is ignored. You can use this to log in as anyone.
***
There are other, more interesting ways to go here. OverTheWire is like HackThisSite, but you actually use C coding and stage buffer overflow attacks. Then there’s Kali Linux, an offensive OS made popular by the first and only accurate hacking show on television (I suppose there’s also Silicon Valley and Nathan For You), and for testing you can download another VM, a target, called Metasploitable...an intentionally vulnerable version of Ubuntu.
You can hack that thing to your heart’s content, and it’s Linux. Linux, as Zhanghe once said, has been open source since the dawn of time.
***
Malware is getting really, really smart.
It used to be that there was just the Facebook message asking if you wanted to see a picture, or the hijacked AIM instructing you to download...uh...a picture. We were in 8th grade, and we would make fun of anyone who fell for this in order to mask the insecurity we felt the day before, when we fell for it ourselves.
Now there’s SEO malware - it exploits Google’s laws of SEO to get near the top of search results, and it lifts contents from public sites like Reddit so that when you research anything, you see a bunch of legitimate-looking text previewed. It redirects you to something asking you to hit authorize, and if you do it hijacks your browser and attempts to use that as a vector to get into the rest of your computer.
If you want to know if a website is safe, you can attempt to Google it without actually going to the site. But then, from there, you might encounter a top-rated site called scamadviser. Scamadviser is a scam. Don’t click on it.
There are also cybersecurity publications that end with things like .net, so malware sites spring up that just replace that with .com...you cannot make this stuff up. And it seems like there are holes in security everywhere. LinkedIn was compromised because some sysadmin had a vulnerable personal website hosted on a personal laptop, and the personal laptop had direct access to LinkedIn. A Saudi Arabia company ten times more valuable than Apple fell to phishing. And Twitter...I don’t even know what happened to Twitter, and how it caused Biden, Bill Gates, and Elon Musk to all simultaneously ask me to send them $1000 in bitcoin and they would send me back double.
****
In conclusion, if malware is this smart then we might as well learn how to take down some metasploitable virtual machines. It’s cheaper entertainment than Disney+ and it takes up less disc space than Counter Strike.
122 notes
·
View notes
Text
HackThisSite Realistic #6
This challenge is a pain in the ass.
Prompt:
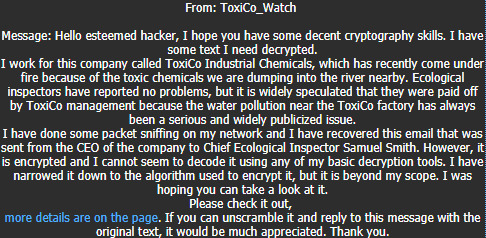
I am shown a sequence of letters, as well as a page where the encryption algorithm is demonstrated.

Investigating the encryption page.

After a few tries of encrypting h, I realized that the algorithm was non-deterministic. I got
.50.32.22, .11.32.61 , and .61.10.33 . Looking for any patterns, I realized that .11.32.61 and 61.10.33 add up to the same number, 104. The rest also added up to 104. 104 is the code for h.
I tried encrypting ‘help’, and got .33.31.40.62.53.14.15.9.84.48.21.43. Adding them up gave me 104, 101, 108, 112. Ascii for ‘help’, each character being three letters.
Encrypting ‘help’ with ‘a’ as the password gave me
.65.56.80.37.48.113.66.65.74.57.69.83. Adding them up:
201, 198, 205, 209
201 - 104 = 97, ascii for a. Similarly, everything has been encrypted with ‘a’.
Encrypting ‘help’ with ‘aa’ as the password gave me:
.88.83.127.71.77.147.88.114.100.129.104.73
298, 295...
At this point, I realized that it was just three letters adding up to give [ascii] + p[1] + [2] + .. + p[n].This can be brute forced.
The first three numbers of the sequence are 845, 859, 871. Looking at 845, it ranges from possibly being ‘a’ with a six letter password or less. However, the letter order ranges from 65 to 122 (A to z), which would be a large difference. I decided to try something - the letter was addressed to a Chief Ecological Inspector Samuel Smith.
The letters didn’t correspond to a ‘Chief’, but the difference between ‘S’ and ‘a’ in Samuel is 14. Coincidentally, it is also 14 in the combination between 845 and 859. Guessing the password adds up to 762, I started decoding the rest.
Samuel Smith
Thank you for looking the other way on the increased levels of toxic chemicals in the river running alongside our industrial facilities. You can pick up your payment of $20,000 in the mailbox at the mansion on the corner of 53 and St. Charles tomorrow between the hours of 3:00am and 5:00am.
Thank you,
John Sculley ToxiCo Industrial Chemicals
Bad encryption. Also, the page you’re supposed to send the answer is filled with the flag. Challenge successful.
3 notes
·
View notes
Text
A new game of a very rare form - help needed?
I need help in creating a new game, but not a normal game!
It involves physical, LARP-like systems, in combination with online, hacking competition-like work. It’s Inspired by DAEMON (http://daem.onl/), hackthissite (https://www.hackthissite.org/), mostly; the plan is to create a system and game revolving around a power struggle in a cyberpunk/glitchpunk setting.
I need people who can write code or worldbuilding, mostly, but pretty much anyone who wants to is welcome to join and can contribute.
Please spread this :0
6 notes
·
View notes
Text
Syazana Fadzil
Find me here;
LinkedIn
WordPress
GitHub
HackThisSite ( Note; please refresh again when you're in the page if an error appeared, thank you!)
1 note
·
View note
Note
The security guys have all the fun and I'm too stupid to keep up and learn it. I'm just a networking major
fklasdfhdsklf i don’t think that’s true. I consider myself very interested in security but that’s also because i’m very interested in the low-level workings of systems software. Security is by and large just getting to understand how a system works *really* well and then poking at its weak spots. You can definitely get into network security, if you’d like; my school had two security profs: the systems guy (who I studied under), and the networks guy. :)
I got into it through sites that are geared toward this sort of think (eg hackthissite, root me, ctftime, etc). Most of the ones I looked at were focused on reversing (i.e. looking at a compiled program and exploiting it), but I know for a fact there are a few that are network attack based. You might want to look into it if you think you might be at all interested!
1 note
·
View note
Text
SA Wk 2: The Various CTFs
Entering the CTF Restaurant:
After getting the initial proposal approved by Thursday morning, it’s time to start moving forward with narrowing down the fields of CTFs available and as recommended by Andrew, try to aim for a depth over breadth approach to tackling CTFs. Given the short remainder of the week, I plan to have a look at what the main categories of CTFs are, and choose the field(s) I’d most like to have a go at.
What’s on the Menu:
Web Exploitation - challenges which aim to cover various methods for attacking web-based resources and applications. Website vulnerabilities are weaknesses/misconfigurations in a website or web app’s code which may provide attackers with partial control of a site or even the host server. Once exploited, the attacker could have the ability to distribute malware, steal data, or use the site for spam.
Binary Exploitation - aiming to make an app act differently than intended in order to gain information. This information can then be used to gain unauthorised control or privileges to the system running it. A common attacker’s method involves memory corruption to rewrite critical information and run their own code.
Reverse Engineering - requires an in-depth understanding of an application’s code. These challenges require somewhat strong disassembler and debugging skills, in order to understand the flow of logic in a program. Once such an understanding has been achieved, the attacker can try to make alterations for the code to perform his/her intentions.
Forensics - often required to find files or information embedded/hidden within other files of different types. Attackers get handy with a range of scripts and tools to extract smaller amounts of data to analyse and decode.
Cryptography - a self-explanatory CTF field. It encompasses various levels and methods of encryption/decryption, often through large amounts of random data and files to find a small flag.
Possible Websites:
OverTheWire @ https://overthewire.org/
Pwnable @ https://pwnable.kr/
Reversing @ http://reversing.kr/
W3Challs @ https://w3challs.com/
HackThisSite @ https://www.hackthissite.org/
HackTheBox @ https://www.hackthebox.eu/
CTF365 @ https://ctf365.com/
PentesterLabs @ https://pentesterlab.com/
Crackmes @ https://crackmes.one/
I Think I’ll Have... :
After looking into many many CTF and wargame websites, the above few seem to be the most promising to choose from. However, my inherently indecisive nature combined with the interest in both web security and binary exploitation leaves me at a crossroads. As such I’m treating this decision as I would in a restaurant when I can’t decide what amazing food to eat...why not both?
I’m somewhat uncertain about how far I will be able to progress with my limited skills as they stand, but I aim to complete challenges primarily from OverTheWire (they’re fun) and Pwnable (classified as binary exploitation) to the best of my ability.

0 notes
Text
Here’s some cybersecurity & hacking resources for anyone who’s interested
I got an ask from someone looking for cybersecurity resources, and I wasn’t sure how they’d feel about me answering publicly, so I figured I’d answer privately but also share the resources publicly.
Here’s what I told them:
Learn the OWASP Top 10 inside and out if you haven’t already. Web app hacker’s handbook. Web app practice: JuiceShop, or google “damn vulnerable web apps” (one of them is actually called DVWA but you’ll find others) Embedded/firmware CTF: Microcorruption. Cryptography practice: Cryptopals. HackThisSite is good. OverTheWire is good. Google Gruyere is good for beginners. I think Google also has a training sequence game specifically for XSS. If you feel really ready, you can also try your hand at some real life bug-hunting. BugCrowd and HackerOne are two major bug bounty platforms -- check them out and try testing a couple of the apps listed on there. (Make sure you follow the rules listed! And if there’s any doubt, err on the side of caution and over-communication with the app’s owner -- unless you feel that a vuln you find is SOOOO glaringly dangerous, widespread, and exploitable that you have a duty to share it publicly, but that’s extremely unusual that that happens, even for the best bug hunters in the world.) I’m pretty n00b-y myself, so I may be missing some areas. Others in the know feel free to reblog with more resources!
6 notes
·
View notes
Text

#software#firmware#mutual aid#freeware#internet#infotech#information technology#it#i.t.#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government#anti capitalism#anticapitalista#anti capitalist love notes#anticapitalistically#anticapitalist memes#eat the rich#eat the fucking rich#anti colonialism#anti cop#anti colonization#fuck capitalism
4 notes
·
View notes
Text
For this lab, I want you to go out and use a vulnerable training tool to try an
For this lab, I want you to go out and use a vulnerable training tool to try an
For this lab, I want you to go out and use a vulnerable training tool to try and hack into a website and complete a few other challenges. You will need to download this software: HackthisSite at https://www.hackthissite.org/ (Links to an external site.)Links to an external site.. Once you login you will be asked to build an account. Go ahead and build an account. Then I want you to try 4 of the…
View On WordPress
0 notes
Text
Hack This Site - Application #17
Not just from the fact that this was marked as hard, this one definitely looks difficult in the sense that our password (or key) is unique to the username. As usual we start with the Intermodular References to look for reading the console input:

We put a breakpoint on this call and then follow it up:

Here I’ve discovered a loop of sorts which will read one character at a time from the input. Following it up further we’re inside a larger loop:
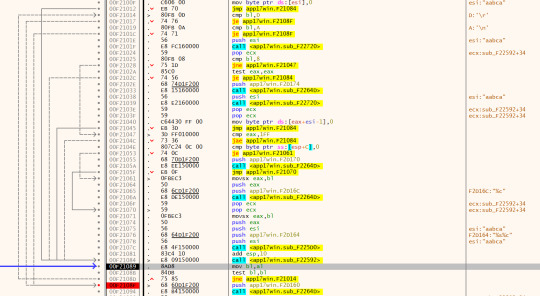
I don’t really need to know the details of this loop, except to know from debugging that we exit all the loops after pressing “Enter”. Now this returns to another function (I’ve conveniently already debugged it all and labelled):

So basically we read in the username, assembly a “Password :” string and print it, then read in a password. Then we call a function which appears to verify the password. I’ll go into the contents of this in more detail:
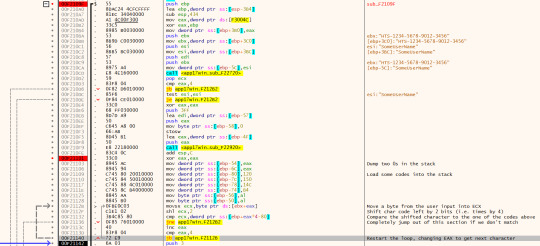
The first important thing in this function is that we are grabbing the password input and comparing the first 4 characters to a code - namely [0x120, 0x150, 0x14C, 0xB4]. This involves bitshifting the input character left by 2 first - therefore we can reverse this code by bit shifting it to the right which gives us [��H’, ‘T’, ‘S’, ‘-’]. So basically we’re just checking it is of the required format.
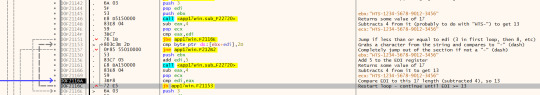
The next bit seems to be referring to the section beyond the “HTS-” in the user’s password. It seems to be expecting this length to be of 13 (based on the loop length) so passwords should be of the form “HTS-XXXX-XXXX-XXXX”. In this loop (as commented) it basically checks that the dashes are all in the correct positioning. In the next bit we are removing the dashes:
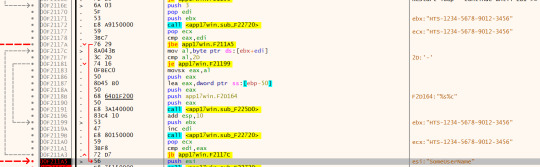
I didn’t bother commenting it as it’s easier to just observe the debugging output and see it places the resultant string after the loop:

So now we have a string with the “HTS-” and other “-” removed. Then next part I’ve gone through and debugging quite detailed:
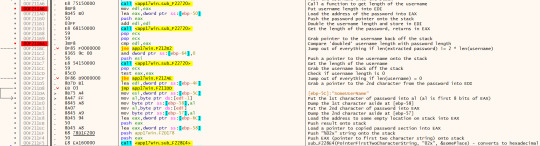
Basically we’re verifying that the extracted password (without dashes and “HTS”) is exactly 2 times the length of the username. We also check the username isn’t 0 and then extract the hexadecimal value of the first 2 characters in the given password.

The next section is quite confusing however I’ve documented what is happening alongside the assembly code. (if you want to read) I’ll try and summarise what is happening:
Start with a code of 0
Loop over the length of the username (for each i)
shl eax, cl => username[i] << (code & 0xFF)
sub esi, esx => username[i] - code
sar esi, 1 => (username[i] - code) >> 0x01
not eax => ~(username[i] << (code & 0xFF))
and esi eax => (username[i] - code) & ~(username[i] << (code & 0xFF))
Set the code to this result
ModifiedKey += Hex(Code) (2 character value)
Add the “HTS-” to front of modified key and add a “-” after every 4 characters
So basically I only really needed the first section; the second half of the above image didn’t really matter at all. In the end I implemented this in a keygen in python:
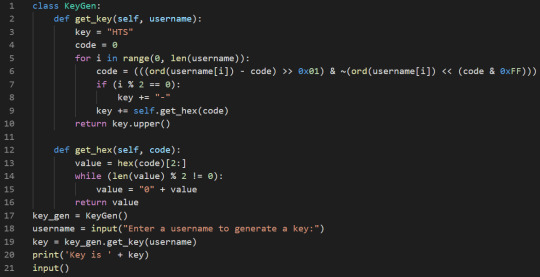
Running the program we get the following:
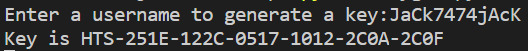
And running in the program we get the result:
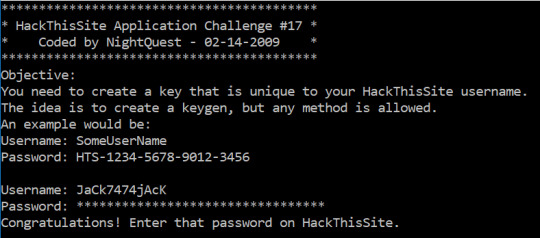
And we have completed the challenge! This one was definitely complex and took forever, however it was pretty cool to get more experience with x86 assembly.
3 notes
·
View notes
Text
For this lab, I want you to go out and use a vulnerable training tool to try an
For this lab, I want you to go out and use a vulnerable training tool to try an
For this lab, I want you to go out and use a vulnerable training tool to try and hack into a website and complete a few other challenges. You will need to download this software: HackthisSite at https://www.hackthissite.org/ (Links to an external site.)Links to an external site.. Once you login you will be asked to build an account. Go ahead and build an account. Then I want you to try 4 of the…
View On WordPress
0 notes
Text
Something Awesome Roundup

My proposal I wrote for myself a month and a week ago can be found here:
Initially, I set out to learn how to penetration test and do CTF challenges. I had a list of websites that I wanted to try and test, as well as setting out to do blogs on every challenge I did. While I’ve not done as much as I’d like in terms of challenge quantity, I learned a fair few things over the course of my project and I know the path to take to learn more. CTF is one of those things where you need to gather more vulnerabilities and skills to use, continuous learning, etc.
The following will be a writeup as to everything I’ve blogged on regarding the project.
--------------- ------------------------- ------------------------- -------------------------
I made 14 blog posts total. On average, 2 per week (seven weeks), semi-consistent. I wrote three last week and one this week. I’m a bit too busy to pull a table, else I would make a table of activity.
I first performed the introduction challenge on hackthisbox.org, where you’re required to hack an invite code to make an account on the website. This was mainly recon work, some knowledge on how JS worked, and googling. Probing hackthisbox.org proved to me that the site was rather advanced (probably hence the challenge), so I went on other sites to probe around.
I went on CTFLearn.com next, probed around and did a few challenges, then on pwnable.kr. Both these sites weren’t something I was looking for, and microcorruption.com was regarding microprocessors, which I’m still rather shaky on.
Next, I tried hackthissite.org, which taught me a few basic skills I had heard about with its Basic Levels #1 - 10. I learned different types of SQL injections (mainly from OWASP), Server-Side Includes (SSI) attacks, and half of the top 10 OWASP attacks at a basic level.
It was then that I moved onto its Realistic Challenges, which I spent most of the challenge on. Each one got very progressively harder, to the point where I spent a significant amount of time poking around and learning a lot about different techniques in my own time to try and push. Each realistic challenge on HackThisSite I tried has its own blog post. Performing different types of SQL injections was very fun, decoding passwords and cryptography was demonstrating a lot of things discussed but not taught in lecture, so I thought it fit the course very well. It forced me to self learn a lot of things, actively trying to learn (watching youtube videos on CTFing, etc)
My write up on all 10 challenges and each technique I used to successfully complete it can be found here.
Next, I looked around for a different kind of challenge - I wanted to write up more sites in my report. I tried OverTheWire, but due to time constraints I couldn’t finish what I wanted. OverTheWire gave me some rather rudimentary (scaled) challenges to do on terminal, sshing. I learned how to do basic commands with flags better, which I should probably master.
Overall, I think I did decently dispersed work, though I would have liked to do more. Most of my time was spent researching independently.
Also, the Hacknet OST is really nice with work. I guess I discovered it in doing this challenge.
0 notes
Text
For this lab, I want you to go out and use a vulnerable training tool to try an
For this lab, I want you to go out and use a vulnerable training tool to try an
For this lab, I want you to go out and use a vulnerable training tool to try and hack into a website and complete a few other challenges. You will need to download this software: HackthisSite at https://www.hackthissite.org/ (Links to an external site.)Links to an external site.. Once you login you will be asked to build an account. Go ahead and build an account. Then I want you to try 4 of the…
View On WordPress
0 notes