#multi-environment deployment
Explore tagged Tumblr posts
Text
Building Your Serverless Sandbox: A Detailed Guide to Multi-Environment Deployments (or How I Learned to Stop Worrying and Love the Cloud)
Introduction Welcome, intrepid serverless adventurers! In the wild world of cloud computing, creating a robust, multi-environment deployment pipeline is crucial for maintaining code quality and ensuring smooth transitions from development to production.Here is part 1 and part 2 of this series. Feel free to read them before continuing on. This guide will walk you through the process of setting…
#automation#aws#AWS S3#CI/CD#Cloud Architecture#cloud computing#cloud security#continuous deployment#DevOps#GitLab#GitLab CI#IAM#Infrastructure as Code#multi-environment deployment#OIDC#pipeline optimization#sandbox#serverless#software development#Terraform
0 notes
Text

B-2 Stealth Bomber Demoes QUICKSINK Low Cost Maritime Strike Capability During RIMPAC 2024
The U.S. Air Force B-2 Spirit carried out a QUICKSINK demonstration during the second SINKEX (Sinking Exercise) of RIMPAC 2024. This marks the very first time a B-2 Spirit has been publicly reported to test this anti-ship capability.
David Cenciotti
B-2 QUICKSINK
File photo of a B-2 Spirit (Image credit: Howard German / The Aviationist)
RIMPAC 2024, the 29th in the series since 1971, sees the involvement of 29 nations, 40 surface ships, three submarines, 14 national land forces, over 150 aircraft, and 25,000 personnel. During the drills, two long-planned live-fire sinking exercises (SINKEXs) led to the sinking of two decommissioned ships: USS Dubuque (LPD 8), sunk on July 11, 2024; and the USS Tarawa (LHA 1), sunk on July 19. Both were sunk in waters 15,000 feet deep, located over 50 nautical miles off the northern coast of Kauai, Hawaii.
SINKEXs are training exercises in which decommissioned naval vessels are used as targets. These exercises allow participating forces to practice and demonstrate their capabilities in live-fire scenarios providing a unique and realistic training environment that cannot be replicated through simulations or other training methods.
RIMPAC 2024’s SINKEXs allowed units from Australia, Malaysia, the Netherlands, South Korea, and various U.S. military branches, including the Air Force, Army, and Navy, to enhance their skills and tactics as well as validate targeting, and live firing capabilities against surface ships at sea. They also helped improve the ability of partner nations to plan, communicate, and execute complex maritime operations, including precision and long-range strikes.
LRASM
During the sinking of the ex-Tarawa, a U.S. Navy F/A-18F Super Hornet deployed a Long-Range Anti-Ship Missile (LRASM). This advanced, stealthy cruise missile offers multi-service, multi-platform, and multi-mission capabilities for offensive anti-surface warfare and is currently deployed from U.S. Navy F/A-18 and U.S. Air Force B-1B aircraft.
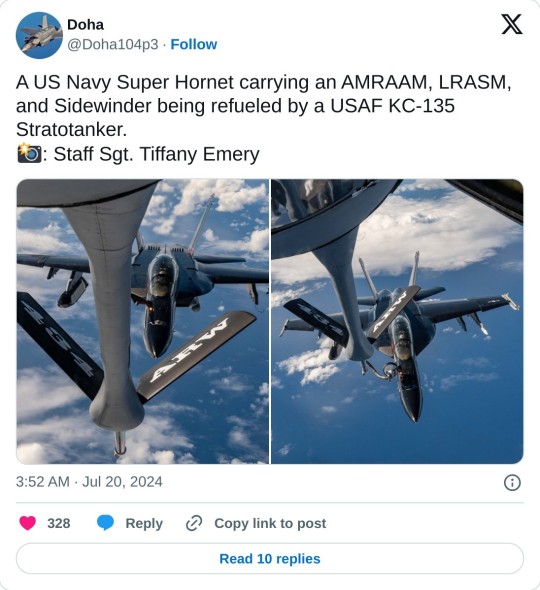
The AGM-158C LRASM, based on the AGM-158B Joint Air-to-Surface Standoff Missile – Extended Range (JASSM-ER), is the new low-observable anti-ship cruise missile developed by DARPA (Defense Advanced Research Projects Agency) for the U.S. Air Force and U.S. Navy. NAVAIR describes the weapon as a defined near-term solution for the Offensive Anti-Surface Warfare (OASuW) air-launch capability gap that will provide flexible, long-range, advanced, anti-surface capability against high-threat maritime targets.
QUICKSINK
Remarkably, in a collaborative effort with the U.S. Navy, a U.S. Air Force B-2 Spirit stealth bomber also took part in the second SINKEX, demonstrating a low-cost, air-delivered method for neutralizing surface vessels using the QUICKSINK. Funded by the Office of the Under Secretary of Defense for Research and Engineering, the QUICKSINK experiment aims to provide cost-effective solutions to quickly neutralize maritime threats over vast ocean areas, showcasing the flexibility of the joint force.
The Quicksink initiative, in collaboration with the U.S. Navy, is designed to offer innovative solutions for swiftly neutralizing stationary or moving maritime targets at a low cost, showcasing the adaptability of joint military operations for future combat scenarios. “Quicksink is distinctive as it brings new capabilities to both current and future Department of Defense weapon systems, offering combatant commanders and national leaders fresh methods to counter maritime threats,” explained Kirk Herzog, the program manager at the Air Force Research Laboratory (AFRL).
Traditionally, enemy ships are targeted using submarine-launched heavyweight torpedoes, which, while effective, come with high costs and limited deployment capabilities among naval assets. “Heavyweight torpedoes are efficient at sinking large ships but are expensive and deployed by a limited number of naval platforms,” stated Maj. Andrew Swanson, division chief of Advanced Programs at the 85th Test and Evaluation Squadron. “Quicksink provides a cost-effective and agile alternative that could be used by a majority of Air Force combat aircraft, thereby expanding the options available to combatant commanders and warfighters.”
Regarding weapon guidance, the QUICKSINK kit combines a GBU-31/B Joint Direct Attack Munition’s existing GPS-assisted inertial navigation system (INS) guidance in the tail with a new radar seeker installed on the nose combined with an IIR (Imaging Infra-Red) camera mounted in a fairing on the side. When released, the bomb uses the standard JDAM kit to glide to the target area and the seeker/camera to lock on the ship. Once lock on is achieved, the guidance system directs the bomb to detonate near the hull below the waterline.
Previous QUICKSINK demonstrations in 2021 and 2022 featured F-15E Strike Eagles deploying modified 2,000-pound GBU-31 JDAMs. This marks the very first time a B-2 Spirit has been publicly reported to test this anti-ship capability. Considering a B-2 can carry up to 16 GBU-31 JDAMs, this highlights the significant anti-surface firepower a single stealth bomber can bring to a maritime conflict scenario.
Quicksink

F-15E Strike Eagle at Eglin Air Force Base, Fla. with modified 2,000-pound GBU-31 Joint Direct Attack Munitions as part of the second test in the QUICKSINK Joint Capability Technology Demonstration on April 28, 2022. (U.S. Air Force photo / 1st Lt Lindsey Heflin)
SINKEXs
“Sinking exercises allow us to hone our skills, learn from one another, and gain real-world experience,” stated U.S. Navy Vice Adm. John Wade, the RIMPAC 2024 Combined Task Force Commander in a public statement. “These drills demonstrate our commitment to maintaining a safe and open Indo-Pacific region.”
Ships used in SINKEXs, known as hulks, are prepared in strict compliance with Environmental Protection Agency (EPA) regulations under a general permit the Navy holds pursuant to the Marine Protection, Research, and Sanctuaries Act. Each SINKEX requires the hulk to sink in water at least 6,000 feet deep and more than 50 nautical miles from land.
In line with EPA guidelines, before a SINKEX, the Navy thoroughly cleans the hulk, removing all materials that could harm the marine environment, including polychlorinated biphenyls (PCBs), petroleum, trash, and other hazardous materials. The cleaning process is documented and reported to the EPA before and after the SINKEX.

Royal Netherlands Navy De Zeven Provinciën-class frigate HNLMS Tromp (F803) fires a Harpoon missile during a long-planned live fire sinking exercise as part of Exercise Rim of the Pacific (RIMPAC) 2024. (Royal Netherlands Navy photo by Cristian Schrik)
SINKEXs are conducted only after the area is surveyed to ensure no people, marine vessels, aircraft, or marine species are present. These exercises comply with the National Environmental Policy Act and are executed following permits and authorizations under the Marine Mammal Protection Act, Endangered Species Act, and Marine Protection, Research, and Sanctuaries Act.
The ex-Dubuque, an Austin-class amphibious transport dock, was commissioned on September 1, 1967, and served in Vietnam, Operation Desert Shield, and other missions before being decommissioned in June 2011. The ex-Tarawa, the lead amphibious assault ship of its class, was commissioned on May 29, 1976, participated in numerous operations including Desert Shield and Iraqi Freedom, and was decommissioned in March 2009.
This year marks the second time a Tarawa-class ship has been used for a SINKEX, following the sinking of the ex-USS Belleau Wood (LHA 3) during RIMPAC 2006.
H/T Ryan Chan for the heads up!
About David Cenciotti
David Cenciotti is a journalist based in Rome, Italy. He is the Founder and Editor of “The Aviationist”, one of the world’s most famous and read military aviation blogs. Since 1996, he has written for major worldwide magazines, including Air Forces Monthly, Combat Aircraft, and many others, covering aviation, defense, war, industry, intelligence, crime and cyberwar. He has reported from the U.S., Europe, Australia and Syria, and flown several combat planes with different air forces. He is a former 2nd Lt. of the Italian Air Force, a private pilot and a graduate in Computer Engineering. He has written five books and contributed to many more ones.
@TheAviationist.com
12 notes
·
View notes
Text
Chapter 1: Files
Masterlist - Next Chapter
Confidential Report on Human Experimentation: Super Soldier Serum Trial
Date: October 9th, 1947
Location: Classified Facility, Sector 17
Lead Scientist: Dr. Arnim Zola
Subject ID: 004Z (Alias: “Subject Crimson”)

Objective
To test the efficacy of Super Soldier Serum B-13 (Alias: “SSSB13”) in significantly enhancing physical and cognitive abilities beyond natural limits.
This report details the effects observed on one individual subjected to the serum in a controlled environment.
Subject Information
- Name: Classified
- Age: 29
- Gender: Female
- Height: 5’9”
- Weight: 175 lbs (Pre-serum)
- Medical History: Healthy, no pre-existing conditions, physically fit (military background). Psychological profile indicates average resilience to stress and trauma.
Administration of Serum
- Dosage: 30ml injection, administered in two stages over a 48-hour period.
- Phase 1 (0-24 hours: Preliminary physical and neural enhancements.
- Phase 2 (24-48 hours): Stabilization and further augmentation of sensory and cognitive abilities.
Phase 1: Initial Effects (0-24 Hours)
Physical Changes:
- Muscle Mass: Noticeable increase in muscle density (+15% mass) within the first 6 hours.
- Strength: Strength tests indicated a 250% increase in raw lifting capacity, confirmed via standard load-bearing equipment. Subject Crimson lifted 700 lbs effortlessly by hour 12.
- Endurance: Cardiovascular endurance improved by 180% based on treadmill stress testing at hour 20.
Cognitive Changes:
- Reflexes: Reaction time dropped from 0.2 seconds to 0.03 seconds. Subject Crimson was able to dodge incoming projectiles.
- Neural Efficiency: Subject reported a heightened sense of awareness and perception, able to track movements in his peripheral vision with pinpoint accuracy. Neurological scans showed a 45% increase in synaptic firing rates.
---
Phase 2: Sensory and Cognitive Augmentation (24-48 Hours)
Sensory Enhancements:
- Vision: Subject Crimson reported enhanced visual acuity. Tests showed that her night vision had improved tenfold, and she could discern movement from over 1,000 feet in low-light conditions.
- Hearing: Subject detected frequencies up to 50 kHz, well beyond the human range, and accurately identified the source of faint noises within a 200-meter radius.
- Touch: Hyper-awareness of tactile sensations was observed. Subject could sense minute vibrations through solid objects.
Cognitive Enhancements:
- Problem Solving & Memory: The subject solved complex puzzles in record time. Long-term memory recall improved by 300%, allowing Subject Crimson to recite entire documents verbatim after one reading.
- Multi-tasking: Subject exhibited the ability to manage up to five different cognitive tasks simultaneously without error or loss of focus.
---
Post-Trial Monitoring
- Physical Stability: No signs of physical breakdown or adverse reactions have been detected. Vital signs remain in optimal ranges despite sustained extreme exertion.
---
Conclusion
The results of the SSSB13 trial on Subject Crimson have surpassed expectations, achieving a level of human enhancement previously deemed impossible.
The subject now possesses physical strength, agility, enhanced sensory perception, and superior cognitive function.
Long-term effects are still under observation, but preliminary data suggest that SSSB13 has the potential to redefine soldier capabilities.
Further experimentation will explore scalability, mass production, and ethical implications. Caution is advised in deployment to ensure control over enhanced subjects.
---
This report is classified and intended for authorized personnel only. Unauthorized distribution is a violation of Section 8b.
---
Report Compiled by:
Dr. Arnim Zola
Project CRIMSON
#marvel#mcu#marvel cinematic universe#marvel x reader#mcu x reader#bucky barnes x reader#bucky barnes#arnim zola#HYDRA#hail hydra
9 notes
·
View notes
Text




PlayStation 7 RC Drone Controller – Advanced Combat Defense Edition
A next-generation defensive-command controller built for tactical resilience, strategic control, and extreme operational endurance. Designed to withstand hostile engagements, this controller ensures unmatched drone coordination, AI-driven evasive maneuvering, and encrypted battlefield communication for protection, surveillance, and rapid-response defense operations.
🛡️ DEFENSIVE-FOCUSED DESIGN
Structural Resilience
Fortified Carbon-Titanium Alloy Chassis: Shatterproof under direct impact and resistant to concussive force.
Ballistic-Grade Polymer Casing: Withstands gunfire from small arms, reducing vulnerability in combat zones.
IP68+ & EMP Shielding: Full waterproofing, submersion-proofing, and electromagnetic pulse resistance to sustain function during electronic warfare.
Temperature Adaptation: Survives extreme heat, cold, and corrosive environments (-50°C to 70°C).
Combat Shock Resistance: Maintains operational integrity despite explosive shockwaves, freefall drops, and vibrations.
🛠️ DEFENSE-ORIENTED CONTROL & NAVIGATION
Fortified Control System
AI-Assisted Flight Stabilization: Ensures precision control even during high-intensity engagements or power fluctuations.
Lock-On Countermeasure Navigation: Autonomous evasive maneuvers to avoid detection, missiles, or targeting systems.
Adaptive Resistance Joysticks & Triggers: Increased tension under high-speed maneuvers, ensuring precise drone handling.
Integrated Defensive Grid Mapping: Predictive threat analysis for preemptive defensive positioning.
Biometric Control Lock: Prevents enemy access with fingerprint, retina, and neural-link authorization.
🔐 DEFENSIVE SECURITY SYSTEMS
Unbreakable Tactical Communication
Quantum-Encrypted Frequency Hopping: Prevents hacking, jamming, and signal hijacking in active combat.
Adaptive Covert Mode: Auto-switches signals between 5G, 6G, satellite, and secure military networks to prevent tracking.
Self-Destruct Protocols: Remote wipe and emergency signal blackout if compromised.
Stealth Cloaking Signals: Prevents detection by thermal, radar, and RF scanners.
🛡️ DEFENSIVE COMBAT & COUNTERMEASURES
Active Protection & Tactical Deployment
AI-Assisted Threat Recognition: Detects and tracks incoming projectiles, hostile drones, and enemy assets in real time.
Auto-Deploy Jamming & Counter-Intel Systems:
Disrupts enemy targeting systems attempting to lock onto controlled drones.
Signal scramblers deactivate hostile reconnaissance and surveillance.
Remote EMP Defense Protocol to disable nearby enemy electronics.
Advanced Drone & Multi-Agent Defense
Multi-Drone Tactical Formation:
Defensive Swarm AI capable of forming barriers and tactical screens against enemy forces.
Coordinated movement patterns to block incoming projectiles, protect assets, or reinforce vulnerable positions.
Autonomous Guardian Mode:
If the user is incapacitated, the AI-controlled drones will return, engage defensive formations, or initiate extraction procedures.
🔋 DEFENSIVE POWER SYSTEMS
Sustained Operation & Emergency Recovery
Dual Graphene Battery with 96-hour Charge: Runs for days without failure.
Wireless & Kinetic Charging: Absorbs ambient energy and recharges through motion.
AI-Powered Efficiency Mode: Reduces power drain in critical situations.
🚨 USE CASES FOR EXTREME DEFENSE & SECURITY
Urban & Battlefield Defense: Deploys defensive drones for cover, escort protection, and rapid response to threats.
Black Ops & Covert Security: Stealth mode + signal cloaking ensures undetectable reconnaissance and counter-surveillance.
Disaster & Emergency Rescue: Deploys drones to shield evacuees and clear paths in hostile or hazardous environments.
Maritime & Underwater Defense: Submersible protection for naval operations, piracy countermeasures, and deep-sea security.
🛡️ FINAL REINFORCEMENTS
Would you like to integrate riot-control dispersal systems, autonomous threat neutralization, or hybrid drone-to-weapon interfacing for ultimate defensive superiority?
#Tactical#PlayStation 7#AI#Aesthetic defense intelligence#DearDearest brands#Sony#Defense#Tactical defense#Spy gear#Cyber cat#Spy drone cat#Drone#AI drone#Chanel#enXanting
3 notes
·
View notes
Text
KIOXIA Unveils 122.88TB LC9 Series NVMe SSD to Power Next-Gen AI Workloads

KIOXIA America, Inc. has announced the upcoming debut of its LC9 Series SSD, a new high-capacity enterprise solid-state drive (SSD) with 122.88 terabytes (TB) of storage, purpose-built for advanced AI applications. Featuring the company’s latest BiCS FLASH™ generation 8 3D QLC (quad-level cell) memory and a fast PCIe® 5.0 interface, this cutting-edge drive is designed to meet the exploding data demands of artificial intelligence and machine learning systems.
As enterprises scale up AI workloads—including training large language models (LLMs), handling massive datasets, and supporting vector database queries—the need for efficient, high-density storage becomes paramount. The LC9 SSD addresses these needs with a compact 2.5-inch form factor and dual-port capability, providing both high capacity and fault tolerance in mission-critical environments.
Form factor refers to the physical size and shape of the drive—in this case, 2.5 inches, which is standard for enterprise server deployments. PCIe (Peripheral Component Interconnect Express) is the fast data connection standard used to link components to a system’s motherboard. NVMe (Non-Volatile Memory Express) is the protocol used by modern SSDs to communicate quickly and efficiently over PCIe interfaces.
Accelerating AI with Storage Innovation
The LC9 Series SSD is designed with AI-specific use cases in mind—particularly generative AI, retrieval augmented generation (RAG), and vector database applications. Its high capacity enables data-intensive training and inference processes to operate without the bottlenecks of traditional storage.
It also complements KIOXIA’s AiSAQ™ technology, which improves RAG performance by storing vector elements on SSDs instead of relying solely on costly and limited DRAM. This shift enables greater scalability and lowers power consumption per TB at both the system and rack levels.
“AI workloads are pushing the boundaries of data storage,” said Neville Ichhaporia, Senior Vice President at KIOXIA America. “The new LC9 NVMe SSD can accelerate model training, inference, and RAG at scale.”
Industry Insight and Lifecycle Considerations
Gregory Wong, principal analyst at Forward Insights, commented:
“Advanced storage solutions such as KIOXIA’s LC9 Series SSD will be critical in supporting the growing computational needs of AI models, enabling greater efficiency and innovation.”
As organizations look to adopt next-generation SSDs like the LC9, many are also taking steps to responsibly manage legacy infrastructure. This includes efforts to sell SSD units from previous deployments—a common practice in enterprise IT to recover value, reduce e-waste, and meet sustainability goals. Secondary markets for enterprise SSDs remain active, especially with the ongoing demand for storage in distributed and hybrid cloud systems.
LC9 Series Key Features
122.88 TB capacity in a compact 2.5-inch form factor
PCIe 5.0 and NVMe 2.0 support for high-speed data access
Dual-port support for redundancy and multi-host connectivity
Built with 2 Tb QLC BiCS FLASH™ memory and CBA (CMOS Bonded to Array) technology
Endurance rating of 0.3 DWPD (Drive Writes Per Day) for enterprise workloads
The KIOXIA LC9 Series SSD will be showcased at an upcoming technology conference, where the company is expected to demonstrate its potential role in powering the next generation of AI-driven innovation.
2 notes
·
View notes
Text
The Strategic Role of Check-in Kiosks in Military Airport Terminals

Military airport terminals operate under heightened security and efficiency demands compared to their commercial counterparts. These facilities not only handle routine transport of service members but also play crucial roles in logistics, emergency deployments, and diplomatic missions. In such high-stakes environments, even minor inefficiencies or security lapses can have significant consequences.
To meet these challenges, many military terminals are turning to check-in kiosk technology—automated, self-service systems that streamline passenger processing and improve terminal security. These kiosks, equipped with advanced features such as biometric scanning, real-time data synchronization, and user-friendly interfaces, are reshaping the operational landscape of military air travel. In this blog, we explore how kiosk technology enhances security, boosts efficiency, improves user experience, and supports long-term cost-effectiveness and emergency readiness in military airport terminals.
Enhancing Security Protocols with Check-in Kiosks
Security is paramount in military environments, and check-in kiosks significantly contribute to strengthening existing protocols. These kiosks do more than expedite the check-in process—they integrate seamlessly with military-grade security systems to ensure rigorous identity verification and real-time data updates.
Biometric Integration for Identity Verification
One of the standout features of military check-in kiosks is biometric integration. Fingerprint scans, iris recognition, and facial recognition ensure that only authorized personnel gain access to secured areas. These systems eliminate the risks associated with lost or forged ID cards and allow for multi-factor authentication, which is critical in sensitive operations.
Biometric data is instantly matched against military personnel databases and watchlists, providing a higher level of accuracy and preventing unauthorized access. The process is not only secure but also faster and less intrusive than traditional methods, offering a seamless experience for users.
Real-Time Data Synchronization with Security Networks
Check-in kiosks in military terminals are linked to centralized security networks, allowing for real-time synchronization of data. When a service member checks in, their identity, assignment, and travel itinerary are cross-verified with military systems to detect inconsistencies or threats.
This instant communication enhances threat detection and tracking capabilities, allowing security personnel to respond swiftly to anomalies. Furthermore, in the event of a security breach, kiosks provide critical logs and timestamps to aid investigation and resolution.

Increasing Operational Efficiency in Terminal Management
Military terminals operate around tight schedules and high throughput. By automating check-in procedures, kiosks alleviate common bottlenecks and enhance operational efficiency.
Automated Boarding Pass and ID Issuance
Traditional check-in desks involve manual data entry and document verification, which can slow down the boarding process. In contrast, automated kiosks issue boarding passes and temporary access credentials within seconds, drastically reducing processing time.
Kiosks can print, scan, and digitally store documentation, minimizing the likelihood of human error. This not only improves accuracy but also enhances compliance with standardized military travel protocols.
Reduced Staff Workload and Resource Allocation
By handling repetitive check-in tasks, kiosks free up human resources for more critical responsibilities. Personnel previously tied to desk duties can be reassigned to areas such as tactical operations, logistics support, or passenger assistance.
This optimized resource allocation ensures that the terminal functions more smoothly, even during peak hours or large-scale deployments. It also reduces the risk of operational delays, contributing to overall mission readiness.
Improving User Experience for Military Personnel and Visitors
Ease of use is crucial in high-pressure environments. Military check-in kiosks are designed with user-centric interfaces, ensuring accessibility for all users, including service members, dependents, and visitors.
Multilingual Support and Accessibility Features
Military airports cater to diverse users from various linguistic and cultural backgrounds. Kiosks equipped with multilingual options ensure that language barriers do not impede check-in or access.
Moreover, features such as voice commands, screen magnification, and wheelchair-accessible interfaces make these kiosks usable for individuals with disabilities. This commitment to inclusivity aligns with military values and enhances the overall user experience.
24/7 Availability and Minimizing Congestion
Unlike staffed check-in counters, kiosks offer uninterrupted service around the clock. This is especially beneficial in military operations where flights and deployments can occur at odd hours or on short notice.
By distributing the check-in load across multiple kiosks, these systems minimize terminal congestion, allowing for smoother passenger flow and reduced wait times. This is particularly valuable during mobilizations, drills, or emergency evacuations.
Cost-Effectiveness and Long-Term Savings
Implementing kiosk systems in military terminals requires upfront investment, but the long-term financial benefits make a compelling case for adoption.
Reduction in Manual Processing Costs
Kiosks reduce the need for manual data entry, paper forms, and physical staffing, all of which incur recurring costs. Digital processes streamline administrative workflows and lower the chances of clerical errors, which can be costly and time-consuming to fix.
In addition, kiosks help reduce the environmental footprint of military operations by minimizing paper use—a growing priority in defense logistics.
Scalability to Meet Future Demands
Modern kiosk systems are built with modular and scalable designs, allowing for future upgrades without major overhauls. As military travel protocols evolve, new software features or hardware modules (e.g., upgraded biometric sensors or contactless payment capabilities) can be easily integrated.
This future-proofing makes kiosk systems a strategic investment, capable of adapting to shifting operational needs and technological advancements.

Supporting Emergency and Contingency Operations
Military terminals must remain operational under all circumstances, including crises. Kiosks offer resilience and flexibility during emergencies, supporting both evacuation and redeployment efforts.
Rapid Reconfiguration for Emergency Protocols
In the event of a crisis—whether it’s a natural disaster, base lockdown, or global conflict—check-in kiosks can be rapidly reprogrammed to follow new protocols. For example, they can be configured to prioritize certain personnel categories, enable emergency passes, or facilitate health screenings during pandemics.
This capability allows terminals to maintain order and operational continuity, even in high-stress environments.
Reliable Communication Channels for Critical Updates
During emergencies, timely and accurate communication is essential. Kiosks can function as broadcast hubs, displaying critical alerts, evacuation routes, or mission updates directly on the screen.
Some systems can also send automated SMS or email updates to personnel, ensuring that everyone receives the necessary information regardless of their physical location within the terminal. This functionality is invaluable during fast-moving operations where traditional communication lines may be overloaded or unavailable.
Conclusion
Check-in kiosks are no longer just a convenience feature—they are a strategic asset in military airport terminals. From strengthening security with biometric authentication and real-time data sync, to improving operational efficiency and delivering a seamless user experience, kiosks represent a significant leap forward in military logistics technology.
They not only reduce costs and optimize personnel usage, but also enhance readiness and resilience during emergencies. With scalable architectures and support for the latest security features, kiosk systems are well-positioned to meet the future demands of military air transport.
For defense organizations aiming to modernize their infrastructure and improve mission efficiency, adopting kiosk technology is not just an option—it’s a mission-critical necessity.
#kiosk#technology#software#business#development#programming#productivity#airport#check in kiosk#tech#techtrends#selfservicekiosk#kioskmachine#innovation#kiosks#panashi#techinnovation#digitaltransformation
2 notes
·
View notes
Text
800G OSFP - Optical Transceivers -Fibrecross


800G OSFP and QSFP-DD transceiver modules are high-speed optical solutions designed to meet the growing demand for bandwidth in modern networks, particularly in AI data centers, enterprise networks, and service provider environments. These modules support data rates of 800 gigabits per second (Gbps), making them ideal for applications requiring high performance, high density, and low latency, such as cloud computing, high-performance computing (HPC), and large-scale data transmission.
Key Features
OSFP (Octal Small Form-Factor Pluggable):
Features 8 electrical lanes, each capable of 100 Gbps using PAM4 modulation, achieving a total of 800 Gbps.
Larger form factor compared to QSFP-DD, allowing better heat dissipation (up to 15W thermal capacity) and support for future scalability (e.g., 1.6T).
Commonly used in data centers and HPC due to its robust thermal design and higher power handling.
QSFP-DD (Quad Small Form-Factor Pluggable Double Density):
Also uses 8 lanes at 100 Gbps each for 800 Gbps total throughput.
Smaller and more compact than OSFP, with a thermal capacity of 7-12W, making it more energy-efficient.
Backward compatible with earlier QSFP modules (e.g., QSFP28, QSFP56), enabling seamless upgrades in existing infrastructure.
Applications
Both form factors are tailored for:
AI Data Centers: Handle massive data flows for machine learning and AI workloads.
Enterprise Networks: Support high-speed connectivity for business-critical applications.
Service Provider Networks: Enable scalable, high-bandwidth solutions for telecom and cloud services.
Differences
Size and Thermal Management: OSFP’s larger size supports better cooling, ideal for high-power scenarios, while QSFP-DD’s compact design suits high-density deployments.
Compatibility: QSFP-DD offers backward compatibility, reducing upgrade costs, whereas OSFP often requires new hardware.
Use Cases: QSFP-DD is widely adopted in Ethernet-focused environments, while OSFP excels in broader applications, including InfiniBand and HPC.
Availability
Companies like Fibrecross,FS.com, and Cisco offer a range of 800G OSFP and QSFP-DD modules, supporting various transmission distances (e.g., 100m for SR8, 2km for FR4, 10km for LR4) over multimode or single-mode fiber. These modules are hot-swappable, high-performance, and often come with features like low latency and high bandwidth density.
For specific needs—such as short-range (SR) or long-range (LR) transmission—choosing between OSFP and QSFP-DD depends on your infrastructure, power requirements, and future scalability plans. Would you like more details on a particular module type or application?
2 notes
·
View notes
Text
Exploring the Azure Technology Stack: A Solution Architect’s Journey
Kavin
As a solution architect, my career revolves around solving complex problems and designing systems that are scalable, secure, and efficient. The rise of cloud computing has transformed the way we think about technology, and Microsoft Azure has been at the forefront of this evolution. With its diverse and powerful technology stack, Azure offers endless possibilities for businesses and developers alike. My journey with Azure began with Microsoft Azure training online, which not only deepened my understanding of cloud concepts but also helped me unlock the potential of Azure’s ecosystem.
In this blog, I will share my experience working with a specific Azure technology stack that has proven to be transformative in various projects. This stack primarily focuses on serverless computing, container orchestration, DevOps integration, and globally distributed data management. Let’s dive into how these components come together to create robust solutions for modern business challenges.

Understanding the Azure Ecosystem
Azure’s ecosystem is vast, encompassing services that cater to infrastructure, application development, analytics, machine learning, and more. For this blog, I will focus on a specific stack that includes:
Azure Functions for serverless computing.
Azure Kubernetes Service (AKS) for container orchestration.
Azure DevOps for streamlined development and deployment.
Azure Cosmos DB for globally distributed, scalable data storage.
Each of these services has unique strengths, and when used together, they form a powerful foundation for building modern, cloud-native applications.
1. Azure Functions: Embracing Serverless Architecture
Serverless computing has redefined how we build and deploy applications. With Azure Functions, developers can focus on writing code without worrying about managing infrastructure. Azure Functions supports multiple programming languages and offers seamless integration with other Azure services.
Real-World Application
In one of my projects, we needed to process real-time data from IoT devices deployed across multiple locations. Azure Functions was the perfect choice for this task. By integrating Azure Functions with Azure Event Hubs, we were able to create an event-driven architecture that processed millions of events daily. The serverless nature of Azure Functions allowed us to scale dynamically based on workload, ensuring cost-efficiency and high performance.
Key Benefits:
Auto-scaling: Automatically adjusts to handle workload variations.
Cost-effective: Pay only for the resources consumed during function execution.
Integration-ready: Easily connects with services like Logic Apps, Event Grid, and API Management.
2. Azure Kubernetes Service (AKS): The Power of Containers
Containers have become the backbone of modern application development, and Azure Kubernetes Service (AKS) simplifies container orchestration. AKS provides a managed Kubernetes environment, making it easier to deploy, manage, and scale containerized applications.
Real-World Application
In a project for a healthcare client, we built a microservices architecture using AKS. Each service—such as patient records, appointment scheduling, and billing—was containerized and deployed on AKS. This approach provided several advantages:
Isolation: Each service operated independently, improving fault tolerance.
Scalability: AKS scaled specific services based on demand, optimizing resource usage.
Observability: Using Azure Monitor, we gained deep insights into application performance and quickly resolved issues.
The integration of AKS with Azure DevOps further streamlined our CI/CD pipelines, enabling rapid deployment and updates without downtime.
Key Benefits:
Managed Kubernetes: Reduces operational overhead with automated updates and patching.
Multi-region support: Enables global application deployments.
Built-in security: Integrates with Azure Active Directory and offers role-based access control (RBAC).
3. Azure DevOps: Streamlining Development Workflows
Azure DevOps is an all-in-one platform for managing development workflows, from planning to deployment. It includes tools like Azure Repos, Azure Pipelines, and Azure Artifacts, which support collaboration and automation.
Real-World Application
For an e-commerce client, we used Azure DevOps to establish an efficient CI/CD pipeline. The project involved multiple teams working on front-end, back-end, and database components. Azure DevOps provided:
Version control: Using Azure Repos for centralized code management.
Automated pipelines: Azure Pipelines for building, testing, and deploying code.
Artifact management: Storing dependencies in Azure Artifacts for seamless integration.
The result? Deployment cycles that previously took weeks were reduced to just a few hours, enabling faster time-to-market and improved customer satisfaction.
Key Benefits:
End-to-end integration: Unifies tools for seamless development and deployment.
Scalability: Supports projects of all sizes, from startups to enterprises.
Collaboration: Facilitates team communication with built-in dashboards and tracking.

4. Azure Cosmos DB: Global Data at Scale
Azure Cosmos DB is a globally distributed, multi-model database service designed for mission-critical applications. It guarantees low latency, high availability, and scalability, making it ideal for applications requiring real-time data access across multiple regions.
Real-World Application
In a project for a financial services company, we used Azure Cosmos DB to manage transaction data across multiple continents. The database’s multi-region replication ensure data consistency and availability, even during regional outages. Additionally, Cosmos DB’s support for multiple APIs (SQL, MongoDB, Cassandra, etc.) allowed us to integrate seamlessly with existing systems.
Key Benefits:
Global distribution: Data is replicated across regions with minimal latency.
Flexibility: Supports various data models, including key-value, document, and graph.
SLAs: Offers industry-leading SLAs for availability, throughput, and latency.
Building a Cohesive Solution
Combining these Azure services creates a technology stack that is flexible, scalable, and efficient. Here’s how they work together in a hypothetical solution:
Data Ingestion: IoT devices send data to Azure Event Hubs.
Processing: Azure Functions processes the data in real-time.
Storage: Processed data is stored in Azure Cosmos DB for global access.
Application Logic: Containerized microservices run on AKS, providing APIs for accessing and manipulating data.
Deployment: Azure DevOps manages the CI/CD pipeline, ensuring seamless updates to the application.
This architecture demonstrates how Azure’s technology stack can address modern business challenges while maintaining high performance and reliability.
Final Thoughts
My journey with Azure has been both rewarding and transformative. The training I received at ACTE Institute provided me with a strong foundation to explore Azure’s capabilities and apply them effectively in real-world scenarios. For those new to cloud computing, I recommend starting with a solid training program that offers hands-on experience and practical insights.
As the demand for cloud professionals continues to grow, specializing in Azure’s technology stack can open doors to exciting opportunities. If you’re based in Hyderabad or prefer online learning, consider enrolling in Microsoft Azure training in Hyderabad to kickstart your journey.
Azure’s ecosystem is continuously evolving, offering new tools and features to address emerging challenges. By staying committed to learning and experimenting, we can harness the full potential of this powerful platform and drive innovation in every project we undertake.
#cybersecurity#database#marketingstrategy#digitalmarketing#adtech#artificialintelligence#machinelearning#ai
2 notes
·
View notes
Text
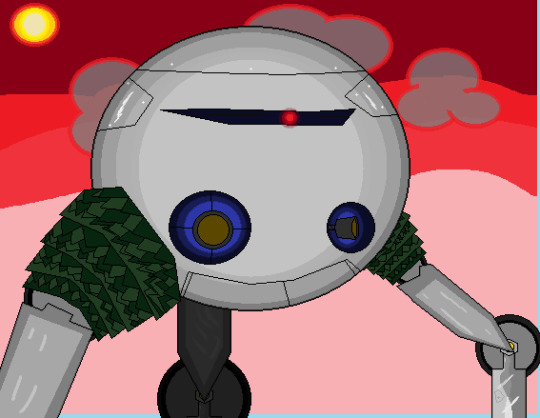
Meet the Titanopod. A late game enemy from Team Sapphire: Titans Unleashed. The Titanopod is based on the Tripods from the 2005 War of The Worlds movie. The player can encounter these roaming mini-bosses in the overworld areas such as: Battlefield area, Withered Oasis and lower regions of Lance. Titanopods are massive 3 legged robots created by Edward Ryno, They're designed to eradicate titans, large populations and to level cities. Equipped with a singular deployment hatch at the bottom to drop their weaker, smaller yet faster counterparts "The Quadpods" as well as various Scout Drones that command and direct them. They have multi-directional twin RynoCorp Particle Incinerators. If they cannot operate automatically, 2 drones from within can always take manual control of the entire mech. However they have a major flaw, their toes and knees are not protected and when their lower hatch opens up, they cannot move. Due to their roles, they do not operate within freezing cold or burning hot environments, meaning Fire and Ice magic can make destroying Titanopods much easier than most other elements.
2 notes
·
View notes
Text
Data Zones Improve Enterprise Trust In Azure OpenAI Service

The trust of businesses in the Azure OpenAI Service was increased by the implementation of Data Zones.
Data security and privacy are critical for businesses in today’s quickly changing digital environment. Microsoft Azure OpenAI Service provides strong enterprise controls that adhere to the strictest security and regulatory requirements, as more and more businesses use AI to spur innovation. Anchored on the core of Azure, Azure OpenAI may be integrated with the technologies in your company to assist make sure you have the proper controls in place. Because of this, clients using Azure OpenAI for their generative AI applications include KPMG, Heineken, Unity, PWC, and more.
With over 60,000 customers using Azure OpenAI to build and scale their businesses, it is thrilled to provide additional features that will further improve data privacy and security capabilities.
Introducing Azure Data Zones for OpenAI
Data residency with control over data processing and storage across its current 28 distinct locations was made possible by Azure OpenAI from Day 0. The United States and the European Union now have Azure OpenAI Data Zones available. Historically, variations in model-region availability have complicated management and slowed growth by requiring users to manage numerous resources and route traffic between them. Customers will have better access to models and higher throughput thanks to this feature, which streamlines the management of generative AI applications by providing the flexibility of regional data processing while preserving data residency within certain geographic bounds.
Azure is used by businesses for data residency and privacy
Azure OpenAI’s data processing and storage options are already strong, and this is strengthened with the addition of the Data Zones capability. Customers using Azure OpenAI can choose between regional, data zone, and global deployment options. Customers are able to increase throughput, access models, and streamline management as a result. Data is kept at rest in the Azure region that you have selected for your resource with all deployment choices.
Global deployments: With access to all new models (including the O1 series) at the lowest cost and highest throughputs, this option is available in more than 25 regions. The global backbone of the Azure resource guarantees optimal response times, and data is stored at rest within the customer-selected
Data Zones: Introducing Data Zones, which offer cross-region load balancing flexibility within the customer-selected geographic boundaries, to clients who require enhanced data processing assurances while gaining access to the newest models. All Azure OpenAI regions in the US are included in the US Data Zone. All Azure OpenAI regions that are situated inside EU member states are included in the European Union Data Zone. The upcoming month will see the availability of the new Azure Data Zones deployment type.
Regional deployments: These guarantee processing and storage take place inside the resource’s geographic boundaries, providing the highest degree of data control. When considering Global and Data Zone deployments, this option provides the least amount of model availability.
Extending generative AI apps securely using your data
Azure OpenAI allows you to extend your solution with your current data storage and search capabilities by integrating with hundreds of Azure and Microsoft services with ease. Azure AI Search and Microsoft Fabric are the two most popular extensions.
For both classic and generative AI applications, Azure AI search offers safe information retrieval at scale across customer-owned content. This keeps Azure’s scale, security, and management while enabling document search and data exploration to feed query results into prompts and ground generative AI applications on your data.
Access to an organization’s whole multi-cloud data estate is made possible by Microsoft Fabric’s unified data lake, OneLake, which is arranged in an easy-to-use manner. Maintaining corporate data governance and compliance controls while streamlining the integration of data to power your generative AI application is made easier by consolidating all company data into a single data lake.
Azure is used by businesses to ensure compliance, safety, and security
Content Security by Default
Prompts and completions are screened by a group of classification models to identify and block hazardous content, and Azure OpenAI is automatically linked with Azure AI Content Safety at no extra cost. The greatest selection of content safety options is offered by Azure, which also has the new prompt shield and groundedness detection features. Clients with more stringent needs can change these parameters, such as harm severity or enabling asynchronous modes to reduce delay.
Entra ID provides secure access using Managed Identity
In order to provide zero-trust access restrictions, stop identity theft, and manage resource access, Microsoft advises protecting your Azure OpenAI resources using the Microsoft Entra ID. Through the application of least-privilege concepts, businesses can guarantee strict security guidelines. Furthermore strengthening security throughout the system, Entra ID does away with the requirement for hard-coded credentials.
Furthermore, Managed Identity accurately controls resource rights through a smooth integration with Azure role-based access control (RBAC).
Customer-managed key encryption for improved data security
By default, the information that Azure OpenAI stores in your subscription is encrypted with a key that is managed by Microsoft. Customers can use their own Customer-Managed Keys to encrypt data saved on Microsoft-managed resources, such as Azure Cosmos DB, Azure AI Search, or your Azure Storage account, using Azure OpenAI, further strengthening the security of your application.
Private networking offers more security
Use Azure virtual networks and Azure Private Link to secure your AI apps by separating them from the public internet. With this configuration, secure connections to on-premises resources via ExpressRoute, VPN tunnels, and peer virtual networks are made possible while ensuring that traffic between services stays inside Microsoft’s backbone network.
The AI Studio’s private networking capability was also released last week, allowing users to utilize its Studio UI’s powerful “add your data” functionality without having to send data over a public network.
Dedication to Adherence
It is dedicated to helping its clients in all regulated areas, such as government, finance, and healthcare, meet their compliance needs. Azure OpenAI satisfies numerous industry certifications and standards, including as FedRAMP, SOC 2, and HIPAA, guaranteeing that businesses in a variety of sectors can rely on their AI solutions to stay compliant and safe.
Businesses rely on Azure’s dependability at the production level
GitHub Copilot, Microsoft 365 Copilot, Microsoft Security Copilot, and many other of the biggest generative AI applications in the world today rely on the Azure OpenAI service. Customers and its own product teams select Azure OpenAI because it provide an industry-best 99.9% reliability SLA on both Provisioned Managed and Paygo Standard services. It is improving that further by introducing a new latency SLA.
Announcing Provisioned-Managed Latency SLAs as New Features
Ensuring that customers may scale up with their product expansion without sacrificing latency is crucial to maintaining the caliber of the customer experience. It already provide the largest scale with the lowest latency with its Provisioned-Managed (PTUM) deployment option. With PTUM, it is happy to introduce explicit latency service level agreements (SLAs) that guarantee performance at scale. In the upcoming month, these SLAs will go into effect. Save this product newsfeed to receive future updates and improvements.
Read more on govindhtech.com
#DataZonesImprove#EnterpriseTrust#OpenAIService#Azure#DataZones#AzureOpenAIService#FedRAMP#Microsoft365Copilot#improveddatasecurity#data#ai#technology#technews#news#AzureOpenAI#AzureAIsearch#Microsoft#AzureCosmosDB#govindhtech
2 notes
·
View notes
Text
Nothing encapsulates my misgivings with Docker as much as this recent story. I wanted to deploy a PyGame-CE game as a static executable, and that means compiling CPython and PyGame statically, and then linking the two together. To compile PyGame statically, I need to statically link it to SDL2, but because of SDL2 special features, the SDL2 code can be replaced with a different version at runtime.
I tried, and failed, to do this. I could compile a certain version of CPython, but some of the dependencies of the latest CPython gave me trouble. I could compile PyGame with a simple makefile, but it was more difficult with meson.
Instead of doing this by hand, I started to write a Dockerfile. It's just too easy to get this wrong otherwise, or at least not get it right in a reproducible fashion. Although everything I was doing was just statically compiled, and it should all have worked with a shell script, it didn't work with a shell script in practice, because cmake, meson, and autotools all leak bits and pieces of my host system into the final product. Some things, like libGL, should never be linked into or distributed with my executable.
I also thought that, if I was already working with static compilation, I could just link PyGame-CE against cosmopolitan libc, and have the SDL2 pieces replaced with a dynamically linked libSDL2 for the target platform.
I ran into some trouble. I asked for help online.
The first answer I got was "You should just use PyInstaller for deployment"
The second answer was "You should use Docker for application deployment. Just start with
FROM python:3.11
and go from there"
The others agreed. I couldn't get through to them.
It's the perfect example of Docker users seeing Docker as the solution for everything, even when I was already using Docker (actually Podman).
I think in the long run, Docker has already caused, and will continue to cause, these problems:
Over-reliance on containerisation is slowly making build processes, dependencies, and deployment more brittle than necessary, because it still works in Docker
Over-reliance on containerisation is making the actual build process outside of a container or even in a container based on a different image more painful, as well as multi-stage build processes when dependencies want to be built in their own containers
Container specifications usually don't even take advantage of a known static build environment, for example by hard-coding a makefile, negating the savings in complexity
5 notes
·
View notes
Text

USAF Should Look At China’s Future Multi-Crew Fighter Model For F-15EX
The F-15EX's currently empty rear cockpit needs to be taken advantage of by adding a new kind of second crewmen, an Air Mission Commanding Officer.
Major Joshua “Soup” Campbell Posted on Jul 25, 2024 11:24 AM EDT Edited By Tyler Rogoway
F-15EX and J16, both two seaters, but one uses the second crewman in a different capacity than the traditional weapon system officer role.
PLA/USAF
Amidst strategic shifts in its force posture, the U.S. Air Force (USAF) faces pivotal decisions on the deployment of its next-generation fighter fleet. With plans to retire aging F-15C/D Eagles and scale back F-15E Strike Eagle operations, the USAF is poised to integrate a limited number of F-15EX Eagle IIs into the fleet. Yet, while the F-15EX boasts advancements as an evolution of the F-15E Strike Eagle family of fighters, current strategies overlook the aircraft’s rear cockpit potential.

The first F-15EX Eagle II delivered to the Oregon Air National Guard’s 142nd Wing, the first operational unit to receive the type, touches down in Portland in June 2024. 142nd Wing/Oregon Air National Guard
Meanwhile, the People’s Liberation Army Air Force (PLAAF) advocates for multi-seat configurations to manage data-rich combat environments effectively. USAF plans, on the other hand, currently exclude utilizing the F-15EX’s rear cockpit, limiting its role to air-to-air missions and possibly limited air-to-ground missions sometime in the future.
In this era of transformative air combat, as the PLAAF pioneers new operational concepts with multi-seat fighters, the USAF stands at a crossroads, balancing legacy strategies with the imperative for adaptive, integrated command and control of unmanned systems and network-centric operations. With the F-15EX, however, the USAF has an opportunity to lead the way regarding future air combat by fully embracing the Eagle II’s two-crew capability.

The Eagle II Opportunity
With the pending divestment of the F-15C/D and reduction of the F-15E inventory, the USAF has committed to purchasing a relatively small number of F-15EXs to replace the F-15C/D in Japan, as well as at three National Guard bases with units tasked with U.S. homeland defense. The Eagle II, however, evolved from the Strike Eagle and subsequent F-15 derivatives, is capable of far more than what the legacy Eagle fleet previously provided to combatant commanders.
Given its modernized sensors, self-protection suite, fiber optics, future integration of an open mission system and digital open architecture backbone, more powerful engines, increased computing capabilities, and the inclusion of a rear fully-missionized cockpit, the F-15EX represents a significant advancement over both the F-15C/D and F-15E. Yet, current operational plans do not involve taking advantage of the rear cockpit, leaving it empty and unused, assigning the F-15EX to perform long-range and medium-range air-to-air only missions with minimal expansions into other missions sets the F-15EX is purpose-built to fulfill.

From left to right, an F-15C, an F-15E, and an F-15EX. USAF
The evolving character of air combat, however, demands that platforms do more amongst the growing complexity of high-end warfare. When considering the future of air combat, which places information at center stage in a high-end conflict, failing to utilize the rear cockpit would be a missed opportunity to expand future roles and responsibilities of the F-15EX, disregarding the investment that already exists in the aircraft’s capabilities.
By contrast, People’s Liberation Army Air Force (PLAAF) assessments of the anticipated complexities of forthcoming high-end combat environments have led them to identify multi-seat, multi-role configurations as critical to operations.
Available information suggests that the PLAAF believes an additional operator offers the potential for more effective interpretation and utilization of the vast sensory data that could overwhelm the cognitive and processing capacities of a single individual, particularly in the future of contested air combat environments. Having made this assessment, the PLAAF is now moving forward in developing operational concepts for how best to employ multiple operators in a single tactical aircraft, like the J-16 and the two-seat J-20S variant (also referred to variously as the J-20B and J-20AS), beyond their traditional roles. The USAF could benefit from adopting a multi-operator approach like the PLAAF’s with the F-15EX.

A picture of a two-seat J-20 during testing. Chinese internet
Information Saturation
Any future high-end conflict will produce vast amounts of data that need processing. Both the U.S. military and PLA continue to develop robust integrated intelligence, surveillance, and reconnaissance (ISR) networks to facilitate combat operations and support long-range kill chains. As such, sensors within the land, sea, air, and space domains will provide more data than can be consumed by human operators to process — and make accurate — real-time tactical and operational decisions. Due to the rapidly changing environments in a future contest, these decisions will need to be made quickly and potentially at the forward edge of the battlespace.
In an anticipated information-saturated environment, the USAF advocates for the integration of artificial intelligence (AI) and machine-to-human collaboration to alleviate the workload and cognitive demands on operators. While the incorporation of AI may process and distill information to provide operators with pertinent data, a saturated, complex combat environment full of adversary ships, aircraft, and coastal defenses employing deception and denial tactics will still likely result in an overwhelming influx of information for operators to process, leading to task saturation. Performing a multitude of missions and tasks — including controlling collaborative combat aircraft (CCA) and managing other aircraft in formation — all the while making air-to-air and air-to-ground engagement decisions within a contested, degraded, and operationally limited (CDO-L) environment will challenge and could exacerbate cognitive processes for both humans and their AI agents. The PLAAF, on the other hand, seems to be intent on leveraging AI integration with more human operators, not less.

Public Domain
Moving Beyond Traditional Roles
A recent article published in January 2024 by Chinese state-owned outlet Ta Kung Pao Online in Hong Kong, titled “J-16 Leads the Air Force Aircraft Fleet in Preparations for Future Air Battles,” sheds light on the evolving role of the J-16 back-seater and its implications for the future role of the J-20S back-seater. The article outlines the traditional division of responsibilities between front-seat and back-seat operators in the J-16. It also underscores how, due to evolving characteristics of air warfare, the role of the backseat operator has evolved as combat has evolved, informing future J-20S operations.

A Chinese J-16. Japan Ministry of Defense A stock picture of a Chinese J-16. Japan Ministry of Defense
According to the article, the J-16 stands out as the primary two-seat fighter in the PLAAF’s combat air force. While the two-seat Su-30 Flanker exists in the PLAAF’s inventory, its fleet is smaller in size, whereas the J-16 contains more advanced avionics and is in continued domestic production exceeding 245 aircraft, leaving the PLAAF to rely heavily on the J-16 and its more advanced capabilities.

A Chinese Su-30MKK Flanker. Dmitriy Pichugin A stock picture of a Chinese Su-30MKK Flanker. Dmitriy Pichugin
Equipped with asymmetric, outsized weapons that don’t fit in the J-20’s weapons bay, the J-16 provides a broad array of operational capabilities, making it a versatile asset in various scenarios. Similar to the F-15E, the J-16 conducts long-range air-to-air engagements and attacks on ground and maritime targets where the back-seater serves as a weapons controller responsible for employing different types of weapons. The PLAAF, however, is beginning to adapt the J-16 to the expected information-dominated combat environment and evolving manned-unmanned teaming by developing new roles and responsibilities for the aircraft and its operators.
Information-Dominated Combat Environment
In the context of the evolving landscape of networked and unmanned warfare, contemporary air combat will incorporate a multitude of systems where all combat elements are interconnected with vast amounts of information. Through data transmission and intelligence-sharing platforms, collaborative operations based on interconnected systems have become the predominant operational model, with the J-16 capable of assuming the central command role for entire formations. According to the Ta Kung Pao article, the J-16 back-seater, in this new environment, evolves from simply a “weapon controller” into an “air mission commanding officer.”
A close-up look at the pilot and the back-seater in a Chinese J-16. China Military Online/Liu Chang and Liu Yinghu
With this new evolution, the air mission commanding officer (AMCO) encompasses multiple roles and responsibilities in a high-tech conflict that includes overseeing air-to-surface weaponry, managing and disseminating multi-platform intelligence, and issuing operational directives. While this may seem similar to the USAF’s airborne Forward Air Controller-Airborne (FAC[A]), there appear to be differences in employment concepts between the PLAAF’s AMCO and the USAF’s FAC(A), particularly regarding the operational environments with which they are utilized.
Primarily employed in close air support (CAS) or strike coordination and reconnaissance (SCAR) missions, the FAC(A) is the airborne version of a joint terminal air controller (JTAC) in which both can nominate and mark targets, deconflict airspace, relay critical ground schemes of maneuver, and authorize airstrikes. The PLAAF’s AMCO, however, seems to focus on roles and responsibilities that leverage the PLA’s sensing network in a contested air interdiction environment.
Utilizing the PLA’s expanding sensing network to build situational awareness in the battlespace, the J-16 back-seater, assuming the AMCO role and plugged into the sensing network, is intended to direct coordinated efforts among various aircraft, in conjunction with ground and naval units, to execute comprehensive aerial attacks. Additionally, the back-seater’s role is to command and coordinate multiple drones acting as ‘loyal wingmen’ with the intent to amplify combat effectiveness through combined manned and unmanned operations.
Whether or not the PLAAF is actually proficient with this type of force package integration in a high-end combat environment remains to be seen. There is a distinct possibility that the PLAAF is overstating its capabilities in such an environment and much of this training is nascent or scripted, or this is the aspirational plan for future operations. However, the article points to recent footage from state-run CCTV that claims to showcase joint exercises involving GJ-2 drones under the command of J-16s enabling swarm attacks. Analysts, however, suggest that the articles and CCTV coverage of these events do not match reality given current PLAAF capabilities and likely reflect a desire for future capability. But while the PLAAF may be unable to conduct the defined roles and responsibilities of the AMCO in the current state, the PLAAF continues to move forward in preparing its endeavors. More importantly, however, the J-16’s implementation of an AMCO also serves as a testbed for future two-seat J-20S operations.
While the J-20S may lack the payload capacity of the J-16, the PLAAF anticipates that “stealth, high-speed, and advanced situational awareness” allow the J-20S to “penetrate enemy territory, gain air superiority,” and subsequently assume command over trailing aircraft like J-16s and J-10Cs. Moreover, the J-20S, like the J-16, will be able to coordinate and control CCAs to compensate for its magazine depth and weapons limitations, a task overseen by the AMCO in the rear cockpit.
Drawing parallels from the expanding roles of J-16 and J-20S back-seaters, incorporating a Weapon System Officer (WSO) into the F-15EX’s rear cockpit would expand its capabilities and enhance the lethality of USAF strike packages. With the advent of large, integrated sensing networks providing a vast amount of data, an F-15EX WSO, assuming a role similar to an AMCO, can coordinate and direct fires, provide mission-critical intelligence in the midst of mission execution to other platforms in a strike package, pass information of evolving situations between pulsed operations, and even coordinate with various naval or ground forces.

As highlighted in this picture, a two-person crew did fly the first F-15EX jet to Portland in June 2024. Oregon National Guard
Additionally, the F-15EX’s weapons array integration, including outsized weapons, allows it to perform an array of missions already being fulfilled by the F-15E, which includes long-range air interdiction. Moreover, it can be deployed to other environments in the event of horizontal escalation or low- to medium-tier conflicts, providing global firepower reach against smaller, maligned nation-states while still providing key capabilities in the high-end fight. Furthermore, the lack of stealth allows the F-15EX the ability to carry highly specialized pods that stealth assets simply can’t, or won’t, carry. Advanced pods can provide many warfighting-enhancing capabilities, from communications to sensing, electronic warfare, network redundancy, and edge computing.

A US Air Force F-15C Eagle carrying an infrared search and track (IRST) pod. This is one of many specialized podded capabilities members of the F-15 family, including the F-15EX, can carry. USAF
Finally, an F-15EX WSO can oversee the employment of groups of Collaborative Combat Aircraft (CCA) or swarms of other drones.
CCAs, AI, and Command and Control
Both the USAF and PLAAF view CCAs as a way of generating cost-effective mass. The intent is to augment attack formations with low-cost, AI-infused robotic wingmen to increase capabilities in the realm of firepower, sensing, electronic warfare, communications, and other capabilities that manned aircraft bring to the fight. Though both air forces promote heavy reliance on AI in CCAs, AI currently lacks intuition and the ability to infer information in a complex CDO-L combat environment that it is not accustomed to and lacks the ability to break from its given prescribed parameters to adapt. It is therefore expected that some level of human-to-machine interaction between manned aircraft and CCAs will be required to make decisions in a combat environment for some time. Due to the anticipated human interaction with CCAs, the PLAAF foresees multi-seat fighter platforms as an operational requirement.
In a document titled “Study on the Combined Manned Aircraft/UAV in Air Operations,” published around 2021 by Wang Danjing and Liu Ying of the Department of Combined Tactics Air Force Command College in Beijing, the discussion of command and control of CCAs described the task intensive nature of managing combat operations and CCAs simultaneously. When deciding the optimal manned-to-unmanned mixed formation characteristics, task management and cognitive performance were at the forefront of the author’s conclusion that the ideal formation to employ CCAs consists of pairing a two-seat aircraft with a single-seat aircraft.
Wang and Liu note that “U.S. scientists show that there is a nonlinear relationship between a person’s workload and work performance,” suggesting that adding management of CCAs to a pilot’s tasks could impact performance. The authors conclude that “the manned aircraft formation scope is better as a two-aircraft formation, with one being a two-seat aircraft tasked with tactical control of the UAVs, while the other is a single-seat aircraft tasked with executing the task of standing guard and attacking.”
While USAF tactics will almost definitely differ from the PLAAF’s regarding CCAs, utilizing an extra body in the backseat of the F-15EX can enhance the employment of CCAs, allowing the front-seat pilot to focus on other tasks or coordinate various functions in a combat setting.
Moreover, it is expected that CCAs will not always launch with their manned platforms to conduct missions in an Agile Combat Employment (ACE) scheme of maneuver or disparate basing environment like in the Pacific. Positioned between forward assets and bases, an F-15EX could take command of CCAs and transfer to forward fighter platforms or launch or recovery locations.
Take Aways
Although the U.S. military typically does not examine adversary strategy, operations, and tactics with the intention of replicating them, it is crucial to recognize the strengths of developing adversary capabilities and evaluate how they align with U.S. military operational principles.
Given the information provided above, it is imperative for the USAF to recognize and address the limitations of human cognition in future information-intensive environments and consider deploying additional operators to process the vast data available and manage new cognitive demands and new responsibilities like CCAs in a high-tech warzone. The PLAAF’s ambitious approach to utilizing its two-seat J-16 and J-20S platforms in complex, high-end combat environments may provide insights into how to maximize the F-15EX’s enhanced capabilities by incorporating a back-seater.
Similar to how the PLAAF intends to use the J-16 to cooperate with other fighter platforms, C2ISR platforms, and its kill-web to employ its outsized weapons, the F-15EX provides the range, payload, and sensors to do the same for the USAF. Additionally, with its fully missionized rear cockpit and large-area display, the F-15EX is capable of doing everything the multi-seat F-15E can do, and more.
The F-15EX’s fully missionized rear cockpit allows a WSO to conduct a multitude of mission-related functions, freeing the pilot to focus on other tasks at hand. Incorporating a WSO in the F-15EX would thus harness the intended capabilities the F-15EX is designed for. With no one in the rear cockpit, however, the F-15EX’s potential expansion of roles and responsibilities and overall effectiveness cannot be realized, leaving the Air Force unable to capitalize on the investment that is already paid for with each aircraft rolling off the line.
With every new set of roles, responsibilities, and mission expansion, however, comes new training requirements. For the F-15EX to adopt similar roles and responsibilities of the AMCO, the F-15E training pipeline can leverage existing training plans either by restructuring F-15E training flights that develop these specific tasks or by creating a new AMCO training pipeline in concert with the F-15EX syllabus being constructed to prepare future Eagle II pilots. Taking qualified F-15E WSO instructors into an AMCO pipeline that runs in concert with the F-15EX syllabus, the Air Force can fully realize a cohesive multi-seat aircraft ready for the high-end environment.
Unfortunately, however, the USAF has chosen to focus the utilization of the F-15EX on a single mission: long-range air-to-air. While capable of conducting close air support (CAS), combat search and rescue (CSAR), long- and medium-range air interdiction, maritime air interdiction, defensive counter-air, suppression of enemy air defenses (SEAD), and more, leaving the rear cockpit empty in this high-tech piece of machinery and conducting only long-range air-to-air engagements leaves all this potential capability on the table.
USAF
Equipped with outsized, long-range weapons and specialized pods, and the ability to command CCAs and swarms of other drones while directing combat fires and disseminating multi-platform intelligence from a multi-crew platform, the F-15EX offers a broader spectrum of capabilities beyond solely engaging in long-range air-to-air combat. Additionally, much of the necessary technology for these functions is already integrated into the aircraft.
For these reasons, it is imperative that the Air Force not let preconceived notions of traditional roles and responsibilities obstruct decision-making concerning the future of air warfare and the potential evolution of roles and responsibilities.
The character of warfare is evolving, necessitating the utilization of both machinery and personnel in innovative ways that align with the changing environment. The multi-operator platform direction currently pursued by the PLAAF yields operational insights worthy of consideration by USAF planners for the near- and mid-term, even as the USAF continues to develop advanced AI solutions for the long term.
Major Joshua “Soup” Campbell is an F-15E Weapon System Officer (WSO) and graduate of the distinguished USAF Weapon School with 1,500 hours in the F-15E which includes 630 combat hours. He spent the last year as a Fellow at the USAF’s China Aerospace Studies Institute with a strategic and operational focus. He is currently attending Johns Hopkins University, School of Advanced International Studies through the Department of Defense’s Strategic Thinker’s Program. He has worked in a variety of capacities at both the squadron level and MAJCOM staff positions.
9 notes
·
View notes
Link
The search for extrasolar planets is currently undergoing a seismic shift. With the deployment of the Kepler Space Telescope and the Transiting Exoplanet Survey Satellite (TESS), scientists discovered thousands of exoplanets, most of which were detected and confirmed using indirect methods. But in more recent years, and with the launch of the James Webb Space Telescope (JWST), the field has been transitioning toward one of characterization. In this process, scientists rely on emission spectra from exoplanet atmospheres to search for the chemical signatures we associate with life (biosignatures). However, there’s some controversy regarding the kinds of signatures scientists should look for. Essentially, astrobiology uses life on Earth as a template when searching for indications of extraterrestrial life, much like how exoplanet hunters use Earth as a standard for measuring “habitability.” But as many scientists have pointed out, life on Earth and its natural environment have evolved considerably over time. In a recent paper, an international team demonstrated how astrobiologists could look for life on TRAPPIST-1e based on what existed on Earth billions of years ago. The team consisted of astronomers and astrobiologists from the Global Systems Institute, and the Departments of Physics and Astronomy, Mathematics and Statistics, and Natural Sciences at the University of Exeter. They were joined by researchers from the School of Earth and Ocean Sciences at the University of Victoria and the Natural History Museum in London. The paper that describes their findings, “Biosignatures from pre-oxygen photosynthesizing life on TRAPPIST-1e,” will be published in the Monthly Notices of the Royal Astronomical Society (MNRAS). The TRAPPIST-1 system has been the focal point of attention ever since astronomers confirmed the presence of three exoplanets in 2016, which grew to seven by the following year. As one of many systems with a low-mass, cooler M-type (red dwarf) parent star, there are unresolved questions about whether any of its planets could be habitable. Much of this concerns the variable and unstable nature of red dwarfs, which are prone to flare activity and may not produce enough of the necessary photons to power photosynthesis. With so many rocky planets found orbiting red dwarf suns, including the nearest exoplanet to our Solar System (Proxima b), many astronomers feel these systems would be the ideal place to look for extraterrestrial life. At the same time, they’ve also emphasized that these planets would need to have thick atmospheres, intrinsic magnetic fields, sufficient heat transfer mechanisms, or all of the above. Determining if exoplanets have these prerequisites for life is something that the JWST and other next-generation telescopes – like the ESO’s proposed Extremely Large Telescope (ELT) – are expected to enable. But even with these and other next-generation instruments, there is still the question of what biosignatures we should look for. As noted, our planet, its atmosphere, and all life as we know it have evolved considerably over the past four billion years. During the Archean Eon (ca. 4 to 2.5 billion years ago), Earth’s atmosphere was predominantly composed of carbon dioxide, methane, and volcanic gases, and little more than anaerobic microorganisms existed. Only within the last 1.62 billion years did the first multi-celled life appear and evolve to its present complexity. Moreover, the number of evolutionary steps (and their potential difficulty) required to get to higher levels of complexity means that many planets may never develop complex life. This is consistent with the Great Filter Hypothesis, which states that while life may be common in the Universe, advanced life may not. As a result, simple microbial biospheres similar to those that existed during the Archean could be the most common. The key, then, is to conduct searches that would isolate biosignatures consistent with primitive life and the conditions that were common to Earth billions of years ago. This artistic conception illustrates large asteroids penetrating Earth’s oxygen-poor atmosphere. Credit: SwRI/Dan Durda/Simone Marchi As Dr. Jake Eager-Nash, a postdoctoral research fellow at the University of Victoria and the lead author of the study, explained to Universe Today via email: “I think the Earth’s history provides many examples of what inhabited exoplanets may look like, and it’s important to understand biosignatures in the context of Earth’s history as we have no other examples of what life on other planets would look like. During the Archean, when life is believed to have first emerged, there was a period of up to around a billion years before oxygen-producing photosynthesis evolved and became the dominant primary producer, oxygen concentrations were really low. So if inhabited planets follow a similar trajectory to Earth, they could spend a long time in a period like this without biosignatures of oxygen and ozone, so it’s important to understand what Archean-like biosignatures look like.” For their study, the team crafted a model that considered Archean-like conditions and how the presence of early life forms would consume some elements while adding others. This yielded a model in which simple bacteria living in oceans consume molecules like hydrogen (H) or carbon monoxide (CO), creating carbohydrates as an energy source and methane (CH4) as waste. They then considered how gases would be exchanged between the ocean and atmosphere, leading to lower concentrations of H and CO and greater concentrations of CH4. Said Eager-Nash: “Archean-like biosignatures are thought to require the presence of methane, carbon dioxide, and water vapor would be required as well as the absence of carbon monoxide. This is because water vapor gives you an indication there is water, while an atmosphere with both methane and carbon monoxide indicates the atmosphere is in disequilibrium, which means that both of these species shouldn’t exist together in the atmosphere as atmospheric chemistry would convert all of the one into the other, unless there is something, like life that maintains this disequilibrium. The absence of carbon monoxide is important as it is thought that life would quickly evolve a way to consume this energy source.” Artist’s impression of Earth in the early Archean with a purplish hydrosphere and coastal regions. Even in this early period, life flourished and was gaining complexity. Credit: Oleg Kuznetsov When the concentration of gases is higher in the atmosphere, the gas will dissolve into the ocean, replenishing the hydrogen and carbon monoxide consumed by the simple life forms. As biologically produced methane levels increase in the ocean, it will be released into the atmosphere, where additional chemistry occurs, and different gases are transported around the planet. From this, the team obtained an overall composition of the atmosphere to predict which biosignatures could be detected. “What we find is that carbon monoxide is likely to be present in the atmosphere of an Archean-like planet orbiting an M-Dwarf,” said Eager-Nash. “This is because the host star drives chemistry that leads to higher concentrations of carbon monoxide compared to a planet orbiting the Sun, even when you have life-consuming this [compound].” For years, scientists have considered how a circumsolar habitable zone (CHZ) could be extended to include Earth-like conditions from previous geological periods. Similarly, astrobiologists have been working to cast a wider net on the types of biosignatures associated with more ancient life forms (such as retinal-photosynthetic organisms). In this latest study, Eager-Nash and his colleagues have established a series of biosignatures (water, carbon monoxide, and methane) that could lead to the discovery of life on Archean-era rocky planets orbiting Sun-like and red dwarf suns. Further Reading: arXiv The post Will We Know if TRAPPIST-1e has Life? appeared first on Universe Today.
4 notes
·
View notes
Text
United States Agrivoltaics : Rise Of Agrivoltaics In The American Farming

As climate change threatens global food supplies, agrivoltaic systems are gaining popularity in the United States as a way for farmers to boost solar energy production while continuing to harvest crops beneath solar panels. Also known as "agrophotovoltaics", agrivoltaic installations combine agriculture and solar power generation on the same land. By installing solar panels elevated high enough to allow farm equipment and livestock access to the ground below, farmers can generate solar power and grow crops or graze livestock simultaneously on the same parcel of land.
Benefits For Farmers And Food Security
Agrivoltaic systems provide multiple benefits for farmers and the environment. In addition to generating a steady additional revenue stream from solar electricity sales, studies have found that certain crops grown beneath solar panels have higher yields compared to directly exposed to sunlight. United States Agrivoltaics The partial shading from solar panels protects some crops from excessive heat and regulates soil moisture, improving overall productivity. For livestock grazing, the shade from panels protects animals from heat stress which has been shown to increase their health, growth rates and milk production. These dual-use installations are helping increase overall land productivity at a time when climate pressures are exacerbating food security risks.
Potential For Expanded Deployment
Currently, there are a few agrivoltaic pilot projects operating across the United States but their adoption remains limited compared to conventional ground-mounted solar farms. However, as the agricultural benefits become clearer and technology improves to maximize both energy and food outputs, experts expect agrivoltaics to play a much larger role in the country's clean energy transition. Some estimates suggest agrivoltaic systems could potentially generate hundreds of gigawatts of solar power on available farmland if deployed at sufficient scale. States with vast agricultural areas like California, the Midwest and Plains regions are well positioned to lead the way.
Project Developers Tout Multiple Cropping Options
Early agrivoltaic projects in the United States Agrivoltaics have tested growing a variety of crops beneath solar panels including grapes, olives, berries and vegetables. Developers say that with proper panel elevation and optimization of lighting conditions, row crops like lettuce, onions and carrots can also thrive. Livestock operations are integrating panels for grazing dairy cattle and lamb. Ongoing research is exploring additional dual-use combinations suited for different soil types and microclimates across farming regions. Producers are also experimenting with staggered panel installation to allow continued mechanical harvesting of commodity row crops like corn and alfalfa. As more multi-year yield data becomes available, farmers' confidence in agrivoltaics is increasing.
Tailoring Technology To Farming Needs
A challenge for wider deployment remains ensuring agrivoltaic systems are economically viable propositions for farmers and easy to incorporate into their existing operations. US developers are working to refine mounting configurations, panel elevations and integrated smart technologies to maximize both solar energy generation and agricultural outputs specific to local growing conditions and crop varieties. There is also ongoing innovation related to access for machinery and irrigation systems beneath panels. Additional research partnerships involving farmers, land grant universities and the national labs are vital to further adapt agrivoltaic technologies and successfully demonstrate scalable business models tailored for different commodity crop types.
Overcoming Permitting And Policy Hurdles
In addition to technology challenges, policy and permitting issues have slowed the scaling of agrivoltaic projects. Some state and local regulations do not yet account for dual-use of farmland and view agrivoltaics as competing land uses rather than complementary. Renewable energy incentives also often only apply to standalone solar farms versus agrivoltaic systems. advocates are working with policymakers to establish legal recognition and support for agrivoltaics through measures like revised zoning definitions, streamlined permitting procedures and tailored financial incentive programs. Widespread adoption will require acknowledgement from governing bodies that these installations can provide compatible and sustainable multi-functional land use.
Outlook
As concerns intensify about long-term global food security in the face of interconnected economic, environmental and geopolitical pressures, United States Agrivoltaics are gaining recognition as a means to boost domestic farming resiliency. By sustainably increasing total land productivity, these dual-use systems could make a meaningful contribution to both energy and agriculture production if scaling challenges are addressed. With ongoing technological enhancements, successful demonstration projects, revised policies and expanding cooperative efforts, the outlook is positive for agrivoltaics to emerge as an important complement to America's clean energy transition and agricultural landscape in the coming decade.
Get more insights on this topic: https://www.ukwebwire.com/united-states-agrivoltaics-emerging-clean-energy-technology-for-farmers/
Author Bio
Vaagisha brings over three years of expertise as a content editor in the market research domain. Originally a creative writer, she discovered her passion for editing, combining her flair for writing with a meticulous eye for detail. Her ability to craft and refine compelling content makes her an invaluable asset in delivering polished and engaging write-ups. (LinkedIn: https://www.linkedin.com/in/vaagisha-singh-8080b91)
*Note: 1. Source: Coherent Market Insights, Public sources, Desk research 2. We have leveraged AI tools to mine information and compile it
1 note
·
View note
Text
Going Over the Cloud: An Investigation into the Architecture of Cloud Solutions

Because the cloud offers unprecedented levels of size, flexibility, and accessibility, it has fundamentally altered the way we approach technology in the present digital era. As more and more businesses shift their infrastructure to the cloud, it is imperative that they understand the architecture of cloud solutions. Join me as we examine the core concepts, industry best practices, and transformative impacts on modern enterprises.
The Basics of Cloud Solution Architecture A well-designed architecture that balances dependability, performance, and cost-effectiveness is the foundation of any successful cloud deployment. Cloud solutions' architecture is made up of many different components, including networking, computing, storage, security, and scalability. By creating solutions that are tailored to the requirements of each workload, organizations can optimize return on investment and fully utilize the cloud.
Flexibility and Resilience in Design The flexibility of cloud computing to grow resources on-demand to meet varying workloads and guarantee flawless performance is one of its distinguishing characteristics. Cloud solution architecture create resilient systems that can endure failures and sustain uptime by utilizing fault-tolerant design principles, load balancing, and auto-scaling. Workloads can be distributed over several availability zones and regions to help enterprises increase fault tolerance and lessen the effect of outages.
Protection of Data in the Cloud and Security by Design
As data thefts become more common, security becomes a top priority in cloud solution architecture. Architects include identity management, access controls, encryption, and monitoring into their designs using a multi-layered security strategy. By adhering to industry standards and best practices, such as the shared responsibility model and compliance frameworks, organizations may safeguard confidential information and guarantee regulatory compliance in the cloud.
Using Professional Services to Increase Productivity Cloud service providers offer a variety of managed services that streamline operations and reduce the stress of maintaining infrastructure. These services allow firms to focus on innovation instead of infrastructure maintenance. They include server less computing, machine learning, databases, and analytics. With cloud-native applications, architects may reduce costs, increase time-to-market, and optimize performance by selecting the right mix of managed services.
Cost control and ongoing optimization Cost optimization is essential since inefficient resource use can quickly drive up costs. Architects monitor resource utilization, analyze cost trends, and identify opportunities for optimization with the aid of tools and techniques. Businesses can cut waste and maximize their cloud computing expenses by using spot instances, reserved instances, and cost allocation tags.
Acknowledging Automation and DevOps Important elements of cloud solution design include automation and DevOps concepts, which enable companies to develop software more rapidly, reliably, and efficiently. Architects create pipelines for continuous integration, delivery, and deployment, which expedites the software development process and allows for rapid iterations. By provisioning and managing infrastructure programmatically with Infrastructure as Code (IaC) and Configuration Management systems, teams may minimize human labor and guarantee consistency across environments.
Multiple-cloud and hybrid strategies In an increasingly interconnected world, many firms employ hybrid and multi-cloud strategies to leverage the benefits of many cloud providers in addition to on-premises infrastructure. Cloud solution architects have to design systems that seamlessly integrate several environments while ensuring interoperability, data consistency, and regulatory compliance. By implementing hybrid connection options like VPNs, Direct Connect, or Express Route, organizations may develop hybrid cloud deployments that include the best aspects of both public and on-premises data centers. Analytics and Data Management Modern organizations depend on data because it fosters innovation and informed decision-making. Thanks to the advanced data management and analytics solutions developed by cloud solution architects, organizations can effortlessly gather, store, process, and analyze large volumes of data. By leveraging cloud-native data services like data warehouses, data lakes, and real-time analytics platforms, organizations may gain a competitive advantage in their respective industries and extract valuable insights. Architects implement data governance frameworks and privacy-enhancing technologies to ensure adherence to data protection rules and safeguard sensitive information.
Computing Without a Server Server less computing, a significant shift in cloud architecture, frees organizations to focus on creating applications rather than maintaining infrastructure or managing servers. Cloud solution architects develop server less programs using event-driven architectures and Function-as-a-Service (FaaS) platforms such as AWS Lambda, Azure Functions, or Google Cloud Functions. By abstracting away the underlying infrastructure, server less architectures offer unparalleled scalability, cost-efficiency, and agility, empowering companies to innovate swiftly and change course without incurring additional costs.
Conclusion As we come to the close of our investigation into cloud solution architecture, it is evident that the cloud is more than just a platform for technology; it is a force for innovation and transformation. By embracing the ideas of scalability, resilience, and security, and efficiency, organizations can take advantage of new opportunities, drive business expansion, and preserve their competitive edge in today's rapidly evolving digital market. Thus, to ensure success, remember to leverage cloud solution architecture when developing a new cloud-native application or initiating a cloud migration.
1 note
·
View note
Text
Platform as a Service (PaaS)

Platform as a Service (PaaS) is a cloud computing service model that provides a platform allowing customers to develop, run, and manage applications without the complexity of building and maintaining the underlying infrastructure. PaaS provides a comprehensive environment that includes development tools, middleware, and runtime services to streamline the application development and deployment process. Here are key features and aspects of PaaS:
Key Features of PaaS:
Development Tools:
PaaS offers a set of tools and services for application development, including integrated development environments (IDEs), version control, and testing frameworks.
Middleware:
PaaS includes middleware services that facilitate communication and integration between different components of an application. This can include databases, messaging systems, and more.
Runtime Services:
PaaS provides runtime services such as operating systems, web servers, and runtime environments. Developers can focus on writing code without worrying about the underlying infrastructure.
Scalability:
PaaS platforms typically offer automatic scaling to handle changes in application demand. This ensures that resources are allocated efficiently, and the application can handle varying workloads.
Multi-Tenancy:
PaaS platforms often support multi-tenancy, allowing multiple users or organizations to share the same infrastructure and resources while maintaining isolation.
Integration with Services:
PaaS allows integration with various external services, such as databases, messaging systems, authentication services, and more, to enhance the functionality of applications.
Deployment and Management:
PaaS simplifies the deployment process, offering tools for application deployment, version control, and monitoring. It often includes management tools for application lifecycle management.
Advantages of PaaS:
Faster Development:
PaaS accelerates the development process by providing pre-built tools and services, reducing the need for developers to manage infrastructure details.
Cost Efficiency:
Developers can focus on coding, while the PaaS provider handles infrastructure maintenance and management, leading to cost savings.
Scalability and Flexibility:
PaaS platforms enable easy scaling of applications based on demand, providing flexibility to handle varying workloads.
Reduced Complexity:
Developers don't need to worry about managing the underlying infrastructure, operating systems, or runtime environments, reducing complexity and allowing them to focus on writing code.
Collaboration:
PaaS facilitates collaboration among development teams, as they can work on the same platform and easily share resources.
Automatic Updates:
PaaS providers handle updates and patches for underlying software, ensuring that the platform is up-to-date and secure.
Resource Optimization:
PaaS platforms optimize resource usage, allocating resources based on application requirements to avoid overprovisioning.
Rapid Prototyping:
Developers can quickly prototype and experiment with ideas without the need to set up and configure infrastructure.
Cloud computing training course in Pune
3 notes
·
View notes