#internet tracking software for parents
Explore tagged Tumblr posts
Note
hiii!! this might be a stupid question, but do you have any headcanons on how andre + cal would act online? like would they have their own webpages, and how they would chat and stuff like that :p
also, i love your writing so much <3
Hii!! :3 That’s not a stupid question at all !! And TYSMM IM SO GLAD :D <33 These were fun to make, I hope you like these!
Andre and Cal Online Headcanons,,
Andre’s username on his favorite social/chatting websites is @ak47_0717, while Cal’s is @gunslinger83. The reasoning behind their usernames, first of all, is that Andre’s initials are AK. Because of his unsettling interest in firearms, he’s bound to be interested in one of the most popular guns in the world— the AK-47. He likes having his initials similar to the “AK” in AK-47. The four numbers at the end of his username are his birthday. Cal’s username is pretty self-explanatory; he calls himself a gunslinger, and the ‘83’ at the end of his username is the year he was born.
Andre and Cal talk to each other on AOL, which was one of the most popular online services for internet users at the time. They also chat on MSN Messenger, and they used to communicate on ISQ, which was more popular in their middle school years and early high school years— the late 90s.
With Blogger having been established in 1999, Andre and Calvin created accounts. They follow gun blogs and blogs dedicated to books, movies, and bands they like. Also, Andre follows— although he doesn’t really interact with— the Iroquois Track Team and Science Club blog pages. Cal follows the school band’s page. Despite following different blogs, they don’t really post much on Blogger; they like to stay relatively quiet and unnoticed. Andre does leave hate comments on posts from people he doesn’t like. Since anonymity wasn’t as robust as it would come to be in the mid 2000s— the years following Cal and Andre’s deaths— he made an alt account with a fake name for the sole purpose of hating on the Iroquois Wrestling Team blog page… for obvious reasons having to do with Brad Huff. He also leaves hate comments on Rachel’s posts. Cal mentions this mysterious user to Andre sometimes, mentioning how Rachel talks about how this unknown person on the internet criticizes her posts. Andre plays dumb and acts uninterested, yet he listens intently, replying with soft “Mhm”s, as well as a “Damn, that sucks”. He doesn’t want Cal growing suspicious.
They play girls’ flash games both for the hell of it and for the irony. They get relatively entertained from these online dress-up, salon, and cooking games, with Cal being aware these games are aimed at girls. He intentionally makes his character look ugly and goes into hysterical laughter over it— he absolutely laughs at the stupidest shit. However, Andre actually tries and is surprisingly concentrated on the game, face frozen with stoicism and focus. Andre would never admit it, but with his family having a cat, Mel, he finds pet care flash games to be genuinely fun.
Andre and Cal illegally download music and share it with each other by Napster or by email. They’ve sacrificed their computers for the sake of copying a System of a Down song onto their files for free, instead of physically buying the CD. In 1998, when Andre was still a freshman in high school, he ended up getting the CIH virus (Chernobyl virus) which practically wrecked his software and ruined his computer. Whole Calvin teased him for getting such a destructive virus on his computer, he ended up informing his parents. He’d told them that Andre needed a new computer, and he suggested that they pitch in to help Andre’s parents buy him a new computer for his 16th birthday in the summer. Because for the time being, Andre would have to use Cal’s.
Andre and Cal share similar humor in most areas. And since internet memes were beginning to rise in popularity, the two boys send or email each other dark humor memes and chuckle at them.
If they were alive in 2003, they would have used 4chan !!
Andre uses all types of different acronyms when chatting, such as but not limited to “ROFL”, “LOL”, “LMFAO”, “BRB”, “ILY”, “IDK”, and “BTW”. He often capitalizes the first letter of his messages and types faces like “:-)” and “>:(”.
Cal, too, uses many acronyms online. He also types with no capital letters, and he often takes shortcuts when he’s chatting with Andre. He creates little faces with the keys on his keyboard and copies and pastes special symbols online. When he’s typing to Andre first, his first message is usually a simple, “hi” of some sort.
They both play Doom together, considering how 1993 Doom was multiplayer when it first came out.
GeoCities !! Cal and Andre created their own website for the Army of Two. They didn’t necessarily say much on the site, and they didn’t give the site name to anyone they knew. But they still specified who they were and their interests without giving away their last names.
In addition, Andre and Cal used GeoCities to make a screamer site, and they made different alt emails to troll Brad Huff by sending the link to him, without him finding out who they were.
Sometime during the final week before Zero Day, their last few days of being alive, they’d both typed up a short, lovesick letter in their notepads— two messages they’d always wanted to tell each other but never got the chance to. Cal had gone on a tangent about how much he enjoyed being Andre’s comrade, how much he enjoyed Andre being his. Also, he was saying his goodbyes before their final mission and how he loved Andre and hoped he’d see him on the flip side. Whereas Andre was saying how he was looking forward to escaping the school with Cal and how he hoped they’d have a better life together, even while they were wanted from the cops. He mentioned how he loved Cal, too, but with his own phrasing of that declaration. But that ended up being an unrealistic expectation on Andre’s end.
#zero day#andre kriegman#cal gabriel#calvin gabriel#zero day 2003#zero day movie#caldre#calvin and andre#andre and cal#cal and andre#ben coccio#andre keuck#calvin robertson#cal robertson#calvin zero day#cal zero day#zero day cal#andre zero day#zero day andre#zero day headcanons#zd#zd 2003#zdblr
79 notes
·
View notes
Text
Why is this Canadian university scared of you seeing its Privacy Impact Assessment?

I'm coming to DEFCON! On Aug 9, I'm emceeing the EFF POKER TOURNAMENT (noon at the Horseshoe Poker Room), and appearing on the BRICKED AND ABANDONED panel (5PM, LVCC - L1 - HW1–11–01). On Aug 10, I'm giving a keynote called "DISENSHITTIFY OR DIE! How hackers can seize the means of computation and build a new, good internet that is hardened against our asshole bosses' insatiable horniness for enshittification" (noon, LVCC - L1 - HW1–11–01).

Barbra Streisand is famous for many things: her exciting performances on the big screen, the small screen, and the stage; her Grammy-winning career as a musician (she's a certified EGOT!); and for all the times she's had to correct people who've added an extra vowel to the spelling of her first name (I can relate!).
But a thousand years from now, her legacy is likely to be linguistic, rather than artistic. The "Streisand Effect" – coined by Mike Masnick – describes what happens when someone tries to suppress a piece of information, only to have that act of attempted suppression backfire by inciting vastly more interest in the subject:
https://en.wikipedia.org/wiki/Streisand_effect
The term dates to 2003, when Streisand sued the website Pictopia and its proprietors for $50m for reproducing an image from the publicly available California Coastal Records Project (which produces a timeseries of photos of the California coastline in order to track coastal erosion). The image ("Image 3850") incidentally captured the roofs of Streisand's rather amazing coastal compound, which upset Streisand.
But here's the thing: before Streisand's lawsuit, Image 3850 had only been viewed six times. After she filed the case, another 420,000 people downloaded that image. Not only did Streisand lose her suit (disastrously so – she was ordered to pay the defendants' lawyers $177,000 in fees), but she catastrophically failed in her goal of keeping this boring, obscure photo from being seen:
https://en.wikipedia.org/wiki/Streisand_effect
Streisand has since called the suit "a mistake." On the one hand, that is very obviously true, but on the other hand, it's still admirable, given how many other failed litigants went to their graves insisting that their foolish and expensive legal gambit was, in fact, very smart and we are all very stupid for failing to understand that.
Which brings me to Ian Linkletter and the Canadian Privacy Library. Linkletter is the librarian and founder of the nonprofit Canadian Privacy Library, a newish online library that collects and organizes privacy-related documents from Canadian public institutions. Linkletter kicked off the project with the goal of collecting the Privacy Impact Assessments from every public university in Canada, starting in his home province of BC.
These PIAs are a legal requirement whenever a public university procures a piece of software, and they're no joke. Ed-tech vendors are pretty goddamned cavalier when it comes to student privacy, as Linkletter knows well. Back in 2020, Linkletter was an ed-tech specialist for the University of British Columbia, where he was called upon to assess Proctorio, a "remote invigilation" tool that monitored remote students while they sat exams.
This is a nightmare category of software, a mix of high-tech phrenology (vendors claim that they can tell when students are cheating by using "AI" to analyze their faces); arrogant techno-sadism (vendors requires students – including those sharing one-room apartments with "essential worker" parents on night shifts who sleep during the day – to pan their cameras around to prove that they are alone); digital racism (products are so bad at recognizing Black faces that some students have had to sit exams with multiple task-lights shining directly onto their faces); and bullshit (vendors routinely lie about their tools' capabilities and efficacy).
Worst: remote invigilation is grounded in the pedagogically bankrupt idea that learning is best (or even plausibly) assessed through high-stakes testing. The kind of person who wants to use these tools generally has no idea how learning works and thinks of students as presumptively guilty cheats. They monitor test-taking students in realtime, and have been known to jiggle test-takers' cursors impatiently when students think too long about their answers. Remote invigilation also captures the eye-movements of test-takers, flagging people who look away from the screen while thinking for potential cheating. No wonder that many students who sit exams under these conditions find themselves so anxious that they vomit or experience diarrhea, carefully staring directly into the camera as they shit themselves or vomit down their shirts, lest they be penalized for looking away or visiting the toilet.
Linkletter quickly realized that Proctorio is a worst-in-class example of a dreadful category. The public-facing materials the company provided about its products were flatly contradicted by the materials they provided to educators, where all the really nasty stuff was buried. The company – whose business exploded during the covid lockdowns – is helmed by CEO Mike Olsen, a nasty piece of work who once doxed a child who criticized him in an online forum:
https://pluralistic.net/2020/07/01/bossware/#moral-exemplar
Proctorio's products are shrouded in secrecy. In 2020, for reasons never explained, all the (terrible, outraged) reviews of its browser plugin disappeared from the Chrome store:
https://pluralistic.net/2021/09/04/hypervigilance/#radical-transparency
Linkletter tweeted his alarming findings, publishing links to the unlisted, but publicly available Youtube videos where Proctorio explained how its products really worked. Proctorio then sued Linkletter, for copyright infringement.
Proctorio's argument is that by linking to materials that they published on Youtube with permissions that let anyone with the link see them, Linkletter infringed upon their copyright. When Linkletter discovered that these videos already had publicly available links, indexed by Google, in the documentation produced by other Proctorio customers for students and teachers, Proctorio doubled down and argued that by collecting these publicly available links to publicly available videos, Linkletter had still somehow infringed on their copyright.
Luckily for Linkletter, BC has an anti-SLAPP law that is supposed to protect whistleblowers facing legal retaliation for publishing protected speech related to matters of public interest (like whether BC's flagship university has bought a defective and harmful product that its students will be forced to use). Unluckily for Linkletter, the law is brand new, lacks jurisprudence, and the courts have decided that he can't use a SLAPP defense and his case must go to trial:
https://pluralistic.net/2023/04/20/links-arent-performances/#free-ian-linkletter
Linkletter could have let that experience frighten him away from the kind of principled advocacy that riles up deep-pocketed, thin-skinned bullies. Instead, he doubled down, founding the Canadian Privacy Library, with the goal of using Freedom of Information requests to catalog all of Canada's post-secondary institutions' privacy assessments. Given how many bodies he found buried in Proctorio's back yard, this feels like the kind of thing that should be made more visible to Canadians.
There are 25 public universities in BC, and Linkletter FOI'ed them all. Eleven provided their PIAs. Eight sent him an estimate of what it would cost them (and thus what they would charge) to assemble these docs for him. Six requested extensions.
One of them threatened to sue.
Langara College is a 19,000-student spinout of Vancouver Community College whose motto is Eruditio Libertas Est ("Knowledge is Freedom"). Linkletter got their 2019 PIA for Microsoft's Office 365 when he FOI'ed the Nicola Valley Institute of Technology (universities often recycle one another's privacy impact assessments, which is fine).
That's where the trouble started. In June, Langara sent Linkletter a letter demanding that he remove their Office 365 PIA; the letter CC'ed two partners in a law firm, and accused Linkletter of copyright infringement. But that's not how copyright – or public records – work. As Linkletter writes, the PIA is "a public record lawfully obtained through an FOI request" – it is neither exempted from disclosure, nor is it confidential:
https://www.privacylibrary.ca/legal-threat/
Langara claims that in making their mandatory Privacy Impact Assessment for Office 365 available, Linkletter has exposed them to "heightened risks of data breaches and privacy incidents," they provided no evidence to support this assertion.
I think they're full of shit, but you don't have to take my word for it. After initially removing the PIA, Linkletter restored it, and you can read it for yourself:
https://www.privacylibrary.ca/langara-college-privacy-impact-assessments/
I read it. It is pretty goddamned anodyne – about as exciting as looking at the roof of Barbra Streisand's mansion.
Sometimes, where there's smoke, there's only Streisand – a person who has foolishly decided to use the law to bully a weaker stranger out of disclosing some innocuous and publicly available fact about themselves. But sometimes, where there's smoke, there's fire. A lot of people who read my work are much more familiar with ed-tech, privacy, and pedagogy than I am. If that's you, maybe you want to peruse the Langara PIA to see if they are hiding something because they're exposing their students to privacy risks and don't want that fact to get out.
There are plenty of potential privacy risks in Office 365! The cloud version of Microsoft Office contains a "bossware" mode that allows bosses to monitor their workers' keystrokes for spelling, content, and accuracy, and produce neat charts of which employees are least "productive." The joke's on the boss, though: Office 365 also has a tool that lets you compare your department's usage of Office 365 to your competitors, which is another way of saying that Microsoft is gathering your trade secrets and handing it out to your direct competitors:
https://pluralistic.net/2021/02/24/gwb-rumsfeld-monsters/#bossware
So, yeah, there are lots of "features" in Office 365 that could give rise to privacy threats when it is used at a university. One hopes that Langara correctly assessed these risks and accounted for them in its PIA, which would mean that they are bullying Linkletter out of reflex, rather than to cover up wrongdoing. But there's only one way to find out: go through the doc that Linkletter has restored to public view.
Linkletter has excellent pro bono representation from Norton Rose Fulbright, a large and powerful law-firm that is handling his Proctorio case. Linkletter writes, "they have put this public college on notice that any proceeding is liable to be dismissed pursuant to the Protection of Public Participation Act, BC’s anti-SLAPP legislation."
Langara has now found themselves at the bottom of a hole, and if they're smart, they'll stop digging.

Support me this summer on the Clarion Write-A-Thon and help raise money for the Clarion Science Fiction and Fantasy Writers' Workshop!

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/08/01/eruditio-libertas-est/#streisand-v-linkletter

Image: Copyright (C) 2002 Kenneth & Gabrielle Adelman, California Coastal Records Project, www.californiacoastline.org (modified) https://en.wikipedia.org/wiki/File:Streisand_Estate.jpgbr>
CC BY-SA 3.0 https://creativecommons.org/licenses/by-sa/3.0/deed.en
--
Langara College (modified) https://langara.ca/
Fair use (parody) https://scholarship.law.ufl.edu/cgi/viewcontent.cgi?article=1104
Fair dealing (parody) https://papers.ssrn.com/sol3/papers.cfm?abstract_id=1468015
#pluralistic#streisand effect#privacy impact assessment#canada#ian linkletter#Canadian Privacy Library#canpoli#foi#pia#Langara College#libraries#glam#Freedom of Information and Protection of Privacy Act#fippa#slapp#anti-slapp#langara college#bullies
227 notes
·
View notes
Note
do you have any suggustions for porygon enrichment? ive been wanting to get one since i was little, but i want to make sure theyll be happy.
(OOC: i really like the aesthetic of your blog and you seem like you could help. have you come across any quality porygon themed desktop pets? ive been trying to find one and theyre shockingly scarce.

Hello! I would be glad to help!
Porygon are quite distinct between individual. As I like to say, if you’ve met a Porygon, you’ve met one Porygon. There are no easy one size fits all approaches to Porygon enrichment as they all have particular interests. Despite all that, there are some trends and patterns you can use as a jumping off point while you get to know your Porygon.
A couple popular toys for Porygon are building blocks, puzzles, puzzle boxes, marble race tracks, abacuses and soundboards. They generally like things that engage their creativity and problem solving skills, as well as audio-visual stimulation (they generally aren’t that big on smells, textures or taste).
Another option is an electronic device, like a computer or phone. You can install different programs and widgets that serve the same purposes the physical toys would. You can also get mods for your Porygon, a lot of them love modifications, like color alterations, accessories or new models.
Finally, you could give your Porygon internet access. The internet is amazing for a porygon’s enrichment, but there are certain precautions you have to take. First of all, make sure your Porygon wants to use the internet. There are Porygon who are completely uninterested on the internet, so verifying they actually want to use it might save you some trouble.
If your Porygon does want to use your internet, you’ll have to install an antivirus for your Porygon’s health and anti-doxing software for your safety and privacy. Parental controls are also a useful feature to make sure your Porygon doesn’t end in a weird corner of the internet, but the best thing you can do is just monitor their internet use.
And those are the basics for Porygon enrichment!
Hope you find this useful!

//No, sorry, I really don’t do widgets or desktop pets (specially since my computer is currently a bit dead). Nell and I are very much not the same person, also. They are just a character with knowledge and interests that differ from mine quite a bit. But I’m glad you like the blog! Hope you can find what you’re looking for, tho!
8 notes
·
View notes
Note
Hi there! Bit of a weird question, and I’m not sure if this is the right blog for this, but… best laptop for privacy? I’m going to go to uni in a year and my parents have said that they’re going to buy me a laptop, which is awesome, except— I don’t know which one to chose? I’ve never had a laptop before but I try to take being private online as seriously as I can, and so I don’t really care… well, like, I do care that the laptop has good storage and works and stuff, but I care mostly about how private it is. Which one supports adding privacy-related stuff the best? Which one steals your data the least? I… am actually not sure what kind of questions I should be asking, since… again, never had a laptop before, and I don’t know what about its make makes it private (other than like general online privacy practices across all devices), so I was just wondering if you had any recommendations for me? Tldr: don’t care about fancy features, just want a laptop that more or less works, but would love privacy to be the main focus. This can sort of come at the expense of convenience - I don’t care it if’s harder to set up, use, etc., so long as I can connect to the internet with it.
So the hardware is pretty agnostic on this, the place where privacy is going to become an issue is in the software.
Windows loves to track you and send your data back to homebase; Apple is a walled garden that doesn't let people get deep into configurations; linux is intimidating for a lot of people.
Your actual best bet on privacy would be to get a laptop with no OS and install a linux distro on it, but it sounds like that's probably not something that's terribly approachable for you. So in that case I'd recommend getting a Windows laptop (mac prices aren't worth it) and going through this list to change the settings to ensure better privacy.
HOWEVER please note that you should be getting a laptop with a full OS. Windows has an option for "windows 11s" or "windows 10s" and first off you should be going with 11 at this point but second that "s" means that there are pretty strict limitations on what you can do as a user in terms of configuration and installation.
If you are willing to pay a bit more for Windows 11 Pro instead of windows 11 Home, the pro license cuts off some of the more annoying tracking that Windows does automatically, but I'd say you're better off simply getting the home license and really digging into the settings and getting to know it and setting it up for yourself.
BUT if it's at all possible, honestly I'd say get a bare metal laptop (that means it's just the hardware, no software, you need to install an operating system before you do anything) and install linux. HOWEVER keep in mind that there are some significant downsides to using linux as a student, mostly that you'll likely run into software at some point that you won't be able to install. Also if you're not already pretty good with computers it can be difficult to keep a linux machine running (but very easy to make it private; that's the tradeoff - you can make it more secure more easily, but you really have to know how to fix your own computer if something goes wrong.)
For your situation, again, I think a Windows 11 Home laptop with the settings adjusted is your best bet.
Absolutely positively don't get a chromebook (you've got no control of the settings on a chromebook and the thing is made to feed information to google) and don't get a mac (you can get better specs on a PC at a lower cost).
For an idea of budget on this, I'd say you can probably get something from Dell, Lenovo, or HP for around $650-1000 dollars that's got decent specs (12th gen or newer i5 processor, 16gb RAM, 512GB SSD) and maybe something more like $500-800 from acer, asus, or samsung. Whatever computer you end up getting, you should get the added drop protection warranty because that means the manufacturer will fix your laptop if you drop it, something that is a bigger deal for college students than most people (because of your environment you're more likely to end up with drop damage than a lot of people AND because you're a college student you probably won't be able to afford to fix or replace the computer)
Good luck!
43 notes
·
View notes
Text
Rockman.EXE and Cyber Security.

When you are a Rockman/Megaman Battle Network fan and you take a college course about networking, you start to notice how broken the internet is in the anime. So just for fun, I want to talk about a few things I learn about network security and how it is interpreted in the Megaman Battle Network anime.
1. Firewalls
What are firewalls? In simple terms, it is a security barrier that is placed between a private network and the public network.
They are configured to monitor and filter networking traffic, hackers go through them by figuring out how they are programed, once they do they can either bypass the security undetected or simply disable the firewall.
Lets take a scene from the movie where Lan sends Megaman into a secretary’s console to destroy a program inside a company’s server.

Megaman is running through the network between the console and the firewall, which protects the private network of the company.

Logically, for Megaman to go through the firewall, he is going to need to use his powers as a Net Navigator (Net Navi) to analyze the firewall at an incredible speed to try to find a way to go through it, right?
WRONG! Battle Network logic says you can just break it with brute force!
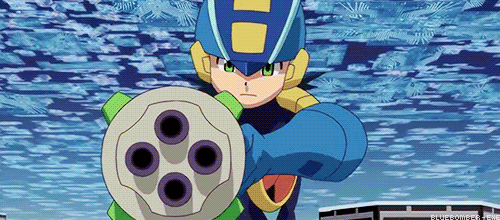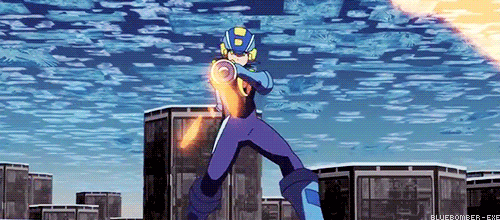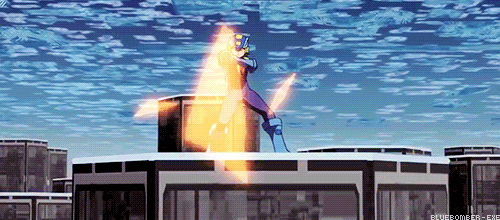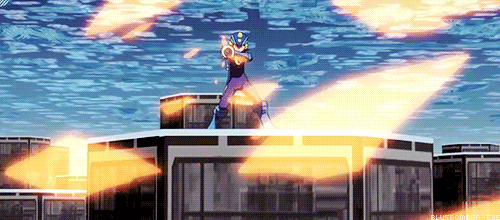

You see the problem?
Does this mean Navis and battle chips are just as destructive to the net as viruses? Because last time I checked, Viruses and malware are the only programs with the ability to destroy networks.
2. Viruses
Viruses are man made, they are programed with a purpose that’s usually to destroy data files. They can also be used to change and manipulate programs, that’s why you can see evil Navis controlling viruses to do specific jobs for them. Viruses can’t replicate on their own without a user interface, so how is this Moloko a baby?!

There was an undubbed episode of Megaman Axess where Rush meets and befriends a baby Moloko virus, which doesn’t make any sense. Yes, Rush is a virus, and it has been established that viruses can communicate with each other, but why does this Moloko have parents? And why was the group of Molokos it separated from was being herded by other viruses like Trumpy? All I’ve seen Molokos do is charge at megaman when they see him, trying to ram him. Why would someone herd them? For the wool? It disappears after you hit it!
And what even is Rush’s purpose anyway? When he first appeared in the anime, he was made to track down Rockman’s frame or structure when they were trying to revive him with the backup data, but now?
All he does is being a crappy character who runs away when things get dangerous, doesn’t act like a dog anymore, and irritates me because he can move between the cyberworld and the real world! He is selfish, lacy, and practically useless, there are several times where Megaman goes missing and Rush is never even called to track him down, so he doesn’t even have that ability anymore.
On a positive note, viruses can be interesting, I found out that there are different types of viruses. For example.
A Stealth virus is a virus that avoids detection from anti virus software, this means it can conceal itself and attack without being spotted, sounds familiar? In this case the anti-virus software would also include Navis.
A retro virus tries to destroy anti-virus programs, I like to think these apply to viruses who specifically target Navis in battle like Canodumbs and Piranahs since they only attack when they detect an enemy in the line of fire.
Armored Viruses are hard to detect or analyze because they have a protective code, These could be Viruses with armors or auras like the Dominerd or even the life virus.
But Phage viruses remind me of these guys because they rewrite programs.

And I guess this one counts too?

Other viruses just act like malware, like the Alpha bug that is more of a worm than a virus, because it can replicate and travel across networks without any human assistance.
Others are obvious like the Pop up virus which is just Rush, and it is supposed to be adware, but just like Rush, it is more annoying than harmful.
In the anime, killereye viruses are used as spyware, there was an episode were Videoman used them to spy on Rockman and make copies of him.

3. Tracing a signal.
Basically, everything you do on the net leaves bread crumps or cookies behind that makes it easy to track a user online, every device have a Mac Address and every network has an IP address, but it takes a special kind of software and advance skills to track down somebody in the real world.
Let’s talk about episode 32 of Stream.
Remember that episode were Megaman followed a revived Shademan to 20 Years in the past and he witnessed a famous hacking incident that was stopped by Colonel?

Aside from the fact that it was 20 years in the past and Megaman is more advance than most of the technology there, there were a few things bothering me.
For starters, why does that computer show a little Colonel doing something to that guy’s hacking program? It’s cute and all, but this is a confusing way to show someone disabling a program, it usually just shows a notification. Or is that how the computer sees colonel, like a little pixel version of him? XD
That hacking program was made to open any cyber lock, it uses three special pillars to disguise the signal so the police wouldn’t be able to track down the address, this means those pillars have some special form of encryption to cover the data to make it untraceable. In the anime’s world, that means it’s invisible, but somehow Megaman can still sense it? And how did Barryl know where the guy was? Did colonel tell him? Or did the viruses he sent to delete colonel revealed his location? Oops.
4. Hard Drives.
To end this post, what are hard drives? They are what your computer uses to store files, so Navis can obviously be stored in a computer as well. The problem is that they are still sentient inside the computer instead of dormant.
The concept of containing a Navi, yes, Navis have their own jail in this universe, doesn’t really make any sense. We know Navis can sleep, but the Navis we see in cages are still active, and if everything is connected to the internet, how can they not escape?
I’m using this scene with Megaman as an example, when he was arrested for being in the wrong place at the wrong time, he was put in a cute little cyber cage.

However, since Megaman is more advance, he wonders if the hard drive of the computer he is stored in is weak against vibrations. What does he mean by that? Physical or cyber vibrations? Does that mean he can control a frequency in that computer’s cyberworld to alter it?
Whatever he did worked, because he left a gap in the cage, but how did he do it without damaging the Hard Drive? The police officer wouldn’t be able to access his files anymore, maybe it was minor file corruption?
And the worst part is that he opened a gateway into the internet, which is still there! I guess Megaman can travel through routers by himself? Maybe that wouldn’t have happen if the officer just disconnected his ethernet cable.
This Network based world is a scary one.
48 notes
·
View notes
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
So, let me put on my Internet Old Person hat and tell you kids about the the way we committed music piracy in the long long ago of 2001, and the fragility of those music collections in those days.
You might know Napster. You might know Limewire. But there was a music piracy tool in between those. A little remembered program called AudioGalaxy, and it worked a little like Napster and a little like BitTorrent. The exact details of how it worked are immaterial, but one thing it did was when you searched for an artist, the songs were sorted, in essence, by popularity (e.g. how many people had that specific song file shared.)
Now, I can’t understand why this was a thing, but there was a strange phenomenon in the early days of file sharing and music piracy where people would share songs with the wrong artist name or song title. Certain bands and artists got a lot of stuff attributed to them that they never recorded. “Weird” Al Yankovic may be the most infamous victim of this, with nearly every novelty song and song parody released attributed to him regardless of quality or subject matter.
The confluence of these two phenomena are how I discovered one of my favorite bands of all time.
So, in my late teens, I found a new favorite band. A quickly little one-hit wonder known as DEVO. Y’know, the band that dd “Whip It.” They had the funny red hats that looked like flowerpots. Those guys.
Anyway, I had become obsessed with this band to the point of autistic hyperfixation, and I wanted to hear everything they’d ever put out. At that point, they’d released nine studio albums, a couple live albums, and two collections of early demos, and I wanted them all. So I would find myself crawling in the bottom pages of the AudioGalaxy search results looking for those obscure tracks—b-sides, songs on soundtracks and compilations, the occasional bootleg, They’d pop up between songs that were obviously not by DEVO, and much like our poor friend Alfred Yankovic, any sort of vaguely quirky 80s song got assigned to DEVO.
That was how I found it. A song called, simply, “Detachable Penis.”
Now, I had never heard of such as song, but I knew on the face of it, it wasn’t a DEVO song.
But with a title like that, I knew I had to find out just what in the name of fuck a song called “Detachable Penis” sounded like.
It sounded, dear reader, like this:
youtube
(CWs: blurry images of a dildo, the word penis, spoken word poetry)
And I immediately went to Google, because this song somehow tickled an itch in my brain, and I had to go and find out the real band that recorded this song, because how the hell else was I going to get every song I could of theirs I could get my grubby little hands on. The band was called King Missile, and I was hooked.
I’d like to see any music discovery algorithm beat that.
I eventually acquired their entire major discography along with a few EPs and B-Sides. I eventually burned those to a CD, which I could listen to with my MP3 CD Player.
And I realize, upon writing that, for you youth “MP3 CD Player” is a noun phrase that needs explaining. See, while the iPod had been released at that point, and similar devices were also on the market, they were all prohibitively expensive. The economical way to listen to pirated music files was to burn them to CD, but some CD players had software that allows you to burn those song as as _data_. Suddenly, you could have a single CD with 700 megabytes of MP3 files—room for an artist’s entire discography, if not multiple artists.
Since I was download a whole lot of MP3s with my high speed DSL connection, I was taking up an awful lot of space on my hard drive that needed to be offloaded somehow. CD-Rs and an MP3 CD Player were the optimal solution. And it worked…
…until it didn’t.
In the summer of 2002, my parents took me on a vacation to Las Vegas and Los Angeles. It was in the latter city where someone got into our rental car and swiped my MP3 CD player and a binder of CDs—both pressed CDs I’d acquired and CD-Rs of illicitly acquired MP3s, along them a CD-R I’d burned containing the nearly complete King Missile discography.
Songs I had only on that one CD-R.
It took me a decade—ten fucking years—before I’d recovered all the music that was on that disc.
This is the sort of discovery and the sort of loss that kids will never experience again in this day of Spotify and the all-you-can-eat buffet of music on demand we have now.
#internet old person#music piracy#music discovery#AudioGalaxy#Napster#Limewire#2001#2002#back in the day#2000s nostalgia#long and rambling story#DEVO#king Missile#Youtube
35 notes
·
View notes
Text
How to Improve Reliability of School Bus Transportation System?
ost parents, who do not have the time to drop and pick their kids to-and-from school, prefer school bus transportation to ensure a safe commute for their children. But there is always a fear in their mind about whether the kids have reached school safely, or why is the school bus late? Did something wrong happen on the road?
A traditional school transportation system with no real time tracking of school buses has witnessed many major safety issues, which call for better reliability of the school transport system. Well, this reliability check has given a big headache to schools.
Improving school bus transportation safety is not at all a complex task to do. By using a simple-to-use GPS school bus tracking solution you can easily improve the reliability of your school bus transportation system.
School bus tracking solution is available as both web and mobile app. The school admin can operate GPS tracking software app through the web, while the mobile app can be used by the school drivers along with the parents. This school bus monitoring software is easy to install, and its user-friendly UI makes it even easier to use. Once school bus tracking software is installed on your device it can work even without the internet.
2 notes
·
View notes
Text
Evolution of Technology and Its Impact on EdTech
In today's digital age, technology continues to evolve at an unprecedented pace, transforming various aspects of our lives, including education. With the advent of EdTech (Educational Technology), traditional educational paradigms are being reshaped, leading to more interactive, accessible, and personalized learning experiences.
Evolution of Technology: A Brief Overview
The evolution of technology has been marked by significant milestones, from the invention of the printing press to the rise of the internet and beyond. Each technological advancement has revolutionized how information is accessed, shared, and utilized, paving the way for transformative changes in education. From chalkboards to interactive whiteboards, from textbooks to digital learning platforms, technology has played a pivotal role in shaping modern education.
Integration of Technology in Education: The Rise of EdTech
As technology continues to advance rapidly, it's crucial for us to stay ahead in the ever-evolving EdTech industry. With this in mind, we've developed an incredibly advanced EdTech software Proctur that offers a comprehensive suite of features tailored to meet the needs of schools, teachers, and parents. We understand the importance of having everyone on the same page, and our platform ensures 100% transparency by bringing schools, teachers, and parents together onto a single unified platform.
Here's a glimpse of the key features our EdTech software offers:
1.User Role Management :Customize user access and ensure data security with ease using our User Role Management feature within our School ERP—empowering efficient administration and peace of mind.

2. Visitor Management : Transform school safety and efficiency with our innovative Visitor Management system! Elevate security while simplifying check-ins for a smarter school experience.

3.Zoom Integration: Facilitate interactive live classes seamlessly with Proctur's ERP Zoom integration feature for enhanced educational engagement.

Bus Tracking System:
We understand the importance of student safety, which is why our software includes a bus tracking system that allows parents to track the whereabouts of their child's school bus in real-time.
At our core, we believe in creating a supportive and inclusive educational ecosystem where every stakeholder – schools, teachers, and parents – plays a vital role in shaping the future of our students.
EdTech Market Size: A Global Perspective:
The global EdTech market has experienced exponential growth in recent years, driven by increasing digitalization, rising demand for online education, and advancements in technology. According to market research reports, the Indian EdTech market size was valued at over $20 billion in 2022, and it is projected to continue its upward trajectory in the coming years.
EdTech Market in India: Trends and Opportunities
In India, the EdTech sector has witnessed remarkable growth fueled by factors such as a large young population, increasing internet penetration, and government initiatives promoting digital education. The market size of EdTech in India is estimated to be around $4.3 billion in 2022, with notable players offering a diverse range of solutions catering to different segments of the education ecosystem.
Conclusion
In conclusion, as technology continues to revolutionize the education sector, Proctur, as showcased on their website proctur.com, exemplifies how advanced EdTech solutions can streamline education management processes and foster transparency between schools, teachers, and parents. Through Proctur's innovative approach to education management, schools can efficiently manage their resources, track student progress, and enhance parent engagement. With Proctur leading the way, the future of education management looks brighter than ever before.
#proctur#edtecherp#edtech#school management software#school management system#classroom management#yourpocketclassroom
2 notes
·
View notes
Text
What is Bitdefender Central & How Do I Use It?
Bitdefender provides one of the most popular antivirus software that protects your computers and mobile phones. The company product helps you by protecting your devices and data as it comes with lots of features. Also, it is a cloud-based engine that will protect devices when browsing or using the internet. It goes light on the system and doesn't take up much space. This blog will discuss what is Bitdefender Central & how do I use it. And explore more on it.
What is Bitdefender Central?
The company created Bitdefender Central, an online platform to manage all the company's products and subscriptions. First, You need to create your account. And then only you will be able to log in to Central's web portal. There you will find the main dashboard, which provides you with details about all your Bitdefender devices. Also, which devices are under protection, and have any new threats been detected?
Further, you can manage any of the active subscriptions. If you are facing any issues, you can browse from the library of help features. So it acts as a hub for all your devices using Bitdefender software. Moreover, the Central hub also facilitates access to premium security services.
How to Use the Bitdefender Central?
Now, we will look at how you can use this platform and manage your devices. Remember, the online portal has many features that simplify managing the devices. Further, it acts as a remote access portal across your devices. Let us see the functions you can access via Cental's portal.
Subscriptions
From the Central managing account, you can access all your subscribed devices. Also, make payments and details of the same. Further, you can even activate a new subscription service and manage your devices.
Remote Management
With the Central portal account, you will be able to view details of any device connected with the Bitdefender product. Also, you can manage certain things directly from the hub, which includes triggering a malware scan. Plus, you can boost the functioning of a device.
Anti-Theft
If ever you lose your mobile or someone steals your laptop, then the Central management hub will enable you to track the lost device. Further, you can even send a message; in the worst cases, you can lock your device or completely delete its files.
Parental Control
If you have subscribed to the Internet or Total Security feature, you will get a parental control feature. So, from this hub, you will be able to monitor your child's online activity, their live location, set screen time, and much more.
Further, it can display the time spent, applications, websites, and even contacts saved on the device. The feature is really helpful in protecting your child from age-inappropriate sites and content.
Digital Identity Protection
In this age, where anyone can be found on the internet, protecting one's identity on the internet becomes important. So, the company assures you by protecting your digital identity. You use the functions in this to see how much of your data is made public or leaked.
Further, you can always be aware of sensitive information about your identity on the Dark Web or public data. Moreover, you will be alerted if there is any attempt on your identity, such as data breaches, account info leaking, and hacking.
Support Portal
If you ever need help, there is a list of options that the company offers that you can use to resolve your issue. The help features include video tutorials, FAQs, a knowledge base, and more. These resources are helpful and come in handy for users who are new to using a Central account.
Conclusion
Bitdefender is a great software that ensures all-around protection of your devices against all threats. You will get many features and functions that create multiple layers of protection. In this blog, we discussed what is Bitdefender Central & how do I use it. Now, this online platform lets you access all your devices, protect your files against device theft, and many more features.
FAQs
How to reset your Central Account password?
If you ever forget your password and are unable to access your account, open the account and Sign in. Later, type your associated email with the account, and then select Next. Now, select the Forgot Password option, and you will receive an email with instructions and reset your password. Further, you have to enter the security code, create a new password, and press save. Finally, you will be able to sign in again with your new password.
How to remove a device from a Central account?
To remove a particular device, first sign in to your account. Later, go to the My Devices section, which is present on the sidebar. Now, you will be able to see all the devices and select view details. After that, you will see the remove option and confirm it. Finally, the device is removed from the subscription list.
How can you delete a Central account?
Bitdefender's Central account is an online hub that helps manage all your subscriptions and devices. To delete the account, you need to sign in to your account. After that, select the account icon, and choose your account. Once, then go to Data & Privacy, and finally select the Delete account option. After this, you will lose all the services and products the company provides.
Visit: bitdefender central login
central.bitdefender.com
Source: https://centralbitdefenderdotcom.wordpress.com/2023/12/14/what-is-bitdefender-central-how-do-i-use-it/
#central.bitdefender.com#bitdefender sign in#bitdefender login#bitdefender central login#www.central.bitdefender.com#bitdefender.com/activate#bitdefender central#bitdefender#bitdefender antivirus#bitdefender log in
2 notes
·
View notes
Text
From the Omegle Website:
““Of all tyrannies, a tyranny sincerely exercised for the good of its victims may be the most oppressive. It would be better to live under robber barons than under omnipotent moral busybodies. The robber baron's cruelty may sometimes sleep, his cupidity may at some point be satiated; but those who torment us for our own good will torment us without end for they do so with the approval of their own conscience.” — C.S. Lewis
“In the beginning the Universe was created. This has made a lot of people very angry and been widely regarded as a bad move.” — Douglas Adams
Dear strangers,
From the moment I discovered the Internet at a young age, it has been a magical place to me. Growing up in a small town, relatively isolated from the larger world, it was a revelation how much more there was to discover – how many interesting people and ideas the world had to offer.
As a young teenager, I couldn’t just waltz onto a college campus and tell a student: “Let’s debate moral philosophy!” I couldn’t walk up to a professor and say: “Tell me something interesting about microeconomics!” But online, I was able to meet those people, and have those conversations. I was also an avid Wikipedia editor; I contributed to open source software projects; and I often helped answer computer programming questions posed by people many years older than me.
In short, the Internet opened the door to a much larger, more diverse, and more vibrant world than I would have otherwise been able to experience; and enabled me to be an active participant in, and contributor to, that world. All of this helped me to learn, and to grow into a more well-rounded person.
Moreover, as a survivor of childhood rape, I was acutely aware that any time I interacted with someone in the physical world, I was risking my physical body. The Internet gave me a refuge from that fear. I was under no illusion that only good people used the Internet; but I knew that, if I said “no” to someone online, they couldn’t physically reach through the screen and hold a weapon to my head, or worse. I saw the miles of copper wires and fiber-optic cables between me and other people as a kind of shield – one that empowered me to be less isolated than my trauma and fear would have otherwise allowed.
I launched Omegle when I was 18 years old, and still living with my parents. It was meant to build on the things I loved about the Internet, while introducing a form of social spontaneity that I felt didn’t exist elsewhere. If the Internet is a manifestation of the “global village”, Omegle was meant to be a way of strolling down a street in that village, striking up conversations with the people you ran into along the way.
The premise was rather straightforward: when you used Omegle, it would randomly place you in a chat with someone else. These chats could be as long or as short as you chose. If you didn’t want to talk to a particular person, for whatever reason, you could simply end the chat and – if desired – move onto another chat with someone else. It was the idea of “meeting new people” distilled down to almost its platonic ideal.
Building on what I saw as the intrinsic safety benefits of the Internet, users were anonymous to each other by default. This made chats more self-contained, and made it less likely that a malicious person would be able to track someone else down off-site after their chat ended.
I didn’t really know what to expect when I launched Omegle. Would anyone even care about some Web site that an 18 year old kid made in his bedroom in his parents’ house in Vermont, with no marketing budget? But it became popular almost instantly after launch, and grew organically from there, reaching millions of daily users. I believe this had something to do with meeting new people being a basic human need, and with Omegle being among the best ways to fulfill that need. As the saying goes: “If you build a better mousetrap, the world will beat a path to your door.”
Over the years, people have used Omegle to explore foreign cultures; to get advice about their lives from impartial third parties; and to help alleviate feelings of loneliness and isolation. I’ve even heard stories of soulmates meeting on Omegle, and getting married. Those are only some of the highlights.
Unfortunately, there are also lowlights. Virtually every tool can be used for good or for evil, and that is especially true of communication tools, due to their innate flexibility. The telephone can be used to wish your grandmother “happy birthday”, but it can also be used to call in a bomb threat. There can be no honest accounting of Omegle without acknowledging that some people misused it, including to commit unspeakably heinous crimes.
I believe in a responsibility to be a “good Samaritan”, and to implement reasonable measures to fight crime and other misuse. That is exactly what Omegle did. In addition to the basic safety feature of anonymity, there was a great deal of moderation behind the scenes, including state-of-the-art AI operating in concert with a wonderful team of human moderators. Omegle punched above its weight in content moderation, and I’m proud of what we accomplished.
Omegle’s moderation even had a positive impact beyond the site. Omegle worked with law enforcement agencies, and the National Center for Missing and Exploited Children, to help put evildoers in prison where they belong. There are “people” rotting behind bars right now thanks in part to evidence that Omegle proactively collected against them, and tipped the authorities off to.
All that said, the fight against crime isn’t one that can ever truly be won. It’s a never-ending battle that must be fought and re-fought every day; and even if you do the very best job it is possible for you to do, you may make a sizable dent, but you won’t “win” in any absolute sense of that word. That’s heartbreaking, but it’s also a basic lesson of criminology, and one that I think the vast majority of people understand on some level. Even superheroes, the fictional characters that our culture imbues with special powers as a form of wish fulfillment in the fight against crime, don’t succeed at eliminating crime altogether.
In recent years, it seems like the whole world has become more ornery. Maybe that has something to do with the pandemic, or with political disagreements. Whatever the reason, people have become faster to attack, and slower to recognize each other’s shared humanity. One aspect of this has been a constant barrage of attacks on communication services, Omegle included, based on the behavior of a malicious subset of users.
To an extent, it is reasonable to question the policies and practices of any place where crime has occurred. I have always welcomed constructive feedback; and indeed, Omegle implemented a number of improvements based on such feedback over the years. However, the recent attacks have felt anything but constructive. The only way to please these people is to stop offering the service. Sometimes they say so, explicitly and avowedly; other times, it can be inferred from their act of setting standards that are not humanly achievable. Either way, the net result is the same.
Omegle is the direct target of these attacks, but their ultimate victim is you: all of you out there who have used, or would have used, Omegle to improve your lives, and the lives of others. When they say Omegle shouldn’t exist, they are really saying that you shouldn’t be allowed to use it; that you shouldn’t be allowed to meet random new people online. That idea is anathema to the ideals I cherish – specifically, to the bedrock principle of a free society that, when restrictions are imposed to prevent crime, the burden of those restrictions must not be targeted at innocent victims or potential victims of crime.
Consider the idea that society ought to force women to dress modestly in order to prevent rape. One counter-argument is that rapists don’t really target women based on their clothing; but a more powerful counter-argument is that, irrespective of what rapists do, women’s rights should remain intact. If society robs women of their rights to bodily autonomy and self-expression based on the actions of rapists – even if it does so with the best intentions in the world – then society is practically doing the work of rapists for them.
Fear can be a valuable tool, guiding us away from danger. However, fear can also be a mental cage that keeps us from all of the things that make life worth living. Individuals and families must be allowed to strike the right balance for themselves, based on their own unique circumstances and needs. A world of mandatory fear is a world ruled by fear – a dark place indeed.
I’ve done my best to weather the attacks, with the interests of Omegle’s users – and the broader principle – in mind. If something as simple as meeting random new people is forbidden, what’s next? That is far and away removed from anything that could be considered a reasonable compromise of the principle I outlined. Analogies are a limited tool, but a physical-world analogy might be shutting down Central Park because crime occurs there – or perhaps more provocatively, destroying the universe because it contains evil. A healthy, free society cannot endure when we are collectively afraid of each other to this extent.
Unfortunately, what is right doesn’t always prevail. As much as I wish circumstances were different, the stress and expense of this fight – coupled with the existing stress and expense of operating Omegle, and fighting its misuse – are simply too much. Operating Omegle is no longer sustainable, financially nor psychologically. Frankly, I don’t want to have a heart attack in my 30s.
The battle for Omegle has been lost, but the war against the Internet rages on. Virtually every online communication service has been subject to the same kinds of attack as Omegle; and while some of them are much larger companies with much greater resources, they all have their breaking point somewhere. I worry that, unless the tide turns soon, the Internet I fell in love with may cease to exist, and in its place, we will have something closer to a souped-up version of TV – focused largely on passive consumption, with much less opportunity for active participation and genuine human connection. If that sounds like a bad idea to you, please consider donating to the Electronic Frontier Foundation, an organization that fights for your rights online.
From the bottom of my heart, thank you to everyone who used Omegle for positive purposes, and to everyone who contributed to the site’s success in any way. I’m so sorry I couldn’t keep fighting for you.
Sincerely,
Leif K-Brooks
Founder, Omegle.com LLC”
2 notes
·
View notes
Text
WhatsApp Spy Features for Child Safety

Going that extra mile and protecting your children is top-most priority for every parent. With great exposure to smartphones and technology, there is an obvious feeling of concern for parents to know what their child is up to.
With the help of a good parental control app you can track every move of your child. These apps were secretly to spy on phones and keep you updated with all the activities of your child. A phone spy app is one great way of keeping up with your child.
Kids online can come across all types of content and it could also include some inappropriate content which can be addictive as well as dangerous for your little one. A good phone spy app can help you to monitor your child’s device, giving you all the information.
Can a phone spy app help ?
A good spy app can make it simple and easy for you to keep your child safe against violating content and unwanted security threats. In today’s time, kids have a smartphone and internet access, being underage and having restrictions to certain activities is now merely a law but once you have easy access to the phone and internet there is every sort of content online.
Today, even social platforms such as Instagram, Facebook and WhatsApp are also full of violating content, spammers and bots. But you can rely on a good mobile spy app to ease your concern. You can keep track of your loved ones’ device and ensure that they do not engage with any inappropriate content.
We recommend that firstly if you witness your loved one engaging in any activity that is harmful for them or for your relationship with them, it’s better to have understanding and open communication with them. Especially with kids, if you try to impose any restrictions on them without a valid reason or in some cases even if your concern is valid, your loved one would be frustrated.
To avoid a challenging situation like this, you can try a spy app for android phone that not only gives you all the information you need but is also fully secure.
Which spy app to go for?
Let us give you a few insights of the app which is loved and recommended by parents. Onemonitar parental app is tried by not only parents but also people who want to ensure the safety of their loved ones in general. This spy phone application has 50+ features and we’ll highlight the most popular ones for you.
Onemonitar gives you options to listen to the calls through its hidden call recorder which provides high quality of audio. You can track the real-time location of the target device and know the whereabouts of your child, this ensures that they are not lying to you and even if they are, you know where they are remotely.
Talking about social media tracking, you can check the accounts of your child across all major social media. You can check their WhatsApp with the help of WhatsApp spy software, you can check their chats, calls and any media that is being exchanged with others. You can scroll through the Instagram and Facebook accounts and who they are interacting with, this will ensure that you are aware of if they are not interacting with any person that could be of danger to them.
Things to remember!
A spy app can be very helpful when you want to control or supervise the activities of your loved ones. With broader usage and multiple features, regardless of who your target is, a spy phone app is now welcomed and has come in use across the globe.
These solutions provide you 100% data protection and security and with a phone spy app like Onemonitar only you have the access to your control panel and nobody other than you can see your personal information. Also, their 24*7 support team is available for your assistance through live chats and calls.
You can use the spy app and ensure high security and safety for your dear ones. Happy monitoring with Onemonitar!
#androidspy#mobilespy#spyappformobile#hiddencallrecorder#spyapp#spyappforandroid#androidspyapp#parentalcontrol#phonespy
2 notes
·
View notes
Text
This day in history

#20yrsago Internet “Hopkin” meme unravelled https://mike.whybark.com/archives/1951
#20yrsago Full-back HTML tattoo https://web.archive.org/web/20050126081525/http://www.bmezine.com/tattoo/A41118/high/tattoo4.jpg
#10yrsago Gates Foundation mandates open access for all the research it funds https://blogs.nature.com/news/2014/11/gates-foundation-announces-worlds-strongest-policy-on-open-access-research.html
#10yrsago Leaked docs detail Big Oil and Big PR’s plans for a opinion-manipulation platform https://www.vice.com/en/article/a-top-pr-firm-promised-big-oil-software-that-can-convert-average-citizens/
#5yrsago "Out of Home Advertising”: the billboards that spy on you as you move through public spaces https://www.consumerreports.org/electronics-computers/privacy/digital-billboards-are-tracking-you-and-they-want-you-to-see-their-ads-a1117246807/
#5yrsago How to recognize AI snake oil https://www.cs.princeton.edu/~arvindn/talks/MIT-STS-AI-snakeoil.pdf
#5yrsago High prices and debt mean millennials don’t plan to stop renting, and that’s before their parents retire and become dependent on them https://www.businessinsider.com/more-millennials-planning-to-rent-forever-cant-afford-housing-2019-11
#5yrsago Mayor Pete: Obama should have left Chelsea Manning to rot in prison for 35 years https://www.cbsnews.com/amp/news/2020-candidate-pete-buttigieg-troubled-by-clemency-for-chelsea-manning/
#1yrago Naomi Kritzer's "Liberty's Daughter" https://pluralistic.net/2023/11/21/podkaynes-dad-was-a-dick/#age-of-consent
6 notes
·
View notes
Text
I know it's been said before, but even with how dangerous the internet is, a lot of kids would be in even more danger if their parents went through their phone or browser history. Either way, it's an invasion of privacy, and it doesn't stop them from doing anything - they only learn that they need to get better at hiding things from their parent(s).
If you want to keep your child safe on the internet, you have to take preventative measures.
As soon as they're old enough to understand, you need to regularly have conversations with them about how the internet works and how to keep themselves safe.
Talk to them about:
how a lot of content on the internet is made to grab your attention so they get more clicks and track your info.
how an algorithm-based internet is designed to constantly stimulate dopamine and other emotional responses and keep you online as long as possible.
Setting both time limits AND emotional limits - if something is making them so angry that it's ruining their whole day, then it's time to step away.
How to tell if a story is made up/exaggerated, or if a picture is ai/photoshopped. Have them ask themselves why they think it's fake, what kind of agenda the OP/ad/website might have, and how to double-check sources and do backwards image results. And on that note —
HOW TO SPOT HATE & PROPAGANDA. This is probably the most important. Talk about how algorithms can start showing them things that push them towards certain beliefs. Teach them about how hate groups and whole governments use the internet to spread their agenda by manipulating information and tugging at a person's emotional response. Teach them how to critically consume their media and when they should back away from
How to use ad blockers and other anti-tracking software.
How to safely pirate things. Don't feel bad about it. Almost everything is subscription-based now, shows are always getting canceled, video games cost $60-80 with additional in-game purchases. The multi-billion dollar companies are still making record profits anyway.
Not to steal content from others and post it as their own.
What kind of information isn't safe for them to reveal online.
How to speak to others kindly online.
Find websites for them that aren't social media or youtube!
When it comes to youtube - don't rely on Youtube Kids to filter out harmful content by itself.
I'm sure there's more. You can't always be watching over your kid's shoulder wherever they go. They won't trust or respect you if you watch their every move. And once your kid knows how to safely navigate the internet, they can teach their friends, too!
1 note
·
View note
Text
How to Monitor Kids' Phones Using Screen Recording Apps

The safety of kids on the internet is more necessary than ever. With so much time they spend on their smartphones, it is difficult to say what they are actually doing. Are they talking to strangers? Visiting risky websites? With the help of a screen recording app, you can easily find out. It allows you to monitor their screen activity in real time, therefore, you do not need to be looking at their phone all the time in order to keep them safe.
Why Screen Recording is the Best Way to Monitor Kids' Phones
Keeping kids safe online is a growing concern for many parents. People spend a lot of time on smartphones. It's important to know what they do, who they talk to, and the content they see. One of the best ways to do this is by using screen recording apps.
Understanding Screen Recording Technology
Screen recording technology allows you to capture everything that happens on a device's screen. It’s like having a video camera watching the screen activity in real-time. Every tap, scroll, and swipe is recorded, giving you clear visibility into what’s happening. Screen recording lets you capture everything your child does. This includes text messages, videos, and social media. You don't have to watch them closely.
Key Advantages of Screen Recording for Parental Control
Screen recording is not only a process of watching what’s going on. It's about understanding and protecting. Here are some key benefits:
Real-time monitoring: See what your child is doing as it happens, not just after the fact.
Full visibility: You won't just see snippets. You'll see the entire conversation and browsing history.
Collect evidence: If you see signs of cyberbullying or risky behavior, keep a clear record. This helps you address the situation properly.
Better conversations: When you know what’s happening, it’s easier to talk about your child's online habits and safety.
Features to look after for right Screen Recording App
Choosing the right screen recording app is crucial for effective monitoring. Here’s what you should consider:
Ease of Use: Choose an app that’s easy to understand and navigate.
High-Quality Video: Choose one that records clear videos so you don’t miss anything.
Storage Options: Make sure it has enough space or cloud storage to save everything.
Security and Privacy: Check that it keeps your data private and secure.
Compatibility: Make sure it works well with your child’s phone whether Android or iOS.
What You Can Monitor with Screen Recording
Screen recording apps reveal different aspects of your kid’s digital life. This is what you can keep track of.
Social Media and Messaging Apps
Platforms like Instagram, WhatsApp, Snapchat, and Facebook are popular among kids. With screen recording, you can:
Monitor conversations and shared media.
Identify risky interactions with strangers.
Keep an eye on posts and status updates.
Online Browsing and Video Content
Kids spend a lot of time browsing the internet and watching videos. Screen recording allows you to:
See which websites they visit
Track YouTube or streaming service activities.
Spot any inappropriate content that they may come across.
Game Interactions and In-App Chats
Online games often have chat features where kids can communicate with other players. With screen recording, you can:
Monitor in-game chats for inappropriate language or behavior.
Identify interactions with unknown players.
Keep track of game spending or purchases.
Discover How Qoli.AI Makes Monitoring Easy
If you want to take monitoring to the next level, Qoli.AI is the perfect solution. It makes screen recording easy and effective. You won't miss anything important. With its advanced features, you can easily track activity and maintain peace of mind. Qoli.ai is a perfect parental control software. It is also a hidden screen recording tool.
Step-by-Step Installation Guide
Getting started with Qoli is quick and simple. Just follow these steps to start tracking with ease:
Step-1 : Create Your Account: Visit the Qoli website and sign up with your email.
Step-2 : Log In: Access your account using your credentials.
Step-3 : Download the App: Install the Qoli tracker app on the target device.
Step-4 : Allow Permissions: Grant all necessary permissions for smooth monitoring.
Step-5 : App Runs Silently: The app operates quietly in the background.
Step-6 : Monitor from the Website: Log in to your dashboard and view activities easily.
Step-7 : Access Key Features: Track calls, messages, location, and more with just a few clicks.
Final Thoughts
Screen recording apps are a great way to keep your kids safe online. They let you see what’s happening on their screens right away. This lets you step in when needed and help your kids build good digital habits. Qoli.AI makes monitoring easy. It helps you stay connected and informed without needing constant supervision.
0 notes
Text
Reliable Bulk SMS Service in Mumbai for Businesses

In the digital age, businesses constantly seek cost-effective, high-impact ways to connect with customers. One such powerful tool is bulk SMS marketing, which ensures instant reach, higher engagement, and a better return on investment. Especially in a bustling commercial hub like Mumbai, choosing the right communication platform can be a game-changer. This article explores the benefits, features, and use cases of a quality bulk SMS service in Mumbai.
What is Bulk SMS and Why Does Your Business Need It?
Bulk SMS refers to the process of sending a large number of text messages simultaneously to a targeted group of recipients. This service is often used by businesses for promotional campaigns, alerts, reminders, and customer service updates.
Benefits of Bulk SMS:
Instant Delivery: Messages reach users within seconds.
High Open Rate: SMS has an open rate of over 90%, significantly higher than emails.
Cost-Effective: Compared to traditional marketing channels, SMS marketing is affordable and scalable.
Wide Reach: Almost every mobile user can receive SMS, regardless of the phone type or internet access.
Why Choose a Local Bulk SMS Service in Mumbai?
Mumbai is home to thousands of businesses, from start-ups to enterprises. For local companies, working with a bulk SMS service in Mumbai brings several advantages:
Faster support and response time
Local understanding of market dynamics
Customizable services for regional campaigns
Ease of integration with local CRM and business tools
Choosing a reliable bulk SMS service in Mumbai allows businesses to leverage regional expertise and better communication infrastructure.
Features to Look for in a Bulk SMS Provider
Not all SMS providers offer the same value. When choosing a service, businesses should evaluate the following features:
1. Delivery Speed and Uptime
Ensure that the provider guarantees high delivery rates and minimal downtime to maintain uninterrupted communication.
2. DND and Non-DND Support
The provider should be compliant with TRAI regulations and offer both promotional and transactional SMS support.
3. Real-Time Analytics
Access to detailed reports on message delivery, open rates, and click-throughs helps improve campaign performance.
4. Easy API Integration
Developers should be able to easily integrate the SMS platform with existing software, websites, and mobile apps.
5. Customization and Personalization
Effective SMS campaigns use personalized messages. Choose a provider that supports dynamic fields like names, dates, and offers.
Use Cases of Bulk SMS in Mumbai-Based Businesses
Bulk SMS services can be used across various industries for multiple purposes:
Retail
Send promotional offers, discount codes, and festive greetings to loyal customers.
Healthcare
Share appointment reminders, prescription updates, or health tips with patients.
Education
Notify students and parents about admissions, exam schedules, or event updates.
Finance
Send OTPs, transaction alerts, EMI reminders, and policy renewals.
Events and Hospitality
Promote events, confirm bookings, or share feedback forms post-service.
How to Get Started
Partnering with a trusted bulk SMS service in Mumbai is the first step. Once you sign up, you typically receive access to a web dashboard or API, from where you can upload contacts, compose messages, and track delivery reports.
Some providers also offer ready-made templates, campaign scheduling, and customer segmentation features for targeted outreach.
Conclusion
Whether you're a small business or an enterprise, SMS marketing remains one of the most powerful and direct communication tools. By leveraging a local and experienced bulk SMS service in Mumbai, you can enhance customer engagement, boost sales, and stay ahead of the competition.
Take the first step towards smarter communication by choosing a reliable provider who understands the local market, offers robust features, and ensures compliance with all telecom regulations. Your next successful marketing campaign could just be one text away.
0 notes