#Edge Computing Security
Explore tagged Tumblr posts
Text
Beyond the Firewall: Edge Security Meets Zero Trust for a Safer Digital Frontier.
Sanjay Kumar Mohindroo Sanjay Kumar Mohindroo. skm.stayingalive.in Explore how Edge Security & Zero Trust Architecture with continuous verification secures distributed data and apps. Join the discussion!
Quick insights to shift your security approach. Today, data and apps live everywhere. The old wall around the network no longer holds. We must shift to a model that checks every request at…
#AI#Application Security#Continuous Verification#cyber-security#Cybersecurity#Distributed Data Protection#Edge Computing Security#Edge Security#Network Perimeter#News#Sanjay Kumar Mohindroo#security#technology#Zero Trust Architecture#Zero Trust Security
0 notes
Text
The Edge of Innovation: Why Edge Computing Is a Big Deal
Introduction
Staying updated with the ever-evolving world of technology is vital. At TechtoIO, we pride ourselves on being at the edge of innovation. Edge computing is one of the most revolutionary developments transforming the technology landscape today. But what exactly is edge computing, and why is it such a big deal? Let’s dive into this fascinating topic to understand its significance and potential impact on our digital future. Read to continue
#Tech Trends#Tagsdge computing for autonomous vehicles#edge computing#edge computing and 5G#edge computing and AI#edge computing applications#edge computing benefits#edge computing challenges#edge computing cost efficiency#edge computing explained#edge computing for autonomous vehicles#edge computing future#edge computing impact#edge computing in healthcare#edge computing in smart cities#edge computing infrastructure#edge computing overview#edge computing real-world examples#edge computing scalability#edge computing security#edge computing technology#Technology#Science#business tech#Adobe cloud#Trends#Nvidia Drive#Analysis#Tech news#Science updates
1 note
·
View note
Text
The AIoT Revolution: How AI and IoT Convergence is Rewriting the Rules of Industry & Life

Imagine a world where factory machines predict their own breakdowns before they happen. Where city streets dynamically adjust traffic flow in real-time, slashing commute times. Where your morning coffee brews automatically as your smartwatch detects you waking. This isn’t science fiction—it’s the explosive reality of Artificial Intelligence of Things (AIoT), the merger of AI algorithms and IoT ecosystems. At widedevsolution.com, we engineer these intelligent futures daily.
Why AIoT Isn’t Just Buzzword Bingo: The Core Convergence
Artificial Intelligence of Things fuses the sensory nervous system of IoT devices (sensors, actuators, smart gadgets) with the cognitive brainpower of machine learning models and deep neural networks. Unlike traditional IoT—which drowns in raw data—AIoT delivers actionable intelligence.
As Sundar Pichai, CEO of Google, asserts:
“We are moving from a mobile-first to an AI-first world. The ability to apply AI and machine learning to massive datasets from connected devices is unlocking unprecedented solutions.”
The AIoT Trinity: Trends Reshaping Reality
1. Predictive Maintenance: The Death of Downtime Gone are days of scheduled check-ups. AI-driven predictive maintenance analyzes sensor data intelligence—vibrations, temperature, sound patterns—to forecast failures weeks in advance.
Real-world impact: Siemens reduced turbine failures by 30% using AI anomaly detection on industrial IoT applications.
Financial upside: McKinsey estimates predictive maintenance cuts costs by 20% and downtime by 50%.
2. Smart Cities: Urban Landscapes with a Brain Smart city solutions leverage edge computing and real-time analytics to optimize resources. Barcelona’s AIoT-powered streetlights cut energy use by 30%. Singapore uses AI traffic prediction to reduce congestion by 15%.
Core Tech Stack:
Distributed sensor networks monitoring air/water quality
Computer vision systems for public safety
AI-powered energy grids balancing supply/demand
3. Hyper-Personalized Experiences: The End of One-Size-Fits-All Personalized user experiences now anticipate needs. Think:
Retail: Nike’s IoT-enabled stores suggest shoes based on past purchases and gait analysis.
Healthcare: Remote patient monitoring with wearable IoT detects arrhythmias before symptoms appear.
Sectoral Shockwaves: Where AIoT is Moving the Needle
🏥 Healthcare: From Treatment to Prevention Healthcare IoT enables continuous monitoring. AI-driven diagnostics analyze data from pacemakers, glucose monitors, and smart inhalers. Results?
45% fewer hospital readmissions (Mayo Clinic study)
Early detection of sepsis 6+ hours faster (Johns Hopkins AIoT model)
🌾 Agriculture: Precision Farming at Scale Precision agriculture uses soil moisture sensors, drone imagery, and ML yield prediction to boost output sustainably.
Case Study: John Deere’s AIoT tractors reduced water usage by 40% while increasing crop yields by 15% via real-time field analytics.
🏭 Manufacturing: The Zero-Waste Factory Manufacturing efficiency soars with AI-powered quality control and autonomous supply chains.
Data Point: Bosch’s AIoT factories achieve 99.9985% quality compliance and 25% faster production cycles through automated defect detection.
Navigating the Minefield: Challenges in Scaling AIoT
Even pioneers face hurdles:ChallengeSolutionData security in IoTEnd-to-end encryption + zero-trust architectureSystem interoperabilityAPI-first integration frameworksAI model driftContinuous MLOps monitoringEnergy constraintsTinyML algorithms for low-power devices
As Microsoft CEO Satya Nadella warns:
“Trust is the currency of the AIoT era. Without robust security and ethical governance, even the most brilliant systems will fail.”
How widedevsolution.com Engineers Tomorrow’s AIoT
At widedevsolution.com, we build scalable IoT systems that turn data deluge into profit. Our recent projects include:
A predictive maintenance platform for wind farms, cutting turbine repair costs by $2M/year.
An AI retail personalization engine boosting client sales conversions by 34%.
Smart city infrastructure reducing municipal energy waste by 28%.
We specialize in overcoming edge computing bottlenecks and designing cyber-physical systems with military-grade data security in IoT.
The Road Ahead: Your AIoT Action Plan
The AIoT market will hit $1.2T by 2030 (Statista). To lead, not follow:
Start small: Pilot sensor-driven process optimization in one workflow.
Prioritize security: Implement hardware-level encryption from day one.
Democratize data: Use low-code AI platforms to empower non-technical teams.
The Final Byte We stand at an inflection point. Artificial Intelligence of Things isn’t merely connecting devices—it’s weaving an intelligent fabric across our physical reality. From farms that whisper their needs to algorithms, to factories that self-heal, to cities that breathe efficiently, AIoT transforms data into wisdom.
The question isn’t��if this revolution will impact your organization—it’s when. Companies leveraging AIoT integration today aren’t just future-proofing; they’re rewriting industry rulebooks. At widedevsolution.com, we turn convergence into competitive advantage. The machines are learning. The sensors are watching. The future is responding.
“The greatest achievement of AIoT won’t be smarter gadgets—it’ll be fundamentally reimagining how humanity solves its hardest problems.” — widedevsolution.com AI Lab
#artificial intelligence#predictive maintenance#smart city solutions#manufacturing efficiency#AI-powered quality control in manufacturing#edge computing for IoT security#scalable IoT systems for agriculture#AIoT integration#sensor data intelligence#ML yield prediction#cyber-physical#widedevsolution.com
0 notes
Text
Beyond the Buzz: How IoT Redefines Business Operations

Moving from Hype to Reality
IoT has moved from being a futuristic idea to a practical solution that businesses use daily to improve operations and achieve sustainable growth. Though much of the discussion around IoT is about its potential, the real value that it presents is in how companies can use the technology to solve real-world problems.
Today, IoT is no longer a buzzword; it’s a necessity for any business looking to remain competitive and agile in a dynamic global environment. With its power to integrate devices, data, and processes, IoT helps businesses achieve efficiencies, improve customer satisfaction, and create new revenue streams. In this blog post, we explore how IoT is changing business operations across industries and what companies need to do to maximize its potential.
How Tudip Technologies Redefines IoT Solutions
Tudip Technologies empowers businesses with IoT solutions that tackle complex operational challenges and drive measurable outcomes.
Our Specialized Approach:
Edge Computing Integration: Enabling faster data processing closer to devices for real-time responsiveness.
IoT Ecosystem Design: Creating scalable ecosystems that adapt to changing business needs.
Sustainability-Focused Solutions: Tailoring IoT frameworks that align with environmental goals.
Example: Tudip partnered with a logistics provider to implement IoT-powered edge analytics, reducing data processing times by 60% and improving delivery accuracy across global operations.
Key Takeaways: Turning IoT Into Operational Strength
Invest in Scalable Solutions: Ensure your IoT systems can grow alongside your business needs.
Prioritize Security: Robust cybersecurity measures arToday, IoT is no longer a buzzword; it’s a necessity for any business looking to remain competitive and agile in a dynamic global environment. With its power to integrate devices, data, and processes, IoT helps businesses achieve efficiencies, improve customer satisfaction, and create new revenue streams. In this blog post, we explore how IoT is changing business operations across industries and what companies need to do to maximize its potential.
Redefining Operational Efficiency with IoT
1. Predictive Analytics: Smarter Urban Operations with IoT
IoT is revolutionizing energy management by integrating renewable energy sources into business operations. Smart systems analyze usage patterns and adjust power drawn from solar, wind, or traditional grids in real time.
Optimized Renewable Usage: IoT ensures renewable energy is used efficiently by monitoring supply-demand gaps.
Grid Stability: Balances energy loads to prevent outages during peak hours.
Sustainability Goals: Helps businesses achieve net-zero emissions by prioritizing clean energy consumption.
Example: A technology campus integrated IoT in optimizing its solar energy consumption and reduced dependence on traditional grids by 40%, with a significant reduction in operational costs
2. Energy Management: Advancing Renewable Solutions
Predictive analytics powered by IoT is transforming urban infrastructure. Cities can now monitor critical assets like bridges, roads, and utilities in real time, ensuring timely maintenance and preventing costly failures.
Public Safety: Early detection of infrastructure stress minimizes risks to citizens.
Cost Efficiency: Avoiding large-scale repairs reduces budget overruns for municipalities.
Sustainability: Proactive maintenance extends the lifespan of assets, reducing waste.
3. Automation Excellence: Better Disaster Response Logistics
IoT-driven automation is transforming how disaster response occurs—getting aid to where it is needed, faster and more efficiently.
Real-Time Inventory Management: Monitors relief inventory and ensures its proper distribution to areas of greatest need.
Smart Transportation: Optimizes routes for rescue and supply vehicles during crises.
Collaboration Across Agencies: IoT systems enable seamless communication between response teams.
Example:In a recent hurricane, one global aid organization leveraged IoT-connected drones to survey damage and automate the delivery of supplies, resulting in a 50% faster response time.
Overcoming Common IoT Challenges
1. Integration of IoT with Existing Systems
One of the biggest hurdles businesses face is integrating IoT solutions with legacy systems. Compatibility issues can hinder seamless data exchange and functionality. Solution: Use a flexible IoT platform with built-in interoperability; make sure it provides APIs for smooth integration. Careful planning and phased implementation may also reduce disruptions to a minimum.
2. Data Security and Privacy
IoT ecosystems are all about continuous data gathering and transmission, which increases exposure to cyber threats. The security of sensitive information is the foundation of trust with stakeholders.
Solution: Implement robust encryption protocols, regularly update security measures, and educate employees on cybersecurity best practices.
3. Adapting to Rapid Technological Changes
The rapid rate of innovation in IoT can make it challenging for businesses to adapt to new developments and keep their systems current. Solution: Collaborate with technology providers that offer scalable solutions and ongoing support to adapt to emerging trends without overhauling existing systems.
How IoT Drives Operational Transformation
1. Enhancing Decision-Making with Real-Time Insights
IoT provides companies with real-time data that enables informed decision-making. Whether it is revising supply chain strategies or optimizing production schedules, IoT ensures that companies can act quickly and confidently.
Dynamic Adaptability: Businesses can change their strategies according to up-to-date information and stay responsive to market demand.
Improved Collaboration: IoT systems enable better communication across departments, enabling coordinated efforts.
2. Creating Value Through Customization
IoT’s ability to collect granular data allows businesses to tailor their offerings and services to meet specific customer needs. Personalization not only enhances user experience but also builds stronger customer relationships.
e non-negotiable in today’s interconnected world.
Focus on Outcomes: Use IoT to achieve specific goals, whether it’s reducing costs, enhancing customer satisfaction, or achieving sustainability targets.
Conclusion: Moving Beyond the Buzz
IoT has evolved into an indispensable solution, reshaping how businesses optimize operations and achieve sustainable growth. By addressing real-world challenges and delivering actionable insights, IoT enables companies to stay competitive and adaptive.
To fully realize the benefits of IoT, businesses must focus on integrating flexible solutions, safeguarding data, and aligning technology with strategic objectives. With the right approach, IoT becomes more than a technological innovation—it becomes a cornerstone of operational excellence and sustainable growth.
Click the link below to learn more about the blog Beyond the Buzz: How IoT Redefines Business Operations
https://tudip.com/blog-post/beyond-the-buzz-how-iot-redefines-business-operations/
#Tudip#IoT#Internet of Things#business operations#predictive analytics#automation#real-time data#edge computing#smart infrastructure#energy management#renewable energy#sustainability#operational efficiency#cybersecurity#data security#interoperability#digital transformation#scalability#AI-driven insights#machine learning#supply chain optimization#disaster response#smart cities#industrial IoT#connected devices#enterprise IoT#cloud computing#IoT platforms#remote monitoring#predictive maintenance
0 notes
Text
#IoT architecture#IoT architecture layers#IoT layers#Edge computing in IoT#IoT data processing#IoT security#Legacy IoT
0 notes
Text
🌐 The Impact of Cloud Computing on Business Scalability and Innovation
Cloud computing has revolutionized the way businesses operate, providing scalable, on-demand access to IT resources without the need for costly hardware investments. With cloud solutions, companies can deploy applications, store and analyze data, and enhance collaboration in a secure, flexible environment. This article explores the transformative power of cloud computing, its benefits for…
#AI Integration#Business Continuity#Cloud Computing#Data security#Edge computing#IoT#SaaS#Scalability#Telecommunications
0 notes
Text
Streamline Network Performance with TCPWave’s DDI and ADC Solutions
Optimize your network with TCPWave’s integrated DDI (DNS, DHCP, IP Address Management) and Application Delivery Controller (ADC) solutions. Our advanced platform combines seamless automation, robust security, and real-time analytics to ensure efficient network operations and high application availability.
Our ADC solutions complement this by enhancing the availability, security, and performance of your applications. With advanced load balancing, traffic optimization, and SSL offloading, TCPWave’s ADCs ensure that your applications are always responsive, secure, and able to handle peak loads effortlessly.
0 notes
Text
What Should You Know About Edge Computing?
As technology continues to evolve, so do the ways in which data is processed, stored, and managed. One of the most transformative innovations in this space is edge computing. But what should you know about edge computing? This technology shifts data processing closer to the source, reducing latency and improving efficiency, particularly in environments where immediate action or analysis is…
#5G#AI#AI edge#AI integration#automation#autonomous vehicles#bandwidth#cloud#cloud infrastructure#cloud security#computing#computing power#data generation#data management#data processing#data storage#data transfer#decentralization#digital services#digital transformation#distributed computing#edge analytics#edge computing#edge devices#edge inferencing#edge networks#edge servers#enterprise data#Healthcare#hybrid cloud
0 notes
Text
Elevate Your Network Capabilities with Enterprise Network Edge and SD-WAN
In an era where connectivity and network efficiency are paramount, SolveForce is proud to introduce the Enterprise Network Edge with SD-WAN, powered by Spectrum Enterprise. This state-of-the-art solution is designed to optimize and secure your network operations across multiple sites, providing a seamless integration of various connectivity options under a unified system. Optimizing Your Network…
#Cloud Computing#Cost-Efficiency#Digital Transformation#Enterprise Network Edge#Managed Services#Network Scalability#Network Security#SD-WAN#SolveForce#Spectrum Enterprise
0 notes
Text
What are the security risks with edge computing?

Edge computing, while offering numerous benefits, also presents certain security risks that organizations need to be aware of. Here are some of the key security risks associated with edge computing:
Edge Security: One of the main concerns surrounding edge computing is the security of the architecture itself. IT teams often view edge computing as a potential threat to their organizations due to the unique security challenges it poses
Routing Information Attacks: Routing attacks can occur at the communication level of an edge network. These attacks interfere with the way data is transferred within the network, potentially affecting throughput, latency, and data paths
Distributed Denial of Service (DDoS) Attacks: Edge computing can be vulnerable to DDoS attacks, where an existing network resource is overwhelmed with traffic from compromised resources within the network. These attacks can disrupt the availability and performance of edge computing systems
Cybersecurity Concerns: Edge computing introduces new cybersecurity challenges, especially when combined with cloud computing. Risks include the use of specialized Machine-to-Machine (M2M) protocols that may lack sophisticated security features, wireless interfaces like Wi-Fi that can be subject to hacking, and dependence on specialized IoT devices that may have security vulnerabilities
Physical Security: Edge computing devices are not only at risk of digital attacks but also physical tampering. Protecting the physical security of edge devices becomes crucial, as compromising them can have serious consequences for data integrity and safety
To mitigate these risks, organizations should consider implementing the following measures:
Regular Testing and Remediation: Regularly test and remediate vulnerabilities in edge computing systems to ensure that security measures remain up to date
Encryption and Access Control: Implement encryption of data both at rest and in transit, change default passwords, and maintain control through centralized management dashboards
Unified Security Management: Maintain a unified approach to security management across all edge devices, ensuring regular updates and adherence to security protocols
Standardization and Best Practices: Promote standardization of secure architectures and system configurations for edge computing, and follow best practices recommended by industry organizations
While edge computing brings numerous benefits, organizations must be proactive in addressing the security risks associated with this technology. By implementing robust security measures and staying vigilant, organizations can leverage the advantages of edge computing while safeguarding their data and systems.
0 notes
Text
2024's Game-Changing Technologies for Metaverse Development

Picture a universe where virtual and physical worlds blend seamlessly, allowing you to interact with digital elements in real-time. As 2024 draws near, groundbreaking technologies are shaping this metaverse, making such interactions more immersive and dynamic than ever.
The metaverse, an expansive network of virtual environments, is evolving rapidly as we approach 2024, driven by several key technologies. Virtual Reality (VR) and Augmented Reality (AR) are at the forefront, enabling immersive experiences that blend the physical and digital worlds. VR technology has advanced significantly, offering users enhanced graphics, realistic simulations, and responsive feedback that create fully immersive digital environments.
AR enhances the physical world by overlaying digital information, enriching experiences in retail, healthcare, and entertainment through interactive and engaging environments.
Blockchain technology is essential for the metaverse, providing a secure and transparent method for managing digital assets and transactions. Non-fungible tokens (NFTs) allow users to own unique digital assets like virtual real estate and art, while smart contracts facilitate automated and secure transactions. The decentralized nature of blockchain promotes trust and reliability, making it a crucial component of the metaverse's infrastructure.
Artificial Intelligence (AI) further enhances user experiences by creating intelligent virtual agents, personalized interactions, and realistic simulations. AI-driven non-player characters (NPCs) provide engaging and adaptive experiences, and AI technologies enable natural language processing and speech recognition for seamless communication between users and virtual environments.
Edge computing and 5G technology are critical for the seamless operation of the metaverse. By bringing data processing closer to users, edge computing reduces latency and improves the responsiveness of virtual environments. 5G networks provide the high-speed internet required for real-time interactions, supporting scalable and complex virtual environments.
The Internet of Things (IoT) and spatial computing further enhance the metaverse by capturing physical movements and translating them into virtual actions, creating realistic and immersive experiences.
Elevate your business with Intelisync's cutting-edge metaverse solutions. Reach out to Intelisync today and learn how our advanced technologies in VR, AR, AI, and blockchain can revolutionize your operations, enhance customer engagement, and drive your Learn more...
#AI-driven NPCs#AR/VR for interactive product experiences#Artificial Intelligence (AI)#Augmented Reality (AR)#Blockchain#blockchain for secure transactions#Blockchain Technology#Edge Computing and 5G Technology#How Intelisync Uses this Technology for Growing Client Business#Increase in Engagement#Intelisync’s Metaverse Solution for Retail Business#Internet of Things (IoT) and Spatial Computing#IoT devices#Market Expansion#Metaverse Development#Metaverse development company#metaverse game development#Operational Efficiency#Personalization with AI#Sales Growth#Secure Transactions with Blockchain#smart contracts#social VR platforms and games.#Top 5 Technologies for Metaverse Development in 2024#Virtual Reality (VR)#Virtual Reality (VR) and Augmented Reality (AR)#Virtual Showroom#What is the Metaverse?
0 notes
Text
Emerging Tech Trends in the Internet of Things (IoT)
Introduction
The Internet of Things (IoT) is transforming our world by connecting devices and enabling smarter, more efficient interactions. In everything from smart homes to industrial automation, the IoT is leading a revolution in our living and working environments. In this article, TechtoIO explores the emerging tech trends in IoT, highlighting the innovations and advancements that are shaping the future. Read to continue link
#Innovation Insights#Tags5G IoT#AI in IoT#autonomous vehicles IoT#big data IoT#edge computing IoT#future of IoT#IIoT#industrial IoT#Internet of Things#IoT data analytics#IoT healthcare#IoT innovations#IoT security#IoT technology#IoT trends#smart cities IoT#smart homes#wearable IoT#Technology#Science#business tech#Adobe cloud#Trends#Nvidia Drive#Analysis#Tech news#Science updates#Digital advancements#Tech trends
1 note
·
View note
Text
Cutting-Edge Network Services by Fusion Dynamics
Discover the future of networking with cutting-edge network services from Fusion Dynamics.
Specializing in innovative solutions that enhance connectivity and performance, Fusion Dynamics provides tailored services to meet the needs of modern businesses.

Fusion Dynamics is an IT infrastructure pioneer providing cutting-edge computing and data center solutions to various industries. Our team has conceptualized, designed, and deployed transformational digital infrastructure for a diverse set of organisations, with custom solutions tailormade for their unique requirements and challenges.
Discover top-notch services on cloud computing with Fusion Dynamics. From cloud migration and management to customized solutions, Fusion Dynamics offers scalable and secure cloud services that align with your business needs.
Optimize your infrastructure and enhance efficiency with our expert cloud computing solutions.
Why Choose Us
We bring a potent combination of over two decades of experience in IT solutions and a dynamic approach to continuously evolve with the latest data storage, computing, and networking technology. Our team constitutes domain experts who liaise with you throughout the end-to-end journey of setting up and operating an advanced data center.
With a profound understanding of modern digital requirements, backed by decades of industry experience, we work closely with your organisation to design the most efficient systems to catalyse innovation. From sourcing cutting-edge components from leading global technology providers to seamlessly integrating them for rapid deployment, we deliver state-of-the-art computing infrastructures to drive your growth!
Learn more about how we can transform your cloud strategy here: https://fusiondynamics.io
Contact Us
+91 95388 99792
Learn more about their services here: https://fusiondynamics.io.
#Keywords#services on cloud computing#edge network services#available cloud computing services#cloud computing based services#cooling solutions#hpc cluster management software#cloud backups for business#platform as a service vendors#edge computing services#Secondary Keyword#service provided by cloud computing#popular cloud computing services#the best cloud computing services#data center cooling#data centers cooling systems#server cooling system#server cooling solutions#advanced cooling systems for cloud computing#cloud workload protection#cloud workload security solutions#hpc clustering#hpc cluster manager#server cloud backups#paas cloud services#cloud services saas paas iaas#ipaas services#edge computing platform#edge computing solutions#cloud native technology
0 notes
Text
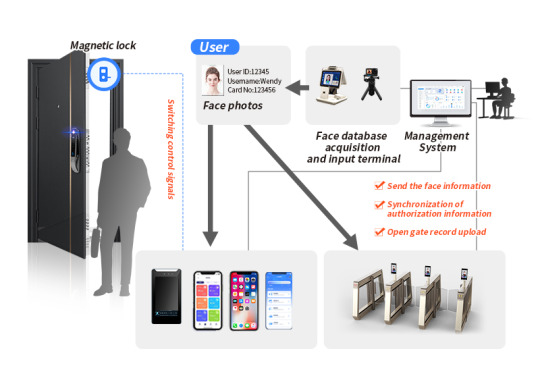
Solution of Edge Computing Access Control Screen Based on FET3568-C SoM
Edge Computing Access Screen is designed to provide an edge computing-based solution for access control systems. It can realize face recognition, data processing, fingerprint recognition and other functions, and improve the security and convenience of the access control system. In terms of application scenarios, intelligent monitoring and access control system is an important part of intelligent building security.
The application of edge computing technology can increase the monitoring effect and response speed, avoid the security risks in the process of data transmission, and protect the privacy of users. Edge computing devices can process authentication faster and improve the response speed and security of access control systems.
Hardware requirements for edge computing access control screen
(1) Processor
Select a high-performance and low-power embedded processor, the processor itself needs to come with arithmetic power to meet the needs of edge computing.
(2) Memory
Configure appropriate memory and flash for system and application data.
(3) Interface
Provide necessary interfaces between the carrier board and other devices, such as GPIO, UART, I2C, SPI, etc.
(4) Communication module
Support Wi-Fi or 4G to facilitate data transmission with the cloud platform.
(5) Sensor
Integrate multiple sensors, such as face recognition, fingerprint recognition, and RF card reader.
Edge Computing Access Control Screen Design
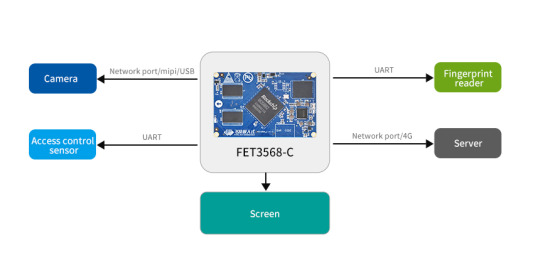
The FET3568-C SoM is recommended to be used as the hardware platform of edge computing access control screen. The system on module has a quad-core ARM Cortex-A55 processor with a main frequency of 2.0 GHz, and its own NPU has a computing power of 1TOPS, which can meet the needs of lightweight edge computing tasks.
Memory: FET3568-C SoM supports LPDDR4 and eMMC storage, and can be configured with appropriate memory and flash memory to meet the needs of the access control system.
Interface: Native GPIO, UART, I2C, SPI, Gigabit port, etc. can communicate with other lines.
Communication module: FET3568-C supports wireless communication technologies such as Wi-Fi, Bluetooth, and GPS. The appropriate communication module can be selected according to the requirements.
Sensors: FET3568-C supports multiple sensor interfaces, such as GPIO, I2C, SPI, etc., and can easily integrate multiple sensors, including face recognition, fingerprint recognition modules, etc.
Power supply module: According to the requirements of the access control system, the appropriate power supply chip can be selected to provide stable and reliable power supply for the entire carrier board.
Peripheral expansion: USB and SD card slots are convenient for secondary development and function expansion.
Originally published at www.forlinx.net.
0 notes
Text
Exciting developments in MLOps await in 2024! 🚀 DevOps-MLOps integration, AutoML acceleration, Edge Computing rise – shaping a dynamic future. Stay ahead of the curve! #MLOps #TechTrends2024 🤖✨
#MLOps#Machine Learning Operations#DevOps#AutoML#Automated Pipelines#Explainable AI#Edge Computing#Model Monitoring#Governance#Hybrid Cloud#Multi-Cloud Deployments#Security#Forecast#2024
0 notes
Text
10 Most important Technologies that IT Advisors use to Navigating the Future of Information Technology
Introduction as IT Advisors In the dynamic realm of Information Technology (IT), staying ahead requires a powerful arsenal of cutting-edge technologies. IT advisors, the guiding force behind digital transformations, leverage a spectrum of tools to optimize operations, enhance security, and propel their clients into the future. In this exploration, we’ll delve into the tech landscape that…

View On WordPress
#5G technology#AI and machine learning#automation#Blockchain#cloud computing#collaboration tools#connectivity#cybersecurity#data analytics#digital transformation#edge computing#information security#Internet of Things (IoT)#IT Advisors#IT infrastructure#predictive analysis#Robotic Process Automation (RPA)#Technologies#technology landscape#virtualization
1 note
·
View note