#what is CSMA
Explore tagged Tumblr posts
Text

Theoretical Foundations to Nobel Glory: John Hopfield’s AI Impact
The story of John Hopfield’s contributions to artificial intelligence is a remarkable journey from theoretical insights to practical applications, culminating in the prestigious Nobel Prize in Physics. His work laid the groundwork for the modern AI revolution, and today’s advanced capabilities are a testament to the power of his foundational ideas.
In the early 1980s, Hopfield’s theoretical research introduced the concept of neural networks with associative memory, a paradigm-shifting idea. His 1982 paper presented the Hopfield network, a novel neural network architecture, which could store and recall patterns, mimicking the brain’s memory and pattern recognition abilities. This energy-based model was a significant departure from existing theories, providing a new direction for AI research.A year later, at the 1983 Meeting of the American Institute of Physics, Hopfield shared his vision. This talk played a pivotal role in disseminating his ideas, explaining how neural networks could revolutionize computing. He described the Hopfield network’s unique capabilities, igniting interest and inspiring future research.
Over the subsequent decades, Hopfield’s theoretical framework blossomed into a full-fledged AI revolution. Researchers built upon his concepts, leading to remarkable advancements. Deep learning architectures, such as Convolutional Neural Networks and Recurrent Neural Networks, emerged, enabling breakthroughs in image and speech recognition, natural language processing, and more.
The evolution of Hopfield’s ideas has resulted in today’s AI capabilities, which are nothing short of extraordinary. Computer vision systems can interpret complex visual data, natural language models generate human-like text, and AI-powered robots perform intricate tasks. Pattern recognition, a core concept from Hopfield’s work, is now applied in facial recognition, autonomous vehicles, and data analysis.
The Nobel Prize in Physics 2024 honored Hopfield’s pioneering contributions, recognizing the transformative impact of his ideas on society. This award celebrated the journey from theoretical neural networks to the practical applications that have revolutionized industries and daily life. It underscored the importance of foundational research in driving technological advancements.
Today, AI continues to evolve, with ongoing research pushing the boundaries of what’s possible. Explainable AI, quantum machine learning, and brain-computer interfaces are just a few areas of exploration. These advancements build upon the strong foundation laid by pioneers like Hopfield, leading to more sophisticated and beneficial AI technologies.
John J. Hopfield: Collective Properties of Neuronal Networks (Xerox Palo Alto Research Center, 1983)
youtube
Hopfield Networks (Artem Kirsanov, July 2024)
youtube
Boltzman machine (Artem Kirsanov, August 2024)
youtube
Dimitry Krotov: Modern Hopfield Networks for Novel Transformer Architectures (Harvard CSMA, New Technologies in Mathematics Seminar, May 2023)
youtube
Dr. Thomas Dietterich: The Future of Machine Learning, Deep Learning and Computer Vision (Craig Smith, Eye on A.I., October 2024)
youtube
Friday, October 11, 2024
#neural networks#hopfield networks#nobel prize#ai evolution#talk#ai assisted writing#machine art#Youtube#presentation#interview
2 notes
·
View notes
Text
ESIC Strengthens Healthcare Access for Pensioners Through Hospital Tie-ups
📅 Notification Date: 11th June 2025 📌 Issued By: Employees’ State Insurance Corporation (ESIC)
The Employees’ State Insurance Corporation (ESIC) has taken a significant step to enhance the quality and reach of medical care for its pensioner community. In a notification dated 11th June 2025, ESIC has directed all Regional Directors to facilitate tie-up arrangements with premier healthcare institutions including AIIMS, CGHS, CSMA, and other State Government-approved private hospitals.

This initiative is aligned with the broader goal of providing cashless, accessible, and comprehensive healthcare to beneficiaries under the ESIC Pensioners’ Medical Scheme (ESIC-PMS), particularly ensuring availability of tertiary care.
🩺 Key Highlights of the Circular:
Tie-Up with Recognized Hospitals: Regional Directors are required to establish partnerships with AIIMS, CGHS, CSMA-affiliated hospitals, and approved private medical institutions within their jurisdiction.
Comprehensive & Cashless Treatment: Eligible pensioners will receive cashless treatment based on their entitlement, ensuring seamless access to primary, secondary, and tertiary medical services.
Standardized Terms: The terms and conditions for these tie-ups will follow the existing CGHS (Central Government Health Scheme) model, ensuring uniformity and quality in service delivery.
🧓 What This Means for ESIC Pensioners:
The directive aims to remove healthcare access barriers faced by retired ESIC employees. With dedicated tie-ups, pensioners can now expect:
Shorter wait times for treatment
Access to multi-specialty care without financial stress
Standardized quality of healthcare, irrespective of geography
Reduction in paperwork through integrated claim systems
This move by ESIC not only improves healthcare outcomes but also reflects a growing recognition of the need for dignified and equitable post-retirement medical support.
💬 Expert Insight from Sankhla Corporate Services Pvt. Ltd.
At Sankhla Corporate Services Pvt. Ltd., we recognize the importance of such progressive steps by statutory bodies. As specialists in ESIC compliance and advisory services, we assist employers and employees — including retirees — in accessing the full spectrum of ESIC benefits with ease.
Whether it’s registration, contribution management, claim support, or ESIC-PMS facilitation, our experts are here to guide you every step of the way.
📞 Need Help Navigating ESIC Services?
Reach out to Sankhla Corporate Services Pvt. Ltd. for ESIC compliance, employee benefits management, and hassle-free support under the latest ESIC-PMS updates.
📧 Email: [email protected] 🌐 Website: www.sankhlaco.com 📍 Serving clients across India
ESIC-PMS hospital tie-up 2025
ESIC pensioner medical scheme
Cashless healthcare for ESIC retirees
ESIC compliance consultants
AIIMS ESIC tie-up
CGHS hospital ESIC partnership
ESIC tertiary care hospital list
Sankhla Corporate Services ESIC support
Let me know if you’d like this content as a newsletter, carousel post, or client advisory note.
0 notes
Text
Ve489 Computer Networks Homework Set 4
Answer following questions about random access protocols: What is the vulnerable period for Aloha? How about slotted Aloha? Explain it. What is vulnerable period of CSMA? How can we make sure the performance of CSMA is better than Aloha? Why collision detection (CD) can improve performance of CSMA? Considering the CSMA/CA based DCF in IEEE 802.11, answer the following questions: What is…
0 notes
Text
Telecommunication protocols application interaction
Let's look at the basics of transferring information between two application processes in the OSI model.
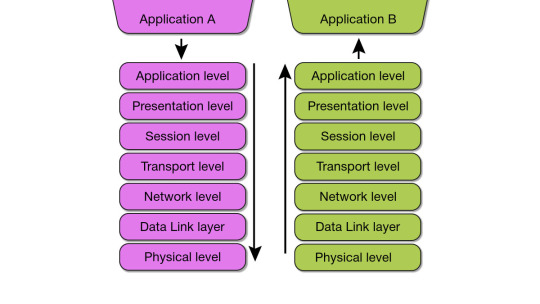
Say an application (in the picture above) needs to access a file service on another computer. It sends a request to the application layer. Based on it, the software generates a standard format message consisting of a data field and a service header. The latter contains a description of actions for the application layer of the other machine to perform, as well as instructions for the adjacent lower layer. The presentation layer, in turn, formats the data according to the instructions received and adds its own header (some protocol implementations also include service data at the end of the message), after which the information is sent to the session layer. This procedure, called encapsulation, is repeated further as data and service information move to the physical layer.
When arriving at the physical layer, i.e., the network, data passes through many other devices (network adapters, hubs, routers, bridges, etc.) and, upon reaching the destination (for example, a SIP phone), undergoes a reverse encapsulation process (right side of the picture).
Data networks can be of two types: local (local area network, LAN) and global (wide area network, WAN). The latter connects any two networks within the globe with dedicated or switched communication channels. Local networks differ in transmission medium, topology, and access control. Depending on the transmission medium, they are divided into wired (using coaxial, twisted pair, or fiber-optic cable) and wireless (WLAN), and according to the type of topology, into networks with 'bus', 'ring', or 'star' topologies.
Each computer on the local network is connected to the transmission medium through a special adapter that "sees" what any other adapter on the same network is transmitting; such systems are called broadcasts.
The MAC protocol regulates the sequence of nodes' access to the transmission medium. It is implemented using two types of schemes: polling or contention-based MAC schemes.
MAC polling networks can be centralized or distributed. Centralized ones have a star topology with a hub as the control node. In contrast, distributed ones have a ring or bus topology with token passing. Contention-based MACs are often implemented as carrier sense multiple access with collision detection (CSMA/CD) or carrier sense multiple access with collision avoidance (CSMA/CA). The first is used in all types of Ethernet LANs, and the second is used in most wireless WLANs.
The unrivaled leader among local networks is the IEEE 802.3 Ethernet network, where coaxial, twisted pair (designated by the letter T for 'twisted') and fiber-optic cables are used as transmission media. The transition to twisted-pair cable made it possible to implement full-duplex transmission over two twisted pairs, leaving the concept of collision meaningless since transmission and reception became independent operations. Ethernet has transmission speeds of 10, 100 ('Fast Ethernet'), 1000 Mbit/s (1 Gbit/s, 'Gigabit Ethernet'), and up to 400 Gigabit Ethernet.
Wireless local networks (wireless LAN, WLAN) have also become widespread. Their parameters are stated in the IEEE 802.11 specifications, known as Wi-Fi.
Today, the most common Wi-Fi 5 or 802.11ac defines the operation of wireless local area networks in the 2.4/5 GHz ranges with a data transfer rate of 1.3 Gbit/s. Shortly, speeds will reach 9.6 Gbit/s over 6 GHz frequency bands.
The range of most WLAN systems is 120 m, depending on the number and type of obstacles encountered. Additional access points will help expand the coverage area. Using two or three carrier frequencies instead of one can increase the number of users and network capacity.
Obviously, with Wi-Fi, network security becomes an important issue. A priori, wireless networks must be equipped with additional means of ensuring reliability compared to wired ones. WLAN uses direct sequence spread spectrum (DSSS) technology, which is highly resistant to data corruption and interference, including intentional ones. The problem of user authentication can be solved by introducing system identifiers. The wired equivalent privacy (WEP) mode is provided to transmit necessary information. In this case, the signal is encrypted with an additional algorithm, and the data is controlled using an electronic key.
Like all IEEE 802.3 standards, 802.11 refers to the lower two layers of the OSI model: physical and link. Any network application, operating system, or protocol (such as TCP/IP) will function equally well on an 802.11 network or Ethernet one.
The original 802.11 standard defines the basic architecture - the features of 802.11 services. The 802.11x specification only addresses the physical layer, introducing higher access speeds.
In conclusion, we should note that thanks to the close ties between Ethernet and the IP protocol, the scope of Ethernet applications is expanding, particularly in broadband subscriber access (BSA) networks.
0 notes
Text
What is cybersecurity mesh architecture (CSMA)?
http://securitytc.com/T6LdRm
0 notes
Text
Cyber Security Maturity Assessment: Everything You Need to Know
In today's digital age, where data is the lifeblood of any organization, protecting it from cyber threats is paramount. That's where cyber security maturity assessment (CSMA) comes in. It's like an X-ray for your cyber defenses, revealing strengths, weaknesses, and areas for improvement to build a robust cybersecurity posture.
youtube
What Is a Cyber Security Maturity Assessment?
A CSMA is a systematic evaluation of an organization's cybersecurity program against a set of established criteria or benchmarks. It helps you understand your current security posture, identify potential vulnerabilities, and prioritize investments to mitigate risks. Think of it as a roadmap to strengthen your digital defenses against ever-evolving cyber threats.
What Does a Cyber Security Maturity Assessment Cover?
A comprehensive CSMA typically assesses five key domains:
Security Risk Management: How effectively you identify, assess, and prioritize cybersecurity risks.
Threat Intelligence and Collaboration: Your ability to gather and share threat intelligence and collaborate with partners.
Cybersecurity Controls: The adequacy and effectiveness of your security controls (firewalls, intrusion detection systems, etc.).
External Dependency Management: How you manage security risks associated with third-party vendors and partners.
Cyber Incident Management and Resilience: Your plan for responding to and recovering from cyber incidents.
The Final Say:
Therefore, investing in a cyber security maturity assessment is an investment in your organization's future. By proactively assessing and strengthening your cybersecurity posture, you can safeguard your valuable data, minimize disruptions, and build a resilient infrastructure that can withstand the ever-changing cyber threat landscape.
The best you can do is to get in touch with a reliable provider who can offer you the most updated software solution. With this, you not only mitigate the digital risks but will also stay informed about the latest updates.
Don't wait! It's high time you need to take action. Book a demo the expert to discover more.
0 notes
Text
Why Is WiGig Better than Wi-Fi and Wi-Fi 6?
We can hardly picture our life in the present without Wi-Fi access. Although our want for data has grown dramatically, you can vividly recall the summer you probably had a blast on a 2Mbps connection.

Higher throughput is required for many reasons than merely supporting 4K streaming and large file downloads. Our Wi-Fi encounters difficulties, which are caused by many client devices.
Therefore, WiGig demand will grow significantly in the coming years. This is owing to the growing need for fast internet, acceptance of the BYOD policy, and surging portable consumer devices sales.
Which is better, Wi-Fi 6 or WiGig?
After covering both of the new Wi-Fi network standards, let's examine what makes them unique from one another. These two technologies support our quest for wireless multi-gigabit speeds. Finally, we can experience flawless 4K streaming of video and quick downloads of large files.
The main distinction between both networks is that. In contrast, low-frequency waves may pass through walls and objects. WiGig travels comparatively shorter distances but attenuates more quickly when obstructed by them.
We can expect the usage of 802.11ay as the network backbone to substitute the fibre network installed outside the homes or for peer-to-peer communication, being aware of the benefits and drawbacks of each of these technologies. On the other hand, the Wi-Fi 6 or 802.11ax may be utilized for Wi-Fi transmission inside houses where the signal has to be given to numerous devices bypassing.
How WiGig Differ from Wi-Fi?
• More than One Access Techniques –
In today's Wi-Fi, a multiple access technique known as CSMA is prevalent. A gadget prepared to broadcast in CSMA first conducts channel detecting and switches off if it discovers that the channel is already occupied. By distributing channel access control across devices, CSMA prevents collisions.
When two devices broadcast to the exact same receiver at the same time, a collision occurs. But with WiGig, CSMA has a "deafness" issue since directed broadcast and receive beams are used.
• Coverage and Range –
WiGig is intended for 60 GHz frequency, whereas Wi-Fi operates on 2.4 GHz and 5 GHz. The WiGig transmission attenuates 100 times more than the Wi-Fi at a given distance because radio-signal reduction is related to the square of the frequency.
WiGig uses focused signal beams on both the receive and transmit sides to combat attenuation. The range of WiGig is still approximately 30 feet even then.
• Interference –
The temptation may be significant to claim that WiGig is the quickest Wi-Fi. However, although WiGig can support a high data throughput of 7 Gbps, 11ax can provide a maximum data rate of 9.6 Gbps.
The actual data rates are frequently lower than the theoretical limit. More significantly, at 60 GHz, WiGig could see a cleaner RF environment. WiGig won't interfere in areas that are divided by walls.
• Multiple-Antenna Transmit –
For "spatial multiplexing," Wi-Fi currently employs a multiple-antenna technology called MIMO. Increasing bandwidth over the wireless network is the goal. Because of reflections from the environment, radio waves travel from the transmitter to the receiver through many pathways.
This is known as "multipath." By using signal processing to establish several wireless transmission streams between the receiver and transmitter, referred to as "spatial streams," MIMO takes advantage of multipath.
0 notes
Text
A primer on MESH networks and MESH cyber security - CyberTalk
New Post has been published on https://thedigitalinsider.com/a-primer-on-mesh-networks-and-mesh-cyber-security-cybertalk/
A primer on MESH networks and MESH cyber security - CyberTalk


Gergana Kungalova is a Security Engineer for Check Point in Bulgaria. She started her journey in the Cyber Security field as Network Security Support Engineer, working with customers across the globe. In her current role, she is connecting people and processes with technology by matching the clients’ business needs with security solutions and services.
In this amazing expert interview, Gergana Kungalova explains why MESH networks can be more advantageous than traditional networks, she addresses common misperceptions around MESH, and then highlights MESH-specific cyber security measures. Don’t miss this!
What is the core idea behind MESH networks?
The MESH network provides ultimate connectivity between nodes like users, servers/applications, and network components. The main driver for this architecture is to provide reliable access that is not dependent on a single device or route.
Why might an organization choose to have a MESH network over traditional network architecture?
The traditional network architecture was suitable for organizations when they had well-defined perimeters and point-to-point connections. All services were hosted within the data centers and users were working strictly from the office. Nowadays, the demand for mobility and scalability has completely changed the picture. We have services that are hosted in the cloud and/or in the data center. At the same time, our users are roaming and should access these services from everywhere. The new connectivity requirements have increased the complexity of managing networks and security to an extreme degree. Many organizations are choosing the MESH networks as an enabler for flexible and scalable infrastructure. It allows them to reduce the management overhead and cut costs.
What are some common misperceptions about MESH that we should debunk for readers, if any?
The most common misperception is that the MESH networks are more secure. They are more agile and resilient, but they introduce new dynamics in the monitoring and the maintenance which may pose risk of security breach. The nature of MESH networks may increase the amount of time required for identifying breaches, determining which nodes have been affected and what the business impact looks like. Also, the root cause analysis is more complex and time consuming.
It is critical to implement cyber security measures at every point of the infrastructure, in the early stages. The security must be multi-layered and part of the planning phase. A cyber security platform that is consolidated and focused on prevention is the best approach to ensure business continuity within organizations with MESH networks.
Examples of typical cyber security threats seen on MESH networks?
The cyber security threats seen on MESH networks are the same as the threats seen on the traditional networks – vulnerability exploits, phishing attacks, account takeover…etc. The only difference is how they are executed.
How does the decentralized nature of MESH networks impact the design and implementation of robust cyber security measures?
The dynamic nature of MESH networks requires multi-layered enforcement of cyber security. The best-of-breed method is bringing more complexity then benefits – multiple management consoles, no full visibility on security posture, lack of expertise…etc. To address these challenges, we should talk about the concept of Cyber Security Mesh Architecture (CSMA)*.
The CSMA approach focuses on platform security that is collaborative across all components in the customer’s environment and it’s built on the following pillars: Security Analytics and Intelligence, Distributed Identity Fabric, Consolidated Privacy and Posture Management, and Consolidated Dashboards. It means that all security components talk with each other, share intelligence and have one single pane of glass for management. The efficient implementation of CSMA has to be enforced based on user identity and zero trust principals, not on network-based access.
*“CSMA is a concept developed by Gartner to help companies move past siloed security to a more collaborative and flexible approach to security. CSMA is designed to make security more composable and scalable by modularizing security functions and enabling them to interoperate through a set of supportive layers. By making security more cohesive and collaborative, CSMA enables an organization to achieve better security with fewer resources.” — Quoted from Check Point’s What is Cybersecurity Mesh Architecture (CSMA)?
Given the potential for node compromise in MESH networks, what strategies can be employed to enhance the security posture of individual nodes, as to prevent cascading security issues across the network?
In case of compromise, the time spent for identification and mitigation is what really matters, as does determining how big the impact on the business will be. The prevention first methodology has to be incorporated into the cyber security strategy. From my experience, it does not matter as to how many security measures are in place – they have to be configured in prevention mode in order to block the attack. Of course, to cover all possible threat vectors, we should have in place strong encryption, zero-day prevention, anti-phishing, anti-ransomware, vulnerability, and patch management.
What other kinds of tools or technologies can cyber leaders use to monitor for suspicious activities within a MESH network?
Cyber leaders can benefit from integrated AI engines:
AI integrated within the prevention engines can reduce the time for mitigation, improve catch rate and discover attacks chains in next to no time.
AI integrated in the monitoring can improve behavior analysis and discover anomalies, provide sophisticated reports, and reduce the time for root cause analysis.
An example of a technology that combines both is MDR/MPR (Managed Detection/Prevention and Respond). It can provide a deeper overview of what is going on in the environment and help to further decrease the reaction time. Basically, it’s providing automation and optimization for how the SOC teams are working with data and dangerous threats.
Is there anything else that you would like to share with the Cyber Talk CxO audience?
Cyber security requires a continuous process of risk management and effectiveness optimization. Building robust architecture requires approach that is collaborative, redistributed within all parts of the environment and focused on prevention.
Stay (cyber) safe 🙂
#account takeover#agile#ai#AI engines#amazing#Analysis#Analytics#applications#approach#architecture#automation#Behavior#breach#Building#Bulgaria#Business#business continuity#Check Point#Cloud#collaborative#Companies#complexity#connectivity#consolidated#continuous#course#csma#CXO#cyber#cyber security
1 note
·
View note
Note
Hii i like your blog a lot bcs ive been getting started on a comp sci bachelor and i understand most of the stuff youre talking about also youre cool.
Anyway have you heard of csma/cd? Like the network protocol? Funniest shit i had all semester. The fact that it's actually pretty usableis even funnier. Pretty sure thats what wed use in an anarchist society.
Have a good day!
ha im glad, thanks! i hadnt heard of it before!
The collision recovery procedure can be likened to what happens at a dinner party, where all the guests talk to each other through a common medium (the air). Before speaking, each guest politely waits for the current speaker to finish. If two guests start speaking at the same time, both stop and wait for short, random periods of time (in Ethernet, this time is measured in microseconds). The hope is that by each choosing a random period of time, both guests will not choose the same time to try to speak again, thus avoiding another collision.
what a mess! (imagining the equivalent of the little hallway dance where the same two collide and restart repeatedly)
7 notes
·
View notes
Text
Ethernet
What is Ethernet?
Definition: Ethernet (pronounced “eether net”) is a computer network technology which is used in different area networks like LAN, MAN, WAN. Ethernet connecting computers together with cable so the computers can share information. Within each main branch of the network, “Ethernet” can connect up to 1,024 personal computers and workstations.
Ethernet provides services on the Physical (Layers 1) and Data Link Layer (Layers 2) of OSI reference model.The Data Link Layer is further divided into two sublayers that are Logical Link Control (LLC) and Media Access Control (MAC),these sublayers can be used to establish the transmission paths and format data before transmiting on the same network segment.
Read More
Systems that use ethernet communication divide their data into packets, which are also known as frames. These frames further contain source and destination address, a mechanism which was used to detect errors in the data and retransmission requests.
History of Ethernet
Ethernet was developed over several years in the early 1970s by group researchers within the company Xerox Palo Alto Research Center (Xerox PARC) including, in particular, Robert Metcalfe (who founded later 3Com company). The goal the research project was to connect networked computers and laser printers. Xerox Corporation filed a patent on this technology late 1977. In 1979, companies Digital Equipment Corporation (DEC), Intel and Xerox combined to improve Ethernet and together published the first standard in 1980: Ethernet Blue Book sometimes called TEN (after the initials of the three companies). Finally, the IEEE this technology became standard in 1983: 802.3 was born … well before the 802.11! A little abuse of language, it is called Ethernet 802.3 standard. The format of DIX Ethernet packets is slightly different from the 802.3 Ethernet packets, but the two can coexist on the same network. The invention of single-chip Ethernet controllers has made Ethernet cards very cheap, and many modern PCs have it built-in on the MOTHERBOARD.
Read More
Wired Ethernet
Initially, ethernet can be designed to run over coaxial cables, twisted pair cables,fiber optic cable.
Wired Ethernet network, devices are connected with the help of a fiber optic cable which connects the devices within a distance of 10km. For this, we have to install a computer network interface card (NIC) in each computer. A unique address is given to each computer that is connected. So, for sharing data and resources like printers, computers, and other machines, Ethernet networking is used as it establishes a communication system.
Ethernet is a shared medium network technology, where all the workstations are connected to the same cable and must connect with one another to send signals over it. The algorithm used to resolve collisions — that is, when two workstations try to speak at the same time — is called CSMA/CD, and works by forcing both workstations to back off for random (and hence probably different) intervals before trying again.
Advantages of using wired Ethernet network
•It is very reliable.
• Ethernet network makes use of firewalls for the security of the data.
Data is transmitted and received at very high speed.
Read More
• It is very easy to use the wired network.
Disadvantages of using wired Ethernet network
• The wired Ethernet network is used only for short distances.
• The mobility is limited.
• Its maintenance is difficult.
• Ethernet cables, hubs, switches, routers increase the cost of installation.
Wireless Ethernet
In this, wireless NICs are used for connecting the computer instead of a cable and these wireless NICs make use of radio waves for communicating between the systems and furthers these NICs are connected with a wireless switch or hub. This technology requires maintenance, but it is more easy to use.
Wired Ethernet network, devices are connected with the help of a fiber optic cable which connects the devices within a distance of 10km. For this, we have to install a computer network interface card (NIC) in each computer. A unique address is given to each computer that is connected. So, for sharing data and resources like printers, computers, and other machines, Ethernet networking is used as it establishes a communication system. Ethernet is a shared medium network technology, where all the workstations are connected to the same cable and must connect with one another to send signals over it. The algorithm used to resolve collisions — that is, when two workstations try to speak at the same time — is called CSMA/CD, and works by forcing both workstations to back off for random (and hence probably different) intervals before trying again.
Read More
Wireless Ethernet
In this, wireless NICs are used for connecting the computer instead of a cable and these wireless NICs make use of radio waves for communicating between the systems and furthers these NICs are connected with a wireless switch or hub. This technology requires maintenance, but it is more easy to use.
2 notes
·
View notes
Text
Types and Benefits of Ethernet Cables to Understand
Recollect going to digital bistros and work environments to utilize the web? Presently everybody has that work environment at home itself. There is no question the way that the web has turned into a substantial piece of everybody's lives now. With the developing reliance on web-based administrations, the requirement for the web is expanding consistently.
This is the reason a large portion of us slobber over the WiFi for its advantages. With public WiFi administrations, one can interface with the web from anyplace and with any gadget. However at that point, there are security issues as well. In the event that anybody can utilize it, then anybody can hack it as well, correct? Simply relax. We have an answer for you-Ethernet links.
These days, we can convey the web any place we go. Be that as it may, the disappointment of buffering is a genuine issue to fix as we as a whole become annoyed when the web dials back. What the vast majority don't understand is that they can utilize the ethernet link to take care of this issue.
Indeed, with an ethernet link, one can utilize a quick web association any place they go. In this article, we will reveal some insight into its unimaginable advantages. In any case, before we move to the advantages, let us have a short prologue to ethernet links, its qualities, and its sorts:
What is an Ethernet Link?
Imagined by: Robert Metcalfe
Normalized as: IEEE 802.3
The ethernet link interfaces the hole between your PC and your web association. They are additionally famously known as organization links. It will rapidly interface the wires of your PC to a switch or a modem. The ethernet link will speed up without any problem. Today, a great many individuals depend on ethernet links as they accelerate their work and assist them with achieving their undertakings on time.
Qualities of Ethernet
Ethernet gives connectionless correspondence.
It is based on a star geography.
Ethernet works by means of the connection layer in TCP/IP model engineering.
Prior to moving any information to the organization, the ethernet framework checks in the event that the entrance medium is allowed to move information or not. It decides free medium via Transporter Sense Numerous Entrance/Crash Identification (CSMA/Disc).
Kinds of Ethernet
According to the link utilized for associating the frameworks over the organization, the ethernet association is of two kinds:
Fiber Optic ethernet association
Bent Pair ethernet association
There are three classifications of ethernet-in view of the information move speed:
Fundamental ethernet-slowest among all and gives the speed of 10Mbps
Quick ethernet-moderate among fundamental and Gigabit organization and gives the speed of 100Mbps
Gigabit ethernet: gives the most elevated information move speed of 1Gbps. This is multiple times quicker than Quick ethernet. It has expanded to 100 Gbps.
Advantages of the Ethernet links:
Speed
Assuming you check for your most extreme Wireless association speed, you will find 866.7 Mb/s. For greatest individuals, this speed is sufficient to finish their everyday web errands on time. While ethernet association gives 10 Gb/s. Furthermore, only for the data, this huge speed is enough for a whole structure. Thus, when you get your hands on the ethernet link, you don't have to stress over your web speed.
Security
The worldwide reliance on the web builds consistently; hence, security strikes here as a central issue for everybody. There are chances of WiFi getting hacked effectively as it is openly accessible. Regardless of how secure the framework you interface with is, there are dependably risks that anybody could undoubtedly hack into your gadget. These assaults are impractical to do remotely by means of an ethernet organization, on the grounds that for that an aggressor would require actual admittance to do as such. In this manner, ethernet links are safer and dependable than WiFi.
Invariance: On the off chance that you have a wired association, you can handle and interface with your organization on your gadget. This is on the grounds that the switch interfaces just a solitary individual with a gadget in it.
Inactivity
This is the course of contortion brought about by the ever changing going of the signs from your gadget to the switch. The Wireless associations can have astoundingly high inertness. In any case, the idleness turns out to be a lot of lower when you pick the cat5e link. Here, with an ethernet connector, you can in any case utilize the greatest accessible data transfer capacity at whatever point you require fast web. Different organizations use ethernet links to boost their efficiency.
Energy-Effective
Congrats! Associations laid out through the ethernet links won't negatively affect your month to month expenses and are energy effective. Indeed, even the ethernet connector consumes less energy and works for an extensive stretch. Furthermore, such links and gadgets benefit the climate over the long haul. Along these lines, you are helping nature and yourself both.
Main concern
An ethernet connector gives total true serenity as you can undoubtedly avoid a few web issues over the long haul. Individuals who use WiFi can change the switch consistently and change its speed and areas to get the signs. Adjusting cat5e link will permit you to appreciate HD gushing with practically no server issues. What's more, when you have a non-support series meeting and continuous work gatherings, your day would probably be great and non-baffling.
For More Information :-
Ethernet Server Adapter For Sale
Router Switches For Sale
0 notes
Text
Free http sniffer 1.1

Free http sniffer 1.1 software#
Free http sniffer 1.1 mac#
Free http sniffer 1.1 windows#
The raw packets in the radio waves without ever having to attach to a WAP. In monitor mode, the wireless network card listens to Operating System) the attacker may be able to use what is known as monitor mode If the attacker is using Linux (or another Unix like Will have to be attached to the wireless networks WAP (Wireless Access Point) toīe able to see anything. If the sniffer's card does support promiscuous mode it
Free http sniffer 1.1 windows#
Wired network card in Windows and Linux (or other Unix like Operating System),īut not all wireless cards support it properly (like Intel's Centrino 802.11gĬhipset know as IPW2200). Promiscuous mode works on pretty much any Of the computer running the sniffer to see the data traveling to other computersĪttached to the same access point. Traffic going to other computers and will instead look at it, allowing the user Network card is put into what is known as promiscuous mode, it will not ignore Reality it's a little more complicated than that, but I want this to be anĪrticle and not a book on the intricacies of 802.11 networks) However, if a Traffic destined to others but normally they just choose to ignore it. Wireless LANs actĪ lot like Ethernet LANs using hubs. The above is about Ethernet networks, WiFi Mirroring traffic to all ports or by a technique know as ARP poisoning (more on Sniffed using the mirrored port on some switches (put there so administratorsĬan use a Sniffer to diagnose network problems), by confusing the switch into
Free http sniffer 1.1 mac#
On the LAN) and packets addresses to its MAC along with the occasional stray Switched network a node can only see broadcast messages (meant for all computers Number of collisions on the network, increasing throughput. Packets only to the nodes they are intended for. A switch on the other hand looks at the MACĪddress of the nodes hooked to it and what ports they are on then tries to send On a network, a hub is a passive device that sends all traffic it Possibility of sniffing data that does not belong to a node, most networks use To cut down on the number of collisions and the Is put into what is known as "promiscuous mode" it will look at all of the The packets that are destined for its MAC address. To send packets of information to each other. Network have their own unique MAC (media access control) address that they use Words in during a lull in everybody else's conversation. Think of CSMA/CD as being like a conversation atĪ loud party, you may have to wait for quite a spell for your chance to get your Sending data using a scheme known as carrier sense multiple access withĬollision detection (CSMA/CD). All of the nodes (computers and otherĭevices) on the network could communicate over the same wires and take turns Most Ethernet networks use to be of a common bus topology, using eitherĬoax cable or twisted pair wire and a hub. Unix like operating system like Linux or FreeBSD-) and its Windows versionįirst an explanation of some network basics is in Sniffer (commercial), Wireshark (previously know as Ethereal, an Open Source GUI Sniffer for Linux, WindowsĪnd other platforms), TCPDump (Open Source command line Sniffer for *nix - any A few popular general purpose Sniffers are NAI Useful tools for deviant computer users since they can be used to pull plain
Free http sniffer 1.1 software#
A Sniffer (also know as a Network Analyzer) is a piece of software that can lookĪt network traffic, decode it, and give meaningful data that a networkĪdministrator can use to diagnose problems on a network. When I tell some of my coworkers that I'm sniffing the network, they have a tendency to look at me funny. Wireshark/Ethereal, ARPSpoof, Ettercap, ARP poisoning and other niceties. A Quick Intro to Sniffers: Wireshark/Ethereal, ARPSpoof, Ettercap, ARP

1 note
·
View note
Text
Migraine Specialist | Sedona Holistic Medicine
Migraine Specialist | Sedona Holistic Medicine
Kindly contact headache expert Dr. Rubiales at
[email protected] for more data about Migraine Headache Treatment in Sedona. Help from Migraine specialist. "To those looking for another way to deal with recuperating: This letter is to communicate my genuine gratitude to Karen Merveldt-Guevara.Particular non-clinical strategies for treatment for cerebral pains and headaches can incorporate needle therapy, biofeedback, avoidance diets, yoga, and natural or homeopathic In a restrictive meeting with Elite Daily, Dr. Susan Hutchinson, a cerebral pain and headache expert Norterra Family Medicine offers regular solutions for treat headaches. Dr. Sarna offers Acupuncture at their Paradise Wellness office in the suite next door.There are in a real sense many regular prescriptions accessible to prescribe.At Release Integrative Medicine in Charlestown, Massachusetts, Tim Eng, LAc, CSMA, adopts an all encompassing strategy to treating headaches. Elective medication. For some individuals, reciprocal or elective treatments offer alleviation from migraine torment .

Dr's significant Darlene Reid-Ahenakew ND is a specialist in headache the board. Gain normal ways of recuperating from headaches with a useful way to deal with your wellbeing! To decide whether an all encompassing treatment is appropriate for you, Dr. Kuruvilla suggests talking with your essential consideration supplier or cerebral pain expert Bonnie S. Friehling, MD, is the main all encompassing medical services supplier in Columbia, creates customized therapy plans for the administration of cerebral pains There is a major range of side effects in headache and normally specialists analyze headache as a serious cerebral pain that confines exercises, and has light or sound At Ketamine Integrative Medicine in Gilbert, Arizona, Annette Lusko, DO, offers redid ketamine therapies, including mixture treatment to assuage headaches Naturopathic doctor Pamela Santapaola, NP, adopts an integrative strategy to migraine care. At Healing Duo Integrative Family Medical Practice in Norwalk As an update, these responses are intended to offer clinical ... Terri inquires: What's your assessment of an all encompassing way to deal with headache treatment.
CONTACT US :Tel. (928) 862-2914
1350 W SR 89 A Suite 26
Sedona, AZ 86336
0 notes
Text
ETHERNET
What is Ethernet?
Definition: Ethernet (pronounced “eether net”) is a computer network technology which is used in different area networks like LAN, MAN, WAN. Ethernet connecting computers together with cable so the computers can share information. Within each main branch of the network, “Ethernet” can connect up to 1,024 personal computers and workstations.
Ethernet provides services on the Physical (Layers 1) and Data Link Layer (Layers 2) of OSI reference model.The Data Link Layer is further divided into two sublayers that are Logical Link Control (LLC) and Media Access Control (MAC),these sublayers can be used to establish the transmission paths and format data before transmiting on the same network segment.
Systems that use ethernet communication divide their data into packets, which are also known as frames. These frames further contain source and destination address, a mechanism which was used to detect errors in the data and retransmission requests.
History of Ethernet
Read More
Ethernet was developed over several years in the early 1970s by group researchers within the company Xerox Palo Alto Research Center (Xerox PARC) including, in particular, Robert Metcalfe (who founded later 3Com company). The goal the research project was to connect networked computers and laser printers. Xerox Corporation filed a patent on this technology late 1977. In 1979, companies Digital Equipment Corporation (DEC), Intel and Xerox combined to improve Ethernet and together published the first standard in 1980: Ethernet Blue Book sometimes called TEN (after the initials of the three companies). Finally, the IEEE this technology became standard in 1983: 802.3 was born … well before the 802.11! A little abuse of language, it is called Ethernet 802.3 standard. The format of DIX Ethernet packets is slightly different from the 802.3 Ethernet packets, but the two can coexist on the same network. The invention of single-chip Ethernet controllers has made Ethernet cards very cheap, and many modern PCs have it built-in on the MOTHERBOARD.
Wired Ethernet
Initially, ethernet can be designed to run over coaxial cables, twisted pair cables,fiber optic cable.
Wired Ethernet network, devices are connected with the help of a fiber optic cable which connects the devices within a distance of 10km. For this, we have to install a computer network interface card (NIC) in each computer. A unique address is given to each computer that is connected. So, for sharing data and resources like printers, computers, and other machines, Ethernet networking is used as it establishes a communication system.
Read More
Ethernet is a shared medium network technology, where all the workstations are connected to the same cable and must connect with one another to send signals over it. The algorithm used to resolve collisions – that is, when two workstations try to speak at the same time – is called CSMA/CD, and works by forcing both workstations to back off for random (and hence probably different) intervals before trying again.
Advantages of using wired Ethernet network
•It is very reliable.
• Ethernet network makes use of firewalls for the security of the data.
• Data is transmitted and received at very high speed.
• It is very easy to use the wired network.
Disadvantages of using wired Ethernet network
• The wired Ethernet network is used only for short distances.
• The mobility is limited.
• Its maintenance is difficult.
• Ethernet cables, hubs, switches, routers increase the cost of installation.
Wireless Ethernet
In this, wireless NICs are used for connecting the computer instead of a cable and these wireless NICs make use of radio waves for communicating between the systems and furthers these NICs are connected with a wireless switch or hub. This technology requires maintenance, but it is more easy to use.
Read More
Wired Ethernet network, devices are connected with the help of a fiber optic cable which connects the devices within a distance of 10km. For this, we have to install a computer network interface card (NIC) in each computer. A unique address is given to each computer that is connected. So, for sharing data and resources like printers, computers, and other machines, Ethernet networking is used as it establishes a communication system. Ethernet is a shared medium network technology, where all the workstations are connected to the same cable and must connect with one another to send signals over it. The algorithm used to resolve collisions – that is, when two workstations try to speak at the same time – is called CSMA/CD, and works by forcing both workstations to back off for random (and hence probably different) intervals before trying again.
Wireless Ethernet
In this, wireless NICs are used for connecting the computer instead of a cable and these wireless NICs make use of radio waves for communicating between the systems and furthers these NICs are connected with a wireless switch or hub. This technology requires maintenance, but it is more easy to use.
1 note
·
View note
Text
Network代写|Assignment 3 Data Link Layer
1.1. Suppose four active nodes—nodes A, B, C and D—are competing for access to a channel using slotted ALOHA. Assume each node has an infinite number of packets to send. Each node attempts to transmit in each slot with probability p. The first slot is numbered slot 1, the second slot is numbered slot 2, and so on. [5]

What is the probability that node A succeeds for the first time in slot 5?
What is the probability that some node (either A, B, C or D) succeeds in slot 4?
What is the probability that the first success occurs in slot 3?
What is the efficiency of this four-node system?Suppose nodes A and B are on the same 10 Mbps broadcast channel, and the propagation delay between the two nodes is 325 bit times. Suppose CSMA/CD and Ethernet packets are used for this broadcast channel. Suppose node A begins transmitting a frame and, before it finishes, node B begins transmitting a frame. Can A finish transmitting before it detects that B has transmitted? Why or why not? If the answer is yes, then A incorrectly believes that its frame was successfully transmitted without a collision. Hint: Suppose at time t = 0 bits, A begins transmitting a frame. In the worst case, A transmits a minimumsized frame of 512+64 bit times. So A would finish transmitting the frame at t =512+64 bit times. Thus, the answer is no, if B’s signal reaches A before bit time t =512+64 In the worst case, when does B’s signal reach A? [10] Consider Figure 1. Provide MAC addresses and IP addresses for the interfaces at Host A, both routers, and Host F. Suppose Host A sends a datagram to Host F. Give the source and destination MAC addresses in the frame encapsulating this IP datagram as the frame is transmitted (i) from A to the left router, (ii) from the left router to the right router, (iii) from the right router to F. Also give the source and destination IP addresses in the IP datagram encapsulated within the frame at each of these points in time. [5]
Let’s consider the operation of a learning switch in the context of a network in which 6 nodes labeled A through F are star connected into an Ethernet switch. Suppose that (i) B sends a frame to E, (ii) E replies with a frame to B, (iii) A sends a frame to B, (iv) B replies with a frame to A. The switch table is initially empty. Show the state of the switch table before and after each of these events. For each of these events, identify the link(s) on which the transmitted frame will be forwarded, and briefly justify your answers. [10] Consider the single switch VLAN in Figure 2, and assume an external router is connected to switch port 1. Assign IP addresses to the EE and CS hosts and router interface. Trace the steps taken at both the network layer and the link layer to transfer an IP datagram from an EE host to a CS host (Hint: Reread the discussion of Figure 6.19 in the textbook). [10]
0 notes