#safeguarding data
Text
oh no, past me, what the hell does this mean????
#talkForge#I know what it LITERALLY means: it means do not delete and it's used to stop the deletion process of the reaction#when you make a decision that affects MC's personality the backend will note how you reacted; implement the personality change; and then#it will delete your reaction (as a safeguard against the game incrementing your personality when you haven't made a choice just because it#technically has the data)#this keeps it from deleting the data...but why?#you make another personality choice at the end of the passage so it's replacing the data anyway why would it need to save your reaction?#the only use case I can imagine is if I wanted to use your reaction further down the line and don't have a choice in between initial choice#and the reaction...but that's not true here#god I have to start commenting my own code
24 notes
·
View notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
Upholding Legal Rights: Gujarat High Court's Stance on Income Tax Department's Seizure
In a recent development at the Gujarat High Court, a division bench comprising Justices Bhargav Karia and Niral Mehta has taken a firm stance regarding the seizure of “non-incriminating” data from a lawyer’s office by the Income Tax department. Refusing to accept the department’s undertaking on sealing the data, the bench has decided to delve into the matter on its merits.
The petition before…

View On WordPress
#court hearing#data seizure#fundamental rights#Gujarat High Court#Income Tax Department#judicial process#lawyer&039;s office raid#legal case#legal challenges#legal counsel#legal integrity#legal justice#legal principles#Legal Proceedings#legal resolution#legal rights#legal safeguards#legal scrutiny#Natural Justice
0 notes
Link
#AI#Comfort#Data#Exploring#Financial#Future#Grow#home#inheritance#Money#Online#retirement#Risk#Safeguard#Sales#Selling#Sensitive#Value#work
0 notes
Text
You're a reasonably informed person on the internet. You've experienced things like no longer being able to get files off an old storage device, media you've downloaded suddenly going poof, sites and forums with troves full of people's thoughts and ideas vanishing forever. You've heard of cybercrime. You've read articles about lost media. You have at least a basic understanding that digital data is vulnerable, is what I'm saying.
I'm guessing that you're also aware that history is, you know... important? And that it's an ongoing study, requiring ... data about how people live? And that it's not just about stanning celebrities that happen to be dead?
Congratulations, you are significantly better-informed than the British government!
So they're currently like "Oh hai can we destroy all these historical documents pls? To save money? Because we'll digitise them first so it's fine! That'll be easy, cheap and reliable -- right? These wills from the 1850s will totally be fine for another 170 years as a PNG or whatever, yeah? We didn't need to do an impact assesment about this because it's clearly win-win! We'd keep the physical wills of Famous People™ though because Famous People™ actually matter, unlike you plebs. We don't think there are any equalities implications about this, either! Also the only examples of Famous People™ we can think of are all white and rich, only one is a woman and she got famous because of the guy she married. Kisses!"
Yes, this is the same Government that's like "Oh no removing a statue of slave trader is erasing history :("
You have, however, until 23 February 2024 to politely inquire of them what the fuck they are smoking. And they will have to publish a summary of the responses they receive. And it will look kind of bad if the feedback is well-argued, informative and overwhelmingly negative and they go ahead and do it anyway. I currently edit documents including responses to consultations like (but significantly less insane) than this one. Responses do actually matter.
I would particularly encourage British people/people based in the UK to do this, but as far as I can see it doesn't say you have to be either. If you are, say, a historian or an archivist, or someone who specialises in digital data do say so and draw on your expertise in your answers.
This isn't a question of filling out a form. You have to manually compose an email answering the 12 questions in the consultation paper at the link above. I'll put my own answers under the fold.
Note -- I never know if I'm being too rude in these sorts of things. You probably shouldn't be ruder than I have been.
Please do not copy and paste any of this: that would defeat the purpose. This isn't a petition, they need to see a range of individual responses. But it may give you a jumping-off point.
Question 1: Should the current law providing for the inspection of wills be preserved?
Yes. Our ability to understand our shared past is a fundamental aspect of our heritage. It is not possible for any authority to know in advance what future insights they are supporting or impeding by their treatment of material evidence. Safeguarding the historical record for future generations should be considered an extremely important duty.
Question 2: Are there any reforms you would suggest to the current law enabling wills to be inspected?
No.
Question 3: Are there any reasons why the High Court should store original paper will documents on a permanent basis, as opposed to just retaining a digitised copy of that material?
Yes. I am amazed that the recent cyber attack on the British Library, which has effectively paralysed it completely, not been sufficient to answer this question for you. I also refer you to the fate of the Domesday Project. Digital storage is useful and can help more people access information; however, it is also inherently fragile. Malice, accident, or eventual inevitable obsolescence not merely might occur, but absolutely should be expected. It is ludicrously naive and reflects a truly unpardonable ignorance to assume that information preserved only in digital form is somehow inviolable and safe, or that a physical document once digitised, never need be digitised again..At absolute minimum, it should be understood as certain that at least some of any digital-only archive will eventually be permanently lost. It is not remotely implausible that all of it would be. Preserving the physical documents provides a crucial failsafe. It also allows any errors in reproduction -- also inevitable-- to be, eventually, seen and corrected. Note that maintaining, upgrading and replacing digital infrastructure is not free, easy or reliable. Over the long term, risks to the data concerned can only accumulate.
"Unlike the methods for preserving analog documents that have been honed over millennia, there is no deep precedence to look to regarding the management of digital records. As such, the processing, long-term storage, and distribution potential of archival digital data are highly unresolved issues. [..] the more digital data is migrated, translated, and re-compressed into new formats, the more room there is for information to be lost, be it at the microbit-level of preservation. Any failure to contend with the instability of digital storage mediums, hardware obsolescence, and software obsolescence thus meets a terminal end—the definitive loss of information. The common belief that digital data is safe so long as it is backed up according to the 3-2-1 rule (3 copies on 2 different formats with 1 copy saved off site) belies the fact that it is fundamentally unclear how long digital information can or will remain intact. What is certain is that its unique vulnerabilities do become more pertinent with age." -- James Boyda, On Loss in the 21st Century: Digital Decay and the Archive, Introduction.
Question 4: Do you agree that after a certain time original paper documents (from 1858 onwards) may be destroyed (other than for famous individuals)? Are there any alternatives, involving the public or private sector, you can suggest to their being destroyed?
Absolutely not. And I would have hoped we were past the "great man" theory of history. Firstly, you do not know which figures will still be considered "famous" in the future and which currently obscure individuals may deserve and eventually receive greater attention. I note that of the three figures you mention here as notable enough to have their wills preserved, all are white, the majority are male (the one woman having achieved fame through marriage) and all were wealthy at the time of their death. Any such approach will certainly cull evidence of the lives of women, people of colour and the poor from the historical record, and send a clear message about whose lives you consider worth remembering.
Secondly, the famous and successsful are only a small part of our history. Understanding the realities that shaped our past and continue to mould our present requires evidence of the lives of so-called "ordinary people"!
Did you even speak to any historians before coming up with this idea?
Entrusting the documents to the private sector would be similarly disastrous. What happens when a private company goes bust or decides that preserving this material is no longer profitable? What reasonable person, confronted with our crumbling privatised water infrastructure, would willingly consign any part of our heritage to a similar fate?
Question 5: Do you agree that there is equivalence between paper and digital copies of wills so that the ECA 2000 can be used?
No. And it raises serious questions about the skill and knowledge base within HMCTS and the government that the very basic concepts of data loss and the digital dark age appear to be unknown to you. I also refer you to the Domesday Project.
Question 6: Are there any other matters directly related to the retention of digital or paper wills that are not covered by the proposed exercise of the powers in the ECA 2000 that you consider are necessary?
Destroying the physical documents will always be an unforgivable dereliction of legal and moral duty.
Question 7: If the Government pursues preserving permanently only a digital copy of a will document, should it seek to reform the primary legislation by introducing a Bill or do so under the ECA 2000?
Destroying the physical documents will always be an unforgivable dereliction of legal and moral duty.
Question 8: If the Government moves to digital only copies of original will documents, what do you think the retention period for the original paper wills should be? Please give reasons and state what you believe the minimum retention period should be and whether you consider the Government’s suggestion of 25 years to be reasonable.
There is no good version of this plan. The physical documents should be preserved.
Question 9: Do you agree with the principle that wills of famous people should be preserved in the original paper form for historic interest?
This question betrays deep ignorance of what "historic interest" actually is. The study of history is not simply glorified celebrity gossip. If anything, the physical wills of currently famous people could be considered more expendable as it is likely that their contents are so widely diffused as to be relatively "safe", whereas the wills of so-called "ordinary people" will, especially in aggregate, provide insights that have not yet been explored.
Question 10: Do you have any initial suggestions on the criteria which should be adopted for identifying famous/historic figures whose original paper will document should be preserved permanently?
Abandon this entire lamentable plan. As previously discussed, you do not and cannot know who will be considered "famous" in the future, and fame is a profoundly flawed criterion of historical significance.
Question 11: Do you agree that the Probate Registries should only permanently retain wills and codicils from the documents submitted in support of a probate application? Please explain, if setting out the case for retention of any other documents.
No, all the documents should be preserved indefinitely.
Question 12: Do you agree that we have correctly identified the range and extent of the equalities impacts under each of these proposals set out in this consultation? Please give reasons and supply evidence of further equalities impacts as appropriate.
No. You appear to have neglected equalities impacts entirely. As discussed, in your drive to prioritise "famous people", your plan will certainly prioritise the white, wealthy and mostly the male, as your "Charles Dickens, Charles Darwin and Princess Diana" examples amply indicate. This plan will create a two-tier system where evidence of the lives of the privileged is carefully preserved while information regarding people of colour, women, the working class and other disadvantaged groups is disproportionately abandoned to digital decay and eventual loss. Current and future historians from, or specialising in the history of minority groups will be especially impoverished by this.
16K notes
·
View notes
Text
A Guide to Safeguard Your Digital World
With the rapidly growing digital landscape, cybersecurity is the guardian of our online well-being, serving as a vital shield against many cyber threats. Its significance cannot be overstated, as it safeguards our personal information and ensures the integrity and security of our digital transactions and communications.
For every individual navigating the vast expanse of the internet, possessing a foundational understanding of cybersecurity is akin to possessing a compass in uncharted territory – essential for steering clear of potential dangers and safeguarding one's digital identity and assets.
In this beginner's guide, we embark on a journey to unravel cybersecurity fundamentals, empowering users with practical knowledge and strategies to fortify their online defenses and navigate the digital world with confidence and peace of mind.
Navigating Cyber Threats: A Simple Overview
Cyber threats come in various forms, ranging from simple phishing emails to complex ransomware attacks and nation-state-sponsored cyber espionage. These threats exploit vulnerabilities in software, networks, and human behavior to gain unauthorized access to sensitive information, disrupt operations, and cause financial harm. With the proliferation of internet-connected devices and the increasing digitization of critical infrastructure, the attack surface for cybercriminals has expanded exponentially, making cybersecurity a paramount concern for individuals, businesses, and governments alike.
The Evolution of Cyber Defense
As cyber threats continue to evolve in complexity and sophistication, the field of cybersecurity has likewise evolved to combat these challenges. Traditional security approaches focused on perimeter defense and reactive measures are no longer sufficient in today's dynamic threat landscape. Instead, cybersecurity professionals are embracing a proactive and multi-layered approach to defense, incorporating technologies such as artificial intelligence, machine learning, and behavioral analytics to detect and mitigate threats in real-time. Additionally, cybersecurity awareness training for employees has become a critical component of defense, as human error remains one of the most significant vulnerabilities in any organization's security posture.
"A Guide to Safeguard Your Digital World" is a comprehensive resource designed to empower individuals with the knowledge and tools needed to protect themselves in today's digital landscape. In addition to the practical strategies outlined in this guide, consider further enhancing your cybersecurity skills with online courses available on Study24hr.com. With a wide range of courses, Study24hr.com offers convenient and accessible learning opportunities for individuals looking to strengthen their digital defenses. Don't hesitate – leap and navigate the digital terrain with assurance by engaging with this invaluable platform today.”
Easy Ways to Boost Your Cybersecurity
Enhance your online security effortlessly through the straightforward methods outlined below. Explore easy yet impactful techniques to fortify your digital protections and surf the web with assurance.
1. Password Power
One of the easiest and most effective ways to protect your online accounts is by using strong, unique passwords. Avoid using easily guessable passwords like "password123" or "123456" and opt for complex combinations of letters, numbers, and symbols. Consider using a reputable password manager to securely store and manage your passwords across different accounts.
2. Stay Updated
Keeping your devices and software up to date is crucial for staying protected against cyber threats. Software updates often contain security patches that address known vulnerabilities, so be sure to regularly install updates for your operating system, antivirus software, web browsers, and other applications.
3. Beware of Phishing
Phishing attacks are one of the most common tactics used by cybercriminals to trick individuals into revealing sensitive information. Be cautious of unsolicited emails, messages, or phone calls asking for personal or financial information. Look out for red flags such as misspelled URLs, urgent requests for action, and suspicious attachments or links.
4. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security to your accounts by requiring a second form of verification, such as a one-time code sent to your phone, in addition to your password. Enable 2FA whenever possible to protect your accounts from unauthorized access, even if your password is compromised.
5. Secure Your Wi-Fi Network
Securing your home Wi-Fi network is essential for protecting your internet-connected devices from unauthorized access. Enable WPA2 or WPA3 encryption, change the default administrator password for your router, and consider hiding your network's SSID to make it less visible to potential attackers.
6. Back Up Your Data
Regularly backing up your important files and data is essential for mitigating the impact of potential cyber incidents such as ransomware attacks or hardware failures. Use cloud storage services or external hard drives to create backups of your files and ensure that they are stored securely.
7. Educate Yourself
Staying informed about the latest cybersecurity threats and best practices is key to protecting yourself online. Take advantage of resources such as online courses, articles, and cybersecurity awareness campaigns to learn more about how to stay safe and secure in the digital world.
The Last Word
It is acknowledged that cybersecurity is a critical pillar of our digital society, safeguarding our data, privacy, and economic prosperity. As the cyber threat landscape continues to evolve, we must remain vigilant, proactive, and collaborative in our approach to cybersecurity. By investing in robust defense mechanisms, fostering a culture of cyber awareness, and promoting information sharing and collaboration, we can build a more resilient and secure digital future for generations to come.
#cybersecurity#data#analytics#data security#privacy#cyber threats#safeguard#business#information security
0 notes
Text
Safeguarding Success: The Crucial Role of Data Protection in E-Commerce Business
#Safeguarding Success: The Crucial Role of Data Protection in E-Commerce Business#starting your business on the right side of the law#what is the use of firewall in a computer#computers privacy & data protection#business#e-commerce#need of encryption and decryption in cryptography#small business credit card processing#starting a business legally#data protection and artificial intelligence#ecommerce success#business communication#the power of personalization: unlocking e-commerce success (free planning kit)
1 note
·
View note
Text

How to Protect Intellectual Property (IP) Data from Modern Bad Actors?
Safeguard Intellectual Property IP Data from Insider and outsider bad actors Kirit shares 6 steps roadmap for the protection of IP data.
#Best IP Data Security Practices#Encrypting Intellectual Property Data#Insider Threat to IP Data#Intellectual Property (IP) Data#Intellectual Property Data#IP Data Protection#IP Data Protection Strategy#IP Data Risk Assessment#IP Data Security#Outsider Threat to IP Data#Safeguard IP (Intellectual Property) Data
0 notes
Text
Data Guardians: Flexcub's Secure Cloud Approach
Data Guardians Explore Flexcub's pioneering approach to cloud-based security and privacy Learn how we safeguard your data with innovative solutions and cutting-edge technology
To know more: https://flexcub.com/blog/data-guardians-explore-flexcubs-secure-cloud-approach/
0 notes
Text

https://goodlawproject.org/crowdfunder/nhs-cyp-guidance/?fbclid=PAZXh0bgNhZW0CMTEAAaadkVMoRUHpcFptnjlifnc1xJ0i7YGVi78tfv2vEXVaVIQDPTEp1-ozNcY_aem_AfqNP9xEERFn6GRCZCIP7B2RriLi8ZN7pVAFzmNwdvqIXW0nmc1mTe5Hq0UV3xC6VPWdYe1x64wHk7O6-HPOhIdf
Please share, tag someone who could bring this to a lot of people, and post to other platforms. Not originally mine, idk who is the source of the screenshots.
Image ID under cut
Image ID:
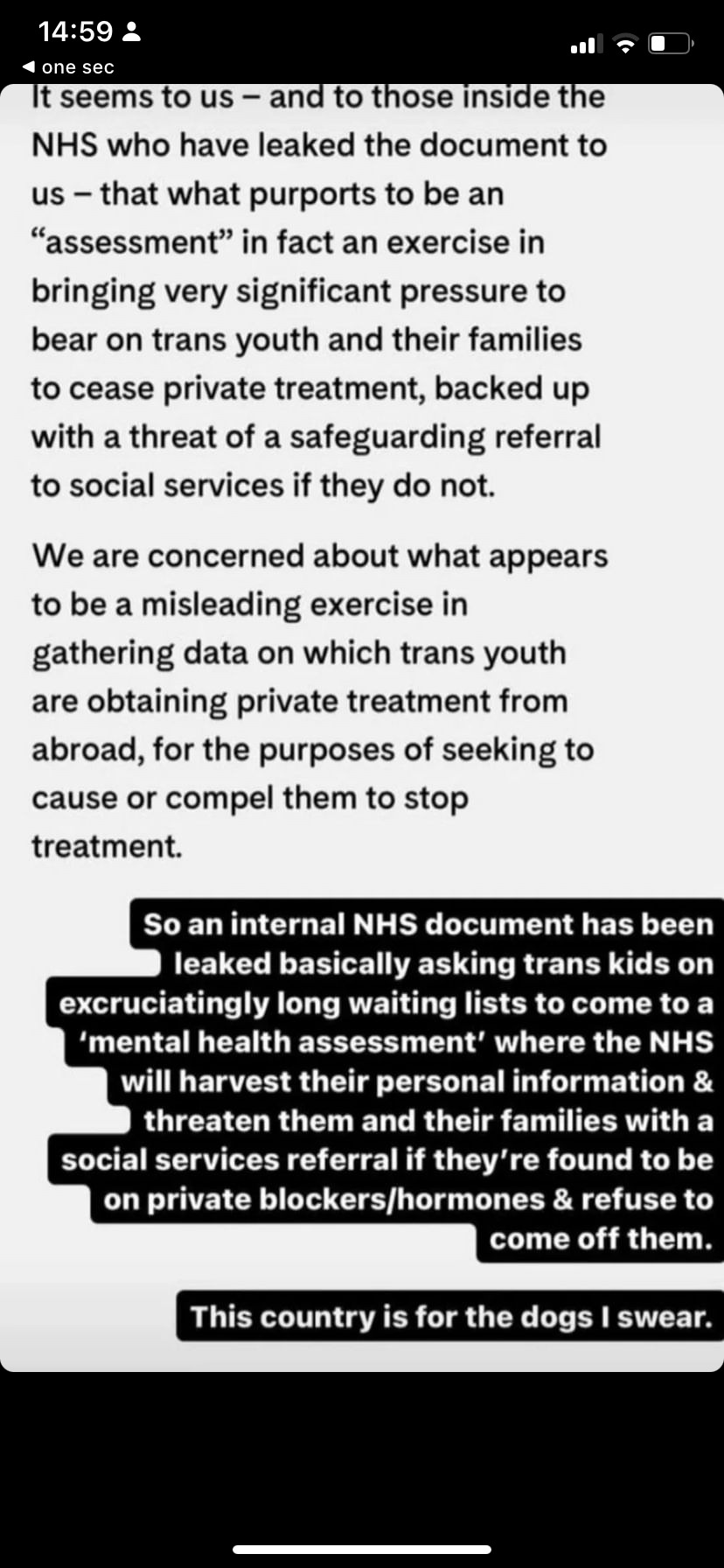
In thick white text on black background-> NHS ENGLAND ARE PLANNING A HONEYPOT WHERE THEY SEND ALL KIDS ON GIDS WAITLIST TO CAHMS TO HAVE THEM BE ASKED IF THEY ARE TAKING BLOCKERS/HRT VIA PRIVATE OR DIY ROUTES
Text is broken and in the middle is an excerpt from a leaked nhs document-> a) For medication sourced directly (e.g via the internet), explain the increased risks of harm due to the unregulated nature of these medicines/products. These may include the use of counterfeit chemicals, unsafe/unknown ancilliary ingredients or variability of potency etc. More information can be found here (link to nhs website). // b) Do not initiate or continue prescribing puberty surpressing hormones or gender affirming hormones. The General Medical Council's guidance to medical professionals on 'bridging prescriptions (a course of endocrine intervention managed by a healthcare professional outside of the specialised gender service while an individual is waiting to be seen) does not apply to care offered to young people under 18 years of age. // c) If the child/young person or their carer disregards your advice and you consider that this puts the child/young person at increased risk, then a safeguarding referral might also be appropriate in line with standard safeguarding approaches. Discuss with your line manager and your organization's safeguarding team.
Thick white text on black background continues-> ANY WHO SAYS YES AND DO NOT DESIST FROM DOING SO WILL BE THREATENED WITH SAFEGUARDING REFERRAL (TAKEN INTO STATE CARE)
Next image ID:
In black text on white background, from the news article linked above-> It seems to us - and to those inside the NHS who have leaked the document to us - that what purports to be an "assessment" in fact an exercise in bringing very significant pressure to bear on trans youth and their families to cease private treatment, backed up with a threat of a safeguarding referral to social services if they do not. // We are concerned about what appears to be a misleading exercise in gathering data on which trans youth are obtaining private treatment from abroad, for the purposes of seeking to cause or compel them to stop treatment.
In the same thick white text on black background as previous image-> So an internal NHS document has been leaked basically asking trans kids on excruciatingly ling waiting lists to come to a 'mental health assessment' where the NHS will harvest their personal information & threaten their families with a social services referral if they're found to be on private blockers/hormones & refuse to come off them. // This country is for dogs i swear.
#trans pride#transblr#trans safety#trans tips#trans uk#uk trans#uk#england#trans ftm#trans mtf#trans nonbinary#trans man#trans woman#trans male#trans female#trans masc#trans femme#transmasculine#transmasc#trans feminine#transfem#trans enby#enby#nonbinary#gender nonconforming#genderqueer#gender queer#gnc#lesbian#gay
5K notes
·
View notes
Text
The Crucial Role of Enterprise Risk Management in Modern Healthcare

Imagine you're a tightrope walker, thousands of feet above the ground. Without a safety net, any misstep can lead to disaster. Now, think of the healthcare sector as this tightrope walker. With the myriad of complexities, regulations, and unpredictable factors that can pop up every day, having a robust safety net is paramount. Entering the safety net we all need: enterprise risk management software in healthcare. This is not just any safety net; it's a dynamic, adaptable, and resilient one that assures everyone on the rope can perform their best without the constant fear of falling.
Ready to know more? Let's unravel the magic thread by thread, shall we?
What is Enterprise Risk Management in Healthcare Anyway?
You might be wondering, what's the big deal about enterprise risk management in healthcare? Let's break it down. At its core, it's about identifying potential risks, assessing them, and putting in place strategies to manage those risks. Think of it as a proactive approach rather than a reactive one.
In the healthcare sector, there are countless unpredictable factors. From patient care challenges to technology hiccups to regulatory changes. Having a system that spots potential threats before they escalate? That’s the golden ticket.
And guess what? This golden ticket isn't reserved for a select few. Every stakeholder, from medical professionals to administrative staff, plays a part in making enterprise risk management in healthcare a success.
By embracing this approach, healthcare providers ensure smoother operations, better patient outcomes, and yes, a sigh of relief knowing they're backed up by a robust system.
The Game-Changing Benefits of Enterprise Risk Management in Healthcare
Sure, enterprise risk management in healthcare sounds neat, but what's in it for the healthcare sector? Well, a lot. For starters, it helps in early risk detection. By spotting issues before they blow up, institutions can save resources, reputation, and most importantly, lives.
Secondly, it promotes a culture of safety. When everyone is tuned into the risk management frequency, it fosters an environment where safety is the norm, not the exception. It's like having a team where everyone is a goalkeeper, always on the lookout, and ready to defend.
Lastly, it enhances decision-making. Armed with the right information and tools, healthcare providers can make informed decisions. It's like having a roadmap in a maze, guiding you at every twist and turn.
Real-Life Instances: Enterprise Risk Management in Action
Picture this: A hospital is planning to implement a new electronic health record (EHR) system. It’s shiny and promising, and everyone’s excited. But with this system come potential risks: data breaches, system downtime, and training challenges, to name a few.
By employing enterprise risk management, the hospital can anticipate these risks. They can put measures in place to mitigate them. So instead of panicking when there's a system glitch, they have a backup plan, trained staff, and solutions ready to deploy.
Another scenario? A sudden outbreak of a contagious disease. With a solid risk management plan, hospitals can predict resource needs, mobilize teams faster, and ensure the safety of both patients and staff.
Best Practices to Maximize Enterprise Risk Management in Healthcare
So, you're sold on enterprise risk management in healthcare. That’s great, but… how do you make the most of it?
Begin by fostering a culture of open communication. Encourage staff at all levels to voice concerns and observations. Remember, it’s a team game.
Secondly, invest in training. Equip your team with the skills and knowledge they need to be effective risk managers. It’s like giving them a magnifying glass to spot even the tiniest of threats.
Lastly, keep revisiting and refining your strategies. The healthcare landscape is ever-evolving, and so should your risk management approach. It's about being agile, adaptable, and always on your toes.
Challenges to Implementing Enterprise Risk Management
While the benefits of enterprise risk management in healthcare are plenty, it’s not without its challenges. First up, is resistance to change. It’s human nature. Introducing a new system or approach can often meet with skepticism. The key? Consistent communication and highlighting the bigger picture.
Then there’s the challenge of resources. Implementing a robust risk management system requires investment: both time and money. Here, long-term vision becomes crucial. It’s not about the immediate costs, but the long-term savings and benefits.
Lastly, the vastness of the healthcare sector can be daunting. With so many departments and functions, integrating them under one risk management umbrella can seem overwhelming. But remember, step by step, brick by brick, it’s doable.
The Future of Enterprise Risk Management in Healthcare
The horizon of healthcare is vast and ever-evolving, and as we stand at its edge, enterprise risk management in healthcare looms large, promising a safer and more efficient future.
Firstly, with the integration of artificial intelligence and machine learning, risk management is on the cusp of a revolution. Predictive models can analyze vast data sets, recognize patterns, and forecast potential risks way before they materialize.
Furthermore, with the global community becoming more interconnected, the sharing of risk management strategies across borders will become commonplace. Hospitals in New York might soon be implementing strategies tested and refined in Tokyo or Mumbai. This cross-pollination of ideas ensures that best practices are not confined within borders but are shared, refined, and implemented globally.
Additionally, as patient care becomes more personalized with treatments like gene therapy and personalized medicine, risk management will need to adapt. Enterprise risk management in healthcare will play a pivotal role in ensuring that these bespoke treatments are delivered safely, taking into account the unique risks they may present.
But it's not just about technology and global collaboration. The future will also see a stronger emphasis on the human aspect. Emotional intelligence, understanding patient behaviors, and predicting human errors will become crucial components of risk management. After all, machines can crunch numbers, but understanding the human heart and mind? That’s where the real challenge and opportunity lie. For more details contact us at https://www.safequal.net/contact-us/.
Lastly, sustainability and eco-friendly practices are making waves in every sector, and healthcare is no exception. The future of enterprise risk management will also encompass strategies to reduce carbon footprints, manage bio-waste efficiently, and ensure a sustainable healthcare environment.
Conclusion
Navigating the intricate world of healthcare can often feel like walking on a tightrope. But with enterprise risk management in healthcare, the sector gets more than just a safety net. It gets a strategy, a plan, and a vision for a future where risks are not just managed but anticipated and mitigated. Embracing it isn’t just a smart move; it's the need of the hour.
Read More:
#enterprise risk management in healthcare#Enterprise Risk Management#Healthcare Safety#Patient Protection#Data Safeguard#Modern Healthcare#Effective Operations#Risk Mitigation#Healthcare ERM
0 notes
Text
VMLogin Secure Browser for Personal Data Security and Privacy

Whether you are a user with commercial business needs, such as e-commerce field, social media marketing, affiliate marketing, crawlers, etc., or just want to safeguard your personal Internet privacy, you need to use a secure browser that protects your data and privacy, to protect your personal data, privacy, money, and money from ads, hackers and other security threats.
📢VMLogin anti-detect browser supports free test.@vmlogin_us
📢https://www.vmlogin.us
📢TG: @vmlogin_us
#secure#data#privacymatters#personaldevelopment#testing#business#ecommerce#ecommercebusiness#affiliatemarketing#socialemediamarketing#crawler#safeguarding#browser#browsersecurity
0 notes
Text
In the vast seas of coworking spaces, data pirates are a real concern that demands attention. By understanding the threats, adopting proactive measures, and staying informed, you can navigate these waters safely.
#coworking space#coworking space data hackers#hackers in coworking space#privacy & safety#safeguard your digital privacy#workspace privacy
0 notes
Text
how many videos about data protection do i have to watch 😭😭😭😭
#i have so many training modules to do and the data protection one is taking sooooo long#violence and aggression was so fast. i still have fire safety - infection prevention- health and safety - safeguarding- and equality to go
1 note
·
View note
Text
#Top Ways to Protect Salesforce Data#Salesforce Data Safeguarding#Salesforce Data Protection#Salesforce data management#Salesforce Data Backup
0 notes
Text
Has tumblr started selling ad data bc I'm suddenly getting a lot of ads abt garden beds right after I bought a couple and got my garden planted... Is everyone else getting these or just me?
#they're from the same brand and everything!#ive never gotten these before#idk how tumblr would know to advertise that to me#and idk how that company would have connected my tumblr acc with their info about me...#so this is a real mystery#im so careful abt safeguarding my data to prevent this why is it happening anyway? :(#teslynn personal
0 notes