#Data Encryption Hardware Market
Explore tagged Tumblr posts
Text
Data Encryption Hardware Market to Maintain Growth Momentum till 2037
The Data Encryption Hardware Market has experienced significant growth driven by escalating concerns around data security and privacy. Estimated at USD 1.73 billion in 2024, the market is poised to expand robustly, reaching an estimated USD 5.17 billion by 2037. This growth trajectory corresponds to a Compound Annual Growth Rate (CAGR) of approximately 8.3% during the forecast period from 2025 to 2037. The expanding digital ecosystem, increasing cyber threats, and stringent regulatory compliance worldwide underpin this accelerating demand for encryption hardware solutions.
Data Encryption Hardware Industry Demand
The Data Encryption Hardware Market encompasses physical devices designed to safeguard sensitive information by encrypting data, ensuring confidentiality, integrity, and authentication across digital communication and storage platforms. These hardware solutions provide an additional layer of security beyond software-based encryption by physically isolating cryptographic operations, thereby mitigating vulnerabilities to cyberattacks.
Demand for Data Encryption Hardware is primarily driven by several critical factors. First, these solutions offer cost-effectiveness by reducing potential financial losses from data breaches and non-compliance penalties. Second, they enable ease of administration, facilitating simplified key management and enhanced control over cryptographic processes. Additionally, many encryption hardware devices boast a long shelf life, supporting sustained security infrastructure investment with minimal maintenance requirements. Collectively, these benefits contribute to the rising adoption of encryption hardware across various industry verticals.
Request Sample@ https://www.researchnester.com/sample-request-7671
Data Encryption Hardware Market: Growth Catalysts and Primary Challenges
Key Growth Drivers:
Technological Advancements: The development of sophisticated cryptographic hardware such as Hardware Security Modules (HSMs) with enhanced processing power and integration capabilities fuels market growth. Innovations in miniaturization and power efficiency further boost adoption.
Outsourcing Trends: With organizations increasingly outsourcing IT and data security functions, reliance on robust hardware encryption solutions managed by third parties has risen. This trend stimulates demand for secure, reliable encryption hardware to safeguard outsourced data.
Regulatory Compliance and Data Privacy: Growing global regulatory mandates such as GDPR, HIPAA, and CCPA necessitate rigorous data protection practices. This compels organizations to invest in encryption hardware to comply with data security standards and avoid substantial penalties.
Market Restraint:
High Initial Investment: The relatively high upfront costs associated with deploying advanced encryption hardware may deter smaller enterprises or startups from immediate adoption, potentially limiting short-term market expansion.
Data Encryption Hardware Market: Segment Analysis
By Deployment Type:
Cloud-Based: This segment caters to organizations leveraging cloud infrastructures, requiring scalable encryption hardware solutions that can integrate with cloud platforms for secure data transmission and storage. Demand here is driven by the increasing migration to cloud environments and the need for remote, accessible security management.
On-Premise: Organizations with strict data sovereignty policies or legacy infrastructure tend to prefer on-premise deployment. This segment continues to hold steady demand due to the perceived control and security benefits it offers, particularly in highly regulated sectors.
By Product Type:
Hardware Security Modules (HSMs): HSMs lead the market as critical components providing secure key storage and cryptographic processing. Their robust security features and compliance alignment position them as preferred encryption devices.
Encryption Appliances: These devices offer dedicated encryption processing capabilities, often used in network security and data centers to ensure high-speed data protection.
Secure Storage Devices: Encrypted USB drives, external hard drives, and other storage devices secure sensitive data at rest, catering especially to mobile and field operations.
Trusted Platform Modules (TPMs): TPMs are embedded hardware chips used for device authentication and platform integrity, crucial for endpoint security.
Cryptographic Processors: These specialized processors accelerate cryptographic operations, supporting encryption in high-performance environments.
By End Use:
Banking & Financial Services: This sector drives substantial demand for encryption hardware, necessitated by the sensitive nature of financial transactions and regulatory mandates to safeguard customer data.
Government: Governments worldwide deploy encryption hardware extensively to protect classified information, secure communication channels, and uphold national security interests, significantly influencing market dynamics.
Data Encryption Hardware Market: Regional Insights
North America: North America remains a dominant market due to the presence of major cybersecurity firms and stringent data protection regulations. The region benefits from early adoption of cutting-edge encryption hardware solutions across industries, driven by heightened cyber threat awareness and substantial IT infrastructure investments.
Europe: Europe’s growth is fueled by strong regulatory frameworks such as GDPR and a growing emphasis on data sovereignty. Enterprises and public sector entities prioritize encryption hardware to meet compliance and protect consumer privacy, fostering steady market expansion.
Asia-Pacific (APAC): APAC is witnessing rapid growth due to increased digital transformation initiatives, expanding IT infrastructure, and rising cyberattacks. Governments and enterprises in emerging economies are investing heavily in encryption hardware to secure sensitive data and comply with evolving cybersecurity policies, positioning the region as a high-potential market.
Top Players in the Data Encryption Hardware Market
The Data Encryption Hardware Market is highly competitive, with several leading companies driving innovation and market expansion. Prominent players include Thales Group, IBM Corporation, Utimaco GmbH, Futurex, Entrust Corporation, Atalla, Securosys SA, Yubico AB, and others. These companies focus on delivering advanced encryption solutions with robust security features, fostering strategic partnerships, and expanding their global footprint to capture growing market demand.
Access Detailed Report@ https://www.researchnester.com/reports/data-encryption-hardware-market/7671
Contact for more Info:
AJ Daniel
Email: [email protected]
U.S. Phone: +1 646 586 9123
U.K. Phone: +44 203 608 5919
#Data Encryption Hardware Market#Data Encryption Hardware Market share#Data Encryption Hardware Market overview
0 notes
Text
"In the age of smart fridges, connected egg crates, and casino fish tanks doubling as entry points for hackers, it shouldn’t come as a surprise that sex toys have joined the Internet of Things (IoT) party.
But not all parties are fun, and this one comes with a hefty dose of risk: data breaches, psychological harm, and even physical danger.
Let’s dig into why your Bluetooth-enabled intimacy gadget might be your most vulnerable possession — and not in the way you think.
The lure of remote-controlled intimacy gadgets isn’t hard to understand. Whether you’re in a long-distance relationship or just like the convenience, these devices have taken the market by storm.
According to a 2023 study commissioned by the U.K.’s Department for Science, Innovation, and Technology (DSIT), these toys are some of the most vulnerable consumer IoT products.
And while a vibrating smart egg or a remotely controlled chastity belt might sound futuristic, the risks involved are decidedly dystopian.
Forbes’ Davey Winder flagged the issue four years ago when hackers locked users into a chastity device, demanding a ransom to unlock it.
Fast forward to now, and the warnings are louder than ever. Researchers led by Dr. Mark Cote found multiple vulnerabilities in these devices, primarily those relying on Bluetooth connectivity.
Alarmingly, many of these connections lack encryption, leaving the door wide open for malicious third parties.
If you’re picturing some low-stakes prank involving vibrating gadgets going haywire, think again. The risks are far graver.
According to the DSIT report, hackers could potentially inflict physical harm by overheating a device or locking it indefinitely. Meanwhile, the psychological harm could stem from sensitive data — yes, that kind of data — being exposed or exploited.
A TechCrunch exposé revealed that a security researcher breached a chastity device’s database containing over 10,000 users’ information. That was back in June, and the manufacturer still hasn’t addressed the issue.
In another incident, users of the CellMate connected chastity belt reported hackers demanding $750 in bitcoin to unlock devices. Fortunately, one man who spoke to Vice hadn’t been wearing his when the attack happened. Small mercies, right?
These aren’t isolated events. Standard Innovation Corp., the maker of the We-Vibe toy, settled for $3.75 million in 2017 after it was discovered the device was collecting intimate data without user consent.
A sex toy with a camera was hacked the same year, granting outsiders access to its live feed.
And let’s not forget: IoT toys are multiplying faster than anyone can track, with websites like Internet of Dongs monitoring the surge.
If the thought of a connected chastity belt being hacked makes you uneasy, consider this: sex toys are just a small piece of the IoT puzzle.
There are an estimated 17 billion connected devices worldwide, ranging from light bulbs to fitness trackers — and, oddly, smart egg crates.
Yet, as Microsoft’s 2022 Digital Defense Report points out, IoT security is lagging far behind its software and hardware counterparts.
Hackers are opportunistic. If there’s a way in, they’ll find it. Case in point: a casino lost sensitive customer data after bad actors accessed its network through smart sensors in a fish tank.
If a fish tank isn’t safe, why would we expect a vibrating gadget to be?
Here’s where the frustration kicks in: these vulnerabilities are preventable.
The DSIT report notes that many devices rely on unencrypted Bluetooth connections or insecure APIs for remote control functionality.
Fixing these flaws is well within the reach of manufacturers, yet companies routinely fail to prioritize security.
Even basic transparency around data collection would be a step in the right direction. Users deserve to know what’s being collected, why, and how it’s protected. But history suggests the industry is reluctant to step up.
After all, if companies like Standard Innovation can get away with quietly siphoning off user data, why would smaller players bother to invest in robust security?
So, what’s a smart-toy enthusiast to do? First, ask yourself: do you really need your device to be connected to an app?
If the answer is no, then maybe it’s best to go old school. If remote connectivity is a must, take some precautions.
Keep software updated: Ensure both the device firmware and your phone’s app are running the latest versions. Updates often include critical security patches.
Use secure passwords: Avoid default settings and choose strong, unique passwords for apps controlling your devices.
Limit app permissions: Only grant the app the bare minimum of permissions needed for functionality.
Vet the manufacturer: Research whether the company has a history of addressing security flaws. If they’ve been caught slacking before, it’s a red flag.
The conversation around sex toy hacking isn’t just about awkward headlines — it’s about how we navigate a world increasingly dependent on connected technology. As devices creep further into every corner of our lives, from the bedroom to the kitchen, the stakes for privacy and security continue to rise.
And let’s face it: there’s something uniquely unsettling about hackers turning moments of intimacy into opportunities for exploitation.
If companies won’t take responsibility for protecting users, then consumers need to start asking tough questions — and maybe think twice before connecting their pleasure devices to the internet.
As for the manufacturers? The message is simple: step up or step aside.
No one wants to be the next headline in a tale of hacked chastity belts and hijacked intimacy. And if you think that’s funny, just wait until your light bulb sells your Wi-Fi password.
This is where IoT meets TMI. Stay connected, but stay safe."
https://thartribune.com/government-warns-couples-that-sex-toys-remain-a-tempting-target-for-hackers-with-the-potential-to-be-weaponized/
#iot#I only want non-smart devices#I don't want my toilet to connect to the internet#seriously#smart devices#ai#anti ai#enshittification#smart sex toys
26 notes
·
View notes
Text
In the era of digital transformation, cloud computing has emerged as a pivotal technology, reshaping the way businesses operate and innovate. Pune, a burgeoning IT and business hub, has seen a significant surge in the adoption of cloud services, with companies seeking to enhance their efficiency, scalability, and agility. Zip Crest stands at the forefront of this revolution, offering comprehensive cloud computing services tailored to meet the diverse needs of businesses in Pune
The Importance of Cloud Computing
Cloud computing enables organizations to leverage a network of remote servers hosted on the internet to store, manage, and process data, rather than relying on local servers or personal computers. This shift provides several key benefits:
- Scalability: Businesses can easily scale their operations up or down based on demand, without the need for significant capital investment in hardware.
- Cost Efficiency: Cloud services operate on a pay-as-you-go model, reducing the need for substantial upfront investment and lowering overall IT costs.
- Accessibility: Cloud computing allows access to data and applications from anywhere, at any time, fostering remote work and collaboration.
- Security: Leading cloud service providers offer robust security measures, including encryption, access controls, and regular security audits, to protect sensitive data.
Zip Crest: Leading Cloud Computing Services in Pune
Zip Crest is committed to empowering businesses in Pune with cutting-edge cloud computing solutions. Our services are designed to address the unique challenges and opportunities that come with the digital age. Here’s how we can transform your business operations:
1. Cloud Strategy and Consulting:
At Zip Crest, we begin by understanding your business objectives and IT infrastructure. Our experts then craft a bespoke cloud strategy that aligns with your goals, ensuring a seamless transition to the cloud and maximizing the benefits of cloud technology.
2. Infrastructure as a Service (IaaS):
Our IaaS offerings provide businesses with virtualized computing resources over the internet. This includes virtual machines, storage, and networking capabilities, allowing you to build and manage your IT infrastructure without the need for physical hardware.
3. Platform as a Service (PaaS):
With our PaaS solutions, developers can build, deploy, and manage applications without worrying about the underlying infrastructure. This accelerates development cycles, enhances productivity, and reduces time to market.
4. Software as a Service (SaaS):
Zip Crest offers a range of SaaS applications that can streamline your business processes. From customer relationship management (CRM) to enterprise resource planning (ERP), our cloud-based software solutions are designed to improve efficiency and drive growth.
5. Cloud Migration Services:
Transitioning to the cloud can be complex. Our cloud migration services ensure a smooth and secure migration of your applications, data, and workloads to the cloud, minimizing downtime and disruption to your business operations.
6. Managed Cloud Services:
Once your infrastructure is on the cloud, ongoing management is crucial to ensure optimal performance and security. Our managed cloud services provide continuous monitoring, maintenance, and support, allowing you to focus on your core business activities.

Why Choose Zip Crest?
Choosing Zip Crest for your cloud computing needs comes with several advantages:
- Expertise: Our team of certified cloud professionals brings extensive experience and deep knowledge of cloud technologies.
- Customized Solutions: We understand that every business is unique. Our solutions are tailored to meet your specific requirements and objectives.
-Proactive Support: We offer 24/7 support to ensure that your cloud infrastructure is always running smoothly and efficiently.
- Security Focus: Security is at the core of our services. We implement robust security measures to protect your data and applications from threats.
Conclusion
In conclusion, cloud computing is transforming the way businesses operate, offering unprecedented levels of flexibility, scalability, and efficiency. Zip Crest is dedicated to helping businesses in Pune harness the power of the cloud to achieve their goals and stay competitive in today’s fast-paced digital landscape. By partnering with Zip Crest, you can ensure that your business is well-equipped to navigate the complexities of cloud computing and reap its many benefits. Embrace the future of technology with Zip Crest and revolutionize your business operations with our top-tier cloud computing services.
Get In Touch
Website: https://zipcrest.com/
Address: 13, 4th Floor, A Building City Vista Office Park Fountain Road Karadi Pune Maharashtra 411014
Email: [email protected] / [email protected]
Call: +912049330928 / 9763702645 / 7020684182
2 notes
·
View notes
Text
Overcoming Challenges in Data Integration: Insights from Consulting Experts
Data integration for enterprises can take longer due to technological, financial, and time constraints. As a result, modifying data strategies to mitigate risks like incompatibility between many tools or budget overruns is crucial. Companies must also prepare for new compliance requirements to ensure ethical data operations. This post will explore such challenges in data integration while listing valuable insights from consulting experts in this domain.
What is Data Integration?
Data integration merges data from disparate origins and presents it to maximize comprehension, consolidation, and summarization effectiveness. Integrated data views rely on data ingestion, preparation, and advanced insight extraction. It also streamlines the data operations services across regulatory report creation, helpdesks, and 360-degree client life cycle management.
All data integration strategies involve the extract, transform, and load (ETL) pipelines regardless of business units or target industries. At the same time, the scope of planning and quality assurance in each process varies due to domain-specific data classification factors.
For instance, the accounting departments must handle extensive numerical data while interpreting legal and organizational requirements for transparency. On the other hand, production engineering and design professionals will use visualizations to improve goods or service packages. Accordingly, accountants will use unique tools distinct from engineers’ software.
Later, the leaders might want a comprehensive overview of the synergy between these departments. Therefore, they must determine efficient data integration strategies. The data will move between several programs, carrying forward many updates throughout a project’s progression based on those roadmaps.
Overcoming the Challenges in Data Integration Using Insights from Consulting Experts
1| Data Quality Hurdles
Linking, consolidating, and updating data from several sources will exponentially increase the quality-related threats. For instance, consider multimedia assets from social networks or unreliable news outlets. They can help your secondary market research and social listening initiatives. However, you want to verify the authenticity of gathered intelligence to avoid inaccurate data ingestion.
Evaluating relevance, freshness, and consistency is essential to data quality assurance from creation to archival. So, corporations have started leveraging data lifecycle management to boost dataset integrity, helping make integration less of a hassle.
Insights:
Most consulting experts suggest developing ecosystems that check and recheck quality metrics at each stage of a data integration lifecycle. Moreover, they recommend maintaining periodic data backups with robust version control mechanisms. Doing so will help quality preservation efforts if errors arise after a feature update or a malicious third party is likely to break the system using malware.
2| Networking and Computing Infrastructure Problems
Legacy hardware and software often introduce bottlenecks, hurting data integration’s efficiency. Modern integration strategies demand more capable IT infrastructure due to the breakthroughs like the internet of things (IoT), 5G networks, big data, and large language models. If a company fails to procure the necessary resources, it must postpone data integration.
Technologies integral to capturing, storing, checking, sorting, transferring, and encrypting data imply significant electricity consumption. Besides, a stable networking environment with adequate governance implementations enables secure data transactions. The underlying computing infrastructure is not immune to physical damage or downtime risks due to maintenance mishaps.
What Consulting Experts Say:
Enterprises must invest in reliable, scalable, and efficient hardware-software infrastructure. This will benefit them by providing a stable working environment and allowing employees to witness productivity improvements. Upgrading IT systems will also enhance cybersecurity, lowering the risk of zero-day vulnerabilities.
3| Data Availability Delays
Governments, global firms, educational institutions, hospitals, and import-export organizations have a vast network of regional offices. These offices must also interact with suppliers, contractors, and customers. Due to the scale of stakeholder engagement, reports concerning office-level performance and inventory might arrive late.
Underproductive employees, tech troubleshooting, slow internet connectivity, and a poor data compression ratio will make data sourcing, updating, and analyzing inefficient. As a result, a data integration officer must address time-consuming activities through strategic resource allocation. If left unaddressed, delays in data delivery will adversely affect conflict resolution and customer service.
Expert Insights:
Train your employees to maximize their potential and reduce data acquisition, categorization, and transformation delays. Additionally, you will want to embrace automation through artificial intelligence (AI) applications. Find methods to increase the data compression ratio and accelerate encryption-decryption processing cycles. These measures will help accomplish near-real-time data integration objectives.
4| Vendor Lock-ins
A vendor lock-in results from inconvenience and restrictions when a client wants to switch to another service provider or toolkit. Although data integration platforms claim they celebrate the ease of migrating databases with competitors, they might covertly create vendor lock-ins.
For instance, some data sourcing and sorting ecosystems might limit the supported formats for bulk export commands. Others will use misleading methods to design the graphical user interface (GUI) of account deletion and data export features. They involve too many alerts or generate corrupt export files.
Practical Insights:
Combining multiple proprietary and open-source software tools offers the best cost optimization opportunities. When you select a data vendor, audit the tools the willing data integration providers use to deliver their assistance. Do they use a completely proprietary system based on an unknown file format unsupported by other platforms?
Finally, you must check all the data import, export, and bulk transfer options in vendors’ documentation. After you check a data firm’s current client base, track its online ratings and scan for red flags indicating potential vendor lock-ins.
5| Data-Related Ethical and Legal Liabilities
Confidentiality of investor communication and stakeholders’ privacy rights are two components of legal risk exposure due to enterprise data integration. Additionally, brands must interpret industry guidelines and regional directives for regulatory disclosures.
They must comply with laws concerning personally identifiable information (PII) about employees and customers. Otherwise, they will attract policymakers’ ire, and customers will lose faith in brands that do not comply with the laws of their countries.
Insights:
Consulting experts recommend collaborating with regional legal teams and global governance compliance specialists. After all, mitigating legal risks can help increase business resilience.
Improved compliance ratings have also benefited several brands wanting to be attractive to impact investors. Meanwhile, customers demanding ethical data operations at business establishments love supporting brands with an exceptional governance culture.
Conclusion
Most brands need specialists' help to develop consolidated data views during reporting because they have flawed data integration strategies. So, they require trustworthy insights from reputed consulting experts with a proven track record of overcoming challenges in data integration. The selected data partners must excel at ETL implementation, governance compliance, and data quality management (DQM).
The corporate world champions data-centric business development. Understandably, the need for scalable data integration reflects the increased stakeholder awareness regarding the importance of connecting disparate data sources. With transparent, fast, and accurate data, organizations will enhance their competitive edge amid this intense digital transformation race.
3 notes
·
View notes
Text
Why Your Business Needs a Cloud Video Platform Today
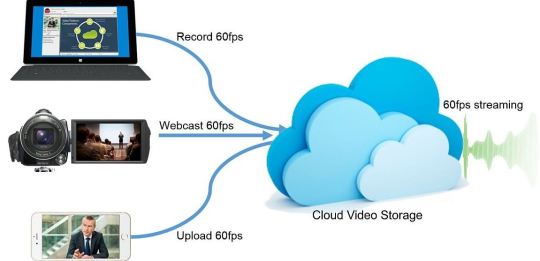
In the digital era, businesses are constantly looking for ways to enhance efficiency, reduce costs, and improve communication and collaboration. One of the technological advances that has been pivotal in achieving these objectives is the cloud video platform. This platform has revolutionized how businesses operate, offering a multitude of benefits ranging from improved communication strategies to expansive data analytics. Additionally, the cloud video platform provides scalable solutions that adapt to the needs of growing businesses, ensuring that they can maintain seamless operations. By facilitating remote work and virtual meetings, these platforms also contribute to better team collaboration and more efficient project management.
Key Benefits of Using Cloud Video Platform
A cloud video platform offers significant advantages to businesses, paramount among them being scalability, accessibility, enhanced collaboration, cost-effectiveness, and security. Understanding these benefits in detail can help organizations make informed decisions about adopting this technology, leading to more efficient operations, improved communication, and ultimately, a competitive edge in the market. Embracing cloud video solutions is a strategic move.
Scalability and Flexibility
One of the primary advantages of cloud video platform is their scalability. Businesses can effortlessly scale their video management needs up or down based on current demand without the need for significant upfront investments in hardware. This flexibility is crucial in adapting to business growth or changes without incurring additional costs or delays. Moreover, it allows companies to efficiently manage resources and respond promptly to evolving market conditions.
Accessibility and Reach
With a cloud video platform, videos can be accessed from anywhere, at any time, on any device with internet access. This global accessibility ensures that employees in different locations can easily participate in training sessions, meetings, and collaborations without the need for physical travel, further enhancing productivity across the organization. Additionally, it allows for seamless integration of remote and on-site teams, fostering a more connected and efficient workplace.
Enhanced Collaboration
A cloud video platform facilitates enhanced collaboration among teams by providing features such as real-time sharing, editing, and communication tools. These integrated features enable teams to work together more effectively, even when members are spread across various geographic locations. This real-time interaction significantly aids in quicker decision-making and problem-solving, ensuring that projects progress smoothly and efficiently regardless of physical distances.
Cost-Effectiveness
Moving to a cloud video platform can significantly reduce costs related to video content management. By leveraging cloud services, businesses eliminate the need for expensive on-premise infrastructure. Additionally, the maintenance and upgrading of systems are handled by the service provider, which can further decrease IT expenses. Furthermore, cloud platforms offer scalable solutions that allow businesses to pay only for the resources they use, optimizing budget allocation.
Security and Compliance
Security is a top concern for any business leveraging digital tools. The cloud video platform is equipped with robust security measures, including data encryption, secure access controls, and compliance with international standards. These features ensure that sensitive content remains protected against unauthorized access and breaches. Additionally, regular security audits and updates further enhance the platform's ability to safeguard valuable data, providing businesses with peace of mind and confidence in their digital security.
Improved Content Management and Analytics
A cloud video platform also offers advanced content management systems, allowing businesses to efficiently organize, manage, and retrieve video content with ease. Additionally, these platforms provide insightful analytics on viewer engagement, content performance, and other key metrics. This data-driven approach enables businesses to make informed decisions to optimize their video strategies, enhance viewer experience, and ultimately drive better results in their video marketing efforts.
Implementing Cloud Video Platform: Considerations and Best Practices
Implementing a cloud video platform yields significant benefits, but its success hinges on strategic planning and factor consideration. Vital elements encompass selecting an appropriate platform, meeting bandwidth needs, prioritizing user adoption tactics, and upholding data governance policies. These measures collectively shape a robust foundation for seamless integration and optimized performance.
Choosing the Right Platform
Selecting the appropriate cloud video platform is critical and should be based on specific business needs such as feature requirements, scalability, security, and compatibility with existing systems. Businesses should conduct thorough research or consult with experts to find the best fit.
Ensuring Adequate Bandwidth
Effective video streaming requires sufficient bandwidth. Before implementation, businesses need to assess their internet bandwidth to ensure smooth video playback and uploading capabilities without disrupting other business operations.
Focusing on User Adoption
To maximize the benefits of cloud video platform, promoting user adoption through training and support is essential. Employees need to understand how to use the platform efficiently and be comfortable with its features to fully leverage its capabilities.
Adhering to Data Governance
Businesses must also consider data governance when implementing cloud video platform. Ensuring that the platform complies with relevant laws and regulations regarding data privacy and protection is crucial.
Conclusion
The adoption of a cloud video platform can bring transformative benefits to businesses, fostering better communication and collaboration, providing scalability and flexibility, enhancing content management and analytics, reducing costs, and bolstering security. By leveraging cloud technology, organizations can streamline their operations and improve efficiency. Moreover, these platforms enable seamless remote work, support real-time collaboration, and offer advanced tools for data-driven decision-making. With careful planning and consideration of the key factors outlined above, organizations can effectively implement and use these platforms to achieve substantial business success, ensuring they stay competitive in an increasingly digital and connected world. please don’t hesitate to contact us via email or phone for further assistance!
#cloud video platform#secure video hosting#streaming video hosting#encrypted video hosting#drm encrypted video streaming#encrypted video streaming#DRM software#video hosting#security video#video platforms#online video platform#video watermark#DRM protected content#video cdn#wide vine#online courses#e-learning platforms#influencers#paid online courses#E-Learning Solutions#Digital content
2 notes
·
View notes
Text
Maximizing ROI: The Cost-Effectiveness of Amazon Web Services (AWS)
In today's digitally driven landscape, cloud computing has become synonymous with innovation and operational efficiency for businesses worldwide. Among the plethora of cloud service providers, Amazon Web Services (AWS) stands tall, offering an extensive suite of tools and solutions to empower organizations on their path to digital transformation. This in-depth exploration navigates through the core features, advantages, and transformative impact that AWS brings to businesses of all sizes.

Introducing Amazon Web Services (AWS)
Amazon Web Services, commonly referred to as AWS, is a cloud computing platform introduced by Amazon.com in 2006. Since its inception, AWS has redefined the accessibility and utilization of computing resources, storage solutions, and an array of IT services. Its distinguishing factors lie in its unmatched scalability, reliability, and diverse service offerings, making it the preferred choice across industries, from startups to enterprise-level corporations and government entities.
Scalability: Harnessing Elasticity for Dynamic Growth
AWS's hallmark feature is its elastic scalability, empowering businesses to seamlessly adjust their computing resources according to fluctuating demands. With AWS, organizations can effortlessly scale their infrastructure up or down, ensuring optimal performance and cost efficiency. Whether handling sudden spikes in website traffic or launching new applications, AWS provides the agility necessary to respond swiftly to evolving business needs.
Reliability: Building Upon a Foundation of Resilience
Reliability is a cornerstone of cloud computing, and AWS excels in this domain. By leveraging multiple data centers distributed across different geographic regions, AWS offers a highly redundant infrastructure, minimizing the risk of downtime and ensuring uninterrupted service availability. Through the strategic distribution of workloads across various availability zones, AWS provides inherent fault tolerance, enabling businesses to achieve exceptional levels of reliability for their critical applications and services.
Cost-effectiveness: Maximizing Value with Flexible Pricing Models
In a competitive market, cost optimization is paramount for businesses. AWS's pay-as-you-go pricing model enables organizations to pay solely for the resources they consume, eliminating the need for upfront investments in hardware or long-term commitments. This flexible pricing structure, coupled with robust cost management tools like AWS Cost Explorer and AWS Budgets, empowers businesses to manage their cloud expenditures effectively and optimize return on investment (ROI).

Security: Fortifying Digital Assets with Comprehensive Protections
Security is a top priority in the cloud, and AWS places great emphasis on it. Through stringent security measures such as encryption, access controls, and network security protocols, AWS provides a secure environment for sensitive data and critical workloads. Additionally, AWS offers compliance certifications tailored to various industry standards, ensuring that businesses can meet regulatory requirements seamlessly. Whether safeguarding customer data or protecting intellectual property, AWS instills confidence through its commitment to best-in-class security practices.
Diverse Service Portfolio: Enabling Innovation Across Industries
AWS boasts a diverse and extensive service portfolio, catering to a myriad of use cases and industry verticals. From foundational services like compute instances (EC2) and storage solutions (S3) to advanced offerings such as machine learning (Amazon SageMaker) and Internet of Things (IoT) platforms, AWS provides the essential tools needed to drive innovation and unlock new opportunities. Whether developing mobile applications, analyzing vast datasets, or deploying global e-commerce platforms, AWS offers the comprehensive suite of services to support diverse business objectives.
Flexibility and Customization: Tailoring Solutions to Unique Needs
A key strength of AWS lies in its flexibility and customization capabilities. With a vibrant ecosystem of third-party integrations and tools, AWS empowers businesses to tailor their cloud environments to align with specific requirements. Whether implementing hybrid cloud architectures, adopting DevOps practices, or integrating seamlessly with existing IT systems, AWS offers the flexibility necessary to adapt and innovate within the dynamic business landscape.
Conclusion: Embracing the Future with AWS
In summary, Amazon Web Services (AWS) transcends the realm of mere cloud computing—it serves as a catalyst for innovation, efficiency, and growth. With its unmatched scalability, reliability, cost-effectiveness, security measures, and diverse service portfolio, AWS empowers businesses to realize their full potential in the digital age. Whether aspiring to disrupt markets as a startup or striving for operational excellence as an enterprise, AWS provides the indispensable tools and services to transform visions into reality. Embrace the future of cloud computing with AWS and embark on a journey of endless possibilities.
2 notes
·
View notes
Text
What is the best web-based enterprise accounting software?

In the fast-paced and ever-evolving landscape of business, staying on top of your finances is crucial. As enterprises expand their operations, managing accounts efficiently becomes a daunting task. Thankfully, with the advent of technology, businesses now have access to a plethora of web-based enterprise accounting software options to streamline their financial processes. In this comprehensive guide, we will explore the ins and outs of web-based enterprise accounting software, helping you make an informed decision on the best solution for your business needs.
Understanding Web-Based Enterprise Accounting Software
Web-based enterprise accounting software, often referred to as cloud accounting software, is a digital solution that allows businesses to manage their financial activities online. Unlike traditional accounting systems that rely on on-premise software, web-based accounting tools operate in the cloud, offering users the flexibility to access their financial data from anywhere with an internet connection.
Advantages of Web-Based Enterprise Accounting Software
1. Accessibility
One of the primary advantages of web-based accounting software is accessibility. With data stored securely in the cloud, users can access their financial information anytime, anywhere. This proves especially beneficial for enterprises with multiple locations or remote teams, fostering collaboration and efficiency.
2. Cost Efficiency
Web-based accounting solutions often follow a subscription-based model, eliminating the need for costly upfront investments in software and hardware. This cost-effective approach makes it easier for businesses to scale their accounting infrastructure according to their needs without breaking the bank.
3. Real-Time Updates
In the dynamic world of business, real-time data is invaluable. Web-based accounting software provides instant updates, ensuring that users have access to the most recent financial information. This feature is crucial for making informed decisions and adapting to market changes promptly.
4. Automatic Updates and Maintenance
Gone are the days of manual software updates and maintenance. With web-based accounting solutions, updates are automatic, and maintenance is handled by the service provider. This frees up valuable time for businesses to focus on core operations rather than managing software updates.
Features to Look for in Web-Based Enterprise Accounting Software
1. User-Friendly Interface
A user-friendly interface is essential for ensuring that your team can navigate the software seamlessly. Look for solutions with intuitive dashboards and easy-to-understand features to minimize the learning curve for your staff.
2. Scalability
As your enterprise grows, so do your accounting needs. Choose a web-based accounting solution that can scale with your business, accommodating increased transaction volumes and additional users without compromising performance.
3. Integration Capabilities
Efficient accounting doesn't happen in isolation. Ensure that the web-based accounting software you choose integrates seamlessly with other essential business tools, such as CRM systems, project management software, and e-commerce platforms.
4. Security
The security of your financial data should be a top priority. Opt for web-based accounting software that employs robust encryption protocols and follows industry best practices for data protection. Additionally, check for features such as multi-factor authentication to add an extra layer of security.
Top Contenders in the Web-Based Enterprise Accounting Software Market
1. MargBooks
MargBooks Online is a India's popular online accounting solution known for its user-friendly interface and robust features. It offers a range of plans to suit businesses of all sizes and provides tools for invoicing, expense tracking, and financial reporting.
2. Xero
Xero is another cloud accounting software that caters to small and medium-sized enterprises. With features like bank reconciliation, inventory management, and payroll integration, Xero is a comprehensive solution for businesses looking to streamline their financial processes.
3. NetSuite
NetSuite, owned by Oracle, is a cloud-based ERP (Enterprise Resource Planning) solution that includes robust accounting functionalities. It is suitable for larger enterprises with complex financial needs and offers features such as financial planning, revenue recognition, and multi-currency support.
4. Zoho Books
Zoho Books is part of the Zoho suite of business applications and is designed for small and medium-sized enterprises. It provides features such as automated workflows, project billing, and collaborative client portals, making it a versatile choice for businesses with diverse needs.
Making the Right Choice for Your Business
Choosing the best web-based enterprise accounting software for your business requires careful consideration of your specific needs and objectives. Here are some steps to guide you through the decision-making process:
1. Assess Your Business Requirements
Start by identifying your business's specific accounting requirements. Consider factors such as the number of users, the complexity of your financial transactions, and the need for integration with other business applications.
2. Set a Budget
Determine a realistic budget for your accounting software. While web-based solutions often offer cost savings compared to traditional software, it's essential to choose a solution that aligns with your financial resources.
3. Explore Free Trials
Many web-based accounting software providers offer free trials of their platforms. Take advantage of these trials to explore the features and functionalities of different solutions before making a commitment.
4. Seek Recommendations and Reviews
Consult with other businesses in your industry or network to gather recommendations and insights. Additionally, read reviews from reputable sources to gain a better understanding of the user experiences with different accounting software options.
The Evolution of Web-Based Enterprise Accounting Software
As technology continues to advance, so does the landscape of web-based enterprise accounting software. The evolution of these platforms is driven by the ever-changing needs of businesses and the ongoing developments in cloud technology. Let's delve deeper into the evolving trends shaping the future of web-based accounting solutions.
1. Artificial Intelligence (AI) and Automation
The integration of artificial intelligence and automation is revolutionizing how businesses handle their financial processes. Modern web-based accounting software is incorporating AI algorithms to automate repetitive tasks, such as data entry and invoice categorization. This not only increases efficiency but also minimizes the risk of human error.
2. Enhanced Data Analytics
In the age of big data, the ability to derive meaningful insights from financial data is paramount. Advanced web-based accounting solutions are now equipped with powerful data analytics tools. These tools help businesses analyze trends, forecast future financial scenarios, and make data-driven decisions.
3. Mobile Accessibility
The shift towards mobile accessibility is a notable trend in web-based enterprise accounting software. Businesses are increasingly relying on mobile devices for day-to-day operations, and accounting software providers are responding by offering mobile-friendly applications. This allows users to manage their finances on the go, providing unparalleled flexibility.
4. Integration with E-Commerce Platforms
As e-commerce continues to thrive, businesses are looking for accounting solutions that seamlessly integrate with their online sales platforms. Modern web-based accounting software often includes features tailored for e-commerce, such as automated transaction reconciliation with online sales channels and inventory management.
5. Blockchain Technology
Blockchain technology is making waves in various industries, and accounting is no exception. Some web-based accounting solutions are exploring the integration of blockchain for enhanced security and transparency in financial transactions. This could revolutionize how businesses handle aspects like auditing and transaction verification.
Common Challenges and How to Overcome Them
While web-based enterprise accounting software offers numerous benefits, it's important to be aware of potential challenges and how to overcome them. Here are some common issues businesses may face:
1. Security Concerns
The sensitive nature of financial data raises concerns about security in the cloud. To address this, choose a web-based accounting solution that employs robust encryption protocols and complies with industry security standards. Additionally, educate your team about best practices for secure online behavior.
2. Connectivity Issues
Reliable internet connectivity is crucial for accessing web-based accounting software. In regions with unstable internet connections, businesses may face challenges in real-time collaboration and data accessibility. Consider implementing backup solutions for offline access or explore accounting software with offline capabilities.
3. Customization Needs
Every business has unique accounting requirements. Some businesses may find that certain web-based accounting solutions lack the level of customization they need. In such cases, explore platforms that offer extensive customization options or consider integrating additional specialized accounting tools.
4. Data Ownership and Control
Understanding the terms of service and data ownership is essential when using web-based accounting software. Ensure that the chosen platform allows you to retain control over your financial data and provides mechanisms for data export in case of migration to a different system.
Conclusion: Making the Right Choice for Long-Term Success
In the fast-paced world of business, the right web-based enterprise accounting software can be a game-changer. Whether you're a small startup or a large enterprise, the key is to stay informed about the latest advancements in accounting technology and align your choice with the long-term goals of your business.
As you navigate the vast landscape of web-based accounting solutions, remember that the best choice is the one that seamlessly integrates with your business processes, enhances efficiency, and adapts to the evolving needs of your enterprise. If you have any specific questions or need further guidance on a particular aspect of web-based accounting software, feel free to ask for more information!
Also read- Online billing and accounting software to manage your business
#Web-based accounting#Cloud software#Financial management#Enterprise solutions#accounting#software#billing#online billing software#technology#programming#erp#tech#drawings#illlustration#artwork#art style#sketchy#art#aspec#aromantic asexual#arospec#acespec#aroace#aro#bg3#astarion#shadowheart#gale dekarios#gale of waterdeep#karlach
2 notes
·
View notes
Text
Chapter 2: Uninvited Guest
Narrated by Netga.
Narrator: Blinking neon lights lie haphazardly in the corner. Optical fiber wires are scattered around the ground like nets.
Narrator: It’s hard to sense the passage of time in the enclosed garage. When I wake up, it’s already noon.
Narrator: The music I forgot to turn off last night is still booming in my workshop. I down my canned lunch in one gulp.
Narrator: How I miss restaurant-made black truffle soup. If I don’t get any orders soon, I won’t be able to afford even canned food.
Narrator: As I check the monitors on the control panel, I turn on the holographic projector to see a bounty on the news.
Newscast: ...The digital stimulant is now available on the black market. If used in mecha battles, it’ll lead to cheating.
Newscast: This stimulant is capable of speedily increasing the reaction speed, willpower, and deadliness of mechas.
Newscast: The suspect is said to be a former advanced researcher in an unnamed institute on Ruins Island.
Newscast: His expertise in neural connection allows him to collect stimulated brainwaves from animal experiments.
Netga: Create neural connection data packs to sell to mecha battle participants? That’s cruel!
Newscast: The suspect is on the police’s wanted list for illegal stimulant trade and cheating in matches. A generous reward will be offered.
Netga: A generous reward?
Narrator: The reward amount scrolls past the bottom of the screen. I look closer, counting the zeros, and inhale sharply.
Narrator: If I have that much money... I can have truffle soup every day and update all the hardware and materials in my workshop!
Narrator: Too bad this reward will never be mine. I sigh, sinking back into the couch.
Narrator: Bang!
Narrator: From the control panel comes the sound of equipment falling over. I leap up from the sofa again.
Narrator: The sound of objects toppling over like dominoes follows. Is someone looking through my possessions? A thief, perhaps?
Narrator: If it’s a thief, he’ll definitely be disappointed. All I have are unwanted mechas.
Narrator: I still pick up my laser melding gun and head towards the source of the commotion with cautious steps to investigate.
Narrator: Shoving aside some stray parts under the window, I find a small bunny. Next to it, the power cord it broke is still fizzling.
Narrator: A bunny?
Narrator: I’ve never seen any fluffy, soft, live animal on this island before.
Narrator: The bunny stares up at me with innocent, round eyes, then bounces to the side and begins to explore my workshop.
Netga: Hey! You!
Narrator: The small bunny squirms a lot, but I still manage to catch it after chasing it all around the place and cornering it by a wall.
Narrator: It won’t stop kicking its legs in my arms, but still...
Narrator: So soft to the touch!
Narrator: I start running my hand down its body, and it soon calms down.
Narrator: It’s rare to see an actual live animal on this island. Perhaps this fluffy bunny is a good imitation?
Narrator: I lift it onto my work table and scan it for electronic signals.
Narrator: Nothing out of the ordinary. Except...
Narrator: The device beeps loudly. An unknown chip has been detected behind an ear of the bunny. It’s an encrypted data pack.
Narrator: Studying this cute intruder sitting on my table, I’m suddenly reminded of the news I just saw.
Narrator: Did this bunny escape from the lab where the animal experiments are performed?
Narrator: Heart rate picking up, I connect my devices to the Internet and begin tracing the source of the data.
Narrator: It’s not that hard, though it can take time.
Narrator: After hacking into the core system of the chip, I find an IP address and soon gain access to heaps of trade records.
Narrator: The money seems to go in and out of several forged accounts owned by one single person.
Narrator: After some decoding, a set of coordinates behind multiple faked identities finally appear like an island in a sea of data.
Netga: Locked onto the target!
Narrator: The coordinates point to a spot in the crowded streets in the city center. Perhaps it’s where the suspect’s lab is located.
Narrator: Night falls and colorful holograms light up the streets. I walk unnoticed behind the groups of mechas and pedestrians.
Narrator: As I weave through the crowd, I remember the series of zeros I saw on the news. Enticing rewards await me!
Narrator: I should get down to business tonight before anyone else can catch up!
Chapter 1
Chapter 3
Chapter 4
#netga#shining nikki#ssr designer#ruins#ruins island#transcript#chapter 2#uninvited guest#bunny#test subject#bounty#experiment#black market#illegal substance#mecha#hacker#programmer
6 notes
·
View notes
Text
Agreed that recall is shit, but there is some misinfo here. Recall actually does run locally, and it's only available on systems that have a dedicated neural processing unit. At the time of posting, the only PC/laptop processors that have NPUs are Intel Core Ultra (both 100 and 200 series, desktop and mobile), AMD Ryzen AI (3 digit skus starting with a 3), and Qualcomm Snapdragon X (the kind in laptops, not the kind in your phone). You only have one of these chips if you're using fairly high end hardware released in the last year and a half or so; I'm not running anything nearly that cutting-edge, and AI is my actual specialization for my degree. Computers with these processors are mostly laptops and are often marketed as "Copilot+ PCs". If you do not have one of these systems, recall will not be enabled for you. Hardware NPU power draw is minimal, so recall won't consume a noticeable amount of battery or CPU resources.
Recall also will not run without full disk encryption and biometric authentication enabled, and the consent of the user. Full disk encryption and biometrics are both things the average user is unlikely to want to use, and you need to explicitly opt in anyway, so it's not like your PC is going to just start taking screenshots and sending them places entirely by itself without asking.
While recall doesn't store data in the cloud or send it to Microsoft, it does persist in Windows backups and system restore snapshots. If you are logged in with a Microsoft account, these snapshots can be stored in the cloud. This is a Big Issue for everyone for reasons that have very little to do with recall as a feature, and is also just fucking annoying. I highly recommend setting up your PC such that your local user account is not tied to a Microsoft account, which disables a huge amount of MS cloud integration. Even if you log into an MS account for their apps, your user account on your PC remains local. Bonus, your documents won't move to OneDrive by themselves without your consent if you do this!
I think every computer user needs to read this because holy fucking shit this is fucking horrible.
So Windows has a new feature incoming called Recall where your computer will first, monitor everything you do with screenshots every couple of seconds and "process that" with an AI.
Hey, errrr, fuck no? This isn't merely because AI is really energy intensive to the point that it causes environmental damage. This is because it's basically surveilling what you are doing on your fucking desktop.
This AI is not going to be on your desktop, like all AI, it's going to be done on another server, "in the cloud" to be precise, so all those data and screenshot? They're going to go off to Microsoft. Microsoft are going to be monitoring what you do on your own computer.
Now of course Microsoft are going to be all "oooh, it's okay, we'll keep your data safe". They won't. Let me just remind you that evidence given over from Facebook has been used to prosecute a mother and daughter for an "illegal abortion", Microsoft will likely do the same.
And before someone goes "durrr, nuthin' to fear, nuthin to hide", let me remind you that you can be doing completely legal and righteous acts and still have the police on your arse. Are you an activist? Don't even need to be a hackivist, you can just be very vocal about something concerning and have the fucking police on your arse. They did this with environmental protesters in the UK. The culture war against transgender people looks likely to be heading in a direction wherein people looking for information on transgender people or help transitioning will be tracked down too. You have plenty to hide from the government, including your opinions and ideas.
Again, look into backing up your shit and switching to Linux Mint or Ubuntu to get away from Microsoft doing this shit.
44K notes
·
View notes
Text
Secure Your Hybrid Cloud with Windows Server 2022 Standard
Building a Fortress: The Future of Hybrid Cloud Security with Windows Server 2022
In today's rapidly evolving digital landscape, securing your hybrid cloud environment is more critical than ever. Windows Server 2022 Standard emerges as a robust foundation, blending innovative security features with flexible management capabilities to empower businesses of all sizes. This powerful server OS is designed to meet the complex demands of modern IT infrastructure, ensuring your data remains protected while maintaining seamless connectivity across on-premises and cloud environments.
One of the standout features of Windows Server 2022 Standard is its secured-core server capabilities. This technology integrates hardware, firmware, and software security measures to create a resilient fortress against cyber threats. By leveraging features like Secure Boot, hardware root of trust, and virtualization-based security, organizations can significantly reduce the attack surface and safeguard critical assets from malicious intrusions.
Furthermore, Windows Server 2022 enhances multi-layer security through advanced threat protection mechanisms. It offers improved encryption protocols, real-time security monitoring, and streamlined patch management, enabling IT teams to identify vulnerabilities and respond swiftly to emerging threats. This comprehensive security approach ensures that your hybrid cloud remains resilient against increasingly sophisticated cyberattacks.
Managing hybrid environments has never been easier thanks to the improved hybrid server management tools integrated into Windows Server 2022. The platform provides a unified management experience, allowing administrators to control both on-premises and cloud resources efficiently. Features like Azure Arc integration facilitate seamless deployment, monitoring, and updating of servers across diverse environments, reducing operational complexity and boosting productivity.
For organizations leveraging containerization, Windows Server 2022 offers significant improvements in windows containers. Enhanced support for Kubernetes, improved isolation, and faster container startup times help developers deploy applications swiftly and securely. This ensures that your development pipeline remains agile and responsive to market needs, all while maintaining a high level of security.
Investing in the right licensing is crucial to unlock the full potential of Windows Server 2022 Standard. For competitive pricing and licensing options, explore the windows server 2022 standard license price. This license provides the essential features needed to build a secure, scalable, and efficient hybrid cloud environment.
In conclusion, Windows Server 2022 Standard is more than just an operating system; it’s a strategic enabler for modern enterprises aiming to harness the power of hybrid cloud while maintaining the highest security standards. Embrace this innovative platform to future-proof your IT infrastructure, safeguard your data, and empower your business to thrive in a digital-first world.
0 notes
Text
How Secure Are Internet of Things (IoT) Devices in 2025?

From smart homes anticipating your every need to industrial sensors optimizing manufacturing lines, Internet of Things (IoT) devices have seamlessly integrated into our lives, promising unparalleled convenience and efficiency. In 2025, are these interconnected gadgets truly secure, or are they opening up a Pandora's Box of vulnerabilities?
The truth is, IoT security is a complex and often concerning landscape. While significant progress is being made by some manufacturers and regulatory bodies, many IoT devices still pose substantial risks, largely due to a race to market that often prioritizes features and cost over robust security.
The Allure vs. The Alarms: Why IoT Devices Are Often Vulnerable
The promise of IoT is immense: automation, data-driven insights, remote control. The peril, however, lies in how easily these devices can become entry points for cyberattacks, leading to privacy breaches, network compromise, and even physical harm.
Here's why many IoT devices remain a security headache:
Weak Default Credentials & Lack of Updates:
The Problem: Many devices are still shipped with easily guessable default usernames and passwords (e.g., "admin/admin," "user/123456"). Even worse, many users never change them. This is the single easiest way for attackers to gain access.
The Challenge: Unlike smartphones or laptops, many IoT devices lack clear, robust, or frequent firmware update mechanisms. Cheaper devices often receive no security patches at all after purchase, leaving critical vulnerabilities unaddressed for their entire lifespan.
Insecure Network Services & Open Ports:
The Problem: Devices sometimes come with unnecessary network services enabled or ports left open to the internet, creating direct pathways for attackers. Poorly configured remote access features are a common culprit.
The Impact: Remember the Mirai botnet? It famously exploited vulnerable IoT devices with open ports and default credentials to launch massive Distributed Denial of Service (DDoS) attacks.
Lack of Encryption (Data In Transit & At Rest):
The Problem: Data transmitted between the device, its mobile app, and the cloud often lacks proper encryption, making it vulnerable to eavesdropping (Man-in-the-Middle attacks). Sensitive data stored directly on the device itself may also be unencrypted.
The Risk: Imagine your smart speaker conversations, security camera footage, or even health data from a wearable being intercepted or accessed.
Insecure Hardware & Physical Tampering:
The Problem: Many IoT devices are designed with minimal physical security. Easily accessible debug ports (like JTAG or UART) or lack of tamper-resistant enclosures can allow attackers to extract sensitive data (like firmware or encryption keys) directly from the device.
The Threat: With physical access, an attacker can potentially rewrite firmware, bypass security controls, or extract confidential information.
Vulnerabilities in Accompanying Apps & Cloud APIs:
The Problem: The web interfaces, mobile applications, and cloud APIs used to control IoT devices are often susceptible to common web vulnerabilities like SQL Injection, Cross-Site Scripting (XSS), or insecure authentication.
The Loophole: Even if the device itself is somewhat secure, a flaw in the control app or cloud backend can compromise the entire ecosystem.
Insufficient Privacy Protections:
The Problem: Many IoT devices collect vast amounts of personal and sensitive data (e.g., location, habits, biometrics) without always providing clear consent mechanisms or robust data handling policies. This data might then be shared with third parties.
The Concern: Beyond direct attacks, the sheer volume of personal data collected raises significant privacy concerns, especially if it falls into the wrong hands.
Supply Chain Risks:
The Problem: Vulnerabilities can be introduced at any stage of the complex IoT supply chain, from compromised components to insecure firmware inserted during manufacturing.
The Fallout: A single compromised component can affect thousands or millions of devices, as seen with some supply chain attacks in the broader tech industry.
The Elephant in the Room: Why Securing IoT is Hard
Diversity & Scale: The sheer number and variety of IoT devices (from tiny sensors to complex industrial machines) make a "one-size-fits-all" security solution impossible.
Resource Constraints: Many devices are low-power, low-cost, or battery-operated, limiting the computational resources available for robust encryption or security features.
Long Lifespans: Unlike phones, many IoT devices are expected to operate for years, even decades, long after manufacturers might cease providing support or updates.
Patching Complexity: Pushing updates to millions of geographically dispersed devices, sometimes with limited connectivity, is a logistical nightmare.
Consumer Awareness: Many consumers prioritize convenience and price over security, often unaware of the risks they introduce into their homes and networks.
Towards a More Secure IoT in 2025: Your Shield & Their Responsibility
While the challenges are significant, there's a collective effort towards a more secure IoT future. Here's what needs to happen and what you can do:
For Manufacturers (Their Responsibility):
Security by Design: Integrate security into the entire product development lifecycle from day one, rather than as an afterthought.
Secure Defaults: Ship devices with unique, strong, and randomly generated default passwords.
Robust Update Mechanisms: Implement easy-to-use, automatic, and regular firmware updates throughout the device's lifecycle.
Clear End-of-Life Policies: Communicate transparently when support and security updates for a device will cease.
Secure APIs: Design secure application programming interfaces (APIs) for cloud communication and mobile app control.
Adhere to Standards: Actively participate in and adopt industry security standards (e.g., ETSI EN 303 645, IoT Security Foundation guidelines, PSA Certified). Regulatory pushes in Europe (like the Cyber Resilience Act) and elsewhere are driving this.
For Consumers & Businesses (Your Shield):
Change Default Passwords IMMEDIATELY: This is your absolute first line of defense. Make them strong and unique.
Network Segmentation: Isolate your IoT devices on a separate Wi-Fi network (a "guest" network or a VLAN if your router supports it). This prevents a compromised IoT device from accessing your main computers and sensitive data.
Keep Firmware Updated: Regularly check for and apply firmware updates for all your smart devices. If a device doesn't offer updates, reconsider its use.
Disable Unused Features: Turn off any unnecessary ports, services, or features on your IoT devices to reduce their attack surface.
Research Before You Buy: Choose reputable brands with a track record of security and clear privacy policies. Read reviews and look for security certifications.
Strong Wi-Fi Security: Ensure your home Wi-Fi uses WPA2 or, ideally, WPA3 encryption with a strong, unique password.
Be Mindful of Data Collected: Understand what data your devices are collecting and how it's being used. If the privacy policy isn't clear or feels invasive, reconsider the device.
Physical Security: Secure physical access to your devices where possible, preventing easy tampering.
Regular Monitoring (for Businesses): Implement tools and processes to monitor network traffic from IoT devices for unusual or suspicious activity.
In 2025, the convenience offered by IoT devices is undeniable. However, their security is not a given. It's a shared responsibility that demands both diligence from manufacturers to build secure products and vigilance from users to deploy and manage them safely.
0 notes
Text
Why Enseur is Among the Best Event Ticketing Platforms for Seamless Event Success
In the fast-evolving world of event planning, offering a smooth and reliable ticketing experience is key to making any event a success. Whether it’s a concert, business conference, festival, or sports event, selecting the right event ticketing platform can set the tone for the entire attendee experience. Organizers today need a solution that not only helps sell tickets but also streamlines management, reporting, and on-site operations.
Among the various ticketing platforms for events, Enseur has earned a reputation for delivering everything event organizers need in one place. Let’s explore what makes Enseur stand out as one of the best solutions in this space.
A User-Friendly Experience for Both Organizers and Attendees
One of the top reasons event organizers look for modern event ticketing platforms is to provide a simple and hassle-free experience. No one wants ticket buyers to struggle with confusing interfaces or lengthy forms. Enseur offers a clean, mobile-friendly ticketing flow where attendees can easily choose their tickets, complete secure payments, and get instant confirmation — all in just a few clicks.
On the organizer’s side, the platform offers an easy-to-navigate dashboard that simplifies event setup. From creating different ticket categories (such as general admission, VIP, or early-bird) to setting up discount codes, everything can be done without any technical knowledge.
Flexible and Customizable Ticketing Options
Every event is unique, and the ticketing system should be able to adapt to its needs. What sets Enseur apart from many ticketing platforms for events is its flexibility. Organizers can create customized ticket types, set booking limits, and even offer group packages or add-ons like merchandise, meal coupons, or backstage passes.
Additionally, the platform supports branded e-tickets with QR codes, making check-in quick and professional. This level of customization ensures that whether you are planning a small workshop or a large-scale concert, you can tailor the ticketing process to fit your audience perfectly.
Secure Payment Processing With Multiple Options
One of the most important aspects of event ticketing platforms is ensuring that payments are handled safely and smoothly. ENSEUR integrates with multiple trusted payment gateways, enabling attendees to pay using a variety of methods, including credit cards, debit cards, UPI, net banking, and digital wallets.
Security is a top priority, and all transactions are encrypted to protect sensitive information. For organizers, the real-time payment tracking feature provides clear visibility into sales performance, helping with budgeting and planning.
Real-Time Analytics and Detailed Reporting
Data-driven decisions can greatly enhance event success. Enseur’s advanced analytics tools help organizers track ticket sales, monitor audience demographics, and identify peak booking times. These insights are presented in an easy-to-understand format through visual dashboards and downloadable reports.
This feature is especially useful for marketers who want to fine-tune their strategies or for organizers planning future events. Compared to many basic ticketing platforms for events, Enseur provides richer data that can help improve outcomes.
Smooth Onsite Check-In and Crowd Management
The event-day experience matters as much as the pre-event ticketing process. This helps reduce entry lines, manage crowd flow efficiently, and enhance overall guest satisfaction. The platform’s mobile-friendly tools ensure that your team can manage check-ins even with handheld devices, avoiding the need for expensive hardware.
Seamless Integration With Other Tools
Today’s events often rely on multiple tools for marketing, communication, audience engagement, and more. A good event ticketing platform should integrate with these tools to create a unified workflow. This means organizers can automate communications, send updates, and manage relationships with ease.
Scalable for Events of All Sizes
Whether you’re hosting a small seminar or a mega festival, Enseur’s platform is built to handle it. Its cloud-based infrastructure ensures that the system can scale to support thousands of attendees without lag or technical glitches. This makes it one of the most reliable ticketing platforms for events, trusted by organizers for everything from intimate gatherings to large public shows.
Affordable and Transparent Pricing
Budget is always a consideration when selecting an event technology partner. There are no hidden fees, and organizers get full value through powerful features, reliable support, and easy-to-use tools. Transparency in pricing helps organizers plan better without worrying about unexpected costs.
Final Thoughts
The right event ticketing platform does more than just sell tickets — it enhances the entire event experience for both attendees and organizers. With features like customization, secure payments, real-time analytics, and seamless check-in options, Enseur has become a trusted choice among event professionals.
If you’re looking to elevate your ticketing experience and create memorable events, choosing a platform like Enseur can make all the difference. A streamlined ticketing process not only boosts attendee satisfaction but also helps you achieve your event goals with confidence.
0 notes
Text
Future-Proof Your SMB: Why Sage Cloud Hosting Is the Smartest Move in 2025
Why SMBs Need Cloud Agility in 2025
The cloud computing market is projected to reach $793.8 billion by the end of 2025, and small-to-medium businesses (SMBs) are at the forefront of this transformation. With tighter margins and growing operational complexity, SMBs can't afford to rely on outdated desktop software or limited local servers.

Enter Sage Cloud Hosting — the bridge between traditional accounting power and the modern, scalable infrastructure needed to stay agile.
What Is Sage Cloud Hosting?
Sage Hosting involves running your Sage software — such as Sage 50, Sage 100, or Sage 300 — on a cloud-based server managed by a third-party hosting provider. This enables secure, remote access to your Sage applications from any device, anytime.
Whether you call it Sage application hosting, Sage hosting services, or Sage hosting solutions, the goal is the same: streamline operations, reduce IT overhead, and enable growth.
The Competitive Edge of Sage Hosting Solutions
Here’s what makes Sage cloud hosting essential for SMBs in 2025:
✅ Remote Flexibility
Empower your team to work securely from anywhere — perfect for hybrid or distributed workforces.
✅ Automatic Backups & Updates
Say goodbye to manual updates or lost data. Hosting providers automate everything in the background.
✅ Bank-Level Security
Advanced encryption, firewalls, and multi-factor authentication protect your financial data 24/7.
✅ Scalable Infrastructure
Add more users, apps, or storage in minutes — no new hardware needed.
✅ Reduced IT Costs
Eliminate the expense of maintaining on-site servers and hiring dedicated IT staff.
Side-by-Side Comparison: Sage Desktop vs. Sage Cloud Hosting
FeatureSage DesktopSage Cloud HostingAccessLocal machine onlyAnywhere, anytimeSecurityManual, limited to deviceAdvanced cloud-level securityUpdatesManualAutomaticBackupsUser-initiatedScheduled & automaticMulti-user SupportComplex setupBuilt-in collaborationIT MaintenanceIn-house requiredHandled by providerScalabilityLimitedEasily scalable
Who Benefits Most from Sage Hosting Services?
If you’re an SMB in industries like retail, construction, manufacturing, or professional services, you’ll see immediate ROI. Sage cloud hosting is especially valuable for:
Multi-location businesses needing centralized data access
Remote teams looking for seamless collaboration
Companies scaling quickly and outgrowing desktop limitations
CPA firms juggling multiple client accounts with security concerns
Step-by-Step Guide: How to Migrate to Sage Cloud Hosting
Making the move is easier than you think. Here’s how most reputable Sage hosting services handle it:
Step 1: Choose a Trusted Sage Hosting Provider
Look for providers with verified Sage compatibility, 24/7 support, and data centers that are SSAE-18 certified.
Step 2: Assess Your Needs
Decide which Sage version you need hosted and how many users will access it.
Step 3: Schedule a Migration
Your hosting partner will back up your current data, test the cloud environment, and set a go-live date.
Step 4: User Training & Access Setup
Each user gets a secure login. Basic training is often included to help your team adapt quickly.
Step 5: Go Live & Monitor
Once live, you’ll have real-time access to your Sage software — with performance monitoring and ongoing support.
Real-World Impact: SMBs Thriving on Sage Application Hosting
Case Example: A 15-employee construction firm in Ohio cut IT costs by 35% and doubled productivity within two months of switching to Sage 100 hosting. With real-time job costing accessible from field tablets, they streamlined billing and payroll like never before.
How to Choose the Right Sage Hosting Solution in 2025
Not all Sage hosting services are created equal. Use this checklist to compare:
✅ 99.99% Uptime Guarantee
✅ 24/7/365 Phone & Chat Support
✅ Compliance (SOC 2, HIPAA, GDPR if needed)
✅ Scalable Plans for Growth
✅ Free Migration Assistance
✅ Data Centers in Your Geographic Region
Final Thoughts: The Future Is in the Cloud
The shift to Sage cloud hosting is not just a trend — it’s a business imperative. SMBs that embrace this transition gain the flexibility, resilience, and agility needed to survive and thrive in today’s digital-first economy.
With the right Sage hosting provider, you’re not just moving software — you’re unlocking new potential for growth, cost-efficiency, and innovation.
#sage application hosting#sage cloud hosting#sage hosting#sage hosting services#sage hosting solutions
0 notes
Text
CPE Chip Market Analysis: CAGR of 12.1% Predicted Between 2025–2032

MARKET INSIGHTS
The global CPE Chip Market size was valued at US$ 1.58 billion in 2024 and is projected to reach US$ 3.47 billion by 2032, at a CAGR of 12.1% during the forecast period 2025-2032. This growth trajectory aligns with the broader semiconductor industry expansion, which was valued at USD 579 billion in 2022 and is expected to reach USD 790 billion by 2029 at a 6% CAGR.
CPE (Customer Premises Equipment) chips are specialized semiconductor components that enable network connectivity in devices such as routers, modems, and gateways. These chips power critical functions including signal processing, data transmission, and protocol conversion for both 4G and 5G networks. The market comprises two primary segments – 4G chips maintaining legacy infrastructure support and 5G chips driving next-generation connectivity with higher bandwidth and lower latency.
Market expansion is being propelled by three key factors: the global rollout of 5G infrastructure, increasing demand for high-speed broadband solutions, and the proliferation of IoT devices requiring robust connectivity. However, supply chain constraints in the semiconductor industry and geopolitical factors affecting chip production present ongoing challenges. Major players like Qualcomm and MediaTek are investing heavily in R&D to develop advanced CPE chipsets, while emerging players such as UNISOC and ASR are gaining traction in cost-sensitive markets. The Asia-Pacific region dominates production and consumption, accounting for over 45% of global CPE chip demand in 2024.
MARKET DYNAMICS
MARKET DRIVERS
5G Network Expansion Accelerates Demand for Advanced CPE Chips
The global transition to 5G networks continues to drive exponential growth in the CPE chip market. As telecom operators roll out next-generation infrastructure, the demand for high-performance customer premise equipment has surged by over 40% in the past two years. Modern 5G CPE devices require specialized chipsets capable of supporting multi-gigabit speeds, ultra-low latency, and massive device connectivity. Leading chip manufacturers are responding with integrated solutions that combine baseband processing, RF front-end modules, and AI acceleration. For instance, Qualcomm’s latest 5G CPE platforms deliver 10Gbps throughput while reducing power consumption by 30% compared to previous generations.
IoT Adoption Creates New Growth Avenues for CPE Chip Vendors
The proliferation of Internet of Things (IoT) applications across smart cities, industrial automation, and connected homes is generating significant opportunities for CPE chip manufacturers. With over 15 billion IoT devices projected to connect to networks by 2025, telecom operators require CPE solutions that can efficiently manage diverse traffic patterns and quality-of-service requirements. This has led to the development of specialized chipsets featuring advanced traffic management, edge computing capabilities, and enhanced security protocols. Recent product launches demonstrate this trend, with companies like MediaTek introducing chips optimized for IoT gateways that support simultaneous connections to hundreds of endpoints while maintaining reliable performance.
Remote Work Infrastructure Investments Fuel Market Expansion
The permanent shift toward hybrid work models continues to stimulate demand for enterprise-grade CPE solutions. Businesses worldwide are upgrading their network infrastructure to support distributed workforces, driving a 25% year-over-year increase in CPE deployments. This trend has particularly benefited manufacturers of chips designed for business routers and SD-WAN appliances, which require robust performance for VPNs, unified communications, and cloud applications. Leading semiconductor firms have responded with system-on-chip solutions integrating Wi-Fi 6/6E, multi-core processors, and hardware-accelerated encryption to meet these evolving requirements.
MARKET RESTRAINTS
Supply Chain Disruptions Continue to Challenge Production Stability
Despite strong demand, the CPE chip market faces persistent supply chain constraints that limit growth potential. The semiconductor industry’s reliance on advanced fabrication nodes has created bottlenecks, with lead times for certain components extending beyond 12 months. These challenges are compounded by geopolitical tensions affecting rare earth material supplies and export controls on specialized manufacturing equipment. While the situation has improved from pandemic-era shortages, inventory levels remain below historical averages, forcing many CPE manufacturers to implement allocation strategies and redesign products with available components.
Rising Component Costs Squeeze Profit Margins
Escalating production expenses present another significant restraint for CPE chip suppliers. The transition to more advanced process nodes has increased wafer costs by approximately 20-30% across the industry. Additionally, testing and packaging expenses have risen due to higher energy prices and labor costs. These factors have compressed gross margins, particularly for mid-range CPE chips where pricing pressure is most intense. Manufacturers are responding by optimizing chip architectures, consolidating IP blocks, and investing in yield improvement initiatives, but these measures require significant R&D expenditures that may take years to yield returns.
Regulatory Complexity Slows Time-to-Market
The CPE chip industry faces growing regulatory scrutiny that delays product launches and increases compliance costs. New spectrum regulations, cybersecurity requirements, and equipment certification processes have extended development cycles by 3-6 months on average. In particular, the automotive and industrial sectors now demand comprehensive safety certifications that require extensive testing and documentation. These regulatory hurdles disproportionately affect smaller chip vendors who lack dedicated compliance teams, potentially limiting innovation and competition in certain market segments.
MARKET CHALLENGES
Technology Complexity Increases Design and Validation Costs
Modern CPE chips incorporate increasingly sophisticated architectures that pose significant engineering challenges. Designs now routinely integrate multiple processor cores, AI accelerators, and specialized radio interfaces, requiring advanced simulation tools and verification methodologies. The associated R&D costs have grown exponentially, with some 5G chip development projects now exceeding $100 million in budget. This creates a high barrier to entry for potential competitors and forces established players to carefully prioritize their product roadmaps. Furthermore, the complexity makes post-silicon validation more difficult, potentially leading to costly respins if critical issues emerge late in the development cycle.
Talent Shortage Constrains Innovation Capacity
The semiconductor industry’s rapid expansion has created intense competition for skilled engineers, particularly in critical areas like RF design, digital signal processing, and physical implementation. CPE chip manufacturers report vacancy rates exceeding 30% for certain technical positions, with hiring cycles stretching to 9-12 months for specialized roles. This talent crunch limits companies’ ability to execute aggressive product roadmaps and forces difficult tradeoffs between projects. While firms are investing in training programs and academic partnerships, the pipeline for experienced chip designers remains insufficient to meet current demand.
Standardization Gaps Create Integration Headaches
The evolving nature of 5G and edge computing technologies has led to fragmented standards across different markets and regions. CPE chip vendors must support multiple protocol variants, frequency bands, and security frameworks, complicating both hardware and software development. This fragmentation increases testing overhead and makes it difficult to achieve economies of scale across product lines. While industry groups continue working toward greater harmonization, interim solutions often require additional engineering resources to implement customized features for specific customers or geographies.
CPE CHIP MARKET TRENDS
5G Network Expansion Accelerates Demand for Advanced CPE Chips
The rapid global deployment of 5G networks is significantly driving the CPE (Customer Premises Equipment) chip market, with the segment projected to grow at over 30% CAGR through 2032. Telecom operators worldwide invested nearly $280 billion in 5G infrastructure in 2023 alone, creating substantial demand for compatible CPE devices. Chip manufacturers are responding with innovative solutions featuring multi-band support and improved power efficiency, with next-generation modem-RF combos now achieving throughputs exceeding 7Gbps. While 4G CPE chips still dominate current installations, representing about 65% of 2024 shipments, 5G solutions are rapidly gaining share due to superior performance in high-density urban environments.
Other Trends
Smart Home Integration
The proliferation of IoT devices in residential settings, expected to reach 29 billion connected units globally by 2027, is creating new requirements for CPE chips that can handle simultaneous broadband and IoT traffic management. Modern gateway solutions now incorporate AI-powered traffic prioritization and mesh networking capabilities to maintain quality of service across dozens of connected devices. Semiconductor vendors have responded with system-on-chip (SoC) designs integrating Wi-Fi 6/6E, Bluetooth, and Zigbee radios alongside traditional cellular modems. North America leads this adoption curve, with over 75% of new home internet subscriptions in 2023 opting for smart gateway solutions compared to just 32% in 2020.
Edge Computing and Network Virtualization Impact Chip Designs
Emerging virtualization technologies are reshaping CPE architectures, creating demand for chips with enhanced processing capabilities beyond traditional modem functions. Virtual CPE (vCPE) solutions now account for 18% of business installations, requiring chipsets that can efficiently run containerized network functions (CNFs) while maintaining low power envelopes. The enterprise segment has proven particularly receptive, with large-scale adoption in multi-tenant office buildings and smart city applications. Meanwhile, silicon designed for edge computing applications is increasingly incorporating hardware acceleration blocks for AI inference, allowing real-time processing of video analytics and other bandwidth-intensive applications at the network periphery. This evolution has prompted traditional chip vendors to expand their portfolios through strategic acquisitions in the FPGA and specialty processor spaces.
COMPETITIVE LANDSCAPE
Key Industry Players
Innovation and Partnerships Fuel Growth in the CPE Chip Market
The global CPE (Customer Premises Equipment) chip market remains highly competitive, characterized by technological innovation and aggressive expansion strategies. Qualcomm dominates the market with its extensive portfolio of 4G and 5G chipsets, capturing approximately 35% revenue share in 2024. The company’s leadership stems from its strong foothold in North America and strategic partnerships with telecom operators.
MediaTek and Intel follow closely, collectively accounting for 28% market share, owing to their cost-effective solutions for emerging markets and industrial applications. These players continue investing heavily in R&D, particularly for energy-efficient 5G chips catering to IoT deployments and smart city infrastructure.
Chinese manufacturers like Hisilicon and UNISOC are rapidly gaining traction through government-supported initiatives and localized supply chains. Their aggressive pricing strategies and custom solutions for Asian markets have enabled 18% year-over-year growth in 2024, challenging established western players.
Meanwhile, specialized firms such as Eigencomm and Sequans are carving niche positions through innovative chip architectures optimized for low-power wide-area networks (LPWAN) and private 5G deployments. Their collaborations with network equipment providers have become crucial differentiators in this evolving landscape.
List of Key CPE Chip Manufacturers Profiled
Qualcomm Technologies, Inc. (U.S.)
UNISOC (Shanghai) Technologies Co., Ltd. (China)
ASR Microelectronics Co., Ltd. (China)
HiSilicon (Huawei Technologies Co., Ltd.) (China)
XINYI Semiconductor (China)
MediaTek Inc. (Taiwan)
Intel Corporation (U.S.)
Eigencomm (China)
Sequans Communications S.A. (France)
Segment Analysis:
By Type
5G Chip Segment Dominates the Market Due to its High-Speed Connectivity and Low Latency
The CPE Chip market is segmented based on type into:
4G Chip
5G Chip
By Application
5G CPE Segment Leads Due to Escalated Demand for High-Performance Wireless Broadband
The market is segmented based on application into:
4G CPE
5G CPE
By End User
Telecom Operators Segment Dominates with Growing Infrastructure Investments
The market is segmented based on end user into:
Telecom Operators
Enterprises
Residential Users
Regional Analysis: CPE Chip Market
North America The mature telecommunications infrastructure and rapid 5G deployments in the U.S. and Canada are fueling demand for high-performance 5G CPE chips, particularly from vendors like Qualcomm and Intel. With major carriers investing over $275 billion in network upgrades, chip manufacturers are prioritizing low-latency, power-efficient designs. However, stringent regulatory scrutiny on semiconductor imports creates supply chain challenges. The region also leads in IoT adoption, driving demand for hybrid 4G/5G chips in smart city solutions and enterprise applications. Local chip designers benefit from strong R&D ecosystems but face growing competition from Asian suppliers.
Europe EU initiatives like the 2030 Digital Compass (targeting gigabit connectivity for all households) are accelerating CPE chip demand, though adoption varies across nations. Germany and the U.K. lead in 5G CPE deployments using chips from MediaTek and Sequans, while Eastern Europe still relies heavily on cost-effective 4G solutions. Strict data privacy laws and emphasis on open RAN architectures are reshaping chip design requirements. The region faces headwinds from component shortages but maintains steady growth through government-industry partnerships in semiconductor sovereignty programs.
Asia-Pacific Accounting for over 60% of global CPE chip consumption, the region is driven by China’s massive “5G+” infrastructure push and India’s expanding broadband networks. Local giants HiSilicon and UNISOC dominate low-to-mid range segments, while South Korean/Japanese firms focus on premium chips. Southeast Asian markets show explosive growth (20%+ CAGR) due to rural connectivity projects. However, geopolitical tensions and import restrictions create supply volatility. Price sensitivity remains high, favoring integrated 4G/5G combo chips over standalone 5G solutions in emerging economies.
South America Limited 5G spectrum availability keeps the market reliant on 4G LTE chips, though Brazil and Chile are early adopters of 5G CPEs using ASR and MediaTek solutions. Economic instability and currency fluctuations hinder large-scale infrastructure investments, causing operators to prioritize cost-effective Chinese chip suppliers. The lack of local semiconductor manufacturing creates import dependency, but recent trade agreements aim to improve component accessibility. Enterprise demand for industrial IoT routers presents niche opportunities for mid-tier chip vendors.
Middle East & Africa Gulf nations (UAE, Saudi Arabia) drive premium 5G CPE adoption through smart city projects, leveraging Qualcomm and Eigencomm chips. Sub-Saharan Africa depends on affordable 4G solutions from Chinese vendors, with mobile network operators deploying low-power chips for extended coverage. While underdeveloped fiber backhaul limits 5G potential, satellite-CPE hybrid chips are gaining traction in remote areas. Political instability in some markets disrupts supply chains, though rising digitalization funds (like Saudi’s $6.4bn ICT strategy) indicate long-term growth potential.
Report Scope
This market research report provides a comprehensive analysis of the global and regional CPE Chip markets, covering the forecast period 2025–2032. It offers detailed insights into market dynamics, technological advancements, competitive landscape, and key trends shaping the industry.
Key focus areas of the report include:
Market Size & Forecast: Historical data and future projections for revenue, unit shipments, and market value across major regions and segments. The global CPE Chip market was valued at USD million in 2024 and is projected to reach USD million by 2032.
Segmentation Analysis: Detailed breakdown by product type (4G Chip, 5G Chip), application (4G CPE, 5G CPE), and end-user industry to identify high-growth segments and investment opportunities.
Regional Outlook: Insights into market performance across North America, Europe, Asia-Pacific, Latin America, and the Middle East & Africa, including country-level analysis where relevant. Asia-Pacific currently dominates the market due to rapid 5G adoption.
Competitive Landscape: Profiles of leading market participants including Qualcomm, UNISOC, ASR, Hisilicon, and MediaTek, including their product offerings, R&D focus, and recent developments.
Technology Trends & Innovation: Assessment of emerging technologies in semiconductor design, fabrication techniques, and evolving industry standards for CPE devices.
Market Drivers & Restraints: Evaluation of factors driving market growth such as 5G rollout and IoT expansion, along with challenges including supply chain constraints and regulatory issues.
Stakeholder Analysis: Insights for chip manufacturers, network equipment providers, telecom operators, investors, and policymakers regarding the evolving ecosystem.
Related Reports:https://semiconductorblogs21.blogspot.com/2025/06/fieldbus-distributors-market-size-and.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/consumer-electronics-printed-circuit.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/metal-alloy-current-sensing-resistor.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/modular-hall-effect-sensors-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/integrated-optic-chip-for-gyroscope.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/industrial-pulsed-fiber-laser-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/unipolar-transistor-market-strategic.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/zener-barrier-market-industry-growth.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/led-shunt-surge-protection-device.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/type-tested-assembly-tta-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/traffic-automatic-identification.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/one-time-fuse-market-how-industry.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/pbga-substrate-market-size-share-and.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/nfc-tag-chip-market-growth-potential-of.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/silver-nanosheets-market-objectives-and.html
0 notes
Text
Computer Storage Devices Market : Size, Trends, and Growth Analysis 2032
The Computer Storage Devices Market was valued at US$ 14,790.32 million in 2024 and is projected to grow at a CAGR of 2.99% from 2025 to 2032. This steady expansion reflects an ever-increasing global demand for faster, more reliable, and scalable storage solutions across both consumer and enterprise environments. As digital transformation intensifies across industries, storage devices are becoming more sophisticated, balancing capacity, speed, durability, and energy efficiency.
Understanding Computer Storage Devices
Computer storage devices refer to hardware components used to store, retrieve, and manage data in computing systems. These devices fall into two primary categories:
Hard Disk Drives (HDDs): Traditional storage media offering large capacities at relatively low costs. HDDs use spinning magnetic disks and are ideal for archival or bulk storage.
Solid-State Drives (SSDs): These use flash memory to deliver faster data access, greater energy efficiency, and enhanced durability. SSDs are rapidly replacing HDDs in laptops, servers, and gaming systems due to their performance advantages.
Other types of storage devices include optical drives (like CDs/DVDs), hybrid drives, USB flash drives, and external storage systems that cater to portable or backup use cases. In enterprise settings, large-scale storage solutions like network-attached storage (NAS), storage area networks (SANs), and cloud-integrated appliances are in high demand.
Market Drivers: Factors Fueling Growth
Digitalization and Data Explosion The exponential growth of data from IoT devices, video streaming, social media, and enterprise operations is fueling the need for advanced storage solutions. Cloud computing, big data analytics, and machine learning models require vast volumes of accessible, fast, and secure data storage.
Shift to SSDs While HDDs still dominate in terms of volume, SSD adoption is accelerating due to faster read/write speeds, lower latency, and decreasing cost per gigabyte. This transition is especially pronounced in laptops, data centers, and gaming devices.
Rise of Cloud Storage and Backup Solutions The increased adoption of hybrid and multi-cloud environments is changing the dynamics of the storage market. Organizations are embracing both on-premise and cloud-based storage for redundancy, disaster recovery, and remote access flexibility.
Edge Computing and Decentralized Storage With more computing power moving to the edge (near the source of data generation), there is growing demand for compact, high-performance local storage to process and store data in real time before syncing to central data centers.
Increased Use of Backup & Disaster Recovery Solutions Business continuity planning and cyber-resilience are critical for enterprises. As ransomware threats grow, companies are investing in robust backup systems and secure archival storage—driving demand for both hardware and cloud-integrated backup solutions.
Competitive Landscape: Key Players Shaping the Market
Numerous companies, from global tech giants to specialized vendors, are competing to offer cutting-edge storage solutions. The key players in the Computer Storage Devices Market include:
Dell EMC A dominant force in enterprise storage, Dell EMC offers a full suite of storage products, including PowerStore and Unity XT series, focusing on scalability, high performance, and data protection.
Quantum Corp Specializing in data backup and archive solutions, Quantum is renowned for its tape storage systems and object storage for unstructured data in media, defense, and surveillance sectors.
Kingston Technology A leading manufacturer of SSDs, memory cards, and USB drives, Kingston serves both consumers and enterprises with affordable, high-performance flash storage.
Blue Coat Systems Known primarily for its security and networking solutions, Blue Coat also contributes to secure data management by enabling encrypted storage and threat mitigation in cloud-based environments.
AWS (Amazon Web Services) As a major player in the cloud storage domain, AWS offers S3, EBS, and Glacier services for everything from high-availability storage to long-term archival.
SanDisk A division of Western Digital, SanDisk provides a wide variety of consumer and enterprise flash storage products, from portable drives to internal SSDs.
NetApp Offers high-performance enterprise data management solutions, including hybrid cloud storage systems and software-defined storage for mission-critical applications.
Polar Backup Focused on cloud backup and archival storage for SMEs and individual users, Polar Backup provides affordable solutions with high levels of data encryption and redundancy.
Challenges in the Market
Despite growth opportunities, the Computer Storage Devices Market faces several challenges:
Price Volatility in Memory Components: SSD prices can fluctuate due to NAND flash shortages or surpluses, affecting profitability and adoption rates.
Data Security and Privacy Concerns: With growing data regulation (e.g., GDPR, CCPA), manufacturers must embed stronger encryption, access control, and data residency features into their devices.
Technological Obsolescence: Rapid innovation means storage solutions can become outdated quickly, requiring businesses to invest in continual upgrades or risk falling behind.
Environmental Impact: E-waste and energy consumption from data centers and personal devices pose sustainability concerns that must be addressed with greener materials and energy-efficient designs.
Future Outlook
Looking ahead, the storage industry is likely to witness transformative developments:
Emergence of NVMe and PCIe 5.0: These interfaces promise massive leaps in SSD performance, enabling faster boot times and data access for applications like real-time analytics and 8K video editing.
Growth of DNA and Quantum Storage: While still in R&D phases, DNA-based and quantum storage technologies could redefine how data is stored in terms of density and longevity.
Integration with AI and Automation: Intelligent storage management, predictive analytics, and self-healing systems will become key differentiators for enterprise storage platforms.
Greater Adoption of Storage-as-a-Service (STaaS): Subscription-based models will gain popularity among SMBs and startups looking to scale storage needs flexibly without significant upfront investment.
Browse more Report:
RTLS in Healthcare Market
Tele-epilepsy Market
eClinical Solutions Market
Automotive Electrical Distribution System Market
Advanced Transportation Pricing System Market
0 notes
Text
SaaS Experts: Powering the Future of Scalable Software Solutions
In today’s fast-paced digital economy, Software as a Service (SaaS) has become the foundation of modern business operations. From startups to global enterprises, organizations rely on SaaS platforms to streamline operations, enhance productivity, and scale without the limitations of traditional software models. Behind every successful SaaS product are SaaS experts—strategists, engineers, and architects who bring innovation, scalability, and intelligent automation to life.
If you're looking to build or scale a cloud-based solution, it's essential to partner with seasoned SaaS experts who understand how to turn your ideas into secure, scalable, and user-centric products.
Who Are SaaS Experts?
SaaS experts are professionals specialized in designing, developing, deploying, and optimizing software delivered via the cloud. They bring a holistic understanding of cloud infrastructure, subscription-based business models, and user experience design to create products that are accessible anytime, anywhere.
Key areas of expertise include:
Cloud Architecture (AWS, GCP, Azure)
Multi-Tenant Systems
Data Security & Compliance
CI/CD Pipelines & DevOps
Performance Optimization
Subscription Billing Integration
Whether you're building a CRM, a financial analytics dashboard, or a niche collaboration tool, SaaS experts are critical to ensuring your product performs reliably and scales efficiently.
Why SaaS Is the Future of Software
SaaS is no longer a trend—it’s a standard. Here’s why businesses across sectors are adopting SaaS platforms at a record pace:
Accessibility: Use applications from any device, anywhere.
Lower Costs: No hardware or installation needed.
Scalability: Easily expand to support growing users.
Faster Deployment: Rapid development and time-to-market.
Automatic Updates: New features roll out seamlessly.
Forward-looking companies are going a step further by integrating AI product development into their SaaS platforms. AI-driven SaaS products offer real-time decision-making, intelligent automation, and personalized user experiences.
How SaaS Experts Power Your Business
Partnering with experienced SaaS experts can accelerate your product lifecycle, reduce development risk, and ensure long-term scalability. Here's how they contribute:
1. Strategic Planning
They help define your SaaS vision, assess the market landscape, and create a roadmap that aligns with your business goals.
2. Custom Architecture Design
From multi-tenancy to cloud-native environments, they build robust architectures optimized for performance and scalability.
3. User Experience Design
SaaS success relies heavily on user experience. Experts ensure intuitive interfaces, seamless navigation, and mobile responsiveness.
4. Security & Compliance
Data protection is critical. SaaS experts implement strong encryption, role-based access control, and regulatory compliance (e.g., GDPR, HIPAA).
5. Ongoing Support & Optimization
Post-launch, they monitor performance, apply updates, and continuously optimize based on user feedback and analytics.
SaaS Meets AI and Web3: A Powerful Convergence
Modern SaaS platforms are becoming smarter and more decentralized. By combining AI product development and Web3 development company capabilities, SaaS experts are building future-ready platforms with intelligent features and blockchain-backed transparency.
AI in SaaS: Automated workflows, chatbots, predictive analytics.
Web3 in SaaS: Decentralized access, token-based subscriptions, enhanced data control.
This convergence is reshaping industries like fintech, healthcare, logistics, and education, empowering users with smart, secure, and autonomous applications.
Choosing the Right Team: What to Look For
When you're ready to build a SaaS product, make sure to hire developers with deep SaaS experience—not just general coders. Look for a team with:
Proven experience in SaaS architecture
Deep knowledge of DevOps and CI/CD
Experience with AI and cloud technologies
Strong UI/UX and product strategy skills
Post-launch support and feature enhancement capabilities
A reliable SaaS partner acts not just as a service provider, but as a long-term product innovation partner.
Real-World Use Cases of SaaS Solutions
CRM & Sales Platforms (e.g., HubSpot, Salesforce)
Project Management Tools (e.g., Trello, Asana)
AI-powered Analytics (e.g., Mixpanel, Amplitude)
Blockchain-enabled Identity Management
Healthcare SaaS with Predictive Diagnostics
These are built and scaled by expert teams that understand both the business and technical aspects of SaaS delivery.
Final Thoughts
The digital-first future belongs to intelligent, flexible, and secure cloud-based platforms. By working with trusted SaaS experts, you ensure that your product is built to scale, perform, and deliver real value in a competitive market.Whether you’re a founder with a disruptive idea, a business leader planning digital transformation, or an enterprise aiming to modernize, SaaS experts are the cornerstone of your success. Combine their skills with innovation in AI product development, insights from a forward-thinking Web3 development company, and the right approach to hire developers, and you’re well on your way to launching software that thrives in today’s evolving digital landscape.
0 notes