#public-key cryptography
Explore tagged Tumblr posts
Text
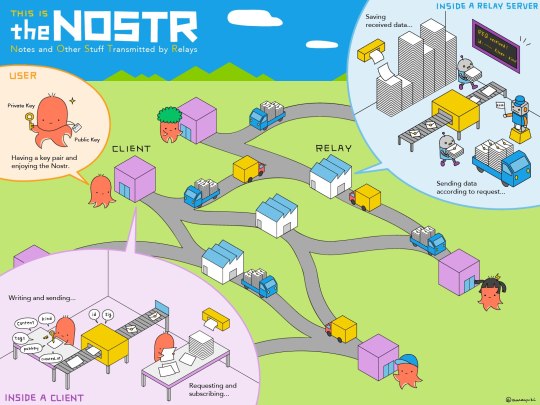
GUIA completo NOSTR
GUIA completo NOSTR: o que é, como surgiu e como usar o protocolo que descentraliza REDES SOCIAIS! Area Bitcoin – 08 ago 2023 PARTES DO VÍDEO: 00:00 – O que é e como surgiu o NOSTR 03:58 – Como NOSTR funciona (relays) 06:58 – NOSTR e Bitcoin: o futuro da internet 08:24 – Como criar uma conta no Damus 11:52 – O que são zaps e como enviar bitcoin via Lighting no NOSTR Nostr é a sigla de…
View On WordPress
#NOSTR zaps lightningnetwork#btc Bitcoin#carteira Lightning ZDB#censorship-resistant social media#chave pública nome de usuário#chave privada senha de sua conta#como surgiu e como usar o protocolo que descentraliza REDES SOCIAIS!#conta no Damus#decentralized#disponível sistemas iOS iPhone#download aplicativo Damus App#enables global#espécie de Twitter descentralizado#fruto da obra brasileiro desenvolvedor#GitHub#GUIA completo NOSTR: o que é#HTTP or TCP-IP#HTTP TCP-IP#livecoins#NOSTR 03:58 relays#Nostr sigla Notes and Other Stuff Transmitted by Relays notas e outras coisas transmitidas por relays#o futuro da internet#primeira aplicação criação do Damus App#protocol open standard#protocolo padrão aberto#pseudônimo de fiatjaf. Luciano Rocha - CriptoFácil#public-key cryptography#Satoshi Bitcoin#sistema de chaves do BTC#site Astral Ninja
0 notes
Text
How to design a tech regulation
TONIGHT (June 20) I'm live onstage in LOS ANGELES for a recording of the GO FACT YOURSELF podcast. TOMORROW (June 21) I'm doing an ONLINE READING for the LOCUS AWARDS at 16hPT. On SATURDAY (June 22) I'll be in OAKLAND, CA for a panel (13hPT) and a keynote (18hPT) at the LOCUS AWARDS.

It's not your imagination: tech really is underregulated. There are plenty of avoidable harms that tech visits upon the world, and while some of these harms are mere negligence, others are self-serving, creating shareholder value and widespread public destruction.
Making good tech policy is hard, but not because "tech moves too fast for regulation to keep up with," nor because "lawmakers are clueless about tech." There are plenty of fast-moving areas that lawmakers manage to stay abreast of (think of the rapid, global adoption of masking and social distancing rules in mid-2020). Likewise we generally manage to make good policy in areas that require highly specific technical knowledge (that's why it's noteworthy and awful when, say, people sicken from badly treated tapwater, even though water safety, toxicology and microbiology are highly technical areas outside the background of most elected officials).
That doesn't mean that technical rigor is irrelevant to making good policy. Well-run "expert agencies" include skilled practitioners on their payrolls – think here of large technical staff at the FTC, or the UK Competition and Markets Authority's best-in-the-world Digital Markets Unit:
https://pluralistic.net/2022/12/13/kitbashed/#app-store-tax
The job of government experts isn't just to research the correct answers. Even more important is experts' role in evaluating conflicting claims from interested parties. When administrative agencies make new rules, they have to collect public comments and counter-comments. The best agencies also hold hearings, and the very best go on "listening tours" where they invite the broad public to weigh in (the FTC has done an awful lot of these during Lina Khan's tenure, to its benefit, and it shows):
https://www.ftc.gov/news-events/events/2022/04/ftc-justice-department-listening-forum-firsthand-effects-mergers-acquisitions-health-care
But when an industry dwindles to a handful of companies, the resulting cartel finds it easy to converge on a single talking point and to maintain strict message discipline. This means that the evidentiary record is starved for disconfirming evidence that would give the agencies contrasting perspectives and context for making good policy.
Tech industry shills have a favorite tactic: whenever there's any proposal that would erode the industry's profits, self-serving experts shout that the rule is technically impossible and deride the proposer as "clueless."
This tactic works so well because the proposers sometimes are clueless. Take Europe's on-again/off-again "chat control" proposal to mandate spyware on every digital device that will screen everything you upload for child sex abuse material (CSAM, better known as "child pornography"). This proposal is profoundly dangerous, as it will weaken end-to-end encryption, the key to all secure and private digital communication:
https://www.theguardian.com/technology/article/2024/jun/18/encryption-is-deeply-threatening-to-power-meredith-whittaker-of-messaging-app-signal
It's also an impossible-to-administer mess that incorrectly assumes that killing working encryption in the two mobile app stores run by the mobile duopoly will actually prevent bad actors from accessing private tools:
https://memex.craphound.com/2018/09/04/oh-for-fucks-sake-not-this-fucking-bullshit-again-cryptography-edition/
When technologists correctly point out the lack of rigor and catastrophic spillover effects from this kind of crackpot proposal, lawmakers stick their fingers in their ears and shout "NERD HARDER!"
https://memex.craphound.com/2018/01/12/nerd-harder-fbi-director-reiterates-faith-based-belief-in-working-crypto-that-he-can-break/
But this is only half the story. The other half is what happens when tech industry shills want to kill good policy proposals, which is the exact same thing that advocates say about bad ones. When lawmakers demand that tech companies respect our privacy rights – for example, by splitting social media or search off from commercial surveillance, the same people shout that this, too, is technologically impossible.
That's a lie, though. Facebook started out as the anti-surveillance alternative to Myspace. We know it's possible to operate Facebook without surveillance, because Facebook used to operate without surveillance:
https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3247362
Likewise, Brin and Page's original Pagerank paper, which described Google's architecture, insisted that search was incompatible with surveillance advertising, and Google established itself as a non-spying search tool:
http://infolab.stanford.edu/pub/papers/google.pdf
Even weirder is what happens when there's a proposal to limit a tech company's power to invoke the government's powers to shut down competitors. Take Ethan Zuckerman's lawsuit to strip Facebook of the legal power to sue people who automate their browsers to uncheck the millions of boxes that Facebook requires you to click by hand in order to unfollow everyone:
https://pluralistic.net/2024/05/02/kaiju-v-kaiju/#cda-230-c-2-b
Facebook's apologists have lost their minds over this, insisting that no one can possibly understand the potential harms of taking away Facebook's legal right to decide how your browser works. They take the position that only Facebook can understand when it's safe and proportional to use Facebook in ways the company didn't explicitly design for, and that they should be able to ask the government to fine or even imprison people who fail to defer to Facebook's decisions about how its users configure their computers.
This is an incredibly convenient position, since it arrogates to Facebook the right to order the rest of us to use our computers in the ways that are most beneficial to its shareholders. But Facebook's apologists insist that they are not motivated by parochial concerns over the value of their stock portfolios; rather, they have objective, technical concerns, that no one except them is qualified to understand or comment on.
There's a great name for this: "scalesplaining." As in "well, actually the platforms are doing an amazing job, but you can't possibly understand that because you don't work for them." It's weird enough when scalesplaining is used to condemn sensible regulation of the platforms; it's even weirder when it's weaponized to defend a system of regulatory protection for the platforms against would-be competitors.
Just as there are no atheists in foxholes, there are no libertarians in government-protected monopolies. Somehow, scalesplaining can be used to condemn governments as incapable of making any tech regulations and to insist that regulations that protect tech monopolies are just perfect and shouldn't ever be weakened. Truly, it's impossible to get someone to understand something when the value of their employee stock options depends on them not understanding it.
None of this is to say that every tech regulation is a good one. Governments often propose bad tech regulations (like chat control), or ones that are technologically impossible (like Article 17 of the EU's 2019 Digital Single Markets Directive, which requires tech companies to detect and block copyright infringements in their users' uploads).
But the fact that scalesplainers use the same argument to criticize both good and bad regulations makes the waters very muddy indeed. Policymakers are rightfully suspicious when they hear "that's not technically possible" because they hear that both for technically impossible proposals and for proposals that scalesplainers just don't like.
After decades of regulations aimed at making platforms behave better, we're finally moving into a new era, where we just make the platforms less important. That is, rather than simply ordering Facebook to block harassment and other bad conduct by its users, laws like the EU's Digital Markets Act will order Facebook and other VLOPs (Very Large Online Platforms, my favorite EU-ism ever) to operate gateways so that users can move to rival services and still communicate with the people who stay behind.
Think of this like number portability, but for digital platforms. Just as you can switch phone companies and keep your number and hear from all the people you spoke to on your old plan, the DMA will make it possible for you to change online services but still exchange messages and data with all the people you're already in touch with.
I love this idea, because it finally grapples with the question we should have been asking all along: why do people stay on platforms where they face harassment and bullying? The answer is simple: because the people – customers, family members, communities – we connect with on the platform are so important to us that we'll tolerate almost anything to avoid losing contact with them:
https://locusmag.com/2023/01/commentary-cory-doctorow-social-quitting/
Platforms deliberately rig the game so that we take each other hostage, locking each other into their badly moderated cesspits by using the love we have for one another as a weapon against us. Interoperability – making platforms connect to each other – shatters those locks and frees the hostages:
https://www.eff.org/deeplinks/2021/08/facebooks-secret-war-switching-costs
But there's another reason to love interoperability (making moderation less important) over rules that require platforms to stamp out bad behavior (making moderation better). Interop rules are much easier to administer than content moderation rules, and when it comes to regulation, administratability is everything.
The DMA isn't the EU's only new rule. They've also passed the Digital Services Act, which is a decidedly mixed bag. Among its provisions are a suite of rules requiring companies to monitor their users for harmful behavior and to intervene to block it. Whether or not you think platforms should do this, there's a much more important question: how can we enforce this rule?
Enforcing a rule requiring platforms to prevent harassment is very "fact intensive." First, we have to agree on a definition of "harassment." Then we have to figure out whether something one user did to another satisfies that definition. Finally, we have to determine whether the platform took reasonable steps to detect and prevent the harassment.
Each step of this is a huge lift, especially that last one, since to a first approximation, everyone who understands a given VLOP's server infrastructure is a partisan, scalesplaining engineer on the VLOP's payroll. By the time we find out whether the company broke the rule, years will have gone by, and millions more users will be in line to get justice for themselves.
So allowing users to leave is a much more practical step than making it so that they've got no reason to want to leave. Figuring out whether a platform will continue to forward your messages to and from the people you left there is a much simpler technical matter than agreeing on what harassment is, whether something is harassment by that definition, and whether the company was negligent in permitting harassment.
But as much as I like the DMA's interop rule, I think it is badly incomplete. Given that the tech industry is so concentrated, it's going to be very hard for us to define standard interop interfaces that don't end up advantaging the tech companies. Standards bodies are extremely easy for big industry players to capture:
https://pluralistic.net/2023/04/30/weak-institutions/
If tech giants refuse to offer access to their gateways to certain rivals because they seem "suspicious," it will be hard to tell whether the companies are just engaged in self-serving smears against a credible rival, or legitimately trying to protect their users from a predator trying to plug into their infrastructure. These fact-intensive questions are the enemy of speedy, responsive, effective policy administration.
But there's more than one way to attain interoperability. Interop doesn't have to come from mandates, interfaces designed and overseen by government agencies. There's a whole other form of interop that's far nimbler than mandates: adversarial interoperability:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
"Adversarial interoperability" is a catch-all term for all the guerrilla warfare tactics deployed in service to unilaterally changing a technology: reverse engineering, bots, scraping and so on. These tactics have a long and honorable history, but they have been slowly choked out of existence with a thicket of IP rights, like the IP rights that allow Facebook to shut down browser automation tools, which Ethan Zuckerman is suing to nullify:
https://locusmag.com/2020/09/cory-doctorow-ip/
Adversarial interop is very flexible. No matter what technological moves a company makes to interfere with interop, there's always a countermove the guerrilla fighter can make – tweak the scraper, decompile the new binary, change the bot's behavior. That's why tech companies use IP rights and courts, not firewall rules, to block adversarial interoperators.
At the same time, adversarial interop is unreliable. The solution that works today can break tomorrow if the company changes its back-end, and it will stay broken until the adversarial interoperator can respond.
But when companies are faced with the prospect of extended asymmetrical war against adversarial interop in the technological trenches, they often surrender. If companies can't sue adversarial interoperators out of existence, they often sue for peace instead. That's because high-tech guerrilla warfare presents unquantifiable risks and resource demands, and, as the scalesplainers never tire of telling us, this can create real operational problems for tech giants.
In other words, if Facebook can't shut down Ethan Zuckerman's browser automation tool in the courts, and if they're sincerely worried that a browser automation tool will uncheck its user interface buttons so quickly that it crashes the server, all it has to do is offer an official "unsubscribe all" button and no one will use Zuckerman's browser automation tool.
We don't have to choose between adversarial interop and interop mandates. The two are better together than they are apart. If companies building and operating DMA-compliant, mandatory gateways know that a failure to make them useful to rivals seeking to help users escape their authority is getting mired in endless hand-to-hand combat with trench-fighting adversarial interoperators, they'll have good reason to cooperate.
And if lawmakers charged with administering the DMA notice that companies are engaging in adversarial interop rather than using the official, reliable gateway they're overseeing, that's a good indicator that the official gateways aren't suitable.
It would be very on-brand for the EU to create the DMA and tell tech companies how they must operate, and for the USA to simply withdraw the state's protection from the Big Tech companies and let smaller companies try their luck at hacking new features into the big companies' servers without the government getting involved.
Indeed, we're seeing some of that today. Oregon just passed the first ever Right to Repair law banning "parts pairing" – basically a way of using IP law to make it illegal to reverse-engineer a device so you can fix it.
https://www.opb.org/article/2024/03/28/oregon-governor-kotek-signs-strong-tech-right-to-repair-bill/
Taken together, the two approaches – mandates and reverse engineering – are stronger than either on their own. Mandates are sturdy and reliable, but slow-moving. Adversarial interop is flexible and nimble, but unreliable. Put 'em together and you get a two-part epoxy, strong and flexible.
Governments can regulate well, with well-funded expert agencies and smart, adminstratable remedies. It's for that reason that the administrative state is under such sustained attack from the GOP and right-wing Dems. The illegitimate Supreme Court is on the verge of gutting expert agencies' power:
https://www.hklaw.com/en/insights/publications/2024/05/us-supreme-court-may-soon-discard-or-modify-chevron-deference
It's never been more important to craft regulations that go beyond mere good intentions and take account of adminsitratability. The easier we can make our rules to enforce, the less our beleaguered agencies will need to do to protect us from corporate predators.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/06/20/scalesplaining/#administratability

Image: Noah Wulf (modified) https://commons.m.wikimedia.org/wiki/File:Thunderbirds_at_Attention_Next_to_Thunderbird_1_-_Aviation_Nation_2019.jpg
CC BY-SA 4.0 https://creativecommons.org/licenses/by-sa/4.0/deed.en
#pluralistic#cda#ethan zuckerman#platforms#platform decay#enshittification#eu#dma#right to repair#transatlantic#administrability#regulation#big tech#scalesplaining#equilibria#interoperability#adversarial interoperability#comcom
99 notes
·
View notes
Text
So, I am away from computer for four days for a really cool event and I come back and in the mean time they maybe found a polynomial quantum attack against Learning With Errors, a lattice problem? (https://eprint.iacr.org/2024/555) If this paper is correct then this is some serious breaking news shit, because lattices are like the main candidate for quantum-secure public key cryptography. (there are others but they are much less practical and for other types there have also been attacks) I mean, this paper seems to attack just a particular setting, is very impractical and does not work for schemes that are actually proposed, but an existing impractical attack often signals the way for more practical attacks. So, if it is not a false alarm, this is pretty big. It could signal the attackability of lattice schemes and undermine the trust in them. And it takes a long time to move to a new standard. Oh well. I guess we have to wait for experts to check the paper for mistakes before we can say anything.
75 notes
·
View notes
Text
annoyingly the most influential thing in my head from Murderbot is the Feed. The Feed is so appealing as a concept. A universally comprehensible and widely accessible mesh-based standard for mixed machine and human communication with a reliable subscription service, that has a ton of things publishing constantly by default but with a robust (assuming no rogue antisocial biological hypercomputers) cryptographic system for secret data. The Feed very clearly can scale up to an entire space station network or down to one person and their accoutrements forming a personal area network.
Some kind of hierarchical MQTT implemented on a mesh network with public key cryptography could get you so close if you just standardized ways to get the MQTT schema of any given endpoint. After that it's all dashboarding. Publish as much or as little information as you want and allow any given device to access that data and respond to it.
Some of this is probably leftovers from $PREVJOB. When I was doing industrial automation our entire fleet of devices lived on a strict schema under one MQTT server that I had complete read/write for so by doing clever subscriptions I could sample anything from a temperature reading from a single appliance in the back of the restaurant I was standing in to accumulating the overall power draw of every single business we were working with all at once.
On more than one occasion something silently broke and I drove up near the back of a facility in my car where I knew the IoT gateway was, connected to our local IoT network over wifi, fixed the issue, and left without telling anyone.
Unfortunately if the Feed existed people like me would make extremely annoying endpoints. To be fair canonically the Feed is absolute dogshit unless you have an Adblock. So really it would be exactly the same as in the books.
148 notes
·
View notes
Text
Still struggling with insomnia so I did more research for PierMesh. I want to keep the code base simple and consistent so I'm looking at using python for the one board/transceiver only setup for mobile users. The main issue here is that unless something changes we cannot use the serial connection without modifying the code significantly on a mobile device running ios/android.
I was gonna say oh well that means we use bluetooth because the http api has no authentication mechanism but since this research is about single user mode I think that's okay because you still have to login to the wifi the board provides with a key you can set via the meshtastic provided bluetooth interface.
That all said here's the plan: write a small adapter js lib to interact with the http endpoint and connect that into the existing architecture so that with some flags it will run in browser with Pyodide/web workers. I should be able to serve this right off the transceiver itself by making some firmware modifications.
So for some use cases I've figured out the single board setup but for people serving public infrastructure to multiple people they will need to wait a bit as I'll have to devise something clever for multi-user setup authentication. I have some ideas to this end but nothing elegant yet. Maybe certain nodes can provide cryptography operations hmm.
13 notes
·
View notes
Text
The Philosophy Behind Bitcoin

Introduction
In the world of finance, few innovations have sparked as much intrigue and debate as Bitcoin. But beyond its role as a digital currency, Bitcoin embodies a profound philosophy that challenges traditional financial systems and proposes a new paradigm for economic freedom. Understanding the philosophy behind Bitcoin is essential to grasp its potential impact on our world.
The Origins of Bitcoin
In 2008, amid the global financial crisis, a mysterious figure known as Satoshi Nakamoto published the Bitcoin whitepaper. This document outlined a revolutionary idea: a decentralized digital currency that operates without the need for a central authority. The financial turmoil of the time, characterized by bank failures and government bailouts, underscored the need for a system that could function independently of traditional financial institutions.
Core Philosophical Principles
Decentralization-Decentralization lies at the heart of Bitcoin’s philosophy. Unlike traditional financial systems that rely on centralized authorities such as banks and governments, Bitcoin operates on a decentralized network of computers (nodes). Each node maintains a copy of the blockchain, Bitcoin's public ledger, ensuring that no single entity has control over the entire network. This decentralization is crucial for maintaining the integrity and security of the system, as it prevents any one party from manipulating the currency or its underlying data.
Trustlessness-Bitcoin's trustless nature is another fundamental principle. In traditional financial systems, trust is placed in intermediaries like banks and payment processors to facilitate transactions. Bitcoin eliminates the need for these intermediaries by using blockchain technology, where transactions are verified by network nodes through cryptography. This system ensures that transactions are secure and reliable without requiring trust in any third party.
Transparency-The transparency of Bitcoin’s blockchain is a key philosophical aspect. Every transaction that has ever occurred on the Bitcoin network is recorded on the blockchain, which is publicly accessible. This transparency allows anyone to verify transactions and ensures accountability. However, while the ledger is public, the identities of the individuals involved in transactions remain pseudonymous, balancing transparency with privacy.
Immutability-Immutability is the concept that once a transaction is recorded on the blockchain, it cannot be altered or deleted. This is achieved through cryptographic hashing and the decentralized nature of the network. Immutability ensures the integrity of the blockchain, making it a reliable and tamper-proof record of transactions. This principle is crucial for maintaining trust in the system, as it prevents fraudulent activities and data corruption.
Financial Sovereignty-Bitcoin empowers individuals by giving them full control over their own money. In traditional financial systems, access to funds can be restricted by banks or governments. Bitcoin, however, allows users to hold and transfer funds without relying on any central authority. This financial sovereignty is particularly valuable in regions with unstable economies or oppressive governments, where individuals may face restrictions on their financial freedom.
The Ideological Spectrum
Bitcoin’s philosophy is deeply rooted in libertarian values, emphasizing personal freedom and minimal government intervention. It also draws inspiration from the cypherpunk movement, a group of activists advocating for privacy-enhancing technologies to promote social and political change. These ideological influences shape Bitcoin's emphasis on decentralization, privacy, and individual empowerment.
Real-World Applications and Challenges
Bitcoin's philosophy extends beyond theory into practical applications. It is used for various purposes, from everyday transactions to a store of value akin to digital gold. However, this revolutionary system also faces challenges. Regulatory issues, scalability concerns, and environmental impact are some of the hurdles that need addressing to realize Bitcoin’s full potential.
Conclusion
The philosophy behind Bitcoin is a radical departure from traditional financial systems. Its principles of decentralization, trustlessness, transparency, immutability, and financial sovereignty offer a new vision for economic freedom and integrity. As Bitcoin continues to evolve, its underlying philosophy will play a crucial role in shaping its future and potentially transforming the global financial landscape.
Call to Action
Explore more about Bitcoin and consider its implications for your own financial freedom. Engage with the community, stay informed, and think critically about the role Bitcoin can play in our economic future. Let’s continue the journey of understanding and embracing the Bitcoin revolution together.
#Bitcoin#Cryptocurrency#FinancialFreedom#Decentralization#Blockchain#DigitalCurrency#CryptoPhilosophy#SatoshiNakamoto#Cypherpunk#FinancialSovereignty#BitcoinRevolution#CryptoCommunity#DigitalEconomy#TechInnovation#FutureOfFinance#EconomicFreedom#CryptoEducation#BitcoinPhilosophy#BlockchainTechnology#financial education#financial empowerment#financial experts#finance#unplugged financial#globaleconomy
6 notes
·
View notes
Text
Pretty Good Privacy: Software that encrypts and decrypts messages, for transmission over the Internet, using public-key cryptography.
Pretty Good Pronouns: A set of pronouns that can be considered reasonably adequate for speech in most cases.
Pretty Gender Privacy: Modes of fashionable dress that create an androgynous appearance.
Pretty Gender Pronouns: ve/vis/vim. They look neat.
Preferred Good Privacy: Whatever adequate crypto scheme you like.
Preferred Good Pronouns: The high-quality and elegant pronoun scheme you prefer.
Preferred Gender Privacy: What level of openness around gender you want in environments you occupy.
Preferred Gender Pronouns: The set of pronouns that an individual wants others to use in order to reflect that person's gender identity.
40 notes
·
View notes
Text
Queer fiction, day 2/30
Since I mentioned it yesterday, let's talk about Widdershins, which is book one of the Whyborne and Griffin books. There are eleven in total, but they're in a series such that you kind of have to read in order, so I'm going to talk about them as a group.

I only have these as ebooks right now, so I'm gonna hotlink to goodreads for the cover. Hopefully that works.
Okay, so the plot. Let's start by saying these do have a plot. Set in a very gothic town called Widdershins, in Massachusetts (just down the road from Arkham, it seems). As places go, it's very Night Vale--people keep to themselves and don't make eye contact if they're out after dark; the city's museum was designed by a man who slowly went mad during the work; everyone worships at a church called First Esoteric, which has some rather non-standard ritual practices.
The books are set around 1900. At the outset, we meet Dr. Percival Endicott Whyborne (he goes by Whyborne, which makes sense). He's highly educated, a philologist (someone who studies the history of languages). He speaks something like thirteen languages himself, and is also interested in cryptography, so it makes sense that when a private eye named Griffin Flaherty is referred to the museum with an occult, encyphered book, Whyborne is the person who's asked to help him. Together, they investigate a secret brotherhood and also fall in love.
I love a bunch of things about these books: the side characters are excellent; the sense of place (for a place that doesn't exist!) is extremely strong, and it's a funny, creepy place; the way the main characters get a chance to grow, both personally and in their relationship across all the books (unusual to find a series with so many entries in this genre); the explicit ways that Hawk deals with and subverts the ideas of "other" in Lovecraftian fiction.
Key quote: "Although the public areas of the museum were designed to give the appearance of a neat and orderly progression through history, the rest of the building exemplified chaos. Storerooms burrowed deep into the earth, while various wings sprawled off in every direction. The library was a literal labyrinth, and shortly after I'd first been hired, I'd found myself obliged to cross the flat roof of one of the wings as the most direct route from one department to another. Even though the museum was less than forty years old, there were rumors of lost storerooms and offices, and I did not doubt the possibility."
These books have a lot of sex in them, so be forewarned. When I read the first book, I found the use of euphemism in these a little grating to the inner ear ("my length" and suchlike), but over the course of the books I came to appreciate the voice. Then I read all the books and turned into a tiny eldrich creature myself.
10/10 for them.
#pride#lgbtq fiction#book reviews#thirty days of books#queer books#queer romance#whyborne and griffin
22 notes
·
View notes
Text
Security Analysis of BitPower

Introduction With the rapid development of blockchain technology and cryptocurrency, decentralized finance (DeFi) platforms have attracted increasing attention. As an innovative DeFi platform, BitPower uses blockchain and smart contract technology to provide users with safe and efficient financial services. This article will explore the security of the BitPower platform in detail, covering three key areas: cryptocurrency, blockchain, and smart contracts, and explain its multiple security measures at the technical and operational levels.
Security of cryptocurrency Cryptography Cryptography uses cryptographic principles to ensure the security and privacy of transactions. BitPower supports a variety of mainstream cryptocurrencies, including Bitcoin and Ethereum, which use advanced encryption algorithms such as SHA-256 and Ethash. These algorithms ensure the encryption and verification of transaction data and improve the system's anti-attack capabilities.
Decentralized characteristics The decentralized nature of cryptocurrency makes it independent of any central agency or government, reducing the risk of being controlled or attacked by a single entity. All transaction records are stored on a distributed ledger to ensure data integrity and transparency.
Immutability Once a cryptocurrency transaction record is recorded on the blockchain, it cannot be tampered with or deleted. Any attempt to change transaction records will be detected and rejected by the entire network nodes, thus ensuring the authenticity and reliability of the data.
Security of blockchain Distributed storage Blockchain is a distributed ledger technology whose data is stored on multiple nodes around the world without a single point of failure. This distributed storage method improves the security of data, and the data is still safe and available even if some nodes are attacked or damaged.
Consensus mechanism Blockchain verifies the validity of transactions through consensus mechanisms such as proof of work PoW and proof of stake PoS. These mechanisms ensure that only legitimate transactions can be recorded on the chain, preventing double payments and fraud.
Immutability Once the data on the blockchain is written, it cannot be changed, and any attempt to tamper with the data will be discovered and rejected. This immutability ensures the reliability and integrity of transaction records, providing users with a transparent and trusted trading environment.
Security of smart contracts Automated execution Smart contracts are self-executing contracts running on blockchains, whose terms and conditions are written in code and automatically executed. The automated execution of smart contracts eliminates the risk of human intervention, all operations are transparent and visible, and users can view the execution of contracts at any time.
Transparency and openness BitPower's smart contract code is public, and anyone can review the logic and rules of the contract to ensure its fairness and transparency. The openness of the code increases the credibility of the contract, and users can use it with confidence.
Security Audit In order to ensure the security of smart contracts, BitPower will conduct strict security audits on the contract code. Audits are conducted by third-party security companies to discover and fix potential vulnerabilities and ensure the security and reliability of the contract. This audit mechanism improves the overall security of the platform and prevents hacker attacks and exploitation of code vulnerabilities.
Decentralization BitPower's platform is completely decentralized and has no central control agency. All transactions and operations are automatically executed through smart contracts, eliminating the risk of single point failures and human manipulation. Users do not need to trust any third party, only the code of the smart contract and the security of the blockchain network.
Other security measures of the BitPower platform Multi-signature BitPower uses multi-signature technology to ensure that only authorized users can perform fund operations. Multi-signature requires multiple independent signatories to jointly sign transactions to prevent single accounts from being hacked. This mechanism increases the security of the account and ensures that funds can only be transferred after multiple authorizations.
Cold wallet storage To prevent online wallets from being attacked, BitPower stores most of its users' assets in offline cold wallets. Cold wallets are not connected to the internet, so they are not vulnerable to hacker attacks, which improves the security of funds. Only a small amount of funds are stored in hot wallets for daily transactions and operational needs.
Two-step verification The BitPower platform implements a two-step verification (2FA) mechanism, which requires users to perform two-step verification when performing important operations (such as withdrawals). 2FA requires users to provide two different authentication information, such as passwords and dynamic verification codes, which improves the security of accounts and prevents unauthorized access.
Regular security updates BitPower regularly performs security updates for systems and software to ensure that the platform is always up to date with the latest security status. Security updates include patching known vulnerabilities, improving system performance, and enhancing security protection. Regular updates reduce security risks and prevent the exploitation of known attack vectors.
Conclusion The BitPower platform has built a highly secure DeFi environment through cryptocurrency, blockchain, and smart contract technology. Its decentralized, transparent, and tamper-proof characteristics, coupled with security measures such as multi-signatures, cold wallet storage, and two-step verification, ensure the security of user assets and data. When choosing a DeFi platform, security is a crucial consideration. BitPower has become a trustworthy choice with its excellent security performance.
By continuously improving and strengthening security measures, BitPower is committed to providing users with a safe, reliable and efficient financial service platform. Whether ordinary users or institutional investors, they can invest and trade with confidence on the BitPower platform and enjoy the innovation and convenience brought by blockchain technology.
2 notes
·
View notes
Text
Asynchronous Consensus Without Trusted Setup or Public-Key Cryptography
https://eprint.iacr.org/2024/677
2 notes
·
View notes
Text
What is Blockchain Technology & How Does Blockchain Work?

Introduction
Gratix Technologies has emerged as one of the most revolutionary and transformative innovations of the 21st century. This decentralized and transparent Blockchain Development Company has the potential to revolutionize various industries, from finance to supply chain management and beyond. Understanding the basics of Custom Blockchain Development Company and how it works is essential for grasping the immense opportunities it presents.
What is Blockchain Development Company
Blockchain Development Company is more than just a buzzword thrown around in tech circles. Simply put, blockchain is a ground-breaking technology that makes digital transactions safe and transparent. Well, think of Custom Blockchain Development Company as a digital ledger that records and stores transactional data in a transparent and secure manner. Instead of relying on a single authority, like a bank or government, blockchain uses a decentralized network of computers to validate and verify transactions.
Brief History of Custom Blockchain Development Company
The Custom Blockchain Development Company was founded in the early 1990s, but it didn't become well-known until the emergence of cryptocurrencies like Bitcoin. The notion of a decentralized digital ledger was initially presented by Scott Stornetta and Stuart Haber. Since then, Blockchain Development Company has advanced beyond cryptocurrency and found uses in a range of sectors, including voting systems, supply chain management, healthcare, and banking.
Cryptography and Security
One of the key features of blockchain is its robust security. Custom Blockchain Development Company relies on advanced cryptographic algorithms to secure transactions and protect the integrity of the data stored within it. By using cryptographic hashing, digital signatures, and asymmetric encryption, blockchain ensures that transactions are tamper-proof and verifiable. This level of security makes blockchain ideal for applications that require a high degree of trust and immutability.
The Inner Workings of Blockchain Development Company
Blockchain Development Company data is structured into blocks, each containing a set of transactions. These blocks are linked together in a chronological order, forming a chain of blocks hence the name of Custom Blockchain Development Company. Each block contains a unique identifier, a timestamp, a reference to the previous block, and the transactions it includes. This interconnected structure ensures the immutability of the data since any changes in one block would require altering all subsequent blocks, which is nearly impossible due to the decentralized nature of the network.
Transaction Validation and Verification
When a new transaction is initiated, it is broadcasted to the network and verified by multiple nodes through consensus mechanisms. Once validated, the transaction is added to a new block, which is then appended to the blockchain. This validation and verification process ensures that fraudulent or invalid transactions are rejected, maintaining the integrity and reliability of the blockchain.
Public vs. Private Blockchains
There are actually two main types of blockchain technology: private and public. Public Custom Blockchain Development Company, like Bitcoin and Ethereum, are open to anyone and allow for a decentralized network of participants. On the other hand, private blockchains restrict access to a select group of participants, offering more control and privacy. Both types have their advantages and use cases, and the choice depends on the specific requirements of the application.
Peer-to-Peer Networking
Custom Blockchain Development Company operates on a peer-to-peer network, where each participant has equal authority. This removes the need for intermediaries, such as banks or clearinghouses, thereby reducing costs and increasing the speed of transactions. Peer-to-peer networking also enhances security as there is no single point of failure or vulnerability. Participants in the network collaborate to maintain the Custom Blockchain Development Company security and validate transactions, creating a decentralized ecosystem that fosters trust and resilience.
Blockchain Applications and Use Cases
If you've ever had to deal with the headache of transferring money internationally or verifying your identity for a new bank account, you'll appreciate How Custom Blockchain Development Company can revolutionize the financial industry. Custom Blockchain Development Company provides a decentralized and transparent ledger system that can streamline transactions, reduce costs, and enhance security. From international remittances to smart contracts, the possibilities are endless for making our financial lives a little easier.
Supply Chain Management
Ever wondered where your new pair of sneakers came from? Custom Blockchain Development Company can trace every step of a product's journey, from raw materials to manufacturing to delivery. By recording each transaction on the Custom Blockchain Development Company supply chain management becomes more transparent, efficient, and trustworthy. No more worrying about counterfeit products or unethical sourcing - blockchain has got your back!
Enhanced Security and Trust
In a world where hacking and data breaches seem to happen on a daily basis, Custom Blockchain Development Company offers a beacon of hope. Its cryptographic algorithms and decentralized nature make it incredibly secure and resistant to tampering. Plus, with its transparent and immutable ledger, Custom Blockchain Development Company builds trust by providing a verifiable record of transactions. So you can say goodbye to those sleepless nights worrying about your data being compromised!
Improved Efficiency and Cost Savings
Who doesn't love a little efficiency and cost savings? With blockchain, intermediaries and third-party intermediaries can be eliminated, reducing the time and cost associated with transactions. Whether it's cross-border payments or supply chain management, Custom blockchain Development Company streamlined processes can save businesses a ton of money. And who doesn't want to see those savings reflected in their bottom line?
The Future of Blockchain: Trends and Innovations
As Custom Blockchain Development Company continues to evolve, one of the key trends we're seeing is the focus on interoperability and integration. Different blockchain platforms and networks are working towards the seamless transfer of data and assets, making it easier for businesses and individuals to connect and collaborate. Imagine a world where blockchain networks can communicate with each other like old friends, enabling new possibilities and unlocking even more potential.
Conclusion
Custom Blockchain Development Company has the potential to transform industries, enhance security, and streamline processes. From financial services to supply chain management to healthcare, the applications are vast and exciting. However, challenges such as scalability and regulatory concerns need to be addressed for widespread adoption. With trends like interoperability and integration, as well as the integration of Blockchain Development Company with IoT and government systems, the future looks bright for blockchain technology. So strap on your digital seatbelt and get ready for the blockchain revolution!
#blockchain development company#smart contracts in blockchain#custom blockchain development company#WEB#websites
3 notes
·
View notes
Text
For 20 years, the only way to really communicate privately was to use a widely hated piece of software called Pretty Good Privacy. The software, known as PGP, aimed to make secure communication accessible to the lay user, but it was so poorly designed that even Edward Snowden messed up his first attempt to use PGP to email a friend of Laura Poitras. It also required its users to think like engineers, which included participating in exceptionally nerdy activities like attending real-life “key-signing parties” to verify your identity to other users. Though anyone could technically use PGP, the barrier to entry was so high that only about 50,000 people used it at its peak, meaning that privacy itself was out of reach for most.
These days, to talk to a friend securely, all you have to do is download a free app. For a certain set, that app will be Signal. Snowden and Elon Musk have recommended it; it’s been name-dropped on big-budget shows like House of Cards, Mr. Robot, and Euphoria, and its users include journalists, members of the White House, NBA players, Black Lives Matters activists, and celebrities trying to get their hands on Ozempic. Its founder has been profiled by The New Yorker and appeared on Joe Rogan’s podcast. A tiny organization with virtually no marketing budget has become synonymous with digital privacy in the public imagination.
Technology can be deeply shaped by the personal inclinations of a founder. Facebook’s light-fingeredness with user data is inseparable from its roots in Zuckerberg’s dorm room as an app for ranking women by their looks; Apple’s minimalist design was influenced by Jobs’ time spent practicing Zen Buddhism. Signal is no different. During its formative years, the charismatic face of Signal was Moxie Marlinspike, a dreadlocked anarchist who spent his time sailing around the world, living in punk houses, and serving free food to the unhoused. He led every aspect of Signal’s development for almost a decade, at one point complaining, “I was writing all the Android code, was writing all of the server code, was the only person on call for the service, was facilitating all product development, and was managing everyone. I couldn’t ever leave cell service.”
In the field of cryptography, Marlinspike is considered the driving force behind bringing end-to-end encryption—the technology underlying Signal—to the real world. In 2017, Marlinspike and his collaborator, Trevor Perrin, received the Levchin Prize, a prominent prize for cryptographers, for their work on the Signal Protocol. Afterward, Dan Boneh, the Stanford professor who chaired the award committee, commented that he wasn’t sure that end-to-end encryption would have become widespread without Marlinspike’s work. At the very least, “it would have taken many more decades,” he said.
The motivations that led to end-to-end encryption going mainstream lie far out on the political fringe. The original impetus for Marlinspike’s entry into cryptography, around 2007, was to challenge existing power structures, particularly the injustice of how (as he put it) “Internet insecurity is used by people I don’t like against people I do: the government against the people.” But sticking to anarchism would imply an almost certain defeat. As Marlinspike once noted, the “trail of ideas that disappears into the horizon behind me is completely and utterly mined over with failures … Anarchists are best known for their failures.”
For an idealistic engineer to succeed, he will have to build something that is useful to many. So there has also been an unusually pragmatic bent to Signal’s approach. Indeed, in many interviews, Marlinspike has taken a mainstream stance, insisting that “Signal is just trying to bring normality to the internet.” Signal’s success depends on maintaining its principled anarchist commitments while finding a wide-ranging appeal to the masses, two goals that might seem at odds. Examining how the app navigates this tension can help us understand what might come next in Signal’s new quest to reach “everyone on the planet.”
Released after WhatsApp set the standards for messaging, Signal’s problem has always been how to keep up with its competition—a fine dance between mimicry (so as to seem familiar to new users) and innovation (to poach users from its competitors). Signal started off by copying WhatsApp's user experience, while at the same time pioneering end-to-end encryption, a feature that WhatsApp turned around and copied from Signal. Throughout this evolutionary dance, Signal has managed to maintain an unusual focus on the autonomy of the individual, a wariness of state authority, and an aversion to making money, characteristics that are recognizably anarchist.
Because a small fringe of cypherpunks, Marlinspike included, came to see cryptography as a way to remedy the imbalance of power between the individual and the state, Signal focused on getting end-to-end encryption on messages and calls absolutely right. With Signal, no one can read your messages. Amazon can’t, the US government can’t, Signal can’t. The same is true for voice calls and metadata: A user’s address book and group chat titles are just as safe. Signal knows basically nothing about you, other than your phone number (which is not mapped to your username), the time you created your account, and the time you last used the app. Your data can’t be sold to others or cause ads to follow you around on the internet. Using Signal is just like talking with your friend in the kitchen.
Because Signal is committed to retaining as little metadata as possible, that makes it hard for it to implement new features that are standard to other apps. Signal is essentially footing the cost of this commitment in engineer-hours, since implementing popular features like group chats, address books, and stickers all required doing novel research in cryptography. That Signal built them anyway is a testament to its desire for mass appeal.
Signal also pioneered features that gave individuals more autonomy over their information, such as disappearing messages (which WhatsApp later adopted) and a feature that let users blur faces in a photo (which it rapidly rolled out to support the Black Lives Matter protests). At the same time, Signal has garnered users' trust because its code is open source, so that security researchers can verify that its end-to-end encryption is as strong as the organization claims.
For the ordinary user, though, individual autonomy and privacy may not be as important. On WhatsApp, users accept that it will be very hard to figure out what exactly the app knows about you and who it might be shared with. Users’ information is governed by an ever-shifting labyrinth of grudging caveats and clauses like “we will share your transaction data and IP address with Facebook” and “we can’t see your precise location, but we’ll still try to estimate it as best as we can” and “we will find out if you click on a WhatsApp share button on the web.” WhatsApp is also closed-source, so its code can’t be audited. If using Signal is like talking in a friend’s kitchen, using WhatsApp is like meeting at a very loud bar—your conversation is safe, but you’re exposed, and you’ll have to pay for your place.
If you’re not an anarchist, you may be less worried about a shadowy state and more worried about actual people you know. People in your community might be harassing you in a group chat, an abusive ex might be searching your chats for old photos to leak, or your child might have gotten access to your unlocked phone. WhatsApp’s features better support a threat model that is sensitive to interpersonal social dynamics: You can leave groups silently, block screenshots for view-once messages, and lock specific chats. WhatsApp can even view the text of end-to-end encrypted messages that have been reported by a user for moderation, whereas Signal has no moderation at all.
Idealists have called centralization one of the main ills of the internet because it locks users into walled gardens controlled by authoritarian companies. In a great stroke of pragmatism, Signal chose to be centralized anyway. Other encrypted-messaging apps like Matrix offer a federated model akin to email, in which users across different servers can still communicate through a shared protocol. (Someone on Gmail can still email someone on Yahoo, whereas someone on Facebook Messenger can’t contact someone on Signal.) This federated approach more closely mirrors anarchy; it could theoretically be better, because there would be no single point of failure and no single service provider for a government to pressure. But federated software creates a proliferation of different clients and servers for the same protocol, making it hard to upgrade. Users are already used to centralized apps that behave like Facebook or Twitter, and email has already become centralized into a few main service providers. It turns out that being authoritarian is important for maintaining a consistent user experience and a trusted brand, and for rolling out software updates quickly. Even anarchism has its limits.
What Signal has accomplished so far is impressive. But users famously judge software not on how much it can do, but on how much it can’t. In that spirit, it’s time to complain.
Because of Signal’s small team, limited funding, and the challenges of implementing features under end-to-end encryption, the app bafflingly lacks a number of important features. It doesn’t have encrypted backups for iOS; messages can only be transferred between phones. If you lose your iPhone, you lose all your Signal chat history.
Signal also doesn’t do a good job serving some of its core users. Activists and organizers deal with huge amounts of messages that involve many people and threads, but Signal’s interface lacks ways to organize all this information. These power users’ group chats become so unwieldy that they migrate to Slack, losing the end-to-end encryption that brought them to Signal in the first place. It’s common to try and make multiple group chats between the same people to manage all their threads. When users are hacking “desire paths” into your interface to create a new feature, or leaving because of the lack of the feature, that’s a strong hint that something is missing.
WhatsApp and Telegram, on the other hand, are leading the way on defining how group chats can scale up. WhatsApp “communities” gather different private group chats in one place, better mimicking the organization of a neighborhood or school that may be discussing several things at once. Telegram’s social media “channel” features are better for broadcasting info en masse, though Telegram’s lack of moderation has been blamed for attracting the kind of fringe crowd that has been banned from all other platforms.
It's no exaggeration to say that small features in a chat app encode different visions of how society should be organized. If the first reacji in the palette was a thumbs down rather than a heart, maybe we would all be more negative, cautious people. What kind of social vision did Signal arise from?
“Looking back, I and everyone I knew was looking for that secret world hidden in this one,” Marlinspike admitted in a 2016 interview. A key text in anarchist theory describes the idea of a “temporary autonomous zone,” a place of short-term freedom where people can experiment with new ways to live together outside the confines of current social norms. Originally coined to describe “pirate utopias” that may be apocryphal, the term has since been used to understand the life and afterlife of real-world DIY spaces like communes, raves, seasteads, and protests. And Signal is, unmistakably, a temporary autonomous zone that Marlinspike has spent almost a decade building.
Because temporary autonomous zones create spaces for the radical urges that society represses, they keep life in the daytime more stable. They can sometimes make money in the way that nightclubs and festivals do. But temporary autonomous zones are temporary for a reason. Over and over, zone denizens make the same mistake: They can’t figure out how to interact productively with the wider society. The zone often runs out of money because it exists in a world where people need to pay rent. Success is elusive; when a temporary autonomous zone becomes compelling enough to threaten daytime stability, it may be violently repressed. Or the attractive freedoms offered by the zone may be taken up in a milder form by the wider society, and eventually the zone ceases to exist because its existence has pressured wider society to be a little more like it. What kind of end might Signal come to?
There are reasons to think that Signal may not be around for very long. The nonprofit’s blog, meant to convince us of the elite nature of its engineers, has the unintentional effect of conveying the incredible difficulty of building any new software feature under end-to-end encryption. Its team numbers roughly 40; Marlinspike has just left the organization. Achieving impossible feats may be fun for a stunt hacker with something to prove, but competing with major tech companies’ engineering teams may not be sustainable for a small nonprofit with Marlinspike no longer at the helm.
Fittingly for an organization formerly led by an anarchist, Signal lacks a sustainable business model, to the point where you might almost call it anti-capitalist. It has survived so far in ways that don’t seem replicable, and that may alienate some users. Signal is largely funded by a big loan from a WhatsApp founder, and that loan has already grown to $100 million. It has also accepted funding from the US government through the Open Technology Fund. Because Signal can’t sell its users’ data, it has recently begun developing a business model based on directly providing services to users and encouraging them to donate to Signal in-app. But to get enough donations, the nonprofit must grow from 40 million users to 100 million. The company’s aggressive pursuit of growth, coupled with lack of moderation in the app, has already led Signal employees themselves to publicly question whether growth might come from abusive users, such as far-right groups using Signal to organize.
But there are also reasons for hope. So far, the most effective change that Signal has created is arguably not the existence of the app itself, but making it easy for WhatsApp to bring Signal-style end-to-end encryption to billions of users. Since WhatsApp’s adoption, Facebook Messenger, Google’s Android Messages, and Microsoft’s Skype have all adopted the open source Signal Protocol, though in milder forms, as the history of temporary autonomous zones would have us guess. Perhaps the existence of the Signal Protocol, coupled with demand from increasingly privacy-conscious users, will encourage better-funded messaging apps to compete against each other to be as encrypted as possible. Then Signal would no longer need to exist. (In fact, this resembles Signal’s original theory of change, before they decided they would rather compete with mainstream tech companies.)
Now, as the era of the global watercooler ends, small private group chats are becoming the future of social life on the internet. Signal started out a renegade, a pirate utopia encircled by cryptography, but the mainstream has become—alarmingly quickly—much closer to the vision Signal sought. In one form or another, its utopia just might last.
9 notes
·
View notes
Text
Akira Ransomware Breaches Over 250 Global Entities, Rakes in $42 Million
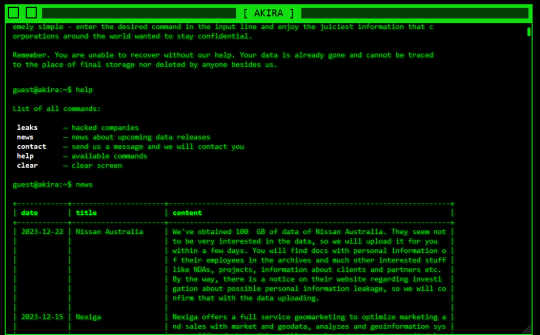
A joint cybersecurity advisory issued by CISA, FBI, Europol, and the Dutch NCSC-NL has uncovered the staggering scale of the Akira ransomware campaign. Since early 2023, the nefarious Akira operators have compromised more than 250 organizations worldwide, extorting a whopping $42 million in ransom payments. Akira's Prolific Targeting Across Industries The Akira ransomware group has been actively infiltrating entities across diverse sectors, including education, finance, and real estate. Staying true to the double extortion playbook, the threat actors exfiltrate sensitive data before encrypting the victims' systems, amplifying the pressure for a ransom payment. Early Akira versions, coded in C++, appended the .akira extension to encrypted files. However, from August 2023 onward, certain attacks deployed Megazord, a Rust-based variant that encrypts data with the .powerranges extension. Investigations reveal the perpetrators interchangeably using both Akira and Megazord, including the updated Akira_v2. Initial Access and Privilege Escalation The cybercriminals exploit various entry points, such as unprotected VPNs, Cisco vulnerabilities (CVE-2020-3259 and CVE-2023-20269), RDP exposures, spear phishing, and stolen credentials. Post-compromise, they create rogue domain accounts, like itadm, to elevate privileges, leveraging techniques like Kerberoasting and credential scraping with Mimikatz and LaZagne. Disabling Security Controls and Lateral Movement To evade detection and facilitate lateral movement, Akira operators disable security software using tools like PowerTool to terminate antivirus processes and exploit vulnerabilities. They employ various tools for reconnaissance, data exfiltration (FileZilla, WinRAR, WinSCP, RClone), and C2 communication (AnyDesk, Cloudflare Tunnel, RustDesk, Ngrok). Sophisticated Encryption The advisory highlights Akira's "sophisticated hybrid encryption scheme" combining ChaCha20 stream cipher with RSA public-key cryptography for efficient and secure encryption tailored to file types and sizes. As the Akira ransomware campaign continues to wreak havoc, the joint advisory provides crucial indicators of compromise (IoCs) to help organizations bolster their defenses against this formidable threat. Read the full article
2 notes
·
View notes
Text
Blockchain: what it is, how it works and the most common uses
What is blockchain?
It literally means blockchain is a database or public registry that can be shared by a multitude of users in peer-to-peer mode (P2P or peer network) and that allows the storage of information in an immutable and organized way.
It is a term associated with cryptocurrencies because, apart from being the technology that supports them, it was born with the first virtual currency in history in 2009, Bitcoin . In this case, the data added to the blockchain is public and can be consulted at any time by network users.
However, it is important to remember that cryptocurrencies are just that, currencies! Just as happens with the euro, the dollar or any type of paper money. Each one is a simple material with a printed value, but what allows its use and generates value are the economic laws that support them.
Something similar happens with virtual currencies. In this case, it is blockchain technology that allows it to function. Its main objective is to create an unchangeable record of everything that happens in the blockchain, which is why we are talking about a secure and transparent system.
Bitcoin (BTC), Ethereum (ETH) or any other cryptocurrency is simply a virtual currency built on the blockchain and used to send or receive the amount of money that each participant has. This technology is what keeps transactions publicly recorded, but keeping the identity of the participants anonymous.
However, although it was created to store the history of Bitcoin operations, over the years it has identified great potential to be applied in other areas and sectors due to the possibilities it offers.
Features of blockchain technology
The progress of this system has been a mystery since its origin, but little by little we are learning more details about its operation:
Security
Cryptography is a fundamental pillar in the operation of the blockchain application development company, which provides security for the data stored in the system, as well as the information shared between the nodes of the network. When we are going to make a transaction, we need a set of valid asymmetric keys to be able to carry it out on the blockchain. It is also known as public key cryptography.
Trust
By representing a shared record of facts, this technology generates trust in users. Not only that, but it eliminates the possibility of manipulation by hackers and generates a ledger of operations that all members of the network can access.
Immutability
When information is added to the distributed database, it is virtually impossible to modify it. Thanks to asymmetric cryptography and hash functions, a distributed ledger can be implemented that guarantees security. In addition, it allows consensus on data integrity to be reached among network participants without having to resort to an entity that centralizes the information.
Transparency
It is one of the basic requirements to generate trust. Transparency in blockchain consulting services is attained by making the chain's software code publicly available and by fostering a network of nodes that use it. Its application in different activities, such as supply chains, allows product traceability from origin.
Traceability
It allows knowledge of all operations carried out, as well as the review of transactions made at a specific time. Traceability is a procedure that allows us to follow the evolution of a product in each of its stages, as well as who, how, when and where it has been intervened on. This is one of the main reasons why many sectors are beginning to apply blockchain technology.
3 keys to understanding how the blockchain works
It will only take you a single step to become an expert on the blockchain consulting services. Now that you know its definition and the main characteristics and related terms, it is time to put everything you have learned together to discover how it works. Take note!
The jack, horse, king of transactions
Networks use peer-to-peer data exchange technology to connect different users who share information. That is, the data is not centralized in a central system, but shared by all users of the network. At the moment a transaction is made, it is recorded as a block of data transmitted to all parties with the objective of being validated.
The transaction is the movement of an asset and the block can record the information of your choice, from what, who, when, to where, how much and how. Like an irreversible record, each block joins the preceding and following ones to form a chain (blockchain). Every new block removes the chance of manipulation and strengthens the previous one's verification. Finally, the transaction is completed.
The structure of the blocks
The chain stores a lot of information, which allows it to grow over time. This is the reason why it has been necessary to create efficient query mechanisms without having to download all the information: the Merkle hash tree.
It is a tree data structure that allows a large number of separate data to be related to a single hash value, providing a very efficient method of verifying the contents of large information structures.
Generation of chain blocks
First of all, it is a decentralized process. And to do this, a distributed consensus is needed in which the nodes have the ability to generate valid data. In order for users to initiate new operations, they must turn into nodes within the system. If what they want is to become miners and create blocks, then they must compete with others. The validation process is based on asymmetric cryptography, with a public key and a private key. The issued transactions are validated by the nodes in the new mined block, as well as their correct linking to the previous block (it must contain the hash).
The most common uses of blockchain
“But this technology was created for cryptocurrency operations.”
That's right, but the passage of time, research and social needs have seen great potential in this technology to be applied in other areas:
Voting systems
Some states such as West Virginia are implementing electronic voting through blockchain, although it is still a framework to be regulated. But that's not necessary to go that far. After the last elections to the Madrid Assembly, as well as the COVID-19 pandemic situation and its restrictions on mobility and the gathering of people, they have proposed the establishment of electronic voting with blockchain.It is an extremely appealing voting system because of its traceability and immutability.Not only would it increase transparency and reliability, but you could audit in real time.
Smart Contracts
They are programs that allow you to fulfill and execute registered agreements between the parties automatically. They can be applied in any type of transaction where a registered agreement is necessary, such as a security deposit or the contracting of a product, among others. Among its main characteristics we find: self-execution and immutability.
Supply chain
Supervision and monitoring in food chains, as well as in production, is one of the main applications proposed with blockchain. Some examples of this technology in the food and agricultural industry are: Walmart China, with food production constituted by IBM; or the Australian AgriDigital, which works with distributed ledgers, blockchain and Smart Contracts.
It is not what has already been done, but what is yet to come. At Occam Agencia Digital , as a blockchain development company, we are convinced that it is not just about programming, but about analyzing the client's needs and designing a unique user experience.
What are some ways that your business can benefit from blockchain technology? Tell us your questions, we can help you solve them.
Tokenization of real estate and assets
Thanks to the transparency of the blockchain, the tokenization of assets is revolutionizing traditional sectors such as real estate investment, democratizing their purchase.
This breaks the barrier to investing in safer assets, since, until now, if you wanted to buy a property, you had to do it alone or among a very small group of people. Thanks to tokenization, now you can buy an apartment between 100, 200, 1000 people by making a small contribution.
This also allows you to diversify and minimize risk, being able to invest €100 in several properties.
It is very important to choose a blockchain development company that has developed a project using this technology, since these are complex developments with very little documentation on the internet to help developers.
How to do good blockchain development?
We invite you to take note of the steps necessary for the development of the blockchain:
The first thing to do is a briefing between both parties . The client provides the information on the business model, and the blockchain development company offers the expertise to design the platform using the most optimal technology.
It is very important to choose the technologies to be used, since in blockchain each transaction has a cost. Depending on the blockchain chosen, it can cost between €10 or €0.0001 each.
It is imperative that the blockchain development company determines which components of the platform need to function in order to have a well-balanced security, user experience, and cost per use system that is suitable and tailored to the client's suggested business model.
For example, if you want to develop a platform to tokenize real estate so that investors can buy tokens from these, the most recommended thing is that all the functionality related to the purchase or investment is developed on blockchain technology, and the rest of the functionalities are developed using the traditional way. In this way, you will achieve a good user experience, great security in purchases and low costs.
Once the briefing is finished, we move on to the design phase . With the briefing in hand, it's time for the UX and UI experts to get to work. With the information collected, you must design a platform with a great user experience and a friendly interface to convey confidence to the user and allow them to operate very easily. You'll be able to stay on the platform and avoid getting frustrated or giving up.
#blockchain#blockchain development#blockchain technology#blockchain development company#private blockchain development
3 notes
·
View notes
Text
Last Monday of the Week 2023-11-13
Snack time
Listening: Recommendation from The Friends after movie night, Czech Cultural Anthropologist and Weird Synth Guy Ventolín. This song is MHD, an ode to the public transport network.
youtube
It kicks ass and I will brook no argument.
Reading: I finally reestablished my RSS reader and got digging into Tons Of Bullshit I have not been reading for a long time. It also makes me much more eager to explore new blogs since I can add them to a collection, one of which was Soatok's bias-affirming (for me who has used ed25519 for years now) rundown of elliptic curve cryptographic algorithms.
Yes boss I assure you I'm looking at this blog of a blue anthro dhole for work reasons. A customer asked for guidance on key replacement.
Watching: Troll 2, at Bad Movie Night with the friends. A very well put together movie held back by not being a very good movie. A lot of fun to watch.
youtube
Really solid makeup work going on in this movie. The troll queen's actor is really having a great time playing a sexy evil goth character.
Playing: Getting back into In Other Waters. I was starting to tear through the story a little and was like "huh I should go check out this rock outcropping" and stumbled onto an entirely new ecosystem that I had not encountered before and ended up bringing back a full load of samples to analyze.
The game does a really great job of explaining the surface appearance of the ecosystem while leaving some of the deeper interactions as speculation, that makes it feel a lot like reading actual research literature about ecosystems. Even when you've filled out the folio on a species you've only just scratched the surface of why it is the way it is, you've fully described its behaviours but that's not near complete.
Making: Diwali over the weekend, so lots of confections. Making a lot of these start to finish for the first time, since I'd usually be in a production line at home.
It went well and involved some interesting problem solving, such as 3D printing a forming die for one of the snacks that needs to be squeezed into noodles directly into hot oil.
Tools and Equipment: Online RSS readers. My last RSS reader was a local affair on my PC and that's fine, but it runs into annoying limitations if you want to read while away from your desk. I would often read comics or blogs while out and then have to come home and manually clear them from my reader.
I'm now self-hosting FreshRSS but you don't have to do that, you can just use one of the many cloud readers. This way I have one reading list always syncing in the background and available on my phone, PC, laptop, work laptop, and anywhere else I want.
12 notes
·
View notes
