#Computer And Network Security
Explore tagged Tumblr posts
Text
Accops and pi-labs Partner to Protect Facial Authentication from Deepfake Threats
Strengthening Facial Authentication Against AI-Driven Fraud Press Release – Tuesday, March 25, 2025 – [Pune, India] – As deepfake attacks on facial authentication systems become increasingly sophisticated, organisations are facing a growing threat of identity fraud.Research indicates that deepfake-enabled cyber fraud is expected to exceed $40 billion by 2027, underscoring the urgent need for…
0 notes
Text
HPE Distributors in Dubai
Numero Systems is at the forefront of Dubai's technology landscape, distinguished as a leading IT products supplier in the region. Renowned for its versatile solutions, Numero Systems caters to diverse technological needs. As an Oracle Partner in UAE, the company integrates cutting-edge Oracle technologies into its offerings, ensuring top-tier solutions for businesses. Numero Systems' role among the leading IT products suppliers in Dubai is marked by a commitment to excellence, innovation, and a customer-centric approach. Businesses can rely on Numero Systems for reliable and advanced IT solutions, making it a pivotal player in Dubai's ever-evolving technological ecosystem.
0 notes
Text
Kasada Introduces New Suite Of Attack Prediction Services: KasadaIQ

The innovative firm Kasada, which specializes in thwarting automated threats powered by humans, has announced KasadaIQ, a package of attack prediction services that go beyond traditional bot management. The first product in this package, KasadaIQ for Fraud, provides actionable indications based on large amounts of data from the Internet. Businesses looking for information on how bots target their digital channels and client data will find this service especially helpful. With its unmatched visibility into adversary communities and non-traditional data sources, KasadaIQ for Fraud distinguishes itself by offering a cutting-edge capacity to identify and validate risks prior to their manifestation.
Businesses face a serious and expensive threat from bot fraud, which may cost them money, effort, and reputational damage in addition to endangering their customers. The environment of eCommerce fraud is expanding globally, with predictions that it will top $48 billion this year. A startling 96% of IT professionals reported that they have lost money as a result of bot assaults in the previous year, according to Kasada's 2023 State of Bot Mitigation Report.
The founder and CEO of Kasada, Sam Crowther, highlighted the increasing sophistication of bots, pointing out that almost eighty percent of business executives find it harder and harder for their security solutions to identify bots. In spite of this, a lot of businesses continue to use antiquated technologies that develop slowly. According to Crowther, businesses can proactively defend against attackers with KasadaIQ for Fraud in conjunction with their current bot detection systems, giving them a competitive edge and avoiding bad press.
Read More - https://bit.ly/3G5EvbD
0 notes
Text
4 nines of uptime for the most duct-taped sopping wet home services solely because i just don't touch the shit that's werking
and by that i mean. what is a software up Date.
#my:poast#compute#yeah yeah security etc but my threat model here is “if a bad guy is in my home network then i have other problems besides the mediaserver”#these aren't exposed 2 the public internet
14 notes
·
View notes
Text

my first introduction to firewall during my childhood
Tom and Jerry Tales | S1 E16 Digital Fireball
#genuinely i thought firewalls must exist like this inside the computer#computer science#computer network#computer security#computer forensics#firewalls#coding#cs#csblr#tom and jerry#tom and jerry tales#tom#jerry#i am talking
4 notes
·
View notes
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
Positioned within the vibrant cityscape of Lubbock, Texas, Precision Managed IT stands as a beacon of technological prowess and reliability in the realm of outsourcing IT support. Our strategically located office embodies accessibility and expertise, catering to businesses seeking seamless and comprehensive IT solutions in this dynamic city.
Strategically situated within Lubbock's thriving business districts, our office serves as a central hub for businesses across diverse industries, from the healthcare sector near the medical facilities to the academic enterprises surrounding Texas Tech University. This strategic placement underscores our commitment to serving the varied tapestry of Lubbock's business community.
The physical space of Precision Managed IT is meticulously designed to exude professionalism and innovation. Boasting state-of-the-art infrastructure and a conducive workspace, our office cultivates an environment that fosters collaboration, trust, and ease for businesses seeking top-tier IT support services.
Beyond merely being a physical office, Precision Managed IT embodies a team of expert professionals deeply entrenched in the intricacies of the modern IT landscape. Each team member brings forth a wealth of technical knowledge, integrity, and proactive problem-solving skills to ensure that every client receives tailored, forward-thinking solutions to their IT needs.
Precision Managed IT isn't merely a service provider; it's a strategic partner invested in the success of the businesses we serve. We actively engage with our clients, forging strong partnerships aimed at elevating their technological infrastructure, optimizing operations, and ensuring seamless growth in an increasingly digital world.
Lubbock's dynamic business environment, educational institutions, and diverse industries align perfectly with Precision Managed IT's commitment to excellence and adaptability in the outsourcing IT support realm. We strive to remain at the forefront of technological advancements, empowering businesses to thrive amidst digital transformations and challenges.
In essence, Precision Managed IT represents more than just an IT support provider—it embodies trust, expertise, and efficiency in managing and optimizing technological infrastructure. Our presence in Lubbock signifies our unwavering dedication to simplifying IT complexities for businesses while upholding values of reliability, transparency, and a steadfast commitment to exceeding expectations.
Website: http://www.precisionmanagedit.com/lubbock-tx
Address: 5307 W Loop 289 Acc Rd, Lubbock, TX, 79414
Phone Number: +1 806-692-2884
Business Hours: Monday - Sunday : 07:00 AM - 07:00 PM
2 notes
·
View notes
Text
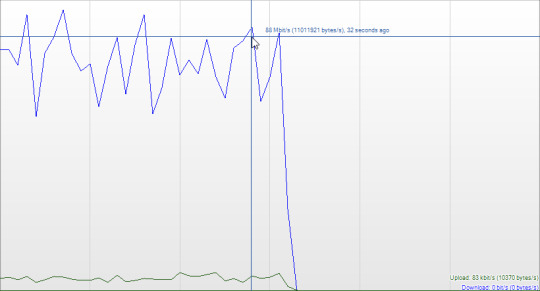
FUCKKKK my school frrr, network is totally capable of allocating me 86Mbp/s for JUST qBITTORRENT but instead of getting access to that we get throttled down to like >400Kbps if even.
#.txt#to explain what this graph is#the blue is my down speed#green is up speed#I have my vpn on and with port forwarding#which is able to circumvent my schools NAT protocol by forwarding the network traffic to a local port on my computer#(its technically remote port forwarding but)#and because I can get traffic directed to my machine a lot of the traffic that gets throttled by the networks security protocols#specifically NAT.( btw I am not inviting hostile activity onto the network I am just choosing to encrypt my data and verify authenticity#with a different protocol than NAT. specifically wireGuard which is the leading VPN protocol now)#however a lot of people dont like port forwarding because of that property and few VPNs support it anymore but its like the only way to#torrent at more than a snails pace#and so my school detected my high network activity and because of the encrypted data I was sending they literally just deny me service#I can just connect back with my regular PC no problem too so its not even stopping me#its just delaying me and making it annoying'
4 notes
·
View notes
Text
SpecterOps Raises $75M Series B to Strengthen Identity Security in Round Led by Insight Partners
Latest funding underscores the heightened priority to protect digital identities and the critical role of Attack Path Management in safeguarding organizations News – Alexandria, VA – March 5, 2025 – SpecterOps, a provider of adversary-focused cybersecurity solutions with targeted insights of advanced threat actor tradecraft, today announced it has raised a $75 million Series B funding round led…
0 notes
Text
You'd think that an industry that gets the concepts of "we should nerf some features so we can offer this at different pricepoints to make it easier for people to get the grants to buy our products" would understand "we'd love to buy a new microscope but have no way of getting the money for it". But unfortunately I'm not surprised that they don't.
abandonware should be public domain. force companies to actively support and provide products if they don't wanna lose the rights to them
#every lab has a airgapped computer#that you can't connect to the network#because it's still running a dated OS#because you need it for your machines#and you can't risk it getting a virus#very very new labs#may only have the air gap for security#but they're few and far between
128K notes
·
View notes
Text
Numerosys: commitment to quality and innovation
Numerosys stands out as the go-to IT products supplier in Dubai, offering a comprehensive range of cutting-edge solutions. Renowned for excellence, we not only serve as leading IT products suppliers in Dubai but also proudly hold the prestigious title of an Oracle Partner in the UAE. Our commitment to quality and innovation sets us apart, ensuring that businesses receive top-notch IT products and benefit from our strategic partnership with Oracle. Trust Numerosys for all your IT needs, where quality meets expertise, making us a reliable choice in the competitive landscape of IT products and solutions in Dubai.
0 notes
Text
Identiv Wins 2023 Security Vanguard Award For Innovation In Community Security

The esteemed 2023 Security Vanguard Award has been given to Identiv, Inc. (NASDAQ: INVE), a well-known worldwide pioneer in digital security and identity within the Internet of Things (IoT), by Endeavor Business Media (EBM) Security Group. Given to trailblazers in the security sector, this award honors Identiv's creative security initiative at Santa Rosa, California's Caritas Village.
Overseen by Catholic Charities of Santa Rosa, Caritas Village is a comprehensive program designed to assist Sonoma County's homeless population. Identiv worked with integrator Blakeslee Electric to create a comprehensive security system that catered to the various requirements of the community, residents, and facilities staff.
uTrust TS Readers, uTrust TS Cards, Hirsch Mx Controllers, Velocity Vision Video Management System (VMS), and the powerful Hirsch Velocity Security Management System were all implemented as part of the highly acclaimed Identiv project. The open and caring culture of the Village was respected while a high level of security was offered by this integrated solution.
The sophisticated system provides an easy-to-use interface for access management, improved audit capabilities, and real-time incident response. The accomplishment of this project demonstrates Identiv's dedication to security that upholds neighborhood values and fosters safety without undermining community spirit.
Read More - https://bit.ly/3SIdRx8
#Identiv#Computer And Network Security#Internet Of Things (IoT)#Endeavor Business Media (EBM)#Video Management System (VMS)
0 notes
Text
Final Year Projects That Impress and Inspire
Stand out with smart, practical final year projects in tech, science, and engineering streams.
#cyber security projects for final year students#cyber security projects for final year#web development projects for final year#final year projects for cse#python projects for final year students#network security projects for final year students#cyber security final year project#data science final year projects#app development projects for final year#cloud computing projects for final year students#best web development projects for final year students#web development project for final year#final year project for cyber security#cloud computing final year project#aws projects for final year github#best computer science projects for final year#best computer science final year projects#best final year projects for it students#best major project for cse#best project for computer science final year#best projects for it final year#best python projects for final year students#cloud based final year projects#cloud computing based projects for final year#cloud computing projects final year#cloud projects for final year students
0 notes
Text


Website: http://triuneinfotech.com/
Address: 31886 Cotton Thorn Ct, Murrieta, CA 92563
Phone: +1 (951) 249-7775
Triune InfoTech has been providing expert IT support in Murrieta since 2013, helping businesses boost productivity and profitability through streamlined technology solutions. We offer reliable computer support, data recovery, cybersecurity, networking, consulting, and repair services—all under a simple flat-rate monthly plan. Our proactive service model ensures timely solutions, expert guidance, and predictable costs. As a trusted computer service provider, IT consultant, and tech support partner, we’re committed to helping your business thrive. Contact us today to get started!
#Computer service#Computer consultant#Data recovery service#Computer repair service#Computer security service#Computer networking service
1 note
·
View note
Text
Post Quantum Blockchain: Future of Decentralized Technology
What will become of our decentralized networks when quantum computers can break our most secure cryptographic defenses today? If quantum attacks eat away at digital security, then the security of blockchain systems has never been more crucial. Welcome to the Post Quantum Blockchain universe, an incoming paradigm shift strategy combining the blockchain’s resilience and the post-quantum cryptography’s next-generation security to protect the immortal digital universe.
In this article, we discuss the important part that quantum-resistant blockchain will have to play in protecting decentralized networks from the increasing menace of quantum computing.
Understanding Post-Quantum Blockchain

Post Quantum Blockchain is a blockchain network that is protected by highly advanced, quantum computer-immune cryptographically secured algorithms. RSA or ECC are conventional tools used for encryption, which would become sitting ducks against attacks from quantum algorithms like Shor’s, which will compromise their integrity. It poses a humongous risk to decentralized networks operating on such algorithms for data assurance, identity authentication, and secured transactions.
With the integration of quantum-resistant cryptography, these blockchain platforms can provide security and trust in a quantum computer-based future. The National Institute of Standards and Technology (NIST) is attempting to develop ultimate encryption standards to be the new way of doing it, and hence quantum-secure blockchain deployment becomes an unavoidable evolution.
Why Traditional Blockchains Are Vulnerable

Although blockchain itself is generally considered secure and unalterable, it is not resistant to the increasing threat of quantum computing. Classical blockchains are highly dependent on classical cryptographic methods — namely, public-key cryptography — to protect digital identities, authenticate transactions, and establish consensus among distributed nodes. But with the accelerated advancement of quantum technology, these methods are in serious jeopardy. A sufficiently powerful quantum computer would be able to take advantage of loopholes in such cryptographic schemes to reverse-engineer private keys from public keys, allowing hackers to impersonate the real users. This can result in unauthorized transactions, loss of funds, or even bulk tampering with the blockchain ledger.
Furthermore, quantum computations like Shor’s algorithm can even break the digital signatures that are employed to secure transactions. If such signatures are compromised, they would no longer provide trust in the authenticity or source of a message. Quantum systems would also destabilize consensus systems, which are critical to all participants in a network adhering to a specified state of the blockchain. These findings point to how unprepared systems are at present for a quantum world.
In order to combat these future threats, cryptographers and developers are turning to Post Quantum Blockchain solutions that build on quantum-resistant protocols and algorithms. This next-generation solution can potentially restore trust and security in decentralized systems in the quantum era.
Core Principles Behind Post-Quantum Blockchain
To create a post-quantum blockchain that is resilient, some principles are used-
Lattice-based cryptography: Lattice-based cryptography is a bedrock, since it is quantum proof. Its mathematical complexity is high and it’s computationally not possible even for quantum computers to reverse-engineer encrypted data, thus it’s a very secure way of safeguarding identity and key exchange.
Hash-based signatures: Hash-based signatures constitute another central element. They provide secure short-term digital authentication to maintain messages and transactions tamper-evident. Hash-based signatures work with irrevocable one-way functions for a quantum system, as opposed to classical digital signatures.
Code-based cryptography: Code-based cryptography is also used to ensure a good level of long-term message security. It uses codes that will resist such forms of decryption, whether classical or quantum.
Zero-knowledge proofs: Finally, we have zero-knowledge proofs, which are incorporated to complete the system. Zero-knowledge proofs allow a party to verify possession of knowledge about a condition or value without sharing underlying information. This maintains confidentiality and guarantees immunity from quantum attacks, such that data confidentiality and trust are achieved in decentralized applications.
Advantages of Post-Quantum Blockchain
1. Future-Proof Security
Most readily apparent benefit of Post Quantum Blockchain is that it will resist quantum attacks. Avoiding future attacks ahead of time, the developers will not need to invest the exorbitant expense of redoing systems down the road.
2. More Privacy
New cryptographic building blocks employed by Post Quantum Blockchain can also enhance the protection of privacy through improved anonymization techniques.
3. Compliance with Regulations
As government agencies start to issue post-quantum compliance requirements, employing Quantum Blockchain protocols puts businesses ahead of the law.
4. Long-Term Data Integrity
In contrast to legacy systems that can grow obsolete in the quantum age, Post Quantum Blockchain solutions guarantee your data is immutable and trusted for decades to come.
Real-World Use Cases for Post-Quantum Blockchain
Some industries are starting to consider Post Quantum Blockchain-
Finance: The banking industry, for example, is among the first to embrace. Encryption is a major source of security for online transactions, customer identity, and online balances for banks. With the danger of traditional cryptography from quantum computers, quantum-resistant blockchain guarantees long-term security for banking services, cryptocurrencies, and smart contracts.
Healthcare: Healthcare, where the confidentiality and integrity of patient data are paramount, sees this technology providing tamper-evident storage and transport of sensitive information. Decentralization, and with it the use of quantum-safe encryption, makes for safe sharing of medical records between health providers and shields against leaks and unauthorized alteration.
Supply Chain: The supply chain sector is also discovering the utility of this new solution. Through the utilization of quantum-resistant blockchain, businesses can create open, immutable records of product origin, transport, and handling. It assists in the prevention of fraud, lowers counterfeiting, and increases efficiency in international logistics.
Government: Governments are exploring their use for secure administration of digital identity, citizenship authentication, and even voting. With election security and identity fraud issues on the rise, a tamper-proof, quantum-secure blockchain can provide more public trust and operational integrity to democratic and administrative systems.
The Rise of Post Quantum Secured Blockchain
Post quantum secured blockchain technology is a giant leap towards the security of decentralized platforms against the impending threat of quantum computers. Traditional blockchains, though secure against classical attacks, are becoming increasingly susceptible to quantum algorithms that support breaking standard encryption schemes employed.
Conversely, post quantum secured blockchain networks are inherently constructed with quantum resistance. Every single aspect — identity verification, transaction verification, smart contracts, and consensus algorithms — is supported by cryptographic algorithms particularly selected for their quantum decrypt resistance.
This method guarantees that important activities such as signing a contract, digital signing, and multi-party cooperation on data are secure, transparent, and tamper-evident even in the future when all have quantum processors. With a trend of industries going quantum-readiness, implementing such infrastructure is not an upgrade — it is a required building block.
METHODOLOGY: Ensuring AI Safety Through Post Quantum Blockchain

To truly safeguard AI’s influence on society, data integrity must be prioritized above all. As artificial intelligence systems become more intertwined with human decision-making, preventing malicious replication of identity and the misuse of personal data is crucial. One reliable approach is the integration of Post Quantum Blockchain…
#post quantum blockchain#post quantum encryption#quantum blockchain#post quantum securityu#blokchain technology#decentralized database#post quantum cryptography#post quantum secure blockchain#blockchain security#ncog#blockchain technology#secure blockchain#secure blockchain technology#quantum safe cryptography#tumblr#blockchain#quantum resistant blockchain#quantum attacks#quantum computer#quantum compting#decentralized system#blockchain network#did#digital security
1 note
·
View note
Text
Beyond the Firewall: Edge Security Meets Zero Trust for a Safer Digital Frontier.
Sanjay Kumar Mohindroo Sanjay Kumar Mohindroo. skm.stayingalive.in Explore how Edge Security & Zero Trust Architecture with continuous verification secures distributed data and apps. Join the discussion!
Quick insights to shift your security approach. Today, data and apps live everywhere. The old wall around the network no longer holds. We must shift to a model that checks every request at…
#AI#Application Security#Continuous Verification#cyber-security#Cybersecurity#Distributed Data Protection#Edge Computing Security#Edge Security#Network Perimeter#News#Sanjay Kumar Mohindroo#security#technology#Zero Trust Architecture#Zero Trust Security
0 notes