#making third party controllers by encrypting their controllers in such a way that they can charge 80 for something standard that's required
Explore tagged Tumblr posts
Note
wow that anon is dumb. anyone who is that concerned about starving artists "taking away" from other people in need of donations - is directing their energy the wrong way.
love the comic, hope you can afford that controller <3
Thank you! Me too! I really really really hope I can!
#Anonymous#asks#remember when hardware was durable and could actually last decades later and now companies like sony block third party manufacturers from#making third party controllers by encrypting their controllers in such a way that they can charge 80 for something standard that's required#to even use their system#I LOVE LATE STAGE CAPITALISM /sarcasm
26 notes
·
View notes
Text
"In the age of smart fridges, connected egg crates, and casino fish tanks doubling as entry points for hackers, it shouldn’t come as a surprise that sex toys have joined the Internet of Things (IoT) party.
But not all parties are fun, and this one comes with a hefty dose of risk: data breaches, psychological harm, and even physical danger.
Let’s dig into why your Bluetooth-enabled intimacy gadget might be your most vulnerable possession — and not in the way you think.
The lure of remote-controlled intimacy gadgets isn’t hard to understand. Whether you’re in a long-distance relationship or just like the convenience, these devices have taken the market by storm.
According to a 2023 study commissioned by the U.K.’s Department for Science, Innovation, and Technology (DSIT), these toys are some of the most vulnerable consumer IoT products.
And while a vibrating smart egg or a remotely controlled chastity belt might sound futuristic, the risks involved are decidedly dystopian.
Forbes’ Davey Winder flagged the issue four years ago when hackers locked users into a chastity device, demanding a ransom to unlock it.
Fast forward to now, and the warnings are louder than ever. Researchers led by Dr. Mark Cote found multiple vulnerabilities in these devices, primarily those relying on Bluetooth connectivity.
Alarmingly, many of these connections lack encryption, leaving the door wide open for malicious third parties.
If you’re picturing some low-stakes prank involving vibrating gadgets going haywire, think again. The risks are far graver.
According to the DSIT report, hackers could potentially inflict physical harm by overheating a device or locking it indefinitely. Meanwhile, the psychological harm could stem from sensitive data — yes, that kind of data — being exposed or exploited.
A TechCrunch exposé revealed that a security researcher breached a chastity device’s database containing over 10,000 users’ information. That was back in June, and the manufacturer still hasn’t addressed the issue.
In another incident, users of the CellMate connected chastity belt reported hackers demanding $750 in bitcoin to unlock devices. Fortunately, one man who spoke to Vice hadn’t been wearing his when the attack happened. Small mercies, right?
These aren’t isolated events. Standard Innovation Corp., the maker of the We-Vibe toy, settled for $3.75 million in 2017 after it was discovered the device was collecting intimate data without user consent.
A sex toy with a camera was hacked the same year, granting outsiders access to its live feed.
And let’s not forget: IoT toys are multiplying faster than anyone can track, with websites like Internet of Dongs monitoring the surge.
If the thought of a connected chastity belt being hacked makes you uneasy, consider this: sex toys are just a small piece of the IoT puzzle.
There are an estimated 17 billion connected devices worldwide, ranging from light bulbs to fitness trackers — and, oddly, smart egg crates.
Yet, as Microsoft’s 2022 Digital Defense Report points out, IoT security is lagging far behind its software and hardware counterparts.
Hackers are opportunistic. If there’s a way in, they’ll find it. Case in point: a casino lost sensitive customer data after bad actors accessed its network through smart sensors in a fish tank.
If a fish tank isn’t safe, why would we expect a vibrating gadget to be?
Here’s where the frustration kicks in: these vulnerabilities are preventable.
The DSIT report notes that many devices rely on unencrypted Bluetooth connections or insecure APIs for remote control functionality.
Fixing these flaws is well within the reach of manufacturers, yet companies routinely fail to prioritize security.
Even basic transparency around data collection would be a step in the right direction. Users deserve to know what’s being collected, why, and how it’s protected. But history suggests the industry is reluctant to step up.
After all, if companies like Standard Innovation can get away with quietly siphoning off user data, why would smaller players bother to invest in robust security?
So, what’s a smart-toy enthusiast to do? First, ask yourself: do you really need your device to be connected to an app?
If the answer is no, then maybe it’s best to go old school. If remote connectivity is a must, take some precautions.
Keep software updated: Ensure both the device firmware and your phone’s app are running the latest versions. Updates often include critical security patches.
Use secure passwords: Avoid default settings and choose strong, unique passwords for apps controlling your devices.
Limit app permissions: Only grant the app the bare minimum of permissions needed for functionality.
Vet the manufacturer: Research whether the company has a history of addressing security flaws. If they’ve been caught slacking before, it’s a red flag.
The conversation around sex toy hacking isn’t just about awkward headlines — it’s about how we navigate a world increasingly dependent on connected technology. As devices creep further into every corner of our lives, from the bedroom to the kitchen, the stakes for privacy and security continue to rise.
And let’s face it: there’s something uniquely unsettling about hackers turning moments of intimacy into opportunities for exploitation.
If companies won’t take responsibility for protecting users, then consumers need to start asking tough questions — and maybe think twice before connecting their pleasure devices to the internet.
As for the manufacturers? The message is simple: step up or step aside.
No one wants to be the next headline in a tale of hacked chastity belts and hijacked intimacy. And if you think that’s funny, just wait until your light bulb sells your Wi-Fi password.
This is where IoT meets TMI. Stay connected, but stay safe."
https://thartribune.com/government-warns-couples-that-sex-toys-remain-a-tempting-target-for-hackers-with-the-potential-to-be-weaponized/
#iot#I only want non-smart devices#I don't want my toilet to connect to the internet#seriously#smart devices#ai#anti ai#enshittification#smart sex toys
26 notes
·
View notes
Text
The end-to-end encrypted communication app WhatsApp, used by roughly 3 billion people around the world, will roll out cloud-based AI capabilities in the coming weeks that are designed to preserve WhatsApp’s defining security and privacy guarantees while offering users access to message summarization and composition tools.
Meta has been incorporating generative AI features across its services that are built on its open source large language model, Llama. And WhatsApp already incorporates a light blue circle that gives users access to the Meta AI assistant. But many users have balked at this addition, given that interactions with the AI assistant aren’t shielded from Meta the way end-to-end encrypted WhatsApp chats are. The new feature, dubbed Private Processing, is meant to address these concerns with what the company says is a carefully architected and purpose-built platform devoted to processing data for AI tasks without the information being accessible to Meta, WhatsApp, or any other party. While initial reviews by researchers of the scheme’s integrity have been positive, some note that the move toward AI features could ultimately put WhatsApp on a slippery slope.
“WhatsApp is targeted and looked at by lots of different researchers and threat actors. That means internally it has a well understood threat model,” says Meta security engineering director Chris Rohlf. “There's also an existing set of privacy expectations from users, so this wasn’t just about managing the expansion of that threat model and making sure the expectations for privacy and security were met—it was about careful consideration of the user experience and making this opt-in.”
End-to-end encrypted communications are only accessible to the sender and receiver, or the people in a group chat. The service provider, in this case WhatsApp and its parent company Meta, is boxed out by design and can’t access users’ messages or calls. This setup is incompatible with typical generative AI platforms that run large language models on cloud servers and need access to users’ requests and data for processing. The goal of Private Processing is to create an alternate framework through which the privacy and security guarantees of end-to-end encrypted communication can be upheld while incorporating AI.
Users opt into using WhatsApp’s AI features, and they can also prevent people they’re chatting with from using the AI features in shared communications by turning on a new WhatsApp control known as “Advanced Chat Privacy.”
“When the setting is on, you can block others from exporting chats, auto-downloading media to their phone, and using messages for AI features,” WhatsApp wrote in a blog post last week. Like disappearing messages, anyone in a chat can turn Advanced Chat Privacy on and off—which is recorded for all to see—so participants just need to be mindful of any adjustments.
Private Processing is built with special hardware that isolates sensitive data in a “Trusted Execution Environment,” a siloed, locked-down region of a processor. The system is built to process and retain data for the minimum amount of time possible and is designed grind to a halt and send alerts if it detects any tampering or adjustments. WhatsApp is already inviting third-party audits of different components of the system and will make it part of the Meta bug bounty program to encourage the security community to submit information about flaws and potential vulnerabilities. Meta also says that, ultimately, it plans to make the components of Private Processing open source, both for expanded verification of its security and privacy guarantees and to make it easier for others to build similar services.
Last year, Apple debuted a similar scheme, known as Private Cloud Compute, for its Apple Intelligence AI platform. And users can turn the service on in Apple’s end-to-end encrypted communication app, Messages, to generate message summaries and compose “Smart Reply” messages on both iPhones and Macs.
Looking at Private Cloud Compute and Private Processing side by side is like comparing, well, Apple(s) and oranges, though. Apple’s Private Cloud Compute underpins all of Apple Intelligence everywhere it can be applied. Private Processing, on the other hand, was purpose-built for WhatsApp and doesn’t underpin Meta’s AI features more broadly. Apple Intelligence is also designed to do as much AI processing as possible on-device and only send requests to the Private Cloud Compute infrastructure when necessary. Since such “on device” or “local” processing requires powerful hardware, Apple only designed Apple Intelligence to run at all on its recent generations of mobile hardware. Old iPhones and iPads will never support Apple Intelligence.
Apple is a manufacturer of high-end smartphones and other hardware, while Meta is a software company, and has about 3 billion users who have all types of smartphones, including old and low-end devices. Rohlf and Colin Clemmons, one of the Private Processing lead engineers, say that it wasn’t feasible to design AI features for WhatsApp that could run locally on the spectrum of devices WhatsApp serves. Instead, WhatsApp focused on designing Private Processing to be as unhelpful as possible to attackers if it were to be breached.
“The design is one of risk minimization,” Clemmons says. “We want to minimize the value of compromising the system.”
The whole effort raises a more basic question, though, about why a secure communication platform like WhatsApp needs to offer AI features at all. Meta is adamant, though, that users expect the features at this point and will go wherever they have to to get them.
“Many people want to use AI tools to help them when they are messaging,” WhatsApp head Will Cathcart told WIRED in an email. “We think building a private way to do that is important, because people shouldn’t have to switch to a less-private platform to have the functionality they need.”
“Any end-to-end encrypted system that uses off-device AI inference is going to be riskier than a pure end to end system. You’re sending data to a computer in a data center, and that machine sees your private texts,” says Matt Green, a Johns Hopkins cryptographer who previewed some of the privacy guarantees of Private Processing, but hasn’t audited the complete system. “I believe WhatsApp when they say that they’ve designed this to be as secure as possible, and I believe them when they say that they can’t read your texts. But I also think there are risks here. More private data will go off device, and the machines that process this data will be a target for hackers and nation state adversaries.”
WhatsApp says, too, that beyond basic AI features like text summarization and writing suggestions, Private Processing will hopefully create a foundation for expanding into more complicated and involved AI features in the future that involve processing, and potentially storing, more data.
As Green puts it, “Given all the crazy things people use secure messengers for, any and all of this will make the Private Processing computers into a very big target.”
3 notes
·
View notes
Text
EU’s proposed Chat Control law has become a bone of contention between members of the bloc. First proposed by the European Commissioner for Home Affairs Ylva Johansson in May 2022 as part of bloc’s push to combat child sexual abuse online, the framework of the bill has now come under fire, earning itself a derisive term “Chat Control”.
France, Germany and Poland have particularly refused to accept a clause that allows for mass scanning of private messages by breaking end-to-end encryption. Some tech companies, along with trade associations, and privacy experts have all vehemently opposed the regulation.
On the other hand, Interior Ministers of Spain and Ireland have supported the proposal. Separately, a network of organisations and individuals, advocating for children’s rights in Europe, have lashed out at EU leaders for failing to tackle child sexual abuse online.
What are the concerns of those against the proposal?
Scanning end-to-end encrypted messages has remained a controversial issue. That’s because there is no way to do this without opening risky backdoors that can be accessed by third parties who can exploit the vulnerability, in turn ending the promise of end-to-end encryption.
Tech firms that treaded the encryption bypassing path have have often been made to retreat. In 2021, Apple announced NeuralHash, a feature that could automatically scan iCloud photo libraries of individual devices for child sexual abuse material, or CSAM. Employees and activist groups expressed concerns over the loss of privacy. A year later, Apple said it had abandoned the initiative.
Another looming issue the iPhone maker recognised in the process was how authoritarian governments could potentially misuse the feature by using it as a tool to target individuals who oppose the regime.
Erik Neuenschwander, Director of user privacy and child safety at Apple, admitted this in a note saying, “It would […] inject the potential for a slippery slope of unintended consequences. Scanning for one type of content, for instance, opens the door for bulk surveillance and could create a desire to search other encrypted messaging systems across content types.”
When brining in a similar clause through the UK’s Online Safety Bill, lawmakers attempted to make way for client-side scanning of private and encrypted messages. The proposal was postponed after receiving pushback from encrypted messaging app owners like WhatsApp and Signal. The duo threatened to leave the UK if such a law was passed. In its final stages, in September, 2023, the House of Lords considered the potential security threat that the clause would bring saying it would not implement scanning until it was “technically feasible.”
What is the status of EU’s Chat Control law?
On June 30, a new draft of the proposal is set to be be reviewed. Legislators have now left the idea of scanning text messages and audio, and are instead targetting shared photos, videos and URLs with an adjustment to appease the naysayers.
Another tweak in the making could be people’s consent in sharing material being scanned before being encrypted. But this compromise has been largely called out as a farcical one. A report by Euractiv which has been confirmed by internal documents show that if a user refuses the scanning, they will simply be blocked from sending or receiving images, videos and links hardly leaving them with a choice.
Despite these measures, EU’s enforcement of such regulations have seen exemptions to the rule. In November 2023, the European Commission reportedly published a proposal to amend the regulation on a temporary derogation of the E-Privacy Directive against CSAM. Under the regulation, specific online communications service providers were allowed to sift through or scan messages to detect, report and remove online child sexual abuse material or CSAM and content that solicits children. The regulation is set to expire in early August . The initial plan on the table was to simply extend this regulation for another three years. But, according to media reports, plans for further extensions were stalled in February this year.
Meredith Whittaker, President of Signal app called the measures to assuage concerns as “cosmetic”, and has signed a joint statement along with a group of over 60 other organisations like Mozilla, Proton, Surfshark and Tuta, voicing out her concerns. Whittaker has echoed her earlier warning saying Signal will leave the UK rather than undermine end-to-end encryption.
A blog, co-authored by Riana Pfefferkorn, a research scholar at the Stanford Internet Observatory and Callum Voge, director of government affairs and advocacy at the Internet Society, notes, ”If government surveillance is a concern in an established democratic entity like the EU, what hope is there for beleaguered democracies like Turkey, India and Brazil, much less autocracies?”
7 notes
·
View notes
Text
Hybrid Cloud Strategies with Azure Arc: My Practical Insight
Are you ready to unlock the true potential of hybrid cloud strategies? Look no further than Azure Arc, the game-changing solution that promises seamless integration and unparalleled flexibility. From streamlining operations to enhancing security, Azure Arc has revolutionized the way organizations harness the power of both on-premises and cloud environments. In this blog post, I’ll be diving into my practical insights on leveraging Azure Arc for your hybrid cloud journey. So buckle up as we explore the endless possibilities and unveil a new era in hybrid computing!

Introduction to Hybrid Cloud Strategies with Azure Arc
I’m under pressure to digitally transform in order to remain competitive. I’m looking to the cloud as a way to accelerate this transformation. Not all workloads, meanwhile, are appropriate for the public cloud. Some may require on-premises or edge computing due to data sovereignty or local regulations. Others may need to be kept on-premises due to performance requirements.
Hybrid cloud strategies allow me to keep some workloads on-premises or at the edge while still taking advantage of the agility and scalability of the public cloud. Azure Arc is a tool that can help me manage and monitor my hybrid cloud deployments. In this blog post, I will share my practical insight into using Azure Arc for my hybrid cloud deployments.
Benefits of Azure Arc Adoption & Challenges in Implementing it
In recent years, using the cloud has grown in popularity among organizations of all sorts. One of the major advantages of cloud computing is its scalability; I can quickly add or remove capacity as needed without making a long-term commitment. Azure Arc is a hybrid cloud solution that allows me to take advantage of the benefits of the cloud while still maintaining control over my data and applications.
There are several benefits to adopting Azure Arc, including:
Increased flexibility and scalability: As mentioned above, one of the major advantages of Azure Arc is its scalability. I can easily add or remove capacity as needed, without making a long-term commitment. This can help me save money on IT infrastructure costs, as well as ensure that I have the necessary resources available when I need them.
Improved disaster recovery: Another benefit of Azure Arc is improved disaster recovery capabilities. With this solution in place, I can quickly recover from outages or disasters with minimal downtime. This can help keep my business up and running even in the event of a major problem.
Enhanced security: Security is always a major concern for me, especially when it comes to sensitive data. With Azure Arc in place, I can take advantage of enhanced security features such as encrypted data storage and multi-factor authentication. This can help give me peace of mind knowing that my data is safe and secure.
Lower maintenance costs: Maintaining on-premises IT infrastructure can be costly and time-consuming. Azure Arc helps me lower maintenance costs by simplifying resource management and automating tasks.
Understanding the Necessary Requirements for Azure Arc Usage
Azure Arc is a cloud management platform that enables me to optimize my hybrid cloud deployments. It provides a unified control plane for managing resources across on-premises, edge, and multi-cloud environments. Azure Arc also simplifies the process of integrating Azure services with on-premises and third-party solutions.
In order to use Azure Arc, I must first have an Azure subscription. I must also have the desired Azure Resource Manager (ARM) template or Resource Manager package deployed in my environment. Azure Arc uses these templates or packages to deploy and manage resources in the target environment.
Once the necessary requirements are met, I can begin using Azure Arc to manage my hybrid cloud deployments. I can use the platform to provision and manage resources, monitor activity and usage patterns, set policies and governance controls, etc. Additionally, I can use Azure Arc to connect my on-premises or third-party solutions with Azure services. This allows me to take advantage of the many benefits that Azure has to offer, such as scalability, high availability, security, and so on.
Steps for Setting Up Azure Arc Configurations
Azure Arc is a cloud service that enables me to manage and monitor my resources whether they’re running on Azure, on-premises, or in other clouds. With Azure Arc, I can use the same tools and portal experiences I’m used to in Azure to centrally govern all my infrastructure.
Setting up an Azure Arc configuration is simple and straightforward. I just need to follow these simple instructions:
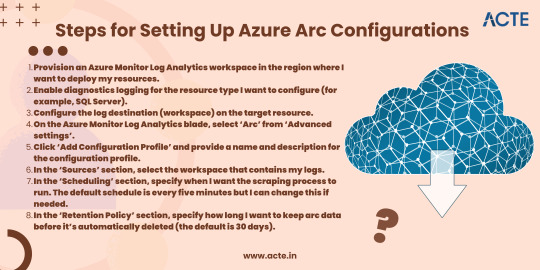
9a. If I want to scrape data from multiple workspaces, I can repeat steps 5–8 for each workspace.
Troubleshooting Common Issues Related to Hybrid Cloud with Azure Arc If I’m working with hybrid cloud and Azure Arc, there are a few common issues I may run into. Here’s how to troubleshoot them:
I can’t see all of my resources in the Azure portal.
Make sure that I’ve selected the correct subscription in the Azure portal. If I’m still not seeing all of my resources, check the resource provider status page to see if there are any known issues.
I’m getting errors when trying to deploy resource group templates.
When deploying resource group templates, make sure that the template includes all required resources for Azure Arc enabled resource providers. Consult the Azure Resource Manager documentation for further details.
My hybrid cloud app isn’t running correctly.
If I’m having trouble with a hybrid cloud app, first check the logs to see if there are any error messages. Then, try redeploying the app using a different approach (for example, using Azure CLI or PowerShell instead of the Azure portal).
Unifying Multiple Clouds with One Platform:
A Comprehensive Overview Azure Arc is a cloud management platform that enables me to unify multiple clouds with one platform. Azure Arc provides a comprehensive overview of my resources and allows for central management and policy enforcement across all of my Azure subscriptions. Azure Arc also provides integrated security and compliance features to help me secure my data and meet regulatory requirements.
Best Practices for Utilizing Hybrid Cloud Strategies with Azure Arc
When it comes to hybrid cloud strategies with Azure Arc, there are a few best practices that I should keep in mind. For starters, I should make sure that I have a clear understanding of my workloads and how they need to be supported. I should also have a clear picture of my network topology and how the different components will interact with each other. Additionally, it’s important to have a plan for data security and management, as well as monitoring and logging. By keeping these things in mind, I can be sure that my hybrid cloud strategy with Azure Arc is as effective as possible.
All things considered, Azure Arc is an impressive offering from Microsoft that can help me realize the potential of hybrid cloud technology. By leveraging my existing infrastructure while taking advantage of the benefits offered by public clouds like Azure, I can enjoy features such as greater scalability and improved flexibility to meet changing needs. Whether I need basic access control or more advanced policies to manage my distributed systems, my practical insight on using Azure Arc for my hybrid cloud strategy shows how powerful this platform is in streamlining and optimizing cloud operations for various enterprises.
2 notes
·
View notes
Text
Why Choose Drupal Over the Other CMSs
Drupal is a free and open-source web content management system (CMS) written in PHP and distributed under the General Public License. Drupal provides an open-source back-end framework for at least 14% of the top 10,000 websites worldwide and 1.2% of the top 10 million websites—from personal blogs to corporate, political, and government sites. Systems also use Drupal for knowledge management and business collaboration.
As of March 2022, the Drupal community had more than 1.39 million members, including 124,000 users actively contributing, resulting in more than 48,300 free modules that extend and customize Drupal functionality, over 3,000 free themes that change the look and feel of Drupal, and at least 1,400 free distributions that allow users to quickly and easily set up a complex, use-specific Drupal in fewer steps.
So, what factors make Drupal so unique in the market of CMSs and become the preferred choice of most users?
1. Multilingual Platform
The ultimate goal of every website is to grow globally. Multilingual platforms are a stepping stone; you can do this effortlessly with Drupal. When your website interacts with visitors in their native language, it creates a pull for them and keeps them stuck for longer. Also, Drupal will dramatically increase their chances of interacting with the website.
With its unwavering support for multilingual websites, Drupal is the ultimate CMS for building websites that support multiple languages. It allows you to choose from more than 100 languages according to your target geographic area. No matter where your target audience lives, you can effortlessly connect with them through a website built with Drupal.
2. Security Function
In this internet-driven world, people share much personal information online, including bank details, credit card details, and other credentials. What followed was a sharp increase in cybercrime cases. There’s no doubt that today’s consumers follow the best online security practices to protect themselves from online fraud and data breaches, but they also expect top-notch security from the sites they trust.
Therefore, website owners must focus on intelligent web security practices. After all, a cyber attack can get their business into trouble. Once they lose the trust of their customers, no matter what they try, there is no way to get it back.
Drupal is one of the most secure CMSs in the history of the world. It offers unparalleled security features to defend against cyber-attacks and protect customer data. Regular security updates, two-factor authentication, user access control, and database encryption are some of the security features offered by Drupal.
3. Great for SEO
A website’s overall search engine ranking depends on the effectiveness of the SEO practices. If a website owner takes SEO seriously, the website can land on the first page of search engines. As a result, the website will experience exponential visitor numbers and sales growth. Realizing the importance of SEO, most CMSs have started to provide users with multiple SEO tools with the promise of improving website rankings.
If you’re looking for a powerful and versatile content management system that will help your website rank higher in search engine results pages, Drupal is an excellent option. Thanks to its well-optimized codebase and many SEO features, Drupal is one of the best CMSs for SEO. Keyword research, keyword management, content auto-linking, and link management are some of its notable SEO features.
Drupal is a popular content management (CMS) system platform worldwide. If you need an open-source and user-friendly CMS to meet your business needs, Drupal is your first choice. From the perspective of security, Drupal has a dedicated security team to review and respond to the kernel, third-party modules, and themes; Drupal’s modules and themes will be covered by Drupal’s internal security program to ensure that malicious codes are removed. In addition, for ongoing maintenance, and long-term development projects, Drupal development is a lower-cost option. Once the main functions are completed, subsequent expansion and customization will not cost more.
If you want to integrate third-party services into your Drupal site, Shinetech will be your excellent partner. Shinetech developers have rich experience in Drupal development and can help you with the operation and maintenance of your existing Drupal site. The custom development team can also expand network functions by installing existing plug-ins or custom-developing your Drupal plug-ins.
2 notes
·
View notes
Text
Beyond Templates: Building Future-Ready Businesses Through Custom Software
In the modern digital economy, businesses are defined not just by their products or services, but by the technology they use to deliver them. With rapid advancements in cloud computing, artificial intelligence, and data integration, relying on generic software can severely limit a company’s potential. Custom software development offers an alternative that’s not only tailored to your business needs but also optimized for long-term success.
Whether you're managing logistics, engaging customers, or streamlining finance, custom-built applications empower you to operate smarter, faster, and more securely. They bridge the gap between your vision and execution, helping you turn ideas into real-world solutions that give you a competitive edge.
The Case Against Off-the-Shelf Software
Pre-packaged software solutions are designed for the masses. They're meant to cover broad use cases across industries but rarely address the specific pain points of an individual business. As companies grow, these limitations become more apparent. Processes become inefficient, integrations fail to sync properly, and critical features may be missing altogether.
Moreover, most of these tools come with recurring license fees, hidden costs for add-ons, and limited control over upgrades or security protocols. This leads to operational bottlenecks and increasing expenses as businesses try to patch together various third-party tools to meet their evolving needs.
Custom Software: Designed to Perform
Custom software development begins with one key principle: the system should work for you, not the other way around. From the initial blueprint to the final line of code, every element is built around your business model. Whether you're automating complex workflows, managing sensitive customer data, or creating proprietary technology, a custom solution ensures that everything functions exactly as it should.
This approach allows for deep system integration, real-time analytics, personalized user experiences, and flexible access controls. It’s the difference between a generic tool that “kind of fits” and a digital solution that transforms your efficiency, accuracy, and decision-making.
Built-In Agility for Evolving Needs
One of the greatest advantages of custom software is agility. Businesses are dynamic—they pivot, grow, and expand. Your software should be just as adaptable. With a custom solution, features can be updated or scaled on demand. You’re not waiting for the next version of someone else’s product; you're continuously evolving your own.
This is especially important for industries that face changing compliance standards, customer behaviors, or market trends. Custom software allows you to respond quickly without overhauling your entire digital infrastructure.
Security at the Core
As cybersecurity threats become more sophisticated, having control over your software’s architecture becomes critical. Custom software gives you the ability to implement robust, industry-specific security measures that go far beyond the standard protections offered in off-the-shelf solutions.
You can encrypt data in ways that align with your legal requirements, restrict access to sensitive areas, and monitor unusual activity through built-in intelligence. In industries like finance, healthcare, and legal services, this level of protection is not just beneficial—it’s essential.
A Smarter Investment with Higher ROI
While the initial investment in custom software may appear higher than subscription-based alternatives, the return on investment is substantially greater over time. You eliminate licensing costs, gain full control over features, and avoid the inefficiencies caused by mismatched tools. What you invest in now pays off in smoother operations, faster workflows, and happier clients.
Also, having full ownership of your technology becomes a powerful asset. It adds to the valuation of your company, provides leverage for funding, and opens doors to new business opportunities that rely on proprietary systems.
Conclusion: The Strategic Advantage of Custom-Built Solutions
In a rapidly evolving marketplace, technology must be more than functional—it must be strategic. Custom software provides that strategic edge, giving you the power to design, refine, and scale digital solutions that match your business ambitions. It’s not just about solving current problems; it’s about positioning your business for tomorrow’s opportunities.
The businesses that will thrive in the next decade are already building the tools they need today. It all begins with the choice to invest in Custom Software Development in USA.
0 notes
Text
Secure Cloud Storage for Medical Images: Protect Patient Privacy
In today’s healthcare world, medical images like X-rays, MRIs, and CT scans are moving to the cloud for easy access and storage.
But with this shift comes a big question: how do you keep patient data safe? Using medical imaging cloud storage can be a game-changer, but only if you do it right.
This article will show you how to protect sensitive images without risking privacy.

Why Storing Medical Images in the Cloud Can Be Tricky
Putting medical images in the cloud isn’t the same as storing them on a local computer.
You’re handing over control to a third party, which can feel risky. If something goes wrong—like a data breach or someone sneaking into the system—patient privacy could be in trouble.
Plus, there are rules to follow, and slipping up can lead to legal headaches. The good news? You can tackle these challenges with the right plan.
How to Keep Your Medical Images Safe?
So, how do you make sure your cloud storage is secure? It’s all about taking smart steps to lock things down.
First, pick a cloud provider you can trust. Not every company out there is ready to handle sensitive medical data.
Look for one with a strong track record in healthcare or dealing with private information. They should have solid security tools and follow the rules you need to meet.
Next, encryption is a must. Think of it as a secret code that scrambles your images so only the right people can see them.
Make sure the images are locked up tight both when they’re being sent and when they’re sitting in storage. A good standard to aim for is something called AES-256—it’s tough to crack.
You’ll also want to control who gets in. Set up strong passwords and add an extra step, like a code sent to a phone, to verify it’s really you or your team.
Decide who needs access and keep everyone else out. This way, only the people who should see the images can.
Finally, keep an eye on things. Check regularly to see who’s looking at the images and when.
If something looks off, you’ll catch it fast. This habit also helps you stay on the right side of privacy laws.
Medical Imaging Cloud Storage and Following the Rules
When you store medical images in the cloud, you can’t ignore the regulations.
In the U.S., the big one is HIPAA—the Health Insurance Portability and Accountability Act. It’s there to protect patient info, and it has some clear demands:
Keep electronic patient data private, safe, and available when needed.
Put up strong defenses against unauthorized eyes.
Check your setup often to spot any weak points.
To stay on track, choose a cloud provider that knows HIPAA inside and out. They should agree in writing to share the responsibility of keeping data safe—look for something called a Business Associate Agreement. This step makes sure you’re both committed to protecting patients.

Setting Up a Secure Workflow
Getting your medical images into the cloud safely isn’t just about storage—it’s about how you work with them too.
You need a system that fits into your daily routine without opening up risks.
Start by making sure the tools you use to move images around are secure. Think of it like using a locked briefcase instead of an open bag.
Train your team on how to handle data the right way—simple rules can go a long way.
And don’t forget backups. If something goes wrong, like a system crash, you’ll want a spare copy ready to go.
Comparing Cloud Providers: A Quick Look
Not sure where to start with providers? Here’s a simple table to compare three imaginary options based on key features:
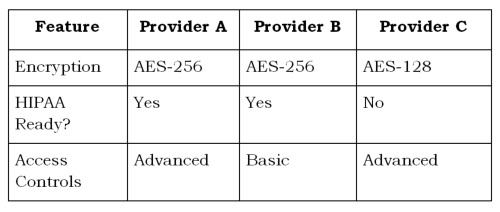
Providers A and B look stronger for medical use, thanks to better encryption and HIPAA support. Pick what fits your needs best.
Wrapping It Up
Storing sensitive medical images in the cloud doesn’t have to be a privacy nightmare.
With the right provider, strong security measures, and a solid workflow, you can keep patient data safe while enjoying the perks of the cloud.
It’s all about staying proactive—understand the risks, follow the rules, and put patient privacy first. That way, your cloud storage solution works for you, not against you.
0 notes
Text
How Secure Are Internet of Things (IoT) Devices in 2025?

From smart homes anticipating your every need to industrial sensors optimizing manufacturing lines, Internet of Things (IoT) devices have seamlessly integrated into our lives, promising unparalleled convenience and efficiency. In 2025, are these interconnected gadgets truly secure, or are they opening up a Pandora's Box of vulnerabilities?
The truth is, IoT security is a complex and often concerning landscape. While significant progress is being made by some manufacturers and regulatory bodies, many IoT devices still pose substantial risks, largely due to a race to market that often prioritizes features and cost over robust security.
The Allure vs. The Alarms: Why IoT Devices Are Often Vulnerable
The promise of IoT is immense: automation, data-driven insights, remote control. The peril, however, lies in how easily these devices can become entry points for cyberattacks, leading to privacy breaches, network compromise, and even physical harm.
Here's why many IoT devices remain a security headache:
Weak Default Credentials & Lack of Updates:
The Problem: Many devices are still shipped with easily guessable default usernames and passwords (e.g., "admin/admin," "user/123456"). Even worse, many users never change them. This is the single easiest way for attackers to gain access.
The Challenge: Unlike smartphones or laptops, many IoT devices lack clear, robust, or frequent firmware update mechanisms. Cheaper devices often receive no security patches at all after purchase, leaving critical vulnerabilities unaddressed for their entire lifespan.
Insecure Network Services & Open Ports:
The Problem: Devices sometimes come with unnecessary network services enabled or ports left open to the internet, creating direct pathways for attackers. Poorly configured remote access features are a common culprit.
The Impact: Remember the Mirai botnet? It famously exploited vulnerable IoT devices with open ports and default credentials to launch massive Distributed Denial of Service (DDoS) attacks.
Lack of Encryption (Data In Transit & At Rest):
The Problem: Data transmitted between the device, its mobile app, and the cloud often lacks proper encryption, making it vulnerable to eavesdropping (Man-in-the-Middle attacks). Sensitive data stored directly on the device itself may also be unencrypted.
The Risk: Imagine your smart speaker conversations, security camera footage, or even health data from a wearable being intercepted or accessed.
Insecure Hardware & Physical Tampering:
The Problem: Many IoT devices are designed with minimal physical security. Easily accessible debug ports (like JTAG or UART) or lack of tamper-resistant enclosures can allow attackers to extract sensitive data (like firmware or encryption keys) directly from the device.
The Threat: With physical access, an attacker can potentially rewrite firmware, bypass security controls, or extract confidential information.
Vulnerabilities in Accompanying Apps & Cloud APIs:
The Problem: The web interfaces, mobile applications, and cloud APIs used to control IoT devices are often susceptible to common web vulnerabilities like SQL Injection, Cross-Site Scripting (XSS), or insecure authentication.
The Loophole: Even if the device itself is somewhat secure, a flaw in the control app or cloud backend can compromise the entire ecosystem.
Insufficient Privacy Protections:
The Problem: Many IoT devices collect vast amounts of personal and sensitive data (e.g., location, habits, biometrics) without always providing clear consent mechanisms or robust data handling policies. This data might then be shared with third parties.
The Concern: Beyond direct attacks, the sheer volume of personal data collected raises significant privacy concerns, especially if it falls into the wrong hands.
Supply Chain Risks:
The Problem: Vulnerabilities can be introduced at any stage of the complex IoT supply chain, from compromised components to insecure firmware inserted during manufacturing.
The Fallout: A single compromised component can affect thousands or millions of devices, as seen with some supply chain attacks in the broader tech industry.
The Elephant in the Room: Why Securing IoT is Hard
Diversity & Scale: The sheer number and variety of IoT devices (from tiny sensors to complex industrial machines) make a "one-size-fits-all" security solution impossible.
Resource Constraints: Many devices are low-power, low-cost, or battery-operated, limiting the computational resources available for robust encryption or security features.
Long Lifespans: Unlike phones, many IoT devices are expected to operate for years, even decades, long after manufacturers might cease providing support or updates.
Patching Complexity: Pushing updates to millions of geographically dispersed devices, sometimes with limited connectivity, is a logistical nightmare.
Consumer Awareness: Many consumers prioritize convenience and price over security, often unaware of the risks they introduce into their homes and networks.
Towards a More Secure IoT in 2025: Your Shield & Their Responsibility
While the challenges are significant, there's a collective effort towards a more secure IoT future. Here's what needs to happen and what you can do:
For Manufacturers (Their Responsibility):
Security by Design: Integrate security into the entire product development lifecycle from day one, rather than as an afterthought.
Secure Defaults: Ship devices with unique, strong, and randomly generated default passwords.
Robust Update Mechanisms: Implement easy-to-use, automatic, and regular firmware updates throughout the device's lifecycle.
Clear End-of-Life Policies: Communicate transparently when support and security updates for a device will cease.
Secure APIs: Design secure application programming interfaces (APIs) for cloud communication and mobile app control.
Adhere to Standards: Actively participate in and adopt industry security standards (e.g., ETSI EN 303 645, IoT Security Foundation guidelines, PSA Certified). Regulatory pushes in Europe (like the Cyber Resilience Act) and elsewhere are driving this.
For Consumers & Businesses (Your Shield):
Change Default Passwords IMMEDIATELY: This is your absolute first line of defense. Make them strong and unique.
Network Segmentation: Isolate your IoT devices on a separate Wi-Fi network (a "guest" network or a VLAN if your router supports it). This prevents a compromised IoT device from accessing your main computers and sensitive data.
Keep Firmware Updated: Regularly check for and apply firmware updates for all your smart devices. If a device doesn't offer updates, reconsider its use.
Disable Unused Features: Turn off any unnecessary ports, services, or features on your IoT devices to reduce their attack surface.
Research Before You Buy: Choose reputable brands with a track record of security and clear privacy policies. Read reviews and look for security certifications.
Strong Wi-Fi Security: Ensure your home Wi-Fi uses WPA2 or, ideally, WPA3 encryption with a strong, unique password.
Be Mindful of Data Collected: Understand what data your devices are collecting and how it's being used. If the privacy policy isn't clear or feels invasive, reconsider the device.
Physical Security: Secure physical access to your devices where possible, preventing easy tampering.
Regular Monitoring (for Businesses): Implement tools and processes to monitor network traffic from IoT devices for unusual or suspicious activity.
In 2025, the convenience offered by IoT devices is undeniable. However, their security is not a given. It's a shared responsibility that demands both diligence from manufacturers to build secure products and vigilance from users to deploy and manage them safely.
0 notes
Text
What Are the Key Considerations When Planning a Fintech Product?

In the rapidly evolving world of finance, fintech software development has emerged as a key driver of innovation, convenience, and accessibility. Whether you're a startup founder or part of a traditional financial institution, developing a fintech product requires more than just technical knowledge—it demands a comprehensive understanding of finance, user behavior, regulatory frameworks, and emerging technologies. To build a successful fintech solution, there are several critical considerations you must address from the very beginning.
1. Understanding the Target Market and Problem Statement
Before writing a single line of code, it's essential to identify your target users and the financial problem you're aiming to solve. Is your product meant to simplify payments, offer better lending options, facilitate investments, or enhance insurance services? Are you targeting millennials, small businesses, rural communities, or enterprise clients?
Defining the problem statement clearly will guide the design and functionality of your product. Additionally, conducting market research helps validate the demand for your solution, assess the competition, and refine your value proposition.
2. Navigating Regulatory and Compliance Requirements
One of the most complex aspects of fintech software development is ensuring full compliance with legal and regulatory requirements. Different countries—and even different states or regions—have specific rules governing digital finance, data storage, user authentication, and financial transactions.
Common regulations include:
KYC (Know Your Customer)
AML (Anti-Money Laundering)
GDPR (for data privacy in the EU)
PCI-DSS (for payment card data security)
Planning your fintech product with compliance in mind from the outset will save time, avoid legal issues, and build trust with your users.
3. Choosing the Right Technology Stack
The technology stack you select forms the foundation of your product’s scalability, performance, and security. Some of the popular technologies used in fintech software development include:
Programming languages like Python, Java, and Kotlin
Frameworks such as React, Node.js, and Spring Boot
Cloud platforms like AWS, Azure, or Google Cloud
Databases like PostgreSQL, MongoDB, and Oracle
The key is to choose technologies that support real-time data processing, high-level security, and easy scalability. Integration with third-party APIs, such as payment gateways, identity verification services, and banking platforms, should also be seamless and secure.
4. Prioritizing Security and Data Protection
Security is at the core of every fintech product. You’re dealing with sensitive user data—bank account numbers, identification details, transaction histories—which makes your platform a potential target for cyberattacks.
Security best practices in fintech include:
End-to-end encryption
Multi-factor authentication (MFA)
Tokenization of payment data
Regular security audits and penetration testing
Role-based access control
Additionally, implementing secure coding practices and training your development team to identify and eliminate vulnerabilities can go a long way in creating a secure fintech environment.
5. User Experience (UX) and Interface Design
No matter how powerful your backend is, a clunky and confusing user interface can drive users away. A clean, intuitive, and responsive interface is critical for adoption and engagement.
Design principles to focus on:
Ease of navigation
Minimalistic yet informative layout
Clear call-to-action buttons
Accessibility for users with disabilities
Consistent branding and visual design
The fintech landscape is extremely competitive, and often, the difference between a successful app and a forgotten one is simply superior UX.
6. Integration with Existing Financial Ecosystems
A successful fintech product often doesn't exist in isolation—it must integrate with existing banking systems, payment processors, credit bureaus, and government portals. These integrations need to be secure, real-time, and capable of handling large transaction volumes.
APIs play a major role here. Your development team should focus on building a flexible architecture that supports third-party API integrations while also allowing easy future enhancements.
7. Scalability and Performance Planning
Fintech products often experience rapid growth—especially if they solve a critical financial problem. Planning for scalability ensures that your infrastructure can handle increasing user loads, transactions, and data volumes without crashing or slowing down.
Cloud-native applications, load balancing, microservices architecture, and automated scaling are essential tools in building a robust and scalable fintech system.
8. Continuous Testing and Feedback Loops
Testing shouldn't be an afterthought. Your development process should include:
Unit testing
Integration testing
User Acceptance Testing (UAT)
Security testing
Performance testing
Once the product is launched, continuous user feedback should be used to improve features, resolve bugs, and refine UX over time. Agile methodologies and DevOps practices can support faster iteration cycles and improved product quality.
9. Cost Management and Development Timelines
Planning your budget and timeline effectively is essential for successful fintech software development. Overruns in either can stall your project or reduce its market competitiveness. Prioritize features using a Minimum Viable Product (MVP) approach and plan for incremental improvements.
10. Partnering with the Right Development Team
Lastly, success in fintech often depends on having the right tech partner. A team that understands both fintech services and the intricacies of the financial industry can bring strategic insights and avoid costly mistakes. For example, Xettle Technologies has built a reputation for delivering secure, scalable, and innovative fintech solutions by combining deep financial expertise with advanced development practices.
Conclusion
Planning a fintech product is a multifaceted process that requires thoughtful strategy, technical excellence, and a deep understanding of user needs and regulations. By considering aspects like compliance, security, scalability, and UX early in the development process, you increase your chances of building a fintech product that not only meets market demands but also leads in innovation and trust.
0 notes
Text
Describe differences between traditional databases and Dataverse
When comparing traditional databases to Dataverse, several key differences in their approach to data management and application development become apparent.
Data Storage: Traditional databases organize data in tables made up of rows and columns, requiring manual setup and ongoing maintenance to ensure proper functionality. While Dataverse also uses tables, it enhances them with built-in features such as rich metadata, defined relationships, and integrated business logic. These enhancements streamline data management, making it more efficient and less labor-intensive. Additionally, Dataverse is designed to handle large volumes of data, supporting complex data models and scaling.
Security: Security configurations in traditional databases typically need to be customized and manually implemented, which can be complex and time-consuming. Dataverse simplifies this process by offering advanced security features out of the box, including role-based security, row-level access controls, and column-level encryption. These features ensure that data is protected and accessible only to authorized users.
Development: Developing applications with traditional databases often requires significant coding expertise, which can be a barrier for those individuals without a technical background. Dataverse addresses this challenge by supporting low-code and no-code development environments. App makers can create powerful solutions without needing extensive programming skills, making it accessible to a broader range of users.
Businesses can better decide which platform aligns with their needs y understanding these differences, whether they require the traditional approach, or the modern capabilities offered by Microsoft Dataverse.
How the Common Data Model powers Dataverse
Central to Dataverse is the Common Data Model (CDM). CDM plays a crucial role in organizing and managing data. Dataverse is designed to store information in a structured format using tables, made up of rows and columns. What sets Dataverse apart is its reliance on the CDM—a standardized schema that simplifies how data is integrated and shared across applications and services.
The CDM provides predefined schemas that represent common business concepts, such as accounts, contacts, and transactions. These schemas include tables, attributes, and relationships, ensuring that data is organized in a consistent way. This standardization makes it easier for different systems to work together, enabling compatibility and interoperability between applications. For example, whether you're working with Dynamics 365 or Power Apps, the CDM ensures that your data follows the same structure, reducing complexity and improving efficiency.
Dataverse uses the Common Data Model to support integration with a wide range of tools and services. It connects seamlessly with Microsoft products like Dynamics 365, Power Apps, and Azure, allowing you to build solutions that span multiple platforms. Additionally, Dataverse can integrate with external systems through connectors and APIs, making it possible to bring in data from third-party applications or share data across different environments. This flexibility ensures that businesses can create connected solutions tailored to their unique needs.
Dataverse not only simplifies data management but also enables powerful integrations by using the Common Data Model as its foundation, making it an essential tool for building scalable and interoperable business applications.
0 notes
Text
Fast Secure Proxy Browser: Browse Anonymously Without Limits

Have you ever tried to access a website, only to be met with a frustrating “This content is not available in your region” message? Or perhaps you've felt uneasy knowing your online activity might be tracked or exposed on public Wi-Fi. In today’s digital landscape, where privacy breaches and content restrictions are increasingly common, it’s no surprise that more users are turning to solutions that offer both security and speed.
That’s where a fast secure proxy browser comes in. It's more than just a digital detour — it’s your shield against surveillance, a bridge to open access, and a tool that puts you back in control of your browsing experience. But what exactly makes a proxy browser both fast and secure? And how can it help you browse anonymously without limits?
In this post, we’ll break down how a fast secure proxy browser works, explore why it matters, and guide you through choosing one that fits your needs. Whether you’re looking to protect your data, bypass geo-blocks, or simply surf without compromise, you’re in the right place. Let’s dive into the tools and tactics that make anonymous browsing not just possible—but effortless.
Understanding Proxy Browsers
Proxy browsers serve as intermediaries between your device and the internet. When you access a website through a proxy browser, your request is rerouted through a remote server. This server masks your IP address, effectively hiding your identity from websites, advertisers, and even government surveillance.
A proxy browser differs from a Virtual Private Network (VPN) in a few key ways. While both hide your IP and offer privacy, VPNs typically encrypt all internet traffic on your device, while proxy browsers work at the application level—usually within the browser itself. This makes proxy browsers lighter and often faster for everyday use.
Why does speed matter? Because privacy tools shouldn't slow you down. A fast proxy browser ensures you're not waiting forever for a webpage to load, all while keeping your identity secure. It also allows seamless streaming, gaming, and general browsing without buffering or lag.
With a secure proxy browser, you no longer need to worry about malicious entities tracking your every move. Your location stays hidden, your data remains encrypted, and your browsing history is safe from third parties.
Key Benefits of a Fast Secure Proxy Browser
Maintain Online Privacy and Hide Your IP
One of the biggest advantages of a fast secure proxy browser is the ability to mask your real IP address. By doing so, your digital footprint is hidden, and your activities can't easily be traced back to you.
Bypass Geo-Restrictions and Censorship
Tired of running into blocked websites? Proxy browsers help you bypass content restrictions imposed by governments, schools, or workplaces. Whether you're accessing streaming services, social media, or news outlets, you can do so freely.
Enjoy Fast Speeds Without Compromising Security
Many users avoid privacy tools due to slow speeds. Fast secure proxy browsers, however, use optimized routing and load-balancing techniques to ensure swift connections, even under heavy traffic.
Protect Data on Public Wi-Fi Networks
Public Wi-Fi is notorious for being a security risk. With a secure proxy browser, you can encrypt your traffic and ensure your data isn’t intercepted by hackers, snoopers, or malicious hotspots.
Essential Features to Look for in a Proxy Browser
End-to-End Encryption Capabilities
Ensure that the proxy browser you choose offers end-to-end encryption. This prevents any third party, including your ISP, from reading your data.
Zero-Log and No Tracking Policies
A true privacy-focused proxy browser won’t log your activity. Check for providers that openly commit to zero-log policies.
Multiple Server Locations for Flexibility
The more server locations available, the easier it is to access global content. It also allows you to switch locations if one is underperforming.
One-Click Access and User-Friendly Interface
Ease of use matters. Look for browsers that require no technical expertise and offer clean, intuitive dashboards for users of all levels.
Use Cases: Who Needs a Fast Secure Proxy Browser?
Journalists and Researchers in Restricted Regions
For those working in countries with limited internet freedom, proxy browsers offer a vital tool for uncensored information gathering.
Everyday Users Who Value Privacy
Even if you're not a whistleblower or journalist, your data matters. Proxy browsers help safeguard everyday browsing activities.
Students Accessing Blocked Educational Resources
Educational institutions sometimes block certain sites. Proxy browsers can help students bypass these restrictions to access learning materials.
Travelers Looking to Avoid Regional Content Blocks
Traveling abroad and can’t access your favorite streaming service? A proxy browser can make it seem like you're back home, unblocking content seamlessly.
How to Get Started with a Secure Proxy Browser
Choosing the Right Tool for Your Needs
Not all proxy browsers are created equal. Look for one that balances speed, privacy, and usability based on your unique needs.
Step-by-Step Setup and Configuration
Download the proxy browser from the official website.
Install and launch the application.
Select a server or location you want to browse from.
Enable encryption settings if available.
Start browsing anonymously.
Tips for Maximizing Speed and Performance
Choose servers closer to your actual location.
Avoid peak usage times when servers may be overloaded.
Clear your browser cache regularly.
Common Mistakes to Avoid
Using free proxies with poor security protocols
Forgetting to turn on encryption settings
Overlooking privacy policies and logging practices
Conclusion
In a world where digital privacy is increasingly under threat, a fast secure proxy browser isn't just a luxury—it's a necessity. From hiding your IP address to bypassing global content barriers, it empowers you to browse anonymously, safely, and without limits.
Whether you're a professional navigating sensitive research or a casual user who values their online freedom, the right proxy browser can redefine your web experience. Choose wisely, stay informed, and take control of your digital journey. Your path to a freer, more secure internet starts now.
FAQ’s
1. What makes a proxy browser fast and secure?It combines optimized server infrastructure with encryption protocols and minimal data logging, ensuring high-speed access and strong privacy.
2. Are proxy browsers legal to use?Yes, using a proxy browser is legal in most countries. However, it's important to comply with local laws regarding internet usage.
3. Can a proxy browser replace a VPN?For basic privacy and unblocking content, yes. But for full-device encryption and enhanced security, a VPN may still be preferable.
4. Do proxy browsers work on mobile devices?Many secure proxy browsers are available for Android and iOS, offering similar features as their desktop counterparts.
5. Are free proxy browsers safe? Not always. Many free services log your data or serve ads. It’s better to choose a reputable proxy browser with a transparent privacy policy.
#secure proxy browser#anonymous web browsing#bypass internet restrictions#online privacy tools#fast proxy service
0 notes
Text
Seamless Transitions: How Blockchain is Revolutionizing Employee Onboarding and Offboarding
The journey of an employee, from their first day to their last, is filled with a myriad of administrative tasks, data exchanges, and critical touchpoints. Traditionally, onboarding is a paperwork-heavy, often fragmented process, while offboarding can be equally cumbersome, involving access revocation, final pay calculations, and knowledge transfer. Both phases are prone to inefficiencies, security risks, and compliance headaches.
Enter blockchain technology – a decentralized, immutable ledger system with the potential to fundamentally transform how HR handles the entire employee lifecycle, particularly the crucial entry and exit points. By leveraging blockchain's inherent security, transparency, and automation capabilities, HR can create a more efficient, secure, and employee-centric experience.
Here are five key ways blockchain is poised to revolutionize employee onboarding and offboarding:
1. Streamlined and Verifiable Credential Verification
One of the most time-consuming and fraud-prone aspects of onboarding is verifying a new hire's credentials: educational degrees, professional certifications, and previous employment history. Blockchain offers a solution by creating immutable, verifiable digital credentials. Universities, professional bodies, and past employers can issue secure digital certificates (often called "verifiable credentials") directly onto a blockchain. During onboarding, HR can instantly and securely verify these credentials with cryptographic certainty, eliminating the need for lengthy background checks, reducing the risk of fraudulent claims, and significantly speeding up the hiring process. This not only saves time and cost but also builds immediate trust.
2. Secure and Immutable Employee Records Management
Employee records contain highly sensitive personal, professional, and financial data. Storing these records on a centralized database makes them vulnerable to data breaches and tampering. Blockchain provides a robust alternative. By storing employee contracts, performance reviews, benefits enrollment forms, tax documents, and intellectual property agreements as encrypted records on a distributed ledger, organizations can ensure unparalleled security, integrity, and immutability. Each update creates a new, time-stamped block in the chain, making it impossible to alter past records without detection. This enhances data security, simplifies audits, and ensures a single source of truth for all employee information throughout their tenure.
3. Automated Compliance and Smart Contracts for Workflow
Smart contracts, self-executing agreements coded onto the blockchain, can automate complex HR workflows with unprecedented efficiency and compliance. During onboarding, smart contracts can automatically trigger actions once conditions are met: for instance, issuing a welcome email, setting up payroll deductions after contract signing, granting system access upon completion of mandatory training, or even automatically enrolling an employee in benefits plans after their probation period. Similarly, during offboarding, smart contracts can ensure a seamless and compliant exit: automatically processing final paychecks, revoking system access, notifying relevant departments, and confirming the return of company assets once specified conditions are met. This automation reduces human error, speeds up processes, and ensures consistent adherence to policies.
4. Enhanced Data Privacy and Employee Control (Self-Sovereign Identity)
Blockchain introduces the concept of Self-Sovereign Identity (SSI), giving employees greater control over their own personal and professional data. Instead of organizations holding all their information, employees can store their verifiable credentials (e.g., identity proofs, qualifications, work history) in a secure digital wallet on their device. When an employer or a third party needs to verify specific information, the employee can selectively disclose only the necessary data with their explicit consent, rather than sharing their entire profile. This enhances privacy, reduces data sprawl across multiple systems, and shifts data ownership towards the individual, building a more trust-based relationship between employee and employer.
5. Seamless Offboarding and Future Re-engagement
Offboarding, while marking an end, is also an opportunity. Blockchain can streamline the process, ensuring all necessary steps are completed securely and efficiently. Access revocations become instant and verifiable. Knowledge transfer assets can be securely linked to the employee's immutable record. Furthermore, for alumni engagement or potential re-hires, the blockchain-based verifiable credentials mean that past performance, skills, and employment history can be instantly re-verified, making future re-onboarding significantly faster and smoother. This maintains a positive relationship and can even facilitate an "alumni network" where former employees' skills remain accessible for future projects or referrals, built on a foundation of secure, verified data.
In conclusion, blockchain technology is not just for cryptocurrencies; its core principles of decentralization, immutability, and transparency offer compelling solutions to long-standing challenges in HR. By integrating blockchain into employee onboarding and offboarding processes, organizations can unlock unprecedented levels of efficiency, security, and trust. This shift promises to create a more streamlined, compliant, and ultimately, a more human-centric employee experience from the moment they join to long after they depart.
To learn more, visit HR Tech Pub.
0 notes
Text
🔗 UPB (Universal Payment Blockchain): The Future of Digital Transactions

🧩 Introduction
In today’s fast-paced digital world, online payments have become an essential part of everyday life. Whether it’s shopping, sending money, or running a business, most of our financial transactions now happen digitally. But there are still problems—high fees, long wait times, and complicated cross-border payments.
That’s where UPB (Universal Payment Blockchain) comes in.
UPB is a new-age crypto token designed to make digital payments faster, cheaper, and more secure. It’s built on blockchain technology and offers a smooth and trustworthy solution for modern financial needs.
In this blog, we’ll explore what UPB is, how it works, where it can be used, and why it’s considered the future of digital finance.
🔍 What is UPB?
UPB stands for Universal Payment Blockchain. It’s a digital cryptocurrency token developed to simplify and improve the way we send and receive money online.
The goal of UPB is simple:
Instant global transactions
Low transaction fees
Secure and transparent system
No need for middlemen like banks or money transfer services
UPB is part of a decentralized blockchain network, which means it isn’t controlled by a single company, government, or bank—instead, it runs on a public network maintained by users all over the world.
⚙️ How Does UPB Work?
UPB works using blockchain technology, which is like a digital ledger that records every transaction securely and transparently.
Here’s how a typical UPB transaction works:
You send UPB tokens to someone.
The transaction is sent to the blockchain network.
The network’s nodes (computers) verify and approve the transaction.
Once verified, it’s recorded on the blockchain.
The receiver gets the UPB tokens—instantly.
No banks, no waiting, no heavy fees. The entire process is fast, secure, and easy.
🔐 Key Features of UPB
✅ 1. Fast Transactions
UPB enables transactions that are completed within seconds, unlike traditional bank transfers that take hours or even days.
✅ 2. Low Fees
UPB offers minimal transaction fees, making it ideal for micro-transactions, freelancing payments, and global transfers.
✅ 3. High Security
Because it’s built on a blockchain, all UPB transactions are encrypted and tamper-proof, making it nearly impossible to hack or manipulate.
✅ 4. Global Access
You can send or receive UPB from anywhere in the world—all you need is an internet connection and a UPB-supported wallet.
✅ 5. No Middlemen
UPB operates on a peer-to-peer basis. No banks, no third-party apps—just you and the person you’re transacting with.
💼 Where Can UPB Be Used?
UPB has many practical uses across different industries and situations:
🔹 Freelancing & Online Work
Freelancers can get paid from international clients using UPB—quickly and with no extra fees or delays.
🔹 E-commerce
Businesses and online stores can accept UPB payments, making checkout faster and safer for customers.
🔹 Cross-border Payments
With UPB, sending money abroad becomes quick and affordable, especially compared to traditional services like Western Union or bank wire transfers.
🔹 Peer-to-Peer Transfers
Whether you’re splitting a bill or sending money to family, UPB is a great choice for direct person-to-person payments.
📈 Future Potential of UPB
As the world shifts more toward digital and decentralized finance, UPB is in a strong position to grow.
Here’s why UPB has long-term potential:
Global demand for fast, borderless payment systems
Blockchain adoption by governments and companies
Growth of Web3, metaverse, and token-based economies
Increased trust in decentralized financial platforms
With the right partnerships and community support, UPB could become a leading digital payment option worldwide.
💡 Why Should You Use UPB?
If you’re someone who
Runs an online business
Works with international clients
Is exploring crypto investment
Wants to send money quickly and securely
Then UPB is for you.
Here’s what makes it worth trying:
Saves time
Reduces costs
Offers better privacy and control
Works globally, 24/7
Easy to use even for beginners
UPB is designed to make digital finance more open and efficient for everyone—not just banks or tech experts.
🛠️ How to Use UPB?
Getting started with UPB is very simple. Just follow these steps:
Step 1: Get a UPB-Compatible Wallet
Install a trusted crypto wallet app (like Trust Wallet or MetaMask) that supports UPB tokens.
Step 2: Add the UPB Token
Manually add the UPB token using its contract address if it’s not listed by default.
Step 3: Receive or Buy UPB
You can get UPB from a friend, a business partner, or purchase it from a crypto exchange (if listed).
Step 4: Start Transacting
Now you can send, receive, or store UPB easily—and use it for online payments or transfers.
❓ Frequently Asked Questions (FAQs)
Q. Is UPB a legal currency?
A. UPB is a cryptocurrency token. Its legal status depends on the regulations of your country, but it’s not illegal in most places. Always check local crypto laws.
Q. Can I earn money using UPB?
A. Yes! You can earn by accepting UPB for services, using it for trading, or holding it as a long-term investment if the token grows in value.
Q. What makes UPB different from Bitcoin?
A. Bitcoin is mainly a store of value. UPB is designed specifically for fast, low-fee payments, making it more practical for everyday use.
🔚 Conclusion
UPB (Universal Payment Blockchain) is more than just a crypto token—it’s a powerful tool for digital finance. It’s fast, secure, easy to use, and built for real-world applications.
In a time when the world is moving away from cash and toward digital money, UPB stands out as a trusted and efficient solution for both individuals and businesses.
Whether you’re a freelancer, business owner, or crypto enthusiast—now is the right time to explore and adopt UPB.
It’s not just the future—it’s the present of smart payments.
0 notes
Text
ISO 27001 Certification in E-Commerce: Why It's Crucial for Bahrain's Online Market

Introduction: Bahrain's e-commerce industry has been on a tear over the last few years. From digital service providers to online retail sites, the business is booming — as are the risks.
In a time when a breach of data can ruin trust in an instant, information security has become the linchpin of e-commerce success. That's where ISO/IEC 27001 certification comes in.
For Bahraini online companies, ISO 27001 is not merely a matter of cybersecurity; it is a matter of gaining customer trust, safeguarding digital property, and adhering to local and global standards. If you have an e-commerce website, payment gateway, or digital logistics system — this certification can be your differentiator.
What Is ISO 27001?
ISO/IEC 27001 is the global standard for Information Security Management Systems (ISMS). It provides a systematic framework to determine, control, and minimize security threats in your business processes.
While you and many companies concentrate on firewalls and antivirus software, ISO 27001 addresses the issue in a more comprehensive, intelligent way. It assists you in controlling:
Data access rights and user permissions
Vulnerabilities to cyberattacks
Customer privacy and confidentiality
Legal and regulatory risks
System availability and dependability
Rather than responding to violations, ISO 27001 prevents them from occurring in the first place.
Why is ISO 27001 Crucial for E-Commerce in Bahrain?
1. Customer Trust Is Everything
Customers in e-commerce exchange confidential information — from bank details to home addresses and shopping history. One leak or hack can destroy your reputation forever.
With ISO 27001, you demonstrate to customers that:
You're serious about their data
You adhere to global best practices
Their personal and financial data is secure
This confidence translates to increased sales, increased retention, and increased word-of-mouth.
2. Cybersecurity Threats Are on the Rise
From phishing sites to ransomware, cybercriminals are attacking online shops more than ever before. Bahrain's move toward digital services also raises local exposure.
ISO 27001 assists you in determining and securing your vulnerabilities prior to attackers. It encompasses not only tech, but also human mistake — such as bad password behavior or unprotected third-party integrations.
3. Regulatory Compliance Is Increasingly Tight
The Personal Data Protection Law (PDPL) in Bahrain and international regulations such as GDPR mandate companies to treat data responsibly.
ISO 27001 assists you in:
Remaining compliant with privacy legislation
Steering clear of enormous fines
Recording and auditing your data handling policies
If you handle foreign customers or partners, certification simplifies overseas data compliance.
4. Encourages Business Partnerships and Expansion
If you are looking to partner with payment processors, logistics firms, or online banks, ISO 27001 provides you with a stamp of credibility.
It demonstrates that your company is dependable, secure, and in compliance with global standards — making it simpler to secure strategic partnerships or attract investment.
E-Commerce Risk Domains Addressed by ISO 27001
This is how ISO 27001 directly relates to e-commerce sites:
E-Commerce Sector
ISO 27001 Implementation
Payment Processing
Secure transaction practices, encryption, fraud management
Customer Data Management
Regulated access, storage security, data classification
Website and App Security
Anti-SQL injection, XSS, DDoS attack protection
Staff Access Controls
Role-based access, password policy
Cloud Hosting
Third-party risk management, backup and availability
Vendor Integrations
Secure APIs and contracts, SLA protections
Email & Marketing
Anti-spam, opt-in/opt-out compliance, email fraud checks
Even one vulnerability might result in a breach. ISO 27001 covers all of them under one umbrella.
Real-World Example: ISO 27001 for a Bahrain-Based Online Retailer
Suppose a Bahrain-based online retail startup sells clothing and electronics throughout the GCC.
Before ISO 27001:
Customer accounts were exposed because of weak password policies
There was no formal process in place for processing data requests or complaints
Third-party plugins within the site were not current
A minor phishing attack briefly took down the site
Following ISO 27001:
Access rights were designated and enforced
Customer information was encrypted and backed up
Periodic risk assessments enabled patching vulnerabilities early on
A well-defined incident response strategy enabled quick recovery by the business from any breach attempt
Result: Customers felt safer, repeat purchases increased, and the company expanded confidently into Saudi Arabia.
Who Should Consider ISO 27001 in Bahrain’s E-Commerce Sector?
Whether you’re a startup or an established platform, ISO 27001 is applicable to:
Online retail stores
B2B e-commerce platforms
Subscription-based service portals
E-wallets and digital payment solutions
Delivery and logistics apps
Online booking and reservation sites
Platforms handling user-generated content or transactions
If your company gathers, maintains, or processes sensitive data, then you must seriously think about ISO 27001 certification.
How to Get ISO 27001 Certified in Bahrain
The certification process usually involves:
Initial Risk Assessment Determine your existing security stance and information assets.
ISMS Development Develop policies and procedures to secure those assets depending on risk levels.
Training and Implementation Train your staff to operate the new system — from management to IT and customer service.
Internal Audit Verify everything is in working order and address any loopholes.
External Certification Audit A certification organization audits your system and grants the ISO 27001 certificate (for 3 years).
Annual Surveillance Keep your system current with audits and improvements.
What Are the Benefits for E-Commerce Businesses?
Increased customer confidence
Less risk of data breaches
Improved compliance with PDPL and global laws
Simplified business partnerships and exports
Improved internal processes and staff accountability
Less downtime due to cyber incidents
All of this ultimately means increased sales, fewer issues, and long-term growth.
How Maxicert Bahrain Can Help
Maxicert provides ISO 27001 consultation and certification services specialized for the e-commerce and digital sectors in Bahrain.
We assist you from initial to final with:
Risk-based gap analysis
Tailor-made policies and documentation
Employee training specific for online businesses
ISMS implementation and sensitization
Co-ordination with Bahrain-approved certifying bodies
Irrespective of whether you're starting a new e-commerce portal or enhancing an existing portal, we make the process of certification easy and cost-effective.
Conclusion:
Bahrain's online marketplace is speedy, intelligent, and full of promise. But it's also constantly at risk from cyber threats and increasing compliance requirements.
ISO 27001 is more than a badge — it's your security play book.
It assists you in establishing a safe, trusted online business that expands without fear. Whether you sell garments, electronics, or services — ISO 27001 is the message that you care about your customers, your brand, and your future.
Frequently Asked Questions (FAQ)
Q1: Is ISO 27001 compulsory for online stores in Bahrain? Not yet, but it's strongly advised — particularly if you process customer information or provide payment services.
Q2: Can small e-commerce companies get ISO 27001? Yes. The system can be scaled to fit your size and scope. Even two-man start-ups can take advantage.
Q3: How long does certification take? Usually 2 to 4 months, depending on your preparedness and team size.
Q4: Is ISO 27001 superior to simply employing cybersecurity software? Yes — because it addresses people, processes, and policies, not solely tech tools.
Q5: Does ISO 27001 assist with GDPR compliance? Definitely. It lays down a framework for privacy protection, breach notification, and data subject rights — which assists with both local and overseas privacy.
0 notes
Text
How Blockchain Technology is Impacting Web Development

You’ve probably heard of blockchain because of cryptocurrencies like Bitcoin, but did you know it’s shaking things up in web development too? Blockchain is like a digital ledger that’s secure, transparent, and super tough to mess with. It’s changing how websites are built, making them safer and more user-focused. In this blog, we’ll chat about how blockchain is impacting web development, what it means for developers, and why businesses, including website development companies in Bhubaneswar, are jumping on board.
What’s Blockchain, Anyway?
At its core, blockchain is a system for storing data across many computers, so no single person or company controls it. Each “block” of data is linked to the one before it, forming a chain that’s nearly impossible to tamper with. Think of it like a shared notebook where everyone can see the entries, but nobody can erase or fake them. In web development, this tech is being used to build websites that are more secure, efficient, and user-friendly.
Why Blockchain Matters for Web Development
Web development is all about creating sites that people trust and enjoy using. Blockchain brings some game-changing benefits to the table:
Better Security: Websites often store sensitive info like passwords or payment details, which hackers love to target. Blockchain’s encryption makes it much harder for bad actors to break in.
Transparency: Because blockchain records are visible to all users, it builds trust. For example, a site using blockchain can show users exactly how their data is being handled.
No Middleman: Blockchain lets users interact directly, cutting out third parties like banks or payment processors. This can make websites faster and cheaper to run.
For website development companies in Bhubaneswar, these perks mean they can offer clients cutting-edge solutions that stand out in a crowded market.
Key Ways Blockchain Is Changing Web Development
Blockchain isn’t just a buzzword—it’s being used in practical ways to improve websites. Here are the big areas where it’s making a difference:
1. Decentralized Websites
Traditional websites rely on central servers, which can crash or get hacked. Blockchain enables decentralized websites, where data is stored across many computers. These sites, often called “Web3” sites, are more reliable because there’s no single point of failure. For example, a blog built on blockchain could stay online even if one server goes down.
2. Smarter Contracts
Smart contracts are like digital agreements that run automatically when certain conditions are met. In web development, they’re used for things like secure payments or user agreements. Imagine an e-commerce site where a smart contract releases payment to the seller only after the buyer confirms delivery—no need for a middleman.
3. Safer User Data
Websites often ask for personal info, which can be a privacy nightmare if mishandled. Blockchain lets users control their own data through decentralized identities. Instead of handing over your details to every site, you share only what’s needed, and it’s stored securely. This is huge for building user trust.
4. Faster Payments with Crypto
Blockchain makes cryptocurrency payments a breeze, which is great for global websites. Developers can integrate crypto wallets into sites, letting users pay instantly without hefty fees. This is especially useful for freelance platforms or online stores targeting international customers.
5. Verifying Digital Assets
Blockchain’s great for proving ownership of things like digital collectibles or domain names. Web developers can use it to create marketplaces where users buy, sell, or trade assets with confidence, knowing the transactions are legit.
Challenges of Using Blockchain
Blockchain sounds awesome, but it’s not all smooth sailing. For one, it’s still pretty complex to set up, so developers need to learn new skills. It can also use a lot of computing power, which isn’t great for the environment. Plus, because blockchain is decentralized, fixing bugs or updating a site can be trickier than with traditional setups. Developers working on blockchain projects need to plan carefully to avoid headaches.
What This Means for Developers
If you’re a web developer, blockchain is an exciting opportunity to level up. Learning tools like Ethereum, Solidity (for smart contracts), or IPFS (for decentralized storage) can make you a hot commodity. Businesses are looking for devs who can build secure, modern websites, and blockchain skills can set you apart. For agencies like those in Bhubaneswar, offering blockchain-based services can attract clients who want the latest tech.
Tips for Getting Started with Blockchain in Web Development
Ready to dip your toes into blockchain? Here’s how to start:
Learn the Basics: Check out free resources on platforms like Coursera or YouTube to understand blockchain and Web3.
Experiment with Tools: Try building a simple decentralized app (dApp) using Ethereum or Polygon to get hands-on experience.
Join Communities: Online forums like Reddit or Discord have tons of blockchain devs sharing tips and ideas.
Start Small: Add blockchain features, like crypto payments, to an existing site before going full Web3.
The Future of Blockchain in Web Development
Blockchain is still young, but it’s growing fast. As more businesses see its value, we’ll likely see websites that are fully decentralized, super secure, and built around user control. This shift could change how we interact online, making the web more open and trustworthy. For developers and agencies, staying ahead of this trend is key to staying competitive.
Wrapping Up
Blockchain is shaking up web development by making websites safer, more transparent, and user-focused. From decentralized sites to smart contracts, it’s opening new doors for developers and businesses alike. While there are some challenges, the benefits are hard to ignore. Whether you’re a developer or a business looking to build a modern site, blockchain is worth exploring. For those partnering with top website development companies in Bhubaneswar, embracing blockchain could be the key to creating websites that stand out and deliver real value.
#digital marketing agency bhubaneswar#website development companies in bhubaneswar#best digital marketing company in bhubaneswar#digital marketing services in bhubaneswar#web development services in bhubaneswar#digital marketing agency in bhubaneswar
0 notes