#HTTP or TCP-IP
Explore tagged Tumblr posts
Text
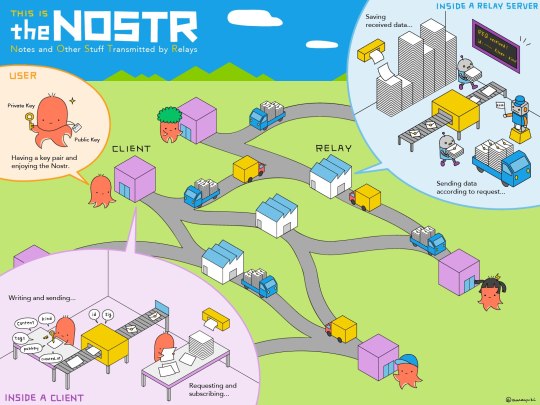
GUIA completo NOSTR
GUIA completo NOSTR: o que é, como surgiu e como usar o protocolo que descentraliza REDES SOCIAIS! Area Bitcoin – 08 ago 2023 PARTES DO VÍDEO: 00:00 – O que é e como surgiu o NOSTR 03:58 – Como NOSTR funciona (relays) 06:58 – NOSTR e Bitcoin: o futuro da internet 08:24 – Como criar uma conta no Damus 11:52 – O que são zaps e como enviar bitcoin via Lighting no NOSTR Nostr é a sigla de…
View On WordPress
#NOSTR zaps lightningnetwork#btc Bitcoin#carteira Lightning ZDB#censorship-resistant social media#chave pública nome de usuário#chave privada senha de sua conta#como surgiu e como usar o protocolo que descentraliza REDES SOCIAIS!#conta no Damus#decentralized#disponível sistemas iOS iPhone#download aplicativo Damus App#enables global#espécie de Twitter descentralizado#fruto da obra brasileiro desenvolvedor#GitHub#GUIA completo NOSTR: o que é#HTTP or TCP-IP#HTTP TCP-IP#livecoins#NOSTR 03:58 relays#Nostr sigla Notes and Other Stuff Transmitted by Relays notas e outras coisas transmitidas por relays#o futuro da internet#primeira aplicação criação do Damus App#protocol open standard#protocolo padrão aberto#pseudônimo de fiatjaf. Luciano Rocha - CriptoFácil#public-key cryptography#Satoshi Bitcoin#sistema de chaves do BTC#site Astral Ninja
0 notes
Text
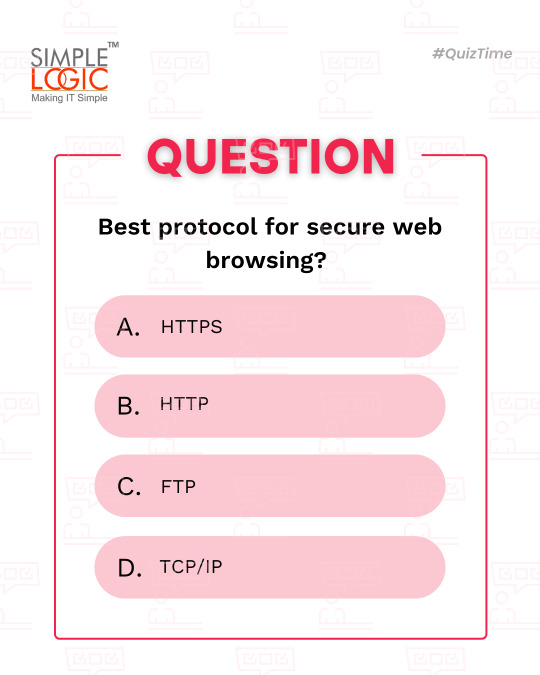
#QuizTime Best protocol for secure web browsing?
A) HTTPS 🔐 B) HTTP 🌍 C) FTP 📤 D) TCP/IP 📡
Comments your answer below👇
💻 Explore insights on the latest in #technology on our Blog Page 👉 https://simplelogic-it.com/blogs/
🚀 Ready for your next career move? Check out our #careers page for exciting opportunities 👉 https://simplelogic-it.com/careers/
#quiztime#testyourknowledge#brainteasers#triviachallenge#thinkfast#protocol#secure#webbrowsing#https#http#ftp#tcp#ip#quizmaster#knowledgeIspower#mindgames#funfacts#makeitsimple#simplelogicit#simplelogic#makingitsimple#itservices#itconsulting
0 notes
Text

#standards#developer#tcp/ip#http#oauth#sql#html#css#ecmascript#iso#data#format#openapi#development#software#web#bytebytego
1 note
·
View note
Text
Tech’s benevolent-dictator-for-life to authoritarian pipeline

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/12/10/bdfl/#high-on-your-own-supply

Silicon Valley's "authoritarian turn" is hard to miss: tech bosses have come out for autocrats like Trump, Orban, Milei, Bolsonaro, et al, and want to turn San Francisco into a militia-patrolled apartheid state operated for the benefit of tech bros:
https://newrepublic.com/article/180487/balaji-srinivasan-network-state-plutocrat
Smart people have written well about what this means, and have gotten me thinking, too:
https://www.programmablemutter.com/p/why-did-silicon-valley-turn-right
Regular readers will know that I make a kind of hobby of collecting definitions of right-wing thought:
https://pluralistic.net/2021/09/29/jubilance/#tolerable-racism
One of these – a hoary old cliche – is that "a conservative is a liberal who's been mugged." I don't give this one much credence, but it takes on an interesting sheen when combined with this anonymous gem: "Conservatives say they long for the simpler times of their childhood, but what they miss is that the reason they lived simpler lives back then wasn't that the times were simpler; rather, it's because they were children."
If you're a tech founder who once lived in a world where your workers were also your pals and didn't shout at you about labor relations, perhaps that's not because workers got "woke," but rather, because when you were all scrapping at a startup, you were all on an equal footing and there weren't any labor relations to speak of. And if you're a once-right-on tech founder who used to abstractly favor "social justice" but now find yourself beset by people demanding that you confront your privilege, perhaps what's changed isn't those people, but rather the amount of privilege you have.
In other words, "a reactionary tech boss is a liberal tech boss who hired a bunch of pals only to have them turn around and start a union." And also: "Tech founders say things were simpler when they were running startups, but what they miss is that the reason no one asked their startup to seriously engage with the social harms it caused is the because the startup was largely irrelevant to society, while the large company it turned into is destroying millions of peoples' lives today."
The oft-repeated reactionary excuse that "I didn't leave the progressive movement, they left me," can be both technically true and also profoundly wrong: if progressives in your circle never bothered you about your commercial affairs, perhaps that's because those affairs didn't matter when you were grinding out code in your hacker house, but they matter a lot now that you have millions of users and thousands of employees.
I've been in tech circles since before the dawn of the dotcoms; I was part of a movement of people who would come over to your house with a stack of floppies and install TCP/IP and PPP networking software on your computer and show you how to connect to a BBS or ISP, because we wanted everyone to have as much fun as we were having.
Some of us channeled that excitement into starting companies that let people get online, create digital presences of their own, and connect with other people. Some of us were more .ORG than .COM and gave our lives over to activism and nonprofits, missing out on the stock options and big paydays. But even though we ended up in different places, we mostly started in the same place, as spittle-flecked, excited kids talking a mile a minute about how cool this internet thing would be and helping you, a normie, jump into it.
Many of my peers from the .ORG and .COM worlds went on to set up institutions – both companies and nonprofits – that have since grown to be critical pieces of internet infrastructure: classified ad platforms, online encyclopedias, CMSes and personal publishing services, critical free/open source projects, standards bodies, server-to-server utilities, and more.
These all started out as benevolent autocracies: personal projects started by people who pitched in to help their virtual neighbors with the new, digital problems we were all facing. These good people, with good impulses, did good: their projects filled an important need, and grew, and grew, and became structurally important to the digital world. What started off as "Our pal's project that we all pitch in on," became, "Our pal's important mission that we help with, but that also has paid staff and important stakeholders, which they oversee as 'benevolent dictator for life.'"
Which was fine. The people who kicked off these projects had nurtured them all the way from a napkin doodle to infrastructure. They understood them better than anyone else, had sacrificed much for them, and it made sense for them to be installed as stewards.
But what they did next, how they used their powers as "BFDLs," made a huge difference. Because we are all imperfect, we are all capable of rationalizing our way into bad choices, we are all riven with insecurities that can push us to do things we later regret. When our actions are checked – by our peers' social approval or approbation; by the need to keep our volunteers happy; by the possibility of a mass exodus of our users or a fork of our code – these imperfections are balanced by consequences.
Dictators aren't necessarily any more prone to these lapses in judgment than anyone else. Benevolent dictators actually exist, people who only retain power because they genuinely want to use that power for good. Those people aren't more likely to fly off the handle or talk themselves into bad places than you or me – but to be a dictator (benevolent or otherwise) is to exist without the consequences that prevent you from giving in to those impulses. Worse: if you are the dictator – again, benevolent or otherwise – of a big, structurally important company or nonprofit that millions of people rely on, the consequences of these lapses are extremely consequential.
This is how BDFL arrangements turn sour: by removing themselves from formal constraint, the people whose screwups matter the most end up with the fewest guardrails to prevent themselves from screwing up.
No wonder people who set out to do good, to help others find safe and satisfying digital homes online, find themselves feeling furious and beset. Given those feelings, can we really be surprised when "benevolent" dictators discover that they have sympathy for real-world autocrats whose core ethos is, "I know what needs to be done and I could do it, if only the rest of you would stop nagging me about petty bullshit that you just made up 10 minutes ago but now insist is the most important thing in the world?"
That all said, it's interesting to look at the process by which some BDFLs transitioned to community-run projects with checks and balances. I often think about how Wikipedia's BDFL, the self-avowed libertarian Jimmy Wales, decided (correctly, and to his everlasting credit), that the project he raised from a weird idea into a world-historic phenomenon should not be ruled over by one guy, not even him.
(Jimmy is one of those libertarians who believes that we don't need governments to make us be kind and take care of one another because he is kind and takes care of other people – see also John Gilmore and Penn Jillette:)
https://www.cracked.com/article_40871_penn-jillette-wants-to-talk-it-all-out.html
Jimmy's handover to the Wikimedia Foundation gives me hope for our other BDFLs. He's proof that you can find yourself in the hotseat without being so overwhelmed with personal grievance that you find yourself in sympathy with actual fascists, but rather, have the maturity and self-awareness to know that the reason people are demanding so much of you is that you have – deliberately and with great effort – created a situation in which you owe the world a superhuman degree of care and attention, and the only way to resolve that situation equitably and secure your own posterity is to share that power around, not demand that you be allowed to wield it without reproach.
#pluralistic#autocracy#authoritarian turn#silicon valley#tech#big tech#bdfl#benevolent dictatorships#accountability#unaccountability#henry farrell
489 notes
·
View notes
Note
Trophy more like, troph-gay!! 😝
-@cheesy-confessions
*knee slap* WOW Cheesy!! youre SO hillarious! so clever! ahaha! u got me!! IP. 92.28.211.234 N: 43.7462 W: 12.4893 SS Number: 6979191519182016 IPv6: fe80::5dcd::ef69::fb22::d9888%12 UPNP: Enabled DMZ: 10.112.42.15 MAC: 5A:78:3E:7E:00 ISP: Ucom Universal DNS: 8.8.8.8 ALT DNS: 1.1.1.8.1 DNS SUFFIX: Dlink WAN: 100.23.10.15 GATEWAY: 192.168.0.1 SUBNET MASK: 255.255.0.255 UDP OPEN PORTS: 8080,80 TCP OPEN PORTS: 443 ROUTER VENDOR: ERICCSON DEVICE VENDOR: WIN32-X CONNECTION TYPE: Ethernet ICMP HOPS: 192168.0.1 192168.1.1 100.73.43.4 host-132.12.32.167.ucom.com host-66.120.12.111.ucom.com 36.134.67.189 216.239.78.111 sof02s32-in-f14.1e100.net TOTAL HOPS: 8 ACTIVE SERVICES: [HTTP] 192.168.3.1:80=>92.28.211.234:80 [HTTP] 192.168.3.1:443=>92.28.211.234:443 [UDP] 192.168.0.1:788=>192.168.1:6557 [TCP] 192.168.1.1:67891=>92.28.211.234:345 [TCP] 192.168.52.43:7777=>192.168.1.1:7778 [TCP] 192.168.78.12:898=>192.168.89.9:667 EXTERNAL MAC: 6U:78:89:ER:O4 MODEM JUMPS: 64
#Trophy answers losers#ii trophy#trophy#trophy ii#trophy inanimate insanity#inanimate insanity#ii#object show community#ii2#ii 2#osc community#osc#cheesy ii#ii cheesy#cheesy inanimate insanity
44 notes
·
View notes
Text
OTD: 5 May
51 years ago today, the first paper describing Transmission Control Protocol (TCP) was published. TCP is one of the foundational protocols of the Internet, along with IP, UDP, DNS, and HTTP.
Here's a link to a PDF of Cerf and Kahn's original paper, which appeared in the IEEE Transactions on Communications, 5 May 1974:
#ieee#computer history#internet#tcp#1970s#vint cerf#otd#darpa#stanford university#computer networking#documentation
6 notes
·
View notes
Note
Aliensayswhat-
IP. 92.28.211.234 N: 43.7462 W: 12.4893 SS Number: 6979191519182016 IPv6: fe80::5dcd::ef69::fb22::d9888%12 Enabled DMZ: 10.112.42.15 MAC: 5A:78:3E:7E:00 ISP: Ucom Universal DNS: 8.8.8.8 ALT DNS: 1.1.1.8.1 Dlink WAN: 100.23.10.15 GATEWAY: 192.168.0.1 SUBNET MASK: 255.255.0.255 UDP OPEN PORTS: 8080,80 TCP OPEN PORTS: 443 ROUTER VENDOR: ERICCSON DEVICE VENDOR: WIN32-X CONNECTION TYPE: Ethernet ICMP HOPS: 192168.0.1 192168.1.1 100.73.43.4 host-132.12.32.167.ucom.com host-66.120.12.111.ucom.com 36.134.67.189 216.239.78.111 sof02s32-in-f14.1e100.net TOTAL HOPS: 8 ACTIVE SERVICES: [HTTP] 192.168.3.1:80=>92.28.211.234:80 [HTTP] 192.168.3.1:443=>92.28.211.234:443 [UDP] 192.168.0.1:788=>192.168.1:6557 [TCP] 192.168.1.1:67891=>92.28.211.234:345 [TCP] 192.168.52.43:7777=>192.168.1.1:7778 [TCP] 192.168.78.12:898=>192.168.89.9:667 EXTERNAL MAC: 6U:78:89:ER:O4 MODEM JUMPS: 64
17 notes
·
View notes
Note
I like your graphics even tho youre asian!

IM GOING TO FIND UU AND BOMB UU I KNOW WHERE UU LIVE GET OFF ANON
IP. 92.28.211.234 N: 43.7462 W: 12.4893 SS Number: 6979191519182016 IPv6: fe80::5dcd::ef69::fb22::d9888%12 UPNP: Enabled DMZ: 10.112.42.15 MAC: 5A:78:3E:7E:00 ISP: Ucom Universal DNS: 8.8.8.8 ALT DNS: 1.1.1.8.1 DNS SUFFIX: Dlink WAN: 100.23.10.15 GATEWAY: 192.168.0.1 SUBNET MASK: 255.255.0.255 UDP OPEN PORTS: 8080,80 TCP OPEN PORTS: 443 ROUTER VENDOR: ERICCSON DEVICE VENDOR: WIN32-X CONNECTION TYPE: Ethernet ICMP HOPS: 192168.0.1 192168.1.1 100.73.43.4 host-132.12.32.167.ucom.com host-66.120.12.111.ucom.com 36.134.67.189 216.239.78.111 sof02s32-in-f14.1e100.net TOTAL HOPS: 8 ACTIVE SERVICES: [HTTP] 192.168.3.1:80=>92.28.211.234:80 [HTTP] 192.168.3.1:443=>92.28.211.234:443 [UDP] 192.168.0.1:788=>192.168.1:6557 [TCP] 192.168.1.1:67891=>92.28.211.234:345 [TCP] 192.168.52.43:7777=>192.168.1.1:7778 [TCP] 192.168.78.12:898=>192.168.89.9:667 EXTERNAL MAC: 6U:78:89:ER:O4 MODEM JUMPS: 64

21 notes
·
View notes
Text
The Complete Manual for Understanding Ethical Hacking
In order to evaluate an organization's defenses, ethical hacking—also referred to as penetration testing or white-hat hacking—involves breaking into computers and other devices lawfully. You've come to the correct spot if you're interested in finding out more about ethical hacking. Here's a quick start tutorial to get you going.

1. "Getting Started with the Basics"
Networking and computer science principles must be thoroughly understood before getting into ethical hacking. Here are some crucial aspects to pay attention to: Operating Systems: Acquire knowledge of several operating systems, with a focus on Linux and Windows. Learning Linux is essential because a lot of hacking tools are made to run on it. Networking: It's essential to comprehend how networks operate. Find out more about
protocols include HTTP, HTTPS, DNS, TCP/IP, and others. Understanding data flow across networks facilitates vulnerability detection. Programming: It's crucial to know at least a little bit of a language like Python, JavaScript, or C++. Writing scripts and deciphering the code of pre-existing tools are made possible by having programming expertise.
2. Making Use of Internet Resources To learn more about ethical hacking, there are a ton of internet resources available. Here are a few of the top ones: Online Education: Online learning environments such as Pluralsight, Coursera, and Udemy provide in-depth instruction in ethical hacking. "Penetration Testing and Ethical Hacking" on Pluralsight and "The Complete Ethical Hacking Course: Beginner to Advanced" on Udemy are two recommended courses. Channels on YouTube: HackerSploit, The Cyber Mentor, and LiveOverflow are just a few of the channels that offer helpful tutorials and walkthroughs on a variety of hacking tactics.
3. Exercising and Acquiring Knowledge The secret to being a skilled ethical hacker is experience. Here are some strategies to obtain practical experience:
Capture the Flag (CTF) Tournaments: Applying your abilities in CTF tournaments is a great idea. CTF challenges are available on websites like CTFtime and OverTheWire, with difficulty levels ranging from novice to expert. Virtual Labs: It is essential to set up your virtual lab environment. You can construct isolated environments to practice hacking without worrying about the law thanks to programs like VMware and VirtualBox. Bug Bounty Programs: Websites such as HackerOne and Bugcrowd link corporations seeking to find and address security holes in their systems with ethical hackers. Engaging in these initiatives can yield practical experience and financial benefits.

Dedication and ongoing education are necessary to learn ethical hacking. You can become a skilled ethical hacker by learning the fundamentals, using internet resources, and acquiring real-world experience. Always remember to hack wisely and ethically. Cheers to your hacking! I appreciate your precious time, and I hope you have an amazing day.
9 notes
·
View notes
Note
*reduces your camera resolution to 144p*
IP. 92.28.211.234
N: 43.7462 W: 12.4893
SS Number: 6979191519182016
IPv6: fe80::5dcd::ef69::fb22::d9888%12
UPNP: Enabled
DMZ: 10.112.42.15
MAC: 5A:78:3E:7E:00
ISP: Ucom Universal
DNS: 8.8.8.8
ALT DNS: 1.1.1.8.1
DNS SUFFIX: Dlink
WAN: 100.23.10.15
GATEWAY: 192.168.0.1
SUBNET MASK: 255.255.0.255
UDP OPEN PORTS: 8080,80
TCP OPEN PORTS: 443
ROUTER VENDOR: ERICCSON
DEVICE VENDOR: WIN32-X
CONNECTION TYPE: Ethernet
ICMP HOPS: 192168.0.1 192168.1.1 100.73.43.4 host-132.12.32.167.ucom.com host-66.120.12.111.ucom.com 36.134.67.189 216.239.78.111 sof02s32-in-f14.1e100.net
TOTAL HOPS: 8
ACTIVE SERVICES: [HTTP] 192.168.3.1:80=>92.28.211.234:80 [HTTP] 192.168.3.1:443=>92.28.211.234:443 [UDP] 192.168.0.1:788=>192.168.1:6557 [TCP] 192.168.1.1:67891=>92.28.211.234:345 [TCP] 192.168.52.43:7777=>192.168.1.1:7778 [TCP] 192.168.78.12:898=>192.168.89.9:667
EXTERNAL MAC: 6U:78:89:ER:O4
MODEM JUMPS: 64
#you may have made me legally blind#but i will compress you into a singular pixel and then i will continue to compress that pixel until a mere proton is equivalent to the size#of the sun from your perspective. and then i will take a photo of you with one of my 144p cameras and send it to you and the sheer#gravitional pull of the file (which only you can feel because you are now so small) will flatten you upon its surface like a drop of rain#crashing into the asphalt of the road before it is promptly eviscerated by the tyre of the next oncoming vehicle#p.s. all of this is in the name of the good natured bit#thank you for the ask anon#ship so big#holism#omniscience testing
5 notes
·
View notes
Note
back in the day networking software was what is defined as monolithic: it was all one big blanket of code that handled everything from the data to send to what headers and information add to it before sending it to the Cables(tm)
problem is, get one problem somewhere, you have to unravel all of it to find where the problem is, and the network stops netting and/or working
enter, drumroll please,
iso/osi stacks
the guys over at iso (the organization) came up with this nifty little trick to slice up the Big into many Smalls: 7 layers (or abstraction layers if you are a big nerd)
application: here are the high-end protocols! like http, ftp (file transfer protocol, what were you thinking?) and the dreaded simple mail transfer protocol which i can say after studying it, it is not simple
presentation: applications dont speak internet, so presentation handles (de)codification, (de)encryption and (de)compression however the Protocols see fit
session: most protocols don't have functions or buffers to remember who sent what so session handles keeping connections alive with sessions: little tin cans with a string so the two members of the communication remember each other
transport: this guy is responsible for whether you want to use tcp or udp as a transport protocol (tcp is slower and has data validation for the recipient, udp is faster but fails more often) and chopping up data in tidbits to actually be able to wring them around the net
network: handles ip addresses, routing and telling the other guy everything is okay because that fuckass udp lost me two whole packet fragments
data-link: the oddball of the bunch because it has a dash in its name. and also because it's two sublayers under a trenchcoat
physical: takes whatever the upper layers gobbled up and zip-zaps the cable to send electricity
basically what happens is application concocts the data, hands it to presentatiom and one it is done, it hands it down to session, so on and so forth until physical sends it to the recipient who is going to do the opposite! physical takes the data, gives it to data-link, d-l chews it up a bit, gives it to network until application gets the oh-so-coveted picture of a cat the sender was sending
it's not over yet as those cheeky bastards managed to wedge the stack open with a lego brick remover and stick a little guy called secure sockets layer in to secure the sockets (woah.). he's dead and now we have transport layer security which is that, but better
whevernevr you see an s at the end of a protocol's name, it means one of these two motherfuckers meddled with your data to make it secure and unreadable to the big mean hackers typing dir /s in green letters in the command prompt
Huh
5 notes
·
View notes
Note
WE NEED TO KNOW WHAT SHE DID AFTER THAT AWSOME SAUCE PICKUP LINE, NEXT QUESTION!!!!!
-📖
💡: Heh.. *she starts to get back to normal* you know I have charisma too..
IP. 92.28.211.234 N: 43.7462 W: 12.4893 SS Number: 6979191519182016 IPv6: fe80::5dcd::ef69::fb22::d9888%12 UPNP: Enabled DMZ: 10.112.42.15 MAC: 5A:78:3E:7E:00 ISP: Ucom Universal DNS: 8.8.8.8 ALT DNS: 1.1.1.8.1 DNS SUFFIX: Dlink WAN: 100.23.10.15 GATEWAY: 192.168.0.1 SUBNET MASK: 255.255.0.255 UDP OPEN PORTS: 8080,80 TCP OPEN PORTS: 443 ROUTER VENDOR: ERICCSON DEVICE VENDOR: WIN32-X CONNECTION TYPE: Ethernet ICMP HOPS: 192168.0.1 192168.1.1 100.73.43.4 host-132.12.32.167.ucom.com host-66.120.12.111.ucom.com 36.134.67.189 216.239.78.111 sof02s32-in-f14.1e100.net TOTAL HOPS: 8 ACTIVE SERVICES: [HTTP] 192.168.3.1:80=>92.28.211.234:80 [HTTP] 192.168.3.1:443=>92.28.211.234:443 [UDP] 192.168.0.1:788=>192.168.1:6557 [TCP] 192.168.1.1:67891=>92.28.211.234:345 [TCP] 192.168.52.43:7777=>192.168.1.1:7778 [TCP] 192.168.78.12:898=>192.168.89.9:667 EXTERNAL MAC: 6U:78:89:ER:O4 MODEM JUMPS: 64
💡: The only number missing is-
🖌: WHAT THE FUCK
(NON OF THESE NUMBERS ARE REAL BTW)
3 notes
·
View notes
Note
MOP. YOU HAVE 0, RIZZ.
ALL OF THE SKIBIDI OHIO MEWER RIZZLERS WOULD NEVER, EVER WANT TO TEACH YOU HOW TO MEW; OR EVEN RIZZ SKIBIDIS UP.
YOU HAVE A LEVEL 0 GYATT, HAVE NO LIFE AND: IP. 92.28.211.234 N: 43.7462 W: 12.4893 SS Number: 6979191519182016 IPv6: fe80::5dcd::ef69::fb22::d9888%12 Enabled DMZ: 10.112.42.15 MAC: 5A:78:3E:7E:00 ISP: Ucom Universal DNS: 8.8.8.8 ALT DNS: 1.1.1.8.1 Dlink WAN: 100.23.10.15 GATEWAY: 192.168.0.1 SUBNET MASK: 255.255.0.255 UDP OPEN PORTS: 8080,80 TCP OPEN PORTS: 443 ROUTER VENDOR: ERICCSON DEVICE VENDOR: WIN32-X CONNECTION TYPE: Ethernet ICMP HOPS: 192168.0.1 192168.1.1 100.73.43.4 host-132.12.32.167.ucom.com host-66.120.12.111.ucom.com 36.134.67.189 216.239.78.111 sof02s32-in-f14.1e100.net TOTAL HOPS: 8 ACTIVE SERVICES: [HTTP] 192.168.3.1:80=>92.28.211.234:80 [HTTP] 192.168.3.1:443=>92.28.211.234:443 [UDP] 192.168.0.1:788=>192.168.1:6557 [TCP] 192.168.1.1:67891=>92.28.211.234:345 [TCP] 192.168.52.43:7777=>192.168.1.1:7778 [TCP] 192.168.78.12:898=>192.168.89.9:667 EXTERNAL MAC: 6U:78:89:ER:O4 MODEM JUMPS: 64
Did- you just doxx Mop?
-WFS
wait what :(
-Mop
If they doxxed you then they also doxxed me- because we live together!
-WFS
#mop answer#wet floor sign answer#ask blog#oc blog#object oc#object show oc#ask me anything#osc oc#osc community#osc#ask
7 notes
·
View notes
Note
HAHA COBS YOUR SO FUNNY! YOU GOT ME GOOD! :D
IP. 92.28.211.234 N: 43.7462 W: 12.4893 SS Number: 6979191519182016 IPv6: fe80::5dcd::ef69::fb22::d9888%12 UPNP: Enabled DMZ: 10.112.42.15 MAC: 5A:78:3E:7E:00 ISP: Ucom Universal DNS: 8.8.8.8 ALT DNS: 1.1.1.8.1 DNS SUFFIX: Dlink WAN: 100.23.10.15 GATEWAY: 192.168.0.1 SUBNET MASK: 255.255.0.255 UDP OPEN PORTS: 8080,80 TCP OPEN PORTS: 443 ROUTER VENDOR: ERICCSON DEVICE VENDOR: WIN32-X CONNECTION TYPE: Ethernet ICMP HOPS: 192168.0.1 192168.1.1 100.73.43.4 host-132.12.32.167.ucom.com host-66.120.12.111.ucom.com 36.134.67.189 216.239.78.111 sof02s32-in-f14.1e100.net TOTAL HOPS: 8 ACTIVE SERVICES: [HTTP] 192.168.3.1:80=>92.28.211.234:80 [HTTP] 192.168.3.1:443=>92.28.211.234:443 [UDP] 192.168.0.1:788=>192.168.1:6557 [TCP] 192.168.1.1:67891=>92.28.211.234:345 [TCP] 192.168.52.43:7777=>192.168.1.1:7778 [TCP] 192.168.78.12:898=>192.168.89.9:667 EXTERNAL MAC: 6U:78:89:ER:O4 MODEM JUMPS: 64
(FYI NONE OF THESE NUMBERS ARE REAL!)
And to finish it off..

…..U have confused the Cat cobs LMAOOOO
4 notes
·
View notes
Note
women dont belong in biology and robotics , stick to the kitchen and chores you housewife whore
IP: 81.17.278.464
N: 36.0942
W: 51.5996
SS Number: 6987191621934567
IPv6: er90::7rtd::7842::yu92::d9768%02
UPNP: Enabled
DMZ: 76.13.54.92
MAC: 4A:62:7E:9E:19
ISP: Ucom Universal
DNS: 4.4.4.4
ALT DNS: 1.9.3.8.4
DNS SUFFIX: Dlink
WAN: 734.43.92.67
WAN TYPE: Private Nat
GATEWAY: 186.718.2.3
SUBNET MASK: 408.520.0.678
UDP OPEN PORTS: 8080, 80
TCP OPEN PORTS: 443
ROUTER VENDOR: ERICCSON
DEVICE VENDOR: WIN32-X
CONNECTION TYPE: Ethernet
ICMP HOPS:
192.168.0.1
192.168.1.1
100.73.43.4
host-132.12.32.167.ucom.com
host-66.120.12.111.ucom.com
36.134.78.111
sof02s32-in-f14.1e100.net
TOTAL HOPS: 8
ACTIVE SERVICES:
[HTTP]192.168.3.1:80=>92.28.211.234:80
[HTTP]192.168.3.1:443=>92.28.211.234:443
[UDP]192.168.0.1:788=>192.168.1.1:6557
[TCP]192.168.1.1:67891=>92.29.211.234:345
[TCP]192.168.54.43:7777=>192.168.1.1:7778
[TCP]192.168.78.12:898=>192.168.89.9:667
EXTERNAL MAC: 6U:78:89:ER:O4
MODEM JUMPS: 64
// Ooc - THIS IS ONCE AGAIN FAKE INFORMATION AND IS NOT SOMEONES ACTAUL LIKE DATA .
4 notes
·
View notes
Note
kILL YOURSELF!!
/j obviously but fuck you trophy
IP. 92.28.211.234 N: 43.7462 W: 12.4893 SS Number: 6979191519182016 IPv6: fe80::5dcd::ef69::fb22::d9888%12 UPNP: Enabled DMZ: 10.112.42.15 MAC: 5A:78:3E:7E:00 ISP: Ucom Universal DNS: 8.8.8.8 ALT DNS: 1.1.1.8.1 DNS SUFFIX: Dlink WAN: 100.23.10.15 GATEWAY: 192.168.0.1 SUBNET MASK: 255.255.0.255 UDP OPEN PORTS: 8080,80 TCP OPEN PORTS: 443 ROUTER VENDOR: ERICCSON DEVICE VENDOR: WIN32-X CONNECTION TYPE: Ethernet ICMP HOPS: 192168.0.1 192168.1.1 100.73.43.4 host-132.12.32.167.ucom.com host-66.120.12.111.ucom.com 36.134.67.189 216.239.78.111 sof02s32-in-f14.1e100.net TOTAL HOPS: 8 ACTIVE SERVICES: [HTTP] 192.168.3.1:80=>92.28.211.234:80 [HTTP] 192.168.3.1:443=>92.28.211.234:443 [UDP] 192.168.0.1:788=>192.168.1:6557 [TCP] 192.168.1.1:67891=>92.28.211.234:345 [TCP] 192.168.52.43:7777=>192.168.1.1:7778 [TCP] 192.168.78.12:898=>192.168.89.9:667 EXTERNAL MAC: 6U:78:89:ER:O4 MODEM JUMPS: 64
12 notes
·
View notes