#icloud bypass software
Explore tagged Tumblr posts
Video
youtube
Haafedk iCloud tool 3.4 \ remove passcode without iCloud iPhone and iPad...
1 note
·
View note
Text
سرویس IKEY
صفحه قفل فعال سازی آیکلود (iCloud) یکی از رایج ترین مشکلاتی است که کاربران آیفون و آیپد ممکن است با آن مواجه شوند. اگر دستگاهی دارید که iCloud قفل شده است، برای باز کردن قفل آن باید Apple ID و رمز عبور داشته باشید. تیم مستر اختاپوس ابزارهای حرفه ای را برای حل این مشکلات توسعه داده است. با استفاده از این ابزارها، کاربران می توانند قفل دستگاه خود را باز کنند، آیفون و آیپد قفل شده آیکلود را دور بزنند و حساب Apple ID را از دستگاه اپل حذف کنند، تنها با یک کلیک با استفاده از سرویس IKEY Tool در مستر اختاپوس.
دریافت سرویس از لینک زیر:
1 note
·
View note
Text
WinRa1n v3.0 new update iOS 17/ 17.0.1/ 17.0.2 jailbreak tool for Windows

View On WordPress
#Bypass iCloud Activation#icloud lock solution 2019#icloud unlock software#iOS 13 Jailbreak#jailbreak VIDEO IOS 13
1 note
·
View note
Text
FoneTool Unlocker Pro - Dacă ai un dispozitiv iOS blocat sau vrei să elimini rapid restricțiile de securitate, avem vești excelente pentru tine: primești gratuit o licență valabilă 1 an pentru FoneTool Unlocker Pro! Este o oportunitate limitată, ideală pentru utilizatorii care vor să economisească timp și bani în gestionarea dispozitivelor iPhone sau iPad. Tot ce trebuie să faci este să urmezi pașii de revendicare a codului de licență și vei putea folosi unul dintre cele mai eficiente instrumente de deblocare pentru iOS – fără costuri! 🔍 Ce este FoneTool Unlocker Pro? FoneTool Unlocker Pro este un software puternic destinat utilizatorilor de iPhone și iPad care au nevoie să deblocheze accesul la dispozitivul lor, indiferent de situație: ai uitat parola, ai cumpărat un telefon second-hand cu Apple ID activ, dispozitivul este blocat sau gestionat de o organizație prin MDM. Programul este conceput pentru a funcționa într-un mod sigur și eficient, fără a compromite integritatea sistemului sau datele utilizatorului. FoneTool Unlocker Pro este compatibil cu cele mai recente versiuni de iOS și cu majoritatea dispozitivelor Apple, inclusiv cele mai noi modele. ✨ Caracteristici Cheie 🔓 Deblocare parolă ecran – Elimină cu ușurință codurile de 4/6 cifre, Face ID sau Touch ID. 🧑💼 Înlăturare Apple ID – Poți șterge contul iCloud activ fără parolă, în mod sigur. 🛡️ Bypass MDM (Mobile Device Management) – Acces complet la dispozitiv fără restricții organizaționale. 📲 Resetare completă fără cod de acces – Poți șterge conținutul dispozitivului fără autentificare. 💻 Interfață intuitivă – Design simplu și prietenos, ghid pas cu pas pentru orice operațiune. 🔁 Compatibilitate – Compatibil cu toate versiunile iPhone/iPad/iPod Touch și iOS. 🧾 Cum obții licența gratuită? Accesează pagina oficială a promoției FoneTool Unlocker Pro. Descarcă software-ul și instalează-l pe PC-ul tău: FoneToolUnlocker_free_installer.exe Introdu codul de licență de mai jos. Cod de licență! MBPR-CBFF2-OK05D-N9UVV Bucură-te de acces complet timp de 1 an – gratuit!
0 notes
Text
Jailbreak iOS 18.2
Apple’s iOS updates bring exciting features, but they also come with restrictions. For users who want complete control of their iPhones or iPads, jailbreaking remains the go-to solution. With the recent release of iOS 18.2, many are wondering: is it possible to Jailbreak iOS 18? The answer is yes! This guide will show you how to jailbreak your device safely and efficiently.
Following this article, you’ll learn the benefits, risks, and step-by-step methods to Jailbreak iOS 18.2. One of the most reliable tools to jailbreak iOS 18.2 is InstantJB, which we will discuss further. Let’s get started.
What is Jailbreaking?
Before we dive into Jailbreak iOS 18.2, let’s clarify what jailbreaking means. Jailbreaking removes Apple’s software restrictions, allowing users to install third-party apps, tweaks, themes, and more. With jailbreaking, you can unlock your iPhone’s full potential and customize it in ways that Apple’s default system doesn’t allow.
For example, jailbreaking gives you access to apps unavailable on the App Store, deeper file system access, and tools to optimize system performance.
Is Jailbreaking iOS 18.2 Safe?
Safety is a common concern when it comes to Jailbreak iOS 18.2. Jailbreaking itself is not harmful when done correctly using trusted tools like InstantJB. However, installing tweaks or apps from unverified sources can cause instability or security risks.
It’s important to:
Use reliable jailbreak tools.
Download tweaks and apps only from trusted repositories.
Always back up your device before attempting to jailbreak.
While jailbreaking may void your warranty, you can easily reverse the process by restoring your device to its factory settings.
Can You Jailbreak iOS 18.2?
Yes, you can Jailbreak iOS 18.2! Thanks to advancements in the jailbreak community, tools are now available to bypass Apple’s restrictions on iOS 18.2. One of the most user-friendly tools for jailbreaking iOS 18.2 is InstantJB.
InstantJB makes the jailbreaking process quick and simple, even for beginners. You don’t need advanced technical knowledge or complex setups. The tool does all the hard work for you.
To get started, visit https://www.instantjb.com and follow their easy step-by-step guide.
Benefits of Jailbreak iOS 18.2
Here are some of the top benefits of choosing Jailbreak iOS 18.2:
Customization: Jailbreaking allows you to change your device’s appearance completely. To personalize your iPhone, you can install themes, custom icons, and widgets.
Third-Party Apps: Access apps and tools unavailable on the App Store, such as emulators, advanced media players, and file managers.
Performance Tweaks: Jailbreaking lets you install tweaks to improve battery life, reduce lag, and optimize system performance.
File System Access: You can access and manage your device’s file system for greater control.
Additional Features: Add new functionality to your iPhone, such as multitasking improvements, gesture controls, and enhanced privacy settings.
Risks of Jailbreaking iOS 18.2
While there are significant benefits, you should also consider the risks of Jailbreak iOS 18.2:
Warranty Void: Jailbreaking may void your Apple warranty. However, restoring your device can undo the jailbreak.
Security Concerns: Installing tweaks or apps from untrusted sources can expose your device to malware.
System Instability: Incompatible tweaks may cause system crashes, app freezes, or unexpected behaviour.
Blocked iOS Updates: Jailbroken devices may receive the latest iOS updates once compatible jailbreak tools are released.
To minimize these risks, use a trusted jailbreak tool like InstantJB and reputable repositories for tweaks and apps.
How to Jailbreak iOS 18.2 Using InstantJB
If you’re ready to Jailbreak iOS 18.2, here is a simple step-by-step guide using InstantJB:
Back-Up Your Device Before starting jailbreak, back up your iPhone or iPad using iCloud or iTunes to prevent data loss.
Visit InstantJB Open Safari on your iPhone and visit https://www.instantjb.com.
Follow the Instructions InstantJB provides clear instructions to guide you through jailbreak. Simply follow the steps as they appear on the screen.
Complete the Jailbreak Once the process is complete, your device will restart, and the jailbreak will be activated.
Install a Package Manager After jailbreaking, tools like Cydia or Sileo will be installed. These package managers allow you to download tweaks, apps, and themes to customize your device.
What to Do After Jailbreaking iOS 18.2
After you successfully Jailbreak iOS 18.2, here are a few tips to get the most out of your device:
Install Trusted Repositories: Add trusted sources to Cydia or Sileo to download safe and reliable tweaks.
Customize Your iPhone: Explore themes, icon packs, and widgets to personalize your device.
Install Tweaks for Performance: Use tweaks to improve battery life, reduce lag, and add new features.
Be Cautious: Avoid downloading tweaks from unverified sources to prevent malware or instability.
Frequently Asked Questions (FAQs)
1. Is jailbreaking iOS 18.2 legal? Yes, jailbreaking is legal in many countries, including the United States. However, it may void your warranty.
2. Can I undo a jailbreak? You can remove the jailbreak by restoring your iPhone or iPad to factory settings using iTunes or Finder.
3. Is InstantJB safe? InstantJB is a trusted tool used by many in the jailbreak community to Jailbreak iOS 18.2.
4. Will jailbreaking affect my data? No, jailbreaking does not delete your data. However, it is always a good idea to back up your device beforehand.
5. What happens if my device becomes unstable? If you experience crashes or glitches, you can enter safe mode to remove problematic tweaks or restore your device.
Final Thoughts on Jailbreak iOS 18.2
Jailbreaking remains a powerful way to customize and unlock the full capabilities of your iPhone or iPad. With tools like InstantJB, the process to Jailbreak iOS 18.2 is now easier, safer, and more accessible than ever before.
By jailbreaking your device, you can install third-party apps, apply stunning themes, and add performance tweaks to enhance your iOS experience. As long as you use trusted tools and repositories, jailbreaking can be a safe and rewarding process.
If you’re ready to take control of your iOS device, visit https://www.instantjb.com and follow the simple steps to Jailbreak iOS 18.2 today!
Unlock the full potential of your iPhone and enjoy a world of freedom, customization, and new possibilities.
0 notes
Text
How Can You Bypass Your iPhone Passcode in Easy Steps?

Forgetting your iPhone passcode can be a frustrating experience, especially when you're locked out of your device and can't access important data. Whether you've recently changed your passcode or haven't used your phone in a while, learning how to bypass iPhone passcode restrictions can seem overwhelming. Fortunately, there are straightforward methods you can follow to unlock your device without requiring advanced technical knowledge.
In this guide, we’ll walk you through how to bypass iPhone passcode locks using step-by-step instructions with iTunes, Finder, or recovery mode. These solutions will help you restore your device and regain access, even if you can't remember the passcode. With easy-to-follow steps and helpful tips, you'll be able to bypass your iPhone passcode and get back to using your phone in no time.
Understanding iPhone Security and Passcodes
Before diving into methods of bypassing your passcode, it’s essential to understand why Apple’s security is so stringent. Apple's iOS operating system is built to protect user data from unauthorized access. One of the primary ways iPhones do this is through passcodes, Face ID, and Touch ID. If you enter the wrong passcode multiple times, your iPhone will lock itself for a specific period and eventually disable completely, requiring you to erase and restore the device.
Apple’s security also ensures that once a passcode is set, you cannot change, remove, or reset it without either the passcode itself or authorized access to your iCloud account.
Is It Possible to Bypass Your iPhone Passcode?
Yes, it is possible to bypass your iPhone passcode in this modern world. With advancements in technology, there are now many ways available to regain access to a locked iPhone. Whether you've forgotten your passcode or inherited a locked device, several methods exist that can help you bypass the passcode and unlock the phone. From using official Apple tools to specialized third-party software, you have a range of options depending on your specific situation.
In this article, we are going to explore the top methods to bypass your iPhone passcode with easy steps. These solutions are designed to guide you through the process quickly and efficiently, ensuring you can regain control of your device without unnecessary complications.
How To Bypass Your iPhone Passcode in Easy Steps Using Passixer:
If you're struggling to unlock your iPhone 11 due to a faulty Face ID sensor or a forgotten passcode, Passixer iPhone Unlocker offers a reliable solution. This tool is specifically designed to bypass various types of screen locks, including 4-digit or 6-digit passcodes, Face ID, and Touch ID. Additionally, Passixer enables the removal of Apple ID, Screen Time restrictions, iCloud activation locks, and MDM (Mobile Device Management) locks. Even if your iPhone's screen is broken, unresponsive, or disabled, this software can help you regain access without needing the passcode.
Compatible with all iOS versions, including iOS 17, Passixer iPhone Unlocker is easy to use, making it an ideal tool for bypassing iPhone passcodes without any technical knowledge. Below, we will outline its features, provide a detailed step-by-step guide, and list its advantages and drawbacks.
Key Features:
Unlock iPhone/iPad Screen Passcode:
Passixer can bypass any type of lock on your iPhone or iPad, whether it’s a forgotten 4-digit or 6-digit passcode, or an issue with Face ID or Touch ID. This tool allows you to bypass the lock without relying on iTunes or iCloud, making it particularly helpful when your device becomes disabled after repeated incorrect passcode attempts.
Remove Apple ID Without a Password:
If you’ve forgotten the password to an old Apple ID and can’t log out, Passixer lets you remove it completely. After removal, you can sign in with a new Apple ID and access services such as iCloud, iMessage, and FaceTime. This feature is especially useful for second-hand devices or when your Apple ID is disabled.
Bypass iCloud Activation Lock:
Passixer can help bypass iCloud Activation Lock without needing the Apple ID or password. This is perfect for those dealing with second-hand devices that are locked by a previous owner's credentials.
Remove MDM (Mobile Device Management) Lock:
If your iPhone or iPad is restricted by MDM, Passixer allows you to remove the MDM lock without requiring administrator credentials, giving you full control of your device again.
Remove Screen Time Passcode Without Data Loss:
Forgot your Screen Time passcode? Passixer can remove it without erasing any data, restoring full access to your device's features without having to reset the device.
Remove iTunes Backup Encryption:
Forgot the password for your encrypted iTunes backup? Passixer can decrypt the backup, ensuring that your data remains intact.
Compatible with a Wide Range of iOS Devices:
Passixer supports many iPhone, iPad, and iPod models, including the latest iPhone 16 and iOS 18, making it a versatile option for a wide user base.
Cross-Platform Support:
Passixer works seamlessly on both Windows and macOS, providing flexibility no matter your preferred operating system.
How To Use:
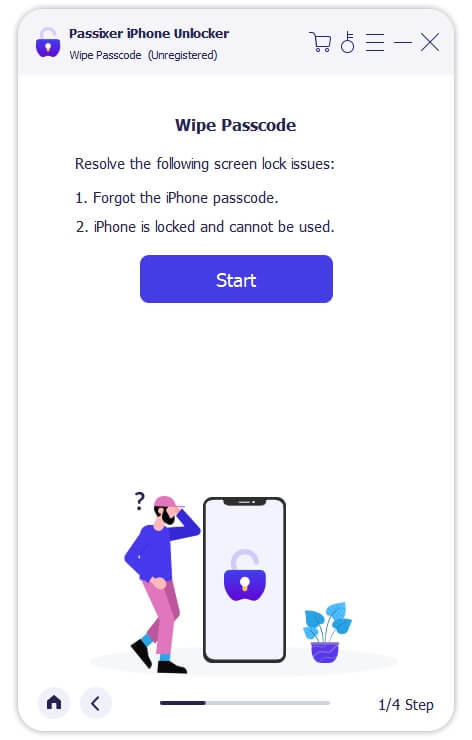
Step 1: Launch Passixer and Select Wipe Passcode
Download and install Passixer iPhone Unlocker on your computer. Launch the app, select "Wipe Passcode," and click "Start."
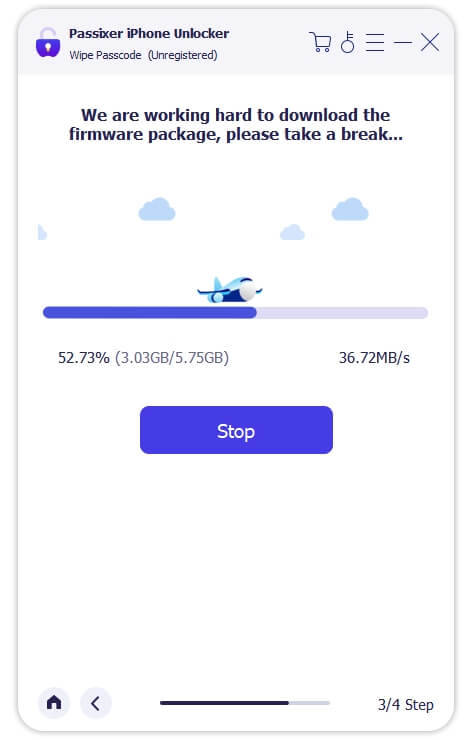
Step 2: Connect Your iPhone to the Computer
Connect your iPhone 11 via USB. Once detected, review your device's info and click "Download" to acquire the necessary firmware.
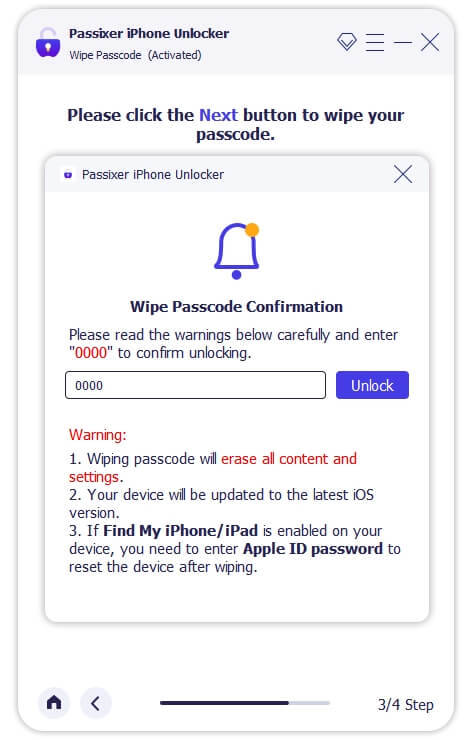
Step 3: Unlock Your iPhone
After downloading the firmware, click "Unlock," then enter "0000" to confirm. Click "Unlock" again and wait for the process to complete. Your iPhone will be unlocked successfully.
Pricing Plans:
Year License: $39.99 (discounted from $59.99, tax excluded). Covers 6 iOS devices and 1 PC.
1-Month License: $29.99 (discounted from $39.99, tax excluded). Suitable for 6 iOS devices and 1 PC.
Lifetime License: $69.99 (tax excluded). Includes coverage for 6 iOS devices and 1 PC, with a one-time payment for lifetime access.
Benefits Of Using Passixer To Bypass Your iPhone Passcode:
Simple and Fast Unlocking: Passixer offers a hassle-free way to bypass your iPhone passcode with an easy-to-use interface. Whether you're locked out due to a forgotten passcode, Face ID malfunction, or issues with Touch ID, Passixer streamlines the process, making it quick and straightforward for anyone to use.
Multiple Unlocking Functions: Passixer does more than just unlock passcodes—it can remove Apple IDs, bypass iCloud activation locks, and disable MDM (Mobile Device Management) restrictions. This makes it a versatile tool for fully regaining access to your device.
Compatible with Various iOS Devices: Supporting a wide range of iPhone, iPad, and iPod models, including the latest iPhone 15 and iOS 17, Passixer ensures its usefulness for both older and newer Apple devices, giving it broad appeal.
No iTunes or iCloud Required: Unlike conventional methods that require syncing with iTunes or iCloud, Passixer operates independently, allowing you to unlock your device without needing access to these services.
Remove Apple ID Without a Password: If you're unable to log into your Apple ID or want to remove an old Apple ID from a second-hand iPhone, Passixer allows you to completely remove the ID, letting you sign in with a new one and restore full device functionality.
Bypass MDM and Screen Time Locks: Passixer can effectively bypass Mobile Device Management (MDM) restrictions and Screen Time passcodes, giving you the freedom to use your iPhone without limitations, especially helpful for school- or company-managed devices.
Available on Windows and macOS: Passixer offers support for both Windows and macOS platforms, making it accessible no matter which operating system you prefer, ensuring flexibility for a wide range of users.
Cost and Time Efficient: Passixer saves you time and money by providing an affordable, at-home solution for unlocking your iPhone, eliminating the need for costly repair services or professional help.
Conclusion:
Forgetting your iPhone passcode can be a frustrating experience, leaving you locked out of your device and unable to access important information. Fortunately, this guide outlines straightforward methods to bypass iPhone passcode restrictions. By following the step-by-step instructions provided, you can regain access to your phone quickly and easily, restoring your ability to use your device without complications.
One of the most effective tools for bypassing iPhone passcodes is Passixer. This software is designed to unlock various types of screen locks, including 4-digit and 6-digit passcodes, as well as Face ID and Touch ID issues. Additionally, Passixer allows you to remove Apple IDs, bypass iCloud activation locks, and disable MDM restrictions, making it a versatile solution for regaining control of your device.
In summary, recovering access to your iPhone after forgetting your passcode is possible and can be done with relative ease. By utilizing tools like Passixer, you can navigate the unlocking process without needing extensive technical knowledge. Don’t let a forgotten passcode keep you from your device; follow the steps in this guide to swiftly regain access and enjoy all the features your iPhone has to offer.
1 note
·
View note
Text
iOS 18.0.1 Jailbreak
If you're looking to unlock the full potential of your iPhone or iPad running iOS 18.0.1, you're in the right place. Jailbreaking your device opens up a world of possibilities, allowing you to install apps and tweaks unavailable on the official App Store. One of the best tools to achieve an iOS 18.0.1 Jailbreak is the InstantJB Tool, which simplifies the process and enables users to download Cydia effortlessly.
What is iOS 18.0.1 Jailbreak?
iOS 18.0.1 Jailbreak refers to removing Apple's software restrictions on devices running iOS 18.0.1. When you jailbreak your iPhone or iPad, you gain complete control over its operating system, allowing you to modify system files, install third-party applications, and customize your device in ways that are impossible with a standard iOS setup.
The main benefit of an iOS 18.0.1 Jailbreak is the ability to download and install Cydia, the go-to platform for downloading apps and tweaks unavailable on the App Store. With Cydia, users can personalize their devices to suit their unique preferences, from changing icons to installing advanced features that enhance their functionality.
Why Jailbreak iOS 18.0.1?
Apple's operating system is highly secure, which is excellent for protecting your data, but it also limits what you can do with your device. Here are a few key reasons why people choose to jailbreak their iPhones and iPads:
Custom Themes: iOS 18.0.1 Jailbreak allows you to apply custom themes that completely change the look of your device. You can replace the standard icons with your designs or download custom themes from Cydia.
Exclusive Apps: Jailbreaking enables you to install unavailable apps in the official App Store. These apps can add new features to your device that Apple's restrictions would typically block.
System Tweaks: From changing how your lock screen looks to adding new functionality to your control center, iOS 18.0.1 Jailbreak gives you complete control over your device's interface.
Removing Bloatware: Apple pre-installs apps that you may never use. Jailbreaking allows you to remove unwanted apps and free up storage space on your device.
iOS 18.0.1 Jailbreak: Is It Safe?
Jailbreaking has come a long way in terms of safety. The process used to be complex, but thanks to tools like InstantJB, it's now straightforward and safe. However, there are still risks involved. Here are a few considerations:
Security Risks: When you jailbreak your device, you bypass some of Apple's security features. This can make your device more vulnerable to malware or other security threats. Always download trusted tweaks and apps from reputable sources like Cydia.
Warranty: Jailbreaking your device can void your warranty. However, the jailbreak process is reversible. You can restore your device to its original state by updating it through iTunes or Finder, which reinstalls Apple's original software and removes the Jailbreak.
System Stability: Some users report that jailbreaking can cause their devices to run slower or encounter bugs. It's essential to install only the tweaks and apps that are necessary to avoid overloading the system.
How to Jailbreak iOS 18.0.1 with InstantJB
The InstantJB Tool is one of the easiest and most reliable ways to perform an iOS 18.0.1 Jailbreak. Here's a step-by-step guide on how you can jailbreak your device and download Cydia using InstantJB:
Backup Your Device: Before you begin, it's always a good idea to back up your device using iCloud or iTunes. This ensures that your data is safe in case something goes wrong during the process.
Visit the Official InstantJB Website: Head to the official InstantJB website at https://www.instantjb.com/cydia-ios-18-1-2-3-4-5-6-7-8-9-jailbreak.html. This is where you'll find the latest version of the tool for iOS 18.0.1 Jailbreak.
Download InstantJB: Follow the instructions on the website to download the InstantJB Tool. The process is simple and doesn't require any technical knowledge.
Install InstantJB on Your Device: Once downloaded, you can install the tool on your iPhone or iPad. InstantJB is compatible with a wide range of iOS devices, so this tool should work seamlessly whether you're using the latest iPhone or an older model.
Run the Jailbreak Process: After installing InstantJB, follow the on-screen instructions to start the jailbreak process. The tool will automatically take you through the steps needed to complete the iOS 18.0.1 Jailbreak.
Download Cydia: Once your device is successfully jailbroken, the InstantJB Tool will allow you to download and install Cydia. Cydia will open the door to thousands of third-party apps, tweaks, and themes.

The Benefits of Using InstantJB for iOS 18.0.1 Jailbreak
InstantJB is one of the most reliable tools for jailbreaking iOS 18.0.1. Here are some reasons why InstantJB is a top choice:
User-Friendly: The interface is simple and straightforward, making it easy for first-time jailbreakers to use.
Regular Updates: InstantJB is consistently updated to ensure it works with the latest iOS versions, including iOS 18.0.1. You don't have to worry about compatibility issues.
Safe and Reliable: InstantJB is trusted by thousands of users worldwide. The tool has been tested extensively to ensure it is safe and reliable.
Cydia Installation: One of the best features of InstantJB is that it automatically installs Cydia after the jailbreak process. This means you don't need to go through additional steps to enjoy the benefits of a jailbroken device.
What to Do After Jailbreaking iOS 18.0.1
The possibilities are endless once you've jailbroken your device using InstantJB and installed Cydia. Here are some things you can do to make the most out of your iOS 18.0.1 Jailbreak:
Install Custom Themes: Personalize your device by installing custom themes from Cydia. You can change the icons, wallpapers, and even the overall appearance of your iPhone or iPad.
Add New Features: Many tweaks available on Cydia allow you to add new features to your device, such as multitasking enhancements, battery-saving tweaks, and much more.
Improve Performance: Jailbreaking can also help improve the performance of your device. For example, you can install tweaks that free up RAM, reduce battery drain, and enhance the speed of your iPhone or iPad.
Explore Third-Party Apps: The App Store has limitations on what developers can offer, but Cydia does not. You'll find apps that provide a wide range of functionality, from file management to advanced photo editing tools.
Final Thoughts on iOS 18.0.1 Jailbreak
The iOS 18.0.1 Jailbreak opens up a new world of customization and control for your device. Whether you're looking to apply custom themes, download exclusive apps, or improve system performance, jailbreaking is the key to unlocking these features. With tools like InstantJB, the process has become more straightforward and safer.
0 notes
Text
How to Remove Activation Lock on iPhone/iPad Without Previous Owner
Are you struggling to remove the activation lock of the iPhone that you just bought from someone? Such a scenario is enough to kill your mood, but how’d one fix this issue? It’s worth mentioning that an activation lock is meant to safeguard an Apple device from unauthorized access. However, buying a used Apple device still linked to its previous owner can be frustrating. We get it; reaching out to the previous owner might feel bothersome. Therefore, we are going to discuss ways in which you can remove the activation lock without the prior owner’s intervention. Excited enough? Let us walk you through removing the activation lock without the previous owner. Part 1: Is Removing an Activation Lock Possible Without a Previous Owner? In short, the answer is yes, you can! But it’s not as simple as it sounds. However, you don’t have to worry about it that much because we are here to help! Activation Lock works with an iCloud account and can only be wiped out in particular conditions. Apple has extreme measures to ensure that devices that have been stolen cannot be used again by the thief, but if you don’t have access to the previous owner’s credentials, then you can unlock the phone. The most effective ones are contacting Apple Support, using DNS bypass methods, and using dedicated software like iToolab UnlockGo iPhone Unlocker. Part 2: How to Remove Activation Lock Without Previous Owner? Now that we know how to remove the Activation Lock without the previous owner is possible, let’s dive into some practical solutions. Way 1. Contact Apple Support The most legal way of unlocking your iPhone or iPad is by contacting Apple support. In most cases, Apple demands proof of ownership to help you remove Activation Lock, yet there are times they may help, including if you bought the phone second-hand or inherited it. Here is how you can do it: First, open the Apple Support page and explain your situation to them. There are times that the support team will require you to provide them with your purchase receipt, and at times, this is not easy, especially if you do not keep your receipt. What is essential here is to find out if Apple can remove the Activation Lock without any form of the purchase invoice. The answer to the question depends on your case and the company's policies. Some people said they could unlock it when they gave details, while others did not without proof. Way 2. Remove Activation Lock Using DNS Bypass The DNS bypass method is a free workaround to remove the Activation Lock without a previous owner. It doesn’t permanently unlock your device; it allows limited use, such as browsing the internet, using apps, and accessing limited settings. Here’s how you can do it: Restart your iPhone and choose the language and the country of your locality. Go to the Wi-Fi menu, ensure you do not input the password, and click on the small “i” icon next to the network you want to connect to. Clear the existing DNS and enter the following DNS based on your location: - USA: 104. 154. 51. 7 - Europe: 104. 155. 28. 90 - Asia: 104. 155. 220. 58 Once you have entered these details, returning to the input screen and connecting to the network would be advisable. However, if the device fails to turn on, press the ‘back’ button to go to the Wi-Fi page, where another link allows the device to work without full activation. This method, however, is not a perfect remedy; it can be helpful when you have to use some of the functions on the given iCloud without having the original iCloud login data. But you must remember here that it is just a temporary fix; thus, you may have to get a permanent one. Way 3. Using the iCloud Lock Removal Tool The third way is the use of the iCloud lock removal tool. If you are searching for a professional and suitable tool to unlock your iPhone or iPad permanently, consider iToolab UnlockGo iPhone Unlocker. This tool was developed for users who want to remove the iCloud Activation Lock without a password or a previous owner. Main Features of iToolab UnlockGo: It’s compatible with iPhone/iPad/iPod models running iOS/iPadOS 12.0-16.7. The tool is easy to use. With the on-screen instructions, you can unlock your device within five steps. Ecolab is a professional team. Therefore, the tool guarantees a high success rate of up to 99%. After removal, you can log into a new Apple ID to enjoy services. If you can’t find proof of purchase, iToolab UnlockGo is your best choice. You can install it on your Windows or Mac computer. Steps to Remove Activation Lock Using iToolab UnlockGo: Head over to the official website of iToolab and ensure you have installed the iToolab UnlockGo program on your Windows or Mac computer. Step 1: go to the main interface and choose “Unlock iCloud Activation Lock”. After that, click the “Start” button. Connect your device to the computer using a USB cable. Step 2: The tool will begin downloading the necessary firmware. This process may take a few minutes, depending on your internet speed. Step 3 Once the firmware download is complete, click “Remove Now.” Your device will automatically enter Recovery mode. You’ll then need to switch to DFU mode to continue. Step 4 After entering DFU mode, the tool will automatically begin jailbreaking. Step 5 To remove Activation Lock, you must reenter your iPhone into DFU mode. The tool will then unlock your device, which should take a minute or two. Part 3: How to Avoid Scams When You Remove Activation Lock As the popularity of the services rose, several fake websites, filled with disreputable services, stated that they would unlock a device. Unfortunately, most of these services are scams, and what they do is either take your money and produce no results or they get your details for malicious intent. Here’s how to protect yourself: Steer clear from the sites that promise to remove the iCloud lock without a previous owner. Such online services carry no assurance that the particular party will enjoy excellent results. Do not give your IMEI or serial number to organizations or people. Choose only the best tools, such as iToolab UnlockGo, which don’t disappoint and have a high success rate and support. People employ various methods to try and remove the Activation Lock, so it is always recommended to be cautious when using these methods for your safety. Your money and personal information can be lost from scams, so it is essential not to fall for them. Conclusion Removing the Activation Lock without the previous owner’s credentials can feel challenging but doable. Whether you contact Apple Support, attempt a DNS bypass, or use a trusted tool like iToolab UnlockGo, there are ways to remove the Activation Lock and regain access to your device. However, be cautious—plenty of online scams promise quick fixes but could put your personal information at risk. If you're after a fast, reliable, and secure solution, iToolab UnlockGo is a hassle-free way to unlock your device easily. Give it a try, and return to using your iPhone or iPad quickly! Read the full article
0 notes
Text
SMD Activator pro Bypass icloud for latest iPhones and iPads A12 + iOS17.x supported
Software Summary: SMD Activator Pro Bypass iCloud Name: SMD Activator Pro Function: Bypass iCloud activation lock for the latest Apple devices Supported Devices: iPhones and iPads with A12 chips and newer Supported iOS Version: iOS 17.xDOWNLOAD SMD PRO v1.1 Key Features: iCloud Bypass: Allows users to bypass the iCloud activation lock, making devices usable again. Compatibility: Supports…
0 notes
Text
Hack Someones Phone Without Them Knowing

In today’s digital age, the thought of someone hacking into your phone can be unsettling. With an ever-growing reliance on smartphones for both personal and professional use, the security of these devices is of paramount importance. This blog aims to demystify the concepts of hacking someone’s phone, outline the possible methods used by hackers, and provide essential tips for safeguarding your phone.
What is Phone Hacking?
Phone hacking refers to any method used to gain unauthorized access to a phone’s data and functions. This could involve accessing text messages, emails, photos, or even remotely controlling the device. Hackers use various techniques to achieve this, exploiting vulnerabilities in the phone’s software or deceiving users into revealing sensitive information.
Common Methods of Phone Hacking
1. Phishing Attacks
Phishing involves tricking a user into providing personal information by masquerading as a trustworthy entity. Hackers may send emails or text messages that appear to be from legitimate sources, such as banks or social media platforms, prompting the user to click on a link or download an attachment.
2. Malware
Malware, or malicious software, can be installed on a phone without the user’s knowledge. This can occur through downloading infected apps, clicking on suspicious links, or connecting to compromised networks. Once installed, malware can capture keystrokes, record conversations, and even access the phone’s camera and microphone.
3. Man-in-the-Middle Attacks
In a man-in-the-middle attack, a hacker intercepts the communication between two parties. This often occurs on unsecured Wi-Fi networks, where the hacker can eavesdrop on conversations, steal login credentials, and monitor data traffic.
4. Exploiting Software Vulnerabilities
Hackers often look for bugs or vulnerabilities in a phone’s operating system or installed apps. When these vulnerabilities are discovered, they can be exploited to gain unauthorized access to the device.
5. Social Engineering
Social engineering involves manipulating individuals into divulging confidential information. This could be through impersonation, deception, or exploiting human psychology. For example, a hacker might pose as a tech support agent to convince a user to reveal their password.
How Can Someone Hack My iPhone?
Despite Apple’s robust security measures, iPhones are not immune to hacking. Here are some ways someone might attempt to hack an iPhone:
1. iCloud Credentials
If a hacker obtains your iCloud credentials, they can access your data stored in the cloud. This includes photos, emails, contacts, and even your device’s backup.
2. Spyware
Spyware can be installed on an iPhone if the device is jailbroken or through sophisticated phishing attacks. This software can track your location, read messages, and monitor your online activity.
3. Public Wi-Fi Networks
Connecting to unsecured public Wi-Fi networks can expose your iPhone to man-in-the-middle attacks. Hackers can intercept data being transmitted over the network and gain access to your personal information.
4. Siri Exploits
There have been instances where Siri could be exploited to bypass the lock screen. While Apple regularly patches such vulnerabilities, it’s essential to keep your device updated with the latest software.
How to Get Into Someone’s iPhone Without the Password
Gaining unauthorized access to someone’s iPhone without their password is illegal and unethical. However, understanding how it might be done can help you better protect your device.
1. Brute Force Attacks
In a brute force attack, a hacker uses software to guess the password by trying various combinations until the correct one is found. Apple’s security measures, such as the increasing delay between failed attempts and data wipes after ten incorrect tries, make this method less effective.
2. Exploiting Security Vulnerabilities
Hackers may exploit security flaws in the iOS operating system to bypass the lock screen. Keeping your device updated with the latest security patches can mitigate this risk.
3. Social Engineering
As mentioned earlier, social engineering can trick a user into revealing their password. Hackers might pose as tech support or use other deceptive tactics to gain access.
How to Access Someone’s WhatsApp
Accessing someone’s WhatsApp messages without their consent is a violation of privacy and illegal. However, it’s important to know how it might be done to prevent unauthorized access to your account.
1. WhatsApp Web
If someone gains physical access to your phone, they can set up WhatsApp Web on their computer by scanning the QR code with your phone. This allows them to read and send messages from your account.
2. Spyware
Installing spyware on a phone can give a hacker access to WhatsApp messages. This can be done through phishing attacks or by tricking the user into installing malicious software.
3. SIM Swap Attacks
In a SIM swap attack, a hacker convinces your mobile carrier to transfer your phone number to a SIM card in their possession. This allows them to receive your WhatsApp verification code and gain access to your account.
How to Access Someone’s Phone Remotely
Remote access to a phone can be achieved through various means, but it is generally illegal without the owner’s consent.
1. Remote Access Tools (RATs)
RATs are a type of malware that allows hackers to control a device remotely. These tools can be installed through phishing attacks or by exploiting software vulnerabilities.
2. Cloud Services
If a hacker gains access to your cloud service credentials (such as iCloud or Google Drive), they can remotely access your data, including backups of your phone.
3. Bluetooth Vulnerabilities
Exploiting vulnerabilities in Bluetooth can allow a hacker to connect to your phone without your knowledge. Ensure your Bluetooth is turned off when not in use and keep your device updated with the latest security patches.
Is it Possible for Someone to Hack Your Phone?
Yes, it is possible for someone to hack your phone, but it requires considerable effort and resources. Understanding the methods used by hackers can help you protect your device.
1. Security Best Practices
Adopting security best practices can significantly reduce the risk of your phone being hacked. These include using strong passwords, enabling two-factor authentication, keeping your software updated, and being cautious of suspicious emails and messages.
2. Awareness
Being aware of the potential threats and staying informed about the latest security trends can help you identify and avoid potential hacking attempts.
How to Hack Someone’s Phone Texts
Accessing someone’s text messages without their consent is illegal. However, it’s important to know how it might be done to protect your own messages.
1. Spyware
Spyware can be installed on a phone to monitor text messages. This software can capture and relay text message content to the hacker.
2. SIM Swap Attacks
As mentioned earlier, SIM swap attacks can give a hacker access to your phone number and text messages.
3. Phishing Attacks
Phishing attacks can trick users into revealing their login credentials or installing malicious software that captures text messages.
How to Hack into a Boyfriend’s Phone
Hacking into someone’s phone without their consent is a breach of trust and illegal. Open communication and trust are the foundation of any healthy relationship. If you have concerns about your boyfriend's activities, it’s best to address them directly rather than resorting to unethical methods.
Hacking a Phone Without Physical Access
Hacking a phone without physical access is more challenging but still possible through remote methods.
1. Phishing Attacks
Phishing remains one of the most effective ways to gain remote access. A hacker can control the device remotely by tricking the user into revealing sensitive information or installing malware.
2. Remote Access Tools (RATs)
RATs can be installed through phishing or by exploiting software vulnerabilities, allowing a hacker to control the phone from a distance.
3. Cloud Services
Access to the victim’s cloud service credentials can provide remote access to their phone’s data.
Conclusion
Phone hacking is a serious concern in our increasingly connected world. Understanding the methods used by hackers and taking proactive steps to secure your device can help protect your personal information. Always prioritize your privacy and security by adopting best practices and staying informed about the latest threats. Remember, hacking into someone’s phone without their consent is illegal and unethical. Instead, focus on protecting your own device and maintaining healthy, trust-based relationships.
1 note
·
View note
Text
10 Best iCloud Activation Lock Removal Tools
Have you forgotten your Apple ID and got stuck on the iCloud activation lock? Have you ever bought a second-hand iPhone that was locked by the previous owner? Or not being able to access your iPhone due to Lost Mode? These can definitely discourage someone who is not professional in fixing an iPhone. It could be time-wasting and a low success rate in finding help from Apple. So, can we bypass the iCloud activation lock by ourselves?
In this article, we explore the possibility of unlocking your iCloud activation lock by yourself and provide you with 10 of the best iCloud activation lock removal software.
0 notes
Text
iOS 17.5 Jailbreak
Are you looking to unlock the full potential of your iPhone or iPad with the latest iOS 17.5 update? Jailbreaking your device can open up a world of customization and enhanced control, allowing you to install apps and tweaks that aren’t available in the official App Store. This guide will walk you through jailbreaking iOS 17.5, offering step-by-step instructions and important considerations to remember.
Understanding Jailbreak
Jailbreaking is removing the restrictions imposed by Apple on devices running the iOS operating system. Through this process, users gain root access to the operating system, allowing them to install additional applications, extensions, and themes unavailable through the official Apple App Store.
Benefits of Jailbreaking
Customization: Jailbreaking allows you to customize everything from the control center to the icons on your home screen.
Extended Functionality: Users can install apps that enhance device functionality, such as better app managers and additional settings shortcuts.
Access to Tweaks and Apps: Jailbreaking provides access to a vast library of tweaks and apps that can dramatically change your user experience.
Pre-Jailbreak Considerations
Before you proceed with jailbreaking your iOS 17.5 device, there are several important factors to consider:
Warranty and Support: Jailbreaking may void your warranty with Apple, and you might not receive support in case of software issues.
Security Risks: Jailbreaking can expose your device to vulnerabilities as you bypass certain Apple protections.
Device Stability: Some jailbreak apps can cause the device to behave unpredictably or crash.

How to Jailbreak iOS 17.5
Jailbreaking iOS 17.5 can be straightforward if you follow these steps carefully. Here’s how you can jailbreak your device:
Backup Your Device: Always start by backing up your device using iCloud or your computer. This ensures your data is safe if anything goes wrong during the Jailbreak.
Visit the Jailbreak Website: Navigate to https://www.instantjb.com/cydia-ios-17-1-2-3-4-5-6-7-8-9-jailbreak.html, which provides a reliable tool for jailbreaking iOS versions up to 17.5.
Download the Jailbreak Tool: Download the appropriate jailbreak tool for iOS 17.5 from the website. Download the tool from a reliable source to avoid any security risks.
Run the Jailbreak Tool: Connect your device to your computer, open the downloaded file, and start the jailbreak process. The tool will guide you through breaking the operating system’s restrictions.
Install Cydia: After jailbreaking, install Cydia, a popular app store for jailbroken devices. Cydia lets you download and install unavailable software through the official App Store.
Enjoy Your Jailbroken Device: Once Cydia is installed, you can explore various apps and tweaks to customize your device.
After Jailbreaking
Once your device is jailbroken, keep these tips in mind to ensure a smooth experience:
Be Cautious with Tweaks: Not all tweaks are stable; some can cause your device to crash or behave erratically. Always research tweaks and read user reviews before installing.
Stay Informed: Keep updated with the latest news in the jailbreaking community to learn about updates, security patches, and new tweaks.
Avoid iOS Updates: Installing iOS updates from Apple after jailbreaking can remove the Jailbreak and the installed tweaks.
Conclusion
Jailbreaking your iOS 17.5 device can significantly enhance its functionality and allow you to customize it far beyond what is officially available. By following the guidelines above and taking appropriate precautions, you can enjoy the benefits of a jailbroken device while minimizing potential risks. Happy jailbreaking!
0 notes
Text
iOS 17.6.1 bypass iCloud 2024 Pro (2nd), 6th Software With Free Crack
Remove Activation Lock Restriction on All Scenarios Forgot Apple ID password and have no access to Email? Or did you buy a second-hand iOS 17.6.1 bypass iCloud 2024 Pro (2nd), 6th Software With Free Crack device with locked iCloud? 4MeKey can offer you the best iCloud unlock service to Bypass Activation Lock in all. Unlock Carriers uses the permanent Official Unlock, available for iPhone 15 Pro…

View On WordPress
0 notes
Text
Mac Password Removal: Hassle-Free Access to Locked Devices
Apple’s Mac computers are renowned for their security features, with password protection being one of the primary ways to secure user data. However, there are times when users may forget their password, find themselves locked out of their MacBook, or inherit a secondhand device with a password they don’t know. When this happens, Mac password removal services can be the solution, providing hassle-free access to locked devices without the frustration of data loss.
Mac Password Protection
Password protection on a Mac is an essential feature designed to protect sensitive data from unauthorized access. Whether it’s an Apple ID password for iCloud or the local system password for logging into the Mac, these security measures ensure that personal files, banking information, and other sensitive content are kept safe.
When users set a password, it encrypts their files and prevents anyone from accessing the device without entering the correct credentials. Unfortunately, in some cases, passwords can be forgotten, misplaced, or inaccessible, leading to the need for Mac password removal.
Common Scenarios That Require Mac Password Removal
While Mac password protection is essential, there are a few common situations in which a user might find themselves locked out of their device. Here are some typical scenarios where password removal services become necessary:
1. Forgotten User Password
One of the most common reasons people need Mac password removal is simply forgetting their user password. It’s easy to forget passwords, especially if you have multiple devices or passwords for various services. A forgotten Mac password can lock users out of their own device, preventing them from accessing important files, applications, and settings.
2. Password Change or Miscommunication
In the case of shared devices or family-owned Macs, passwords can be changed without the user’s knowledge. This could also occur if a password was set by someone else, such as a former employee or a friend, and the user no longer has access to it.
3. Secondhand Mac Devices
Buying a secondhand MacBook can be a great way to save money, but sometimes, these devices are still locked with a password set by the previous owner. This is especially problematic when the previous owner has forgotten or neglected to remove the password before selling or giving away the device.
4. iCloud Account Lock
Another common issue arises when users forget the Apple ID or iCloud password linked to their Mac. This can prevent access to the system or lead to issues with iCloud features like Find My Mac, data syncing, and app store downloads. Apple’s security measures make it difficult to bypass iCloud locks without proper credentials.
5. Hardware Malfunctions
In some cases, Mac password-related issues may arise due to software corruption, a failed system update, or hardware malfunctions that prevent users from logging in. In these cases, password removal may be part of a larger repair or system recovery process.
How Professional Mac Password Removal Services Work
If you find yourself locked out of your Mac, professional password removal services can help you regain access quickly and safely. The process usually involves specialized tools and techniques that ensure you don’t lose data in the process. Here’s an overview of how professional services generally work:
1. Initial Assessment
When you bring your Mac to a professional repair service, the technician will first assess the situation. They will identify the type of password issue you’re facing, whether it’s a forgotten user password, an iCloud lock, or another problem. Depending on the severity of the issue, the technician will determine the best course of action.
2. Data Backup (If Possible)
Before proceeding with password removal, reputable repair services will often back up any accessible data on the device. This is an important step in case the removal process involves erasing the device’s contents. This ensures that no valuable files, documents, or media are lost during the process.
3. Password Removal or Reset
Once the technician has evaluated the device and backed up the data, they will proceed with the password removal or reset. There are various methods for this process:
Password Reset Tools: If the MacBook is running macOS, a technician can use specialized tools to bypass or reset the password, allowing the user to regain access without deleting files.
Apple ID Recovery: If the issue is related to iCloud or Apple ID, technicians can assist in recovering the Apple ID credentials through Apple’s account recovery process. This often involves verifying the identity of the user before unlocking the device.
Reinstalling macOS: In some cases, where all else fails, the technician may reinstall macOS, which will effectively remove any password and restore the device to its factory settings. Although this method may result in data loss, it is sometimes the only viable option when other methods don’t work.
4. Verification and Testing
After the password has been removed or reset, the technician will test the Mac to ensure that it boots up correctly and that all features are functioning as expected. The device will be fully tested to ensure it is accessible and ready to use once again.
5. Providing New Password Setup
Once the device is unlocked, the technician may assist the user in setting up a new password or passcode to secure their device moving forward. They may also recommend setting up security questions or enabling two-factor authentication for added protection.
Why Choose Professional Mac Password Removal Services?
While there are DIY methods available online for removing Mac passwords, they often come with risks. Using unverified tools can damage your MacBook, result in data loss, or even cause additional security vulnerabilities. Here's why professional services are the best choice for password removal:
1. Expertise and Experience
Certified technicians who specialize in MacBook repairs and password recovery know the ins and outs of Apple devices. They have the knowledge and tools to safely remove passwords without damaging the system or compromising security.
2. Safe and Secure
Professional password removal services ensure your data is safe. Reputable services use secure methods that protect your privacy and ensure no data is lost unless absolutely necessary.
3. Preserving Warranty
Attempting password removal using third-party software or DIY methods may void your warranty or damage the device further. Professional services are more likely to preserve your warranty and ensure the device is repaired without compromising its integrity.
4. Time-Saving
Password removal can be a time-consuming process if attempted on your own. Professional technicians can complete the task quickly and efficiently, allowing you to get back to using your MacBook without prolonged downtime.
Whether you’ve forgotten your password, are dealing with a secondhand device, or need to regain access due to a malfunction, Mac password removal services provide a reliable solution for unlocking your device. These services are fast, secure, and professional, ensuring that you regain full access to your MacBook without the risk of data loss or further complications.
By choosing a trusted service provider, you can rest assured that your MacBook will be restored to full functionality quickly, allowing you to get back to your tasks without delay. Always choose a certified and reputable repair center to ensure that the password removal process is done correctly and securely.
#MacBook Repair Calgary#Apple MacBook Services#MacBook Screen Fix#MacBook Battery Replacement#MacBook Keyboard Repair#MacBook Water Damage#MacBook Logic Board Repair#MacBook Performance Boost#Affordable MacBook Repair#MacBook Software Support
0 notes
Text
does icloud private relay work like a vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does icloud private relay work like a vpn
iCloud Private Relay Encryption
iCloud Private Relay Encryption is a cutting-edge technology introduced by Apple to enhance the privacy and security of its users. This feature is designed to protect the data that users send and receive over the internet, preventing it from being intercepted or tracked by malicious third parties.
The encryption process begins when a user activates Private Relay on their device. When the user browses the internet, the feature encrypts their traffic and sends it through two separate internet relays. The first relay assigns the user an anonymous IP address, while the second relay decrypts the traffic and sends it to its destination. This dual-layered approach ensures that no single entity can access both the user's IP address and the website they are visiting, enhancing privacy and security.
Moreover, iCloud Private Relay doesn't just encrypt web browsing traffic – it also encrypts all internet traffic, including emails, messages, and app data. This comprehensive protection ensures that users can safely access online services without worrying about their personal information being exposed.
Overall, iCloud Private Relay Encryption is a powerful tool that provides an additional layer of security for Apple users. By encrypting and routing internet traffic through multiple relays, this feature effectively shields user data from prying eyes and potential threats. With privacy and security becoming increasingly important in today's digital age, iCloud Private Relay Encryption sets a high standard for safeguarding user information online.
VPN vs iCloud Private Relay
In the digital age, privacy and security have become paramount concerns for internet users. With the proliferation of online threats and the increasing scrutiny of personal data by both hackers and corporations, individuals are seeking ways to safeguard their online activities. Two popular tools for enhancing online privacy are VPNs (Virtual Private Networks) and iCloud Private Relay. While both aim to protect user data, they operate in slightly different ways and offer distinct advantages.
VPN, or Virtual Private Network, routes your internet connection through a remote server, encrypting your data and masking your IP address. This helps to shield your online activities from prying eyes, whether it's your internet service provider (ISP), government agencies, or hackers. VPNs are commonly used for accessing geo-blocked content, bypassing censorship, and securing public Wi-Fi connections.
On the other hand, iCloud Private Relay is a feature introduced by Apple that works within the Safari browser. It encrypts the web traffic leaving your device and sends it through two separate relays, making it more difficult for anyone, including Apple, to track your browsing habits. Unlike a VPN, iCloud Private Relay is built into the operating system of Apple devices, providing seamless integration and ease of use for users within the Apple ecosystem.
While both VPNs and iCloud Private Relay offer privacy benefits, they have different strengths and weaknesses. VPNs are more versatile, allowing users to protect all internet traffic on any device, while iCloud Private Relay is limited to Safari browsing on Apple devices. However, iCloud Private Relay may be more convenient for users already invested in the Apple ecosystem, providing an extra layer of privacy without the need for third-party software. Ultimately, the choice between VPN and iCloud Private Relay depends on individual preferences and the level of privacy and security desired.
iCloud Private Relay Data Protection
iCloud Private Relay is a revolutionary feature introduced by Apple that aims to enhance data protection and privacy for users of its ecosystem. This feature is designed to encrypt all internet traffic leaving a device and then route that traffic through two separate internet relays, making it virtually impossible for anyone, including Apple, to track or intercept the data.
One of the key aspects of iCloud Private Relay is its emphasis on user privacy. By encrypting internet traffic and routing it through multiple relays, Apple ensures that even if someone were to intercept the data, they would only see encrypted information that is virtually impossible to decipher. This is particularly important in an age where online privacy concerns are at an all-time high, with hackers and data thieves constantly looking for ways to access sensitive information.
Additionally, iCloud Private Relay helps protect user data by preventing websites and online services from tracking users across the web. By obscuring IP addresses and other identifying information, Private Relay makes it much more difficult for advertisers and other third parties to build detailed profiles of users based on their online activities.
Moreover, iCloud Private Relay is seamlessly integrated into the Apple ecosystem, providing users with a simple and convenient way to enhance their privacy without sacrificing usability. With just a few clicks, users can enable Private Relay on their devices and enjoy enhanced data protection without having to worry about complicated settings or configurations.
In conclusion, iCloud Private Relay represents a significant step forward in data protection and privacy for Apple users. By encrypting and anonymizing internet traffic, this feature helps safeguard user privacy and security in an increasingly connected world.
Secure Browsing with iCloud Private Relay
iCloud Private Relay is a privacy feature that offers users a secure browsing experience by encrypting their internet traffic and routing it through two separate relays. This innovative technology helps protect user privacy by ensuring that no single entity, including Apple, can see both the user's IP address and the websites they visit. By using iCloud Private Relay, users can browse anonymously with peace of mind, knowing that their online activities are shielded from prying eyes.
One key benefit of iCloud Private Relay is its ability to prevent third parties from tracking users' online behavior and building profiles based on their browsing habits. This feature adds an extra layer of security, particularly when using unsecured public Wi-Fi networks where cyber threats are more prevalent. Moreover, iCloud Private Relay enhances user confidentiality by masking their IP addresses and location information, thereby reducing the risk of targeted ads and location-based tracking.
Another advantage of iCloud Private Relay is its seamless integration with Safari, Apple's web browser. Users can enable Private Relay with a simple toggle switch in Safari settings, allowing for hassle-free activation of this privacy-enhancing feature. Additionally, iCloud Private Relay does not log user activity, ensuring that sensitive information remains private and secure.
Overall, iCloud Private Relay is a valuable tool for individuals seeking to safeguard their online privacy and protect their personal data from potential threats. By encrypting internet traffic and concealing user IP addresses, this feature offers a peace of mind and a safer browsing experience in today's increasingly interconnected digital world.
iCloud Private Relay Privacy Features
iCloud Private Relay is a groundbreaking privacy feature introduced by Apple, designed to enhance users' online security and privacy. This feature works by encrypting internet traffic leaving a user's device and routing it through two separate internet relays, effectively masking the user's IP address and preventing third parties from tracking their online activities.
One of the key benefits of iCloud Private Relay is its ability to protect users' privacy while browsing the web. By encrypting internet traffic and routing it through relay servers, iCloud Private Relay prevents internet service providers, advertisers, and other third parties from tracking users' online behavior and gathering personal information without their consent.
Furthermore, iCloud Private Relay enhances security by preventing attackers from intercepting and accessing sensitive information transmitted over unsecured networks. With end-to-end encryption and relay servers that strip identifying information from internet traffic, iCloud Private Relay helps safeguard users' data against interception and unauthorized access.
Another important aspect of iCloud Private Relay is its commitment to user privacy. Unlike traditional VPN services that may log users' browsing history and other sensitive data, iCloud Private Relay does not store any personally identifiable information or browsing history on Apple's servers. This ensures that users can browse the web with confidence, knowing that their privacy is protected at all times.
In conclusion, iCloud Private Relay offers a comprehensive solution for users who value their online privacy and security. By encrypting internet traffic, masking IP addresses, and preventing tracking, iCloud Private Relay helps users browse the web anonymously and securely, without compromising their privacy.
0 notes
Text
does private relay work like a vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does private relay work like a vpn
Private Relay vs VPN
Private Relay and VPNs (Virtual Private Networks) are two popular tools used to enhance online privacy and security, but they operate in different ways and offer distinct features.
Private Relay is a privacy feature introduced by Apple, designed to enhance user privacy by obscuring their IP address and encrypting their internet traffic. It works by routing internet traffic through two separate relays, similar to a VPN, but with some notable differences. Private Relay encrypts user data so that even Apple cannot see the websites users visit or the content they access. Additionally, it assigns users a temporary IP address that is not linked to their identity, further protecting their privacy. However, Private Relay is currently only available to users with iCloud+ subscriptions and is limited to Safari browsing.
On the other hand, VPNs have been around for much longer and offer a broader range of features and capabilities. A VPN creates a secure, encrypted connection between the user's device and a remote server operated by the VPN provider. This not only hides the user's IP address but also encrypts all data transmitted over the internet, protecting it from prying eyes. VPNs can be used to bypass geographic restrictions, access region-locked content, and secure connections on public Wi-Fi networks.
While both Private Relay and VPNs aim to enhance privacy and security online, they serve different purposes and cater to different needs. Private Relay is more focused on obscuring user identity and preventing tracking, while VPNs offer a wider array of features such as bypassing censorship and accessing geo-blocked content. Ultimately, the choice between Private Relay and VPN depends on the user's specific requirements and preferences for online privacy and security.
Privacy Protection Methods
Privacy protection methods are crucial in today's digitally-driven world where personal information is constantly at risk of being compromised. With the advancement of technology, there are various effective ways to safeguard your privacy and data.
One of the most basic yet important privacy protection methods is to use strong and unique passwords for all your online accounts. Using a combination of letters, numbers, and special characters can make it harder for hackers to crack your passwords. It is also recommended to enable two-factor authentication whenever possible for an added layer of security.
Another effective method to protect your privacy is to regularly update your software and apps. Developers often release security patches to fix vulnerabilities that could potentially be exploited by cybercriminals. By keeping your devices and software up-to-date, you can reduce the risk of unauthorized access to your personal information.
Encrypting your sensitive data is also a great way to ensure privacy. Encryption converts your data into a code that can only be accessed with the correct key, making it extremely difficult for unauthorized users to decipher. You can use encryption tools or enable encryption features built into your devices or software to secure your data.
Furthermore, being mindful of the information you share online and limiting the amount of personal data you provide on social media platforms can also help protect your privacy. Avoid clicking on suspicious links or emails, and be cautious when sharing personal information with unknown sources.
Overall, implementing these privacy protection methods can significantly reduce the risk of your personal information falling into the wrong hands and help you stay safe in the digital world.
Data Encryption Comparison
In the realm of cybersecurity, data encryption stands as a formidable barrier against unauthorized access and data breaches. It serves as a safeguard for sensitive information, ensuring that only intended recipients can decipher the encoded data. However, not all encryption methods are created equal. Let's delve into a comparison of some popular data encryption techniques:
Symmetric Encryption: This method employs a single key for both encryption and decryption. While it's fast and efficient, the challenge lies in securely sharing the key between parties, as any compromise could lead to data exposure.
Asymmetric Encryption: Also known as public-key encryption, this technique uses a pair of keys - public and private. The public key encrypts the data, while the private key decrypts it. It eliminates the need for key sharing but is computationally more intensive.
Hashing: Unlike encryption, hashing is a one-way process where data is converted into a fixed-size string of characters. While it's useful for verifying data integrity, it's irreversible, making it unsuitable for encrypting sensitive information.
Quantum Encryption: Leveraging the principles of quantum mechanics, this cutting-edge technique offers unparalleled security. It relies on the laws of physics to encrypt data, making it theoretically immune to hacking attempts. However, its practical implementation is still in its infancy and limited to specialized applications.
End-to-End Encryption (E2EE): Widely adopted in messaging apps and communication platforms, E2EE ensures that only the sender and recipient can access the message contents. It prevents intermediaries, including service providers, from intercepting or viewing the data.
In conclusion, choosing the right encryption method depends on various factors such as security requirements, computational resources, and practicality. While each technique has its strengths and limitations, the ultimate goal remains consistent: to protect sensitive data from falling into the wrong hands.
Internet Anonymity Solutions
Internet anonymity solutions are essential for individuals seeking to protect their privacy and security while browsing the web. With the increasing prevalence of data breaches, cyberattacks, and online surveillance, it has become more important than ever to safeguard personal information and online activities from prying eyes.
One of the popular solutions for achieving internet anonymity is using a virtual private network (VPN). A VPN encrypts all internet traffic and routes it through remote servers, masking the user's IP address and location. This helps in preventing third parties, such as hackers or government agencies, from monitoring online activities and tracking user's online behavior. VPNs are widely available and offer varying levels of encryption and server locations to choose from.
Another effective tool for internet anonymity is the Tor browser. Tor stands for "The Onion Router" and works by routing internet traffic through a network of servers to conceal the user's identity and location. This helps in circumventing censorship and surveillance, making it a popular choice for journalists, activists, and individuals in repressive regimes.
Additionally, using secure communication tools like encrypted messaging apps and email services can help in maintaining anonymity while communicating online. Apps like Signal and ProtonMail offer end-to-end encryption, ensuring that only the intended recipients can access the messages.
Overall, internet anonymity solutions play a crucial role in protecting online privacy and security. By utilizing tools like VPNs, Tor browser, and secure communication apps, individuals can safeguard their personal information and browse the internet without compromising their privacy.
Network Security Technologies
Network security technologies are essential in safeguarding sensitive data and ensuring the integrity of computer networks. With the increasing prevalence of cyber threats, organizations of all sizes are recognizing the importance of implementing robust security measures to protect their digital assets.
One of the key network security technologies is firewalls, which act as a barrier between a trusted internal network and untrusted external networks, such as the internet. Firewalls monitor and control incoming and outgoing network traffic based on predetermined security rules, helping to prevent unauthorized access and malicious activities.
Intrusion detection systems (IDS) and intrusion prevention systems (IPS) are another critical component of network security. IDS monitors network traffic for suspicious activity or security policy violations, while IPS proactively blocks or mitigates potential threats based on predefined rules. These technologies work together to identify and respond to security incidents in real-time, helping to minimize the impact of cyber attacks.
Virtual private networks (VPNs) provide a secure way to establish encrypted connections over the internet, allowing users to access a private network remotely. By encrypting data transmissions, VPNs ensure confidentiality and integrity, making it difficult for cybercriminals to intercept sensitive information.
In conclusion, network security technologies play a vital role in protecting organizations against a wide range of cyber threats. By deploying effective solutions such as firewalls, IDS/IPS, and VPNs, businesses can enhance their security posture and minimize the risk of data breaches and unauthorized access. Stay informed and proactive in implementing the latest network security technologies to safeguard your digital assets effectively.
0 notes