#secure iOS apps
Explore tagged Tumblr posts
Text
Quokka Labs delivers professional iOS app development services, creating innovative, secure, and high-performance apps for iPhone and iPad. Leverage our expertise in custom app development to bring your vision to life.
#iOS app development#iPhone app development#iPad app development#custom iOS app development#scalable app solutions#professional iOS app developers#iOS app design#secure iOS apps#high-performance app development#mobile app solutions.
0 notes
Text
The antitrust case against Apple

I'm on tour with my new, nationally bestselling novel The Bezzle! Catch me TONIGHT (Mar 22) in TORONTO, then SUNDAY (Mar 24) with LAURA POITRAS in NYC, then Anaheim, and beyond!

The foundational tenet of "the Cult of Mac" is that buying products from a $3t company makes you a member of an oppressed ethnic minority and therefore every criticism of that corporation is an ethnic slur:
https://pluralistic.net/2024/01/12/youre-holding-it-wrong/#if-dishwashers-were-iphones
Call it "Apple exceptionalism" – the idea that Apple, alone among the Big Tech firms, is virtuous, and therefore its conduct should be interpreted through that lens of virtue. The wellspring of this virtue is conveniently nebulous, which allows for endless goal-post shifting by members of the Cult of Mac when Apple's sins are made manifest.
Take the claim that Apple is "privacy respecting," which is attributed to Apple's business model of financing its services though cash transactions, rather than by selling it customers to advertisers. This is the (widely misunderstood) crux of the "surveillance capitalism" hypothesis: that capitalism is just fine, but once surveillance is in the mix, capitalism fails.
Apple, then, is said to be a virtuous company because its behavior is disciplined by market forces, unlike its spying rivals, whose ability to "hack our dopamine loops" immobilizes the market's invisible hand with "behavior-shaping" shackles:
http://pluralistic.net/HowToDestroySurveillanceCapitalism
Apple makes a big deal out of its privacy-respecting ethos, and not without some justification. After all, Apple went to the mattresses to fight the FBI when they tried to force Apple to introduced defects into its encryption systems:
https://www.eff.org/deeplinks/2018/04/fbi-could-have-gotten-san-bernardino-shooters-iphone-leadership-didnt-say
And Apple gave Ios users the power to opt out of Facebook spying with a single click; 96% of its customers took them up on this offer, costing Facebook $10b (one fifth of the pricetag of the metaverse boondoggle!) in a single year (you love to see it):
https://arstechnica.com/gadgets/2021/02/facebook-makes-the-case-for-activity-tracking-to-ios-14-users-in-new-pop-ups/
Bruce Schneier has a name for this practice: "feudal security." That's when you cede control over your device to a Big Tech warlord whose "walled garden" becomes a fortress that defends you against external threats:
https://pluralistic.net/2021/06/08/leona-helmsley-was-a-pioneer/#manorialism
The keyword here is external threats. When Apple itself threatens your privacy, the fortress becomes a prison. The fact that you can't install unapproved apps on your Ios device means that when Apple decides to harm you, you have nowhere to turn. The first Apple customers to discover this were in China. When the Chinese government ordered Apple to remove all working privacy tools from its App Store, the company obliged, rather than risk losing access to its ultra-cheap manufacturing base (Tim Cook's signal accomplishment, the one that vaulted him into the CEO's seat, was figuring out how to offshore Apple manufacturing to China) and hundreds of millions of middle-class consumers:
https://www.reuters.com/article/us-china-apple-vpn/apple-says-it-is-removing-vpn-services-from-china-app-store-idUSKBN1AE0BQ
Killing VPNs and other privacy tools was just for openers. After Apple caved to Beijing, the demands kept coming. Next, Apple willingly backdoored all its Chinese cloud services, so that the Chinese state could plunder its customers' data at will:
https://www.nytimes.com/2021/05/17/technology/apple-china-censorship-data.html
This was the completely foreseeable consequence of Apple's "curated computing" model: once the company arrogated to itself the power to decide which software you could run on your own computer, it was inevitable that powerful actors – like the Chinese Communist Party – would lean on Apple to exercise that power in service to its goals.
Unsurprisingly, the Chinese state's appetite for deputizing Apple to help with its spying and oppression was not sated by backdooring iCloud and kicking VPNs out of the App Store. As recently as 2022, Apple continued to neuter its tools at the behest of the Chinese state, breaking Airdrop to make it useless for organizing protests in China:
https://pluralistic.net/2022/11/11/foreseeable-consequences/#airdropped
But the threat of Apple turning on its customers isn't limited to China. While the company has been unwilling to spy on its users on behalf of the US government, it's proven more than willing to compromise its worldwide users' privacy to pad its own profits. Remember when Apple let its users opt out of Facebook surveillance with one click? At the very same time, Apple was spinning up its own commercial surveillance program, spying on Ios customers, gathering the very same data as Facebook, and for the very same purpose: to target ads. When it came to its own surveillance, Apple completely ignored its customers' explicit refusal to consent to spying, spied on them anyway, and lied about it:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
Here's the thing: even if you believe that Apple has a "corporate personality" that makes it want to do the right thing, that desire to be virtuous is dependent on the constraints Apple faces. The fact that Apple has complete legal and technical control over the hardware it sells – the power to decide who can make software that runs on that hardware, the power to decide who can fix that hardware, the power to decide who can sell parts for that hardware – represents an irresistible temptation to enshittify Apple products.
"Constraints" are the crux of the enshittification hypothesis. The contagion that spread enshittification to every corner of our technological world isn't a newfound sadism or indifference among tech bosses. Those bosses are the same people they've always been – the difference is that today, they are unconstrained.
Having bought, merged or formed a cartel with all their rivals, they don't fear competition (Apple buys 90+ companies per year, and Google pays it an annual $26.3b bribe for default search on its operating systems and programs).
Having captured their regulators, they don't fear fines or other penalties for cheating their customers, workers or suppliers (Apple led the coalition that defeated dozens of Right to Repair bills, year after year, in the late 2010s).
Having wrapped themselves in IP law, they don't fear rivals who make alternative clients, mods, privacy tools or other "adversarial interoperability" tools that disenshittify their products (Apple uses the DMCA, trademark, and other exotic rules to block third-party software, repair, and clients).
True virtue rests not merely in resisting temptation to be wicked, but in recognizing your own weakness and avoiding temptation. As I wrote when Apple embarked on its "curated computing" path, the company would eventually – inevitably – use its power to veto its customers' choices to harm those customers:
https://memex.craphound.com/2010/04/01/why-i-wont-buy-an-ipad-and-think-you-shouldnt-either/
Which is where we're at today. Apple – uniquely among electronics companies – shreds every device that is traded in by its customers, to block third parties from harvesting working components and using them for independent repair:
https://www.vice.com/en/article/yp73jw/apple-recycling-iphones-macbooks
Apple engraves microscopic Apple logos on those parts and uses these as the basis for trademark complaints to US customs, to block the re-importation of parts that escape its shredders:
https://repair.eu/news/apple-uses-trademark-law-to-strengthen-its-monopoly-on-repair/
Apple entered into an illegal price-fixing conspiracy with Amazon to prevent used and refurbished devices from being sold in the "world's biggest marketplace":
https://pluralistic.net/2022/11/10/you-had-one-job/#thats-just-the-as
Why is Apple so opposed to independent repair? Well, they say it's to keep users safe from unscrupulous or incompetent repair technicians (feudal security). But when Tim Cook speaks to his investors, he tells a different story, warning them that the company's profits are threatened by customers who choose to repair (rather than replace) their slippery, fragile glass $1,000 pocket computers (the fortress becomes a prison):
https://www.apple.com/newsroom/2019/01/letter-from-tim-cook-to-apple-investors/
All this adds up to a growing mountain of immortal e-waste, festooned with miniature Apple logos, that our descendants will be dealing with for the next 1,000 years. In the face of this unspeakable crime, Apple engaged in a string of dishonest maneuvers, claiming that it would support independent repair. In 2022, Apple announced a home repair program that turned out to be a laughably absurd con:
https://pluralistic.net/2022/05/22/apples-cement-overshoes/
Then in 2023, Apple announced a fresh "pro-repair" initiative that, once again, actually blocked repair:
https://pluralistic.net/2023/09/22/vin-locking/#thought-differently
Let's pause here a moment and remember that Apple once stood for independent repair, and celebrated the independent repair technicians that kept its customers' beloved Macs running:
https://pluralistic.net/2021/10/29/norwegian-potato-flour-enchiladas/#r2r
Whatever virtue lurks in Apple's corporate personhood, it is no match for the temptation that comes from running a locked-down platform designed to capture IP rights so that it can prevent normal competitive activities, like fixing phones, processing payments, or offering apps.
When Apple rolled out the App Store, Steve Jobs promised that it would save journalism and other forms of "content creation" by finally giving users a way to pay rightsholders. A decade later, that promise has been shattered by the app tax – a 30% rake on every in-app transaction that can't be avoided because Apple will kick your app out of the App Store if you even mention that your customers can pay you via the web in order to avoid giving a third of their content dollars to a hardware manufacturer that contributed nothing to the production of that material:
https://www.eff.org/deeplinks/2023/06/save-news-we-must-open-app-stores
Among the apps that Apple also refuses to allow on Ios is third-party browsers. Every Iphone browser is just a reskinned version of Apple's Safari, running on the same antiquated, insecure Webkit browser engine. The fact that Webkit is incomplete and outdated is a feature, not a bug, because it lets Apple block web apps – apps delivered via browsers, rather than app stores:
https://pluralistic.net/2022/12/13/kitbashed/#app-store-tax
Last month, the EU took aim at Apple's veto over its users' and software vendors' ability to transact with one another. The newly in-effect Digital Markets Act requires Apple to open up both third-party payment processing and third-party app stores. Apple's response to this is the very definition of malicious compliance, a snake's nest of junk-fees, onerous terms of service, and petty punitive measures that all add up to a great, big "Go fuck yourself":
https://pluralistic.net/2024/02/06/spoil-the-bunch/#dma
But Apple's bullying, privacy invasion, price-gouging and environmental crimes are global, and the EU isn't the only government seeking to end them. They're in the firing line in Japan:
https://asia.nikkei.com/Business/Technology/Japan-to-crack-down-on-Apple-and-Google-app-store-monopolies
And in the UK:
https://www.gov.uk/government/news/cma-wins-appeal-in-apple-case
And now, famously, the US Department of Justice is coming for Apple, with a bold antitrust complaint that strikes at the heart of Apple exceptionalism, the idea that monopoly is safer for users than technological self-determination:
https://www.justice.gov/opa/media/1344546/dl?inline
There's passages in the complaint that read like I wrote them:
Apple wraps itself in a cloak of privacy, security, and consumer preferences to justify its anticompetitive conduct. Indeed, it spends billions on marketing and branding to promote the self-serving premise that only Apple can safeguard consumers’ privacy and security interests. Apple selectively compromises privacy and security interests when doing so is in Apple’s own financial interest—such as degrading the security of text messages, offering governments and certain companies the chance to access more private and secure versions of app stores, or accepting billions of dollars each year for choosing Google as its default search engine when more private options are available. In the end, Apple deploys privacy and security justifications as an elastic shield that can stretch or contract to serve Apple’s financial and business interests.
After all, Apple punishes its customers for communicating with Android users by forcing them to do so without any encryption. When Beeper Mini rolled out an Imessage-compatible Android app that fixed this, giving Iphone owners the privacy Apple says they deserve but denies to them, Apple destroyed Beeper Mini:
https://blog.beeper.com/p/beeper-moving-forward
Tim Cook is on record about this: if you want to securely communicate with an Android user, you must "buy them an Iphone":
https://www.theverge.com/2022/9/7/23342243/tim-cook-apple-rcs-imessage-android-iphone-compatibility
If your friend, family member or customer declines to change mobile operating systems, Tim Cook insists that you must communicate without any privacy or security.
Even where Apple tries for security, it sometimes fails ("security is a process, not a product" -B. Schneier). To be secure in a benevolent dictatorship, it must also be an infallible dictatorship. Apple's far from infallible: Eight generations of Iphones have unpatchable hardware defects:
https://checkm8.info/
And Apple's latest custom chips have secret-leaking, unpatchable vulnerabilities:
https://arstechnica.com/security/2024/03/hackers-can-extract-secret-encryption-keys-from-apples-mac-chips/
Apple's far from infallible – but they're also far from benevolent. Despite Apple's claims, its hardware, operating system and apps are riddled with deliberate privacy defects, introduce to protect Apple's shareholders at the expense of its customers:
https://proton.me/blog/iphone-privacy
Now, antitrust suits are notoriously hard to make, especially after 40 years of bad-precedent-setting, monopoly-friendly antitrust malpractice. Much of the time, these suits fail because they can't prove that tech bosses intentionally built their monopolies. However, tech is a written culture, one that leaves abundant, indelible records of corporate deliberations. What's more, tech bosses are notoriously prone to bragging about their nefarious intentions, committing them to writing:
https://pluralistic.net/2023/09/03/big-tech-cant-stop-telling-on-itself/
Apple is no exception – there's an abundance of written records that establish that Apple deliberately, illegally set out to create and maintain a monopoly:
https://www.wired.com/story/4-internal-apple-emails-helped-doj-build-antitrust-case/
Apple claims that its monopoly is beneficent, used to protect its users, making its products more "elegant" and safe. But when Apple's interests conflict with its customers' safety and privacy – and pocketbooks – Apple always puts itself first, just like every other corporation. In other words: Apple is unexceptional.
The Cult of Mac denies this. They say that no one wants to use a third-party app store, no one wants third-party payments, no one wants third-party repair. This is obviously wrong and trivially disproved: if no Apple customer wanted these things, Apple wouldn't have to go to enormous lengths to prevent them. The only phones that an independent Iphone repair shop fixes are Iphones: which means Iphone owners want independent repair.
The rejoinder from the Cult of Mac is that those Iphone owners shouldn't own Iphones: if they wanted to exercise property rights over their phones, they shouldn't have bought a phone from Apple. This is the "No True Scotsman" fallacy for distraction-rectangles, and moreover, it's impossible to square with Tim Cook's insistence that if you want private communications, you must buy an Iphone.
Apple is unexceptional. It's just another Big Tech monopolist. Rounded corners don't preserve virtue any better than square ones. Any company that is freed from constraints – of competition, regulation and interoperability – will always enshittify. Apple – being unexceptional – is no exception.

Name your price for 18 of my DRM-free ebooks and support the Electronic Frontier Foundation with the Humble Cory Doctorow Bundle.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/03/22/reality-distortion-field/#three-trillion-here-three-trillion-there-pretty-soon-youre-talking-real-money
#pluralistic#apple#antitrust#cult of mac#ios#mobile#app tax#infosec#feudal security#doj#jonathan kanter#doj v apple#big tech#trustbusting#monopolies#app stores#technofeudalism#technomaorialism#privacy#right to repair#corruption
239 notes
·
View notes
Text
🎉 Say Hello to Seamless Event Planning with Ootbo App! 🎉
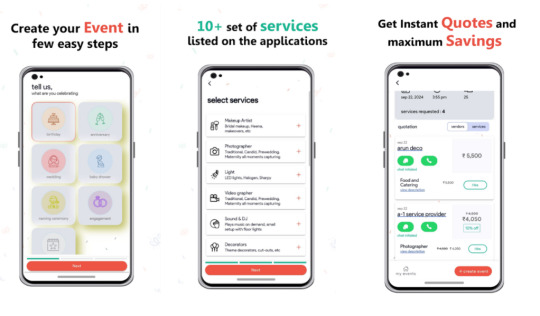
Planning an event can feel like juggling too many tasks at once. From finding the perfect venue to managing vendor communications and staying within budget, it’s easy to get overwhelmed. But what if you had an app that handled everything in one place? Enter the Ootbo App—the ultimate event planning tool designed to make organizing events stress-free, seamless, and fun! 🎈
Whether you’re planning a wedding, corporate event, birthday party, or any special occasion, the Ootbo App is your go-to solution for managing every aspect of the event planning process. 🗓️✨
🌟 Why Choose Ootbo App?
Gone are the days of switching between multiple apps, emails, and spreadsheets. Ootbo App simplifies the entire event planning process, from start to finish. Here’s how:
1. Create Events Effortlessly 🎨
Ootbo offers an intuitive interface that allows you to create detailed events in minutes. Simply input event details, set the date and time, and let Ootbo do the rest. 💡 Pro Tip: Customize your event profile to include specific requirements and preferences for vendors!
2. Receive Multiple Vendor Quotes 💼
Why chase down vendors when they can come to you? With Ootbo, you can: 🔍 Post your event requirements. 📩 Receive multiple quotes from verified vendors. 📊 Compare options side-by-side to choose the best fit.
This saves you time and ensures you get competitive pricing without the hassle of endless phone calls. 📞
3. In-App Vendor Chats 💬
Communication is key when planning an event, and Ootbo has you covered! 📱 Chat with potential vendors directly through the app. 📋 Discuss availability, services, and pricing in real time. 📎 Share documents, photos, and event details seamlessly.
Forget the confusion of scattered email threads—Ootbo keeps all your conversations in one place, organized and easy to access.
4. In-App Calls for Quick Decisions 📞
Sometimes, a quick call can make all the difference. Ootbo allows you to: 🔊 Make in-app calls to vendors without sharing personal contact details. 📌 Record important discussions and reference them later. 📈 Keep all event-related calls connected to your event profile.
No more searching through your call history for vendor numbers—everything stays in the app!
5. Hire Vendors with Confidence 🤝
Once you’ve reviewed quotes and discussed details, hiring your chosen vendor is as easy as a tap! 📄 Securely finalize agreements within the app. 💳 Pay vendors through a secure payment gateway. 🔒 Enjoy peace of mind knowing your transactions are protected.
With Ootbo, you’re not just hiring vendors—you’re partnering with professionals who are ready to make your event a success! 🎉
🏆 The Benefits of Using Ootbo App
All-in-One Solution: Manage your event from creation to completion in a single app.
Time-Saving: No more endless emails, phone calls, or spreadsheets.
Competitive Pricing: Receive and compare quotes to get the best value for your budget.
Seamless Communication: Chat and call vendors directly within the app.
Secure Transactions: Make payments and finalize contracts with confidence.
🎯 Who Can Use Ootbo?
Ootbo is designed for everyone! Whether you’re:
👰 Planning a wedding. 🏢 Organizing a corporate event. 🎂 Hosting a birthday party. 🎭 Coordinating a community event.
Ootbo App is your trusted event planning companion.
📲 Download the Ootbo App Today!
Ready to take the stress out of event planning? Download the Ootbo App today and experience the future of event management!
🔗 Visit Ootbo App to learn more. 📱 Available on iOS and Android.
Make your next event unforgettable with Ootbo! 🎉
With the Ootbo App, event planning has never been easier or more efficient. Start planning your dream event today! 🎈
#vent planning app#Best event management tool#Event vendor management#In-app vendor communication#Compare event vendor quotes#Event budget management app#Online event planning solution#Seamless event planning app#Event planning made easy#Chat with event vendors#Event organizer tool#Hire vendors online#Manage events from mobile#Event planning software for Android & iOS#ow to plan events with a mobile app#Best app to hire event vendors#Manage event budgets and vendors in one app#Event planning solution for weddings and parties#Secure in-app payments for event vendors
2 notes
·
View notes
Text
Experience the power of smart file sharing with eShare – your pocket-friendly solution for secure, fast, and simple file management. This splash screen video highlights the intuitive design and efficiency of the eShare mobile app.
#eShare#file sharing app#splash screen video#file transfer#mobile sharing app#data sharing#tech startup#app UI#Android file manager#iOS sharing app#digital communication#secure file sharing#productivity app
0 notes
Text
#Mycelium wallet#Mycelium wallet setup#how to use Mycelium wallet#Bitcoin wallet app#best crypto wallet#Mycelium Bitcoin wallet#Mycelium Android app#Mycelium iOS wallet#secure Bitcoin wallet#non-custodial wallet#Mycelium seed phrase#send Bitcoin with Mycelium#receive Bitcoin wallet#hardware wallet integration#crypto mobile wallet
0 notes
Text
At Bilions.co, we specialize in creating high-quality mobile applications for iOS and Android platforms. Our team of experienced developers works closely with businesses to design and develop custom mobile apps that are intuitive, secure, and scalable. We focus on delivering innovative solutions that enhance user experience, increase engagement, and drive business growth. From concept to deployment, we provide end-to-end mobile app development services, ensuring your app performs seamlessly and meets the specific needs of your customers.
#Mobile Application Development#Custom Mobile Apps#iOS App Development#Android App Development#Mobile App Development Company#Scalable Mobile Solutions#Business Mobile Apps#App Development Services#Cross-Platform Mobile Apps#Mobile Development Agency#Secure Mobile Apps#User-Friendly App Development#Mobile Solutions for Businesses
0 notes
Text
Android and iOS Development: Bring Your Concepts to Life with Lexmetech Systems

In today’s mobile-centric environment, having a strong and user-friendly application is essential, not optional. Whether you're a new business, a scaling company, or a well-established organization, a thoughtfully crafted mobile app can assist you in reaching your target demographic, improving customer interaction, and fostering business expansion. At Lexmetech Systems, we focus on Android and iOS development, transforming your creative concepts into high-quality, scalable, and visually appealing mobile applications.
The Importance of Mobile App Development
Mobile applications have become fundamental to our everyday activities. Whether it's shopping, banking, staying fit, or entertainment, apps are revolutionizing our interactions with the world. Here’s why investing in mobile app development is vital:
Broader Outreach: With approximately 6.8 billion smartphone users worldwide, apps allow you to engage a large audience.
Improved Customer Experience: Applications provide a smooth and personalized user interface.
Greater Brand Loyalty: A well-crafted app keeps your brand readily accessible to your customers.
Enhanced Revenue Potential: Apps create additional income opportunities through in-app purchases, subscriptions, and advertisements.
Distinct Competitive Edge: Differentiate yourself in your market with a unique and creative app.
Reasons to Opt for Lexmetech Systems for Android and iOS Development
At Lexmetech Systems, we blend technological skill, creativity, and a focus on the customer to produce outstanding mobile applications. Here are the qualities that distinguish us:
1. Customized App Development
We reject generic solutions. Our team collaborates closely with you to comprehend your business objectives and develop a tailored application that satisfies your precise requirements
2. Cross-Platform Proficiency
Whether you're in need of an Android app, an iOS app, or a cross-platform solution, we can help. Our developers are skilled in:
Android Development: Utilizing Kotlin, Java, and Android Studio.
iOS Development: Using Swift, Objective-C, and Xcode.
Cross-Platform Development: Employing Flutter and React Native for economical options.
3. User-Centric Design
We create applications that are not only visually striking but also intuitive and straightforward to navigate. Our aim is to develop a seamless user experience that captivates your audience.
4. Scalable and Secure Solutions
Our applications are designed to grow alongside your business. We prioritize scalability, performance, and security to safeguard your information and ensure a smooth user experience.
5. Comprehensive Services
From ideation and design to development, testing, and deployment, we provide complete mobile app development services. We also offer support and maintenance after launch to keep your app operational.
Core Features of Our Mobile Applications
Intuitive UI/UX Design: Captivating interfaces that enhance user satisfaction.
High Performance: Applications that load quickly and respond effectively.
Offline Functionality: Apps that function seamlessly regardless of internet connectivity.
Third-Party Integrations: Connections with APIs, payment processors, and social media platforms.
Push Notifications: Keep users updated and involved with timely information.
Analytics and Reporting: Monitor user activity and app performance with integrated analytics.
Sectors We Serve
Our Android and iOS development solutions cover a diverse range of sectors, including:
E-commerce: Build shopping applications with smooth payment and delivery capabilities.
Healthcare: Develop telehealth applications, fitness trackers, and patient management systems.
Education: Create online learning platforms and virtual classroom applications.
Finance: Design safe banking and investment applications.
Entertainment: Develop gaming, streaming, and social networking applications.
Logistics: Create delivery tracking and fleet management applications.
Our Development Workflow
At Lexmetech Systems, we adhere to a streamlined and clear process to guarantee the success of your application:
Discovery and Planning: Identify your needs and establish the project scope.
Design and Prototyping: Create wireframes and prototypes to visualize the application.
Development and Testing: Construct the app and perform thorough testing to ensure quality.
Launch and Support: Release the application and provide continuous support for updates and maintenance.
Why Choose Lexmetech Systems?
Skilled Professionals: Our team of developers, designers, and project managers are specialists in their areas of expertise.
Demonstrated Success: We’ve successfully launched applications for clients in various sectors.
Focus on Clients: Your satisfaction is our highest priority.
Cost-Effective Solutions: We offer high-quality applications at competitive rates.
Punctual Delivery: We value deadlines and ensure prompt project completion.
Ready to Create Your Ideal App?
Your app concept has the power to revolutionize your business and leave a lasting impression. With Lexmetech Systems as your development ally, you can turn your vision into reality and reach your objectives.
Don’t hesitate—reach out to Lexmetech Systems now, and let’s develop a mobile app that distinguishes you from your competitors!
Lexmetech Systems – Your Reliable Partner for Android and iOS Development!
#Android app development#iOS app development#mobile app development#custom app solutions#cross-platform apps#user-friendly app design#scalable mobile apps#secure app development#app development services#Lexmetech Systems
0 notes
Text
How to Secure Your Mobile App from Cyber Threats
Mobile apps handle a lot of user data, making security a top priority. If your app is not secure, hackers can steal information, inject malware, or cause serious damage. At Cloudi5 Technologies, a trusted mobile app development company, we follow strict security practices to protect apps from cyber threats. Here’s how you can secure your mobile app effectively.
1. Use Strong Authentication
Implement multi-factor authentication (MFA) to add extra security layers. Encourage users to set strong passwords and use biometric authentication like fingerprints or facial recognition.
2. Encrypt Data
Data encryption converts sensitive information into unreadable code. Use strong encryption methods such as AES (Advanced Encryption Standard) to protect data during storage and transmission.
3. Secure APIs
APIs (Application Programming Interfaces) are commonly targeted by hackers. Use secure API authentication methods like OAuth and API keys to prevent unauthorized access.
4. Keep Your App Updated
Regular updates fix security vulnerabilities. Always update your app and third-party libraries to prevent hackers from exploiting old security flaws.
5. Protect Against Malware
Hackers inject malware into apps to steal data. Use security tools to scan and remove any suspicious code before launching your app.
6. Implement Secure Data Storage
Avoid storing sensitive data on a user’s device. If necessary, use encrypted storage solutions and ensure data is not exposed to unauthorized access.
7. Test for Security Risks
Conduct regular security testing, such as penetration testing and code reviews, to identify and fix potential vulnerabilities.
By following these security measures, you can protect your mobile app from cyber threats. At Cloudi5 Technologies, we focus on building secure and reliable mobile applications. Contact us for expert mobile app development services.
#cloudi5technologies#mobile app developers#mobileappdesign#mobile application services#ios app development#android#android app development#app development#cyber security#data privacy#internet privacy
0 notes
Text
Android vs iOS - Which OS is right for you?
Over the years, the debate between Android and iOS has intensified, making it vital for you to understand the unique features each operating system offers. Android provides a wide range of devices with customizable options, while iOS boasts a seamless user experience and consistent updates. Your choice can impact everything from app availability to device performance. Whether you prioritize…
#AI-powered mobile operating systems#Android benefits#Android customization options#Android features#Android flexibility vs iOS simplicity#Android market share vs iOS#Android or iOS which is better#Android vs iOS#Android vs iOS comparison#Android vs iOS for app development#Android vs iOS for gaming#Android vs iOS performance analysis#Android vs iOS security features#Android vs iOS user experience#best mobile operating system#choose between Android and iOS#choosing the right OS for developers#cross-platform app development Android vs iOS#generative AI apps on Android#generative AI apps on iOS#generative AI in mobile apps#iOS benefits#iOS exclusive features#iOS features#iOS smoothness and stability#mobile apps on Android vs iOS#mobile operating system trends#mobile OS comparison#mobile platform comparison for AI#next-gen mobile technologies comparison
1 note
·
View note
Text

The big changes coming to UK and European travel in 2025
Read more click here
#the big changes#what are the big changes coming to medicare in 2025#what are the big changes coming to medicare#what are the big changes in real estate#what are the big changes coming to siriusxm in 2024#behind the big changes at wheel of fortune#what are the big changes in social security#what are the big changes coming to medicare in 2024#what are the big changes in ios 18#what are the big changes coming to subway#what are the big changes coming to walmart#the big change app#considering the major changes and shifts#what are the big changes for mormon missionaries#the big change book#the big change theory#the big change universe#the big change roundup#what are the changes to the big mac#what are the big life changes#what are the big changes coming to costco#the big change by frederick lewis allen#the big con change break guide#big change reviews#big changes in history#big change pricing#big big changes#beyond measure the big impact of small changes#belmont at the big a changes#big changes in the big apple
0 notes
Text
Revitalize Your Online Platform with a Framework Upgrade
Are you noticing slower load times or increased downtime on your website? It may be time for a "Website and Application Framework Upgrade." This essential step revitalizes your online platform, ensuring that it runs optimally, securely, and with advanced functionalities. Upgrading your framework enhances performance, allowing for smoother navigation, faster load times, and a more engaging user experience. At ATCuality, we understand the importance of a responsive and reliable website. Our team of experts will assess your current setup and implement the necessary framework upgrades, tailored to the specific needs of your business. By modernizing your platform, you provide users with a seamless digital experience, increase engagement, and keep up with industry trends. Let ATCuality help you stay ahead with a framework that supports your business goals and adapts to future advancements.
#seo services#artificial intelligence#seo marketing#seo company#ai powered application#iot applications#digital marketing#amazon web services#seo agency#azure cloud services#ai applications#android app development#mobile app development company#mobile application development#mobile app developers#ios app development#app development company#app design#augmented reality development services#augmented reality agency#augmented reality#virtual reality#azure cloud computing#azure cloud migration#blockchain technology#blockchain#cash collection application#cloud security services#cloud server hosting#web developers
1 note
·
View note
Text
#web design#website development#artificial intelligence#web service#digital marketing#cyber security#ai#branding#app development#software development#ios#smartphone#application#apple music#mobile app development#web development#website#ecommerce website development
0 notes
Text
youtube
Flat Earth Dave's App Massive Security Breach
#flat earth#youtube#stupid#app#data breach#mctoon#flat earth dave#data leak#ios#android#Youtube#security
0 notes
Text
Experience the power of smart file sharing with eShare – your pocket-friendly solution for secure, fast, and simple file management. This splash screen video highlights the intuitive design and efficiency of the eShare mobile app.
#eShare#file sharing app#splash screen video#file transfer#mobile sharing app#data sharing#tech startup#app UI#Android file manager#iOS sharing app#digital communication#secure file sharing#productivity app
0 notes
Text
Discover the essential tactics for fortifying your iOS app security in our latest blog post: 'Building a Digital Fortress: Essential iOS App Security Tactics'. Strengthen your defenses and safeguard your digital assets today!
1 note
·
View note