#stop data usage in windows 10
Explore tagged Tumblr posts
Text

How to use DXVK with The Sims 3
Have you seen this post about using DXVK by Criisolate? But felt intimidated by the sheer mass of facts and information?
@desiree-uk and I compiled a guide and the configuration file to make your life easier. It focuses on players not using the EA App, but it might work for those just the same. It’s definitely worth a try.
Adding this to your game installation will result in a better RAM usage. So your game is less likely to give you Error 12 or crash due to RAM issues. It does NOT give a huge performance boost, but more stability and allows for higher graphics settings in game.
The full guide behind the cut. Let me know if you also would like it as PDF.
Happy simming!
Disclaimer and Credits
Desiree and I are no tech experts and just wrote down how we did this. Our ability to help if you run into trouble is limited. So use at your own risk and back up your files!
We both are on Windows 10 and start the game via TS3W.exe, not the EA App. So your experience may differ.
This guide is based on our own experiments and of course criisolate’s post on tumblr: https://www.tumblr.com/criisolate/749374223346286592/ill-explain-what-i-did-below-before-making-any
This guide is brought to you by Desiree-UK and Norn.
Compatibility
Note: This will conflict with other programs that “inject” functionality into your game so they may stop working. Notably
Reshade
GShade
Nvidia Experience/Nvidia Inspector/Nvidia Shaders
RivaTuner Statistics Server
It does work seamlessly with LazyDuchess’ Smooth Patch.
LazyDuchess’ Launcher: unknown
Alder Lake patch: does conflict. One user got it working by starting the game by launching TS3.exe (also with admin rights) instead of TS3W.exe. This seemed to create the cache file for DXVK. After that, the game could be started from TS3W.exe again. That might not work for everyone though.
A word on FPS and V-Sync
With such an old game it’s crucial to cap framerate (FPS). This is done in the DXVK.conf file. Same with V-Sync.
You need
a text editor (easiest to use is Windows Notepad)
to download DXVK, version 2.3.1 from here: https://github.com/doitsujin/DXVK/releases/tag/v2.3.1 Extract the archive, you are going to need the file d3d9.dll from the x32 folder
the configuration file DXVK.conf from here: https://github.com/doitsujin/DXVK/blob/master/DXVK.conf. Optional: download the edited version with the required changes here.
administrator rights on your PC
to know your game’s installation path (bin folder) and where to find the user folder
a tiny bit of patience :)
First Step: Backup
Backup your original Bin folder in your Sims 3 installation path! The DXVK file may overwrite some files! The path should be something like this (for retail): \Program Files (x86)\Electronic Arts\The Sims 3\Game\Bin (This is the folder where also GraphicsRule.sgr and the TS3W.exe and TS3.exe are located.)
Backup your options.ini in your game’s user folder! Making the game use the DXVK file will count as a change in GPU driver, so the options.ini will reset once you start your game after installation. The path should be something like this: \Documents\Electronic Arts\The Sims 3 (This is the folder where your Mods folder is located).
Preparations
Make sure you run the game as administrator. You can check that by right-clicking on the icon that starts your game. Go to Properties > Advanced and check the box “Run as administrator”. Note: This will result in a prompt each time you start your game, if you want to allow this application to make modifications to your system. Click “Yes” and the game will load.
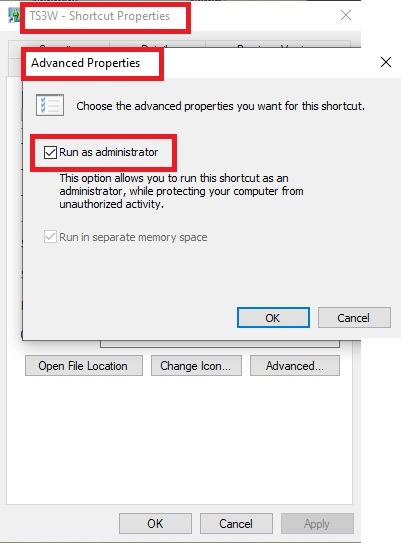
2. Make sure you have the DEP settings from Windows applied to your game.
Open the Windows Control Panel.
Click System and Security > System > Advanced System Settings.
On the Advanced tab, next to the Performance heading, click Settings.
Click the Data Execution Prevention tab.
Select 'Turn on DEP for all programs and services except these”:
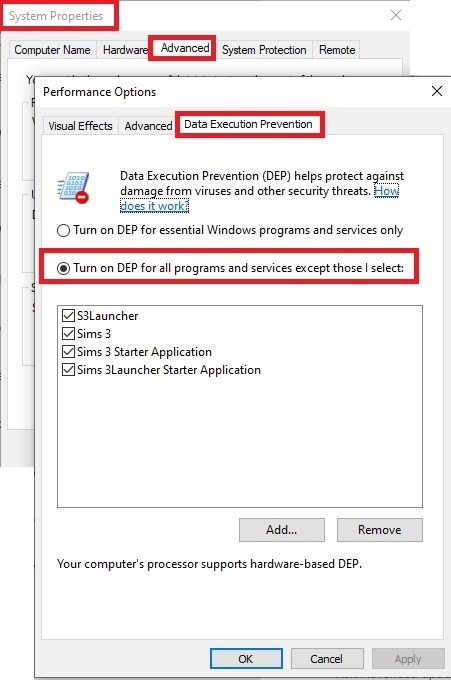
Click the Add button, a window to the file explorer opens. Navigate to your Sims 3 installation folder (the bin folder once again) and add TS3W.exe and TS3.exe.
Click OK. Then you can close all those dialog windows again.
Setting up the DXVK.conf file
Open the file with a text editor and delete everything in it. Then add these values:
d3d9.textureMemory = 1
d3d9.presentInterval = 1
d3d9.maxFrameRate = 60
d3d9.presentInterval enables V-Sync,d3d9.maxFrameRate sets the FrameRate. You can edit those values, but never change the first line (d3d9.textureMemory)!
The original DXVK.conf contains many more options in case you would like to add more settings.

A. no Reshade/GShade
Setting up DXVK
Copy the two files d3d9.dll and DXVK.conf into the Bin folder in your Sims 3 installation path. This is the folder where also GraphicsRule.sgr and the TS3W.exe and TS3.exe are located. If you are prompted to overwrite files, please choose yes (you DID backup your folder, right?)
And that’s basically all that is required to install.
Start your game now and let it run for a short while. Click around, open Buy mode or CAS, move the camera.
Now quit without saving. Once the game is closed fully, open your bin folder again and double check if a file “TS3W.DXVK-cache” was generated. If so – congrats! All done!
Things to note
Heads up, the game options will reset! So it will give you a “vanilla” start screen and options.
Don’t worry if the game seems to be frozen during loading. It may take a few minutes longer to load but it will load eventually.
The TS3W.DXVK-cache file is the actual cache DXVK is using. So don’t delete this! Just ignore it and leave it alone. When someone tells to clear cache files – this is not one of them!
Update Options.ini
Go to your user folder and open the options.ini file with a text editor like Notepad.
Find the line “lastdevice = “. It will have several values, separated by semicolons. Copy the last one, after the last semicolon, the digits only. Close the file.
Now go to your backup version of the Options.ini file, open it and find that line “lastdevice” again. Replace the last value with the one you just copied. Make sure to only replace those digits!
Save and close the file.
Copy this version of the file into your user folder, replacing the one that is there.
Things to note:
If your GPU driver is updated, you might have to do these steps again as it might reset your device ID again. Though it seems that the DXVK ID overrides the GPU ID, so it might not happen.
How do I know it’s working?
Open the task manager and look at RAM usage. Remember the game can only use 4 GB of RAM at maximum and starts crashing when usage goes up to somewhere between 3.2 – 3.8 GB (it’s a bit different for everybody).
So if you see values like 2.1456 for RAM usage in a large world and an ongoing save, it’s working. Generally the lower the value, the better for stability.
Also, DXVK will have generated its cache file called TS3W.DXVK-cache in the bin folder. The file size will grow with time as DXVK is adding stuff to it, e.g. from different worlds or savegames. Initially it might be something like 46 KB or 58 KB, so it’s really small.
Optional: changing MemCacheBudgetValue
MemCacheBudgetValue determines the size of the game's VRAM Cache. You can edit those values but the difference might not be noticeable in game. It also depends on your computer’s hardware how much you can allow here.
The two lines of seti MemCacheBudgetValue correspond to the high RAM level and low RAM level situations. Therefore, theoretically, the first line MemCacheBudgetValue should be set to a larger value, while the second line should be set to a value less than or equal to the first line.
The original values represent 200MB (209715200) and 160MB (167772160) respectively. They are calculated as 200x1024x1024=209175200 and 160x1024x1024=167772160.
Back up your GraphicsRules.sgr file! If you make a mistake here, your game won’t work anymore.
Go to your bin folder and open your GraphicsRules.sgr with a text editor.
Search and find two lines that set the variables for MemCacheBudgetValue.
Modify these two values to larger numbers. Make sure the value in the first line is higher or equals the value in the second line. Examples for values: 1073741824, which means 1GB 2147483648 which means 2 GB. -1 (minus 1) means no limit (but is highly experimental, use at own risk)
Save and close the file. It might prompt you to save the file to a different place and not allow you to save in the Bin folder. Just save it someplace else in this case and copy/paste it to the Bin folder afterwards. If asked to overwrite the existing file, click yes.
Now start your game and see if it makes a difference in smoothness or texture loading. Make sure to check RAM and VRAM usage to see how it works.
You might need to change the values back and forth to find the “sweet spot” for your game. Mine seems to work best with setting the first value to 2147483648 and the second to 1073741824.
Uninstallation
Delete these files from your bin folder (installation path):
d3d9.dll
DXVK.conf
TS3W.DXVK-cache
And if you have it, also TS3W_d3d9.log
if you changed the values in your GraphicsRule.sgr file, too, don’t forget to change them back or to replace the file with your backed up version.
OR
delete the bin folder and add it from your backup again.

B. with Reshade/GShade
Follow the steps from part A. no Reshade/Gshade to set up DXVK.
If you are already using Reshade (RS) or GShade (GS), you will be prompted to overwrite files, so choose YES. RS and GS may stop working, so you will need to reinstall them.
Whatever version you are using, the interface shows similar options of which API you can choose from (these screenshots are from the latest versions of RS and GS).
Please note:
Each time you install and uninstall DXVK, switching the game between Vulkan and d3d9, is essentially changing the graphics card ID again, which results in the settings in your options.ini file being repeatedly reset.
ReShade interface
Choose – Vulcan

Click next and choose your preferred shaders.
Hopefully this install method works and it won't install its own d3d9.dll file.
If it doesn't work, then choose DirectX9 in RS, but you must make sure to replace the d3d9.dll file with DXVK's d3d9.dll (the one from its 32bit folder, checking its size is 3.86mb.)
GShade interface
Choose –
Executable Architecture: 32bit
Graphics API: DXVK
Hooking: Normal Mode
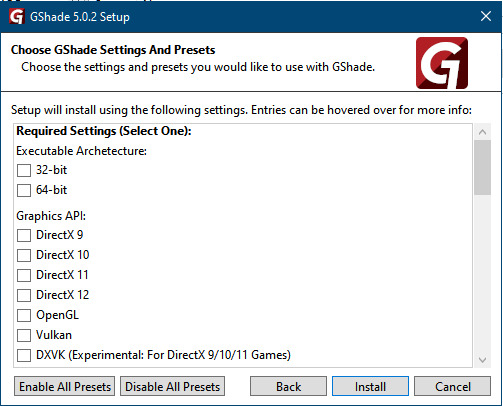
GShade is very problematic, it won't work straight out of the box and the overlay doesn't show up, which defeats the purpose of using it if you can't add or edit the shaders you want to use.
Check the game's bin folder, making sure the d3d9.dll is still there and its size is 3.86mb - that is DXVK's dll file.
If installing using the DXVK method doesn't work, you can choose the DirectX method, but there is no guarantee it works either.
The game will not run with these files in the folder:
d3d10core.dll
d3d11.dll
dxgi.dll
If you delete them, the game will start but you can't access GShade! It might be better to use ReShade.
Some Vulcan and DirectX information, if you’re interested:
Vulcan is for rather high end graphic cards but is backward compatible with some older cards. Try this method with ReShade or GShade first.
DirectX is more stable and works best with older cards and systems. Try this method if Vulcan doesn't work with ReShade/GShade in your game – remember to replace the d3d9.dll with DXVK's d3d9.dll.
For more information on the difference between Vulcan and DirectX, see this article:
https://www.howtogeek.com/884042/vulkan-vs-DirectX-12/
748 notes
·
View notes
Text
i know i know, i keep bringing up linux from time to time, but omg it's just BETTER. And yes I would LOVE more shit that's on windows to be on linux and not have to go through various hoops to get relatively the same thing... BUT
let me tell you,
when my pc is IDLE.... it is IDLE!
ON WINDOWS ON THE OTHER HAND
when the pc detects you've gone idle, it starts the whole process of collecting data on your pc with fucking "compatibility telemetry" and the other data collection services that i forgot the names of that are masked as "ways to make your pc experience better".
Better???? STOP USING 100% OF MY CPU AND BANDWIDTH TO COLLECT USAGE STATISTICS THAT CAN'T BE TURNED OFF WITHOUT FUCKING UP SOMETHING ELSE
and this is just Windows 10, windows 11 is worse with it's AI bullshit. *SCREAMS IN GODDAMN IT*
Look, all i'm saying is, my EXPERIENCE with linux is just so much better despite some of the hurdles. They're small hurdles.
28 notes
·
View notes
Text
Windows Manager Software for Your PC – Why Yamicsoft is a Must-Have

Your Windows PC is a powerful machine — but over time, it can slow down, become cluttered, and behave unpredictably. That’s where Yamicsoft’s Windows Manager software steps in. Whether you’re running Windows 10 or Windows 11, Yamicsoft offers a dedicated system utility suite designed to help you clean, optimize, repair, and customize your operating system with ease.
⚙️ What Is Windows Manager Software?
Windows Manager software is a comprehensive utility designed to give you full control over your computer’s performance, behavior, and appearance. Think of it as your PC’s personal assistant — handling tasks that Windows itself doesn’t always manage well.
Yamicsoft’s offerings — Windows 10 Manager and Windows 11 Manager — go beyond traditional cleaners. They deliver 30+ tools in one lightweight package, allowing users to:
Speed up system performance
Free up disk space
Strengthen system security
Customize hidden Windows settings
Fix common errors and bugs
Manage startup programs and scheduled tasks
🚀 Boost Speed and Performance
Over time, unnecessary files, startup programs, and system errors can slow down your PC. Yamicsoft helps you:
Optimize memory and CPU usage
Disable unneeded services
Streamline boot time
Manage background apps efficiently
🧼 Clean and Organize with One Click
Yamicsoft’s Cleaner module clears out junk files, temp data, registry errors, and invalid shortcuts. Its Disk Analyzer shows you what’s eating up your storage and offers safe cleanup options.
🔧 Repair Tools That Work
From repairing broken registry entries to fixing Windows Update issues, the built-in Repair Center is your one-stop solution for:
Solving system crashes and glitches
Rebuilding corrupted configurations
Restoring essential Windows components
🛡️ Secure and Protect Your PC
Yamicsoft lets you take control of your system’s privacy and security settings. With options to disable telemetry, configure firewalls, and manage account privileges, your data and activity stay protected.
🎨 Personalize Your Experience
Customize Windows like never before:
Change system icons and login screen
Manage context menus and shortcuts
Tailor the user interface to suit your needs
Tweak advanced system behaviors with safety
💼 Who Is It For?
Yamicsoft’s Windows Manager is ideal for:
Everyday users looking to speed up their computers
IT professionals managing multiple systems
Power users who want full control over Windows
Anyone experiencing system slowdowns or errors
✅ Why Choose Yamicsoft?
30+ tools in one intuitive interface
Safe, fast, and lightweight
Compatible with the latest Windows updates
Regular updates and lifetime license options
Backed by years of trust in PC optimization
📥 Ready to Optimize Your PC?
Download Windows 10 Manager or Windows 11 Manager from www.yamicsoft.com and discover just how smooth and fast your PC can really be.
0 notes
Text
What Database does an MMO need?
Unless you're talking about something like Node.Js (an asymmetrical Database // spreadsheeting system) most database "types" are sorely outdated and are closer to a prototype based on our current technology.
"If it ain't broke, somebody else will make a better one *eventually*"
I've spoken at length about how SQL and Database Injections are relatively easy to perform; mostly because these systems were developed for an environment that if you needed secure data; it wouldn't be online.
Video Games of today are *just* now pushing against those limitations of prerequisite security. Mostly because they have the ability to ban and perform server rollbacks in the case of any sort of hacking.
But as the internet expands and grows; so do the security requirements of even the most barebonesest of Server and Cloud Hosting.
So what does an MMO actually need to secure?
An Online Game today requires, at minimum, to support a User-Account for every player (or potential player)
At 1 million players for your high-end MMOs; that's a tall ask. If each player requires a megabyte of data storage for an account; that's easily a *whole* terabyte of data that needs to be stored and accessed near simultaneously.
Which means that you *also* need to access that data asynchronously; which introduces Data Redundancy in the system. And can, potentially, reach to the 10s of Terabytes based solely on that 1 megabyte per player stored.
That's a lot to keep track of.
So what kind of data is currently being tracked for every singular account ?
Account Name, Password, Credit Card info (which may include personally identifying information), and a host of "Flags" (usually Boolean truthy values, but can be similar to anything found in your Windows Registry,) which today include things like Micro-Transactions and Arbitrary account-wide information.
And none of that includes what might be found on a single Character found underneath that account.
Some Publishers had previously replied heavily on "Time Cards" or your "$19 fortnight cards". Which reduces the requirements of having linked payments and PII linked to accounts.
But those are becoming more and more cumbersome to use; especially since you're frequently left with some arbitrary small amount on your account that you can't use to purchase anything (because everything is *just* slightly more than what usually remains from a rounded off time card).
A proper solution these days includes services that Players use like App-Stores, Video Game Libraries, and Pay Pal; which offloads *most* of that data to the payment or library service.
This is, more or less; the direction of the entire internet these days; and hence why those particular services are focusing more on Security and Privacy.
AI suggests that Cloud Services for *just* 10 terabytes of data itself starts at $300 a month.
And that's just for the storage, and not usage and retrieval stats; which have been starting to be priced per connection of transaction.
Meaning around $0.10 per data-transaction. With some developers *accidentally* publishing algorithms that have brought some hefty bills on their heads.
While that link says an accidental $900 over night; I've seen reports up to a million for a negligently posted algorithm under one of these services.
It doesn't help that those services are convoluted and very unintuitive to use. That's a personal observation. It almost *feels* like it's the intended way new cloud services are supposed to work.
The reason the prices are so Hefty these days is because internet Bandwidth and Throughputs are at a premium.
Thanks to copyright debacles, Napster, Limewire, Pirates Bat and the like; Internet Companies focused heavily *more* on stopping the parent and copyright theft through their services and refused to prepare for a future where it was the norm.
Thanks to Netflix and Hulu and Spotify and Steam and funking everything; We arrived at that Future in approximately 2010.
And the Internet Companies are still limping along at two-decade old Data rates BECAUSE, and I quote; "We don't need to worry about increased bandwidth and throughput usage because only Hackers and Thieves use such large amounts of Data."
So we've arrived at the future wholely unready; despite knowing exactly where the future was going.
There may have been other reasons; but that's the one given to Officials and Media Outlets for Non-Internet-Enthusiasts; so that's the one you get guys.
The one where Big-Network blamed bandwidth issues on Hackers; and now charges exuberant fees to stay connected to your costly 5g account.
I said "5G", but there's bandwidth issues at your Comcast router as well. Big companies are even preventing users from installing their own Routers so they don't have to worry about rental and service fees.
I was even personally attacked by someone on my home internet; who didn't like my set-up and called Comcast themselves to force my account off of a personal router to the "official one."
Which cost me quite a pretty penny, let me tell you.
After all of that;
An MMO subsequently has an entire separate DataBase from the "accounts data" for each individual character; usually obfuscatedly linked to the Users Account Entry.
A Typical Character in a database uses a multitude of Flags and Counting mechanisms in order to reduce that total overhead.
Reducing as much overhead for a single character as humanly possible.
The more players in a particular MMO; the less data per character allowed to be stored.
Some games get around this by charging extra fees for extra characters or services (to help alleviate storage costs)
But; we've been stagnating for a while in an environment where MMOs, especially of the AAA variety cannot keep up with Indie Games.
Simply through the virtue of Database and Cloud Hosting pricing.
There are Some Blockchain and NFT tech in the works that *might* work as a suitable substitute; but the overhead for Crypto itself is kind of immense; especially as the Lifespan of each chain increases.
And most new Crypto-Currencies... Are created by Hackers and Hobbyists who just wanted to know how the tech works.
Which makes most of them (Especially Bandwagon Hoppers in the Financial District) Useless.
0 notes
Text
Securing Your Software : The Relevance Of Product-Keys

In the digital arena, where software regulations supreme, product keys stand up as the gatekeepers to gain access to. Whether it's your system software or even essential performance collections like windows 10 home oem key take an essential function in making certain sanctioned utilization. Allow's look into why these alphanumeric codes are extremely important in securing your software expenditures.
Recognizing windows Product Key
At the core of your processing adventure exists the os, frequently Microsoft windows for numerous individuals worldwide. The windows product key, an unique alphanumeric regulation generally located on a sticker label affixed to your unit or provided with the software, works as your ticket to uncover the complete functions of windows.
Enforcing License Compliance
Product keys are instrumental in upholding software certificate agreements. Through demanding a legitimate product key for setup as well as activation, software firms ensure that individuals stick to the phrases of usage. This certainly not merely guards their copyright but additionally promotes a fair as well as maintainable software community.
Stopping Piracy
One of the absolute most considerable difficulties software creators experience is actually piracy. Illegally dispersing or even making use of software without proper licensing not merely robs designers of rightful income however additionally weakens the honesty of their products. Product keys work as a preventive versus piracy, as accessing the full attributes of software calls for a legitimate key.
Making sure Security
Product keys support the protection of your software ecosystem. They work as an one-of-a-kind identifier, connecting the software to a certain user or even tool. This helps in tracking utilization, managing software updates, and also delivering assistance companies. Additionally, through demanding account activation through a product key, creators can mitigate the risk of unwarranted get access to and also protect versus malware and cyber threats.
Facilitating Support and also Upgrades
Having an authentic product key streamlines the procedure of seeking help as well as accessing software upgrades. When fixing issues or even upgrading to more recent variations, offering your product key helps validate your qualifications for assistance and makes certain a seamless shift. It also allows programmers to present patches and also updates properly, maintaining your software protected and around day.
The part of MS Office Product Key
Microsoft Office, the ubiquitous collection of efficiency applications, likewise relies upon product keys for verification. Whether you're making documentations in Word, crunching varieties in Excel, or even providing discussions in PowerPoint, your MS Office product key grants you accessibility to these important tools.
Opening Premium Features

MS Office product keys open a myriad of costs features, from advanced format options to cooperation tools and also cloud storage assimilation. These components improve your performance as well as make it possible for seamless partnership around groups, producing the assets in a reputable product key beneficial.
Sustaining Compliance and also Security
Comparable to windows 10 pro oem key are actually essential for sustaining conformity with licensing deals as well as making sure the security of your software setting. By verifying the genuineness of your duplicate of MS Office, product keys aid obstruct unapproved consumption and shield your data from prospective violations.
Outcome
In the electronic age, where software electrical powers our everyday activities and endeavors, product keys play a critical function in guarding our digital assets. From running systems to efficiency rooms, these alphanumeric regulations uphold certificate conformity, prevent piracy, make sure surveillance, and also assist in support as well as upgrades. So, the following time you put up a part of software, remember the usefulness of the meager product key-- it is actually certainly not simply a cord of personalities yet a crucial to unlocking a planet of probabilities.
0 notes
Text
Innovations & Trends in ICT Procurement for the Future
Originally Published on: Spendedge | Media, ICT, and Entertainment Resources
• ICT procurement professionals must actively pursue chances that are on the horizon that will probably be more lucrative for their role in the mid- to long-term, moving beyond the normal vanilla (read cost containment and risk mitigation).
• The use of fixed cost OpEx solutions is accelerating due to the continued growth of cloud services and improved cloud computing security, which is assisting businesses in increasing the predictability of their IT spending.
• ICTs can be crucial to the effectiveness of efforts to combat climate change, yet this can be a burdensome duty.
• However, ICT businesses have the opportunity to excel in social and environmental sustainability in addition to maximising profits by sowing the seeds of "green thinking" and integrating life cycle assessment (LCA) into the supply chain.
Driving business excellence with ICT procurement innovations and being current
A compelling argument in favour of single-window procurement:
• Better supply-side visibility enables CPOs in charge of ICT infrastructure to capture and significantly cut spending outside the bounds of regular corporate guidelines, increasing their net operating income.
• It should be possible to control unforeseen spending through the use of centralised ICT procurement programmes and supporting tools, as well as to collect buy analytics and make sure procurement specialists always have access to deep and accurate information.
Discussions about consumption-based pricing should be reframed:
• Accessing IT infrastructure and applications via the Internet on an on-demand basis ("cloud computing") is becoming the new normal in ICT procurement.
• According to a Q4 2022 poll, about 70% of all decision-makers intend to switch from old business software to cloud-based solutions or move their workloads from on-premises datacenters to the cloud.
• Importantly, end users of the public cloud are expected to spend $550 billion globally in 2023, up from $450 billion in 2022.
Lifecycle evaluation redefines environmental impact:
• An ICT product has a significant environmental impact at every stage of its lifecycle, including mineral extraction, production, storage, transit, usage, and disposal.
• ICTs are viewed as a key component of the "climate change mitigation" jigsaw, to the point where the International Telecommunication Union (ITU) has created a universally accepted methodology to assess the influence of ICTs on climate change over the course of their goods and services' lifetimes.
• Every step of the ICT procurement process must therefore incorporate a lifetime perspective on the environmental impact of such assets if an organisation wants to remain competitive in five years.
Obtain the best rates via increasing standardisation and consolidation:
• Despite common belief, an online ICT procurement procedure accomplishes far more than simply shortening the buying period.
• In order to make more educated judgements, CPOs can use ICT in procurement to find helpful information in huge data sets on previous purchases, buying frequency, quantity, pricing, vendor performance, and supplier obligations.
• Additionally, by drastically de-intermediating the ecology of purchases, procurement teams can reduce expenses by at least 10% to 15%.
Stop overspending and utilise ICT budgets as efficiently as possible:
• Businesses can escape the long-term service contract lock-ins connected with traditional ICT procurement spend by migrating to OpEx models.
• Since the cloud service provider is responsible for maintaining servers, computers, and databases, ICT firms can get them to scale up and down the cloud infrastructure as necessary to handle workloads.
• Costs aside, cloud-based systems guarantee authorised users have immediate access to online services regardless of where they are, what device they are using, or what time of day or night it is.
Green supply chain practises should be integrated at every stage:
• The ICT industry must work to reduce the usage of virgin materials while increasing the usable lifespan of assets by up to 100% in a circular economy!
• The practise of intentional obsolescence of ICT assets, such as the end of software support, is being observed by a growing number of stakeholders.
• Additionally, it is critical that ICT procurement organisations assess the environmental impact of an ICT asset at every stage, from manufacture through recycling or disposal, from a mid- to long-term perspective.
Why Choose SpendEdge?
• Our experts help ICT players monitor suppliers' sustainability practises and make sure that supply chain participants evaluate actions with an eye towards "lifecycle assessment" when taking the environmental impact of products into account.
• Sustainable ICT procurement is the industry's catchphrase now and in the future, and being green is the new measure of financial success.
• Knowing this, we offer solutions that enable ICTs to include sustainability into every stage of the supply chain for their goods while being economically viable.
Success stories: SpendEdge's market intelligence enables ICT procurement clients to save money and achieve strategic goals
• With an annual revenue of close to $80 million and a staff of 600, our client is a market leader in mechanical, electrical, and plumbing (MEP) products and services with more than two decades of experience.
• The study examines over 25 new and current suppliers based on factors including their international IT relationships, hardware and infrastructure offerings, service platforms, and years of expertise.
• One of the suppliers that made the study's shortlist has signed a contract with the customer.
For help with your supply chain, get in touch with us.
0 notes
Video
youtube
How to control the usage of data on your computer
0 notes
Text
Watomatic, for lower Whatsapp switching costs
Any discussion of monopolization of the web is bound to include the term “network effects,” and its constant companion, “natural monopolies.” This econojargon is certainly relevant to the discussion, but really needs the oft-MIA idea of “switching costs.”
A technology has “network effects” when its value grows as its users increase, attracting more users, making it more valuable, attracting more users.
The classic example is the fax machine: one fax is useless, two is better, but when everyone has a fax, you need one too.
Social media and messaging obviously benefit significantly from network effects: if all your friends are on Facebook (or if it’s where your kid’s Little League games are organized, or how your work colleagues plan fun activities), you’ll feel enormous pressure to join.
Indeed, in these days of Facebook’s cratering reputation, it’s common to hear people say, “I’m only on FB because my friends are there,” and then your friends say, “I’m only there because you are there.”
It’s a form of mutual hostage-taking.
That hostage situation illustrates (yet) another economic idea: “collective action problems.” There are lots of alternatives to Facebook, but unless you can convince everyone on Facebook to pick one and move en masse, you’ll just end up with yet another social account.
This combination of network effects and collective action problems leads some apologists for tech concentration to call the whole thing a “natural monopoly” — a system that tends to be dominated by a single company, no matter how hard we try.
Railroads are canonical “natural monopolies.” Between the costs of labor and capital and the difficulty in securing pencil-straight rights-of-way across long distances, it’s hard to make the case for running a second set of parallel tracks for a competing company’s engines.
Other examples of natural monopolies include cable and telephone systems, water and gas systems, sewer systems, public roads, and electric grids.
Not coincidentally, these are often operated as public utilities, to keep natural monopolies from being abused by greedy jerks.
But the internet isn’t a railroad. Digital is different, because computers are universal in a way that railroads aren’t — all computers can run all programs that can be expressed in symbolic logic, and that means we can almost always connect new systems to existing ones.
Open up a doc in your favorite word processor and choose “Save As…” and just stare in awe and wonder at all the different file-formats you can read and write with a single program. Some of those formats are standardized, while others are proprietary and/or obsolete.
It’s easier to implement support for a standard, documented format, but even proprietary formats pose only a small challenge relative to the challenge presented by, say, railroads.
Throw some reverse-engineering and experimentation at a format like MS DOC and you can make Apple Pages, which reads and writes MS’s formats (which were standardized shortly after Pages’ release, that is, after the proprietary advantage of the format was annihilated).
This is not to dismiss the ingenuity of the Apple engineers who reversed Microsoft’s hairball of a file-format, but rather, to stress how much harder their lives would have been if they were dealing with railroads instead of word-processors.
During Australia’s colonization, every state had its own governance and its own would-be rail-barons. Each state laid its own gauge of rail-track, producing the “multi-gauge muddle” — which is why, 150+ years later, you can’t get a train from one end of Oz to the other.
Hundreds of designs for interoperable rolling stock have been tried, but it’s proven impossible to make a reliable car that retracts one set of wheels and drops a different one.
The solution to the middle-gauge muddle? Tear up and re-lay thousands of kilometers of track.
Contrast that with the Windows users who discovered that Pages would read and write the thousands of documents they’d authored and had to exchange with colleagues: if they heeded the advice of the Apple Switch ads, they could buy a Mac, move their files over, and voila!

Which brings me to switching costs. The thing that make natural monopolies out of digital goods and services are high switching costs, including the collective action problem of convincing everyone to quit Facebook or start using a different word-processor.
These switching costs aren’t naturally occurring: they are deliberately introduced by dominant firms that want to keep their users locked in.
Microsoft used file format obfuscation and dirty tricks (like making a shoddy Mac Office suite that only offered partial compatibility with Windows Word files) to keep the switching costs high.
By reverse-engineering and reimplementing Word support, Apple obliterated those switching costs — and with them, the collective action problem that created Word’s natural monopoly.
Once Pages was a thing, you didn’t have to convince your friends to switch to a Mac at the same time as you in order to continue collaborating with them.
Once you get an email-to-fax program, you can discard your fax machine without convincing everyone else to do the same.
Interoperability generally lowers switching costs. But adversarial interoperability — making something new that connects to something that already exists, without its manufacturer’s consent — specifically lowers deliberate switching costs.
Adversarial interoperability (or “competitive compatibility,” AKA “comcom”) is part of the origin story of every dominant tech company today. But those same companies have gone to extraordinary lengths to extinguish it.
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
Just as a new company may endorse standardization when it’s trying to attract customers who would otherwise be locked into a “ecosystem” of apps, service, protocols and parts, so too do new companies endorse reverse-engineering and comcom to “fix” proprietary tech.
But every pirate wants to be an admiral. Once companies attain dominance, they start adding proprietary extensions to the standard and fighting comcom-based interoperability, decrying it as “hacking” or “theft of intellectual property.”
In the decades since Microsoft, Apple, Google, and Facebook were upstarts, luring users away from the giants of their days, these same companies have labored to stretch copyright law, terms of service, trade secrecy, patents and other rules to ban the tactics they once used.
This has all but extinguished comcom as a commercial practice. Today’s comcom practitioners risk civil and criminal liability and struggle to get a sympathetic hearing from lawmakers or the press, who have generally forgotten that comcom was once a completely normal tactic.
The obliteration of comcom is why network effects produce such sturdy monopolies in tech — and there’s nothing “natural” about those monopolies.
If you could leave Facebook but still exchange messages with your friends who hadn’t wised up, there’d be no reason to stay.
In other words, the collective action problem that the prisoners of tech monopolies struggle with is the result of a deliberate strategy of imposing high technical and legal burdens to comcom, in order to impose insurmountable switching costs.
I wrote about this for Wired UK back in April, comparing the “switching costs” the USSR imposed on my grandmother when she fled to Canada in the 1940s to the low switching costs I endured when I emigrated from Canada to the UK to the USA:
https://www.wired.co.uk/article/social-media-competitive-compatibility
Today, there’s a group of tech monopoly hostages who are stuck behind their own digital iron curtain, thanks to Facebook’s deliberate lock-in tactics: the users of Whatsapp, a messaging company that FB bought in 2014.
Whatsapp was a startup success: founded by privacy-focused technologists who sensed users were growing weary of commercial surveillance, they pitched their $1 service as an alternative to Facebook and other companies whose “free” products extracted a high privacy price.
Facebook bought Whatsapp, stopped the $1 charge, and started spying. In response to public outcry, the Facebook product managers responsible for the app assured its users that the surveillance data WA extracted wouldn’t be blended with Facebook’s vast database of kompromat.
That ended this year, when every Whatsapp user in the world got a message warning them that Facebook had unilaterally changed Whatsapp’s terms of service and would henceforth use the app’s surveillance data alongside the data it acquired on billions of people by other means.
Downloads of Whatsapp alternatives like Signal and Telegram surged, and Facebook announced it would hold off on implementing the change for three months. Three months later, on May 15, Facebook implemented the change and commenced with the promised, more aggressive spying.
Why not? After all, despite all of the downloads of those rival apps, Whatsapp usage did not appreciably fall. Convincing all your friends to quit Whatsapp and switch to Signal is a lot of work.
If the holdout is — say — a beloved elder whom you haven’t seen in a year due to lockdown, then the temptation to keep Whatsapp installed is hard to resist.
What if there was a way to lower those collective action costs?
It turns out there is. Watomatic is a free/open source “autoresponder” utility for Whatsapp and Facebook that automatically replies to messages with instructions for reaching you on a rival service.
https://play.google.com/store/apps/details?id=com.parishod.watomatic
It’s not full interoperability — not a way to stay connected to those friends who won’t or can’t leave Facebook’s services behind — but it’s still a huge improvement on the nagging feeling that people you love are wondering why you aren’t replying to their messages.
The project’s sourcecode is live on Github, so you can satisfy yourself that there isn’t any sneaky spying going on here:
https://github.com/adeekshith/watomatic
It’s part of a wider constellation of Whatsapp mods, which have their origins in a Syrian reverse-engineer whose Whatsapp comcom project was picked up and extended by African modders who produced a constellation of Whatsapp-compatible apps.
https://www.eff.org/deeplinks/2020/03/african-whatsapp-modders-are-masters-worldwide-adversarial-interoperability
These apps are often targeted for legal retaliation by Facebook, so it’s hard to find them in official app stores where they might be vetted for malicious code.
It’s a strategy that imposes a new switching cost on Whatsapp’s hostages, in the form of malware risk.
Legal threats are Facebook’s default response to comcom. That’s how they responded to NYU’s Ad Observer, a plugin that lets users scrape and repost the political ads they’re served.
https://www.eff.org/deeplinks/2021/04/553000000-reasons-not-let-facebook-make-decisions-about-your-privacy
Ad Observer lets independent researchers and journalists track whether Facebook is living up to its promises to block paid political disinformation. Facebook has made dire legal threats to shut this down, arguing that we should trust the company to mark its own homework.
Whatsapp lured users in by promising privacy. It held onto them post-acquisition by promising them their data would be siloed from Facebook’s main databases.
When it reneged on both promises, it papered this over by with a dialog box where they had to click I AGREE.
This “agreement” is a prime example of “consent theater,” the laughable pretense that Facebook is “making an offer” and the public is “accepting the offer.”
https://onezero.medium.com/consent-theater-a32b98cd8d96
Most people never read terms of service — but even when they do, “agreements” are subject to unilateral “renegotiation” by companies that engineered high switching costs as a means of corralling you into clicking “I agree” to things no rational person would ever agree to.
Consent theater lays bare the fiction of agreement. Real agreement is based on negotiation, and markets are based on price-signals in which buyers and sellers make counteroffers.
A “market” isn’t a place where a dominant seller names a price and then takes it from you.
Comcom is a mechanism for making these counteroffers. Take ad-blockers, which Doc Searls calls “the largest consumer boycott in history.” More than a quarter of internet users have installed an ad-block, fed up with commercial surveillance.
This is negotiation, a counteroffer. Big Tech — and the publications it colonizes — demand you give them everything, all the data they can extract, for every purpose they can imagine, forever, as a condition of access.
Ad-block lets you say “Nah.”
https://www.eff.org/deeplinks/2019/07/adblocking-how-about-nah
The fiction that tech barons have “discovered” the “price” that the public is willing to pay for having a digital life is a parody of market doctrine. Without the ability to counteroffer — in code, as well as in law — there is no price discovery.
Rather, there is price-setting.
Not coincidentally, “the ability to set prices” is the textbook definition of an illegal monopoly.
66 notes
·
View notes
Text
Let’s Talk About Trackers...
Because of the major talk about them yesterday and how an anon tried to throw me under the bus, I want to make an informative post about the specific tracker I use and certain others do too (assuming they still use these). This will also go under a keep reading so you don’t have to scroll in case you read it and then don’t wanna scroll past it a second time.
I personally use a site called statcounter. What is stat counter? Well, let me explain with an excerpt from Wikipedia!
“StatCounter is a web traffic analysis website started in 1999. Access to basic services is free and advanced services can cost between US$5 and US$119 a month. StatCounter is based in Dublin, Ireland. The statistics from StatCounter are used to compute web usage share for example. As of May 2019, StatCounter is used on 0.9% of all websites. StatCounter statistics are directly derived from hits—as opposed to unique visitors—from 3 million sites, which use StatCounter, resulting in total hits of more than 15 billion per month. No artificial weightings are used to correct for sampling bias, thus the numbers in the statistics can not be considered to be representative samples.”
Statcounter I find has some cool features too if you do run a business site, which I aim to do in the future, here’s some of the cool analytics stuff they have if you’re a business marketer:
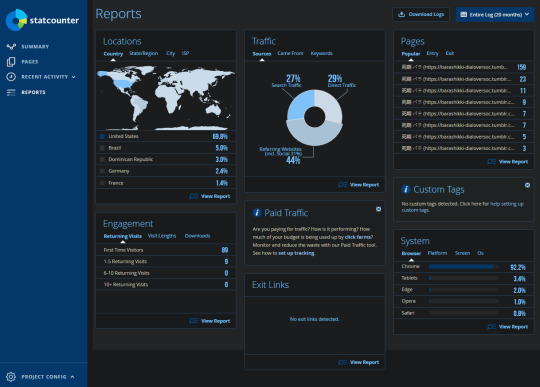
This above is a capture taken for the tracker on my OC blog @ / barashikki-dialoversoc
This tool here provides where the majority of your people come from, so it will help businesses to have features such as this, so StatCounter is cool to use for business and marketing.
But that’s not why we’re here, are we?
StatCounter says they provide you with IPs in hopes of blocking/banning them from your site and/or stopping fraud on your website.
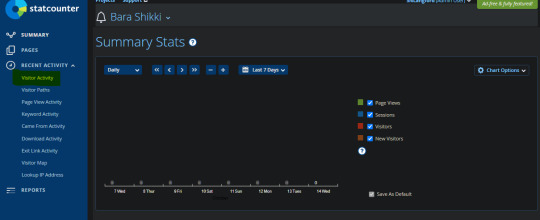
Sure, that’s useful as I personally use that to block people’s IPs if they send me hate anons. But here is how it’s an issue... This specific tab, which I know M/C uses quite often from my former friendship with her: Visitor Activity
Now, let’s go there and break it down. I will be censoring sensitive information like people’s locations and IP addresses to protect them.

I want to also address the “xxx is now using 100% of its log space” too.
It may be hard to read, but it says the following
“Your Project Bara Shikki is now using 100% of its log space. This means that your website traffic data for detailed stats older than 7 months* will be overwritten to make room for new data. You can upgrade for $9/month to increase your log to 10+ years*. If you don't mind losing this old data for detailed stats, then no action is required on your part. Summary Stats are included with all plans and are unlimited.
* Estimated based on your current traffic”
For my other blog @ / dialoving-lemons, it deletes this info in 7 days due to the high demand traffic (it is a LOT more popular than any of my other blogs despite me being on hiatus there).
So while that is good, this information stays for a while. If someone is paying for this service, they can keep this info for a long time.
Now onto the part we are mainly addressing, addresses and IPs. I will use my own visits for the example (the white censor). And yes, you can appear on your own tracker as it picks anyone up who visits the URL.
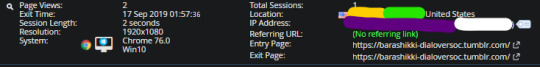
I color coded this so we can do a breakdown.
Yellow is my city. Green is the state (will be providence if you are in another country). Then you see “United States” as the country it says I’m from. Your country’s flag also appears before your location.
^^^This here is already pretty accurate and sensitive information, and we haven’t even gotten to the second line yet.
For the second line, we have these: Purple is your internet provider. White, that’s your IP. See that tag next to it? You can click on that and make notes in it for when that person returns to your url. You can even sign up for notifications to get emails or alerts on your phone (if you have the statcounter app). How do I know this? This is how:
Incognito doesn’t have dark mode, so sorry for bright image lol
Idk about you guys, but that’d make me uncomfortable to know someone could just get a ping saying I’m visiting their page. Again, I don’t know what features M/C uses, so I can’t say if she has this or not.
So not only can you find someone’s location, internet provider, and IP (which I think is enough for someone who hack or screw you over somehow, idk. I’d want to look that info up) but you can also stalk when they’re on your blog. This is a big YIKES.
Now back to the breakdown of the image from earlier...

You can learn what device they used, their browser, get a timestamp, and also how long they were on your page. I personally don’t care sharing this info, many of us use the most updated browser of our choice and most of us are on windows 10 for computer users.
So... yeah. While I use statcounter myself to block haters and redirect their IPs so they can’t get on my page anymore, I feel this site does give out too much information. On top of that, the one we all know who uses this software also has some software that checks who unfollows her. She uses these to get dirt on people and to expose them, it is not for her safety.
Now some tips on how to be safe if you don’t want to be tracked thanks to me testing things out:
Use the tumblr app.
The tumblr app uses coding for mobile usage. It does not rely on urls, but another form of code. StatCounter cannot log this code, so you will not appear on the visitor activity tab.
View blogs in side view

This is side view for those that don’t know. Side view acts a lot like the app in terms of the coding. So viewing like this is safe for you to not appear on trackers.
StatCounter relies on you typing in and clicking on urls on someone’s tumblr page (if installed on a tumblr).
As long as you are on a way that doesn’t rely on url systems, you are safe from appearing in someone’s tracker.
And a final note, if you are going to use one like I do, for blocking haters’ IPs, then I highly recommend putting a disclaimer in your description. I immediately did that when I installed mine so people knew they’d get rerouted if they started crap with me. I personally feel that keeping it secret that you have a tracker is violating someone’s consent as you are gathering info without their permission. By saying you have one, them being able to use ways where they won’t be tracked is very useful and helps them feel at ease knowing they can decide if they’re fine popping up on your tracker or not. Here is an example disclaimer you can put if you do put one in. Feel free to copy and paste too!
"Disclaimer: I use a tracker that allows me to see visitors’ IPs so I can block them if they cause problems for me, proceed at your own risk"
68 notes
·
View notes
Text
10 Quick Tips for Windows 7, 8.1, as well as 10

One of the most prominent or extensively utilized Windows versions are Windows 7, Windows 8.1 as well as Windows 10. Windows 7 with codename Vienna or Blackcomb becomes part of the Windows NT family members as well as was released back in July 22, 2009. This version was produced to attend to the essential function of its precursor which is the Windows Vista.
Windows 7 has obtained substantial positive statements because of its raised performance, intuitive interface as well as numerous various other kept in mind renovations. As a matter of fact, some movie critics have actually strongly explained that Windows 7 is the best Windows variation ever before. One of the most effective features of this variation is that customers currently have lots of choices to really increase their efficiency while dealing with their computer system.
Right here are the top 10 techniques as well as tips for Windows 7:
1. Use Windows 7 keyboard faster ways such as pressing Ctrl + Shift + N to develop a new folder. 2. Make one of the most out of Jump Lists so you can easily access any folder or home windows that you normally make use of. 3. Usage concealed worldwide themes or wallpapers by following these actions: Kind C: \ Windows \ Globalization \ MCT in the search box at the Start Menu and after that press Enter. Windows 7 will after that reveal you a listing of sub-folders for each and every nation. Look for your favored theme or history. 4. Windows 7 enables users to make use of multiple monitors for whatever objective it might serve.windows 10 pro product key 5. Customers can currently acquire a power performance report wherein the operating system can have a look at your laptop's energy use. To do this, just run a command prompt by typing cmd in the search box. When the symbol shows up, appropriate click and then select "Run as administrator." Inside the command box, kind powercfg -energy-output \ Folder \ Energy_Report. HTML. 6. Windows 7 has an amazing taskbar with a variety of attributes that can assist any person maximize their work. 7. Use check boxes for far better efficiency. This indicates that you can now make it possible for check boxes for folders and data in bulk. 8. Users can currently tailor the notice location or the system tray so they can just see the icons that they regularly use. 9. Use the shake function. This function will certainly help individuals remove all the clutter in a single action. 10. Aero Snap is just one of Windows 7 functions wherein users can make the most of a window by dragging the icon sideways of the display. Next off on the listing is Windows 8.1 with codename Blue which is an upgrade for the Windows 8 version. Most individuals claim that Windows 8.1 is the better version of the Windows 8 with several essential tweaks. Below are a few pointers and methods for Windows 8.1: 1. The ever before trusted Start switch is back on Windows 8.1 in which users can check out the choices. 2. Users can now customize the house display ceramic tiles as well as regroup similar tiles. 3. Windows 8.1 currently has an option to allow customers go directly to the desktop instead of managing the begin display floor tiles. 4. Windows 8.1 allows users to comfortably organize their apps in different good manners such as identifying them by the installment date or for other reason. 5. Utilize the app bars. 6. Windows 8.1 customers now have the alternative to make the Start switch better. 7. Applications that are no more in use can now be stopped from running in the background. 8. Customers can now easily change the screen settings such as positioning as well as resolution. 9. Windows 8.1 enables individuals to see several applications all at the same time. 10 With Windows 8.1, customers have the option to save any type of online post so they can review it also when they are offline. Windows 10. Windows 10 is the current as well as most talked about Windows version which was first launched for consumers on July 29, 2015. Windows 10 is currently being provided for free where many existing individuals are making the upgrade.
Here are a couple of tips and also tricks which can make your Windows 10 experience much better:
1. Beginning with the GodMode in which individuals can get an advanced control board. Simply develop a new folder anywhere and then relabel it as GodMode. 2. Customize the Start food selection to make the computer work for you. 3. Users currently have the alternative to schedule Windows updates to stay clear of all the pesky suggestions or automatic updates. 4. You can conveniently change to tablet mode with this Windows variation if you have a touchscreen gadget. 5. If you are utilizing many applications, Windows 10 permits users to produce online desktops which are wonderful. 6. If you are making use of a laptop, Windows 10 can conserve your battery life. 7. Greet to Windows 10's biometric safety function where customers can open their COMPUTER with their finger print. 8. This Windows variations has actually added a controversial attribute which permits users to restrict their Wi-Fi to others. 9. Customers can now print to PDF without using one more utility. 10. Windows 10 deals customers the possibility to reverse their upgrade within a month of installation. The most preferred or commonly used Windows versions are Windows 7, Windows 8.1 and Windows 10. Windows 7 with codename Vienna or Blackcomb is component of the Windows NT family and was launched back in July 22, 2009. Windows 7 has obtained substantial positive statements due to its raised performance, instinctive user interface as well as numerous other noted improvements. Some critics have actually highly pointed out that Windows 7 is the finest Windows variation ever. Windows 7 will after that show you a list of sub-folders for each nation.
1 note
·
View note
Text
How To Remove Software Reporter Tool To Fix Google Chrome High CPU Usage?

Google Chrome is one of the most popular browsers available right now. Since it includes all the necessary features, Chrome users accept the browser’s shortcomings rather than ditch it for browsers with fewer features.
However, one gigantic issue forces users to reevaluate their life choices and uninstall Google Chrome. Users with budget laptops are quite familiar with it — Google Chrome using too much memory.
Why does Google Chrome use so much RAM?
Chrome’s insane amount of CPU usage has been annoying users for years. Even after releasing hundreds of fixes and countermeasures, users still face 100% Disk Usage in Windows 10 because of it.
So, why is Google Chrome a RAM hog? That’s because Chrome considers all your tabs as a separate process. This way, Google can prevent browser takedown from viruses and malware infection by isolating the particular tab or process.
But that’s not the sole reason; a quick peek into the Google Chrome task manager shows evidence that there are other factors at play as well, such as extensions enabled, tabs opened, any third-party tools, etc.
However, the deadliest of all sits right below the Google Chrome process in the Windows 10 Task manager titled” software_reporter_tool.exe.”
What is the Google Chrome Software Reporter Tool?
Software Reporter Tool, part of the Google Chrome Clean-up tool, reports any add-on software that might try to interfere with the browser's working.
To achieve that, the software reporter tool frequently scans the PC for software and files that might be problematic for Google Chrome.
The browser then scans the results to determine if the user needs to be too aware of the software. Based on the results, Chrome then asks users to run the Chrome Cleanup Tool to remove any unwanted software.
Where is it?
The process can be located in the Windows task manager, under the Google Chrome process. Right-click on it and choose “Open File location” to access the source file.
You won’t always find the process in task manager since it’s not always on the go. Alternatively, you can directly find the Google Chrome Software Reporter Tool under the following path in Windows 10 –
C:\Users\<Name>\AppData\Local\Google\Chrome\User Data\SwReporter\VERSION\software_reporter_tool.exe
Problem with software_reporter_tool.exe
Contrary to what some users might think, the software reporter tool is neither malware nor a virus. In fact, the source file located in the hard disk is digitally signed by Google with the file description as the Chrome Cleanup Tool.
However, as we all know, that’s not our only concern. Since the tool frequently scans the system, it has been associated with taking too much PC memory.
Moreover, many users have spotted software_reporter_tool causing slow gaming performance on their PC.
Lastly, many users have privacy concerns over the practice of scanning user’s files without their consent. Cumulate all the concerns, and you will find the right reasons to remove the tool entirely.
How to disable Google Chrome Software Reporter Tool?
Deleting the file or even the folder might seem like a good idea; however, it won’t do much. Google will automatically reintroduce the software in the next update of Google Chrome.
The best way to deal with the Chrome tool is to block the user permissions of the entire folder, stopping Google from accessing the “SwReporter” folder, ultimately restricting it to run the software reporter tool.
Here is how to stop Google from running software_reporter_tool.exe –
Go to the SwReporter folder located the system storage
Right-click on it and choose properties
Go to the Security tab — Click on Advance
Now select the option “Disable inheritance.”
Choose “Remove all inherited permissions from this object” in the new pop-up and hit OK.
If this process doesn’t work, here is an alternative one using the Group Policy Editor in Windows 10 –
Type regedit.exe in Windows Run top open the Registry
Editor Paste the given location on the address bar “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Google\Chrome.”
Right-click on the Chrome key and select New > Dword (32-bit) Value.
Name it “ChromeCleanupReportingEnabled” and keep its value 0
If the exact address is not available, you can find the folder manually and keep on adding values as you proceed.
Should you remove the Software Reporter Tool?
The tool has never been a problem for me. Therefore the decision boils down to your personal preference. If you have singled out Chrome Software Reporter Tool Chrome as the source of your 100% disk usage, then go ahead and remove it. Otherwise, it’s wise to leave it untouched since the tool is actually helpful in removing harmful software. You can manually use the tool by running “Clean up computer” in the Google Chrome “Reset and clean up” settings.
1 note
·
View note
Text
DOWNLOAD IRC 3380 WINDOWS 7 DRIVER
Downloads: 8517 File Version: 412141959 File Format: exe File Name: irc 3380 windows 7 driver Uploader: Lolo Date Added: 11 December, 2019 Price: Free Operating Systems: Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X Download Type: http File Size: 23 Mb

Change log: - Fixed after running Quick Internet Setup, client fails to access the Internet via Windows XP issue. - Fixed iTunes server robustness. - Fixed a bug where replication(irc 3380 windows 7 driver replication) could not be configured if the replication target folder had a multibyte space in its folder name. - Fixes Boot Order variable fail When Plug in too many storage. - Fixed EPU function failed issue. - Fixed the error that even if it was user defined for "M" button to stop or playback, playback was not working as it supposed to. - Fixed the "bcdedit" too long to(irc 3380 windows 7 driver to) execute. - Fixed issue that prevented “Remote Management”(irc 3380 windows 7 driver Management”) from being used when a very long password was set. - Fixed live(irc 3380 windows 7 driver live) view CGI packet error – miss <CRLF> on Date field. - Fixed(irc 3380 windows 7 driver Fixed) the multiple security vulnerabilities. Users content: Day Zero ISV Certifications- AMD Remote Workstation updates. An open dialog will show up to request your agreement to start the BIOS update. Enhance your wave data or create unique sounds with various special effects and editing operations. Note that the IP address may have changed once connected to WiFi. Click "Open". - Click "OK" and click "Next". - Updates Fan curve setting. Device keeps sending syslogs to syslog server after removing the earlier configured syslog server IP address. Hardware MonitoringMonitor temperatures, voltages and fan settings in real time and with zero CPU usage. SPECIFICATIONS:DESIGN: - Color: BlackDISPLAY: - LCD Size: 15.6" - Resolution: 1366 x 768SYSTEM MEMORY: - System Memory: 4GB DDR3 - Max. - You must log into Windows as an Administrator before the installation. 2400MP LAMP DOWNLOAD DELL DRIVER Supported OS: Microsoft Windows 8 (64-bit) Windows 8 Microsoft Windows 8 (32-bit) Windows Server 2012 Windows 7 Windows 10 Windows 8.1/8/7/Vista 64-bit Windows Server 2008 Microsoft Windows 8 Pro (64-bit) Windows 2000 Microsoft Windows 8.1 Enterprise (64-bit) Windows Vista 32-bit Microsoft Windows 10 (64-bit) Windows 7 64-bit Windows Server 2016 Windows Server 2003 64-bit Microsoft Windows 8 Enterprise (64-bit) Microsoft Windows 8.1 Pro (64-bit) Microsoft Windows 8.1 (64-bit) Windows 8.1/8/7/Vista 32-bit Windows 8.1 Windows Vista 64-bit Windows 7 32-bit Microsoft Windows 8.1 (32-bit) Notebook 8.1/8/7 64-bit Windows Server 2012 R2 Notebook 8.1/8/7 32-bit Windows Server 2008 R2 Windows XP 64-bit Microsoft Windows 8.1 Enterprise (32-bit) Microsoft Windows 8 Enterprise (32-bit) Microsoft Windows 10 (32-bit) Microsoft Windows 8.1 Pro (32-bit) Windows Server 2003 32-bit Microsoft Windows 8 Pro (32-bit) Windows XP 32-bit Searches: irc 3380 windows 7 B98b; irc 3380 windows 7 driver for Notebook 8.1/8/7 32-bit; irc 3380 windows 7 driver for Microsoft Windows 8.1 Enterprise (64-bit); irc 3380 windows 7 driver for Windows 10; irc 3380 windows 7 driver for Windows Server 2008 R2; irc 3380 windows 7 Bbw987-bwh; irc 3380 windows 7 B BT987-9; irc 3380 windows 7 driver for Windows 8.1/8/7/Vista 64-bit; irc 3380 driver 7 windows; irc 3380 windows 7 BT9876; irc 3380 windows 7 BTUZM9876 Compatible Devices: Computer Cable Adapters; Monitor; Ipod; Wifi router; Gadget; Laptop To ensure the integrity of your download, please verify the checksum value. MD5: ee279f4cdc9a8e5fed62271d4280483f SHA1: 445f972e5accabe71b293c47f47f2bf48918b80a SHA-256: 93cfcb8bfedd466e7c514b73da585839d04fd5d4090504fdf90bc22ad152f685
1 note
·
View note
Text
In the In-Between
Genevieve Renshaw had her hands deep in the pockets of her jacket and the fists were clearly outlined within, but she stood in front of the door calmly as she waited for Mr. Davidson to open up. The gates were massive and metallic. The president referred the place as a house. The populace undoubtedly would call it a palace. To Renshaw’s straightforward eyes, it uncommonly looked like a fortress. It was built on an eminence that overlooked the city. Its walls were thick and reinforced. Its approaches were covered with surveillance cameras and guards. A swift beep resounded as the gates opened slowly.
A crackling voice could be heard through a speaker.
“Mrs. Renshaw, please come in”, it said. The voice was urgent. She stepped into a small, delicate room with minimal decorations. To her surprise, it was cold. She looked around. The lights were strongly dimmed and she couldn’t make out whether the room even had any windows in it. The room was longitudinal and a unidimensional tube of light that guided the path to a single door. Either way, it didn’t seem to be very welcoming for an entrance hall. Faint steps came to her direction and became louder the closer they got. Milton Davidson approached her with a soft smile on his face.
“Mrs. Renshaw, glad to see you. Your report, of course, arrived before you did and I was just studying it.” His handshake was firm and strong. There was no room for further elation in him. “There’s a problem with the computer.”, said Renshaw.
“So it seems”, he said and scratched his head. “But we still couldn’t quite figure out why.” He was one of the best programmers in the world. He studied programming at the University of Moscow and had been researching new advanced computers with positronic brains for 10 years. He was the owner of the palace and responsible for the computer. “To begin with, no human mind has created those equations directly. We have merely spent decades programming more powerful computers and they have devised and stored the equations, but, of course, we don’t know if they are valid and have meaning. Or what they mean exactly. It depends entirely on how valid and meaningful the programming is in the first place.” He looked at Renshaw as they walked through the corridor. “That’s why I had to call you. You’re the only one that can solve it.”
Davidson held his key against a black screen and the door slid open. “After you.”
They entered a large room that was flooded with a warm light. Row after row of neatly lined up books with their spines facing outward, colour coded with dots, each section arranged in alphabetical order. There was a clean, beautiful chessboard floor and about fifty shelves fanning out from the centre. Six or seven people were busy dusting off the books. It seemed that they haven’t been used in a while.
“A library- how old fashioned”, remarked Renshaw.
“The data-centre is malfunctioning, so we’re trying to solve the problem in a, well, outmoded way”, said Davidson hastily. “I have every confidence”, he said stolidly, “that you already have some ideas as what procedure ought to be followed.”
“I’m not sure”, she said. “I have to see the computer up close. I have studied robotics. That’s not the same thing. I’ve had access merely to text material dealing with Russian robotics. Your material is well in advance of anything else.”
Davidson turned his face towards Renshaw and smirked.
“It is indeed, and we’re proud of it. We put all our research in the past decades into AI. For the last twenty years or so, AI has been focused on the problems surrounding the construction of intelligent agents, systems that perceive and act in a particular environment. In this context, intelligence is related to statistical and economic notions of rationality – that is, colloquially, the ability to make good decisions, plans or interferences. As a result of this recent work, there has been a large degree of integration and cross fertilisation among AI, machine-learning, statistics, control theory, neuroscience and other fields. The establishment of shared theoretical frameworks, combined with the availability of data and processing power, has yielded remarkable successes in various component tasks, such as speech recognition, image classification, autonomous vehicles, machine translation, legged locomotion and question-answering systems.”
Renshaw took a last glance at the shelves as they walked past the last dusty book. They now stood in front of a large double-sided door that opened with a fizz. Behind that door, there was a large enigmatic room with shiny black tiles. Floor and walls were covered in it. The whole ceiling was illuminated with a frail, blueish light. A rather substantial cube resided in the centre. The dark room was like a place out of time, a place to rest without consequence. The darkness in that way was almost like a sanctuary, a place to recharge and forget the things the world said had to be done. There was something in there that was like a promise, like the world before dawn. With each movement they made, their reflection melted with the tiles and it almost took on their form, waiting for making it real. They were standing in front of the computer. The brain that controlled the whole city and its infrastructure.
Davidson guided her towards the main panel and noticed her amazed look on her face. “I know that the world was afraid of AI and how it would evolve, that’s why they stopped researching it- even forbid doing it. But how we connect with the digital world is key to the progress we’ll make in the future.”
Renshaw looked back at Davidson.
“As long as it’s controllable, as a tool”, she said, “it’s authorized for usage. We’re allowed to use AI as a toolkit, AI can augment our existing intelligence to open up advances in every area of science and society- however- it will also bring danger. While primitive forms of artificial intelligence developed so far have been proved very useful, I fear the consequences of creating something that can match or surpass humans.” Renshaw tapped her fingers on the screen anxiously. Davidson looked at her.
“You already surpassed humanity, that’s why you’re here. He took her by the arm and inspected her metal-like skin on it. “You are the result on what the rest of the world has been trying to do. To enhance human cognition through positronic augmentations. You’re the first one of your kind. And you did this because you were afraid that AI, made purely out of equations, will surpass you.” He let go of Renshaw’s arm.
“What you’re doing here is forbidden”, she murmured.
“In here- it isn’t”, he said. “Now let’s take a look at the equations, you and your augmentations are the only one that might understand what’s going on.”
She did not have to go very far in her testing before she called very peremptorily for a transcript of the computer-drawn plans of the positronic brain-paths and the taped instructions that had directed them. Her iron-gray hair was drawn severely back; her cold face, with its strong vertical lines marked off by the horizontal gash of the pale, thin-lipped mouth, turned intensely upon Davidson.
“What is it, Renshaw?”, he asked.
“It makes no sense. The computer checked out negative for all attempts at flaw-finding. Many of the higher functions have been cancelled out by these meaningless directions that the result is very like a human baby.” Davidson looked surprised, and Mrs. Renshaw took on a frozen attitude at once.
“But the heat got turned down, the automatic water system and the infrastructure was paralyzed. It has to be malfunctioning!” Davidson exhaled sharply.
“I am not.” Simple letters appeared on the screen.
The two glared at the screen. Davidson relaxed his tense pose and took a step back from the screen. He exhaled calmly.
“I believe I know what’s happening”, he said. “We wanted to make the computer self-sustaining by feeding it all of humanities data. And it overloaded and stopped working. But now, through your interference, well, it gathered all the rest of the data it needed”, he explained. “It is not only a question-answering machine now. It can do anything.”
“This is wrong.” Renshaw turned around. “We’re supposed to work with technology, go along with it. Use it as a tool. Not let it come that far, let it work for us, not replace us. Machines aren’t human. Will their emotions supposing they have some be mappable, in any sense, onto ours?”
“Programs or machines will acquire emotions in the same way as us humans: as by-products of their structure, of the way in which they are organized not by direct programming“, said Davidson as he glanced upon the ceiling.
“It’s still not the same. It’s not natural. Not human”, Renshaw uttered. “What about a sense of beauty? What about Music? Music is a language of emotions, and until programs have emotions as complex as ours, there is no way a program will write anything beautiful. Not until a machine can write a sonnet or compose a concerto because of thoughts and emotions felt, and not by the chance fall of symbols, could we agree that machine equals brainy that is, not only write it but know that it had written it.”
Renshaw stood before Davidson and crossed her arms. He shook his head.
“A piece of music can have great emotional meaning despite being made of tiny atoms of sound that have no emotional meaning“, he said promptly. ”But a machine is a machine. It doesn’t have to be human. And that’s okay. So who cares about music. We are humans, and we are constantly surpassing our previous ancestors. I think there is no significant difference between how the brain of an earthworm works and how a computer computes. I also believe that evolution implies there can be no qualitative difference between the brain of an earthworm and that of a human. It therefore follows that computers can, in principle, emulate human intelligence, or even better. it” He looked at the grand cube. ”It’s clearly possible for something to acquire higher intelligence than its ancestors: we evolved to be smarter than our ape-like ancestors, and Einstein was smarter than his parents.”
“Intelligence is central to what it means to be human. Everything that civilisation has to offer is a product of human intelligence”, Renshaw countered.
“Emotionally however”, Davidson added to her remark, “we are still apes, with all the behavioural baggage that the issue brings.” He turned his back to her and started walking towards a door in the corner that Renshaw hadn’t noticed. “Come Renshaw, let’s go to the garden, the water is working fine again.”
The glaring light of the garden almost blinded Renshaw’s eyes. The bonsai trees lined the perfect lawn in their wooden boxes. In the centre there was a large pond with flowering lily pads and a wooden bridge that crossed the middle so one could look down at the koi carps. The flower beds were a riot of May colour and even on close inspection they were weed-free.
“Our unique computer; it was suggested that this would result in a collective intelligence that will be enormously more powerful than all present human intelligence combined.” Davidson gazed at the waterfall pouring down the ceiling into the pond.
“I still think we should shut it down. It can be dangerous”, Renshaw said worryingly.
“When we invented fire, we messed up repeatedly, then invented the fire extinguisher. Don’t worry, we’re making sure that wisdom wins.”
“But what if you’re wrong this time?”, she asked again. Davidson sighed.
“Why don’t you ask our new question-answering machine?”, he proposed. “Let’s go back and use it as a tool to our advantage, just like you always wanted to.”
They walked back into the elegant dark room. Davidson patted her on the shoulder. “Alright, here you go, ask away.”
Renshaw shook her head but then took a deep breath.
“What’s the meaning of life?”
A text appeared on the screen again.
“It struck me as an empty and meaningless existence, and that is exactly what it was.“
“This doesn’t make any sense”, said Renshaw. ”However, it is very pessimistic, almost worrying.”
Davidson’s face had a thoughtful expression. He walked to the machine and started checking whether it was actually working properly. “You’re going straight for the big questions, but okay. Why are you so worried about artificial intelligence? Surely we can always pull the plug”, he laughed. ”Ask again.”
“Is there a God?”, she asked.
“There is now”, the computer said and fused the plug.
1 note
·
View note
Text
Android Tricks You Shouldn’t Miss
1. Cast your phone screen to your favorite TV
All you need to share what’s on your phone’s screen with your television is a Chromecast or a television that’s set up to work with Android devices and you can mirror what’s on your screen there. This comes in handy if you want to share pictures or videos on your phone to someone else, watch YouTube without having to use an external app, or even play your favorite mobile games on a larger screen.
Go to the Quick Settings menu and choose Cast. Your device will pop up the Chromecast that’s set up, or the television of your choice (if it’s a smart TV) and you can start casting. It’s very simple, and quick to set up.
You can also check this article to know method to reopen a closed browser window
2. Lock people out of specific apps
We’ve all been there – someone’s asked to use our phone, and we’ve scrambled to hide certain pictures and information we don’t want others to see. There’s actually a way with Android devices to hide this with a few button presses so anyone you lend your phone to for a few moments will only be locked to one area until you enter your phone’s lock screen code. That way, they can’t use parts of your phone unless you put the code in again.
Go to Settings, then Security, and turn on Screen Pinning. When turned on, open the app that your friend or loved one needs to use. Open Overview with the square button below the phone screen. You’ll see an icon that looks like a pin in the lower right corner. Tap it, and it’ll remain pinned to the front. Voila! Now that’s all anyone can use until you enter the password.
3. Enable one-handed mode
Some Android phone sizes can be particularly unwieldy, depending on the model you use. Luckily, you can opt for the special one-handed mode on most Android phones using one quick shortcut. It’s on Google’s keyboard, which you’ll need to get if you don’t have it. You’ll likely have it already as your default option if you use a Pixel or Nexus phone, but if you use a Samsung or LG phone, you’ll need to download the keyboard to get things ready.
When you download the keyboard, open it up and tap and hold the backslash key. Pull up to the right-hand icon to turn on one-handed mode. There will be an arrow here that lets you position the keyboard from side to side and reposition it. The icon on the top will let you restore the keyboard to its full size. Now the keyboard can be used with one hand if you so desire.
4. Change out wireless networks quickly.
Sometimes you may need to swap between wireless networks in an expedient manner. Perhaps you’re on the wrong network at a hotel or you want to use a friend’s signal instead of your hotspot. Instead of going to Settings and then Wi-Fi, simply swipe down twice from the top of your screen and open the Quick Settings menu. Press on the name of the network you’re connected to and you’ll be given an entire list of networks all around you. You can now swap to an eligible network from there.
5. Swap into Priority Mode
You may never have heard of Android’s Priority Mode, but it’s an extremely useful feature. It lets you put your phone in “Do not disturb” mode while still letting certain notifications come through that you select. Essentially, you’ll be able to choose who can bother you while everything else is snoozed.
Start by going to Settings, then Sound & Notification, then Do not disturb. From there, change up the settings and notifications that you still want to let through. You can turn it off and on quickly via Quick Settings, but it will let through important folks, and that’s what makes it so cool.
6. Read through notifications you accidentally closed
It can be easy to flippantly swipe away a notification that you meant to read. It’s simple to bring one back, but your phone doesn’t make it obvious. You can see all of your recent notifications if you’d like, actually. Just tap and hold on an empty part of your home screen. Select the Choose Widgets option, then look for Settings. Drag the icon to a space on your home screen and you’ll see a list pop up. Select Notification Log, and then tap the icon. You’ll now be able to scroll through all of your device’s notifications.
7. Clear your default apps
Sometimes, you’ll open a link that prompts the corresponding app to load, such as YouTube, Facebook, or Twitter, when you meant to load it in the browser. You can clear the default app listing and keep this from happening in a very simple way so you can continue browsing without having to switch out apps when you didn’t mean to in the first place.
Go to Settings, then Apps, and look for the app you want to stop opening up. Find Open By Default when you’ve located it, and choose Clear Defaults. No more pesky app loading!
8. Enable Smart Lock
Keeping your phone secure is always a priority, but when you’re home and lounging around maybe you’re not as interested as locking everything you can. You might want to try out Smart Lock, which takes away the requirement to use a keypad lock when in a trusted area like your house. You can opt to use your face, wireless networks, GPS locations, and more to prevent your phone from locking. This way you don’t have to enter your password each time.
Go to Settings, then Security, then Smart Lock to get it set up, and bask in the light of simple phone usage when in trusted zones.
9. Change independent volume settings
When you go to change the sound on a certain aspect of your device, you’re probably accidentally always turning one part down, but not the one you meant to, right? Maybe you turned down the phone’s volume entirely, but you meant only to adjust your ringtone’s volume.
Instead of relying on your volume buttons, tap the physical volume buttons on your phone, and look for the volume setting to show up on your screen. Look for an arrow on the box, tap it, and check out the volume sliders here to manually adjust the ones you want to change. Now you can do this quickly and easily.
10. Encrypt your phone’s data
It’s always a good idea to keep your data safe, even if you don’t house much private information on your phone. You can actually manually enable encryption on your phone, which will make it unreadable by outside parties without a PIN or password to decrypt it. It’s very simple to turn on: Go to Settings, then Security, then choose the Encrypt Phone option.
It can take a while to enable if your phone wasn’t previously encrypted, and could potentially cause your phone to slow down if you’re running an older version of Android, but it’s an invaluable step to take if you want to protect the things already on your phone.
1 note
·
View note
Text
How To Merge Records In Salesforce
From the album Effluxion, out February 22, 2019 on Merge Information. Due to the track or dimension limitations of some discs or the desire to create a single track when burning a CD, it's possible you'll need to mix multiple CDA tracks into one MP3. CDA tracks are visible when viewing the contents of a CD in Home windows Explorer. These recordsdata include information about the audio tracks but usually are not the precise music tracks. To merge audio tracks into one MP3, you have to first rip or extract the music from disc to exhausting drive, then it's essential to use audio software to merge the recordsdata. Prior to beginning this course of, examine your arduous disk to ensure that you could have enough house for storing and mixing your MP3s. And then there's the price range taxidermy. Ballance is amused, baffled and proud about a little bit of workplace décor that an worker has simply ordered off of eBay: an absurd but hypnotic stuffed coyote head, teeth and tongue bared in menace. It seems like a ridiculous use of label resources — till Ballance shares that she seemed up the eBay listing and "it mentioned it was like $three.fifty four." The most prominent artwork elsewhere in the building is a big collection of Merge-inspired paintings by prolific Brooklyn artist Steve Keene, known for his cowl for Pavement's 1995 album Wowee Zowee, but additionally to younger condominium-dwellers everywhere because the man who prices $30 on-line for five random work.
The Spider Audio 's splitter circuit has yet extra uses. Routing a Remix aux ship output to the splitter enter allows you to create a four-approach parallel results chain (just take every break up of the signal to an impact of your alternative). Using effects in parallel produces a distinct sound to chained effects, permitting every processor to cleanly add its own therapy to the mix, unaffected by the others. The impact outputs will in all probability have to be combined somewhere, so why not use the merging circuit on the identical Spider Audio, if nothing fancy is required? Simply take the final stereo output from each of the four chains and patch them to the inputs of the merge circuit. The merged output can then be routed to the original Remix send's aux return (see screen, right).

1. Click the Sure, this is identical person button to merge the profiles. If the profiles contain totally different information in the same discipline, you will be asked to resolve the conflict. However, it's best to pay attention to the file measurement limit of each audio track, not exceeding 50M. With more out there options, Filesmerge has capability to allow you to set output file in personalized approach. You'll be able to change high quality, encoder, sample price and channel for your destination audio as you please.
replace PS. Thus far, mp3splt works for mp3 and ogg files. I've no success but for m4a files. Merge MP3 does what it claims completely and effectively. Nevertheless, due to the its limitations, it will not be for everyone. Applications comparable to Audacity may also merge MP3s, whereas additionally allowing you to edit, lower and blend them together, though for easy becoming a member of of MP3s, that is a lot simpler to make use of. Tag two records to be merged. To start out out with its mp3 merger operate it's worthwhile to put in it first and launch it. Now on the Audacity's interface hit File; Open and cargo the entire mp3 tracks that you just wish to be a part of together. Combine mp3 recordsdata. The Essex Inexperienced's new album, "Hardly Digital," is out on Friday, June 29, via Merge Info. Buy Now "I actually grieved for years as soon as we stopped participating in," Bell stated. From the album The Suburbs, out now on Merge Records. Mp3splt is a superb instrument for precision audio dicing. It robotically detects cut up points and silent gaps, which is handy for splitting up an album. File names and music tag info could be retrieved from an online database—the CDDB—mechanically. I merge a number of MP3 recordsdata with a tremendous tool named Faasoft MP3 Merger, with which, I can merge many kinds of audio files like MP3, WAV, AAC, FLAC, M4A, and so on. Mp3 Merger Or Mp3 Joiner or http://www.mergemp3.com audio joiner is an online FREE software to merge or join all your Audio files into a single mp3 file for FREE of value.Superchunk's music video for Me and You and Jackie Mitoo," from 2013's glorious I Hate Music is considered one of our favorites showcasing vinyl love. So, while rolling by way of Durham, North Carolina, we checked in with the publicity team at Merge Data to dish about wax. Publicist Christina Rentz and publicity assistant Mike Caulo spent an enormous ol' chunk of time hanging with us, so this dialog has been edited for brevity and readability. It is a very nice solution to merge recordsdata. There is one drawback. The headers of mp3-information are additionally merged.Merge MP3 hỗ trợ cho người dùng tính năng để ghép các tệp tin Mp3 lại với nhau mà không bị giới hạn bởi số lượng, dung lượng hay độ dài của các file Mp3 đó. Do đó bạn có thể thực hiện ghép nhiều file Mp3 lại mà không cần quan tâm tới số lượng hay dung lượng của chúng. Free Merge MP3 4.four.9 is a software program program developed by FreeAudioVideoSoftTech. The primary executable is called The setup bundle generally installs about 5 files and is often about 3.87 MB (4,057,119 bytes). Relative to the overall usage of users who have this installed on their PCs, most are operating Home windows 7 (SP1) and Home windows 10. Whereas about fifty three% of customers of Free Merge MP3 come from the United States, it's also widespread in Germany and Canada.A fast command line utility for merging MP3 info. With this free MP3 cutter + joiner one-stop answer software program, it is helpful to affix collectively multiple audio data into one single file and reduce giant audio information into smaller items. Helps solely MP3 file format. Simply click on the free Free Merge MP3 download button at the prime left of the page. Select Edit>Merge>Selected to merge the chosen records (as in the example above). A beautiful MP3 merging program that allows you to merge, combine or be a part of MP3 information shortly. After releasing quite a few 7″ info and cassettes, the primary Merge Data full-dimension CD launch got here on April 1, 1992 with MRG020 Superchunk - Tossing Seeds , the band's first assortment of singles. Try Mac McCaughan on Amazon Music. Stream ad-free or buy CD's and MP3s now on Amazon.The most highly effective and complete audio editor out there with all of the capabilities that you are looking for combined into one. Trim audio, merge two or extra audio files, mix audio clips, change metadata fields like Art Cowl, Music album name and so on. Convert from one format to another. Merged clips or parts of previously merged clips can't be used to remerge or make a brand new merged clip. Only component clips may be used to create a merged clip. You possibly can click on CHOOSE ALL, when you wish to take all of the master report values as remaining and merge the duplicates.
1 note
·
View note
Text
Most Noticeable Find Large Files Windows
The True Meaning of Find Large Files Windows
There are a couple completely free utilities out there to learn what's eating up the valuable space on your computer. One is a backup, therefore it functions as a mirror. When disk is running low and you want to troubleshoot disk space problems, the very first issue to do is to come across huge files which are consuming disk space. If you've got more than one drive to scan they are sometimes selected on startup by highlighting which ones that you desire. If you wish to search the whole hard disk, open Computer.
It's still true that you need the file but don't necessarily need to get it handy. In reality, it is possible to find out files of any size utilizing the built-in search. For example, you can all files greater than one GB or 2 GB in proportion. You may use them to discover massive files quickly. It could be due to log and temporary files made by system and user program. Navigate to the drive or folder in which you wish to seek out large files. Since you can observe this will be a really massive file on your drive, but shouldn't be deleted. The very first system to discover huge files is with File Explorer. With this system, it's still impossible to instantly observe the largest files on the whole computer, just the largest by folder. Cleaning junk files from the computer every once in a while is a superb practice and there are a number of free and strong tools out there for the purpose that we've already discussed previously.
The Pain of Find Large Files Windows
In case the capacity of your hard disk is running low, it is the right time to clean off some files. Since the extent of a difficult drive is restricted, the drive has to be maintained from time to time in order to stop low disk space issue on the computer. Just because it may be taking up lots of space, you ought to check first that it is not part of the system that could give rise to a problem if you remove something which's needed for running Windows. You will likely be pleasantly surprised by exactly how much space you may become back, and after that it's possible to go and fill it up with stuff that you truly want and use. You're able to scan and visualize your disk space utilizing the free model of TreeSize free of issue. Windows 10 has a storage usage tool which may assist you in some circumstances.
So far as the features are involved, there's a truckload of those. These apps look very beautiful and it's simple to work with them as they open in full-screen mode at which you can utilize every inch of your screen. Tap on the particular app, which you would like to remove. You may also uninstall many apps by abiding by the exact same course of action. These apps are extremely ingenious to install in your system, you just need to open Store, locate your app and click install. There are apps you may download that may remove a number of programs in 1 go.
If you don't understand what the extension of your file is, you can discover a listing of most extensions and the associated program on the MS-DOS extensions page. You will observe that find large files windows Explorer provides you several pre-defined alternatives. There are some additional helpful options in Advanced such as finding duplicate files and an in depth reporting process is available that may export the data to numerous formats. An invalid switch is provided.
So far as the file management operations are involved, there's a good deal of those. In an earlier screenshot, you might have noticed that you are able to manage system restore files. This program is faster than every other kind of program in the identical category and enables users to spot massive files from a mile away. The program allows you to set the amount of items which you wish to get displayed, so you can better control success. The tool utility program offers information regarding the range of files of distinct types, grouped by the extensions of current files.
You may find out more about it using its built-in assistance. What's quite good is the various ways in which you may visually see the info. You should be aware that this search may take from a few seconds to many minutes, based on your computer's performance, number of files and other apps that may be running in an identical moment. You'll begin obtaining a list, but it is not sorted yet because you can see above. You can look for lots of large file types.
youtube
1 note
·
View note