#BitLocker Keys in AD
Explore tagged Tumblr posts
Text
How to fix BitLocker always prompting for Recovery Key
In this article, we will discuss how to fix BitLocker always prompting for Recovery Key. Please see “How to fix you are not allowed to view this folder on SSRS: MBAM reports cannot be accessed because it could not load folder contents“, and How to Change the Lock Screen Wallpaper in Windows 11. BitLocker is an encryption function of the Windows Operating System. Encrypted drives can only be…

View On WordPress
#Bitlocker#BitLocker Backup#bitlocker key#BitLocker Key Recovery#BitLocker Keys in AD#BitLocker Network Unlock#BitLocker Recovery Key Request#BitLocker Recovery Keys#BitLocker Recovery Mode prompted#BitLocker Recovery Password Viewer#Bitlocker Recovery Prompt#Windows#Windows 10#Windows 11
0 notes
Text
CrowdStrike'd and BitLocker'd
With yesterday's CrowdStrike outage. I'm sure a number of you are probably wondering "what does BitLocker have to do with any of this?" Well, it all has to do with an added layer of security many organizations use to keep data from being stolen if a computers ends up in the hands of an "unauthorized user."
To start, let me briefly explain what the CrowdStrike driver issue did and what the fix for it is.
After the update was automatically installed to computers running the CrowdStrike Falcon Sensor, a faulty driver file caused the Windows kernel on those computers to crash and display a Blue Screen of Death. How Windows typically handles a crash like this is to create a crash log file, then perform a reboot. Since this driver would launch shortly after Windows finished booting, it would cause the operating system to crash and reboot again. When two crashes have occurred in sequence, Windows will automatically boot into Recovery Mode. Hence why we say several pictures of the Recovery Mode screen across social media yesterday.

Unfortunately, this update was automatically pushed out to around 8.5 million computers across several organizations, causing widespread chaos within the matter of a few hours. And the fix for this issue had to be performed by physically accessing each computer, which required those of us working in I.T. to have to run around several facilities, locate each affected computer, and apply the fix one by one.
The short and simple of the fix is either one of two options. You can either use the Recovery Mode that Windows was already booted into to navigate to Start-Up Setting, and launch Safe Mode. Once Windows boots into Safe Mode, the technician can navigate to C:\Windows\System32\Drivers\CrowdStrike, and delete the file C00000291-*.sys. After that the computer can be rebooted as normal, and the crashing will stop.
Or the technician can open System Restore from Recovery Mode. And, assuming there is a recovery point, restore the computer back to a good known working state.
Now, this may all seem simple enough. So why were so many organizations having trouble running this fix? That all has to do with BitLocker. As an added security measure, many organizations use BitLocker on their computers to perform a full hard disk encryption. This is done so that if a computer ends up being lost or stolen, and ends up in the hands of an "unauthorized user" they will not be able to access any of the data stored on the computer without a password to log into the computer, or the computer's BitLocker recovery key.
This presented a problem when trying to restore all of these affected computers, because when either trying to launch Safe Mode or System Restore, the user would be prompted for the BitLocker recovery key.
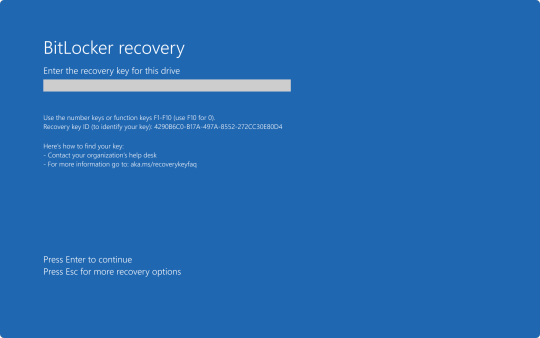
In my organization's case, we found we could save time by providing our end user the steps to perform one of the two fixes on their own to save time. But the problem we still continue to run into is the need for these BitLocker recovery keys. In my case, I've been fielding several calls where I've had end users walking from one computer to another while I provide them with the key as they walk through reverting back to a previous restore point.
Again, a pretty long story, but hopefully that can provide some context as to what's been happening over the past 48 hours.
30 notes
·
View notes
Text
Do not implement changes on a Friday afternoon. Ever. That is, unless working 48 hours straight over the weekend is your goal.
Another lesson - Grampa IT reminds you that your backup is only as good as your last restore. A lesson learned with 9 track magtape.
Addendum from: https://www.tumblr.com/phantomrose96
7h ago
This is all true, but it's worth noting the fix (honestly more like "fix", as in it at least stops the crashing) can only be implemented if someone is capable of booting their machine in safe mode.
If a machine is encrypted via Bitlocker (an added safety measure), booting into safe mode requires unlocking Bitlocker with the machine's Bitlocker key. And if you weren't keeping that key on hand on a post-it note or in your notes app (neither of which is a good idea) then you need to access it via the Bitlocker system on another machine... which is likely also bricked.
So the "luckier" companies out there are spending the whole day manually safe-booting and file-deleting across 10s of thousands of computers, one at a time. The unluckier companies are locked out of the house without their keys. I've yet to hear a solution for those in the Bitlocker scenario.
idk if people on tumblr know about this but a cybersecurity software called crowdstrike just did what is probably the single biggest fuck up in any sector in the past 10 years. it's monumentally bad. literally the most horror-inducing nightmare scenario for a tech company.
some info, crowdstrike is essentially an antivirus software for enterprises. which means normal laypeople cant really get it, they're for businesses and organisations and important stuff.
so, on a friday evening (it of course wasnt friday everywhere but it was friday evening in oceania which is where it first started causing damage due to europe and na being asleep), crowdstrike pushed out an update to their windows users that caused a bug.
before i get into what the bug is, know that friday evening is the worst possible time to do this because people are going home. the weekend is starting. offices dont have people in them. this is just one of many perfectly placed failures in the rube goldburg machine of crowdstrike. there's a reason friday is called 'dont push to live friday' or more to the point 'dont fuck it up friday'
so, at 3pm at friday, an update comes rolling into crowdstrike users which is automatically implemented. this update immediately causes the computer to blue screen of death. very very bad. but it's not simply a 'you need to restart' crash, because the computer then gets stuck into a boot loop.
this is the worst possible thing because, in a boot loop state, a computer is never really able to get to a point where it can do anything. like download a fix. so there is nothing crowdstrike can do to remedy this death update anymore. it is now left to the end users.
it was pretty quickly identified what the problem was. you had to boot it in safe mode, and a very small file needed to be deleted. or you could just rename crowdstrike to something else so windows never attempts to use it.
it's a fairly easy fix in the grand scheme of things, but the issue is that it is effecting enterprises. which can have a looooot of computers. in many different locations. so an IT person would need to manually fix hundreds of computers, sometimes in whole other cities and perhaps even other countries if theyre big enough.
another fuck up crowdstrike did was they did not stagger the update, so they could catch any mistakes before they wrecked havoc. (and also how how HOW do you not catch this before deploying it. this isn't a code oopsie this is a complete failure of quality ensurance that probably permeates the whole company to not realise their update was an instant kill). they rolled it out to everyone of their clients in the world at the same time.
and this seems pretty hilarious on the surface. i was havin a good chuckle as eftpos went down in the store i was working at, chaos was definitely ensuring lmao. im in aus, and banking was literally down nationwide.
but then you start hearing about the entire country's planes being grounded because the airport's computers are bricked. and hospitals having no computers anymore. emergency call centres crashing. and you realised that, wow. crowdstrike just killed people probably. this is literally the worst thing possible for a company like this to do.
crowdstrike was kinda on the come up too, they were starting to become a big name in the tech world as a new face. but that has definitely vanished now. to fuck up at this many places, is almost extremely impressive. its hard to even think of a comparable fuckup.
a friday evening simultaneous rollout boot loop is a phrase that haunts IT people in their darkest hours. it's the monster that drags people down into the swamp. it's the big bag in the horror movie. it's the end of the road. and for crowdstrike, that reaper of souls just knocked on their doorstep.
114K notes
·
View notes
Text
Sconti sulla licenza a vita e sulla chiave Pro di Windows 10 in Italia
Nel mondo digitale odierno, disporre del sistema operativo giusto è fondamentale sia per le attività personali che professionali. Una comoda licenza a vita di Windows 10 è un ottimo modo per garantire il corretto funzionamento del computer senza l'incertezza dei costi sistematici. Per chi vive in Italia, lo sconto sulla chiave Pro di Windows 10 in Italia offre un modo conveniente per accedere ai componenti premium di Windows 10 Pro senza spendere una fortuna. Queste offerte offrono agli utenti una soluzione efficiente per migliorare la produttività e le prestazioni.
Perché una licenza a vita di Windows 10 è conveniente
Scegliere una comoda licenza windows 10 a vita conveniente offre importanti vantaggi sia per gli utenti domestici che per le aziende. Il vantaggio più evidente è che elimina la necessità di rinnovi annuali o abbonamenti. Una volta acquistata, la licenza è valida a vita, garantendo che il sistema operativo rimanga attivo a tempo indeterminato. Questa comodità elimina il fastidio di doversi preoccupare della scadenza della licenza o di pagamenti ripetuti. È molto utile per gli utenti di lunga data che desiderano un sistema operativo affidabile senza impegni finanziari costanti.
Accesso alle funzionalità Premium con la chiave di Windows 10 Pro
Per gli utenti che desiderano funzionalità avanzate, uno sconto sulla chiave di Windows 10 Pro key discount in Italy offre un modo conveniente per sbloccare le credenziali premium della versione Pro. Windows 10 Pro offre funzionalità diverse che si rivolgono ad aziende e utenti esperti, come l'accesso al desktop remoto, la crittografia BitLocker e strumenti avanzati di gestione dei gruppi. Con uno sconto sulla chiave di Windows 10 Pro in Italia, privati e aziende possono accedere a queste funzionalità avanzate senza dover pagare l'intero prezzo di vendita, il che lo rende un'ottima soluzione per chi necessita di funzionalità aggiuntive.
Vantaggi di una licenza a vita
Una licenza a vita di Windows 10 offre stabilità e tranquillità agli utenti. Con questo tipo di licenza, non ci sono costi nascosti o rinnovi imprevisti. Si tratta di un investimento una tantum che garantisce aggiornamenti e supporto per tutta la durata del prodotto. Questa affidabilità a lungo termine è particolarmente vantaggiosa per chi utilizza il computer per le attività quotidiane o per chi lo utilizza in modo intensivo. Inoltre, garantisce che gli utenti dispongano sempre dei segmenti più vecchi e delle patch di protezione, mantenendo i loro sistemi sicuri.
Risparmio sui costi con gli sconti sulle chiavi di Windows 10 Pro
Acquistare una chiave di Windows 10 Pro scontata in Italia è un modo ideale per risparmiare denaro e accedere a tutte le potenti funzionalità che Windows 10 Pro ha da offrire. Questa riduzione offre una soluzione ottimale per gli utenti che necessitano di ulteriori funzionalità di Windows 10 Pro ma non desiderano pagare l'intero importo. È particolarmente vantaggiosa per piccole imprese, liberi professionisti o chiunque in Italia cerchi un modo conveniente per migliorare la propria esperienza informatica, garantendo al contempo l'utilizzo dell'ultima versione di Windows 10 Pro.
Perché l'Italia offre fantastiche offerte Windows
L'Italia è diventata un ottimo posto per trovare sconti sui prodotti Windows 10, come lo sconto sulle chiavi di Windows 10 Pro in Italia. Diversi rivenditori e rivenditori autorizzati nella regione offrono prezzi competitivi, principalmente per coloro che desiderano passare a Windows 10 Pro. Grazie all'attenzione del Paese verso l'economia digitale, gli utenti possono trovare offerte e pacchetti esclusivi che rendono l'aggiornamento o l'acquisto di una nuova licenza molto più economici. Per chi risiede in Italia, questa è un'opportunità per risparmiare garantendo al contempo l'acquisto di software legittimo e di alta qualità.
Conclusione
Ottenere una licenza a vita di Windows 10 e usufruire di uno sconto sulla chiave di Windows 10 Pro in Italia offre notevoli risparmi sui costi e vantaggi a lungo termine. Con queste licenze, gli utenti possono usufruire di tutte le potenti funzionalità di Windows 10 senza doversi preoccupare del rinnovo dell'abbonamento o di elevati costi iniziali. Per maggiori dettagli su come accedere a queste offerte, visita elevatesoftwere.com. Ahave Education offre un modo semplice e affidabile per ottenere il massimo dalla tua esperienza con Windows 10 senza rinunciare al budget.
Per saperne di più su questo argomento, visita il nostro sito web.
acquista licenze software garantite in italia
acquista nuance power pdf advanced download
0 notes
Text
Maximize Your Control with Dedicated Windows Servers
When it comes to web hosting and managing digital resources, the need for control, reliability, and high performance is non-negotiable. This is where Dedicated Windows Servers step in, offering a premium solution for businesses, developers, and enterprises looking to elevate their web presence. Unlike shared hosting or virtual private servers (VPS), dedicated servers provide an exclusive environment, giving you full control over your resources and software configurations.
In this blog, we'll explore the benefits and reasons why dedicated Windows servers are the ideal choice for those seeking maximum control over their hosting environment.
What is a Dedicated Windows Server?
A Dedicated Windows Server refers to a physical server that is entirely dedicated to a single user or organization. This means that you don’t share resources like CPU, RAM, or bandwidth with other clients. Powered by the Windows operating system, these servers support a variety of enterprise-level applications, including SQL Server, Active Directory, and custom web hosting environments.
The Windows environment is known for its user-friendly interface and wide support for software, making it an excellent choice for businesses that rely on Microsoft-based applications and require a stable, familiar platform.
1. Full Control Over Your Server
One of the most significant advantages of using a dedicated Windows server is complete control. As the sole user of the server, you have administrative access to the entire machine. This means you can install and configure any software, change system settings, and implement custom solutions according to your needs.
With root access to the operating system, you can:
Install and update software without restrictions.
Set up complex configurations to meet business requirements.
Ensure maximum security by controlling firewall settings and access permissions.
Install custom scripts and tools that may not be available in shared hosting environments.
This level of flexibility is essential for businesses with specific software needs or those operating resource-intensive applications.
2. Enhanced Performance and Reliability
With a dedicated Windows server, performance is vastly improved compared to shared hosting or VPS. Since you're the only user, the server's resources are allocated entirely to your applications and websites, ensuring faster load times and better overall performance.
Key performance benefits include:
No Resource Sharing: Unlike shared hosting, where multiple users share the same server, a dedicated server's resources are all yours.
Better Uptime: Since the server is dedicated to your use, there's less likelihood of experiencing downtime caused by the actions of other users.
Scalability: Dedicated servers can be easily upgraded to accommodate growing needs, whether that involves adding more RAM, storage, or processing power.
This reliability is crucial for businesses that require constant uptime, such as e-commerce stores, large websites, and enterprise applications.
3. Improved Security and Customization
Security is one of the most critical factors for any business operating online. With a dedicated Windows server, you can take control of your security measures and implement custom security protocols. Unlike shared hosting, where security depends on the actions of other users, a dedicated server offers isolated resources, reducing the risk of cyber-attacks and data breaches.
You can customize security settings by:
Installing and configuring your own firewalls.
Using Windows Security features such as BitLocker and Windows Defender.
Creating isolated environments with virtual machines (VMs).
Enabling regular backups and disaster recovery plans.
Implementing SSL certificates for secure transactions.
These customizable options allow you to create a robust security framework suited to your business’s specific needs.
4. Dedicated Support and Expert Assistance
When you opt for a dedicated Windows server, you're not just paying for the hardware and software – you're also getting access to expert technical support. Most hosting providers offer 24/7 support with dedicated teams that understand the intricacies of Windows servers.
This means:
Quick Resolution of Issues: Any technical difficulties or issues are resolved faster with a team that understands your specific setup.
Proactive Monitoring: Many providers offer proactive server monitoring services to identify potential issues before they impact your operations.
Consultation and Optimization: Dedicated support staff can guide you through system optimization and help you get the most out of your server.
This hands-on support ensures you can maintain your server's performance, security, and stability with ease.
5. Cost-Effective for Large Operations
Although dedicated Windows servers are generally more expensive than shared hosting or VPS options, they can be incredibly cost-effective for larger operations or businesses with high resource demands. By consolidating multiple applications, websites, and services onto a single dedicated server, you can save money on multiple hosting solutions.
Additionally, with full control over your server, you can optimize costs by adjusting the configuration to your precise needs, avoiding unnecessary expenses for resources you don’t use.
Conclusion
A Dedicated Windows Server offers unmatched control, performance, and security, making it the ideal choice for businesses that require a customized, scalable, and reliable hosting environment. Whether you’re running mission-critical applications, handling sensitive data, or operating large-scale websites, the flexibility and power provided by a dedicated server can take your business to the next level.
If you’re ready to maximize your control and optimize your online presence, consider upgrading to a dedicated Windows server today. With the right configuration and support, you’ll experience an enhanced digital experience that positions your business for long-term success.
0 notes
Text
Understanding the BitLocker Recovery Key: What It Is and How to Use It

Hey Tumblr friends! 🌟
If you've recently enabled BitLocker on your Windows device and suddenly find yourself staring at a prompt asking for a BitLocker recovery key, you might be wondering what this mysterious key is all about. Let’s dive into the essentials of the BitLocker recovery key, why you might need it, and how to find it when necessary.
What is a BitLocker Recovery Key?
A BitLocker recovery key is a 48-digit numerical password that acts as a backup method to unlock your encrypted drive. This key is generated when you first enable BitLocker on a drive and is crucial for situations where you can’t access your drive through the usual means.
Why Might You Need a BitLocker Recovery Key?
There are several reasons why you might be prompted to enter your BitLocker recovery key:
Forgotten Password: If you forget your BitLocker password, the recovery key is your only way to regain access.
Hardware Changes: Making significant changes to your computer’s hardware, like replacing the motherboard, can trigger the recovery key prompt.
Software Updates: Major updates to your operating system or BIOS might require you to enter the recovery key.
Security Concerns: If BitLocker detects potential security threats or unauthorized access attempts, it will ask for the recovery key.
Where to Find Your BitLocker Recovery Key
If you’re in a pinch and need to find your BitLocker recovery key, here are some common places to check:
Microsoft Account: If you linked BitLocker to your Microsoft account, you can find your key on the Microsoft BitLocker recovery key portal.
USB Drive: If you saved the recovery key to a USB drive, make sure to keep it somewhere safe and accessible.
Printout: Some folks print their recovery key and store it securely.
Azure Active Directory (AAD): If your device is connected to an organization’s AAD, your IT department might have a copy.
File: If you saved the recovery key as a file, it’s usually named something like BitLocker Recovery Key.txt.
What to Do if You Can’t Find Your Recovery Key
If you can’t locate your BitLocker recovery key, your options are unfortunately limited. Without the recovery key, accessing your encrypted data is not possible. This is a vital reminder to store your recovery key securely in multiple locations.
Best Practices for Managing Your BitLocker Recovery Key
Store Multiple Copies: Keep your recovery key in several places, such as your Microsoft account, a USB drive, a printout, and a secure digital file.
Secure Storage: Ensure your recovery key is stored in a safe location, like a safe or encrypted digital storage.
Keep Updated: Regularly update your recovery key and ensure it’s accessible, especially after significant system changes.
By following these best practices, you can avoid the potential frustration and data loss associated with being locked out of your BitLocker-encrypted drive.
For a more detailed guide on BitLocker and managing recovery keys, including step-by-step instructions and troubleshooting tips, check out this Comprehensive BitLocker Recovery Key Guide.
Hope this helps you stay secure and stress-free! If you have any more questions about BitLocker or need further assistance, feel free to drop a comment. 💬✨
Also read our related articals:
How Ad Blockers Might Trigger BSOD Blue Screen
Audio Troubleshooter: Resolve No Sound Issues On Dell Laptop
Laptop Not Connecting To WiFi? Fix Laptop WiFi Issues Today!
How To Fix ‘No Sound’ Issues On Your Laptop Or PC: A Comprehensive Guide
1 note
·
View note
Text
Navigating Windows 10: A Comprehensive Guide to Home Edition and Beyond
Windows 10 continues to be a frontrunner in operating systems, offering a range of editions to cater to diverse user needs. In this guide, we will explore the features and functionalities of Windows 10 Home, examine the significance of a Windows 10 Home key, understand the importance of a Windows 10 Home license, and discuss the seamless transition from Windows 10 Home to Pro.
Unveiling Windows 10 Home: A User-Friendly Experience
Windows 10 Home is the gateway to a user-friendly and efficient computing experience for many users. Let's explore the key attributes that make Windows 10 Home popular for individuals and families.
Intuitive Interface and Accessibility
Windows 10 Home boasts an intuitive interface, ensuring seamless navigation for all levels. With features like the Start Menu and Cortana, accessibility is prioritized, making the operating system suitable for many users.
Cortana Integration for Enhanced Productivity
Microsoft's virtual assistant, Cortana, seamlessly integrates into Windows 10 Home. From setting reminders to answering queries, Cortana enhances productivity by providing quick and efficient assistance.
Security Features for Peace of Mind
Windows 10 Home prioritizes security with features like Windows Defender Antivirus and Windows Hello. Safeguard your system against threats and enjoy the convenience of password-free sign-ins for added peace of mind.
Unlocking Windows 10 Home with a Key
A valid Windows 10 Home key is essential for fully accessing its features. This alphanumeric code is your digital ticket to unlocking the operating system's full potential. Ensure you secure your key from a trusted source for a seamless and secure experience.
The Importance of a Windows 10 Home License
A Windows 10 Home license is your official authorization to use the operating system. Beyond legality, a genuine license ensures access to updates, support, and additional features that might not be available in unlicensed versions. Protect your investment by acquiring a legitimate license for Windows 10 Home.
Elevating Your Experience: Windows 10 Home to Pro Upgrade
As your computing needs evolve, you may require the advanced features offered by Windows 10 Professional. Transitioning from Windows 10 Home to Pro is straightforward and unlocks a host of additional functionalities.
Advanced Security Measures
Windows 10 Professional introduces BitLocker, a powerful encryption tool that enhances data security. If data protection is a top priority, upgrading to Pro is strategic.
Enhanced Remote Desktop Capability
For professionals or businesses needing remote access, Windows 10 Pro's enhanced Remote Desktop feature provides a seamless connection to your device from anywhere, fostering flexibility and productivity.
Domain Join for Business Integration
Windows 10 Pro allows for easy integration into business networks through Domain Join. This feature is especially crucial for enterprises looking to streamline network management and user access.
Conclusion: Optimizing Your Windows 10 Journey
Windows 10 Home provides the foundation for a user-friendly and secure computing experience. From the initial acquisition of a Windows 10 Home key to securing a valid Windows 10 Home license, users can maximize the potential of this versatile operating system.
Should your needs expand, consider the seamless transition from Windows 10 Home to Pro, unlocking advanced features and capabilities. Windows 10 continues to evolve, offering a dynamic and efficient platform for users worldwide. Secure your key, obtain your license, and enjoy the journey of optimizing your computing experience with Windows 10.
0 notes
Text
The Essential Guide to Windows Server: Unveiling the Power of Microsoft's Robust Operating System
In the realm of enterprise-level computing, Windows Server stands as a stalwart, serving as the backbone for countless organizations worldwide. Microsoft's Windows Server is a powerful operating system designed specifically to meet the demanding needs of businesses, providing a robust platform for running applications, managing network infrastructure, and ensuring data security. In this article, we will explore the key features, functionalities, and benefits of Windows Server, shedding light on why it remains a preferred choice for businesses across diverse industries.
Foundation of Windows Server:
Windows Server is built upon the same core architecture as its desktop counterpart, Windows 10. However, it is enhanced with additional features and capabilities specifically tailored to the requirements of server environments. These include advanced networking functions, robust security measures, and scalability options that make it suitable for a wide range of applications.
Server Roles and Features:
One of the defining aspects of Windows Server is its flexibility in adapting to various roles within an IT infrastructure. Through the installation of specific server roles and features, organizations can customize their server environment to meet specific needs. Whether it's acting as a domain controller, file server, web server, or virtualization host, Windows Server excels in its adaptability.
Active Directory:
At the heart of Windows Server's identity and access management capabilities is Active Directory. This centralized authentication and authorization service play a pivotal role in managing user accounts, permissions, and network resources. Active Directory simplifies the administration of large networks and ensures a secure and organized IT environment.
Virtualization with Hyper-V:
Windows Server incorporates Hyper-V, Microsoft's hypervisor-based virtualization platform. Hyper-V enables organizations to create and manage virtual machines (VMs), facilitating server consolidation, resource optimization, and improved scalability. This virtualization solution is a cornerstone for modern data centers seeking efficiency and flexibility.
Security Measures:
In the constantly evolving landscape of cybersecurity threats, Windows Server has fortified its defenses. Features such as Windows Defender, BitLocker, and Credential Guard work in tandem to safeguard servers and data against malicious activities. Regular security updates and patches are part of Microsoft's commitment to keeping Windows Server resilient against emerging threats.
Scalability and Performance:
As businesses grow, their IT infrastructure must evolve accordingly. Windows Server addresses this need by providing scalability options that allow organizations to expand their resources seamlessly. Whether it's adding more servers to a network, scaling up virtual machines, or enhancing storage capacity, Windows Server adapts to the changing demands of a dynamic business environment.
Integration with Cloud Services:
Recognizing the importance of cloud computing, Microsoft has integrated Windows Server with its Azure cloud platform. This integration facilitates hybrid cloud deployments, enabling organizations to leverage the benefits of both on-premises and cloud-based solutions. This hybrid approach provides flexibility, scalability, and cost-effectiveness.
User Interface and Management:
Windows Server offers a user-friendly interface for administrators to manage and monitor server functions. The Server Manager console provides a centralized location for configuring server roles, features, and system settings. Additionally, PowerShell, Microsoft's scripting language, allows for efficient automation and management of tasks.
Conclusion:
Windows Server continues to play a pivotal role in the IT infrastructure of businesses worldwide, offering a comprehensive solution for diverse server-related needs. Its versatility, security features, and integration with cloud services make it an indispensable tool for organizations striving to maintain a reliable, scalable, and secure IT environment. As technology evolves, Windows Server is poised to adapt and remain a cornerstone for businesses seeking a robust and efficient server operating system.
1 note
·
View note
Text
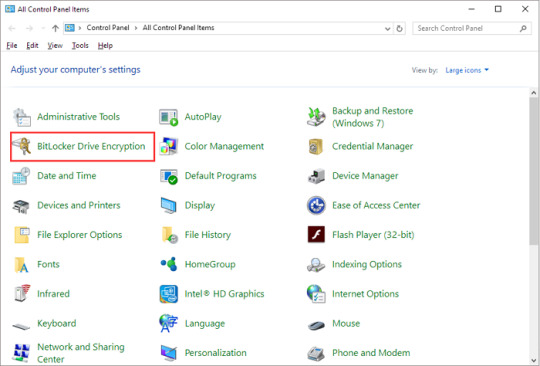
Choosing Turn on Bitlocker
The remaining part of the procedure is the very same as the normal BitLocker setup procedure. You can locate the remainder of the BitLocker specific PowerShell cmdlets here. The period of time required will be contingent on the size of the drive. Before you do so, you can want to learn the time needed to encrypt the drive. Adding BitLocker is not going to encrypt any drives, it will merely make BitLocker available should you desire to utilize it. Just click each option you wish to utilize in turn, and stick to the directions. Find the flash drive you desire to encrypt, and click the Turn on BitLocker link.
For most people, it's not an easy job. The practice requires a while and it involves a reboot, but it is a very excellent concept to run it. After a while, it completes. The entire process is really easy, easy and takes a couple of clicks. Theencryption process will begin.
Hopefully by this time, you ought to be convinced that using BitLocker together with a TPM chip is a great thing. Turning off BitLocker isn't an intuitive practice. It is not recommended by Troy IT under any circumstances. BitLocker To Go will ask you to choose how you wish to unlock the drive once it's encrypted. BitLocker to Go can definitely supply the kind of encryption that you require, but the encryption method which I demonstrated in the very first region of the series requires users to manually encrypt their very own USB flash drives.
To back as much as a BitLocker encrypted destination, the drive has to be unlocked. You can't eject a drive that's being encrypted. If you would like to decrypt your hard disk, all you have to do is turn off BitLocker. So before you begin to encrypt the hard disk, you have to do some particular TPM operations, which we are going to discuss in detail a bit later. With BitLocker, you make a digital hard disk, and encrypt it.
It's possible to select the method by which the drive needs to be unlocked, either with a password or an intelligent card. A partially encrypted drive can still be obtained in Windows but it cannot serve as a backup destination for a BitLocker job. When you choose the encrypted drive, you'll be prompted to join the password.

It's possible to encrypt more than 1 drive at one time, reducing the whole time necessary to encrypt your set of prepared drives. The BitLocker key can likewise be stored on a USB drive. Ever since your USB drive ought to be locked away, you'll be prompted for the PIN, but again, another fine option if necessary. Note, it is going to take a while particularly if it's a huge drive.
Your drive will then be secure with BitLocker. You can pick the drive that you need to encrypt with BitLocker. It's possible to select several various ways of unlocking the drive. You're able to choose how much of the drive you would like to encrypt. In precisely the same process it's possible to decrypt more drives if you would like. If you must be in a position to access a BitLocker-to-Go-protected drive on a Vista or XP system, you are able to but with a few caveats. You are able to also encrypt different drives than only the system drive.
In order to facilitate the process of producing the system volume Microsoft provides a tool known as the BitLocker Driver Preparation Tool. It may either be run as a graphical tool or run from a command prompt with a variety of command-line options to perform the required task. The bitlocker tool wants a reboot after producing the partition anyway.
An unusual icon near the hard disk can reveal an issue. You will notice the screen below asking if you prefer to run the BitLocker check. If a blank screen appears and the computer doesn't restart after you apply the SDR disk, make sure that the boot drive has the required number of free space. After the window is shaken again, all of them are restored, very similar to desktop preview. Following that, your computer should reboot and as soon as you log in again you'll observe the BitLocker window.
If necessary, the choice is there. On the next page you will be given the choice of running a BitLocker Check. Well, cancelling isn't the ideal word as there is not any choice to cancel but only Decrypt'. If you selected the sensible card option, you'll be prompted to insert the intelligent card. When it's already being used, pick the second option Encrypt entire drive. Please be aware that anybody may use the recovery key to access the drive, even in case they do not know the password entered in the former step, so please don't disclose it to others.
Anyone with local accessibility to a Windows machine on the opposite hand may exploit the matter.
youtube
1 note
·
View note
Text
How to Finding your BitLocker recovery key on Aka.ms/recoverykeyfaq

Aka.ms/recoverykeyfaq: BitLocker is one of the security incorporates that go with Windows working framework. It turned out in 2007 as circle encryption programming that uses the AES encryption computation or XTS mode with a 128-digit or 256-cycle key. It was first added to the functioning structure Windows Vista, which came after Windows XP. BitLocker is used to encode all client reports, including structure records and plans, to safeguard them from unapproved access.
The best technique to Find Your BitLocker Recuperation Key in Windows
aka.ms/myrecoverykeyfaq is a component in Windows that scrambles your gadget's hard drive to safeguard your data from unapproved access. In any case, to a great extent you could need to open your gadget with a BitLocker recuperation key, which is a 48-digit code that was delivered when you sanctioned BitLocker.
There are a couple of supports for why you could require a BitLocker recuperation key, for instance,
You neglected to recall your gadget secret word or PIN
You changed your gadget hardware or firmware
You moved your gadget to a substitute association or space
You revived your gadget Profiles or UEFI settings
Your gadget experienced a gear error or power outage
Where could I anytime find my BitLocker recuperation key?
BitLocker presumably ensured that a recuperation key was safely maintained going before ordering protection. There are a couple of spots that your recuperation key may be, dependent upon the choice that was made while ordering BitLocker:
On a printout: You could have printed your recuperation key when BitLocker was instituted. Look where you keep critical papers associated with your PC.
On a USB streak drive: Fitting the USB streak collide with your locked PC and comply with the bearings. In case you saved the key as a text record on the flash drive, use a substitute PC to scrutinize the text report.
In a work or school account: Expecting your gadget was anytime supported into an affiliation using a work or school email account, your recuperation key may be taken care of in that affiliation's Purplish blue Advancement account. You could have the choice to get to it clearly or you could need to contact the IT support for that relationship to get to your recuperation key.
Expecting none of these decisions work for you, then again if you have lost or neglected to recollect your BitLocker recuperation key, you will in all probability not be able to get to your gadget. Taking everything into account, you ought to reset your gadget using one of the Windows recuperation decisions. In any case, this will destroy your reports overall and data on the gadget. Microsoft support can't give or replicate a lost Aka.ms/myrecoverykey BitLocker recuperation key.
To do whatever it takes not to lose permission to your gadget and data later on, guarantee you back up your BitLocker recuperation key in a secured and open spot. You can similarly turn off BitLocker to use it any longer, yet this will in like manner decode your gadget and make it less secure.
End
BitLocker is a phenomenal intrinsic security incorporate available simply on Windows-based laptops. It safeguards your gadget from intruders, developers, and other unapproved clients by encoding all of the reports on the drive. BitLocker in like manner ensures that data will recover with the right recuperation key. Right when you need help figuring out what to do, getting your BitLocker-safeguarded PC back can be hard. Along these lines, this guide should help you with finding your BitLocker recuperation key to get by and by into your gadget. If you have any issue associated with this site, contact us. I trust this article helps you with understanding what is aka microsoft myrecoverykey and how to find it.
0 notes
Text
Acunetix Crack With License Key [Latest]
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 Acunetix Web Vulnerability Scanner Cracked creates several types of reports. Compliance reports confirm compliance with various security. Acunetix Crack [] + Serial Key [] Download. Acunetix Crack A security program that is effective will require collaboration and teamwork. How To install Acunetix Crack: Download the crack from the links below. Extract the archive via the Winrar software on your PC. Run the setup. Acunetix Crack has a web-based easy to use start by adding one or more destination sites that can be organized into multiple. Acunetix Crack includes a large scanning which can recognize objects all across the entire globe. It really is effective security review. Acunetix Web Vulnerability Scanner Cracked. Also, Teamwork and collaboration are necessary to create and maintain effective security programs. Acunetix Crack requires teamwork and collaboration to create and maintain an effective security program. With Acunetix , you can. acunetix__xsh 2. Скопировать Crack/wvsc в "/home/acunetix/.acunetix/v_/scanner/" и перезаписать оригинальный файл. Acunetix V Cracked Hello Everyone Today I have one Tool is best for you to Pentest Web Target. Acunetix is Best Tool Hacking ( News about Acunetix ). Acunetix Crack Download in automated web application security software, has announced the release of Acunetix Version but the new version comes. Acunetix Crack With Full License Key Download Latest Acunetix Crack requires teamwork and collaboration to create and maintain an. With crack Free Download full Version. Acunetix Crack improves the webpages by addressing internet flaws. It creates a secure relationship between. scanner for Linux, vulnerability scanner Acunetix cracked with 0x22, acunetix ## #25 January Acunetix Web Vulnerability Scanner Crack + License Key. Acunetix Crack requires teamwork and collaboration to create and maintain an effective security program. With Acunetix , you can easily. Acunetix Web Vulnerability Scanner 10 COMPLETELY CRACKED! November 17, . Download Acunetix Vulnerability Scanner [Cracked by. Download Acunetix Full Crack is a well-known vulnerability scanner. Additionally, Acunetix can examine folder permissions and identify. Acunetix Crack A security program that is effective will require collaboration and teamwork. With Acunetix , you can easily configure. Acunetix, the pioneer in automated web application security software, BitCracker - BitLocker Password Cracking Tool (Windows Encryption Tool). Acunetix Web Vulnerability Scanner Full Crack Acunetix Web Interface Acunetix ships with an easy to use web interface.
Acunetix V Cracked - DEDSEC T00L
Acunetix v Crack + Serial Key [Latest]
Acunetix Crack v + Serial Key Free Download
Acunetix Crack + Serial Key Free Download Latest
Acunetix Crack With License Key & Full Free Download
Acunetix Crack Full Version Free Download
Acunetix Crack With License Key [Latest]
Acunetix Crack + Serial Key Free Download Latest
Acunetix Crack Full Reviews Free Download [ Latest ]
Acunetix Vulnerability Scanner Version For Linux - Hacking Land - Hack, Crack and Pentest
1 note
·
View note
Text
Acunetix v Crack + Serial Key [Latest]
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 Acunetix Web Vulnerability Scanner Cracked creates several types of reports. Compliance reports confirm compliance with various security. Acunetix Crack [] + Serial Key [] Download. Acunetix Crack A security program that is effective will require collaboration and teamwork. How To install Acunetix Crack: Download the crack from the links below. Extract the archive via the Winrar software on your PC. Run the setup. Acunetix Crack has a web-based easy to use start by adding one or more destination sites that can be organized into multiple. Acunetix Crack includes a large scanning which can recognize objects all across the entire globe. It really is effective security review. Acunetix Web Vulnerability Scanner Cracked. Also, Teamwork and collaboration are necessary to create and maintain effective security programs. Acunetix Crack requires teamwork and collaboration to create and maintain an effective security program. With Acunetix , you can. acunetix__xsh 2. Скопировать Crack/wvsc в "/home/acunetix/.acunetix/v_/scanner/" и перезаписать оригинальный файл. Acunetix V Cracked Hello Everyone Today I have one Tool is best for you to Pentest Web Target. Acunetix is Best Tool Hacking ( News about Acunetix ). Acunetix Crack Download in automated web application security software, has announced the release of Acunetix Version but the new version comes. Acunetix Crack With Full License Key Download Latest Acunetix Crack requires teamwork and collaboration to create and maintain an. With crack Free Download full Version. Acunetix Crack improves the webpages by addressing internet flaws. It creates a secure relationship between. scanner for Linux, vulnerability scanner Acunetix cracked with 0x22, acunetix ## #25 January Acunetix Web Vulnerability Scanner Crack + License Key. Acunetix Crack requires teamwork and collaboration to create and maintain an effective security program. With Acunetix , you can easily. Acunetix Web Vulnerability Scanner 10 COMPLETELY CRACKED! November 17, . Download Acunetix Vulnerability Scanner [Cracked by. Download Acunetix Full Crack is a well-known vulnerability scanner. Additionally, Acunetix can examine folder permissions and identify. Acunetix Crack A security program that is effective will require collaboration and teamwork. With Acunetix , you can easily configure. Acunetix, the pioneer in automated web application security software, BitCracker - BitLocker Password Cracking Tool (Windows Encryption Tool). Acunetix Web Vulnerability Scanner Full Crack Acunetix Web Interface Acunetix ships with an easy to use web interface.
Acunetix V Cracked - DEDSEC T00L
Acunetix v Crack + Serial Key [Latest]
Acunetix Crack v + Serial Key Free Download
Acunetix Crack + Serial Key Free Download Latest
Acunetix Crack With License Key & Full Free Download
Acunetix Crack Full Version Free Download
Acunetix Crack With License Key [Latest]
Acunetix Crack + Serial Key Free Download Latest
Acunetix Crack Full Reviews Free Download [ Latest ]
Acunetix Vulnerability Scanner Version For Linux - Hacking Land - Hack, Crack and Pentest
1 note
·
View note
Photo
What Is This Required Technology For Moving To Windows 11?
The new version of Windows requires the presence of the latest-generation security module. The good news is that your computer is likely to have such a component already.
To be able to install Windows 11 on a computer, it will be necessary to respect a minimum hardware configuration. This specifies, among other things, the presence of a “Trusted Platform Module” (TPM) in version 2.0. A TPM is a cryptographic safe that allows you to create, manage and store secret keys and very sensitive system data. This component makes it possible to create a computing space totally separate from that of the operating system and access to its data is highly secure, in order to protect as much as possible from a possible hacker who might infect the machine.
Used by BitLocker to encrypt disks
Within Windows 10 the TPM is used in different ways. It is used to encrypt hard drive data, whether as part of "BitLocker Drive Encryption" (available on Pro and Enterprise versions) or its watered-down "Device Encryption" version (available on Windows consumer versions). As part of a process called "Measured Boot", it also allows you to monitor and verify the various stages of machine startup.
The TPM also makes it possible to generate and store secret keys and cryptographic data for system applications (“Platform Crypto Provider”), and in particular for Windows Hello, the biometric access control function, and Windows Defender, the anti-security software. -malware from Windows. In professional environments, the TPM can also play the role of a smart card (“Virtual Smart Card”) and protect access tokens to various company resources (“Credential Guard”). According to Microsoft, using these different protective measures would reduce the probability of being infected with malware by 60%.
A component now very common
In short, TPM is today an essential security brick on which more and more features of Windows and third-party applications are based. And under Windows 11, this component will inevitably gain in importance. To run Windows 10, the presence of a TPM 2.0 is not mandatory. However, Microsoft has forced its manufacturing partners to integrate one systematically since July 2016. If your PC is not too old, then there is a good chance that you have one. If it is not enabled, you can do so through your UEFI BIOS menu.
What does a TPM actually look like? In the past, these components have systematically taken the form of a stand-alone chip, soldered to the motherboard, and connected by an LPC or SPI bus. With version 2.0, this module can also be implemented at the firmware level as a separate execution space. These "firmware TPM" (or fTPM) save space on the motherboard and save energy while having a similar level of security. It is the most common form of TPM and the major chip vendors have such technology. It is called "Platform Trust Technology" (PTT) at Intel, "fTPM" at AMD, and "TrustZone" at ARM.
Windows upgrades from mobile OS
If Microsoft now requires the presence of a TPM 2.0 for Windows 11, it is to raise the general level of security of its operating system. As computer attacks become more and more sophisticated, bypassing a cryptographic vault today would be suicidal. The actors of the mobile world have understood it well. Android and iOS smartphones have had a kind of TPM for years, called “TrustZone” and “Secure Enclave” respectively. Moreover, Microsoft cannot be satisfied with the previous version of TPM 1.2, whose services offered have become obsolete. Indeed, it only integrated the SHA-1 and RSA cryptographic algorithms, knowing that AES was optional. Its successor offers a much stronger palette, adding SHA-256, ECC, HMAC, and 128-bit AES.
We are here to hear from you
Of course, you can contact us to let us know if we are missing something on our stepphase.com page. I hope you like it and by the way, thank you for your visit.
Have a good day! See you all soon.
It may interest you
Google is looking to integrate a high-quality photo sensor on the front of its smartphones
Apple Glass patent shows how it could avoid Google Glass fail
Windows 11: all about Microsoft's new OS like release date, new features
Best Photo Editor for iPhone free apps list is here
Windows 11: new features, release date, all about Microsoft's new OS
Source : Microsoft
#Stepphase #technologies #technology #tech #technews #techworld #techtrends #smartphone #apple #techupdates #futuretechnology #newtech #techgeek #technologynews #technologythesedays #smarttechnology #technologylover #technologytrends #technologyblog #gadgets #smartphone #gadget #marketing #digital #india #technologyisawesome #amazing #repost
0 notes
Text
Disable bitlocker

manage-bde –unlock drive-letter: -rp 48-digit-numerical-recovery-keyĮ.g.
Once you find the drive letter of the encrypted drive, give the following command to unlock the encrypted drive by using the recovery key. In command prompt, give the following command to view the BitLocker status of all drives:ĥ. Then go to Troubleshoot -> Advanced options -> Command promptĤ.
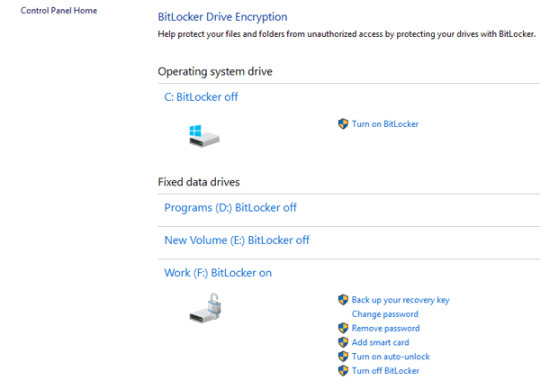
In the screen you asked for the recovery key, click Skip this drive.ģ. At the first screen click Next and then Repair you computer.Ģ. Boot your system from a Windows 10 Installation Media (USB or DVD).Ģ. After unlocking the drive, follow the instructions at case-1 to turn off the bitlocker encryption. Attach the encrypted drive on another Windows 10 PC and then double click on the drive and type the recovery key to unlock it. If the Bitlocker recovery key, is not accepted at system startup, then you have the following options: Type the bitlocker recovery key (48-digit number) at system startup. Unlock the drive by Entering the Recovery key. If you find the recovery key, proceed to step-2 below, otherwise proceed to step-3. if you use an MSA account to logon to Windows 10, or to download Apps from the Microsoft Store, or to get your emails, or to activate Microsoft Office), then from another device with Internet access, sign in with that Microsoft Account at Microsoft's Bitlocker Recover Key webpage to get the Recovery key for your device. Note for DELL devices: If you own a Dell PC or laptop and you have added a Microsoft account (MSA) on you device, for any reason (e.g.
On your Azure Account if you sign in with an Azure Active Directory account.
(Plug the USB drive on the locked PC and follow the instructions) (Type the 24-digit number recovery key from the printout) So, If you have enabled the Bitlocker Drive encryption on your system, then look at the following locations to find the bitlocker recovery key: First of all, you should know that there is no way to bypass the Bitlocker encryption, if you don't have the Bitlocker password or the bitlocker recovery key. How to Disable Bitlocker if you Cannot login to Windows. Click Turn off Bitlocker on the encrypted drive.Ĭase 2. At 'Manage Bitlocker' section, click Bitlocker Drive Encryption.ģ. Navigate to Windows Control Panel and open System and Security.Ģ. The normal way to disable the bitlocker encryption in Windows 10 is the following:ġ. How to Disable Bitlocker Encryption If you can login to Windows 10. How to Remove Bitlocker Encryption in Windows 10.Ĭase 1.
Related article: How to Encrypt Drive C: with BitLocker in Windows 10 Pro & Enterprise.
In this tutorial, you 'll find all the available methods to remove the Bitlocker Drive Encryption in Windows 10. In other cases, some users complained that the Bitlocker encryption was enabled automatically, after updating the BIOS on their Dell laptop. Recently, one of my customers, brought his Windows 10 Dell laptop to our service, with the following problem: When the laptop starts, it prompts to enter the BitLocker recovery key, but, as my customer says, it has never enabled the BitLocker encryption on the system.Īfter some research on the Internet, I found that on some Dell devices the bitlocker is starting automatically to encrypt the drive if a Microsoft Account (MSA) is used on the system.

0 notes