#yubico
Text

Xác thực 2 yếu tố là phương pháp cho phép các dịch vụ máy tính và người dùng sử dụng nhiều phương pháp xác thực đề định danh cũng như bảo vệ tài khoản
Yubikey là một loại khoá bảo mật được cung cấp bởi công ty Yubico. Đây là loại khoá bảo mật vật lý phổ biến bậc nhất của thị trường, thường được sử dụng để xác thực hai yếu tố (2FA) và xác minh không cần mật khẩu, giúp người dùng đăng nhập tài khoản thuận tiện hơn mà vẫn đảm bảo tính bảo mật.
0 notes
Text
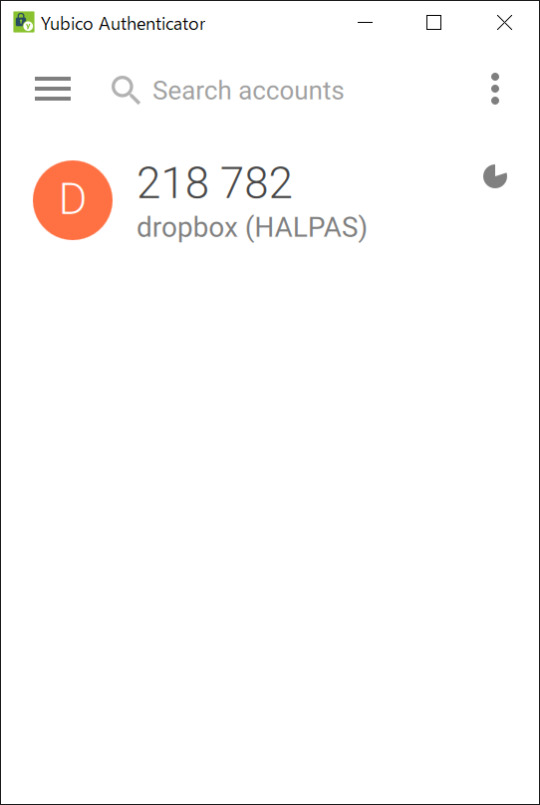
YubiKeyをGoogle Authenticator代わりに使用する方法
YubiKeyを、Google Authenticator(Google 認証システム)やMicrosoft Authenticatorのようなワンタイムパスワード生成アプリとして使用できる「Yubico Authenticator」のご紹介です。
(more…)
View On WordPress
#Authenticator#Dropbox#Google Authenticator#Microsoft Authenticator#TOTP#Windows#Yubico#YubiKey#セキュリティ#タイムベースドワンタイムパスワード#ワンタイムキー
0 notes
Photo

D3FC0N Swag Reveal 📣 We will have these new #DC30 #YubiStyle covers available at #DEFCON30. Come see us at the Keyport booth in the vendor room to get a set for your #YubiKey ⇨ Swipe for more ⇨ . . . #d3fc0n #lasvegas #defconswag #defconvendor #yubico #edcgear #defcon #everydaycarry #edc #keyport #keyorganizer #edccommunity #keyportpivot2 #securitykey #yubicoxkeyport (at Las Vegas, Nevada) https://www.instagram.com/p/CgnE9JQPzqO/?igshid=NGJjMDIxMWI=
#dc30#yubistyle#defcon30#yubikey#d3fc0n#lasvegas#defconswag#defconvendor#yubico#edcgear#defcon#everydaycarry#edc#keyport#keyorganizer#edccommunity#keyportpivot2#securitykey#yubicoxkeyport
0 notes
Video
youtube
Yubico Authenticator vs Google Auth vs Twilio Authy - BEST 2FA App in 2024
0 notes
Text
Yubikey.Support for 2-Factor Verification | Yubikey Support
Check out YubiKey's strong support for 2-factor verification. Use hardware-based authentication to increase your online security. YubiKey Support offers dependable setup and troubleshooting support. Your route to better online safety.
With YubiKey's capability for 2-factor verification, security is enhanced. Use this reliable hardware-based solution to protect your internet presence. Get timely support for installation and troubleshooting to guarantee a secure digital experience. Your ideal ally in security.
#yubico support#yubikey support#yubikey supported#yubikey supported services#yubico customer service
0 notes
Text
How To Wipe Out All The Data On An YubiKey In One Gesture

What happens when I touch my YubiKey?
When you touch your YubiKey, it sends a very weak 5v signal to your computer. The signal is only strong enough to trigger a response from the YubiKey. You can think of this like an electric doorbell: A doorbell sends out a short burst of high-voltage AC power when it's pressed; when the low-voltage AC voltage hits the contacts of the receiver (which may be an electromagnet), it causes them to momentarily close and send out DC power that pushes through wires back to your house's main circuit breaker box which then turns on an LED lamp as part of an interlock system that prevents any power from coming through unless someone presses the doorbell button first.
Does YubiKey work without the Internet?
Yes, YubiKey Support can be used without any internet connection. The YubiKey has all the data that you need to be stored on the device in an encrypted manner. Only when you want to login into a site or service will it ask for the data from your key and then it decrypts it using a password or PIN which you entered earlier.
What is the difference between YubiKey and the security key?
YubiKey does not use public-key cryptography. Instead, it creates a challenge-response code that is unique to the device and thus cannot be spoofed. YubiKey is more effective than standard passwords and PINs at mitigating phishing, man-in-the-middle attacks, replay attacks, and other situations where a thief can intercept or steal your credentials.
How many passwords can YubiKey hold?
Yubico's YubiKey can hold up to 32 unique credentials, in addition to a single PIN. If you use Yubico apps and services that require more than 32 credentials, your master password can be used as an override to let you switch between them.
How do I use YubiKey for personal use?
YubiKey for personal use is designed for the everyday user that wants to protect and secure their online accounts. YubiKey can be used to replace passwords, 2FA codes, or other secrets to help prevent unauthorized access.
YubiKey is a security key that protects you against phishing and hijacking. With FIDO standards-based strong authentication, it can be used to securely login to your favorite websites, computers, and applications.
#yubico support#yubikey support#how does yubikey work#yubico customer service#yubikey supported services
0 notes
Text
Clé de sécurité Yubico NFC
Si vous souhaitez protéger vos comptes en ligne, il sera important de vous y connecter correctement et d'empêcher tout accès indésirable. La clé de sécurité Yubico NFC est l'une des options matérielles les plus recherchées qui peut être facilement intégrée au système. Choisissez la meilleure clé de sécurité qui aide à prévenir le vol des détails du compte en ligne et ainsi garder les informations privées.
Rendez nous visite:- https://yubikey-shop.eisn.fr/yubikey-bio
Lire Aussi le blog:- https://medium.com/@webeisn/comment-prot%C3%A9ger-lacc%C3%A8s-aux-comptes-en-ligne-avec-la-cl%C3%A9-de-s%C3%A9curit%C3%A9-yubico-nfc-669e2ec77e58
0 notes
Text
Les meilleurs systèmes de sécurité pour la protection contre les violations
L'authentificateur de bureau Yubico permet la meilleure utilisation des systèmes de sécurité pour la protection contre toutes sortes de violations. La prévention des interférences extérieures vous aidera à garder les motivations commerciales au premier plan et ainsi à obtenir les résultats souhaités. La sélection des clés de sécurité peut être difficile et donc prendre l'appel en fonction des fonctionnalités pertinentes. Rendez-nous visite sur : https://yubikey-shop.eisn.fr/
0 notes
Note
what's a good authenticator app to use? and how is it more secure than using sms? I keep seeing horror stories in the news about "such and such app is being used to download malware to your phone!" so how do you figure out what's safe?
i just use google authenticator, i think iphones have some kind of authenticator built into ios
microsoft authenticator and authy are also fine
i just found out yubico authenticator exists, i assume that's fine also
at work i use this browser extension because i'm lazy
proton pass and i think bitwarden technically have the ability to generate 2fa codes but whether you consider having those in your password manager to be missing the point is up to you
tl;dr sim swapping exists and overall sms just isn't a secure medium because it wasn't designed to be
a lot of banks and government websites don't actually give you the option to use anything but sms, which are the places i least want to use sms, so you can imagine how i feel about that
#original#however many of them let me use my google voice number. probably unsafe but also fuck you.
172 notes
·
View notes
Quote
不明な Wi-Fi ネットワークには接続しないでください
空港や駅など交通量の多い旅行エリアでの公衆 Wi-Fi ネットワークの使用は便利ですが、リスクも伴います。 NordVPN が実施した調査によると、旅行者の 4 人に 1 人が海外旅行中に公共 Wi-Fi の使用中にハッキングされた経験があることがわかっています。したがって、身を守る最善の方法の 1 つは、公共 Wi-Fi をまったく使用しないことです。
ユーザーの同意なしにデバイスが最初に利用可能な Wi-Fi ネットワークに接続しないようにするには、設定で Wi-Fi 自動接続を無効にすることができます。これにより、潜在的な悪意のある攻撃者にさらされる可能性が減り、ユーザーのアクセス制御が強化されます。電話の設定。
携帯電話をモバイル ホットスポットとして使用すると、不正なネットワークに接続するリスクがほとんど、またはまったくなくなることを意味します。 これは、公共 Wi-Fi に依存したくない場合、特に何かをすばやく行う必要がある場合に最適なオプションです。
使用していないときはデバイスをシャットダウンする
空港や税関の保安検査を通過するとき、または放置する必要があるときは、コンピューターと携帯電話の電源を切ります (スリープまたは休止状態ではありません)。 これにより、フルディスク暗号化などのデバイスのハードウェア セキュリティ機能を最大限に活用でき、デバイスの制御を失った場合にデータを保護できます。
不明な充電ポートに接続しないでください
公共またはホテルの USB ポートや Lightning ポート、信頼できないソースからのケーブルや USB デバイスを直接使用しないでください。 このようなサイバー攻撃は一般的ではありませんが、発生する可能性はあります。 データ ブロッカーや電源バンクからのデイジー チェーンを使用して、悪意のあるポートやケーブルへの露出を制限できます。
ロック画面の表示を制限する
私たちの多くは、テキスト メッセージの内容やカレンダーの予定など、モバイル デバイスのロック画面上で意図した以上の個人情報を共有しています。 設定を調整することで、ロックを解除せずに携帯電話で利用できるものを制御するための高レベルの情報のみを共有するようにすることができます。 誰かが通りかかってあなたの携帯電話をのぞき見した場合、ロック画面を使用して数秒間に収集できる情報の量を制限できます。
Bluetooth 接続を確認してください
ベスト プラクティスとして、使用しないときは必ず Bluetooth をオフにしてください。 オンにすると、悪意のある攻撃者が以前に接続したデバイスを発見し、デバイスにアクセスできる可能性があります。
Bluetooth 設定でデバイスを「検出可能」モードではなく「非表示」モードに設定することもできます。これにより、未知のデバイスが Bluetooth 接続を見つけられないようにすることができます。 また、不明なデバイスが公の場でコンテンツを共有できないように、必ず Airdrop 設定を「連絡先のみ」に調整してください。
休暇中に安全を確保するための旅行の安全に関するヒント - Yubico
6 notes
·
View notes
Text
Yubico Security Key – Two Factor Authentication USB Security Key, Fits USB-A Ports – Protect Your Online Accounts with More Than a Password, FIDO Certified USB Password Key
http://i.securitythinkingcap.com/T3xrjr
2 notes
·
View notes
Text
6 notes
·
View notes
Text
【買ったらすべき】YubiKeyが本物かチェックできる「YubiKey Verification」
購入したYubiKeyが本物であるかチェックできる公式ツール「YubiKey Verification」のご紹介です。
(more…)

View On WordPress
0 notes
Text
Setup Yubikey 2FA on Debian 11
So you want to harden security by enabling two-factor authentication using Yubikey.
WARNING: VERY REAL RISK OF LOCKING YOURSELF OUT! MAKE SURE YOU KNOW WHAT YOU'RE DOING AND HAVE BACKUPS!
This guide will set up the so-called Challenge Response OTP mode. The online mode which require access to internet + Yubikey registration is out of scope.
Read the whole guide and then proceed step by step.
In a separate terminal get root console and keep it open in case you need to rollback changes (don't do anything in it):
$ sudo -s
Install Yubikey personalization package:
$ sudo apt install yubikey-personalization
Install "libpam-yubico" package:
$ sudo apt install libpam-yubico
Configuration of the Yubico PAM module will be requested. Enter this (do not enable anything!):
mode=challenge-response
Check installed package contents (will be useful later):
$ dpkg -L libpam-yubico
The main document of interest is
/usr/share/doc/libpam-yubico/Authentication_Using_Challenge-Response.adoc.gz
Read it as this guide is heavily inspired on it.
Plug in your Yubikey now.
Setup the slot #2 of the Yubikey for the OTP challenge-response mode:
$ ykpersonalize -2 -ochal-resp -ochal-hmac -ohmac-lt62 -oserial-api-visible
This should generate a challenge-<digits> file in ~/.yubico/ directory.
This file is critical and should be protected.
$ chmod 600 ~/.yubico/challenge-<digits>
Return to libpam-yubico configuration and enable Yubikey support (first choice):
$ sudo dpkg-reconfigure libpam-yubico
Make sure the mode string is entered as shown above, asterisk is set next to Yubikey support and hit <Ok>.
Check PAM configuration:
$ cat /etc/pam.d/common-auth
You should see a line:
auth required pam_yubico.so mode=challenge-response
Now run the PAM update utility (read the man page):
$ sudo pam-auth-update
Open a new terminal and try running a sudo command:
$ sudo echo "It works!"
Enter your user password and notice green LED on the Yubikey lighting up. Remove the Yubikey, open another terminal and try to log in - it should fail.
You now have hardened system which requires two-factor authentication!
To troubleshoot issues, use the following mode line:
mode=challenge-response debug
Follow the same steps of the guide. Each sudo call will get a verbose log written to the console.
To uninstall, edit "/etc/pam.d/common-auth" to its previous state. Run pam-auth-update. Check log in works without a Yubikey.
2 notes
·
View notes
Text

Yubikey.Support for 2-Factor Verification | Yubikey Support
Experience heightened security with YubiKey's 2-factor verification support. Safeguard your online presence using this robust hardware-based solution. Receive prompt assistance for setup and troubleshooting, ensuring a secure digital journey. Your ultimate security companion.
Discover the power of YubiKey support for seamless 2-factor verification. Enhance your online security with this hardware-based authentication solution. Get quick and reliable assistance for setup and troubleshooting. Your key to a safer digital experience.
#yubikey support#yubikey support Service#yubikey supported#yubikey supported services#yubico customer service
0 notes
Text
FabSec05 - Security Posture
Tempo fa avevo pubblicato un paio di post legati all’utilizzo delle password e all’uso che ne facciamo. Il primo era questo, mentre il secondo lo trovate qui
L'altro giorno mi sono imbattuto in un articolo di Daniel Miessler, un esperto di sicurezza informatica che seguo con interesse. L’articolo contiene una sorta di classificazione della sicurezza e gestione delle nostre password, riassunta da questo diagramma:

Il diagramma mostra quanto debole o robusto possa essere il modo in cui utilizziamo le password tutti i giorni. Si parte da
1 = password condivise = male, molto male!
e si arriva a
8 = utilizzo di un token fisico, tipo Yubico o Thetis = well done!
Sul lato destro è anche presente una lista di attacchi associati a ciascuna “security posture”, attacchi che sono obbligati a diventare sempre più sofisticati man mano che si sale.
Il diagramma è un buono strumento per incentivare le persone a migliorare la propria sicurezza (chi non vuole scalare una classifica?! :), perciò ho pensato fosse un ottimo complemento a quella discussione.
Per chi fosse interessato all’articolo completo, eccolo qui
#infosec#infomation security#fabsec#password#password management#sicurezza#sicurezza informatica#cyber#cybersecurity
4 notes
·
View notes