#AWS Security
Explore tagged Tumblr posts
Text
How to download the PEM file from aws ec2
Learn how to download and secure a PEM file from AWS EC2. Step-by-step guide, best practices, and troubleshooting to prevent lost key issues.
If you are working with AWS EC2 instances, you need a PEM file (Privacy Enhanced Mail) to connect securely via SSH. However, once an EC2 instance is launched, you cannot download the PEM file again from AWS. This guide will show you how to download and secure your PEM file correctly. Table of Contents Introduction to PEM Files Importance of PEM Files in AWS EC2 How to Download a PEM File from…
0 notes
Text

FNAF Vanny and Michael if they met as teens
#myart#chloesimagination#comic#fnaf#five nights at freddy's#fnaf fanart#fnaf vanny#fnaf vanessa#michael afton#security breach#fnaf 4#A good portion of folks wanted teen Michael and Vanny to meet#SO finally I delivered on that request 🩵#TBH it was really fun to draw them too#they kinda just match each other#Michael would definitely try and bully Vanny#but I wanna believe Vanny as a teen could talk back BAHA#So stunlocks him HFHFHH#they’d bump heads at first but I think they could be friends#they’d still pick on each other still though#they are both lonely kids with awful dads so they’d get each other#maybe I’ll draw more of them we’ll see
8K notes
·
View notes
Text
Safeguarding Your Assets: Exploring Cloud Security on AWS
In the realm of modern technology, cloud computing has emerged as a game-changer, offering unparalleled flexibility, scalability, and efficiency to businesses worldwide. However, as organizations increasingly rely on cloud services to store sensitive data and run critical applications, ensuring robust security measures becomes paramount. In this article, we'll delve into the intricacies of cloud security on Amazon Web Services (AWS) and explore the best practices for safeguarding your assets in the cloud.
Understanding Cloud Security on AWS: Amazon Web Services (AWS) is a leading cloud computing platform that provides a vast array of services, ranging from compute and storage to networking and security. While AWS offers a highly secure infrastructure, it's essential for organizations to implement additional security measures to protect their data and applications from potential threats.
Key Security Features of AWS: AWS offers a comprehensive set of security features and tools to help organizations build a secure and compliant environment in the cloud. Some of the key security features provided by AWS include:
Identity and Access Management (IAM): IAM allows organizations to manage user identities and access permissions for AWS resources. With IAM, organizations can create and manage user accounts, assign permissions, and enforce multi-factor authentication to enhance security.
Network Security: AWS provides various networking features, such as Virtual Private Cloud (VPC), Security Groups, and Network Access Control Lists (NACLs), to secure network traffic and control access to resources. These features enable organizations to create secure network architectures and enforce firewall rules to protect against unauthorized access.
Data Encryption: AWS offers robust encryption capabilities to protect data both at rest and in transit. Organizations can use services like AWS Key Management Service (KMS) to manage encryption keys and encrypt data stored in AWS services such as Amazon S3, Amazon RDS, and Amazon EBS.
Compliance and Governance: AWS adheres to industry-standard security certifications and compliance frameworks, such as SOC 2, ISO 27001, and HIPAA, to ensure the security and privacy of customer data. Additionally, AWS provides services like AWS Config and AWS CloudTrail to monitor and audit AWS resource configurations and API activity for compliance purposes.
Best Practices for Cloud Security on AWS: While AWS offers robust security features, implementing best practices is essential to enhance the security posture of your cloud environment. Some of the key best practices for cloud security on AWS include:
Implementing Least Privilege Access: Follow the principle of least privilege to grant users only the permissions they need to perform their job roles. Use IAM policies to enforce granular access controls and regularly review permissions to prevent unauthorized access.
Securing Data with Encryption: Encrypt sensitive data both at rest and in transit using strong encryption algorithms and key management practices. Utilize AWS services like AWS KMS and AWS CloudHSM to manage encryption keys securely.
Enforcing Network Security Controls: Configure security groups and network ACLs to control inbound and outbound traffic to your AWS resources. Use VPC flow logs to monitor network traffic and detect potential security threats.
Monitoring and Logging: Enable logging and monitoring features like AWS CloudTrail, Amazon CloudWatch, and AWS Config to monitor resource activity, detect security incidents, and ensure compliance with security policies.
Regularly Updating and Patching: Keep your AWS resources and software up to date by applying security patches and updates regularly. Utilize AWS services like AWS Systems Manager to automate patch management and ensure timely updates across your environment.
Conclusion: In conclusion, cloud security on AWS is a shared responsibility between AWS and the customer. While AWS provides a secure and compliant infrastructure, organizations must implement additional security measures and best practices to protect their data and applications in the cloud. By understanding the key security features of AWS and following best practices for cloud security, organizations can build a robust security posture and mitigate potential security risks in the cloud.
0 notes
Video
youtube
How To Configure Account | Create a Billing Alarm | Hands On
Video Link: https://youtu.be/yK4jFUope9M Channel : https://www.youtube.com/@cloudolus Playlist-01: https://www.youtube.com/playlist?list=PLBurDmQJIVqwYhjHYL08c8i5M1EQezUAI Playlist-02: https://www.youtube.com/playlist?list=PLBurDmQJIVqyKmDftrSCYMoZhpaqykJJw Playlist-03: https://www.youtube.com/playlist?list=PLBurDmQJIVqzT4xtZdJeniQVyWaSfb6r8 Playlist-04: https://www.youtube.com/playlist?list=PLBurDmQJIVqyMiO0qbLl4JYdNLBWYprs7 Playlist-05: https://www.youtube.com/playlist?list=PLBurDmQJIVqxshpWQ01-92hjLEzkNh6dU *****************************
***************************** To configure an AWS billing alarm, you need to set up Amazon CloudWatch Alarms. These alarms can be triggered based on defined thresholds, allowing you to monitor your AWS usage and get notified when your estimated charges exceed a certain limit. Here's a step-by-step guide on how to configure an AWS billing alarm:
Step 1: Sign in to the AWS Management Console Go to the AWS Management Console and sign in to your AWS account.
Step 2: Navigate to the CloudWatch Console In the AWS Management Console, find and click on the "Services" dropdown. Under the "Management & Governance" section, click on "CloudWatch." Step 3: Access Billing Metrics In the CloudWatch console, find and click on "Billing" in the left navigation pane. Select "Billing" from the drop-down menu.
Step 4: Create a Billing Alarm In the "Billing" dashboard, click on the "Create Alarm" button.
In the "Create Alarm" wizard, you'll see a list of metrics. Select the "Total Estimated Charge" metric.
Choose the appropriate statistic, such as "Maximum."
Set the conditions for the alarm. For example:
Threshold Type: Static Whenever: "Total Estimated Charge" is greater than [your specified amount]. Define actions for the alarm. This includes specifying an SNS (Simple Notification Service) topic to notify you when the alarm is triggered. If you haven't set up an SNS topic, you'll need to create one.
Provide a name and description for your alarm.
Click "Create Alarm" to save your configuration.
Step 5: Set Up Notifications If you haven't created an SNS topic:
Open the SNS console in a new tab. In the left navigation pane, click on "Topics" and then "Create topic." Provide a name and display name for your topic. Under "Access Policy," choose "Advanced" and add a policy that allows CloudWatch to publish to this topic. Click "Create topic." Go back to the CloudWatch console.
In the left navigation pane, click on "Alarms." Select your alarm from the list. Click the "Actions" tab. Under the "Actions" section, click "Add notification." Select the SNS topic you created. Click "Update Alarm."
Step 6: Test the Alarm You can test the alarm by intentionally exceeding the billing threshold you set. This will trigger the alarm and send a notification to the specified SNS topic.
By following these steps, you've configured an AWS billing alarm to monitor your estimated charges and receive notifications when they exceed a defined limit. Adjust the alarm threshold and notification settings based on your specific needs and budget considerations.
***************************** Follow Me: Facebook Page Link: https://www.facebook.com/cloudolus/ Facebook Group Link: https://www.facebook.com/groups/cloudolus LinkedIn Group Link: https://www.linkedin.com/groups/14347089/ Instagram Link: https://www.instagram.com/cloudolus/ Twitter Link: https://twitter.com/cloudolus Pinterest Link: https://www.pinterest.com/cloudolus/ Tumblr Link: https://www.tumblr.com/blog/cloudolus YouTube Link: https://www.youtube.com/channel/UCnOIfrUDCOlz5RUVKFTkktQ ***************************** #freecourse #free #youtube #DevOps #ClouDolus #awstutorial #awstutorialforbeginners #AWSBangla
aws,amazon web services,cloud computing,aws cloud,aws tutorial for beginners,aws tutorial,ClouDolus,amazon aws tutorial,AWS,aws bangla,free,free aws cloud,free course,devops,AWS certification,AWS SAA-C03,aws certified solutions architect associate,pass aws solutions architect,aws solutions,courses,certifications,aws certification path,aws full course tutorial,aws certification training,youtube,exam preparation,Configure Account,Create a Billing Alarm
#youtube#cloudolus#aws#aws course#aws devops#aws lambda#aws security#aws cloud#aws certification#aws training
0 notes
Text
I never know what to do with the colors. (._. )

#my art#digital art#ibispaintx#art dump#fnaf daycare attendant#fnaf security breach#sundrop#this is awful
297 notes
·
View notes
Text
As per usual, it’s DP crossover with (probably) DC, although you could probably adjust it for other fandoms
ANYWAYS
A little kid and his mother are trick or treating in another city, perhaps at some kind of event rather than knocking on doors, and the kid is dressed as Phantom. It’s very adorable, with his little ghost-shaped bucket and clearly homemade and already stained costume—listen, white only works if you can just fly over street grime or phase it out of your clothes—and his slightly I’ll fitting wig. The kid is SO happy to be out and about dressed as his favorite, and maybe even showed it off to Phantom back in Amity Park before his family left.
The hero, insert whoever you wish here, is probably in civvies and just enjoying the event. The kid, meanwhile, is so glad when people ask who he is so he can explain, and so- the hero gets to hear ALL ABOUT the local town hero who is probably pretty small time despite the kid’s clearly exaggerated stories. The hero certainly never heard of him, but the kid’s mom confirms that Phantom really was the town hero, despite some mixed reviews of the poor guy.
“Did you manage to show him your costume?” the hero asks.
“Yeah! We went down to the cemetery to leave flowers and I got to show him my costume.”
Wait. Cemetery? Maybe it was part of theme, because Phantom had to be named that for a reason, but… it sounded like…
The kid ignores the suddenly VERY still hero and instead turns to his mom. “Momma, do you think we should bring him candy? He doesn’t get to trick or treat like we do, and I can work super hard to get him a bunch!”
The kid’s mom just smiles. “We could, but maybe we should bring him something homemade. I bet he’d like something more filling, teen boys like him have a hollow leg.”
The kid wrinkles his nose. “Like Vernie with the pizza bagels?”
“Like your cousin, yes. We can make some cinnamon rolls and take them to his memorial, maybe bring some of the apples from your grandpa’s garden…”
The hero is pretty much forgotten as the two-part family wanders off, not quite intentionally forgetting the hero is there so much as the hero somewhat accidentally ended the conversation when they just froze and didn’t ask anything further.
Not that the hero didn’t want to. But they’d learn something very serious.
One—there was a small town hero they’d never heard of. Two—that hero was apparently a teen. Third—most pressingly, the teen hero was both beloved enough to have kids dressing up as him and dead enough to have a grave.
This… might require some phone calls.
#dpxdc#danny phantom crossover#meanwhile Danny. sitting on a giant marble slab that has the most ridiculous gag gifts a ghost could ever ask for#he’s just like Oh Sweet Cinnamon Rolls!#he would try to convince people to bring him nasty burger but while val has MOSTLY gotten over her vindictive anger at Phantom DOES decide#that she’s gonna be petty and add cilantro to everything#because Danny has the cilantro soap gene#jokes on her he’ll still eat it#Danny likes his little memorial in the grave. it helps settle him sometimes. also he’s gotten to know the security guards for the cemetery#they’re fun. a bit morbid. they LIKE his jokes so you can stuff it JAZZ#MEANWHILE the hero. Whomstever they are but like 90% of you are thinking either batfam or Justice league#are having just. a TOUCH of a crisis#now they gotta figure out where the kid and his mom are from without either of them figuring out#dealer’s choice on what the GIW and why Amity Park isn’t on the radar#I’ll add my two cents bc when don’t I but I’m by and large not like… dictating this? anyways#I like making the GIW just a BIT more incompetent or just having some massive flaws as an organizational group#so they keep forgetting to tell people to not LEAVE and to keep quiet#average amity Parker if the GIW tried this anyways: aw that’s cute. anyways-#and if it’s dc I guess you need to figure out how the jl never found out. so#i mean there’s a LOT of heroes and cities in dc#and amity park is just lost to the noise or. bc Fenton bad luck#every time Danny tried to call. the jl had some insane disaster and or their systems were down#he eventually figured he might actually be cursed- jury’s still out on that -and he’s saving lives by just handling it himself#he can handle rhe metaphorical mega thunderstorms if it means he doesn’t accidentally summon a fucking tsunami to hit the planet ya know?#the kid and the mom have no idea that what they said was Odd#they are just so used to it. amity park already was using death puns and had an. interesting history and relation with death#even BEFORE there was a dead kid flying around in his white gogo boots
825 notes
·
View notes
Text

sad newt doodle 4 tonite. the scar on his cheek is that nasty wound he has inside the cell at the end of uprising
#hc that the precursors were very uncooperative during an interrogation and one of the guards pistol whipped him#that guy better watch out though . hermann just watched the security footage and is on the Move....#pacific rim#newton geiszler#pacrim#my art#starting to feel a lil self conscious about how much ive posted in this tag oh god. huehrg. its fine my anxiety has just been really awful
219 notes
·
View notes
Text

#HELLO CHAT......#my lappalter pulls were so bad i had to draw an offering#180 pulls deep rn and i have 2 suzumoms and 1 qiubai o(-(#nyway if anyone reads these#i hope u are doing well !!#mia bc i am abt to graduate + recently secured a job + am touching (a little) grass#also social media gives me awful anxiety i apologize#blue poison#bloopy#lappland#lappland the decadenza
330 notes
·
View notes
Text
Random things i didn't really like, but. Why not




Ok, i lied, i really like the last doodle
#fnaf#five nights at freddy's#fnaf gregory#fnaf cassie#fnaf tony#tony becker#fnaf ellis#fnaf vanessa#fnaf amelia#look. it's supposed to be her#fnaf security breach#fnaf sb#fnaf dlc ruin#fnaf ruin#fnaf ggy#ggy#fnaf tftp#I have no clue what they saw btw#heehee#I wanted to practice emotions but they came out awful 😭#It was fun though#doublestar duo#my art
766 notes
·
View notes
Text




eclipse got the star and immediately went I. Have. To Touch. People.
#awful wretched creature /pos#tsams eclipse#tsams#sun and moon show#tsbs#the security breach show#chris flemming voice hes been stranded in the wilderness of suns head for too long hes forgotten how to act like a person#and kcs lab#im so glad hes around people now
423 notes
·
View notes
Text
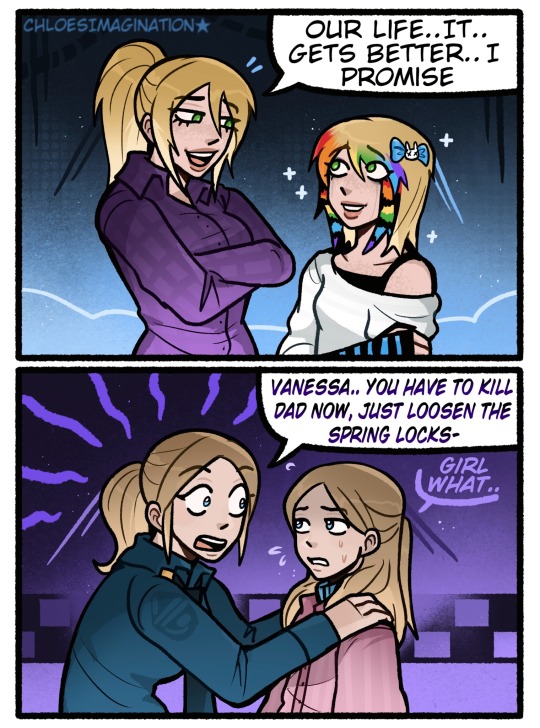
The FNAF Vanessas meet their younger selves..
#myart#chloesimagination#comic#fnaf#five nights at freddy's#fnaf vanny#fnaf vanessa#vanessa shelly#vanessa afton#fnaf movie#security breach#fnaf fanart#MORE SCENE VANNY 🩵🩵🩵#also this is a semi sequel to the Mikes ver I made#seeing I think the Vanessas deserve the funny too 😤#I like to think Vanny would tell her younger self white lies#she knows at that age she just wanted to know life would get better for her#seeing teen her was stuck living with her awful father#Vanessa’s life does get hard again as an adult but.. SINCE HW2 I think she’s in a better place#finally stood up to her abuser and all so it does get better#WHILE MOVIE VANESSA …#bit more manic here BAHAH#listen if younger Vanessa loosen screws on her fathers suit#would anyone even know 🙏🏾#she could get away with it-#Movie Vanessa of course would want to prevent things anyway she can#the Afton kids always being a lil crazy is so real
10K notes
·
View notes
Text
Top 10 Effective Practices To Secure Application Modernization On AWS
This is where AWS Cloud steps in, helping businesses upgrade their application portfolios for the future. At every level of the organization, it necessitates careful planning, effective implementation, and readiness to embrace change. Let’s discover the best 10 practices for effective application modernization on the AWS cloud.
#AWS Cloud#Application Modernization#application modernization services#aws security#aws security services#cloud security#cloud computing security#AWS Managed Services Providers#AWS Services#migrate to AWS
0 notes
Text
Exploring Comprehensive Data Protection on AWS
In the digital age, where data is the lifeblood of organizations, ensuring robust data protection measures is paramount.

Amazon Web Services (AWS), a leading cloud service provider, takes on the role of a guardian, offering a suite of comprehensive tools and features to safeguard the confidentiality, integrity, and availability of data hosted on its platform. This in-depth article explores the multifaceted aspects of data protection on AWS, providing insights into the measures and best practices that organizations can employ to fortify their data against potential threats.
I. Introduction
In an era marked by the proliferation of data and the omnipresence of digital assets, the significance of robust data protection cannot be overstated. AWS, as a major player in the cloud computing domain, plays a pivotal role in championing data protection through an array of services and features designed to address the evolving needs and challenges faced by businesses in safeguarding their information.
II. Secure Data Storage and Encryption
A. S3 Data Encryption: Amazon Simple Storage Service (S3), a cornerstone of AWS, provides native encryption capabilities to protect data at rest. Organizations can leverage server-side encryption options, including Amazon S3 Managed Keys (SSE-S3), AWS Key Management Service (SSE-KMS), or even customer-provided keys (SSE-C).
B. EBS Volume Encryption: AWS Elastic Block Store (EBS) volumes, commonly used for storage in EC2 instances, support encryption for data at rest. By enabling EBS volume encryption, organizations add an additional layer of protection to sensitive data stored within these volumes.
III. Network Security and Access Controls
A. Virtual Private Cloud (VPC): AWS VPC allows organizations to create isolated, private networks in the cloud. By defining network architecture, controlling inbound and outbound traffic, and implementing security groups and Network Access Control Lists (NACLs), businesses can establish a secure network environment.
B. Identity and Access Management (IAM): AWS IAM enables organizations to manage user access to AWS resources securely. By defining granular permissions, enforcing the principle of least privilege, and implementing multi-factor authentication (MFA), businesses can ensure that only authorized personnel have access to critical data.
IV. Data Lifecycle Management and Backups
A. Amazon Glacier for Archival: AWS Glacier serves as a cost-effective solution for archival storage. By implementing lifecycle policies, organizations can automatically transition data to Glacier for long-term retention, ensuring compliance with data governance requirements.
B. Amazon RDS Automated Backups: AWS Relational Database Service (RDS) offers automated backups for relational databases. Organizations can configure backup retention periods, enabling point-in-time recovery to restore databases to specific timestamps in case of data corruption or loss.
V. Threat Detection and Monitoring
A. Amazon GuardDuty: GuardDuty is a managed threat detection service that continuously monitors for malicious activity in AWS environments. Leveraging machine learning and anomaly detection, GuardDuty alerts organizations to potential security threats, helping them respond promptly.
B. CloudWatch Logs and Metrics: AWS CloudWatch provides logging and monitoring capabilities to track system and application performance. By monitoring logs and setting up custom metrics, organizations gain insights into activities and potential security incidents, enhancing their ability to detect and respond to threats.
VI. Compliance and Data Governance
A. AWS Key Management Service (KMS): KMS is a fully managed encryption service that assists organizations in meeting data compliance requirements. By centrally managing encryption keys, organizations maintain control over data access and encryption policies, ensuring compliance with regulations.
B. AWS Artifact: AWS Artifact provides on-demand access to compliance documentation, including reports and certifications. Organizations can utilize this resource to verify AWS's adherence to various industry standards and regulations, enhancing their own compliance posture.
VII. Disaster Recovery Planning
A. Amazon S3 Versioning: S3 versioning allows organizations to preserve, retrieve, and restore every version of every object stored in a bucket. By enabling versioning, businesses can safeguard against accidental deletions or modifications, providing a comprehensive backup mechanism.
B. AWS Disaster Recovery Solutions: AWS offers various disaster recovery solutions, such as AWS Backup and AWS Disaster Recovery. These services enable organizations to implement robust backup and recovery strategies, ensuring business continuity in the face of unforeseen events.
VIII. Conclusion
As organizations increasingly migrate their operations to the cloud, the responsibility of safeguarding sensitive data becomes a shared endeavor between businesses and their cloud service providers. AWS, with its extensive array of data protection tools and features, empowers organizations to navigate the complexities of the digital landscape securely. By implementing best practices in secure storage, encryption, access controls, and monitoring, businesses can harness the full potential of AWS while maintaining the confidentiality, integrity, and availability of their critical data. As data continues to be a driving force in the digital transformation journey, the robust data protection measures provided by AWS serve as a pillar of trust for businesses seeking to thrive in the cloud era.
0 notes
Video
youtube
AWS Global Infrastructure | Regions AZs & Edge Locations
Video Link: https://youtu.be/zUyi_zx_cm4 Channel : https://www.youtube.com/@cloudolus Playlist-01: https://www.youtube.com/playlist?list=PLBurDmQJIVqwYhjHYL08c8i5M1EQezUAI Playlist-02: https://www.youtube.com/playlist?list=PLBurDmQJIVqyKmDftrSCYMoZhpaqykJJw Playlist-03: https://www.youtube.com/playlist?list=PLBurDmQJIVqzT4xtZdJeniQVyWaSfb6r8 Playlist-04: https://www.youtube.com/playlist?list=PLBurDmQJIVqyMiO0qbLl4JYdNLBWYprs7 Playlist-05: https://www.youtube.com/playlist?list=PLBurDmQJIVqxshpWQ01-92hjLEzkNh6dU *****************************
***************************** In the context of cloud computing, regions, availability zones (AZs), and edge locations are key concepts associated with the infrastructure of cloud service providers. Let's break down each term:
Regions: Definition: A region is a geographical area in the world where a cloud provider operates data centers. Each region is made up of multiple availability zones. Purpose: Regions allow cloud users to deploy resources in specific locations. This can be chosen based on factors like proximity to end-users, regulatory requirements, and redundancy planning.
Availability Zones (AZs): Definition: An availability zone is essentially a data center, or a cluster of data centers, within a specific region. Each availability zone has its own power, cooling, and networking infrastructure. Purpose: Availability zones are designed to be isolated from each other, providing fault tolerance and high availability. If one availability zone experiences a failure, the others can continue to operate.
Edge Locations: Definition: Edge locations are part of the content delivery network (CDN) infrastructure. They are used to cache and deliver content, such as images, videos, and web pages, to end-users with lower latency. Purpose: Edge locations help improve the performance and reduce the latency of applications by distributing content closer to the end-users. They are typically located in major cities and regions around the world.
In summary: Region is a large geographic area where a cloud provider operates multiple data centers. Availability Zone (AZ) is a data center or a cluster of data centers within a region. Multiple AZs within a region provide redundancy and fault tolerance. Edge Location is part of a content delivery network and is focused on caching and delivering content to end-users with low latency.
These concepts are important for cloud users to understand when designing and deploying applications, as they allow for strategic resource placement and help ensure high availability and performance. Different cloud providers may use slightly different terminology, but the fundamental concepts are similar across the industry.
AWS is a popular cloud service provider with a well-established global infrastructure.
Regions: Example: "US East (Northern Virginia)" Explanation: This is a region provided by AWS, and it represents a geographic area in the northern part of the United States. It includes multiple data centers and is one of the earliest and most frequently used AWS regions.
Availability Zones (AZs): Example: Within the "US East (Northern Virginia)" region, there are three availability zones: us-east-1a, us-east-1b, and us-east-1c. Explanation: Each availability zone (e.g., us-east-1a) is a separate data center with its own facilities. These AZs are designed to be isolated from each other to provide redundancy and fault tolerance.
Edge Locations: Example: AWS CloudFront, the content delivery network (CDN) service, has edge locations in cities around the world, such as New York, London, Tokyo, and Sydney.
Explanation: These edge locations cache and deliver content to users globally. For example, if a user in Tokyo requests a piece of content, AWS CloudFront might serve it from the edge location in Tokyo rather than fetching it from the origin server, reducing latency.
When deploying resources on AWS, users can choose the region and availability zone for their services. For example, when launching a virtual machine (EC2 instance) or setting up a database (Amazon RDS), users specify the AWS region and, optionally, the availability zone where they want their resources to be located.
It's important to note that other cloud providers, such as Microsoft Azure and Google Cloud Platform, have similar concepts with their own terminology, but the fundamental principles of regions, availability zones, and edge locations remain consistent.
***************************** Follow Me: Facebook Page Link: https://www.facebook.com/cloudolus/ Facebook Group Link: https://www.facebook.com/groups/cloudolus LinkedIn Group Link: https://www.linkedin.com/groups/14347089/ Instagram Link: https://www.instagram.com/cloudolus/ Twitter Link: https://twitter.com/cloudolus Pinterest Link: https://www.pinterest.com/cloudolus/ Tumblr Link: https://www.tumblr.com/blog/cloudolus YouTube Link: https://www.youtube.com/channel/UCnOIfrUDCOlz5RUVKFTkktQ ***************************** #freecourse #free #youtube #DevOps #ClouDolus #awstutorial #awstutorialforbeginners #AWSBangla
aws,aws global infrastructure,amazon web services,aws cloud,aws tutorial for beginners,aws tutorial,ClouDolus,amazon aws tutorial,AWS,aws bangla,free,free aws cloud,free course,devops,AWS certification,AWS SAA-C03,aws certified solutions architect associate,pass aws solutions architect,aws solutions,architect exam,courses,certifications,aws certification path,aws full course tutorial,aws certification,aws certification training,youtube,exam preparation
#youtube#cloudolus#aws#aws course#aws devops#aws lambda#aws security#aws cloud#aws certification#aws training#aws free
0 notes
Text

Angelic.
#meri and the ominous creatures#looks like I DID not finish this#if you were following me when i was making the og you get it#my art#art#digital art#sketch#painting#digital painting#concept art#im naming my meri drawings btw#i suck reall bad and the only person i can draw well is meri my sincere condolences#meri wojciechowski#meridiana wojciechoski#meri clef#meri#scp 166#scp fan art#scp fanart#scp art#scp fandom#scp#scp foundation#fanart#secure contain protect#hey old mutuals from scp heyyyyyy#i swear if author clef finds this im gonna scream this has happened twice now and im in awe#i also have a sore throat#sore throat posting or something idk
247 notes
·
View notes
Text
listen i do appreciate canon marineford for the tragedy it is. however it does happen to also be extremely funny.
ace is on his knees on the execution platform, the same place the father that he despises and has tried to define himself outside for his whole life had knelt, thinking this might be the most fitting ending to the life long crashout ace started when he found out who his father was
and then in comes LUFFY, his cheerful persistent little menace of a brother, who has come to COP CENTRAL to break ace out PUBLICLY.
Not only that, but he’s staged a mass break out of the formerly inescapable prison IMPEL DOWN (HE WASNT EVEN LOCKED UP IN THERE? SO EVERYONES A LITTLE BIT CONFUSED AS TO HOW THAT HAPPENED???)
He also kind of looks like shit? But he’s fighting like he’s on day three of a methamphetamine high so no one can be sure how injured luffy Really is.
side note: luffy tanked a lung full of Kills You Dead Toxin and then got shot full of Lowers Your Lifespan Drug and on top of all that, DEMANDED the Super Lowers Your Lifespan Drug when he realized he might need anything resembling recovery time.
as an elder sibling myself, ace might’ve been truly grateful for being loved at the end, but i KNOW there’s a part of him that was INFURIATED that his kid brother managed to crash out harder than he did like OMG STOP COPYING ME FRRRRRRRRRR.
#one piece#marineford#portgas d ace#my posts#imagine being upstaged at your own execution by the snot nosed kid brother you used to bully for sport. PERSONALLY I WOULD BE FURIOUS.#ace looks at luffy like: surely his disregard for his own life and reckless actions have nothing to do with my influence on him as a child.#surely not!#ace and sabo raised each other and luffy. and i do think that the crashout gene that the three of them seem to share is directly bc of that#like luffy and sabo were professional crash outs before. like there’s a certain level of ‘idc if i get beat to shit i’m taking you with me’#that growing up fighting tigers and bears and wolves or whatever instills in a person#but after marineford? you cannot tell me that luffy and sabo aren’t fighting for the empty throne of crashout king in aces honor.#sure they have REASONS for what they do. but the casual disregard for ANY personal consequences post marineford is kind of awe inspiring.#after luffy beat enels ass with the golden mii fists after getting his ass beat into the ground three full times i truly thought that#was as far as luffys ‘crashout harder than my opponent’ strategy went. pre time skip luffy crashouts are NOTHING compared to post time skip.#and given how sabo is rolling in the manga rn he’s doing the same thing#like it’s one thing to want to fight someone bc they fucked with a homie#it’s another thing entirely to think the solution is shouting your name address and social security at them repeatedly#before you fight Unkillable David the Destroyer with nothing but hands flip flops and a dream#before marineford he was somewhat cognizant of his own mortality. not by much mind you but enough to have that shit make him pause for a#second#i promise that if crocodile had the same amnt of advantage over luffy and tossed his ass into the sandpit after beating luffy to a pulp#luffy would EAT the sand and get back to fighting crocodile#crashout is an excellent word. that describes such a specific state of mind and set of actions. and it is THE most succinct answer to the#question: what the fuck is wrong with the ASL brothers.#the only difference between an irl d1 crashout and monkey d. luffy is that he’s dodged most if not all consequences.
54 notes
·
View notes