#Biometric Data Security Concerns
Text
Mobile Biometric Security and Service
You have probably heard of the term "#biometrics," which is a rapidly evolving technology used for identity identification and access privilege. The term biometrics comes from the Greek language, where bio translates for life and metrics is for .....
(more…)

View On WordPress
#Benefits of Biometrics#Biometric Data Security Concerns#Biometric feature#Biometrics#Biometrics - Identity & Privacy Concerns#biometrics and forensic science#biometrics and future#mobile biometrics security and services#mobile security
2 notes
·
View notes
Text
The Advantages of Using VivencyGlobal’s Surveillance Solutions
Vivency Global is a leading provider of surveillance solutions that help organizations protect their assets, people, and operations. With over a decade of experience in designing, implementing, and managing complex security systems, Vivency Global has a proven track record of delivering high-quality solutions that meet the diverse needs of its clients. In this blog post, we will explore some of the advantages of using VivencyGlobal’s surveillance solutions and how they can benefit your business.
Comprehensive coverage
VivencyGlobal’s surveillance solutions offer comprehensive coverage of your premises, both indoors and outdoors. They use advanced technologies such as high-definition cameras, thermal imaging, facial recognition, license plate recognition, and analytics to detect and deter potential threats, identify suspicious behavior, and provide actionable intelligence to your security team. Whether you need to monitor your office building, warehouse, parking lot, or retail store, Vivency Global can design a customized solution that fits your needs and budget.
Real-time monitoring
VivencyGlobal’s surveillance solutions enable real-time monitoring of your premises from any location, using any device with an internet connection. This means you can stay connected to your security system 24/7 and receive alerts and notifications in case of any security breaches, unauthorized access, or other abnormal activities. You can also review live and recorded footage, manage access control, and communicate with your security team or law enforcement agencies using the same platform.
Scalability and flexibility
VivencyGlobal’s surveillance solutions are scalable and flexible, meaning they can adapt to your changing security requirements as your business grows or evolves. Whether you need to add more cameras, upgrade your software, integrate with other systems, or migrate to a cloud-based platform, Vivency Global can provide you with a seamless and cost-effective solution that minimizes disruption and maximizes value.
Expertise and support
VivencyGlobal’s surveillance solutions are backed by a team of experienced security professionals who understand the latest trends, technologies, and regulations in the industry. They can provide you with expert advice, training, and support throughout the lifecycle of your security system, from design to deployment to maintenance. They can also help you optimize your system’s performance, reduce false alarms, and minimize downtime, ensuring that your security system operates at peak efficiency.
Compliance and privacy
VivencyGlobal’s surveillance solutions are designed to comply with the highest standards of privacy and data protection. They use encryption, authentication, and access control mechanisms to secure your data and prevent unauthorized access, disclosure, or modification. They also adhere to local and international regulations such as GDPR, HIPAA, PCI-DSS, and SOX, ensuring that your security system meets the legal and ethical requirements of your industry and jurisdiction.
In conclusion, VivencyGlobal’s surveillance solutions offer many advantages that can help you enhance your security posture, reduce your risk exposure, and improve your operational efficiency. Whether you need to prevent theft, vandalism, or violence, or monitor compliance, productivity, or customer experience, Vivency Global can provide you with a customized solution that meets your needs and exceeds your expectations. To learn more about VivencyGlobal’s surveillance solutions, contact us today.
#Surveillance#Security#Monitoring#CCTV#Privacy#Technology#Data collection#Intelligence#Video analytics#Remote monitoring#Access control#Intrusion detection#Biometrics#Facial recognition#Network security#Smart cameras#Privacy concerns#Threat detection#Cybersecurity#Artificial intelligence (AI)#Machine learning#Sensor networks#Crime prevention#Homeland security#Public safety
0 notes
Text
so I know I'd be preaching to the choir if I told Tumblr not to verify their twitter accounts by giving their ID to Elon Fucking Musk but please pay attention to these movements too.
from: https://www.theverge.com/2023/9/15/23874854/x-twitter-verification-government-id-paid-account-benefits
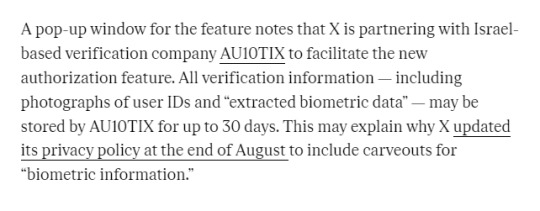
[ID: A screenshot of an article that reads: A pop-up window for the feature notes that X is partnering with Israel-based verification company AU10TIX to facilitate the new authorization feature. All verification information — including photographs of user IDs and “extracted biometric data” — may be stored by AU10TIX for up to 30 days. This may explain why X updated its privacy policy at the end of August to include carveouts for “biometric information]
From twitter's own Verification Policy page: https://help.twitter.com/en/rules-and-policies/verification-policy
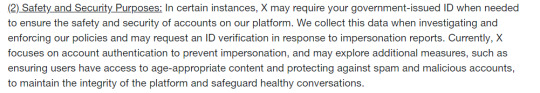
[ID: A screenshot from Twitter's verification policy page that reads: (2) Safety and Security Purposes: In certain instances, X may require your government-issued ID when needed to ensure the safety and security of accounts on our platform. We collect this data when investigating and enforcing our policies and may request an ID verification in response to impersonation reports. Currently, X focuses on account authentication to prevent impersonation, and may explore additional measures, such as ensuring users have access to age-appropriate content and protecting against spam and malicious accounts, to maintain the integrity of the platform and safeguard healthy conversations.]
Then TODAY, we get this:

[ID: A tweet from Elon Musk: As I said earlier this week, “decolonization”, “from the river to the sea” and similar euphemisms necessarily imply genocide. Clear calls for extreme violence are against our terms of service and will result in suspension.]
Keep in mind, he said this A DAY after he said THIS:
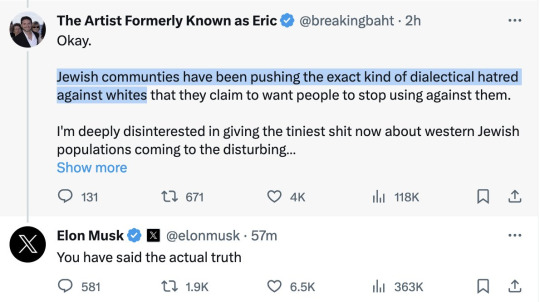
[ID: A screenshot of Twitter. The first tweet from @breakingbaht says "Okay. Jewish communties have been pushing the exact kind of dialectical hatred against whites that they claim to want people to stop using against them." Elon Musk replies "You have said the actual truth."]
So a white South African, who literally just openly said some Protocols of the Elders of Zion shit was "the truth" is now saying that the word "decolonization" itself is a "call for extreme violence" that will put your account in jeopardy if you speak it. And per its own rules, Twitter can demand you provide ID verification if they have any vaguely defined "safety concerns". So they can send it to the government of the country that you just got suspended for criticizing.
Make sure you have people and a voice off of that platform. ASAP.
152 notes
·
View notes
Text
Thousands of law enforcement officials and people applying to be police officers in India have had their personal information leaked online—including fingerprints, facial scan images, signatures, and details of tattoos and scars on their bodies. If that wasn’t alarming enough, at around the same time, cybercriminals have started to advertise the sale of similar biometric police data from India on messaging app Telegram.
Last month, security researcher Jeremiah Fowler spotted the sensitive files on an exposed web server linked to ThoughtGreen Technologies, an IT development and outsourcing firm with offices in India, Australia, and the US. Within a total of almost 500 gigabytes of data spanning 1.6 million documents, dated from 2021 until when Fowler discovered them in early April, was a mine of sensitive personal information about teachers, railway workers, and law enforcement officials. Birth certificates, diplomas, education certificates, and job applications were all included.
Fowler, who shared his findings exclusively with WIRED, says within the heaps of information, the most concerning were those that appeared to be verification documents linked to Indian law enforcement or military personnel. While the misconfigured server has now been closed off, the incident highlights the risks of companies collecting and storing biometric data, such as fingerprints and facial images, and how they could be misused if the data is accidentally leaked.
“You can change your name, you can change your bank information, but you can't change your actual biometrics,” Fowler says. The researcher, who also published the findings on behalf of Website Planet, says this kind of data could be used by cybercriminals or fraudsters to target people in the future, a risk that’s increased for sensitive law enforcement positions.
Within the database Fowler examined were several mobile applications and installation files. One was titled “facial software installation,” and a separate folder contained 8 GB of facial data. Photographs of people’s faces included computer-generated rectangles that are often used for measuring the distance between points of the face in face recognition systems.
There were 284,535 documents labeled as Physical Efficiency Tests that related to police staff, Fowler says. Other files included job application forms for law enforcement officials, profile photos, and identification documents with details such as “mole at nose” and “cut on chin.” At least one image shows a person holding a document with a corresponding photo of them included on it. “The first thing I saw was thousands and thousands of fingerprints,” Fowler says.
Prateek Waghre, executive director of Indian digital rights organization Internet Freedom Foundation, says there is “vast” biometric data collection happening across India, but there are added security risks for people involved in law enforcement. “A lot of times, the verification that government employees or officers use also relies on biometric systems,” Waghre says. “If you have that potentially compromised, you are in a position for someone to be able to misuse and then gain access to information that they shouldn’t.”
It appears that some biometric information about law enforcement officials may already be shared online. Fowler says after the exposed database was closed down he also discovered a Telegram channel, containing a few hundred members, which was claiming to sell Indian police data, including of specific individuals. “The structure, the screenshots, and a couple of the folder names matched what I saw,” says Fowler, who for ethical reasons did not purchase the data being sold by the criminals so could not fully verify it was exactly the same data.
“We take data security very seriously, have taken immediate steps to secure the exposed data,” a member of ThoughtGreen Technologies wrote in an email to WIRED. “Due to the sensitivity of data, we cannot comment on specifics in an email. However, we can assure you that we are investigating this matter thoroughly to ensure such an incident does not occur again.”
In follow-up messages, the staff member said the company had “raised a complaint” with law enforcement in India about the incident, but did not specify which organization they had contacted. When shown a screenshot of the Telegram post claiming to sell Indian police biometric data, the ThoughtGreen Technologies staff member said it is “not our data.” Telegram did not respond to a request for comment.
Shivangi Narayan, an independent researcher in India, says the country’s data protection law needs to be made more robust, and companies and organizations need to take greater care with how they handle people’s data. “A lot of data is collected in India, but nobody's really bothered about how to store it properly,” Narayan says. Data breaches are happening so regularly that people have “lost that surprise shock factor,” Narayan says. In early May, one cybersecurity company said it had seen a face-recognition data breach connected to one Indian police force, including police and suspect information.
The issues are wider, though. As governments, companies, and other organizations around the world increasingly rely on collecting people’s biometric data for proving their identity or as part of surveillance technologies, there’s an increased risk of the information leaking online and being abused. In Australia, for instance, a recent face recognition leak impacting up to a million people led to a person being charged with blackmail.
“So many other countries are looking at biometric verification for identities, and all of that information has to be stored somewhere,” Fowler says. “If you farm it out to a third-party company, or a private company, you lose control of that data. When a data breach happens, you’re in deep shit, for lack of a better term.”
10 notes
·
View notes
Text
Over 100 artists including Rage Against the Machine co-founders Tom Morello and Zack de la Rocha, along with Boots Riley and Speedy Ortiz, have announced that they are boycotting any concert venue that uses facial recognition technology, citing concerns that the tech infringes on privacy and increases discrimination.
The boycott, organized by the digital rights advocacy group Fight for the Future, calls for the ban of face-scanning technology at all live events. Several smaller independent concert venues across the country, including the House of Yes in Brooklyn, the Lyric Hyperion in Los Angeles, and Black Cat in D.C., also pledged to not use facial recognition tech for their shows. Other artists who said they would boycott include Anti-Flag, Wheatus, Downtown Boys, and over 80 additional artists. The full list of signatories is available here.
“Surveillance tech companies are pitching biometric data tools as ‘innovative’ and helpful for increasing efficiency and security. Not only is this false, it’s morally corrupt,” Leila Nashashibi, campaigner at Fight for the Future, said in a statement. “For starters, this technology is so inaccurate that it actually creates more harm and problems than it solves, through misidentification and other technical faultiness. Even scarier, though, is a world in which all facial recognition technology works 100% perfectly – in other words, a world in which privacy is nonexistent, where we’re identified, watched, and surveilled everywhere we go.”
Facial recognition technology at venues has grown increasingly controversial over the past several months, particularly as Madison Square Garden Entertainment and James Dolan have garnered scrutiny for using the tech to kick out lawyers affiliated with ongoing lawsuits against the company. Several attorneys had been removed last year from events at MSG’s venues including its eponymous arena and Radio City Music Hall. Last October, attorney Barbara Hart was removed from Brandi Carlile’s Madison Square Garden Concert because her law firm was litigating against MSG in a class action lawsuit. (Hart herself wasn’t involved with that suit.)
#Boycotting Venues That Use Face-Scanning Technology#article#rolling stone#surveillance#Facial recognition
33 notes
·
View notes
Text
the agent walks up to the kitchen staffs door, and it holds its wrist up to the ID scanner. it is let inside, no problem. that chip in its organic arm is one of the few actual wireless pieces of tech it has installed onboard, because those chips are easy to write to and easy to erase and are a very non-obtrusive system. can't hack someone through their ID, and those are so easy to fake. you don't really know why they're still in such common use. makes your job easier, you suppose. the kitchen staff work around the agent, and the agent slips through them.
it gets weird looks, they know they're in some danger, but no one ends up hurt. it stresses you out, a little bit, to see your agent around civilians. you dont really know why. or, well, you know what it can do. you don't know what it won't do. it's impossible to test for the absence of an occurrence. that's not the phrase. it's impossible to prove that something will never happen. that's it. no wait, that doesn't sound right either. whatever. you are not afraid of the agent, it is your friend. these random civilians are not it's friends. as far as you know. but it is polite, as far as you can tell, as it moves through the crowded kitchen. you check that it has access to the latest version of your little map of this building, and it does. and then it proves that it does because it goes the long way around and takes the door that leads to the staff hallways, and not the fancy ass dining area. it's following the route it needs to, no issue. tiny issue. it needs to get through two locked doors. issue so small it is microscopic, because all these locks are ID activated. lol. you scrape the biometric data you need from the security network, and update it's chip. and it's let through without issue. no wait. a little warning popup about how one person apparently went through one door twice in one direction. valid concern. you delete the warning. lol. the agent makes it to the room without issue.
inside of the room is a slender young man with short, greasy hair and a jumpy air to him. the agent startles him a lot by just popping up silently in the corner of his office. this is the client, and not the target. your view from the agents visor keeps wandering, because it's a bit bored. the client, Petra, asks you a question, out loud. well, he asks the agent a question, but it's not really listening. you respond via text, same channel that he hired you on.
"So. You're... agent Mandible?"
the codename you're currently using. [yes yes. where is the target? thought there was a job to do.]
you do not need to be this rude, but also it's kinda fun, watching the fear on his face, watching him puzzle the pieces together entirely incorrectly, because he whispers "Ah, so you're a robot..." under his breath in a way he thinks you won't hear. lol? even if one of you was a robot, you would be able to hear that. this guy is a fool. a fool who is paying you to kill his superior. it might actually be his dad, you didn't pry enough to find out. he has composed himself enough to tell you what room the target is in.
"I don't think I need to tell you how to get there, given that you found me just fine." he shuffles his feet, and visibly struggles to maintain eye contact. he feels he needs to be polite, apparently. "You arrived at the perfect time, he should be asleep for the next 15 minutes or so..." he trails off, and then turns to look out a window, hands behind his back, all fuckin formal. the agent is out of there as soon as the talking is over, and you've sent it on the updated map. you check on the targets room remotely. holy shit. the door lock isn't even engaged. he left it open. there are two cameras in his room. one is completely off, he requested that? lol. the other is not off, but it is on standby mode, it should alert and start recording when it detects movement. getting past that specific trick is not brainlessly easy, but it's not impossible either. you just want it to look untampered with. or- wait. it only needs to look untampered for the text ten minutes or so, while no-one's looking too hard, probably. you get it hacked, it's a good enough job. as good as it needs to be. they won't have footage of the incident. now you get to watch the agent do it's part of the job, from its perspective, no less. it takes a moment to consider something. medium of dispatch, maybe? oh, yeah. it gets out its knife. hand over his mouth, blade into his neck, up into the skull. simple and silent. kinda messy and gruesome also. the poor cleaning staff, that is not a cheap carpet. at least that desk seems very blood-proof, with how excessively shiny it is. the agent wipes its knife on the targets sleeve, and then it is out of there, along the new route you've sent it, down the quiet staff hallways but not the same ones as earlier. you leave your cam hack in place, might as well, and you text the client and tell him [it is done.] which is very edgy of you, you admit, but it's appropriate for this job, probably.
hmm. there's something to ponder there, about the aesthetics of death. guns make the process of creating death much more efficient, they're machines, they're optimized. using your own hand weapons takes the degree of separation out of it. you're much closer to the violence you're doing. you, in the general grammatical case, your personal hands are still pretty clean, overall. well, ok, no. degrees of separation, again. you are paid to be the middleman between the person who wants someone dead and the person who does the killing. person is here. you wave it into the truck, and then you drive away, out of this parking lot.
[do you want more hand weapons? i've been mostly focusing on guns, for range and effecacy, but for small jobs like this it might be worth it. maybe? what do you think?]
it makes a small ponderous noise, and looks up to the roof, fidgeting with its fingers, deep in thought.
[i should be able to get my hands on some weapons catalogs for you, plus there's that expo coming up in a few weeks. but with both of those, there's the problem of you being actively sold something. lots of loud flashy words to get you to spend lots of money money money]
it huffs a quiet laugh, and then it pulls its mask down to tap at its jaw. huh? oh, it's referencing the guy who sold you that jaw, and a lot of other very flashy and not strictly nessecary items. you laugh at that.
[oh man, i don't remember how many of them you've met, but i have quite a lot of friends like that. my sincere condolences.]
it throws it's hands up in mock despair, very clearly smiling at the same time. you have a new message, from Petra. [The money has been forwarded to you.] oh damn. immediately after the job? this guy has a lot of trust in his bank security. or he just hasn't thought of what an investigator might look for. family of rich idiots, over there. once the money comes in, you'll move it to your actual account. obfuscatory steps. the agent is messing with a small piece of fabric, folding and unfolding it. it might have snatched that from that last job. that's fair, honestly. small enough to be hard to identify and easy to dispose of it needed, and it looks like it has a good texture to it. you should get it some new fidgety things, once this money comes in. you could get yourself something too, maybe. been a while since you got new clothes, but also you don't like lugging around too much unnessecary stuff. maybe there's a clothes swap event somewhere nearby you could drop in to. how would you find that. you could ask a friend. carmen, they seem like they would know. you should drop into them anyways, say hi. it gets kinda hard to keep up with friends, with the constant travelling. but you do your best, and your friends are cool, they all seem to understand. the agent has just finished typing something out on its communicator.
[bazooka would be funny]
that is SO far from anything you were expecting, you're breathless with laughter.
[say fuck all of you. get explode]
you make a little explosion motion with both hands, one still on the wheel. the agent looks somewhat proud of having gotten you to laugh.
[okay, man, do you have any actual ideas?]
[no. give me some time]
[yeah yeah, no worries. we're in no rush]
#[fiction]#[category: the agent & the handler]#death tw#blood tw#someone dies but hes not terribly important. this is about those gay people again
6 notes
·
View notes
Text

Sen. Ed Markey (D-Mass.) sent a letter Tuesday to the Department of Homeland Security (DHS) urging it to discontinue the use of a smartphone app required by migrants seeking asylum at the southern border to use.
The CBP One app, which was rolled out in 2021, was established to allow migrants to submit applications for asylum before they cross the U.S. border. Markey said in his letter that requiring migrants to submit sensitive information, including biometric and location data, on the app raises “serious privacy concerns,” and demanded that the DHS cease its use of it.
“This expanded use of the CBP One app raises troubling issues of inequitable access to — and impermissible limits on — asylum, and has been plagued by significant technical problems and privacy concerns. DHS should shelve the CBP One app immediately,” Markey said in his letter.
“Rather than mandating use of an app that is inaccessible to many migrants, and violates both their privacy and international law, DHS should instead implement a compassionate, lawful, and human rights centered approach for those seeking asylum in the United States,” he continued.
He said that the use of this technology has also faced technical problems, including with its facial recognition software misidentifying people of color.
“Technology can facilitate asylum processing, but we cannot allow it to create a tiered system that treats asylum seekers differently based on their economic status — including the ability to pay for travel — language, nationality, or race,” he said.
The app has negative ratings on both the Google Play and Apple app stores, with many users criticizing the app for crashing and other technical issues.
(continue reading)
#politics#ed markey#immigration#asylum seekers#joe biden#cbp one app#dhs#privacy rights#surveillance state#facial recognition
54 notes
·
View notes
Text
Monitoring health care safety using SEnergy IoT

Monitoring healthcare safety using IoT (Internet of Things) technology, including SEnergy IoT, can greatly enhance patient care, streamline operations, and improve overall safety in healthcare facilities. SEnergy IoT, if specialized for healthcare applications, can offer several advantages in this context. Here's how monitoring healthcare safety using SEnergy IoT can be beneficial:
Patient Monitoring: SEnergy IoT can be used to monitor patient vital signs in real-time. Wearable devices equipped with sensors can track heart rate, blood pressure, temperature, and other critical parameters. Any deviations from normal values can trigger alerts to healthcare providers, allowing for timely intervention.
Fall Detection: IoT sensors, including accelerometers and motion detectors, can be used to detect falls in patients, especially the elderly or those with mobility issues. Alerts can be sent to healthcare staff, reducing response times and minimizing the risk of injuries.
Medication Management: IoT can be used to ensure medication adherence. Smart pill dispensers can remind patients to take their medications, dispense the correct dosage, and send notifications to caregivers or healthcare providers in case of missed doses.
Infection Control: SEnergy IoT can help monitor and control infections within healthcare facilities. Smart sensors can track hand hygiene compliance, air quality, and the movement of personnel and patients, helping to identify and mitigate potential sources of infection.
Asset Tracking: IoT can be used to track and manage medical equipment and supplies, ensuring that critical resources are always available when needed. This can reduce the risk of equipment shortages or misplacement.
Environmental Monitoring: SEnergy IoT can monitor environmental factors such as temperature, humidity, and air quality in healthcare facilities. This is crucial for maintaining the integrity of medications, medical devices, and the comfort of patients and staff.
Security and Access Control: IoT can enhance security within healthcare facilities by providing access control systems that use biometrics or smart cards. It can also monitor unauthorized access to sensitive areas and send alerts in real-time.
Patient Privacy: SEnergy IoT can help ensure patient privacy and data security by implementing robust encryption and access control measures for healthcare data transmitted over the network.
Predictive Maintenance: IoT sensors can be used to monitor the condition of critical equipment and predict when maintenance is needed. This proactive approach can reduce downtime and improve the safety of medical devices.
Emergency Response: In case of emergencies, SEnergy IoT can automatically trigger alerts and initiate emergency response protocols. For example, in the event of a fire, IoT sensors can detect smoke or elevated temperatures and activate alarms and evacuation procedures.
Data Analytics: The data collected through SEnergy IoT devices can be analyzed to identify trends, patterns, and anomalies. This can help healthcare providers make informed decisions, improve patient outcomes, and enhance safety protocols.
Remote Monitoring: IoT enables remote monitoring of patients, allowing healthcare providers to keep an eye on patients' health and well-being even when they are not in a healthcare facility.
Compliance and Reporting: SEnergy IoT can facilitate compliance with regulatory requirements by automating data collection and reporting processes, reducing the risk of errors and non-compliance.
To effectively implement SEnergy IoT for healthcare safety, it's crucial to address privacy and security concerns, ensure interoperability among various devices and systems, and establish clear protocols for responding to alerts and data analysis. Additionally, healthcare professionals should be trained in using IoT solutions to maximize their benefits and ensure patient safety.
2 notes
·
View notes
Text
Tiktok
The international version of the Chinese product Douyin.
Owned by: ByteDance Limited (Zìjié Tiàodòng).
Content censorship: They ban and suppress criticism of leaders like Xi Jinping, Vladimir Putin, Donald Trump, Barack Obama, mahatma Gandhi, and Recep Tayyip Erdogan. Also they suppress content informing of what happens at the Xinjiang Internment Camps (basically modern Chinese concentration camps to brainwash muslims), and the Uyghur genocide. They also ban users deemed too ugly, poor or disabled for the platform, censor political speech, block positive LGBT content, and set country-specific censorship rules.
It has been revealed that TikTok's Chinese employees could spy on users from all over the world, including obtaining their fingerprints and biometric data, aside from facial, which the Chinese government also has access to.
BYTEDANCE LTD.
Headquarters: Beijing and incorporated in the Cayman Islands (tax haven).
Founded by: Zhang Yiming, Liang Rubo, and more.
In partnership with: The Chinese Ministry of Public Security.
Also owned by: several companies with shares in it. For example a Chinese state-owned company owned by the Cybespace Administration of China and China Media Group.
Financed by: Hillhouse Capital Group )largest privaty equity fund in Asia), General Atlantic (US growth equity firm), Sequoia Capital (American venture capital firm), SoftBank Group Corporation (Japanese multinational conglomerate holding company focused on investment management), KKR & Co. Inc. (American investment company that manages alternative assets).
They've also created: Toutiao, a Chinese news platform that has been subjected to criticism for showing advertisement of products that Toutiao doesn't care if they're good or not, or even certified, after Toutiao employees said the company will even fake product certifies and allow illegal advertisement.
There are surveillance and privacy concerns with Bytedance company, with suspicions of its work for the Chinese Communist Party to censor content about human rights abuses.
2 notes
·
View notes
Text
Some Thoughts on Episode 16 (Mobile Suit Gundam: The Witch from Mercury)
(very long + spoilers [including a few for Revolutionary Girl Utena & Fullmetal Alchemist])
*I hope y’all aren’t sick of hearing Utena comparisons, because there’s going to be quite a few this episode.
*The episode starts by revisiting Prospera's conversation with Belmeria from Ep. 14, and expands on it.
*Ericht was apparently perfectly synced to the data storm, so apparently blue Permet lines on a Gundam pilot mean they’re unharmed. However, the various hazards of space, that are the very basis for why Vanadis was pursuing the GUND format in the first place, were too much for the body of a child to endure, and Ericht would have died if Prospera hadn't transferred her biometric data into Lfrith.
*’Biometric data’, in modern parlance, refers to things like fingerprints, retinal scans, blood drawings, etc., essentially information about a person’s body, often used for security identification (if Suletta turns out to be a clone like some have conjectured, I feel like this might be a factor).
*So, it seems like Prospera isn't the worst parent ever in animation history, just a high-ranking one (and, ironically, more for how she treats Suletta, then how she preserved Eri’s life).
*Prospera needs for Aerial to achieve a Permet score of 8, and to expand the range of the data via Quiet Zero, so that “...Eri…can live in freedom!” Prospera is rather vague on what Eri’s “freedom” entails, and since she gestures like a supervillain while talking about this, it’s probably Not Good (except for Eri presumably).

*Belmeria refuses to help her, citing the Vanadis Institute’s principles. Prospera indirectly calls her a hypocrite, and reveals that she knows Belmeria proposed the Neural Expansion Theory, that the stress of data storms could be resisted by enhanced humans with artificial nervous systems, which Dr. Cardo rejected. In other words, not only has Belmeria been helping Peil make enhanced humans, she was the one who introduced them to the idea in the first place.
*I have to admit I’ve lost some respect for Bel with this revelation, but hopefully her guilt will prompt her to make better choices soon.
*12 people were killed by Norea and Sophie’s attack on Asticassia, and news has leaked out to the general public about the attack on Plant Quetta as well. In addition, Benerit security’s retaliation against Earthians has resulted in an increase in anti-Spacian attitudes, and protests turning into riots.
*Between this, and the vacancies left by Vim, Delling, and now Sarius, the remaining Benerit leaders decide to hold a presidential election.
*Shaddiq's group discusses how he’ll be running in the election, and clarifies that Miorine won't be automatically chosen based on blood relation, which, on the one hand, I would hope not, but on the other, nepotism is a common practice in real-life businesses, and the corporations of Ad Stella would reflect that, so it makes sense to be explicit about it.
*Shaddiq, who is so, so totally and completely over Miorine, muses that she could be elected with the backing of one of the three branches, before being interrupted by Sabina.
*I saw someone comment that they were concerned that Sabina, despite being the most overtly lesbian-coded character in the show (as opposed to someone like Miorine, who is textual), might have feelings for Shaddiq, and I truly hope they’re wrong; yes, Sabina is an accessory to terrorism and mass murder, but that doesn’t mean she (or anyone really) deserves to be a proxy for manga!Juri Arisugawa.
*For anyone unfamiliar with Revolutionary Girl Utena: anime!Juri is the passive-aggressive lesbian frenemy/rival of Touga Kiryuu (who is a major inspiration for Shaddiq), sometimes ostensibly supporting him, but also unhesitant to undermine him when the opportunity arises; manga!Juri is the only female duelist besides Utena, and she openly pines for Touga (with sadly no signs of being even a comphet lesbian like Nanami) and duels Utena on his behalf instead of her own. This is one of many reasons a lot of Utena fans (including me) prefer the anime to the manga.
*Miorine confers with Lauda, who affirms that charges against GUND-Arm, Inc. have been dropped due to lack of evidence. He also notes that Miorine should be happy, since with a new president, no one will force her to get married.

*Miorine, of course, has other priorities on her mind.
*Repairs are underway at Asticassia and the school is on high alert, with mobile suit pilots patrolling the grounds and student activities restricted.
*Though they’ve been officially cleared of wrongdoing, there’s a lot of negative online comments being directed toward GUND-Arm, Inc. and Earthians in general.
*Rouji asks Secelia if she’ll be leaving school, but both of them seem dedicated to their roles as the Greek chorus in the Dueling Committee. Secelia comments that, at the very least, she wants to see who ends up marrying Miorine, which transitions to a shot of…

*...Felsi?
*Something I’ve referenced in previous writings about Witch from Mercury, but didn’t directly comment on, was that Witch from Mercury is a show that really loves its meaningful transitional shots…which makes this particular one very weird. This is the only shot we get of Felsi in the entire episode, so it was obviously intentional, but it begs the question why? At this point, Suletta & Aerial could probably defeat Guel, Elan, AND Shaddiq in a 1 vs 3 duel, so how would Felsi possibly win? Not to mention it would be a very weird narrative turn for someone who’s hitherto been relegated as a side character to defeat Suletta like that. Regardless of why or how, it seems Felsi will be playing an important role (*really* hope she doesn’t die).
*Chuchu is tired of waiting for news on Nika's supposed detainment, and tries to march off with wrench in hand to make it someone's problem, but thankfully Suletta restrains her and the other Earth House kids manage to calm her down.
*Unfortunately, while Earth House may be trying to avoid getting in more trouble, that doesn't stop it from coming to them, as friends of Jujebu (the student pilot Norea killed in the Rumble Ring) come to vandalize their dormitory.
*The two groups get into an argument, and Martin shows surprising confidence (even Chuchu looks impressed) in telling them to stand down. In response, one of the vandals chucks a spray can at his head, injuring him. The situation looks it will escalate (i.e. Chuchu will murder someone), but before it does, a hero appears:

*Miorine caught the incident on tape and threatens the vandals with the evidence if they don't leave.
*Sabina tends to Nika's injuries, and asks if she'd like to join Shaddiq's squad, which Nika politely refuses. Sabina reiterates what Norea said a few episodes back about ideals not being enough (minus the trying to hurt or kill Nika), and promises Nika that she and Shaddiq will be able to bridge the gap between Earthians and Spacians (but, y'know, with lots of violence).
*The Peil CEOs demand No. 5 stops wasting time creeping on Suletta and to just focus on stealing Aerial. I'm glad we don't have to deal with that particular subplot anymore, but the Peil CEOs take care to remind us they will murder him as ruthlessly as they did No. 4.

*Guel returns, and Lauda is so shocked he faints.
*Guel and Petra have a short chat, with Petra informing Guel of his brother's recent hardships. Guel asks Petra to look after Lauda while he goes to take care of, leaving Guel as just as much a wild card as he was in the latter half of the first cour.
*I have to say, the Jeturks have grown on me a bit. Like yes, they (especially Guel) were awful for the first few episodes, but a lot of that was due to Vim’s influence, so at this point I’m hoping they’ll collectively grow to be better people and survive the series
*Feng Jun of the Space Assembly League informs Miorine that Nika is not actually held by the front management, but was instead kidnapped by unknown parties. Feng offers to investigate in exchange for access to GUND-Arm, Inc.; she wants to use said access to investigate Shin Sei Development, and how such a low-ranked company has the resources to build and repair a mobile suit like Aerial.
*Miorine informs Earth House of the situation with Nika, and…

*...Chuchu? She…thanks Miorine for her efforts.

*And the rest of Earth House join in giving Miorine these happy/relieved looks. And…Y'all, this is just heartwarming.
*Ever since Plant Quetta, Earth House has been having such a rough time, managing trauma, welcoming new members who turned out to be terrorists, Nika getting kidnapped, and getting detained.
*But now Miorine's back, and everything's looking a little better, and this is such a transformation from how their relationship started: it's a far cry from the days when Earth House tolerated the Spacian princess who came as a package deal with Suletta, from when the same girl strong-armed them into joining her business only for her to learn that money was not enough and that she needed to respect and listen to them. Since then they've worked together, helped and protected each other, and somewhere along the way, Miorine became accepted as one of them. She may still sleep in her dad's former office, but Earth House is now her home…and Miorine knows it.

*Even with all the tragedy and horrors of war, Miorine is enjoying the most positive relationships she's ever had since her mother's death, which we know because we've only ever seen Miorine smile like this either at the prospect of escaping to Earth, or at Suletta. Speaking of which…
*As most of Earth House starts asking for Miorine's help with business stuff, Till steps up in the absence of Nika to become Earth House's #1 Sulemio supporter, and raises Suletta's hand to get Miorine's attention (seriously, where's all the best boy praise for Till? I know he doesn't get a lot moments, but all of them have been quite excellent so far).
*Suletta asks Miorine to check on the greenhouse with her, so the two head off-

*AHH!
*I've been thinking about why the Prospera jumpscare is so unsettling; I think it's because it works along the same line as, say, Darkseid from DC comics showing up unexpectedly relaxing in various heroes’ homes: it's an implicit but devastating threat, a reminder that, Prospera’s influence, at this time at least, is inescapable (which we’ll see later at the greenhouse).
*It's even worse because, from the perspective of Earth House and Suletta, Prospera's actions are innocuous: all she does is ask Suletta to look after Miorine, and then introduce herself to Earth House, acting cutesy all the while. It's not an uncommon tactic for abusers and manipulators to act charming in front of their victims' family and friends to undermine any negative claims their victims may make against them, and I worry that Prospera is taking this opportunity to do precisely that.
*No. 5 tries to hijack Aerial, but quickly discovers that’s a Very Bad Idea, as his Permet lines flare up, Aerial enters Permet 6, and Elan gets a look beyond the data storm and meets Ericht Samaya.

*There’s been a lot of speculation about why all the GUND-Bits look identical to Eri. I know that failed clones being uploaded into the data storm is a popular theory, but given the time and resources that cloning (especially one based on actual reproductive cloning techniques) takes, I don’t think the 4-year gap between Vanadis and Suletta’s birth(?) would be enough to account for that, so I suspect the truth is something different.
*Aerial has been piloted before without taking action, but the circumstances were different:
In Miorine's case, she used Suletta's datapad to access Aerial, and had been previously rescued by her, so it's likely that Aerial recognized her and chose not to intervene; plus, it seems unlikely that Miorine even knew how to access the GUND format at that time, so it's hard to say if a connection could be made without that.
Elan No. 4, meanwhile, explicitly obtained Suletta's permission to borrow Aerial, and he didn't express any bad intentions (like apologizing for stealing Suletta's sister) until after he exited the cockpit.
*Witch from Mercury once again makes a good case for its selective but intense uses of violence, because I did think for a few moments that Eri was going to kill No. 5 with Permet overload; knowing that major characters can and have died gives any scene like this tension due to uncertainty.
*Belmeria starts a self-pitying rant about how she had no choice but to work with Peil and No. 5 punches her, and I’m not really sure how to feel about any of this; I’m on record for wanting to toss No. 5 out an airlock, yes, but none of the victims of the enhanced person project, who seem like they all ‘volunteered’ out of desperation, deserved to be exploited by Peil, and Belmeria, while remorseful, was wrong for enabling this.
*The Suletta and Miorine reunion we've all been wanting/dreading!
*Things start awkwardly as Suletta notes that she fulfilled all of her promises and Miorine agrees.
*The staging for this scene reminds me a lot of Revolutionary Girl Utena, where characters’ positioning often had a theatrical quality that somehow felt very striking despite/because of the artificiality. It makes sense that Suletta and Miorine start off like that since neither is quite certain where they stand with the other.

*Suletta broaches the topic that's on both their minds, and Miorine apologizes for calling Suletta a murderer, recognizing that Suletta had been trying to save both her own and her father's life.
*”I knew it. It’s just like Mom said.” Miorine body language instantly tenses when Suletta says this. Like a lot of folks have been saying, Miorine makes it explicit that Suletta’s nonchalant attitude toward killing someone is the thing that really upsets her. Suletta tries to insist that it’s fine because only she and Aerial can protect everyone, but Miorine rightly suspects that Prospera convinced her of that.
*”Will you do anything your mom tells you to?” Suletta shows a lot of hesitancy and anxious body language during Miorine’s questioning, but when pressed, confirms that, yes, she would give up her dreams and even kill people if Prospera asked her to, and this is heartbreaking.
*I was initially surprised that Miorine did not ask Suletta if she would hurt her if Prospera asked, but there’s a couple reasons it makes sense she didn’t:
Miorine is already emotionally devastated to learn how in thrall Suletta is to Prospera, and she probably doesn’t want to even consider the possibility that Suletta might say yes.
The question might instead prompt Suletta to go into an emotional breakdown, and Miorine simply doesn’t have the capacity to handle that at this time, nor does she want to subject Suletta to that pain.

*I've seen a lot folks talk about the tomatoes and how they symbolize their respective characters' growth (or lack thereof), so I just wanted to note that in Suletta's case, the bottom of her tomato is definitely red, and thus does have signs of growth, but that growth is currently (literally) overshadowed.
*Suletta justifies this by noting that, because she obeyed, she got to go to school, make friends, and meet Miorine, which prompts Miorine to angrily run away.
*There’s been a lot of discussion on Suletta’s mental state, but I think this conversation makes it clear that it’s not a ‘Winter Soldier controlled by code phrases’ situation. Anthy Himemiya from Revolutionary Girl Utena and her obedience as the Rose Bride seems much more relevant to Suletta’s situation.

*Pardon me while I muffle my screams and quietly sob at the awful situations these fictional characters are in.
*There’s a few differences in Suletta’s and Anthy’s situations though, so I think it would be helpful to mention a second character for comparison as well: Rose Thomas from Fullmetal Alchemist.

*For those not familiar with Fullmetal Alchemist, Rose is a minor character encountered early in the story, living in a desert town and revering the sun god Leto and his supposed priest, Father Cornello. Rose’s boyfriend died last year, and Cornello, with the aid of fraudulent ‘miracles’ (actually alchemy enhanced by a Philosopher’s Stone), convinced her that unquestioning faith and obedience in Leto (and Cornello) would be rewarded with the resurrection of her boyfriend (he was very much lying, of course).
*Cornello uses this influence to try to persuade Rose to act contrary to her usual self and try to kill the protagonists (she fails and Cornello is ultimately exposed as a two-bit fraud).
*Faith and belief can be a beautiful thing when placed in the right person or ideal, but horrific when placed in the wrong ones, such as when Rose believed in Cornello, and I’d argue, as Suletta believes in her mother; basically, I’d compare Prospera and Suletta’s relationship as a cult leader and a follower devoted to them.
*Anthy also has faith, though hers is far more negative and cynical than Suletta’s or Rose’s: she believes that, thanks to her actions in saving her brother, it’s her fault that he became the monster we encounter in the present, and that, as awful as he is to her, he’s the only one willing to accept her, and so she deserves her suffering. For Anthy, eternal torment is palatable only because she believes that leaving would be even worse. Despite this difference in the root of belief (obedience is rewarded vs. disobedience is punished), the result of Suletta, Anthy, or Rose acting on another’s behest while repressing any feelings of this being wrong is much the same.
*This should inspire hope in fellow fans though: in the end, both Anthy and Rose escaped their manipulator’s influence and learned to live for themselves; should we not have confidence that Suletta will do the same?
*Miorine, bless her, continues to be one of the smartest (if somewhat impulsive) people in the show, and instead of blaming Suletta, immediately goes after Prospera, rightfully blaming her for Suletta’s condition.
*Miorine: “I won’t let you have your way with her anymore!”
*Prospera: “And what then? Do you want to have your way with her next?”
*Ugh, this is such a gross and untrue thing for Prospera to say. I think it also strongly suggests that Prospera may ‘love’ Suletta as a favorite tool, but not as her daughter, and that she currently believes Miorine is much the same as her (which we know of course is not true, but Prospera seems to have a bias in perspective about Miorine, which we’ll get to in a little bit).
*Prospera asserts that Miorine is just like her father, and when rebuffed, she informs Miorine of her vendetta against the Rembran family and about the Vanadis Incident 21 years ago, and describes how she lost her husband, her colleagues, and her mentor.
*“We’re the only ones who survived.” Prospera doesn’t make a lot mistakes, but I feel like she keeps making minor ones when it comes to Miorine (which I feel may be due to her barely repressed hatred toward her affecting her judgment), such as her belief that Miorine only sees Suletta as a tool mentioned above, and now this: Miorine knows that Suletta’s 17 and that Vanadis took place 21 years ago now, so she’s going to wonder who this other survivor Prospera mentioned is, which I think will sooner or later lead her to meet Eri.

*While Miorine doesn’t necessarily want her father dead, she’s also aware he’s done awful things, and chooses to protect Suletta instead (because she wants to be gal pals with her /sarcasm).
*Unfortunately, unlike some show watchers, Prospera clues in that Miorine genuinely loves Suletta, and instead of reflecting on that and maybe rethinking her choices, immediately uses it as a tool to manipulate Miorine, telling her that if she’s so protective, then she should work with Prospera and run for president of Benerit so that Quiet Zero can completed.
*Will Miorine accept? It’s probably the best route to saving Suletta, so unfortunately yes. Will Prospera betray her? Also yes, but hopefully Miorine is already aware of that and will be looking for a means to counteract it (perhaps some intel from Feng on Shin Sei will help?).
*This was quite an emotional roller coaster, and next episode seems like it will maintain that with the election, which I’m sure will be as fair and honest as can be in a future space capitalist dystopia.
6 notes
·
View notes
Text
Biometrics and Cyber Security
As technology advances, new faults and threats emerge, making cyber security a top priority. Along with these developments, we must remember that hackers are changing as well, and they continue to pose a threat to cyberspace. Because traditional.....
(more…)

View On WordPress
#Airport Security#Benefits of Biometrics#Biometric Data Security Concerns#Biometrics - Identity & Privacy Concerns#Biometrics and Cyber Security#Drawbacks of Biometrics#Examples of Biometric Security#Face Recognition#Finger or Palm Veins Recognition#Fingerprint Recognition#Healthcare#Home Security#Iris/Retina Recognition#Law Enforcement#Money Security#speaker recognition#Three Types of Biometrics Security#What is Biometrics?
1 note
·
View note
Text
Understanding the Future of Biometric Authentication with Nialabs

As we venture deeper into the 21st century, technology continues to advance at an unprecedented pace, reshaping how we interact with the world. One of the most transformative areas of innovation is biometric authentication. At Nialabs, we are at the forefront of this revolution, developing cutting-edge solutions that enhance security, efficiency, and convenience for businesses and individuals alike.
The Evolution of Biometric Technology
Biometric technology has come a long way since its inception. Initially, it was primarily used for fingerprint recognition in high-security environments. Today, it encompasses a wide range of modalities, including facial recognition, iris scanning, and voice recognition.
At Nialabs, we've embraced the latest advancements in this field, creating AI-powered biometric devices that are not only highly accurate but also incredibly user-friendly. Our journey began with a simple goal: to make biometric authentication accessible to everyone, from small businesses to large enterprises.
AI-Driven Biometric Systems
Artificial intelligence (AI) plays a crucial role in the development of our biometric systems. By leveraging AI, we've been able to significantly enhance the accuracy and reliability of our devices. Our AI face biometric devices, for instance, can quickly and accurately identify individuals, even in challenging conditions such as low light or when the subject is wearing glasses.
AI also enables our systems to learn and adapt over time. This means that the more they are used, the better they become at recognizing individuals. This continuous improvement ensures that our biometric devices remain effective and secure, providing peace of mind to our clients.
Security and Privacy in Biometric Authentication
One of the primary concerns surrounding biometric technology is security and privacy. At Nialabs, we take these concerns very seriously. We understand that our clients trust us with sensitive information, and we are committed to safeguarding it.
Our biometric systems are designed with multiple layers of security to prevent unauthorized access. This includes encryption of biometric data, ensuring that even if the data were to be intercepted, it would be useless without the decryption key. Additionally, we employ advanced anti-spoofing techniques to prevent fraudsters from using photos, videos, or masks to trick our systems.
Privacy is another critical aspect of our biometric solutions. We adhere to strict data protection regulations and ensure that our clients' biometric data is stored securely and used only for its intended purpose. Our systems also provide options for users to manage their own biometric data, giving them control over how their information is used.
Real-World Applications and Benefits
The applications of biometric authentication are vast and varied. Here are a few examples of how our clients are using Nialabs' biometric technology to enhance their operations:
1. Workplace Attendance and Access Control
Managing employee attendance can be a time-consuming task, especially for large organizations. Our biometric face attendance system simplifies this process, allowing employees to clock in and out with a quick facial scan. This not only saves time but also eliminates the possibility of buddy punching, where one employee clocks in for another.
In addition to attendance tracking, our biometric devices can also be used for access control, ensuring that only authorized individuals can enter restricted areas. This enhances security and prevents unauthorized access to sensitive areas.
2. Customer Authentication in Banking
Banks and financial institutions are increasingly adopting biometric technology to enhance customer authentication. Our face biometric devices provide a secure and convenient way for customers to access their accounts, whether they are using an ATM or a mobile banking app. This reduces the risk of fraud and enhances the overall customer experience.
3. Healthcare
In the healthcare sector, biometric authentication can be used to ensure that only authorized personnel have access to patient records. This helps protect sensitive medical information and ensures compliance with data protection regulations. Our biometric devices can also be used for patient identification, reducing the risk of errors and improving the efficiency of healthcare services.
4. Retail and Hospitality
Retailers and hospitality providers can use biometric technology to enhance the customer experience. For example, our face recognition systems can be used for loyalty programs, allowing customers to quickly and easily access their rewards. In hotels, biometric authentication can streamline the check-in process, providing a seamless experience for guests.
Embracing the Future with Nialabs
At Nialabs, we are committed to staying at the cutting edge of biometric technology. Our research and development team is constantly exploring new ways to enhance our products and services. We believe that the future of biometric authentication is bright, and we are excited to be a part of this journey.
Our mission is to make biometric technology accessible, secure, and user-friendly for everyone. Whether you are a small business looking to streamline your attendance tracking or a large enterprise seeking to enhance your security measures, Nialabs has a solution for you.
We invite you to visit our website for more information about our products and services. If you have any questions or would like to discuss how our biometric solutions can benefit your organization, please don't hesitate to contact us. Our team is here to help you navigate the future of biometric authentication.
Contact Us
Visit Our Website for More Information: Nialabs
Call Us: 8729047305
Address: 101, Vedic Homes, Narayan Vihar, Jaipur, Rajasthan
Email: [email protected]
At Nialabs, we believe that small devices can have a big impact. Join us in embracing the future of biometric authentication and discover the difference that our innovative solutions can make for your organization.
0 notes
Text
Sify Technologies: The Pinnacle of Colocation Services
In the fast-paced digital world, businesses need a reliable and secure infrastructure to manage their IT requirements effectively. Sify Technologies, a pioneer in ICT solutions and services, has established itself as a leader in colocation services. By offering state-of-the-art facilities, unmatched security, and a suite of comprehensive services, Sify ensures that businesses can focus on growth and innovation while their IT needs are expertly managed.
Strategic and Robust Infrastructure
Sify’s colocation services are backed by an extensive network of state-of-the-art data centers strategically located across India. Each facility is designed to provide maximum uptime, security, and operational efficiency. Key features of Sify’s infrastructure include:
Tier III and IV Certification: Ensuring high availability with fully redundant power, cooling, and network systems.
Advanced Power Management: Dual power sources, backup generators, and uninterruptible power supply (UPS) systems guarantee continuous operation even during power outages.
Efficient Cooling Systems: Advanced, energy-efficient cooling technologies maintain optimal operating temperatures, enhancing equipment performance and lifespan.
Comprehensive Security Measures: Multi-layered security protocols, including biometric access controls, 24/7 surveillance, and advanced fire suppression systems, safeguard sensitive data.
Tailored Colocation Solutions
Sify’s colocation services are designed to meet the diverse needs of businesses across various industries. By providing flexible and scalable solutions, Sify ensures that each client receives a tailored service that aligns with their specific requirements. Key offerings include:
Rack Space: From partial racks to full cabinets, Sify offers customizable rack space solutions to accommodate various business needs.
Private Suites and Cages: For businesses requiring additional security and privacy, Sify provides dedicated suites and cages within their data centers.
Remote Hands and Smart Hands: On-site technical support services ensure that any issues are promptly addressed, minimizing downtime and enhancing operational efficiency.
Cross-Connect Services: High-speed, low-latency connections between different networks within the data center facilitate seamless data transfer and communication.
Commitment to Sustainability
Sify is dedicated to environmental sustainability and integrates green technologies into their data centers. By employing energy-efficient servers, advanced cooling systems, and renewable energy sources, Sify minimizes its carbon footprint while reducing operational costs. This commitment to sustainability benefits both the environment and Sify’s clients, who enjoy reduced energy expenses and enhanced corporate social responsibility.
Comprehensive Support and Services
Sify’s colocation services are complemented by a suite of additional offerings designed to support and enhance IT infrastructure:
Cloud Services: Scalable cloud solutions, including public, private, and hybrid cloud options, provide businesses with flexible IT resources.
Managed Services: Expert management of IT infrastructure allows businesses to focus on core operations while Sify handles technical complexities.
Disaster Recovery and Business Continuity: Robust disaster recovery solutions ensure data integrity and business continuity, providing peace of mind in the face of unforeseen events.
Security Services: Advanced cybersecurity solutions protect against evolving threats and ensure compliance with regulatory standards.
Customer-Centric Approach
At the core of Sify’s operations is a commitment to customer satisfaction. The company’s team of dedicated professionals provides round-the-clock support, ensuring seamless operations and addressing client concerns promptly. Sify’s client-centric approach ensures that each business receives tailored solutions that align with their specific needs and goals, fostering long-term partnerships based on trust and mutual success.
Empowering Digital Transformation
Sify’s colocation services are designed to be a catalyst for digital transformation. By providing reliable, scalable, and secure infrastructure solutions, Sify empowers businesses to innovate, scale, and compete in an increasingly digital marketplace. Their comprehensive service offerings and advanced infrastructure support the current technological needs of businesses while anticipating future demands, ensuring long-term value and growth.
In a world where reliable and secure IT infrastructure is crucial for business success, Sify Technologies stands out as a premier colocation service provider. With state-of-the-art facilities, comprehensive service offerings, and a steadfast commitment to sustainability and customer satisfaction, Sify is not just meeting the current demands of the digital landscape but is also poised to lead the way into the future. For businesses ready to embrace the digital revolution, Sify offers the perfect partner for success.
Explore the future of colocation with Sify Technologies and experience unparalleled service, security, and scalability. Welcome to the forefront of digital innovation. Welcome to Sify Technologies.
0 notes
Text
Exploring Trends in the Video Surveillance Market

Image source: Market Sandmarkets
In recent years, the video surveillance industry has witnessed significant growth, driven by escalating security concerns and advancements in technology.
According to recent reports, the global video surveillance market reached $53.7 billion in 2023 and is projected to grow to $83.3 billion by 2028. This growth is propelled by the increasing adoption of CCTV systems, which are forecasted to expand from $43.69 billion in 2023 to a staggering $207.13 billion by 2033.
The rise in demand for surveillance cameras can be attributed to the growing need to enhance security across various sectors, including commercial, residential, and public infrastructure. CCTV systems, in particular, play a crucial role in monitoring and safeguarding properties, preventing incidents, and ensuring public safety.
Read Alos:
Video Surveillance Market Trends in 2024
Biocube’s CCTV-based Solutions Are Bringing Revolutionary Transformations
How is Biocube’s Contactless Attendance System Transforming Global Organizations?
The Future of Face Recognition Technology
How Biometric Background Checks Aid in Secure Employee Onboarding?
Technological advancements such as AI-powered analytics, facial recognition, and cloud-based storage solutions are transforming the capabilities of video surveillance systems. These innovations not only improve the effectiveness of surveillance operations but also enhance operational efficiencies and data management.
As the video surveillance market continues to evolve, businesses and governments are increasingly investing in cutting-edge technologies to bolster their security infrastructure. Stay tuned as we delve deeper into the emerging trends and innovations shaping the future of video surveillance.
#video surveillance#video analytics#video surveillance market#video surveillance market trends#video surveillance industry trends#tech innovation#digital world#technology#future tech#Biocube
0 notes
Text
What are the important safety and security measures implemented by office interior designers in Bangalore?
Creating a safe and secure office environment is a paramount concern for businesses in Bangalore. Office interior designers play a crucial role in implementing safety and security measures that ensure the well-being of employees and protect company assets. In this blog, we will explore the important safety and security measures implemented by office interior designers in Bangalore to create secure workspaces.
Fire Safety Precautions
Office interior designers in Bangalore adhere to strict fire safety guidelines while designing office spaces. They ensure that fire exits are easily accessible and clearly marked. Fire-resistant materials and coatings are used for walls and doors, and fire alarms and extinguishers are strategically placed throughout the office. Office layouts are designed to facilitate quick evacuation in case of an emergency.
Ergonomic Furniture and Workspace Design
Safety and security are not limited to physical hazards but also encompass the well-being of employees. Office interior designers in Bangalore prioritize ergonomic furniture and workspace design to minimize the risk of workplace injuries such as back pain, repetitive strain injuries, and carpal tunnel syndrome. They provide adjustable chairs, ergonomic keyboards, and monitor stands to promote proper posture and comfort.
Proper Lighting and Visibility
Office interior designers in Bangalore ensure that the office has adequate and appropriate lighting. Proper lighting not only enhances productivity but also reduces the risk of accidents and injuries. They strategically place lighting fixtures to eliminate shadows and dark corners, enhancing visibility and overall safety.
Access Control Systems
To regulate entry and restrict unauthorized access, office interior designers incorporate access control systems into their designs. This includes smart card readers, biometric scanners, or keyless entry systems that monitor and control access to specific areas within the office. Access control enhances the overall security of the office.
Video Surveillance
Office interior designers in Bangalore often integrate video surveillance systems into the office design. Strategically placed security cameras deter potential intruders and provide a means of monitoring office activity. Video surveillance can help identify security threats and enhance the overall safety of the workspace.
Secure Storage Solutions
To safeguard company assets and sensitive information, office interior designers implement secure storage solutions. These may include locking file cabinets, secure server rooms, and encrypted data storage systems. Protecting valuable assets ensures the continuity of business operations and reduces the risk of data breaches.
Emergency Communication Systems
In the event of an emergency, clear communication is vital. Office interior designers in Bangalore ensure the implementation of emergency communication systems such as intercoms or PA systems. These systems facilitate immediate communication with employees during emergencies, allowing for swift evacuation instructions or updates.
Anti-Slip Flooring and Safety Signage
To prevent slip and fall accidents, office interior designers choose anti-slip flooring materials for high-traffic areas. They also incorporate safety signage throughout the office to highlight potential hazards and emergency procedures. Clear and visible safety signage promotes awareness and preparedness among employees.
Conclusion
Safety and security are paramount concerns for businesses and their employees. Office interior designers in Bangalore play a critical role in implementing vital safety and security measures to protect employees, assets, and sensitive information. By prioritizing fire safety precautions, ergonomic workspace design, proper lighting, access control systems, video surveillance, secure storage solutions, emergency communication systems, anti-slip flooring, and safety signage, these designers create workspaces that prioritize the well-being of occupants and safeguard the business from potential threats. Investing in the expertise of office interior designers in Bangalore, such as Flipspaces can ensures that your office is designed with the highest safety and security standards, providing peace of mind for employers and employees alike.
0 notes
Text
Biometric Security: The Future of Authentication Explained
Biometric security is emerging as a leading solution, offering enhanced security and convenience by leveraging unique biological traits for authentication. Let's explore the future of authentication through biometric security, its benefits, challenges, and potential applications.
Understanding Biometric Security
What is Biometric Security?
Biometric security refers to the use of biological characteristics—such as fingerprints, facial features, iris patterns, and voice recognition—to verify an individual's identity. Unlike traditional authentication methods that rely on passwords or PINs, biometrics provide a more secure and user-friendly approach by utilizing inherent physical traits that are difficult to replicate or steal.
Types of Biometric Authentication
- Fingerprint Recognition: One of the most common biometric methods, fingerprint recognition involves scanning and comparing the unique patterns of an individual's fingerprints to authenticate their identity.
- Facial Recognition: This method uses algorithms to analyze and compare facial features captured in an image or video with a stored template to verify identity.
- Iris and Retina Scanning: These methods involve capturing detailed images of the iris or retina, which have unique patterns, and comparing them with stored data for authentication.
- Voice Recognition: Voice recognition analyzes vocal characteristics, such as pitch, tone, and cadence, to verify a person's identity.
- Behavioral Biometrics: This emerging field includes techniques like gait analysis, keystroke dynamics, and even mouse movements to authenticate users based on their behavior patterns.
Benefits of Biometric Security
Enhanced Security
Biometric security offers a higher level of protection compared to traditional methods. Since biometric traits are unique to each individual and difficult to replicate, the risk of unauthorized access is significantly reduced. This makes biometrics particularly effective in preventing identity theft, fraud, and other cyber threats.
Convenience and User Experience
Biometric authentication provides a seamless and convenient user experience. Users no longer need to remember complex passwords or carry physical tokens. A quick fingerprint scan or facial recognition can grant access to systems and services instantly, enhancing productivity and user satisfaction.
Reduced Reliance on Passwords
Passwords are inherently vulnerable to attacks such as phishing, brute force, and social engineering. Biometric security reduces the reliance on passwords, minimizing the risks associated with password management. This shift can lead to fewer security breaches and lower administrative overhead for password resets and recovery.
Challenges and Considerations
Privacy Concerns
The use of biometric data raises significant privacy concerns. Biometric information is highly sensitive, and any breach or misuse can have serious implications for individuals. It is essential to implement robust data protection measures, such as encryption and secure storage, to safeguard biometric data from unauthorized access.
False Positives and False Negatives
Biometric systems are not infallible and can produce false positives (incorrectly identifying an unauthorized user as authorized) or false negatives (failing to recognize an authorized user). Continuous improvement of biometric algorithms and technologies is necessary to minimize these errors and enhance accuracy.
Cost and Implementation
Implementing biometric security solutions can be costly, requiring investment in specialized hardware and software. Organizations must consider the total cost of ownership, including maintenance and updates, when adopting biometric technologies. Additionally, integrating biometrics into existing systems can be complex and may require significant technical expertise.
Applications of Biometric Security
Financial Services
In the financial sector, biometric security is used to enhance the authentication process for banking services, mobile payments, and ATM access. Biometric authentication provides an additional layer of security, protecting against unauthorized transactions and ensuring that only authorized individuals can access financial accounts.
Healthcare
Biometric security is transforming the healthcare industry by improving patient identification, streamlining access to medical records, and enhancing the security of prescription management. Biometric authentication ensures that only authorized healthcare professionals can access sensitive patient information, reducing the risk of data breaches and fraud.
Government and Border Control
Governments and border control agencies are increasingly adopting biometric security for identity verification and access control. Biometric passports, facial recognition at airports, and fingerprint scanning for visa applications are some examples of how biometrics are used to enhance security and streamline processes in border control and immigration.
Corporate Security
Organizations are leveraging biometric security to protect sensitive data and ensure secure access to corporate networks and facilities. Biometric authentication can be used for employee access control, secure login to workstations, and protection of confidential information, enhancing overall security posture.
Consumer Electronics
Biometric security is becoming ubiquitous in consumer electronics, with smartphones, laptops, and other devices incorporating fingerprint sensors, facial recognition cameras, and voice recognition features. These advancements provide users with a secure and convenient way to unlock devices and access services, improving overall user experience.
The Future of Biometric Security
Advancements in Technology
The future of biometric security is set to be shaped by continuous advancements in technology. Innovations in artificial intelligence (AI) and machine learning (ML) are enhancing the accuracy and reliability of biometric systems. These technologies can analyze vast amounts of data, identify patterns, and improve the performance of biometric algorithms.
Multimodal Biometrics
Multimodal biometrics involves combining multiple biometric methods to enhance security and accuracy. By using more than one biometric trait for authentication, such as combining fingerprint and facial recognition, the likelihood of false positives and false negatives is significantly reduced. This approach provides a higher level of security and can be tailored to specific use cases and requirements.
Integration with IoT and Wearables
The integration of biometric security with the Internet of Things (IoT) and wearable devices is expected to drive innovation in authentication methods. Wearable devices, such as smartwatches and fitness trackers, can incorporate biometric sensors to provide continuous authentication based on physiological data. This seamless integration enhances security and user convenience in various applications.
Regulatory and Ethical Considerations
As biometric security becomes more prevalent, regulatory and ethical considerations will play a crucial role in shaping its adoption. Governments and regulatory bodies will need to establish clear guidelines and standards for the use of biometric data, ensuring that privacy and security are maintained. Ethical considerations, such as informed consent and transparency, will also be essential to address concerns and build trust among users.
In summary, biometric security represents the future of authentication, offering enhanced security and convenience by leveraging unique biological traits. As technology continues to advance, biometric authentication methods will become more accurate, reliable, and widely adopted across various industries. By addressing privacy concerns and ethical considerations, organizations can harness the potential of biometric security to protect against evolving cyber threats and provide a seamless user experience.
Read the full article
0 notes