#CPU utilization
Explore tagged Tumblr posts
Text
ESXTOP commands: The Ultimate Guide
ESXTOP commands: The Ultimate Guide @vexpert #vmwarecommunities #100daysofhomelab #homelab #ESXTOPGuide #VMwarePerformanceMonitoring #ESXiHostOptimization #VirtualMachineTroubleshooting #CPUUtilization #MemoryManagement #ESXTOPCommands
When performance issues arise in your virtual machines running in VMware vSphere, understanding how to troubleshoot and optimize is crucial. One versatile tool at your disposal is ESXTOP, a command line interface that provides real-time data on the ESXi host and its virtual machines. Let’s take a look at ESXTOP commands you need to know. Table of contentsWhat is ESXTOP?ESXTOP commands for…

View On WordPress
#batch mode ESXTOP#CPU utilization#ESXi host optimization#ESXTOP commands#ESXTOP guide#memory management#network statistics#storage performance issues#virtual machine troubleshooting#VMware performance monitoring
0 notes
Text
Identifying Query CPU Core Utilization in SQL Server 2022
Diving into the world of database management, especially when it comes to enhancing performance, can sometimes feel like you’re solving a complex puzzle. With SQL Server 2022, this journey gets a bit more intriguing thanks to its new features designed to help us peek under the hood and see how our queries interact with the system’s resources. For those of you who’ve been wondering if there’s a…
View On WordPress
#CPU core utilization#dynamic management views#query profiling SQL#SQL Server 2022 performance#SQL Server optimization
0 notes
Text
GOG has announced a Preservation Program, preserving old games for current and future PC setups. Over 100 games have now been "preserved by GOG". one of these games is Dragon Age: Origins - Ultimate Edition. change notes/updates made:
"Dragon Age: Origins – Ultimate Edition #### Update (13 November 2024) – Enabled Large Address Aware (LAA) support to enhance memory utilization. – Limited the game to 2 CPU cores to boost performance and stability. – Verified compatibility with Windows 10 and 11. – Added Cloud Saves support."
[source]
909 notes
·
View notes
Text
Every computer is worth something but most normal users can get great use out of a computer with at least 2 sata connections and capacity for at least 4 gigabytes of memory, the cpu on a machine with these specs should be good enough but aim for 1.5+ ghz. You can pretty commonly find these specs on donated or very cheap computers.
You can get an 8 terabyte sata drive for less then $200 and have a great amount of storage for as long as the disk lasts and more if you set up a backup/raid
With Linux (I reccomend Ubuntu server for beginners) this will give you enough power to run some network utilities like pi-hole for dns ad blocking and/or a network attached storage setup and/or a media server software like Jellyfin.
This is a great way to reuse old tech and improve your digital life.
61 notes
·
View notes
Text
Desperate PC Tenno calling for help!
Calling all the tech-savvy players here on Tumblr who may hopefully lend me and tech support a hand. Yes, the situation is that bad. More under the cut to spare a lengthy wall of text!
I've been experiencing totally random and sudden crashes with WF since a month and half, by now.
The game first freezes for less than a minute, then crashes to desktop bringing up the window to report crashes. This happens literally anywhere and anytime in the game. During mission, at the end of the mission, while idling in the Orbiter/base of operations, sitting in the pause menu, checking the settings menu. All kind of possible scenarios. Ah, and DX11 or DX12 make no difference either.
It's driving me - and tech support - insane. Because it is so HARD to pinpoint the root cause! Every log file so far has reported some kind of General Protection Failure (GPF) error followed by different numbers.
I'm running the game on a brand new, pre-built computer from Megaport. Which I moved to from my old potato of a PC back in late November. Specs are the following: Windows 11 Home (build 24H2) Intel Core I7-12700KF, 8x 3.60 Ghz + 4x 2.70 Ghz ASUS Prime Z790-A Wifi DDR5 NVidia GeForce RTX 4070 Dual Palit 12GB 2x 32GB Corsair Vengeance RGB DDR5-6000 1 TB SSD 1000 Watt PSU
I have done everything tech support has suggested me to do and: - Uninstalled and re-installed the game, - Update drivers. Being a new computer, everything is pretty much up to date. I had to do a clean install for the GPU drivers only using DDU, though, - Verified game files, - Emptied the shader cache on the drive game is saved to, - Repaired Steam library, - Lowered graphic settings, - Attempted to launch and run Warframe in Clean Boot mode to exclude background programs/services <- unsuccessfully; Steam didn't work at all (which I kind of figured would happen) and trying to launch the game straight from the launcher...triggered a download of the game files in the App Data folder on main (C) drive. O_o The random crashes don't even appear in the Windows Event Viewer. Nowhere to be found. And believe me, I have looked into every single category. I've been keeping track of the time(s) of the crashes but, alas, found nothing that could possibly be related to those. (also, I'm not a computer expert so perhaps I'm doing things wrong)
So far, the only weird thing I've noticed is...Most of the times there seemingly is a "break" in between each series of crashes. A few days at worst, 10-12 days at best. Yes, I checked even the Task Scheduler utility on Windows. Found no program/app that runs automatically that matches with the timing/days when the crashes have occurred so far.
Really losing my mind to this. It's frustrating, it's unnerving, it's making me genuinely terrified of playing the game. And the reason I got this PC in the first place was being finally able to play my favorite game without worrying about being unable to because of my old (and obsolete) machine! Because I don't know when the next crash shall decide to happen and oh boy it's gonna be so fun losing progress. Or having a couple of players reasonably angry at me for suddenly poofing as host. I'm really sorry about that, folks.
I'm already considering the option of total formatting this computer, should there be no other way. But not before entirely giving up. And maybe make things a little less complicated for tech support team.
I can't thank these guys enough for their help and most importantly patience over the past month and half. This mess has been handed to three different people already and a solution hasn't been found yet.
So, if there are fellow Tenno on Tumblr who have either experienced something like this before and found a fix or are just more knowledgeable about computers and whatnot, your help would be GREATLY appreciated. ;.;
EDIT: I forgot to mention a few important things! - Hardware temperatures are within optimal range while in game (CPU never above 65°C, GPU has been running ice cold and has rarely exceeded 50°C so far, RAM is chilling at 45°C average). - GPU memory usage averages around at max (peak) 77% on HWInfo. - CPU usage I honestly need to check! D: - Ran disk cleanup, scans with sfc, chkdsk and DISM (all through command prompts ran as admin) and no issues were found. - Checked RAM health as well with Windows' memory diagnostic tool. However, it seems to give many false positives even on perfectly functional RAM banks. Looking for a more reliable alternative. - Warframe is the only game that keeps crashing on this PC. I haven't been getting any with other games/programs (Hades II; need to test how Ultrakill performs) or any warning signs (BSODs, freezes, sluggish PC, etc) that could suggest hardware failure.
#warframe#I even made a post on the official WF forums but nobody bothered to answer#don't know where else I should ask for help
34 notes
·
View notes
Note
recently i was watching a youtuber play mario party against 3 other AI controlled characters and it got me thinking. when it comes to games like mario party (Or any other game where you have an AI controlled opponent like XCOM) how do developers even begin to design an AI opponent who isnt automatically faster than you in a mini game of speed, or doesnt automatically know the solution to a puzzle in a room before you do and still has to figure it out, or cant guess the correct solution to a quiz automatically, all while still making it feel like you could actually lose to the AI without it feeling overly unfair?

Whenever we design anything, we usually start from the goal and work our way backwards. Our goal for these AI players is absolutely not for them to try to win - that would actually be quite easy, as you say. If we wanted the AI to win, it would always play optimally and, if we wanted, could cheat via inhuman reactions, frame-perfect inputs, utilize CPU-only knowledge, never take a shot that could miss, never make an execution mistake, and so on. However, this is not fun or engaging for players by any stretch. Most players would not want to play against such AI. Our goal is to make AI that players want to play against. That means our goal is for our AI to lose convincingly, much like how parents feign weakness or ignorance while playing with their children.

How do we do that? Well, we can consider the kind of mistakes we expect human players to make and expand on those. Players often overestimate their own resources and overextend. Perhaps the AI spends everything it has immediately and keeps nothing in reserve, leaving itself open after exhausting all of its resources. Players can also play too cautiously, keeping too much in reserve and only spending the absolute minimum. We could make an AI greedy to stockpile resources but only use them when they're near full. Players often tunnel vision on one target and forget to tend other tasks they need to do. We can make an AI do that as well.

These design choices would make the AI players feel more like human players to play against by embracing human foibles as their own driving directives. Similarly, such directives also give the AI weaknesses that a player can observe and exploit to win. If you take a step back, you're looking at the basis for all of game design. We want the players to have a specific experience (e.g. a match that feels like playing another human player rather than an AI), so we figure out what it would take for the player to have that experience, and we construct those bits to convince the player it is happening.
[Join us on Discord] and/or [Support us on Patreon]
Got a burning question you want answered?
Short questions: Ask a Game Dev on Twitter
Long questions: Ask a Game Dev on Tumblr
Frequent Questions: The FAQ
48 notes
·
View notes
Text
What is the kernel of an operating system ?
You can think of the kernel as the core component of an operating system, just like the CPU is the core component of a computer. The kernel of an operating system, such as the Linux kernel, is responsible for managing system resources ( such as the CPU, memory, and devices ) . The kernel of an operating system is not a physical entity that can be seen. It is a computer program that resides in memory.
Key points to understand the relationship between the kernel and the OS:
The kernel acts as the intermediary between the hardware and the software layers of the system. It provides a layer of abstraction that allows software applications to interact with the hardware without needing to understand the low-level details of the hardware
The kernel controls and manages system resources such as the CPU, memory, devices, and file systems. It ensures that these resources are allocated and utilized efficiently by different processes and applications running on the system.
The kernel handles tasks like process scheduling, memory management, device drivers, file system access, and handling interrupts from hardware devices.
The kernel can be extended through the use of loadable kernel modules (LKM). LKMs allow for the addition of new functionality or device drivers without modifying the kernel itself.
#linux#arch linux#ubuntu#debian#code#codeblr#css#html#javascript#java development company#python#studyblr#progblr#programming#comp sci#web design#web developers#web development#website design#webdev#website#tech#html css#learn to code#Youtube
225 notes
·
View notes
Text
very brief torrent security primer
some brief comments on piracy safety for @goblin-thembo who has been asking a lot of questions in the notes of that post...
OK, so when you download a torrent, you are downloading some files. The BitTorrent protocol makes it almost impossible to substitute a different file than the one you request, but you have no way to be absolutely certain that the original file is 'safe' - that depends on the properties of the file, and what you do with it. Some types of file are safer than others.
Here's some jargon you may find useful.
torrent: a file that describes how to download some files through the BitTorrent protocol. we won't go into the technicalities, but when you load a torrent into your torrent client, you will connect to other people who have parts of the files, download the pieces, and reassemble the files you want.
seeding: providing a copy of the files in a torrent to other people.
ISP: Internet Service Provider, the company that connects you to the internet.
IP address: your computer's identity on a network, notably the public internet. When you connect to a website, they know your IP address. Your IP address is assigned by your ISP.
From an IP address, you can determine someone's broad geographical location (which country they're connected in) and which ISP they are using. You can contact the ISP, who will be able to associate it with a specific user.
swarm: the collection of users downloading or seeding a particular torrent.
VPN: Virtual Private Network, a relay service which hides your IP address from the public internet. People who connect to you will see the VPN's IP instead of your real IP. Your ISP will be able to know that you connected to a VPN, but not what you send through it. So they wouldn't be able to tell if you are using BitTorrent. VPNs usually cost a fairly small amount of money as a subscription service.
Threat model
In security we talk about a 'threat model', which is what you think you need to protect yourself from. There are two major threats when downloading files using BitTorrent.
copyright claims: your computer's IP is broadcast when you use BitTorrent. Copyright holders will often put 'sniffers' on the network which will monitor the IPs in the swarm of popular torrents. They will then send a takedown letter to your internet service provider (ISP), who will usually send you an email to stop sharing copyrighted media on their network, and then cut off your internet on multiple offences. This can easily be circumvented using a VPN. I strongly recommend using a VPN if you download any copyrighted content through BitTorrent.
attacks through the file you download: someone might upload a virus as a torrent, presenting it as a file you might be looking for (e.g. cracked software). So let's go over different types of file you might download and how they could be used to attack you.
Executable files, such as pirated software, are not safe. If you download a program and run it, you are potentially giving the author full control over your computer. So you should make damn sure the uploader is trustworthy. If you're downloading open source software from the maintainer's github release page, you're probably good. If you're downloading cracked art programs or games... good luck lol.
On a public torrent tracker, to which anyone can upload, there is no guarantee that any file is what anyone says. You have to make your own determination of which uploaders are trustworthy. I can't give you great advice on this, since I generally do not download cracked executables. For games, FitGirl Repacks is generally a pretty good source.
If you are on Windows, the default Windows Defender software should be used to scan any file you download. (Paid antivirus software is of somewhat dubious utility, often pushing ads and using CPU resources in its own right.) Fewer attackers will target desktop Linux or OSX, which doesn't mean you're guaranteed safe, but Windows is the biggest target as the most widely used operating system.
Videos, music and images are generally safe. I say 'generally' because it's possible, in theory, to create a video that exploits a vulnerability in your video player (e.g. mpv or VLC) and uses it to execute code. So far as I know this is largely theoretical, and known vulns have been patched, but make sure to keep your player up to date to mitigate against known vulnerabilities.
Any compressed archives (zip, rar, 7zip) can be used to create something called a 'zip bomb', which is a file which goes into an infinite loop when you try to decompress it, swallowing up more and more memory and hard drive space. I've never seen this actually be done, but it's possible. More subtle attacks would attempt to attack the program you use to decompress the file. Keep your software up to date to mitigate against known vulnerabilities.
Besides taking care about what you download, on Windows you should either not run your main account as an admin account, or make sure to set User Account Control to require a credentials check for admin operations, and also keep your operating system and software up to date. Make sure file extensions are visible so you don't get fooled by a file disguised as a different file type. And y'know, if the torrent tracker has comments, check to see if a lot of people are saying it's a virus.
What could happen if your computer gets infected? Well, they might use your computer to mine crypto at the cost of your CPU performance, they might encrypt and ransom your files, and they might steal your credentials for online services (including banking and the like). There are various measures you can take against this, such as making sure to encrypt sensitive data such as passwords, but the best defense is to not infect your computer in the first place.
The most likely time for people to upload viruses is when something is in high demand and there isn't a single authoritative high-quality source out yet.
Ultimately you get to decide what you consider an acceptable level of risk. There is no such thing as perfect safety. I would recommend using your own initiative to learn about computer security and not badger random tumblr users to explain it to you, but hopefully the above guidelines should help you avoid doing anything too dangerous.
189 notes
·
View notes
Text
Sonic 1 Mega CD Port


(download here)
(if you think this is cool, consider helping me find work/money <3)
Welcome to the Next Level!
NOTE: I'm aware of issues regarding audio playback and transitioning between zones, and intend to push an update once the contest judging period is over. In the meantime, you can use level select (Up Down Left Right A + Start at title screen) to explore the game.
At the 1992 Consumer Electronics Show, a teaser for a Mega CD version of Sonic 1 was shown within a sizzle reel. No Mega CD version of Sonic 1 was ever produced, and this footage is almost everything we know about this project, but it's extremely likely that this idea is what morphed into the separate game Sonic CD, the only Sonic game officially released for the console.
In 2006, Stealth released the Sonic for MegaCD tech demo, marking the first time any substantial effort was made to bring another Sonic game to the console. It contained the title screens and first levels of Sonic 1 and 2, with three playable characters. In the following years, he would build on the ideas in that demo further, eventually reaching a point where his setup accommodated a Mega CD version of a rom hack called Sonic Megamix.
For a long time, this rom hack was the only way to experience Sonic 1's levels, and was the closest you could get to playing the original game on your Mega CD...
until now.
This is a port of the original Sonic the Hedgehog (revision 1, mostly) to the Sega Mega CD (running in Mode 2/off a CD). Not a mere one-zone demo, not affected by an original hack's mechanics, this is a full playable Sonic game running on the Mega CD, with the source fully available, and with the intent of enhancing the game with the extra hardware.
I started this project about a month and a half ago to enter into the annual Sonic Hacking Contest. This was done as both a learning experience for myself to learn new hardware (I was already familiar with programming for Mega Drive, but wanted to explore its addons), and as an example others can learn from.
This has been tested with BlastEm, Fusion, Gens, and on real hardware using a Mega Everdrive Pro.
Features:
Expanded Sound.
The Mega CD comes with a chip supporting PCM playback for up to 8 channels, complementing the 10 sound channels already in the Mega Drive. This port leverages that by moving playback of drum samples to a custom PCM sound driver running on the Mega CD CPU.
Because drums no longer need to play on the Mega Drive hardware, an extra sound channel was added in the main sound driver to allow for more sound effects to play without cutting out channels of the music.
Unfortunately, I was not able to get CD audio playback fully implemented in time for the initial release. Most of the pieces are there though, and I intend to add it in a future update.
An open-source Mega CD game. The scene for Mega CD has grown significantly over time, and over the years there has been new homebrew and hacks of other games, but not nearly as much done with the blue guy this contest is about. This port aims to change that; this is a full game running on Mega CD, with source code and development history available for browsing right now. Code for the kernel programs to load and run the game from disk is written in mostly C using the megadev toolchain. Rom hackers and developers more familiar with the Mega Drive standalone can use the code repository as an example of how to bring more full-fledged MD projects over to Mega CD with as few changes as possible.
Other features:
Custom loading screen while files are loaded from CD
Modified title screen, to remind you that this is indeed utilizing Mega CD hardware
Various bugfixes applied (for those familiar with Sonic Retro's Sonic 1 disassembly, FixBugs is turned on)
Much smoother special stage. The movement of objects making up the maze was unlocked, and the walls now display with 128 degrees of rotation (up from 16).
Even though I started this project to have something for the contest, I'm incredibly happy with what's been done so far, and I intend to work on it further after the contest to add more features. I consider this the beginning of a goodbright future for Sonic games and hacks on Mega CD.
Note: Debug mode and sound test have not been fixed to accommodate for the code that has been moved around. Try at your own risk!
Credits
Main developer: Amy Farbright
Playtesting and bug reporting: The Let's Talk About Sonic Discord
Special thanks: @fiffle, @milly, @crepe
Code used/referenced:
drojaazu's megadev toolchain
Devon's partial Sonic CD disassembly
SCHG How-to Guide
tversteeg's Rust implementation of rotsprite
Graphics used:
CD graphic on title screen: Sega Multimedia Studio, converted from sprites ripped by Mister Man
35 notes
·
View notes
Text
20250308 Major ALICE update!
For a couple months i've been working on a bunch of new stuff and improvements for Aubery's Logic Integrated Circuit Emulator (ALICE), and yesterday i concluded the works that have been planned! I am very happy to tell everyone that ALICE now crashes much less, the circuit tracing GUI became much more usable, and even more high-level devices were programmed!~
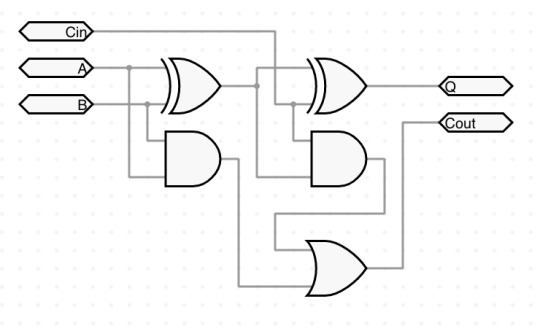
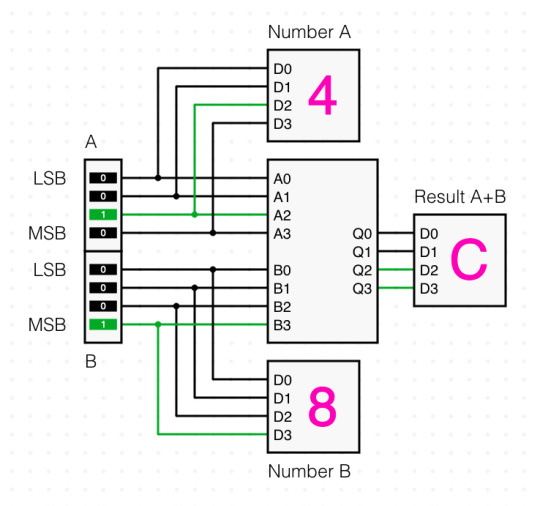
Circuit integration now works in full - watch me go from a basic logic gate based single-bit full adder to a 4-bit adder IC with a whole demo setup to test it, inside the same project!
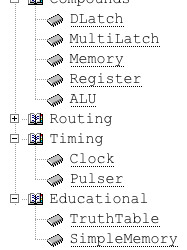
Some high-level devices were added: everything but the ALU seems to be working correctly. TruthTable allows you to build a circuit and then compose its truth table in realtime! Using the pre-made compounds can be easier on the CPU than user-made ICs, even though i'm working on making everything run even faster. Oh, and now there's a "text" device to leave notes right on top of the circuit!
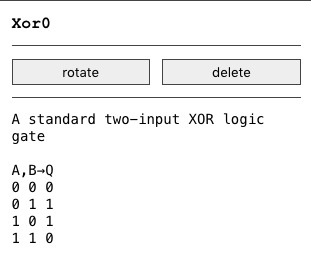
All devices now show a memo on what they do when selected, and a cohesive (although still and forever lacking) manual was started!
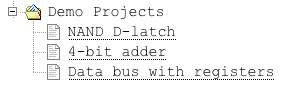
Finally, there are now demo projects! They and the manual are bundled within ALICE itself, so no need to download them separately from anywhere. I will work on adding more to them, with the general goal of one day having a "full basic 8-bit CPU" on the list!
Aside from these novelties, i worked real hard and made the GUI run smoother and explode less. Frankly, the code was pure spaghetti before this overhaul, and now it's at least meatballs with a side of spaghetti. It became better, i promise. Along with this, a bunch of minor bugs were eliminated, and i'm slowly ridding the project from depending on my old bmco.js utility library, which would make it run smoother.
There's a lot of plans for this project, and seeing people using it at all would greatly increase my motivation to implement them. Not like i am not motivated.. but you could make things happen faster! So! Use the thing, tell me when it explodes in your face - with saves and bug error texts preferrably - and show me what you made with it!
And one last thing: ALICE is now hosted on Gitea because i am tired of github's copilot bullshit. I will shut down the github repository soon enough -- nothing to lose, since there are no open issues out there or anything. If you feel like digging through my caverns of nonsense, or run ALICE locally, go ahead and download the source code from the Gitea repo!
13 notes
·
View notes
Text
Because the idea won't leave my brain, I made some more drawings and ideas.

First off - The Seiman/Pentagram features HEAVILY in the nation's technology, most significantly in the Seiman unit - a sort of combination reactor/CPU. Full-scale ones are complex, generally used for large-scale operations like ships. (As a side effect, engineers from this nation generally expect power systems and core computer systems to be in the same room.) Smaller ones are used for things like vehicles or even personal items.
Combat talismans generally feature a Pentagram in the center, with a character in the middle of that determining what element a particular technique will be. The ones you saw on the previous post would be "utility" talismans.
The Kujiin limiter system is specifically for those who utilize their equivalent of the Jade system - specifically, it caps the amount of Ki a user can draw upon to prevent themselves from being exhausted due to expenditure - or worse. Disabling it is an intensive process to prevent arbitrary usage. (And even then, the passphrase and gestures to even turn it off are usually kept secret to make sure some idiot doesn't accidentally kill themselves trying to show off.) Before you ask, yes, it's the whole Rin-Pyo-To-Sha-etc... thing.
(Once again, credit to @kai7kh for putting the idea in my head to begin with)
9 notes
·
View notes
Text





What is there to say about an Amiga 1000 that hasn't been said by people more qualified than I to say it.
This unit is more or less stock although showing no signs of life when I got it. The prior owner fitted a pistorm to it that unfortunately corrupted it's install and will need to be rebuilt but for the time being I have installed the MC68000 CPU in it and it came up immediately.
Here's a tip where my normal troubleshooting method backfired, the A1000 needs it's WOM board installed to do anything so stripping the system down to it's motherboard for testing will only render a brick.
On a successful POST as it is, the system will ask for it's kickstart disk and load from that. Then it asks for the workbench disk. which is the actual OS. Kickstart is the systems extended BIOs and is loaded into the WOM board which is then gated so it can only be read afterwards. Supposedly, once the WOM is loaded, even if the machine crashes, so long as it's reset and not power cycled, you won't need to load kickstart again, I have not tested this at this time.
Surprisingly using workbench is very easy if you are used to OS's like classic MacOS. However unlike the Mac, the disk drive has a mechanical eject button so no dragging anything to the trash can to eject a disk. Right now since I don't have any applications or games for it, I just have a booting machine and not much else.
A quirk of the system, I'm not sure if it's something wrong with my system or it's just how the A1000 behaves, it does not like an empty disk drive, if there's no disk present, it will seek the drive periodically looking for a disk. If a disk is present, it will try to read it and mount the disk on the desktop.
TO DO:
Acquire software and utilities
Get the Pistorm working and reinstalled.
Fix that sad 1084
Upgrades?
Long Term To Do? (Don't hold me to this list at all)
Custom expansion chassis?
37 notes
·
View notes
Text
a lot of people, especially linux people who should know better, have a bizarre idea of how resource usage works. in a perfect dream world you should be at max utilization like all the time! like obviously you do want to keep some spare memory for new processes, but generally speaking unused ram is just a shitload of gates you already paid for that are, you guessed it, unused. it doesn't matter how efficiently you code, if you're dealing with large blobs you can always go faster by cacheing them. chrome will run ok with way less ram, the developers simply chose not to make it slow on purpose for no reason. cpu use is less of an unadulterated W because of power and downclocking but from a pure speed perspective higher cpu usage means you're not twiddling your thumbs waiting for IO to finish. if you want your cpu to idle more just switch your ssd out for a hard drive, see how much faster your machine runs
23 notes
·
View notes
Text


So. I honestly realized I needed a quick detour just to avoid burning out on cryptography. For that reason (and because I have a habit of not wanting to leave UI worked unfinished) I have the TUI set up to my satisfaction for the prototype. With the work over the past day I implemented:
Single key (q) tear down that kills the TUI and the PierMesh service
Full screen (f) toggles whether the PierMesh icon on the left is collapsed, giving a better view of the logs
UI elements to display both the cpu and memory usage at a glance
A good bit of tcss to prettify the UI (mainly surrounding colors and scrollbars)
What I plan on adding/doing:
Node to node messenger utility
Testing on older/weaker systems to make sure it doesn't break regarding color usage
Last I want to point out that this will make dev/testing/debugging significantly easier on my end
20 notes
·
View notes
Text
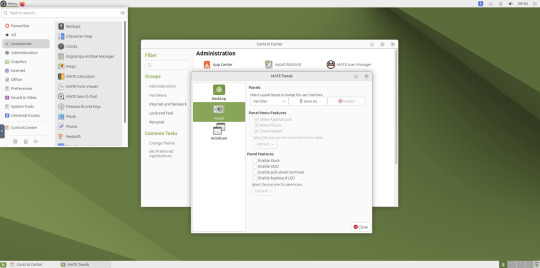
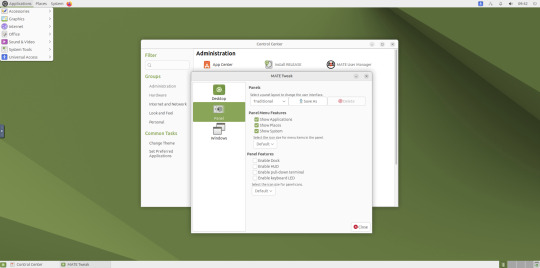
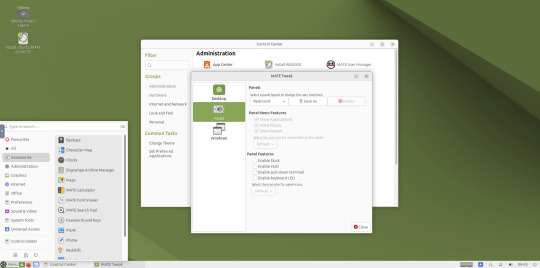
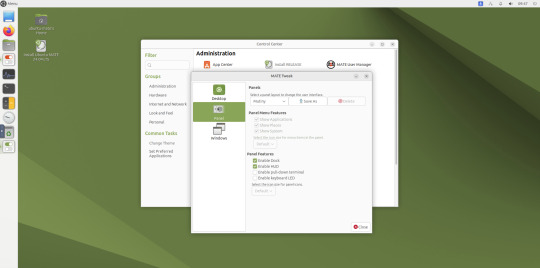
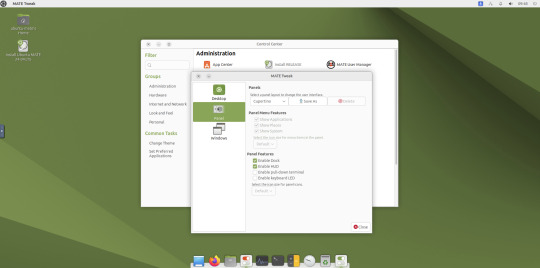
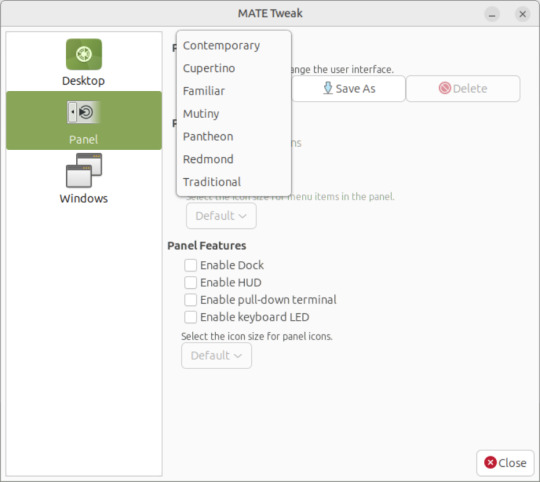
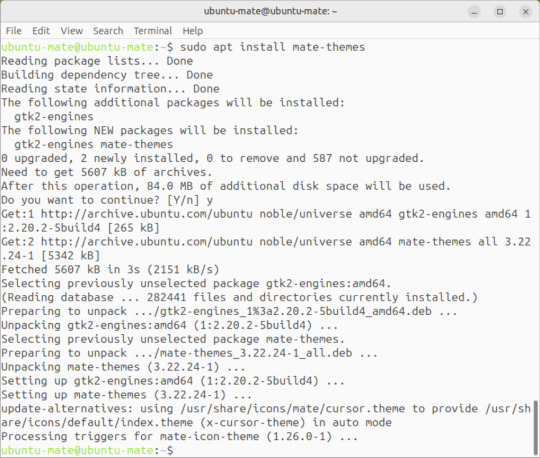
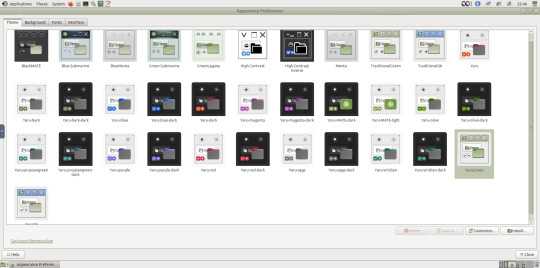
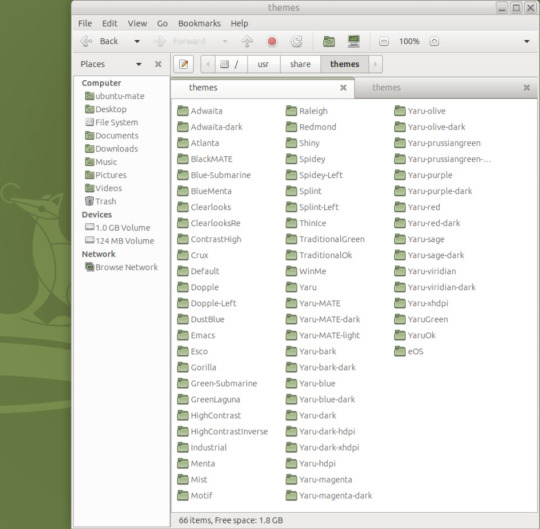
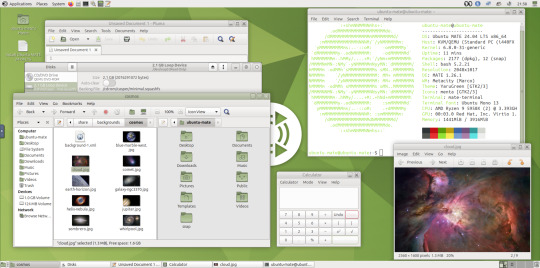
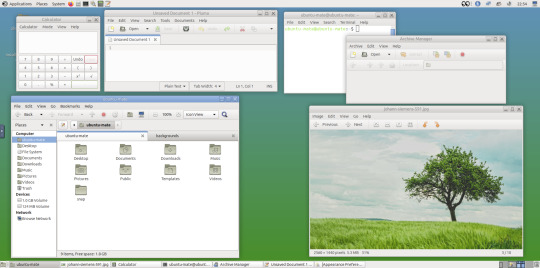
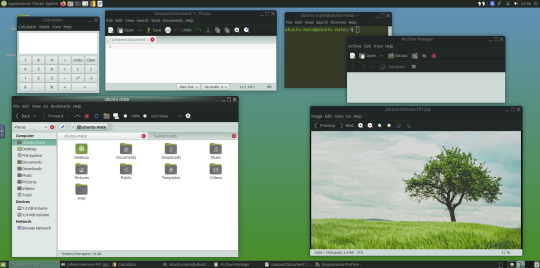
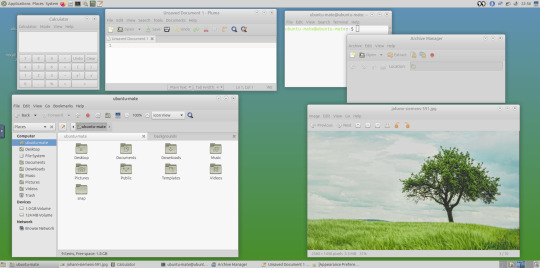
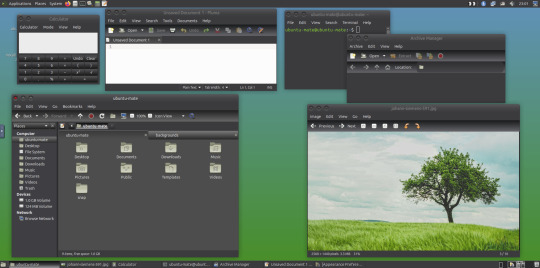

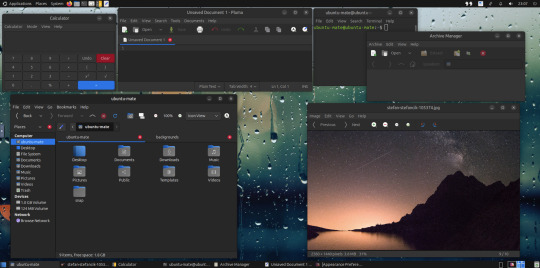
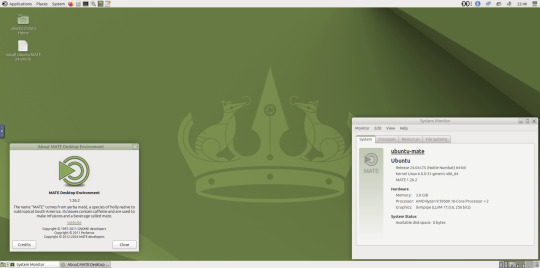

May 2025.
I tried installing a set of themes on Ubuntu MATE 24.04.1 LTS in Distrosea today.
https://distrosea.com/
These themes are provided as a theme package found in vanilla MATE desktops such as Debian and Fedora.
MATE is the modern day continuation of GNOME 2, a very popular, efficient and functional desktop environment from the early 2000s.
The theme pack I selected are compactable GTK3/4 (Graphical Toolkit) versions based on classic GNOME 2 era themes.
Ubuntu MATE website:
https://ubuntu-mate.org/
Debian Linux website:
https://www.debian.org/
Fedora Linux website:
https://fedoraproject.org/spins/mate
See MATE Desktop website here:
https://mate-desktop.org/blog/
About the Graphical Toolkit user interface:
https://en.wikipedia.org/wiki/GTK
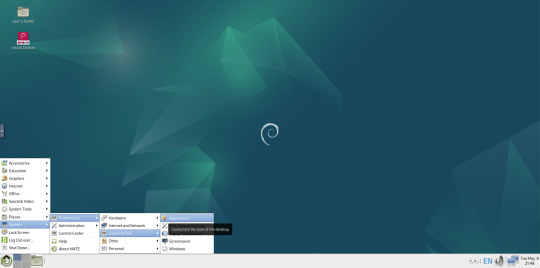
I used the MATE Tweak tool to adjust the panels from the 'familiar' layout to the 'traditional' layout. Here are many of the layouts available.
MATE Tweak can change the panel layout between Traditional (GNOME 2), Unity, Redmond (Windows) contemporary (Mac OS) style.
Here are many of the layouts available.
Afterwards, I used the command line to install the themes with the command: sudo apt install mate-themes.
This command then prompted me to agree the system changes and then it installed the required theme files to the list.
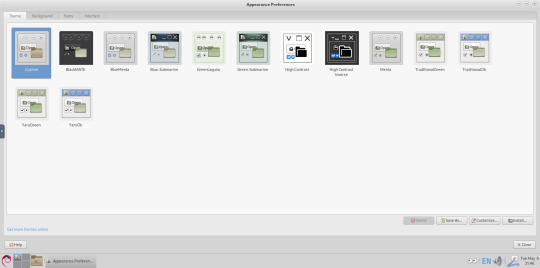
I opened up the theme folder in the Caja file manager. This shows all the ones installed on the system.
Next I opened the appearance preferences and cycled through each theme. There are a total of 12 new themes it added alongside the existing Yaru Colour theme collection for Ubuntu.
This package couldn't be installed graphical so this is why I installed it through the terminal. It is also available to install through the Software Manager on Linux Mint.
The theme package can also be installed on the Cinnamon desktop and other linux distributions.
I like these themes as they provide a more 3D feel and is refreshing to see themes for a desktop environment that hasn't moved towards flat design. It themes all the desktop elements from the windows, panels, drop down menus, CSD apps and widgets.
My favourite one is called YaruOK (blue), as it provides resizable window controls, 3D controls and provides a familiar look to the desktop. The theme is also called TraditionalOK.
This theme is a fork of a GTK2 theme called Clear-looks, which was created by Red Hat developers.
YaruOK is a modern variant that uses GTK3 & 4. The theme is rendered in SVG instead of PNG format which improves HiDpi scaling and features themed client side decorations for header bar windows such as the Disks utility.
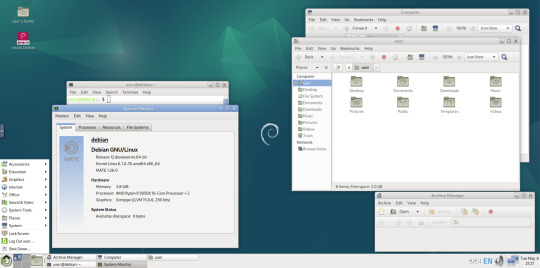
I also added a GNOME Eyes widget onto the panel!
These fun set of eyes follow your mouse cursor around the screen and can help you find the cursor amongst the clutter of windows. It is built to be very lightweight.
I also like the workspace switcher on the bottom left, which allows you to switch between as many desktop workspaces as you want.
The little square windows within each desktop can be clicked on and moved to another workspace.
Like with other desktop environments, you can also right click a window and move it onto another workspace. Each desktop can be named for a assigned task.
A System Monitor widget can also be added to the panels to display CPU, Memory, Swap and Network processes.
There are many other very interesting widget to play around with on the desktop and panels as well!
Here are the MATE themes in Ubuntu Linux 24.04.1, integrating with the Cinnamon desktop.
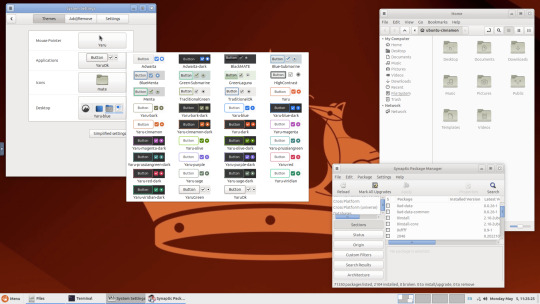
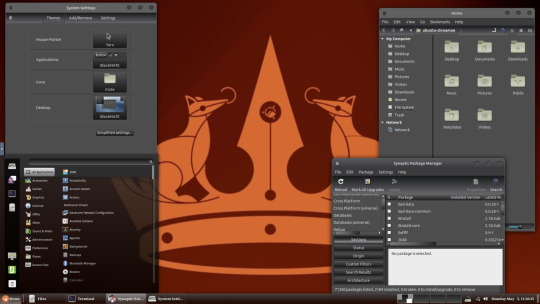
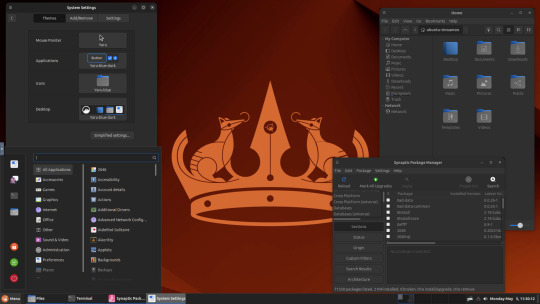
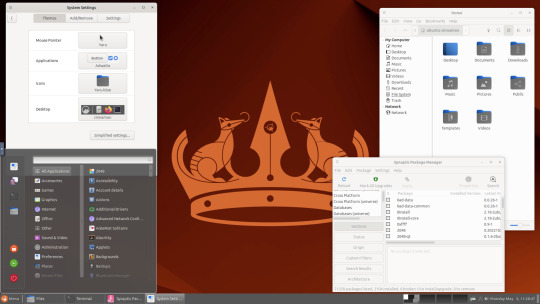
Below are some theming screenshots from Debian MATE 12 Linux.
I've customised the panel, selected the compact menu and changed notification sizes to make it more clearer. The window lists stack onto each other with the increased size.
The MATE panels have adjustable transparency and can be re-coloured and textured very easily through its own preferences box.
See screenshots below!
A very interesting look at the user interface elements found in GNOME 2, MATE and Cinnamon Linux desktop environments!
5 notes
·
View notes
Note
Is it possible for W to utilize the secondary CPU it took on to do crazy multitasking? like can they gameing and cooka da meatball at the same time?
yes.it definitely could
11 notes
·
View notes