#oidc
Explore tagged Tumblr posts
Text
Building Your Serverless Sandbox: A Detailed Guide to Multi-Environment Deployments (or How I Learned to Stop Worrying and Love the Cloud)
Introduction Welcome, intrepid serverless adventurers! In the wild world of cloud computing, creating a robust, multi-environment deployment pipeline is crucial for maintaining code quality and ensuring smooth transitions from development to production.Here is part 1 and part 2 of this series. Feel free to read them before continuing on. This guide will walk you through the process of setting…
#automation#aws#AWS S3#CI/CD#Cloud Architecture#cloud computing#cloud security#continuous deployment#DevOps#GitLab#GitLab CI#IAM#Infrastructure as Code#multi-environment deployment#OIDC#pipeline optimization#sandbox#serverless#software development#Terraform
0 notes
Text
What is Argo CD? And When Was Argo CD Established?

What Is Argo CD?
Argo CD is declarative Kubernetes GitOps continuous delivery.
In DevOps, ArgoCD is a Continuous Delivery (CD) technology that has become well-liked for delivering applications to Kubernetes. It is based on the GitOps deployment methodology.
When was Argo CD Established?
Argo CD was created at Intuit and made publicly available following Applatix’s 2018 acquisition by Intuit. The founding developers of Applatix, Hong Wang, Jesse Suen, and Alexander Matyushentsev, made the Argo project open-source in 2017.
Why Argo CD?
Declarative and version-controlled application definitions, configurations, and environments are ideal. Automated, auditable, and easily comprehensible application deployment and lifecycle management are essential.
Getting Started
Quick Start
kubectl create namespace argocd kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/stable/manifests/install.yaml
For some features, more user-friendly documentation is offered. Refer to the upgrade guide if you want to upgrade your Argo CD. Those interested in creating third-party connectors can access developer-oriented resources.
How it works
Argo CD defines the intended application state by employing Git repositories as the source of truth, in accordance with the GitOps pattern. There are various approaches to specify Kubernetes manifests:
Applications for Customization
Helm charts
JSONNET files
Simple YAML/JSON manifest directory
Any custom configuration management tool that is set up as a plugin
The deployment of the intended application states in the designated target settings is automated by Argo CD. Deployments of applications can monitor changes to branches, tags, or pinned to a particular manifest version at a Git commit.
Architecture
The implementation of Argo CD is a Kubernetes controller that continually observes active apps and contrasts their present, live state with the target state (as defined in the Git repository). Out Of Sync is the term used to describe a deployed application whose live state differs from the target state. In addition to reporting and visualizing the differences, Argo CD offers the ability to manually or automatically sync the current state back to the intended goal state. The designated target environments can automatically apply and reflect any changes made to the intended target state in the Git repository.
Components
API Server
The Web UI, CLI, and CI/CD systems use the API, which is exposed by the gRPC/REST server. Its duties include the following:
Status reporting and application management
Launching application functions (such as rollback, sync, and user-defined actions)
Cluster credential management and repository (k8s secrets)
RBAC enforcement
Authentication, and auth delegation to outside identity providers
Git webhook event listener/forwarder
Repository Server
An internal service called the repository server keeps a local cache of the Git repository containing the application manifests. When given the following inputs, it is in charge of creating and returning the Kubernetes manifests:
URL of the repository
Revision (tag, branch, commit)
Path of the application
Template-specific configurations: helm values.yaml, parameters
A Kubernetes controller known as the application controller keeps an eye on all active apps and contrasts their actual, live state with the intended target state as defined in the repository. When it identifies an Out Of Sync application state, it may take remedial action. It is in charge of calling any user-specified hooks for lifecycle events (Sync, PostSync, and PreSync).
Features
Applications are automatically deployed to designated target environments.
Multiple configuration management/templating tools (Kustomize, Helm, Jsonnet, and plain-YAML) are supported.
Capacity to oversee and implement across several clusters
Integration of SSO (OIDC, OAuth2, LDAP, SAML 2.0, Microsoft, LinkedIn, GitHub, GitLab)
RBAC and multi-tenancy authorization policies
Rollback/Roll-anywhere to any Git repository-committed application configuration
Analysis of the application resources’ health state
Automated visualization and detection of configuration drift
Applications can be synced manually or automatically to their desired state.
Web user interface that shows program activity in real time
CLI for CI integration and automation
Integration of webhooks (GitHub, BitBucket, GitLab)
Tokens of access for automation
Hooks for PreSync, Sync, and PostSync to facilitate intricate application rollouts (such as canary and blue/green upgrades)
Application event and API call audit trails
Prometheus measurements
To override helm parameters in Git, use parameter overrides.
Read more on Govindhtech.com
#ArgoCD#CD#GitOps#API#Kubernetes#Git#Argoproject#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
2 notes
·
View notes
Text
LiftMore Update 9.04.2023
I was posting updates on my Medium (see the pinned post), but lately I haven't had time to make a thorough post. Instead, I want to update on a few things in a more informal post here.
API Updates
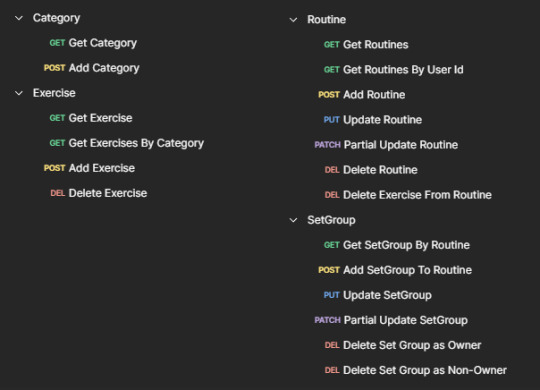
Finally went through and added all of the endpoints I'll need. There are a few endpoints on this list that I'm still in the process of refining permissions and making more secure.
Unit Testing ...ayup.. I came this far into the project without writing a single unit test. I really do want to strive for best TDD practices, but when there's no code at all in my application, it feels really unsatisfying to start working on tests before my code is capable of doing anything. Moving forward in the project, I will definitely strive to do TDD well.
Security Currently, the API just processes users via Basic Authentication. In this upcoming week, I'm planning on creating an identity server and using that server to issue my own OAuth2.0 tokens. I'm not sure yet how I want to set up my IDP service and OIDC Identity Providers.
Deployments Before moving onto the Front-End for this project, I want to make sure that my app is as secure and robust as possible. For this, I want to create 3 different environments (Development, Test, and Production), use a secret manager to inject secrets into the application, and have all of my deployments automated with GitHub Actions. In addition to all this, I want to make sure my application is set up properly between GitHub Actions and AWS so that I can manage dashboards and collect usage/cost information before having any users.
Finally, I'm happy to say that I've acquired the domain name "liftmore.app". After I get through some of the things I mentioned here, I'll push out a landing page and more information of LiftMore from a user perspective in case anybody wants to use it :)
Lastly, little brief preview of my Project board in GitHub at the moment.
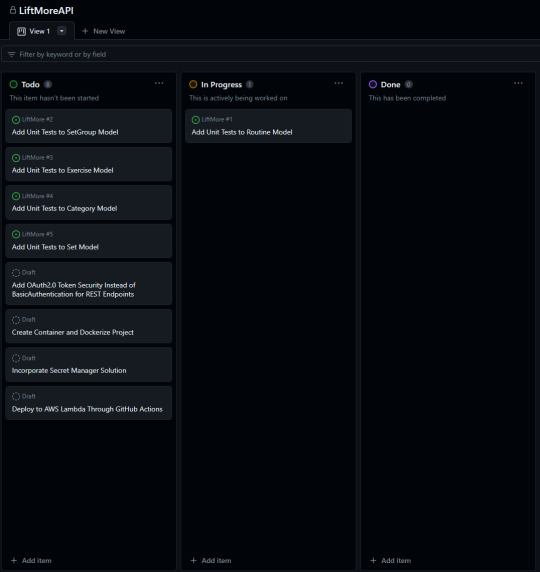
8 notes
·
View notes
Quote
GitHub ActionsのOIDC認証が壊れた件でAWSと限定が付いてたのは、別にエンドポイントがAWS用というわけではなく、中間証明書をpinしろとTLSの証明書チェインを信頼してないのがAWSだけということっぽい。GitHubが悪いというよりAWSが悪い。
城陽人さんはTwitterを使っています
3 notes
·
View notes
Text
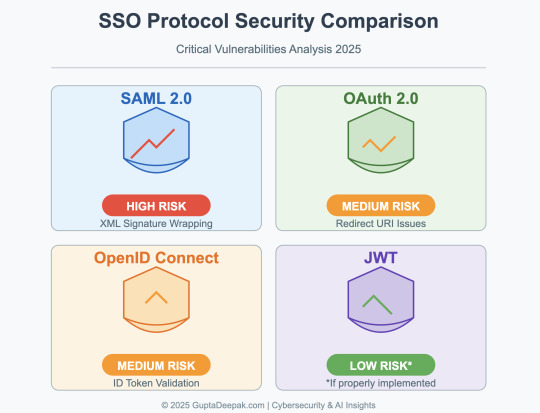
Security Vulnerabilities in SAML, OAuth 2.0, OpenID Connect, and JWT
Single Sign-On (SSO) protocols are critical for enterprise security but have a history of severe vulnerabilities. This report provides a data-rich overview of known security flaws in four major SSO technologies – SAML, OAuth 2.0, OpenID Connect (OIDC), and JSON Web Tokens (JWT) – including both historical exploits and recent findings. We compare the frequency and impact of these vulnerabilities,…
View On WordPress
#assistant professor#computer science#computer scientist#engineering#experimental roboticist#research scientist#university of denver
0 notes
Text
"OIDC and GraphQL: Securing Your API with Identity and Access Control"
1. Introduction In today’s digital landscape, securing APIs is crucial to protect sensitive data and prevent unauthorized access. OpenID Connect (OIDC) and GraphQL are two popular technologies that can help achieve this by providing robust identity and access control mechanisms. In this tutorial, we will explore the basics of OIDC and GraphQL, their benefits, and how they can be used together to…
0 notes
Text
How To: Configure Qlik Sense Enterprise SaaS to Use Azure AD as an IdP
Introduction
Establishing Qlik Sense Enterprise SaaS to use Azure Active Directory (Azure AD) as an identity provider (IdP) is key for companies aiming to streamline access control and authentication for users. Integration between Azure AD and Qlik Sense Enterprise SaaS allows organizations to take advantage of single sign-on (SSO), multi-factor Authentication (MFA), enhanced security features that improve user experience while increasing security simultaneously.

This detailed guide will take you step-by-step through the steps to configure Qlik Sense Enterprise SaaS so it authenticates users by using Azure A.
Prerequisites
Before starting, be sure to are:
An active Azure AD subscription
An Qlik Sense Enterprise SaaS account with administrative access
Permissions to sign up an application within Azure AD
A brief introduction of OAuth 2.0 as well as OpenID Connect (OIDC).
Step 1: Register Qlik Sense Enterprise SaaS in Azure AD
1.1 Access Azure AD
Log into the Azure portal (https://portal.azure.com).
Go through Azure Active Directory from the left menu.
Click on App registrations, then Click New registration.
1.2 Create a New Application Registration
Choose a name for the application (e.g., "Qlik Sense SaaS").
Under the account types that are supported choose Accounts in this organization directory only.
Under the Redirect URI section, click Web and type in the URL:
https:// .qlikcloud.com/login/callback
Click Register.
1.3 Copy Application Credentials
After registration Copy and store the data science information for future use:
Application (client) ID
Directory (tenant) ID
Step 2: Configure Client Secret
2.1 Generate a Client Secret
Click on Certificates and Secrets within the Azure AD application.
Under Client secret, select for a new client's secret.
Select a description, and then an expiration date.
Copy the secret value.
Step 3: Configure API Permissions
3.1 Assign API Permissions
Visit API permissions in the account of your Azure AD application.
Add permissions by clicking the Add button. Microsoft Graph - Delegated permissions.
Find and select:
openid
Email
Profile
offline_access
Select Add Permissions, and Grant admin permission.
Step 4: Configure Qlik Sense Enterprise SaaS
4.1 Access Identity Provider Settings
Log into Qlik Sense Enterprise SaaS as an administrator.
Navigate to Management Console - Identity Providers.
Click Create New, then select OIDC.
4.2 Enter Azure AD Configuration Details
Complete the fields required:
Issuer (Discovery URL):
https://login.microsoftonline.com//v2.0
(Replace"tenant_id" with Your Azure Directory ID)
Client ID (Paste your Application ID into Azure AD)
The Client Secret (Paste your generated secret client)
Authentication Method: Choose Authorization Code
Redirect URL:
https:// .qlikcloud.com/login/callback
4.3 Map User Claims
In the section titled User Claims Mapping Section, you can configure:
Sub - User ID
email - email
Name - Display name
Click Save to save the settings.
Step 5: Test and Verify Integration
5.1 Assign Users in Azure AD
Go to Enterprise Applications in Azure AD.
Choose which Qlik Sense SaaS application.
Click Users and Groups to add users and groups. Assign appropriate users.
5.2 Log into Qlik Sense SaaS with Azure AD
Open Qlik Sense Enterprise SaaS within browser.
Click Sign In with Microsoft.
Log in using in your Azure AD credentials and verify your account.
If the login succeeds, Azure AD is successfully set up to be the IdP to QlikSense Enterprise SaaS.
Troubleshooting Common Issues
Issue 1: Authentication Error
Make sure the redirect URI is identical to the one to the settings in Azure AD and Qlik Sense settings.
Verify that the client's ID and secret are accurate.
Issue 2: User Not Found in Qlik Sense
Confirm that the user has been associated with an account in the Azure AD application.
Make sure you check the claim mappings in Qlik Sense.
Issue 3: Invalid Permissions
Make sure Admin Consent is granted In API Permissions.
Verify that email, openid profile and offline_access permissions are granted.
Conclusion
Follow this step-by-step guide to set up Qlik Sense Enterprise SaaS to utilize Azure AD for its identity Provider (IdP). This integration improves the security of users, their management and access control, while simplifying authentication using SSO. (SSO).
The implementation of Azure Active Directory with Qlik Sense SaaS gives users an improved user experience, improves the compliance of users, and simplifies identity management. If problems arise, examining the claim mappings API access rights, and redirect URIs can help you resolve the issue quickly.
Utilizing Azure AD's authentication capabilities companies can enhance both security and efficiency in the Qlik Sense training enterprise SaaS environment.
FAQs
Q1. Do I have the ability to configure the multi-factor authentication (MFA) in Qlik Sense SaaS users?
Yes MFA can be enabled MFA via Azure AD's Conditional Access Policies.
Q2. Does this integration work with user groups?
Sure, however you must to set up group claim mappings within Azure AD as well as Qlik Sense.
Q3. What is the consequence if the secret client expires?
You must create the new client key in Azure AD and update it to the Qlik Sense settings.
0 notes
Video
youtube
Everything You Ever Wanted to Know About OAuth and OIDC
1 note
·
View note
Text
GitLab Environments: Your Cloud Playground Blueprint
Remember when you were a kid and tried to build the ultimate LEGO castle? You had all these cool pieces, but figuring out how they fit together was the real challenge. Well, welcome to the grown-up version: building your serverless cloud playground! Let’s take a bird’s-eye view of our LEGO set… err, I mean, our solution components. The Grand Blueprint: Components Overview Imagine you’re an…
#aws#CI/CD Pipeline#Cloud Architecture#DevOps Automation#GitLab Environments#GitLab Runner#Infrastructure as Code#OIDC Integration#Parallel Environments#Secure Cloud Access#Serverless Development#Terraform State Management
0 notes
Text
MCP Toolbox for Databases Simplifies AI Agent Data Access

AI Agent Access to Enterprise Data Made Easy with MCP Toolbox for Databases
Google Cloud Next 25 showed organisations how to develop multi-agent ecosystems using Vertex AI and Google Cloud Databases. Agent2Agent Protocol and Model Context Protocol increase agent interactions. Due to developer interest in MCP, we're offering MCP Toolbox for Databases (formerly Gen AI Toolbox for Databases) easy to access your company data in databases. This advances standardised and safe agentic application experimentation.
Previous names: Gen AI Toolbox for Databases, MCP Toolbox
Developers may securely and easily interface new AI agents to business data using MCP Toolbox for Databases (Toolbox), an open-source MCP server. Anthropic created MCP, an open standard that links AI systems to data sources without specific integrations.
Toolbox can now generate tools for self-managed MySQL and PostgreSQL, Spanner, Cloud SQL for PostgreSQL, Cloud SQL for MySQL, and AlloyDB for PostgreSQL (with Omni). As an open-source project, it uses Neo4j and Dgraph. Toolbox integrates OpenTelemetry for end-to-end observability, OAuth2 and OIDC for security, and reduced boilerplate code for simpler development. This simplifies, speeds up, and secures tool creation by managing connection pooling, authentication, and more.
MCP server Toolbox provides the framework needed to construct production-quality database utilities and make them available to all clients in the increasing MCP ecosystem. This compatibility lets agentic app developers leverage Toolbox and reliably query several databases using a single protocol, simplifying development and improving interoperability.
MCP Toolbox for Databases supports ATK
The Agent Development Kit (ADK), an open-source framework that simplifies complicated multi-agent systems while maintaining fine-grained agent behaviour management, was later introduced. You can construct an AI agent using ADK in under 100 lines of user-friendly code. ADK lets you:
Orchestration controls and deterministic guardrails affect agents' thinking, reasoning, and collaboration.
ADK's patented bidirectional audio and video streaming features allow human-like interactions with agents with just a few lines of code.
Choose your preferred deployment or model. ADK supports your stack, whether it's your top-tier model, deployment target, or remote agent interface with other frameworks. ADK also supports the Model Context Protocol (MCP), which secures data source-AI agent communication.
Release to production using Vertex AI Agent Engine's direct interface. This reliable and transparent approach from development to enterprise-grade deployment eliminates agent production overhead.
Add LangGraph support
LangGraph offers essential persistence layer support with checkpointers. This helps create powerful, stateful agents that can complete long tasks or resume where they left off.
For state storage, Google Cloud provides integration libraries that employ powerful managed databases. The following are developer options:
Access the extremely scalable AlloyDB for PostgreSQL using the langchain-google-alloydb-pg-python library's AlloyDBSaver class, or pick
Cloud SQL for PostgreSQL utilising langchain-google-cloud-sql-pg-python's PostgresSaver checkpointer.
With Google Cloud's PostgreSQL performance and management, both store and load agent execution states easily, allowing operations to be halted, resumed, and audited with dependability.
When assembling a graph, a checkpointer records a graph state checkpoint at each super-step. These checkpoints are saved in a thread accessible after graph execution. Threads offer access to the graph's state after execution, enabling fault-tolerance, memory, time travel, and human-in-the-loop.
#technology#technews#govindhtech#news#technologynews#MCP Toolbox for Databases#AI Agent Data Access#Gen AI Toolbox for Databases#MCP Toolbox#Toolbox for Databases#Agent Development Kit
0 notes
Text
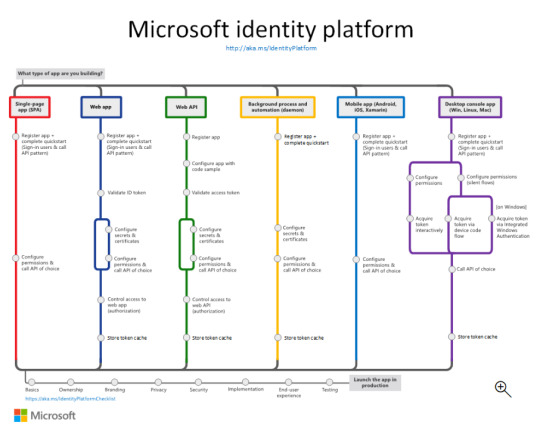
Exploring the Power of Microsoft Identity Platform

Join us on a journey to understand how Microsoft Identity Platform revolutionizes user access, enhancing both security and user experience.
What is microsoft identity platform?
The Microsoft identity platform is a cloud identity service that allows you to build applications your users and customers can sign in to using their Microsoft identities or social accounts. It authorizes access to your own APIs or Microsoft APIs like Microsoft Graph.
OAuth 2.0 and OpenID Connect standard-compliant authentication service enabling developers to authenticate several identity types, including:
Work or school accounts, provisioned through Microsoft Entra ID
Personal Microsoft accounts (Skype, Xbox, Outlook.com)
Social or local accounts, by using Azure AD B2C
Social or local customer accounts, by using Microsoft Entra External ID
Open-source libraries:
Microsoft Authentication Library (MSAL) and support for other standards-compliant libraries. The open source MSAL libraries are recommended as they provide built-in support for conditional access scenarios, single sign-on (SSO) experiences for your users, built-in token caching support, and more. MSAL supports the different authorization grants and token flows used in different application types and scenarios.
Microsoft identity platform endpoint:
The Microsoft identity platform endpoint is OIDC certified. It works with the Microsoft Authentication Libraries (MSAL) or any other standards-compliant library. It implements human readable scopes, in accordance with industry standards.
Application management portal:
A registration and configuration experience in the Microsoft Entra admin center, along with the other application management capabilities.
Application configuration API and PowerShell:
Programmatic configuration of your applications through the Microsoft Graph API and PowerShell so you can automate your DevOps tasks.
Developer content:
Technical documentation including quickstarts, tutorials, how-to guides, API reference, and code samples.
For developers, the Microsoft identity platform offers integration of modern innovations in the identity and security space like passwordless authentication, step-up authentication, and Conditional Access. You don't need to implement such functionality yourself. Applications integrated with the Microsoft identity platform natively take advantage of such innovations.
With the Microsoft identity platform, you can write code once and reach any user. You can build an app once and have it work across many platforms, or build an app that functions as both a client and a resource application (API).
More identity and access management options
Azure AD B2C - Build customer-facing applications your users can sign in to using their social accounts like Facebook or Google, or by using an email address and password.
Microsoft Entra B2B - Invite external users into your Microsoft Entra tenant as "guest" users, and assign permissions for authorization while they use their existing credentials for authentication.
Microsoft Entra External ID - A customer identity and access management (CIAM) solution that lets you create secure, customized sign-in experiences for your customer-facing apps and services.
The Components that make up the Microsoft identity platform:
OAuth 2.0 and OpenID Connect standard-compliant authentication service enabling developers to authenticate several identity types, including:
Work or school accounts, provisioned through Microsoft Entra ID
Personal Microsoft accounts (Skype, Xbox, Outlook.com)
Social or local accounts, by using Azure AD B2C
Social or local customer accounts, by using Microsoft Entra External ID
Open-source libraries: Microsoft Authentication Library (MSAL) and support for other standards-compliant libraries. The open source MSAL libraries are recommended as they provide built-in support for conditional access scenarios, single sign-on (SSO) experiences for your users, built-in token caching support, and more. MSAL supports the different authorization grants and token flows used in different application types and scenarios.
Microsoft identity platform endpoint - The Microsoft identity platform endpoint is OIDC certified. It works with the Microsoft Authentication Libraries (MSAL) or any other standards-compliant library. It implements human readable scopes, in accordance with industry standards.
Application management portal: A registration and configuration experience in the Microsoft Entra admin center, along with the other application management capabilities.
Application configuration API and PowerShell: Programmatic configuration of your applications through the Microsoft Graph API and PowerShell so you can automate your DevOps tasks.
Developer content: Technical documentation including quickstarts, tutorials, how-to guides, API reference, and code samples.
0 notes
Text
SSO Deep Dive: SAML, OAuth, and SCIM in Enterprise Identity Management
Modern enterprises face escalating challenges in managing digital identities across hundreds of applications while maintaining security and compliance. This deep dive explores how SAML, OAuth/OIDC, and SCIM form the backbone of enterprise single sign-on (SSO) ecosystems, addressing critical pain points around user access management, security vulnerabilities, and operational…

View On WordPress
#assistant professor#computer science#computer scientist#engineering#experimental roboticist#research scientist#university of denver
0 notes
Text
0 notes
Text
OIDC vs SAML: A Comprehensive Technical Comparison
http://i.securitythinkingcap.com/T9VlNF
0 notes
Text
PRIME MINISTER DR. DREW DISCUSSES FURTHER COLLABORATION WITH OIDC FOLLOWING CECI VISIT
Published 26 June 2024 Buckie Got It, St. Kitts and Nevis News Source PRIME MINISTER DR. DREW DISCUSSES FURTHER COLLABORATION WITH OIDC FOLLOWING CECI VISIT Taipei, Taiwan, June 26, 2024 (SKNIS): Continuing his official State Visit to the Republic of China (Taiwan), Prime Minister of St. Kitts and Nevis, the Honourable Dr. Terrance Drew, along with his delegation, visited the Overseas…

View On WordPress
0 notes