#iot data collection
Explore tagged Tumblr posts
Text
IoT Platform Integration: A Step-By-Step Guide
The Internet of Things (IoT) has evolved into a transformative technological paradigm that affects nearly every aspect of our lives. IoT devices, ranging from smart thermostats in homes to sophisticated sensors in industrial settings, generate a staggering volume of data. To harness the full potential of IoT, organizations and individuals alike rely on IoT platforms. However, the often-overlooked key to a successful IoT ecosystem is IoT platform integration. In this comprehensive guide, we’ll delve deep into IoT platform system integration, explore its significance, and provide a detailed roadmap for navigating this complex landscape.
Importance of IoT Platform Integration
The IoT landscape is expanding at an astonishing rate. By 2021, it was estimated that there were over 30 billion connected IoT devices globally. With this exponential growth comes the need for effective management and utilization of IoT-generated data. IoT platforms, which form the foundation of these ecosystems, facilitate the collection, processing, and analysis of data from diverse devices. Yet, the true power of IoT emerges when these platforms can seamlessly communicate and share data with each other. This is where IoT platform integration comes into play.
Consider a Third-Party Integrator
IoT platform integration can be a formidable challenge due to the sheer diversity of devices, protocols, and data sources involved. To navigate this complexity and ensure interoperability of your IoT ecosystem, many organizations turn to third-party integrators. These experts specialize in bridging the gaps between diverse IoT components, saving time, reducing headaches, and ultimately, ensuring that your IoT system operates harmoniously.
Scope of IoT System Integration
Before diving into the intricacies of IoT platform integration, it’s crucial to gain a holistic understanding of the scope of your IoT system. This involves considering the following factors:
1. Device Variety:
Identify the different types of IoT devices present in your ecosystem, ranging from sensors and actuators to gateways and control units.
2. Protocols and Communication:
Take stock of the communication protocols used by these devices, as they play a pivotal role in integration. Common protocols include MQTT, HTTP, CoAP, and more.
3. Data Sources:
Recognize the various data sources within your ecosystem, which may include real-time sensor data, historical databases, external APIs, and more.
4. User Interfaces:
Consider how users interact with your IoT system, whether through mobile apps, web interfaces, or other means.
5. Scalability:
Anticipate the growth of your IoT ecosystem and plan for scalability accordingly.
Understanding these elements is fundamental to planning and executing a successful IoT platform integration strategy.
What IoT platform Integrators Deliver
IoT system integrators offer a wide range of services and solutions to ensure the seamless operation of your IoT ecosystem:
1. Interoperability:
Integrators work to ensure that devices from different manufacturers and with varying communication protocols can communicate seamlessly within your IoT ecosystem.
2. Data Management:
They handle the flow of data from devices to the cloud, ensuring efficient processing, storage, and retrieval of data.
3. Security:
Integrators implement robust security measures to protect sensitive data and IoT devices from cyber threats, safeguarding your entire ecosystem.
4. Scalability:
Integrators design your IoT system to be scalable, accommodating future growth and expansion without major disruptions.
5. Analytics and Insights:
They assist in extracting meaningful insights from the data generated by your IoT devices, enabling data-driven decision-making.
How to Select an IoT System Integrator
Choosing the right IoT system integrator is a critical decision that can significantly impact the success of your IoT project. Here’s a step-by-step guide on how to select the ideal partner:
1. Experience:
Look for integrators with a proven track record in your industry or a related field. Experienced integrators often have a deeper understanding of industry-specific challenges and requirements.
2. References:
Request references from past clients to gauge their satisfaction with the integrator’s services. This can provide valuable insights into the integrator’s reliability and performance.
3. Expertise:
Ensure that the integrator possesses expertise in the specific technologies, protocols, and IoT standards relevant to your project. A knowledgeable integrator is better equipped to address unique challenges.
4. Scalability:
Confirm that the integrator can design your IoT ecosystem with scalability in mind. They should be able to outline how your system can grow seamlessly as your needs evolve.
5. Cost:
While cost is an important factor, it should not be the sole determinant in your decision. Compare quotes from different integrators, but prioritize quality and reliability over cost savings.
6. Communication:
Effective communication is key to a successful partnership. Ensure that the integrator has a clear communication plan in place to keep you updated on project progress.
The Role of Cloud Technology
Cloud technology plays a central role in IoT platform integration, providing a flexible and scalable infrastructure to manage and process the vast amount of data generated by IoT devices. Several major cloud providers offer dedicated IoT platforms and services designed to simplify integration, including AWS IoT, Azure IoT, and Google Cloud IoT. Here’s how cloud technology contributes to IoT integration:
1. Scalability:
Cloud platforms can easily accommodate the growing number of devices and data streams within your IoT ecosystem. They offer the ability to scale resources up or down as needed.
2. Data Processing:
Cloud services provide powerful tools for real-time data processing, analysis, and storage, making it easier to derive valuable insights from IoT data.
3. Device Management:
Cloud platforms often include features for remote device management, allowing you to update firmware, configure settings, and troubleshoot devices from a centralized location.
4. Security:
Cloud providers invest heavily in security measures, including encryption, access control, and threat detection, enhancing the overall security of your IoT ecosystem.
4. Integration Tools:
Many cloud platforms offer pre-built integrations with common IoT protocols and device manufacturers, simplifying the integration process.
Key Takeaways
IoT platform integration is the linchpin of IoT success, enabling the seamless operation of interconnected devices and data sources. To summarize the key takeaways:
Consider a third-party integrator to streamline the integration process and ensure interoperability.
Understand the scope of your IoT system by identifying devices, protocols, data sources, user interfaces, and scalability requirements.
Be aware of what integrators deliver, including interoperability, data management, security, scalability, and analytics capabilities.
When selecting an IoT system integrator, prioritize experience, references, expertise, scalability, cost, and effective communication.
Recognize the crucial role of cloud technology in IoT integration, providing scalability, data processing, device management, security, and integration tools.
By following these steps and understanding the significance of IoT platform integration, you can ensure that your IoT ecosystem operates seamlessly and efficiently, paving the way for innovation and growth in your industry. In a world increasingly shaped by IoT, successful integration is the key to unlocking its boundless potential.
#iot platform#iot#iotdevices#iot platfrom integration#iot data collection#iot technology#iot applications#iotsolutions#iotdashboard
0 notes
Text
#Tags:AI-Driven Analysis#Data Collection#Data Monetization#Elon Musk#facts#Global Connectivity#Global Surveillance#Internet Privacy#IoT Integration#life#Metadata#Podcast#Privacy Concerns#Satellite Internet#Satellite Technology#serious#Social Media Platforms#Space Missions#SpaceX#Starlink#straight forward#Telemetry Data#truth#upfront#website#X (formerly Twitter)
0 notes
Text
The Age of the Digital Precog: How AI Predicts Our Every Move
Just like the precogs could glimpse future events, AI sifts through enormous amounts of data to make informed guesses about what we’ll do next.
Whats On My Mind Today? Who Are You? How to passively gather personal information is a fascinating look into how businesses, marketers, and tech giants employ techniques to connect your protected data to the information you freely share. Passive information gathering means collecting data about a person without actively seeking it or requiring direct interaction. This can happen through…
#AI data gathering#ChatGPT#data transparency#digital privacy#digital surveillance#IoT privacy#MidJourney#passive data collection#personal privacy#predictive AI#public records#social media analysis#synthetic data
0 notes
Text
The Role Of Machine Learning In Predictive Maintenance
A machinery or equipment failure can lead to increased costs, production delays, and downtimes. This further can impact productivity and efficiency as well.

Therefore, before such failures occur, it is important to foresee equipment issues and perform maintenance exactly when needed. This helps maintain productivity and leads to cost savings. By adopting predictive maintenance based on machine learning, manufacturers can reduce downtime and repair time.
Predictive maintenance with machine learning can yield substantial benefits such as minimizing the time for maintenance schedules, cutting down maintenance costs, and increasing the runtime.
In this blog post, we’ll be exploring everything a manufacturer should know about predictive maintenance with the help of machine learning models, its applications, and the future of predictive maintenance. Read More!!!
#machine learning#Predictive Maintenance#Anomalies#Asset performance#Automotive#cost savings#Data analytics#Data collection#Downtime reduction#Equipment failures#Equipment reliability#Healthcare#Historical data#IoT devices#Maintenance schedules
0 notes
Text
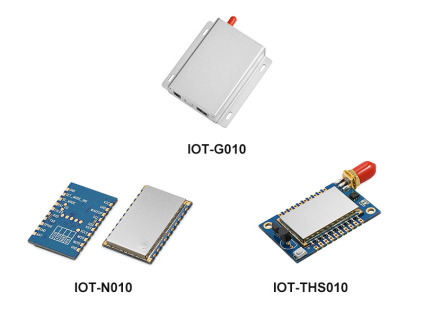
High Compatibility Multi-Node Synchronization and Expansion Support - IOT-G010 Achieves Precise Data Collection and Transmission
The ultra-low power sensor monitoring star network system is mainly used for sensor data acquisition and control of the Internet of Things. The whole network system is composed of gateway IOT-G010 and node IOT-N010/ IOT-THS010, which uses a wireless star network combined with Mesh networking. A good coordination mechanism and precise scheduling algorithm are used internally between the node and the gateway to avoid collisions between data packets in the air. The communication protocol between the node and the gateway has been implemented by the system, and customers can build a reliable acquisition and control network as long as they follow a simple configuration.
What is IoT Data Collection Gateway?
The application system that utilizes a wireless module and sensors to collect data from external sources and input it into the system for data statistics. Its working principle involves automatically collecting non-electrical or electrical signals from wireless modules, sensors, and other analog and digital measurement units, and sending them to a computer system for analysis and processing. Data collection is developed as an application system to measure physical phenomena such as voltage, current, temperature, pressure, humidity, etc. It is based on hardware like wireless modules and sensors, combined with application software and computers, to measure various physical phenomena.
The Features of IoT Sensor Data Collection Gateway
Ultra-Low Power Consumption for Nodes: Designed with ultra-low power consumption to effectively extend battery life, making it suitable for long-term operation, especially for battery-powered devices.
Multi-Point Data Collection: A single gateway can support up to 255 nodes, meeting the needs of large-scale data collection and is ideal for applications requiring simultaneous monitoring of multiple sensors.
Multi-Level Data Collision Avoidance Mechanism: Equipped with a multi-level data collision avoidance mechanism to ensure the reliability and integrity of data transmission when multiple nodes are transmitting data simultaneously.
Over-the-Air Wake-Up and Wake-Up of Subordinate Devices: Supports remote wake-up functionality, allowing devices to enter sleep mode when not in use, thereby effectively reducing power consumption and extending the device's lifespan.
Multiple Crash Prevention Mechanisms: Built-in multiple crash prevention mechanisms ensure long-term stable operation of the device, maintaining high reliability even in complex environments.
Automatic Re-transmission Mechanism: Equipped with an automatic re-transmission mechanism, ensuring that if data loss occurs during transmission, it can be automatically resent, thereby improving the reliability of data transmission.
Multi-Node Time Synchronization: IOT-G010 has powerful time synchronization capabilities, ensuring time consistency across all nodes in the network.
Gateway and Node Time Synchronization: IOT-G010 uses efficient synchronization algorithms to ensure consistent time synchronization between the gateway and all connected nodes.
Multi-Sensor Support: IOT-G010 supports various types of sensors, including but not limited to temperature, humidity, pressure, light, motion, and gas detection. Its robust compatibility and scalability allow it to be widely used in various IoT scenarios, such as smart cities, smart homes, environmental monitoring, and industrial automation. Users can flexibly configure and add different types of sensors based on specific needs.
Quickly customize various functions: The IOT-G010 supports rapid customization, allowing for functional adjustments and optimizations according to different application scenarios. Whether it is data collection frequency, transmission methods, power management, or security strategies, users can flexibly configure these settings through a user-friendly configuration interface or command-line interface.
Data Packet Length: Due to the physical limitations of the wireless chip, the maximum length of a single data packet is 120 bytes. If the customer's data length exceeds 120 bytes, the customer needs to divide the data into smaller packets for transmission.
Rate Selection: The system supports wireless rates from 1200bps to 500Kbps. The selection of the rate requires a balance between power consumption and distance based on the actual application. Choosing a lower rate can achieve longer distances, but it will increase the transmission time, which in turn increases power consumption.

The Functions of IoT Sensor Data Collection Gateway
Data Collection: Collects data from various sensors and devices within the network.
Data Transmission: The IOT-G010 gateway is equipped with multiple data transmission interfaces, such as serial ports, Ethernet, and wireless communication. It can transmit the collected data to a central system or cloud service through these interfaces.
Network Management: The IOT-G010 has robust network management capabilities, effectively managing and maintaining the entire network.
Topology: It supports star network architecture and multi-level automatic relay functions, ensuring stable communication and data transmission between nodes.
Firmware Management: The gateway supports local and remote firmware updates and maintenance, allowing users to upgrade firmware via serial port or OTA (Over-The-Air).
Parameter Configuration: The IOT-G010 allows users to flexibly configure and adjust operating parameters to meet the real-time needs of different application scenarios.
Security: Uses AES-128 encryption technology during data transmission to effectively prevent data theft or tampering.
Easy Expansion of Interfaces: The IOT-G010 supports multiple interfaces to ensure compatibility with various devices and sensors. It has reserved interfaces such as SPI, I2C, and GPIO, providing great expand ability.

The Operating Modes of IoT Sensor Data Collection Gateway Using different commands, the gateway can enter the configuration mode. In this mode, it can set its own parameters and those of the corresponding nodes. After the command is sent, it will automatically enter the normal operation mode. The Data Output Options for IoT Sensor Data Collection Gateway The gateway has two data output options: USB output and Ethernet output. You can switch those two option by using the button. Red light double flash indicates that the serial port is switched to the Ethernet module and outputs data through the RJ45 interface. Blue light double flash indicates that the serial port is switched to the USB-to-serial chip and outputs data through the USB interface. The IOT-G010 IoT sensor data collection gateway from NiceRF company, with its powerful features, reliable performance, and flexible expand-ability, meets various IoT application’s needs. It is a comprehensive and high-performance IoT sensor data collection gateway that provides users with efficient and reliable IoT solutions.
For details, please click:https://www.nicerf.com/products/ Or click:https://nicerf.en.alibaba.com/productlist.html?spm=a2700.shop_index.88.4.1fec2b006JKUsd For consultation, please contact NiceRF (Email: [email protected]).
0 notes
Text
Battery-operated Remote Terminal Units Market Research, Size, Share, Analysis, Overview and Regional Outlook Study 2017 – 2032
The market for Remote Terminal Units (RTUs) that are battery-operated allows them to function in isolated or off-grid regions where access to a reliable power supply is restricted. RTUs are electronic devices used to monitor and manage remote equipment and processes in many different industries, such as oil and gas, water and wastewater management, power distribution, and telecommunications. Here is a summary of the market for battery-operated RTUs, including information on demand:
Market Overview: Due to a number of circumstances, the market for battery-operated RTUs has been expanding. The need for battery-operated RTUs has been fueled by the necessity for remote monitoring and control capabilities in various industries, particularly in places with weak power infrastructure. These devices enable efficient monitoring and control of remote assets without the requirement for a continual external power source thanks to their dependable and autonomous operation.
Demand Drivers:
1. Real-time monitoring and control of assets: situated in remote or isolating locations are necessary in many businesses. Without the requirement for a sizable power infrastructure or reliance on cable connections, battery-operated RTUs allow for effective data gathering, monitoring, and control of these assets.
2. Applications Off-Grid: In off-grid applications where access to a dependable power supply is restricted or nonexistent, battery-operated RTUs are widely used. Examples include remote water pumping stations in rural areas, environmental monitoring stations, remote weather monitoring stations, and remote oil and gas wellheads.
3. Emergency and Temporary Installations: Whereas immediate deployment is necessary, battery-powered RTUs are also used in emergency and temporary installations. When catastrophe recovery, building projects, or temporary infrastructure installations are taking place, these machines can instantly provide remote monitoring and control capabilities.
4. Environmental Monitoring: Data collection from remote weather stations, air quality sensors, and water quality sensors are all important aspects of environmental monitoring that battery-operated RTUs play a key role in. Continuous monitoring is made possible in remote or environmentally delicate locations by these equipment.
5. IoT Connectivity: The need for battery-operated RTUs has increased as the Internet of Things (IoT) is becoming more widely used in a variety of businesses. These devices are essential parts of IoT networks because they provide seamless data transmission, communication, and control between remote assets and central management systems.
Here are some of the key benefits for Stakeholders:
Remote Monitoring and Control
Flexibility and Mobility
Cost-Effective Deployment
Resilience to Power Outages
Integration with IoT and Smart Grids
Increased Data Accessibility
Environmental Monitoring and Compliance
Rapid Deployment for Emergency Response
Redundancy and Reliability
Scalability and Future-Proofing
We recommend referring our Stringent datalytics firm, industry publications, and websites that specialize in providing market reports. These sources often offer comprehensive analysis, market trends, growth forecasts, competitive landscape, and other valuable insights into this market.
By visiting our website or contacting us directly, you can explore the availability of specific reports related to this market. These reports often require a purchase or subscription, but we provide comprehensive and in-depth information that can be valuable for businesses, investors, and individuals interested in this market.
“Remember to look for recent reports to ensure you have the most current and relevant information.”
Click Here, To Get Free Sample Report: https://stringentdatalytics.com/sample-request/battery-operated-remote-terminal-units-market/10333/
Market Segmentations:
Global Battery-operated Remote Terminal Units Market: By Company • SIEMENS • SENECA • Omniflex • King Pigeon Communication Co.,Limited • Servelec Group • TEKBOX • Micro Sensor Co., Ltd. • Hitachi Group • Remsdaq Ltd Global Battery-operated Remote Terminal Units Market: By Type • GPRS • GSM • Modular • Others Global Battery-operated Remote Terminal Units Market: By Application • Power Industry • Government and Utilities • Industrial Global Battery-operated Remote Terminal Units Market: Regional Analysis The regional analysis of the global Battery-operated Remote Terminal Units market provides insights into the market's performance across different regions of the world. The analysis is based on recent and future trends and includes market forecast for the prediction period. The countries covered in the regional analysis of the Battery-operated Remote Terminal Units market report are as follows: North America: The North America region includes the U.S., Canada, and Mexico. The U.S. is the largest market for Battery-operated Remote Terminal Units in this region, followed by Canada and Mexico. The market growth in this region is primarily driven by the presence of key market players and the increasing demand for the product. Europe: The Europe region includes Germany, France, U.K., Russia, Italy, Spain, Turkey, Netherlands, Switzerland, Belgium, and Rest of Europe. Germany is the largest market for Battery-operated Remote Terminal Units in this region, followed by the U.K. and France. The market growth in this region is driven by the increasing demand for the product in the automotive and aerospace sectors. Asia-Pacific: TheAsia-Pacific region includes Singapore, Malaysia, Australia, Thailand, Indonesia, Philippines, China, Japan, India, South Korea, and Rest of Asia-Pacific. China is the largest market for Battery-operated Remote Terminal Units in this region, followed by Japan and India. The market growth in this region is driven by the increasing adoption of the product in various end-use industries, such as automotive, aerospace, and construction. Middle East and Africa: The Middle East and Africa region includes Saudi Arabia, U.A.E, South Africa, Egypt, Israel, and Rest of Middle East and Africa. The market growth in this region is driven by the increasing demand for the product in the aerospace and defense sectors. South America: The South America region includes Argentina, Brazil, and Rest of South America. Brazil is the largest market for Battery-operated Remote Terminal Units in this region, followed by Argentina. The market growth in this region is primarily driven by the increasing demand for the product in the automotive sector.
Visit Report Page for More Details: https://stringentdatalytics.com/reports/battery-operated-remote-terminal-units-market/10333/
Reasons to Purchase Battery-operated Remote Terminal Units Market Report:
• To obtain insights into industry trends and dynamics, including market size, growth rates, and important factors and difficulties. This study offers insightful information on these topics.
• To identify important participants and rivals: This research studies can assist companies in identifying key participants and rivals in their sector, along with their market share, business plans, and strengths and weaknesses.
• To comprehend consumer behaviour: these research studies can offer insightful information about customer behaviour, including preferences, spending patterns, and demographics.
• To assess market opportunities: These research studies can aid companies in assessing market chances, such as prospective new goods or services, fresh markets, and new trends.
In general, market research studies offer companies and organisations useful data that can aid in making decisions and maintaining competitiveness in their industry. They can offer a strong basis for decision-making, strategy formulation, and company planning.
About US:
Stringent Datalytics offers both custom and syndicated market research reports. Custom market research reports are tailored to a specific client's needs and requirements. These reports provide unique insights into a particular industry or market segment and can help businesses make informed decisions about their strategies and operations.
Syndicated market research reports, on the other hand, are pre-existing reports that are available for purchase by multiple clients. These reports are often produced on a regular basis, such as annually or quarterly, and cover a broad range of industries and market segments. Syndicated reports provide clients with insights into industry trends, market sizes, and competitive landscapes. By offering both custom and syndicated reports, Stringent Datalytics can provide clients with a range of market research solutions that can be customized to their specific needs
Contact US:
Stringent Datalytics
Contact No - +1 346 666 6655
Email Id - [email protected]
Web - https://stringentdatalytics.com/
#Battery-operated Remote Terminal Units#RTU Market#Remote Monitoring#Wireless RTU#Industrial Automation#Battery-powered RTU#IoT (Internet of Things)#Energy Efficiency#Data Collection#Telemetry#Remote Control#Battery-powered Sensors#SCADA (Supervisory Control and Data Acquisition)#Energy Management#Off-grid Applications#Renewable Energy#Battery Technology#Remote Sensing#Communication Protocols#Edge Computing#Connectivity Solutions#Remote Data Acquisition#Condition Monitoring#Asset Management.
0 notes
Text
"In the age of smart fridges, connected egg crates, and casino fish tanks doubling as entry points for hackers, it shouldn’t come as a surprise that sex toys have joined the Internet of Things (IoT) party.
But not all parties are fun, and this one comes with a hefty dose of risk: data breaches, psychological harm, and even physical danger.
Let’s dig into why your Bluetooth-enabled intimacy gadget might be your most vulnerable possession — and not in the way you think.
The lure of remote-controlled intimacy gadgets isn’t hard to understand. Whether you’re in a long-distance relationship or just like the convenience, these devices have taken the market by storm.
According to a 2023 study commissioned by the U.K.’s Department for Science, Innovation, and Technology (DSIT), these toys are some of the most vulnerable consumer IoT products.
And while a vibrating smart egg or a remotely controlled chastity belt might sound futuristic, the risks involved are decidedly dystopian.
Forbes’ Davey Winder flagged the issue four years ago when hackers locked users into a chastity device, demanding a ransom to unlock it.
Fast forward to now, and the warnings are louder than ever. Researchers led by Dr. Mark Cote found multiple vulnerabilities in these devices, primarily those relying on Bluetooth connectivity.
Alarmingly, many of these connections lack encryption, leaving the door wide open for malicious third parties.
If you’re picturing some low-stakes prank involving vibrating gadgets going haywire, think again. The risks are far graver.
According to the DSIT report, hackers could potentially inflict physical harm by overheating a device or locking it indefinitely. Meanwhile, the psychological harm could stem from sensitive data — yes, that kind of data — being exposed or exploited.
A TechCrunch exposé revealed that a security researcher breached a chastity device’s database containing over 10,000 users’ information. That was back in June, and the manufacturer still hasn’t addressed the issue.
In another incident, users of the CellMate connected chastity belt reported hackers demanding $750 in bitcoin to unlock devices. Fortunately, one man who spoke to Vice hadn’t been wearing his when the attack happened. Small mercies, right?
These aren’t isolated events. Standard Innovation Corp., the maker of the We-Vibe toy, settled for $3.75 million in 2017 after it was discovered the device was collecting intimate data without user consent.
A sex toy with a camera was hacked the same year, granting outsiders access to its live feed.
And let’s not forget: IoT toys are multiplying faster than anyone can track, with websites like Internet of Dongs monitoring the surge.
If the thought of a connected chastity belt being hacked makes you uneasy, consider this: sex toys are just a small piece of the IoT puzzle.
There are an estimated 17 billion connected devices worldwide, ranging from light bulbs to fitness trackers — and, oddly, smart egg crates.
Yet, as Microsoft’s 2022 Digital Defense Report points out, IoT security is lagging far behind its software and hardware counterparts.
Hackers are opportunistic. If there’s a way in, they’ll find it. Case in point: a casino lost sensitive customer data after bad actors accessed its network through smart sensors in a fish tank.
If a fish tank isn’t safe, why would we expect a vibrating gadget to be?
Here’s where the frustration kicks in: these vulnerabilities are preventable.
The DSIT report notes that many devices rely on unencrypted Bluetooth connections or insecure APIs for remote control functionality.
Fixing these flaws is well within the reach of manufacturers, yet companies routinely fail to prioritize security.
Even basic transparency around data collection would be a step in the right direction. Users deserve to know what’s being collected, why, and how it’s protected. But history suggests the industry is reluctant to step up.
After all, if companies like Standard Innovation can get away with quietly siphoning off user data, why would smaller players bother to invest in robust security?
So, what’s a smart-toy enthusiast to do? First, ask yourself: do you really need your device to be connected to an app?
If the answer is no, then maybe it’s best to go old school. If remote connectivity is a must, take some precautions.
Keep software updated: Ensure both the device firmware and your phone’s app are running the latest versions. Updates often include critical security patches.
Use secure passwords: Avoid default settings and choose strong, unique passwords for apps controlling your devices.
Limit app permissions: Only grant the app the bare minimum of permissions needed for functionality.
Vet the manufacturer: Research whether the company has a history of addressing security flaws. If they’ve been caught slacking before, it’s a red flag.
The conversation around sex toy hacking isn’t just about awkward headlines — it’s about how we navigate a world increasingly dependent on connected technology. As devices creep further into every corner of our lives, from the bedroom to the kitchen, the stakes for privacy and security continue to rise.
And let’s face it: there’s something uniquely unsettling about hackers turning moments of intimacy into opportunities for exploitation.
If companies won’t take responsibility for protecting users, then consumers need to start asking tough questions — and maybe think twice before connecting their pleasure devices to the internet.
As for the manufacturers? The message is simple: step up or step aside.
No one wants to be the next headline in a tale of hacked chastity belts and hijacked intimacy. And if you think that’s funny, just wait until your light bulb sells your Wi-Fi password.
This is where IoT meets TMI. Stay connected, but stay safe."
https://thartribune.com/government-warns-couples-that-sex-toys-remain-a-tempting-target-for-hackers-with-the-potential-to-be-weaponized/
#iot#I only want non-smart devices#I don't want my toilet to connect to the internet#seriously#smart devices#ai#anti ai#enshittification#smart sex toys
26 notes
·
View notes
Text
It starts with him
What was once a promise of technology to allow us to automate and analyze the environments in our physical spaces is now a heap of broken ideas and broken products. Technology products have been deployed en masse, our personal data collected and sold without our consent, and then abandoned as soon as companies strip mined all the profit they thought they could wring out. And why not? They already have our money.
The Philips Hue, poster child of the smart home, used to work entirely on your local network. After all, do you really need to connect to the Internet to control the lights in your own house? Well you do now!Philips has announced it will require cloud accounts for all users—including users who had already purchased the hardware thinking they wouldn’t need an account (and the inevitable security breaches that come with it) to use their lights.
Will you really trust any promises from a company that unilaterally forces a change like this on you? Does the user actually benefit from any of this?
Matter in its current version … doesn’t really help resolve the key issue of the smart home, namely that most companies view smart homes as a way to sell more individual devices and generate recurring revenue.
It keeps happening. Stuff you bought isn’t yours because the company you bought it from can take away features and force you to do things you don’t want or need to do—ultimately because they want to make more money off of you. It’s frustrating, it’s exhausting, and it’s discouraging.
And it has stopped IoT for the rest of us in its tracks. Industrial IoT is doing great—data collection is the point for the customer. But the consumer electronics business model does not mesh with the expected lifespan of home products, and so enshittification began as soon as those first warranties ran out.
How can we reset the expectations we have of connected devices, so that they are again worthy of our trust and money? Before we can bring the promise back, we must deweaponize the technology.
Guidelines for the hardware producer
What we can do as engineers and business owners is make sure the stuff we’re building can’t be wielded as a lever against our own customers, and to show consumers how things could be. These are things we want consumers to expect and demand of manufacturers.
Control
Think local
Decouple
Open interfaces
Be a good citizen
1) Control over firmware updates.
You scream, “What about security updates!” But a company taking away a feature you use or requiring personal data for no reason is arguably a security flaw.
We were once outraged when intangible software products went from something that remained unchanging on your computer, to a cloud service, with all the ephemerality that term promises. Now they’re coming for our tangible possessions.
No one should be able to do this with hardware that you own. Breaking functionality is entirely what security updates are supposed to prevent! A better checklist for firmware updates:
Allow users to control when and what updates they want to apply.
Be thorough and clear as to what the update does and provide the ability to downgrade if needed.
Separate security updates from feature additions or changes.
Never force an update unless you are sure you want to accept (financial) responsibility for whatever you inadvertently break.
Consider that you are sending software updates to other people’s hardware. Ask them for permission (which includes respecting “no”) before touching their stuff!
2) Do less on the Internet.
A large part of the security issues with IoT products stem from the Internet connectivity itself. Any server in the cloud has an attack surface, and now that means your physical devices do.
The solution here is “do less”. All functionality should be local-only unless it has a really good reason to use the Internet. Remotely controlling your lights while in your own house does not require the cloud and certainly does not require an account with your personal information attached to it. Limit the use of the cloud to only the functions that cannot work without it.
As a bonus, less networked functionality means fewer maintenance costs for you.
3) Decouple products and services.
It’s fine to need a cloud service. But making a product that requires a specific cloud service is a guarantee that it can be enshittified at any point later on, with no alternative for the user owner.
Design products to be able to interact with other servers. You have sold someone hardware and now they own it, not you. They have a right to keep using it even if you shut down or break your servers. Allow them the ability to point their devices to another service. If you want them to use your service, make it worthwhile enough for them to choose you.
Finally, if your product has a heavy reliance on the cloud to work, consider enabling your users to self-host their own cloud tooling if they so desire. A lot of people are perfectly capable of doing this on their own and can help others do the same.
4) Use open and standard protocols and interfaces.
Most networked devices have no reason to use proprietary protocols, interfaces, and data formats. There are open standards with communities and software available for almost anything you could want to do. Re-inventing the wheel just wastes resources and makes it harder for users to keep using their stuff after you’re long gone. We did this with Twine, creating an encrypted protocol that minimized chatter, because we needed to squeeze battery life out of WiFi back when there weren’t good options.
If you do have a need for a proprietary protocol (and there are valid reasons to do so):
Document it.
If possible, have a fallback option that uses an open standard.
Provide tooling and software to interact with your custom protocols, at the very least enough for open source developers to be able to work with it. This goes for physical interfaces as much as it does for cloud protocols.
If the interface requires a custom-made, expensive, and/or hard-to-find tool to use, then consider using something else that is commonly available and off the shelf instead.
5) Be a good citizen.
Breaking paid-for functionality on other people’s stuff is inherently unethical. Consider not doing this! Enshittification is not a technical problem, it is a behavioral one. Offer better products that are designed to resist enshittification, and resist it yourself in everything you do.
Nothing forced Philips to do what they are doing: a human made a decision to do it. They could have just as easily chosen not to. With Twine’s server lock-in, at least we chose to keep it running, for 12 years now. Consider that you can still make a decent living by being honest and ethical towards the people who are, by purchasing your products, paying for your lifestyle.
We didn’t get here by accident. Humans made choices that brought us to this point, and we can’t blame anyone for being turned off by it. But we can choose to do better. We can design better stuff. And we can choose not to mess things up after the fact.
We’re putting this into practice with Pickup. (We also think that part of an IoT reset is giving users the creative freedom of a general-purpose device.) If you’re looking for something better and our product can fill a need you have, consider backing us. We cannot claim to be perfect or have all of the answers, but we are absolutely going to try. The status quo sucks. Let’s do something about it.
Published October 15, 2023 By Jeremy Billheimer
137 notes
·
View notes
Text
The Community-Based Restoration Monitoring System (CBRMS)

Well-designed monitoring programmes can improve the effectiveness of restoration efforts. Monitoring can measure progress toward restoration goals, and further improve the efficacy of the restoration process itself. Monitoring an ongoing project can also directly enhance restoration outcomes and improve future restoration decision making.
Restoration monitoring does pose challenges and frequently faces constraints, including limited funds and human resources. Internet of Things (IoT)-based monitoring systems are available for doing so, but their coverage is limited, and they are unable to show restoration impacts on a local scale.
Accordingly, we developed the Community-Based Restoration Monitoring System (CBRMS). This CIFOR-ICRAF flagship product offers the capacity to work offline, is compatible with more affordable smartphones, allows safe storage on cloud systems, is transparent and accessible, and facilitates local community involvement.
It is designed as an organized system for collecting, processing and validating data necessary for measuring implementation progress and impacts, while empowering communities to participate in monitoring processes.
The mobile application is designed to be user friendly and reliable, and offers high flexibility for modification to suit user requirements.
This book outlines the monitoring system framework and provides guidelines for its application.
We hope it can help practitioners and facilitators in monitoring progress made in restoration efforts on the ground.
#solarpunk#solar punk#solarpunk granny#jua kali solarpunk#indigenous knowledge#reculture#community#informal economy#restoration monitoring#free book#download#PDF#monitoring community based restoration efforts#indonesia
13 notes
·
View notes
Text
“If technocracy wins this battle and they implement it on a global basis, it will again take hundreds of years before the concept of freedom and liberty will resurface again. It will take a very long time; it won’t just come snapping back, it will not be a fade. Once they get control over the economic mechanism, they will virtually have control over life itself. They will make people of the world dance like puppets on a string.” ⁃ Patrick Wood, TN Editor.
This is a very important question. I think about it daily as the meteoric rise of scientism creates a new materialistic priest class, in whom you must put your faith and devotion.
What is Technocracy?
A scientific dictatorship, enabled by full-scale surveillance, in which an elite class of scientists and engineers manages every facet of life. Technocrats are “persons who exercise power by virtue of their technical knowledge.”
Technocracy is the Brave New World in Aldous Huxley’s 1932 novel, which was more a “I just got out of a meeting and here’s how it’s going down,” memo rather than a cautionary tale.
In this presentation about COVID-19, Dr. Lee Merritt, influenced by Patrick Wood’s writings on technocracy, shared the etymology:
Techn = skillKrat = kratos (divine personification of power)
She summed up technocracy: Data gathered on everybody in the world and fed to un-elected officials, who are smarter than everybody, and will use the information to create amazing solutions. It boils down to “power via differential knowledge,” meaning if you have knowledge that only a select few have, you can lord it over the majority of people.
The Internet and Total Surveillance
Once the possibility of a total surveillance state materialized with the inception of the Internet, technocracy became the crown jewel in the Cabal’s totalitarian New World Order agenda.
The timeline is speeding up. Their dreams of ruling the world are veering toward a terrifying reality with artificial intelligence, propaganda in everybody’s pocket, and a bazillion data points on every man, woman, and child on Earth.
Patrick Wood, the OG of technocracy research, said once we reach a scientific dictatorship society … “liberty will be a historic curiosity.”
In order to achieve this goal, the technocrats developed mass surveillance, which has only been possible in the modern age with the Internet. This is their time to act.
Smart meters on houses monitor how much energy you consume.
Credit card transactions track consumer behavior and move people away from hard currency.
Social media fills out the dossier with beliefs, names of friends and family, images, and much more.
The Affordable Care Act digitizes your medical history.
Smart gadgets—Fitbit, Oura Ring, etc.—pass all of your vital stats to central repositories.
Smartphones track where you are, what you’re doing (they can listen in), and what information you’re consuming and entertainment you are consuming.
The Internet of Things (IoT) adds more daily data. What’s in your fridge? What do you watch on TV? And even more nefarious, there are credible reports detailing how they can watch us through our TVs.
Facial recognition software and cameras monitor every square inch of public space.
Virtual assistants like Alexa monitor your every word and train people to be useless (“please machine, turn on that light … I cannot do it myself”).
Public school jams cultural Marxism down the throat of every child, while Common Core collects 400 pieces of data on every child, which is on their record for life.
5 notes
·
View notes
Text

First Industrial Revolution (1760s-1830s): Steam power, water power, and the development of new machines led to a dramatic increase in productivity. This led to the growth of factories and cities and the rise of a new middle class.
Second Industrial Revolution (1870s-1914): Electricity, the internal combustion engine, and the development of new steelmaking techniques led to even more rapid technological change. This revolution was also characterized by the development of new transportation systems, such as the steamship and the railroad, which helped to connect markets and people around the world.
Third Industrial Revolution (1950s-present): Computers, the internet, and robotics led to a new era of automation and connectivity. This revolution has had a profound impact on the way we live, work, and communicate.
Fourth Industrial Revolution (2010s-present): The IoT is a major part of this revolution, which is characterized by the convergence of physical, digital, and biological technologies. This is leading to new possibilities in areas such as artificial intelligence, self-driving cars, and 3D printing.
#iot#iotdevices#iotproducts#iot platform#data collection solutions#data management#data analysis#iotdashboard#iotsolutions
0 notes
Text
IoT Security Challenges in India: Protecting Smart Homes & Connected Devices

IoT is transforming the way people live by making their homes smart with devices such as security cameras, smart locks, and voice assistants. In India, IoT technology is adopted at a pace that cyber threats are rising rapidly. With weak security protocols, outdated software, and unawareness, Indian households are vulnerable to cyberattacks. In this blog, we will explore the major IoT security challenges in India and how individuals can safeguard their smart homes and connected devices. If you are looking to strengthen your understanding of cybersecurity, enrolling in a cyber security course can be a game-changer.
The IoT Boom in India
India is witnessing the highest adoption of IoT across homes and businesses. From smart TVs to intelligent thermostats, IoT is revolutionizing life. This booming technology, however, offers a large target size for hackers too who exploit the vulnerability of devices to gain unauthorized access to data.
Fundamental Drivers of IoT Adoption in India:
Increased internet penetration with low-priced data plans
Government initiatives such as Smart Cities Mission and Digital India
Increasing adoption of smart home devices as they become increasingly affordable
Growing application of industrial IoT in health, agriculture, and manufacturing
Chief IoT Security Challenges in India
Poor Authentication & Default Passwords
Most IoT devices have a factory-set password that the user ignores or fails to change. Hackers exploit these default credentials to take over the devices, entry private networks, and crack sensitive information.
Lack of Security Updates & Patches
Most smart devices have limited or no firmware updates, which makes them vulnerable to cyber threats. Many Indian consumers do not check for security updates, leaving their devices susceptible to known exploits.
Data Privacy Concerns
Smart devices collect vast amounts of personal data, from voice recordings to daily routines. Without stringent data protection policies, this information can be misused or leaked by malicious actors.
Botnet Attacks & DDoS Threats
Cybercriminals hijack unprotected IoT devices to form botnets, which are used to launch massive Distributed Denial of Service (DDoS) attacks. These attacks can cripple networks and cause disruptions to online services.
Unsecured Wi-Fi Networks
Many Indian households rely on poorly secured Wi-Fi connections, providing an easy entry point for hackers. Without encryption or strong passwords, attackers can intercept sensitive information and compromise connected devices.
Absence of Specific Cybersecurity Legislation for IoT
India has advanced in data protection with the Digital Personal Data Protection Act, but there is no dedicated IoT security framework. The absence of it leaves the manufacturer to choose cost over security and sell devices which are not so well protected in the market.
How to Secure Smart Homes & Connected Devices
Change Default Credentials
Always change the default usernames and passwords of the IoT after installation. Use strong, unique passwords and implement multi-factor authentication wherever possible.
Update Firmware Periodically
Scan for software and security updates on all smart devices, and install them as soon as they are available. In case your device can no longer get any updates, consider replacing it with a newer version that is at least as secure.
Secure Your Wi-Fi Network
Use a robust Wi-Fi password, and make sure WPA3 encryption is turned on. Limit remote access to your router, and make an IoT-specific network so that those devices can't contaminate your primary network.
Firewall & Security Solutions The use of firewalls and network security solutions monitors traffic and can block malicious activity on IoT networks. 5. Limit Data Sharing & Permissions
Assess permission for smart appliances and reduce or limit the devices from accessing unsecured personal information. De-activate unused add-ons, remote access in devices.
Cyber Security Courses
IoT-based cyber-attacks are minimized if awareness against the threat builds. To boost that awareness further, take time out to become a certified graduate of cyber security by signing for courses in areas like best security practices, principles of ethical hacking, and defending digital systems.
Road Ahead to Improving Indian IoT Security:
The Indian government, device manufacturers, and consumers must take proactive steps to mitigate IoT security risks. Stronger security standards, public awareness, and robust cybersecurity laws are the need of the hour to secure the future of IoT in India.
Conclusion
IoT devices offer incredible convenience but also introduce significant security risks. Protecting smart homes and connected devices requires a combination of best practices, awareness, and robust cybersecurity measures. By staying informed and adopting the right security strategies, individuals can ensure a safer IoT experience.
If you’re passionate about cybersecurity and want to build expertise in protecting digital systems, consider taking a cyber security course to gain hands-on knowledge and skills in ethical hacking, network security, and data protection.
3 notes
·
View notes
Text
Smart Switchgear in 2025: What Electrical Engineers Need to Know

In the fast-evolving world of electrical infrastructure, smart switchgear is no longer a futuristic concept — it’s the new standard. As we move through 2025, the integration of intelligent systems into traditional switchgear is redefining how engineers design, monitor, and maintain power distribution networks.
This shift is particularly crucial for electrical engineers, who are at the heart of innovation in sectors like manufacturing, utilities, data centers, commercial construction, and renewable energy.
In this article, we’ll break down what smart switchgear means in 2025, the technologies behind it, its benefits, and what every electrical engineer should keep in mind.
What is Smart Switchgear?
Smart switchgear refers to traditional switchgear (devices used for controlling, protecting, and isolating electrical equipment) enhanced with digital technologies, sensors, and communication modules that allow:
Real-time monitoring
Predictive maintenance
Remote operation and control
Data-driven diagnostics and performance analytics
This transformation is powered by IoT (Internet of Things), AI, cloud computing, and edge devices, which work together to improve reliability, safety, and efficiency in electrical networks.
Key Innovations in Smart Switchgear (2025 Edition)
1. IoT Integration
Smart switchgear is equipped with intelligent sensors that collect data on temperature, current, voltage, humidity, and insulation. These sensors communicate wirelessly with central systems to provide real-time status and alerts.
2. AI-Based Predictive Maintenance
Instead of traditional scheduled inspections, AI algorithms can now predict component failure based on usage trends and environmental data. This helps avoid downtime and reduces maintenance costs.
3. Cloud Connectivity
Cloud platforms allow engineers to remotely access switchgear data from any location. With user-friendly dashboards, they can visualize key metrics, monitor health conditions, and set thresholds for automated alerts.
4. Cybersecurity Enhancements
As devices get connected to networks, cybersecurity becomes crucial. In 2025, smart switchgear is embedded with secure communication protocols, access control layers, and encrypted data streams to prevent unauthorized access.
5. Digital Twin Technology
Some manufacturers now offer a digital twin of the switchgear — a virtual replica that updates in real-time. Engineers can simulate fault conditions, test load responses, and plan future expansions without touching the physical system.
Benefits for Electrical Engineers
1. Operational Efficiency
Smart switchgear reduces manual inspections and allows remote diagnostics, leading to faster response times and reduced human error.
2. Enhanced Safety
Early detection of overload, arc flash risks, or abnormal temperatures enhances on-site safety, especially in high-voltage environments.
3. Data-Driven Decisions
Real-time analytics help engineers understand load patterns and optimize distribution for efficiency and cost savings.
4. Seamless Scalability
Modular smart systems allow for quick expansion of power infrastructure, particularly useful in growing industrial or smart city projects.
Applications Across Industries
Manufacturing Plants — Monitor energy use per production line
Data Centers — Ensure uninterrupted uptime and cooling load balance
Commercial Buildings — Integrate with BMS (Building Management Systems)
Renewable Energy Projects — Balance grid load from solar or wind sources
Oil & Gas Facilities — Improve safety and compliance through monitoring
What Engineers Need to Know Moving Forward
1. Stay Updated with IEC & IEEE Standards
Smart switchgear must comply with global standards. Engineers need to be familiar with updates related to IEC 62271, IEC 61850, and IEEE C37 series.
2. Learn Communication Protocols
Proficiency in Modbus, DNP3, IEC 61850, and OPC UA is essential to integrating and troubleshooting intelligent systems.
3. Understand Lifecycle Costing
Smart switchgear might have a higher upfront cost but offers significant savings in maintenance, energy efficiency, and downtime over its lifespan.
4. Collaborate with IT Teams
The line between electrical and IT is blurring. Engineers should work closely with cybersecurity and cloud teams for seamless, secure integration.
Conclusion
Smart switchgear is reshaping the way electrical systems are built and managed in 2025. For electrical engineers, embracing this innovation isn’t just an option — it’s a career necessity.
At Blitz Bahrain, we specialize in providing cutting-edge switchgear solutions built for the smart, digital future. Whether you’re an engineer designing the next big project or a facility manager looking to upgrade existing systems, we’re here to power your progress.
#switchgear#panel#manufacturer#bahrain25#electrical supplies#electrical equipment#electrical engineers#electrical
6 notes
·
View notes
Text
What are the Latest Trends in Building Construction in Dubai?

The construction industry in Dubai has long been a symbol of innovation, luxury, and futuristic design. With its rapid development and architectural marvels, the emirate has consistently set the bar for what is possible in the construction sector. Over the years, the building construction industry in Dubai has evolved significantly, and new trends continue to emerge, reshaping the landscape of urban development. From sustainability to technology integration, Dubai is at the forefront of the latest building construction trends. In this article, we will explore the key trends influencing the building construction sector in Dubai.
1. Sustainable and Green Building Practices
As the global emphasis on sustainability continues to grow, Dubai is also embracing green building practices. This trend is driven by the increasing need for energy-efficient buildings and eco-friendly solutions that minimize the environmental footprint of construction projects. Developers and building construction company in Dubai are now focusing on incorporating sustainable materials, energy-saving technologies, and eco-friendly designs in their projects.
One of the key features of sustainable buildings in Dubai is the use of solar panels. Solar energy is becoming a popular choice for powering buildings, helping to reduce energy consumption and carbon emissions. In addition to this, there is an increased use of recycled materials such as reclaimed wood, steel, and glass, which not only helps to preserve natural resources but also contributes to the reduction of construction waste.
Moreover, Dubai's commitment to sustainability is evident in the numerous green certifications, such as the Dubai Green Building Regulations, which encourage developers to integrate environmentally friendly technologies into their buildings. The use of smart building systems that optimize energy consumption and reduce water usage is also a growing trend. The shift towards green building practices is expected to continue as Dubai aims to reduce its carbon footprint and enhance the quality of life for its residents.
2. Smart and Connected Buildings
The concept of smart buildings has gained significant traction in Dubai over the past few years. With advancements in technology, there is a growing demand for buildings that are equipped with intelligent systems capable of enhancing comfort, convenience, and security. Smart buildings in Dubai are being designed with integrated technologies that allow for real-time monitoring and management of building systems such as lighting, HVAC (heating, ventilation, and air conditioning), security, and energy consumption.
The integration of Internet of Things (IoT) devices into building infrastructure is another trend that is revolutionizing the construction industry in Dubai. These devices can collect data on building performance, detect anomalies, and provide insights into how the building can be optimized for energy efficiency and occupant comfort. For instance, smart thermostats can automatically adjust the temperature based on occupancy, while intelligent lighting systems can dim or brighten according to the time of day or the presence of people.
Building automation systems (BAS) are becoming a crucial part of construction projects, allowing building managers to remotely control and monitor systems, reducing operational costs and improving efficiency. These smart technologies not only enhance the living and working experience but also provide a competitive edge for property developers and investors who are looking to attract tech-savvy tenants.
3. Modular and Prefabricated Construction
Modular and prefabricated construction is gaining popularity in Dubai as a way to speed up the construction process and reduce costs. Prefabricated construction involves assembling parts of a building off-site in a controlled environment before transporting and assembling them at the construction site. This method allows for greater precision and quality control, as the components are built in a factory setting rather than at the construction site.
One of the main benefits of modular and prefabricated construction is the significant reduction in construction time. In Dubai, where there is a constant demand for rapid development, this approach helps to meet deadlines and reduces the overall time required to complete projects. Additionally, it minimizes the disruption to the surrounding environment, as fewer materials are stored and handled on-site.
Another advantage of this construction method is the potential for cost savings. Since much of the work is completed off-site, labor costs are lower, and there is less waste generated. Furthermore, modular and prefabricated construction allows for the creation of more standardized and repeatable designs, which is ideal for large-scale developments such as residential communities or commercial buildings.
4. Use of Advanced Building Materials
Dubai’s construction industry is also witnessing a shift toward the use of advanced building materials that offer improved durability, sustainability, and aesthetic appeal. These materials include high-performance concrete, glass, and steel, as well as newer innovations such as self-healing concrete, transparent aluminum, and carbon fiber.
Self-healing concrete, for example, is a breakthrough material that has the ability to repair its cracks over time. This material can significantly extend the lifespan of buildings and reduce maintenance costs, making it an attractive option for developers in Dubai. Transparent aluminum, on the other hand, offers a unique combination of strength and transparency, making it an ideal material for modern facades and windows.
The use of carbon fiber in construction is also on the rise, particularly in the reinforcement of concrete structures. Carbon fiber is lightweight yet incredibly strong, making it an ideal material for improving the structural integrity of buildings without adding significant weight. As the demand for innovative, high-performance materials continues to grow, building construction companies in Dubai are exploring new ways to incorporate these materials into their projects.
5. Vertical Construction and Skyscrapers
As land space becomes increasingly limited in Dubai, vertical construction continues to be a key trend. Skyscrapers and high-rise buildings are a hallmark of Dubai’s skyline, and this trend is not slowing down. The demand for tall buildings in Dubai is driven by the need to accommodate a growing population and provide commercial and residential spaces in the limited available land area.
Dubai has already set several records in the construction of skyscrapers, including the iconic Burj Khalifa, the tallest building in the world. Vertical construction allows for the development of more compact, space-efficient buildings that maximize the use of available land. In addition, skyscrapers are designed to be multi-purpose, combining residential, commercial, and leisure spaces within the same structure.
In recent years, there has been a push towards even taller and more innovative designs. Architects and developers are constantly pushing the boundaries of what is possible in vertical construction, incorporating advanced technologies and engineering solutions to create more sustainable and energy-efficient high-rise buildings.
6. Luxury and High-End Residential Developments
Dubai has long been known for its luxury real estate market, and this trend shows no signs of slowing down. In recent years, there has been an increasing demand for high-end villas and residential properties that offer exceptional levels of comfort, style, and exclusivity. Developers are focusing on creating luxurious living spaces that cater to the needs and desires of affluent residents.
Villa construction companies in Abu Dhabi and Dubai are capitalizing on this demand by designing and building opulent villas with state-of-the-art amenities, such as private pools, gyms, and expansive gardens. These properties are often located in prime locations, such as beachfront areas or exclusive gated communities, providing residents with the ultimate in privacy and luxury.
The rise of luxury residential developments is also influencing the broader construction market in Dubai. Developers are incorporating cutting-edge designs, high-end finishes, and the latest technologies to ensure that their properties stand out in a competitive market. With a growing number of wealthy investors and residents, the demand for top-tier residential developments is expected to continue.
7. Focus on Mixed-Use Developments
Mixed-use developments are another major trend shaping the construction industry in Dubai. These projects combine residential, commercial, retail, and recreational spaces into a single, integrated development. The goal of mixed-use developments is to create self-sufficient communities where residents can live, work, and play without having to leave the development.
The rise of mixed-use developments in Dubai is driven by the need for more efficient land use and the desire to create vibrant, walkable communities. These developments often feature high-rise buildings, modern amenities, and extensive green spaces, providing a balanced lifestyle for residents and workers alike. Mixed-use developments also offer a sustainable solution to urban growth by reducing the need for long commutes and promoting a more connected, community-oriented way of life.
Conclusion
The construction industry in Dubai is undergoing significant transformations, with new trends and innovations reshaping the way buildings are designed and constructed. From sustainable building practices to the use of cutting-edge technologies, the emirate continues to set the standard for modern construction. As the demand for luxury, smart, and sustainable buildings continues to grow, building construction companies in Dubai will need to adapt and embrace these trends to stay competitive and meet the evolving needs of the market.
With the increasing popularity of modular and prefabricated construction, advanced materials, and vertical construction, Dubai’s skyline will continue to evolve, providing residents and visitors with an ever-changing and dynamic urban landscape. The future of construction in Dubai looks bright, and the trends we are witnessing today are only the beginning of what promises to be an exciting era for the industry.
#Building Contracting Company In Dubai#Building Construction Company In Dubai#General Contracting Company In Abu Dhabi#Best Construction Companies In Abu Dhabi#Contracting Companies In Al Ain#Construction Companies In Al Ain#Interior Design Fit Out Company Dubai#Interior Fit Out Contracting Company Dubai#Fit Out Contracting Company In Abu Dhabi#Villa Construction Companies In Abu Dhabi
2 notes
·
View notes
Text
What is artificial intelligence (AI)?

Imagine asking Siri about the weather, receiving a personalized Netflix recommendation, or unlocking your phone with facial recognition. These everyday conveniences are powered by Artificial Intelligence (AI), a transformative technology reshaping our world. This post delves into AI, exploring its definition, history, mechanisms, applications, ethical dilemmas, and future potential.
What is Artificial Intelligence? Definition: AI refers to machines or software designed to mimic human intelligence, performing tasks like learning, problem-solving, and decision-making. Unlike basic automation, AI adapts and improves through experience.
Brief History:
1950: Alan Turing proposes the Turing Test, questioning if machines can think.
1956: The Dartmouth Conference coins the term "Artificial Intelligence," sparking early optimism.
1970s–80s: "AI winters" due to unmet expectations, followed by resurgence in the 2000s with advances in computing and data availability.
21st Century: Breakthroughs in machine learning and neural networks drive AI into mainstream use.
How Does AI Work? AI systems process vast data to identify patterns and make decisions. Key components include:
Machine Learning (ML): A subset where algorithms learn from data.
Supervised Learning: Uses labeled data (e.g., spam detection).
Unsupervised Learning: Finds patterns in unlabeled data (e.g., customer segmentation).
Reinforcement Learning: Learns via trial and error (e.g., AlphaGo).
Neural Networks & Deep Learning: Inspired by the human brain, these layered algorithms excel in tasks like image recognition.
Big Data & GPUs: Massive datasets and powerful processors enable training complex models.
Types of AI
Narrow AI: Specialized in one task (e.g., Alexa, chess engines).
General AI: Hypothetical, human-like adaptability (not yet realized).
Superintelligence: A speculative future AI surpassing human intellect.
Other Classifications:
Reactive Machines: Respond to inputs without memory (e.g., IBM’s Deep Blue).
Limited Memory: Uses past data (e.g., self-driving cars).
Theory of Mind: Understands emotions (in research).
Self-Aware: Conscious AI (purely theoretical).
Applications of AI
Healthcare: Diagnosing diseases via imaging, accelerating drug discovery.
Finance: Detecting fraud, algorithmic trading, and robo-advisors.
Retail: Personalized recommendations, inventory management.
Manufacturing: Predictive maintenance using IoT sensors.
Entertainment: AI-generated music, art, and deepfake technology.
Autonomous Systems: Self-driving cars (Tesla, Waymo), delivery drones.
Ethical Considerations
Bias & Fairness: Biased training data can lead to discriminatory outcomes (e.g., facial recognition errors in darker skin tones).
Privacy: Concerns over data collection by smart devices and surveillance systems.
Job Displacement: Automation risks certain roles but may create new industries.
Accountability: Determining liability for AI errors (e.g., autonomous vehicle accidents).
The Future of AI
Integration: Smarter personal assistants, seamless human-AI collaboration.
Advancements: Improved natural language processing (e.g., ChatGPT), climate change solutions (optimizing energy grids).
Regulation: Growing need for ethical guidelines and governance frameworks.
Conclusion AI holds immense potential to revolutionize industries, enhance efficiency, and solve global challenges. However, balancing innovation with ethical stewardship is crucial. By fostering responsible development, society can harness AI’s benefits while mitigating risks.
2 notes
·
View notes
Text
The Automation Revolution: How Embedded Analytics is Leading the Way

Embedded analytics tools have emerged as game-changers, seamlessly integrating data-driven insights into business applications and enabling automation across various industries. By providing real-time analytics within existing workflows, these tools empower organizations to make informed decisions without switching between multiple platforms.
The Role of Embedded Analytics in Automation
Embedded analytics refers to the integration of analytical capabilities directly into business applications, eliminating the need for separate business intelligence (BI) tools. This integration enhances automation by:
Reducing Manual Data Analysis: Automated dashboards and real-time reporting eliminate the need for manual data extraction and processing.
Improving Decision-Making: AI-powered analytics provide predictive insights, helping businesses anticipate trends and make proactive decisions.
Enhancing Operational Efficiency: Automated alerts and anomaly detection streamline workflow management, reducing bottlenecks and inefficiencies.
Increasing User Accessibility: Non-technical users can easily access and interpret data within familiar applications, enabling data-driven culture across organizations.
Industry-Wide Impact of Embedded Analytics
1. Manufacturing: Predictive Maintenance & Process Optimization
By analyzing real-time sensor data, predictive maintenance reduces downtime, enhances production efficiency, and minimizes repair costs.
2. Healthcare: Enhancing Patient Outcomes & Resource Management
Healthcare providers use embedded analytics to track patient records, optimize treatment plans, and manage hospital resources effectively.
3. Retail: Personalized Customer Experiences & Inventory Optimization
Retailers integrate embedded analytics into e-commerce platforms to analyze customer preferences, optimize pricing, and manage inventory.
4. Finance: Fraud Detection & Risk Management
Financial institutions use embedded analytics to detect fraudulent activities, assess credit risks, and automate compliance monitoring.
5. Logistics: Supply Chain Optimization & Route Planning
Supply chain managers use embedded analytics to track shipments, optimize delivery routes, and manage inventory levels.
6. Education: Student Performance Analysis & Learning Personalization
Educational institutions utilize embedded analytics to track student performance, identify learning gaps, and personalize educational experiences.
The Future of Embedded Analytics in Automation
As AI and machine learning continue to evolve, embedded analytics will play an even greater role in automation. Future advancements may include:
Self-Service BI: Empowering users with more intuitive, AI-driven analytics tools that require minimal technical expertise.
Hyperautomation: Combining embedded analytics with robotic process automation (RPA) for end-to-end business process automation.
Advanced Predictive & Prescriptive Analytics: Leveraging AI for more accurate forecasting and decision-making support.
Greater Integration with IoT & Edge Computing: Enhancing real-time analytics capabilities for industries reliant on IoT sensors and connected devices.
Conclusion
By integrating analytics within existing workflows, businesses can improve efficiency, reduce operational costs, and enhance customer experiences. As technology continues to advance, the synergy between embedded analytics and automation will drive innovation and reshape the future of various industries.
To know more: data collection and insights
data analytics services
2 notes
·
View notes