#secure blockchain
Text
Cardano (ADA): Sell it for Solana?
New Post has been published on https://www.ultragamerz.com/cardano-ada-sell-it-for-solana/
Cardano (ADA): Sell it for Solana?
Cardano (ADA): Sell it for Solana?
Cardano (ADA), the brainchild of Ethereum co-founder Charles Hoskinson, has been a hot topic in the crypto space. However, with a recent barrage of bearish news and influencer skepticism, some are questioning whether ADA is all it’s cracked up to be. Let’s delve into the world of Cardano, separating hype from reality.
Influencer FOMO and the Solana Shadow:
Social media is flooded with “Cardano killers” like Solana (SOL) boasting lightning-fast transaction speeds and lower fees. Influencers, often swayed by short-term gains, are hyping SOL to the moon, leaving Cardano seemingly stuck in the dust.
Cardano’s Different Path:
However, Cardano takes a much different approach than the “move fast and break things” mentality of some competitors. Cardano prioritizes meticulous research and a peer-reviewed development process. This methodical approach, while slower, aims to deliver a more secure and scalable blockchain in the long run.
Cardano vs. The Hype Machine:
Recent bearish articles highlight Cardano’s slow development progress and missed deadlines. While these criticisms hold some weight, it’s important to remember Cardano is building a complex ecosystem.
The ADA Price:
Cardano’s Bullish Trajectory: A Technical Analysis Glimpse
Cardano (ADA) has been on a tear lately, and technical analysts are using charting tools to predict its potential price path. Here’s a breakdown of three possible targets based on different timeframes:
Short-Term (1-2 Months): Applying the Fibonacci retracement tool to ADA’s recent price surge suggests a first target of around $2.20. This level represents the 61.8% retracement of the current upswing, a common support zone after a price increase.
Mid-Term (3-6 Months): If the bullish momentum continues, a more ambitious target could be $14. This aligns with the 161.8% Fibonacci extension level, indicating a potential doubling of the current price within the next half year. However, reaching this target zone would require sustained buying pressure and positive news surrounding the Cardano ecosystem.
Long-Term (1+ Years): For the long-term hodlers (holders on for a dear life), some analysts are charting a much more aggressive target – a staggering $55. This aligns with the 261.8% Fibonacci extension, signifying a potential 25x return on investment from current levels. However, reaching this price point would require significant adoption of Cardano’s blockchain technology and widespread recognition of its functionalities.
Remember: This is for informational purposes only and should not be considered financial advice. Technical analysis is just one tool, and market conditions can change rapidly. Always conduct your own research before making any investment decisions.
Is ADA a Worthy Investment?
While some influencers are quick to dismiss ADA, it’s crucial to conduct your own research and understand Cardano’s unique value proposition. Here are some key aspects to consider:
Scalability: Cardano’s Ouroboros proof-of-stake consensus mechanism aims to achieve high transaction throughput without sacrificing decentralization, a challenge faced by many blockchains.
Smart Contracts: Cardano’s smart contract platform, Plutus, is built with security and formal verification in mind, aiming to minimize bugs and vulnerabilities.
Interoperability: Cardano’s vision includes interoperability with other blockchains, allowing seamless transfer of data and assets across different ecosystems.
Bearish News and Price Performance:
Despite the recent bearish sentiment, it’s worth noting that ADA started the current market cycle at around $0.20 and reached a peak of over $3.00, a significant increase. This demonstrates that long-term investors still see value in Cardano’s long-term vision.
Is ADA Right for You?
The decision to invest in ADA depends on your risk tolerance and investment horizon. If you’re looking for a quick pump based on influencer hype, Cardano might not be the best choice. However, if you believe in Cardano’s long-term vision of a secure and scalable blockchain platform, ADA could be a worthwhile investment for your portfolio.
Remember:
The cryptocurrency market is notoriously volatile and prone to hype cycles. Always conduct thorough research, understand the risks involved, and never invest more than you can afford to lose.
#bearish news#Cardano (ADA)#Cardano killers#Charles Hoskinson#consensus mechanism#Cryptocurrency Market#decentralization#Ethereum (ETH)#Ethereum co-founder#fees#formal verification#hype#hype cycles#influencer FOMO (Fear of Missing Out)#interoperability#investment#long-term vision#Ouroboros proof-of-stake#peer-reviewed development process#Plutus#price performance#research#risk#risk tolerance#scalability#secure blockchain#security#smart contracts#Solana (SOL)#transaction speeds
0 notes
Text
How DLT is Changing the Way We Vote: A Look at Digital Voting Systems
Voting is a fundamental right in democratic societies. However, traditional voting systems have been plagued by issues such as voter fraud, low voter turnout, and long wait times. With the emergence of Distributed Ledger Technology (DLT), also known as blockchain technology, there is a growing interest in digital voting systems. In this blog post, we will explore how DLT is changing the way we vote and the potential benefits and challenges of digital voting systems.
What is DLT?
Before we dive into how DLT is changing the way we vote, let's first define what DLT is. DLT is a type of database distributed across a computer network. Each computer in the network has a copy of the database, and any changes to the database are recorded in a transparent and immutable way. This means that once data is recorded on the blockchain, it cannot be altered or deleted.
How DLT is Changing the Way We Vote
Digital voting systems that utilize DLT have the potential to revolutionize the way we vote. Here are some of the ways that DLT is changing the way we vote:
Increased Transparency and Security
One of the most significant benefits of digital voting systems that use DLT is increased transparency and security. DLT provides a secure and transparent platform for recording and counting votes. Each vote is recorded on the blockchain, and once recorded, it cannot be altered or deleted. This ensures that the voting process is secure and transparent, and it helps prevent voter fraud.
Increased Accessibility
Digital voting systems that use DLT can also increase accessibility. Traditional voting systems often require voters to be physically present at a polling station, which can be challenging for people with disabilities or those who live in remote areas. Digital voting systems can allow voters to cast their votes from anywhere, using a computer or mobile device. This can help increase voter turnout and make it easier for people to exercise their right to vote.
Increased Efficiency
Digital voting systems that use DLT can also increase efficiency. Traditional voting systems can be time-consuming and expensive to administer. Digital voting systems can automate many of the processes involved in voting, such as voter registration, ballot counting, and result reporting. This can help reduce the cost and time required to administer elections.
Potential Challenges
While digital voting systems that use DLT offer many potential benefits, some challenges need to be addressed. Here are some of the potential challenges:
Technical Challenges
Digital voting systems that use DLT require a high level of technical expertise to develop and maintain. This can be a challenge for some election authorities, especially those in developing countries or those with limited resources.
Security Concerns
While DLT provides a secure platform for recording and counting votes, there are still security concerns that need to be addressed. Hackers could potentially compromise the voting system, which could lead to voter fraud or other security breaches.
Privacy Concerns
Digital voting systems that use DLT also raise privacy concerns. Voters must be assured that their votes are anonymous and that their personal information is protected.
Conclusion
Digital voting systems that use DLT have the potential to revolutionize the way we vote. They offer increased transparency, security, accessibility, and efficiency. However, there are also potential challenges that need to be addressed. As DLT continues to evolve, we can expect to see more innovative digital voting systems emerge in the future.
#vote#pls vote#democracy#DLT#blockchain#BlockchainTechnology#digitalvoting#transparency#security#accesibility#efficiency#voterfraud#privacy#technical analysis#electionadminstration#turkey#general election#turkey2023generalelection
23 notes
·
View notes
Text
The Importance of Data Privacy in the Age of Big Data

In today’s digital world, “big data” is a buzzword you probably hear a lot. It refers to the huge volumes of data that businesses and governments collect about us, the consumers. From what we buy to where we go, our data is constantly being gathered. But alongside this vast gathering of data comes a crucial aspect—data privacy.
Understanding and protecting our personal information has never been more important. Here’s why it matters, explained through simple insights and personal touches that you can relate to.
Click here for details...
#artificial intelligence security#big data#Blockchain Technology#consumer data protection#consumer rights#cyber security#data breach prevention#data ethics#data privacy#data privacy rights#data protection#data transparency#digital footprint#GDPR compliance#identity theft protection#internet safety#online data protection#online security#personal data safety#privacy law#privacy policies#safeguarding data#secure browsing#tech privacy#tech trends
2 notes
·
View notes
Text
Governance Tokens DeFi: Empowering Decentralized Finance
Decentralized Finance, or DeFi, is a quickly growing industry of the blockchain sector that is revolutionizing traditional financing. It uses a variety of economic solutions, such as borrowing, trading, and also borrowing, without the requirement for intermediaries like financial institutions. However, to make certain the smooth functioning of DeFi methods, administration is crucial. This is where Governance Tokens enter into play.
What are Governance Tokens?
Governance Tokens are digital possessions that grant their owners the right to get involved in the decision-making procedure of a DeFi method. They permit token owners to suggest, vote, and implement changes to the protocol's procedures and also regulations. Governance Tokens are important for the decentralized governance of DeFi methods, as they allow an autonomous decision-making procedure without the requirement for centralized authorities.
How do Governance Tokens function?
Governance Tokens work with a Proof-of-Stake (PoS) consensus mechanism, which means that the more tokens an individual holds, the more ballot power they have. This makes sure that those that have a larger stake in the procedure have a greater say in the decision-making procedure. Governance Tokens are typically dispersed with Initial Coin Offerings (ICOs) or airdrops, where users can get them by staking other cryptocurrencies or by holding a specific quantity of symbols.
What are the advantages of Governance Tokens?
Governance Tokens supply numerous advantages to both DeFi procedures as well as token holders. Firstly, they supply a device for decentralized decision-making, ensuring that the protocol holds to its decentralized nature. This likewise makes certain that the method can adjust to altering market problems and also user demands, making it a lot more resistant and also sustainable over time.
Secondly, Governance Tokens incentivize active participation from token holders, as they have a direct risk in the success of the method. This ensures that token owners are more probable to participate in the decision-making procedure, causing even more informed and autonomous decisions.
Finally, Governance Tokens additionally supply a potential roi for token owners. As the method grows and also comes to be extra effective, the worth of the Governance Tokens may increase, resulting in resources gains for token holders.
What are the challenges of Governance Tokens?
While Governance Tokens offer several advantages, there are also some difficulties that need to be dealt with. https://manocoin.net/category/crypto-exchanges/ Firstly, the circulation of Governance Tokens might not constantly be fair, as those that have much more sources may be able to obtain a larger risk in the protocol. This can result in a focus of power, which might not be preferable in a decentralized system.
Secondly, the decision-making process might be sluggish and inefficient, as token owners might not always settle on the very best strategy. This can bring about hold-ups in implementing adjustments and might hinder the method's growth and also advancement.
Finally, Governance Tokens might also go through regulatory analysis, as they may be considered securities in some jurisdictions. This can cause legal challenges as well as might restrict the fostering of Governance Tokens in particular regions.
Conclusion
Governance Tokens are a crucial part of decentralized financing, making it possible for democratic decision-making and also incentivizing active engagement from token owners. While there are some challenges to be attended to, the benefits of Governance Tokens far surpass the drawbacks. As DeFi continues to grow and expand, Governance Tokens will certainly play a progressively essential function in ensuring the sustainability as well as durability of these methods.
#Blockchain#Crypto Mining#Crypto Security#Crypto Wallets#Decentralized Finance#Crypto Exchanges#Non-Fungible Tokens#Cryptocurrency#DeFi#NFTs
2 notes
·
View notes
Text
👺 “CBDC: La Minaccia alla Privacy nel Mondo delle Valute Digitali Centrali” 👺
🤫 Nel panorama inquietante di un mondo sempre più avvolto nel “pensiero unico”, una nuova minaccia alla privacy emerge con forza: le valute digitali della Banca Centrale, meglio conosciute come CBDC. A differenza delle tradizionali monete cartacee, queste valute digitali centrali (CBDC) presentano rischi senza precedenti per la privacy.

🤫 Un recente rapporto pubblicato da Big Brother Watch, intitolato ‘CBDC — una sterlina che erode la privacy? Lezioni dai piloti internazionali delle valute digitali delle banche centrali per il Regno Unito,’ rivela un’analisi approfondita dei progetti pilota CBDC provenienti da tutto il mondo.
🤫 “Oltre 130 banche centrali nel mondo stanno attualmente studiando, sperimentando o hanno introdotto una forma di Central Bank Digital Currency,” afferma il rapporto. “Tra i paesi che esplorano lo sviluppo di una CBDC c’è il Regno Unito, dove la proposta è soprannominata ‘Britcoin’… Big Brother Watch è preoccupata che una CBDC nel Regno Unito, come delineato nella consultazione, sarebbe dannosa per la privacy delle persone, la libertà di spendere denaro in modo anonimo e il potenziale utilizzo dei dati raccolti per la sorveglianza.”
🤫 Dopo l’analisi dei progetti CBDC in Nigeria, Giamaica, Israele, Uruguay, Svezia, Unione Europea e Cina, Big Brother Watch ha concluso che nessuna delle CBDC preserva la privacy.
🤫 A fronte di queste allarmanti scoperte, Big Brother Watch ha lanciato la campagna “No Spycoin,” incoraggiando le persone a inviare email ai loro rappresentanti in Parlamento:
🤫 “Nessuno ha dimostrato la necessità di una ‘sterlina digitale’ nel Regno Unito, ma ciò comporterebbe un grave costo per la nostra privacy, la libertà finanziaria e l’uguaglianza. I rischi sono enormi. In un peggior caso, una CBDC potrebbe creare una vasta rete di sorveglianza finanziaria e controllo.”
🤫 Tutti i progetti CBDC esaminati hanno sollevato gravi preoccupazioni e tutti hanno rappresentato minacce alla privacy. Mentre chiediamo al governo di ripensare ai loro piani per uno spycoin, questo rapporto ci aiuterà a mostrare ai decisori politici i rischi che una CBDC del Regno Unito comporterebbe per i nostri diritti umani e le libertà civili. Agisci ora. No Spycoin, Big Brother Watch.
🤫 La questione della privacy è strettamente legata al livello di controllo. Poiché coloro che vogliono emettere CBDC desiderano controllare tutte le transazioni, la privacy è impossibile.
🤫 Valuta cartacea o digitale sono attivi fungibili. Possono essere scambiati con altre valute, beni o servizi. La valuta non fungibile è un tipo di asset digitale che non è direttamente sostituibile con un altro asset digitale. Le CBDC sono asset digitali non fungibili e pertanto ogni singola moneta è unica e programmabile in modo personalizzato, indipendentemente dalle altre.
🤫 Per illustrare le limitazioni dello scambio di asset non fungibili, useremo l’esempio di arte e collezionabili come asset non fungibili. Arte e collezionabili hanno proprietà uniche e non possono essere facilmente valutati o scambiati. In circostanze eccezionali, non possiamo acquistare beni, nemmeno altri pezzi d’arte, o pagare servizi utilizzando l’arte come metodo di pagamento.
🤫 Nel suo ‘Manuale Virtuale sulla Central Bank Digital Currency,’ il Fondo Monetario Internazionale cerca di promuovere l’idea che le CBDC sono denaro fungibile. “L’attuazione delle misure di gestione dei flussi di capitale sfrutterebbe la programmabilità delle transazioni CBDC, non della CBDC stessa, poiché il denaro deve rimanere fungibile,” sostiene il FMI.
🤫 Fidarti di ciò che dice il FMI, che fa parte della struttura delle Nazioni Unite? No? Nemmeno Edward Snowden, e può dimostrare perché non dovremmo.
🤫 Edward Snowden, ex contractor dell’intelligence americana e informatore, ha svelato al mondo l’esistenza di un programma di sorveglianza segreto, illegale e pervasivo condotto dalla NSA contro il popolo americano.
🤫 Il mese scorso, si è unito al Logos Podcast per discutere della resistenza alla censura, degli stati cibernetici e della privacy. “La privacy è potere. Se non hai privacy, non hai potere,” ha detto.
🤫 “I governi non vogliono denaro fungibile. Non vogliono denaro sano. Vogliono denaro controllabile. Vogliono denaro che li serva,” ha detto Snowden.
🤫 “Quando vedi tutte queste valute digitali delle banche centrali di cui parlano, indipendentemente dal paese in cui vengono lanciate… l’idea è che possano prendere il tuo denaro e dire ‘puff, è andato’. Possono dire che vogliono accreditare più denaro su questo e puff, è lì.”
🤫 Anche se non è diverso dal funzionamento tradizionale delle valute, ha detto Snowden, le CBDC saranno più facili per loro da raggiungere.
🤫 “Non devono entrare nel tuo materasso, non devono contare le tue banconote, perché possono vedere ogni ‘banconota’ ovunque, tutto il tempo possono tracciare tutti i token CBDC e questo è straordinariamente pericoloso… Questo è ciò che stanno tutti perseguendo,” ha detto.
🤫 Nella sua pagina Substack, Snowden ha pubblicato un articolo nel 2021 spiegando cos’è una CBDC, o come ha scritto: “Piuttosto, ti dirò cos’è una NON CBDC — NON è, come Wikipedia potrebbe dirti, un dollaro digitale.” È semplicemente un’entrata nel database di una banca.
🤫 Ha fornito l’immagine sotto per dimostrare che, indipendentemente da come sono implementate, le CBDC non possono esistere senza che la banca centrale conosca i dettagli di ogni transazione.
🤫 “Né una Central Bank Digital Currency è un abbraccio a livello di stato della criptovaluta, almeno non della criptovaluta come attualmente la intende praticamente tutto il mondo che la utilizza,” ha scritto.
🤫 Invece, una CBDC è qualcosa di più vicino a essere una perversa versione della criptovaluta, o almeno dei principi fondamentali e dei protocolli della criptovaluta — una valuta cripto-fascista, un gemello malvagio inserito nei registri nel Giorno Opposto, progettato appositamente per negare ai suoi utenti la proprietà di base del loro denaro e per installare lo Stato al centro di ogni transazione.
🤫 “Your Money AND Your Life: Le Central Banks Digital Currencies riscatteranno il nostro futuro,” Edward Snowden, 9 ottobre 2021.
🚨 Scopri come Bitcoin sta veramente cambiando il mondo!
Entra nella nostra community Telegram per approfondire la discussione sulla rivoluzione Bitcoin, strategie di trading e altro ancora! 🚀
📣 https://t.me/Bitcoin_Report_Italia
🚀 Leggi tutti i nostri articoli: https://t.me/BitcoinReportChannel
#blockchain technology#bitget#btc#cryptocurrency#cryptonews#blockchain development#cryptocurency news#decentralized#business#bitcoin#crypto#cbdc#wef#davos#privacy#online privacy#internet security#edward snowden#agenda 2030
2 notes
·
View notes
Text
Pinksale: The Biggest Launchpad on BNB Chain
The world of cryptocurrency has witnessed remarkable growth, and with it, the rise of various blockchain networks catering to different needs. Binance Smart Chain (BNB) has emerged as a prominent player, providing a robust ecosystem for decentralized applications and token sales. Among the projects making waves on the BNB chain is Pinksale, a platform that enables seamless and secure token sales.…

View On WordPress
#Binance#Binance Chain#Blockchain#BNB#BNB Chain#Cryptocurrency#PINK#Pinksale#Security#Tokenomics#Value
10 notes
·
View notes
Text
How To Become Cybersecurity Expert: Scope, Skills, and Salary
In today's digitally interconnected world, it is of utmost importance to secure your company from online threats. Cybersecurity experts play a crucial role in achieving this goal. Their primary responsibility is to proactively identify and prevent potential attacks. They conduct scans and analyze network data to detect any weaknesses and dangers in networks, data centres, and software systems. Additionally, they ensure that hardware and software are always kept up-to-date.
In this article, we'll explore what a cybersecurity professional does, the skills they need, the career growth possibilities, and the typical salary. You can enhance your knowledge in this field by taking a cybersecurity certification online course to learn about modern information and system protection technologies.
What Does a Cybersecurity Specialist Do?
A cyber security specialist is essentially a guardian of computer networks and systems. Their primary mission is to shield these digital domains from a multitude of cyber threats while ensuring the confidentiality, integrity, and availability of critical data. Here are some key responsibilities of a cyber security specialist:
Identifying Vulnerabilities: Their first task is to hunt down and fix security weaknesses in networks, data centres, and software systems. Think of them as the digital detectives who uncover potential entry points for cybercriminals.
Implementing Security Controls: Cyber security specialists employ a variety of security measures such as firewalls, encryption, and multi-factor authentication to fortify digital assets against potential attacks. These measures act as digital barriers, thwarting unauthorized access.
Monitoring Activity: They keep a vigilant eye on network and system activity, looking for any signs of intrusion or suspicious behaviour. This proactive approach enables them to respond swiftly to potential threats.
Responding to Incidents: In the event of a cyberattack, cyber security specialists jump into action. They react swiftly, notifying law enforcement, restoring backups, and communicating with the affected parties through public statements.
Keeping Up with Trends: The ever-evolving nature of cyber threats means that cyber security specialists must stay updated on the latest trends and technologies in the field. Being one step ahead is essential in this game.
Depending on their specialization and level of expertise, cyber security specialists may have different job titles, including:
Cybersecurity Analyst: Responsible for planning, implementing, and monitoring security strategies within an organization.
Cybersecurity Engineer: Designing and building systems to safeguard digital information.
Cybersecurity Architect: Developing and overseeing an organization's entire cyber security strategy.
Cybersecurity Manager: Formulating and implementing security policies while managing security teams.
Penetration Tester: Simulating cyberattacks to identify security weaknesses and providing recommendations.
Chief Information Security Officer: Leading an organization's cybersecurity efforts and collaborating with other executives.
Information Security Crime Investigator: Reviewing evidence to determine if cybercrimes have occurred and assisting law enforcement in apprehending suspects.
Cybersecurity Consultant: Advising organizations on how to identify and mitigate network risks.
Cybersecurity Specialist Skills
Cybersecurity specialist requirements include a blend of technical and soft skills. Here's a breakdown:
Technical Skills:
Network Security: The ability to protect networks from unauthorized access, misuse, or disruption is a foundational skill.
Cryptography: Understanding mathematical techniques to encrypt and decrypt data is essential for securing sensitive information.
Risk Management: Assessing and mitigating potential threats to an organization's information systems is crucial to avoid vulnerabilities.
Cybersecurity Tools and Technologies: Proficiency in using various software and hardware tools for tasks like scanning, testing, and auditing is vital.
Soft Skills:
Communication Skills: Effectively conveying security concepts and findings to both technical and non-technical audiences is essential for collaboration and understanding.
Problem-Solving Skills: The ability to analyze complex situations and find effective solutions is key to navigating the ever-changing cyber landscape.
Critical Thinking Skills: Evaluating information objectively and logically helps make informed decisions in high-pressure situations.
Strategic Thinking Skills: Planning and anticipating future scenarios enable proactive security measures.
How to Become a Cybersecurity Specialist?
Entering the field of cyber security can be achieved through various avenues. Here are some common paths:
Formal Education: Enroll in college or university programs that offer degrees or diplomas in cyber security or related fields. This provides a solid academic foundation.
Self-Study and Certification: Study independently using online resources and obtain relevant certifications to showcase your knowledge and skills. This self-driven approach allows flexibility.
Volunteering and Training: Seek opportunities to volunteer or join organizations offering cybersecurity training programs or internships. Practical experience is invaluable.
Entrepreneurship: Consider starting your own cybersecurity business or joining a team of experts. This path offers autonomy and the chance to work on diverse projects.
What Certifications are Needed for Cybersecurity?
Cyber security certifications are vital for validating your expertise and commitment to the field. They also provide a structured path for acquiring the necessary skills and knowledge. Here are some common certifications:
Certified Cybersecurity Expert™: Ideal for entry-level professionals, this certification covers the fundamentals of cyber security, including network security, threat management, and cryptography.
Certified Information Security Executive™: Designed for experienced professionals, it delves into advanced aspects like security architecture, risk management, and governance.
Certified White Hat Hacker™: Specializing in offensive security, this certification covers ethical hacking techniques, including penetration testing, vulnerability assessment, and malware analysis.
Salary Expectations for Cybersecurity Specialists
The salary of a cyber security specialist can vary based on factors such as location, experience, education, and certifications. However, the average salary in the United States is approximately $117,419 per year. Experienced professionals can command even higher earnings, while those with advanced degrees or certifications enjoy enhanced job prospects.
In conclusion, cyber security is a dynamic and rewarding field that offers a wide array of career opportunities. By understanding the role, acquiring the necessary skills and certifications, and exploring salary prospects, you can embark on a fulfilling journey to become a cybersecurity specialist. Online cyber security certification courses are readily available to help you gain knowledge and skills in modern information and system protection technologies. With dedication and the right tools, you can help safeguard the digital world from cyber threats and play a crucial role in our increasingly digital lives.
If you're interested in pursuing cyber security or blockchain security certifications with a focus on emerging technologies like blockchain, consider exploring the offerings provided by the Blockchain Council. The Blockchain Council is a respected consortium of subject matter experts and enthusiasts dedicated to advancing blockchain research and development, exploring use cases and products, and disseminating knowledge for a better world.
2 notes
·
View notes
Text
Exploring WEB3: The Decentralized Future of the Internet
Hey friends! 🌐 Discover the transformative power of #WEB3 - the decentralized future of the internet. Unveil the benefits of data privacy, ownership, and smart contracts that empower users. #Decentralization #BlockchainTech #DigitalEmpowerment
The Internet has revolutionized the way we live, communicate, and conduct business. With its widespread adoption, the centralized nature of the current web has become increasingly apparent, raising concerns about data privacy, security, and control. WEB3 emerges as a promising solution, aiming to reshape the digital landscape by decentralizing control and empowering users. In this blog, we will…

View On WordPress
#autonomy#blockchain technology#blockchain transparency#content delivery#data privacy#data security#decentralized finance#decentralized governance#decentralized intermediaries#decentralized internet#decentralized social media#DeFi#digital identity#immutable ledger#NFTs#non-fungible tokens#ownership#reputation#Smart Contracts#transparent transactions#Trust#user empowerment#user-centric internet#Web hosting#WEB3#WEB3 benefits
4 notes
·
View notes
Text
Tronpick.io: The Ultimate Destination for Crypto Enthusiasts

Cryptocurrencies have emerged as the most talked-about and debated topic in the financial world. The digital currencies have brought a paradigm shift in the way people perceive money, investments, and transactions. The decentralized and secure nature of cryptocurrencies has made them popular among people across the globe. And Tronpick.io is a platform that is leading the revolution in the world of cryptocurrencies.
Tronpick.io is a decentralized platform that is built on the Tron blockchain. It offers a range of services, including cryptocurrency trading, staking, and liquidity provision. The platform is designed to provide users with a seamless and secure trading experience. With its user-friendly interface, Tronpick.io is a one-stop-shop for all your cryptocurrency needs.
Here are some of the top features of Tronpick.io that make it stand out from other cryptocurrency platforms:
Security
Security is a top priority for Tronpick.io, and the platform has implemented several security measures to protect user funds and personal information. The platform uses state-of-the-art encryption technology to secure user data and funds. Additionally, Tronpick.io follows strict KYC and AML policies to ensure that only legitimate users can access the platform.
2. User-friendly Interface
Tronpick.io has a user-friendly interface that makes it easy for users to navigate the platform. Whether you are a beginner or an experienced trader, you will find it easy to use Tronpick.io. The platform offers a range of trading tools and features that can help you make informed trading decisions.
3. Range of Cryptocurrencies
Tronpick.io supports a wide range of cryptocurrencies, including TRX, USDT, BTC, ETH, and more. You can trade these cryptocurrencies against each other or against fiat currencies like USD and EUR.
4. Liquidity Provision
Tronpick.io offers liquidity provision services, which can help traders access liquidity and improve trading performance. The platform has a dedicated team that works to ensure that there is always sufficient liquidity on the platform.
5. Staking
Tronpick.io also offers staking services that enable users to earn passive income by holding cryptocurrencies. You can stake your cryptocurrencies and earn rewards in the form of additional tokens or coins.
Conclusion
Tronpick.io is a reliable and secure platform that offers a range of services for crypto enthusiasts. With its user-friendly interface, a wide range of cryptocurrencies, and advanced security features, Tronpick.io is the ultimate destination for traders and investors looking to take their cryptocurrency game to the next level. Sign up today and start making money at
https://tronpick.io/?ref=Bevpro
2 notes
·
View notes
Link
11 notes
·
View notes
Text
VerifBox is a secure and reliable solution for digital image verification, enabling you to notarize your images on the Ethereum blockchain
Table of Contents
Introduction
What is VerifBox and How Does it Use the Ethereum Blockchain to Notarize Images?
The Benefits of Notarizing Images on the Ethereum Blockchain with VerifBox
How to Ensure the Security and Reliability of Digital Images with VerifBox
What You Need to Know Before Notarizing Your Images with VerifBox
What is the Cost of Notarizing Images on the Ethereum Blockchain…

View On WordPress
#Authentication#blockchain#Cryptocurrency#Decentralization#Digital assets#Ethereum#Immutable#Innovation#Interoperability#MINTER#NFT#Notarization#ownership#Scalability#security#Smart Contracts#Tokenization#Transparency#Trust#verification
2 notes
·
View notes
Text
Crypto Tokens: The New Shade of Lifestyle

#Crypto tokens are digital assets that use cryptography to secure their transactions and to control the creation of new units. Crypto tokens#Crypto tokens are created through a process called “tokenization.” In tokenization#a company converts some of its assets into digital tokens that can be traded on a blockchain. These tokens can represent anything from the#Crypto power up the Dapps#Crypto tokens are often used to power dapps. Dapps are applications that are built on top of a blockchain platform. These applications use#a company might issue tokens that represent shares of its stock. These tokens can be traded on a blockchain and can be used to purchase pro#What are the benefits of using crypto tokens?#Crypto tokens offer a number of benefits over traditional cryptocurrencies. They are easier to use and can be integrated into a variety of#crypto tokens offer a number of benefits to businesses#including faster transactions and lower costs.#Tokens improve your lifestyle#In the modern world#people are always looking for new and innovative ways to improve their lifestyles. One of the latest trends in the use of crypto tokens to#including:#Paying for goods and services: Crypto tokens can be used to pay for goods and services#both online and offline. This makes it easy to purchase items without having to use a traditional currency.#Reducing transaction costs: The use of crypto tokens can help to reduce transaction costs#as there are no fees associated with the use of tokens. This can save you money when you are making purchases online or in-store.#Earning rewards: Many crypto tokens offer rewards for their users. This can include discounts on products or services or bonus points that#Improving security: One of the main advantages of using crypto tokens is the increased security that they offer. Tokens are stored on block#which is a secure and tamper-proof system. This makes it difficult for criminals to steal your tokens or access your information.#Choose the right token for your lifestyle#So#how can you start using crypto tokens to improve your lifestyle? There are a number of options available#so it’s important to do your research and find the right token for you.
3 notes
·
View notes
Photo
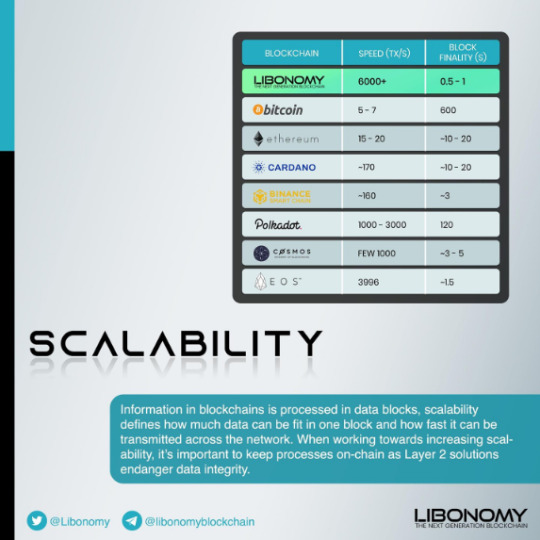
Build your technology on Libonomy Consensus and your find you have no limits, your be faster than any other. You have AI keeping you secure, totally decentralized from the second your download LibonomyOS.
2 notes
·
View notes
Link
Azgari Lipshy writes about technology, yoga and her solo travels around the world. She is a degreed quota-carrying technology industry sales and account management professional with progressive territory growth for enterprise and channel sales.
3 notes
·
View notes
Note
So as far as I can tell jyp is still going to be making photocards and stuff just not a physical cd? Hybe actually did this too recently with jhope's solo where for cheaper you could buy a "special" idk what they actually called it but it was 2 or 3 photocards and a qr code card that presumably linked to the digital version of everything else that typically would be in an album. My biggest worry with this idea would be if they end up doing something closer to nfts by trying to go full virtual
eh it's not going to go to nfts specifically bc they can't make the claim that they're doing it 'for the environment' to then turn around and do something worse for the environment. also there's no payout for nfts anymore and one fandom has already successfully bullied a company out of them. it's more likely to be headed towards exclusive streaming apps and the like so that they can mandate that people do things like pay for subscriptions in order to have access to stuff they already bought (which a lot of tech companies already do).
#theyre probably looking into some kind of blockchain tech bc a lot of companies are in terms of potentiality for exclusivity#+ security#but none of the tech is actually there yet and there's been a falloff from crypto + related in the public eye#so it might be a while before any of that makes it to consumers again#they'll test with the photocard only digital copies like ist and hybe for now#but i still think getting rid of producing all physical cds is a bad idea and they should have both options available#text#answers
2 notes
·
View notes
Text
it rly depends on the slot but really i kind of want to change my major from gaming to information security
#if i dont get into information security then maybe cloud computing#i dont think im interested in IOT or devops but hmmm#and theres literally no benefit in studying blockchain bc that branch hasnt developed enuf in my uni yet#im not taking any risk ;-;#i mean Technically speaking my major is comp science but like idk is it called specialization or major#those r such western terms how do i even define my degree lmao
3 notes
·
View notes