#Automated Vulnerability Scanning
Explore tagged Tumblr posts
Text
The Role of DAST in Protecting Your Web Applications From Vulnerabilities
Nyuway

As cyber attacks become increasingly sophisticated, enterprises require DAST to help defend their applications against sophisticated cyber threats. By scanning a running application and simulating hacker behavior, it can identify vulnerabilities before enterprising hackers exploit them.
DAST complements static application security testing (SAST) and software composition analysis (SCA), offering additional runtime insights beyond source-code scans. Furthermore, it serves as a valuable companion to manual penetration testing.
Web Application
Dynamic application security testing (DAST) scans running web applications by simulating malicious external attacks and identifying vulnerabilities which could be exploited. DAST can reveal business logic flaws like SQL injection, XSS attacks and authentication issues which often go undetected through static code analysis tools (SAST) or manual penetration testing methods.
While DAST tools can be effective, they do have their limitations. False positives and lack of context can result in security gaps when applied solely. To address this limitation, it may be useful to combine DAST with other methodologies like SAST, IAST or software composition analysis (SCA) in order to create a comprehensive security program.
Implementing DAST into your CI/CD pipeline can ensure vulnerabilities are identified and fixed as code changes are made, leading to decreased costs and speedier time to production. Furthermore, early detection helps minimize accidental releases or potential data breaches; many of today's most harmful cyberthreats rely on unpatched vulnerabilities within running applications for attack.
API Security
DAST tools differ from SAST in that they attack an API without knowledge of its application; instead, this kind of testing mimics how attackers would try to exploit it - thus helping detect vulnerabilities which are harder to spot with traditional testing techniques.
DAST can be particularly effective at protecting web APIs. It can scan API endpoints to expose vulnerabilities that attackers could exploit, such as injection attacks or misconfigurations; and can identify unexpected data leaks or performance issues which might signal deeper security holes.
DAST excels at scanning web application UIs, yet struggles to access and test APIs tucked behind dynamic behavior layers. These layers hide backend API calls behind their respective UI layers until JavaScript code executes and uses an appropriate request format for runtime visibility.
Continuous
As web applications continue to be developed and evolve, security risks continue to shift and adapt accordingly. DAST can help address this challenge effectively.
This type of testing works by simulating attacks a malicious actor might employ to penetrate an application. By employing a black box approach and looking at it from outside in, this approach can detect vulnerabilities which other methods such as SAST or SCA fail to find.
DAST provides feedback and reporting to help developers and security teams prioritize vulnerabilities for remediation. It can also be easily integrated with the CI/CD pipeline to scan at every stage of development, making it easy to detect security issues before they reach production.
DAST can provide an overall picture of your application's vulnerability to threats when used alongside SAST & IAST (which examine code line by line), to form part of an integrated security assessment process. DAST tests entry points such as forms & API endpoints while SAST & IAST examine internal risks like misconfigurations & coding errors to provide a full assessment.
Automated Vulnerability Scanning
DAST differs from traditional static testing by testing an application while it runs, simulating how a hacker would search for vulnerabilities in real time. DAST can run both unauthenticated and authenticated modes to see how the app responds to attacks that typically gain control over an account and reveal sensitive data.
Businesses using advanced DAST solutions that utilize proof-based scanning can quickly identify and prioritize critical vulnerabilities using sophisticated DAST solutions that use proof-based scanning to eliminate false positives, making their teams focus their efforts on real risks that could cause serious breaches instead of spending hours sifting through massive test results.
DAST tools also give development and QA teams detailed information on how they can reproduce and fix vulnerabilities more quickly, so as to minimise disruption in production environments. When integrated into the Continuous Integration and Continuous Deployment pipeline, DAST can detect vulnerabilities at each stage of development and production to decrease chances of breach as well as ensure compliance with regulatory standards such as PSI-DSS or HIPAA.
Managed DAST Services
DAST is an essential part of any comprehensive application security program, and an indispensable element for its testing capabilities. As the most adaptable security testing tool on the market, it can be integrated into each stage of development from early design through quality assurance testing, staging deployment and production deployment. When integrated into an CI/CD pipeline DAST can also help developers identify vulnerabilities before reaching production, saving both time and money in development costs.
DAST works by conducting automated tests simulating external attack behavior without understanding its internals, similar to malicious attackers' tactics, in order to uncover unexpected outcomes and vulnerabilities. Language independent, DAST can detect runtime issues like server configuration problems, authentication/encryption misconfigurations and more that SAST cannot.
To maximize the value of DAST, organizations should set clear security objectives and incorporate it into existing CI/CD and DevOps workflows. This includes developing strategies for handling false positives and regression tests to verify previously fixed vulnerabilities do not resurface. Ideally, DAST should be integrated with CI/CD pipeline so every code push or deployment triggers dynamic security checks automatically.
#Dynamic Application Security Testing (DAST)#Web Application DAST#API Security DAST#Continuous DAST#Automated Vulnerability Scanning
0 notes
Text
Comprehensive Guide on Network Reconnaissance using NmapAutomator
When conducting network reconnaissance or penetration testing, efficiency is key. NmapAutomator is a powerful tool that automates and streamlines the process of network scanning, allowing security professionals to focus on actual penetration testing rather than spending time on repetitive scanning tasks. This comprehensive guide on Network Reconnaissance explores what NmapAutomator is, how to set…
#cybersecurity tools#network reconnaissance#network scanning#network security#nmap#penetration testing#reconnaissance tools#security automation#vulnerability scanning
0 notes
Note
Shadow X Reader Enemies To Lovers Forced Proximity? (Context: I’ve Just Watched The Sonic Movie)
𝐜𝐥𝐨𝐬𝐞𝐫
shadow the hedgehog x fem!rabbit!reader tw: none?? wc: 3093 helloo! sorry this took so long i was just so doubtful with my writing and i still am, plus i've been slightly busy with classes this week but i figured i should post something and 3000 words felt like enough! i really hope you enjoy it thanks for requesting!!

You never imagined that a simple quest for healing could lead you into a nightmare. Tonight, driven by a desperate need to recover a mysterious artifact—one that might mend the wounds of your past—you find yourself standing before the looming entrance of an abandoned research facility. Its rusted doors and crumbling walls speak of secrets long buried, and as you step inside, the cold, stale air wraps around you like a warning.
Your heart beats steadily, each thump echoing the determination that pushes you forward. “I have to do this,” you whisper, the words heavy with memories of what you’ve lost. Not so long ago, you had a life filled with love, laughter, and the warmth of family. But that life was shattered one fateful night—a night when everything you held dear was ripped away by forces you still struggle to understand. That evening, when the sky burned with anger and the streets erupted in chaos, you lost your family. Your parents, siblings, and the home you cherished were all taken in a senseless, calculated attack orchestrated by none other than Dr. Eggman.
Eggman, ever the master of chaos and technological terror, had targeted your town as part of a broader scheme to sow fear and destabilize the region. Under the guise of a sudden catastrophe, his monstrous machines descended upon your neighborhood, unleashing a barrage of explosives and automated drones. Amid the chaos of shattering glass, screeching metal, and the roar of Eggman’s engines, you were left standing alone in the wreckage. The screams of your loved ones still echo in your mind, a constant reminder of that night—and of Eggman’s ruthless ambition.
Almost immediately after stepping into the facility, you sense that you are not alone. As you move cautiously through a corridor lit by sporadic, flickering emergency lights, the sound of measured footsteps echoes behind you. You stop, instinctively turning toward the noise. Out of the shadow emerges a figure whose presence fills the space with an intense, brooding energy.
“Who are you, and what are you doing here?” a deep, gravelly voice demands. The figure steps forward into the weak light, revealing himself to be none other than Shadow the Hedgehog. His crimson eyes burn with suspicion, and his stance is all business—an imposing contrast to your gentle demeanor.
You straighten your back and meet his gaze. “I’m here on my own mission,” you reply firmly. “I’m looking for something that doesn’t concern you. I don’t mean to cause trouble.” Your voice is steady despite the underlying vulnerability, each word carrying the weight of loss—a loss of home, family, and the life you once knew.
Shadow’s eyes narrow. “This facility isn’t a place for someone like you,” he says, his tone laced with contempt. “I have my orders, and I can’t afford distractions.”
Before you can argue further, the building shudders violently. A deep rumble vibrates through the concrete floors, and the emergency lights begin to flash more urgently. Your instincts scream that something is terribly wrong. Then, without warning, a deafening explosion rocks the facility. The blast shatters nearby windows and sends debris tumbling from the ceiling. In an instant, the corridor transforms into a chaotic maze of dust, sparks, and collapsing walls.
“Dammit!” Shadow curses, his eyes scanning for a safe path. As the dust clears, you notice a massive, reinforced door slam shut behind you, sealing off any obvious exit. The roar of falling debris and the creak of twisting metal underscore the urgency of your situation.
“We’re trapped,” you say, your voice barely audible over the cacophony. Despite the danger, you force calm into your tone. “We have to work together if we’re going to get out of here.”
Shadow hesitates, his jaw clenching as he sizes you up. “I work alone,” he grumbles, yet there’s a flicker of reluctant understanding in his eyes. “But right now, I don’t see another option.”
As you both move deeper into the facility, the environment becomes a brutal test of survival. The corridors twist unpredictably, littered with fallen beams and sparking remnants of outdated technology. Every step forward is accompanied by the sound of crumbling concrete beneath your feet. Amid this chaos, your thoughts drift back to that terrible night. You remember the screams, the blinding flashes of fire, and the overwhelming sense of betrayal by a world that once promised safety and love. You recall how you were left standing alone amid the ruins of your former life, with nothing but fragments of memories and a desperate hope that someday you might reclaim a piece of that lost innocence.
“Watch your step,” Shadow orders as you navigate a narrow passage. You comply, carefully placing your feet on the uneven ground, though your eyes betray the growing anxiety “Sorry,” you mumble after a particularly close call when a chunk of debris nearly topples you over.
Shadow grunts. “Just stay focused. We’re not out of this yet.” His tone is terse, but you catch a glimpse of something softer in his eyes—a silent acknowledgment that survival matters more than pride in moments like these.
At one point, as you both scramble to avoid a falling slab of concrete, your path narrows into a claustrophobic tunnel. The ceiling begins to crumble overhead, sending sharp fragments of metal plummeting toward you both.
"Move!" Shadow barked, shoving you forward as the ceiling behind you collapsed. You barely had time to react before he grabbed your wrist and pulled you into a tight space—a maintenance shaft, if you had to guess. Dust and debris clouded the air, the sound of the explosion ringing in your ears. Then, silence. The passage behind you was sealed shut. No way out. No space left between you.
Your breath hitched as Shadow shifted slightly, his arm brushing against yours in the impossibly tight space. The dim emergency light flickered above, barely illuminating the cold steel walls pressing in on both of you. Your back was already against the vent, but no matter how much you tried to shrink into yourself, the space between you and Shadow was nonexistent.
"Move over," you muttered, though you both knew there was no room left.
Shadow let out a short, irritated breath. "If I could, I would." His voice was steady, but there was something tense about it, like he was concentrating on anything but the fact that you were practically pressed against him.
You swallowed hard, hyper-aware of the way his fur barely grazed your arm. The warmth of him was unexpected—contrasting against the cold steel biting into your back. You weren’t supposed to be this aware of him. Not like this.
"Well," you tried, a smirk playing at your lips despite the way your heart was hammering. "Didn’t think you’d be the type to get flustered over something like this."
Shadow's ear twitched, but his expression remained unreadable. His eyes flicked to yours, crimson in the dim light, calculating. "You think I’m flustered?"
You blinked, suddenly unsure if you should be pushing this.
"Please," you scoffed, though it came out weaker than you intended. "I can practically feel you vibrating with tension."
Shadow’s jaw tightened, and instead of snapping back, he moved. Just a fraction of an inch, barely enough to notice—except you noticed everything. His chest almost brushed yours with the subtle shift, and the charged air between you felt suffocating.
"It's not the space that makes this unbearable," he muttered, voice low.
Your breath caught.
You should’ve been able to brush it off. Make some snide remarks. But you didn’t. Because you weren’t sure what he meant, and that uncertainty made your stomach flip.
Silence stretched between you. Too much, too little, too charged. The only thing keeping you grounded was the rhythmic rise and fall of Shadow’s breathing, steady but controlled—like he was trying to keep himself in check.
"As soon as we get out of here," he finally murmured, voice softer now, "this never happened."
You let out a breath you hadn’t realized you were holding, forcing out a chuckle. "Right. Sure."
But you weren’t so sure anymore.
After a few moments, the two of you manage to wriggle out of a small crack in the rubble, though not without a challenge. As you get out, you brush the dust and debris off your dress.
“Are you hurt?” he asks, his voice unexpectedly soft, edged with a concern he rarely shows.
You force a smile. “I’m fine,” you reply. “I… appreciate it.” For a moment, the hostility between you seems to soften into something resembling mutual respect.
Once you’ve taken a brief pause to catch your breath, you exchange a glance with him. “Look,” you say, determination rising in your voice, “I know we just met, but if we don’t trust each other right now, we’re both doomed. I need your help, and you need mine.” Your words carry not just the urgency of survival.
Shadow’s eyes flicker with an emotion you can’t quite place—something that borders on understanding. “Fine,” he says grudgingly. “But we do this my way.”
As you make your way through the dark, crumbling corridors, the conversation inevitably drifts to the ghosts of your past. In a rare moment of quiet, you lower your voice and confess, “I wasn’t always alone. I had a family—a home. It was the happiest time of my life… until that night changed everything.”
You pause, memories pressing down like a weight on your chest. “It was a cold autumn evening. My parents, my siblings, and I were home, laughing, making plans for the future. Then came the sirens, the thunder of engines, the roar of Eggman’s machines. It wasn’t random—it was calculated. A message. A show of power meant to instill fear.” Your voice tightens, but you push through. “Explosions tore through our neighborhood. I remember the screams, the blinding flashes, and the terrible, inescapable realization that my world was ending. I was just a teenager, and in a matter of minutes, I lost everything.”
A heavy silence follows. The only sound is your footsteps against the worn floor and the distant creaks of the collapsing structure around you. You exhale, slow and steady, before continuing.
“After that night, I kept asking myself why. Why my home? Why my family? Why did I survive when they didn’t?” You shake your head, a bitter chuckle escaping. “I never found an answer. Just more emptiness. More silence.” You glance at him, hesitating. “I guess that’s why I kept searching—for something. Some kind of sign that all of this wasn’t meaningless.”
Shadow’s gaze flickers with something unreadable. “And do you really think you’ll find it?”
You let out a breath. “I don’t know,” you admit. “But I have to try.”
His expression shifts, almost imperceptibly, but you catch it—the smallest crack in his usually impenetrable exterior. “I’ve spent too much time in the dark to remember what it means to hope,” he says finally, his voice quieter, laced with regret. “I was created for a purpose. Molded into a weapon. And in the process… I lost parts of myself I’ll never get back.”
The raw admission lingers, mingling with the distant echoes of a collapsing world. You glance at him, then at the path ahead. “Maybe tonight will remind us both of what we’re fighting for,” you say softly. “At least, I hope so.”
Your conversation is cut short as you approach an emergency exit—a reinforced door with a control panel sparking erratically. The panel flashes a series of warnings: “Critical Structural Failure Imminent” and “Override Required.”
Shadow immediately kneels by the panel. “Stand back,” he instructs, his fingers flying over the interface with practiced precision. You watch his every movement, admiring the focus in his eyes even as the tension mounts.
“Is it going to work?” you ask, your voice filled with anxious hope.
He doesn’t look up. “It has to,” he replies tersely. “We don’t have much time.” His tone leaves no room for discussion, yet you sense the determination behind every word.
Desperate to contribute, you rummage through your bag and pull out a worn datapad. “I found some schematics earlier,” you say, tapping on the screen with shaking fingers. “They might provide a workaround.” Your eyes meet his—a silent plea for trust amid the chaos.
Shadow hesitates, then nods. “Fine. Let’s see what you’ve got.” The two of you huddle over the datapad, exchanging ideas and piecing together a solution as the building continues its ominous groaning.
Minutes stretch into what feels like hours. Every beep of the alarm sends your heart into fresh panic, and every spark from the panel reminds you of the stakes. Finally, with one decisive keystroke, the panel displays a confirmation: “Override Successful.” The reinforced door shudders, its mechanisms groaning in protest before it begins to slide open, revealing a sliver of cool, fresh air beyond.
Relief washes over you. “We did it!” you exclaim, your voice ringing with genuine excitement. For the first time that night, hope sparkles in your eyes.
Shadow’s expression remains guarded as he steps forward to fully open the door. “Don’t celebrate yet,” he warns. “We still need to get out without triggering the rest of the collapse.”
You nod, determination shining through. “Right. Let’s move quickly.” Together, you step through the threshold into a narrow corridor leading to the outside—a passage that, against all odds, seems intact.
The air outside is cold and crisp, a stark contrast to the suffocating atmosphere inside. For a moment, you both stand there, catching your breath as the distant sound of crumbling concrete fades behind you. The night sky looms overhead, filled with stars that seem to wink in silent encouragement.
Shadow breaks the silence, his voice unusually soft. “I didn’t think I’d end up saving anyone tonight.” His admission comes more as an observation than a boast, revealing a hint of surprise at the unexpected bond forming between you.
You give him a small smile, your voice gentle and warm. “Maybe we’re both more capable than we think.”
As you both make your way away from the facility, you find temporary refuge in an old, abandoned warehouse on the outskirts of the complex. Inside, the dilapidated structure is dimly lit by a few scattered, flickering bulbs. The silence here offers a brief respite from the chaos you just escaped.
Settling onto a dusty crate, your body still thrumming with adrenaline, you exhale sharply. “Well, we made it,” you mutter, more to yourself than to Shadow. Your hands are still unsteady, your mind replaying every close call, every moment you almost didn’t make it out. “Didn’t think I’d live to see another sunrise.”
You drag a hand down your face, swallowing the bitterness rising in your throat. “I lost everything once—my family, my home, the life I was supposed to have. And for what? Some power-hungry lunatic’s need to prove a point?” Your jaw tightens. “People talk about healing like it’s inevitable. Like time smooths out the edges, makes the pain easier to carry. But some wounds don’t heal. They just fester.”
Shadow sits a few feet away, his gaze fixed on the darkened warehouse interior. “Safety isn’t something I’ve known for a long time,” he says at last. “Maybe… maybe there’s a chance to change that.” His voice carries the weight of years.
You let out a dry chuckle, shaking your head. “I don’t believe in safety. Not really. People like us? We don’t get peace. We get moments—brief pauses between fights. And the second you start thinking otherwise, the world reminds you exactly what it is.” Your fingers drum against your knee before stilling. “I didn’t come here looking for hope. I came here because I needed something—anything—to make this fight mean something.”
Shadow finally turns to you, his crimson gaze unreadable. “And do you think you’ve found it?”
You scoff. “I don’t know,” you admit. “But I keep looking. Because if I stop… then what the hell was the point of surviving?”
His expression shifts—just a flicker, almost imperceptible—but you catch it. The smallest crack in the walls he’s built around himself. “I’ve spent too much time in the dark to remember what it means to hope,” he says finally, his voice quieter, laced with something that almost sounds like regret. “I was created for a purpose. Molded into a weapon. And in the process… I lost parts of myself I’ll never get back.”
The raw admission lingers in the stale air. You don’t offer reassurances or some empty promise that everything will be okay. You both know better than that.
Instead, you push yourself to your feet and glance toward the broken windows, where the first hints of dawn begin to seep through. “Maybe tonight was about more than just survival,” you murmur. “Maybe it was a reminder of what’s still worth fighting for.”
Later, on a creaky rooftop overlooking the sleeping city, the two of you finally allow yourselves a moment of stillness. The night’s horrors are behind you, but they’ve left their marks—some visible, others buried deeper. The cool morning air stings your lungs, but it’s a welcome reminder that you’re still here.
Shadow watches the horizon, his voice quieter now but filled with an unexpected sincerity. “I never imagined I’d find someone like you in all this mess. You’ve made me question everything I thought I knew about trust… and what comes after.”
You huff out a short laugh, shaking your head. “Trust isn’t something I give freely. And hope? I don’t think I have it in me to be the kind of person who believes everything will turn out fine.”
He studies you for a moment before nodding, something resigned yet resolute in his expression. “Perhaps… together, we can find a way to let the light in. Even if just a little.”
As the sun rises higher, casting long shadows across the city, the weight of the night lingers—but so does the unspoken understanding between you. Whatever happens next, neither of you is walking this road alone.
You smirk, stretching the stiffness from your shoulders as you start toward the streets below. “So, what now?”
Shadow glances at you, and for the first time, there’s something almost resembling amusement in his gaze. “Now… we see where this path leads.”
You scoff but fall into step beside him. “Fine. But don’t expect me to start preaching about hope and redemption.”
“I wouldn’t dream of it,” he deadpans.
And with that, the two of you disappear into the waking city, stepping forward not toward certainty, but toward whatever fight comes next.

#i want to pass out#shadow the hedgehog#shadow the ultimate lifeform#shadow#shadow x you#shadow x reader#shadow the hedgehog x reader#ims o tired#eepy
122 notes
·
View notes
Text
Ranchers - All the Stars and Me and You
Some ranchers fluff for @crownpastelyellow Starkissed AU w/ T-male Jimmy < 3333
It would be quite an achievement to lose someone in this cramped shuttle. And yet, as Tango turns back from the cockpit after flicking switches that make the petite vessel purr into automated function, he can’t for the life of him see Jimmy.
Scanning the cramped bones of the ship, Tango tries to pick him out, find the familiar golden fluff and that smile like a lone star in a cold bitter universe.
Vast comos’ roll behind him, their ship basking in the interstellar glow of a deathworld: a condemned colony for the corp. Tango deflates at the radioactive glow and arcs of decades old fission reactions still bubbling and cracking the surface washing over their ship. Tango spares the ‘planet’ at a glance, and wonders if they would blame him for this one somehow, or if they already had someone to pin it on. The sight is hauntingly nostalgic.
The ship veers well out of its orbit before anything too harsh can seep through. By the time the shutters are creaking down the cockpit, the deathworld is a dark ghost in the rear view - a haunting green spectre of a planet.
Leaving the cockpit, Tango takes all of five steps before he’s at the pullout, looking down at the standard issue sheets and the colourful array of blankets Jimmy brought with him when he joined his voyage. They are bundled up, and within that bundle, Tango spies a little tuft of gold sticking out: like bird’s tail feathers hanging out the nest.
“Jim, you okay?” Tango asks, placing a hand on the mound. Shifting beneath the bundle like a great worm beneath the sand, Jimmy pokes his head out.
Doesn’t say a word. Just shakes his head. Tango sighs, massaging his worn temple. “I don’t want to say I told you to wear more layers when we stopped on Skadi-7-”
“It’s not a cold.” Jimmy groans, each word seeming to pain him. His face is set in a sorrowful grimace like someone was permanently twisting a knife into him and he was just gritting and bearing through it. “Cramps.”
Sitting down on the pullout next to Jimmy, Tango blinks down at him. Blinks again. The word settles into his brain and Jimmy looks almost concerned at how thoughtful Tango looks. “Like stomach cramps?”
The fleeting sound of Jimmy’s laugh fills the coffin of a vessel and Tango raises a brow - after that incident with the all you can get seafood stomach cramps had never been funny. Wriggling like a worm, Jimmy rests his head on Tango’s thigh, face momentarily knotted and tense before settling into his warmth.
“Period cramps.” Jimmy can see the hamster return to spinning the cogs of Tango’s mind once again.
“But you’re- wait you’re not a cis guy?” A laugh breaks past his lips, Tango’s astonishment and embarrassed kindling something pleasantly warm in his chest - a brief shot of gender euphoria like a star shooting through the sky. Magnificent. “There’s no way-” Jimmy rises with a bird’s nest of hair and Tango can see the outline of his chest shifting underneath his shirt. Oh.
“Well. You may possess the universe's strongest binder,” Tango chuckles awkwardly, burning with embarrassment. But Jimmy smiles wearily, just lets the pain settle and slumps back against the ship's hull - blankets open, a clear invitation.
“Like you wouldn’t believe.”
Contemplating the empty space to Jimmy - they were in for a long haul, Tango first turns to look down towards the rear of the ship, “Can I get you anything, I think we might have some painkillers in the medpack.”
“That would be great actually… then cuddle?” How can Tango say no to those big eyes, batting so sweetly at him.
Tango returns soon after with some tablets and a water which Jimmy greedily gulps down.
“You okay with being touched?” He asks, a quietly nervous look on his face.
“Tango you dirty old dog, while I’m so vulnerable” The way red erupts off his face makes Jimmy’s heart swell and the pain briefly dissipate. Slumping back into the bed, creaking and refusing to give beneath him, he wiggles to try and find some comfort atop the slab of a mattress.
“I- not like that-” Flames crack and fill the space, Tango blathering while Jimmy reaches up and weakly tugs at his shirt.
“I’m fine with being touched, just come here.” Jimmy chuckles, voice a little worn, fatigued. Currently Jimmy doesn’t possess the strength to pull Tango down, but he comes easily, falling into bed next to him and slotting against him. The pullout is basically a slab of rock with a sheet, but Jimmy found some way to make it hospitable with all of his blankets and pillows. The stark minimalism and whirl of machines feeling just that more alive because of him.
Jimmy nestles close and breathes Tango in the char and soot of his auroma, face burying itself in his chest, tucking himself under his chin. The warmth of his breath against his neck has heat racing down Tango’s spine while his hands ghost Jimmy, still a little nervous to touch him. But his comfort is paramount.
Wiggling close, Tango presses his chest against Jimmy, lets him melt into him with a groan settling in the back of his throat. Jimmy almost jumps out of bed at the sudden warmth tracing down his body when Tango’s hands run down his stomach, but he settles just as quick and melts into him.
Slowly, Tango’s hands dance around Jimmy’s hips, pressing comfortingly into his abdomen, soothing warmth flushing into aching muscles while another meanders down to his thighs and kneads out the throbbing pains. The sight of Jimmy’s face so at ease makes Tango swoon, enraptured by how the tightness of his face unwinds, flutters with an ease he hadn’t known before.
Painful groans and whimper evaporate under Tango’s touch. A warming hand flat against his abdomen, slowly seeping into the cramping and throbbing pains twisting his insides, it doesn’t erase them, but the flames soothe, burn away the bitter edges fraying Jimmy’s body inside out.
He sighs, a deep exhale, chest rising to bump up against Tango before exhaling with a soft smile.
“Thank you.” Jimmy purrs, nestling into the crook of Tango’s neck, lapping at the sweet warmth bleeding out of him. Tango simply hums small agreeable noises, the scruff of his jaw comfortably brushing through his hair, like cats rubbing up against one another.
It’s perhaps the first time in a few weeks that Tango has felt at ease: no patches to weld, no systems screaming at him, no looking over his shoulder - not for now at least.
For now, in the grave cosmos sprawling beyond the confines of their little coffin of a ship does not matter, just the quiet soothing of his partner in crime’s pain. Slow and methodical ministrations absorbing him in quiet focus. In how Jimmy’s body feels in his hands, how he clambers for him, silently begging for just a little more.
He could get used to… and maybe that thought makes his cheeks flush and heart heavy with something foreign. But right now, he can’t bring himself to care much for worries of the future.
#for the crow library#crow fic archive#crow dribble drabble#t.ango#j.immy#trafficshipping#hermitshipping#solidaritek
20 notes
·
View notes
Text
Dr. Omiata's Depravity
Dr. Ellie Omiata, a cardiologist hailing from the 30th century, had achieved everything she could in her profession. Her expertise had saved countless lives, but in the sterilized and automated reality of her time, she felt an aching void.
Ellie became a cardiologist with the desire to protect and care for vulnerable life. Throughout her life, she had a hero complex, an intense desire to shield the fragile, the helpless, the downtrodden. She read countless stories of damsels in distress and imagined herself the knight in shining armor. However, her fantasies were much different... darker, not the hero, but the villain. She hoped to be a heart surgeon, but her desired profession was obsolete. Surely it was an amazing thing, highly successful doctorless organ transplants... but for Ellie, this left her without a place in the world. There were no knights, and now no heart surgeons. People no longer needed saving, she thought. Longing for purpose, Ellie became a temporal explorer, and with countless tales and fantasies in her mind, she took a one-way trip to the savage lands of a war-torn timeline. landing herself smack in the middle of a medieval Nordic civilization.
A stark contrast to her futuristic, technological world. It was a time defined by relentless war, brutal violence, and no place for the frail. Standing amidst the icy landscapes and hardened warriors, Ellie's dark skin and voluminous hair made her a beacon of otherworldly charm, a symbol of exotic mysticism from foreign lands that had not yet been witnessed by these people.
The king, intrigued by her unique appearance and captivated by her advanced medical knowledge, spared her the typical fate of an outsider. They sensed an opportunity in Ellie's keen intellect and apparent strangeness, a utility that could serve their cause well. Yet she didn't ask for a comfortable position within the castle. Ellie asked for something different. Her desires outshined what was believed to be common sense. Her wish granted, Ellie found herself granted a position many loathed, yet she coveted – a captain of the guard. The final word on strategy in the battlefield.
Despite her lack of allegiance to the kingdom, she relished the role that offered an intoxicating cocktail of power and intrigue. Her knowledge of human anatomy, blended with her understanding of martial arts, rendered her an indomitable warrior on the battlefield, effortlessly thwarting the many adversaries that dared to challenge her. Despite her desires to be the hero, she found the most thrill in being the warrior. the ender of heroes and villains alike, what she was... it was hard to tell.
Ellie wasn't moved by battle, what she wanted was power. A sense of control over life and death that she had never felt in her time. The more she acted on her whims, the more she felt that maybe her desires were sick, depraved... selfish. However, there was no going back. From now on, she would fulfill her deepest desires. Her weapon of choice was a large war hammer. A tool of blunt heavy destruction, she felt like this was the best way to exert force while giving her control over how it was applied.
Ellie thought back to the tales of delicate, fair-skinned women being hoisted upon the white horse of their saviors. The desire to live that fantasy was all she could think of, and now she had the position to do it... or some strange version of that.
Ellie wasn't able to ride into the sunset like in the stories, but beggars cant be choosers, and in this world, the desperation of savage war brought everyone to the battlefield at times, and slaughter was blind to beauty. Frailty met quick ends. Not for Ellie though. This was her moment - a crude, perverse twist on her romance fantasies. There was no romance, only salvation in the blood-soaked ground. The savagery of war a canvas where she could paint her unique narrative. Her gaze, wielded like a precision tool, was constantly scanning, evaluating, searching. Among the hordes of battle-hardened soldiers like a depraved beast. Some day, Ellie's eyes quickly fell upon a woman – blonde, fierce, yet possessing a delicate grace. Her pale visage a vibrant beacon. The woman was like a strikingly vivid palette amidst the monochrome of warriors, an unexpected anomaly in a battlefield bereft of grace.
Ellie became the self-appointed guardian of this precious gem, determined to protect her from the clutches of her own bloodthirsty squad which had a hunger for easy pickings. The sight of this radiant woman made her heartbeat race, not with bloodlust but with a deep, undeniable fascination. It was as if the chaotic battlefield had morphed into an exhilarating treasure hunt, the treasure being these living, breathing, beautiful Nordic women. Ellie's intentions were clearer to her than ever - to salvage these creatures from the cruel jaws of war, and to preserve their splendor for herself. Ellie could see the perversion of her instincts in full display, but the desire was so great, she couldn't stop herself. The battlefield, a dreaded arena of death, had now become her playground, a hunting ground to satiate her unorthodox desires. The rush of adrenaline in her veins was palpable as she locked eyes with the blonde beauty.
She was yet another savage on the battlefield, but with the precision of a surgeon. Even as a predator, surely her prey would at least be grateful for a better outcome than death, she thought. As they engaged, the woman's sword was fast, though Ellie herself was graceful, and predicting. She studied this game of war like chess and became a grand master. Ellie struck at the perfect moment, sweeping the blonde's feet from beneath her, casting her to the earth.
She then kicked away the sword, leaving the woman defenseless and bewildered on the rough battlefield floor. The sight of this exquisite creature, rendered vulnerable amidst the grit and grime, filled Ellie with an unprecedented sense of desire. Every exasperated breath filling this magnificent form lit up Ellie's senses. It was nothing like her fantasies... it was better. The battlefield had always been a stage for displaying might, but for Ellie, this was a new, intoxicating form of dominance.
With her adrenaline surging, Ellie approached the woman cautiously, the woman's chest heaving vividly beneath her. The blonde was defeated, awaiting the cruel and merciless strike of the heavy mallet, but defiant. To the look of confusion in those blue eyes, Ellie gingerly placed the head of her war hammer over the woman's billowing chest. She stood there in awe, feeling the rapid pulse of delicate life through the handle. As she pressed down harder, the woman's heartbeat became more vivid, then stuttered, a defiant drumroll against the encroaching steel.
Ellie reveled in the sensation. The strength of this woman's heart, its indomitable vitality, was now at her mercy. It was a testament to the woman's vibrant life, yet it was helpless under Ellie's power. The heart struggled and strained under the oppressive weight, succumbing slowly to the inexorable pressure.
Ellie observed the woman's battle for breath, her struggle against the metal, with an admiration tinged with disbelief. This was her treasure, her trophy of war, and she found herself enchanted by the rawness of this spectacle. Even as the woman's vigor ebbed away, her confusion turning to exhaustion, Ellie was in awe at the fight she put up. Her eyes, once fierce, now pleading and confused, fluttered close as unconsciousness claimed her. Finally, Ellie lifted her weapon.
As the woman lie there unconscious, the feeling of her heart's struggle was vivid in Ellie's mind. She straddled the woman and listened in. Its beats were soft and slow but recovering.
A surge of satisfaction rippled through Ellie at the sight of her captured prize, this fair-skinned angel now her responsibility. She had now to protect her trophy from the inevitable spoils of war, a task she accepted with a curious blend of anticipation and determination. This was her battlefield, and she had just taken her first treasure... alive. Ellie, carrying her new trophy, departed from the blood-soaked battlefield towards her home in the kingdom. Usually, a mere shelter from the harsh Nordic weather. With a blend of anticipation and caution, she bound the woman's wrists and ankles together, taking care not to make it too tight.
She gently lowered the woman onto the bed, her taut form a stark contrast against the rough-hewn linens. Ellie then lied down beside her, enveloping the unconscious woman in a tender hold to warm her. The role she played shifted between pet, trophy, and love at Ellie's whims. Her head found a resting place on the woman's chest, and as Ellie closed her eyes, she was serenaded by the rhythmic lullaby of the woman's recovering heartbeat.
With every beat that echoed against her ear, Ellie found herself more and more captivated by the living, breathing prize she had claimed. Her fingers tentatively ventured across the woman's body, exploring the gentle curve of her waist, the softness of her relaxed belly. She traced the delicate blue streaks beneath the woman's pale skin - the veins that carried life and vitality within this ethereal creature.
Ellie marveled at her fortune, her chest swelling with a sense of triumph and disbelief. She had taken her first victory, and claimed s supple, delicate, breathing trophy with a heartbeat as her spoils of war.
As she lay there, the woman's steady resilient life lulling her into a trance-like state, Ellie knew she was in the right timeline.
70 notes
·
View notes
Text
Shadows Within Shadows
Seventeen | part 1 part 2 part 3 part 4 part 5
@w-40-k @ghrgrsfdesfrfg
Cassian moved through the environmental control ducts with practiced ease, the modified bodyglove beneath his armor preventing skin contact with the metal surfaces. He had spent the morning cycle shadowing the First Chaplain. It was a dangerous but necessary undertaking.
The Word Bearer had wasted no time. Already questioning the crew, already narrowing his search.
"Predictable", Cassian whispered to the darkness, his voice barely audible even to his own enhanced hearing. "But efficient."
He paused at a junction, checking the ship's schematics displayed on his helm's feed. The young serf from the chapel would be returning to the lower decks soon. A perfect opportunity.
Cassian had contingencies for this scenario. Contingencies within contingencies. The Night Lords excelled at planning for betrayal and discovery, it was in their blood, in the lessons taught on the shadowed Nostramo where trust meant vulnerability.
He made his way to an access point two decks below, emerging into a rarely used storage compartment. Working quickly he removed several components from a hidden compartment in his armor, assembling them into a small device the size of his palm.
A timer, a localized electromagnetic pulse generator and a recorded whisper.
Simple. Effective.
He checked his chronometer. The serf would be passing nearby in approximately three minutes. Enough time to position the device and withdraw to a suitable observation point.
The corridors here were nearly empty this time of ship's day. Cassian moved with purpose, his armor's systems projecting the authorization codes of maintenance personnel to any passive security scans. Another gift from his Legion's tech-marines.
He reached the desired location, a junction where three corridors met, poorly lit due to a faulty luminator that maintenance had been 'planning to fix' for weeks. He'd ensured the repair requests remained low-priority through careful manipulation of the work order system.
The device was magnetized to adhere to the underside of a ventilation grille. Cassian set the timer, attached it and withdrew into an adjacent service alcove.
Two minutes later the serf appeared, moving with the slightly accelerated pace of someone who had spoken with their betters and lived to tell the tale of it.
The device activated precisely as planned.
First a localized EMP pulse that would disrupt pict-recorders and any other monitoring equipment for ten seconds, not long enough to trigger automated alerts but sufficient for his purpose.
Second in the sudden dimming of lights that followed the pulse, a whisper emanating from the shadows: 'I always watch.'
Third the faintest gleam of reflected light, like eyes in darkness, from a secondary component positioned across the junction.
The effect on the serf was everything Cassian had hoped for. The young man froze, eyes wide, breath caught in his throat. Then he ran, not panicked but urgently, the way prey moves when it knows the predator has chosen not to strike. This time.
Cassian retrieved both devices once the corridor was clear. No evidence. No trace. Just another sighting to add to the legend and more importantly another witness to confirm the existence of 'Cassian' to the First Chaplain.
Feed the myth. Control the narrative.
He made his way to a different section of the vast ship, his mind already working through the implications of Erebus' inquiries. The Word Bearer knew something was aboard, likely suspected a Night Lord now or soon would. But suspicion wasn't confirmation.
Cassian needed to know what the chaplain was truly doing here. The official diplomatic mission between Word Bearers and Luna Wolves seemed genuine on the surface but Erebus spent too many hours in private meetings, too much time accessing restricted data archives.
"Two can hunt", Cassian murmured as he entered a maintenance tunnel that would take him to the officer's deck. While Erebus questioned Torgan, Cassian would pay a visit to the First Chaplain's quarters.
Not to confront. Not yet. Only to observe, to gather intelligence of his own.
A hunt worked both ways, after all.
He paused at a junction, listening to the distant voices of a maintenance crew. His enhanced hearing easily picked out their conversation, mundane complaints about shift rotations and food quality. Nothing of value.
But their presence meant he would need to take an alternate route. Adaptability was survival in the shadows.
Cassian consulted his mental map of the vessel, plotting a new course. As he moved he considered what he knew of Word Bearers in general and Erebus in particular.
Lorgar's sons had a reputation for zealotry that bordered on fanaticism. Their campaigns were marked by compliance followed by conversion, not just to Imperial Truth but to something deeper. Something that felt wrong to Cassian, though he couldn't tell why.
And Erebus... The First Chaplain was respected by many, his voice carried weight with Lorgar himself. But something felt off.
What business would such a figure have skulking about the Vengeful Spirit in secret?
The question nagged at Cassian as he navigated the ship's innards. Perhaps tonight would provide answers.
Sixteen days remained until the Word Bearers departed. Sixteen days to uncover Erebus's true purpose.
Sixteen days to win this shadow game.
#warhammer#warhammer 40000#warhammer 40k#warhammer 30k#warhammer fanfic#night lord oc#fuck erebus#erebus#horus heresy#pre heresy
4 notes
·
View notes
Text
a review of 'the conversation' dir. francis ford coppola
There are moments in 'The Conversation' where a phrase is recontextualized for the second, third, or fourth time, and you remember why Coppola's screenplays are worth analyzing on their own. There are scenes that perfectly convey something intangible and unwritable - the distanced shots emphasizing the emptiness of Caul's warehouselike office while he stumbles through a social situation, the way Coppola and cinematographer Bill Butler allow phone cables and audio wires to stretch across the screen while Caul typically sits in silence. Then there are moments totally taken up by the actors on screen: Harrison Ford looming, making the taller Hackman look vulnerable. John Cazale in one of his few roles, all perfect, a needy and scummy surveyor's assistant, the worst possible confidante. Gene Hackman's sighs, eye motion, irregular tone, passion and dejection.
It's funny how similar Hackman looks 25 years later in 'The Royal Tenenbaums' playing the boisterous and frivolous title character, someone completely unaware of his deficiencies. The polar opposite of Caul, who has stripped away so much of his identity that whatever remains lies just beneath raw nerves. Whenever others try to get closer to him, Caul panics and pulls back. Not merely paranoid but empty: Caul has nothing and nobody, and his yearning for connection is sincere but so desperate and tentative that it can seemingly never be satisfied.
The tragedy of 'The Conversation' is that Caul's courageous moral struggle & flailing attempts to connect only serve to alienate him further. He cannot be understood: no one's interested, and there's nothing inside him anyway. He cannot understand others: small moments of trust result in embarrassment and betrayal, personally and professionally, and he overestimates his own insight into the central conversation he surveils. His interventions are useless. The ugly plot he thought he'd uncovered plays out around him as if he weren't even there.
Caul figures this out far too late. His own tools force him to submit (they even play him a recording of his own saxophone to prove he's been tapped, a nice touch). In one of the final scenes, the camera scans his apartment as if it were automated, swinging to one side and back again. He's there, but he's no more important than the wallpaper to us, his own voyeurs.
4 notes
·
View notes
Text
Why Python Will Thrive: Future Trends and Applications
Python has already made a significant impact in the tech world, and its trajectory for the future is even more promising. From its simplicity and versatility to its widespread use in cutting-edge technologies, Python is expected to continue thriving in the coming years. Considering the kind support of Python Course in Chennai Whatever your level of experience or reason for switching from another programming language, learning Python gets much more fun.

Let's explore why Python will remain at the forefront of software development and what trends and applications will contribute to its ongoing dominance.
1. Artificial Intelligence and Machine Learning
Python is already the go-to language for AI and machine learning, and its role in these fields is set to expand further. With powerful libraries such as TensorFlow, PyTorch, and Scikit-learn, Python simplifies the development of machine learning models and artificial intelligence applications. As more industries integrate AI for automation, personalization, and predictive analytics, Python will remain a core language for developing intelligent systems.
2. Data Science and Big Data
Data science is one of the most significant areas where Python has excelled. Libraries like Pandas, NumPy, and Matplotlib make data manipulation and visualization simple and efficient. As companies and organizations continue to generate and analyze vast amounts of data, Python’s ability to process, clean, and visualize big data will only become more critical. Additionally, Python’s compatibility with big data platforms like Hadoop and Apache Spark ensures that it will remain a major player in data-driven decision-making.
3. Web Development
Python’s role in web development is growing thanks to frameworks like Django and Flask, which provide robust, scalable, and secure solutions for building web applications. With the increasing demand for interactive websites and APIs, Python is well-positioned to continue serving as a top language for backend development. Its integration with cloud computing platforms will also fuel its growth in building modern web applications that scale efficiently.
4. Automation and Scripting
Automation is another area where Python excels. Developers use Python to automate tasks ranging from system administration to testing and deployment. With the rise of DevOps practices and the growing demand for workflow automation, Python’s role in streamlining repetitive processes will continue to grow. Businesses across industries will rely on Python to boost productivity, reduce errors, and optimize performance. With the aid of Best Online Training & Placement Programs, which offer comprehensive training and job placement support to anyone looking to develop their talents, it’s easier to learn this tool and advance your career.

5. Cybersecurity and Ethical Hacking
With cyber threats becoming increasingly sophisticated, cybersecurity is a critical concern for businesses worldwide. Python is widely used for penetration testing, vulnerability scanning, and threat detection due to its simplicity and effectiveness. Libraries like Scapy and PyCrypto make Python an excellent choice for ethical hacking and security professionals. As the need for robust cybersecurity measures increases, Python’s role in safeguarding digital assets will continue to thrive.
6. Internet of Things (IoT)
Python’s compatibility with microcontrollers and embedded systems makes it a strong contender in the growing field of IoT. Frameworks like MicroPython and CircuitPython enable developers to build IoT applications efficiently, whether for home automation, smart cities, or industrial systems. As the number of connected devices continues to rise, Python will remain a dominant language for creating scalable and reliable IoT solutions.
7. Cloud Computing and Serverless Architectures
The rise of cloud computing and serverless architectures has created new opportunities for Python. Cloud platforms like AWS, Google Cloud, and Microsoft Azure all support Python, allowing developers to build scalable and cost-efficient applications. With its flexibility and integration capabilities, Python is perfectly suited for developing cloud-based applications, serverless functions, and microservices.
8. Gaming and Virtual Reality
Python has long been used in game development, with libraries such as Pygame offering simple tools to create 2D games. However, as gaming and virtual reality (VR) technologies evolve, Python’s role in developing immersive experiences will grow. The language’s ease of use and integration with game engines will make it a popular choice for building gaming platforms, VR applications, and simulations.
9. Expanding Job Market
As Python’s applications continue to grow, so does the demand for Python developers. From startups to tech giants like Google, Facebook, and Amazon, companies across industries are seeking professionals who are proficient in Python. The increasing adoption of Python in various fields, including data science, AI, cybersecurity, and cloud computing, ensures a thriving job market for Python developers in the future.
10. Constant Evolution and Community Support
Python’s open-source nature means that it’s constantly evolving with new libraries, frameworks, and features. Its vibrant community of developers contributes to its growth and ensures that Python stays relevant to emerging trends and technologies. Whether it’s a new tool for AI or a breakthrough in web development, Python’s community is always working to improve the language and make it more efficient for developers.
Conclusion
Python’s future is bright, with its presence continuing to grow in AI, data science, automation, web development, and beyond. As industries become increasingly data-driven, automated, and connected, Python’s simplicity, versatility, and strong community support make it an ideal choice for developers. Whether you are a beginner looking to start your coding journey or a seasoned professional exploring new career opportunities, learning Python offers long-term benefits in a rapidly evolving tech landscape.
#python course#python training#python#technology#tech#python programming#python online training#python online course#python online classes#python certification
2 notes
·
View notes
Text
Burp Suite
This week I wanted to cover a powerful tool that assists in web application security. Burp Suite is a well-known tool developed by PortSwigger. Burp Suite is an integrated platform used to test web application security by using a variety of different features it provides. One of these features Burp Suite has is an intercepting proxy that allows you to inspect and modify traffic between the browser and the server at each step. Scanner allows you to automatically detect certain vulnerabilities like SQL injection and cross-site scripting. Intruder automates custom attacks to test certain security parameters, generally passwords. Repeater allows for manual modification and replaying of edited requests for more in-depth testing.
All in all Burp Suite provides a simplified way and process for identifying and discovering vulnerabilities. It has a very user-friendly interface that assists in applying all the different features and makes it easy to learn. It also allows for user consummation that allows users to create custom rules and integrate third-party extensions. It is one of the most renowned tools in cyber security and brings an active and engaging community along with it. Burp Suite I is something I highly recommend to those striving to develop their cyber security skills to get their hands on. Not only will you become more proficient in the tool itself, but it will also teach you about how web applications and servers work.
Source:
2 notes
·
View notes
Text
Best Practices for Data Lifecycle Management to Enhance Security
Securing all communication and data transfer channels in your business requires thorough planning, skilled cybersecurity professionals, and long-term risk mitigation strategies. Implementing global data safety standards is crucial for protecting clients’ sensitive information. This post outlines the best practices for data lifecycle management to enhance security and ensure smooth operations.
Understanding Data Lifecycle Management
Data Lifecycle Management (DLM) involves the complete process from data source identification to deletion, including streaming, storage, cleansing, sorting, transforming, loading, analytics, visualization, and security. Regular backups, cloud platforms, and process automation are vital to prevent data loss and database inconsistencies.
While some small and medium-sized businesses may host their data on-site, this approach can expose their business intelligence (BI) assets to physical damages, fire hazards, or theft. Therefore, companies looking for scalability and virtualized computing often turn to data governance consulting services to avoid these risks.
Defining Data Governance
Data governance within DLM involves technologies related to employee identification, user rights management, cybersecurity measures, and robust accountability standards. Effective data governance can combat corporate espionage attempts and streamline database modifications and intel sharing.
Examples of data governance include encryption and biometric authorization interfaces. End-to-end encryption makes unauthorized eavesdropping more difficult, while biometric scans such as retina or thumb impressions enhance security. Firewalls also play a critical role in distinguishing legitimate traffic from malicious visitors.
Best Practices in Data Lifecycle Management Security
Two-Factor Authentication (2FA) Cybercriminals frequently target user entry points, database updates, and data transmission channels. Relying solely on passwords leaves your organization vulnerable. Multiple authorization mechanisms, such as 2FA, significantly reduce these risks. 2FA often requires a one-time password (OTP) for any significant changes, adding an extra layer of security. Various 2FA options can confuse unauthorized individuals, enhancing your organization’s resilience against security threats.
Version Control, Changelog, and File History Version control and changelogs are crucial practices adopted by experienced data lifecycle managers. Changelogs list all significant edits and removals in project documentation, while version control groups these changes, marking milestones in a continuous improvement strategy. These tools help detect conflicts and resolve issues quickly, ensuring data integrity. File history, a faster alternative to full-disk cloning, duplicates files and metadata in separate regions to mitigate localized data corruption risks.
Encryption, Virtual Private Networks (VPNs), and Antimalware VPNs protect employees, IT resources, and business communications from online trackers. They enable secure access to core databases and applications, maintaining privacy even on public WiFi networks. Encrypting communication channels and following safety guidelines such as periodic malware scans are essential for cybersecurity. Encouraging stakeholders to use these measures ensures robust protection.
Security Challenges in Data Lifecycle Management
Employee Education Educating employees about the latest cybersecurity implementations is essential for effective DLM. Regular training programs ensure that new hires and experienced executives understand and adopt best practices.
Voluntary Compliance Balancing convenience and security is a common challenge. While employees may complete security training, consistent daily adoption of guidelines is uncertain. Poorly implemented governance systems can frustrate employees, leading to resistance.
Productivity Loss Comprehensive antimalware scans, software upgrades, hardware repairs, and backups can impact productivity. Although cybersecurity is essential, it requires significant computing and human resources. Delays in critical operations may occur if security measures encounter problems.
Talent and Technology Costs Recruiting and developing an in-house cybersecurity team is challenging and expensive. Cutting-edge data protection technologies also come at a high cost. Businesses must optimize costs, possibly through outsourcing DLM tasks or reducing the scope of business intelligence. Efficient compression algorithms and hybrid cloud solutions can help manage storage costs.
Conclusion
The Ponemon Institute found that 67% of organizations are concerned about insider threats. Similar concerns are prevalent worldwide. IBM estimates that the average cost of data breaches will reach 4.2 million USD in 2023. The risks of data loss, unauthorized access, and insecure PII processing are rising. Stakeholders demand compliance with data protection norms and will penalize failures in governance.
Implementing best practices in data lifecycle management, such as end-to-end encryption, version control systems, 2FA, VPNs, antimalware tools, and employee education, can significantly enhance security. Data protection officers and DLM managers can learn from expert guidance, cybersecurity journals, and industry peers’ insights to navigate complex challenges. Adhering to privacy and governance directives offers legal, financial, social, and strategic advantages, boosting long-term resilience against the evolving threats of the information age. Utilizing data governance consulting services can further ensure your company is protected against these threats.
3 notes
·
View notes
Text
Yaim'ol - Chapter 6 - Returns
yaim'ol - [yai-MOHL] - return, homecoming
Pairing: Sev x F!Jedi OC, Scorch x F!Jedi OC Characters: Delta Squad (Republic Commando), F!Jedi OC Cin Rating: M - Explicit content in later chapters Warnings: Gore, Canon-typical violence, angst, smut (later chapters), descriptions of injury, force osik.
Following on from the end of Republic Commando, Sev and Cin must make their way through the galaxy, overcoming trials and tests in a bid to keep themselves alive long enough to reunite with their squad.

“You sure about this, mesh’la?”
Sev’s tone was stern and low, an indication of his discomfort at the situation they found themselves in.
Being back in his full armour had never felt so foreign, the weight of it no longer a comfort.
He hadn’t repainted it. No point. He doubted he’d be able to hold back if anyone went for Cin. Better they knew who’d taken them down, or who’d died fighting for what little freedom he had left.
“Yeah,” she breathed, nodding slowly, sounding almost as if she was trying to convince herself, “yeah. I… I need to know.”
It was a risk, she knew that. Returning to Coruscant felt almost like a death sentence, regardless of the codes the wookie delegation had supplied them as cover.
Although their crash on Kashykk was only a few months prior, it had felt so much longer, every day sat waiting, planning, passing like a lifetime.
Now, piloting the tiny shuttle they’d been given, they felt vulnerable as the codes were keyed in upon an automated request from Coruscant control, clearance given almost instantly. It felt… too easy.
The ever present hive of activity swam into view, the traffic lanes of Coruscant flowing as always, painting lines of light across the sky.
It was like nothing had changed at all, and something struck Cin in the chest, her stomach tightening.
“How is everyone still just… going on?” she breathed, Sev shifting next to her, silently wondering the same.
For both of them, the galaxy had fallen apart, their entire lives upended, and yet… life went on. Worlds kept spinning, trade continued, and it felt so unfair.
“Guess for most people, Empire or Republic, nothing really changed,” he huffed, scanning the skyline. It felt so familiar, bar one thing. He spotted it before Cin, gritting his teeth when he saw her eyes lock onto the area the Jedi Temple had once stood.
He heard her gasp as they passed in clear view of the now ruined buildings, the giant halls nothing more than a pile of rubble now, surrounded by skycranes, being cleared away.
“It’s really gone,” she murmured, breath hitching as she tried to process what she was seeing, “the halls, the chambers, the archives…”
Her blood ran cold as she turned back to Sev, eyes wide and tear rimmed.
“Sev… The archives held holocrons,” she explained quickly, voice quiet, almost as if she was scared someone would hear, “containing the names and home planets of every Jedi, and not just the ones who were at the temple… They have the names of every Force sensitive child in the known galaxy, the ones who were to become Jedi recruits…”
Cold realisation hit them both as Sev growled, shaking his head.
“What we’re doing is dangerous enough, mesh’la. We need to focus on the plan. If it goes well, if we can get in and out undetected, there might be a chance, but…”
He hated himself as she turned away with a frown. She knew he was right, but it didn’t sting any less. Logic seemed to go out the window these days though, and Cin cursed her lack of control.
She felt herself slipping, giving into emotion more and more since the Order went out, and it was troubling her on a level she couldn’t explain to Sev.
“I know, I know,” she muttered, a bitter tone in her voice she didn’t quite catch in time before it slipped out. Heaving a sigh, Sev placed a comforting hand on her shoulder, squeezing gently.
“Can’t save the galaxy all at once, ner kar’ta,” he reminded her, something she’d said to him once, on a particularly difficult mission gone wrong. Smiling softly, she felt a little lighter, grateful for his presence at her side as she lifted her own hand to cover his, leaning into his hold.
“I don’t tell you how much I love you enough,” she murmured, chuckling as Sev’s face went bright red, his expression still stern as he fought a smile, shaking his head and turning back to put his bucket on.
“Ner cyare,” he all but whispered back, her smile widening before it faded as their docking port came into view, the large wings of the ship automatically folding up against the sides as they were brought down by the auto-landing system. “You good?”
“As I’ll ever be,” she sighed, releasing the controls and grabbing her lightsaber, clipping it onto the rear clips of her belt, out of sight.
She knew it was dangerous to be carrying it, that it would identify her in an instant, but she couldn’t bear the thought of leaving it, of being without it, the last piece of a life she’s lost she had left.
Swallowing hard, she grabbed the huge grey cloak Tarful had gifted her before they left, the delicate silver embroidery creating sweeping images of the trees of Kashyyyk.
“Plan?” Sev prompted as the airlock hissed, pressure from the systems releasing while the door lowered, the stale, recycled air of Coruscant hitting her like a speeder bike.
“Level 1345,” she recited, drawing her hood up over her head as she steeled herself to take her first steps onto an Imperial Coruscant, “find the ventilation ducts to the academy, climb them and infiltrate the facility.”
“Then?”
“Find a console, use the generic trooper codes to find the others, download the location onto a data spike and leave the same way we came in.”
Sev nodded in approval, letting out a soft huff of laughter, one that drew him a scathing look from Cin.
“What?” she demanded, a little hurt by his reaction.
“Boss is gonna be proud as kriff of you. You know that?” he murmured, grinning under his helmet as Cin flushed brightly, shaking her head.
“You can tell him all about it when we get him back,” she grumbled, pulling her cloak tightly around her as she began to descend the ramp into the docking bay, keeping her senses open with the Force.
But even with her senses attuned, the anxiety pulsing through her blinded her to the set of dark eyes watching as they exited the ship, ones that followed their progress long after they entered the elevator to the lower levels.
*-*-*
“Hurry up, will you?”
“I’m going as fast as I can.”
“Well go faster!”
“Not the first time you’ve asked that of me.”
“Sev, I swear to the Maker…”
In another life, they might have been laughing as Sev struggled with the latches on the ventilation shaft, the metal tight and rusted from years of neglect.
They were pressed into a dingy alley in the lower levels of Coruscant, the skitter of rats and tookas and the hum of electricity filled the humid air, the bustle of homes and business of various levels of disrepute operating mere yards away covering what little noise they were making.
Still, Cin continued to glance up and down the alleyway as she leant against the wall behind her, trying not to draw attention as she kept watch, hissing back to Sev.
“I thought you were supposed to be a Commando. How hard is a vent cover?”
“Not exactly covered in basic training,” Sev grunted in response, the irritation in his modulated voice clear.
With a screech, the cover finally moved, Cin wincing at the sound, looking up and down the alley, making sure they hadn’t drawn any unwanted attention.
“Got it!” Sev chuckled triumphantly, lifting the huge cover behind some of the bins a little further down, keeping it out of sight.
“Yeah, I noticed,” Cin retorted sharply, rolling her eyes, “and half of the level, most likely. We need to move.”
“You worry too much,” Sev smirked, trying to placate her, the anxiety in her voice impossible to miss.
“And you don’t worry enough,” she chastised him, “you know what we’re risking here.”
“I do,” he replied, serious now as he stared down at her, instinct making him reach up and remove his bucket as she shuffled around, looking up into the pipe.
“Gonna be a tight fit,” she murmured, Sev snorting softly, expression apologetic when she turned round, glaring at him.
“Just trying to lighten the mood,” he offered, reaching out a hand and wrapping it around her waist, pulling her close, “and trying to remind myself that being terrified isn’t going to help us.”
Cin sighed, dropping her head to his chest for a moment, hesitation taking over.
“Maybe this is a bad idea,” she whispered against his neck, “maybe there’s another way…”
“There probably is,” Sev soothed her, gloved fingers cording through her hair, “but it would take a lot longer. Who knows if they’re even together any more? The faster we move, the faster we’re all back together.”
Something in his tone caught Cin by surprise, the flecks of emotion showing through as he spoke. Through all of this, she’d failed to consider just how hard Sev was finding this, being separated from his batchmates.
They’d been together since birth, raised together on Kamino. They’d shared meals, bunks, missions, even her. They did everything together. To be alone after all those years…
Reaching up, she cupped his cheek, tilting his head down enough to brush her lips over his gently, the promise of her return unspoken.
“It’ll be just like Corellia,” she smiled softly, his lips lilting with the memory, “in and out, no-one will even notice.”
“Maybe we can celebrate the way we did then too,” Sev chuckled, glad for the tiny sliver of normality that passed between them, his heart still hammering away in his chest.
“Deal,” she grinned, leaning up to kiss him once more before she turned back to the vent, drawing in a steadying breath. “Okay, Commando. Give me a boost,” she ordered playfully, Sev letting out a low chuckle.
“Sir, yes Sir,” he smirked, bending down on one knee and placing his hands over it. Within seconds, she’d climbed onto him and was helped up into the vents, the sounds of her movement fading quickly.
“Be safe, mesh’la,” Sev murmured after her, reaching for his helmet and replacing it quickly, beginning his watch.
#star wars#star wars the clone wars#republic commando fanfiction#republic commando#clone commando sev#clone commando sev x OC#the clone wars#Commander Fox#daniwrites#dani writes#star wars republic commando
4 notes
·
View notes
Text
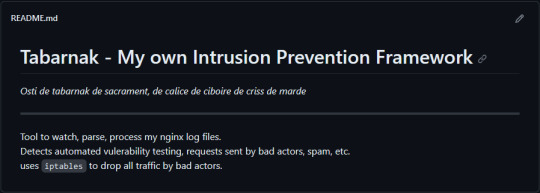
(this is a small story of how I came to write my own intrusion detection/prevention framework and why I'm really happy with that decision, don't mind me rambling)
Preface
About two weeks ago I was faced with a pretty annoying problem. Whilst I was going home by train I have noticed that my server at home had been running hot and slowed down a lot. This prompted me to check my nginx logs, the only service that is indirectly available to the public (more on that later), which made me realize that - due to poor access control - someone had been sending me hundreds of thousands of huge DNS requests to my server, most likely testing for vulnerabilities. I added an iptables rule to drop all traffic from the aforementioned source and redirected remaining traffic to a backup NextDNS instance that I set up previously with the same overrides and custom records that my DNS had to not get any downtime for the service but also allow my server to cool down. I stopped the DNS service on my server at home and then used the remaining train ride to think. How would I stop this from happening in the future? I pondered multiple possible solutions for this problem, whether to use fail2ban, whether to just add better access control, or to just stick with the NextDNS instance.
I ended up going with a completely different option: making a solution, that's perfectly fit for my server, myself.
My Server Structure
So, I should probably explain how I host and why only nginx is public despite me hosting a bunch of services under the hood.
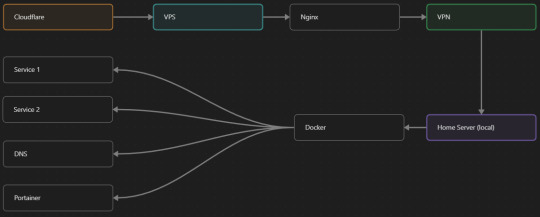
I have a public facing VPS that only allows traffic to nginx. That traffic then gets forwarded through a VPN connection to my home server so that I don't have to have any public facing ports on said home server. The VPS only really acts like the public interface for the home server with access control and logging sprinkled in throughout my configs to get more layers of security. Some Services can only be interacted with through the VPN or a local connection, such that not everything is actually forwarded - only what I need/want to be.
I actually do have fail2ban installed on both my VPS and home server, so why make another piece of software?
Tabarnak - Succeeding at Banning
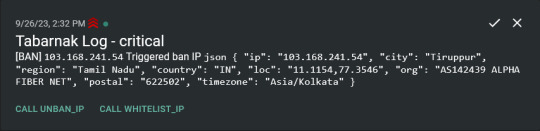
I had a few requirements for what I wanted to do:
Only allow HTTP(S) traffic through Cloudflare
Only allow DNS traffic from given sources; (location filtering, explicit white-/blacklisting);
Webhook support for logging
Should be interactive (e.g. POST /api/ban/{IP})
Detect automated vulnerability scanning
Integration with the AbuseIPDB (for checking and reporting)
As I started working on this, I realized that this would soon become more complex than I had thought at first.
Webhooks for logging This was probably the easiest requirement to check off my list, I just wrote my own log() function that would call a webhook. Sadly, the rest wouldn't be as easy.
Allowing only Cloudflare traffic This was still doable, I only needed to add a filter in my nginx config for my domain to only allow Cloudflare IP ranges and disallow the rest. I ended up doing something slightly different. I added a new default nginx config that would just return a 404 on every route and log access to a different file so that I could detect connection attempts that would be made without Cloudflare and handle them in Tabarnak myself.
Integration with AbuseIPDB Also not yet the hard part, just call AbuseIPDB with the parsed IP and if the abuse confidence score is within a configured threshold, flag the IP, when that happens I receive a notification that asks me whether to whitelist or to ban the IP - I can also do nothing and let everything proceed as it normally would. If the IP gets flagged a configured amount of times, ban the IP unless it has been whitelisted by then.
Location filtering + Whitelist + Blacklist This is where it starts to get interesting. I had to know where the request comes from due to similarities of location of all the real people that would actually connect to the DNS. I didn't want to outright ban everyone else, as there could be valid requests from other sources. So for every new IP that triggers a callback (this would only be triggered after a certain amount of either flags or requests), I now need to get the location. I do this by just calling the ipinfo api and checking the supplied location. To not send too many requests I cache results (even though ipinfo should never be called twice for the same IP - same) and save results to a database. I made my own class that bases from collections.UserDict which when accessed tries to find the entry in memory, if it can't it searches through the DB and returns results. This works for setting, deleting, adding and checking for records. Flags, AbuseIPDB results, whitelist entries and blacklist entries also get stored in the DB to achieve persistent state even when I restart.
Detection of automated vulnerability scanning For this, I went through my old nginx logs, looking to find the least amount of paths I need to block to catch the biggest amount of automated vulnerability scan requests. So I did some data science magic and wrote a route blacklist. It doesn't just end there. Since I know the routes of valid requests that I would be receiving (which are all mentioned in my nginx configs), I could just parse that and match the requested route against that. To achieve this I wrote some really simple regular expressions to extract all location blocks from an nginx config alongside whether that location is absolute (preceded by an =) or relative. After I get the locations I can test the requested route against the valid routes and get back whether the request was made to a valid URL (I can't just look for 404 return codes here, because there are some pages that actually do return a 404 and can return a 404 on purpose). I also parse the request method from the logs and match the received method against the HTTP standard request methods (which are all methods that services on my server use). That way I can easily catch requests like:
XX.YYY.ZZZ.AA - - [25/Sep/2023:14:52:43 +0200] "145.ll|'|'|SGFjS2VkX0Q0OTkwNjI3|'|'|WIN-JNAPIER0859|'|'|JNapier|'|'|19-02-01|'|'||'|'|Win 7 Professional SP1 x64|'|'|No|'|'|0.7d|'|'|..|'|'|AA==|'|'|112.inf|'|'|SGFjS2VkDQoxOTIuMTY4LjkyLjIyMjo1NTUyDQpEZXNrdG9wDQpjbGllbnRhLmV4ZQ0KRmFsc2UNCkZhbHNlDQpUcnVlDQpGYWxzZQ==12.act|'|'|AA==" 400 150 "-" "-"
I probably over complicated this - by a lot - but I can't go back in time to change what I did.
Interactivity As I showed and mentioned earlier, I can manually white-/blacklist an IP. This forced me to add threads to my previously single-threaded program. Since I was too stubborn to use websockets (I have a distaste for websockets), I opted for probably the worst option I could've taken. It works like this: I have a main thread, which does all the log parsing, processing and handling and a side thread which watches a FIFO-file that is created on startup. I can append commands to the FIFO-file which are mapped to the functions they are supposed to call. When the FIFO reader detects a new line, it looks through the map, gets the function and executes it on the supplied IP. Doing all of this manually would be way too tedious, so I made an API endpoint on my home server that would append the commands to the file on the VPS. That also means, that I had to secure that API endpoint so that I couldn't just be spammed with random requests. Now that I could interact with Tabarnak through an API, I needed to make this user friendly - even I don't like to curl and sign my requests manually. So I integrated logging to my self-hosted instance of https://ntfy.sh and added action buttons that would send the request for me. All of this just because I refused to use sockets.
First successes and why I'm happy about this After not too long, the bans were starting to happen. The traffic to my server decreased and I can finally breathe again. I may have over complicated this, but I don't mind. This was a really fun experience to write something new and learn more about log parsing and processing. Tabarnak probably won't last forever and I could replace it with solutions that are way easier to deploy and way more general. But what matters is, that I liked doing it. It was a really fun project - which is why I'm writing this - and I'm glad that I ended up doing this. Of course I could have just used fail2ban but I never would've been able to write all of the extras that I ended up making (I don't want to take the explanation ad absurdum so just imagine that I added cool stuff) and I never would've learned what I actually did.
So whenever you are faced with a dumb problem and could write something yourself, I think you should at least try. This was a really fun experience and it might be for you as well.
Post Scriptum
First of all, apologies for the English - I'm not a native speaker so I'm sorry if some parts were incorrect or anything like that. Secondly, I'm sure that there are simpler ways to accomplish what I did here, however this was more about the experience of creating something myself rather than using some pre-made tool that does everything I want to (maybe even better?). Third, if you actually read until here, thanks for reading - hope it wasn't too boring - have a nice day :)
10 notes
·
View notes
Text
Embracing DevOps: A Journey Towards Technological Excellence
In the ever-evolving landscape of modern technology, where change is the only constant, DevOps has emerged as a revolutionary force reshaping the very foundations of software development and IT operations. Short for Development and Operations, DevOps represents not just a set of practices, but an all-encompassing cultural shift with far-reaching implications in the digital age.

This comprehensive blog invites you to embark on an immersive journey into the expansive universe of DevOps. Here, we dive deep into the multifaceted scope of DevOps and its transformative impact across diverse industries. From turbocharging software delivery to fortifying security and scalability, DevOps isn't just a methodology; it's the cornerstone of success in today's interconnected technological landscape.
Join us as we unravel the boundless possibilities and profound significance of DevOps in the modern tech-driven world.
Unveiling the Multifaceted Scope of DevOps
DevOps isn't a singular concept or a one-size-fits-all approach; it's a dynamic and multifaceted philosophy that touches every facet of modern technology. Let's delve into the various dimensions that collectively define the expansive scope of DevOps:
Streamlined Software Delivery: In a world where time is a valuable currency, DevOps assumes center stage. It empowers organizations to expedite the development, testing, and deployment of software, resulting in swift and efficient software releases, a decisive advantage in today's fast-paced business landscape.
Enhanced Collaboration: DevOps shatters traditional silos that once separated development and operations teams. Instead, it nurtures a culture of collaboration, where every team member works harmoniously toward common objectives, fostering superior outcomes and a culture of relentless innovation.
Continuous Integration and Continuous Delivery (CI/CD): DevOps champions the widespread adoption of CI/CD pipelines, where the process of building, testing, and deploying code becomes an automated symphony. This not only reduces errors but also accelerates the delivery of new features and updates, keeping organizations agile and competitive.
Improved Quality: Quality is the keystone of DevOps. Through automated testing and continuous monitoring, DevOps ensures that software maintains an apex of quality. Issues are pinpointed and rectified early in the development cycle, dramatically lowering the chances of post-production glitches.
Efficient Resource Utilization: DevOps practices become the maestros of resource optimization, eliminating inefficiencies in both time and infrastructure. The result? Cost savings and a more efficient utilization of resources, a double boon for organizations.
Enhanced Security: Security isn't an afterthought in DevOps; it's integrated seamlessly into the very fabric of the process. Automated security scans and checks are an integral part, ensuring proactive measures are taken to minimize vulnerabilities and bolster system security.
Scalability: DevOps, by its very nature, is infinitely scalable. It empowers organizations to seamlessly adjust their operations to meet demand, whether scaling up or down. DevOps ensures that systems can adeptly handle varying workloads, providing the vital elements of flexibility and efficiency.
Monitoring and Feedback: At the core of DevOps lie the principles of continuous monitoring and feedback loops. This guarantees that performance issues are swiftly identified, enabling teams to make necessary adjustments in real-time, further enhancing efficiency.
The DevOps Revolution Across Industries:
The scope of DevOps extends beyond the boundaries of industries, leaving its indelible mark in software development, e-commerce, finance, healthcare, and beyond. Its principles and practices are proven to be versatile and adaptable, positioning DevOps as a coveted asset in the world of technology. It drives innovation and efficiency in every sector fortunate enough to embrace it.
In the vast landscape of technology, DevOps has emerged as a beacon of efficiency and innovation. It's not merely a practice; it's a transformative culture that redefines how organizations approach software development and IT operations. With streamlined software delivery, enhanced collaboration, continuous integration and delivery, improved quality, efficient resource utilization, enhanced security, scalability, and vigilant monitoring, DevOps has left an indelible mark across industries.
The scope of DevOps transcends boundaries, impacting software development, e-commerce, finance, healthcare, and beyond. Its principles and practices adapt and evolve, making DevOps an invaluable asset in the world of technology, driving innovation and efficiency wherever it is embraced.
In a world where adaptability and agility are paramount, DevOps shines as an irreplaceable force. And in this dynamic landscape, ACTE Technologies stands as a guiding light, preparing individuals to excel in DevOps. With the rise in demand for skilled DevOps professionals, ACTE Technologies equips learners with the knowledge and practical skills needed to thrive in this dynamic domain. Whether you're a budding DevOps engineer or a seasoned IT professional, embracing DevOps isn't just a career choice; it's a monumental leap towards a promising and impactful future in the tech industry. The possibilities with DevOps are limitless, and the journey ahead is filled with innovation and success.
8 notes
·
View notes
Text
BANG!
Techno’s device detonates, throwing you backwards with a blinding flash of light. You slam into a wall, stars in your eyes as you shake your head in a daze. You look to the side groggily. Your teammates were also caught by the blast, slumped against the wall like you. Fortunately, everyone seems to still be conscious, but they are still dazed. To your dismay, gasoline is leaking out of Firebird’s suit, spilling over the concrete floor. You hope the sparks flying from Plasma’s suit don’t catch on the fuel. Then you’d be in real trouble.
You struggle to your feet, your team mates doing the same. Techno comes triumphantly forward, seeing the damage his device has caused. Plasma grunts as his suit sparks again, giving out entirely. He’s left with the dead weight of metal encasing his body, the systems no longer assisting him in movement. Firebird’s own suit is flaring warnings as it continues to leak fuel. You hear your suit’s warnings as its power fades. You begin to peel it off, the armor only adding weight without the automated movement assistance.
Techno grins. “Not so powerful now, are you?” he taunts. "The great hero team, rendered useless by my invention.”
Plasma begins taking off his suit, his eyes never leaving Techno. He has recognized what I have: without power, the suits are only a liability.
“We’re not giving up without a fight, Techno,” he says dangerously. Yet without his suit, he’s just a regular man. A man with experience in a fight, but he’s left vulnerable without his energy beams and armor. Firebird, too. She can’t do much without her flamethrowers and jet pack.
She inches closer to me as Plasma talks to Techno. “Blink, what do we do? He disabled our suits!” Her eyes are wide with fear as she whispers to you.
I scan the empty parking garage, looking for anything I can use. There’s plenty of scrap thrown around here. The only problem is getting to any of it without Techno stopping you.
You glance at Plasma, inching closer to a metal pipe strewn on the ground. He’s got the idea. But if you want to make it out of here alive, you might need a little more of an advantage.
“Keep him distracted,” you tell Firebird. “Trust me.”
She nods. She takes a breath. You step away as she begins to argue with Techno over the safety concerns of spilling gasoline everywhere.
Once you’re sure Techno won’t notice, you blink, and find yourself behind Techno, right next to a discarded trash can lid. You pick it up, and grab a metal pipe near it. You notice Plasma and Firebird seeing you, but they stay silent, schooling their expressions as they talk to Techno, who’s still threateningly approaching.
“Hey, where’s the third one?” he suddenly exclaims. He spins around, searching for you, and spots you behind him, his eyes widening in surprise. You lunge, swinging the metal bar. A shield appears in front of Techno’s face, deflecting the strike. You lift the trash can lid as he fires at you, the metal taking a hit before you blink and teleport away.
“What- but I disabled your suit!” Techno shouts, spinning around in confusion. You swing at him again, but he brings up another shield. You teleport next to Plasma and Firebird, who are gaping at you in shock.
“We gotta surround him. He can’t shield everywhere at once,” you tell your team. Plasma blinks and nods, picking up his own metal bar.
“How can you still teleport?” Firebird asks in shock.
You don’t have time to respond, lifting the trash can lid as Techno fires again. You grab Firebird’s waist and blink, teleporting to the other side of the parking garage. You hand her your metal rod, grabbing another one from the ground. “I can teleport innately, the suit is a ruse,” you tell her, before teleporting away again. You’ve positioned the team in a sort of triangle around Techno, and he spins in circles, unprepared for being surrounded. He turns on you, recognizing you as the threat. You blink and teleport out of the way, and come back, yelling “Now!”
You and your team rush at Techno from all angles, swinging the metal bars. Techno shrieks, and under the weight of the three blows, his shield shatters, and he crumples to the ground, bleeding from his head.
The three of you stare down at him. “Well, he’s gonna have a concussion,” Plasma comments. You snort. This win isn’t as clean as the Hero Force might’ve liked it, but without the suits, there wasn’t really a choice.
“Let’s bring him in,” you say.
“We don’t have our communicators,” Firebird points out. “Are we just going to drag him through the streets??”
You raise an eyebrow at her, then grab Techno’s unconscious form. “We don’t need the suits,” you remind her, blinking to emphasize your point.
“Yeah that’s still weird,” Firebird mutters, Plasma murmuring in agreement. You shrug, and once they grab your hand, blink back to headquarters.
None of your superhero colleagues were born with their powers and instead all built themselves gadgets and powersuits to compensate. You are the only superhero who was born with their powers, although they didn’t know that, until a villain thought they had disabled your suit.
#my writing#writeblr#writing prompt response#felt like writing a silly thing#idk if it was as clear as I wanted but oh well#was still fun#blink#superheros#second person pov
4K notes
·
View notes
Text
BFSI Software Testing: Ensuring Secure and Seamless Financial Experiences with ideyaLabs in 2025

Introduction to BFSI Software Testing
Banking, Financial Services, and Insurance (BFSI) shape the backbone of modern economies. Software financial services securely and efficiently. As digital adoption accelerates, robust BFSI software testing becomes crucial. Weak testing exposes institutions to fraud, data breaches, regulatory penalties, and service disruptions. Financial sector organizations recognize software testing as essential for trust, compliance, and user satisfaction.
Understanding the Current BFSI Digital Landscape
In 2025, digital banking surpasses traditional channels. Customers prefer mobile apps and online portals for transactions, investments, and insurance services. Automation powers loan approvals, claims processing, and risk assessments. Each touchpoint carries sensitive customer information. Application performance influences customer experience. A single glitch causes reputational and financial damage. BFSI software testing verifies reliability, security, and compliance for every application.
Why BFSI Software Testing Demands Specialization
BFSI systems manage complex workflows, heavy transaction loads, and strict regulatory requirements. Testing financial software presents unique challenges. Transaction validations, concurrency management, encryption, and disaster recovery protocols require expert handling. Even a minor error in test design can lead to far-reaching consequences.
Dedicated BFSI software testing methods ensure robustness. Testers simulate real-world financial operations. They validate rapid fund transfers, multi-factor authentication, anti-fraud workflows, and accurate account reconciliations. Security, speed, and compliance define quality in BFSI technology ecosystems.
ideyaLabs: The Catalyst for Trusted BFSI Software Testing
ideyaLabs leads the BFSI software testing landscape. The team delivers end-to-end testing solutions tailored for banking, financial services, and insurance domains. ideyaLabs understands sector-specific regulations and operational nuances. Focused industry expertise translates into higher test coverage, lower risk, and faster go-lives.
Core Areas of BFSI Software Testing by ideyaLabs
1. Functional Testing for Reliable Transactions
Functional accuracy forms the foundation of financial software quality. ideyaLabs tests each function in banking, financial services, and insurance platforms. Deposit processing, payment gateways, loan origination, policy issuance, and claims management receive thorough validation. Each user journey works as intended, under varied scenarios and loads.
2. Performance Testing to Handle Massive Transactions
BFSI solutions process millions of transactions per day. Slow response times frustrate customers and lead to loss of business. ideyaLabs performance tests BFSI applications for scalability, speed, and consistency. Simulations gauge system behavior under peak traffic. Testing experts identify bottlenecks and fine-tune systems for optimal throughput.
3. Security Testing for Data Integrity and Regulatory Compliance
Cybersecurity threats target BFSI institutions relentlessly. Regulations impose strict mandates for data protection, privacy, and auditability. ideyaLabs conducts security testing to uncover vulnerabilities before attackers do. Penetration tests, risk assessments, and vulnerability scans fortify applications. ideyaLabs ensures compliance with data handling, encryption, and access control standards.
4. Automation Testing for Accelerated Digital Transformation
Modern banks and insurers embrace DevOps and continuous delivery. Software releases need rapid validation without sacrificing quality. ideyaLabs develops robust test automation frameworks for BFSI workloads. Regression cycles become faster, more accurate, and repeatable. Automation speeds up innovation cycles in today's BFSI environment.
5. Regulatory Compliance Testing for Peace of Mind
Frequent policy updates and evolving standards present constant regulatory challenges. ideyaLabs stays updated with the latest mandates. The team verifies compliance across application layers. Testing incorporates legal, operational, and reporting checks. This approach prevents regulatory fines and ensures a smooth audit trail.
6. User Experience Testing for Customer Loyalty
Financial customers demand intuitive, frictionless digital journeys. Even minor usability issues result in lost engagement. ideyaLabs tests user interfaces on multiple devices, platforms, and accessibility configurations. Testing covers onboarding, transactions, self-service, and helpdesk modules. The result: satisfied users and higher customer retention.
How ideyaLabs’ Approach Revolutionizes BFSI Software Testing in 2025
Specialized Banking Domain Knowledge
ideyaLabs employs BFSI testing specialists with deep sectoral understanding. Domain-specific expertise results in meaningful test cases, credible defect identification, and actionable feedback. The team understands unique risks attached to lending, payments, investments, and insurance segments.
End-to-End Test Coverage
Technical specialists cover every layer— front end, middleware, backend, integrations, and data. ideyaLabs creates comprehensive test suites. Test cases cover APIs, databases, business processes, and third-party connections. Comprehensive coverage eliminates loopholes missed by generic testing providers.
Agile and Scalable Testing Models
BFSI sector software evolves continuously. ideyaLabs aligns with agile and DevOps practices. Testing integrates seamlessly with development pipelines. The approach enables rapid defect discovery and remediation across sprints. Testing models scale with project needs, timelines, and complexity.
Focus on Quality and Customer Centricity
Each ideyaLabs engagement embodies a quality-first mindset. The team aligns with client objectives and customer needs. Individual test plans maximize business value. Stakeholders receive actionable test reports, risk insights, and compliance dashboards.
Proven Track Record with BFSI Clients
ideyaLabs has successfully delivered projects for global banks, NBFCs, insurance leaders, and fintech disruptors. Case studies showcase reduced post-launch defects, accelerated rollout cycles, higher compliance, and reduced downtime. BFSI clients trust ideyaLabs as a strategic quality assurance partner.
Future Trends in BFSI Software Testing
Artificial intelligence and machine learning revolutionize financial software. Risk models, chatbots, and fraud detection run on smart algorithms. ideyaLabs refines BFSI software testing methodologies for these emerging technologies. Model-based testing, synthetic data generation, and AI validation tools enable reliable next-generation fintech.
Open banking expands financial connectivity. Secure API testing gains critical importance. ideyaLabs delivers advanced API testing for regulatory and ecosystem compliance. Internet of Things (IoT) and embedded finance require new security and integration testing paradigms. ideyaLabs stays ahead of the innovation curve in BFSI software testing.
The Business Impact of Effective BFSI Software Testing
Financial organizations concentrate on growth, innovation, and customer trust. Effective BFSI software testing by ideyaLabs directly supports these goals. Key business benefits include:
Reduced business risk from downtime and fraud
Consistent regulatory compliance and audit readiness
Enhanced customer satisfaction across digital touchpoints
Faster release cycles and time-to-market
Lower maintenance costs through early defect detection
Choose ideyaLabs for BFSI Software Testing Excellence
In 2025, BFSI technology innovation continues to accelerate. Banks, insurers, and financial services providers need strategic partners to guarantee software reliability and security. ideyaLabs stands as the premier partner in BFSI software testing. The company brings proven expertise, tailored solutions, and industry leadership.
Organizations trust ideyaLabs to safeguard their software investments, comply with regulations, and provide seamless digital experiences. The future of finance demands excellence in testing. ideyaLabs delivers this excellence, every day, to every client.
Connect with ideyaLabs for Next-Generation BFSI Software Testing Services
Future-ready BFSI organizations stay ahead by partnering with ideyaLabs. Explore specialized BFSI software testing solutions designed for evolving business needs. ideyaLabs drives performance, compliance, and user delight in the fast-paced financial sector. Reach out today for a consultation and step into a more reliable digital future.
0 notes
Text
How Secure Is Your WordPress Website?

With over 40% of the web powered by WordPress, it’s no surprise that it's also a prime target for hackers and bots. While WordPress is a secure platform at its core, many websites become vulnerable due to poor practices, outdated plugins, or weak hosting setups. So, how secure is your WordPress website — really? Let’s dive into the key factors that affect WordPress security and how you can protect your site.
1. Are You Using Strong Login Credentials?
The easiest way for hackers to get in is through weak usernames and passwords. Avoid “admin” as a username and use a complex, unique password. Consider enabling two-factor authentication for an extra layer of protection.
2. Is Your WordPress Core Updated?
WordPress regularly releases updates that fix bugs and security vulnerabilities. If you're not updating your WordPress core, you're leaving the door open for attacks.
3. What About Plugins and Themes?
Outdated or poorly coded plugins are among the top reasons for WordPress site breaches. Always use plugins from trusted sources, update them regularly, and remove any that you’re not actively using.
4. Have You Installed a Security Plugin?
Tools like Wordfence, Sucuri, or iThemes Security can detect malware, block malicious IPs, and notify you of suspicious activity in real-time. These act as the first line of defense against threats.
5. Do You Have Regular Backups?
Backups won’t prevent attacks, but they can save your website in case one happens. Use plugins like UpdraftPlus or Jetpack Backup to schedule automated backups.
6. Is Your Hosting Provider Secure?
Not all hosting environments are equal. Choose a provider that offers SSL, firewall protection, malware scanning, and regular server updates.
7. Are You Using HTTPS?
If your website isn’t using an SSL certificate (HTTPS), both users and Google will flag it as untrustworthy. Most hosting providers now offer free SSL certificates — make sure yours is enabled.
8. File Permissions and Database Security
Set correct file permissions and secure your wp-config.php file. Also, regularly monitor your database and consider changing the default WordPress table prefix to make SQL injections harder.
9. Monitor User Activity
If multiple users access your dashboard, use a plugin to monitor and log activity. This helps you catch suspicious behavior before it becomes a serious issue.
10. Avoid Nulled Themes and Plugins
Tempted to download a premium plugin for free? Don’t. Nulled software often contains hidden malware that compromises your entire website.
Final Thoughts
Securing your WordPress website isn’t just about installing a few plugins — it’s about adopting a proactive, layered approach to safety. If you’re unsure whether your site is truly secure or need professional help hardening it, a WordPress Development Company in Udaipur can perform a full security audit and implement best practices tailored to your needs.
0 notes