#CVE summaries
Explore tagged Tumblr posts
Text
LibTracker Updates 11/25/24: Simplify Dependency Management with this simple SBOM Tool
We are excited to announce the latest updates to *LibTracker*, our VSCode extension designed for professionals to simplify software bill of materials (SBOM) management. With LibTracker, you can effortlessly analyze and manage your apps, ensuring up-to-date versions, addressing security vulnerabilities, and resolving licensing issues—all at a glance.
Access it here: [LibTracker on VSCode Marketplace](https://marketplace.visualstudio.com/items?itemName=windmillcode-publisher-0.lib-tracker)
### New Features in the Latest Release:
- **Grouped Paths**: Added the ability to associate multiple apps with a root folder, easing project transfers between computers.
- **App Detail Page**:
- **Subdependency Information**: View detailed info and license info for subdependencies.
- Toggle between root and subdependency data to explore license and CVE details.
- **Bulk Group Path Update**:
- Recursively searches for app basenames within directories. or the exact subPath. Can specify a recusion level
### Upcoming Features:
- **App Detail Page Enhancements**:
- Integration of CVE details for all subdependencies.
- Search functionality extended to include nested child rows.
- Expand and collapse all subtables within rows for streamlined navigation.
- Responsive design updates to allow a card-based layout for improved usability.
- **Toggle Select All Apps**: Introducing a select-all option on the project detail page.
- **Workspace Folder Management**: Development depends on VSCode API’s ability to support VSCode profiles.
- **SBOM Generation**: Investigating whether to retrieve license and CVE details for every version of each package used in the app.
### Future Milestones (Exploring Feasibility):
- **Git Backup Changes**: Enhancements to streamline version control and backup capabilities.
- **AI-Powered Summaries**: Considering automated generation of license and CVE category summaries.
- **Subdependency Navigation**: Exploring the possibility of linking subdependencies in the license pane to their locations in the dependency table
- **Advanced Table Features** - the current package does not support
- child row search
- expand and collapse all subtables in a given row

- responsiveness (remove columns or using cards at a certain viewport)
#sort functionality#grouped paths#app detail page#subdependency information#license data#CVE information#bulk group path update#recursive path search#project demonstrations#app transfers#app basenames#toggle root dependencies#toggle subdependencies#latest app details#package release dates#changelog URLs#expand subtables#collapse subtables#app detail responsiveness#card layout#SBOM generation#AI summaries#license summaries#CVE summaries#subdependency navigation#project management#VSCode API integration#workspace folder management#Git backup#app updates
0 notes
Text
Zyxel security advisory for authentication bypass and command injection vulnerabilities in NAS products | Zyxel Networks
CVEs: CVE-2023-35137, CVE-2023-35138, CVE-2023-37927, CVE-2023-37928, CVE-2023-4473, CVE-2023-4474 Summary Zyxel has released patches addressing an authentication bypass vulnerability and command injection vulnerabilities in NAS products. Users are advised to install them for optimal protection. What are the vulnerabilities? CVE-2023-35137 An improper authentication vulnerability in the…
View On WordPress
#addressing#CVE202335137#CVE202335138#CVE202337927#CVE202337928#CVE20234473#CVE20234474 Summary Zyxel#CVEs#patches#released
0 notes
Text

Summary of Cybersecurity Alert: Hackers Exploit Logging Errors!
Importance of Logs: Logs are essential for monitoring, maintaining, and troubleshooting IT systems. However, mismanaged or poorly configured logs can expose vulnerabilities to attackers.
Exploitation by Hackers: Cybercriminals target logging systems to inject malicious code, gain unauthorised access, or steal data. Examples include the Log4Shell vulnerability in the Log4j library.
Consequences of Compromised Logs: A compromised logging system can lead to data breaches, business disruptions, financial losses, regulatory fines, and damaged stakeholder trust.
Securing Logging Systems: Businesses should upgrade to advanced log management tools that provide real-time monitoring, anomaly detection, and centralised secure log storage.
Zero Trust Security Model: Adopting a zero trust approach combined with smart logging practices prevents attackers from freely moving within compromised systems and helps detect malicious activities.
Common Hacker Techniques:
Log Deletion: Attackers delete logs to erase evidence, as seen in the 2017 Equifax breach.
Log Alteration: Hackers modify or forge logs to mislead investigators, as in the 2018 SingHealth breach.
Disabling Logs: Disabling logging services to avoid detection, as in the 2020 SolarWinds attack.
Encrypting Logs: Attackers encrypt logs to prevent analysis, as in the NotPetya ransomware attack.
Changing Retention Policies: Altering log retention settings to ensure evidence is purged before investigation, as seen in the 2018 Marriott breach.
Historical Examples: Real-world breaches like Equifax (2017), SingHealth (2018), SolarWinds (2020), and NotPetya (2017) demonstrate the devastating impact of log manipulation.
Protecting Logs:
Store logs securely.
Restrict access to authorised personnel.
Mask sensitive information in logs.
Error Logs as Targets: Hackers analyse error logs to find vulnerabilities and misconfigurations, crafting precise attacks to exploit these weaknesses.
Business Risk Management: Protecting logging systems is not just an IT issue—it’s a critical part of business risk management to prevent dangers.
The Log4Shell Vulnerability
In late 2021, a critical vulnerability known as Log4Shell (CVE-2021-44228) was discovered in Apache Log4j 2, a widely used Java logging library. This vulnerability allowed attackers to execute arbitrary code on affected systems by exploiting how logs were processed. The flaw was particularly dangerous because it was easy to exploit and affected a vast number of applications and services globally.
1. financial losses and safeguard company reputation.
Consequences of Compromised Logging Systems
When attackers exploit vulnerabilities in logging systems, the repercussions can be severe:
Data Breaches: Unauthorised access to sensitive information can lead to data theft and privacy violations.
Business Interruptions: System compromises can cause operational disruptions, affecting service availability and productivity.
Financial Losses: The costs associated with remediation, legal penalties, and loss of business can be substantial.
Reputational Damage: Loss of stakeholder trust and potential regulatory fines can harm a company's reputation and customer relationships.
Real-World Examples of Log Manipulation
Several high-profile incidents illustrate the impact of log manipulation:
Equifax Breach (2017): Attackers exploited a vulnerability in the Apache Struts framework and manipulated system logs to cover their activities.
SingHealth Breach (2018): Attackers used advanced techniques to hide their presence by altering log entries, delaying detection.
SolarWinds Attack (2020): Attackers disabled logging mechanisms and monitoring systems to avoid detection during their intrusion.
NotPetya Ransomware (2017): Attackers encrypted key system files, including logs, to hamper recovery efforts and obscure their actions.
Protecting logging systems is not merely a technical concern but a critical aspect of comprehensive business risk management. By understanding the risks associated with logging vulnerabilities and implementing robust security strategies, organisations can defend against these hidden dangers and safeguard their operations.
1 note
·
View note
Text
youtube
Summary
🛡️ What is Threat Research? Threat research is essential for identifying, understanding, and mitigating evolving cyber threats. It involves gathering, analyzing, and acting on data from diverse sources.
🌐 Key Information Sources:
Vendor Vulnerability Databases: Companies like Microsoft and Cisco provide updates on vulnerabilities specific to their products.
National Vulnerability Database (NVD): Maintained by NIST, it catalogues vulnerabilities using Common Vulnerabilities and Exposures (CVEs).
Conferences and Journals: Provide insights into new vulnerabilities, attack methods, and defensive strategies.
RFCs and Standards: Detail protocols and associated vulnerabilities (e.g., DNS analysis in RFC 3833).
Social Media and Threat Feeds: Real-time updates from trusted sources, such as Twitter honeypot accounts.
🔒 Practical Applications:
Using vulnerability management systems to track and mitigate risks.
Leveraging Tactics, Techniques, and Procedures (TTPs) to understand attacker behaviors and strengthen defenses.
0 notes
Text
This Week in Rust 563
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tag us at @ThisWeekInRust on X (formerly Twitter) or @ThisWeekinRust on mastodon.social, or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub and archives can be viewed at this-week-in-rust.org. If you find any errors in this week's issue, please submit a PR.
Want TWIR in your inbox? Subscribe here.
Updates from Rust Community
Official
Security advisory for the standard library (CVE-2024-43402)
Newsletters
This Month in Rust OSDev: August 2024
This Week In Bevy - Required Components, Curves, and the Bevy CLI Working Group
Project/Tooling Updates
FreeBSD considers Rust in the base system
GCC Rust - August 2024 Monthly report
This month in Servo: tabbed browsing, Windows buffs, devtools, and more!
iroh 0.24.0 - Upgrading to Quinn 11
Swiftide 0.9 - Fluvio, Lancedb and RAGAS support
Next-gen builder macro Bon 2.1 release 🎉. Compilation is faster by 36% 🚀
Nutype 0.5.0: the newtype with guarantees supports custom errors now
BackON Reaches v1
Observations/Thoughts
Defeating Coherence in Rust with Tacit Trait Parameters
Rust On Illumos
Rust for Linux revisited
Async Rust can be a pleasure to work with (without Send + Sync + 'static)
Rust - A low-level echo server using io_uring
Deploying Rust in Existing Firmware Codebases
Your own little memory strategy
Code Generation with GraphQL in Rust
How to deadlock Tokio application in Rust with just a single mutex
Is this trait sealed, or not sealed — that is the question
Beyond Ctrl-C: The dark corners of Unix signal handling
Rust to Assembly: Understanding the Inner Workings of Rust
K-Means Image Compression
Hey Rustaceans: Rust freelancers do exist!
Why Rust needs scoped generics
Rust Walkthroughs
[series] [video] Rust for Beginners in Arabic
[video] Crafting an Interpreter in Rust #01: Basic Bytecode Chunks
[video] Crafting an Interpreter in Rust #02: First Virtual Machine
[video] Explore Linux TTY, process, signals w/ Rust - Part 2/3 (signal, proc, IPC egs)
Miscellaneous
Whither the Apple AGX graphics driver?
Counting iterations - count() vs collect().len()
[audio] Learn Rust, Train Doctors – Interview With Caroline Morton
[video] Creating a modding system with Rust and WebAssembly [Voxel Devlog #21]
[video] From Zero to Async in Embedded Rust
Crate of the Week
This week's crate is vimania-uri-rs, a VIM plugin for file and URI handling.
Thanks to sysid for the self-suggestion!
Please submit your suggestions and votes for next week!
Calls for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization. The following RFCs would benefit from user testing before moving forward:
RFCs
No calls for testing were issued this week.
Rust
No calls for testing were issued this week.
Rustup
No calls for testing were issued this week.
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Call for Participation; projects and speakers
CFP - Projects
Always wanted to contribute to open-source projects but did not know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
If you are a Rust project owner and are looking for contributors, please submit tasks here or through a PR to TWiR or by reaching out on X (formerly Twitter) or Mastodon!
CFP - Events
Are you a new or experienced speaker looking for a place to share something cool? This section highlights events that are being planned and are accepting submissions to join their event as a speaker.
If you are an event organizer hoping to expand the reach of your event, please submit a link to the website through a PR to TWiR or by reaching out on X (formerly Twitter) or Mastodon!
Updates from the Rust Project
416 pull requests were merged in the last week
ABI compat check: detect unadjusted ABI mismatches
rustc_target: Add various aarch64 features
ub_checks intrinsics: fall back to cfg(ub_checks)
add aarch64_unknown_nto_qnx700 target - QNX 7.0 support for aarch64le
add needs-unwind compiletest directive to libtest-thread-limit and replace some Path with path in run-make
add an ability to convert between Span and visit::Location
add missing needs-llvm-components directives for run-make tests that need target-specific codegen
add repr to the allowlist for naked functions
const fn stability checking: also check declared language features
const-eval: do not make UbChecks behavior depend on current crate's flags
coverage: rename CodeRegion to SourceRegion
create opaque definitions in resolver
debug-fmt-detail option
deny wasm_c_abi lint to nudge the last 25%
deny imports of rustc_type_ir::inherent outside of type ir + new trait solver
do not call source_span when not tracking dependencies
don't make statement nonterminals match pattern nonterminals
don't use TyKind in a lint
emit specific message for time<=0.3.35
enable Miri to pass pointers through FFI
exit: explain our expectations for the exit handlers registered in a Rust program
expand NLL MIR dumps
fix LLVM ABI NAME for riscv64imac-unknown-nuttx-elf
get rid of predicates_defined_on
implement a first version of RFC 3525: struct target features
interpret, codegen: tweak some comments and checks regarding Box with custom allocator
interpret/visitor: make memory order iteration slightly more efficient
interpret: add missing alignment check in raw_eq
interpret: do not make const-eval query result depend on tcx.sess
linker: synchronize native library search in rustc and linker
lint that warns when an elided lifetime ends up being a named lifetime (elided_named_lifetimes)
llvm-wrapper: adapt for LLVM API changes
make decoding non-optional LazyArray panic if not set
make it possible to enable const_precise_live_drops per-function
make the "detect-old-time" UI test more representative
make the const-unstable-in-stable error more clear
more unreachable_pub
move 'tcx lifetime off of impl and onto methods for CrateMetadataRef
move the Windows remove_dir_all impl into a module and make it more race resistant
process.rs: remove "Basic usage" text where not useful
re-enable android tests/benches in alloc/core
refactor: standardize duplicate processes in parser
rename BikeshedIntrinsicFrom to TransmuteFrom
replace walk with visit so we dont skip outermost expr kind in def collector
rewrite lint_expectations in a single pass
riscv64imac: allow shadow call stack sanitizer
separate core search logic with search ui
simplify some extern providers
std: move allocators to sys
stop storing a special inner body for the coroutine by-move body for async closures
stop using ty::GenericPredicates for non-predicates_of queries
tweak some attributes to improve panic_immediate_abort
use a reduced recursion limit in the MIR inliner's cycle breaker
use equality when relating formal and expected type in arg checking
use unsafe extern blocks throughout the compiler
wasi: fix sleeping for Duration::MAX
miri: add tokio io test
miri: make TB tree traversal bottom-up
miri: make Tree Borrows Provenance GC compact the tree
miri: support blocking for epoll
apply size optimizations to panic machinery and some cold functions
derive(SmartPointer): assume pointee from the single generic and better error messages
add fmt::Debug to sync::Weak<T, A>
add missing read_buf stub for x86_64-unknown-l4re-uclibc
allow BufReader::peek to be called on unsized types
core: use compare_bytes for more slice element types
fix Pin::set bounds regression
improved checked_isqrt and isqrt methods
partially stabilize feature(new_uninit)
hashbrown: add HashTable::iter_hash, HashTable::iter_hash_mut
cargo: resolve: Report incompatible-with-rustc when MSRV-resolver is disabled
cargo: resolve: Report incompatible packages with precise Rust version
cargo: pkgid: Allow open namespaces in PackageIdSpec's
cargo: fix elided lifetime
rustfmt: implement 2024 expression overflowing
clippy: extend implicit_saturating_sub lint
clippy: new lint: zombie_processes
clippy: remove feature=cargo-clippy argument
rust-analyzer: extra sugar auto-completion async fn ... in impl trait for async fn in trait that's defined in desugar form
rust-analyzer: fix handling of for in impl T for A in function body
rust-analyzer: add explicit enum discriminant assist
rust-analyzer: do not report missing unsafe on addr_of[_mut]!(EXTERN_OR_MUT_STATIC)
rust-analyzer: create an assist to convert closure to freestanding fn
rust-analyzer: implement cast typecheck and diagnostics
rust-analyzer: implement object safety and its hovering hint
rust-analyzer: suggest name in completion for let_stmt and fn_param
rust-analyzer: support fn-ptr and fn-path types for lifetime elision hints
rust-analyzer: fix incorrect symbol definitions in SCIP output
rust-analyzer: std::error::Error is object unsafe
rust-analyzer: consider field attributes when converting from tuple to named struct and the opposite
rust-analyzer: consider indentation in the "Generate impl" and "Generate trait impl" assists
rust-analyzer: don't add reference when it isn't needed for the "Extract variable" assist
rust-analyzer: fix TokenStream::to_string implementation dropping quotation marks
rust-analyzer: fix lifetime elision inlay hints breaking for ranged requests
rust-analyzer: fix name resolution of shadowed builtin macro
rust-analyzer: handle attributes correctly in "Flip comma"
rust-analyzer: lifetime hint panic in non generic defs
rust-analyzer: use Result type aliases in "Wrap return type in Result" assist
rust-analyzer: provide an option to hide deprecated items from completion
rust-analyzer: recategorize config classes
Rust Compiler Performance Triage
This week we had some trouble with our performance bot, but luckily the issue has been resolved. In the end, we saw much more improvements than regressions.
Triage done by @kobzol. Revision range: acb4e8b6..6199b69c
Summary:
(instructions:u) mean range count Regressions ❌ (primary) 0.3% [0.2%, 0.4%] 8 Regressions ❌ (secondary) 0.7% [0.2%, 1.5%] 9 Improvements ✅ (primary) -0.8% [-3.4%, -0.2%] 158 Improvements ✅ (secondary) -0.7% [-2.3%, -0.2%] 96 All ❌✅ (primary) -0.7% [-3.4%, 0.4%] 166
2 Regressions, 3 Improvements, 1 Mixed; 3 of them in rollups 19 artifact comparisons made in total
Full report here
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
Add "crates.io: Crate Deletions" RFC
Merge RFC 3529: Add named path bases to cargo
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
No RFCs entered Final Comment Period this week.
Tracking Issues & PRs
Rust
[disposition: merge] Update catch_unwind doc comments for c_unwind
[disposition: merge] stabilize const_extern_fn
[disposition: merge] stabilize const_float_bits_conv
[disposition: merge] Make destructors on extern "C" frames to be executed
[disposition: merge] Don't warn empty branches unreachable for now
[disposition: merge] Tracking Issue for char::MIN
[disposition: merge] Tracking issue for #![feature(entry_insert)]
Cargo
No Cargo Tracking Issues or PRs entered Final Comment Period this week.
Language Team
No Language Team Tracking Issues or PRs entered Final Comment Period this week.
Language Reference
No Language Reference RFCs entered Final Comment Period this week.
Unsafe Code Guidelines
No Unsafe Code Guideline Tracking Issues or PRs entered Final Comment Period this week.
New and Updated RFCs
[new] [RFC] code name support
[new] Generic Integers V2: It's Time
[new] Simplify lightweight clones, including into closures and async blocks
Upcoming Events
Rusty Events between 2024-09-04 - 2024-10-02 🦀
Virtual
2024-09-04 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - Typestate Pattern in Rust: With a Strict Builder Example
2024-09-05 | Virtual (Buenos Aires, AR) | LambdaClass
Meetup Rust Septiembre [Spanish]
2024-09-05 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2024-09-05 | Virtual (Nürnberg, DE) | Rust Nuremberg
Rust Nürnberg online
2024-09-10 | Virtual (Dallas, TX, US) | Dallas Rust
Second Tuesday
2024-09-10 - 2024-09-13 | Hybrid: Virtual and In-Person (Montreal, QC, CA) | Rust Conf
Rust Conf 2024
2024-09-12 | Virtual (Berlin, DE) | OpenTechSchool Berlin + Rust Berlin
Rust Hack and Learn | Mirror: Rust Hack n Learn Meetup
2024-09-12 | Virtual (Rotterdam, NL) | Bevy Game Development
Bevy Meetup #6
2024-09-16 | Virtual | Women in Rust
👋 Community Catch Up
2024-09-17 | Virtual (Washington, DC, US) | Rust DC
Mid-month Rustful
2024-09-18 | Virtual and In-Person (Vancouver, BC, CA) | Vancouver Rust
Cells
2024-09-18 - 2024-09-20 | Hybrid - Virtual and In-Person (Vienna, AT) | Linux Plumbers Conference
Rust Microconference in LPC 2024
2024-09-19 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2024-09-19 | Virtual and In-Person (Seattle, WA, US) | Seattle Rust User Group
September Meetup
2024-09-24 | Virtual (Dallas, TX, US) | Dallas Rust
Last Tuesday
2024-09-26 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Rusty secure communication on embedded devices
2024-10-02 | Virtual (Vancouver, BC, CA) | Vancouver Postgres
Leveraging a PL/RUST extension to protect sensitive data in PostgreSQL
Africa
2024-09-06 | Kampala, UG | Rust Circle Kampala
Rust Circle Meetup
Asia
2024-09-07 - 2024-09-08 | Shanghai, CN | Rust China
Rust China Conf: Shanghai
2024-09-09 | Ramat Gan, IL | Coralogix
Rust as Scale
2024-09-14 | Bangalore, IN | Rust Bangalore
September 2024 Rustacean meetup
Europe
2024-09-04 | Oxford, UK | Oxfrod Rust Meetup Group
More Rust - Generics, constraints, safety.
2024-09-11 | Reading, UK | Reading Rust Workshop
Reading Rust Meetup
2024-09-17 | Leipzig, DE | Rust - Modern Systems Programming in Leipzig
Topic TBD
2024-09-17 | Trondheim, NO | Rust Trondheim
Making AI-models perform tasks, in Rust!
2024-09-18 | Moravia, CZ | Rust Moravia
Rust Moravia Meetup (September 2024)
2024-09-18 | Vienna, AT + Virtual | Linux Plumbers Conference
Rust Microconference in LPC 2024 (Sep 18-20)
2024-09-21 | Stockholm, SE | Stockholm Rust
Ferris' Fika Forum #5
2024-09-23 | Bratislava, SK | Bratislava Rust Meetup Group
Rust Meetup by Sonalake #6
2024-09-24 | Stockholm, SE | Stockholm Rust
Rust meetup #70
2024-09-26 | Aarhus, DK | Rust Aarhus
Talk Night
2024-09-27 | Mannheim, DE | Hackerstolz e.V.
Hackerstolz Stammtisch Rhein-Neckar
2024-10-02 | Stockholm, SE | Stockholm Rust
Rust Meetup @Funnel
North America
2024-09-05 | Lehi, UT, US | Utah Rust
Shooting Stars: Create a game from scratch in 25 minutes!
2024-09-05 | Mountain View, CA, US | Mountain View Rust Meetup
Rust Meetup at Hacker Dojo
2024-09-05 | Portland, OR, US | PDX Rust
PDX Rust September!
2024-09-05 | St. Louis, MO, US | STL Rust
Lifetimes
2024-09-07 | Longview, TX, US | Longview Code and Coffee
Longview Code and Coffee
2024-09-08 | Cambridge, MA, US | Boston Rust Meetup
Northeastern Rust Lunch, Sep 8
2024-09-10 - 2024-09-13 | Hybrid: Virtual and In-Person (Montreal, QC, CA) | Rust Conf
Rust Conf 2024
2024-09-11 | Boulder, CO, US | Boulder Rust Meetup
Boulder Elixir Meetup
2024-09-16 | Cambridge, MA, US | Boston Rust Meetup
Somerville Union Square Rust Lunch, Sep 16
2024-09-17 | San Francisco, CA, US | San Francisco Rust Study Group
Rust Hacking in Person
2024-09-18 | Virtual and In-Person (Vancouver, BC, CA) | Vancouver Rust
Cells
2024-09-19 | Virtual and In-Person (Seattle, WA, US) | Seattle Rust User Group
September Meetup
2024-09-21 | Longview, TX, US | Longview Code and Coffee
Longview Code and Coffee
2024-09-24 | Detroit, MI, US | Detroit Rust
Rust Community Meetup - Ferndale
2024-09-25 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
I'm pretty sure I'm the only person ever to single handedly write a complex GPU kernel driver that has never had a memory safety kernel panic bug (itself) in production, running on thousands of users' systems for 1.5 years now.
Because I wrote it in Rust.
– Asahi Lina on vt.social
Thanks to Ludwig Stecher for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, andrewpollack, U007D, kolharsam, joelmarcey, mariannegoldin, bennyvasquez.
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
1 note
·
View note
Text
New MOVEit transfer vulnerabilities that require patching (2024) - CyberTalk
New Post has been published on https://thedigitalinsider.com/new-moveit-transfer-vulnerabilities-that-require-patching-2024-cybertalk/
New MOVEit transfer vulnerabilities that require patching (2024) - CyberTalk


EXECUTIVE SUMMARY:
Remember last year’s MOVEit meltdown? Get ready for a reprise…
For anyone who missed last year’s madness, MOVEit Transfer is a popular managed file transfer product sold by Progress Software, which provides business applications and services to more than 100,000 organizations globally.
In 2023, the software code for the MOVEit Transfer product was found to contain multiple vulnerabilities, leading to a rash of ransomware attacks, and data exposure for thousands of organizations.
The level of business exploitation was so severe that it impacted the results of this year’s “Data Breach Investigations Report” (DBIR) from Verizon.
Earlier this month, Progress Software contacted users about two high-severity vulnerabilities, CVE-2024-5805 and CVE-2024-5806. Both are categorized as authentication bypass-style vulnerabilities. Each one has been assigned a 9.1 severity score.
To allow adequate time for patching, the information was under embargo until June 25th. This appears to have been a wise move, as just hours after being made public, at least one vulnerability is seeing active exploit attempts in the wild.
The Shadowserver Foundation has detected exploitation efforts that hone in on honeypot systems, in particular.
The new bugs
“To be clear, these vulnerabilities are not related to the zero-day MOVEit Transfer vulnerability we reported in May 2023,” said a Progress Software spokesperson.
CVE-2024-5806 is an improper authentication vulnerability in MOVEit’s SFTP module, which can potentially lead to authentication bypass in some instances.
Cyber security researchers have noted that this CVE could be weaponized to “impersonate any user on the server.”
CVE-2024-5805 is another SFTP-associated authentication bypass vulnerability, which affects MOVEit Gateway version 2024.0.0.
Action items
As a cyber security leader, have your team check on whether or not your MOVEit Transfer software is up-to-date. Patches are available for all vulnerabilities.
Communicate to your team that these vulnerabilities are a priority, as they have serious business implications. If patching hasn’t yet been completed, emphasize the importance of patching quickly. After patching, confirm successful implementation.
Additional considerations
Reassess your organization’s vulnerability to ransomware attacks. Take a layered approach to cyber security and consider additional cyber security measures. You might want to invest in proactive processes like vulnerability assessments and red teaming. In addition, review and update your incident response plan, as to address potential MOVEit Transfer exploitation attempts. Further information
As compared to the MOVEit Transfer exposure numbers from last year, experts say that the numbers appear similar – the geographies and networks where MOVEit Transfer is observed also mirror those of the 2023 incident.
See CyberTalk.org’s past MOVEit Transfer coverage here. Get more insights into software supply chain vulnerabilities here.
Lastly, to receive cyber security thought leadership articles, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#000#2023#2024#analyses#applications#approach#Articles#authentication#breach#bugs#Business#business applications#code#cyber#cyber attack#cyber security#cyberattack#data#data breach#Foundation#incident#Incident Response#insights#it#leadership#module#MOVEit#MOVEit Transfer#networks#newsletter
0 notes
Text
Google Fixes fifth Chrome Zero-Day of 2024 (CVE-2024-4671)

Chrome zero-day
Google patched a major Chrome security problem. Google corrected this Chrome zero-day vulnerability five times this year, highlighting its ongoing fight against online threats. Here’s a brief summary:
Vulnerability Type: Chrome zero-day (CVE-2024-4671), a “use-after-free” vulnerability in the Visuals component of Chrome (which shows content). Severity: High; may cause browser crashes, code execution, and data leaks. Yes, attackers exploited this vulnerability. Install the latest Chrome browser for safety. Google Chrome usually updates automatically, but you can check settings manually. The latest Chrome zero-day vulnerability This is Google’s fifth 2024 patch. This significant security vulnerability allows an attacker to take control of your browser, run malicious code, or steal data. The vulnerability is in Chrome’s “Visuals” component, which displays content. Google is aware of exploit-based assaults occurring in the wild. To protect yourself, it’s critical that you update Chrome to the most recent version (124.0.6367.201/.202 for Mac and Windows, 124.0.6367.201 for Linux) as soon as you can. Although it isn’t stated clearly in the material I found, the Chrome update that fixed the fifth Chrome zero-day vulnerability this year was released quite recently, according to news reports. May 10, 2024 is the date on which articles addressing the upgrade are dated, suggesting that the release happened on or around that day. Chrome zero-day vulnerability
Indeed, the following is what it know about the fifth zero-day vulnerability in Chrome that Google has patched:
Potential vulnerability: “Use-after-free”. Attackers can exploit software that doesn’t properly free memory.
Component: “Visuals” component in Chrome. This section of Chrome controls how your browser displays material. High severity, with a rating of 8.8 out of 10. This suggests a major vulnerability that might be used for malicious activities.
Exploitation: In the wild, actively exploited. This indicates that before the patch was made available, attackers were already utilizing this vulnerability to conduct attacks.
Status of the Patch: Versions 124.0.6367.201/.202 (Mac & Windows) and 124.0.6367.201 (Linux) of Chrome have been patched.
Suggestions: As soon as you can, update Chrome to the most recent version. Although Chrome usually updates itself, you may manually check for updates by going to Settings > About Chrome. Make sure you follow reliable security news sources to stay informed about upcoming vulnerabilities. Google Chrome zero-day 2024
According to sources, Google fixed Chrome’s fifth zero-day vulnerability this year (2024). What is known as follows:
Frequency: Google has patched this sixth zero-day issue in 2024, demonstrating the continuous fight against such dangers. Severity: Because of its high-severity classification, attackers may be able to use it to steal your data, execute malicious software, or cause your browser to crash. Technical information The “Visuals” component in Chrome, which controls how content is shown on your screen, is specifically flawed. The use of this vulnerability “in the wild” by attackers has been verified by Google prior to the patch. Chrome zero-day most recent version It is essential that you update Chrome to the most recent version for your protection:
124.0.6367.201/.202 for Windows and Mac Linux: 124.0.6367.201 (likely to be updated in the next several days) To manually check for updates, navigate to Settings > About Chrome, even though Chrome updates automatically most of the time. Chrome zero-day vulnerabilities
Chrome zero-day vulnerabilities have been fixed as follows:
CVE-2024-0519: A high-severity out-of-bounds memory access vulnerability in Chrome V8’s JavaScript engine that allows remote attackers to leverage heap corruption through a carefully crafted HTML page to obtain confidential data. High-severity WebAssembly (Wasm) confusion bug CVE-2024-2887. Malicious HTML webpages can launch RCE attacks. Web programmes use the WebCodecs API to encode and decode audio and video, which has a use-after-free vulnerability CVE-2024-2886. Attackers could execute code remotely using specially crafted HTML sites.
High-severity Chrome V8 JavaScript engine out-of-bounds read vulnerability CVE-2024-3159. Remote attackers exploited this vulnerability by carefully designing HTML sites to access data outside the memory buffer. This caused heap corruption, which may steal confidential data.
Pwn2Own, Google fixes another Chrome zero-day Another Chrome zero-day vulnerability from last month’s Pwn2Own hacking competition been updated by Google.
CVE-2024-3159 is a high-severity security vulnerability caused by Chrome V8 JavaScript engine out-of-bounds read. Remote attackers can exploit this vulnerability by using specially built HTML sites to access data beyond the memory buffer using heap corruption. They may gain access to confidential data or crash. On the second day of Pwn2Own Vancouver 2024, security researchers Edouard Bochin and Tao Yan from Palo Alto Networks demonstrated how to circumvent V8 hardening using a zero-day exploit. They were awarded $42,500 for their double-tap attack, which gave them the ability to run arbitrary code on Microsoft Edge and Google Chrome.
Chrome zero-days exploited at Pwn2Own Vancouver 2024 With Google Chrome stable channel version 123.0.6312.105/.106/.107 (Windows and Mac) and 123.0.6312.105 (Linux), the zero-day has finally been solved. This version will be released globally in the next days.
Two more Chrome zero-day that were exploited at Pwn2Own Vancouver 2024 were resolved by Google. A double-tap RCE exploit by Manfred Paul targeted the first, a high-severity type confusion vulnerability (CVE-2024-2887) in the Reassembly (Wasm) open standard, affecting both Chrome and Edge.
Seunghyun Lee of the KAIST Hacking Lab additionally used the second, a use-after-free (UAF) vulnerability in the WebCodecs API (CVE-2024-2886), to obtain remote code execution on both Chromium web browsers.
On the same day that the bugs were exploited, Mozilla also patched two Firefox zero-days that Manfred Paul had used at this year’s Pwn2Own Vancouver competition.
While companies often take their time fixing Pwn2Own zero-days, as Trend Micro’s Zero Day Initiative publicly exposes bug details after 90 days, Google and Mozilla both delivered security patches within a week.
Four Chrome zero-days have been patched by Google this year; the fourth was fixed in January as an actively exploited zero-day (CVE-2024-0519) that allowed attackers to access sensitive data or crash unpatched browsers by taking advantage of an out-of-bounds memory access vulnerability in the V8 JavaScript engine.
Additionally, the business patched two Android zero-days on Tuesday that were being used by forensic companies to unlock Pixel phones without a PIN and retrieve the data they contained.
Read more on Govindhtech.com
#google#chrome#chromezeroday#zerodayvulnerability#android#pixelphone#technology#technews#news#govindhtech
0 notes
Text
Malicious SSH backdoor sneaks into xz, Linux world's data compression library [ Fedora Linux ]
Malicious SSH backdoor sneaks into xz, Linux world’s data compression library [News Summary] Red Hat on Friday warned that a malicious backdoor found in the widely used data compression software library xz may be present in instances… Malicious code planted in xz Utils has been circulating for more than a month. The malicious code (which is being tracked as CVE-2024-3094) is embedded in XZ Utils…

View On WordPress
0 notes
Text
Advanced Notice from Atlassian: RCE Vulnerabilities Identified in Multiple Products

On December 6, 2023, at 12 AM EST / 5 AM UTC, a Critical severity security advisory will be publicly announced for multiple Atlassian products. Atlassian has discovered four critical vulnerabilities with a severity score of 9.0 or higher, demanding immediate action to safeguard your instances.
Affected Products and Vulnerabilities: CVE-2022-1471 - SnakeYAML library RCE Vulnerability Impacts Multiple Products Automation for Jira (A4J) app (including Server Lite edition) Bitbucket Data Center and Server Confluence Cloud Migration App (CCMA) Confluence Data Center and Server Jira Core Data Center and Server Jira Service Management Data Center and Server Jira Software Data Center and Server Affected Versions + Mitigation (Updated on December 5 16:50 EST)
CVE-2023-22522 - RCE Vulnerability in Confluence Data Center and Server Confluence Data Center and Server Affected Versions + Mitigation
CVE-2023-22524 - RCE Vulnerability in Atlassian Companion App for MacOS Confluence Data Center and Server (former and present customers) Affected Versions + Mitigation
CVE-2023-22523 - RCE Vulnerability in Assets Discovery (stand-alone app) Jira Service Management Cloud Jira Service Management Data Center and Server Affected Versions + Mitigation
Atlassian found these vulnerabilities during a routine security review, and while there's no evidence of exploitation, taking proactive measures is crucial to protect your data.
Please plan and act promptly upon this information, but remember, it is embargoed until the public release on December 6, 2023. Once released, follow the Critical Advisory for updates and mitigation instructions. Your security matters to Atlassian and to us. For more details you can visit: Partner Portal blog.
Quick Summary:
We, at Amrut Software, want to inform you about a crucial security update that affects Atlassian products. As a platinum partner of Atlassian, your security is our priority, and we're sharing this early notice to ensure your systems remain secure.
For more details visit : amrutsoftware.com / amrutsoftware.ae
Contact no : +91 22 48971025 | +91 22 67391900 | +91 22 67391901 | +91 22 67391902
0 notes
Text
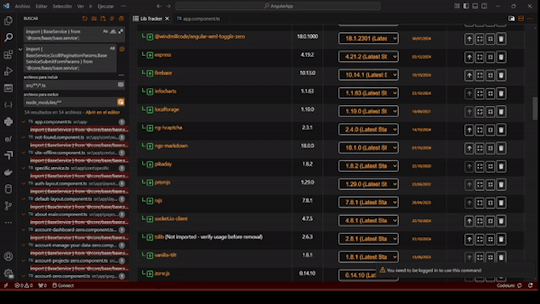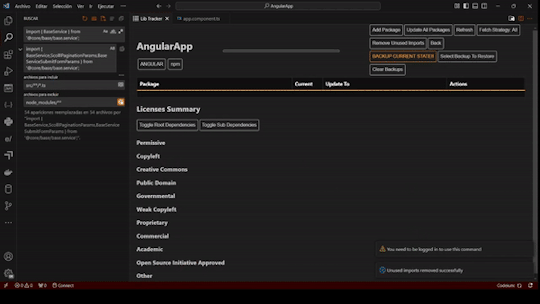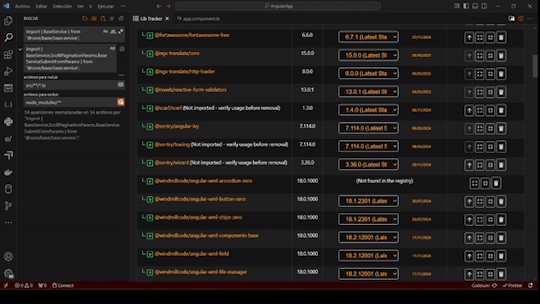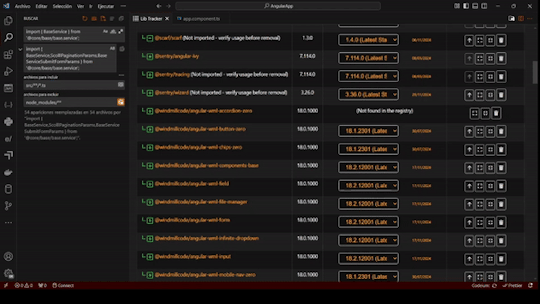
LibTracker Updates 12/16/24: Simplifying Dependency Management for Developers
Managing dependencies is one of the most critical aspects of modern software development. With LibTracker, our VSCode extension, we’re empowering developers to maintain up-to-date, secure, and compliant applications effortlessly.
View your app's dependencies at a glance, identify outdated versions, fix security vulnerabilities, and address problematic licensing—all in one streamlined tool.
Access LibTracker here: [Visual Studio Marketplace](https://marketplace.visualstudio.com/items?itemName=windmillcode-publisher-0.lib-tracker)
New Features:
- Dependency Insights: Now see the latest available version and the recommended stable version for each dependency. The stable version aligns with your package manager's suggestions, helping you make safe updates without risking app stability.
- Enhanced Usability: Added action icons with tooltips for a more intuitive experience.
- Unused Code Detection: Identify unused packages and imports with ease.
- Edge Case Handling: Improved handling for non-registry packages, ensuring you receive as much information as possible.
Upcoming Enhancements:
- Progress Indicators: Visualize progress for checks like outdated versions, unused dependencies, and pre-fetch operations.
- Collapsible Action Icons: Streamline the interface by collapsing less frequently used tools.
- Advanced Filters: Add glob or regex-based ignore patterns for app subpath searches.
- Git-Based Backups: Explore using Git instead of the filesystem for enhanced backup reliability.
- App Detail Page Improvements:
- Display CVE information.
- Advanced search functionality.
- Responsive design with card-based layouts for better readability.
Future Goals:
- SBOM Generation: Automatically create a comprehensive Software Bill of Materials for your projects.
- License and CVE Summaries: Summarize key insights using URLs or AI-generated categories.
- Subdependency Insights: Enable direct navigation to subdependencies within the license pane.
At Windmillcode, we are committed to helping developers build secure, efficient, and scalable applications. Stay tuned for continuous updates, and let us know how we can further improve LibTracker to meet your needs.
#libtracker#vscodeextension#dependencymanagement#cvescanning#softwarebillofmaterials#sbom#securityvulnerabilities#performanceoptimization#gitintegration#licensecompliance#CVE
0 notes
Text
Russian Foreign Intelligence Service (SVR) Exploiting JetBrains TeamCity CVE Globally | CISA
SUMMARY The U.S. Federal Bureau of Investigation (FBI), U.S. Cybersecurity & Infrastructure Security Agency (CISA), U.S. National Security Agency (NSA), Polish Military Counterintelligence Service (SKW), CERT Polska (CERT.PL), and the UK’s National Cyber Security Centre (NCSC) assess Russian Foreign Intelligence Service (SVR) cyber actors—also known as Advanced Persistent Threat 29 (APT 29), the…
View On WordPress
#Agency#Bureau#CISA#Cybersecurity#federal#infrastructure#Investigation#national#security#SUMMARY The
0 notes
Text
Report on Surprise hyper CVE from 2023-04-11
Meta
This document is meant to help publicize the learnings from a recent emergency in hyper. Documents like these are common within various organizations. Some call them "postmortems", others say "incident reports". I quite like what Amazon calls them, since it aptly describes the purpose: Correction of Error. There was an error that caused an emergency, and we want to correct that error.
Summary
A surprise CVE publicly filed for hyper on April 11, 2023 caused an emergency situation for several collaborators, and sent out dependabot warnings with no actionable advice. By day's end, we identified a best-guess at what the cause of the low-severity vulnerability was. By the next morning, a fix was available.
That the issue should have been a CVE is uncertain.
The bigger concern is the way the CVE was filed bypassing the existing security policy. That is similar to finding a lighter in a school, and pulling the fire alarm. This COE discusses both why it may have happened, and how we can try to reduce future occurrences.
The impact
The RustSec1 advisory explains the issue this way:
If an attacker is able to flood the network with pairs of HEADERS/RST_STREAM frames, such that the h2 application is not able to accept them faster than the bytes are received, the pending accept queue can grow in memory usage. Being able to do this consistently can result in excessive memory use, and eventually trigger Out Of Memory.
In reality, being able to consistently accomplish those conditions would be very difficult for an attack, and so the likelihood of this affecting anyone is minimal. Certainly low severity.
But the bigger impact was not this particular issue, but rather that a CVE caused a sudden panic for the maintainers and for users as dependabot alerted people with nothing that they could do.
The story
The original issue was filed on May 27, 2022. Trying to better understand, I asked some poorly worded follow-up questions. Another contributor filed a pull request trying to fix the underlying issue. Several collaborators reviewed that PR, but didn't fully grasp what it was trying to fix. It then fell into the void.
On April 11, 2023, someone decided to file a public CVE for the described issue, without following the security policy. I commented on the issue that while the motivation for doing so was likely good-intentioned, it was the wrong way to go about it. GitHub imported the report, which started triggering dependabot warnings.2 This surprised us, and at least four people dropped everything to handle the fire alarm.3
The first step was trying to determine a reproducible example. We didn't notice at the time it was filed, but the original issue did not include full reproducible instructions. We tried to create some unit tests to mimic the behavior described, but couldn't trigger the issue.
Eventually, we noticed that a modified test that stopped "accepting" requests from the connection, but still polled it, would cause the accept queue to grow. But hyper makes sure to have a task that is always accepting requests, unless you specifically ask it to stop. Thus, the modified test seemed like user error, but it was a just guess.
It just seemed too convuluted. Then we arrived at a much better guess.
We finally found a way to grow the accept queue even when continuously accepting, by creating a test to blast thousands of requests in a loop. Since h2s test suite uses in-memory IO streams, we are able to fill the read buffer to near infinity. That's when we settled on our best guess: if someone can fill the socket's read buffer faster than the server can pop requests, then the accept queue could grow unbounded. While there is a setting to limit concurrent requests, because these are immediately reset, the limit would never be checked.
After 14 hours, we had a fix written and reviewed. We determined that the issue was low severity, as the likelihood of being able to consistently attack was extremely low. And since we were adding a new limit, there was a possiblity of causing a new bug. So, better to not push something right before going to sleep.
The following morning we published the fix, as h2 v0.3.17. Surprising everyone who has rushed out new code, a new bug in it was indeed found. We then published v0.3.18.4
Five whys5
Why did someone file a CVE suddenly? We don't know for sure, but we can guess.6 A related issue had been open for a year, not fixed, so perhaps the reporter thought this was the only way to move forward.
Why wasn't the issue acted upon a year ago? When it was initially opened, the maintainers didn't fully understand what the problem was. Follow-up questions were asked, but even our questions weren't that clear. Eventually, we forgot about it.
Why was it forgotten? We didn't have any recurring reason to check back and try to understand what the issue was. If it had been reported privately to the security address, it would have stayed high priority until it was solved or determined incorrect.
Why wasn't the initial issue reported privately? Perhaps the original reporter didn't know about the policy.
What we're doing to prevent a next time
We can't completely control someone randomly filing a new CVE and causing another fire drill. But there are other things we can improve at to reduce the likelihood of one.
Schedule routine triage. This could be a synchronous meeting, such as in a text channel, or an audio channel. Or maybe over Twitch. But it can also just be a thing that triagers agree to do asynchronously, with a brief routine report to make sure we actually do it.
⚠️ If you or your company uses hyper, this would be an especially useful way to help with maintenance. Have an engineer or two dedicate a few hours each month helping us triage.
Setup a bug report checklist. There is a triage guide for bug reports, which is a good thing. But that doesn't mean everyone (me included!) always remembers all the steps. Checklists are famous in aviation and medicine for their effectiveness in saving lives. They can also help us make sure all issues are treated properly.
Update the issue templates to use forms instead. We do have an issue template in place, to try to get people to fill in more information initially. But it's pretty easy to skip it. It's possible using GitHub's new forms instead of just a text template could guide people more often.
RustSec and the CVE database are different. RustSec was much more helpful, coordinating with us by waiting until the emergency panic was over, and then discussing the best way to describe the advisory. ↩︎
I updated the advisory on GitHub's end to only indicate h2, not hyper. I also indicated my disappointment in GitHub's amplifying of the alarm and making the day much more stressful. Their reply: "We do that sometimes XD". Cool. ↩︎
Meanwhile, a reddit thread took off, watching the action, commenting, and mostly criticizing the actions of all involved. Thankfully, I didn't read comments like "I don't have any sympathy for the maintainers" until after the fix was completed. ↩︎
"At least this made you fix it, right?" No. This attitude is toxic. Doing it this way burns out everyone around who could fix it. There is a reporting process for a reason. It helps the most amount of people. Please use it. ↩︎
Not literally five questions, but an exercise to try to find the root cause, and to note any extra things that could be fixed along the way. ↩︎
Some people tried to infer bad motives, such as for clout or "another notch on a security researchers belt". I see no reason to assume that with no evidence. ↩︎
5 notes
·
View notes
Text
I'm old enough to remember it was a conspiracy theory when Trump said so.
Now the government admits how vulnerable the system is.
2.2 VULNERABILITY OVERVIEW
NOTE: Mitigations to reduce the risk of exploitation of these vulnerabilities can be found in Section 3 of this document.
2.2.1 IMPROPER VERIFICATION OF CRYPTOGRAPHIC SIGNATURE CWE-347
The tested version of ImageCast X does not validate application signatures to a trusted root certificate. Use of a trusted root certificate ensures software installed on a device is traceable to, or verifiable against, a cryptographic key provided by the manufacturer to detect tampering. An attacker could leverage this vulnerability to install malicious code, which could also be spread to other vulnerable ImageCast X devices via removable media.
CVE-2022-1739 has been assigned to this vulnerability.
2.2.2 MUTABLE ATTESTATION OR MEASUREMENT REPORTING DATA CWE-1283
The tested version of ImageCast X’s on-screen application hash display feature, audit log export, and application export functionality rely on self-attestation mechanisms. An attacker could leverage this vulnerability to disguise malicious applications on a device.
CVE-2022-1740 has been assigned to this vulnerability.
2.2.3 HIDDEN FUNCTIONALITY CWE-912
The tested version of ImageCast X has a Terminal Emulator application which could be leveraged by an attacker to gain elevated privileges on a device and/or install malicious code.
CVE-2022-1741 has been assigned to this vulnerability.
2.2.4 IMPROPER PROTECTION OF ALTERNATE PATH CWE-424
The tested version of ImageCast X allows for rebooting into Android Safe Mode, which allows an attacker to directly access the operating system. An attacker could leverage this vulnerability to escalate privileges on a device and/or install malicious code.
CVE-2022-1742 has been assigned to this vulnerability.
2.2.5 PATH TRAVERSAL: '../FILEDIR' CWE-24
The tested version of ImageCast X can be manipulated to cause arbitrary code execution by specially crafted election definition files. An attacker could leverage this vulnerability to spread malicious code to ImageCast X devices from the EMS.
CVE-2022-1743 has been assigned to this vulnerability.
2.2.6 EXECUTION WITH UNNECESSARY PRIVILEGES CWE-250
Applications on the tested version of ImageCast X can execute code with elevated privileges by exploiting a system level service. An attacker could leverage this vulnerability to escalate privileges on a device and/or install malicious code.
CVE-2022-1744 has been assigned to this vulnerability.
2.2.7 AUTHENTICATION BYPASS BY SPOOFING CWE-290
The authentication mechanism used by technicians on the tested version of ImageCast X is susceptible to forgery. An attacker with physical access may use this to gain administrative privileges on a device and install malicious code or perform arbitrary administrative actions.
CVE-2022-1745 has been assigned to this vulnerability.
2.2.8 INCORRECT PRIVILEGE ASSIGNMENT CWE-266
The authentication mechanism used by poll workers to administer voting using the tested version of ImageCast X can expose cryptographic secrets used to protect election information. An attacker could leverage this vulnerability to gain access to sensitive information and perform privileged actions, potentially affecting other election equipment.
CVE-2022-1746 has been assigned to this vulnerability.
2.2.9 ORIGIN VALIDATION ERROR CWE-346
The authentication mechanism used by voters to activate a voting session on the tested version of ImageCast X is susceptible to forgery. An attacker could leverage this vulnerability to print an arbitrary number of ballots without authorization.
CVE-2022-1747 has been assigned to this vulnerability.
2.3 BACKGROUND
CRITICAL INFRASTRUCTURE SECTORS Government Facilities / Election Infrastructure
COUNTRIES/AREAS DEPLOYED: Multiple
COMPANY HEADQUARTERS LOCATION: Denver, Colorado
2.4 RESEARCHER
J. Alex Halderman, University of Michigan, and Drew Springall, Auburn University, reported these vulnerabilities to CISA.
3. MITIGATIONS
CISA recommends election officials continue to take and further enhance defensive measures to reduce the risk of exploitation of these vulnerabilities. Specifically, for each election, election officials should:
Contact Dominion Voting Systems to determine which software and/or firmware updates need to be applied. Dominion Voting Systems reports to CISA that the above vulnerabilities have been addressed in subsequent software versions.
Ensure all affected devices are physically protected before, during, and after voting.
Ensure compliance with chain of custody procedures throughout the election cycle.
Ensure that ImageCast X and the Election Management System (EMS) are not connected to any external (i.e., Internet accessible) networks.
Ensure carefully selected protective and detective physical security measures (for example, locks and tamper-evident seals) are implemented on all affected devices, including on connected devices such as printers and connecting cables.
Close any background application windows on each ImageCast X device.
Use read-only media to update software or install files onto ImageCast X devices.
Use separate, unique passcodes for each poll worker card.
Ensure all ImageCast X devices are subjected to rigorous pre- and post-election testing.
Disable the “Unify Tabulator Security Keys” feature on the election management system and ensure new cryptographic keys are used for each election.
As recommended by Dominion Voting Systems, use the supplemental method to validate hashes on applications, audit log exports, and application exports.
Encourage voters to verify the human-readable votes on printout.
Conduct rigorous post-election tabulation audits of the human-readable portions of physical ballots and paper records, to include reviewing ballot chain of custody and conducting voter/ballot reconciliation procedures. These activities are especially crucial to detect attacks where the listed vulnerabilities are exploited such that a barcode is manipulated to be tabulated inconsistently with the human-readable portion of the paper ballot. (NOTE: If states and jurisdictions so choose, the ImageCast X provides the configuration option to produce ballots that do not print barcodes for tabulation.)
Contact Information
For any questions related to this report, please contact the CISA at:
Wow, this is really screwed up, and nobody knows about it. Let's shine a light on this critical topic.
Why doesn't congress know about this? Let's tag MTG, Jim Jordan, and Matt Gaetz?
Thank you, Anon!
Love, JD 😜💋
#Anon#matt gaetz#MTG#Jim Jordan#Marco Rubio#Dominion voting systems#trump#voting scam#illegal elections#2000 mules#dinesh d'souza#Fox News
17 notes
·
View notes
Note
Last week you mentioned GPG has really serious problems. Could you tell me more about them? I can't find much of anything online.
first, thanks for your patience with this appallingly late reply! september hit me like a truck :P
second: huh, wow, okay, a cursory google search really failed to turn up much stuff, huh. depressing!
i'm-a talk about the summer 2019 keyserver attack, not because that's the only issue / security vuln / fuck-up the project has ever had, but because it's (1) a hilariously bad fuck-up, and (2) generally reflective of how the project deals with security concerns, and thus demonstrates that the project is fundamentally pretty unserious
so.
this gist, by one of GnuPG's maintainers, does an okay job of summarizing the problem. a brief summary:
* one of the putative purposes of OpenPGP is to provide a "web of trust" via keyservers. i know Jane Doe, i meet her in person, i verify she is who she says she is, and i sign her key; that signature gets reflected in some keyserver, which acts like a big phone book. now, in the future, if you can't personally go verify Jane Doe's trustworthiness, but you do trust me, you can trust communications from Jane Doe, and you looked all this info up in the keyserver
* "what if a malicious actor tried to overload the keyserver?!?!" e.g. what if i spam ~150k signatures on some dude's key just to fuck with the network
* the answer, in the case of GnuPG, is, "this software is shitty and bad and can't deal with that volume so it just grinds to a fucking halt"
* ...and also most the keyservers try to copy their data from each other so you can have a ~web of trust~ throughout the network, which means, these malicious keys quickly perpetuate through the entire nnetwork
* which means anyone who receives the Forbidden Key Data TM, in practical terms, has broken their fucking GnuPG install, and that whole ~web of trust~ thing we built up is now unusable
technically speaking, this is not a security lapse per se! no cryptography has been broken; no secret data has been leaked. it is, however, a fairly straightforward denial of service attack, and is probably kind of disappointing if you wanted your security software to, you know, do software things
and look, anyone can be bitten by a nasty bug. you'll never see me being like "WOW WHAT DUMBFUCKS, HOW COULD ANYONE WRITE SUCH A STUPID BUG," because, y'know, there but for the grace of god i go, and all that. if anyone tells you they're smart enough to never write a bug, they're a fucking liar. (my full-time job for a while was literally proving those people liars, and i never fucking failed, not because i am brilliant, but because all have sinned and fallen short of the glory of god. [sorry for all the god stuff; my long-abandoned southern baptist heritage comes through when i'm talking security for some reason])
however! the manner in which you respond to such a vulnerability matters:
* let's say i had discovered this bug in GnuPG. the industry standard, if i'm kind and polite, is: i disclose the bug privately to the maintainers, and they have a 90-day window during which to fix it. if they still haven't fixed the problem at the end of the 90 days, that's fine, that's their prerogative, but *i* also get to announce to the world "hey there's this bad bug, here's how i found it, and here's how to exploit it."
this is done to keep The World In General TM safer. see, i'm just some rando. if *i'm* able to find a bug in your shitty software, then it's guaranteed the NSA or Unit 8200 or some-other-super-secret-government-agency absolutely has the resources and wherewithal to find the same bug. and also, some slimy just-in-it-for-the-money hacker gang probably also has the resources to find it. by telling the company "hey, i will go public with this in 90 days," i'm lighting a fire under their ass to actually fix the problem, rather than just letting them pretend security by obscurity will save them, and if they don't fix it by then, then at least users have a prayer of finding out, hey, these dudes do not take security problems seriously, and making informed choices based on that.
there is some wiggle room in this. for instance, the fuck are cloud vendors supposed to do about something like Spectre/Meltdown? there were some shitty, not-100%-effective mitigations that could be done in software, but fundamentally the only real fix was getting new hardware, and tragically, we cannot redesign, manufacture, and ship brand new CPUs to everybody who might be affected within a 90-day timeframe. ergo, Google Project Zero pushed their disclosure deadline way out on that. but, crucially: they still went public at some point, and Intel did not cry "wah" or "no fair" or anything like that. they worked with researchers as best as they could, and once the cat was out of the bag, they offered public resources to help developers understand how their software might be affected. that's the rules of the game.
compare this to, uh, GnuPG's outrageously shitty response (from the previously-linked gist), which can basically be summarized as:
* "wah ocaml is complicated and we don't know how to maintain our own fucking software wah"
* "ten years [?!?!?!] wasn't enough time for us to fix the problem wah"
* "whoever did this attack is a hater :((((("
which. what. what the actual fuck. those are not actual reasons to not fix your sofwtare.
also, the way in which you present your software matters:
* i've thrown up shitty hobby projects on github before. if someone came to me all earnest with a CVE against them, i'd laugh, append the README to say "yo i threw this together on a weekend while i was buzzed, you should absolutely not be relying on this for anything that matters, xoxo lua." that is 100% fine! advertising THIS SOFTWARE IS NOT NECESSARILY SECURE and thus electing not to give a shit about security problems is fine.
* i've been a part of things that are... somewhere between a hobby project and Real Software TM. e.g., research prototypes that you're hoping will be widely used so you can get a better sense of desired use cases and unexpected constraints, but which you hope will be used primarily by "power users" or others who are interested in that project's specific goals.
such a project may not be able to offer the same kinds of security guarantees as Fancy Corporate Software, and that's fine, so long as they're open and honest about stuff like: what the goals of the project are, what we're sure of and what we're less sure of, how we're vetting our stuff, what our policies are when someone does report a security issue, stuff like that. there's plenty of stuff maintained on a volunteer basis that i'd generally trust because, i expect they'll notify me if there is a serious security concern to be worried about, or they have a long track record of excellence in a narrowly-tailored space, etc. that's all good.
* what you cannot, cannot, cannot do, is: claim to offer some kind of robust security solution to people in actually-precarious situations, and then not actually act like a steward of those person's interests. if you're, oh, telling Venezeulan dissidents "our [shitty hobby] software [with gaping, well-known vulnerabilities that haven't been exploited yet ONLY because no major nation-state entity has felt threatened by our code yet, but if they were so threatened, they could trivially wreck the entire project using a well-documented years-old vulnerability we can't be assed to fix because ocaml is hard i guess] is safe and reliable to use!"
...if you're telling political dissidents that? and then you get over-the-top pissed off at someone pointing out the fucking problem you refuse to fix? and somehow make it all about mememe? then fuck you, sincerely. the threat those dissidents face is not someone breaking the fucking key network. the threat is you, you personally, because you are fucking lying to them about what your software is able to do.
GOD. sorry, just. i reread that link and got so pissed again. fuck that attitude entirely. if you let people down, fucking just sit with that for a bit, okay? sit and think and do better next time. christ.
anyway.
this is a particularly gratuitous example of GnuPG maintainers being little shits, but in general they've been lackadaisical and dismissive some other times in the past when people have brought them real security problems, and then act all pissy if, y'know, people go public with said security problems. i haven't kept up with their work lately (i think maybe the community got kind of annihilated by this keyserver thing?) & i have other bones to pick with any project of that type (it's kind of taking the wrong tack entirely imho), but like, yeah, in general if a software community's response to security bugs is "oh gosh that's hard maybe we'll get to it someday," you should not be trusting that software lol
#filthy hacker shit#LONG post#honestly it took me like three times to keep this from spiraling into a fucking novel so#here's the shortest version i could manage.#hit me up for pissy computer security rants: if you really want to know#also this tone is like... probably more pissy than necessary sorry#there is some more nuance that could be had here but i just get kinda miffed when people claim to do A Security and then do the opposite
17 notes
·
View notes
Text
This Week in Rust 542
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tag us at @ThisWeekInRust on Twitter or @ThisWeekinRust on mastodon.social, or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub and archives can be viewed at this-week-in-rust.org. If you find any errors in this week's issue, please submit a PR.
Updates from Rust Community
Official
Announcing Rust 1.77.2
Security advisory for the standard library (CVE-2024-24576)
Changes to Rust's WASI targets
Rust Nation UK
Hannah Aubrey - A Web of Rust: The Future of the Internet Depends on Trust
JD Nose - Rust Infrastructure: What it takes to keep Rust running
Amanieu D'Antras - The path to a stable ABI for Rust
Luca Palmieri - Pavex: re-imaging API development in Rust
Lachezar Lechev - Typed for Safety
Marco Concetto Rudilosso - Building a profiler for web assembly
Jon Gjengset - Towards Impeccable Rust
Nicholas Yang - Porting Turborepo From Go To Rust
David Haig - What’s that behind your ear? An open source hearing aid in Rust.
Frédéric Ameye - Renault want to sell cars with rust!
Nikita Lapkov - Type-safe and fault-tolerant mesh services with Rust
Andre Bogus - Easy Mode Rust
Lars Bergstrom - Beyond Safety and Speed: How Rust Fuels Team Productivity
Tim McNamara - Unwrapping unsafe
Nicholas Matsakis - Rust 2024 and beyond
Project/Tooling Updates
Shipping Jco 1.0, WASI 0.2
This month in Pavex, #10
"Containerize" individual functions in Rust with extrasafe
rust-analyzer changelog #228
Rerun 0.15.0 - Blueprints from Python · rerun-io/rerun
Bevy 0.13.2, Curves, Gizmos, and Games
What's new in SeaORM 1.0-rc.x
Observations/Thoughts
Improve performance of you Rust functions by const currying
Ownership in Rust
Thoughts on the xz backdoor: an lzma-rs perspective
hyper HTTP/2 Continuation Flood
Leaky Abstractions and a Rusty Pin
[audio] Launching RustRover: JetBrains' Investment in Rust
[audio] Pavex with Luca Palmieri
[video] Decrusting the tokio crate
[video] Rust 1.77.0: 70 highlights in 30 minutes
[video] Simulate the three body problem in #rustlang
[video] Exploring Fiberplane's 3-Year Rust Journey - with Benno van den Berg
Rust Walkthroughs
Working with OpenAPI using Rust
Zed Decoded: Async Rust
Writing a Unix-like OS in Rust
Fivefold Slower Compared to Go? Optimizing Rust's Protobuf Decoding Performance
Write Cleaner, More Maintainable Rust Code with PhantomData
[video] Extreme Clippy for an existing Rust Crate
[video] developerlife.com - Build a color gradient animation for a spinner component, for CLI, in Rust
[video] developerlife.com - Build a spinner component, for CLI, in Rust
[video] developerlife.com - Build an async readline, and spinner in Rust, for interactive CLI
Research
"Against the Void": An Interview and Survey Study on How Rust Developers Use Unsafe Code
Sound Borrow-Checking for Rust via Symbolic Semantics
Miscellaneous
Rust indexed - Rust mdbooks search
March 2024 Rust Jobs Report
Rust Meetup and user groups (updated)
Embedding the Servo Web Engine in Qt
A memory model for Rust code in the kernel
Building Stock Market Engine from scratch in Rust (II)
Ratatui Received Funding: What's Next?
Crate of the Week
This week's crate is archspec-rs, a library to track system architecture aspects.
Thanks to Orhun Parmaksız for the suggestion!
Please submit your suggestions and votes for next week!
Call for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization. The following RFCs would benefit from user testing before moving forward:
No calls for testing were issued this week.
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Call for Participation; projects and speakers
CFP - Projects
Always wanted to contribute to open-source projects but did not know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
If you are a Rust project owner and are looking for contributors, please submit tasks here.
CFP - Speakers
Are you a new or experienced speaker looking for a place to share something cool? This section highlights events that are being planned and are accepting submissions to join their event as a speaker.
If you are an event organizer hoping to expand the reach of your event, please submit a link to the submission website through a PR to TWiR.
Updates from the Rust Project
431 pull requests were merged in the last week
CFI: change type transformation to use TypeFolder
CFI: fix ICE in KCFI non-associated function pointers
CFI: restore typeid_for_instance default behavior
CFI: support function pointers for trait methods
CFI: support non-general coroutines
MSVC targets should use COFF as their archive format
actually use the inferred ClosureKind from signature inference in coroutine-closures
add Ord::cmp for primitives as a BinOp in MIR
add a debug asserts call to match_projection_projections to ensure invariant
add aarch64-apple-visionos and aarch64-apple-visionos-sim tier 3 targets
add consistency with phrases "meantime" and "mean time"
assert FnDef kind
assert that args are actually compatible with their generics, rather than just their count
avoid ICEing without the pattern_types feature gate
avoid expanding to unstable internal method
avoid panicking unnecessarily on startup
better reporting on generic argument mismatchs
cleanup: rename HAS_PROJECTIONS to HAS_ALIASES etc
do not ICE in fn forced_ambiguity if we get an error
do not ICE on field access check on expr with ty::Error
do not ICE when calling incorrectly defined transmute intrinsic
fix ByMove coroutine-closure shim (for 2021 precise closure capturing behavior)
fix capture analysis for by-move closure bodies
fix diagnostic for qualifier in extern block
hir: use ItemLocalId::ZERO in a couple more places
impl get_mut_or_init and get_mut_or_try_init for OnceCell and OnceLock
implement T-types suggested logic for perfect non-local impl detection
implement minimal, internal-only pattern types in the type system
instantiate higher ranked goals outside of candidate selection
link against libc++abi and libunwind as well when building LLVM wrappers on AIX
make inductive cycles always ambiguous
make sure to insert Sized bound first into clauses list
match ergonomics: implement "&pat everywhere"
match lowering: make false edges more precise
more postfix match fixes
move check for error in impl header outside of reporting
only allow compiler_builtins to call LLVM intrinsics, not any link_name function
only inspect user-written predicates for privacy concerns
pass list of defineable opaque types into canonical queries
pattern analysis: fix union handling
postfix match fixes
privacy: stabilize lint unnameable_types
put checks that detect UB under their own flag below debug_assertions
revert removing miri jobserver workaround
safe Transmute: Compute transmutability from rustc_target::abi::Layout
sanitizers: create the rustc_sanitizers crate
split hir ty lowerer's error reporting code in check functions to mod errors
teach MIR inliner query cycle avoidance about const_eval_select
transforms match into an assignment statement
use the more informative generic type inference failure error on method calls on raw pointers
add missing ?Sized bounds for HasInterner impls
introduce Lifetime::Error
perf: cache type info for ParamEnv
encode dep graph edges directly from the previous graph when promoting
remove debuginfo from rustc-demangle too
stabilize const_caller_location and const_location_fields
stabilize proc_macro_byte_character and proc_macro_c_str_literals
stabilize const Atomic*::into_inner
de-LLVM the unchecked shifts
rename expose_addr to expose_provenance
rename ptr::from_exposed_addr → ptr::with_exposed_provenance
remove rt::init allocation for thread name
use unchecked_sub in str indexing
don't emit divide-by-zero panic paths in StepBy::len
add fn const BuildHasherDefault::new
add invariant to VecDeque::pop_* that len < cap if pop successful
add Context::ext
provide cabi_realloc on wasm32-wasip2 by default
vendor rustc_codegen_gcc
cargo: Build script not rerun when target rustflags change
cargo add: Stabilize MSRV-aware version req selection
cargo toml: Decouple target discovery from Target creation
cargo toml: Split out an explicit step to resolve Cargo.toml
cargo metadata: Show behavior with TOML-specific types
cargo: don't depend on ? affecting type inference in weird ways
cargo: fix github fast path redirect
cargo: maintain sorting of dependency features
cargo: switch to using gitoxide by default for listing files
rustdoc-search: shard the search result descriptions
rustdoc: default to light theme if JS is enabled but not working
rustdoc: heavily simplify the synthesis of auto trait impls
rustdoc: synthetic auto trait impls: accept unresolved region vars for now
clippy: manual_swap auto fix
clippy: manual_unwrap_or_default: check for Default trait implementation in initial condition when linting and use IfLetOrMatch
clippy: allow cast lints in macros
clippy: avoid an ICE in ptr_as_ptr when getting the def_id of a local
clippy: correct parentheses for needless_borrow suggestion
clippy: do not suggest assigning_clones in Clone impl
clippy: fix ice reporting in lintcheck
clippy: fix incorrect suggestion for !(a as type >= b)
clippy: reword arc_with_non_send_sync note and help messages
clippy: type certainty: clear DefId when an expression's type changes to non-adt
rust-analyzer: apply cargo flags in test explorer
rust-analyzer: fix off-by-one error converting to LSP UTF8 offsets with multi-byte char
rust-analyzer: consider exported_name="main" functions in test modules as tests
rust-analyzer: fix patch_cfg_if not applying with stitched sysroot
rust-analyzer: set the right postfix snippets competion source range
Rust Compiler Performance Triage
A quiet week; all the outright regressions were already triaged (the one biggish one was #122077, which is justified as an important bug fix). There was a very nice set of improvements from PR #122070, which cleverly avoids a lot of unnecessary allocator calls when building an incremental dep graph by reusing the old edges from the previous graph.
Triage done by @pnkfelix. Revision range: 3d5528c2..86b603cd
3 Regressions, 3 Improvements, 7 Mixed; 1 of them in rollups 78 artifact comparisons made in total
See full report here
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
Merge RFC 3513: Add gen blocks
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
[disposition: merge] RFC: Drop temporaries in tail expressions before local variables
[disposition: merge] RFC: Reserve unprefixed guarded string literals in Edition 2024
Tracking Issues & PRs
Rust
[disposition: merge] Always display stability version even if it's the same as the containing item
[disposition: merge] Tracking Issue for cstr_count_bytes
[disposition: merge] rustdoc-search: single result for items with multiple paths
[disposition: merge] Tracking Issue for #![feature(const_io_structs)]
[disposition: merge] Tracking Issue for alloc::collections::BinaryHeap::as_slice
[disposition: merge] Tracking Issue for fs_try_exists
[disposition: merge] stabilize -Znext-solver=coherence
[disposition: merge] Document overrides of clone_from() in core/std
[disposition: merge] Stabilise inline_const
[disposition: merge] Tracking Issue for RFC 3013: Checking conditional compilation at compile time
[disposition: merge] sess: stabilize -Zrelro-level as -Crelro-level
[disposition: merge] Implement FromIterator for (impl Default + Extend, impl Default + Extend)
[disposition: close] Return the delimiter from slice::split_once
[disposition: merge] Support type '/' to search
[disposition: merge] Tracking Issue for Seek::seek_relative
[disposition: merge] Tracking Issue for generic NonZero
New and Updated RFCs
[new] Add an expression for direct access to an enum's discriminant
[new] RFC: Drop temporaries in tail expressions before local variables
Upcoming Events
Rusty Events between 2024-04-10 - 2024-05-08 🦀
Virtual
2024-04-11 | Virtual + In Person (Berlin, DE) | OpenTechSchool Berlin + Rust Berlin
Rust Hack and Learn | Mirror: Rust Hack n Learn Meetup
2024-04-11 | Virtual (Nürnberg, DE) | Rust Nüremberg
Rust Nürnberg online
2024-04-11 | Virtual (San Diego, CA, US) | San Diego Rust
San Diego Rust April 2024 Tele-Meetup
2024-04-15 & 2024-04-16 | Virtual | Mainmatter
Remote Workshop: Testing for Rust projects – going beyond the basics
2024-04-16 | Virtual (Dublin, IE) | Rust Dublin
A reverse proxy with Tower and Hyperv1
2024-04-16 | Virtual (Washington, DC, US) | Rust DC
Mid-month Rustful—forensic parsing via Artemis
2024-04-17 | Virtual | Rust for Lunch
April 2024 Rust for Lunch
2024-04-17 | Virtual (Cardiff, UK) | Rust and C++ Cardiff
Reflections on RustNation UK 2024
2024-04-17 | Virtual (Vancouver, BC, CA) | Vancouver Rust
Rust Study/Hack/Hang-out
2024-04-18 | Virtual (Charlottesville, VA, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2024-04-21 | Virtual (Israel) | Rust in Israel
Using AstroNvim for Rust development (in Hebrew)
2024-04-25 | Virtual + In Person (Berlin, DE) | OpenTechSchool Berlin + Rust Berlin
Rust Hack and Learn | Mirror: Rust Hack n Learn Meetup
2024-04-30 | Virtual (Dallas, TX, US) | Dallas Rust
Last Tuesday
2024-05-01 | Virtual (Cardiff, UK) | Rust and C++ Cardiff
Rust for Rustaceans Book Club: Chapter 5 - Project Structure
2024-05-01 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2024-05-02 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2024-05-07 | Virtual (Buffalo, NY) | Buffalo Rust Meetup
Buffalo Rust User Group
Africa
2024-05-04 | Kampala, UG | Rust Circle Kampala
Rust Circle Meetup
Asia
2024-04-16 | Tokyo, JP | Tokyo Rust Meetup
The Good, the Bad, and the Async (RSVP by 15 Apr)
Europe
2024-04-10 | Cambridge, UK | Cambridge Rust Meetup
Rust Meetup Reboot 3
2024-04-10 | Cologne/Köln, DE | Rust Cologne
This Month in Rust, April
2024-04-10 | Manchester, UK | Rust Manchester
Rust Manchester April 2024
2024-04-10 | Oslo, NO | Rust Oslo
Rust Hack'n'Learn at Kampen Bistro
2024-04-11 | Bordeaux, FR | Rust Bordeaux
Rust Bordeaux #2 : Présentations
2024-04-11 | Reading, UK | Reading Rust Workshop
Reading Rust Meetup at Browns
2024-04-15 | Zagreb, HR | impl Zagreb for Rust
Rust Meetup 2024/04: Building cargo projects with NIX
2024-04-16 | Bratislava, SK | Bratislava Rust Meetup Group
Rust Meetup by Sonalake #5
2024-04-16 | Leipzig, DE | Rust - Modern Systems Programming in Leipzig
winnow/nom
2024-04-16 | Munich, DE + Virtual | Rust Munich
Rust Munich 2024 / 1 - hybrid
2024-04-17 | Bergen, NO | Hubbel kodeklubb
Lær Rust med Conways Game of Life
2024-04-17 | Ostrava, CZ | TechMeetup Ostrava
TechMeetup: RUST
2024-04-20 | Augsburg, DE | Augsburger Linux-Infotag 2024
Augsburger Linux-Infotag 2024: Workshop Einstieg in Embedded Rust mit dem Raspberry Pico WH
2024-04-23 | Berlin, DE | Rust Berlin
Rust'n'Tell - Rust for the Web
2024-04-23 | Paris, FR | Rust Paris
Paris Rust Meetup #67
2024-04-25 | Aarhus, DK | Rust Aarhus
Talk Night at MFT Energy
2024-04-23 | Berlin, DE | Rust Berlin
Rust'n'Tell - Rust for the Web
2024-04-25 | Berlin, DE | Rust Berlin
Rust and Tell - TBD
2024-04-27 | Basel, CH | Rust Basel
Fullstack Rust - Workshop #2 (Register by 23 April)
2024-04-30 | Budapest, HU | Budapest Rust Meetup Group
Rust Meetup Budapest 2
2024-04-30 | Salzburg, AT | Rust Salzburg
[Rust Salzburg meetup]: 6:30pm - CCC Salzburg, 1. OG, ArgeKultur, Ulrike-Gschwandtner-Straße 5, 5020 Salzburg
2024-05-01 | Utrecht, NL | NL-RSE Community
NL-RSE RUST meetup
2024-05-06 | Delft, NL | GOSIM
GOSIM Europe 2024
2024-05-07 & 2024-05-08 | Delft, NL | RustNL
RustNL 2024
North America
2024-04-10 | Boulder, CO, US | Boulder Rust Meetup
Rust Meetup: Better Builds w/ Flox + Hangs
2024-04-11 | Lehi, UT, US | Utah Rust
Interactive Storytelling using Yarn Spinner with Rex Magana
2024-04-11 | Seattle, WA, US | Seattle Rust User Group
Seattle Rust User Group Meetup
2024-04-11 | Spokane, WA, US | Spohttps://www.meetup.com/minneapolis-rust-meetup/kane Rust
Monthly Meetup: The Rust Full-Stack Experience
2024-04-15 | Minneapolis, MN, US | Minneapolish Rust Meetup
Minneapolis Rust: Getting started with Rust! #2
2024-04-15 | Somerville, MA, US | Boston Rust Meetup
Davis Square Rust Lunch, Apr 15
2024-04-16 | San Francisco, CA, US | San Francisco Rust Study Group
Rust Hacking in Person
2024-04-16 | Seattle, WA, US | Seattle Rust User Group
Seattle Rust User Group: Meet Servo and Robius Open Source Projects
2024-04-18 | Chicago, IL, US | Deep Dish Rust
Rust Talk: What Are Panics?
2024-04-18 | Mountain View, CA, US | Mountain View Rust Meetup
Rust Meetup at Hacker Dojo
2024-04-24 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
2024-04-25 | Nashville, TN, US | Music City Rust Developers
Music City Rust Developers - Async Rust on Embedded
2024-04-26 | Boston, MA, US | Boston Rust Meetup
North End Rust Lunch, Apr 26
Oceania
2024-04-15 | Melbourne, VIC, AU | Rust Melbourne
April 2024 Rust Melbourne Meetup
2024-04-17 | Sydney, NSW, AU | Rust Sydney
WMaTIR 2024 Gala & Talks
2024-04-30 | Auckland, NZ | Rust AKL
Rust AKL: Why Rust? Convince Me!
2024-04-30 | Canberra, ACT, AU | Canberra Rust User Group
CRUG April Meetup: Generics and Traits
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
As a former JavaScript plebeian who has only been semi-recently illuminated by the suspiciously pastel pink, white and blue radiance of Rust developers, NOT having to sit in my web console debugger for hours pushing some lovingly crafted [object Object] or undefined is a blessing.
– Julien Robert rage-blogging against bevy
Thanks to scottmcm for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, andrewpollack, U007D, kolharsam, joelmarcey, mariannegoldin, bennyvasquez.
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
1 note
·
View note
Text
AI, CVEs and Swiss cheese - CyberTalk
New Post has been published on https://thedigitalinsider.com/ai-cves-and-swiss-cheese-cybertalk/
AI, CVEs and Swiss cheese - CyberTalk


By Grant Asplund, Cyber Security Evangelist, Check Point. For more than 25 years, Grant Asplund has been sharing his insights into how businesses can best protect themselves from sophisticated cyber attacks in an increasingly complex world.
Grant was Check Point first worldwide evangelist from 1998 to 2002 and returned to Check Point with the acquisition of Dome9. Grant’s wide range of cyber security experience informs his talks, as he has served in diverse roles, ranging from sales, to marketing, to business development, and to senior management for Dome 9, Blue Coat Systems, Neustar, and Altor Networks. As CEO of MetaInfo, he led its acquisition by Neustar. Grant is the host of the CISO Secrets podcast (cp.buzzsprout.com) and the Talking Cloud Podcast (talkingcloud.podbean.com) on cloud security.
EXECUTIVE SUMMARY:
AI, AI, OH!
If you’ve attended a cyber security conference in the past several months, you know the topic of artificial intelligence is in just about every vendor presentation. And I suspect, we’re going to hear a lot more about it in the coming months and years.
Our lives are certainly going to change due to AI. I’m not sure if any of us really appreciates what it will be like to have an assistant that knows everything that the internet knows.
Unfortunately, not everyone will be utilizing these AI assistants for good. Additionally, the profound impact from employing AI will be just as significant for the nefarious as for the well-intended.
Consider what’s right around the corner…
Hackers often begin their social engineering schemes by directing their AI assistants (and custom bots) to conduct reconnaissance on their target.
The first phase is to gather intelligence and information about the target. Using any and every means available, they will determine what general technology products and which security products are being used and the current versions in-use. This phase might last weeks or months.
Once gathered, the hacker will utilize AI to correlate the products and versions in-use with the known CVE’s issued for the same versions of products, and clearly identify the exploitable path(s).
200,000 known CVEs
And odds are on the hackers’ side. According to the National Vulnerability Database, there are currently over 200,000 known CVEs. Fifty percent of vulnerability exploits occur within 2-4 weeks of a patch being released, while the average time for an enterprise to respond to a critical vulnerability is 120 days.
All of this leads me to ask: When selecting a security vendor and security products, why don’t more companies ask the vendor how many CVEs have been released concerning the products being purchased?
After all, these ‘security’ products are being purchased to secure valuable business assets! Some vendors’ products have more holes than Swiss cheese!
Comprehensive, consolidated and collaborative
Of course, I’m not suggesting an organization usurp their rigorous assessment, evaluation, and selection process when choosing their security vendors and products, basing the decision solely on the number of CVEs; especially considering that today’s computing environments and overall digital footprints are vastly more complex than ever before and they continue to expand.
What I am suggesting is that now, more than ever, organizations need to step back and re-assess their overall security platform. Due to the increased complexity and ever-increasing number of point solutions, companies must consider deploying a comprehensive, consolidated, and highly collaborative security platform.
Reducing CVEs and Swiss cheese
Once your organization has identified the possible vendors who can help consolidate your security stack, be sure and check how many HIGH or CRITICAL CVE’s have been released in the last few years on the products you’re considering. And check on how long it took to fix them.
By consolidating your stack, you will reduce complexity. By eliminating the ‘Swiss cheese’ products in your security stack, you will eliminate the gaps most likely to be exploited in the future by artificial intelligence.
For information about cyber security products powered by AI, click here. To receive compelling cyber insights, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#000#ai#analyses#artificial#Artificial Intelligence#assessment#assets#Blue#bots#Business#Business development#CEO#change#Check Point#CISO#Cloud#Cloud Security#collaborative#Companies#complexity#comprehensive#computing#conference#consolidated#course#cyber#cyber attacks#cyber security#cyber security conference#Cyber Security Evangelist
0 notes