#secure Java applications
Explore tagged Tumblr posts
Text

Java web frameworks are pivotal for developers building high-performance, scalable web applications. These frameworks simplify the development process by offering reusable components, making it easier to manage complex applications. In 2025, several Java frameworks continue to dominate, offering advanced features for building modern web solutions.
#Java development services#Java development company in USA#enterprise Java solutions#custom Java application development#Java web development#secure Java applications#scalable Java solutions.
0 notes
Text
Find out useful JavaScript features in this guide for web application development from the Outsource Java Development Company. Make use of JavaScript for enhanced development with the utmost security.
0 notes
Text
All right, since I bombarded a poor mutual yesterday...
Privacy is not security and security is not privacy. These terms are not interchangeable, but they are intrinsically linked.
While we're at this, anonymity =/= security either. For example, Tor provides the former, but not necessarily the latter, hence using Https is always essential.
It is impossible to have privacy without security, but you can have security without privacy.
A case in point is administrators being able to view any data they want due to their full-access rights to a system. That being said, there are ethics and policies that usually prevent such behavior.
Some general tips:
Operating System: Switch to Linux. Ubuntu and Linux Mint are widely used for a reason. Fedora too. And don't worry! You can keep your current operating system, apps and data. If you're on a Mac computer, you can easily partition your hard drive or SSD by using Disk Utility. If you're on Windows, you can follow this guide.
You want to go a step further? Go with Whonix or Tails. They're Linux distributions as well, but they're both aiming for security, not beauty so the interface might not be ideal for everyone. Many political activists and journalists use them.
You want anonymity? Then you need to familiarize yourself with Tor. Also, Tor and HTTPS and Tor’s weaknesses. When you're using it, don't log in to sites like Google, Facebook, Twitter etc. and make sure to stay away from Java and Javascript, because those things make you traceable.
Alternatives for dealing with censorship? i2p and Freenet.
Is ^ too much? Welp. All right. Let's see. The first step is to degoogle.
Switch to a user-friendly browser like Firefox (or better yet LibreWolf), Brave or Vivaldi. There are plenty of hardened browsers, but they can be overwhelming for a beginner.
Get an ad blocker like Ublock Origin.
Search Engine? StartPage or Duckduckgo. SearXNG too. Like I said degoogle.
Get a PGP encrypted e-mail. Check Protonmail out.
There's also Tutamail that doesn't cover PGP, but uses hybrid encryption that avoids some of the cons of PGP.
Skiff mail is also a decent option.
Use an e-mail aliasing service such as SimpleLogin or AnonAddy.
Check OpenPGP out. Claws Mail is a good e-mail client for Windows and Linux, Thunderbird for Mac OS.
Gpg4win is free and easy to use for anyone that wants to encrypt/decrypt e-mails.
Instead of Whatsapp, Facebook messenger, Telegram etc. use Signal for your encrypted insant messaging, voice and video calls.
Get a metadata cleaner.
Get a firewall like Opensnitch, Portmaster or Netguard which can block Internet for trackers.
Alternatively, go with a private DNS that blocks these trackers. NextDNS is a good paid service. Rethink a good free option.
Replace as many of your applications as you can with FOSS (free and open source) ones. Alternativeto can help you.
Always have automatic updates on. They are annoying af, I know, but they are necessary.
Keep your distance from outdated software.
Always have two-factor authentication (2FA) enabled.
Do not use your administrator account for casual stuff. If you're on Linux, you probably know you can be sudo, but not root.
On Linux distributions use AppArmor, but stay away from random antivirus scanners. Other distributions default to SELinux, which is less suited to a beginner.
Never repeat your passwords. If you can't remember them all, use a password manager like KeePass.
Encrypt your drive.
Honestly, VPNs have their uses and ProtonVPN, Mullvad and Windscribe are decent, but eh. If you don't trust your ISP, why would you trust the VPN provider that claims they don't log you when you can't verify such a thing?
57 notes
·
View notes
Text
(remaking the post because you can't edit polls and i gave the wrong options)
Alright I'm registering for classes and someone needs to talk me out of doing stupid shit but I'm unsure of what shit is stupidest.
Winter term:
I just finished an 8-week photo class that ended up being a huge investment in time just to go and shoot. However that was introductory photography and there is a 6-week intermediate photography class over winter term. I am signed up for photography. (Elective option for AA in Visual Arts)
There is also a 6-week introductory python course over winter term that I am signed up for and will be taking. I'm solid on that one, as long as I pass my C# class this term I'm going to be taking Python for 6 weeks at the beginning of the year.
Spring term:
College Chemistry Saturday class. 7am to 12pm for sixteen weeks. Lab and lecture; this school doesn't offer any chem classes that are after standard 9-5 hours during the regular week or that can be taken even partially online. Pretty sure I'm going to be stuck with this one and am configuring the rest of my schedule around being *less* miserable because of this class.
Survey of Western Art - Online, seems like a gimme. Does have a textbook but not one that I'm going to pay for. (Required for AA in Visual Arts)
2-Dimensional Design - Online, seems fun and like a gimme, Free/No textbook. (Required for AA in Visual Arts)
Object-Oriented Programming - Online, seems difficult, expensive textbook. Will probably be very necessary if I end up going down a more CS/tech path. Probably going to force myself to take this class.
Java Programming - Online, seems not unapproachable, expensive textbook. I don't particularly wanna but my school offers really limited options for computer science and I want to get what I can out of it before I go somewhere else.
Rationale for these weird combinations:
I'm applying as a nursing student at three schools and a biochem student at one of those schools (nutrition programs are apparently only for first-time students; 2nd Bachelor's applications are a lot more limited. I could apply to major in Francophone Studies at one of the schools though). Supposing I get accepted, these classes certainly won't hurt my status at any school that accepts me and the chemistry class is going to be really really necessary. This is the "i give a fuck about nutrition science and also directly helping people" path and if I go this way I'm interested in NP programs down the line. LOTS more school of the serious "I can't work and do this kind of school at the same time" variety.
If I *don't* get accepted to the programs I'm applying to, I'm going to go to a different community college and start working on a couple of AS degrees in computer junk (network admin and security management, computer and networking technology) and get some computer junk certs. I don't think I want/need a BS in compute science, this is the "practical" route of "I could finish this stuff pretty easily and continue working in a field where I have a lot of connections and familiarity with the industry but I am indifferent about a lot of it (pretty passionate about security and accessibility tho). Also allows me to keep working while I just churn school in the background, and all of the computer classes are transferable between the two schools.
Art classes: I think having multiple degrees is funney. I am currently 5 classes away from an AA in visual arts, at the end of this term I will be 4 classes away; if I take all the classes here and can take an elective over the summer I'll have a degree in visual arts. (There is a reasonable possibility that I'll continue taking bullshit classes behind the scenes to get silly degrees regardless of what happens otherwise)
Pretty sure the sensible thing is to drop *at least* photography and survey of western art and also possibly Java and 2D design. I'm somewhat concerned that if my spring term is just Saturday chem and object oriented programming I will start biting things.
So:
86 notes
·
View notes
Text
The Soviet intervention in Hungary and the Khrushchev revelations produced in Europe a process that led – gradually – to the Eurocommunism of the Communist Party of Spain’s leader Santiago Carrillo, who said, in 1976, ‘once Moscow was our Rome, but no more. Now we acknowledge no guiding centre, no international discipline’. This was a communism that no longer believed in revolution but was quite satisfied with an evolutionary dynamic. The European parties, correct in their desire for the right to develop their own strategies and tactics, nonetheless, threw themselves onto a self-destructive path. Few remained standing after the USSR collapsed in 1991. They campaigned for polycentrism but, in the end, achieved only a return to social democracy.
Amongst the Third World communist parties, a different orientation became clear after 1956. While the Western European parties seemed eager to denigrate the USSR and its contributions, the parties in the Third World acknowledged the importance of the USSR but sought some distance from its political orientation. During their visits to Moscow in the 1960s, champions of ‘African socialism’ such as Modibo Keïta of Mali and Mamadou Dia of Senegal announced the necessity of non-alignment and the importance of nationally developed processes of socialist construction. Marshal Lin Biao spoke of the need for a ‘creative application’ of Marxism in the Chinese context. The young leader of the Indonesian Communist Party – Dipa Nusantara Aidit – moved his party towards a firm grounding in both Marxism-Leninism and the peculiarities of Indonesian history. [...]
In the Third World, where Communism was a dynamic movement, it was not treated as a religion that was incapable of error. ‘Socialism is young’, Che Guevara wrote in 1965, ‘and has its mistakes.’ Socialism required ceaseless criticism in order to strengthen it. Such an attitude was missing in Cold War Europe and North America [...] After 1956, Communism was penalized by the Cold Warriors for the Soviet intervention in Hungary. This played some role in the Third World, but it was not decisive. In India, in 1957 the Communists won an election in Kerala to become the ruling party in that state. In 1959, the Cuban revolution overthrew a dictatorship and adopted Marxism-Leninism as its general theory. In Vietnam, from 1954, the Communists took charge of the north of the country and valiantly fought to liberate the rest of their country. These were communist victories despite the intervention in Hungary.
[...]
Much the same history propelled the Indonesian Communist Party (PKI) forward from 1951, when it had merely 5,000 members, to 1964, when it had two million party members and an additional fifteen million members in its mass organizations (half of them in the Indonesian Peasants’ Front). The party had deep roots in the heavily populated sections of east and central Java but had – in the decade after 1951 – begun to make gains in the outer islands, such as Sumatra. A viciously anti-communist military was unable to stop the growth of the party. The new leadership from the 1953 Party Central Committee meeting were all in their thirties, with the new Secretary General – Aidit – merely thirty-one years old. These communists were committed to mass struggles and to mass campaigns, to building up the party base in rural Indonesia. The Indonesian Peasants’ Front and the Plantation Workers’ Union – both PKI mass organizations – fought against forced labour (romusha) and encouraged land seizures (aksi sepihak). These campaigns became more and more radical. In February 1965, the Plantation Workers’ Union occupied land held by the US Rubber Company in North Sumatra. US Rubber and Goodyear Tires saw this as a direct threat to their interests in Indonesia. Such audacity would not be tolerated. Three multinational oil companies (Caltex, Stanvac and Shell) watched this with alarm. US diplomat George Ball wrote to US National Security Advisor McGeorge Bundy that in ‘the long run’ events in Indonesia such as these land seizures ‘may be more important than South Vietnam’. Ball would know. He oversaw the 1963 coup in South Vietnam against the US ally Ngô Đình Diệm. The West felt it could not stand by as the PKI got more aggressive.
By 1965, the PKI had three million party members – adding a million members in the year. It had emerged as a serious political force in Indonesia, despite the anti-communist military’s attempts to squelch its growth. Membership in its mass organizations went up to 18 million. A strange incident – the killing of three generals in Jakarta – set off a massive campaign, helped along by the CIA and Australian intelligence, to excise the communists from Indonesia. Mass murder was the order of the day. The worst killings were in East Java and in Bali. Colonel Sarwo Edhie’s forces, for instance, trained militia squads to kill communists. ‘We gave them two or three days’ training,’ Sarwo Edhie told journalist John Hughes, ‘then sent them out to kill the communists.’ In East Java, one eyewitness recounted, the prisoners were forced to dig a grave, then ‘one by one, they were beaten with bamboo clubs, their throats slit, and they were pushed into the mass grave’. By the end of the massacre, a million Indonesian men and women of the left were sent to these graves. Many millions more were isolated, without work and friends. Aidit was arrested by Colonel Yasir Hadibroto, brought to Boyolali (in Central Java) and executed. He was 42.
There was no way for the world communist movement to protect their Indonesian comrades. The USSR’s reaction was tepid. The Chinese called it a ‘heinous and diabolical’ crime. But neither the USSR nor China could do anything. The United Nations stayed silent. The PKI had decided to take a path that was without the guns. Its cadre could not defend themselves. They were not able to fight the military and the anti-communist gangs. It was a bloodbath.
[...]
There was little mention in Havana of the Soviet Union. It had slowed down its support for national liberation movements, eager for detente and conciliation with the West by the mid-1960s. In 1963, Aidit had chastised the Soviets, saying, ‘Socialist states are not genuine if they fail to really give assistance to the national liberation struggle’. The reason why parties such as the PKI held fast to ‘Stalin’ was not because they defended the purges or collectivization in the USSR. It was because ‘Stalin’ in the debate around militancy had come to stand in for revolutionary idealism and for the anti-fascist struggle. Aidit had agreed that the Soviets could have any interpretation of Stalin in terms of domestic policy (‘criticize him, remove his remains from the mausoleum, rename Stalingrad’), but other Communist Parties had the right to assess his role on the international level. He was a ‘lighthouse’, Aidit said in 1961, whose work was ‘still useful to Eastern countries’. This was a statement against the conciliation towards imperialism of the Khrushchev era. It was a position shared across many of the Communist Parties of the Third World.
Many Communist parties, frustrated with the pace of change and with the brutality of the attacks on them, would take to the gun in this period – from Peru to the Philippines. The massacre in Indonesia hung heavily on the world communist movement. But this move to the gun had its limitations, for many of these parties would mistake the tactics of armed revolution for a strategy of violence. The violence worked most effectively the other way. The communists were massacred in Indonesia – as we have seen – and they were butchered in Iraq and Sudan, in Central Asia and South America. The image of communists being thrown from helicopters off the coast of Chile is far less known than any cliché about the USSR.
Red Star Over the Third World, Vijay Prashad, 2019
23 notes
·
View notes
Text

Ubuntu is a popular open-source operating system based on the Linux kernel. It's known for its user-friendliness, stability, and security, making it a great choice for both beginners and experienced users. Ubuntu can be used for a variety of purposes, including:
Key Features and Uses of Ubuntu:
Desktop Environment: Ubuntu offers a modern, intuitive desktop environment that is easy to navigate. It comes with a set of pre-installed applications for everyday tasks like web browsing, email, and office productivity.
Development: Ubuntu is widely used by developers due to its robust development tools, package management system, and support for programming languages like Python, Java, and C++.
Servers: Ubuntu Server is a popular choice for hosting websites, databases, and other server applications. It's known for its performance, security, and ease of use.
Cloud Computing: Ubuntu is a preferred operating system for cloud environments, supporting platforms like OpenStack and Kubernetes for managing cloud infrastructure.
Education: Ubuntu is used in educational institutions for teaching computer science and IT courses. It's free and has a vast repository of educational software.
Customization: Users can customize their Ubuntu installation to fit their specific needs, with a variety of desktop environments, themes, and software available.
Installing Ubuntu on Windows:
The image you shared shows that you are installing Ubuntu using the Windows Subsystem for Linux (WSL). This allows you to run Ubuntu natively on your Windows machine, giving you the best of both worlds.
Benefits of Ubuntu:
Free and Open-Source: Ubuntu is free to use and open-source, meaning anyone can contribute to its development.
Regular Updates: Ubuntu receives regular updates to ensure security and performance.
Large Community: Ubuntu has a large, active community that provides support and contributes to its development.
4 notes
·
View notes
Text
Artificial Intelligence: Transforming the Future of Technology

Introduction: Artificial intelligence (AI) has become increasingly prominent in our everyday lives, revolutionizing the way we interact with technology. From virtual assistants like Siri and Alexa to predictive algorithms used in healthcare and finance, AI is shaping the future of innovation and automation.
Understanding Artificial Intelligence
Artificial intelligence (AI) involves creating computer systems capable of performing tasks that usually require human intelligence, including visual perception, speech recognition, decision-making, and language translation. By utilizing algorithms and machine learning, AI can analyze vast amounts of data and identify patterns to make autonomous decisions.
Applications of Artificial Intelligence
Healthcare: AI is being used to streamline medical processes, diagnose diseases, and personalize patient care.
Finance: Banks and financial institutions are leveraging AI for fraud detection, risk management, and investment strategies.
Retail: AI-powered chatbots and recommendation engines are enhancing customer shopping experiences.
Automotive: Self-driving cars are a prime example of AI technology revolutionizing transportation.
How Artificial Intelligence Works
AI systems are designed to mimic human intelligence by processing large datasets, learning from patterns, and adapting to new information. Machine learning algorithms and neural networks enable AI to continuously improve its performance and make more accurate predictions over time.
Advantages of Artificial Intelligence
Efficiency: AI can automate repetitive tasks, saving time and increasing productivity.
Precision: AI algorithms can analyze data with precision, leading to more accurate predictions and insights.
Personalization: AI can tailor recommendations and services to individual preferences, enhancing the customer experience.
Challenges and Limitations
Ethical Concerns: The use of AI raises ethical questions around data privacy, algorithm bias, and job displacement.
Security Risks: As AI becomes more integrated into critical systems, the risk of cyber attacks and data breaches increases.
Regulatory Compliance: Organizations must adhere to strict regulations and guidelines when implementing AI solutions to ensure transparency and accountability.
Conclusion: As artificial intelligence continues to evolve and expand its capabilities, it is essential for businesses and individuals to adapt to this technological shift. By leveraging AI's potential for innovation and efficiency, we can unlock new possibilities and drive progress in various industries. Embracing artificial intelligence is not just about staying competitive; it is about shaping a future where intelligent machines work hand in hand with humans to create a smarter and more connected world.
Syntax Minds is a training institute located in the Hyderabad. The institute provides various technical courses, typically focusing on software development, web design, and digital marketing. Their curriculum often includes subjects like Java, Python, Full Stack Development, Data Science, Machine Learning, Angular JS , React JS and other tech-related fields.
For the most accurate and up-to-date information, I recommend checking their official website or contacting them directly for details on courses, fees, batch timings, and admission procedures.
If you'd like help with more specific queries about their offerings or services, feel free to ask!
2 notes
·
View notes
Text
What Happened to Innaflash?
This might seem random/sudden but I wanted to make this post. Innaflash is not dead, but like I warned, between schoolwork, adhd, narcolepsy, etc... yeah. Also, I have been working on building my skills.
I am most likely going to move Innaflash from a Java application you need to install to a neocities site potentially, but I do want to hear your opinions if you have any! I still plan on keeping personal data local on your computer because of both storage and potential security issues. If you have any questions as always let me know. XX
#Innaflash#Innaflash Update#Java#Java Coding#coding#computer coding#programming#computer programming#computer science#comp sci#quizlet#study tools#studying#game development#game dev#🍒🌹 rambles
7 notes
·
View notes
Text
SQLi Potential Mitigation Measures
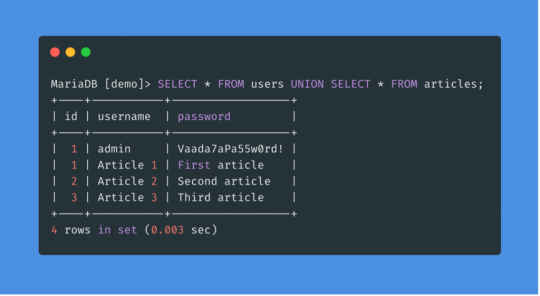
Phase: Architecture and Design
Strategy: Libraries or Frameworks
Use a vetted library or framework that prevents this weakness or makes it easier to avoid. For example, persistence layers like Hibernate or Enterprise Java Beans can offer protection against SQL injection when used correctly.
Phase: Architecture and Design
Strategy: Parameterization
Use structured mechanisms that enforce separation between data and code, such as prepared statements, parameterized queries, or stored procedures. Avoid constructing and executing query strings with "exec" to prevent SQL injection [REF-867].
Phases: Architecture and Design; Operation
Strategy: Environment Hardening
Run your code with the minimum privileges necessary for the task [REF-76]. Limit user privileges to prevent unauthorized access if an attack occurs, such as by ensuring database applications don’t run as an administrator.
Phase: Architecture and Design
Duplicate client-side security checks on the server to avoid CWE-602. Attackers can bypass client checks by altering values or removing checks entirely, making server-side validation essential.
Phase: Implementation
Strategy: Output Encoding
Avoid dynamically generating query strings, code, or commands that mix control and data. If unavoidable, use strict allowlists, escape/filter characters, and quote arguments to mitigate risks like SQL injection (CWE-88).
Phase: Implementation
Strategy: Input Validation
Assume all input is malicious. Use strict input validation with allowlists for specifications and reject non-conforming inputs. For SQL queries, limit characters based on parameter expectations for attack prevention.
Phase: Architecture and Design
Strategy: Enforcement by Conversion
For limited sets of acceptable inputs, map fixed values like numeric IDs to filenames or URLs, rejecting anything outside the known set.
Phase: Implementation
Ensure error messages reveal only necessary details, avoiding cryptic language or excessive information. Store sensitive error details in logs but be cautious with content visible to users to prevent revealing internal states.
Phase: Operation
Strategy: Firewall
Use an application firewall to detect attacks against weaknesses in cases where the code can’t be fixed. Firewalls offer defense in depth, though they may require customization and won’t cover all input vectors.
Phases: Operation; Implementation
Strategy: Environment Hardening
In PHP, avoid using register_globals to prevent weaknesses like CWE-95 and CWE-621. Avoid emulating this feature to reduce risks. source
3 notes
·
View notes
Text
Gemini Code Assist Enterprise: AI App Development Tool

Introducing Gemini Code Assist Enterprise’s AI-powered app development tool that allows for code customisation.
The modern economy is driven by software development. Unfortunately, due to a lack of skilled developers, a growing number of integrations, vendors, and abstraction levels, developing effective apps across the tech stack is difficult.
To expedite application delivery and stay competitive, IT leaders must provide their teams with AI-powered solutions that assist developers in navigating complexity.
Google Cloud thinks that offering an AI-powered application development solution that works across the tech stack, along with enterprise-grade security guarantees, better contextual suggestions, and cloud integrations that let developers work more quickly and versatile with a wider range of services, is the best way to address development challenges.
Google Cloud is presenting Gemini Code Assist Enterprise, the next generation of application development capabilities.
Beyond AI-powered coding aid in the IDE, Gemini Code Assist Enterprise goes. This is application development support at the corporate level. Gemini’s huge token context window supports deep local codebase awareness. You can use a wide context window to consider the details of your local codebase and ongoing development session, allowing you to generate or transform code that is better appropriate for your application.
With code customization, Code Assist Enterprise not only comprehends your local codebase but also provides code recommendations based on internal libraries and best practices within your company. As a result, Code Assist can produce personalized code recommendations that are more precise and pertinent to your company. In addition to finishing difficult activities like updating the Java version across a whole repository, developers can remain in the flow state for longer and provide more insights directly to their IDEs. Because of this, developers can concentrate on coming up with original solutions to problems, which increases job satisfaction and gives them a competitive advantage. You can also come to market more quickly.
GitLab.com and GitHub.com repos can be indexed by Gemini Code Assist Enterprise code customisation; support for self-hosted, on-premise repos and other source control systems will be added in early 2025.
Yet IDEs are not the only tool used to construct apps. It integrates coding support into all of Google Cloud’s services to help specialist coders become more adaptable builders. The time required to transition to new technologies is significantly decreased by a code assistant, which also integrates the subtleties of an organization’s coding standards into its recommendations. Therefore, the faster your builders can create and deliver applications, the more services it impacts. To meet developers where they are, Code Assist Enterprise provides coding assistance in Firebase, Databases, BigQuery, Colab Enterprise, Apigee, and Application Integration. Furthermore, each Gemini Code Assist Enterprise user can access these products’ features; they are not separate purchases.
Gemini Code Support BigQuery enterprise users can benefit from SQL and Python code support. With the creation of pre-validated, ready-to-run queries (data insights) and a natural language-based interface for data exploration, curation, wrangling, analysis, and visualization (data canvas), they can enhance their data journeys beyond editor-based code assistance and speed up their analytics workflows.
Furthermore, Code Assist Enterprise does not use the proprietary data from your firm to train the Gemini model, since security and privacy are of utmost importance to any business. Source code that is kept separate from each customer’s organization and kept for usage in code customization is kept in a Google Cloud-managed project. Clients are in complete control of which source repositories to utilize for customization, and they can delete all data at any moment.
Your company and data are safeguarded by Google Cloud’s dedication to enterprise preparedness, data governance, and security. This is demonstrated by projects like software supply chain security, Mandiant research, and purpose-built infrastructure, as well as by generative AI indemnification.
Google Cloud provides you with the greatest tools for AI coding support so that your engineers may work happily and effectively. The market is also paying attention. Because of its ability to execute and completeness of vision, Google Cloud has been ranked as a Leader in the Gartner Magic Quadrant for AI Code Assistants for 2024.
Gemini Code Assist Enterprise Costs
In general, Gemini Code Assist Enterprise costs $45 per month per user; however, a one-year membership that ends on March 31, 2025, will only cost $19 per month per user.
Read more on Govindhtech.com
#Gemini#GeminiCodeAssist#AIApp#AI#AICodeAssistants#CodeAssistEnterprise#BigQuery#Geminimodel#News#Technews#TechnologyNews#Technologytrends#Govindhtech#technology
3 notes
·
View notes
Text
The History of Java Programming: From Its Humble Beginnings to Dominance in Software Development
Java is one of the most influential programming languages in the modern era, known for its versatility, portability, and robustness. Developed in the early 1990s, it has left a lasting impact on the software industry, helping build countless applications, from mobile games to enterprise-level software. In this blog, we'll explore Java’s fascinating history, its motivations, its growth, and its influence on today’s technology landscape.
The Genesis of Java
Java originated in the early 1990s as part of a project at Sun Microsystems. The project, initially called the "Green Project," was led by James Gosling, alongside Mike Sheridan and Patrick Naughton. The team's goal was to develop a language for embedded systems, specifically for appliances like televisions, which were beginning to incorporate smart technology.
The language was initially called "Oak," named after an oak tree outside Gosling's office. However, due to a trademark conflict, it was eventually renamed Java. The name "Java" was inspired by a type of coffee popular with the developers, signifying their relentless energy and drive.
Motivation Behind Java's Creation
Java was developed to address several key challenges in software development at the time:
Portability: Most languages of the day, such as C and C++, were platform-dependent. This meant that software needed significant modification to run on different operating systems. Gosling and his team envisioned a language that could be executed anywhere without alteration. This led to the now-famous slogan, "Write Once, Run Anywhere" (WORA).
Reliability: C and C++ were powerful, but they had pitfalls like manual memory management and complex pointers, which often led to errors. Java aimed to eliminate these issues by offering features like automatic memory management through garbage collection.
Internet Revolution: As the internet began to take shape, Java was positioned to take advantage of this growing technology. Java’s platform independence and security made it an ideal choice for internet-based applications.
The Birth of Java (1995)
The Green Project initially produced a device called Star7, an interactive television set-top box. While innovative, it didn't achieve widespread success. However, by the mid-1990s, the internet was gaining traction, and Sun Microsystems realized Java’s true potential as a programming language for web applications.
In 1995, Java was officially launched with the release of the Java Development Kit (JDK) 1.0. At the same time, Netscape Navigator, a popular web browser, announced that it would support Java applets. This gave Java immense exposure and set the stage for its rapid adoption in the software development community.
Key Features that Set Java Apart
From the beginning, Java had several features that distinguished it from its contemporaries:
Platform Independence: Java programs are compiled into an intermediate form called bytecode, which runs on the Java Virtual Machine (JVM). The JVM acts as a mediator between the bytecode and the underlying system, allowing Java programs to be executed on any platform without modification.
Object-Oriented: Java was designed from the ground up as an object-oriented language, emphasizing modularity, reusability, and scalability. This feature made Java particularly attractive for building complex and large-scale applications.
Automatic Memory Management: Java's garbage collector automatically handles memory deallocation, reducing the risk of memory leaks and other errors that plagued languages like C and C++.
Security: Java was designed with a focus on security, particularly given its intended use for internet applications. The JVM serves as a secure sandbox, and Java’s bytecode verification process ensures that malicious code cannot be executed.
Evolution of Java Versions
Since its release in 1995, Java has undergone several iterations, each bringing new features and improvements to enhance the developer experience and address the evolving needs of software applications.
Java 1.0 (1996): The first version of Java was mainly used for applets on web browsers. It came with basic tools, libraries, and APIs, establishing Java as a mainstream programming language.
Java 2 (1998): With the release of J2SE (Java 2 Platform, Standard Edition), Java evolved from a simple web language to a complete, general-purpose development platform. Java 2 introduced the Swing library, which provided advanced tools for building graphical user interfaces (GUIs). This release also marked the beginning of Java Enterprise Edition (J2EE), which extended Java for server-side applications.
Java 5 (2004): Java 5, initially called Java 1.5, was a significant update. It introduced Generics, Annotations, Enumerations, and Autoboxing/Unboxing. The updated version also brought improved syntax and functionality, which simplified writing and reading code.
Java SE 7 (2011) and Java SE 8 (2014): Java SE 7 brought features like try-with-resources, simplifying exception handling. Java SE 8 was a transformative release, introducing Lambda expressions and Stream APIs. This version brought functional programming aspects to Java, allowing developers to write more concise and expressive code.
Java 9 to Java 17 (2017-2021): Java 9 introduced the module system to help organize large applications. Java 11 and later versions moved towards a more rapid release cadence, with new features appearing every six months. Java 17, released in 2021, became a long-term support (LTS) version, offering several advancements like improved garbage collection, pattern matching, and record classes.
The Java Community and OpenJDK
Java's development has always been characterized by a strong community influence. Initially controlled by Sun Microsystems, Java's fate changed when Oracle Corporation acquired Sun in 2010. After the acquisition, Oracle made significant strides towards making Java more open and community-driven.
OpenJDK, an open-source implementation of Java, became the reference implementation starting from Java 7. This move encouraged greater collaboration, transparency, and diversity within the Java ecosystem. OpenJDK allowed more organizations to contribute to Java’s development and ensure its continued growth.
Java in the Enterprise and Beyond
Java has become synonymous with enterprise-level software development, thanks in part to the introduction of Java EE (now known as Jakarta EE). Java EE provides a set of specifications and tools for building large-scale, distributed, and highly reliable applications. The Java ecosystem, including frameworks like Spring, Hibernate, and Apache Struts, has contributed to its popularity in enterprise environments.
Java also became a key player in the development of Android applications. Android Studio, Google's official IDE for Android development, is powered by Java, which contributed significantly to its widespread adoption. Although Kotlin, another JVM language, is now gaining popularity, Java remains a core language for Android.
The Challenges Java Faced
Despite its success, Java faced competition and challenges over the years. Languages like C#, developed by Microsoft, and Python have gained traction due to their developer-friendly features. Java has been criticized for its verbosity compared to more modern languages. However, the Java community’s active contributions and Oracle’s improvements, including adding modern programming paradigms, have kept it relevant.
Another significant challenge was the rise of JavaScript for web development. While Java was initially popular for web applets, JavaScript became the dominant language for front-end development. Java's relevance in web applications decreased, but it found its niche in server-side applications, enterprise systems, and Android.
Java Today and Its Future
Today, Java is one of the most popular programming languages globally, powering applications across various sectors, including finance, healthcare, telecommunications, and education. Java’s strength lies in its mature ecosystem, robust performance, and scalability.
The new six-month release cycle initiated by Oracle has brought excitement back into the Java world, with new features being added frequently, keeping the language modern and in line with developer needs. Java 17, as an LTS version, is a stable platform for enterprises looking for reliable updates and support over the long term.
Looking forward, Java’s evolution focuses on improving developer productivity, adding more concise language features, and optimizing performance. Java's adaptability and continuous evolution ensure its place as a leading language for both new projects and legacy systems.
Conclusion
Java’s journey from a language for set-top boxes to becoming a foundational tool in enterprise computing, Android applications, and beyond is nothing short of remarkable. Its creation was driven by a need for portability, reliability, and ease of use. Over nearly three decades, Java has evolved to remain relevant, keeping pace with technological advancements while preserving its core values of reliability and platform independence.
The language’s robust community, open-source development model, and wide adoption in critical applications guarantee that Java will remain a force in software development for many years to come. It has not only withstood the test of time but continues to thrive in a constantly changing technology landscape—an enduring testament to the vision of its creators and the collective effort of its global community.
2 notes
·
View notes
Text
How to Become a Cloud Computing Engineer
Introduction:
Cloud computing has become a cornerstone of modern IT infrastructure, making the role of a Cloud Computing Engineer highly in demand. If you're looking to enter this field, here's a roadmap to help you get started:
Build a Strong Foundation in IT A solid understanding of computer networks, operating systems, and basic programming is essential. Consider getting a degree in Computer Science or Information Technology. Alternatively, Jetking offer you to make your career in Cloud computing Courses and gain the technical knowledge needed.
Learn Cloud Platforms Familiarize yourself with popular cloud service providers such as AWS (Amazon Web Services), Microsoft Azure, and Google Cloud. Many platforms offer certification courses, like AWS Certified Solutions Architect, which will help validate your skills.
Gain Hands-On Experience Practical experience is critical. Set up your own cloud projects, manage databases, configure servers, and practice deploying applications. This will give you the real-world experience that employers seek.
Master Programming Languages Learn programming languages commonly used in cloud environments, such as Python, Java, or Ruby. Scripting helps automate tasks, making your work as a cloud engineer more efficient.
Understand Security in the Cloud Security is paramount in cloud computing. Gain knowledge of cloud security best practices, such as encryption, data protection, and compliance standards to ensure safe operations and become Master in cloud computing courses.
Get Certified Earning cloud certifications from AWS, Azure, or Google Cloud can enhance your credibility. Certifications like AWS Certified Cloud Practitioner or Microsoft Certified: Azure Fundamentals can provide you a competitive edge.
Keep Learning Cloud technology evolves rapidly, so continuous learning is key. Stay updated by taking advanced courses and attending cloud tech conferences.
Join Jetking today! Click Here
By building your expertise in these areas, you’ll be well on your way to a successful career as a Cloud Computing Engineer!
2 notes
·
View notes
Text
Which programming language performs better on the web, Java, C#, PHP, or Python?
The performance of a programming language on the web depends on various factors such as the specific requirements of the project, the expertise of the development team, and the scalability of the language. Each programming language you mentioned—Java, C#, PHP, and Python—has its strengths and use cases:
Java: Known for its performance, scalability, and security, Java is widely used in enterprise-level web applications, especially for large-scale projects. It's commonly used in backend development and is favored for its robustness and ability to handle high loads.
C#: Similar to Java, C# is often used in enterprise-level web development, particularly for building applications on the Microsoft .NET framework. It offers strong performance and is well-suited for Windows-based environments.
PHP: PHP is a server-side scripting language specifically designed for web development. It's known for its simplicity, ease of use, and extensive community support. PHP powers a large portion of the web, particularly in content management systems like WordPress and e-commerce platforms like Magento.
Python: Python is a versatile language that is gaining popularity in web development due to its simplicity, readability, and extensive libraries. It's commonly used in web frameworks like Django and Flask, making it suitable for building web applications of various scales.
Ultimately, the best programming language for web development depends on the specific requirements of your project, the preferences of your development team, and the goals of your business. Each language has its advantages and trade-offs, so it's essential to evaluate them based on your project's needs.
4 notes
·
View notes
Text
Manipal University Online MCA
Conquering the Digital Frontier: Unraveling the Manipal University Online MCA Program

In the whirlwind of the digital age, a Master of Computer Applications (MCA) degree has become the gold standard for aspiring IT professionals. If you crave the flexibility of online learning while seeking the prestige of a renowned university, Manipal University Online's MCA program might be your perfect launchpad. Let's delve into this innovative program, examining its curriculum, eligibility criteria, fees, and the key factors that make it stand out.
Unveiling the Course Structure:
Manipal University Online's MCA program spans across four semesters, meticulously crafted to equip you with cutting-edge knowledge and hands-on skills. Here's a glimpse into the core areas you'll conquer:
Foundational Semesters (Semesters 1 & 2): Laying the groundwork, you'll master programming languages like C++, Java, and Python. Data structures, algorithms, and operating systems will become your playground, while subjects like computer networks and web technologies open doors to the digital world's infrastructure.
Specialization Semesters (Semesters 3 & 4): This is where you carve your niche. Choose from specializations like Artificial Intelligence and Machine Learning, Cloud Computing, Software Development, or Cyber Security. Deepen your expertise in your chosen domain with advanced electives and capstone projects that put your skills to the test.
Eligibility Criteria: Unlocking the Gateway:
To embark on this journey, you must have:
A Bachelor's degree in any discipline with Mathematics or Statistics as a compulsory subject at the 10+2 level or at the graduation level.
Secured a valid score in national entrance exams like NIMCAT, MAT, or ATMA.
A passion for technology and a thirst for continuous learning.
Admission Criteria: Demystifying the Selection Process:
Once you meet the eligibility criteria, your merit score in the chosen entrance exam forms the basis for selection. Shortlisted candidates are then invited for an online interview where your communication skills, technical aptitude, and career aspirations are assessed.
Financial Considerations: Unmasking the Fees:
The program fee for the Manipal University Online MCA program is currently set at around INR 2.5 lakhs per semester. However, scholarships and financial aid options are available for deserving students, easing the financial burden and making the program accessible to a wider pool of talented individuals.
Beyond the Classroom: What Sets Manipal Online MCA Apart:
While a robust curriculum is crucial, Manipal University Online goes the extra mile to elevate your learning experience:
Renowned Faculty: Learn from industry experts and academic stalwarts who bring real-world experience and a passion for teaching to the virtual classroom.
Interactive Learning Platform: Engage in live online sessions, access comprehensive study materials, and collaborate with peers through a user-friendly learning management system.
Industry Connect: Gain an edge with industry internships and mentorship opportunities that bridge the gap between theory and practical application.
Placement Assistance: Leverage the university's strong industry network and dedicated placement cell to land your dream job in the booming IT sector.
Embarking on Your Digital Quest:
The Manipal University Online MCA program is not just a degree; it's a passport to a rewarding career in the ever-evolving IT landscape. If you're driven by ambition, possess a curious mind, and yearn to make your mark in the digital world, this program can be your stepping stone to success.
Spotlight on Specializations: Dive deeper into each specialization, highlighting the specific courses, industry trends, and career prospects.
Alumni Success Stories: Feature interviews with successful alumni who have carved their niche in the IT world after graduating from the program.
Comparison with other Online MCA Programs: Briefly compare Manipal's program with other online MCA offerings, highlighting its unique strengths and value proposition.
Student Testimonies: Include quotes from current or past students about their experiences with the program, its challenges, and its rewards.
Career Outlook: Discuss the job market for MCA graduates, highlighting growth trends, in-demand skills, and potential salary ranges.
Q&A Section: Address frequently asked questions about the program, admission process, and career opportunities.
For further information and updates ,please visit on:-
Top MCA colleges in india with low fees ,visit on :-
11 notes
·
View notes
Text

Improve Your Java Projects with Hosting Home's Java VPS Servers
With Hosting Home’s Java VPS servers, your Java applications get the speed and reliability they deserve. Enjoy top-tier performance, robust security, and expert support tailored for your success.
#java vps#vps java hosting#java hosting vps#vps hosting java#vps java#best vps hosting for java#best java servers#best java web server#tomcat server in java#java server
2 notes
·
View notes
Text
NodeJS excels in web development with its event-driven, non-blocking I/O model, making it ideal for handling concurrent connections and real-time applications like chat apps and live streaming. Its single-threaded architecture and use of JavaScript, both on the server and client side, allow for seamless development across the entire stack. NodeJS is especially suitable for startups and projects that require fast, scalable, and high-performance solutions.
Java, on the other hand, is renowned for its robustness, security, and platform independence. It is a mature technology with a vast ecosystem and a wealth of libraries and frameworks, such as Spring and Hibernate, which facilitate the development of large-scale, enterprise-grade applications. Java's multithreading capabilities and strong memory management make it well-suited for complex, resource-intensive applications where stability and reliability are paramount.
Choosing between NodeJS and Java ultimately depends on the specific needs of your project. For real-time, scalable applications with a need for rapid development, NodeJS is a compelling choice. For enterprise-level applications requiring high stability, security, and comprehensive tool support, Java is often the preferred technology.
#nodejs#javascript#web development#framework#best web development company in usa#software#node js development company#javaprogramming#programming
3 notes
·
View notes