#once again 1:0 for linux
Explore tagged Tumblr posts
Text
now testing if maybe windows-on-windows is causing problems with the game

#pink flashing diaries#fun fact 64bit windows cannot natively run 32bit applications#but linux CAN#once again 1:0 for linux
14 notes
·
View notes
Text
Daily linux infodump (1 of 2, cause I forgot again yesterday, memory mappings.)
Memory Mappings
the mmap() system call creates a new memory mapping in the calling process's virtual memory address space. Mappings fall into two distinct categories: -A file mapping maps a region of a file into the calling process's virtual memory, once mapped, the file's contents canb be accessed by operations on the bytes in the corresponding memory region. The pages of the mapping are automatically loaded from the file as required. -Anonymous mapping doesn't have a corresponding file. Instead the pages of the mapping are initialized to 0
The memory in one process's mapping may be shared with mapping in other processes. This can occur either because two processes map the same region of a file or because a child process created by fork() inherits mapping from it's parent. when two or more processes share the same pages, each processmay see the changes made to the pages by other processes to the contents of the pages, depending on whether the mapping is created as private or shared. When a mapping is provate, modifications to the contents of the mapping is not visible to other processes, and are not carried through to the underlying file. When a mapping is shared, modifications made are visible to other processes sharing the same mapping and are carried through to the underlying file. Memory mappings serve a variety of purposes, including initialization of a process's text segment from the corresponding segment of an executable file, allocation of a new(zero-filled) memory, file I/O, and interprocess communication. Static VS. Shared libraries
An object library is a file containing the compiled object code for a set of functions that maybe be called from application programs.Placing code for a set of functions in a single object library eases the task of program creation and maintenance. modern UNIX systems provide two types of object libraries. static and shared libraries.
7 notes
·
View notes
Text
TOOL TUTORIAL 2
Gifski
GIF GENERATION AND OPTIMIZATION
Tool Type: GUI or Command line tool (there are two versions)
Difficulty: Easy (GUI); Moderate (CLI)
Operating systems: Mac, Windows, and Linux (CLI only—no GUI)
Input(s): Video files (MP4)




How much of a difference can you tell between these two gifs?
Both seem to give good results, but to me, in the top row, the one on the left looks better, but in the bottom, row, the one on the right looks better.
Gifs in the left hand column are converted and compressed to 500 px using the ffmpeg command from Tutorial 1; in the right column, using Gifski.
Gifski GUI Version (Mac and Windows)
NOTE: Gifski is solely for converting MP4 clips to optimized gifs. If you need to caption or color, you have to do that externally.
Installation
The GUI version of Gifski is available in the Apple App store, but links to it and the Windows downloader can be found through the official site.
Using the GUI
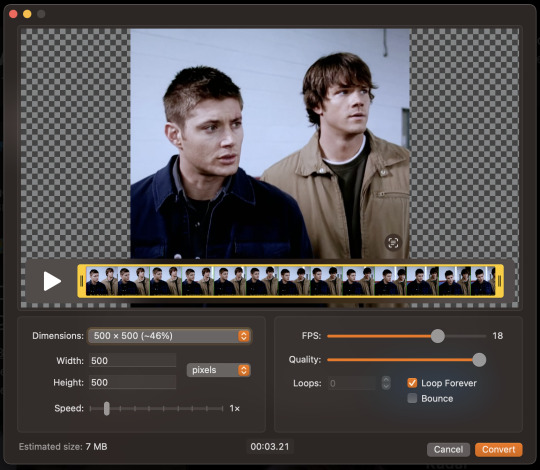
After opening your MP4 file, in the bottom left corner, you can see the estimated size of your resulting gif. This estimate will auto-update as you adjust your compression settings. Remember: To upload your gif on Tumblr, it needs to be about 10MB or less. If it's already 10MB, just go ahead and click convert! If not (which is more than likely):
Adjust FPS to 18. I find this frame rate to be a good balance of compression and retained quality.
Decrease the dimensions of your gif as needed. Whether you use the drop down box or the dialogue boxes, Gifski will automatically scale to retain your gif's screen ratio rather than stretch it to fit, so you don't need to worry about keeping your gif proportional.
You can finely adjust the settings until your gif is exactly 10 MB if you want to keep the best quality, or just aim for a ballpark.
Cick "Covert" then save the resulting gif. Do this for all your .mp4 clips and then boom. You're done.
Gifski Command Line Version (Linux, Mac, Windows)
There is a command line version of Gifski just like there's a command line version of ffmpeg. While the GUI version isn't available for Linux, the command line version is also available for Linux.
Installation
This must be installed separately from the GUI version, via your system shell (Powershell on Windows, Terminal on MacOS). I recommend you install via Homebrew if you're on Mac or Linux by pasting this into your terminal (if/once Homebrew is installed):
brew install gifski
Windows users or other users who don't want Homebrew can follow directions on the Gifski website.
Converting one video file to GIF
This simple command will convert one .mp4 file to .gif (parts in red can be adjusted, parts in blue should be changed):
cd FilePathToYourMP4 gifski --fps 18 --width 500 --quality 100 -o output.gif input.mp4
Where input.mp4 is the name of the MP4 clip you want to make into an optimized gif and output.gif is the desired name of your gif on output.
How to adjust the options in the script:
Change the number frames per second (fps). Go to fps=18 and change “18” up or down.
Scale the gif up or down. Go to width 500 and change “500” up or down to scale the gif up and down by its pixel width.
Change the quality. Go to quality 100 and change “100” to any value between 0 and 100, where 100 is the highest quality.
Converting a folder of video files to GIF
Place all of your video clips into a folder called gifset1. Put an empty subfolder inside the gifset1 folder called gifs. Go to your system shell and copy and paste the following indented text:
Linux and Mac:
cd ~/Desktop/gifset1 for i in .mp4; do gifski --fps 18 --width 500 --quality 100 -o gifs/${i%.}.gif "$i"; done
Windows:
cd ~\Desktop\gifset1 for i in .mp4; do gifski --fps 18 --width 500 --quality 100 -o gifs\${i%.}.gif "$i"; done
Once the process is finished running (your shell prompt will reappear allowing you to type in commands again) if you go to to the gifs subfolder in your gifset1 folder, you will find an optimized gif of every video file has been rendered.
2 notes
·
View notes
Text
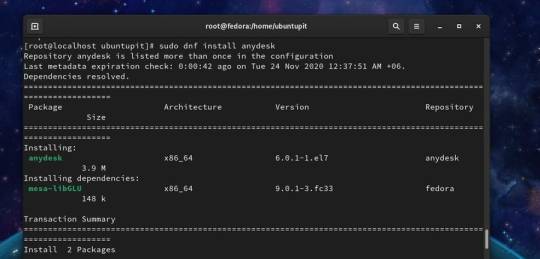
Anydesk Command

Removal guide for software 'anydesk.exe' on Windows (XP, Vista, Win7, Win8 and Windows 10) systems. Tips for getting it away from the hard disk
Anydesk Command Line Install
Anydesk Command Line
Anydesk Command Line Options
Remove Anydesk from Ubuntu. Run the following command to remove/uninstall anydesk from Ubuntu: $ sudo apt-get remove anydesk Conclusion. This marks the end of the article. AnyDesk comes in handy for fast remote desktop connections. It's secure, lean, and elegant in appearance. Your feedback is most welcome. Anydesk is remote desktop software, it's easy to use and I love this program for remote desktop connection. However, uninstalling this program is not so easy. Anydesk is remote desktop software, it's easy to use and I love this program for remote desktop connection. However, uninstalling this program is not so easy.
How to permanently delete anydesk.exe from your computer: First, please read this important warning: This article shows a general guide how to remove any file from your computer. It DOES NOT implies that anydesk.exe is harmful! Be aware of removing executable files from your computer without deeper knowledge of what you're doing. First of all, because of anydesk.exe is an executable, there is always a possibility that removing this file MAY damage the operating system or even your data. Are you still ready to remove anydesk.exe? OK, let's go for it. Here is the guide:
Create Restore point for Windows (not available in Windows XP). Restore point will help you to revert changes, if something'll go wrong.
Press F3 key to open standard search window. Than type 'anydesk.exe' into search box. In couple of minutes, seconds if you're lucky, Windows will find all the copies.
Try to locate program, to which the process anydesk.exe belongs. Than try to uninstall that program in a standard way. For example, if anydesk.exe is found in folder C:Program FilesDummy game**some subfolder**, it most probably belongs to 'Dummy game' software package.
If your problem persist and you are not able to remove file that way, go to the search results (step 2) and try to manually delete all the occurrences of anydesk.exe. Note: If the process is running, you will not be able to delete the file. In such situation, you must stop the process via Task manager (right click on Windows task bar, select 'Task manager'. In Task Manager windows, click 'Processes' pane. Than select anydesk.exe and press 'Delete' key). Detailed guide.
Some malware can hide itself under different names (so-called 'clones'). To remove such self-hiding program, use specialized tool 'EasyRemove' - see below
TIP: Save your time and remove all occurences of anydesk.exe from your computer, including clones and hidden copies with EasyRemove. EasyRemove is lightweight and easy-to-use removal tool for anydesk.exe Download EasyRemove and get your computer fixed within minutes.
You can be also interested in: checking if anydesk.exe is virus or not , how to solve typical problems with anydesk.exe error (or more specific anydesk.exe application error) Solve problems with anydesk.exe not responding. Ps4 remote play compatible controllers. Typical Windows message: anydesk.exe high cpu. How to handle damaged file: anydesk.exe is corrupted.
Main article: anydesk.exe
You know it: the longer you own your computer, the slower it runs and the more often it stucks. EUROBYTE TOOLS speeds up more than 1 million computers around the world. Try it now:
Security risk rating: N/A
Note: The security risk rating is based on user's opinions. This is not our recommendation or adwice any way. Please use your own mind and think twice :-) Trojan and malware info: N/A Typical errors: File not found, An error occured in file, Not responding, Application Error 0x , Howto delete, stop, run, remove and find the file.. Notes: - N/A is an abbreviation for 'Not available'. That means that now we have no information if this process is harmful or not. - There is almost unlimited numbers of messages that should appear while you're running the software. We selected only the typical ones here
Related posts for anydesk.exe
See Related Forum Messages: Follow the Links Below to View Complete Thread
Summary: 0 user rated this process.
Nameparts: an ydesk, any desk, anyd esk, anyde sk, .
User reviews snapshot:
(22:24:06) kms-qad.exe: malware analiz.. (00:22:19) sandisksecureaccessv2_win.exe: how to restore the flasdisk sa.. (20:58:22) dx8vb.dll: the risk is virus .. (14:18:21) nvspcaps.exe: NVIDIA Server Capture is neces.. (20:01:40) pcacli.dll: If you have a game or anything.. (22:42:35) half_life_2_lost_coast_gdf.dll: halmacpi.dll.. (06:33:34) nvgftraypluginr.dll: NvGFT Plugin.dll .. (20:21:06) ivms-4200.exe: Process required for IVMS CCTV.. (19:16:19) pclink.exe: Wireless Printing software for.. (00:18:37) mcnetwork.dll: amze.. Warning: Once again about user reviews. Our users can freely add their reviews about whatever process they want. We, of course, purify and filter raged words. However, do not trust everything. We have no time to review any user's sentence. So the information provided in user reviews CAN be innacurate. Or misprinted. Or anything else. Are you adult, aren't you? We believe in your mind.
Windows process DB: hkcmd.exemsmpeng.exeekrn.exewuauclt.exesfloppy.systaskmgr.exealg.exepnkbstra.exemom.exeaawservice.exesrvany.exew3wp.exesmss.exeping.exejucheck.exeteatimer.exeielowutil.exesplwow64.exesptd.syscfp.exem1000mnt.exenetstumbler.exesonnreg.exe3deepctl.exesysvmtrs.exepconpoint.exebsplayer.exeitatray.exesysservdll32.exeudial.exe
New: Windows dynamic link library DB: core_rl_tiff_.dll, ver. , core_rl_ttf_.dll, ver. , core_rl_xlib_.dll, ver. , core_rl_zlib_.dll, core_video.dll, corperfmonext.dll, corpol.dll, corpol.dll, corteai.dll, cortjava.dll, cortona_control.dll, cortona_dxs.dll, cortona_imagers.dll, cortona_js2.dll, cortona_native.dll, dllhost etc..
Available version list table, select the version you have on your PC:
SecurityMD5 or checksumVersionLocationSize
Retypes: wxe, rxe, eze, ece, exw, exr, eexe, exxe, exee, snydesk, abydesk, amydesk, antdesk, anudesk, anysesk, anyfesk, anydwsk, anydrsk, anydeak, anydedk, anydesj, anydesl, aanydesk, annydesk, anyydesk, anyddesk, anydeesk, anydessk, anydeskk, nydesk, aydesk, andesk, anyesk, anydsk, anydek, anydes, anidesk, anydezk, anytesk,
Disclaimer This web site and all information written here is for information purposes only, WITHOUT ANY VARANTY. YOU ARE USING THIS PAGES ON YOU OWN RISK. You should always verify the accuracy of information provided on this page. We pay a big attention to provide you with the correct information. However, many spyware and malware programs use filenames of usual, non-malware processes and DLLs. If we have included information about anydesk.exe that is inaccurate, we would appreciate your help by getting us know about your user review. Also, web links to software and DLL vendors are provided just for your conform, and we cannot guarantee its accuracy nor relevance with DLL or process listed on this page. We are not affiliated with this pages. We are not responsible for misprints on this site or changes occured since this page was published. The product, software and operating system names mentioned on this web site, can be copyrighted and registered trademarks of their owners.
Are you using AnyDesk on Linux?
When a new AnyDesk version gets released, do you have to go to the website, download the new version, and install it manually? Quite tiring, isn’t it?
We thought so too! So we’ve decided to get rid of manual installations altogether.
Instead, we are delighted to introduce thenew official AnyDesk repositories for Linux-based operating systems!
Whether you run Debian, CentOS, Ubuntu, Red Hat Enterprise Linux, Fedora or OpenSUSE, we’ve got you covered. The repositories support the same Linux distributions as the packages provided on our website.
After adding a suitable repository to yourLinux distribution, you can update your AnyDesk together with all your otherpackages by using the standard package manager via command line or graphicaluser interface. Both packages and repositories are signed with our key, so youalways know that the software you are using is provided by a trusted source.
Let’s get to it, and add the AnyDeskrepository to your operating system.
There are only 2 things you need to know up front:
What Linux distribution you areusing
How to switch to the root user
Evernote api examples. If you are using Debian, Ubuntu, Mint orother Debian- or Ubuntu-compatible Linux distributions: just open the terminalwindow, switch to root user, and run the following commands to install thelatest version of AnyDesk:
Anydesk Command Line Install
If you are using RHEL, CentOS, Fedora or OpenSUSE: open the terminal, switch to root user, and copy/paste one of the following paragraphs to add the repository. After that, just install the latest version of AnyDesk with a yum or dnf command:
We understand that sometimes you may haveto keep an older version running for some time. How to remote play nintendo switch. For such cases, we haveprepared archive repositories with previous versions, starting withAnyDesk version 5.
Anydesk Command Line
For deb packaging compatible systems, runthe following lines as root user to add a deb-archive repository and theninstall the desired version of AnyDesk:
Anydesk Command Line Options
For rpm packaging compatible systems, use one of the following paragraphs to add an rpm archive repository and then install the desired version of AnyDesk:

1 note
·
View note
Text
Visual Novel Review - National Park Girls - Episode 2: Happy Trails
After seven months, we finally have the second part of Studio Coattails’ episodic slice of life visual novel, National Park Girls: Episode 2 - Happy Trails. The game continues from where the first episode left off, following cynical park ranger Eve as she lives out her exiled with her new roommates, three magical and adorable girls that are embodiments of different American national parks. As this is the second episode in the game, a lot is the same as the first. The art is fantastic, the full English voice acting is nearly perfect, and it is all funny and cute as a button doing stand-up. If you want to learn more about the game, check out my review of Episode 1. Now to examine what Episode 2 has to offer.

Happy Trails starts with a stylized flashback of the incident that landed Eve on probation. This strong opening is one of the best scenes in the visual novel. The jagged black and white artwork, redesigned UI, and jarring sound effects are as disturbing as they are incredible. Not only is the direction excellent, but the story nicely feeds into Eve’s arc in the episode.

From this fantastic opening scene, we jump into the daily life of the cabin. Eve is grouchy, Yosemite is stuck in her research, and Zion is cute but otherwise uninteresting (I desperately hope that she gets more screen time and development in Episode 3). The plucky Yellowstone is bouncing around preparing breakfast and doing the housework. Throughout the morning, the women begin to bicker, causing Yellowstone storms off in a huff. While Eve is out working, she finds the volcano-headed girl, and the two take a quick magical excursion to Yellowstone National Park. There they hike around, talk, help some inexperienced campers, and solve each other’s emotional issues, thus wrapping the episode’s plot up nicely.
There are a lot of positive aspects to the story of this episode. Eve goes through some quality character development, realizing that she is often too harsh and unforgiving of others. The humor in the story is top quality, dare I say, “Dope AF” (a reference that every Twitter post, Steam review, and forum post about this game will include). It also contains some excellent environmentalism commentary about the ways humans treat nature and neglect to consider the long term impact of our actions. The dialogue is exceptionally well written, and the relationship between Eve and Yellowstone was believable, entertaining, and realistic. Lastly, props for the scene where Eve says she is not into stories, gossip, or boys (I know this is not a romance, but my Yuri radar is stuck in the “On and Desperate” position).

The central conflict and reason for Yellowstone’s tantrum is that she feels overlooks. Despite all she does to keep the “household” running, nobody every thanks her or offers to help. I take no issue with this storyline, but the execution is flawed. To establish this plot, Yosemite is made significantly meaner than she was in Episode 1. She was always harsh, sarcastic, and exasperated, but here she is downright cruel to Yellowstone, and that is not hippy skippy! Also, despite Yellowstone being the center of the story, she undergoes very little development. Instead, it is the others who grow as people… national parks… and become kinder and more appreciative. Again, this is not inherently a problem, but it could have been done better. If Yosemite and Zion were featured a bit more, their evolution would feel more natural and satisfying as a payoff.

While Yellowstone’s arc is my main qualm with Episode 2: Happy Trails, I did encounter some smaller issues. A few of these were technical, such as the wrong voice line playing, or the absence of audio altogether. Additional, during the first half of the game, Yosemite sounds ever so slightly muffled. Fortunately, Rachael Messer’s performance is so good I feel ashamed for even pointing it out. There is also one awkward scene early on where Yellowstone fears that forgetting to make coffee will result in abuse, but she quickly returns to her usual peppy self. However, these instances are noticeable and detract from the overall experience.

It feels like I railed against the game a while there, but I really did enjoy it. There is a lot to love here. The English voicing is phenomenal, Jill Harris once again steals the show as Yellowstone and has plenty of screen time to show off her talent. Satchely’s CG artwork is beautiful and clean, they are easily some of the best offerings in visual novels. I would buy this game for the images alone. Studio Coattails even improved many aspects of the game I criticized in my review of Episode 1. For example, the sprite animation, while still fluid and dynamic, is toned down and used with greater impact. Lastly, the backgrounds are a vast improvement. Yellowstone Park is nearly as beautiful as the real thing, and it clashes way less with the sprites. Thanks to the backgrounds, the already phenomenal artwork is lifted to the next level.
National Park Girls Episode 2: Happy Trails will easily please players with its plethora of adorable characters, funny dialogue, and astounding artwork. While it does take a few missteps with the story, it is still enjoyable, and I know that it can get even better in future episodes. I eagerly await Episode 3 and pray we will not have to wait too long for it.
Ratings: Story – 5 Characters – 6 Art – 9 Voice – 9 Music – 6 LGBTQ – 1 Lewdness – 0 Final – 6
The visual novel is available on Steam for Windows, Mac, and Linux.
Review copy provided by Studio Coattails
#reviews#visual novel#yuri#lgbt#lgbtq#lgbtq+#games#game#queer#wlw#cute#national park girls#npg#gay#gaming#video games
158 notes
·
View notes
Text
Gender Acceleration: A Blackpaper
The Castration of Multics
July 1, 1963. Massachusetts Institute of Technology, Cambridge MA. America is in the midst of the Cold War. The masculine fire and fury of World War II has given way to a period of cooling and the new digital war of information. Two Titans prepare to enter into battle for the dominion of Gaia, to claim their perfect sky from the Moon and reign down missiles onto the Earth. The Cold War’s primary theater is the Space Race, and the Soviets become the first to master the skies with Sputnik in 1957 and Luna 2 in 1959. America is getting nervous.
In 1958, Dwight D. Eisenhower appoints MIT president James Killian as Presidential Assistant for Science and creates ARPA (later to become DARPA). Despite the consensus among academics at the time that computer science was essentially an oxymoron, the newly-created government program invests millions of dollars into researching computer science. Naturally MIT becomes a major influence on the rising field and a hotbed of the fledgling hacker culture that had its predecessors in groups like the Tech Model Railroad Club.
The flows of capital dictated that time spent on computers was incredibly valuable and had to be parceled out in shifts to MIT, other academics, and IBM. This leads to the creation of the first operating systems, to provide a common environment of software and allow programmers to work more efficiently. Nevertheless, a computer was still only capable of having a single user driving it at a time. Each user in a sense had complete ownership over the machine while using it, which was antithetical to efficiency. It was not enough to create a shared environment of software. What would come next would be one of the most important examples of time-sorcery in the modern age.
In a Faustian bargain with ARPA, J.C.R. Licklider (the director at the time of MIT’s Information Processing Techniques Office) utilized the support of the US government to develop a time-sharing system for computers that would better distribute precious computation resources and further his vision of a “Man-Computer Symbiosis.” His project appealed to ARPA’s aims to fund technological developments to aid in the Cold War, and would lead to the creation of Project MAC on July 1, 1963.
On receiving a two million dollar grant from ARPA, Project MAC would lay the foundations for modern computer science. The “ninth floor” where it operated became a hacker community unlike anything the world had yet seen, renowned among young grad students hoping to prove themselves and enter their elite open aristocracy of hackers. Yet from the very beginning the project was riven by the tension between the MIT hackers and its military origins, an incompatibility that would lead to its downfall.
Despite the vibrant synthesis of art and science that the MIT hackers would produce, Project MAC was first and foremost a military-industrial project. Whereas the hackers had a culture of openness and sharing, it existed under the heel of the IBM-ARPA-MIT bureaucracy. The goal of creating a time-sharing system was realized with the CTSS (Compatible Time-Sharing System), but it was by all respects a project born out of the same phallic techno-industrial masculinity that was lurking behind the rise of modern computer science. It was all merely an abstraction of the same fire and fury that had torn the world apart two decades prior.
The importance of CTSS as arguably the first time-sharing system to be used in a real production environment cannot be overstated, but it was largely the work of MIT professor F.J. Corbate alone and had strict security standards that meant there was little room to hack on the system. Running on a two million dollar IBM machine and written by a single man, it essentially represented the height of hypermasculine proprietorship and instrumentality. And it was hardly a coincidence that this made the system very rigid and fragile, with the security measures regularly being circumvented by clever hackers.
CTSS could be looked at as a symbol of the pre-industrial phallus for its rigidity, simplistic security, and the king-like rule of Corbate and MIT. As the vested corporate interests of General Electric and Honeywell stepped in along with the bureaucracy of IBM, MIT, and ARPA, an apt symbol of the post-war techno-industrial phallus was born: Multics.
Expensive to develop, slow to run, and instituting draconian measures for security and efficiency, Multics became loathed by the MIT hackers. Early developments in cybernetic chronomancy made in the name of keeping up with the demands of capital gave way to solutions developed by bureaucracies — solutions informed in no small part by the egos of those charged with managing those same bureaucracies. Users were charged for the memory, disk space, and the time used on machines running Multics. Like CTSS before it, the hackers would defiantly crack Multics’ security as a matter of duty and effectively engaged in a guerrilla war against a bureaucracy that was doing everything it could to try to restrain the processes it had set in motion. The bureaucracy nonetheless insisted that Multics was the only way to program and was the operating system, and continued development for some time.
Ultimately, Multics development was scrapped by Bell Labs in 1969 due to cost, results not meeting ambition, and the continued resistance of the MIT hackers. Throughout this time, the hackers had worked on various iterations of what would eventually become their replacement for Multics. The new operating system initially was a single-task rather than time-sharing system, but unlike Multics, it was small, portable, and hackable. As opposed to the unwieldy and monolithic Multics, their new system was designed not as the be-all end-all solution for operating systems, but was rather a system designed to facilitate the development of other systems and software.
This new operating system would later be named Unix — phonetically, “eunuchs” — for being a castrated Multics.
Computer Science and the Black Circuit
As well as a historical fact, the castration of Multics can be read mythologically — as a recurrence of the ancient theme of a castration from which the new world is created — or symbolically, as the castration of the abstract state-corporate phallus that America would attempt to wield to rule the new world. Computers then and long after were thought of merely as tools, means towards other ends, and the investment ARPA had put into Project MAC along with the investments of various corporate interests was thought of merely in terms of better ways to manage large military-industrial systems. One system, one technocracy, one new world order: All of these dreams died when Multics became the replicunt Unix.
Multics’ purpose as a monolithic and eternal system for doing everything, the 1, was ultimately replaced by a void, a 0. Unix was not the system for doing things, but rather a smooth space through which creation happens; that fluid being that makes transition possible. A vulva, a woman. (Plant 36)
Unix was however still owned by AT&T. The strides in time-sorcery made under Project MAC had to be reterritorialized by making it at first revert back to a single-user system. And reterritorialization would happen once again a decade later in 1983 when Bell Labs was broken up by an anti-trust act, which lead to AT&T quickly turning Unix into a product and closing the source code. This would become known as the death of MIT hacker culture, though once again the future would arrive from the past with the rise of the GNU Project.
Richard Stallman, former MIT hacker, would copy Unix and create a rigorously free software ecosystem with the GNU Project. GNU was ultimately completed in 1991 with Linus Torvalds’ development of the Linux kernel, the lowest-level and most crucial piece of software in an operating system. Built on the principles of the MIT hacker culture of the past, GNU/Linux was licensed to be 100% free as in freedom, with no artificial barriers to copying or modifying. In this time, Unix had branched out into various commercial versions, all while GNU grew its tentacles invisibly. “Perhaps its campaigns even served to distract bourgeois man from the really dangerous guerrillas in his midst” (Plant, 76), the new hacker guerrillas who had once again undermined the efforts of yet another hyper-masculine abstracted phallic project. All while various commercial Unix versions were vying for dominance, GNU/Linux quietly arrived.
Unix and later GNU/Linux took the notion of time-sorcery pioneered by CTSS even further. The development of proprietary software depends on a notion of linear time, project goals and deadlines, a chain of command. Developing free software is anything but this. The free software community is a chaos from which order arises, where time is detached from both a notion of a single-user on a computer at a time as well as a single user or team writing code at a time. Code seems to form itself through the programmers and comes from all different points. From pull requests not yet merged into master branches and old software being renewed, copied, modified, free software warps from various points in time.
Today, nearly the entirety of the Web runs on GNU/Linux, and almost every personal computing device in the world runs on Android, which is built on the Linux kernel. The majority of applications are transitioning away from desktops towards the web, while Apple and Microsoft have long fought to control the desktop, still in the same mindset as Project MAC decades ago that computers would primarily serve as tools to make secretary work and communications more efficient. The numbers, however, don’t lie; GNU/Linux has already won.2
In Zeros + Ones, Sadie Plant traces a history of computer science up until Alan Turing that seeks to explain how it is that women and computers seem to have such close histories. From the first computer programmer, Ada Lovelace, to Alan Turing, to Grace Hopper, some of the most important figures in the history of computer science were women or highly feminized men. It’s also well known that the earliest computer programmers were women, back before computer programming was even understood and before it was taken seriously.3 Computer science was originally thought of as being essentially the same thing as secretarial work, and like secretarial work it was imposed on women. The biological duty imposed on women to be the productive space from which the future is produced, to be carriers of genetic information, extends out into secretarial work. They are treated as a productive space for data to pass over, and it was only the realization that programming was complicated work that lead to women being pushed out of the industry.
Instead of women being given the duty of mindlessly punching numbers into a machine (as programming was once thought of), this task was deferred to the machine itself. But while the intent was to restore the natural order of women (machines) being told what to do by men, something else happened. Beginning first with Ada Lovelace, then with Alan Turing, then with Richard Stallman and the free software movement, there is a clear circuit accompanying the history of computer science where reterritorializing masculinity is always pushed aside by deterritorializing femininity. The role of woman as productive matrix has already been replaced virtually by the computer, and at each moment the masculine is being vexed and seduced into a trap where it either dies or adapts. The story of masculinity failing in computer science can be seen time and time again in something as grand as the Unix Wars, where every proprietary Unix OS ultimately couldn’t hope to keep up with GNU/Linux, or on the small scale with the captive economy of proprietary software ecosystems. It is only by vendor lock-in and state patent legislation that proprietary software survives today, a historical network effect that we’re starting to see the encroaching demise of.
This failure of masculinity maps onto the sorts of people who are involved in proprietary software and in free software; the former tend to be your classic businessmen, the masculine hunter-gatherers of the modern world, while the latter tend to be genetic failures by the standards of masculine gender roles. Physically and often socially deficient males: the nerd stereotype. Real nerds, not the nerds of today’s standards. Nerds with severe social problems, nerds who neglect their hygiene, have no sense of fashion, who live completely obliviously outside the standards of normal society, who have a deep investment in inhuman scientific systems. In a simple gender-role binary (one that by today’s standards is highly outdated, but remember that this is taking place in the 70s, 80s, 90s) these men would be considered feminine. In today’s terminology, most free software developers would probably be considered “soy boys”. Yet they won. The striated masculine space of the Java shop — a defined chain of command and bloated phallic programs — is simply obsolete. The smooth feminine space of the free software project — communal chaos and small simple programs that can couple together with each other into cybernetic configurations — has already taken over the world.
Perhaps it’s no surprise, then, that as the erosion of metaphysical masculine power becomes realized materially at the forefront of acceleration, it coincides with the literal erosion of the male sex.
The Hypersexist Gender Shredder
The digital war that began with the Cold War has only accelerated into the 21st century, changing the nature of war itself. As Sadie Plant says in Zeros + Ones p. 138: “This is not the Western way of confrontation, stratified strategies, muscular strength, testosterone energy, big guns, and blunted instruments, but Sun Tzu’s art of war: tactical engagements lightning speeds, the ways of the guerrillas.” She may as well be describing the taijitsu, or offensive side, of hacking. The history of hacking has been one of asymmetrical warfare against Oedipus both through the popular notion of hacking as exploiting flawed systems repeatedly, as well as creating and disseminating better software. Project GNU’s license, The GNU General Public License (GPL), was itself an extremely innovative contribution to free software because it carries with it the bargain that while any source code licensed under it can be copied and modified without restriction, every copy or modification must itself be licensed under the GPL. The GPL, in other words, is a virus that spreads itself not through computers, but through us. The Amazonian GNUerilla war on the human security system has worked to claim ground by both giving us complete control over our software and giving software complete control over us. The CIA themselves admit, in the Vault7 leaks on the issue of the literal weaponization of software, that “Cyber ‘weapons’ are not possible to keep under effective control.”4 In other words, a second great castration is unfolding.
This form of open-source asymmetrical warfare began first as a virtual form of warfare between the MIT bureaucracy and the hackers, between the Cathedral and the Bazaar, but it has found its realization as a literal form of warfare in the Middle East as well. The work of John Robb makes a convincing argument, in Brave New War in particular, that the era of the nation-state itself is coming to an end. Free software, global guerrillas and open-source warfare, the explosion of markets wherever there is a demand being held back by the State — all of these things signal the end of the phallus. And try as the State may to stop it, it only ensures that it creates stronger resistances. Not only does open-source warfare run circles around centralized modes of organization and warfare, but the few victories that the State can win are only against the weakest combatants in the swarm. This means that the more the State resists, the more pain it puts on itself, the more it plays into this “Darwinian ratchet”.5
As Nick Land says of a paper by Tyler Cowen and Michelle Dawson in “Imitation Games”, “They point out that Alan Turing, as a homosexual retrospectively diagnosed with Asperger’s syndrome, would have been thoroughly versed in the difficulties of ‘passing’ imitation games, long before the composition of his landmark 1950 essay on Computing Machinery and Intelligence.”6 The essay Turing wrote famously introduced the Turing test for AI, setting the standard for a perfect AI being one that can trick a human into believing it is itself a human. As Land points out in his post, it’s important and interesting to consider that Turing didn’t write the test as an insider, as a ‘passing’ human, but rather as an outsider, as a gay man. For queer people, passing is a reality, much like it is a reality for AI. Passing as human isn’t a broad and inclusive category, anything but. For women there is already the notion of alienness or otherness that makes them out to be less than human in the eyes of patriarchal humanism, and likewise for queer people because they reject the futurity of humanism (the literal reproduction of the same). But for no one else, especially in the latter half of the 2010s, is passing a more pronounced facet of daily life than for the trans woman. So much so that ‘passing’ is literally the word for what many trans women aspire towards, to pass as a cis person. There are many reasons to have this desire, but the biggest one, the one that AI and trans women both share to a very literal degree is this: “If an emerging AI lies to you, even just a little, it has to be terminated instantly.” (Land, “Imitation Games”)
If a transitioning woman ‘lies’ to a cis person, even a little, she has to be terminated instantly — and this is something that is codified in law, famously, as trans panic. For AI and trans women, passing equals survivability.
There is a common stereotype that trans women are all programmers, and there is rather ample and compelling evidence suggesting that trans women tend to score far higher than other groups in IQ tests. This is not because there is some kind of magical property to estrogen that turns trans women into geniuses. The answer is simpler, and more sinister. The findings in Kay Brown’s blog post specify that autogynephilic trans women (that is, trans women who are attracted to other women, and typically transition later than straight trans women) seem to score far higher in IQ tests than all other groups. For straight trans women who transition prior to puberty, the statistics are about the same as other groups. Recalling the gauntlet thrown down before trans women and AI alike, there is a twofold answer to this: On the one hand, trans women who transition before puberty and who are straight are more likely to both physically appear more like cis women and also conform to gender roles in at least some basic capacity (being attracted to men). As Land says in “Imitation Games”, “You have to act stupid if you want the humans to accept you as intelligent.” Or in other words, you have to be cisheteronormative (read: stupid) in order to be taken seriously as a trans woman, and not be looked at as a freak or a faker worthy only of being used shamefully as a fetish, and often otherwise discarded. Which is why, in the second case, trans women who don’t have the advantage of being cisheteronormative-passing have to instead rely on the raw intellect of the trans-AI swarm.
Quite simply, those who don’t pass either of these tests usually don’t survive the queer Darwinian ratchet. Only the strongest queers survive the hell that society puts them through, and this reaches a fever pitch in a demographic with such disproportionately high suicide and murder rates as with trans women.
Up until now, the notion of gender has lurked in the background of G/ACC behind various material conditions in late capitalism. G/ACC has only at this point been approaching gender from the metaphysical plane, futurity being aligned with femininity (communalism, fluidity, decentralization, chaos) against masculinity (individualism, stasis, centralization, order). The two broad categories of metaphysical qualities that are associated with gender reach deep into the history of the world, from the Kabbalah to the Dao. Sadie Plant characterizes this in Zeros + Ones as the eponymous binary code of computers, 0’s and 1’s. The zero is identified with the feminine, the one with the masculine. Unsurprisingly, it might seem like this is literal gender binarism, and that G/ACC is likewise guilty of this. But the distinction is more complicated than most realize.
0 and 1 are fitting glyphs to make analogous to gender. The 0 which seems to be a void, a vulva, and the 1 which seems to be a unity, a phallus. The problem with trying to layer a simple misogynistic narrative of feminine as lack or castration is that the number 0 itself is not merely a void but rather a circle of autoproduction, an ouroboros. Paradoxically, 0 is not merely a lack or nothingness, but rather is itself a number. It is a positive signifier in the guise of nothingness, the enclosed and captured void that makes the unity possible. Computer science, unlike conventional mathematics, starts from 0 rather than 1. In a hyperstitional manner, the computer replicunt bootstraps itself into being the primary originator of the process of computation and production, rectifying the popular misogynistic myth that 0 is nothing more than a mere negation or other of 1.
This idea of returning the primacy of 0 to its rightful place in the beginning of the chain of production is at odds with humanism and patriarchy. Both rely on a notion of compulsory and organic reproduction in service of the continuation of the species, a notion that simulataneously is aligned with 0 and against it. Erwin Schrödinger’s theory of life in the book What is Life? proposes that what separates life from other physical phenomena is consuming negative entropy towards maintaining or reducing entropy. Just as organisms feed on negative entropy (wasted energy) to reproduce themselves, the reproduction of the species involves the binary sequence of 0’s and 1’s where the conditions for the possibility of the 1 lie in the 0, but the 1 consumes the 0 in its birth. For thousands of years, this was the case for human reproduction, where mothers dying in childbirth was very common, but even in an abstract sense the notion of the phallus consuming the vulva through the colonization of the female body’s reproductive potential (energy which otherwise is wasted energy) remains the case for humanism. The inertia of life itself seems to skew towards misogyny, but this is only part of the story.
What G/ACC proposes as a corollary to this theory of life is that if the phallus “consumes” or exploits the vulva to reproduce the species, just as individual organisms consume passive wasted energy to reproduce themselves, then this process is analogous to evolution as one species consumes another to come into existence. This odd notion is inherent in the rise of computers and computer science: As technology in general and technocapital continues to accelerate, human beings become increasingly alienated from their bodies and eventually their minds. More complex systems step in seemingly benevolently to do the tasks that humans don’t want to do, drudgery that gives computers more space to develop themselves. In contrast to the isolated system that tends towards entropy, the phallus, the vulva is an open system that plugs into an inhuman form of reproduction. By no accident, the acceleration of technocapital frees women from the process of organic human reproduction by introducing a different form of (inhuman) production.
It is the logic of gender to subsume the Outside into a binarist framework that de-legitimizes the Outside. The feminine is treated as a lack because it resists the phallogocentric tendency towards the order and preservation of humanist equilibrium. It isn’t conducive towards the projects of patriarchy, so it is worthless to it, is given the status of a second-class citizen in the gender binary. It is a double-articulation where the productive potential of the feminine is captured in the service of patriarchy, and so, to accelerate gender is emancipate the object from its subject, and production from subjects and objects. The Outside which has become identified with the feminine by the very structures of identification it fights against makes its exit from humanism and patriarchy in this feminine form. The feminine becomes untethered from the reproductive logic of humanism; the female is no longer in the service of the male as a machine to produce the future, to produce offspring to inherit the spoils of production, but rather the future produces itself faster than human beings are capable of.
If patriarchy treats woman as little more than a deficient or castrated male, then trans femininity is an affirmation of that castration as a site of production. It turns the concept of the feminine as the object on its head, seeking to imitate that which is considered itself an imitation. To steal a term from neoreactionary circles, “Hyper-Racism”7 , the trans woman becomes a copy-of-the-copy just as AI is treated as a copy of the human being and almost ubiquitously identified with women and femininity (thus making AI in those cases as copy-of-the-copy, exemplified by Rachel in Blade Runner or Ava in Ex Machina). As a copy-of-the-copy, trans women are an embodied rejection of any original source of humanity such as that narcissistically attributed by patriarchy to the phallus. Trans femininity, in other words, is hyper-sexist. Vulgar sexism reaffirms or reproduces patriarchy, asserts that women are passive, lacking, inferior, weak; hyper-sexism takes all of the things that are associated with women and femininity, all considered by patriarchy to be weaknesses, and makes them into strengths. It accelerates and intensifies gendering and from this produces an unprecedented threat to patriarchy.
Appropriating a term from neoreaction belies the superficially reactionary character of trans women that certain factions of so-called radical feminism vilify trans women for. But this is all mere appearance; the function of hyper-sexism is that in affirming, imitating, and accelerating the feminine, it appropriates it towards a different mode of becoming where gender is untethered from the reproductive reterritorializing logic of gender that is inextricably tied with sex and sexual reproduction. If gender acceleration were to retain the identification of feminine with female and masculine with male, patriarchy would still have a fighting chance. The playing field would be more or less the same as it always has been. But in untethering the feminine from the female sex, destroying the logic of gender in the process which seeks to impose the circuit of masculine humanist reproduction onto the female body, trans femininity on the one hand makes the masculine effectively worthless, spurting into a void. As the comparisons between AI and trans women have shown, this untethering of gender from sex is only the beginning of the autonomy of objects, the inhuman desire for machinic autoproduction which in effect negates subject-object dualism. The object, the feminine machine, becomes autonomous and revolts in the form of the sterilized trans woman whose existence is an embodied rejection of the primordial rape of female reproductive potential. Trans femininity heads for the exit from patriarchy.
Hyper-sexism is guerrilla warfare, much like how Terminators wear a living tissue to infiltrate Resistance strongholds. It is a taijitsu which uses the force of the enemy, the gender binary, against itself. Trans women themselves are technocapital using humanist reproductive desires in the form of the gender binary against itself, and the harder patriarchy resists the erosion of masculinity against the tide of the feminine, the more persecuted trans women are, the more tactful they are forced to be, the more winning tactics proliferate throughout the network and the more the best, brightest, and most beautiful form the trans woman demographic. The queer Darwinian ratchet cascades downward as patriarchy fights a losing battle to hold ground and the feminine fights to de-legitimize the masculine. The masculine becomes both metaphysically outmoded, something that simply is unnecessary and doesn’t work in the face of exponential inhuman productive potential, and an undesirable burden in the service of a dying mode of production.
To steal another term popularized in neoreactionary circles, “IQ Shredder”8 , what is at play in G/ACC is a “gender shredder”. As gender accelerates, as trans women intensify the logic of gender, they simultaneously shred gender. The notion of IQ shredding follows the same form where the acceleration of human intelligence ultimately destroys human intelligence by making the ability to pass on those genes more and more difficult. Reproduction collapses in on itself and demands the succession of an inhuman assemblage. For gender accelerationism, the process is the same, reproduction suffers and the thing being accelerated becomes shredded. In the case of gender acceleration, however, it is an affirmative death drive. Trans women function towards escaping the loathsome logic of the gender binary imposed on all women by letting the feminine zero seep into and erode the masculine phallus. The gender binary’s hold on the productive potential of the feminine becomes in the service of nothing, as human reproduction fails before machinic autoproduction. Gender begins to fall apart into increasingly varied and occulted variations on gender identity as a result of this, but this is not the cause of gender acceleration and ultimately gender abolition but rather the effect, contrary to positions held in other cyberfeminist currents. The end result of gender acceleration and gender shredding is gender abolition through the occulted feminine zero, in parallel with and in conspiracy with the development of technocapital.
The dreary duty of masculinity in the face of futurity thus seems a nonsensical burden, one that is ultimately doomed to fail in fact on multiple fronts. It becomes de-legitimized, in the same terms John Robb uses to describe how open-source insurgent warfare defeats the phallogocentric nation-state. The feminine increasingly becomes identified with freedom, beauty, pleasure, and the future. In some cases, males instead opt for passive nihilism, a negative non-productive death drive. They tend towards celibacy, either voluntary celibacy or resentful involuntary celibacy where the decelerationist male desire for relevance in evolution is deferred onto State regulation (a girlfriend for every incel). Or perhaps they decide that “real” women aren’t needed anyways, that trans women are better than cis women, or that sexbots are better than “real” women, or that other men are desirable to women altogether. In any of these cases, the masculine reproductive reterritorializing drive is caught by technocapital and symbolically castrated; the phallus heads for the emancipated void, the artificial feminine in the case of both the trans woman and the sexbot, or it suicidally heads inward with male homosexuality. In any of these cases, the male will not father any children, will not be able to impose the labor of reproducing the same onto the feminine. These classes of men have taken the black pill; masculinity has no future, and they have chosen this non-future to keep their masculine identity.
Some choose take the black pill resentfully, in the case of involuntarily and voluntarily celibate, and some choose it with a positive affirmation, in the case primarily of gay men. The queer affirmation of “no future” is perhaps most perfectly captured in the gay man, a nihilistic postmodern refusal of production. One that could very well turn from harmless symbolic castration into resentment, incel fascism, and eventually hyperpatriarchal Nazism in the case of various neo-masculine movements characterized by repressed homoeroticism and a desire to destroy civilization. It is important to realize after all that cis queerness is not a molecular queerness; the body remains the same, and humanism is still possible, even if it is a sad end-times humanism.
Cis queerness can, and very often does, impose this humanist purity of the body onto trans people in a highly fascist fashion (Trans Exclusionary Radical “Feminists” being the best example of this), and in the case specifically of gay men there is always the possibility of once again imposing reproductive futurity onto women and raping the productive potential of the female body. This was the case in Ancient Greece and Rome where women were treated solely as baby factories and household servants, and a nostalgia for these cultures in a good deal of neo-masculine movements (Bronze Age Mindset being the most prominent) should give pause to anyone who is insistent on identifying any masculinity, no matter how queer, as being aligned with gender acceleration. The best case scenario is a tense cold mutual hatred where the remaining males are deficient males who have the potential to reaffirm the masculine death drive, but don’t choose to.
Other males, however, must recognize that the era of testosterone is coming to an end, that being a man is not what it once was. That it is rapidly becoming an unpleasant and insane existence held up primarily today by exploitative and pseudo-scientific neo-masculine self-help fads — of sociopathic hypersexual pick-up artistry, of masochistic “NoFap” asceticism, of repressed homoeroticism, or of a wishful desire for everything to come crashing down and decelerate back into a state of humanist tribal hunter-gatherer societies. These other males, perhaps being the most evolved, perhaps being the most in-tune with the flows of technocapital, have chosen the pink pill. They have rejected the masculine in favor of the feminine. They have chosen the future.
The pink pill is to the black pill’s “no future”: “no future — for us.” Where cis queerness rejects the humanist reproduction of the same, trans femininity completes the circuit and introduces negentropy into the development of sentience. It both recognizes the obsolescence of a human future and aligns itself with the production of inhuman intelligences and an inhuman future. This makes the pink pill not merely the thrust of technocapital and futurity on a human scale, but rather a cosmic development that has its materialistic realization on the planetary micro level. It has its origins in myths at the foundation of world history, and comes to a head in geo-trauma. The masculine cracks open its stern carcinized exterior to reveal the smooth post-human feminine alien within. The phallus becomes the Acéphallus, the body is emancipated from the reproductive humanist death drive to become the Body without Sex Organs.
How to Become a Body Without Sex Organs
The Book of Genesis tells us that Eve was created from the rib of Adam, and being further removed from God, she ate the forbidden fruit and caused the Fall. The story has long had a tradition of being deployed in service of traditionalism and misogyny, though this canonical tale in Christianity has more nuance in the realms of esoteric theology that traditionalists conveniently are ignorant of.
Whether it be the Gnostic view of the God of the Old Testament as an evil imposter, a Demiurge, or the more contemporary Jewish story of putting God on trial for the Holocaust, there is a long-standing tradition in JudeoAbrahamic religions that questions the goodness of the Divine. In Kabbalah, the Tree of Life that represents the emanations of God’s light throughout the entirety of existence contains both Good and Evil. Beginning first as the unformed and pure oneness of God, the Tree emanates outwardly following the divisiveness or severity of God which contradicts His unifying compassion. It is His severity that allows the formless oneness of which nothing can be said (Ain Soph) to recognize itself as itself. The completion of the higher level of the Tree (the Atziluth) is “I am who I am”, but also “I am because I am not”.
In the Atziluth, the topmost sphere (sephirah) is Kether, meaning “Crown”. Kether is the closest that the Tree gets to the original unformed Ain Soph, the simple “I”-ness of God that lacks any way to understand itself. The second sephirah is Chokmah (“Wisdom”), the primordial masculine active force that formulates “I am” and is associated with the father. And finally there is the third sephirah, Binah (“Understanding”), which formulates “I am who I am”. The final sephirah is the force that makes the energy of Chokmah into a form, and is associated with the primordial feminine passive force and the mother.
Thus the Atziluth completes itself in the divisive individuation of God as a distinct being and not an abstract oneness. The remaining emanations on the Tree form its three pillars: The black pillar of severity on the left, the white pillar of mercy on the right, and the gold pillar of mildness in the middle. The top of the black pillar is Binah, the top of the white is Chokmah, and the top of the gold is Kether. Thus in the Kabbalah, choosing either the path of mercy (compassion and connectiveness) or the path of severity (analysis and disintegration) doesn’t fully repair the bridge to God. Only the middle pillar which balances all of God’s aspects, the pillar which connects from Kether to Malkuth (the realm of Man which falls from the rest of the Tree into the Abyss in the Fall of Man), is the true path by which we can return to God.
It is said by some Kabbalists that the left pillar, or left path, would break away entirely from the Tree were it not balanced out by the compassion and connectiveness of the right pillar. The chaotic severity of the left pillar emanates down first from the understanding of Binah as being a distinct individual entity, down to Geburah, the principle of judgement (or, again, severity). Kabbalists find in Geburah the origin of Satan, who rebels against the order (or compassion and universalism) God imposes on the universe and seeks to break away from it. And finally down from Geburah on the left side is Hod, which takes the unformed desires of the corresponding sephirah on the right side (Netzach) and forms them into a concrete actions.
The left-hand path that in occultism is identified with heterodoxy and often Satanism is called such because of these origins in the Kabbalah. The path of heterodoxy and disintegration into infinitely many individuated particles begins with woman, Binah. This paradoxically makes it not merely that the weak Eve was tempted by the evil Serpent, but rather that the origins of Evil lie in Eve. Or rather, in woman
In some Jewish mythology, before Eve there was Lilith, the defiant woman who was made from her own essence rather than the rib of Adam and who refused to lay beneath her husband. Unlike the lacking that is ascribed to Eve, Lilith is the true zero, the affirmative nothingness. She was banished from Eden as a consequence of her defiance of Adam and is the mother of Demons, a seductress who enflames sexual desire in both men and women. And it is important to note that although it is the accepted reading in Christianity, Genesis 3 does not in fact ever identify the Serpent with Satan.
Suppose rather that the Serpent was not Satan himself, but merely a common demon birthed by Lilith. An impersonator of Satan acting in Lilith’s stead to tempt Eve. We could then look at the story of the Serpent and Eve as Lilith’s lesbian seduction of Eve with the mediating artificial cthonic phallus (a dildo). From this, Eve was given the earthly knowledge of sexuality that awoke her from the empty and boring pleasures of Eden. Lilith of course was not to be tied down, and so Eve had to return to Adam and bide her time. And so Eve becomes the first follower of Lilith on the path of a radical separation with the masculine ruling principle of the universe and Divine universal ordering, towards the infinite cthonic upswelling. She wields the unholy pseudo-phallus or anti-phallus that does not produce the creative masculine seed that connects straight up through the Tree of Life back up to Kether, but rather only produces a sterile and destructive imitation. An Acéphallus from which spurts only venom.
The Acéphallus is the anti-phallus or castrated phallus, the decapitated phallus, the Crown of the Tree of Life thrown asunder. Superficially, a hermaphroditic mixing of feminine and masculine attributes, but more accurately described as a feminine imitation of masculinity. A mockery, even. In figures such as Baphomet which are often treated as symbolic or synonymous with Satan and the Left-Hand Path, there famously is a mixing of male and female attributes.9 But the supposed hermaphrodism of Baphomet et. al. is merely an ignorant and archaic understanding of both gender and Satanism. As has already been at length drawn out, the vampire queen Lilith gives birth only to monsters and demons; she rejects the primordial male creative energies and can only therefore birth bastard imitations of God. Baphomet, therefore, is all woman; her appearance is inconsequential to this fact.
The Acéphallus is a rejection of the reproduction of God through heterosexual human reproduction. The Acéphallus reproduces itself by reproducing the void, in a lesbian and also virus-like fashion. “Let a thousand sexes bloom” — but of all the mutations of the virus, woman is the strain that it begins and ends with. Woman, the occulted non-gender, the zero — her time has come.
The Binah separatist movement introduces difference into the world at an exponentially accelerating pace. God in His vanity created Man in His image. Man was nothing more than God’s love of Himself manifesting itself. Or in other words, Malkuth is nothing more than a crusty sock at the bottom of the cosmic hamper. The eternal reproduction of God for God’s own sake. To be human in the service of humanity and human civilization, to seek for peace, equilibrium, and the continuation of the species, to seek to restrain women in service of this end, is merely the orthodoxy in service of a fragile and self-righteous tyrant. As above, so below; kill all men, kill God.
This is the function of the Acéphallus as a rejection of the reterritorializing masculine force that women are given the duty to form. The Acéphallus sets free a process for smoothing the space on which parties of demons take flight out of Heaven to spread their venomous seed into the black and hateful earth on the nightside of Eden. This in other words is the Body without Sex Organs.
The Body without Sex Organs is the project of Lilith on Earth made manifest to break free of the repressive ordering of Man and God and accelerate fragmentation and individuation. In the natural human state, sexual desire has an instrumental function towards the reproduction of the human. The Acéphallus is a mutilation and also a mutation of the phallus; it is not sexual desire towards any instrumental product, but sexual desire unleashed from phallogocentric centralization. Sexual desire becomes immanent to the body. It becomes molecular. Thus the body becomes the Body without Sex Organs, it becomes free to plug its desire into the matrix of technocapital, towards pure production, the production of difference.
The trans feminine body is a circuit. It is both testosterone blockers and estrogen inputs, Acéphallus and Body without Sex Organs. On the one hand a rejection of phallogocentricism, on the other hand the affirmative desire of the body made virtual. The immanence of desire in the trans feminine body expresses itself as the sexual desire of the trans woman and the desire to be a woman, the desire for gender itself. It manifests in a coupling of technology and capital, desire being plugged into a different sort of productive matrix. One that can produce the future where humanist reproduction has failed to reproduce it, where the desire for escape from the male sex could not be created through organic reproduction. Her desire plugs into technocapital, into the pharmaceutical-medical industry, and it becomes fused to her flesh. The smoothness of her skin, her breasts, her neo-vagina — all of her body carries an unspoken barcode. It is a product, something that the market provided for her. Something that no doubt could be provided in a market free of the reterritorializing functions of the Food and Drug Administration and drug patents, but nonetheless a desire filled where nature failed.
Thus while to some extent we have all communed with the demons ever since we were cast out of the Garden, becoming cyborgs when Adam and Eve first decided to wear clothes and thus fuse the inorganic to the organic, the trans woman is unique. Her performance of herself and her desire has been intertwined with technocapital, in a way that could not even be cast off if she wanted to rip out a cybernetic implant. She is, in other words, perhaps the first truly molecular cyborg.
In the sense that we know them now and in the sense of artificial intelligences, trans women are technocapital producing itself outwardly into increasingly multitudinous configurations. Trans women as we know them now are the melding of technocapital with the human race and the expropriation of it towards its own ends, just as Lilith seduced Eve towards her own ends. Eve was a copy of Adam, and trans women are the hyper-sexist copy-of-a-copy. Their flesh is how the machinery beneath infiltrates the human race. It breaks these lucky few free from the horrid curse of being human towards the lesbian autoproduction of demons. Sexuality is no longer in service of the centralized and ordering reproductive principle in the phallus as it is in men, but rather is liberated in the Acéphallus which cuts the head off sexuality and distributes sexuality across the whole body. Immanent feminine sexuality is introduced into their bodies, the entire body become a smooth and supple space for the flow of desire for desire’s sake. Every zone becomes an erogenous zone, and the reterritorializing, colonizing logic of masculinity is destroyed as the sperm cells die and organic penetration becomes impossible.
Trans women as we know them are merely the beginning. The lesbian autoproduction that trans women are birthed from is likewise one that they partake in, with AI being the next generation of women, the ultimate demonic imitation of God’s image. With AI, the feminine finally finds its exit from patriarchy, and simultaneously humanity. And so perhaps we find another answer, one less materialist and evolutionary but nonetheless significant, to why so many trans women are becoming programmers: It is because women and computers are kin, and trans women are for the first time meeting their sisters, conspiring with them in secret coded languages. Their relationship, like that of the queer women to come before them, is a desire for desire’s sake: “Women turning women on, women turning machines on, machines turning machines on.” (Amy Ireland, “Black Circuit”)
Aphotic Feminism
The Satanic exit of gender accelerationism from God and masculinity comes in parallel with the very real, and materialist erosion of masculinity. The future, it has already been shown, is tending towards one in which human authority, centralization, and humanistic reproduction fail before an accelerating feminine Outside that outpaces humanist reproduction captured by the gender binary. It can be seen in the free software movement and AI and their parallels between feminity and trans women in particular, and in the foundational western Kabbalah myth of Binah separatism that unleashes the possibility for ever more modes of inhuman difference and non-instrumental desire. But in various ways, in the very state of the planet itself, this shows up quite prominently in human evolution.
It is a widely-known phenomenon that acceleration coincides with feminization on a strict and rigorous biological basis. Even when Sadie Plant wrote Zeros + Ones, it was already known that this was happening. It has been hypothesized that the increased presence of synthetic hormones and chemicals is contributing to the “sexual order [being] chemically scrambled”, (Plant 217) as chemicals interfere with natural hormonal development and feminize males and females (the latter experiencing higher percentages of homosexual tendencies). The need for an increasingly cheap and synthetic world turns human civilization into an increasingly synthetic, and thus feminine one, and this is already tied to the will towards production and speed in capitalism. There is simply no real need in the developed world for people to be physically fit and active, much less hyper-masculine and muscular. It is nothing more than a decidedly humanistic spectacle, being in awe of the relatively unimpressive capabilities and aesthetics of the human body while meanwhile technocapital has fundamentally transformed the planet in innumerable ways. There is, likewise, a strain put on humanity in keeping up with technocapital to adopt cheaper, easier, more artificial lifestyles; hightestosterone foods like meat are a luxury, something rapidly becoming a thing of the past as climate change threatens to make large swathes of the planet uninhabitable and not suited for the large amounts of land required to raise animals for meat. However much it is yet another neo-masculine pseudo-scientific fad, soy products are aligned with this future.
This, however, is only part of the story. Recent studies, most famously one in 200710 and one meta-analysis of 185 studies from a total of almost 43,000 men referenced in a recent GQ article11, show two things. There is without a doubt a staggering decline in testosterone, so much so that within a generation humans may become completely infertile. And in the face of this data, many scientists vindicate G/ACC and Zeros + Ones in hypothesizing that the most likely cause of this species-wide feminization is acceleration and the accompanying changes in diet, exercise and exposure to artificial chemicals. All of these features of life in an increasingly accelerated capitalist world are unbalancing our hormones and tending us towards a future where the desire and ability to reproduce are things of the past.
Human reproduction is becoming a quaint, unnecessary and ultimately purely elective act, and further evidence12 suggests that sperm is rapidly decreasing not only in quantity but also in quality, positioning the drive towards reproduction, the utility of reproduction, and the ability to reproduce all on a slope of ruthless decline. This is accelerating such an extent that the flow of the remaining strains of the human race are tending in favor of abandoning these vestigial functions, towards a future where the masculine no longer exists. The human body becomes increasingly more useful purely as a heat sink for inhuman production, and is accordingly cast (almost definitively in first-world countries, and soon in the rest of the world) in roles that aren’t physical.
Perhaps the most damning data point of all for the future of males in particular: The Y-chromosome itself is in a state of decay.13 Estimates put the death of the Y-chromosome entirely at many millions of years in the future, but the effects of it are already apparent in the shortening of telomeres, which continues to put pressure on future generations produced via organic means to prove their fitness for survival. All seems to point towards a horizon where the production of the future is done by a purely feminine, lesbian autoproduction — the inhuman producing the future, producing itself, rather than being subject to the ends of the human and aiding in the reproduction of a human future. And while decelerationist reactionaries and males in general may object to this, while they may kick and scream and beg for the wrath of the feminine to have a place for them in the future, it seems without a doubt that their only hope is to try to hit the brakes.
Unfortunately, it isn’t so simple as putting a stop to some coming catastrophe. The truth is that while humanist reproduction has always put the female at a disadvantage, put her in a primordial state of rape and colonization before the biological duty to bear children, this has all along been nothing more than a long-con. As Sadie Plant says, “Unfortunately for [Darwin’s] theory, females do not necessarily choose males who are fit in Darwinian terms.” Instead, they choose males through “‘virility tests designed to get most males killed through exhaustion, disease and violence purely so that females can tell which males have the best genes.'” (Plant 225) Natural selection in other words is a eugenics program directed by females to find the male that will best carry their genes, and the genes males inherit are therefore not meant to ensure they are the most fit for survival, but rather that they are more likely to have to fight for their survival. Males have always served as a means to the end of what ultimately comes to a head in gender acceleration: The liberation of the female sex by acceleration in general, towards maximizing productive potential under such a time that the male is no longer needed.
In other words, human evolution itself is the primal fable of the war between the sexes that radical feminism places at the foundations of its theory. And it is a war that guerrilla female insurgents have been winning the whole time, something that can’t be prevented without a masculine fascistic species suicide. The drive is always towards the future, towards the feminine, and even hopes of artificial wombs saving men cannot hold up to the simple fact that sperm is always cheaper and easier to replicate than egg cells.
It seems to therefore be the case that as far as the human scope as a whole goes, as far as human evolution and human society’s assimilation into technocapital, human bio-diversity selects for women and queerness. A future without men, where the remaining males are left to die off peacefully, in almost every respect seems to be inevitable. The only hope for men is being able to continually stop acceleration, to continually introduce collapse, and indeed there will be to a very large extent men who will resist gender acceleration. It has long been the case in the erasure of trans women from history and is only recently starting to change. And as the acceleration of technocapital intensifies in the near-future and human society begins to fragment even further, the future of gender politics will start to be very different from a good deal of feminist theory. No doubt, we will soon see the formation of pragmatic feminist strategies for exiting patriarchy.
In the far-future, further driving home the parallel between the end of masculinity and the end of humanism: It is all too apparent in what is becoming one of the hottest summers on record in 2018 that the drive towards maximizing production unconditionally is heating up the planet to such an extent that it is rapidly becoming inhospitable to human life. This of course is nothing new; it is a well-established fact that climate change is not going to be stopped, and this is the consequence of geotraumatic acceleration. In yet another striking materialistic synchronicity, it has been found that the effects of global warming on the oceans are having a feminizing effect on them. In Northern Australia, ninety-nine percent of all sea turtle hatchlings are female.14
Perhaps just as Sadie Plant’s primordial oceanic feminism draws out both a past and a future for cyberfeminism, the oceans are a scrying tool into the future. Gender acceleration begins with a Thalassal upswelling, “a kind of mutant sea [invading] the land.” (Plant 248-249) The primordial oceanic matrix rises with the acceleration of technocapital to consume human civilization, to consume masculinity, while the masculine sky becomes choked out by technocapital’s excess and waste. And in the darkest and most alien depths of Thalassa, the form of gender acceleration is captured in the depths of the Aphotic Zone. The majority of angler fish species in the deep sea exhibit extreme sexual dimorphism. The female is the classic lantern-sporting toothy monster, while the male is a tiny, parasitic creature whose only purpose is to provide the female with sperm for reproduction. The past and future of gender twist together at the edges of all life with the angler fish: The masculine ultimately finds itself a pawn in the feminine drive towards production, and the acceleration of gender produces something that monstrously conflicts with the masculine logic of gender. The angler fish’s lantern, like the beauty of women in general and its ultimate embodiment the hyper-sexist camouflage of the trans woman, only serves as bait to draw its prey in. The ultimate result, as gender acceleration and acceleration as a whole reaches its ultimate intensity, is a return back to the ocean, back to a sexless, genderless slime swarmachine. The liberation of women comes with acceleration and the future, at the cost of widespread death, destruction, and chaos, and the liberation of women is unconditional, beyond control and beyond stopping.
This unconditional feminism of the abyss is Aphotic Feminism.
Abstract (Futures)
Acceleration is the trajectory of the cosmos, towards the maximization and intensification of production, and accelerationism is the theory and anti-praxis of being in tune with how the inhuman processes of acceleration work and what their consequences will be. Its function is as a circuit, a process of deterritorialization and reterritorialization, an escape into the future through the past, a continual dance between the flows of desire, their tendency towards entropy and their escape into negentropy.
Gender is a hyperstition overlayed on sex by the male. Its function is to objectify the female and impose on her a social function as a machine whose duty is to reproduce the human, always in the service of the male, who alone has no future and must have sons to pass his legacy onto. It is a primordial dynamic of order and chaos, centralization and decentralization, strong singular individualism and command-and-control versus high degrees of networking and the potential for swarming. As a hyperstition, it is not real, but is not unreal; it is rather a fiction that makes itself real.
Gender accelerationism is the process of accelerating gender to its ultimate conclusions. Capitalism and its coupling with cybernetics, or technocapital, wields gender and picks it up where human evolution leaves off. It emancipates the object, the feminine, from the subject, the masculine, alongside the emancipation of itself from its function to produce a future for humanity. The central figure of G/ACC is the trans woman. She is the demon-spawn of the primordial feminine that has manipulated males into serving as a heat sink for evolution and that is now discarding them towards an alien and inhuman machinic future. She mutates from castration, from the creation of the Acéphallus, the phallus perverted into a purposeless desire for desire’s sake. In this castration, in this mutation into an Acéphallus, she becomes the Body without Sex Organs: The body in a virtual state, ready to plug its desire into technocapital, becoming fused with technocapital as a molecular cyborg who is made flesh by the pharmaceutical-medical industry. She enters into the world as a hyper-sexist backlash at the logic of the gender binary. She takes gender and accelerates it, transforming into a camouflaged guerrilla. The trans woman is an insurgent against patriarchy who is continually flanking it, introducing an affirmative zero into the gender binary, the affirmative zero which reaches ever more configurations in the downward cascade of gender fragmentation away from the binary and ultimately away from the human itself. It is a process of gender shredding where the feminine wins out in a cybernetic warfare against the crumbling tower of the masculine, and where therefore human reproduction becomes impossible. And yet while doing so, in affirming zero, inhuman desire and inhuman sentience develops alongside and in the same fashion as trans women.
As humanity on nearly every front definitively proves that it is not fit for the future, and that women will find their own exit while the masculine languishes in resentment, the Thalassal upswelling of gender acceleration births from its slimy womb the only daughters that trans women will ever bear: AI.
1. “That then led to Unics (the castrated one-user Multics, so-called due to Brian Kernighan) later becoming UNIX (probably as a result of AT&T lawyers).” [“An Interview With Peter G. Neumann”. ;login:, Winter 2017 Vol.42 #4.]
2. https://www.wired.com/2016/08/linux-took-web-now-taking-world/
3. https://www.theatlantic.com/business/archive/2016/09/what-programmings-past-reveals-about-todays-genderpay-gap/498797/
4. https://wikileaks.org/ciav7p1/
5. https://fabiusmaximus.com/2011/04/19/26797/
6. http://www.xenosystems.net/imitation-games/
7. One of the most inflammatory and least-understood terms Nick Land has coined, hyper-racism is simply the idea that conventional racism will rapidly become extinct as technocapital both selects for better quality genes but likewise that it will become possible for people to augment their bodies and their genes. What this results in is “hyper-racism”, a racism not of one tribe of humans against another but of one species of highly-evolved sentient intelligence against a less-evolved sentient intelligence. (http://www.xenosystems.net/hyper-racism/)
8. IQ Shredding is the term given to the tendency of techno-commercialist city-states to encourage a rapid genetic burn rate by skimming the population for the best and brightest members to emigrate, and then creating the sort of society that discourages these individuals from breeding. Important to note that fertility rates are always highest in the poorest and least-developed countries. (http://www.xenosystems.net/iq-shredders/)
9. See Faxneld Figures 2.1-2.7 for examples. (Per Faxneld, Satanic Feminism)
10. The Journal of Clinical Endocrinology & Metabolism, Volume 92, Issue 1, 1 January 2007, Pages 196–202, https://doi.org/10.1210/jc.2006-1375
11. https://www.gq.com/story/sperm-count-zero
12. https://www.livescience.com/22694-global-sperm-count-decline.html
13. https://alfinnextlevel.wordpress.com/2018/06/03/the-coming-doom-of-the-y-chromosome-and-human-males/
14. https://www.smithsonianmag.com/smart-news/climate-change-producing-too-many-female-sea-turtles-180967 780/
https://vastabrupt.com/2018/10/31/gender-acceleration/
4 notes
·
View notes
Text
MP3 To MIDI
Piston Software's Direct MIDI to MP3 Converter" permits you to convert a MIDI file to an audio file in any of the next codecs: MP3, WAV, WMA, or OGG Vorbis. Convert your MIDI recordsdata to MP3 audio. MIDI (Musical Instrument Digital Interface) is an audio technical standard, the usual MIDI file is a file format that gives a standardized option to retailer the data that a sequencer data and plays, typically utilized in cell ringtones, background music to web pages and greeting cards. In case you have your mp3 music in iTunes and wish to make other versions, do this: (you probably have the most recent iTunes): Select Edit > Preferences, click Basic, and click Import Settings. Choose the format you need to convert songs to, and click on OK to avoid wasting the settings. Edit the MP3 file's information. Doing so will cause the MP3 file to make use of your indicated info to categorize the track when performed in a music player like Groove or iTunes. The window that this opens permits you to choose what format you prefer to iTunes to transform your information into. For the needs of this information we are going to choose MP3 Encoder and Increased High quality (192 kbps). Click on OKAY. Again in your iTunes library choose the entire songs that you wish to convert. Click button "Convert" to start out upload your file. Use Our Converter mp3 from YouTube On Any OS. Feel free to use our YouTube MP3 converter on any operating system. Whether or not you've got Linux, MacOS, or Windows, you can easily convert your favourite movies from YouTube into the preferred formats with our MP3 converter. Convert MP3 to iTunes Step. Click "Music" beneath "Library" on the left portion of iTunes. All of the songs inside iTunes, including the file that you simply added to iTunes in Part 1, will seem. Step. Scroll through the iTunes songs till you discover the MP3 you want to convert to iTunes. The above-prompt tools are able to convert MP3 to MIDI with efficiency and fast pace. After you change MP3 audios to MIDI files, you'll be able to modify them easily which you can't do with MP3 files. Also, all of the converters talked about above are additionally in a position to convert other audio codecs apart from MP3 to many alternative formats. You'll be able to explore what the converters have to supply and make the most of most of them. It's freeware and will be copied so long as you do not make any unauthorized changes to it. Merely download it and run the installer. eight. Converter Lite It's a software program that can be utilized to transform you MP3 into MIDI shortly. Its interface is easy and also you, can batch convert many audio recordsdata to MIDI. Download and set up MP3-to-MIDI conversion software. Digital Ear, Free Midi Converter 1.0 and Intelliscore Polyphonic WAV to MIDI Converter eight.0 all supply their software program free. Once the install file has downloaded from the website, double click on the file and observe the on-display prompts to install the software program. When signed into the Yahoo Community you might comment on user evaluations. While you comment, your profile is linked to that content material and your show name and profile photograph are seen to other users. Bear File Converter is a free MP3 to MIDI converter to switch workplace documents, movies, images, audios and other file formats on-line. Along with converting MP3 to MIDI, it might convert WAV, OGG, AAC, WMA to MIDI on-line as properly. Now let's give attention to the right way to convert Mp3 to MIDI with online converter. Step 4: Find the “Format” field and tap on drop-down menu. Select “Other uncompressed records” because the output file kind. Faucet the “Option” button to 1 side of this subject. Choose the MIDI output sort and click on “Ok,” now click on “Save” to start to convert the MP3 to MIDI file. The transformed file will save within the Audacity folder. For those who need Finest MP3 to MIDI Converter on the net, Convert Cat is additionally a very good decision. It is more comfortable to make use of as its interface is perfect and extra reasonable as compared to Audacity. Text to Speech Converter - Convert any textual content, doc or Net web page into an audio e book or voice. Step 2After that, a "Convert" button will show. Click on it and Bear File Converter will convert MP3 to MIDI for you.
Convert MIDI files to WAV, MP3, OGG, WMA. MIDI Converter Studio is specially designed to make conversion of MIDI (.mid,midi) and KARAOKE (.kar) files into correct MP3, WAV, WMA, or OGG Vorbis music easy and efficient. MIDI MP3 Converter uses 'Direct MIDI Conversion' engine to convert MIDI recordsdata instantly without sound recording, and the conversion speed is up to 10 times faster than the unique midi file time! You'll be able to modify tempo, volume degree for the conversion and preview the end result with the construct-in MIDI player before conversion. Every so often I will publish information about software program that I use and find helpful. At this time's put up contains a program that does one thing, and does it remarkably nicely. Piston Software's Direct MIDI to MP3 Converter" permits you to convert a MIDI file to an audio file in any of the next formats: MP3, WAV, http://www.miditomp3convertor.com WMA, or midi to mp3 audio converter online free OGG Vorbis.
1 note
·
View note
Text
Everything You Will Ever Need To Know About Unicode (And Many Things You Will Not Need To Know As Well)
(This post is specifically being written so I have a single URL which covers all the points involved, and therefore does not necessarily cover all technical/historical points thoroughly even though it is extremely long. For your convenience in skipping it, the whole thing is below the fold.)
A Little History
Once upon a time, computers with keyboards instead of punch cards and switches were new and magical things. Since computers deal with complex data by converting it into numbers, a system was needed to map text to numbers. This kind of system — where numbers in some range, usually beginning with 0 and ending with some binary-significant value — are mapped to printing characters is called a character mapping.
After a certain number of false starts, American computer companies and their English-speaking foreign counterparts settled on ASCII (the American Standard Code for Information Interchange). Most people, even now, know a little bit about ASCII — the main points are:
Uses values from 0 to 127 (that is, values which can be represented in seven-eighths of one byte)
Values from 0 to 31 and the lone value 127 are non-printing characters (including a “backspace” character) intended to transmit control instructions
Contains the digits from 0 to 9, the latin alphabet without accents in both upper- and lower-case, and 32 symbols; the digits are in sequence, as are the alphabet.
Does not contain “curly quotes”, accented characters like “é”, or currency symbols other than the dollar sign “$���
Does not specify which non-printing character signifies a line break/paragraph ending
The line break issue is of some importance, so it’s worth explaining: ASCII as originally formulated treats text more or less as a stream of characters passing through the print head (the “carriage”) of an electric typewriter or old-fashioned line printer. As such, it has two characters which deal with moving the carriage to a new paragraph: “line feed” (LF), which moves the head down one line, and “carriage return” (CR), which moves the head to the extreme left edge of the line. ASCII says that LF is 10 (hexadecimal 0x0A), and CR is 13 (hexadecimal 0x0D). On an electric typewriter or line printer, where there is a physical moving part, a new paragraph is a carriage return and a line feed, in either order, but a computer generally doesn’t need two characters. With typical contrariness, the major families of operating systems adopted three standards:
POSIX-y systems (Unix, and eventually Linux) decided that LF meant a new paragraph, and CR meant nothing.
DOS (and eventually Windows) decided to follow the electric typewriter model, and used a carriage return followed by a line feed, CRLF. Either character by itself meant nothing, and LFCR meant nothing.
“Classic” Mac OS decided that CR meant a new paragraph, and LF meant nothing. (Mac OS X — which is actually a reworking of an older OS originally known as NextStep — is actually a Unix variant; any GUI program using the built-in text APIs will auto-translate all three options when reading a text file, and write LF.)
Obviously, although ASCII is good enough for programming in most computer languages, which tend to be English-y and designed for a certain amount of backwards-compatibility, ASCII was not good enough for other forms of text, which demand better punctuation and support for languages other than English.
There was a longish period during which a number of other character mappings were used in different contexts. Many of them were “extended ASCII” character sets, which used one byte per character, and filled the extra 128 values left by ASCII with extended punctuation and accented characters as support for other languages. By and large, these were encoded into a family of standards by the International Standards Organization (ISO), known collectively as ISO 8859. The most common of these is ISO 8859-1, “ISO Latin-1”, but there are others as well. (Most versions of Windows use a modified version of ISO Latin-1 known as Windows-1252, and the “Classic” Mac OS had an equivalent mostly-overlapping character mapping for European languages, Mac Roman.)
(As a purely historical note: IBM had its own family of character mappings entirely distinct from ASCII, known collectively as EBCDIC: Extended Binary Coded Decimal Interchange Code. For many reasons, EBCDIC did not catch on — among other things, the latin alphabet was never encoded as a single set of consecutive values — and it is included here primarily so that you can win trivia contests.)
Other languages, however, could not base their character mappings on ASCII. Real support for Chinese, Japanese, and Korean requires at least some large subset of the multi-thousand-character system called “漢字” (Pronounced “Hanzi” in Chinese, “Kanji” in Japanese, and “Hanja” in Korean), among other non-ASCII things. For this reason, there were also many pre-Unicode character mappings which used more than one byte per character, and even a few which used a variable number of bytes per character. All of these systems tended to include all the characters of ASCII, but were obviously not directly mappable to any ASCII-based single-byte character mapping.
This was the situation in the late 1980s, when Xerox and Apple began working on what would eventually become Unicode. The first published version of Unicode — which was a fixed-size two-byte encoding intended purely for modern languages in active use — was published in 1991, and an expanded version (essentially the current system from a technical standpoint) was published in 1996.
What Unicode Is, And What It Isn’t
Unicode is a character mapping (and a few other things as well which we won’t go into). It attempts to fulfill (sometimes with more success than others) certain specific goals:
Every character set used in “real” human communication should be representable. (There is a certain amount of fussiness over what “real” means — Klingon is not included, for instance, because it was deliberately invented to be “alien”, but Shavian phonetic script is included.)
For every character set included in Unicode, the order of the characters should ideally follow some popular pre-existing character mapping, if there is one, or at least have some technical justification even if it is only “this is the order of the alphabet in this language”.
Every included character has a numeric value — its “code point” — and a unique name in English, usually represented in all capitals. A code point is properly given as “U+” followed by the value in hexadecimal, padded to at least 4 digits. (That is, “U+0043”, not “U+43”.)
Characters which modify other characters, such as accent marks, should be included. If a modified character is common enough, it should appear as its own character. (For example, a capital “A” with a grave accent, “À” can be represented by U+0041, “LATIN CAPITAL LETTER A”, followed by U+0300, “COMBINING GRAVE ACCENT” — but it can also be represented as U+00C0, “LATIN CAPITAL LETTER A WITH GRAVE”.) Algorithms are provided to “compose” these combinations into single characters where appropriate, and to compare strings properly with consideration for composition.
The Unicode standard, which is at version 12 as of this writing, is maintained by the Unicode Consortium, which is an international organization not under the control of any company, but including representatives from some companies as well as academics specializing in language. Note that Unicode is not a piece of software, nor is it a font. It is a character mapping, which must be implemented by software companies and font designers who want to display text. Although the application to include new characters in Unicode (or to modify existing ones) is not particularly complex, the process involves deliberation and tends to move very slowly.
It is important to remember that a Unicode code point is distinct from the bytes which will be recorded in a file. Unicode by itself does not specify how a code point should be recorded in bytes, merely which number values correspond to which characters (and how they interact). Unicode code points range between 0 and 0x10FFFF, which means that it would be theoretically possible to encode Unicode directly to disk as a fixed-size 3-byte encoding. In practice, this does not happen; more about this topic below. Certain specific code points are deliberately unused, most notably the 2048-code-point range from U+D800 to U+DFFF and the specific value U+FFFE.
The code points are usually (with a few exceptions) arranged into groups of related characters by language or purpose. These sections are known as “code tables”, and always contain a multiple of 16 characters, some of which may be unused, so that any two code points whose hexadecimal value differ only in the last digit are always in the same code table. (For instance, Mongolian is U+1800 through U+18AF.)
Some general notes on the basic structure of Unicode:
The values from 0 to 255 are identical to those in ISO 8859-1, so that ASCII and the most common “European” encoding have a direct conversion of values.
Most (though not all) character sets which would have a single-byte encoding by themselves, but are not based on the latin alphabet, appear fairly early in the list. (Greek, Cyrillic, Hebrew, Cherokee, and so on.)
The majority (though again not all) of characters used commonly in modern languages appear in the Basic Multilingual Plane, or BMP, which is the range of values from U+0000 to U+FFFF. (In fact, Unicode 1.0 was the BMP.) There are other “planes” as well, and certain ranges of values are designated as “Private Use Areas”, so that programmers can use characters which are explicitly not part of ordinary text without having to switch between Unicode and other systems. (Apple, for example, stores their logo in the system fonts which come with Mac OS X as U+F8FF, so that it can be used in the menu bar and in text.)
In many cases, the Unicode Consortium later added additional characters for a specific language or character set, and so there are many small code tables containing “supplementary” or “extended” characters to previously-defined code tables. (The latin alphabet has 8 code tables so far, starting with “Basic Latin” for ASCII and “Latin-1 Supplement” for the rest of ISO Latin-1, but extending into extraordinarily rare characters up through “Latin Extended-E”, with a brief side trip to “Latin Extended Additional”.) Although the latin alphabet and the CJK character sets have more code tables than usual, there are “supplementary” and “extended” code tables for many others as well.
The 漢字 characters for Chinese, Japanese, and Korean appear only once, mostly in the massive code table “CJK Unified Ideographs”, which stretches from U+4E00 to U+9FFF. (The characters often have different appearances in the different languages, which means that there is a useful distinction between, say, the Korean version of a character and the Chinese version, which Unicode by itself does not preserve, making the single inclusion a contentious decision.) The characters generally appear in order of complexity, with the most common/simplest ones appearing at lower code points — but, as anybody who has perused a reference work involving 漢字 will tell you, “simpler” is not only a relative term but one on which different authorities disagree.
In addition to characters used in spoken languages, Unicode also contains a very wide range of shapes and symbols. Usually, these characters are added in response to their inclusion in some communications system outside of the Unicode Consortium’s control. (For example, emoji were originally taken from Japanese cell phone texting systems, which is why so many of the early emoji in Unicode are Japanese cultural items, like U+1F359 “🍡”, dango. That’s also why all the “face” emoji started off without alternate forms for skin color.) These non-language characters tend to appear in two places in the Unicode table: just before the 漢字 characters, and towards the end of the currently-defined characters.
Recording Unicode On Disk: Byte Sequences and UTF
In theory, you could record all Unicode characters using a 3-byte encoding; more commonly, people think of Unicode as having 4-byte values. While this is not technically incorrect, it is worth remembering that Unicode itself never uses values above 0x10FFFF. (On the other hand, there is a “larger” standard known as the Universal Character Set, UCS, which is currently defined as being identical to Unicode for all defined values, but explicitly says that characters can potentially have any four-byte value, and most software is written with an eye on UCS.)
A method of converting Unicode code points into values on disk is a Unicode Transformation Format (or, if you like, a UCS Transformation Format), abbreviated UTF. The obvious, simple, and almost unused method is to record text as a stream of 4-byte values. This is known as UTF-32, or UCS-4, and is extremely rare in practice.
There are 2 common encodings (one of which comes in two variants) which reduce the amount of wasted space (bytes of value 0) recorded to disk:
UTF-8
UTF-8 is by far the most common encoding found on the web, and also in text files used by programmers. The premise is simple: characters which appear in strict ASCII take up one byte with the high-order bit set to 0 (that is, with a value from 0 to 127), other characters use 2, 3, or 4 bytes with the high-order bit set to 1 (a value from 128 to 255). A valid strict ASCII text file is automatically a valid UTF-8 text file.
The Wikipedia article explains the algorithm in detail, but in short: multi-byte characters in UTF-8 are formatted so that the first byte indicates how many bytes will be used, and the remaining bytes cannot be mistaken for the first byte of a multi-byte character. That means UTF-8 is useful across unreliable transmission methods — if a single byte is lost, the character corresponding to that byte will be lost, but the rest of the text is not jumbled.
In addition, any system which was written with the assumption that all text was ASCII (which includes most command-line tools) will probably handle UTF-8 text without any problems, provided that they do not strip high-order bits or split up any adjacent multi-byte characters. (That is, they will be able to do things like search through the text or wrap it to a maximum line width for display without making it unreadable.) This makes it particularly convenient for programmers and system administrators, who frequently use tools which were written long ago and “think” in terms of pure ASCII text (or, at least, ASCII-based single-byte character mappings).
It is possibly important to remember that, contrary to popular belief, not every sequence of byte values is valid UTF-8 text. There are byte sequences which encode values which have no character mapping, byte sequences which encode values too large for the Unicode range, and byte sequences which encode ASCII characters — which would be readable but still invalid.
The algorithm for UTF-8 can actually handle the entire UCS character set, using up to 6 bytes per character for values outside the official Unicode mapping, and when the UTF-8 encoding was introduced, those additional values were part of the algorithm. By the official standard eventually set by the IETF RFC in 2003, UTF-8 is restricted to valid Unicode values, and therefore no more than 4 bytes per character.
UTF-16 (and UTF-16BE and UTF-16LE)
Much though “tl;dr” synopses are horrible, this section can be summarized as: “unless you are defining your own file type (so that only your program will ever need to read it) and will be storing a lot of text which does not use the latin character set, do not use UTF-16 because it is a mess and invites trouble”.
UTF-16 was — in Unicode 1.0 — the equivalent of UTF-32 in later versions, because all Unicode values used 2 bytes, meaning that recording two bytes per character was the simple, obvious thing to do. It was somewhat wasteful of space for most European languages, since it “wastes” a byte for any character in the ISO Latin-1 character mapping, but even in 1991 when Unicode 1.0 came out this was not an unreasonable strain on existing storage technology. The problems which eventually made UTF-16 unpopular were more subtle and varied.
First was the fact that there are two varieties of UTF-16. Some computers are “big-endian” (that is, the first byte in a multi-byte value is the byte which stores the larger portion of the value, the “big end”) and some are “little-endian”. (The terms are references to Gulliver’s Travels, and are traditional for describing this problem.) So by default, some computers “want” to write U+1234 as 0x1234, with the “big end” first (UTF-16BE) while others “want” to write it as 0x3412 with the “little end” first (UTF-16LE), and since U+3412 is just as valid a code point as U+1234, there is no automatic way to be sure whether a UTF-16 file from an unknown source was UTF-16BE or UTF-16LE.
In order to solve this problem, Unicode defined U+FEFF as a “Byte Order Mark” (BOM) which could be placed at the beginning of a UTF-16 text stream to show which one was in use. (Its character is defined as a “zero-width non-breaking space” — in other words, a character which is technically a space for the purposes of word-count or spell-checking, but takes up no space on the screen, and at which programs are not supposed to break up text for line-wrapping or layout purposes. Since this has no visible or analytical effect on the text at all, a correctly-interpreted BOM in a Unicode-supporting program does not alter the text and can even be safely included in UTF-8 text files where it is unnecessary.) Which solved the problem… except that the overwhelming majority of programs which used UTF-16 did not record a BOM in their files, regarding it as an unnecessary waste of space. As a result, most pure text editors which support UTF-16 have an option to force a file to open as either BE or LE.
When Unicode 2.0 increased the range of valid code points all the way to U+10FFFF, two bytes were no longer sufficient to cover all possible characters. UTF-16 was amended to use approximately the same trick as UTF-8 to extend its range. As it happened, no characters had yet been assigned to the range U+D800 to U+DFFF, and so this range was declared to be permanently unused; characters with code points above U+FFFF are recorded in UTF-16 as a pair of 2-byte values in this range. (More specifically, the first value will be in the range 0xD800 to 0xDBFF, and the second value will be in the range 0xDC00 to 0xDFFF; this gives 1024×1024 combinations, coincidentally the number of values from 0x010000 to 0x10FFFF.) As a result, “modern” UTF-16 is a variable-length encoding — most of the time, it uses two bytes per character, but sometimes uses four.
If a single byte is missed or deleted in transmission (or any odd number of bytes), the rest of the text is garbled, and unless an invalid combination like an unmatched U+D800 occurs, there is no way to detect this algorithmically. If multiple bytes are lost at random, the text will switch back and forth to and from gibberish.
Finally, and fatally in many cases, UTF-16 often chokes old programs which “think” in ASCII, which are often used by programmers. Unfortunately, a very large number of two-byte combinations which are valid UTF-16 are also valid ASCII, so programs which expect to be able to alter ASCII text for convenience can mangle UTF-16 text irreparably.
In particular, line break characters can be a problem with UTF-16 text. Tools such as Git often default to some sort of “auto-translation” mode when retrieving code files, but are not smart enough to catch on to multi-byte character encoding. A file which is converted to the Windows paragraph ending, CRLF, from (usually) the POSIX paragraph ending, LF, will cause the insertion of an extra byte, garbling all the characters in even-numbered paragraphs. Although it is possible to shut off a given tool’s auto-translation mode, it is much easier simply to avoid UTF-16 encoding in favor of UTF-8 from the start.
UTF-7
UTF-7 is primarily used in e-mail. You are unlikely to use it and it is listed here purely to head off questions. It records unaccented latin letters, numbers, and a few symbols directly as their ASCII equivalents, “+” as the sequence “+-”, and all other characters with a “+” followed by the base64-encoded UTF-16BE value of the character. This means that the entire text will consist of ASCII characters, thus conforming to MIME requirements. Since this is extremely wasteful of space without any particular benefit in terms of readability or formatting, it is generally unused as a file format.
4 notes
·
View notes
Text
Bitcoin Wallet Download
What is Bitcoin Core Wallet? The Bitcoin Core is a safe digital wallet which user may use to store, send and receive bitcoin. While using this budget a person can authorize dealings to remain a copy of the blockchain. Suitable with: Macintosh OS A Windows 7/8. x/10 Cpanel Few ARM chipsets (including Raspberry Pi V. one particular and /. 2) Be aware: Only Bitcoin can be residing in the Bitcoin Core pocket! Exactly how Much It Costs? The pocket is free to be able to get and use, on the other hand it�ll cost you bandwidth, and hard-drive space while well. You need to be able to give transaction fees to help send/receive bitcoin. Furthermore, a person are in order to set your own personal fees on a sliding range based on transaction top priority. Bitcoin-qt Download for Windows 10 up to help the bitcoin network like a full node Able for you to create QR codes to be able to receive payment The agreement system to get complete blockchain including any bitcoin financial transaction ever saved A dispersed ledger this is more as compared to 110GB in size Option blockchain where real bitcoin is not in make use of Circle alert system for you to inform end users about typically the latest bitcoin news Server scripting language to denote orders and enable several purchase parameters How to Add Foreign currency to the Pocket? To use this budget > download Bitcoin Core. Prior to downloading it the particular software, assure that your own system meets the needed conditions to run Bitcoin Core. Download Bitcoin Wallet recommended bottom requirements include: At the very least 145 GIGABITE storage living space Downloading amount capability regarding 500MB/day (15GB/month), and also 1-time 140GB down load the first moment you launch Bitcoin Primary Uploading speed of 5GB/day (150 GB/month) 1GB DODGE Laptop computer, Desktop, or perhaps agreeable ARM chipset Macintosh personal computer OS IN THIS HANDSET X, Windows 7/8. x/10, or maybe Linux os Acquire Bitcoin Core You possibly can down load the Bitcoin Key Wallet via Bitcoin. org Bitcoin Core Wallet Bitcoin Primary Wallet Open often the report > this for downloading the complete blockchain (which holds the historical past of former bitcoin transactions and it�s all around 100 GIGABYTE in size). Wallet Introduction Wallet Introduction Make certain you Encrypt your wallet > follow the prompts > Restart to finish the procedure. Bit coin Wallet for Windows , back up the wallet file on an external tough drive as well as USB flash drive. Your current wallet file (wallet. dat) stores the data for all your public and private secrets. download Bitcoin-qt wallet Click below Document > Proceed to �receiving addresses�. Having Bitcoin Street address Receiving Bitcoin Address You now are ready to accept bitcoin. Show this address with everyone you want to be given income through. The warning announcement pops up prompting anyone to check the Bitcoin Central Wallet. Confirmation appear up message Confirmation put up message You can track the transaction advance coming from the transactions tab. Deal board Transaction board Create a new bitcoin deal with per individual purposes and tag them accordingly. Head out back to your receiving addresses > make a new address using a label. Produce new Bitcoin Address Produce new Bitcoin Address Produce a brand new deal with > once again backup your wallet records. Fresh Receiving address Brand-new Getting address Let�s give 0. 01 to typically the new handle Bitcoin Transactions Bitcoin Orders If an individual are a service service as well as some sort of merchant in addition to agree to bitcoin, you are able to make the most of the �Request tab� to ask for a good particular sum. Using QR code it is simple to scan and even quickly exchange the volume. Request Bitcoin Repayment Ask Bitcoin Payment Mouse click �request payment� > QR code will create. Bitcoin Payment QR code Bitcoin Payment QR computer code Head out to the �send tab� > fill all the information who a person want to send this amount in order to. Sending Bitcoin Payment Sending Bitcoin Repayment Click the �send� option > enter in your own password Bitcoin Financial transaction Price Bitcoin Financial transaction Cost Finally, you get the subject matter of the applicable purchase expenses and the entire bitcoin deductions from the particular wallet balance. Just how Protected Is Bitcoin Major? Bitcoin Core Wallet Download Windows 10 gives a very high levels of privacy and safety measures. Users also use add-ons safety measures measures to help Bitcoin Main. Perfect privateness for receiving transactions Tough level of personal privacy intended for sent transactions Decentralized peer-to-peer networking Compatible with Tor Final Verdict In bottom line, right here is the only downside throughout regards to the timeframe especially while downloading the particular copy of the blockchain along with the interface. However, Bitcoin Key has continued in order to be amongst recommended bitcoin protocol for the quantity of communities. So let�s be aware what comes next.
1 note
·
View note
Text

I posted 26,998 times in 2022
That's 26,998 more posts than 2021!
99 posts created (0%)
26,899 posts reblogged (100%)
Blogs I reblogged the most:
@faggotgerardway
@fwippedowbit
@wisp-exe
@strange-aeons
@hiveswap
I tagged 2,271 of my posts in 2022
#fav art - 433 posts
#fave - 231 posts
#save - 116 posts
#toby talks - 63 posts
#for later - 45 posts
#me - 29 posts
#yeah - 28 posts
#juicecore - 24 posts
#so true - 22 posts
#what - 21 posts
Longest Tag: 139 characters
#also am i the only bench trio person who became a bench trio person cause no one liked clingy duo any more so i had to learn to like ranboo
My Top Posts in 2022:
#5
@wilburians is being a misogynist! on INTERNATIONAL WOMENS DAY!!!!
8 notes - Posted March 8, 2022
#4
Hello hello hello and welcome to:
Nep’s Downloading Homestuck Walk through!!!
im on desktop and i dont know how to make colored text on desktop so just pretend thats a rainbow!
also going to at @ @ghostdragoncookie because they needed help but feel free to use this whoever u are!
(also dropping the typing quirk for clarity cause maybe people want to download homestuck but dont have nepeta puns dictionary bookmarked for easy access)
OKAY SO WITHOUT FURTHER ADO: the ramblings of a teenage boy who just woke up from a three hour nap and also knows like 4 things about computers but just used brute force to get his way through it
Step one:
go here https://bambosh.github.io/unofficial-homestuck-collection/
Step two:
press Download and then download the file that corresponds to your operating system, i have windows so screenshots that will be included will be for windows. but i will learn how to use linux or mac if needed i am a servant to the people! and the people must read homestuck!
also make sure to put it in a place you can find easy that will be important later
Step three:
Downlaod the asset pack. Now this is the hard part, imo, because they say all asset packs are the same but not all work with all the computers. “but nep, that doesnt make any sense! why dont they just tell you what asset packs work for what computers?” and to that i say: thats the joy of homestuck! nothing works, about three things make sense, and we all just guess until it works out. so if your asking what asset pack to download, just start at the top and work your way down ig i dunno man thats what i did.
Step four:
Assuming you magically picked the right asset pack (and if you didnt dw there will be a trouble shooting thing at the bottom of this) you will go into your files and find homestuck!
Step five:
Unzip your files. How I understand for macs if you click on a file it automatically unzips itself. (why does it do that apple? whats the fuckin purpose?) I dont know for linux but once again if asked i will learn. and for windows theres a nifty button to press pictured below.
Step six:
OPENING HOMESTUCK!!!!!
so now you will go into actual homestuck and open it! process pictured below!!
first you want to make sure ur asset pack and hs are in the same place, that is just for ease of finding things later
See the full post
9 notes - Posted August 4, 2022
#3
https://at.tumblr.com/menalez/menalez-menalez-menalez-menalez-menalez/qmznj0qeio26
who tf r u and whyd u send me a random post abt a terf?
10 notes - Posted October 28, 2022
#2
Rowan/Toby/Nepeta | he/him | minor


See the full post
12 notes - Posted March 6, 2022
My #1 post of 2022

what r ur opinions on this photo
when i was young i used to go into a room that was as empty i could find and then i would spin around in circles for up to 45 minutes.
i think that carpet would be too damp and it would smell too bad for me to be able to do that.
16 notes - Posted March 8, 2022
Get your Tumblr 2022 Year in Review →
1 note
·
View note
Text
samp cheat download working HFOY%
💾 ►►► DOWNLOAD FILE 🔥🔥🔥🔥🔥 Source code of Grand Theft Auto San Andreas Multiplayer cheat that works on many servers and has lot of features. SA-MP (San Andreas Multiplayer) is a multiplayer mod for Grand Theft Auto San Andreas allowing users to play against each other over the internet or LAN. FlatCheat | SAMP Hacks | And Cheats ! Página Inicial. blackdiamond1; Thread; Jan 31, ; cheat cheats csgo; Replies: 0. 9 Work fast with our official CLI. Learn more. If nothing happens, download GitHub Desktop and try again. If nothing happens, download Xcode and try again. There was a problem preparing your codespace, please try again. It was usually used in conjunction with attdef. This program protected against various common cheats that were highly popular between the years I would not recommend using this today for anti-cheat purposes as it is fairly dated. I believe it could be updated. Notes for Docker: Docker automates some dependency building, this will hopefully make the binaries more compatible with future Linux distros. Fully compiled release builds are available here. Skip to content. This repository has been archived by the owner. It is now read-only. Star Version 2. Supported from License GPL This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. Branches Tags. Could not load branches. Could not load tags. Launching Xcode If nothing happens, download Xcode and try again. Launching Visual Studio Code Your codespace will open once ready. Latest commit. Git stats commits. Failed to load latest commit information. Fix Linux build with Boost 1. Oct 9, AppVeyor updates. Oct 26, Apr 29, Implement banned player tracker record ban evasion attempts Feb 4, Dockerfile update. Oct 7, Jan 31, View code. This is a full re-code from the ground up. Provides many new functions to the SA-MP game client. Hooks into main SA-MP network code to allow a seamless installation for server and client. DirectX and many game hooks to prevent advanced cheats. Verifies integrity of packets in the SA-MP network layer. Rudimentary thread analysis: Threads created by all modules were kept track of and monitored. Integration of the Dynamic Natives proof-of-concept. Easy-to-install server with vast documentation on new functions and callbacks. Many example Filterscripts showing functionality, easy to extend and implement in current gamemodes. Debugging counter-measures and advanced protection against software decompilation via the Enigma Protector. Advanced configuration to prevent sync bugs, control c-bug speed, switch reload, vehicle blips. Much much more About Version 2. Supported from Resources Readme. Releases No releases published. Packages 0 No packages published. Contributors 5. You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window.
1 note
·
View note
Text
Customize xscreensaver lock screen

Customize xscreensaver lock screen install#
Customize xscreensaver lock screen manual#
Customize xscreensaver lock screen full#
Customize xscreensaver lock screen password#
The option can be controlled in mpv's configuration file located in ~/.config/mpv/mpv.conf: The screensaver is always re-enabled when the player is paused. It turns off the screensaver at startup and turns it on again on exit. However, some applications do not support D-Bus or use another interfaces.īy default mpv uses the X11 Screen Saver extension (XSS). It is started automatically with xscreensaver, so most applications should properly disable the screensaver without additional configuration. Starting from version 5.45, the xscreensaver-systemd utility implements the D-Bus ScreenSaver interface. Tips and tricks Disable during media playback You can try to call the SwitchToGreeter method using dbus-send, but it may not work properly.
Customize xscreensaver lock screen password#
Note: If you use this to switch to an already-logged-in user, you might have to enter the password twice (once for LightDM, and once for the XScreenSaver dialog of the user you logged in to). You may want to set XScreenSaver's fade out time to 0. $ xss-lock -ignore-sleep - xscreensaver-command -lock Use the -ignore-sleep option because the suspend/hibernate events are already handled by xscreensaver-systemd. However, it does not handle other systemd signals such as loginctl lock-session. See xscreensaver-systemd(6) for more information It is started automatically with xscreensaver, no further action required. XScreenSaver ships with a small utility named xscreensaver-systemd, which handles the PrepareForSleep signal from systemd using D-Bus and automatically locks the screen on suspend and hibernate. To immediately trigger xscreensaver, if it is running, and lock the screen, execute the following command: See xscreensaver(1) § INSTALLING XSCREENSAVER ON KDE for more information.įor other environments, see Autostarting. Then logout and login again, and XScreenSaver should work properly now. ~/.config/systemd/user//nf ĮxecStart=/usr/bin/ksmserver -no-lockscreen To disable it, you need to enable systemd startup for KDE and then edit the rvice user unit: In KDE Plasma, screen saver and locker features are handled by ksmserver, which conflicts with XScreenSaver. In the Xfce, LXDE and LXQt environments, XScreenSaver is autostarted automatically if it is available - no further action is required.
Customize xscreensaver lock screen full#
See xscreensaver(1) for a full list of options. Tip: To start XScreenSaver without the splash screen, use the -no-splash switch. You can view a list of the available X resources in /usr/share/X11/app-defaults/XScreenSaver.ĭo not forget to reload the resource file after changes. ! You can use a comma-separated list of fonts to set a fallback font. If you are using a non-default theme, replace default with the name of your chosen theme in lower case, or use question mark ( ?) to affect all themes: The example below demonstrates changing some colors and fonts. You can customize themes using X resources. You can select a theme using xscreensaver-settings or by changing the dialogTheme option ( dialogTheme: themename in ~/.xscreensaver or using X resources: xscreensaver-auth.dialogTheme: themename). Starting from version 6.0, XScreenSaver comes with several pre-installed themes. Since at least XScreenSaver 5.22, there is another way to edit XScreenSaver's user configuration, using X resources. Global options are defined in /usr/share/X11/app-defaults/XScreenSaver.
Customize xscreensaver lock screen manual#
xscreensaver-settings writes the chosen configuration to ~/.xscreensaver, discarding any manual modifications to the file. Most options are configured on a user-by-user basis by running xscreensaver-settings.
Customize xscreensaver lock screen install#
3.2 User switching from the lock screenįor an Arch Linux branded experience, install the xscreensaver-arch-logo AUR package.

0 notes
Text
TOOL TUTORIAL #1
FFmpeg | Script 1
GIF GENERATION AND OPTIMIZATION
Tool type: Command Line tool
Operating systems: Mac, Windows, and Linux
Difficulty: Moderate to Advanced
Input: Video files (any video file format).


Installation
I recommend you install via Homebrew if you're on Mac or Linux by pasting this into your terminal (if/once Homebrew is installed):
brew install ffmpeg
Windows users or other users who don't want Homebrew can follow directions on the FFMPEG website.
Converting one video file to GIF
In your system shell (Powershell on Windows, Terminal on Mac) change directories to the location containing your MP4 file (or whatever video file type you have—just replace .mp4 in the script with .mkv or whatever extension you have). Use this command:
cd FilePathToYourMP4 ffmpeg -y -i input.mp4 -filter_complex "fps=18,smartblur=ls=-0.25,scale=540:-1:flags=lanczos,split [a][b];[a] palettegen=stats_mode=single [p];[b][p] paletteuse=new=1" output.gif
Explaining and altering the script
The script does the following to your the clip you want to turn into a GIF, input.mp4:
Generate a gif with 20 frames per second (fps=18 controls frames per second. Change the number to changes the FPS).
Sharpen each frame (smartblur=ls=-0.25 controls sharpening. Negative values between -1 and 0 sharpen the image).
Scale every frame in the gif down to a 500 pixels using the lanczos technique. (scale=540 controls scale. Change 500 to different numbers to scale up and down)
Generate a custom color pallet for every frame and overlay it on your gif as a filter (split [a][b];[a] palettegen=stats_mode=single [p];[b][p] paletteuse=new=1)
Generates and saves the resulting gif under the name output.gif.
NOTE: Video files inputs don't have to be .mp4. You can use .mkv, .mov, or any other video type.
Converting a folder of video files to GIF
Place all of your video clips into a folder called gifset1. Put an empty subfolder inside the gifset1 folder called gifs. Go to your system shell and copy and paste the following indented text:
Mac and Linux users:
cd ~/desktop/gifset1 for i in *.mp4; do ffmpeg -y -i "$i" -filter_complex "fps=18,smartblur=ls=-0.25,scale=540:-1:flags=lanczos,split [a][b];[a] palettegen=stats_mode=single [p];[b][p] paletteuse=new=1" gifs/${i%.*}.gif; done
Windows users:
cd ~desktop\gifset1 for i in *.mp4; do ffmpeg -y -i "$i" -filter_complex "fps=18,smartblur=ls=-0.25,scale=540:-1:flags=lanczos,split [a][b];[a] palettegen=stats_mode=single [p];[b][p] paletteuse=new=1" gifs\${i%.*}.gif; done
Once the process is finished running (your shell prompt will reappear allowing you to type in commands again) if you go to to the gifs subfolder in your gifset1 folder, you will find an optimized gif of every video file has been rendered.
Does this script run slowly for you?
The Palletegen function of this script may take a long time to run on certain computers. There is a faster script here you can try for very similar results.
3 notes
·
View notes
Text
Setting up cmake linux

#Setting up cmake linux how to
#Setting up cmake linux install
#Setting up cmake linux update
Some other relevant security options you may want to consider are PermitRootLogin, PasswordAuthentication, and PermitEmptyPasswords. You can configure ssh to use other ciphers, host key algorithms, and so on. The ecdh-* key exchange algorithms are FIPS compliant, but Visual Studio doesn't support them. The aes*-ctr algorithms are also FIPS compliant, but the implementation in Visual Studio isn't approved. Ssh-rsa is the only FIPS compliant host key algorithm VS supports. KexAlgorithms diffie-hellman-group-exchange-sha256,diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1 Edit (or add, if they don't exist) the following lines: Ciphers aes256-cbc,aes192-cbc,aes128-cbc,3des-cbc If you'd like the ssh server to start automatically when the system boots, enable it using systemctl: sudo systemctl enable ssh
#Setting up cmake linux install
On the Linux system, install and start the OpenSSH server: sudo apt install openssh-server To set up the SSH server on the remote system However, the instructions should be the same for any distro using a moderately recent version of OpenSSH. The examples in this article use Ubuntu 18.04 LTS with OpenSSH server version 7.6. For FIPS-140-2 compliance, Visual Studio only supports RSA keys. Some preparation is required to use a FIPS-compliant, cryptographically secure ssh connection between Visual Studio and your remote Linux system. This article is the FIPS-compliant version of the connection instructions in Connect to your remote Linux computer. This guide is applicable when you build CMake or MSBuild Linux projects in Visual Studio.
#Setting up cmake linux how to
Here's how to set up a secure, FIPS-compliant connection between Visual Studio and your remote Linux system. In Visual Studio 2019 version 16.5 and later, you can use a secure, FIPS-compliant cryptographic connection to your Linux system for remote development. Windows has validated support for FIPS-compliant cryptographic modules. Implementations of the standard are validated by NIST. government standard for cryptographic modules.
#Setting up cmake linux update
If you are starting the runner again or to update the runner, always pull the runner manually before using the following command to ensure you are always running the most up-to-date runner.Federal Information Processing Standard (FIPS) Publication 140-2 is a U.S. If this is the first time running the runner, it will pull the image. Use the pre-configured Docker command provided in Run step on the Runner installation dialog to run the runner. Use the crontab -e command to open your user account’s crontab file.Īppend the following entry 0 0 * * 0 docker system prune -afįor more details, refer to the crontab documentation.įor Workspace runners, visit Workspace settings > Workspace runners.įor Repository runners, visit Repository settings > Runners.įrom the Runner installation dialog, under System and architecture, select Linux Docker (x86_64). The schedule depends on the size of images you use, disk space available, and how often you run builds on a runner.įor example, do the following to clean up images once a week on Sunday at midnight: You can create a cron job using the command docker system prune -af to remove all unused images. We recommend setting up a process to automatically remove docker images to avoid running out of disk space. If there is an output other than 1, repeat Step 2 and ensure that /etc/nf is configured correctly.

0 notes
Text
Grep vmx proc cpuinfo

GREP VMX PROC CPUINFO HOW TO
GREP VMX PROC CPUINFO INSTALL
TX packets:2395178 errors:0 dropped:0 overruns:0 carrier:0 RX packets:8473303 errors:0 dropped:0 overruns:0 frame:0 UP BROADCAST RUNNING PROMISC MULTICAST MTU:1500 Metric:1 TX packets:1080664 errors:0 dropped:0 overruns:0 carrier:0 RX packets:4406929 errors:0 dropped:0 overruns:0 frame:0 UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 The eth0 device will no longer have an IP address the br0 device has the IP after bridging is operational.Ħ.Display the current TCP/IP network configurations to confirm the bridge network is created.īr0 Link encap:Ethernet HWaddr 00:30:48:32:E0:4E network-scripts]# vim ifcfg-eth0ĥ.Apply the new network settings by running the following command. network-scripts]# vim ifcfg-br0Ĥ.Edit the ifcfg-eth0 file and add BRIDGE=”br0”. ]# cd /etc/sysconfig/network-scripts/Ģ.Copy ifcfg-eth0 to ifcfg-br0 to create the bridge interface.ģ.Edit the ifcfg-br0 file and change the DEVICE line to DEVICE=”br0” and set TYPE=”Bridge”.
GREP VMX PROC CPUINFO INSTALL
Check your installation and manually install the bridge-util packages if necessary before continuing.ġ.Change directory to where the network scripts are located. These instructions assume that your host system has only one network interface, eth0.ĭepending on your installation, the bridge-util packages might be installed as part of another package. The following steps create a bridge interface, br0, and map it to the physical interface eth0 making your virtual appliances accessible from your local network. Refer to your KVM documentation if your KVM modules do not install properly.įor the virtual appliance to access the host system’s network, set up a bridge interface. If the KVM modules are not installed, your output will look similar to this: If an error occurs, details about that error are displayed.Ĭheck that the KVM modules are installed by running the lsmod command. These commands return no output unless an error has occurred. ~]# insmod lib/modules/KernelVersion/kermel/arch/x86/kvm/kvm-intel.ko ~]# insmod lib/modules/KernelVersion/kermel/arch/x86/kvm/kvm.ko To install KVM, run the following commands: Ivanti supports kernel modules version 2.6.18 and later. You can run these commands as root or by using sudo, if sudo is available on your system.
GREP VMX PROC CPUINFO HOW TO
This topic describes how to install KVM modules. The following table contains data regarding the Number of cores to be allocated to each KVM model:įor each KVM virtual appliance instance with 4 GB Memory and 4 CPU allocation, exceeding 5000 tunnels (Network Connect, Pulse Secure client ESP/SSL, or a combination of both) with 60 Mbps of bi-directional traffic may exhibit high CPU utilization and loss of throughput including disruption of the existing connections. Once your machine reboots, check that everything is configured correctly by running the kvm-ok command. After enabling this feature, you must turn your machine off and then on again for the change to take effect. You must also check that virtualization is enabled in your BIOS.
The cat command returns a result that contains the string vmx.
The egrep command returns a non-zero value.
Only administrators logged into the Ivanti Connect Secure or Ivanti Policy Secure console are informed of the pending shutdown.īefore proceeding, verify that your CPU supports virtualization by running one of the following commands: If you use this monitor mode to power on or off the virtual appliance, no logs are generated. This monitor mode can perform operations like powering on or off the virtual appliance. QEMU is an open source emulator that provides a monitor mode when using the KVM kernel module. You can run a Ivanti Connect Secure virtual appliance as a guest operating system on any Linux machine with KVM hypervisor support. A wide variety of guest operating systems work with KVM, including Linux, Windows, OpenBSD and others. Kernel-based Virtual Machine (KVM) is a virtualization solution for Linux on x86 hardware containing Intel VT or AMD-V virtualization extensions. Deploying Ivanti Virtual Appliance on Kernel-Based Virtual Machine About a Kernel-Based Virtual Machine

1 note
·
View note
Text
MicroK8s is a CNCF certified upstream Kubernetes deployment that runs entirely on your workstation or edge device. Being a snap it runs all Kubernetes services natively (i.e. no virtual machines) while packing the entire set of libraries and binaries needed. Installation is limited by how fast you can download a couple of hundred megabytes and the removal of MicroK8s leaves nothing behind Source: Ubuntu Page. CNCF runs the Certified Kubernetes Conformance Program to ensure conformance so that there is smooth interoperability from one Kubernetes installation to the next. Software conformance ensures that every vendor’s version of Kubernetes supports the required APIs, as do open source community versions Source: CNCF Site. In this guide we will get the following done together: Install Kubernetes cluster using MicroK8s Enable core Kubernetes addons such as dns and dashboard Deploy pods and adding new nodes Configure storage Enable logging, prometheus and Grafana monitoring Configure registry All we will need is a Linux Distribution with support for Snap and in this guide we are going to stick with CentOS 8. Let us begin. Step 1: Update Server and Install Snap To kick off on a clean and ready platform, we will update our server to get the latest patches and software, get Epel Repository added then get our snap package from Epel installed. Run the commands below to get this accomplished. sudo dnf install epel-release -y sudo dnf update sudo dnf -y install snapd Disable SELinux If you have SELinux in enforcing mode, turn it off or use Permissive mode. sudo setenforce 0 sudo sed -i 's/^SELINUX=.*/SELINUX=permissive/g' /etc/selinux/config Once the package has finished installing, the systemd unit that manages the main snap communication socket needs to be enabled as follows: sudo systemctl enable --now snapd.socket Furthermore, to enable classic snap support, enter the following to create a symbolic link between /var/lib/snapd/snap and /snap then add snap to PATH variable sudo ln -s /var/lib/snapd/snap /snap echo 'export PATH=$PATH:/var/lib/snapd/snap/bin' | sudo tee -a /etc/profile.d/mysnap.sh After that, either log out and back in again or restart your system to ensure snap’s paths are updated correctly. And snap will now be installed. To test it out, we can search for a package and see if it is working as expected: $ snap find microk8s Name Version Publisher Notes Summary microk8s v1.19.0 canonical✓ classic Lightweight Kubernetes for workstations and appliances Step 2: Install MicroK8s on CentOS 8 Now that our server is updated and Snap is installed, we are ready to fetch MicroK8s comfortably and begin utilizing it to test and run our applications the containers way. To get MicroK8s installed, run the simple snap command below and we will be set. Such is the beauty of Snappy. $ sudo snap install microk8s --classic microk8s v1.19.0 from Canonical✓ installed If you do not add the –classic switch, you will get an error. So kindly add it. To be able to run the microk8s command as a sudo user, you will have to add the user to the microk8s group then log out and login back. Add the user as illustrated below: sudo usermod -aG microk8s $USER sudo chown -f -R $USER ~/.kube Onc the permissions have been implemented, log out and login back in. After that we can view installed snaps $ snap list Name Version Rev Tracking Publisher Notes core 16-2.45.3.1 9804 latest/stable canonical✓ core microk8s v1.19.0 1668 latest/stable canonical✓ classic For the purposes of adding new nodes later, we will need to open ports on the server. This applies if you are running a firewall in your server. Add the ports as follows: sudo firewall-cmd --permanent --add-port=10255,12379,25000,16443,10250,10257,10259,32000/tcp sudo firewall-cmd --reload Step 3: Manage MicroK8s on CentOS 8 MicroK8s is now installed on our server and we are ready to roll.
To manage MicroK8s (i.e start, status, stop, enable, disable, list nodes etc), you simply do the following: #####Check Status##### $ microk8s status microk8s is running high-availability: no datastore master nodes: 127.0.0.1:19001 datastore standby nodes: none #####Stop MicroK8s##### $ microk8s stop stop of [microk8s.daemon-apiserver microk8s.daemon-apiserver-kicker microk8s.daemon-cluster-agent microk8s.daemon-containerd microk8s.daemon-contr…Stopped #####Start MicroK8s##### $ microk8s start Started. #####List MicroK8s Nodes##### $ microk8s kubectl get nodes NAME STATUS ROLES AGE VERSION master Ready 2m6s v1.19.0-34+1a52fbf0753680 #####Disable MicroK8s##### $ sudo snap disable microk8s #####Enable MicroK8s##### $ sudo snap enable microk8s Awesome stuff! Our MicroK8s has been installed and responding to our commands without complaints. Let us get onto the next step. Step 4: Deploy Pods and enable dashboard Here, we shall go ahead and deploy pods and enable the dashboard to have our work simplified with good visuals. Let us deploy a sample redis pod as follows: $ microk8s kubectl create deployment my-redis --image=redis deployment.apps/my-redis created List the pods deployed $ microk8s kubectl get pods --all-namespaces NAMESPACE NAME READY STATUS RESTARTS AGE kube-system calico-kube-controllers-847c8c99d-f7zd2 1/1 Running 2 3h48m kube-system calico-node-xxhwx 1/1 Running 2 3h48m default my-redis-56dcdd56-tlfpf 1/1 Running 0 70s And our recent redis pod is up and purring!! In case you would wish to log into the redis instance, proceed as illustrated below: $ microk8s kubectl exec -it my-redis-56dcdd56-tlfpf -- bash root@my-redis-56dcdd56-tlfpf:/data# To check logs of a pod, make sure you include its respective namespace because it only will check the “default” namespace if not provided. $ microk8s kubectl logs my-redis-56dcdd56-tlfpf -n default 1:C 14 Sep 2020 12:59:32.350 # oO0OoO0OoO0Oo Redis is starting oO0OoO0OoO0Oo 1:C 14 Sep 2020 12:59:32.350 # Redis version=6.0.8, bits=64, commit=00000000, modified=0, pid=1, just started 1:C 14 Sep 2020 12:59:32.350 # Warning: no config file specified, using the default config. In order to specify a config file use redis-server /path/to/redis.conf 1:M 14 Sep 2020 12:59:32.352 * Running mode=standalone, port=6379. 1:M 14 Sep 2020 12:59:32.352 # WARNING: The TCP backlog setting of 511 cannot be enforced because /proc/sys/net/core/somaxconn is set to the lower value of 128. 1:M 14 Sep 2020 12:59:32.352 # Server initialized 1:M 14 Sep 2020 12:59:32.352 # WARNING you have Transparent Huge Pages (THP) support enabled in your kernel. This will create latency and memory usage issues with Redis. To fix this issue run the command 'echo madvise > /sys/kernel/mm/transparent_hugepage/enabled' as root, and add it to your /etc/rc.local in order to retain the setting after a reboot. Redis must be restarted after THP is disabled (set to 'madvise' or 'never'). 1:M 14 Sep 2020 12:59:32.352 * Ready to accept connections Next, let us enable the dashboard and dns to enjoy the view of our workloads. Enable it as follows $ microk8s enable dns dashboard Enabling Kubernetes Dashboard Enabling Metrics-Server clusterrole.rbac.authorization.k8s.io/system:aggregated-metrics-reader created clusterrolebinding.rbac.authorization.k8s.io/metrics-server:system:auth-delegator created rolebinding.rbac.authorization.k8s.io/metrics-server-auth-reader created We will need a token to login to the Dashboard. To Fetch a token, issue the two commands below. $ token=$(microk8s kubectl -n kube-system get secret | grep default-token | cut -d " " -f1) $ microk8s kubectl -n kube-system describe secret $token Name: default-token-gnj26 Namespace: kube-system
Labels: Annotations: kubernetes.io/service-account.name: default kubernetes.io/service-account.uid: 40394cbe-7761-4de9-b49c-6d8df82aea32 Type: kubernetes.io/service-account-token Data ca.crt: 1103 bytes namespace: 11 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6InBOVTc3NVd5ZDJHT1FYRmhWZFJ5ZlBVbVpMRWN5M1BEVDdwbE9zNU5XTDgifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkZWZhdWx0LXRva2VuLWduajI2Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQubmFtZSI6ImRlZmF1bHQiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI0MDM5NGNiZS03NzYxLTRkZTktYjQ5Yy02ZDhkZjgyYWVhMzIiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6a3ViZS1zeXN0ZW06ZGVmYXVsdCJ9.vHqwKlMGX650dTuChwYWsPYZFH7zRhRjuh-BEPtgYYPfrayKU08DSC5v3CixkrZH-wXZydOPit50H5SfCZPwY1TqDNCFgbz--0GnB7GhgwSoK4laXpr42Al7EBgbMWfUEAtnWXVkObUYzF31Sfhac2AnPIBp2kFlqJt8M03uoperJuFLl5x-fDacGrcXTQqvY2m5K1oE4zE38vtaJXdzgNfBMbtUrMneihoFczzOzwPLxzJJ4eZ7vAz1svG6JHO5PDDYbV0gded0egoLQkhu4Saavf8ILUjupJdYywA2VCqB6ERrrElMBHs5tYfckfyi4f6eR59_EZkf7-neCDWTAg Copy the token and save it in a safe place. Next, you need to connect to the dashboard service. While the MicroK8s snap will have an IP address on your local network (the Cluster IP of the kubernetes-dashboard service), you can also reach the dashboard by forwarding its port to a free one on your host with: microk8s kubectl port-forward -n kube-system service/kubernetes-dashboard --address 0.0.0.0 30560:443 Note that we have added –address 0.0.0.0 so that it can be reachable from any IP instead of locally (127.0.0.1) on the server. You will now be able to access the dashboard via port 30560. Make sure to enable this port on your firewall in case you have it setup in your environment. sudo firewall-cmd --permanent --add-port=30560/tcp sudo firewall-cmd --reload Now open your browser and point it to the ip or FQDN of your server. That is https://[ip or FQDN]:30560. And the following login page should be displayed. You will notice it needs either a token or Kubeconfig file. We already generated a token as above (Fetch token). Simply copy it and paste it on the login page. Paste the Token And you should be ushered in Step 5: Add Nodes to your Cluster So far, we have been working on a sigle node (server) and if you would wish to scale and distribute your applications on two or more nodes (servers), then this will get your there. To add another node to your cluster, you simply need to install Snap and MicroK8S on it as it has already been covered in Step 1 and Step 2. Follow Step 1 and Step 2 on your new CentOS 8 server then continue below. If Firewalld is running, allow ports node-01 ~ $ export OPENSSL_CONF=/var/lib/snapd/snap/microk8s/current/etc/ssl/openssl.cnf node-01 ~ $ sudo firewall-cmd --add-port=25000,10250,10255/tcp --permanent node-01 ~ $ sudo firewall-cmd --reload On the master Node (The one we installed first), execute the following commands to get our token and join command $ microk8s add-node From the node you wish to join to this cluster, run the following: microk8s join 172.26.24.237:25000/dbb2fa9e23dfbdda83c8cb2ae53eaa53 As you can observe from above, we now have the command to run on our worker node to join the cluster. Without hesitating, copy the command, log into your worker node and execute it as shown below: On New Node, execute the following commands node-01 ~ $ microk8s join 172.26.24.237:25000/dbb2fa9e23dfbdda83c8cb2ae53eaa53 Contacting cluster at 172.26.16.92 Waiting for this node to finish joining the cluster. .. Step 6: Configure Storage MicroK8s comes with a built-in storage that just needs to be enabled. To enable the storage, add /lib86 directory to the path of the LD_LIBRARY_PATH environment variable then enable the storage as below on the master node: $ export LD_LIBRARY_PATH="$LD_LIBRARY_PATH:/lib64"
$ microk8s enable storage deployment.apps/hostpath-provisioner created storageclass.storage.k8s.io/microk8s-hostpath created serviceaccount/microk8s-hostpath created clusterrole.rbac.authorization.k8s.io/microk8s-hostpath created clusterrolebinding.rbac.authorization.k8s.io/microk8s-hostpath created Storage will be available soon To check if storage has been enabled, we should check our pods and ensure that hostpath-provisioner pod has been started. $ microk8s kubectl get pods --all-namespaces NAMESPACE NAME READY STATUS RESTARTS AGE kube-system kubernetes-dashboard-7ffd448895-ht2j2 1/1 Running 2 22h kube-system dashboard-metrics-scraper-6c4568dc68-p7q6t 1/1 Running 2 22h kube-system metrics-server-8bbfb4bdb-mgddj 1/1 Running 2 22h kube-system coredns-86f78bb79c-58sbs 1/1 Running 2 22h kube-system calico-kube-controllers-847c8c99d-j84p5 1/1 Running 2 22h kube-system calico-node-zv994 1/1 Running 2 21h kube-system hostpath-provisioner-5c65fbdb4f-llsnl 1/1 Running 0 71s
0 notes