#Advanced cloud computing projects
Explore tagged Tumblr posts
Text
Unique Cloud Computing Projects for Final year Students
Do you want to make your Cloud Computing Projects more Innovative? Now Takeoff Edu group furnishes all kind of projects for engineering students. Here we also gives the best support and guidance to the students.
Today cloud computing projects are rapidly growing as a massive undertaking in different sectors redefining how companies conduct IT business. These projects take advantage of cloud infrastructure capability, making it possible to scale resources on demand, reduce costs and improve overall operations. These projects are a major concern in the education sector, revolutionizing the way learning resources are created, available, accessible and technologically updated. Cloud acts as a foundation for innovation, pushing forward digitalization inside the educational sphere.
In addition, the majority cloud computing projects concentrate on designing and deploying scalable and resilient applications with cloud-native architectures. This includes the use of micro services, containerization, and server less computing, to build applications that effortlessly adjust to changing workloads.
Titles of Cloud computing Projects:
Latest:
Secure and Efficient online Fingerprint Authentication Scheme based on Cloud Computing.
Efficient Identity-Based Public Integrity Auditing of Shared Data in Cloud Storage with User Privacy Preserving.
Secure Data Storage and Sharing Techniques for Data Protection in Cloud Environments: A Systematic Review, Analysis, and Future Directions.
Forward Secure Public Key Encryption with Keyword Search for Outsourced Cloud Storage.
Data Security and Privacy Protection for Cloud Storage: A Survey.
Trendy:
Semantic-aware searching over Encrypted Data for Cloud Computing.
Dynamic Multi Keyword Ranked Search Based On Bloom Filter over Encrypted Cloud Data.
A Raas Model Based On Emotion Analysis And Double Labelling Applied To Mobile Terminal.
Towards Privacy-preserving Content-based Image Retrieval in Cloud Computing.
Normal Cloud Model-based Algorithm for Multi-attribute Trusted Cloud Service Selection.
Standard:
Identity-Based Data Outsourcing Using Proxy Auditing In Clouds
Data Leakage Detection Using Cloud Computing
Security And Privacy-preserving Challenges Of E-health Solutions In Cloud Computing
Dynamic Multi-keyword Ranked Search Based On Bloom Filter Over Encrypted Cloud Data
A Secure Cloud-of-Clouds System for Storing and Sharing Big Data
The above titles are the examples of Takeoff Edu group cloud computing projects. Here our cloud computing projectsare also perfect for professionals who are looking to upgrade their skills and stay up-to-date with the present latest technology.
#Advanced cloud computing projects#Cloud computing mini projects#Engineering Projects#Cloud projects#Cloud computing Projects
0 notes
Text
Your Guide to B.Tech in Computer Science & Engineering Colleges

In today's technology-driven world, pursuing a B.Tech in Computer Science and Engineering (CSE) has become a popular choice among students aspiring for a bright future. The demand for skilled professionals in areas like Artificial Intelligence, Machine Learning, Data Science, and Cloud Computing has made computer science engineering colleges crucial in shaping tomorrow's innovators. Saraswati College of Engineering (SCOE), a leader in engineering education, provides students with a perfect platform to build a successful career in this evolving field.
Whether you're passionate about coding, software development, or the latest advancements in AI, pursuing a B.Tech in Computer Science and Engineering at SCOE can open doors to endless opportunities.
Why Choose B.Tech in Computer Science and Engineering?
Choosing a B.Tech in Computer Science and Engineering isn't just about learning to code; it's about mastering problem-solving, logical thinking, and the ability to work with cutting-edge technologies. The course offers a robust foundation that combines theoretical knowledge with practical skills, enabling students to excel in the tech industry.
At SCOE, the computer science engineering courses are designed to meet industry standards and keep up with the rapidly evolving tech landscape. With its AICTE Approved, NAAC Accredited With Grade-"A+" credentials, the college provides quality education in a nurturing environment. SCOE's curriculum goes beyond textbooks, focusing on hands-on learning through projects, labs, workshops, and internships. This approach ensures that students graduate not only with a degree but with the skills needed to thrive in their careers.
The Role of Computer Science Engineering Colleges in Career Development
The role of computer science engineering colleges like SCOE is not limited to classroom teaching. These institutions play a crucial role in shaping students' futures by providing the necessary infrastructure, faculty expertise, and placement opportunities. SCOE, established in 2004, is recognized as one of the top engineering colleges in Navi Mumbai. It boasts a strong placement record, with companies like Goldman Sachs, Cisco, and Microsoft offering lucrative job opportunities to its graduates.
The computer science engineering courses at SCOE are structured to provide a blend of technical and soft skills. From the basics of computer programming to advanced topics like Artificial Intelligence and Data Science, students at SCOE are trained to be industry-ready. The faculty at SCOE comprises experienced professionals who not only impart theoretical knowledge but also mentor students for real-world challenges.
Highlights of the B.Tech in Computer Science and Engineering Program at SCOE
Comprehensive Curriculum: The B.Tech in Computer Science and Engineering program at SCOE covers all major areas, including programming languages, algorithms, data structures, computer networks, operating systems, AI, and Machine Learning. This ensures that students receive a well-rounded education, preparing them for various roles in the tech industry.
Industry-Relevant Learning: SCOE’s focus is on creating professionals who can immediately contribute to the tech industry. The college regularly collaborates with industry leaders to update its curriculum, ensuring students learn the latest technologies and trends in computer science engineering.
State-of-the-Art Infrastructure: SCOE is equipped with modern laboratories, computer centers, and research facilities, providing students with the tools they need to gain practical experience. The institution’s infrastructure fosters innovation, helping students work on cutting-edge projects and ideas during their B.Tech in Computer Science and Engineering.
Practical Exposure: One of the key benefits of studying at SCOE is the emphasis on practical learning. Students participate in hands-on projects, internships, and industry visits, giving them real-world exposure to how technology is applied in various sectors.
Placement Support: SCOE has a dedicated placement cell that works tirelessly to ensure students secure internships and job offers from top companies. The B.Tech in Computer Science and Engineering program boasts a strong placement record, with top tech companies visiting the campus every year. The highest on-campus placement offer for the academic year 2022-23 was an impressive 22 LPA from Goldman Sachs, reflecting the college’s commitment to student success.
Personal Growth: Beyond academics, SCOE encourages students to participate in extracurricular activities, coding competitions, and tech fests. These activities enhance their learning experience, promote teamwork, and help students build a well-rounded personality that is essential in today’s competitive job market.
What Makes SCOE Stand Out?
With so many computer science engineering colleges to choose from, why should you consider SCOE for your B.Tech in Computer Science and Engineering? Here are a few factors that make SCOE a top choice for students:
Experienced Faculty: SCOE prides itself on having a team of highly qualified and experienced faculty members. The faculty’s approach to teaching is both theoretical and practical, ensuring students are equipped to tackle real-world challenges.
Strong Industry Connections: The college maintains strong relationships with leading tech companies, ensuring that students have access to internship opportunities and campus recruitment drives. This gives SCOE graduates a competitive edge in the job market.
Holistic Development: SCOE believes in the holistic development of students. In addition to academic learning, the college offers opportunities for personal growth through various student clubs, sports activities, and cultural events.
Supportive Learning Environment: SCOE provides a nurturing environment where students can focus on their academic and personal growth. The campus is equipped with modern facilities, including spacious classrooms, labs, a library, and a recreation center.
Career Opportunities After B.Tech in Computer Science and Engineering from SCOE
Graduates with a B.Tech in Computer Science and Engineering from SCOE are well-prepared to take on various roles in the tech industry. Some of the most common career paths for CSE graduates include:
Software Engineer: Developing software applications, web development, and mobile app development are some of the key responsibilities of software engineers. This role requires strong programming skills and a deep understanding of software design.
Data Scientist: With the rise of big data, data scientists are in high demand. CSE graduates with knowledge of data science can work on data analysis, machine learning models, and predictive analytics.
AI Engineer: Artificial Intelligence is revolutionizing various industries, and AI engineers are at the forefront of this change. SCOE’s curriculum includes AI and Machine Learning, preparing students for roles in this cutting-edge field.
System Administrator: Maintaining and managing computer systems and networks is a crucial role in any organization. CSE graduates can work as system administrators, ensuring the smooth functioning of IT infrastructure.
Cybersecurity Specialist: With the growing threat of cyberattacks, cybersecurity specialists are essential in protecting an organization’s digital assets. CSE graduates can pursue careers in cybersecurity, safeguarding sensitive information from hackers.
Conclusion: Why B.Tech in Computer Science and Engineering at SCOE is the Right Choice
Choosing the right college is crucial for a successful career in B.Tech in Computer Science and Engineering. Saraswati College of Engineering (SCOE) stands out as one of the best computer science engineering colleges in Navi Mumbai. With its industry-aligned curriculum, state-of-the-art infrastructure, and excellent placement record, SCOE offers students the perfect environment to build a successful career in computer science.
Whether you're interested in AI, data science, software development, or any other field in computer science, SCOE provides the knowledge, skills, and opportunities you need to succeed. With a strong focus on hands-on learning and personal growth, SCOE ensures that students graduate not only as engineers but as professionals ready to take on the challenges of the tech world.
If you're ready to embark on an exciting journey in the world of technology, consider pursuing your B.Tech in Computer Science and Engineering at SCOE—a college where your future takes shape.
#In today's technology-driven world#pursuing a B.Tech in Computer Science and Engineering (CSE) has become a popular choice among students aspiring for a bright future. The de#Machine Learning#Data Science#and Cloud Computing has made computer science engineering colleges crucial in shaping tomorrow's innovators. Saraswati College of Engineeri#a leader in engineering education#provides students with a perfect platform to build a successful career in this evolving field.#Whether you're passionate about coding#software development#or the latest advancements in AI#pursuing a B.Tech in Computer Science and Engineering at SCOE can open doors to endless opportunities.#Why Choose B.Tech in Computer Science and Engineering?#Choosing a B.Tech in Computer Science and Engineering isn't just about learning to code; it's about mastering problem-solving#logical thinking#and the ability to work with cutting-edge technologies. The course offers a robust foundation that combines theoretical knowledge with prac#enabling students to excel in the tech industry.#At SCOE#the computer science engineering courses are designed to meet industry standards and keep up with the rapidly evolving tech landscape. With#NAAC Accredited With Grade-“A+” credentials#the college provides quality education in a nurturing environment. SCOE's curriculum goes beyond textbooks#focusing on hands-on learning through projects#labs#workshops#and internships. This approach ensures that students graduate not only with a degree but with the skills needed to thrive in their careers.#The Role of Computer Science Engineering Colleges in Career Development#The role of computer science engineering colleges like SCOE is not limited to classroom teaching. These institutions play a crucial role in#faculty expertise#and placement opportunities. SCOE#established in 2004#is recognized as one of the top engineering colleges in Navi Mumbai. It boasts a strong placement record
2 notes
·
View notes
Text
The Future of Work: Technology and Remote Collaboration
Introduction
The future of work is rapidly evolving, driven by technological advancements and the increasing popularity of remote collaboration. At TechtoIO, we delve into how these changes are shaping the workplace, impacting productivity, and altering traditional work paradigms. This blog post explores the key technologies enabling remote work and the benefits and challenges associated with this new way of working. Read to continue link
#Innovation Insights#Tagsbenefits of remote work#cloud computing for remote work#communication tools for remote work#cybersecurity for remote work#effective remote collaboration strategies#employee satisfaction remote work#future of remote work#future of work#project management software#remote collaboration#remote collaboration tools#remote team management#remote work challenges#remote work cost savings#remote work innovations#remote work productivity#remote work technology#remote work tools#remote work trends#Technology#Science#business tech#Adobe cloud#Trends#Nvidia Drive#Analysis#Tech news#Science updates#Digital advancements
1 note
·
View note
Text
Research Data Management. Or, How I made multiple backups and still almost lost my honours thesis.
This is a story I used to tell while teaching fieldworkers and other researchers about how to manage their data. It’s a moderately improbable story, but it happened to me and others have benefited from my misadventures. I haven't had reason to tell it much lately, and I thought it might be useful to put into writing. This is a story from before cloud storage was common - back when you could, and often would, run out of online email storage space. Content note: this story includes some unpleasant things that happened to me, including multiple stories of theft (cf. moderately improbable). Also, because it's stressful for most of the story, I want to reassure you that it does have a happy conclusion. It explains a lot of my enthusiasm for good research data management. In Australia, 'honours' is an optional fourth year for a three year degree. It's a chance to do some more advanced coursework and try your hand at research, with a small thesis project. Of course, it doesn't feel small when it's the first time you've done a project that takes a whole year and is five times bigger than anything you’ve ever written. I've written briefly about my honours story (here, and here in a longer post about my late honours supervisor Barb Kelly) . While I did finish my project, it all ended a bit weirdly when my supervisor Barb got ill and left during the analysis/writing crunch. The year after finishing honours I got an office job. I hoped to maybe do something more with my honours work, but I wasn't sure what, and figured I would wait until Barb was better. During that year, my sharehouse flat was broken into and the thief walked out with the laptop I'd used to do my honours project. The computer had all my university files on it, including my data and the Word version of my thesis. I lost interview video files, transcriptions, drafts, notes and everything except the PDF version I had uploaded to the University's online portal. Uploading was optional at the time, if I didn't do that I probably would have just been left with a single printed copy. I also lost all my jewellery and my brother’s base guitar, but I was most sad about the data (sorry bro). Thankfully, I made a backup of my data and files on a USB drive that I kept in my handbag. This was back when a 4GB thumb drive was an investment. That Friday, feeling sorry for myself after losing so many things I couldn't replace, I decided to go dancing to cheer myself up. While out with a group of friends, my bag was stolen. It was the first time I had a nice handbag, and I still miss it. Thankfully, I knew to make more than one back up. I had an older USB that I'd tucked down the back of the books on my shelf (a vintage 256MB drive my dad kindly got for me in undergrad after a very bad week when I lost an essay to a corrupted floppy disk). When I went to retrieve the files, the drive was (also) corrupted. This happens with hard drives sometimes. My three different copies in three different locations were now lost to me.
Thankfully, my computer had a CD/DVD burner. This was a very cool feature in the mid-tens, and I used to make a lot of mixed CDs for my friends. During my honours project I had burned backed up files on some discs and left them at my parents house. It was this third backup, kept off site, which became the only copy of my project. I very quickly made more copies. When Barb was back at work, and I rejoined her as a PhD student, it meant we could return to the data and all my notes. The thesis went through a complete rewrite and many years later was published as a journal article (Gawne & Kelly 2014). It would have probably never happened if I didn’t have those project files. I continued with the same cautious approach to my research data ever since, including sending home SD cards while on field trips, making use of online storage, and archiving data with institutional repositories while a project is ongoing.
I’m glad that I made enough copies that I learnt a good lesson from a terrible series of events. Hopefully this will prompt you, too, to think about how many copies you have, where they’re located, and what would happen if you lost access to your online storage.
72 notes
·
View notes
Text
With the United Kingdom poised to begin geoengineering experiments, ICAN is sounding the alarm to policymakers at the highest levels of the U.S. and U.K. governments.
Through its legal team, ICAN has sent letters to the U.S. Secretary of State, Secretary of Commerce, Secretary of Defense, UN ambassador, and the U.K.’s Advanced Research and Innovation Agency (ARIA), and Secretary of State for the Department for Science, Innovation & Technology (DSIT), warning of the dangers these experiments pose to our health, the environment, informed consent, and national security.
In September 2024, ARIA allocated £56.8m (about $75 million) to research whether geoengineering could be used to cool the earth. Concerningly, unlike other geoengineering research programs that limit their research to computer modeling, ARIA’s “Exploring Climate Cooling” program will conduct outdoor experiments to “test” and “validate” sun-blocking methods.
In fact, the Climate Cooling program has already funded five planned outdoor projects. The experiments include spraying clouds with novel spray technology, manipulating clouds’ electrical charges, and launching specially adapted weather balloons from sites in the U.S. and/or U.K. to study how high altitude affects minerals being considered for use in stratospheric aerosol injection. In response, U.K. citizens have filed a petition to ban geoengineering in the U.K.
While ARIA claims “program transparency, public participation and consultation” are core to the program, the agency itself is shockingly exempt from the U.K.’s Freedom of Information Act. Undeterred, ICAN’s attorneys are pursuing all options to obtain information about these experiments, including seeking any communications of American researchers to see if they are collaborating with their British counterparts.
5 notes
·
View notes
Text
autumn night
Sighing with your shoulders slumped at your sides, you sluggishly shuffle into the bathroom. Refining your clothes to a pile on the floor, you twist the complex knob of your shower, effectively earning the correct temperature. As you see your reflection slowly fog up. Looking at your body through the glass, you’re adoring it more than usual. Your skin shining just right in the lighting, your boobs sitting just right all by themselves, your waist and chubby stomach not bothering you as much as it used to. Eyeing the shiny string of beads that sit on the small of your waist, you lightly tug on them and slide them down your hips. The jewelry sitting atop the pile of clothes on the floor. Picking up the dazzling beads, you place it on the counter and get in the shower.
Lathering your body up, the water hits the shower floor in a continuous pattern. From the bed he can’t help but fantasize about your naked body, even if his focus is on his computer filing hero reports. Hearing the shower stop, he types faster, wanting to finish the mandatory work.
Walking out the bathroom with a towel hugging and hiding your body, a cloud of steam stalks behind you. Putting on panties and one of your husband’s t-shirts, you hang up your towel and look back at him.
“kats? baby?” You softly call out to him. He mumbles to you a moment later. His crimson eyes accompanied by glasses resting on the bridge of his nose.
“are you almost done?” You whine and he doesn’t grace you with an answer. Although his annoyance is projected through his furrow eyebrows and pierced lips.
Walking up to your side of the bed, you nudge your knee on the mattress. A noticeable dip in the comfortable surface. Gazing at him for a moment, you hesitantly lean towards him for a kiss. He glances at your actions and ignores the advance. Huffing to yourself you leave the room, making sure to put a sway in your hips to mess with him. Since he was clearly messing around with you. Your sweet tooth was aching. No matter how bad it is to eat sweets so late at night, you needed to satisfy the urge.
Opening the fridge door in search for ice cream, you are unpleasantly surprised to see nothing. Glaring intensely at the shelf its supposed to be on, you know who’s the culprit. And all you can think is how he could be so selfish. Eating all the ice cream and not leaving one single scoop for you. And he has the nerve to preach about being healthy. Trudging back to the bedroom, your sweet tooth is gone and all you have on your mind is confrontation.
“You ate my stuff.” You exclaim to him, voice mixed with annoyance and amusement at his unfazed face.
“I eat a lot of your stuff, be specific.”
“You-“ Halting your sentence with a huff, you roll your eyes and shut the door behind you, “the ice cream. You ate it. The pint that had a sticky note that specifically says my name on it!”
You could find this all so laughable if it wasn’t for his little attitude. Closing his laptop, he folds his hands on top the device and motions for you to come close to him.
“Yeah I ate it. Now what?” Shaking your head at his intimidating words, your eyes narrowed as you look at him.
He must love when you’re upset at him. Maybe it’s because you suck his cock better with more malus than caution or because you ride him rougher than you would ever normally. He probably loves the way you grip onto his chest when you throw your ass back on him as he grips your hair until you have a throbbing headache. It could be over the littlest things but still, it makes your movements and intent more careless towards your husband.
Gritting your teeth as he holds you in a headlock with your back arched against his chest. You grunt as you bathe in the twisted euphoria of being “mad” at each other. Short and quick thrusts into your cunt, the corner of his lip is upturned in a small smirk at the position he has you in. Showing how much stronger and dominant he is. Feeling your curvy body tremble against him as he forces another orgasm out of you.
‘Over some damn ice cream.’ He thinks.
In his eyes you’re begging to be fucked into oblivion. Maybe it’s been a long week, no dick and now you forgot how to act with him. But don’t worry, he’ll whip you back into shape. Pounding his cock into your tight gummy walls, to remind you of the burn. The burn of his cock molding itself back into your pussy after a long break. He’ll even feel up your lower abdomen to feel him puncturing your stomach and will even press onto your tummy to hear your pleading whines and cries.
He loves your pained whining, it’s a wonder really. How you can find the breath to scream when he’s basically smashing your organs together with how deep he’s fucking you.
kinktober list
regular writing list
#fanfiction#y/n#smut#freaktober#bakugou x fem!reader#bakugou x reader#yandere bakugo katsuki#bnha bakugo katsuki#bakugou katuski x reader#katsuki x reader#katsuki x you#katsuki x y/n
90 notes
·
View notes
Text
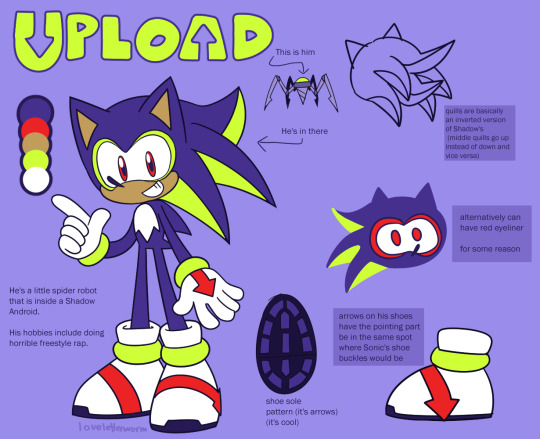
BEHOLD. UPLOAD THE HEDGEHOG / UPLOAD.EXE
Originally a contingency plan from GUN, Upload was created as part of Project Usurper: an under-wraps military experiment to create a machine that could neurologically possess Sonic the Hedgehog in the event he was labeled a liability.
The original Upload existed solely as a computer program, "usurper_upload.exe". Once the highly advanced AI software was in place, a small mechanical "surgical spider" was developed to contain it, allowing the program to attach itself to the frontal lobe of any unwitting victim after releasing a paralyzing gas modeled after that which clouded the Earth during the Black Arms incident. Experiments showed full loyalty to GUN in patients, however side effects included intense irritability and brain hemorrhaging resulting in the appearance of bleeding from the eyes.
Eventually, the program developed a form of sentience and managed to escape from GUN in its spider body. After wandering, it was able to attached itself to a decommissioned Shadow Android, which it then modified to its liking. Its current M.O. is unknown, however GUN speculates it's seeking Sonic the Hedgehog to attempt to preemptively fulfill its programming, which would both destroy Sonic and reveal the nature of the experiment to the world.
"Upload the Hedgehog" is considered GUN property and must be captured at all costs.
Thank you @loveletterworm for the redesign and model sheet! Statement from the designer: "Jenny just asked me to give him different shoes but then I drew a completely different character because I thought it would be funny"
#sonic oc#sonic the hedgehog#sonic.exe#sonic.exe oc#but only tangentially#upload the hedgehog#upload exists to almost parody sonic.exe in that Sonic.exe is a bad end. Surely Upload is seeking Sonic to usurp his position! Right...?
30 notes
·
View notes
Text
Cloud and AI are ‘fundamentally changing’ ability to forecast weather, NOAA chief says
LAS VEGAS — National Oceanic and Atmospheric Administration head Rick Spinrad said this week that even as hurricanes, wildfires and other weather events worsen, the use of innovative tech like cloud computing and AI is improving the agency’s ability to predict and forecast them.
“This is fundamentally changing our ability to do probably the most important thing in our business, and that's predict, project and forecast,” said Spinrad, speaking at AWS’ re:Invent 2024 conference in Las Vegas.
Spinrad said NOAA, which houses the National Weather Service and owns or operates 18 weather satellites, archives about 230 terabytes of environmental data per month from various observational platforms, ranging from the sea, to ships and even space.
That data is then hosted by commercial cloud service providers and made available to the public and nascent climate industry through NOAA’s Open Data Dissemination program, or NODD. AWS, Spinrad said, now hosts 32 petabytes of environmental information, or about “half of [NOAA’s] holdings.”
“Our ability to collect these data, put them on NODD, store them in a system that allows AI applications, is really critical,” Spinrad said. “And it's not just for our use at NOAA. We are supporting a burgeoning climate industrial effort, a commercial weather enterprise. We are now collecting enough environmental information — enough environmental intelligence — to make a fundamental difference.”
According to Spinrad, the difference includes improved access to critical weather data for incident meteorologists in the field. Using another tool from Amazon, AppStream 2.0, incident meteorologists dispatched to the scenes of floods, droughts, storms and wildfires can “have the same kind of access to our advanced weather information and interactive processing system that they would back at the home office.”
Spinrad said forecasters have been able to make a “seven year advancement in forecast capability in a matter of months using AI, using the training data [NOAA] now has access to.” Such advancements would not be possible without the ability to assimilate new data types, he added, noting that autonomous systems, satellites and surface-based robots all provide data that can go into forecasts.
7 notes
·
View notes
Text
World's Most Powerful Business Leaders: Insights from Visionaries Across the Globe

In the fast-evolving world of business and innovation, visionary leadership has become the cornerstone of driving global progress. Recently, Fortune magazine recognized the world's most powerful business leaders, acknowledging their transformative influence on industries, economies, and societies.
Among these extraordinary figures, Elon Musk emerged as the most powerful business leader, symbolizing the future of technological and entrepreneurial excellence.

Elon Musk: The Game-Changer
Elon Musk, the CEO of Tesla, SpaceX, and X (formerly Twitter), has redefined innovation with his futuristic endeavors. From pioneering electric vehicles at Tesla to envisioning Mars colonization with SpaceX, Musk's revolutionary ideas continue to shape industries. Recognized as the most powerful business leader by Fortune, his ventures stand as a testament to what relentless ambition and innovation can achieve. Digital Fraud and Cybercrime: India Blocks 59,000 WhatsApp Accounts and 6.7 Lakh SIM Cards Also Read This....
Musk's influence extends beyond his corporate achievements. As a driver of artificial intelligence and space exploration, he inspires the next generation of leaders to push boundaries. His leadership exemplifies the power of daring to dream big and executing with precision.

Mukesh Ambani: The Indian Powerhouse
Mukesh Ambani, the chairman of Reliance Industries, represents the epitome of Indian business success. Ranked among the top 15 most powerful business leaders globally, Ambani has spearheaded transformative projects in telecommunications, retail, and energy, reshaping India's economic landscape. His relentless focus on innovation, particularly with Reliance Jio, has revolutionized the digital ecosystem in India.
Under his leadership, Reliance Industries has expanded its global footprint, setting new benchmarks in business growth and sustainability. Ambani’s vision reflects the critical role of emerging economies in shaping the global business narrative.

Defining Powerful Leadership
The criteria for identifying powerful business leaders are multifaceted. According to Fortune, leaders were evaluated based on six key metrics:
Business Scale: The size and impact of their ventures on a global level.
Innovation: Their ability to pioneer advancements that redefine industries.
Influence: How effectively they inspire others and create a lasting impact.
Trajectory: The journey of their career and the milestones achieved.
Business Health: Metrics like profitability, liquidity, and operational efficiency.
Global Impact: Their contribution to society and how their leadership addresses global challenges.
Elon Musk and Mukesh Ambani exemplify these qualities, demonstrating how strategic vision and innovative execution can create monumental change.

Other Global Icons in Leadership
The list of the world's most powerful business leaders features numerous iconic personalities, each excelling in their respective domains:
Satya Nadella (Microsoft): A transformative leader who has repositioned Microsoft as a cloud-computing leader, emphasizing customer-centric innovation.
Sundar Pichai (Alphabet/Google): A driving force behind Google’s expansion into artificial intelligence, cloud computing, and global digital services.
Jensen Huang (NVIDIA): The architect of the AI revolution, whose GPUs have become indispensable in AI-driven industries.
Tim Cook (Apple): Building on Steve Jobs' legacy, Cook has solidified Apple as a leader in innovation and user-centric design.
These leaders have shown that their influence isn’t confined to financial success alone; it extends to creating a better future for the world.
Leadership in Action: Driving Innovation and Progress
One common thread unites these leaders—their ability to drive innovation. For example:
Mary Barra (General Motors) is transforming the auto industry with her push toward electric vehicles, ensuring a sustainable future.
Sam Altman (OpenAI) leads advancements in artificial intelligence, shaping ethical AI practices with groundbreaking models like ChatGPT.
These visionaries have proven that impactful leadership is about staying ahead of trends, embracing challenges, and delivering solutions that inspire change.
The Indian Connection: Rising Global Influence
Apart from Mukesh Ambani, Indian-origin leaders such as Sundar Pichai and Satya Nadella have earned global recognition. Their ability to bridge cultural boundaries and lead multinational corporations demonstrates the increasing prominence of Indian talent on the world stage.

Conclusion
From technological advancements to economic transformation, these powerful business leaders are shaping the future of our world. Elon Musk and Mukesh Ambani stand at the forefront, representing the limitless potential of visionary leadership. As industries continue to evolve, their impact serves as a beacon for aspiring leaders worldwide.
This era of leadership emphasizes not only achieving success but also leveraging it to create meaningful change. In the words of Elon Musk: "When something is important enough, you do it even if the odds are not in your favor." Rajkot Job Update
#elon musk#mukesh ambani#x platform#spacex#tesla#satya nadella#sundar pichai#jensen huang#rajkot#our rajkot#Rajkot Job#Rajkot Job Vacancy#job vacancy#it jobs
8 notes
·
View notes
Text

The A-12 pilot who while looking for a crashed F-105 in Utah came across a brothel with a runway (A C-7A Caribou was the largest aircraft to ever land there)
The Oxcart
In 1959, Lockheed began work on the design of a long-range, high-altitude plane, then known as the A-11. It was a Cold War project. Heading the project team was Clarence “Kelly” Johnson, Lockheed’s Vice President for Advanced Development Projects. Johnson had previously led the development of the U-2 spy plane. Five years after work began on the A-11, on Feb. 29, 1964, President Lyndon Johnson told reporters that the aircraft (by that time modified to the A-12 Oxcart production version with a reduced radar cross section) had attained speeds of over 2,000 mph and altitudes of more than 70,000 feet in tests at Edwards Air Force Base (AFB).

CLICK HERE to see The Aviation Geek Club contributor Linda Sheffield’s T-shirt designs! Linda has a personal relationship with the SR-71 because her father Butch Sheffield flew the Blackbird from test flight in 1965 until 1973. Butch’s Granddaughter’s Lisa Burroughs and Susan Miller are graphic designers. They designed most of the merchandise that is for sale on Threadless. A percentage of the profits go to Flight Test Museum at Edwards Air Force Base. This nonprofit charity is personal to the Sheffield family because they are raising money to house SR-71, #955. This was the first Blackbird that Butch Sheffield flew on Oct. 4, 1965.
Noteworthy, according to Col. Richard H. Graham’s book The Complete Book of the SR-71 Blackbird: The Illustrated Profile of Every Aircraft, Crew, and Breakthrough of the World’s Fastest Stealth Jet, during the first three years of pre-operational testing, three A-12s crashed – two from mechanical malfunctions and one because of ground crew error. All pilots ejected safely.
The A-12 crash in Utah and the F-105 crash cover story
On May 24, 1963, A-12 number 926 involved in a subsonic engine test flight and piloted by Ken Collins, crashed fourteen miles south of Wendover, Utah. While testing an inertial navigation system, Collins flew into heavy clouds above thirty thousand feet and began noticing erroneous and confusing airspeed and altitude readings just before the A-12 pitched up, stalled, and went into an inverted spin. Unable to regain control, he ejected at around twenty-five thousand feet and was unhurt. A press cover story referred to the crashed aircraft as being a Republic F-105.
It was first thought that it was a pilot error but later confirmed that it was an inadequate pitot tube design that had caused the air data computer to fail.
Because his sortie was low altitude, Collins was not in his pressure suit, so it added to the credence that the crash was an F-105.

This print is available in multiple sizes from AircraftProfilePrints.com – CLICK HERE TO GET YOURS. SR-71A Blackbird 61-7972 “Skunkworks”
‘With an ironic twist of faith sometime after the loss of Article 123, an F-105 from Nellis was lost and members of the Oxcart (code word of A-12) program were involved in the search for the crash site,’ A-12 pilot Frank Murray recalls in Paul Crickmore‘s latest book “Lockheed Blackbird Beyond the Secret Missions.
A-12 pilot searching for crashed F-105
Frank Murray and Dr. Roger Anderson were airborne in a Cessna searching for the crashed F-105 when they located the crash near a small lake with the adjoining property of one of the brothels in the area known as Ash Meadow Ranch. The brothel provided a small dirt runway graded out to allow its customers the option of air travel into the facility.
‘We taxied into Ash Meadow Ranch and we explained that we were here looking for the crash site and we had located it,’ Murray explains.
‘By then it was lunchtime and the Madame got the cook to rustle up some lunch. There was some polite conversation with the Madame and my aviation curiosity got the better of me.
Brothel with landing strip
The A-12 pilot who while looking for a crashed F-105 in Utah came across a brothel with a runway (A C-7A Caribou was the largest aircraft to ever land there)
C-7A Caribou

‘I asked her what was the largest aircraft ever to use the landing strip.
‘She replied the largest was an Army C- 7A Caribou full of GIs from an army base in California! ‘Mind you” she added mischievously they weren’t looking for any downed airplanes!’
Murray concludes;
‘After lunch, the three of us said our goodbyes and departed for our lives back at our Ranch [“Groom Lake,” “The Ranch,” “Area 51,” and “Dreamland” are all names that have been associated with the Groom Lake facility in the Nevada desert]. ‘
I had heard when I was a girl growing up in California that brothels were legal in Nevada. These kinds of rumors were hard for me to believe, but I believe them now!
Be sure to check out Linda Sheffield Miller (Col Richard (Butch) Sheffield’s daughter, Col. Sheffield was an SR-71 Reconnaissance Systems Officer) Twitter X Page Habubrats SR-71, Instagram Page SR71Habubrats and Facebook Page Born into the Wilde Blue Yonder Habubrats for awesome Blackbird’s photos and stories.
@Habubrats71 via X
19 notes
·
View notes
Text
Donald Trump vs. Kamala Harris: What It Means For IT Companies in India
When it comes to U.S. politics, Indian IT companies pay close attention, especially in races with heavyweights like former President Donald Trump and Vice President Kamala Harris. Each candidate’s policies can have ripple effects, impacting everything from visa policies to foreign direct investment and trade partnerships. For India’s booming IT sector, this rivalry could shape the future in major ways, particularly around outsourcing, talent mobility, and international tech collaborations. Here’s what each candidate brings to the table and what it could mean for the Indian IT industry.

Donald Trump’s Policies and Their Potential Impact
Trump’s “America First” agenda in his previous term brought significant shifts to immigration and outsourcing policies. His administration’s stance leaned toward prioritizing American jobs and reducing dependency on foreign workers, which affected the H-1B visa system, a crucial pathway for many skilled Indian IT professionals to work in the United States.
Key Areas to Watch if Trump Returns to Power
H-1B Visa Reform: Under Trump, the H-1B visa process became more stringent, with increased scrutiny on applications and tightened eligibility criteria. The approach aimed to reduce the number of visas granted, thus limiting the talent flow from India to the U.S. If Trump were to return, he might push for more reforms that could make it harder for Indian IT companies to place skilled workers in the U.S. for long-term assignments.
Outsourcing Policies: Trump’s stance on outsourcing often pointed toward creating incentives for American companies to move jobs back to the U.S. Although a complete shutdown of outsourcing is unlikely, a renewed Trump presidency might include policies that create hurdles or add costs to IT companies operating in India to reduce offshoring.
Taxation and Trade Barriers: Trump previously aimed to negotiate trade deals that reduced the U.S. trade deficit. Indian IT firms could face higher tariffs or restrictions if they want to establish more U.S. partnerships or expand operations on American soil.
Potential Upside: Some experts argue that Trump’s pro-business mindset and regulatory reforms, such as tax cuts, could indirectly benefit Indian IT companies if they lead to economic growth. With more American firms thriving, there may still be demand for Indian IT services, albeit in a more restrictive environment.
Kamala Harris’s Approach and Potential Influence
As the daughter of Indian immigrants, Kamala Harris’s connection to India is often highlighted. Her political stance, generally aligned with Democratic ideals, has favored immigrant rights, inclusivity, and technological advancement. Harris’s policies could potentially be more favorable for Indian IT companies, especially regarding immigration and tech collaborations.
Key Areas to Watch if Harris Gains More Influence
Visa and Immigration Reform: Harris has shown consistent support for immigration reform that would protect skilled foreign workers, including those from India. Her stance could bring improvements to the H-1B program, possibly increasing quotas or reducing the administrative burden on Indian IT professionals. This would be a welcome shift, making it easier for Indian firms to deploy talent in the U.S.
Tech Collaborations and Bilateral Ties: Given Harris’s strong ties to India, she could prioritize policies that foster U.S.-India tech partnerships. This could mean better collaboration on AI, cybersecurity, and cloud computing initiatives, offering Indian IT companies more opportunities to work alongside American firms on high-stakes projects.
Outsourcing Flexibility: Unlike Trump, Harris is less likely to advocate for aggressive curbs on outsourcing. While some regulations may still push companies to consider American workers first, it’s likely that Harris’s approach would be more balanced and encourage mutual growth, allowing Indian IT firms to continue serving U.S. clients without significant restrictions.
STEM Education and Training Initiatives: Harris may also introduce policies aimed at training and upskilling the American workforce. However, this approach could complement the Indian IT industry rather than limit it, as it could create avenues for partnerships in training programs or tech-driven education solutions.
Potential Upside: A Harris-led approach may result in more collaborative policies, boosting IT companies’ confidence in expanding U.S. operations. By maintaining a balanced approach to immigration and tech regulations, she could make it easier for Indian firms to both work in the U.S. and bring American investments back to India.
What This Means for Indian IT Companies
Indian IT companies like TCS, Infosys, and Wipro rely heavily on their U.S. clientele, and visa restrictions can significantly impact how they operate. Here’s a summary of what IT firms should expect:
Talent Mobility: A Trump-led administration might restrict it, while Harris would likely enhance it.
Outsourcing Stability: Trump could discourage offshoring, whereas Harris might adopt a more relaxed stance.
Trade Relations: Trump’s trade policies could become more protectionist, while Harris might lean toward fostering partnerships.
Adaptations and Strategic Moves for Indian IT Firms
Regardless of who wins, Indian IT companies should prepare by adopting a flexible approach:
Diversifying Talent Locations: With potential visa issues on the horizon, companies can consider moving talent to other locations, such as Canada or even remote setups within India, to serve U.S. clients.
Increasing Local Hiring in the U.S.: To align with possible hiring preferences, Indian firms may continue to hire more U.S.-based talent and offer training to local employees.
Emphasizing Partnerships and Joint Ventures: Both political paths present opportunities for tech collaborations. Indian firms could look for joint ventures with U.S. companies, fostering a partnership approach that aligns with potential regulations.
Final Thoughts
The outcome of a Trump vs. Harris contest would have unique implications for the Indian IT industry. Trump’s focus on reducing dependency on foreign talent and protecting U.S. jobs could mean tighter visa regulations and fewer opportunities for Indian workers in the U.S. Harris, on the other hand, could be a gateway to a more balanced, globally-minded U.S. policy that emphasizes collaboration and growth.
Regardless of the outcome, Indian IT firms have shown resilience and adaptability, adjusting to regulatory changes while remaining global leaders in IT services.
#technology#tech news#tech world#donald trump#kamala harris#usa news#us politics#election 2024#us elections
7 notes
·
View notes
Text
Took a break because of Deltarune ch3+4 & other things, but now I got back to my volumetric cloud rendering project in Godot. Finally, I have some decent looking clouds!
I have many improvement ideas, and I want to make a way to design individual clouds as well.
I studied a bunch of cloud optics and how volumetric clouds are rendered (and meteorology as well, but that wasn't super useful for this)
The most helpful sources, on the top of my head, were Maxime Heckel's blog post on real-time cloudscape rendering (https://blog.maximeheckel.com/posts/real-time-cloudscapes-with-volumetric-raymarching/) , and this article: https://cglearn.eu/pub/advanced-computer-graphics/volumetric-rendering
Maxime Heckel's blog post was useful, and I ended up copying and adapting it's code a lot, though I did change a few things, like I had a different lightmarching loop.
What I did different from Maxime was that instead of summing together densities of each lightmarch samplepoint and applying the Beer's law at the end, I instead applied the Beer's law for every sample and multiplied the results together.
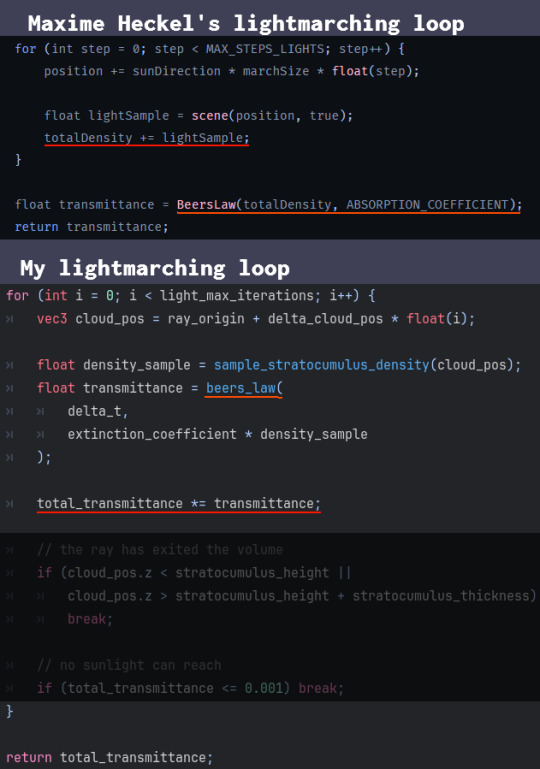
I'm not 100% sure which way is correct, but I didn't need the extra value term on my light energy which he needed, and assumed it was because of some issue in his code.
2 notes
·
View notes
Text
The Trump administration has scrapped its predecessor’s sweeping export controls for advanced artificial intelligence chips, known as the AI diffusion rule.
“To win the AI race, the Biden AI diffusion rule must go,” posted David Sacks, U.S. President Donald Trump’s top AI advisor, on May 8. Sacks continued his criticism at the Saudi-U.S. Investment Forum a few days later, arguing that the rule “restricted the diffusion or proliferation of American technology all over the world.”
As the administration decides what comes next, it should raise its sights from merely proposing a “simpler” rule to manage the diffusion of AI chips. Instead, it should seize the opportunity to offer an ambitious vision to promote the broader diffusion of U.S. technology.
After all, the world not only wants the United States’ AI chips, but also its AI applications, data centers, cloud services, satellites, and advanced technology offerings generally. But even as Beijing extends its digital offerings in key emerging markets, U.S. foreign policy has failed to adapt for a global technology competition with era-defining stakes. Whether you agree with the Trump administration or not, its disruption is an opportunity to forge a new model of technology statecraft to help the United States win the race to shape strategic digital infrastructure and technology diffusion across the globe.
To start, Washington must finally learn from its failure in the transition to 4G and 5G telecommunications networks, where Beijing’s state-backed model—and the absence of a compelling U.S.-led alternative—enabled Huawei and ZTE to all but corner emerging markets. Huawei now operates in more than 170 countries worldwide and is the top global provider of telecommunications equipment. But if there is broad consensus among U.S. policymakers that Beijing won that global technology transition, there is little agreement about how to win the next.
They have little time to waste. From Brasília to New Delhi, technology has moved to the center of government ambitions to drive growth, improve governance, and modernize security. Indonesian President Prabowo Subianto views the digital sector as essential to diversifying the country’s commodity-reliant economy. Kenyan President William Ruto hopes to boost the country’s “Silicon Savannah” by accelerating cloud migration. Saudi Crown Prince Mohammed bin Salman has made AI central to his “Vision 2030” framework for the kingdom’s modernization. The result is surging global demand not only for AI data centers, but also for cutting-edge digital infrastructure, services, and skilling more broadly.
In the coming years, foreign capitals and corporate boards will make potentially generational decisions about whether to meet this demand by partnering with the United States and its allies or China. These short-term decisions could have generational consequences. Projects to lay a transcontinental submarine cable or build large-scale data centers, for instance, are mapped in decades.
Even virtual cloud and AI services can have long-term stickiness. Imagine the pain of migrating an entire ministry’s data to a new cloud provider, or switching from an AI model that has been fine-tuned with a company’s sensitive data over time. Consider Beijing’s decade-plus struggle to transition its government computers from Windows. First movers reap powerful advantages.
If the stakes are great in the current round of global technology diffusion, so is the United States’ hand. Unlike the transition to 4G and 5G networks, where Western competitors such as Ericsson and Nokia struggled to match Huawei’s and ZTE’s subsidized offerings in emerging markets, the United States enters this technology transition with formidable advantages.
The United States occupies a commanding position in AI, with leadership or leverage over every part of the stack, ranging from chip design, tooling, and fabrication to model training and testing. U.S. companies hold at least a 70 percent share of the global cloud market. In space, Starlink has launched more satellites than all its competitors combined since 2020. Below the waves, three of the top four companies deploying subsea fiberoptic cables—the internet’s backbone—are from the United States or its close allies: SubCom (U.S.), Alcatel (France), and NEC (Japan). China controls the fourth, HMN Technologies (formerly Huawei Marine), which has deployed a mere 7 percent of the world’s submarine cables.
Despite powerful advantages, U.S. success is far from assured. The lesson of the 4G and 5G race is not to mirror China’s state-driven approach or to leave the private sector to fend for itself against Chinese competitors with powerful state backing. Nor is it to rely solely on export controls and other restrictive measures, however necessary those may be. The answer is to make U.S. foreign policy fit the global technology competition.
Washington can start with reforms in three broad areas.
First, unleash the United States’ strategic investment tools. One of Washington’s most promising but underused tools is the International Development Finance Corporation (DFC). Created during the first Trump administration, the DFC makes market-driven investments to advance both humanitarian and national security goals, and it has several tools to attract private capital from equity investments to political risk insurance.
As Congress considers DFC reauthorization—its current mandate expires in September—it should raise the existing cap on its lending authority from $60 billion to at least $100 billion and make strategic technologies and digital infrastructure an explicit priority. Congress should also loosen restrictions that can block DFC from supporting digital infrastructure projects that incidentally benefit high-income countries, which has kept it from financing critical subsea cables in the Indo-Pacific that invariably have landing points in Singapore, a major interconnection hub for the region.
The Export-Import Bank (EXIM) also punches below its weight. EXIM helps level the playing firm for U.S. firms competing abroad with a $135 billion lending limit and tools such as direct loans, loan guarantees, and insurance to de-risk purchases of U.S. exports. The United States once led the world in export financing, but China now dominates. In 2022, Chinese export credit agencies provided $11 billion in export support, compared to just $2.7 billion from EXIM.
Under the first Trump administration, EXIM created a new China and Transformational Exports Program (CTEP) to prioritize investments that counter Beijing’s subsidies and support advanced technologies such as AI and semiconductors. EXIM now aims to reserve at least 20 percent of its support for the program.
Despite progress, EXIM remains plagued with issues. To receive CTEP support, at least 51 percent of the exported content must be American-made—far higher than requirements in competitor agencies. Another requirement that EXIM-supported goods travel on U.S.-flagged vessels also hinders participation. Although well-intentioned, EXIM’s mandate to create jobs can deprioritize the export of low-labor digital exports such as AI and cloud services. Compounding the problem, EXIM is also required to limit defaults across its total lending portfolio to less than 2 percent, fueling risk-aversion.
Washington should reform EXIM for the global technology competition by at least doubling the 20 percent allocation for CTEP, relaxing shipping rules, and counting some allied components toward its content requirement. Lawmakers could also loosen the mandate to support U.S. job creation for digital services and double EXIM’s default cap to encourage more risk-taking.
Second, Washington should turbocharge its commercial diplomacy for technology. Between 2016 and 2020, an average of just 900 U.S. personnel from the State and Commerce departments were deployed abroad for commercial diplomacy, and just a fraction focused on technology. Since 2022, the State Department has taken important steps by establishing a new Bureau of Cyberspace and Digital Policy, a special envoy for critical and emerging technologies, and a course on cyberspace and digital policy tradecraft.
Despite this progress, few U.S. diplomats—and even fewer ambassadors—have deep technology expertise, which means that front-line opportunities to secure key technology bids and shape emerging AI or data policies can go unnoticed or suffer from inadequate staff or substance to engage effectively.
As the administration reforms the State Department, it should reinforce the Bureau of Cyberspace and Digital Policy, which has elevated and streamlined technology diplomacy across the government; expand technology training for foreign service officers; and, more ambitiously, launch a dedicated career track within the diplomatic corps for foreign technology officers.
Two smaller and often overlooked arms of the country’s technology diplomacy are the U.S. Foreign Commercial Service and the U.S. Trade and Development Agency (USTDA). The Commercial Service is a roughly 2,200-person global network of trade specialists that helps U.S. businesses identify and navigate foreign markets. But just 225 of its staff deploy abroad across 80 countries, which means that they constantly struggle to meet demand from U.S. technology companies and foreign partners. The USTDA helps identify and mature commercial opportunities abroad to boost U.S. exports. Digital infrastructure is one of the agency’s four priority sectors, but surging interest has far outpaced current resources.
The Trump administration can turbocharge U.S. commercial diplomacy by consolidating USTDA and the Commercial Service, elevating technology and digital infrastructure as a priority, and allocating more resources and personnel.
Finally, the United States should embrace a newly ambitious vision for technology partnerships. Too often, U.S. and allied firms lose one-off bids to subsidized, politically backed Chinese competitors, even if the firms might prefer to align with the high-tech U.S. ecosystem. Washington should explore how to make such an offer without simply imitating Beijing’s state-led model.
For example, Washington could create opportunities for foreign governments to request strategic technology partnerships that match their specific needs—for example, to accelerate AI adoption in government, expand data center capacity, or improve rural connectivity with low earth orbit satellites.
Washington could lay out clear, broadly consistent criteria as a condition for these partnerships—such as robust IP and cybersecurity protections, divestment from China-linked digital infrastructure, purchase commitments for U.S. goods and services, and even investment in the United States. The Trump administration has begun to model such an approach in its recent deals with Saudi Arabia and the United Arab Emirates, but it could go even further.
If countries meet these conditions, Washington should commit not only to loosening export controls on advanced AI chips, but also to fast-tracking support from the DFC, EXIM, and USTDA; expanding technology trade missions, talent exchange programs, and research collaboration; and facilitating connections with U.S. technology firms. The United States holds the strongest hand in advanced technology and should drive a hard bargain, but it should also be generous when countries agree.
Washington can also do more to align with technology-leading allies on joint investments in strategic emerging markets. For example, Washington could better coordinate with Japan’s Overseas Development Assistance program to boost Open RAN networks across the Indo-Pacific, tap the European Union’s Global Gateway to connect subsea cables to Africa, and support India’s Digital Public Infrastructure to counter China’s “smart city” offerings.
Middle Eastern sovereign wealth funds may raise tricky strategic questions as longer-term partners, but there are other, less controversial players that Washington has yet to fully explore—such as Norway, which has both attractive conditions for AI data centers and the world’s largest sovereign wealth fund. Washington and its allies may struggle to match Beijing’s subsidies on their own, but they can easily do so together.
As the world rushes into an accelerating competition to deploy strategic technologies and digital infrastructure across the globe, the United States has almost everything it needs to prevail—world-leading companies and products, an unrivaled network of technology-leading allies, and an administration eager for reform. What Washington lacks, however, is a vision to harness these strengths in a new model of technology statecraft to help the United States win.
3 notes
·
View notes
Text



An extreme cousin for Pluto? Possible dwarf planet discovered at solar system's edge
A small team led by Sihao Cheng, Martin A. and Helen Chooljian Member in the Institute for Advanced Study's School of Natural Sciences, has discovered an extraordinary trans-Neptunian object (TNO), named 2017 OF201, at the edge of our solar system.
The TNO is potentially large enough to qualify as a dwarf planet, the same category as the much more well-known Pluto. The new object is one of the most distant visible objects in our solar system and, significantly, suggests that the empty section of space thought to exist beyond Neptune in the Kuiper Belt is not, in fact, empty at all.
Cheng made the discovery alongside colleagues Jiaxuan Li and Eritas Yang from Princeton University, using advanced computational methods to identify the object's distinctive trajectory pattern on the sky. The new object was officially announced by the International Astronomical Union's Minor Planet Center on May 21, 2025, and shared in an arXiv pre-print.
Trans-Neptunian objects are minor planets that orbit the sun at a greater average distance than the orbit of Neptune. The new TNO is special for two reasons: its extreme orbit and its large size.
"The object's aphelion—the farthest point on the orbit from the sun—is more than 1600 times that of Earth's orbit," explains Cheng. "Meanwhile, its perihelion—the closest point on its orbit to the sun—is 44.5 times that of Earth's orbit, similar to Pluto's orbit."
This extreme orbit, which takes the object approximately 25,000 years to complete, suggests a complex history of gravitational interactions.
"It must have experienced close encounters with a giant planet, causing it to be ejected to a wide orbit," says Yang.
"There may have been more than one step in its migration. It's possible that this object was first ejected to the Oort cloud, the most distant region in our solar system, which is home to many comets, and then sent back," Cheng adds.
"Many extreme TNOs have orbits that appear to cluster in specific orientations, but 2017 OF201 deviates from this," says Li.
This clustering has been interpreted as indirect evidence for the existence of another planet in the solar system, Planet X or Planet Nine, which could be gravitationally shepherding these objects into their observed patterns. The existence of 2017 OF201 as an outlier to such clustering could potentially challenge this hypothesis.
Cheng and his colleagues estimate 2017 OF201's diameter to be 700 km, which would make it the second largest known object in such a wide orbit. The diameter of Pluto, meanwhile, is 2,377 km. Further observations, potentially using radio telescopes, are needed to determine the object's exact size.
Cheng discovered the object as part of an ongoing research project to identify TNOs and possible new planets in the outer solar system. The object was identified by pinpointing bright spots in an astronomical image database from the Victor M. Blanco Telescope and Canada France Hawaii Telescope (CFHT), and trying to connect all possible groups of such spots that appeared to move across the sky in the way a single TNO might.
This search was carried out using a computationally efficient algorithm produced by Cheng. Ultimately, they identified 2017 OF201 in 19 different exposures, captured over 7 years.
The discovery has significant implications for our understanding of the outer solar system. The area beyond the Kuiper Belt, where the object is located, has previously been thought to be essentially empty, but the team's discovery suggests that this is not so.
"2017 OF201 spends only 1% of its orbital time close enough to us to be detectable. The presence of this single object suggests that there could be another hundred or so other objects with similar orbit and size; they are just too far away to be detectable now," Cheng states.
"Even though advances in telescopes have enabled us to explore distant parts of the universe, there is still a great deal to discover about our own solar system."
The detection also demonstrates the power of open science. "All the data we used to identify and characterize this object are archival data that are available to anyone, not only professional astronomers," says Li.
"This means that groundbreaking discoveries aren't limited to those with access to the world's largest telescopes. Any researcher, student, or even citizen scientist with the right tools and knowledge could have made this discovery, highlighting the value of sharing scientific resources."
TOP IMAGE: A composite image showing the five dwarf planets recognized by the International Astronomical Union, plus the newly discovered trans-Neptunian object 2017 OF201. Credit: Images of dwarf planets: NASA/JPL-Caltech; image of 2017 OF201: Sihao Cheng et al.
CENTRE IMAGE: Credit: Institute for Advanced Study
LOWER IMAGE: Credit: Institute for Advanced Study
2 notes
·
View notes
Text

In today's rapidly improving technology industry, staying ahead and advancing in your career requires more than just technical skills. To thrive in this competitive field, individuals must continuously learn, adapt, and position themselves as valuable assets to potential employers.
In this blog post, we'll explore practical strategies and resources to boost your career in the technology industry.
We'll discuss the value of xml epg guide, provide career-boosting strategies, and offer tips on sharing helpful content to showcase your expertise.
The Power of EPG Guides Online
EPG (Electronic Program Guide) guides aren't just for TV programming; they can also serve as a valuable resource for job seekers in the technology industry.
EPG guides provide a centralized source of information to research and prepare for job opportunities. They offer insights into industry trends, emerging technologies, and the latest developments, ensuring you stay informed and ahead of the curve.
Career Boosting Strategies
To enhance your career prospects in the technology industry, consider these strategies:
Building a Strong Professional Network: Cultivate relationships with professionals in your field through networking events, online communities, and industry conferences. Establishing meaningful connections can lead to mentorship opportunities, job referrals, and valuable insights.
Developing In-demand Technical Skills: Continuously invest in upgrading and expanding your technical skills. Stay updated with emerging technologies and industry trends. Consider pursuing certifications or online courses to gain expertise in high-demand areas, such as cloud computing, artificial intelligence, or cybersecurity.
Crafting an Effective Resume and Cover Letter: Tailor your resume and cover letter to highlight relevant skills and experiences. Showcase your accomplishments, projects, and impact in previous roles. Ensure that your application materials are concise, well-structured, and free from errors.
Acing Job Interviews: Prepare thoroughly for job interviews by researching the company, understanding the job requirements, and practicing common interview questions. Demonstrate your problem-solving abilities, communication skills, and a genuine passion for technology.
Sharing Helpful Content
Creating and sharing relevant, informative content is an effective way to demonstrate your expertise and increase visibility in the technology industry. Consider the following tips:
Start a Tech Blog: Share your knowledge, experiences, and insights through a personal tech blog. Write about industry trends, tutorials, or showcase your project work. Engage with the tech community by commenting on related blogs or participating in forums.
Active Social Media Presence: Utilize social media platforms, such as Twitter, LinkedIn, and GitHub, to share relevant industry news, showcase your projects, and engage with industry professionals. Building an active and professional social media presence can increase your visibility and attract potential employers.
Online Portfolio/Projects: Create an online portfolio showcasing your technical projects, such as coding samples, applications, or website designs. Demonstrating your practical skills through tangible examples can pique the interest of hiring managers and give them an insight into your capabilities.
In the ever-rising technology industry, boosting your career requires a proactive approach. Utilize the power of xml epg guide to stay informed, adopt effective career-boosting strategies, and share helpful content to showcase your expertise.
By continuously investing in your professional development, building a robust network, and actively engaging with the tech community, you'll be well-positioned to advance your career and achieve your goals.
Remember, success in the technology industry requires not only technical proficiency but also a commitment to continuous learning, adaptability, and a passion for innovation.
youtube
8 notes
·
View notes
Text
Breaking into Tech: How Linux Skills Can Launch Your Career in 2025
In today's rapidly evolving tech landscape, Linux skills have become increasingly valuable for professionals looking to transition into rewarding IT careers. As we move through 2025, the demand for Linux System Administrators continues to grow across industries, creating excellent opportunities for career changers—even those without traditional technical backgrounds.
Why Linux Skills Are in High Demand
Linux powers much of the world's technology infrastructure. From enterprise servers to cloud computing environments, this open-source operating system has become the backbone of modern IT operations. Organizations need skilled professionals who can:
Deploy and manage enterprise-level IT infrastructure
Ensure system security and stability
Troubleshoot complex technical issues
Implement automation to improve efficiency
The beauty of Linux as a career path is that it's accessible to motivated individuals willing to invest time in learning the necessary skills. Unlike some tech specialties that require years of formal education, Linux administration can be mastered through focused training programs and hands-on experience.
The Path to Becoming a Linux System Administrator
1. Structured Learning
The journey begins with structured learning. Comprehensive training programs that cover Linux fundamentals, system administration, networking, and security provide the knowledge base needed to succeed. The most effective programs:
Teach practical, job-relevant skills
Offer instruction from industry professionals
Pace the learning to allow for deep understanding
Prepare students for respected certifications like Red Hat
2. Certification
Industry certifications validate your skills to potential employers. Red Hat certifications are particularly valuable, demonstrating your ability to work with enterprise Linux environments. These credentials help you stand out in a competitive job market and often lead to higher starting salaries.
3. Hands-On Experience
Theoretical knowledge isn't enough—employers want to see practical experience. Apprenticeship opportunities allow aspiring Linux administrators to:
Apply their skills in real-world scenarios
Build a portfolio of completed projects
Gain confidence in their abilities
Bridge the gap between training and employment
4. Job Search Strategy
With the right skills and experience, the final step is finding that first position. Successful job seekers:
Tailor their resumes to highlight relevant skills
Prepare thoroughly for technical interviews
Network with industry professionals
Target companies that value their newly acquired skills
Time Investment and Commitment
Becoming job-ready as a Linux System Administrator typically requires:
10-15+ hours per week for studying
A commitment to consistent learning over several months
Persistence through challenging technical concepts
A growth mindset and motivation to succeed
The Career Outlook
For those willing to make the investment, the rewards can be substantial. Linux professionals enjoy:
Competitive salaries
Strong job security
Opportunities for remote work
Clear paths for career advancement
Intellectually stimulating work environments
Conclusion
The path to becoming a Linux System Administrator is more accessible than many people realize. With the right training, certification, and hands-on experience, motivated individuals can transition into rewarding tech careers—regardless of their previous background. As we continue through 2025, the demand for these skills shows no signs of slowing down, making now an excellent time to begin this journey.
2 notes
·
View notes