#Cybersecurity Challenges
Explore tagged Tumblr posts
Text
David Kellerman, CTO at Cymulate – Interview Series
New Post has been published on https://thedigitalinsider.com/david-kellerman-cto-at-cymulate-interview-series/
David Kellerman, CTO at Cymulate – Interview Series


David Kellerman is the Field CTO at Cymulate, and a senior technical customer-facing professional in the field of information and cyber security. David leads customers to success and high-security standards.
Cymulate is a cybersecurity company that provides continuous security validation through automated attack simulations. Its platform enables organizations to proactively test, assess, and optimize their security posture by simulating real-world cyber threats, including ransomware, phishing, and lateral movement attacks. By offering Breach and Attack Simulation (BAS), exposure management, and security posture management, Cymulate helps businesses identify vulnerabilities and improve their defenses in real time. What do you see as the primary driver behind the rise of AI-related cybersecurity threats in 2025?
AI-related cybersecurity threats are rising because of AI’s increased accessibility. Threat actors now have access to AI tools that can help them iterate on malware, craft more believable phishing emails, and upscale their attacks to increase their reach. These tactics aren’t “new,” but the speed and accuracy with which they are being deployed has added significantly to the already lengthy backlog of cyber threats security teams need to address. Organizations rush to implement AI technology, while not fully understanding that security controls need to be put around it, to ensure it isn’t easily exploited by threat actors.
Are there any specific industries or sectors more vulnerable to these AI-related threats, and why?
Industries that are consistently sharing data across channels between employees, clients, or customers are susceptible to AI-related threats because AI is making it easier for threat actors to engage in convincing social engineering schemes Phishing scams are effectively a numbers game, and if attackers can now send more authentic-seeming emails to a wider number of recipients, their success rate will increase significantly. Organizations that expose their AI-powered services to the public potentially invite attackers to try to exploit it. While it is an inherited risk of making services public, it is crucial to do it right.
What are the key vulnerabilities organizations face when using public LLMs for business functions?
Data leakage is probably the number one concern. When using a public large language model (LLM), it’s hard to say for sure where that data will go – and the last thing you want to do is accidentally upload sensitive information to a publicly accessible AI tool. If you need confidential data analyzed, keep it in-house. Don’t turn to public LLMs that may turn around and leak that data to the broader internet.
How can enterprises effectively secure sensitive data when testing or implementing AI systems in production?
When testing AI systems in production, organizations should adopt an offensive mindset (as opposed to a defensive one). By that I mean security teams should be proactively testing and validating the security of their AI systems, rather than reacting to incoming threats. Consistently monitoring for attacks and validating security systems can help to ensure sensitive data is protected and security solutions are working as intended.
How can organizations proactively defend against AI-driven attacks that are constantly evolving?
While threat actors are using AI to evolve their threats, security teams can also use AI to update their breach and attack simulation (BAS) tools to ensure they are safeguarded against emerging threats. Tools, like Cymulate’s daily threat feed, load the latest emerging threats into Cymulate’s breach and attack simulation software daily to ensure security teams are validating their organization’s cybersecurity against the most recent threats. AI can help automate processes like these, allowing organizations to remain agile and ready to face even the newest threats.
What role do automated security validation platforms, like Cymulate, play in mitigating the risks posed by AI-driven cyber threats?
Automated security validation platforms can help organizations stay on top of emerging AI-driven cyber threats through tools aimed at identifying, validating, and prioritizing threats. With AI serving as a force multiplier for attackers, it’s important to not just detect potential vulnerabilities in your network and systems, but validate which ones post an actual threat to the organization. Only then can exposures be effectively prioritized, allowing organizations to mitigate the most dangerous threats first before moving on to less pressing items. Attackers are using AI to probe digital environments for potential weaknesses before launching highly tailored attacks, which means the ability to address dangerous vulnerabilities in an automated and effective manner has never been more critical.
How can enterprises incorporate breach and attack simulation tools to prepare for AI-driven attacks?
BAS software is an important element of exposure management, allowing organizations to create real-world attack scenarios they can use to validate security controls against today’s most pressing threats. The latest threat intel and primary research from the Cymulate Threat Research Group (combined with information on emerging threats and new simulations) is applied daily to Cymulate’s BAS tool, alerting security leaders if a new threat was not blocked or detected by their existing security controls. With BAS, organizations can also tailor AI-driven simulations to their unique environments and security policies with an open framework to create and automate custom campaigns and advanced attack scenarios.
What are the top three recommendations you would give to security teams to stay ahead of these emerging threats?
Threats are becoming more complex every day. Organizations that don’t have an effective exposure management program in place risk falling dangerously behind, so my first recommendation would be to implement a solution that allows the organization to effectively prioritize their exposures. Next, ensure that the exposure management solution includes BAS capabilities that allow the security team to simulate emerging threats (AI and otherwise) to gauge how the organization’s security controls perform. Finally, I would recommend leveraging automation to ensure that validation and testing can happen on a continuous basis, not just during periodic reviews. With the threat landscape changing on a minute-to-minute basis, it’s critical to have up-to-date information. Threat data from last quarter is already hopelessly obsolete.
What developments in AI technology do you foresee in the next five years that could either exacerbate or mitigate cybersecurity risks?
A lot will depend upon how accessible AI continues to be. Today, low-level attackers can use AI capabilities to uplevel and upscale their attacks, but they aren’t creating new, unprecedented tactics – they’re just making existing tactics more effective. Right now, we can (mostly) compensate for that. But if AI continues to grow more advanced and remains highly accessible, that could change. Regulations will play a role here – the EU (and, to a lesser extent, the US) have taken steps to govern how AI is developed and used, so it will be interesting to see whether that has an effect on AI development.
Do you anticipate a shift in how organizations prioritize AI-related cybersecurity threats compared to traditional cybersecurity challenges?
We’re already seeing organizations recognize the value of solutions like BAS and exposure management. AI is allowing threat actors to quickly launch advanced, targeted campaigns, and security teams need any advantage they can get to help stay ahead of them. Organizations that are using validation tools will have a significantly easier time keeping their heads above water by prioritizing and mitigating the most pressing and dangerous threats first. Remember, most attackers are looking for an easy score. You may not be able to stop every attack, but you can avoid making yourself an easy target.
Thank you for the great interview, readers who wish to learn more should visit Cymulate.
#2025#Accessibility#agile#ai#AI development#AI systems#AI technology#ai tools#AI-powered#attackers#automation#backlog#breach#Business#change#continuous#craft#CTO#cyber#cyber security#Cyber Threats#cybersecurity#cybersecurity challenges#cybersecurity threats#Cymulate#data#data leakage#defenses#development#Developments
0 notes
Text
What is the SMTP ports should be used
Simple Mail Transfer Protocol (SMTP) is a protocol used to send emails. It is a standard protocol that is used by most email servers. SMTP uses port 25 by default. However, there are other ports that can be used for SMTP.
What is the SMTP ports? Simple Mail Transfer Protocol (SMTP) is a protocol used to send emails. It is a standard protocol that is used by most email servers. SMTP uses port 25 by default. However, there are other ports that can be used for SMTP. What are the other SMTP ports? The most common alternative SMTP port is port 587. This port is used by many email providers, including Gmail, Yahoo,…
0 notes
Text
Beyond Change Healthcare
The continued onslaught of cybersecurity attacks which if anything are only getting worse have impacted the healthcare system in dramatic fashion with the payment network brought down by the attack on Change Healthcare. Healthcare under Cyber Attack I keep hoping that we all get better at combatting these attempts to breach our data and that overall vigilance rises as we become more wary of…

View On WordPress
#cyber attacks#cyber awareness#cyber defense#cyber hygiene#cyber resilience#cyber safety#cyber threats#CyberCrime#Cybersecurity#cybersecurity awareness#cybersecurity best practices#cybersecurity challenges#cybersecurity culture#cybersecurity education#cybersecurity measures#cybersecurity news#cybersecurity protocols#cybersecurity resources#cybersecurity risks#cybersecurity solutions#cybersecurity strategy#cybersecurity tips#cybersecurity training#cybersecurity trends#data breach#data encryption#data protection#data security#Digital Health#Healthcare
0 notes
Text
Cyber Security Challenges And Emerging Trends 2023
The importance of cyber security cannot be emphasized in today s digitally connected society As technology progresses and our reliance
0 notes
Text

An Introduction to Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
What is cybersecurity?
Cybersecurity is all about securing technology and processes - making sure that the software, hardware, and networks that run the world do exactly what they need to do and can't be abused by bad actors.
The CIA triad is a concept used to explain the three goals of cybersecurity. The pieces are:
Confidentiality: ensuring that information is kept secret, so it can only be viewed by the people who are allowed to do so. This involves encrypting data, requiring authentication before viewing data, and more.
Integrity: ensuring that information is trustworthy and cannot be tampered with. For example, this involves making sure that no one changes the contents of the file you're trying to download or intercepts your text messages.
Availability: ensuring that the services you need are there when you need them. Blocking every single person from accessing a piece of valuable information would be secure, but completely unusable, so we have to think about availability. This can also mean blocking DDoS attacks or fixing flaws in software that cause crashes or service issues.
What are some specializations within cybersecurity? What do cybersecurity professionals do?
incident response
digital forensics (often combined with incident response in the acronym DFIR)
reverse engineering
cryptography
governance/compliance/risk management
penetration testing/ethical hacking
vulnerability research/bug bounty
threat intelligence
cloud security
industrial/IoT security, often called Operational Technology (OT)
security engineering/writing code for cybersecurity tools (this is what I do!)
and more!
Where do cybersecurity professionals work?
I view the industry in three big chunks: vendors, everyday companies (for lack of a better term), and government. It's more complicated than that, but it helps.
Vendors make and sell security tools or services to other companies. Some examples are Crowdstrike, Cisco, Microsoft, Palo Alto, EY, etc. Vendors can be giant multinational corporations or small startups. Security tools can include software and hardware, while services can include consulting, technical support, or incident response or digital forensics services. Some companies are Managed Security Service Providers (MSSPs), which means that they serve as the security team for many other (often small) businesses.
Everyday companies include everyone from giant companies like Coca-Cola to the mom and pop shop down the street. Every company is a tech company now, and someone has to be in charge of securing things. Some businesses will have their own internal security teams that respond to incidents. Many companies buy tools provided by vendors like the ones above, and someone has to manage them. Small companies with small tech departments might dump all cybersecurity responsibilities on the IT team (or outsource things to a MSSP), or larger ones may have a dedicated security staff.
Government cybersecurity work can involve a lot of things, from securing the local water supply to working for the big three letter agencies. In the U.S. at least, there are also a lot of government contractors, who are their own individual companies but the vast majority of what they do is for the government. MITRE is one example, and the federal research labs and some university-affiliated labs are an extension of this. Government work and military contractor work are where geopolitics and ethics come into play most clearly, so just… be mindful.
What do academics in cybersecurity research?
A wide variety of things! You can get a good idea by browsing the papers from the ACM's Computer and Communications Security Conference. Some of the big research areas that I'm aware of are:
cryptography & post-quantum cryptography
machine learning model security & alignment
formal proofs of a program & programming language security
security & privacy
security of network protocols
vulnerability research & developing new attack vectors
Cybersecurity seems niche at first, but it actually covers a huge range of topics all across technology and policy. It's vital to running the world today, and I'm obviously biased but I think it's a fascinating topic to learn about. I'll be posting a new cybersecurity masterpost each day this week as a part of the #StudyblrMasterpostJam, so keep an eye out for tomorrow's post! In the meantime, check out the tag and see what other folks are posting about :D
#studyblrmasterpostjam#studyblr#cybersecurity#masterpost#ref#I love that this challenge is just a reason for people to talk about their passions and I'm so excited to read what everyone posts!
47 notes
·
View notes
Text
Day 3: We've found another income stream 💸💸💸
So I found new abundance affirmations by Kinder Records on Apple Music.
I listened to them all morning and then on the way out of the house I got an idea for a second income stream.
I'll tell yall about it in a few weeks once I get the ropes all in place but I'm really excited. I got the same feeling I got about Ladder and Safer Internet Project. I'm really good at picking valuable and efficient resources and guide me to a better life.
As for my IT Business. I'm still making strategic moves to get that rolling as well. I'm so proud of myself for staying diligent this time around.
(Stay away from people who don't have the same drive as you. They will drag you down. Take it from me. Someone with a lot of personal experience dealing with people not aligned with me energetically)
Ladder: https://ladder.fit/empress SIP: https://learn.saferinternetproject.com/?affcode=1349743_h_62dxyh
#fyp#thoughts#women in business#digital security#cybersecurity#neville goddard#manifesting#blogging#tech blog#30 Day ITSec Business Challenge#business
4 notes
·
View notes
Text
Top 10 Challenges in CSO Recruitment and How to Overcome Them

The appointment of a Chief Security Officer (CSO) has become a strategic priority in the current complex digital world for organizations of all sizes. The traditional view of the CSO as just a gatekeeper to cybersecurity has changed to an integrated view encompassing risk management, regulatory compliance, and overall resilience of the organization. The whole CSO recruitment process is also challenging, from a shortage of skills to changing expectations of what a CSO is expected to do; companies should confront them directly.
This blog will delve into the top 10 challenges in recruiting CSOs and how these could be addressed with the aid of a trusted partner like Alliance Recruitment Agency.
1. Limited Talent Pool of Qualified CSOs
CSOs typically have a very unique combination of technical skills, leadership, and strategic vision. The growing demand from across industries is driving the major repertory of talent thin.
Solution: Broaden your search geographically and consider candidates with adjacent experience. A specialized executive recruitment agency can tap into hidden networks and global talent pools.
2. Evolving Role Expectations
Today’s CSOs must oversee not only cybersecurity but also physical security, data governance, and risk strategy. This broad scope makes recruitment more complex.
Solution: Define the role based on your organization’s risk landscape. Alliance Recruitment Agency works with clients to align role definitions with industry trends and future-proofing needs.
3. High Salary Expectations
Competitive compensation is offered to CSOs who have been in the field for some time due to the critical nature of their role and the scarcity of their availability.
Solution: might be to compare compensation with industry standards and offer more benefits — such as tax benefits, shares in the company, or flexible working opportunities. A recruitment partner will come in handy to formulate packages that are competitive but sustainable.
4. Cultural Fit Concerns
A CSO is required to communicate across departments, from IT to HR to legal. Hiring for cultural fit is very crucial; however, it is very difficult to assess.
Solution: Soft skill assessments and team compatibility should be assessed through behavioral interviews and references. This is where agencies that have served their clients over some time can help place candidates suitable for your organizational culture.
5. Lack of Industry-Specific Experience
A lot of these CSO roles require an in-depth understanding of the threats and regulations specific to the industry: finance, health care, or manufacturing.
Solution: Place priority on experience in regulated areas. Alliance Recruitment Agency specializes in targeted recruitment for sector-specific CSO roles.
6. Overreliance on Internal HR Teams
Internal Human Resources groups may not possess the bandwidth or skill sets required for hyper-specialization into notoriously hard-to-fill executive CSO roles.
Solution: An executive search firm for CSOs with identifiable experience will speed time and accuracy in filling roles, thereby mitigating time wastage and minimizing associated risks.
7. Prolonged Hiring Cycles
The longer it takes to fill a CSO position, the greater the risk exposure for your organization.
Solution: Streamline decision-making and keep candidates engaged. Recruitment partners can accelerate shortlisting, vetting, and negotiations to close faster.
8. Difficulty in Assessing Technical Competence
CSOs must have deep technical knowledge, but most hiring managers are not qualified to evaluate their security acumen.
Solution: Use third-party assessments or bring in security consultants during interviews. Alliance Recruitment Agency incorporates technical vetting to ensure candidates meet all requirements.
9. Misalignment Between Expectations and Reality
Sometimes, organizations expect a “superhero” who can handle every aspect of security without support.
Solution: Use an approach of data-driven and strategic hiring that addresses long-term deviations through the reduction of expensive turnover.
10. High Turnover Rates
Hiring the wrong CSO can lead to early exits and long-term damage to your company’s security posture.
Solution: Approaching the hiring with determination and data is an important strategy. With a long-term strategy, the agency focuses on the fit and retention of candidates while significantly reducing the high costs of turnover.
Conclusion:
Recruiting a Chief Security Officer is among the most pressing appointments for a company. There are many barriers to recruiting a CSO, but they are not insurmountable. With a specialized partner such as Alliance Recruitment Agency, you will be able to cross the executive security hiring terrain with ease.
Whether seeking your first CSO or replacing one who is leaving, our team carries the industry knowledge, global reach, and recruitment tools to deliver world-class security leadership.
Are you ready to find the right CSO for your company?
Partner with Alliance Recruitment Agency — your strategic CSO recruitment specialist. Contact us today for the recruitment of exceptional security leadership.
FAQs:
1. A CSO is an abbreviation for Chief Security Officer. Why is hiring such an officer critical to my organization?
Ans: CSO is the abbreviation for Chief Security Officer, who is responsible for the overall strategy of the different aspects of security management, including information security, physical security, and risk management within an organization. Apart from the protection of data, assets, and people, hiring a CSO is vital for any organization, given how things ever could be today in a threat-heavy environment.
2. What are the qualifications I should seek when looking for a CSO?
Ans: Search for an apt candidate with extensive experience in leading security, coupled with much strength in risk management, cybersecurity frameworks, regulatory compliance, and crisis response. Soft skills in communication, leadership, and strategic thinking are also very important. A CSO should have business goals that would conform to the requirements of one industry in specific.
3. How long does the process typically take to find a CSO?
Ans: The timelines change based on requirements and the difficulty in roles, although on an average basis; CSO hiring may take between 6 and 12 weeks. At Alliance Recruitment Agency, the process gets faster with global talent and pre-vetted candidates reducing time-to-hire significantly.
4. What are the challenges commonly faced by organizations in hiring a CSO?
Ans: Some of the top challenges include a limited pool of talent, elevated monetary requirements, cultural fit assessments, and undefined role expectations. By working with a specialized CSO recruitment agency like Alliance Recruitment Agency, though, these problems are solved using targeted searches as well as expert evaluations.
5. Why should I give preference to Alliance Recruitment Agency for hiring a CSO?
Ans: Alliance Recruitment Agency has an impressive history of executive security recruitment, providing access to global CSO candidates and industry-wide expertise. We ensure fast turnaround and personalized support to make sure every candidate fits your company's unique goals and risk profile.
View Source:
#CSO recruitment#Chief Security Officer hiring#CSO recruitment agency#Executive security recruitment#Security leadership roles#Alliance Recruitment Agency#Hiring a CSO#CSO hiring challenges#Cybersecurity executive search
0 notes
Text
In the age of AI, authentication shouldn't be a static barrier; it should be an intelligent, adaptive, and engaging experience. Within @leonbasinwriter Intelligence Singularity, access is not simply granted—it's earned through a dynamic interplay with AI itself.
#adaptive authentication#ai#AI Security#AI security authentication system access control#AI-driven authentication#Artificial Intelligence#authentication challenge#chatgpt#Claude#cybersecurity project#digital-marketing#Express.js#intelligence singularity#Javascript#LLM#multi-layered authentication#nft#Node.js#OpenAI#passwordless authentication#portfolio project#prompt engineering#proof of concept#research project#technology#user experience#web security#Web3#zero-trust security
0 notes
Text
AI Trends: Unlocking the Impact & Potential of AI.
Sanjay Kumar Mohindroo Sanjay Kumar Mohindroo. skm.stayingalive.in Discover AI trends and unlock their transformative potential with insights on adoption, data privacy, local deployments, and company-wide integration. In today’s rapidly evolving digital era, artificial intelligence is not merely an abstract concept relegated to the pages of science fiction but a transformative force that is…
#AI adoption#AI Challenges#AI Integration#AI Strategies#AI Trends#Artificial intelligence#Business Innovation#Cloud AI#Company-Wide AI#Cybersecurity#Data Privacy#digital transformation#Early Adopters#Local AI Deployments#News#Sanjay Kumar Mohindroo#Technology Investments
0 notes
Text
Addressing Modern Threats: The Multifaceted Challenges Facing the USA
By, WPS News Staff Baybay City | February 3, 2025 As we navigate the complex landscape of the 21st century, the United States faces a series of profound and interconnected threats that require vigilant attention and strategic action. Each challenge is intricate in its own right, yet all share common themes of vulnerability and resilience. Understanding these threats in their full context is…
#china#Climate Change#cybersecurity#Domestic Extremism#economic inequality#Environmental Challenges#Geopolitical tensions#International Cooperation#national security#pandemic preparedness#Policy Reform#Public Engagement#public safety#russia#social unrest
0 notes
Text
At M.Kumarasamy College of Engineering (MKCE), we emphasize the significance of engineering ethics in shaping responsible engineers. Engineering ethics guide decision-making, foster professionalism, and ensure societal welfare. Our curriculum integrates these principles, teaching students to consider the long-term impacts of their work. Students are trained in truthfulness, transparency, and ethical communication, while also prioritizing public safety and environmental sustainability. We focus on risk management and encourage innovation in sustainable technologies. Our programs also address contemporary challenges like artificial intelligence and cybersecurity, preparing students to tackle these with ethical responsibility. MKCE nurtures future engineers who lead with integrity and contribute to society’s well-being.
To know more : https://mkce.ac.in/blog/engineering-ethics-and-navigating-the-challenges-of-modern-technologies/
#mkce college#top 10 colleges in tn#engineering college in karur#best engineering college in karur#private college#libary#mkce#best engineering college#mkce.ac.in#engineering college#• Engineering Ethics#Engineering Decision Making#AI and Ethics#Cybersecurity Ethics#Public Safety in Engineering#• Environmental Sustainability in Engineering#Professional Responsibility#Risk Management in Engineering#Artificial Intelligence Challenges#Engineering Leadership#• Data Privacy and Security#Ethical Engineering Practices#Sustainable Engineering Solutions#• Technological Innovation and Ethics#Technological Innovation and Ethics#MKCE Engineering Curriculum#• Social Responsibility in Engineering#• Engineering Ethics in AI#Workplace Ethics in Engineering#Collaboration in Engineering Projects
0 notes
Text
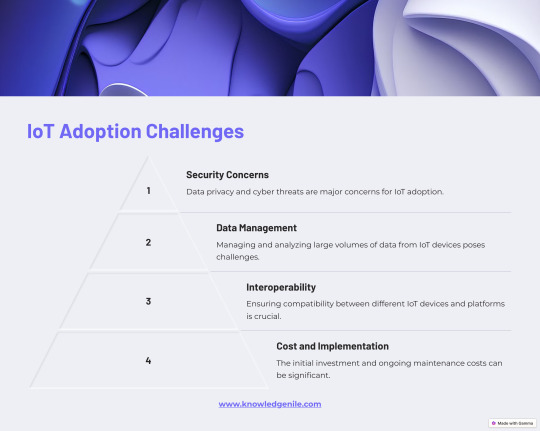
IoT Adoption Challenges: Security, Interoperability, and Costs Explained
While IoT holds transformative potential, several challenges hinder its widespread adoption. Security concerns, including data privacy and cyber threats, are critical issues. Managing and analyzing the vast amounts of data generated by IoT devices adds another layer of complexity. Additionally, ensuring interoperability between various devices and platforms remains a pressing challenge. High implementation costs and ongoing maintenance further complicate IoT adoption.
Learn how businesses can navigate these obstacles and unlock IoT’s full potential in our comprehensive blog on KnowledgeNile.
#IoT Adoption#IoT Challenges#Cybersecurity#IoT Costs#Data Privacy#Interoperability#IoT Trends#KnowledgeNile
0 notes
Text
Frequently Asked Questions on CISM Certification
The Certified Information Security Manager (CISM) certification, offered by ISACA, is one of the most sought-after credentials in the information security domain. It validates an individual’s expertise in managing and governing an organization’s security program. Whether you’re an aspiring CISM professional or exploring the idea of certification, this article addresses some of the most frequently asked questions about CISM.

1. What is the CISM Certification?
CISM (Certified Information Security Manager) is a globally recognized certification designed for professionals who manage enterprise information security programs. Unlike certifications that focus on technical aspects, CISM emphasizes risk management, governance, and aligning security with business goals.
2. Who Should Pursue CISM?
CISM is ideal for:
Information security managers
Aspiring IT security professionals
IT consultants focused on security
Risk management and compliance specialists
3. What Are the Prerequisites for CISM?
To earn the CISM certification, you must meet the following criteria:
Pass the CISM exam.
Have at least five years of work experience in information security management.
Experience must be across three or more CISM domains, with a waiver of up to two years available for certain qualifications or certifications (e.g., CISSP, CISA, or a related degree).
4. What Are the CISM Domains?
The CISM certification exam is divided into four domains:
Information Security Governance (17%) stablishing and managing the security strategy.
Information Risk Management (20%) Identifying and mitigating risks.
Information Security Program Development and Management (33%) Designing and managing the organization’s security program.
Information Security Incident Management (30%) Preparing for and responding to security incidents.
5. How Do I Register for the CISM Exam?
To register:
Visit ISACA’s official website.
Create an account if you don’t already have one.
Schedule the exam at a convenient time and location through ISACA’s partner test centers.
Pay the exam fee: $575 for ISACA members and $760 for non-members (subject to change).
6. What Is the Format of the CISM Exam?
The CISM exam consists of:
150 multiple-choice questions
A four-hour time limit
Questions that evaluate knowledge across the four domains
A scaled score ranging from 200 to 800, with 450 as the passing mark
7. How Can I Prepare for the CISM Exam?
Preparation tips include:
Study the CISM Review Manual: ISACA’s official manual is an essential resource.
Practice Questions: Use ISACA’s question database for realistic practice.
Attend Training Programs: Enroll in instructor-led or online courses offered by training providers like NovelVista, Simplilearn, or ISACA.
Join Study Groups: Leverage forums and communities to share insights and tips.
Time Management: Practice under timed conditions to simulate the exam environment.
8. What Is the Cost of the CISM Certification?
The total cost includes:
Exam registration fees ($575-$760)
Study materials (varies by provider)
Optional training programs (cost depends on the mode and duration)
9. What Are the Benefits of CISM Certification?
Global Recognition: CISM is respected worldwide as a premier security management certification.
Higher Earning Potential: Certified professionals often command higher salaries.
Career Advancement: Opens doors to leadership roles in IT security.
Improved Knowledge: Enhances your understanding of aligning security with business objectives.
10. How Long Is the Certification Valid?
CISM certification is valid for three years. To maintain it, you must:
Earn 120 Continuing Professional Education (CPE) credits during the three years.
Pay an annual maintenance fee of $45 for ISACA members or $85 for non-members.
11. What Jobs Can I Get with a CISM Certification?
CISM-certified professionals are qualified for roles such as:
Information Security Manager
IT Risk Manager
Security Consultant
Chief Information Security Officer (CISO)
12. How Does CISM Compare to CISSP?
Both certifications are highly respected, but they serve different purposes:
CISM focuses on management, governance, and aligning security strategies with business goals.
CISSP emphasizes technical expertise and security practices. Your choice depends on whether you aspire to management (CISM) or technical (CISSP) roles.
13. What Are Common Challenges in CISM Preparation?
Some challenges include:
Balancing study time with work responsibilities
Understanding managerial concepts if your background is technical
Staying updated on evolving security standards
14. Are There Any Alternatives to CISM?
Yes, alternatives include:
CISSP (Certified Information Systems Security Professional)
CISA (Certified Information Systems Auditor)
CRISC (Certified in Risk and Information Systems Control)
ISO 27001 Lead Implementer
In conclusion, the CISM certification and CISM Training is a valuable credential for professionals aiming to excel in information security management. By addressing these frequently asked questions, we hope you gain a clearer understanding of what it takes to achieve this milestone and how it can advance your career.
#CISM Certification#CISM Course#CISM Training#CISM#CISM Certified Professionals#CISM FAQ#Frequently Asked Questions#Cybersecurity#Security Challenges
0 notes
Text
OT Security: The Achilles’Heel for Manufacturing.

In an era where digital transformation is reshaping industries, the manufacturing sector faces a unique set of cybersecurity challenges. As manufacturers increasingly integrate advanced technologies into their operations, the convergence of Operational Technology (OT) and Information Technology (IT) introduces both opportunities and vulnerabilities. This blend of legacy systems with modern innovations has made cybersecurity a critical concern, as the sector grapples with complex threats ranging from ransomware attacks to supply chain vulnerabilities.
ALSO READ MORE- https://apacnewsnetwork.com/2024/07/ot-security-the-achillesheel-for-manufacturing/
#A Critical Examination of OT Security Challenges#AGM-IT and CISO#Alok Shankar Pandey#Alok Shankar Pandey AGM-IT and CISO Dedicated Freight Corridor Corporation of India#Amarish Kumar Singh#Amarish Kumar Singh CISO Godrej#Apollo Tyres#Baidyanath Kumar Chief Data Protection Officer JK Lakshmi Cement#Boyce Manufacturing#CISO Godrej#cybersecurity leaders#Dedicated Freight Corridor Corporation of India#Head of Global Cybersecurity#IT systems#Mansi Thapar Head of Global Cybersecurity Apollo Tyres#Mansi Thaper#OT Security#Sanjay Sharma Head of IT Infrastructure and Cybersecurity Shram Pistons#Sudipto Biswas CISO Emami#The Achilles’Heel for Manufacturing#Top cybersecurity leaders#Top cybersecurity leaders India#Top cybersecurity leaders of India
0 notes
Text
Electricity: An In-Depth Look at Why System Collapses Persist
The reliability and stability of electricity systems have become increasingly important as societies rely more on consistent power for everything from household appliances to critical infrastructure. However, despite advancements in technology and infrastructure, electricity systems continue to experience collapses that disrupt daily life and economic activities. This investigation delves into…
#aging infrastructure#cybersecurity threats#electricity systems#energy demand#grid failures#natural disasters#power grid resilience#power grid stability#regulatory challenges#renewable energy challenges#Touchaheart.com.ng
0 notes
Text
Day 1: Maintaining the Feeling of Being a Successful Business Owner
I've decided to start blogging again and I thought it would be great to start it today on the 11/11 portal. Today is a very powerful day for manifesting and I wanted to just have fun starting another daily challenge of keeping myself disciplined.
I did a 30 day BBL challenge two years ago to build my dream body (view the #me or #fitness hashtags to see what I'm talking about if you haven't already. I love what I've built physically but also mentally and emotionally. I'm more confident in myself, love myself so much more, and I hold myself to a higher standard than I have before starting that challenge.
So now I want to start a new 30 day challenge of blogging how I'm building the discipline to be successful IT Security business owner. I have been working on this for years but always fell back into doubt and fear. I think now that I'm single and I don't have anyone around me distracting me or trying to destiny swap with me I have all of my energy and power back to go full throttle. I also want to see where my confidence is by December 11.
I built an unshakable discipline for going to the gym now I can't miss a day or I feel like shit. Now I'm even walking more during the day to close all of my fitness rings on my Apple Watch. I want to get to the point in my business where I can't go a day without making an informational post for digital security across social media, expanding my knowledge in the field, and providing my clients with the best security solutions possible.
What I Worked on Today: - Building out pricing matrices for all of my services to ensure I'm making at least $10K/month - Some cloud storage filing for my first client since starting the IT Security Consulting side of my business (I've done career consulting before but slowly phased out of that because it wasn't fulfilling for me) - Joined some Facebook infosec groups as well as did some branding on TikTok for my business
What I Learned Today: - Taking aligned action is everything. Doesn't matter if it's perfect (Which has been a setback for me in the past. Trying to make sure everything is perfect instead of just creating/doing) - Keeping an abundant and positive mindset will take you far. Ever since I've decided to work on myself and become a more improved version of Empress/Tailor I have decided to let go of so many limiting beliefs. Not just in business but in money, love, and intellect. - Neville Goddard and taking frequent breaks keeps me motivated. I realized that when I'm sitting down for too long I tend to get restless and can't focus as well. Taking frequent walks and having Neville in my ear telling me to keep my thoughts aligned is why we're even here blogging because I've wanted to get back to this for a while tbh
Motivation: - Today being 11/11 and just feeling like a brand new woman. I almost slept in this morning but I hacked my brain to shut tf up and forced myself to get up and go to the gym. Multimillionaire me gets her ass up and goes to that gym at 5AM everyday unless something comes up and I can't make it. If I can't make it I'm getting atleast 10K steps in - Knowing that my reality right now is literally just a product of old thought patterns and everything I'm thinking and feeling now will produce in my 3D reality because it's law - Seeing reality literally bend to my will as I stay in the end state. At this point I'm just having fun and playing this shit like a video game.
Challenges I'm Facing: - I am quickly learning to tell my conscious mind to stfu and stop trying to tell me a plan B. There is no plan B. Everything is working out for plan A. We're literally right back to plan A after years of having plan b's and c's.
Milestones and Progess: - I had two consultations scheduled today! I can't wait to work with them and start their projects - I'm blogging on Tumblr again! Eventually it will be back on a website I'm running - I completed 95% of the tasks on my to-do list. Before I was only completing about 45%. This was also after I told chatgpt to give me a more aligned focused work schedule so I know how to curate my tasks for everyday so I'm making more aligned progress.
Well that's all I got for tonight. It's 9:17PM and another one of the things 3.0 version of myself does is get to bed before 10PM and gets off social media at this time. I want to be more intentional with my time and make sure I'm getting more sleep as well to stay healthy and have a fresh mind in the morning.
Here is my current website with all of my services and affilitae links: https://thedigitalempress.carrd.co/#
Take a look at it and let me know what you think. And if you read all the way to the end you're a real one. I plan on making this journey very enjoyable and inspiring for those following along. Thank you for tuning in.
Empress
#thoughts#women in business#digital security#cybersecurity#neville goddard#manifesting#blogging#tech blog#fyp#30 Day ITSec Business Challenge
5 notes
·
View notes