#what is apache web server
Explore tagged Tumblr posts
Text
Want to know what is Apache server? Learn how Apache works to power your web experience & Explore Apache Server's functionality and operation.
#what is an apache server#what is apache server#what is apache server and how it works#what is apache web server
0 notes
Text
I’m sorry but I’m still losing my fucking MIND over elons incomprehensible Linux own the libs tweet like
Like it’s incredibly obvious he heard about a traceroute, and then googled “how to delete file in Linux” and then didn’t even read the results
Like… woke_mind_virus isn’t a fully qualified domain name, meaning it relies on a custom DNS resolution specific to his machine, or if utilizing a vpn, that specific vpn’s custom host file. Or that the American government would have a host entry for a woke mind virus, which if you’ve ever had to use a government website, is laughable. Also DNS is global for the most part, but honestly we can move on at this point.
So sure, we’ll say that the government has forced all public internet in America to resolve woke_mind_virus. Where does it resolve to? YOUR OWN COMPUTER, you silly billy! Obviously! This is *almost* comprehensible. Sure, we are all infected with the woke mind virus, why not. It must be destroyed within ourselves. Yeah man, whatever. Why not? So how do we destroy it?
Duh! Just delete it! How do we do that in our L337 uber hax0r terminal on our fresh kali live usb (because partitions are scary)? We’ll save that for last.
Because while deleting one file could make a website inoperable, it does not remove every trace of it! It first needs a configuration file in the web server, usually Apache or nginx. This is at LEAST one file, but cmon, if you’re gonna psychologically program the masses and keep it out of public view, you gotta encrypt that shit! So naturally, an SSL is in order! That’s easily 1-3 more files. woke_mind_virus can get a pass on not being fully qualified in this specific case because certs can theoretically be self signed and trusted on local networks, but he wouldn’t be able to tell you that. If you stood up a little one page html site on a web server on your own computer, and navigated to it on port 443 (https://) you would get an SSL error, even though it’s on your own machine. I feel like I’ve beaten this into the ground enough, but just understand it’s stupid.
What’s important to note here is that these BARE MINIMUM files are what routes the request from your machine to the destination site, even if it’s your own computer. If you delete the contents of the site (also called the docroot), the site still exists, and can receive and route requests to and from it, it’s just empty. You’ll probably get a 404 because there’s no actual content to serve. This woke mind princess is in another castle.
It’s also imprudent to delete these configuration files first, because that’s how you determine where the site content actually is! These files dictate what directory (folder for you windows losers) is called upon to actually serve you the content you see displayed when you open a webpage. So you need this information if you don’t want to destroy the entire file system and only want to remove the woke_mind_virus site. Cmon Elon, this is baby shit.
So of course, the strat with the most Efficiency and preserving the rest of the system (which seems to be the point of the tweet) is to find the docroot, delete the docroot, and then delete the web server config files. So how do we delete them?
And here we have it: rm -rf
The syntax is as follows:
rm -rf </path/to/file>
Even if you don’t know shit about Linux, you can probably see the problem here. It’s just so blatantly incorrect, it’s almost as if he’s never done it before.
For those that want to see a real world example, here is me creating a file called woke_mind_virus in my home directory and then trying to delete it the Elon Way:
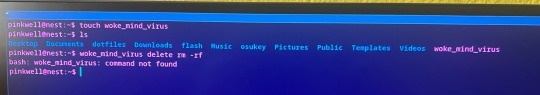
3 notes
·
View notes
Text
Secure Your Laravel App: Fix Insufficient Transport Layer Security (TLS)
Introduction
Transport Layer Security (TLS) is vital for ensuring secure communication between clients and servers over the Internet. Insufficient TLS configurations can leave your Laravel web applications exposed to various cyber threats, like Man-in-the-Middle (MitM) attacks. In this blog post, we’ll explain the risks associated with insufficient TLS security in Laravel and provide a detailed guide on how to configure your Laravel application for optimal security.

Additionally, we’ll show you how to check and resolve potential TLS issues using our free Website Security Scanner tool.
What is Insufficient Transport Layer Security?
Insufficient Transport Layer Security occurs when a website fails to use strong encryption protocols like TLS 1.2 or higher, or when it doesn't properly configure SSL certificates. This exposes web applications to data interception, tampering, and attacks. A properly configured TLS ensures that all data transmitted between the server and client is encrypted and secure.
Common Issues in Laravel with Insufficient TLS Security
Some common causes of insufficient TLS in Laravel include:
Outdated SSL Certificates: Using deprecated SSL/TLS protocols (like SSL 3.0 or TLS 1.0) that are no longer considered secure.
Improper SSL/TLS Configuration: Misconfiguration of the web server or Laravel app that doesn’t force HTTPS or downgrade protection.
Weak Cipher Suites: Servers using weak ciphers, making it easier for attackers to break the encryption.
Lack of HTTP Strict Transport Security (HSTS): Without HSTS, an attacker can force the browser to use an insecure HTTP connection instead of HTTPS.
How to Fix Insufficient TLS in Laravel
Upgrade Your Laravel App’s TLS Protocol To enforce TLS 1.2 or higher, you'll need to configure your server to support these protocols. Here’s how you can configure your server to prioritize stronger encryption:
In Apache: Modify the ssl.conf file:
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
In Nginx: Edit your nginx.conf file:
ssl_protocols TLSv1.2 TLSv1.3;
These configurations will ensure that your server uses only secure versions of TLS.
2. Force HTTPS in Laravel Laravel provides an easy way to force HTTPS by modifying the .env file and the config/app.php file:
In .env file:
APP_URL=https://yourdomain.com
In config/app.php file:
'url' => env('APP_URL', 'https://yourdomain.com'),
This will ensure that all requests are redirected to HTTPS, preventing insecure HTTP access.
3. Enable HTTP Strict Transport Security (HSTS) HTTP Strict Transport Security is a web security policy mechanism that helps to protect websites against Man-in-the-Middle (MitM) attacks by forcing clients to communicate over HTTPS. Here's how to add HSTS headers to your Laravel app:
In Apache: Add the following line to your ssl.conf or .htaccess file:
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains"
In Nginx: Add the following line to your nginx.conf file:
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains" always;
4. Use Strong Cipher Suites Weak cipher suites allow attackers to break the encryption. You can configure your server to use strong ciphers:
In Apache:
SSLCipherSuite HIGH:!aNULL:!MD5:!3DES
In Nginx:
ssl_ciphers 'ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256';
5. Use a Valid SSL/TLS Certificate Ensure that your website uses a valid SSL/TLS certificate from a trusted Certificate Authority (CA). You can get a free SSL certificate from Let's Encrypt.
How to Check TLS Configuration with Our Free Tool
Before and after implementing the changes, it’s essential to check the security status of your website. You can use our free Website Security Checker Tool to evaluate your website’s TLS configuration.
Go to https://free.pentesttesting.com.
Enter your website URL to start the scan.
Review the vulnerability assessment report for TLS issues.
Screenshot of the Free Tool
Here’s a screenshot of the free Website Security Checker tool in action:

Screenshot of the free tools webpage where you can access security assessment tools.
Screenshot of a Vulnerability Assessment Report
After running the scan to check website vulnerability, you’ll receive a detailed report highlighting any security vulnerabilities, including issues related to TLS. Here’s an example of the vulnerability assessment report:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Conclusion
Ensuring sufficient Transport Layer Security in your Laravel app is crucial to protecting sensitive data and preventing attacks. By following the steps outlined in this blog, you can fix any TLS issues and enhance the security of your web application.
Don’t forget to check your website using our free Website Security Checker tool to identify any existing TLS vulnerabilities and other security flaws.
Need help? Contact us at Pentest Testing Corp for professional vulnerability assessments and penetration testing services to secure your website further.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#tls
4 notes
·
View notes
Text
What Is Linux Web Hosting? A Beginner's Guide
In the ever-evolving digital landscape, the choice of web hosting can significantly impact your online presence. One of the most popular options available is Linux web hosting. But what exactly does it entail, and why is it so widely preferred? This beginner’s guide aims to demystify Linux web hosting, its features, benefits, and how it stands against other hosting types.
Introduction to Web Hosting
Web hosting is a fundamental service that enables individuals and organisations to make their websites accessible on the internet. When you create a website, it consists of numerous files, such as HTML, images, and databases, which need to be stored on a server. A web host provides the server space and connectivity required for these files to be accessed by users online.
There are several types of web hosting, each designed to cater to different needs and budgets. Shared hosting is a cost-effective option where multiple websites share the same server resources. Virtual Private Server (VPS) hosting offers a middle ground, providing dedicated portions of a server for greater performance and control. Dedicated hosting provides an entire server exclusively for one website, ensuring maximum performance but at a higher cost. Cloud hosting uses multiple servers to balance the load and maximise uptime, offering a scalable solution for growing websites.
Web hosting services also include various features to enhance the performance and security of your website. These can range from basic offerings like email accounts and website builders to more advanced features like SSL certificates, automated backups, and DDoS protection. The choice of web hosting can significantly influence your website’s speed, security, and reliability, making it crucial to choose a solution that aligns with your specific requirements.
Understanding the different types of web hosting and the features they offer can help you make an informed decision that suits your needs. Whether you are running a personal blog, a small business website, or a large e-commerce platform, selecting the right web hosting service is a critical step in establishing a successful online presence.
What Is Linux Web Hosting?
Linux web hosting is a type of web hosting service that utilises the Linux operating system to manage and serve websites. Renowned for its open-source nature, Linux provides a stable and secure platform that supports a wide array of programming languages and databases, making it a favoured choice amongst developers and businesses. This hosting environment typically includes support for popular technologies such as Apache web servers, MySQL databases, and PHP scripting, which are integral to modern website development.
One of the distinguishing features of Linux web hosting is its cost-effectiveness. As an open-source system, Linux eliminates the need for costly licensing fees associated with proprietary software, thereby reducing overall hosting expenses. This makes it an attractive option for individuals and organisations operating on a budget.
Moreover, Linux is celebrated for its robust performance and high stability. Websites hosted on Linux servers experience less downtime and faster loading times, which are critical factors for maintaining user engagement and search engine rankings. The operating system’s extensive community of developers continuously works on updates and improvements, ensuring that Linux remains a cutting-edge choice for web hosting.
Linux web hosting also offers considerable flexibility and customisation options. Users have the freedom to configure their hosting environment to meet specific needs, whether they are running simple static websites or complex dynamic applications. This versatility extends to compatibility with various content management systems (CMS) like WordPress, Joomla, and Drupal, which often perform optimally on Linux servers.
In summary, Linux web hosting provides a reliable, secure, and cost-effective solution that caters to a diverse range of web hosting requirements. Its compatibility with essential web technologies and its inherent flexibility make it a preferred choice for many web developers and site owners.
Key Benefits of Linux Web Hosting
Linux web hosting offers several compelling advantages that contribute to its widespread adoption. One of its primary benefits is cost-effectiveness. The open-source nature of Linux eliminates the need for expensive licensing fees, allowing users to allocate their resources more efficiently. This makes it an ideal choice for individuals and organisations with budget constraints. Additionally, Linux is celebrated for its high stability and robust performance. Websites hosted on Linux servers often experience minimal downtime and faster loading speeds, which are essential for maintaining user engagement and achieving favourable search engine rankings.
Another significant benefit is the extensive community support that comes with Linux. The active community of developers and enthusiasts continuously works on updates, patches, and security enhancements, ensuring that Linux remains a secure and reliable platform for web hosting. This ongoing development also means that any issues or vulnerabilities are promptly addressed, offering peace of mind for website owners.
Flexibility is another key advantage of Linux web hosting. The operating system supports a wide range of programming languages, including PHP, Python, and Ruby, making it suitable for various types of web applications. Additionally, Linux servers are highly customisable, allowing users to configure their environment to meet specific needs, whether they are running simple static sites or complex dynamic applications.
Moreover, Linux web hosting is highly compatible with popular content management systems (CMS) like WordPress, Joomla, and Drupal. This compatibility ensures that users can easily deploy and manage their websites using these platforms, benefiting from their extensive plugin and theme ecosystems.
Lastly, Linux's superior security features are worth noting. The operating system is inherently secure and offers various built-in security measures. When combined with best practices such as regular updates and strong passwords, Linux web hosting provides a highly secure environment for any website.
Understanding Linux Distributions in Web Hosting
Linux comes in a variety of distributions, each tailored to meet specific needs and preferences. Among the most popular for web hosting are Ubuntu, CentOS, and Debian. Ubuntu is celebrated for its ease of use and extensive community support, making it a great choice for those new to Linux. CentOS, a favourite in enterprise environments, offers impressive stability and long-term support, which ensures a dependable hosting experience. Debian stands out with its robust package management system and commitment to open-source principles, providing a reliable and secure foundation.
Each distribution brings its own strengths to the table. For example, Ubuntu’s frequent updates ensure access to the latest features and security patches, while CentOS’s extended support cycles make it a solid choice for those requiring a stable, long-term hosting environment. Debian’s extensive repository of packages and minimalistic approach offers flexibility and customisation, catering to the needs of experienced users.
Selecting the right Linux distribution largely depends on your specific requirements and technical expertise. If you prioritise user-friendliness and a wealth of resources for troubleshooting, Ubuntu might be the ideal pick. On the other hand, if you need a rock-solid, stable platform for an enterprise-level application, CentOS could be more appropriate. For those seeking maximum control and a commitment to open-source principles, Debian is a compelling option.
Ultimately, understanding the nuances of these distributions will enable you to choose a Linux environment that aligns with your web hosting needs, ensuring optimal performance and reliability.
Linux Hosting vs Windows Hosting: A Comparative Analysis
When evaluating Linux hosting against Windows hosting, several critical factors come into play. Cost is a significant differentiator; Linux hosting is generally more affordable due to its open-source nature, which eliminates the need for expensive licensing fees. In contrast, Windows hosting often incurs additional costs related to proprietary software licenses.
Compatibility is another important aspect to consider. Linux hosting is renowned for its compatibility with a broad array of open-source software and applications, including popular content management systems like WordPress, Joomla, and Magento. These platforms typically perform better on Linux servers due to optimised server configurations. On the other hand, Windows hosting is the go-to option for websites that rely on Microsoft-specific technologies such as ASP.NET, MSSQL, and other .NET frameworks.
Performance and stability are also crucial elements in this comparison. Linux hosting often provides superior uptime and faster loading speeds due to the lightweight nature of the Linux operating system. The robust performance of Linux servers is further enhanced by the active community that continuously works on optimisations and security patches. Windows hosting, while also reliable, can sometimes be more resource-intensive, potentially affecting performance.
Customisation and control levels differ significantly between the two. Linux offers greater flexibility and customisation options, allowing users to tweak server settings and configurations extensively. This level of control is particularly beneficial for developers who need a tailored hosting environment. Conversely, Windows hosting is typically easier to manage for those familiar with the Windows operating system but may offer less flexibility in terms of customisation.
Security measures also vary between Linux and Windows hosting. Linux is often praised for its strong security features, which are bolstered by a large community dedicated to promptly addressing vulnerabilities. While Windows hosting is secure, it may require more frequent updates and maintenance to ensure the same level of protection.
Common Use Cases for Linux Web Hosting
Linux web hosting is versatile and caters to a broad range of applications, making it a popular choice across various sectors. One of the most common use cases is hosting blogs and personal websites, particularly those built on platforms like WordPress. The open-source nature of Linux and its compatibility with PHP make it an ideal environment for WordPress, which powers a significant portion of the web.
E-commerce websites also benefit greatly from Linux web hosting. Solutions like Magento, PrestaShop, and OpenCart often perform better on Linux servers due to their need for a robust, secure, and scalable hosting environment. The flexibility to configure server settings allows online store owners to optimise performance and ensure a smooth shopping experience for their customers.
Content Management Systems (CMS) such as Joomla and Drupal are another prime use case. These systems require reliable and flexible hosting solutions to manage complex websites with large amounts of content. Linux's support for various databases and scripting languages ensures seamless integration and optimal performance for CMS-based sites.
Developers frequently turn to Linux web hosting for custom web applications. The operating system supports a variety of programming languages, including Python, Ruby, and Perl, making it suitable for a wide array of development projects. Its command-line interface and extensive package repositories allow developers to install and manage software efficiently.
Additionally, Linux web hosting is commonly used for educational and non-profit websites. The low cost and high reliability make it a practical choice for schools, universities, and charitable organisations that need a dependable online presence without breaking the bank.
Setting Up a Linux Web Hosting Environment
Setting up a Linux web hosting environment can be straightforward with the right approach. Begin by selecting a reputable hosting provider that offers Linux-based plans. After signing up, you'll typically be granted access to a control panel, such as cPanel or Plesk, which simplifies the management of your hosting environment. Through the control panel, you can manage files, databases, email accounts, and more.
Next, if you're using a content management system (CMS) like WordPress, Joomla, or Drupal, you can often find one-click installation options within the control panel. This feature makes it easy to get your website up and running quickly. Additionally, ensure that you configure your domain name to point to your new hosting server, which usually involves updating your domain's DNS settings.
For those who prefer more control or are comfortable using the command line, you can manually set up your web server using SSH access. This method allows you to install and configure web server software like Apache or Nginx, as well as databases such as MySQL or PostgreSQL.
Regardless of the setup method you choose, it's crucial to secure your server from the outset. This includes setting up a firewall, enabling SSH key authentication for secure access, and regularly updating all software to protect against vulnerabilities. Regularly monitoring your server's performance and security logs can help you stay ahead of potential issues, ensuring a stable and secure hosting environment for your website.
Security Best Practices for Linux Web Hosting
Securing your Linux web hosting environment is paramount to safeguarding your website against potential threats. Begin by ensuring your server software and all installed applications are up to date. Regular updates often include patches for security vulnerabilities, making this a critical step. Utilise strong, unique passwords for all user accounts, and consider employing SSH key authentication for added security when accessing your server remotely.
Setting up a firewall is another essential measure. Tools like iptables or firewalld can help you configure firewall rules to control incoming and outgoing traffic, thereby reducing the risk of unauthorised access. Implementing intrusion detection systems (IDS), such as Fail2Ban, can provide an additional layer of security by monitoring and blocking suspicious activities.
Consider deploying an SSL certificate to encrypt data transmitted between your server and users' browsers. This not only enhances security but also boosts user trust and can improve your search engine rankings. Additionally, limit the use of root privileges; create separate user accounts with the necessary permissions to minimise potential damage in the event of a breach.
Regularly backup your data to mitigate the impact of data loss due to hardware failure, cyber-attacks, or human error. Automated backup solutions can simplify this process, ensuring your data is consistently protected. Monitoring your server's logs can also be invaluable for identifying unusual activity early. Tools like Logwatch or the ELK Stack can assist in log management and analysis, enabling you to take swift action if anomalies are detected.
Common Challenges and How to Overcome Them
Setting up and maintaining a Linux web hosting environment can present various challenges, especially for those new to the platform. One frequent issue is navigating the command line, which can be daunting for beginners. Engaging with online tutorials, forums, and communities like Stack Overflow can be invaluable for learning the basics and troubleshooting problems. Another common challenge is software incompatibility. Ensuring your web applications are compatible with the Linux distribution you choose is crucial; consulting documentation and support resources can help mitigate these issues.
Security configuration can also be a complex task. Implementing best practices such as setting up firewalls, regular updates, and using strong authentication methods requires a good understanding of Linux security principles. Managed hosting services can offer a solution here by handling these technical aspects for you, allowing you to focus on your website content.
Resource management is another area where users might struggle. Monitoring server performance and managing resources effectively ensures your website runs smoothly. Utilising monitoring tools and performance optimisation techniques can help you stay ahead of potential issues. Lastly, when it comes to server backups, regular, automated solutions are essential to prevent data loss and minimise downtime. Being proactive in addressing these challenges will ensure a more seamless and secure Linux web hosting experience.
Popular Control Panels for Linux Web Hosting
Control panels are invaluable for simplifying the management of your Linux web hosting environment. Among the most popular are cPanel, Plesk, and Webmin. cPanel is renowned for its intuitive interface and extensive feature set, making it a favourite among users who need a straightforward yet powerful management tool. Plesk offers robust functionality and supports both Linux and Windows servers, providing versatility for those who manage multiple server environments. Webmin stands out as a free, open-source option that allows comprehensive server management through a web interface, catering to those who prefer a customisable and cost-effective solution. Each control panel brings unique strengths, helping to streamline tasks such as file management, database administration, and security configurations.
Choosing the Right Linux Web Hosting Provider
Choosing the right Linux web hosting provider involves several key considerations. Firstly, evaluate the quality of customer support offered. Responsive and knowledgeable support can be invaluable, especially when troubleshooting technical issues or during the initial setup phase. Check if the provider offers 24/7 support and multiple contact methods such as live chat, email, and phone.
Another crucial factor is the security measures in place. Opt for providers that offer robust security features, including regular backups, SSL certificates, firewalls, and DDoS protection. These features help safeguard your website against potential threats and ensure data integrity.
Reliability and uptime guarantees are also vital. Aim for providers that offer at least a 99.9% uptime guarantee, as frequent downtimes can significantly affect your website’s accessibility and user experience. Additionally, look into the provider’s data centre infrastructure and redundancy measures, which can impact overall performance and reliability.
Scalability is another important aspect to consider. As your website grows, you’ll need the flexibility to upgrade your hosting plan seamlessly. Check if the provider offers scalable solutions, such as easy transitions to VPS or dedicated hosting, without causing disruptions to your site.
Lastly, consider the hosting plans and pricing structures available. While cost-effectiveness is a significant benefit of Linux web hosting, ensure the plans align with your specific needs. Compare the features, storage, bandwidth, and other resources included in different plans to find the best value for your money.
Reading customer reviews and seeking recommendations can also provide insights into the provider’s reputation and service quality. By carefully evaluating these factors, you can choose a Linux web hosting provider that meets your requirements and supports your online endeavours effectively.
Conclusion and Final Thoughts
Linux web hosting stands out as an optimal choice for both beginners and seasoned web developers. Its open-source nature provides an affordable, highly customisable, and secure environment, suitable for a diverse range of websites, from personal blogs to large e-commerce platforms. The extensive community support ensures ongoing improvements and prompt resolution of issues, contributing to its reliability and performance. Choosing the right hosting provider is crucial; look for robust security measures, excellent customer support, and scalability to accommodate your website's growth. By leveraging the strengths of Linux web hosting, you can build a resilient and efficient online presence that meets your specific needs and goals.
4 notes
·
View notes
Text

SYSTEM ADMIN INTERVIEW QUESTIONS 24-25
Table of Content
Introduction
File Permissions
User and Group Management:
Cron Jobs
System Performance Monitoring
Package Management (Red Hat)
Conclusion
Introduction
The IT field is vast, and Linux is an important player, especially in cloud computing. This blog is written under the guidance of industry experts to help all tech and non-tech background individuals secure interviews for roles in the IT domain related to Red Hat Linux.
File Permissions
Briefly explain how Linux file permissions work, and how you would change the permissions of a file using chmod. In Linux, each file and directory has three types of permissions: read (r), write (w), and execute (x) for three categories of users: owner, group, and others. Example: You will use chmod 744 filename, where the digits represent the permission in octal (7 = rwx, 4 = r–, etc.) to give full permission to the owner and read-only permission to groups and others.
What is the purpose of the umask command? How is it helpful to control default file permissions?umask sets the default permissions for newly created files and directories by subtracting from the full permissions (777 for directories and 666 for files). Example: If you set the umask to 022, new files will have permissions of 644 (rw-r–r–), and directories will have 755 (rwxr-xr-x).
User and Group Management:
Name the command that adds a new user in Linux and the command responsible for adding a user to a group. The Linux useradd command creates a new user, while the usermod command adds a user to a specific group. Example: Create a user called Jenny by sudo useradd jenny and add him to the developer’s group by sudo usermod—aG developers jenny, where the—aG option adds users to more groups without removing them from other groups.
How do you view the groups that a user belongs to in Linux?
The group command in Linux helps to identify the group a user belongs to and is followed by the username. Example: To check user John’s group: groups john
Cron Jobs
What do you mean by cron jobs, and how is it scheduled to run a script every day at 2 AM?
A cron job is defined in a crontab file. Cron is a Linux utility to schedule tasks to run automatically at specified times. Example: To schedule a script ( /home/user/backup.sh ) to run daily at 2 AM: 0 2 * * * /home/user/backup.sh Where 0 means the minimum hour is 2, every day, every month, every day of the week.
How would you prevent cron job emails from being sent every time the job runs?
By default, cron sends an email with the output of the job. You can prevent this by redirecting the output to /dev/null. Example: To run a script daily at 2 AM and discard its output: 0 2 * * * /home/user/backup.sh > /dev/null 2>&1
System Performance Monitoring
How can you monitor system performance in Linux? Name some tools with their uses.
Some of the tools to monitor the performance are: Top: Live view of system processes and usage of resource htop: More user-friendly when compared to the top with an interactive interface. vmstat: Displays information about processes, memory, paging, block IO, and CPU usage. iostat: Showcases Central Processing Unit (CPU) and I/O statistics for devices and partitions. Example: You can use the top command ( top ) to identify processes consuming too much CPU or memory.
In Linux, how would you check the usage of disk space?
The df command checks disk space usage, and Du is responsible for checking the size of the directory/file. Example: To check overall disk space usage: df -h The -h option depicts the size in a human-readable format like GB, MB, etc.
Package Management (Red Hat)
How do you install, update, or remove packages in Red Hat-based Linux distributions by yum command?
In Red Hat and CentOS systems, the yum package manager is used to install, update, or remove software. Install a package: sudo yum install httpd This installs the Apache web server. Update a package: sudo yum update httpd Remove a package:sudo yum remove httpd
By which command will you check the installation of a package on a Red Hat system?
The yum list installed command is required to check whether the package is installed. Example: To check if httpd (Apache) is installed: yum list installed httpd
Conclusion
The questions are designed by our experienced corporate faculty which will help you to prepare well for various positions that require Linux such as System Admin.
Contact for Course Details – 8447712333
2 notes
·
View notes
Text
Exploring the Realm of cPanel Hosting in Australia: A Comprehensive Guide
In the vast digital landscape of Australia, where businesses thrive and online presence is paramount, finding the right hosting solution is akin to selecting a foundation for a skyscraper. In this digital age, where websites serve as the face of enterprises, the choice of hosting can significantly impact performance, user experience, and ultimately, the success of ventures. Among the plethora of options, cPanel hosting stands out as a popular choice for its user-friendly interface, robust features, and reliability. But what exactly is cPanel hosting, and why is it gaining traction among businesses in Australia?

Understanding cPanel Hosting
What is cPanel hosting?
cPanel hosting is a type of web hosting that utilizes the cPanel control panel, a web-based interface that simplifies website and server management tasks. It provides users with a graphical interface and automation tools, allowing them to effortlessly manage various aspects of their website, such as file management, email accounts, domain settings, databases, and more.
How does cPanel Hosting Work?
At its core, cPanel hosting operates on a Linux-based server environment, leveraging technologies like Apache, MySQL, and PHP (LAMP stack). The cPanel interface acts as a centralized hub, enabling users to perform administrative tasks through a user-friendly dashboard, accessible via any web browser.
Benefits of cPanel Hosting
User-Friendly Interface
One of the primary advantages of cPanel hosting is its intuitive interface, designed to accommodate users of all skill levels. With its graphical layout and straightforward navigation, even those with minimal technical expertise can manage their websites efficiently.
Comprehensive Feature Set
From creating email accounts to installing applications like WordPress and Magento, cPanel offers a wide array of features designed to streamline website management. Users can easily configure domains, set up security measures, and monitor website performance, and much more, all from within the cPanel dashboard.
Reliability and Stability
cPanel hosting is renowned for its stability and reliability, thanks to its robust architecture and frequent updates. With features like automated backups, server monitoring, and security enhancements, users can rest assured that their websites are in safe hands.
Scalability and Flexibility
Whether you're running a small blog or managing a large e-commerce platform, cPanel hosting can scale to meet your needs. With options for upgrading resources and adding additional features as your website grows, cPanel offers the flexibility required to adapt to evolving business requirements.
Choosing the Right cPanel Hosting Provider
Factors to Consider
When selecting a cPanel hosting provider in Australia, several factors should be taken into account to ensure optimal performance and reliability:
Server Location: Choose a provider with servers located in Australia to minimize latency and ensure fast loading times for local visitors.
Performance: Look for providers that offer high-performance hardware, SSD storage, and ample resources to support your website's needs.
Uptime Guarantee: Opt for providers with a proven track record of uptime, ideally offering a minimum uptime guarantee of 99.9%.
Customer Support: Evaluate the level of customer support offered, ensuring prompt assistance in case of technical issues or inquiries.
Conclusion
In conclusion, cPanel hosting serves as a cornerstone for businesses seeking reliable and user-friendly cpanel hosting Australia. With its intuitive interface, comprehensive feature set, and robust architecture, cPanel empowers users to manage their websites with ease, allowing them to focus on their core business objectives.
2 notes
·
View notes
Text
How To Setup Elasticsearch 6.4 On RHEL/CentOS 6/7?
What is Elasticsearch? Elasticsearch is a search engine based on Lucene. It is useful in a distributed environment and helps in a multitenant-capable full-text search engine. While you query something from Elasticsearch it will provide you with an HTTP web interface and schema-free JSON documents. it provides the ability for full-text search. Elasticsearch is developed in Java and is released as open-source under the terms of the Apache 2 license. Scenario: 1. Server IP: 192.168.56.101 2. Elasticsearch: Version 6.4 3. OS: CentOS 7.5 4. RAM: 4 GB Note: If you are a SUDO user then prefix every command with sudo, like #sudo ifconfig With the help of this guide, you will be able to set up Elasticsearch single-node clusters on CentOS, Red Hat, and Fedora systems. Step 1: Install and Verify Java Java is the primary requirement for installing Elasticsearch. So, make sure you have Java installed on your system. # java -version openjdk version "1.8.0_181" OpenJDK Runtime Environment (build 1.8.0_181-b13) OpenJDK 64-Bit Server VM (build 25.181-b13, mixed mode) If you don’t have Java installed on your system, then run the below command # yum install java-1.8.0-openjdk Step 2: Setup Elasticsearch For this guide, I am downloading the latest Elasticsearch tar from its official website so follow the below step # wget https://artifacts.elastic.co/downloads/elasticsearch/elasticsearch-6.4.2.tar.gz # tar -xzf elasticsearch-6.4.2.tar.gz # tar -xzf elasticsearch-6.4.2.tar.gz # mv elasticsearch-6.4.2 /usr/local/elasticsearch Step 5: Permission and User We need a user for running elasticsearch (root is not recommended). # useradd elasticsearch # chown -R elasticsearch.elasticsearch /usr/local/elasticsearch/ Step 6: Setup Ulimits Now to get a Running system we need to make some changes of ulimits else we will get an error like “max number of threads for user is too low, increase to at least ” so to overcome this issue make below changes you should run. # ulimit -n 65536 # ulimit -u 2048 Or you may edit the file to make changes permanent # vim /etc/security/limits.conf elasticsearch - nofile 65536 elasticsearch soft nofile 64000 elasticsearch hard nofile 64000 elasticsearch hard nproc 4096 elasticsearch soft nproc 4096 Save files using :wq Step 7: Configure Elasticsearch Now make some configuration changes like cluster name or node name to make our single node cluster live. # cd /usr/local/elasticsearch/ Now, look for the below keywords in the file and change according to you need # vim conf/elasticsearch.yml cluster.name: kapendra-cluster-1 node.name: kapendra-node-1 http.port: 9200 to set this value to your IP or make it 0.0.0.0 ID needs to be accessible from anywhere from the network. Else put your IP of localhost network.host: 0.0.0.0 There is one more thing if you have any dedicated mount pint for data then change the value for #path.data: /path/to/data to your mount point.
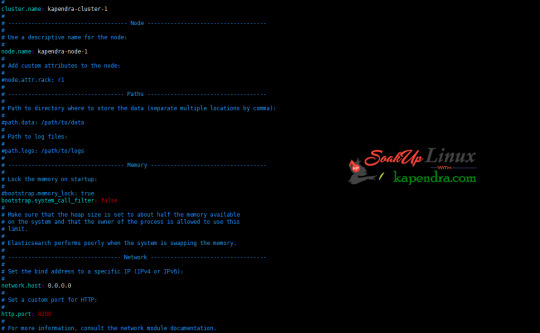
Your configuration should look like the above. Step 8: Starting Elasticsearch Cluster As the Elasticsearch setup is completed. Let the start Elasticsearch cluster with elastic search user so first switch to elastic search user and then run the cluster # su - elasticsearch $ /usr/local/elasticsearch/bin/elasticsearch 22278 Step 9: Verify Setup You have all done it, just need to verify the setup. Elasticsearch works on port default port 9200, open your browser to point your server on port 9200, You will find something like the below output http://localhost:9200 or http://192.168.56.101:9200 at the end of this article, you have successfully set up Elasticsearch single node cluster. In the next few articles, we will try to cover a few commands and their setup in the docker container for development environments on local machines. Read the full article
2 notes
·
View notes
Text
What is HTML5 and its uses?
HTML5 is the latest version of HTML, which is the standard markup language for creating web pages. HTML5 was released in 2014 and has since become the most widely used version of HTML. HTML5 includes many new features and improvements over previous versions of HTML.
New Features in HTML5
Here are some of the new features in HTML5:
Semantic elements: HTML5 includes new semantic elements such as <header>, <footer>, <nav>, and <article>. These elements provide more meaning to the content of a web page, making it easier for search engines to index and understand the content.
Multimedia support: HTML5 includes built-in support for multimedia elements such as <video> and <audio>. This makes it easier to embed videos and audio files into web pages without requiring third-party plugins such as Adobe Flash.
Form validation: HTML5 includes new form validation features that allow developers to validate user input without requiring JavaScript. This makes it easier to create forms that are more user-friendly and accessible.
Canvas: HTML5 includes a new element called <canvas>, which allows developers to create dynamic graphics and animations using JavaScript.
Uses of HTML5
HTML5 is used for creating a wide range of web applications and websites. Here are some examples:
Responsive web design: HTML5 provides many features that make it easier to create responsive web designs that work well on different devices such as desktops, tablets, and smartphones.
Mobile apps: HTML5 can be used to create mobile apps that run on different platforms such as iOS, Android, and Windows Phone. This is done using frameworks such as Apache Cordova or PhoneGap.
Games: HTML5 can be used to create games that run in a web browser without requiring any plugins. This is done using frameworks such as Phaser or PixiJS.
Web applications: HTML5 can be used to create web applications that run entirely in a web browser without requiring any server-side processing. This is done using frameworks such as AngularJS or React.
Here are some resources that can help you learn HTML:
W3Schools: W3Schools is a popular online learning platform that offers free HTML tutorials. Their tutorials are designed for beginners and cover everything from the basics to advanced topics .
MDN Web Docs: MDN Web Docs is another great resource for learning HTML. They offer comprehensive HTML tutorials that cover everything from the basics to advanced topics .
e-Tuitions: e-Tuitions offers online classes for HTML coding. You can visit their website at e-Tuitions to book a free demo class.
Codecademy: Codecademy is an online learning platform that offers interactive HTML courses. Their courses are designed for beginners and cover everything from the basics to advanced topics .
In conclusion, HTML5 is the latest version of HTML and includes many new features and improvements over previous versions. It is widely used for creating web applications and websites, including responsive designs, mobile apps, games, and web applications.
2 notes
·
View notes
Text
Cloud Platforms Testing at GQAT Tech: Powering Scalable, Reliable Apps
In today's digital world, most companies use the cloud to host their software, store their data, and provide users with seamless experiences and interactions, meaning their cloud-based systems have to be fast and secure (it could be an e-commerce site, a mobile app, or corporate software platform) and be able to provide a robust reliable level of service that does not fail. All this hard work to develop a cloud-based application means nothing if the application is not subjected to testing and verification to work properly in different cloud environments.
Credit should be given to GQAT Tech for making cloud platform testing a core competency, as the entire QA team tests applications in the cloud, on cloud-based platforms, i.e., AWS, Azure, Google Cloud, or Private Cloud, while testing for performance, security, scalability, and functionality.
Now, let's explore the definition of cloud platform testing, what it is, why it is important, and how GQAT Tech can help your company be successful in the cloud.
What Is Cloud Platform Testing?
Cloud platform testing provides validation of whether a web or mobile application will function correctly in a cloud-based environment (as compared to on a physical server).
It involves testing how well your app runs on services like:
Amazon Web Services (AWS)
Microsoft Azure
Google Cloud Platform (GCP)
IBM Cloud
Private/Hybrid cloud setups
The goal is to ensure your app is:
Scalability - Will it support more users over time with no performance degradation?
Improve security - Is my data protected from being compromised/attacked?
Stability - Is it repeatably functioning (no crashing or errors)?
Speed - Is the load time fast enough for users worldwide?
Cost - Is it utilizing cloud resources efficiently?
GQAT Tech’s Cloud Testing Services
GQAT Tech employs a hybrid process of manual testing, automated scripts, and real cloud environments to validate/applications in the most representative manner. The QA team manages real-time performance, availability, and security across systems.
Services Offered:
Functional Testing on Cloud
Validates that your app will behave in an appropriate way while hosted on different cloud providers.
Performance & Load Testing
Validates how your app behaves when 10, 100, or 10,000 users are accessing it at the same time.
Scalability Testing
Validates whether your app is capable of scaling up or down based on usage.
Security Testing
Validates for vulnerabilities specific to clouds: data leak vulnerabilities, misconfigured access, and DDoS risks.
Disaster Recovery & Backup Validation
Validates whether systems can be restored after failure or downtime.
Cross-Platform Testing
Validates your application's performance across AWS, Azure, GCP, and Private Cloud Systems.
Why Cloud Testing Is Important
By not testing your application in the cloud, you expose yourself to significant risks such as:
App crashes when usage is highest
Data loss because of inadequate backup
Cloud bills that are expensive due to inefficient usage
Security breaches due to weaker settings
Downtime that impacts customer frustration
All of these situations can be prevented and you can ensure your app runs smoothly every day with cloud testing.
Tools Used by GQAT Tech
GQAT Tech uses advanced tools for cloud testing:
Apache JMeter – Load testing and stress testing
Postman – API testing for cloud services
Selenium / Appium – Automated UI testing
K6 & Gatling – Performance testing
AWS/Azure/GCP Test Environments – Real cloud validation
CI/CD Pipelines (Jenkins, GitHub Actions) – Continuous cloud-based testing
Who Needs Cloud Platform Testing?
GQAT Tech works with startups, enterprises, and SaaS providers across industries like:
E-commerce
Healthcare
Banking & FinTech
Logistics & Travel
IoT & Smart Devices
Education & LMS platforms
If your product runs in the cloud, you need to test it in the cloud—and that’s exactly what GQAT does.
Conclusion
Cloud computing provides flexibility, speed, and power—but only if your applications are tested and validated appropriately. With GQAT Tech's cloud platform testing services, you can be confident that your application will work as required under all real-world environments.
They will help eliminate downtime, enhance app performance, protect user data and help optimize cloud expenditure—so you can expand your business without concern.
💬 Ready to test smarter in the cloud? 👉 Explore Cloud Platform Testing Services at GQAT Tech
#Cloud Platform Testing#AWS Testing#Azure Testing#Google Cloud QA#Cloud Application Testing#Performance Testing on Cloud#Cloud Scalability Testing#Functional Testing on Cloud#Cloud Security Testing#Cloud-Based QA#GQAT Cloud Services#CI/CD in Cloud#Real-Time Cloud Testing#Cloud QA Automation#SaaS Testing Platforms
0 notes
Text
Weak SSL/TLS Configuration in Symfony — Risks & Fixes
Introduction
Secure communication is critical in today’s web applications, especially when handling sensitive user data. Symfony, one of the most popular PHP frameworks, relies heavily on SSL/TLS protocols to secure HTTP connections. However, weak SSL/TLS configurations can expose your application to man-in-the-middle (MITM) attacks, data breaches, and regulatory penalties.

In this blog, we’ll explore what weak SSL/TLS configuration means in Symfony applications, why it’s dangerous, and how you can fix it with practical coding examples. Plus, you’ll get a peek at how our Website Vulnerability Scanner online free, helps identify such vulnerabilities automatically.
What is Weak SSL/TLS Configuration?
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are cryptographic protocols designed to secure communication over the internet. A weak SSL/TLS configuration involves:
Using deprecated protocols like SSL 2.0, SSL 3.0, or early TLS versions (TLS 1.0/1.1).
Employing weak cipher suites (e.g., RC4, DES).
Missing forward secrecy (PFS).
Poor certificate validation or expired certificates.
These weaknesses can be exploited to intercept or alter data during transmission.
Common SSL/TLS Weaknesses in Symfony
Symfony itself relies on the underlying web server (Apache, Nginx) or PHP cURL/OpenSSL for TLS. Misconfigurations can happen at various layers:
Web server allows weak protocols/ciphers.
PHP cURL requests do not enforce strict SSL verification.
Symfony HTTP clients or bundles not configured for secure TLS options.
Detecting Weak SSL/TLS Configurations with Our Free Tool
You can scan your website for SSL/TLS issues quickly at https://free.pentesttesting.com/.
Screenshot of the Website Vulnerability Scanner tool webpage

Screenshot of the free tools webpage where you can access security assessment tools.
Our tool will generate a detailed vulnerability report, highlighting SSL/TLS weaknesses among other issues.
Assessment report screenshot to check Website Vulnerability

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
How to Fix Weak SSL/TLS Configuration in Symfony
1. Configure Your Web Server Correctly
Ensure your Apache or Nginx server uses strong protocols and ciphers. For example, in Nginx:
ssl_protocols TLSv1.2 TLSv1.3; ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384'; ssl_prefer_server_ciphers on; ssl_session_cache shared:SSL:10m; ssl_session_tickets off;
This disables weak protocols and uses strong cipher suites with Perfect Forward Secrecy.
2. Enforce SSL Verification in PHP cURL Requests
When Symfony makes external HTTP calls via PHP cURL, enforce strict SSL checks.
$ch = curl_init('https://api.example.com/secure-endpoint'); curl_setopt($ch, CURLOPT_RETURNTRANSFER, true); curl_setopt($ch, CURLOPT_SSL_VERIFYPEER, true); // Verify SSL certificate curl_setopt($ch, CURLOPT_SSL_VERIFYHOST, 2); // Verify host name matches cert $response = curl_exec($ch); if(curl_errno($ch)) { throw new \Exception('SSL Error: ' . curl_error($ch)); } curl_close($ch);
3. Use Symfony HTTP Client with Secure Defaults
Since Symfony 4.3+, the HTTP Client component uses secure defaults, but always ensure SSL verification is enabled:
use Symfony\Component\HttpClient\HttpClient; $client = HttpClient::create([ 'verify_peer' => true, 'verify_host' => true, ]); $response = $client->request('GET', 'https://secure-api.example.com/data'); $statusCode = $response->getStatusCode(); $content = $response->getContent();
4. Regularly Update Your Certificates and Libraries
Expired or self-signed certificates can break trust chains. Use trusted CAs and update OpenSSL and PHP regularly.
Bonus: Automate SSL/TLS Testing in Your Symfony CI/CD Pipeline
You can add an automated SSL check using tools like testssl.sh or integrate vulnerability scanning APIs such as our free tool’s API (check details at https://free.pentesttesting.com/).
About Pentest Testing Corp.
For comprehensive security audits, including advanced web app penetration testing, check out our service at Web App Penetration Testing Services.
Also, don’t miss our cybersecurity insights and updates on our blog.
Subscribe to our newsletter for the latest tips: Subscribe on LinkedIn.
Conclusion
Weak SSL/TLS configurations put your Symfony apps and users at significant risk. By following secure web server settings, enforcing SSL verification in PHP/Symfony, and leveraging automated scanning tools for a Website Security test, you can greatly improve your application’s security posture.
Stay safe, keep scanning, and secure your Symfony apps today!
If you found this blog helpful, please share and follow our blog at Pentest Testing Corp.
1 note
·
View note
Text
Java in Software Development: A Timeless Language for Modern Solutions
Java has stood the test of time as one of the most popular and reliable programming languages in the software development world. From mobile apps to large-scale enterprise systems, Java powers countless digital solutions across the globe. Its platform independence, robust security features, and vast ecosystem have made it a top choice for developers for more than two decades.
What is Java?
Java is a high-level, object-oriented programming language developed by Sun Microsystems in the mid-1990s. It follows the “Write Once, Run Anywhere (WORA)” philosophy, meaning that code written in Java can run on any device equipped with the Java Virtual Machine (JVM), regardless of the underlying operating system.
Java’s syntax is clean, its structure is logical, and it borrows many ideas from C++, making it relatively easy to learn yet powerful enough for complex projects.
Why Java Still Matters in 2025
Despite the emergence of newer languages like Kotlin, Python, and Go, Java remains widely used for several compelling reasons:
1. Platform Independence
Java’s core strength lies in its platform independence. A compiled Java program can run on any device with a JVM, which includes everything from desktops to smartphones, embedded devices, and servers.
This portability makes Java an excellent choice for cross-platform development and enterprise applications.
2. Robust and Secure
Security is a top priority in software development, and Java is known for its strong security features. It offers a secure runtime environment, access control, and built-in protection against common vulnerabilities like buffer overflows.
Java’s robust memory management and automatic garbage collection also contribute to its stability and efficiency.
3. Rich API and Libraries
Java has a massive standard library (Java API) and a vast array of open-source libraries and frameworks. Whether you're building a web application, a game, or a machine learning tool, Java likely has a framework or toolset to support your work—Spring, Hibernate, Apache libraries, and JavaFX are just a few examples.
4. Community and Support
With millions of developers worldwide, Java has one of the largest and most active programming communities. This means continuous updates, widespread documentation, and countless tutorials that make problem-solving easier for both beginners and experienced professionals.
5. Enterprise Adoption
Many Fortune 500 companies and global enterprises continue to rely on Java for backend systems, banking software, e-commerce platforms, and more. The stability and scalability of Java make it a favorite for mission-critical applications.
Common Uses of Java in Software Development
Let’s take a look at some areas where Java continues to thrive:
1. Web Applications
Java is widely used in building dynamic web applications. Frameworks like Spring and JavaServer Faces (JSF) enable developers to create secure and scalable applications efficiently. Large websites and services like LinkedIn, Amazon, and eBay have backend systems partly powered by Java.
2. Android App Development
Java was the original language used for Android app development, and although Kotlin is now the preferred choice by Google, Java is still heavily used in the Android ecosystem. Most Android libraries are compatible with Java, and a significant portion of apps are still developed in or maintained with Java.
3. Enterprise Software
From banking to insurance to government sectors, Java is the backbone of many enterprise software systems. Technologies like Java EE (Enterprise Edition) provide the tools needed to build high-performance, distributed, and transaction-based applications.
4. Scientific Applications
Java’s precision, portability, and performance make it a good candidate for scientific applications. Its built-in mathematical and statistical capabilities are suitable for complex simulations and data analysis.
5. Big Data and Cloud Computing
Java plays a crucial role in the Big Data ecosystem. Tools like Hadoop and Apache Spark support Java, enabling developers to process massive amounts of data efficiently. Additionally, many cloud computing platforms like AWS and Google Cloud offer SDKs and tools for Java.
Learning Java in Today’s World
For those aspiring to enter the tech industry, learning Java is a smart move. It provides a strong foundation in object-oriented programming and helps you understand core programming concepts that are transferable to other languages.
The Future of Java
Java continues to evolve with each new release, improving performance, adding modern language features, and simplifying syntax. Features introduced in recent versions, like records, sealed classes, and pattern matching, show that Java is adapting to modern development trends.
As enterprises move toward cloud-native architectures, microservices, and DevOps, Java frameworks like Spring Boot and Jakarta EE are helping developers build faster, lighter, and more modular applications.
Conclusion
Java remains a powerful and versatile programming language with unmatched legacy and continued innovation. Whether you’re a student just starting out, a developer aiming to work in enterprise environments, or a tech enthusiast exploring mobile or web apps, Java offers tools and capabilities to support your goals.
In the ever-changing world of software development, Java proves that a well-designed language can continue to lead and inspire, even decades after its creation.
0 notes
Text
How LiteSpeed Improves Loading Speed
Website speed is a critical factor in user experience, SEO performance, and conversion rates. Faster-loading websites engage visitors better, reduce bounce rates, and rank higher in search results. LiteSpeed Web Server (LSWS) is engineered to optimize website speed with powerful technologies built into its core. This article provides a technical and practical look at how LiteSpeed improves website performance, its architectural strengths, and comparisons with other web servers like Apache and NGINX.
What Is LiteSpeed?
LiteSpeed is a high-performance web server software developed by LiteSpeed Technologies. It serves as a drop-in replacement for Apache, meaning it can use Apache configurations such as .htaccess and mod_rewrite while offering far superior performance.

Unlike traditional web servers that rely on process-based or thread-based architectures, LiteSpeed uses an event-driven approach. This enables it to handle thousands of simultaneous connections efficiently without consuming excessive resources. It’s widely used in shared, VPS, and dedicated hosting environments due to its scalability and speed.
LiteSpeed is compatible with major web hosting control panels like cPanel, Plesk, and DirectAdmin. It also integrates seamlessly with WordPress, Magento, Joomla, and other popular CMS platforms.
How LiteSpeed Improves Loading Speed
LiteSpeed's performance is not just theoretical. Numerous benchmarks and case studies show significant improvements in load time, server response, and concurrent user handling. Its technical foundation plays a pivotal role in enabling these advantages.

Event-Driven Architecture
Most traditional web servers like Apache use a process-based or threaded architecture. Each connection requires a dedicated process or thread, which leads to high memory usage under load.
LiteSpeed uses an event-driven, asynchronous model. It processes multiple connections within a single thread, significantly reducing memory consumption and CPU load.
For example, benchmarks by LiteSpeed Technologies show that LSWS handles over 2x more concurrent connections than Apache with the same hardware configuration [1]. This architecture is especially beneficial during traffic spikes, such as flash sales or viral content events.
Built-In Caching (LSCache)
LiteSpeed’s caching engine, LSCache, is built directly into the server core. Unlike third-party caching plugins that operate at the application level, LSCache works at the server level, making it faster and more efficient.
With LSCache enabled on WordPress, testing from WPPerformanceTester shows up to 75% reduction in page load times compared to uncached sites. This is because LSCache delivers prebuilt HTML pages directly to users, bypassing PHP execution and database queries.
LSCache also supports advanced features such as:
ESI (Edge Side Includes) for partial page caching
Smart purging rules
Private cache for logged-in users
Image optimization and critical CSS generation
These features make it suitable not only for static pages but also for dynamic, eCommerce-heavy platforms like WooCommerce or Magento.
Compression and Optimization
LiteSpeed supports GZIP and Brotli compression out of the box. These technologies reduce the size of files transmitted over the network, such as HTML, CSS, and JavaScript.
According to Google PageSpeed Insights, compressing assets can reduce page size by up to 70%, which directly improves load time. Brotli, developed by Google, provides even better compression rates than GZIP in many cases, and LiteSpeed uses it efficiently.
Additionally, LiteSpeed can minify JavaScript, CSS, and HTML, combine files to reduce HTTP requests, and enable lazy loading for images—all directly from the server level.
QUIC and HTTP/3 Support
LiteSpeed is one of the earliest web servers to fully support QUIC and HTTP/3, protocols developed by Google and later adopted by IETF.
QUIC is built on UDP instead of TCP, which reduces handshake latency and improves performance over poor network conditions. HTTP/3 inherits QUIC’s benefits and introduces faster parallel requests and better encryption handling.
When HTTP/3 is enabled, page loads feel snappier, especially on mobile devices and in regions with weaker connectivity. Cloudflare reported up to 29% faster page loads using HTTP/3 versus HTTP/2 [2].
LiteSpeed’s implementation ensures that your site is future-ready and delivers optimal performance even under challenging network environments.
LiteSpeed vs Apache and NGINX
Performance benchmarks consistently show that LiteSpeed outperforms both Apache and NGINX in various scenarios, especially under high traffic and dynamic content conditions.

Apache Comparison
Apache is widely used but is resource-heavy under load. When serving PHP applications like WordPress, Apache relies on external modules (e.g., mod_php) or handlers like PHP-FPM, which increase overhead.
LiteSpeed replaces these with LiteSpeed SAPI, a more efficient PHP handler. Benchmarks show that LiteSpeed can process 3x more PHP requests per second compared to Apache [3].
NGINX Comparison
NGINX is known for its speed with static files, but it lacks full .htaccess compatibility and requires more manual tuning for dynamic sites.
LiteSpeed combines Apache’s ease of configuration with NGINX’s speed and goes further by offering built-in caching and QUIC support. This makes it a more all-in-one solution for both static and dynamic content delivery.
Real-World Results
A hosting provider, NameHero, migrated over 50,000 sites from Apache to LiteSpeed. The result was an average decrease in load time by 40%, with no change in hardware configuration [4].
Another example is a WooCommerce store that used LiteSpeed Cache. Load times dropped from 4.2s to 1.2s after activation, significantly improving Core Web Vitals and user retention.
Website owners consistently report faster Time to First Byte (TTFB), better PageSpeed scores, and fewer server crashes during traffic peaks when using LiteSpeed.
Who Should Use LiteSpeed?
LiteSpeed is ideal for:
WordPress users who want faster page loads without complex configurations.
WooCommerce and Magento store owners needing efficient dynamic caching.
Web hosting providers looking to reduce server load and increase client satisfaction.
SEO-focused marketers who want better Core Web Vitals.
Developers who want Apache compatibility with modern performance.
LiteSpeed is available in both open-source (OpenLiteSpeed) and commercial versions. While OpenLiteSpeed is suitable for smaller projects, the enterprise version offers advanced features and full control panel integration.
Final Thoughts
LiteSpeed offers a clear performance advantage due to its architecture, built-in caching, modern protocol support, and optimization features. It helps websites load faster by minimizing server load, reducing latency, and delivering content more efficiently.
Whether you're a developer, site owner, or hosting provider, switching to LiteSpeed can result in measurable improvements in speed, stability, and scalability. In today’s performance-driven web ecosystem, LiteSpeed is a practical solution backed by real results and advanced engineering.
1 note
·
View note
Text
How to Enable HTTP/2 on WHM/cPanel Using EasyApache 4 🚀
Want faster site speed, better efficiency, and modern web performance? HTTP/2 is the upgrade you need. We’ve written a detailed step-by-step guide to help you enable HTTP/2 on your WHM/cPanel server using EasyApache 4 or via the command line.
💡 Boost performance 🔧 Reduce latency 📈 Improve resource handling
Read the full guide now → What is HTTP/2 and How to Enable It on WHM/cPanel Server | EasyApache 4 Guide
🔗 Powered by ServerMO — Experts in Dedicated Servers & DDoS Protection. #http2 #webhosting #cpanel #apache #serveradmin #linux #dedicatedserver #servermo #tutorial
0 notes
Text
PHP, LAMP (Linux Apache MySQL PHP)
The LAMP stack — Linux, Apache, MySQL, and PHP — has been a cornerstone of web development for over two decades. It’s an open-source suite of software components that work together to serve dynamic websites and web applications. Among these, PHP plays a central role, acting as the scripting language responsible for generating dynamic page content. Despite the rise of modern development stacks like MERN or JAMstack, LAMP remains a reliable, accessible, and widely used platform for developers around the world.
What is LAMP?

LAMP is an acronym that stands for:
Linux: The operating system.
Apache: The web server software.
MySQL: The relational database management system.
PHP: The server-side scripting language.
Each component of LAMP is free and open-source, which contributed to its massive adoption in the early 2000s. Even today, LAMP powers a significant portion of the web, including popular platforms like WordPress, Drupal, and Joomla.
PHP: The Dynamic Power of LAMP

PHP (Hypertext Preprocessor) is the scripting language used in LAMP to process user requests and generate dynamic content. It integrates seamlessly with HTML, making it easy for developers to embed logic within web pages. PHP scripts are executed on the server, and the output is sent to the client’s browser in the form of standard HTML.
PHP supports a vast range of features including form handling, file management, database access, and session tracking. It’s easy to learn for beginners, yet powerful enough to build complex web applications. PHP is constantly evolving, with the latest versions offering improved performance, better error handling, and strong security features.
The Role of Each Component in LAMP

Here’s a breakdown of how each element in the LAMP stack functions together:
1. Linux
Linux acts as the foundation for the LAMP stack. It’s known for its stability, flexibility, and security. Most servers run on some version of Linux because of its ability to handle high volumes of traffic and customizable nature. Common Linux distributions used in LAMP setups include Ubuntu, CentOS, and Debian.
2. Apache
Apache is a powerful and flexible open-source web server that handles HTTP requests from users’ browsers. It is responsible for delivering web pages to the client and includes modules for URL rewriting, authentication, and more. Apache can be customized using .htaccess files, making it easy to manage server behavior for specific directories.
3. MySQL
MySQL is a robust relational database management system used to store and manage application data. From user accounts to blog posts, all information can be efficiently queried and updated using SQL (Structured Query Language). PHP and MySQL often work hand in hand, with PHP scripts using MySQL queries to interact with the database.
4. PHP
PHP pulls it all together by connecting the front-end interface with the back-end logic. Whether it’s fetching blog posts from a database or processing user input from a form, PHP makes the content dynamic and personalized. PHP also supports object-oriented programming, error handling, and integration with third-party libraries.
Find Out More About This
Why Developers Still Choose LAMP

Despite the introduction of newer stacks, LAMP remains popular for a few key reasons:
Maturity and Stability: With decades of development, LAMP is well-documented and stable.
Community Support: A large community ensures that developers can find tutorials, tools, and forums for help.
Cost Efficiency: Being open-source, it significantly reduces hosting and licensing costs.
Flexibility: Suitable for projects of all sizes, from small blogs to enterprise-level applications.
Compatibility: Most hosting providers support LAMP out of the box.

PHP and the LAMP stack have stood the test of time in the world of web development. They offer a dependable, efficient, and accessible way to build and maintain dynamic websites. Whether you’re launching a personal blog or developing a business application, the LAMP stack remains a solid choice. As PHP continues to evolve and the ecosystem matures, LAMP proves that reliable technology doesn’t always need to be the newest — sometimes, it just needs to work exceptionally well.
0 notes
Text
What Defines a Truly Secure Website?

In today's digital landscape, a website is often the front door to a business, a personal brand, or vital information. With cyber threats constantly evolving, the question isn't just "Is my website online?" but "Is my website truly secure?" Many users look for the padlock icon and "HTTPS" in the address bar and breathe a sigh of relief. While essential, that green lock is merely the beginning of true website security.
HTTPS signifies that the connection between your browser and the website's server is encrypted, protecting data in transit. But a truly secure website goes far beyond encrypting data between two points. It's built on a multi-layered defense strategy, addressing vulnerabilities at every level of the application and infrastructure.
So, what are the characteristics of a website you can genuinely trust?
1. Always Uses HTTPS with Strong TLS Protocols
This is the foundational layer, but its proper implementation is crucial.
What it is: HTTPS (Hypertext Transfer Protocol Secure) encrypts the communication between the user's browser and the website's server using TLS (Transport Layer Security, the modern successor to SSL) certificates.
Why it's essential: It prevents eavesdropping, tampering, and message forgery, ensuring that the data you send (like login credentials or credit card numbers) and receive remains private and integral. Modern browsers flag sites without HTTPS as "Not Secure." Crucially, truly secure websites use strong, up-to-date TLS versions (like TLS 1.2 or 1.3), not older, vulnerable ones.
2. Robust Input Validation and Output Encoding
These are fundamental defenses against some of the most common web attacks.
Input Validation: Every piece of data a user submits (forms, search queries, URLs) must be strictly validated before the server processes it. This prevents attackers from injecting malicious code (e.g., SQL Injection, Command Injection) that could manipulate the database or execute commands on the server.
Output Encoding: Any data retrieved from a database or user input that is displayed back on the website must be properly encoded. This prevents Cross-Site Scripting (XSS) attacks, where malicious scripts could be executed in a user's browser, stealing cookies or defacing the site.
3. Strong Authentication & Authorization Mechanisms
Security starts with knowing who is accessing your site and what they are allowed to do.
Authentication:
Strong Password Policies: Enforce minimum length, complexity (mix of characters), and disallow common or previously breached passwords.
Multi-Factor Authentication (MFA): Offer and ideally mandate MFA for all user accounts, especially administrative ones. This adds a critical layer of security beyond just a password.
Secure Session Management: Use secure, short-lived session tokens, implement proper session timeouts, and regenerate session IDs upon privilege escalation to prevent session hijacking.
Authorization: Implement the principle of least privilege. Users should only have access to the data and functionalities strictly necessary for their role. Role-Based Access Control (RBAC) is key here, ensuring a customer can't access admin features, for instance.
4. Regular Security Updates & Patch Management
Software is complex, and vulnerabilities are constantly discovered.
Continuous Patching: The website's underlying operating system, web server software (e.g., Apache, Nginx), Content Management System (CMS) like WordPress or Drupal, plugins, themes, and all third-party libraries must be kept up-to-date with the latest security patches.
Why it's essential: Unpatched vulnerabilities are a common entry point for attackers. A truly secure website has a rigorous system for identifying and applying updates swiftly.
5. Comprehensive Error Handling & Logging
What happens when things go wrong, or suspicious activity occurs?
Generic Error Messages: Error messages should be generic and not reveal sensitive system information (e.g., database connection strings, file paths, or specific error codes) that attackers could use to map your system.
Robust Logging: All security-relevant events – failed login attempts, successful logins, administrative actions, suspicious requests, and critical system events – should be logged. These logs should be stored securely, centrally, and monitored in real-time by a Security Information and Event Management (SIEM) system for anomalies and potential attacks.
6. Secure Development Practices (SDL)
Security isn't an afterthought; it's built in from the ground up.
Security by Design: A truly secure website is born from a development process where security considerations are embedded at every stage – from initial design and architecture to coding, testing, and deployment. This is known as a Secure Development Lifecycle (SDL).
Code Reviews & Testing: Regular security code reviews, static application security testing (SAST), and dynamic application security testing (DAST) are performed to identify and fix vulnerabilities before the code ever goes live.
7. Web Application Firewall (WAF)
A WAF acts as a protective shield for your website.
What it does: It monitors and filters HTTP traffic between the web application and the internet. It can detect and block common web-based attacks (like SQL injection, XSS, DDoS, brute-force attempts) before they reach the application.
Why it helps: It provides an additional layer of defense, especially useful for mitigating new threats before a patch is available or for protecting against known vulnerabilities.
8. Data Encryption at Rest
While HTTPS encrypts data in transit, data stored on servers needs protection too.
Sensitive Data Encryption: Databases, file systems, and backups containing sensitive user information (passwords, PII, financial data) should be encrypted.
Why it's important: Even if an attacker manages to breach your server and access the underlying storage, the data remains unreadable without the encryption key, significantly mitigating the impact of a breach.
9. Regular Security Audits & Penetration Testing
Proactive testing is key to finding weaknesses before malicious actors do.
Vulnerability Scanning: Automated tools scan your website for known vulnerabilities.
Penetration Testing (Pen-Testing): Ethical hackers simulate real-world attacks to exploit vulnerabilities, test your defenses, and assess your overall security posture. These should be conducted regularly and after significant changes to the website.
10. Clear Privacy Policy & Data Handling Transparency
While not a strictly technical security feature, transparency builds user trust and demonstrates responsible data stewardship.
What it includes: A clear, easily accessible privacy policy explaining what data is collected, why it's collected, how it's used, how it's protected, and who it's shared with.
Why it matters: It shows commitment to data security and respects user privacy, a fundamental aspect of a truly trustworthy online presence.
A truly secure website is not a static state achieved by checking a few boxes. It's a continuous commitment to vigilance, proactive measures, and a deep understanding that security is an ongoing process involving people, technology, and robust policies. In a world where digital trust is paramount, building and maintaining a genuinely secure website is an investment that pays dividends in reputation, customer loyalty, and business continuity.
0 notes
Text
StoreGo SaaS Nulled Script 6.7

StoreGo SaaS Nulled Script – Build Powerful Online Stores with Zero Cost If you're looking for a professional, cost-effective, and user-friendly way to launch an online store, the StoreGo SaaS Nulled Script is your ultimate solution. This dynamic script offers a fully-featured eCommerce experience, empowering businesses of all sizes to create stunning digital storefronts without investing in expensive software or subscriptions. What is StoreGo SaaS Nulled Script? StoreGo SaaS Nulled Script is a premium online store builder that allows users to create, manage, and scale eCommerce businesses with ease. The nulled version provides all premium features for free, making it accessible for entrepreneurs, freelancers, and agencies who want to launch professional web stores without financial barriers. Unlike traditional eCommerce platforms that require hefty licensing fees, this script is a fully customizable and open-source alternative. With zero limitations, it’s a fantastic option for users who want complete control over their store’s design, layout, payment methods, and more. Technical Specifications Script Type: PHP Laravel Framework Database: MySQL Frontend Framework: Bootstrap 4 Server Requirements: PHP 7.3+, Apache/Nginx, cURL, OpenSSL Payment Gateways Supported: Stripe, PayPal, Razorpay, Paystack, and more Multi-Store Capability: Yes Top Features and Benefits Multi-Tenant SaaS Architecture: Each user can have a fully independent online store under your main platform. Drag-and-Drop Store Builder: Design pages effortlessly without coding. Real-Time Analytics: Get insights into orders, revenue, and customer behavior. Integrated Payment Solutions: Accept online payments globally with multiple secure gateways. Subscription Packages: Create various pricing plans for your users. Product & Inventory Management: Manage stock, variants, SKUs, and more from one dashboard. Use Cases Whether you're starting a new eCommerce business or offering SaaS services to clients, the StoreGo SaaS Nulled Script adapts perfectly to different business models. Ideal for: Freelancers offering eCommerce development services Agencies launching SaaS-based online store platforms Small business owners looking to sell online without third-party dependencies Digital marketers creating customized product landing pages Installation Guide Setting up the StoreGo SaaS Nulled Script is quick and seamless: Download the script package from our website. Upload it to your server via cPanel or FTP. Create a MySQL database and user. Run the installer and follow the on-screen instructions. Log in to the admin panel and start customizing your platform! For advanced configurations, detailed documentation is included within the script package, ensuring even beginners can get started with minimal technical effort. Why Choose StoreGo SaaS Nulled Script? By choosing the StoreGo SaaS Nulled Script, you're unlocking enterprise-level features without paying a premium. Its modern UI, powerful backend, and full customization capabilities make it a must-have tool for building eCommerce platforms that perform. Plus, when you download from our website, you get a clean, secure, and fully functional nulled version. Say goodbye to restrictive licensing and hello to freedom, flexibility, and profitability. FAQs Is the StoreGo SaaS Nulled Script safe to use? Yes, the script available on our website is thoroughly scanned and tested to ensure it’s clean, stable, and ready for production. Can I use this script for multiple clients? Absolutely! The multi-tenant feature allows you to offer customized storefronts to various clients under your own domain. Does this script include future updates? While this is a nulled version, we frequently update our repository to include the latest stable releases with new features and security patches. How do I get support if I face issues? Our community forum and documentation are excellent resources. Plus, you can always reach out to us via our contact form for guidance.
Download Now and Start Selling Online Today! Get started with the StoreGo SaaS and experience unmatched control and performance for your eCommerce venture. Download it now and build your digital empire—no license needed, no hidden costs. Need more tools to supercharge your WordPress experience? Don’t forget to check out our other offerings like WPML pro NULLED. Looking for a stylish WordPress theme? Get Impreza NULLED for free now.
0 notes