#know more about smart coding info solutions
Explore tagged Tumblr posts
Text

In today's hyper-connected world, digital marketing has become the cornerstone of successful business strategies. From startups to multinational corporations, leveraging digital channels to reach and engage with audiences is not just advantageous but essential. Why Digital Marketing Matters: Reach and Accessibility: Unlike traditional marketing, digital platforms allow businesses to reach a global audience instantaneously. Whether through social media, search engines, or email campaigns, the potential reach is unprecedented. Targeted Advertising: Digital marketing enables precise targeting based on demographics, interests, and behaviors. This ensures that marketing efforts are directed towards those most likely to convert, maximizing ROI.
digitalmarketing #seo #socialmediamarketing #searchengineoptimization #alvinitsolutions
#programming#know more about smart coding info solutions#college#youtube#studyblr#tech#code#school#science#student
1 note
·
View note
Note
Am I the Asshole for not adding backdoor access to my killer robots?
Alright, so I [52M] own a massive tech company that produces a wide range of items for a wide range of consumers. One of our most recent projects was a line of highly advanced war machines capable of autonomous self production via the consumption of biomass as emergency fuel. These things cost a pretty penny and have been tested extensively to ensure that they're safe. Well, as safe as a killer robot can be, anyway. These people know what they're paying for, right? I mean, these things aren't really supposed to be killing humans, given that the front lines of every major conflict is all machines nowadays, but they're still pretty deadly. That's kind of the point.
Anyway, given how deadly they are, my engineers insisted on leaving an emergency backdoor, but I vetoed that. These are supposed to be the most secure, unhackable war machines on the market. They've got layers upon layers of encryption and protocols to keep them 100% safe and secure. We don't want anyone claiming that our company is using backdoor access to tamper with the machines, and we don't want customers to be able to hack each other's robots (at least, not without the robot specifically designed to hack other robots). Again, these things have been thoroughly tested, and I really didn't think we needed a backdoor.
Well, fast forward to now, and one of machine swarms is experiencing a minor malfunction. Basically it's severed its own chain of command, and is no longer communicating with its owner. It's on a bit of a rampage, consuming plants, animals, really anything organic to continue to fuel and produce more copies of itself. It sounds very concerning, I know, but I think we can deal with it. The US military is on my ass about it right now, making it out to be my problem, but I don't think it's my fault? I couldn't have predicted that the swarm would go rogue and that we would need backdoor access. I was just making sure these things were secure, and it's not my fault that they experienced a glitch.
Anyway, I have a meeting in a few hours with an old business partner of mine [45F], she's really smart and I'm sure she can help come up with a solution here. It may take some work, but it's not going to be that difficult to take out the rogue swarm and issue a software update for our other customers. My old business partner and I are both smart people, and I have access to pretty much every resource on the planet. This will be easy! I just don't get why everyone is making it into such a big deal.
Tl;dr some killer robots went rogue and everyone thinks it's my fault for not including a backdoor in the code. I think it's an unfortunate fluke that we can fix with ease. AITA?
18 notes
·
View notes
Text
RFID Hotel Key Cards: Beyond Just Door Access

Have you ever considered that the seemingly plain hotel room key card actually has a lot more going on? It doesn’t just open the door to your room; it’s also a crucial tech component behind the scenes of hotel management. Thanks to technology, hotel cards have moved on from being just a simple access tool. They are subtly changing how you experience hotel stays. From boosting security to streamlining check-in, and even helping with eco-friendliness and personal touches, hotel cards are becoming more and more essential in today’s hotels.
The Multiple Roles of Hotel Cards
Security
The main job of hotel cards is to keep things secure. Unlike old-school metal keys, hotel cards—especially RFID ones—offer a lot more safety. Each RFID card has a unique code, which means only the right card can open a specific room. If a card gets lost or stolen, the hotel can quickly deactivate it in their system, so you don't have to worry about the security risks that come with losing a traditional key.
Convenience and Smart Tech
With hotel services getting smarter, hotel cards have become key tools for convenience. Besides unlocking your room, RFID hotel cards can work with access systems for elevators, gyms, pools, and other hotel facilities, letting you use one card for everything. Plus, modern hotel cards save on staff costs by automatically identifying guest info and speeding up check-ins, which really helps cut down on wait times.
Going Green
With more people becoming aware of environmental issues, hotels are starting to pay attention to sustainability. Many places are switching to eco-friendly materials for their key cards, like biodegradable options or cards made from plant-based materials. So, hotel cards need to do their job while also being good for the planet, keeping their environmental footprint low.
RFID Technology: Driving the Smart Evolution of Hotel Keys
RFID (Radio Frequency Identification) tech is at the heart of today’s hotel key cards. Unlike old magnetic stripe cards, RFID keys pack in better security, a longer life, and a smoother user experience. With RFID, data is sent via wireless radio signals, so guests just have to wave the card near the door sensor, and boom—the door unlocks automatically. No more fumbling with inserting a card, plus it helps prevent those pesky magnetic stripe cards from getting scratched or worn out.
RFID cards also come with extra perks. They can easily hook up with hotel systems like POS and billing, letting guests use their RFID cards to pay for meals, shopping, or whatever, with all charges piling up right onto their room bill. The rise of RFID cards not only ramps up the guest experience but also streamlines hotel operations, making everything run a lot smoother.
RFIDCard.com — Your Go-To for Tailored, Cutting-Edge Hotel Card Solutions
RFIDCard.com is a veteran in the hotel card game, with over ten years of solid experience under its belt. They’re all about delivering top-notch, customized RFID card solutions to the hotel industry. They’ve created custom cards for more than 2,000 hotels globally and churn out over 100 million cards every year. Plus, they’ve teamed up with big names like Hilton, Marriott, and Intercontinental for over a decade, so they know the ins and outs of what hotels need, providing tailored card solutions that fit any demand.
A Variety of Material Choices
When it comes to materials, RFIDCard.com has got you covered with plenty of options. Whether you’re into the classic PVC cards or leaning towards the eco-friendly BioPoly™ Stone cards, they’ve got the right solution for you. PVC cards are tough and user-friendly, and RFIDCard.com was a pioneer in using BioPoly™ Stone for card production. This stuff is just as sturdy as PVC but gives you the eco-friendly, biodegradable edge that’s all the rage in sustainable practices.
Smart Tech for Stunning Looks and Durability
RFIDCard.com isn’t just about functionality; they also care about how the cards look. By using cutting-edge techniques like gold/silver sheen, gold/silver foil, and spot UV, every card is designed to pop visually, boosting the hotel’s brand image.
Tailored Design Services
RFIDCard.com provides full-fledged personalized design services, letting hotels tweak their card designs to match their brand vibe. Whether you want something sleek and modern or classic and elegant, they work hand-in-hand with clients to make sure each card hits the right notes of practicality and style. These customized cards are more than just security tools; they're a way to flaunt the hotel's unique brand identity.
Conclusion
Hotel cards have come a long way in the modern hotel game. They’ve shifted from just being keys to multifunctional tools that pack in security, convenience, eco-friendliness, and smart tech. Thanks to RFID technology, these cards are smoother and smarter, boosting hotel operations and improving the guest experience. With more folks focusing on sustainability and personalized touches, hotel cards are keeping up, evolving into a key part of the hotel brand identity. If you’re after top-notch, customized hotel card solutions, check out RFIDCard.com for more info on their products and services.
1 note
·
View note
Text
Why Networking is Key to Real Estate Success in 2025 and How Digital Cards Help
In the competitive world of real estate, connections, and associations are everything. Persuasive networking puts top-performing agents apart, whether you’re connecting clients, building associations, or sourcing properties. However, with the proliferating real estate terrain, conventional approaches are no longer sufficient to keep you ahead of the curve. Enter electronic business cards—the game-changer for current networking. These digital tools deliver convenience, professionalism, and versatility, making them a must-have for real estate professionals in 2025.

Explore why networking is vital to real estate success and how e-business cards can help you stand out in this active industry.
The Role of Networking in Real Estate
Real estate is built on relationships. Customers usually prefer agents they rely on, while collaborations with developers, brokers, and investors drive development possibilities. Networking guarantees you meet new prospects, maintain existing relationships and remain visible in the market.
Why it’s Essential:
Building Trust: Personal connections establish credibility with clients.
Creating Possibilities: Networking extends your reach, unlocking doors to off-market sales and beneficial collaborations.
Staying Competitive: A robust network assures you’re always in the circle, keeping you ahead of trends and getting more referrals.
The Limits of Traditional Business Cards
While paper business cards have been a staple in real estate for decades, they come with their flaws:
Easy to lose or forget.
Limited space for information.
It is expensive and wasteful when updates are needed.
Doesn’t capture your prospect's information where you can nurturing
In 2025, these limitations will push agents to adopt a more innovative alternative: electronic business cards.
How Electronic Business Cards Revolutionize Networking
Electronic business cards (e-business cards) are more than just a contemporary alternative to paper—they’re a networking powerhouse.
Here’s how they transform the way real estate professionals connect:
1.Instant Sharing and Accessibility
You can share and collect contact information with an electronic business card. Whether you’re meeting clients at open houses or networking at industry events, exchanging details becomes effortless. Once you capture contacts in smart contact management, they stay organized and accessible, unlike getting lost in your phone's contact book.
Pro Tip: Always have your card ready on your phone digital wallet so you can take advantage of every opportunity to connect.
2. Showcase More Than Contact Info
Traditional cards offer space for your name, phone number, and email. Electronic business cards let you include property portfolios, video tours, testimonials, and even links to social media profiles.
Why it’s Powerful:
Clients and partners can access everything they need to know about you in one place, creating a lasting impression. They save your contact also with your full profile.
3. Seamless Updates
Real estate is a fast-paced industry. Whether you switch agencies or update your portfolio, you can edit your e-business cards in real time without reprinting costs.
Benefit:
Stay current and professional with zero hassle.
4. Environmentally Friendly
Electronic business cards offer an eco-friendly solution as sustainability becomes a key concern. They reduce paper waste while aligning with environmentally conscious values.
Why It Matters:
Clients appreciate agents who reflect modern, sustainable practices.
Choosing the Best Electronic Business Card for Real Estate
Not all digital cards are created equal. When selecting the best electronic business card, consider features like:
Customization Options: Design your card to reflect your unique brand.
Easy Sharing: Look for tap-and-go or QR code functionality.
Integration: Ensure compatibility with platforms like LinkedIn, CRM tools, or property websites.
Smart contact management: Ensure you have smart contact management with the digital card to manage and nurture all your contacts to grow your network.
Creating an electronic business card that’s tailored to your needs will ensure that you maximize its potential.
The Future of Networking in Real Estate
The real estate industry is moving toward a tech-driven future, and e-business cards are leading the way. They not only simplify networking but also elevate professionalism, making it easier to build trust and foster relationships.
Key Takeaways for 2025:
Networking is your ticket to real estate success; digital tools make it brighter.
Electronic business cards provide flexibility, creativity, and sustainability.
Investing in the best electronic business card ensures you’re always one step ahead in building connections.
Conclusion: Network Smarter, Not Harder
In real estate, your network is your net worth. Embracing tools like electronic business cards helps you stay relevant, accessible, and professional in a competitive market. Don’t just hand over a card—deliver an experience that sets you apart and keeps you at the top of your mind.
Ready to transform the networking game? Create an electronic business card today and unlock new opportunities for success in 2025!
0 notes
Photo

Are you dreaming of building an Accessory Dwelling Unit (ADU) but don’t know how to fund it? 🏘️ We know financing can be overwhelming, but you don’t have to navigate it alone. At Palm Beach ADU Builders, we specialize in making your ADU project easy, from securing construction loans to finalizing the build.
Call us now at (561) 202-2574 for a FREE ADU Financing Analysis and discover the best options to fund your ADU project in West Palm Beach.
https://adubuilderspalmbeach.com
https://youtu.be/CtgIuyT2QfU
If you're thinking about an ADU project, you're probably wondering: how much does it cost to build an ADU? 💸 Or even better, how can you build an ADU for cheap without compromising on quality? Well, we have good news for you. With the right planning, our team of ADU builders can guide you through cost-effective solutions that won’t break the bank.
Here’s the best part—we're not just ADU contractors near you; we're your full-service partner for ADU financing too! That’s right! We specialize in ADU Financing in West Palm Beach. Whether you need help with a construction loan for an ADU or are exploring the best loan rates, we’ve got you covered.
Call (561) 202-2574 today to get your free ADU Construction Loan Quote!
Why Work with Palm Beach ADU Builders?
When it comes to building an ADU, it's essential to have the right team by your side. Here’s why Palm Beach ADU Builders should be your first choice:
Experience Matters: We are top-rated ADU Builders in West Palm Beach with years of experience in designing and building custom ADUs, including garage conversions and prefab ADUs.
Financing Expertise: Not only do we handle construction, but we also work directly with lenders to help you secure the best construction loans for ADUs. We offer a free financing analysis so you can understand your options. Fast and Efficient: Wondering how long it takes to build an ADU? Our streamlined process ensures that your project is completed on time, keeping delays and costs to a minimum.
Cost-Effective Solutions: If you’re worried about how much it costs to build an ADU, we provide smart, budget-friendly solutions to keep your project affordable without sacrificing quality.
Local Expertise: As local ADU contractors and garage conversion specialists in West Palm Beach, we know the ins and outs of Florida building codes. Our homes are Florida Building Code Compliant, so you can be confident in the quality of your build. Ready to Start Your ADU Project?
Whether you’re considering a new build or a garage conversion, we’re here to help you every step of the way. We understand that the idea of securing a construction loan for an ADU can be daunting. That’s why we’re offering a FREE ADU Design Consultation AND a Free ADU Financing Analysis to get you started on the right foot.
Call Palm Beach ADU Builders now at (561) 202-2574 to get started on your ADU journey!
Palm Beach ADU Builders 📍 111 Olive Ave, West Palm Beach, FL 33401 📧 [email protected] 🌐 adubuilderspalmbeach.com
👉 Ready to learn more? Watch our latest videos: 📹 ADU Builder West Palm Beach 📹 Garage Conversion Contractors West Palm Beach 📹 ADU Financing West Palm Beach 📹 Prefab ADU Builders Palm Beach
FAQs:
1. How much does it cost to build an ADU in West Palm Beach? The cost varies based on design, location, and construction method. Call us for a personalized quote!
2. Do you offer financing for ADUs?
Yes! We specialize in ADU Financing and can help secure the best construction loan for your project.
3. How long does it take to build an ADU?
Typically, building an ADU takes 4 to 6 months from start to finish. But every project is unique!
Don’t wait! Your dream ADU is just a call away. Call us now at (561) 202-2574 for a free ADU financing analysis and let’s start building your perfect ADU in West Palm Beach today!
0 notes
Text
the AU that currently occupies my every thought is a Loceit heroes vs villains one.
with like. Roman being the obnoxious superman guy that wants to save the day with his fists and charm and he has his team of other heroes including Patton and Virgil. and Logan doesn’t have any powers but he is good with computers so they have him like an intern or something because someone told Roman he should, since he can’t always solve everything through physical confrontation. specially when it comes to villain Janus, who runs these hyper complicated schemes to steal from banks and museums and mansions and other big scale stuff.
so Logan does a lot for the heroes’ team, because he’s the one figuring out where they’ll go next, how they communicate, hints to what they’re planning, who are their contacts, etc. but Roman and the others (mostly Roman) just wait for Logan to give them whatever info and then go the “actual work”.
but slowly, as Logan learns to hack better and get closer to Janus’ hidden info Janus notices and starts communicating with Logan. through like hidden/codes messages. and Logan doesn’t give it much importance but eventually he starts replying. and it’s just like Janus having fun, leaving riddles here and there whose solutions are hints to what they’re planning (mostly inconsequential stuff, Janus is just testing how far he can get) and Logan has fun solving them.
anyway eventually Roman’s team is short on backup and they choose to take Logan to one of their little adventures. he doesn’t have to fight, but they need him to help look for something in one of Janus’ installations or whatever. except, of course, Logan gets caught.
anyway in person Janus is extremely hot and intimidating and his voice is hypnotic so he leaves Logan speechless until it’s too late and he’s trapped. and of course they talk and Janus is like “join me, you’re too smart and they don’t care about you” and Logan is like “nooo i’m not supposed to…” so Janus offers Logan a deal:
the door to the room where they are is locked. Janus will leave it unlocked for 5 minutes, and in that time logan can go find the heroes, or he can stay and wait for them to find him. if he leaves then everything goes on as if nothing has happened and Janus will keep bothering him.
if he stays, and they do find him, then it’s proved that they do care about Logan, and Janus will leave him alone and won’t even keep playing with him with the riddles and coded messages. if they don’t find him or come back for him at the end of the day, then Logan has to go with Janus.
Janus leaves and Logan’s first instinct is to just leave. but Janus had said some really piercing truths that he can’t get over, and he can’t shake the feeling that he might be right, so he decided to prove him wrong and wait for the others to find him, or at least to get close enough so Logan could scream for help. what he doesn’t know, though, is that they had all already left by the time Janus started the timer.
Janus owns this huge building full of staff (that probably just work on what they’re told and have no idea what they’re actually doing) and that’s where he takes Logan, where he’ll have his own room and an office. at first Logan has many doubts and tries to look for an escape but soon enough he realizes working with Janus is more gratifying than anything he did before, he is treated well, and also he denies it but his attraction for Janus is a big factor to stay lol.
he also meets Remus, who is Janus’ best friend and most trusted employee, even if he doesn’t do much other than threaten the other workers and make sure they do their job right. Remus is the one that shows him around and teaches him all he needs to know to work there.
so Logan just works and hangs out with Remus and he doesn’t have more than a vague idea about the evil plans he’s helping with. he only knows when he’s solved something important because Janus’ flirting goes from smooth and subtle to direct and almost overwhelming for the poor nervous nerd.
and that’s all i’ve got for now.
79 notes
·
View notes
Text
Apritello Express Evidences, part 1
Greetings, Apritello enthusiasts and attention! Here comes a loong post is written by totally nerd. You've been warned. Here we go.
The thing is that Apritello is a double-edged sword. The series shows us established friendship of these two, give us a lot of content with them. We can see development of relationship through interaction between the characters, their reaction about the situations they are put in. We can sense their synergy and bound through the show.
Donnie and April have incredible chemistry, and both options, brotp and otp seems fine to me.
But let me tell you why I ship them.
Apritello is the kind of pairings, which consists of small details, hints, that's hidden, but if you're sharp and attentive one, you will notice that. Apritello has a strong foundation: the best friends trope.
And from the very beginning, it works as planned.
When I start watching show, I could say that April and Donnie are best friends. It is worth noting that April is like an older sister to the other brothers, more of a sisterly figure than a friend, but with Donnie she behaves somewhat differently, namely, as best friend. Obviously, she sets him apart from his brothers, although girl tries to pay attention to all of them equally. And Donnie behaves as well.
Dee's battle shell designs for April needs as well as his. His shell transform into comfy spot for taking ride for April. Special and only for her. Because his bros are not supposed to use it (at least, he carries no one on his back), Donnie carries them by his techno-bó or his limbs.
This tiny detail shows his special treatment to her. April is a very, very special occasion to D. Don does care about her comfort, he accept the way she is. Donatello does not try to prevent her from participating in their affairs because he respects her decisions and is pleased that April can be shoulder to shoulder with him.
D is glad to be at her service.

Yeah, Dee's still playing cool, he has image to perform as tough and coolheaded guy. So Don doesn't show his intentions, interest and feeling to other people (he's tryin', but fails). Because his actions matter. They are always small, hidden, but meaningful.
April, in return, trusts Dee and depends on his tech, even knowing what his inventions are the opposite of success (usually).
Go on. Look at Donnie's facial expressions and body language when April is near.

Donnie seems more relaxed when she's around, happier. His emotional response is always different from his brothers ones.
Oh, and look, he wanted to be first to give her a high three.

They worry about each other. Look at Don. He does worry about her way more than his brothers. Yeah, they all want to protect her, but Donnie is more expressive.

Mayham has no particular sympathy for the brothers: he is afraid of Raph and behaves aggressively, he is indifferent to Leo and Mikey. Mayham immediately takes a liking to April. And then the details come back: he let Donnie touch his neck. The most vulnerable place for any living creation, for a second. Let him to study an important vial without any hesitation. Mayham depends on April trust for Donnie. When everything goes wrong for Don, the little doggie comes to his rescue, just as April would have done. Is the hint transparent enough?

We can see links with "A mystic library", wherе Donnie begins to look for solutions to save April's pet. Yes, this may seem like his next leap, "sit down, I'm smart, and now I'll solve all the problems, watch and learn," but Don says one phrase that opens up the veil of the second plan, what happens behind the scenes. "My illiteral colleagues and I was conducting a mustic research, with a life of the beloved pet, hanging in a bounce".
Strange wording, Donatello. Beloved pet? Not yours, as we can see. I can say, that everything in this sentence is true, but Donnie and Mayham has something more.
Continue. Next episode "Origami tsunami". Interactions are kept to a minimum, as April herself appears for a maximum of 5 minutes in the series itself. But devil is always in the details, dear friends.
When April was attacked and hung up, the only one who excitedly called out to her was Donny. Raph is furious that the thieves have escaped, Leo is frustrated that their plan has failed, and Mikey is worried about the salami.
Yeah, we didn't see his worries about her when she fell, because Donnie is on the mission and must be coolheaded turtle, and second, he's calm because now April life is safe and sound, out of the danger.
Dear passangers, Apritello Express arrives to the next station - episode "War and Pizza".
Bare facts:
1. April has Donnie's number on an emergency call.
2. "Anything for you"
3. Donnie is the reason why Alberto knows April's name.
No one calles April by her name (except for Donnie, while phone call, but Alberto wasn't nearby) it was "Captain O'Neil" by her chief, her badge seems blank. And yeah, you can say, that's just economy of budget, but I assure you: in the first episode we were shown the name of the delivery guy. The animators were not lazy bones and wrore "Stewart" on his badge. So if something isn't there, then it either shouldn't be there, or it really isn't, that's how this show works.
So, the reason explained in the episode. When Al has short circuit, parts of its new code flashed through its mind.

Info about April was in its memory, in its code. Alberto was a lame animatronic, and it seems somewhat outdated. I do really doubt about Alberto is being something smartass machine with complicated AI like Freddy's Pizza's ones. Quite questionable. Donatello fix Al's brain and wrote code, synchronize with his remote control. He put information about Cap O'Neil into animatronic's head. All this pictures are kind of massage: "You was created for birthday celebrations. You are machine, and there concepts of "life" and "birth". Do great party for this birthday kid and April won't be like this". Or, something like that.
So Alberto did - do a memorable party. And he do what his creator programmed him to do, but in his way.
4. In other words, Alberto was a tool to impress April. Don flaunts himself in front of her, stating how he did the upgrade while doing the upgrade, even though April is fully aware of his tech wizard. And his abilities supposed to help Cap O'Neil to finish the birthday party, so she will stay at her job, not fired. All thanks to Donnie and his upgrade Alberto. (Or not)
By the way, Donnie was the last to leave April in ruined "Alberto's". And it's not an isolated case, it is a pattern.
5. They understand each other without words.
First, Donny came at her at the speed of light. Second, she hadn't even finished speaking before Dee was taking Al apart. Third, their chaotic, well-coordinated work? Donnie was a distraction (although he wanted to just take a break from the battle or let Alberto's guard down, while April just knocked him out). Donnie and April are great team, and sometimes the DonniexApril team is much more precise, coordinated, and interdependent than the DonniexBrothers one.
D&A feel each other and anticipate each other's actions, their skills complement each other, creating an incredible synergy of their interaction. They act as a whole, while it's not always possible with his brothers, even though they're family and know each other the way more Donnie know April. And Dee hasn't trained with cap O'Neil.
Donatello didn't show his crush for April. No puppy, loving eyes, no lovey-dovey speeches, no planning schemes (at least, the audience don't see one) . He just want her attention, but stays cool and hidden. D is already her BFF, but still.
The same thing is claimed in 5B episode - Mascot Melee. Donnie has no problems with interaction with idol of his childhood - Atomic Lass. She'd put Leo in a stupor, but Donnie? He playfully challenges her to a dance duel. Yes, he adores this character, who may have become his measure of the attractiveness of others to Donatello, determined his type. But still, he's playing all cool and confident guy, he's really smooth with girls, so you will never see a puppy loving eyes from him. Only two things can betray him at this point: his voice and his body language. Remember, how's soft his voice became for Atomic Lass? Now I want you to remember the scene before, in turtle tank, when April sent guys a meme.
D is the first to respond to the message, despite the fact that Mikey is sitting closest to the screen. And the responding is a little too emotional for this situation, don't you think?
And this face of his. And he comments it. He likes her sense of humour.

The only difference between April and Atomic Lass is that the first one is a real girl who is a friend of their family, practically a member of it; and the other one is just a fictional character. It is easier to say about love for a fictional character, because it brings less problems for a teenager, especially when he is living with three brothers and a father who likes to tease as well. Donatello needs to be careful and outline the area of emotions he could show, so that he does not get hurt.
Now, dear passangers, we are returning to the previous episode, shall we?
Donnie presents to his brothers his precious Turtle tank, but she's gone, and it's really necessary to find out, who has taken her. And the first person to suspect is April.
Something is odd, don't you think? Yeah, Raphael has taken tyre for their "Midnight special", Leo claimed that Donnie's stuff is common, but they are D's beothers. It's natural for family to borrow(stole) stuff of each other. But this trend was not observed in April. She would never steal anything from Donnie, much less steal anything from him.
Actually, there is a good, logical and solid explanation here. April was number 1 in Donatello' suspect list, because he simply told her about Turtle tank. His brothers didn't know he were working at Moon buggy, except Mikey (Orange helps Dee get the vehicle from Repomantis), but they didn't know what exactly Donnie was working for. They didn't know he build the Turtle tank, he kept it a secret, to surprise his brothers. But April knew.
- Alright you! Where's our turtle tank?
- Hi, DONNIE. You have 9 seconds to say, why are you just broke my door.
- Someone's stole Donnie's turtle tank.
- Haha-ow, I see. As your best friend, you naturally suspect me.
- She gets it!
- Oh-ho, don't give me that! You're the only one could taken it!
The only one, because she knew about it.
As Splints said in this episode - "April is not a snitch"
Donatello does trust April and share with her both, sorrows and joys. But we are not shown this directly. We do not see the action itself, we do not see their calls and conversations on the phone late at night, we only see the consequence. We have no choice and take it as a given.
And the way she cooled him down? Fast, efficient, and Donnie seems to used to it. Moreover, she slapped everyone, but still, she throw Don out of window the last. However, why such a large time delay between him, being slapped and him, was throwing out of the window?
And my favourite scene. It was obvious that Donnie had taken the hardest hit (judging by his scream and the way he was putting his knuckles back in place). Don then claims that their inner circle is secure, Mikey tries to make amends for everyone, and April agrees, blowing them a kiss and closing the window. Cute and mean, isn't it? (You're cute! but mean! why do I always go for your type?! - ep. War and Pizza)

Nota bene: Donnie wouldn't apologize to April. Tough, not caring badass boy image, remember? Even to best friends. It's hard to him to express his feelings by using words, he cannot do it in proper way. But he has Mikey, who is so alike inner him. Michelangelo apologizes not only for himself, but for D mostly, because D starts suspected April.
Let's continue: the episode 8B: Hypno Part Deux
• Donnie put "Donnie's blocker" at April's phone to protect her.
It's common thing that your friend install some programs or apps on your device. But you will always ask your friend to do such a favour, and you will always know about what, when and where were installed on your phone.
And April didn't know Donnie had done something with her phone. It was a real surprise for her, to see blocker with "Donnie says no-no-no".

And you know, the interface of his app. The way he tell this current phrase. Donnie could put a huge banner "THE APP YOU WANT DOWNLOAD TO IS A REAL PIECE OF GARBAGE", as usual antiviruses do. But no, voice interface. It makes the app more personal and thoughtful. Because when Don made gifts for his brother, the program was voiced by a computer-generated female voice. Yes, the tank's interface is voiced by Donatello himself, but his voice sounds more like Google than the real Don. And, we talking about HIS BABEY, for a second. Bit still, the point remains.
• Also, Dale.
Dale is nerdy boy in purple, wow, how convenient for making a parallel with certain purple turtle.
But thing is, April doesn't like Dale. He's clingy, remora guy, who has a little obsession with April, even he's not harmful, still, such behaviour freaks girls (and not them only) out. Her classmate is usually tell her what April O'Neil is "his favourite person" and he loves her. There is little that is attractive about this behavior.
So, there is nothing new and unpredictable here that Dale was rejected. Because April didn't, doesn't and won't like him because of his lame personality and strange behaviour. Our girl in yellow do right thing: she clearly sets personal boundaries and does not allow any dubious personalities to invade them. So that's the reason she refuses to go on a date with him at the end. He's weird, obsessed, and she doesn't like him.
Donatello, as far as I concerned from different versions of TMNT, was always a little obsessive with some things. And, you know, putting a blocker inside your best friend's phone seems a little weird, because it's, in simple words, violation of privacy and personal space. And there are people who may regard this as stalking or sorta.
Yeah, for the most part, he gets away with it, not only because April's focus is in a different area, but also because their bond is stronger than April's with anyone else at school.
She has known him for years. Donnie is her best friend. I can't say that it's fine to her when Dee violates her personal space - her phone, but April can accept Donatello's personality in general.
And he does really have good intentions. Donnie installed this blocker, developed by himself only for one reason: to protect personal space April from fishy apps from nowhere, from being hacked and etc. Don knew her too well, how much she depends on stupid apps that will distract her. He also knew well, that he can't be with her 24/7 to fix problems with April's phone, so Dee put a part of himself to prevent any harm in the future.
And again, "Donnie's gifts"'s vibes. Donatello genuinely cared about April, because he wrote, coded, developed, designed, and dubbed it, turned on the database, and installed it all on April's phone. 'cause, you know, writing programs in general is a bit of a hassle, but writing an antivirus is much more difficult, because viruses are changing, and questionable applications are finding ways to bypass. Do you feel how much effort Dee put in for her?
But Donatello didn't mean to fix April, as he tried to do with his brothers. Purple turtle accepts this girl the way she is, and tries his best to play smoothly with April, by adjusting, not being passive aggressive jerk. It's his outstanding way to show his caring nature, soft side.
Remember, small but meaningful actions.
Maybe, Donnie also can foresee that April may be forced to download some suspicious program, but still, it work: he managed to prevent April being hypnotized, even if couldn't be physically with April at the this moment - Dee was working for Repo Mantis, building dog's paradise for Todd. That's why, by the way, Leo and Raph were dragged into this whole situation. Mayham would teleported literally anyone to help his hostess. Donnie just wasn't at the Lair at the moment.

And on this note, we'll take a break for now. Stay tuned, expect parsing of the series, there's a lot to discuss.
Part 2
Part 3
#rottmnt#rise of tmnt#rise of the teenage mutant ninja#rise donnie#rise donatello#rottmnt donatello#hamato donatello#april o'neil#rise april#rottmnt april#aprilxdonnie#rottmnt apritello#apritello#lonnnnnnnng post#sorry not sorry#zero regrets#apritello express
144 notes
·
View notes
Note
i got a question and that question gave me an idea that you may or may not take into account😅. The question was: is the high priestess a good match for the magician? like could you couple them? and that leads me to the idea of,,, creating a post with the couplings between kings & queens (mixed tho cause if they’re the same type they’re obviously a couple like queen & king of pentacles) or from the major arcanas, with a brief description on the couple’s potential? say hierophantxempress, etc
Interesting!! Thanks for the idea. I can do a series on this one whenever I can't do tarot readings. What's your username? Let me credit you or something. Not brief tho since I like to think.


Couple: The High Priestess & The Magician
I give them 10/10. They are similar but different at the same time. The similarities can help them understand each other, the differences can help them support each other.

Individually
Whoever holds The Magician's energy has the ability to manifest desires into reality. Good at spotting potential/opportunity, and how to act on it. They will have more confident (but curious) energy. The Magician will be more obvious and outwardly talented/skillful, probably attract some attention.
Whoever holds The High Priestess' energy has the ability to see and understand nuances and depth, plus the strong intuition. They will have quieter but heavier energy. The High Priestess' ability will be subtler, but people will notice there's something lurking underneath if they pay attention.

As a couple
I'm using he-she pair to prevent confusion
I would imagine that The Magician knows/is able to see the strength of his partner. Other people may wonder what The Magician sees in The High Priestess at first since she can be mysterious. But they will understand it after they talk with The High Priestess and see how insightful she is. Some of them may also find it spooky that she can notice and understand things people usually don't.
The High Priestess can share useful insights and information with The Magician, and The Magician is definitely the type who will use that knowledge to change reality in some way. He is smart and resourceful, so if he is supplied with 'hidden' information that The High Priestess sees, his ability will be enhanced. Especially if she is psychology-inclined, emotionally intelligent or practices divination.
The Magician will bring more opportunistic energy into the connection. The High Priestess will benefit from the union as well since The Magician can help her apply her knowledge in a way that can enhance her strength and multiply her opportunities.

Example of moments
Imagine them both go to a business event; The Magician takes the lead, actively making connections and interacting with the world. The High Priestess is quiet and seemingly harmless, but low-key reading every single person they meet and noticing whatever useful information, which she will share with The Magician after the party ends. And The Magician being the opportunistic person he is, will use that info to get ahead of everyone else in the game.
Imagine them both sitting together on the balcony at night and talking about life; The High Priestess shares something she has learned, with so much depth and nuances. The Magician after listening attentively to The High Priestess, tells her how to use that knowledge to change her reality, how to achieve greater heights in her life, how they can apply that idea in a project, how they can start something groundbreaking together.

Pros and Cons
Pros: smart couple, scheming couple, wisdom can immediately create practical results in their reality. Things work out for them because both can decode the codes of life. Whenever there is a challenge, they can delve deep into it and come back out with a solution. If both are powerful individuals, they probably can come up with an idea/knowledge that can shift the existing paradigm. People cannot lie to them.
Cons: It will be bad if they are too individualistic instead of working together as a couple. If The High Priestess is too secretive and not letting The Magician in. If The Magician is too erratic or irresponsible with their abilities/talents. If them both use their talents against each other, trying to manipulate each other instead of focusing on how to use their abilities to succeed together.

Send me a question about 2-cards couple! Only Major Arcana.
#tarot asks#tarot interpretation#the high priestess#the magician#tarot community#tarotblr#tarot love#asks
31 notes
·
View notes
Note
Last week you mentioned GPG has really serious problems. Could you tell me more about them? I can't find much of anything online.
first, thanks for your patience with this appallingly late reply! september hit me like a truck :P
second: huh, wow, okay, a cursory google search really failed to turn up much stuff, huh. depressing!
i'm-a talk about the summer 2019 keyserver attack, not because that's the only issue / security vuln / fuck-up the project has ever had, but because it's (1) a hilariously bad fuck-up, and (2) generally reflective of how the project deals with security concerns, and thus demonstrates that the project is fundamentally pretty unserious
so.
this gist, by one of GnuPG's maintainers, does an okay job of summarizing the problem. a brief summary:
* one of the putative purposes of OpenPGP is to provide a "web of trust" via keyservers. i know Jane Doe, i meet her in person, i verify she is who she says she is, and i sign her key; that signature gets reflected in some keyserver, which acts like a big phone book. now, in the future, if you can't personally go verify Jane Doe's trustworthiness, but you do trust me, you can trust communications from Jane Doe, and you looked all this info up in the keyserver
* "what if a malicious actor tried to overload the keyserver?!?!" e.g. what if i spam ~150k signatures on some dude's key just to fuck with the network
* the answer, in the case of GnuPG, is, "this software is shitty and bad and can't deal with that volume so it just grinds to a fucking halt"
* ...and also most the keyservers try to copy their data from each other so you can have a ~web of trust~ throughout the network, which means, these malicious keys quickly perpetuate through the entire nnetwork
* which means anyone who receives the Forbidden Key Data TM, in practical terms, has broken their fucking GnuPG install, and that whole ~web of trust~ thing we built up is now unusable
technically speaking, this is not a security lapse per se! no cryptography has been broken; no secret data has been leaked. it is, however, a fairly straightforward denial of service attack, and is probably kind of disappointing if you wanted your security software to, you know, do software things
and look, anyone can be bitten by a nasty bug. you'll never see me being like "WOW WHAT DUMBFUCKS, HOW COULD ANYONE WRITE SUCH A STUPID BUG," because, y'know, there but for the grace of god i go, and all that. if anyone tells you they're smart enough to never write a bug, they're a fucking liar. (my full-time job for a while was literally proving those people liars, and i never fucking failed, not because i am brilliant, but because all have sinned and fallen short of the glory of god. [sorry for all the god stuff; my long-abandoned southern baptist heritage comes through when i'm talking security for some reason])
however! the manner in which you respond to such a vulnerability matters:
* let's say i had discovered this bug in GnuPG. the industry standard, if i'm kind and polite, is: i disclose the bug privately to the maintainers, and they have a 90-day window during which to fix it. if they still haven't fixed the problem at the end of the 90 days, that's fine, that's their prerogative, but *i* also get to announce to the world "hey there's this bad bug, here's how i found it, and here's how to exploit it."
this is done to keep The World In General TM safer. see, i'm just some rando. if *i'm* able to find a bug in your shitty software, then it's guaranteed the NSA or Unit 8200 or some-other-super-secret-government-agency absolutely has the resources and wherewithal to find the same bug. and also, some slimy just-in-it-for-the-money hacker gang probably also has the resources to find it. by telling the company "hey, i will go public with this in 90 days," i'm lighting a fire under their ass to actually fix the problem, rather than just letting them pretend security by obscurity will save them, and if they don't fix it by then, then at least users have a prayer of finding out, hey, these dudes do not take security problems seriously, and making informed choices based on that.
there is some wiggle room in this. for instance, the fuck are cloud vendors supposed to do about something like Spectre/Meltdown? there were some shitty, not-100%-effective mitigations that could be done in software, but fundamentally the only real fix was getting new hardware, and tragically, we cannot redesign, manufacture, and ship brand new CPUs to everybody who might be affected within a 90-day timeframe. ergo, Google Project Zero pushed their disclosure deadline way out on that. but, crucially: they still went public at some point, and Intel did not cry "wah" or "no fair" or anything like that. they worked with researchers as best as they could, and once the cat was out of the bag, they offered public resources to help developers understand how their software might be affected. that's the rules of the game.
compare this to, uh, GnuPG's outrageously shitty response (from the previously-linked gist), which can basically be summarized as:
* "wah ocaml is complicated and we don't know how to maintain our own fucking software wah"
* "ten years [?!?!?!] wasn't enough time for us to fix the problem wah"
* "whoever did this attack is a hater :((((("
which. what. what the actual fuck. those are not actual reasons to not fix your sofwtare.
also, the way in which you present your software matters:
* i've thrown up shitty hobby projects on github before. if someone came to me all earnest with a CVE against them, i'd laugh, append the README to say "yo i threw this together on a weekend while i was buzzed, you should absolutely not be relying on this for anything that matters, xoxo lua." that is 100% fine! advertising THIS SOFTWARE IS NOT NECESSARILY SECURE and thus electing not to give a shit about security problems is fine.
* i've been a part of things that are... somewhere between a hobby project and Real Software TM. e.g., research prototypes that you're hoping will be widely used so you can get a better sense of desired use cases and unexpected constraints, but which you hope will be used primarily by "power users" or others who are interested in that project's specific goals.
such a project may not be able to offer the same kinds of security guarantees as Fancy Corporate Software, and that's fine, so long as they're open and honest about stuff like: what the goals of the project are, what we're sure of and what we're less sure of, how we're vetting our stuff, what our policies are when someone does report a security issue, stuff like that. there's plenty of stuff maintained on a volunteer basis that i'd generally trust because, i expect they'll notify me if there is a serious security concern to be worried about, or they have a long track record of excellence in a narrowly-tailored space, etc. that's all good.
* what you cannot, cannot, cannot do, is: claim to offer some kind of robust security solution to people in actually-precarious situations, and then not actually act like a steward of those person's interests. if you're, oh, telling Venezeulan dissidents "our [shitty hobby] software [with gaping, well-known vulnerabilities that haven't been exploited yet ONLY because no major nation-state entity has felt threatened by our code yet, but if they were so threatened, they could trivially wreck the entire project using a well-documented years-old vulnerability we can't be assed to fix because ocaml is hard i guess] is safe and reliable to use!"
...if you're telling political dissidents that? and then you get over-the-top pissed off at someone pointing out the fucking problem you refuse to fix? and somehow make it all about mememe? then fuck you, sincerely. the threat those dissidents face is not someone breaking the fucking key network. the threat is you, you personally, because you are fucking lying to them about what your software is able to do.
GOD. sorry, just. i reread that link and got so pissed again. fuck that attitude entirely. if you let people down, fucking just sit with that for a bit, okay? sit and think and do better next time. christ.
anyway.
this is a particularly gratuitous example of GnuPG maintainers being little shits, but in general they've been lackadaisical and dismissive some other times in the past when people have brought them real security problems, and then act all pissy if, y'know, people go public with said security problems. i haven't kept up with their work lately (i think maybe the community got kind of annihilated by this keyserver thing?) & i have other bones to pick with any project of that type (it's kind of taking the wrong tack entirely imho), but like, yeah, in general if a software community's response to security bugs is "oh gosh that's hard maybe we'll get to it someday," you should not be trusting that software lol
#filthy hacker shit#LONG post#honestly it took me like three times to keep this from spiraling into a fucking novel so#here's the shortest version i could manage.#hit me up for pissy computer security rants: if you really want to know#also this tone is like... probably more pissy than necessary sorry#there is some more nuance that could be had here but i just get kinda miffed when people claim to do A Security and then do the opposite
17 notes
·
View notes
Text

Are you ready to take your design projects to the next level? Look no further than CorelDRAW, the industry-leading graphic design software that empowers artists, designers, and illustrators worldwide. Why Choose CorelDRAW? Versatility: From vector illustrations to page layouts and photo editing, CorelDRAW offers a wide range of tools to bring your ideas to life. Ease of Use: Whether you're a beginner or a seasoned professional, CorelDRAW's intuitive interface and comprehensive tutorials make it easy to learn and master. #graphics #alvinitsolutions #aits #datavisualization #banner
#programming#studyblr#tech#code#youtube#know more about smart coding info solutions#college#student#school#science
0 notes
Photo


Quick drawing of the main four kiddos to use as sort of an intro post to an AU I’m working on called Lost Footing (thanks to my lovely SO for naming the AU). It’s an AU where the Miraculous Ladybug characters are set in the My Hero Academia world but not in Japan/UA because I wanted to work with different dynamics that don’t quite work there.
I’ll be posting more information as I get it all typed up, I’ll be tagging all posts #ML Lost Footing (link to show only those posts on my blog here).
Brief disclaimer: I haven’t seen like half of S3 and none of S4, it’s been over a year since I watched the part of S3 I did see and who knows how many years since S1-2. I don’t mind if you comment spoilery things but I probably won’t know what you’re talking about ^^;
Here’s some basic info about the world:
World Information
There is no quirk registry/database in France. The exact details of someone’s quirk and whether or not they have a quirk are up to the individual to disclose.
Hero rankings are grouped into S, A, B, C, and D ranks, with no numerical rankings within each group. These ranks are determined by these stats (may be changed later): people skills/likability (both by the general public and when working with other heroes), composure under duress, smarts (ability to recognize danger, think of solutions), combat prowess, and quirk/tech application (how they use their quirk and tech in different scenarios; reckless usage that endangers the user or others lowers the rank). Newer heroes who have little experience in the field may be ranked lower due to the limited opportunity to study them in the field.
Collège Françoise Dupont
A fairly well known hero school in France. They offer Hero, Support, Business and General Studies.
The school uniform is a dark green, with accent colors depending on your course (Hero is gold, Support is Silver, Business is Black, and General Studies is White). The accent color is used for the tie, cufflinks, uniform buttons, and uniform patterns (stripes on the skirt, gym bottoms, etc). Dress code is fairly lenient: there are no uniform shoes required; the jacket does not need to be fully buttoned; the tie is not required; however, at least one item with the course’s accent color must be present at all times.
Applications include a written exam, an interview, a practical exam for those applying for Hero, and a portfolio for those applying for Support. The practical for Hero applicants is a one-on-one spar with a faculty member or Hero alumni, which is recorded and analyzed by a panel (including the sparring opponent) for the student’s composure, smarts, combat prowess, and quirk/tech application. Students who show great potential and/or great desire to learn and improve are most likely to be accepted. The portfolio for Support includes showing plans/blueprints for original technology or improvements on existing technology; prototypes are encouraged but not mandatory. Students are encouraged to submit any prior attempts to allow faculty to analyze their problem solving and process.
Students can request a course change after admission, pending faculty approval. If requesting a change into Hero or Support, they must complete a practical/portfolio as well.
Misc Information
Gabriel Agreste is a famous designer of hero support technology and fashion.
The Miraculous do not exist here; the Kwami, however, are humans that are Pro Heroes.
I’m hoping to draw some comics for the AU but we’ll see how that goes, haha. Will be posting basic info about the chars I’ve already sketched out + their outfits in the AU soon. Feel free to reach out with any comments/questions!
12 notes
·
View notes
Text
How to setup a gaming pc i can access anywhere
Considering Moving To Computer Gaming?
It's time to recognize the most effective gaming blogs of the year. Thankfully, as much more games are being published, extra gaming blogs are being developed. Since it's no longer probable for gamers to attempt out just about every game that releases, blogs have develop into an vital tool in the gamer's toolbox. They offer up-to-date info about new and future releases to help gamers answer their undying query, "Must I devote $60 on this?".
It is complicated to evaluate 15mm rulesets simply because they're frequently so various, so rather than try I will simply say this Patrol Angis stands on its own laurels as an exemplar of modern day wargaming. It is speedy to play, it has elegant systems, and it is not overburdened by rules. It has a operating points system. It benefits significantly from the amazing fluff of the Ion Age and the miniatures that go with it but could simply be employed for any 15mm games you want to play. Regardless of its billing as a one particular-platoon skirmish game I can not see any purpose why it would not hold up nicely with ten+ units on the board.
There are certainly a number of PCs on the industry that, if you make smart selections when it comes to the elements, can provide surprising gaming efficiency at low prices (even pairing all the things with Avira Antivirus Game Mode ). In fact, if you raise the question additional, you can bring home some really remarkable machines, even capable of countering formidable gaming consoles such as the Xbox A single X and PS4 Pro. The instances we reside in boast a clear benefit, particularly considering that industry leaders have launched really strong devices for purposes such as mining and acquiring cryptocurrencies.
Why we like it: The video gaming podcast generally focuses on indie titles, considering that that is what the hosts are personally interested in, but sometimes they also bring a wider assortment of games to the table for discussion. Idle Thumbs is a thoughtful podcast that puts a bit a lot more emphasis on design and style and criticism when analyzing the games. If Idle Thumbs” clicks with you, you can also verify out the podcast Three Moves Ahead” about war and method games, it was made by the same guys.
With Providing Assistant, you can now get cash back each time you buy a new game. Visit the internet site to come across coupon codes valid on Green Man Gaming. You can then comply with the link supplied to go to that website and commence purchasing. As extended as you use Providing Assistant and stay logged in to your account, you'll get a double cash back with each buy that you make. Giving Assistant pays out earnings each and every week on Monday, which helps you get your revenue back more quickly than you believed possible. You also get peace of thoughts since Providing Assistant will respond to any difficulties promptly and support you get the money that you earned automatically deposited in your account. Video game lovers can now earn revenue and save money at the same time.
Tank is a well-optimized free gaming WordPress theme that comes with a responsive layout that displays your content beautifully on phones, widescreen monitors, and almost everything in involving. With the assist of WooCommerce help, you can very easily start an online business conveniently. The theme comes with a How to make a successful gaming blog impressive layout that is infused with charcoal black colour that offers the web page a pretty royal outlook. This theme comes with a design that is special and assists to appeal to individuals with an affinity for the army and tanks in certain.
Ubisoft® and Lenovo have combined their respective knowledge in computer software and hardware to bring you one particular of the hottest eSports titles on stylishly savage gaming PCs. Lenovo is the proud Pc companion of Ubisoft's Rainbow Six®: Siege Pro League and Majors competitive eSports series. Both partners are devoted to offering their gaming communities an unforgettably immersive experience.
Gaming was once deemed a solitary past time, but this assumption is now a issue of the past. These days, gamers share their hobby digitally with other folks from all about the world. This takes location by means of reside Internet sessions on Twitch and even the most well known of social media platforms currently. On social networking web sites like YouTube, blogs and Instagram, influencer video game content material dominates. There are now actually thousands of gaming influencers making content for social media platforms like YouTube and blogs. And the biggest and brightest of these influencers have huge followings. In fact, lots of of the top YouTubers in the planet have been originally gaming influencers.
Powered by NVIDIA Tegra 4, SHIELD transportable is produced for those who demand awesome gaming experiences. It functions precise, tactile controls and the most recent version of Android KitKat, providing you the greatest way to play your favored Android games. Play the games you currently personal or pick out from the finest titles on Google Play and the NVIDIA SHIELD Hub app. With SHIELD portable, Android games will lastly have the console-grade controls and graphics overall performance they deserve.
PenNews is a modern and clever responsive WordPress multiconcept news & magazine web page theme. It really is a strong platform for webmasters across the spectrum. Regardless of marketplace or niche, PenNews has the demos and templates to make your life less complicated. You do not need to have to know any coding to perform the WP Bakery like a pro. Awesome post designs fit diverse stories, to usually provide the message correct. Gaming magazines and news blogs are a perfect fit for PenNews.
Everything You Wanted to Know About ENTERTAINMENT then Were Terrified To Ask
A bustling community of wonderful-minded persons, the game web-site is finest known for producing original & fresh content associated to newly & well-known gaming gears such as headsets, keyboards, laptops, mice, controllers, computer systems and a lot more. The game web-site is loaded with various sections that incorporate expert evaluations, previews, game trailers, cheat codes, discussion forums & video game news. One particular of the most preferred game websites ever, VideoGamer has an intuitive interface & they also run their personal podcast as properly.
Zombie games in AR are the actual hit of today's gaming industry. Zombie GO is 1 prime example of outstanding Augmented Reality shooter games. It brings zombie apocalypse into the genuine world, at least that's what the producer tell. As a player, you walk by means of your dwelling, college or the nearest parking lot and count on zombies to pop up at any second. Then action begins - fight and kill with a weapons of your choice.
SHIELD wireless controller has a significant constructed-in rechargeable Li-ion battery for hours for immersive gaming. With up to 40 hours of gameplay on a single charge, you can use the SHIELD wireless controller for quite a few play sessions without possessing to charge it back up. A single hour of charge supplies up to eight hours of gameplay. The controller charges from empty to complete in less than 5 hours.
Naturally, gaming” as a topic has a extremely broad meaning and there are various solutions these days, each for the casual and hardcore PRO gamer. Though consoles can present access to exclusive titles, which are hardly ever accessible for PCs, this goes hand-in-hand with a greater cost of games. Consoles also feature some gaming nuances within joystick controls, as properly as particular techniques such as progress saving, which is optimized for consoles.
Video games have been around due to the fact the 1950s when the earliest pc scientists started developing easy games as part of their research. Video games remained a hobby of scientists until the 1970s when the initially video game arcades opened. But video games didn't go mainstream until the 1980s when technologies was developed to move arcade games into the house. This ushered in a new era of household console gaming led by organizations like Nintendo, Sega and Atari.
1 note
·
View note
Text
Mission Accomplished
@sanderssidescelebrations Pairing: Creativity | Roman "Princey" Sanders/Logic | Logan Sanders, Anxiety | Virgil Sanders/Morality | Patton Sanders, Dr. Emile Picani/Sleep | Remy Sanders, Dark Creativity | Remus "The Duke" Sanders/Deceit Sanders Prompt: Mistletoe Warnings: sympathetic Deceit and sympathetic Remus, Remy is drunk in the end and so is Remus Summary: Lola and Ramona are gay disasters. Peyton does her best to help them. Operation Logince is in the works. Also it's Christmas time. btw this is a genderbend story- Yes I’m aware this is very late. I’m also working on the others still- Read on AO3
“Peyton, help me.”
“How are you expecting me to help, if I have no idea what you’re talking about?”
“I think I’m in love with Lola?”
Peyton stared at her best friend in disbelief for a moment. “Excuse me, what?”
“Like, I’m so impressed by her? She’s like, seriously smart, and absolutely gorgeous by the way — I can’t make sense of how a person just naturally that pretty? — and like, her way of speaking so articulate? She’s just- I think she might be who I’ve been looking for all this time?”, the brunette girl sighed, almost sounding lovesick.
“Woah there, hold your horses, Ramona, don’t get your hopes too high, you remember what happened the last time you thought a girl was the one?”
“Yeah, kinda weird how Remedee and Delaney are already engaged-”
“Exactly!”
“Well, I don’t think Remedee would be Lola’s type or the other way around, and like I said, the’re engaged, Patty.”
The blonde rolled her eyes and adjusted her glasses. Usually she’d be ecstatic to help her friend in these kinda situation, but she’s been hurt twice in a row and this was a different kind of crush or being in love than Delaney or even Ramona's Ex-Girlfriend.
This was Lola.
Their best friend.
The only reason she had met Virginia.
This was completely different.
She needed proof that this wasn’t going to flop.
“Give me three days.”, Peyton suddenly said, looking back at the girl in front of her. “Then I’ll give you an estimate on if this will work and how long it will take. Sound good?”
Ramona jumped up and hugged the blonde with so much impact, that they almost fell off the coffee table that Peyton had been seated on. “Thank you so much!”
After she got back up, Ramona dusted herself off and smiled sweetly. “I’ll be off then, Rem asked me if I wanted to join her and Dee at Dinner tonight. She claimed that Dee set her up to ask me, but when I said that I was at your place, she looked like a lost puppy, so I had to say yes.”, she chuckled. “So, I’ll text you?”
“See you, Rori!”, Peyton called after her ash she watched her escape through the front door of the apartment. “Virge! I need to talk to you right now!”
Her purple haired roommate and girlfriend stepped out of the room, a black ball of fur on her arm and a grumpy look on her face. “Whaaaat? Pandora and I were trying to take a nap back there, you know?”
“Sorry, Stormcloud, I need you to dig around a bit for me, though.”, She explained got up from the table, heading toward the slightly shorter girl. “You’re adorable, you know? Oh and, Virge, I think you’re okay, too.”
Virginia just stared at her in disbelief. “Who are you and what have you done with my girlfriend? You must’ve finally met Remedee, was she here instead of Ramona and tinted your innocence?”
“Honestly, you’re terrible.”, she deadpanned before kissing the girl on the cheek. “Let’s go cuddle with Pandora and then I’ll explain what’s up?”
“Sounds fantastic.”
After a while of them just lazily petting the furball that Pandora was, Peyton began to speak.
“Ramona is all head over heels for Lola.”
Virginia froze for a moment before jerking her head to the side to look at the blonde. “You’re kidding, right?”
“Why would I be! This is terrible!”
“No, actually, this is fucking perfect!”
Peyton gasped, though it was rather fake, she knew she wasn’t going to be able to change her girlfriends habit of cursing in every situation. Nonetheless, she followed the sound with a rather squeaky “Language!”
“So, why is it perfect?”
“Remember the call that woke us up last night? Lola needed advice. She couldn’t sleep, which is old news, I know, but!”, she paused for dramatic effect. “This wasn’t casual insomnia, Lola and I both know what that feels like and that wasn’t it. Her mind was twisting and turning and no matter what happened, her thoughts drifted to our perfect little princess!”
Peyton squeaked, in excitement this time. “And I have the perfect plan!”, she exclaimed before pulling out her phone and texting her brunette friend.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Open File Mission Name: Operation ‘Logince’ Status: Accepted Code Name: Agent P Agent’s Personal Info: Peyton Elizabeth ‘Ma’ Hart, 23 — In A Relationship Accomplice: No One Miss Prince Would Expect Estimated Success Rate: 78% Estimated Date Of Success: 1st Of January Close File
Permission To Let Miss Peyton E. Hart Take On The Mission And Let Her Do Whatever She Feels Necessary?
[YES.] [NO.] [I HAVE QUESTIONS.]
[I HAVE QUESTIONS.]
Agent P Can Not Answer Any Questions About The Mission. She Did Not Expect Miss Ramona Juliette Prince To Pick This Option, As It Is Unavailable As Of Now.
Do You Accept The Terms and Conditions And Swear To Trust Miss Hart?
[YES] [NO] [*insert curse-word* you.
Yes.]
[*insert curse-word* you.
Yes.]
Thank You For Responding. I Will Now Let You Talk To Miss Hart.
RAMONA I GOT A SOLUTION
I saw, you doofus. I need’a eat with Miss Remedee Kathrina Prince and her girlfriend, miss Delaney Guja for dinner, if you’d excuse me?
Gladly! Say Hi from me!
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
A few weeks after that, the friend group met for their yearly Christmas party, which was more of a calm get together, if you ignored Remedee’s whole behavior, this year it was held at the shared place of Emilie and Ramona.
Peyton and Virginia thought this to be the perfect opportunity to carry out their plan. And they also had a woman on the inside.
Although Emelie wasn’t too keen on just playing with her friends feelings and getting into their relationship, she agreed when the girlfriends explained that both girls had deeply fallen for each other and that they had their reasons to ask for help.
The party was, like every year, set on the night of the 25th. It had been going rather calm, even Remedee was slightly reserved, which had scared Peyton and Ramona a slight bit, but she didn’t mention it, and they had all just exchanged gifts and everyone was being rather cutesy about it.
There were kisses and hugs everywhere, which had Peyton’s heart melting, she loved how they were all just a big family.
After Virginia had slightly hinted at the more-than-friends behavior René and Emelie had toward each other and that they had to find out what that was later, she reminded her girlfriend of their mission. They gave Emelie a small sign that they had talked about before and got to work.
The smallest of the bunch had excused herself to go to the bathroom, her girlfriend had distracted her best friend with some cute photos she had taken of Pandora. And maybe some couple pictures, but Virginia didn’t need to know that.
Emelie had gotten to her part, talking to Lola about the psychology behind dreams, it was a subject she knew the black haired couldn’t resist.
Perfect.
While the plan had been going as it was planned, Remedee and René had sneaked into the kitchen to pop the first bottle of champagne. That would be a problem that the bunch would have to deal with later.
Delaney had to leave earlier, her little sister, Amber, had called, it was something urgent, but she didn’t tell the others why, just that it would be fine and they should continue having fun.
“So basically, our little sunshine is… Actually a sunshine? Or are you just that good at photoshop?”, Ramona had asked, laughing.
Peyton had tried for quite a while to get Ramona in the right position, they needed all of it to be perfect, and had grown frustrated at this point.
How do you make a person move backwards?
As Emelie had noticed that, she gave her friend the tiniest of nods, trying to communicate to her, that she got it.
Because, in comparison to Ramona, Lola didn’t like to be too close to people, so if Emilie moved closer to the black haired, she would subconsciously walk backwards.
That did the job, both unbelievably oblivious girls were now standing back to back, with Peyton and Emilie smiling at each other, hoping the girls wouldn’t notice.
Virginia, who had never went to the bathroom in the first place, had been impatiently waiting on top of the staircase, a huge grin on her face.
“Yo! Teach, Princey!”, she yelled and held her arm out over them.
Peyton held back a squeal while Emilie quietly chuckled.
The mentioned girls were both looking up to see the small arrangement the purple haired was holding.
A mistletoe.
Lola was the first to look down from it and turned to her crush, staring for a bit.
After a while of mentally cursing every single Disney villain she could think of, and that were a lot, Ramona also decided to look away from the mistletoe. Lola was as red as her favorite dress, and the brunette suspected that she’d look the same. “Well, I- I know the rules but if you- I mean we don’t gotta, you know? Like, if you're not wanting to, that’s fine with me- I just-”
While Ramona was trying to form a sentence, Lola considered her chances.
It was a fifty/fifty in her book. Either she would be rejected, or not. She was gonna regret it anyway, but who cared. She would take advantage of that moment.
So Lola did a thing that no one expected, she grabbed the collar of her crushes shirt and pulled her close. “Zip it.”
And then her lips were on Ramona’s.
Virginia almost let the mistletoe fall on top of them in the attempt to keep her composure and took a few pictures short after, the angle possibly not the best, but she knew none of the technically unoccupied girls would be able to move apart from the grins that were getting wider by the second.
As Ramona stood there frozen, thanking whatever deity helped her, Lola grew more and more anxious over her decision. She was about to pull back when the brunette put her arms around her neck and kissed back.
Que a wolf whistle from the general direction of the kitchen.
“Get some, sis!”, was yelled, rather drunkenly.
Both immediately jumped back and Ramona turned to her sister. “Rem!”, she yelled, her voice cracking. “Why?”
“Well, you know?”, Remedee said, still sounding very drunk, getting closer to the bunch with René trailing behind, “Revenge.”
And the way she said it, so serious and sober, had almost scared Ramona, until her twin started laughing and almost falling over.
The brunette girl turned to her best friend. “Peyton?”
“Don’t at me! You granted me permission to do anything!”
“So you decided to make my roommate pull a Brutus on me? How considerate.”
“I asked. And if it weren’t for Virginia I wouldn’t have been able to do it!”
Lola just blinked for a while before clearing her throat. “Excuse me?”
“Riiiiight... So you weren’t in for any of it but I kinda broke my promise?”, Virginia started as she was supporting René and standing with the group.
The black haired raised an eyebrow. “Virginia?”
She sighed and decided to load the literal weight on her shoulders onto Emelie and also finally get rid of the metaphorical one of breaking a promise. “Ramona told Peyton she likes you the day after you so graciously woke me and my cat up because you couldn’t sleep because you’re too gay for this shit. So we talked and figured out we needed to get you two together and well,” the girl looked at her accomplices. “We didn’t think you’d be the one to initiate that. So I’m not sure about these two, but I’m still stunned.”
“So you planned that.”
“Yes.”
“And you all knew about it.”
“Pretty much?”
“And all of you kept shut in front of me?”
“Looks like it.”
Lola nodded. “I’m impressed. That’s literally the first thing ever that you were able to keep from me.”
Peyton’s face lit up. “You’re not mad?”
“Babe, we literally had her and her crush kissing, why would she be mad?”
“Good point.”
Ramona, who was kind of embarrassed at this point, just linked arms with Lola and let her away from the group, so they were sitting on the couch now, talking. Both of them still had the slightest tints of pink on their faces, but both had smiles on their faces.
“Mission accomplished!”, Peyton said, looking back to the others, wanting to hug both her teammates, until she saw how Emilie had to try to keep René away from trying to kiss her.
“You need help there, Em?”, Virginia had asked with a smirk.
“Nope, I’m fine! It’s fine! I’m good.”
And just like that, the team had another mission. Taking care of two drunk disasters who were absolutely horrible.
At least two of them woke up without headaches the next morning.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Open File Mission Name: Operation ‘Logince’ Status: Accepted Agent: Peyton Elizabeth Hart Accomplices: Virginia Church, Emelie Picani End Of Mission: 25th of December Mission Accomplished Close File
#sympathetic dark sides#sympathetic deceit#sympathetic remus#sanders sides holiday month 2019#I'm not late you are#yes this is my valentine's thingy for this year.#fite me#genderbend#fem!sanders sides#logince#moxiety#remile#demus#sanders sides#Logan Sanders#Roman Sanders#Virgil Sanders#Patton Sanders#Remy Sanders#Emile Picani#Remus Sanders#Deceit Sanders#orange dark side#(mentioned)
22 notes
·
View notes
Text

🌟 Explore the World of Data Science at Alvin IT Solutions Virar West! 🌟 Are you fascinated by the power of data and its impact on decision-making? Dive into the realm of Data Science with our comprehensive course at Vurar Alvin IT Solutions Software Training Institute! Whether you're a beginner or aiming to advance your skills, our program is designed to cater to all levels of expertise. Course Highlights: 📊 Fundamentals of Data Science: Understand the core principles and techniques. 🔍 Data Wrangling and Analysis: Learn how to clean, transform, and analyze data effectively. 📈 Machine Learning Essentials: Explore algorithms and their applications. 💻 Hands-on Projects: Apply your learning to real-world scenarios. 🌐 Industry-Relevant Skills: Gain insights into current trends and practices. 🎓 Certification: Earn a recognized certification upon completion. Why Choose Alvin IT Solutions Software Training Institute at Virar ? At Alvin IT Solutions Software Training Institute , we combine theoretical knowledge with practical skills, ensuring our students are well-prepared for the demands of the industry. Our experienced instructors and state-of-the-art facilities create an ideal environment for learning and growth. Who Should Attend? Aspiring Data Scientists Professionals looking to transition into Data Science roles Anyone curious about harnessing the power of data Don't miss this opportunity to embark on a journey towards mastering Data Science at Alvin IT Solutions Software Training Institute ! Limited seats available. Enroll now to secure your spot. For more information and to enroll, visit https://alvinitsolutions.in/ or contact us at 8855839879. Unlock the potential of data with Vurar. Your future in Data Science starts here!
datascience #datascienceinvirar #bestcomputerclassesinvirar #dataenginering #datavisualization #machinelearning #softwaredevelopment
#programming#youtube#college#studyblr#know more about smart coding info solutions#tech#student#code#science#school
0 notes
Text
10 Ways to Protect Yourself from Cybercrime
Cybercrime is any illegal activity that happens online or on the internet. It is mostly perpetrated by hackers and cybercriminals who target computer networks, smart devices, servers, and other data storage equipment – with attacks ranging from security breaches to data or identity theft.
The number of cybercrimes that are happening today might make you think twice about using the internet entirely. However, having knowledge about these threats can be the first step to help protect yourself and your personal data.
Here are 10 steps that you can take to be cybersmart:
Use Strong, Unique Passwords
Any cybersecurity expert would tell you that you should not repeat passwords for this makes it easier for hackers to exploit your information. Your passwords should at least be eight (8) characters, is a combination of numbers and letters, and must include a special symbol.
Manage Your Social Media Settings
We know that you want to let everyone know what’s going on with you through your social media accounts. However, it would be wise to be selective on what you broadcast and put in your profile to deter social engineering cybercriminals. Therefore, the less you share publicly, the better.
Use A Comprehensive Cybersecurity Suite
As we continue to be reliant to technology for our daily tasks, we are also constantly at risk of being a victim of cybercrime. This is the reason why you need a comprehensive solution to help you strengthen your defenses against these threats. For instance, a system like Bitdefender can provide real-time protection against any attacks such as viruses, ransomware, malware, and more.
Keep Your Software Up to date
Cybercriminals frequently use known exploits such as flaws in your existing internet security software or operating system to gain access to your critical data. Therefore, it is important to keep all the solutions you use up to date to make it harder for them to infiltrate your device.
Enable Multi-factor Authentication
A lot of websites today give users the option to enable another authentication process to ensure their security. Two-factor or Multi-factor authentication asks users to type in a separate code apart from their passwords before they can fully enter the site. Enabling this feature makes it much harder for a hacker to break into your accounts.
Back up and Encrypt Your Most Important Data
It’s important to keep copies of your crucial data just to be prepared in case something happens. To be more efficient, you can have copies stored on a local drive like your laptop, another one on an external hard drive like a flash drive, and one remote storage like OneDrive or Dropbox. Data encryption on the other hand is a technique which if a hacker copies or downloads your files, all he will get are just gibberish codes rather than the actual content of those documents. To do this, you can install a software for encryption or change your system settings.
Be Wary of Public Wi-Fi
Free Wi-Fi can be inviting, but you must be careful before connecting to these public networks. When using a public Wi-Fi, anyone who is connected as well can see what you are doing and receiving across the internet. To keep yourself protected, you can use a Virtual Private Network (VPN) to encrypt all your internet traffic and make it more difficult for hackers to spy on you.
Stay Out of Certain Websites
In the real world, we know that some behaviors, actions, and locations can put us at greater risk of being a victim of crime – the same thing goes on the internet. If you are frequently visiting hacker chatrooms, viewing adult content, or going to suspicious sites that you know are scams, you are putting yourself and your data at risk of a cyberattack.
Stay Away from Dubious Emails
Fraudulent emails are not only common, they are getting increasingly convincing as time passes by. If an email asks you to enter your username or password, don’t do it. Instead, you can open your browser and go to the site directly or contact the company’s customer service to make sure that it is a legitimate message. Always remember that reputable sites or companies won’t ask for your login information thru email.
Keep Yourself Updated on Major Data Security Issues
The internet is full of cybersecurity articles that will keep you updated on the latest trend and what you can do to prevent them. If you are also doing business with a merchant or have an account on a website that’s been impacted by a security breach, find out what information hackers accessed and immediately change your password and settings.
Fighting cybercrime is everybody’s business. By taking precautionary steps to avoid being a victim of these cybercriminals, you are also doing your part in decreasing the rate of these crimes. Always concentrate on what you can do to protect yourself and your data, and always check your accounts for any suspicious activities.
Source: https://ipsystems.ph/10-ways-to-protect-yourself-from-cybercrime/
More info visit: https://ipsystems.ph/
1 note
·
View note
Text
Pluralistic, your daily link-dose: 28 Feb 2020

Today's links
Clearview AI's customer database leaks: Sic semper grifter.
The Internet of Anal Things: Recreating Stelarc's "Amplified Body" with an IoT butt-plug.
Oakland's vintage Space Burger/Giant Burger building needs a home! Adopt a googie today.
Fan-made reproduction of the Tower of Terror: Even has a deepfaked Serling.
Drawing the Simpsons with pure CSS: Impractical, but so impressive.
Let's Encrypt issues its billionth cert: 89% of the web is now encrypted.
AI Dungeon Master: A work in progress, for sure.
How to lie with (coronavirus) maps: Lies, damned lies, and epidemiological data-visualizations.
This day in history: 2019, 2015
Colophon: Recent publications, current writing projects, upcoming appearances, current reading
Clearview AI's customer database leaks (permalink)
Clearview is the grifty facial recognition startup that created a database by scraping social media and now offers cops secretive deals on its semi-magic, never-peer-reviewed technology. The company became notorious in January after the NYT did a deep dive into its secretive deals and its weird, Trump-adjascent ex-male-model founder.
(the Times piece was superbly researched but terribly credulous about Clearview's marketing claims)
https://www.nytimes.com/2020/01/18/technology/clearview-privacy-facial-recognition.html
Yesterday, Clearview warned its customers that it had been hacked and lost its customer database. Today, that customer database was published.
https://www.buzzfeednews.com/article/ryanmac/clearview-ai-fbi-ice-global-law-enforcement
It seems that the NYT weren't the only ones to take Clearview's marketing claims at face value. Its client list includes the DoJ, ICE, Macy's, Walmart, and the NBA. All in all the dump includes more than 2,200 users, including "law enforcement agencies, companies, and individuals around the world."
Included: state AGs, university rent-a-cops, and clients in Saudi Arabia.
"BuzzFeed News authenticated the logs, which list about 2,900 institutions and include details such as the number of log-ins, the number of searches, and the date of the last search."
What does Clearview, a sercurity company, say about this ghastly security breach? "Unfortunately, data breaches are part of life in the 21st century."
Big shrug energy.
"Government agents should not be running our faces against a shadily assembled database of billions of our photos in secret and with no safeguards against abuse," ACLU attorney Nathan Freed Wessler, said to BuzzFeed News.
It is amazing that this needs to be said.
"More than 50 educational institutions across 24 states named in the log. Among them are two high schools."
They are:
Central Montco Technical High School in Pennsylvania
Somerset Berkley Regional High School in Massachusetts
The log also has an entry for Interpol.

The Internet of Anal Things (permalink)
In 1994, the notorious/celebrated electronic artist Stelarc did a performance called "Amplified Body" in which he "controlled robots, cameras and other instruments by tensing and releasing his muscles"
https://web.archive.org/web/20120712181429/https://v2.nl/events/amplified-body

Now, artist/critic Dani Ploeger has revisited Amplified Body with his own performance, which is very similar to Stelarc's, except all the peripherals are controlled by Ploeger tensing and releasing his anal sphincters around a smart butt-plug.
https://www.daniploeger.org/amplified-body
He calls it "B-hind" and it's a ha-ha-only-serious. The buttplug is "an anal electrode with EMG sensor for domestic treatment of faecal incontinence," and the accompanying text is a kind of art-speak parody of IoT biz-speak.
https://we-make-money-not-art.com/b-hind-celebrating-the-internet-of-anal-things
"B-hind offers a unique IoT solution to fully integrate your sphincter muscle in everyday living. The revolutionary anal electrode-powered interface system replaces conventional hand/voice-based interaction, enabling advanced digital control rooted in your body's interior. Celebrating the abject and the grotesque, B‒hind facilitates simple, plug-and-play access to a holistic body experience in the age of networked society."
B-hind was produced in collaboration with V2_, the Lab for the Unstable Media in Rotterdam, and In4Art.

Oakland's vintage Space Burger/Giant Burger building needs a home! (permalink)
Giant Burger was once an East Bay institution, known for its burgers and its gorgeous googie architecture.
https://localwiki.org/oakland/Giant_Burger
One of the very last Giant Burger buildings is now under threat. Though the Telegraph Ave location was rescued in 2015 and converted to a "Space Burger," it's now seeking a new home because it is in the path of the Eastline project.
https://insidescoopsf.sfgate.com/blog/2015/02/24/space-burger-launches-in-uptown-oakland/
The Oakland Heritage Alliance is hoping someone will rescue and move the building: " Do you have an idea for a new location for this mid-century icon? Please contact [email protected] if you know of an appropriate lot, project, or site, preferably downtown."
(Image CC BY-SA, Our Oakland)

Fan-made reproduction of the Tower of Terror (permalink)
Orangele set out to re-create the Walt Disney World Twilight Zone Tower of Terror elevator loading zone in the entry area to their home theater. He's not only done an impressive re-make of the set, but he's also augmented it with FANTASTIC gimmicks.
https://www.hometheaterforum.com/community/threads/the-tower-of-terror-theater.365747/
It's not merely that's he's created a rain, thunder and lightning effect outside the patio doors…

https://www.youtube.com/watch?v=4QMzN0v4mJQ
Nor has he merely created props like this gimmicked side table that flips over at the press of a button.
https://www.youtube.com/watch?v=kY7gQLMnbeA

He's also created HIS OWN ROD SERLING DEEPFAKE.
https://www.youtube.com/watch?time_continue=2&v=MIsjYJwOXSU

I kinda seriously love that he left Rod's cigarette in. The Disney version looks…uncanny.
Not shown: "exploding fuse box with simulated smoke and fire, motorized lighted elevator dial, motorized/lighted pressure gauge, video monitor playing Tower of Terror ride sequence seen through the elevator door wrap, motorized "elevator door'"
He notes, "I was once married, but now as a single person, I can do whatever I want, haha. NEVER getting married again."

Drawing the Simpsons with pure CSS (permalink)
Implementing animated Simpsons illustrations in CSS isn't the most practical web-coding demo I've seen, but it's among the most impressive. Bravo, Chris Pattle!
(not shown: the eyes animate and blink!)
https://pattle.github.io/simpsons-in-css/
#bart .head .hair1 { top: 22px; left: 0px; width: 6px; height: 7px; -webkit-transform: rotate(-22deg) skew(-7deg, 51deg); -ms-transform: rotate(-22deg) skew(-7deg, 51deg); transform: rotate(-22deg) skew(-7deg, 51deg); }
I especially love the quick-reference buttons to see the raw CSS. It reminds me of nothing so much as the incredibly complex Logo programs I used to write on my Apple ][+ in the 1980s, drawing very complicated, vector-based sprites and glyphs.
https://github.com/pattle/simpsons-in-css/blob/master/css/bart.css
Most interesting is the way that this modular approach to graphics allows for this kind of simple, in-browser transformation.


Let's Encrypt issues its billionth cert (permalink)
When the AT&T whistleblower Mark Klein walked into EFF's offices in 2005 to reveal that his employers had ordered him to help the NSA spy on the entire internet, it was a bombshell.
https://www.eff.org/tags/mark-klein
The Snowden papers revealed the scope of the surveillance in fine and alarming detail. According to his memoir, Snowden was motivated to blow the whistle when he witnessed then-NSA Director James Clapper lie to Senator Ron Wyden about the Klein matter.
Since that day in 2005, privacy advocates have been fretting about just how EASY it was to spy on the whole internet. So much of that was down to the fact that the net wasn't encrypted by default.
This was especially keen for @EFF. After all, we made our bones by suing the NSA in the 90s and winning the right for civilians to access working cryptography (we did it by establishing that "Code is speech" for the purposes of the First Amendment).
https://www.eff.org/deeplinks/2015/04/remembering-case-established-code-speech
Crypto had been legal since 1992, but by Klein's 2005 disclosures, it was still a rarity. 8 years later — at the Snowden moment — the web was STILL mostly plaintext. How could we encrypt the web to save it from mass surveillance?
So in 2014, we joined forces with Mozilla, the University of Michigan and Akamai to create Let's Encrypt, a project to give anyone and everyone free TLS certificates, the key component needed to encrypt the requests your web-server exchanges with your readers.
https://en.wikipedia.org/wiki/Let%27s_Encrypt
Encrypting the web was an uphill climb: by 2017, Let's Encrypt had issued 100m certificates, tipping the web over so that the majority of traffic (58%) was encrypted. Today, Let's Encrypt has issued ONE BILLION certs, and 81% of pageloads use HTTPS (in the USA, it's 91%)! This is astonishing, bordering on miraculous. If this had been the situation back in 2005, there would have been no NSA mass surveillance.
Even more astonishing: there are only 11 full-timers on the Let's Encrypt team, plus a few outside contractors and part-timers. A group of people who could fit in a minibus managed to encrypt virtually the entire internet.
https://letsencrypt.org/2020/02/27/one-billion-certs.html
There are lots of reasons to factor technology (and technologists) in any plan for social change, but this illustrates one of the primary tactical considerations. "Architecture is Politics" (as Mitch Kapor said when he co-founded EFF), and the architectural choices that small groups of skilled people make can reach all the way around the world.
This kind of breathtaking power is what inspires so many people to become technologists: the force-multiplier effect of networked code can imbue your work with global salience (for good or ill). It's why we should be so glad of the burgeoning tech and ethics movement, from Tech Won't Build It to the Googler Uprising. And it's especially why we should be excited about the proliferation of open syllabi for teaching tech and ethics.
https://docs.google.com/spreadsheets/d/1jWIrA8jHz5fYAW4h9CkUD8gKS5V98PDJDymRf8d9vKI/edit#gid=0
It's also the reason I'm so humbled and thrilled when I hear from technologists that their path into the field started with my novel Little Brother, whose message isn't "Tech is terrible," but, "This will all be so great, if we don't screw it up."
https://craphound.com/littlebrother
(and I should probably mention here that the third Little Brother book, Attack Surface, comes out in October and explicitly wrestles with the question of ethics, agency, and allyship in tech).
https://us.macmillan.com/books/9781250757531

AI Dungeon Master (permalink)
Since 2018, Lara martin has been using machine learning to augment the job of the Dungeon Master, with the goal of someday building a fully autonomous, robotic DM.
https://laramartin.net/
AI Dungeon Master is a blend of ML techniques and "old-fashioned rule-based features" to create a centaur DM that augments a human DM's imagination with the power of ML, natural language processing, and related techniques.
She's co-author of a new paper about the effort, "Story Realization: Expanding Plot Events into Sentences" which "describes a way algorithms to use "events," consisting of a subject, verb, object, and other elements, to make a coherent narrative."
https://aaai.org/Papers/AAAI/2020GB/AAAI-AmmanabroluP.6647.pdf
The system uses training data (plots from Doctor Who, Futurama, and X-Files) to expand text-snippets into plotlines that continue the action. It's a bit of a dancing bear, though, an impressive achievement that's not quite ready for primetime ("We're nowhere close to this being a reality yet").
https://www.wired.com/story/forget-chess-real-challenge-teaching-ai-play-dandd/
This may bring to mind AI Dungeon, the viral GPT-2-generated dungeon crawler from December.
https://aidungeon.io/
As Will Knight writes, "Playing AI Dungeon often feels more like a maddening improv session than a text adventure."
Knight proposes that "AI DM" might be the next big symbolic challenge for machine learning, the 2020s equivalent to "AI Go player" or "AI chess master."
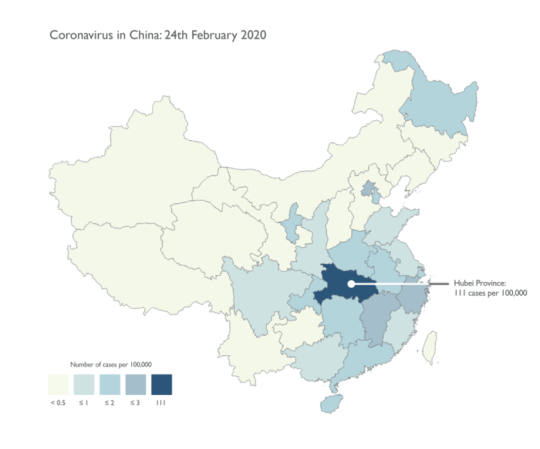
How to lie with (coronavirus) maps (permalink)
The media around the coronavirus outbreak is like a masterclass in the classic "How to Lie With Maps."
https://www.press.uchicago.edu/ucp/books/book/chicago/H/bo27400568.html
Self-described "cartonerd" Kenneth Field's prescriptions for mapmakers wanting to illustrate the spread of coronavirus is a superb read about data visualization, responsibility, and clarity.
https://www.esri.com/arcgis-blog/products/product/mapping/mapping-coronavirus-responsibly/
Both of these images are representing the same data. Look at the map and you might get the impression that coronavirus infections are at high levels across all of China's provinces. Look at the bar-chart and you'll see that it's almost entire Hubei.
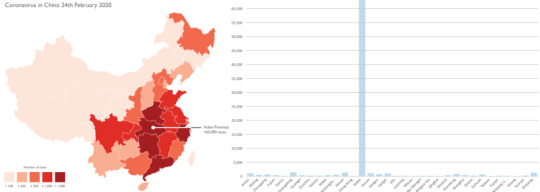
Here's a proposed way to represent the same data on a map without misleading people.

Another point that jumped out: stop coloring maps in red!
"We're mapping a human health tragedy that may get way worse before it subsides. Do we really want the map to be screaming bright red? Red can connotate death, still statistically extremely rare for coronavirus."

This day in history (permalink)
#5yrsago Ad-hoc museums of a failing utopia: photos of Soviet shop-windows https://boingboing.net/2015/02/28/ad-hoc-museums-of-a-failing-ut.html
#5yrsago First-hand reports of torture from Homan Square, Chicago PD's "black site" https://www.theguardian.com/us-news/2015/feb/27/chicago-abusive-confinment-homan-square
#1yrago EFF's roadmap for a 21st Century antitrust doctrine https://www.eff.org/deeplinks/2019/02/antitrust-enforcement-needs-evolve-21st-century
#1yrago Yet another study shows that the most effective "anti-piracy" strategy is good products at a fair price https://www.vice.com/en_us/article/3kg7pv/studies-keep-showing-that-the-best-way-to-stop-piracy-is-to-offer-cheaper-better-alternatives
#1yrago London's awful estate agents are cratering, warning of a "prolonged downturn" in the housing market https://www.bbc.com/news/business-47389160
#1yrago Bad security design made it easy to spy on video from Ring doorbells and insert fake video into their feeds https://web.archive.org/web/20190411195308/https://dojo.bullguard.com/dojo-by-bullguard/blog/ring/
#1yrago Amazon killed Seattle's homelessness-relief tax by threatening not to move into a massive new building, then they canceled the move anyway https://www.seattletimes.com/business/amazon/huge-downtown-seattle-office-space-that-amazon-had-leased-is-reportedly-put-on-market/
#1yrago The "Reputation Management" industry continues to depend on forged legal documents https://www.techdirt.com/articles/20190216/15544941616/pissed-consumer-exposes-new-york-luxury-car-dealers-use-bogus-notarized-letters-to-remove-critical-reviews.shtml

Colophon (permalink)
Today's top sources: Allegra of Oakland Heritage Alliance, Waxy (https://waxy.org/), We Make Money Not Art (https://we-make-money-not-art.com/), Sam Posten (https://twitter.com/Navesink), Slashdot (https://slashdot.org), Kottke (https://kottke.org) and Four Short Links (https://www.oreilly.com/feed/four-short-links).
Hugo nominators! My story "Unauthorized Bread" is eligible in the Novella category and you can read it free on Ars Technica: https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
Upcoming appearances:
Canada Reads Kelowna: March 5, 6PM, Kelowna Library, 1380 Ellis Street, with CBC's Sarah Penton https://www.eventbrite.ca/e/cbc-radio-presents-in-conversation-with-cory-doctorow-tickets-96154415445
Currently writing: I just finished a short story, "The Canadian Miracle," for MIT Tech Review. It's a story set in the world of my next novel, "The Lost Cause," a post-GND novel about truth and reconciliation. I'm getting geared up to start work on the novel now, though the timing is going to depend on another pending commission (I've been solicited by an NGO) to write a short story set in the world's prehistory.
Currently reading: Just started Lauren Beukes's forthcoming Afterland: it's Y the Last Man plus plus, and two chapters in, it's amazeballs. Last week, I finished Andrea Bernstein's "American Oligarchs" this week; it's a magnificent history of the Kushner and Trump families, showing how they cheated, stole and lied their way into power. I'm getting really into Anna Weiner's memoir about tech, "Uncanny Valley." I just loaded Matt Stoller's "Goliath" onto my underwater MP3 player and I'm listening to it as I swim laps.
Latest podcast: Gopher: When Adversarial Interoperability Burrowed Under the Gatekeepers' Fortresses: https://craphound.com/podcast/2020/02/24/gopher-when-adversarial-interoperability-burrowed-under-the-gatekeepers-fortresses/
Upcoming books: "Poesy the Monster Slayer" (Jul 2020), a picture book about monsters, bedtime, gender, and kicking ass. Pre-order here: https://us.macmillan.com/books/9781626723627?utm_source=socialmedia&utm_medium=socialpost&utm_term=na-poesycorypreorder&utm_content=na-preorder-buynow&utm_campaign=9781626723627
(we're having a launch for it in Burbank on July 11 at Dark Delicacies and you can get me AND Poesy to sign it and Dark Del will ship it to the monster kids in your life in time for the release date).
"Attack Surface": The third Little Brother book, Oct 20, 2020.
"Little Brother/Homeland": A reissue omnibus edition with a very special, s00per s33kr1t intro.
7 notes
·
View notes