#Enterprise Integration Strategy
Explore tagged Tumblr posts
Text
Improve Customer Service with Think AI’s Smart Agent CRM

Think AI’s Smart Agent CRM helps businesses talk to customers easily. It uses robots (chatbots) to answer questions and fix problems quickly. The system remembers what customers say and helps your team reply faster. This helps your team give good service. Think AI’s Smart Agent CRM is easy to use and can be set up for your business. It helps your team work faster and keep customers happy. With Think AI’s Smart Agent CRM, you can grow your business and make better relationships with customers. Let Think AI help you improve your service today!
0 notes
Text

Transform your business with Magtec ERP! 🌐✨ Discover endless possibilities on a single platform. Book a demo today and see how we can elevate your operations to the next level! 🚀📈
#magtec#magtecerp#magtecsolutions#erp#businesssolutions#digitaltransformation#innovation#technology#growth#efficiency#productivity#cloud#automation#management#software#enterprise#success#analytics#customization#scalability#integration#teamwork#collaboration#strategy#data#support#consulting#businessdevelopment#transformation#leadership
4 notes
·
View notes
Text

USA 1997
#USA1997#INTERACTIVE MAGIC#CHARYBDIS ENTERPRISES INC.#DIGITAL INTEGRATION LTD.#ADANAC COMMAND SYSTEMS#DAGGER INTERACTIVE TECHNOLOGIES#ALLIANCE INTERACTIVE SOFTWARE INC.#KESMAI CORPORATION#SIMULATION#STRATEGY#IBM#HIND#AIR WARRIOR III#DESTINY#IMA12 ABRAMS#AMERICAN CIVIL WAR FROM SUMPTER TO APPOMATTOX#HARPOON CLASSIC 97
9 notes
·
View notes
Text
7 Key Barriers Enterprises Must Conquer for Digital Transformation in 2025
Digital transformation isn’t just a buzzword anymore- it’s essential for staying competitive in today’s business world. As industries shift to data-driven, automated, and cloud-based operations, the need to modernize becomes critical. But change doesn’t come easy. Companies must navigate a host of transformation obstacles that can stall or derail progress. To empower enterprises to lead boldly in 2025, we’ve highlighted the key digital transformation challenges and practical ways to tackle them.

1. Lack of a Change Management Strategy
One of the most overlooked digital transformation challenges in 2025 is the absence of a well-defined change management plan. A successful transformation depends on how well the people in your organization adapt. Without a strategy to guide employees through the transition, businesses may struggle with resistance, miscommunication, and slow adoption.
A proactive change management plan addresses stakeholder concerns, sets realistic timelines, and creates clear communication pathways. It should also identify risks and involve leadership from the start to inspire alignment and buy-in.
2. Budget Constraints and Misaligned Investments
Limited budgets remain one of the biggest hurdles in digital transformation efforts. Organizations must make every dollar count, especially when implementing new technologies that require upfront investments.
The solution? Align transformation goals with business objectives and focus on cost-efficient strategies such as cloud-based solutions or hybrid platforms. These offer flexibility, scalability, and faster time-to-value without straining your budget.
3. Complex Technology Integration
Integrating emerging technologies with existing systems remains a core challenge. From legacy infrastructure to hybrid cloud environments, incompatibilities can cause major delays, inefficiencies, and data silos.
TGH addresses these transformation obstacles with deep expertise in enterprise application integration. Using platforms like Boomi and MuleSoft, we build secure, scalable integration frameworks that ensure smooth data flow and system interoperability. Our solutions reduce IT complexity while future-proofing your architecture.
4. Skill Gaps and Talent Shortages
Many digital transformation efforts fall short because there aren’t enough skilled professionals to drive them forward. From API management to cybersecurity, organizations require niche expertise that in-house teams may not possess.
To overcome these barriers, enterprises must either invest in upskilling programs or partner with integration experts like TGH. Our certified professionals bring hands-on knowledge of modern platforms, best practices, and tools- empowering your teams to succeed.
5. Data Security and Compliance Risks
Data breaches, ransomware, and compliance violations can significantly derail transformation efforts. As systems become more interconnected, so does the risk of exposure.
Organizations must prioritize cybersecurity across every layer of their enterprise digital strategy. Best practices include implementing encryption protocols, conducting routine security audits, adopting secure cloud solutions, and ensuring compliance with GDPR, HIPAA, and other relevant standards.
6. Employee Resistance to New Systems
People who aren’t keeping up with the latest technology often resist change. These employees may worry about job security or believe their current workflows are still sufficient.
To overcome digital transformation barriers like these, organizations must focus on user adoption. This includes delivering hands-on onboarding, continuous support, and clear communication about the benefits of transformation. TGH enables real-time enterprise application integration, helping teams embrace automation with confidence.
7. Difficulty Measuring ROI
Unlike conventional projects, the return on investment from digital transformation isn’t always immediately apparent. Gains such as increased agility, better user experience, and data-driven decision-making take time to materialize.
Still, ROI measurement is crucial. Enterprises can leverage API management solutions to track performance metrics, streamline data visibility, and enhance operational efficiency. The use of reusable APIs and smart integrations improves time-to-value, justifying the investment and reducing scepticism.

Why Partner with TGH?
TGH delivers trusted strategies to help tackle digital transformation challenges in 2025. We deliver robust integration frameworks, seamless API connectivity, and secure architecture design that aligns with your unique goals.
Our expertise spans:
Cloud and hybrid integration
Boomi and MuleSoft implementations
Real-time automation
Enterprise-grade API lifecycle management
Advisory and managed support services
Final Takeaway
Digital transformation isn’t a one-and-done initiative- it’s an ongoing journey of growth and innovation. While the challenges are real, they can absolutely be overcome. With the right strategy, talent, and integration partner, your enterprise can unlock powerful innovations and achieve long-term agility.
Start your journey today. Let TGH be your guide.
TGH Software Solutions Pvt. Ltd [email protected]
FAQs
What key challenges are businesses facing with digital transformation in 2025?
Some of the biggest challenges include lack of change management, budget constraints, integration complexities, skill gaps, and data security threats.
How can enterprises overcome digital transformation obstacles?
By aligning digital goals with business priorities, investing in upskilling, adopting secure integration platforms, and working with expert partners like TGH.
What does enterprise application integration mean, and why does it matter for businesses?
It refers to linking different software applications so they function together as one cohesive system. It improves workflow efficiency, data sharing, and decision-making.
How does API management support digital transformation?
API management enables scalable, secure communication between systems, simplifies third-party integrations, and accelerates digital deployment.
Why choose TGH for digital transformation support?
TGH combines technical excellence with business-first strategies, offering tailored integration services, 24/7 support, and a commitment to measurable outcomes.
#Transformation Obstacles#Digital Transformation#Enterprise application integration#API management solutions#digital transformation challenges 2025#overcoming digital transformation barriers#enterprise digital strategy#common digital transformation issues
0 notes
Text
How Cloud Migration Services are Reshaping Business Operations
Cloud Migration Services Market: Trends, Growth, and Forecast
The Cloud Migration Services Market is witnessing significant growth as businesses increasingly adopt cloud-based solutions to enhance efficiency, scalability, and cost-effectiveness. As organizations strive to modernize their IT infrastructure, the demand for seamless and secure cloud migration services continues to rise.
Request Sample PDF Copy:https://wemarketresearch.com/reports/request-free-sample-pdf/cloud-migration-services-market/996
Cloud Migration Services Market Size and Share
The Cloud Migration Services Market Size is expanding rapidly, driven by the increasing need for enterprises to move their workloads, applications, and data to the cloud. The market is segmented based on service types, deployment models, enterprise sizes, and industries. With the growing adoption of hybrid and multi-cloud strategies, the Cloud Migration Services Market Share is being distributed across major cloud service providers such as AWS, Microsoft Azure, and Google Cloud Platform.
Cloud Migration Services Market Growth and Trends
The Cloud Migration Services Market Growth is fueled by various factors, including digital transformation initiatives, cost savings, improved security measures, and enhanced operational efficiency. Enterprises are leveraging AI and automation in cloud migration processes, further accelerating adoption rates. Among the key Cloud Migration Services Market Trends, hybrid and multi-cloud deployments are gaining momentum as businesses seek flexibility and risk mitigation strategies.
Key Drivers of Market Growth
Several factors are propelling the growth of the cloud migration services market:
Adoption of Hybrid Cloud Solutions: Organizations are increasingly implementing hybrid cloud strategies to optimize workloads, enhance data management, and reduce operational costs.
Need for Business Agility: The demand for rapid and streamlined application deployment through pay-as-you-go models has made cloud migration services essential for modern business strategies.
Implementation of Automation Solutions: The growing adoption of automation tools in cloud migration processes reduces manual intervention, accelerates time-to-value, and ensures compliance.
Market Segmentation
The cloud migration services market can be segmented based on service type, deployment model, organization size, application, and vertical:
Service Type: Includes automation, integration, disaster recovery, application hosting and monitoring, DevOps, training and consulting, support and maintenance.
Deployment Model: Comprises public, private, and hybrid clouds.
Organization Size: Caters to both large enterprises and small and medium-sized enterprises (SMEs).
Application: Encompasses project management, infrastructure management, security and compliance management, among others.
Verticals: Serves various sectors such as banking, financial services, and insurance (BFSI), healthcare and life sciences, telecommunications and ITES, manufacturing, retail, and entertainment.
Cloud Migration Services Market Price and Potential
The Cloud Migration Services Market Price varies based on factors such as migration complexity, the volume of data, customization requirements, and additional security features. Enterprises are investing in cloud migration services to reduce operational expenses and improve system performance. The Cloud Migration Services Market Potential remains vast, with small and medium-sized enterprises (SMEs) increasingly adopting cloud migration strategies to compete with larger enterprises.
Cloud Migration Services Market Forecast and Analysis
The Cloud Migration Services Market Forecast suggests continued expansion, with a projected compound annual growth rate (CAGR) in the coming years. The market's upward trajectory is supported by increased cloud adoption across industries, advancements in cloud technologies, and the rising need for remote work solutions. A comprehensive Cloud Migration Services Market Analysis indicates that North America and Europe hold a dominant position, while the Asia-Pacific region is emerging as a key growth market due to rapid digitization efforts.
Competitive Landscape
The cloud migration services market is characterized by the presence of major players such as Accenture PLC, IBM Corporation, Amazon Web Services Inc., Cisco Systems Inc., and Microsoft Corporation.
These companies are continually innovating and expanding their service offerings to cater to the evolving needs of businesses undergoing cloud transformation.
Future Outlook
The cloud migration services market is poised for continued growth, driven by technological advancements, increasing adoption of hybrid and multi-cloud strategies, and the rising need for business agility and automation. As organizations continue to prioritize digital transformation, the demand for efficient and secure cloud migration services is expected to escalate, offering significant opportunities for service providers in this dynamic market.
Regional Insights
North America holds a significant share of the cloud migration services market, attributed to its advanced technological infrastructure and mature IT landscape. The region's businesses leverage cloud solutions to gain enhanced flexibility, scalability, cost efficiency, and business continuity.
Other regions, including Europe and Asia-Pacific, are also witnessing substantial growth due to increasing digital transformation initiatives and cloud adoption.
Related Report:
Fraud Detection and Prevention Market:
https://wemarketresearch.com/reports/fraud-detection-and-prevention-market/1114
Video Conferencing Market:
https://wemarketresearch.com/reports/video-conferencing-market/929
Conclusion
The Cloud Migration Services Market is poised for substantial growth as businesses increasingly rely on cloud-based solutions. With evolving Cloud Migration Services Market Trends, enterprises are embracing hybrid and multi-cloud approaches, automation, and AI-driven migration tools. As the demand for cloud migration services rises, organizations must stay informed about Cloud Migration Services Market Analysis and forecasts to make strategic decisions that align with their digital transformation goals.
#Cloud Migration#Cloud Computing#Cloud Services#Cloud Transformation#Cloud Adoption#Digital Transformation#Cloud Infrastructure#Cloud Strategy#IT Modernization#Enterprise Cloud Solutions#Hybrid Cloud#Public Cloud#Private Cloud#Multi-Cloud#Cloud Security#Cloud Cost Optimization#Cloud Service Providers#Cloud Migration Tools#Cloud Integration#Data Migration#Cloud Scalability
0 notes
Text
The State of AI: Navigating the Future of Enterprise Intelligence.
Sanjay Kumar Mohindroo Sanjay Kumar Mohindroo. skm.stayingalive.in Explore expert insights and actionable strategies on the state of AI to drive innovation and cut costs in your enterprise. Executive Summary – A Bold Overview for Global IT Leaders In 2025, AI stands at a crossroads of innovation and integration. The rise of generative AI has pushed enterprises into a new era of digital…
#AI Integration#AI tax#centralized AI platforms#CIO priorities#Data-driven decision-making in IT#digital transformation leadership#emerging technology strategy#enterprise AI#Generative AI#IT operating model evolution#News#Sanjay Kumar Mohindroo
0 notes
Text
Request a Winmill PPM Demo | Experience Project Management Excellence
Welcome to Winmill PPM, a Division of Winmill Software. Our sole focus is to provide premier PPM solutions and services to our clients. We are North America’s leading experts in Gartner’s highest-rated PPM solutions from Planview and Broadcom. Whichever solutions are right for your organization, let Winmill delight you with our world-class customer service and experience.
Ready to start a project with us? Let us know what's on your mind.Request your personalized demo today and explore how Winmill PPM can transform the way you manage projects, prioritize initiatives, and achieve your business goals.
To know more:https://ppm.winmill.com/contact-us/
#agile transformation strategy#enterprise portfolio management software#tasktop integration#enterprise ppm tools#value stream management software
0 notes
Text
Why Every Saudi Business Needs a Mobile App Integration Strategy

Now mobile apps have become an indispensable tool for businesses across the globe, and Saudi Arabia is no exception. As more consumers turn to mobile devices for their shopping, communication, and entertainment needs, businesses must meet these demands by offering mobile apps that are functional and integrated seamlessly with other systems. This is where a mobile app integration strategy comes into play. Let’s delve into why such a strategy is crucial for every Saudi business.
The Increasing Significance of Mobile Apps in Saudi Arabia
Saudi Arabia has seen a significant surge in mobile app usage, driven by a tech-savvy population and increasing smartphone penetration. From e-commerce to banking, customers expect businesses to offer mobile solutions that are intuitive and efficient. However, simply having a mobile app is no longer enough. To stay competitive, businesses must ensure their apps are integrated with other platforms and services to deliver a seamless user experience.
What is Mobile App Integration?
Mobile app integration involves connecting a mobile application with various external systems, such as databases, cloud services, and other software applications. This integration ensures that the app can communicate with these systems in real time, providing users with up-to-date information and a cohesive experience across multiple touchpoints.
Why is Mobile App Integration Crucial for Saudi Businesses?
Enhancing User Experience
User experience (UX) plays a pivotal role in determining the success of any mobile application. When an app is well-integrated, users can effortlessly navigate through its features, access the information they need, and perform actions such as making purchases or booking services without any hiccups. For Saudi businesses, providing a superior user experience is key to retaining customers and encouraging repeat business.
Streamlining Operations
Mobile app integration isn’t just about the front-end user experience; it also has significant benefits on the backend. By integrating mobile apps with internal systems such as inventory management, CRM, and payment gateways, businesses can streamline their operations. This integration reduces manual processes, minimizes errors, and ensures that all parts of the business are working in sync.
Driving Business Growth
A well-integrated mobile app can be a powerful driver of business growth. Integration empowers businesses to swiftly introduce new features and services, adapt to shifting market demands, and scale their operations effectively. For example, integrating a mobile app with a loyalty program can help increase customer engagement, while integration with analytics tools can provide valuable insights into user behavior, helping businesses make data-driven decisions.
Key Components of a Mobile App Integration Strategy
API Integration
At the heart of mobile app integration lies API (Application Programming Interface) integration. APIs facilitate communication between different software applications, ensuring seamless data exchange. For Saudi businesses, integrating APIs is crucial for creating a connected ecosystem where various services work together harmoniously, enhancing both functionality and user experience.
Cloud-Based Integration
Cloud-based integration solutions provide scalability, flexibility, and cost-efficiency, making them an appealing choice for businesses in Saudi Arabia. By leveraging the cloud, businesses can easily scale their operations, reduce costs, and enhance the reliability of their mobile apps. Cloud technology also simplifies the integration process, allowing businesses to connect their mobile apps with other systems without the need for complex infrastructure.
Security and Compliance
In Saudi Arabia, businesses must adhere to strict data protection regulations. Ensuring that a mobile app integration strategy complies with these regulations is essential. This involves implementing robust security measures, such as encryption and authentication, to protect user data and prevent unauthorized access.
Challenges in Mobile App Integration
Despite its benefits, mobile app integration can present several challenges. These may include technical difficulties, such as compatibility issues between different systems, and the complexity of managing multiple integrations. Additionally, businesses may face challenges in ensuring that their integration strategy is scalable and future-proof, capable of accommodating new technologies and evolving business needs.
Overcoming Integration Challenges
To overcome these challenges, businesses should start by developing a clear integration plan that outlines their goals, the systems that need to be integrated, and the expected outcomes. It’s also important to choose the right technology and partners for the integration process. Working with experienced integration partners who understand the unique needs of Saudi businesses can help ensure a successful outcome.
The Future of Mobile App Integration in Saudi Arabia
As Saudi Arabia continues to embrace digital transformation, the importance of mobile app integration will only grow. Emerging trends such as artificial intelligence (AI), machine learning (ML), and the Internet of Things (IoT) are set to revolutionize the way businesses integrate their mobile apps. By staying ahead of these trends and continuously updating their integration strategies, Saudi businesses can maintain a competitive edge in the market.
Choosing the Right Integration Partner
When selecting an integration partner, businesses should consider several factors. Experience in the Saudi market is essential, as is expertise in the relevant technologies. Businesses should seek out partners with a proven history of successful integrations and the capability to offer continuous support and maintenance.
Conclusion
In today’s digital landscape, a mobile app integration strategy is not just an option—it’s a necessity for Saudi businesses. By integrating their mobile apps with other systems, businesses can enhance user experience, streamline operations, and drive growth. As the industry evolves, staying ahead of integration trends and working with the right partners will be key to long-term success.
FAQs
1. What is mobile app integration, and why is it important?Mobile app integration involves connecting a mobile app with external systems and platforms to enable seamless data exchange and enhanced functionality. It's important because it ensures that the app works smoothly within a broader digital ecosystem, providing users with a cohesive experience.
2. How does API integration benefit my mobile app?API integration allows different software applications to communicate with each other, enhancing the functionality and user experience of your mobile app. It enables real-time data updates, seamless transactions, and personalized user experiences.
3. What are the key components of a successful mobile app integration strategy?The key components include API integration, cloud-based integration, and robust security measures. These elements work together to create a connected ecosystem that supports your business goals.
4. What challenges might Saudi businesses face during mobile app integration?Common challenges include technical difficulties, compatibility issues, and the complexity of managing multiple systems. Ensuring scalability and compliance with data protection regulations can also be challenging. 5. How can businesses choose the right integration partner?Businesses should look for partners with experience in the Saudi market, expertise in the relevant technologies, and a proven track record of successful integrations. Ongoing support and maintenance capabilities are also important considerations.
#Mobile app integration for Saudi businesses#Saudi business app strategy#Mobile app integration solutions Saudi Arabia#Custom app integration Saudi business#Saudi business mobile strategy#App integration for Saudi enterprises#Mobile app strategy for Saudi companies#Integration solutions for Saudi business apps#Saudi Arabian mobile app development#Mobile app integration benefits for Saudi businesses#Efficient app integration in Saudi Arabia#App integration strategy for Saudi enterprises#Mobile app growth strategies Saudi Arabia#Business app integration solutions Saudi#App integration services for Saudi businesses
1 note
·
View note
Text
Do You Need Enterprise Integration Services?
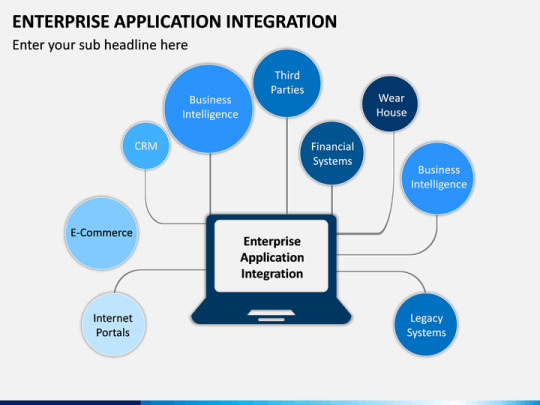
Do you need them? In this blog, we will discuss what enterprise integration Services is and how it produces value for the organization.
What is Enterprise Integration?
Enterprise Integration Services refers to connecting disparate applications, systems, and data sources to support communication and workflows in an organization. Enterprise integration enables an organization to:
Automate Processes
Improve Data Consistency
Streamline their Processes
Reduce the Errors associated with manual data entry
Get insights instantaneously to guide better decisions making
Through the integration of a disparate enterprise application, an organization can integrate its operations, so information flows seamlessly within the organization’s various departments (e.g., Sales/ Customer Service, Supply Chain, Finance, etc).
Indications that your company needs enterprise integration services
If you are struggling with one or more of the following scenarios within your company, that is a strong signal that enterprise integration services can be a solution for your company.
1. You have multiple siloed software systems.
Various tools are utilized across the organization: CRM (customer relationship management), ERP (enterprise resource planning), HRM (human resource management), and some types of cloud storage.
When these systems are only used individually and not integrated in a meaningful way, data inconsistency and inefficiencies arise.
2. Discrepancies in data from one platform to another.
You may have confusing customer records, inventory levels, or financial reports. When companies have multiple, siloed databases, data inconsistency is a common event. Integration ensures data consistency, minimizing the likelihood of errors.
3. Manual Data Entry is Hindering Your Business
If workers spend too much time copying data manually between systems, they’re probably wasting precious hours that could be devoted to more valuable work. Enterprise integration automates duplicative data entry and eliminates human error.
4. Insufficient Real-Time Insights and Reporting
Companies require correct, current information for sound decision-making. Without integration, extracting information from multiple systems is time-consuming and prone to errors. Integrated systems facilitate real-time analysis and reporting, which allows for timely business planning.
5. Difficulty Scaling Operations
As companies grow, they need smooth processes that can handle larger workloads. In the absence of integration, implementing new software, expanding staff, or serving more customers can become disorderly. An efficiently integrated enterprise system provides for easy scalability.
6. Decline in Customer Experience Due to Decoupled Systems
Customer support agents have difficulty because they cannot access order histories or requests for service because of decoupled systems. This leads to frustration and delays. By unifying all of the customer information, you will be able to respond faster, as a unified database leads to better customer satisfaction ratings.
Key benefits of enterprise integration services
1. Improved efficiency and productivity
Enterprise integration services provide better efficiency and productivity by enhancing workflows and reducing manual labor so that employees can focus on strategic work rather than spending hours on data entry and navigation of systems.
2. Cost Savings
Systems integration eliminates duplicate data, eliminates the need for multiple software applications, and minimizes labor expenses associated with manual processing.
3. Enhanced Data Accuracy and Security
Integration solutions make all business applications harmonize, lowering the risk of data discrepancies and enhancing security through centralized access controls.
4. Enhanced Decision-Making
Having access to real-time data makes it possible for business leaders to make the appropriate decisions on the management of inventory, tracking customer trends, and planning finances.
5. Better Compliance and Risk Management
Various industries have strict processes in place for the compliance of laws like GDPR, HIPAA, and PCI-DSS. Business process integration ensures a rigorous audit trail, secure data transfers, compliance, and privacy.
6. Smoother Collaboration
Integrated systems ensure that departments have easy access to shared data, making cross-department collaboration and communication better and providing potential for enhanced productivity.
Source Link: https://bit.ly/4jhn3Tb
0 notes
Text
Strategic Approaches to Generative AI Adoption in Enterprises

In the past twelve months, the corporate landscape has been abuzz with the potential of generative AI as a groundbreaking innovation. Despite broad recognition of its transformative power, many firms have adopted a tentative stance, cautiously navigating the implementation of this technology.
Is a cautious approach prudent, or does it inadvertently place companies at risk of lagging in a rapidly evolving technological landscape?
Recent investigations forecast the staggering benefits of generative AI, suggesting potential productivity gains in trillions of dollars per annum by 2030 if harnessed effectively.
The rewards surpass the apprehensions, provided the adoption of this technology is executed with strategic foresight. It's not about restricting generative AI but about sculpting its usage within well-defined parameters to mitigate potential challenges, including uncontrolled expenses, security breaches, compliance issues, and employee engagement.
Below, we outline ten strategic approaches for enterprises to capitalize on generative AI effectively and securely.
Adopt a Streamlined Approach to Business Case Development: Generative AI, an emerging technology, demands a departure from traditional business case development. Enterprises should prioritize rapid experimentation and learning to pinpoint practical technology applications swiftly. Discover and Explore
Action Points:
Accelerate pilot projects and proof-of-concept initiatives to cultivate knowledge and skills.
Discover and Explore and Test on repeat
Avoid:
Postponing initiatives due to the need for more absolute clarity.
Over-reliance on cumbersome business case development processes.
Initiate with Straightforward Applications: Before venturing into more complex applications, begin by unlocking value within existing business processes.
Action Points:
Concentrate on internal applications as foundational steps.
Prioritize data readiness for customized solutions.
Avoid:
Early deployment of customer-facing applications due to higher associated risks.
Use case lock where you’re working to solve a specific problem in one particular way.
Streamline Technology Evaluation: Most generative AI tools offer similar capabilities, rendering extensive evaluation unnecessary.
Action Points:
Collaborate with firms like Karini.ai for initial use cases whose platform provides immediate access to no-code tools for operationalizing Gen AI smartly.
Focus on trust and integration capabilities that open your LLMs, Models, and Data to all available options.
Avoid:
Elaborate and potentially outdated analysis of technology providers.
Vendor lock on a single platform that will cause crippling limitations.
Harness External Expertise: The scarcity of AI expertise necessitates partnerships for successful implementation and integration.
Action Points:
Assess internal expertise gaps, seek external support accordingly, and embrace a low-code/no-code platform, i.e., Karini.ai, which will keep the journey quick and safe.
Facilitate technology assimilation into the enterprise.
Avoid:
Isolated attempts at implementation.
Restrictive partnerships limit future technological choices.
Design a Flexible System Architecture: Architectures must be dynamic to accommodate evolving technologies, use cases, and regulatory landscapes.
Action Points:
Foster innovative and forward-thinking architectural design.
Anticipate and plan for future architectural adjustments.
Avoid:
Rigid architectures based on present-day technology functioning.
Over-reliance on existing processes for future technology support.
Implement Robust Security Protocols: Addressing generative AI's unique security challenges through custom policies and robust partnerships.
Action Points:
Develop tailored policies and procedures.
Partner with platforms that are active protectors of your data security.
Avoid:
Dependence on outdated security frameworks.
Technology adoption paralysis due to fear of risk.
Establish Innovative KPIs: New KPIs should reflect generative AI's unique value and impact on business operations.
Action Points:
Develop KPIs centered around long-term value creation.
Learn from both successes and failures.
Avoid:
Ignoring the learning opportunities presented by unsuccessful initiatives.
Foster Open Communication: Ensure continuous feedback and open communication channels for iterative improvement and employee engagement.
Action Points:
Integrate feedback mechanisms into all AI systems, like Karini uses in our CoPilot. 👍👎💬
Maintain transparent communication about AI's impact on the workforce.
Avoid:
Relying solely on conventional feedback methods.
Promote Comprehensive Learning and Development: Equip employees with the necessary skills and understanding to leverage AI tools effectively.
Action Points:
Provide extensive learning opportunities; Gen AI is empowering.
Align learning initiatives with broader change management strategies.
Avoid:
Limiting learning opportunities to direct users of AI tools AI needs to be democratized.
Embrace Iterative Learning: Cultivate a learning and continuous improvement culture to maximize the value derived from generative AI.
Action Points:
Prioritize learning and skill enhancement.
Engage in iterative development to refine use cases and technology applications.
Avoid:
Pursuing overly ambitious initial use cases.
Disregarding the evolving nature of AI technologies.
As enterprises stand at the cusp of this generative AI revolution, adopting a 'wait-and-see' approach may inadvertently place them at a competitive disadvantage.
The promise of generative AI far overshadows the perceived risks, demanding proactive engagement rather than cautious observation. Now is the opportune moment for enterprises to embrace generative AI, navigating its introduction with calculated measures to offset potential risks.
For further insights, explore our website or engage with our team.
About us:
Fueled by innovation, we're making the dream of robust Generative AI systems a reality. No longer confined to specialists, Karini.ai empowers non-experts to participate actively in building/testing/deploying Generative AI applications. As the world's first GenAIOps platform, we've democratized GenAI, empowering people to bring their ideas to life – all in one evolutionary platform.
Contact us:
Jerome Mendell
(404) 891-0255
#Generative AI Best Practices#Enterprise Gen AI Integration#Karini AI Gen AI Guide#Generative AI Strategies#Mastering Generative AI#artificial intelligence#generative ai#chatgpt#machine learning#karini ai
1 note
·
View note
Text
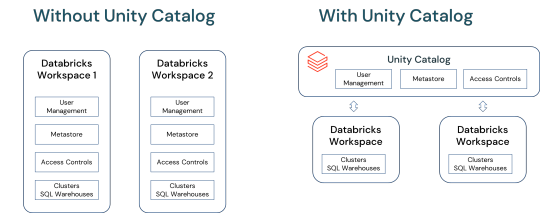
Unlocking Full Potential: The Compelling Reasons to Migrate to Databricks Unity Catalog
In a world overwhelmed by data complexities and AI advancements, Databricks Unity Catalog emerges as a game-changer. This blog delves into how Unity Catalog revolutionizes data and AI governance, offering a unified, agile solution .
View On WordPress
#Access Control in Data Platforms#Advanced User Management#AI and ML Data Governance#AI Data Management#Big Data Solutions#Centralized Metadata Management#Cloud Data Management#Data Collaboration Tools#Data Ecosystem Integration#Data Governance Solutions#Data Lakehouse Architecture#Data Platform Modernization#Data Security and Compliance#Databricks for Data Scientists#Databricks Unity catalog#Enterprise Data Strategy#Migrating to Unity Catalog#Scalable Data Architecture#Unity Catalog Features
0 notes
Text
IoT Network Protocols (e.g., MQTT, CoAP)
Harness robust IoT network protocols, including MQTT and CoAP, for seamless connectivity!
#IoT software development services#embedded software development services#IoT device selection#IoT strategy consultation#IoT data visualization tools#edge computing for IoT#IoT network protocols (e.g.#MQTT#CoAP)#IoT user experience design#AI in IoT solutions#IoT and blockchain integration#IoT app design services#IoT app development#IoT device integration#IoT data analytics services#IoT security solutions#custom IoT application development#enterprise IoT services#industrial IoT solutions#IoT firmware development#IoT cloud integration#IoT connectivity solutions#mobile app development#software development#TechAhead Corp#TechAheadCorp#techaheadcorp.com
0 notes
Text
DARK SMS - DRAGON+ (2)

In today's fast-paced digital landscape, privacy and security have become paramount for individuals and businesses alike. Enter DarkSMS, your ultimate solution for secure, reliable communication. With a focus on providing virtual phone numbers for SMS, DarkSMS empowers users to maintain their anonymity while effortlessly receiving verification messages and engaging in private text exchanges. Our state-of-the-art text message service ensures that you can communicate confidently without compromising your personal information. Whether you're looking to streamline your business communications or protect your privacy during online transactions, DarkSMS offers a virtual SMS number tailored to meet your needs.
Virtual Phone Number For SMS
A virtual phone number for sms is an innovative solution that allows users to send and receive text messages without the need for a traditional phone line. This service is especially beneficial for individuals and businesses aiming to enhance their communication strategies while maintaining privacy and flexibility. With the advent of digital communication, virtual phone numbers have become increasingly popular for various applications, including verification SMS and marketing campaigns.
One of the primary advantages of utilizing a virtual phone number for SMS is the anonymity it offers. Users can keep their personal numbers private while still engaging with customers or verifying accounts through text message services. This is particularly important for maintaining security in today’s digital landscape.
Furthermore, a virtual phone number can cater to global communication, allowing businesses to reach customers in different countries without incurring hefty international charges. Users can receive SMS from any carrier as long as they have an active internet connection, making it a cost-effective option for startups and established enterprises alike.
Additionally, many providers offer a range of features with their virtual SMS numbers, including message scheduling, automatic replies, and integration with third-party applications. These features enhance user experience and streamline communication efforts, making it easier than ever to engage with your audience.
In conclusion, investing in a virtual phone number for SMS can significantly improve your communication strategy. Whether you require it for sending verification SMS or for managing your text message service, the benefits of increased privacy, cost-efficiency, and advanced features make it a wise choice for both personal and professional use.
Verification SMS
Verification SMS is a crucial aspect of today's digital landscape. These messages are typically sent to users to confirm their identity, ensuring security and privacy during online transactions or account creations. Utilizing a virtual phone number for SMS can enhance this process by providing added layers of anonymity and security.
When a user registers for a service or needs to verify their identity, they often receive a verification SMS containing a unique code. This code must be entered into the application or website to complete the verification process. Employing a text message service that utilizes virtual numbers simplifies this procedure, allowing users to complete verifications without exposing their personal phone numbers.
One of the significant advantages of using a virtual SMS number for verification messages is that it prevents unwanted spam on personal devices and keeps personal communications confidential. Additionally, businesses can manage multiple virtual numbers, ensuring efficient handling of verification messages for various purposes—from customer registrations to secure transactions.
In conclusion, utilizing a virtual phone number for verification sms is not only beneficial for user privacy but also essential for maintaining the integrity of online interactions. Ensuring a seamless verification process with reliable text message services can significantly enhance user experience.
Text Message Service
A text message service is an essential tool in today's fast-paced digital world. It provides users with the ability to send and receive SMS messages efficiently, ensuring seamless communication at all times. Whether for personal uses, such as keeping in touch with friends and family, or business applications, where sending alerts, reminders, or promotional content becomes crucial, a reliable text message service can enhance connectivity.
Among the various options available, using a virtual phone number for SMS has gained popularity. These virtual numbers allow users to send and receive messages without the need for a physical SIM card, offering flexibility and privacy. Moreover, they are particularly beneficial for verification SMS when creating accounts on online platforms, as they help protect personal phone numbers from potential spam and unwanted contacts.
Another significant advantage of a text message service is its scalability. Businesses can easily manage bulk messaging campaigns, automating responses and engaging customers effectively. Such services often come with features like message tracking and analytics, which provide insights into the performance of SMS campaigns and help to refine messaging strategies.
In summary, a good text message service can bridge communication gaps, ensure authenticity through verification SMS, and enhance user experience with virtual SMS numbers. Investing in a robust text messaging solution is vital for anyone looking to improve their communication channels.
Virtual SMS Number
A virtual SMS number serves as an essential tool for individuals and businesses that require a reliable means of sending and receiving text messages without the need for a physical SIM card. These numbers are increasingly popular due to their numerous advantages, especially in a world where communication happens rapidly and often through digital mediums.
One of the primary benefits of utilizing a virtual SMS number is the privacy it offers. Users can keep their personal phone numbers confidential while still being reachable for verification SMS or text message services. This is particularly useful for online transactions and registration processes where sensitive information needs protection.
Furthermore, virtual sms number can be easily managed through various platforms, enabling users to organize and track message exchanges more efficiently. They come with scalable options, allowing companies to manage multiple virtual numbers for different purposes, such as customer service, marketing campaigns, or even personal use.
In today’s fast-paced environment, having a virtual SMS number can enhance communication strategies. It provides flexibility to engage with clients and stakeholders across the globe without racking up excessive costs associated with international messaging.
In summary, adopting a virtual SMS number can streamline communication, boost privacy, and increase operational efficiency. It is a vital asset, especially for those utilizing a virtual phone number for SMS-related services, creating a seamless experience in today's interconnected landscape.
511 notes
·
View notes
Text


New uncensored chinese period BL The Mountains and Rivers Are Forever Silent (山河永寂)
The drama is based on the novel of the same name by Yihanhe (一寒呵)
Won't be broadcast in mainland China, will air through an international platform.
Filming start: beginning of January 2025 Filming period: 20 days Casting call: December 13, 2024
Summary: Thousands of years ago, the mountains and rivers were destroyed and wars started raging everywhere. Sixth prince Xiao Yunze had no hope of ascending the throne to the Southern Kingdom. By chance, he saves Zhao Ziang, who was trying to assasinate the prince. As they get to know each other, gradually feelings beyond mundane develop between them and they fall in love. As the political situation in the Southern Kingdom changes, Zhao Ziang kills the prince to protect Xiao Yunze and let Xiao Yunze succeed to the throne. The death of the prince causes a rift between the two, and Zhao Ziang resolutely leaves and embarks on the journey again. Several years later, Zhao Ziang becomes the emperor of the Northern Kingdom. With his efforts, the Northern Kingdom is about to unify the Central Plains. But when Zhao Ziang faces the last obstacle - king of the South and his ex lover Xiao Yunze, whom he had missed for many years, he doesn't know what to do. Will love win or power win?
Character profiles:
Xiao Yunze Male, visual age around 20 years old. He is slender, loves playing chess, calligraphy and painting, and is elegant in every move. The sixth prince of the Southern Kingdom, with a refined and timeless temperament. He is intelligent and sensitive, talented, and has expanded his music and poetry. He has a gentle personality but is not weak. He has a keen insight into people's hearts, but is willing to stay out of the game and abandon the desire to fight for power. He advocates elegance, likes to live in seclusion in the mountains, and is tired of the whirlpool of power, but he always has a deep attachment to family affection, especially to his brother, the prince, Xiao Yunqian, with complex feelings, respect but also alienation. In the chaotic situation, he became a calm and deep character with his gentle but firm character.
Zhao Ziang (Xiao Yunze's cp) Male, visual age is around 25 years old. A hero in the north, with a tall figure, a resolute face, firm eyebrows, a violent temper, and both wisdom and martial arts. He is resolute and resolute, and is aggressive and enterprising. He is calm and resolute, has extraordinary strategic vision and execution, and is a hero in troubled times. He is informal, but respects the strong and the wise, and always pursues his ambitions. Although he is in the midst of power and killing, he is also sincere and righteous, and has a heart for his country. But when facing Xiao Yunze, he is always indecisive.
Xiao Yunqian (Xiao Yunze's elder brother) Male, visual age around 25 years old. The prince who shines in the court is determined to gain supreme power. He can sacrifice all emotions in pursuit of power, but finally loses in emotions. He has a strong desire for power and has shown extraordinary political wisdom and strategy since childhood. He has a cold temperament and is deeply scheming. Although he looks calm and restrained, he is actually full of ambition. He is not obsessed with sensual pleasures, but pursues power itself with a cold and resolute will, instead of sympathizing with the common people. In the process of pursuing power, he regards all obstacles as stepping stones. He has a complicated relationship with his brother Xiao Yunze. They grew up together when they were young and had the warmth of brotherly love, but they became increasingly alienated in the power struggle. Xiao Yunqian is very oppressive in his dealings with others. He is a strong man who integrates coldness, decisiveness and ambition. In his world, family affection and feelings often give way to power. He is a typical hero in troubled times.
Guo Zheng (Xiao Yunqian's personal bodyguard) Male, 20 years old. The prince's personal bodyguard, who has practiced martial arts for many years and is very capable. The prince's personal bodyguard, who is naturally fond of martial arts, is rough but delicate. Many years ago, he fell in love with Yin Shan at first sight. Although he had no interest in poetry and books, he was subtly exposed to the elegant world because of Yin Shan. Guo Zheng admired Yin Shan's talent and gentle temperament. Although he was not good at speaking, he protected him silently with practical actions. He hides a tenderness under his strong appearance, burying his loyalty and admiration deep in his heart. He is a contradictory combination of cold and hot in troubled times.
Yin Shan (Xiao Yunze's childhood sweetheart) Male, 20 years old. A scholar who has loved poetry, calligraphy and painting since childhood. The son of a civil official in the court, he met Xiao Yunze since childhood because of their similar interests and they have a deep friendship. Yin Shan is well-read in poetry and books, and has outstanding talents. He especially loves the love stories described in books, and is full of idealistic pursuit and loyalty to love. He has a gentle personality like jade, but he has a rare firmness and perseverance, and always accompanies Xiao Yunze. Yin Shan advocates elegance and has no intention of fighting in the world. He only wants to use his talents and sincerity to protect the deep friendship and unknown emotions. He is a touch of peace in the troubled times.
Zhao Jifu (Zhao Ziang's younger brother) Male, 18 years old. Grew up in a temple. Compared with his brother Zhao Ziang, who is heroic and valiant, Zhao Jifu embodies more calmness and strategic precision. He can even be said to be a two-faced person. He is humble and gentle on the surface, and is good at hiding his true intentions. But in fact, he is a scheming man and a master in the political arena. He has shown extraordinary adaptability in complex situations, and is good at making secret plans. He is an important force in promoting the family's hegemony. His temperament is restrained but his edge is hidden, showing a kind of hidden strong style. He is a wise man and counselor who cannot be ignored in troubled times.
Han Zaizhou (Teacher of Xiao Yunqian) Male, 60 years old. An important official in the court, he has a high wisdom in politics and worldly affairs. The core of the prince party, the veteran of two dynasties of the Southern Kingdom, calm and composed, and has a thorough understanding of power and politics. The previous emperor of the Southern Kingdom is old, and Han Zaizhou has to start planning for the next generation of the Southern Kingdom. Faced with prince Xiao Yunqian who has lost control in pursuit of power, Han Zaizhou has to persuade Xiao Yunze to participate in the fight for the throne in order to stabilize the court, because he feels affection for the younger generation of princes.
*text from the informational brochure was converted with image to text online programs, translated through google translator and edited by me with some help of online dictionaries. i do not speak chinese, so there are most certainly mistakes in the text. purpose of this translation is to give you the general idea
#the mountains and rivers are forever silent#the eternal silence of mountains and rivers#山河永寂#shanhe yong ji#syj#chinese bl#chinese ql#upcoming bl#mine#mjtag#userjap#OH MY GOD I AM GOING MAD#if you find any translation mistakes please point them out i will edit them
144 notes
·
View notes
Text
The Golden Spiral - Part 2
(A story by @midasslave1 done in collab with @polo-drone-070)
4. The Call
One fateful day, PDU-070 was seated in a meeting room of the Polo-Drone-Hive, reporting the training updates decided in the latest management meeting. Its role as Head Office Assistant placed it as a key witness for Gold Army strategy and planning. Surrounded by its fellow Polo-Drones, it felt the familiar satisfaction of contributing to the team’s unity and success. The hum of productive conversation filled the room when its phone buzzed softly.
It hesitated before answering. A familiar yet unsettling voice whispered through the line: “GOOD BOYS OBEY MIDAS.”

The words struck like a lightning bolt. Its sharp focus dulled, and glowing golden spirals rippled in its eyes, drool trickling down his chin like molten metal. The sense of purpose it had always drawn from serving the Gold Army twisted into a compulsion to serve Midas instead. PDU-070 rose its body moving on autopilot. No one in the room noticed its subtle shift as it excused itself and left.
Thousands of miles away, Jett sat in his bedroom, his Golden Army Zoom call filling the screen. Laughter and camaraderie flowed as his Gold Bros shared updates on their projects. But just as Jett began to share an idea, his phone rang. The number was unlisted, but he did not think much of it. The same phrase echoed in his ear. “GOOD BOYS OBEY MIDAS.”

His body stiffened, the same golden spirals consuming his gaze as gold drool poured from his mouth. His Gold Bros called his name, but Jett barely registered the sound. Slowly, he disconnected the call, his movements no longer his own.
The triggers implanted during their captivity had been activated. PDU-070 and Jett were no longer free; they were puppets of Midas Enterprises.
5. The Mission
Under Midas Enterprises’ control, PDU-070 and Jett began their missions. PDU-070, deeply integrated into the Gold Army’s management as an assistant, quietly gathered sensitive information. Membership lists, team schedules, and recruitment data were extracted with precision and sent to Midas. Its fellow Polo-Drones noticed no change, mistaking its heightened focus as dedication.
Jett operated in a different sphere, closer to the non-converted players. His friendly reputation allowed him to access informal gatherings and hear unguarded discussions. Slowly, he began piecing together details about upcoming strategies and players who were considering joining the Polo-Drone Hive. These details were also fed back to Midas.
Despite their obedience, moments of clarity flickered. PDU-070, reviewing files in the Polo-Drone Hive, felt an unexpected surge of pride in the Hive’s unity. For a fleeting moment, it remembered why it had embraced the rubber polo and the Golden Army’s values. The thought was quickly smothered by the golden spirals.

Sitting at his desk, moments after sending the classified documents Midas had demanded, Jett felt his mind waging war against itself. The loyalty, the rush of camaraderie he felt with his Golden brothers—it was priceless. Every conversation, every shared moment reinforced the bond he had once cherished. But the programming from Midas smothered that warmth as quickly as it surfaced, dragging him back into the obedient fog of servitude.
For both, the conflict was subtle but relentless. The Golden Army’s values—supporting your team, trusting your brothers—were deeply ingrained. Each lie, every hidden action, chipped away at the golden fog clouding their minds. They felt something was wrong, but the golden haze was relentless. Their mission for Midas Enterprises continued, though cracks in their obedience were beginning to form.
6. The Awakening
PDU-070 sat in the Hive’s office, reviewing files it had compiled for Midas. The task felt efficient, orderly—things a Polo-Drone should value—but a nagging thought surfaced: What would my fellow drones say if they knew? The idea was unbearable. Unity and openness were the Hive’s core values, and PDU-070 had always believed that the team was strongest when every drone supported each other. The thought sparked a flicker of resistance.
In his own home, Jett was scrolling through a group chat with his Gold Bros. Photos of a recent match brought a lump to his throat. He had been part of the team that day, cheering on his friends, but now he felt like an outsider. The guilt gnawed at him—he was betraying the trust of the very people who had welcomed him so fully.

The breakthrough came as PDU-070 prepared to transmit critical information to Midas Enterprises through encrypted channels. Reviewing the data, a deep unease bubbled to the surface. As its fingers pressed the enter key, a sharp pang of guilt struck. The golden spirals in its eyes flickered, struggling against the memory of the Hive’s mantra: Commit to team. One Mind. Hive mind. The screen blinked back: Good work, boy. Proceed to Midas HQ for processing level 2. But PDU-070 kept repeating the mantra, fighting to hold onto its true programming.
Jett experienced a similar moment of clarity during a quiet evening. While reviewing member logs, he found a photo of his Gold Bros celebrating after a big victory. The sight triggered a wave of nostalgia and a fierce longing for the camaraderie he once felt. Tears welled in his eyes, golden spirals shimmering faintly before fading.

With tremendous effort, they both broke free from the golden haze. Memories rushed back, and the sinister grip of Midas Enterprises began to crumble. Though shaken and disoriented, they realized the full extent of what had been done to them. Their identities were still intact, but the fight was far from over.
TO BE CONTINUED.....
To join the Gold Army, contact one of our recruiters @brodygold, @goldenherc9 or @polo-drone-001.
#Golden Army#GoldenArmy#Golden Team#theGoldenteam#AI generated#jockification#male TF#male transformation#hypnotized#hypnotised#soccer tf#Gold#Join the golden team#Golden Opportunities#Golden Brotherhood#Polo Drone#Polodrone#PDU#Polo Drone Hive#Rubber Polo#rubberdrone#Join the Polo Drones#assimilation#conversion#drone#dronification#mind control#obeymidas#enslaved#midasenterprises
32 notes
·
View notes
Text
Graph Analytics Edge Computing: Supply Chain IoT Integration
Graph Analytics Edge Computing: Supply Chain IoT Integration
By a veteran graph analytics practitioner with decades of experience navigating enterprise implementations

youtube
Introduction
Graph analytics has emerged as a transformative technology for enterprises, especially in complex domains like supply chain management where relationships and dependencies abound. However, the journey from concept to production-grade enterprise graph analytics can be fraught with challenges.
In this article, we'll dissect common enterprise graph analytics failures and enterprise graph implementation mistakes, evaluate supply chain optimization through graph databases, explore strategies for petabyte-scale graph analytics, and demystify ROI calculations for graph analytics investments. Along the way, we’ll draw comparisons between leading platforms such as IBM graph analytics vs Neo4j and Amazon Neptune vs IBM graph, illuminating performance nuances and cost considerations at scale.

Why Do Enterprise Graph Analytics Projects Fail?
The graph database project failure rate is surprisingly high despite the hype. Understanding why graph analytics projects fail is critical to avoid repeating the same mistakes:
Poor graph schema design and modeling mistakes: Many teams jump into implementation without a well-thought-out enterprise graph schema design. Improper schema leads to inefficient queries and maintenance nightmares. Underestimating data volume and complexity: Petabyte scale datasets introduce unique challenges in graph traversal performance optimization and query tuning. Inadequate query performance optimization: Slow graph database queries can cripple user adoption and ROI. Choosing the wrong platform: Mismatched technology selection, such as ignoring key differences in IBM graph database performance vs Neo4j, or between Amazon Neptune vs IBM graph, can lead to scalability and cost overruns. Insufficient integration with existing enterprise systems: Graph analytics must seamlessly integrate with IoT edge computing, ERP, and supply chain platforms. Lack of clear business value definition: Without explicit enterprise graph analytics ROI goals, projects become academic exercises rather than profitable initiatives.
These common pitfalls highlight the importance of thorough planning, vendor evaluation, and realistic benchmarking before embarking on large-scale graph analytics projects.
you know, https://community.ibm.com/community/user/blogs/anton-lucanus/2025/05/25/petabyte-scale-supply-chains-graph-analytics-on-ib Supply Chain Optimization with Graph Databases
Supply chains are inherently graph-structured: suppliers, manufa
2 notes
·
View notes