#Frequently Used Linux Commands
Explore tagged Tumblr posts
Note
for college i frequently have to use "lockout" anti-cheat software like respondus lockdown that totally seizes control of my computer (which is bullshit, but i digress) and i've adopted the three word password method to deal with it with the relevant accounts i have to use with that type of software. i struggle with adhd so this has been the most efficient method for me because i can remember "blast fish motorcycle" with some numbers or characters tossed in versus a long 20+ jumbled string of characters i would NEED a post-it note or a password manager for.
one of my professors suggested the three word method WRT linux command line work with expediently logging in and managing a server while having a modicum of security that isn't just "name1234", with the idea that if we're setting up a machine or can't access the internet while we're working, it's not an inaccessible disaster.
in the event of situations like this what's your recommendation? if this is an annoying ask i'm sorry btw, i'm trying not to throw a curveball at you.
There are good reasons sometimes to use a passphrase rather than a complex password and you've given a couple good examples, though I would say for the server example especially you shouldn't be doing "correct horse battery staple" or "blast fish motorcycle", you should be doing "fulminate igneous dodecahedron" (words that are not in any lists of those most commonly used in the English language) AND you should be having a randomizer select the words - aaaand even then I'm more likely to do something like the " Atss"twotpawotsw64 " lyric initialism example. I've got one of those for my password manager for work and it's really automatic to type now while still being long and complex.
228 notes
·
View notes
Text
So I have a Linux problem, and I'm just gonna post it here. I dunno if I have the reach for this, but if you know a potential fix, I will gladly accept it:
Basically, I run Zorin OS 17.2 Core on my Mid-2017 MacBook Pro (Two Thunderbolt Ports). This computer has been hell to make work, but after years of fiddling and finding drivers and terminal commands, it works almost like OEM.
My last problem with this machine, and the only thing that does not function like it's OEM, is the Sleep/Wake function. This is a known issue with 2016 and newer MacBooks on Linux; However, there are workarounds.
Namely, I found a kernel parameter that prevents Deep sleep and only allows the computer to go into s2idle when the lid is shut. This isn't great because it means the dies quickly and gets hot when the lid is shut, but I can't really do anything about it. This did, however, fix an issue I was having where the audio would just stop working if I ever shut the lid.
The final issue was getting the computer to wake up on its own. Every time I start the computer up (not waking it up; only powering it up from a complete shutdown) I have go into terminal and run this:
sudo bash -c 'echo "0" > /sys/bus/pci/devices/0000\:01\:00.0/d3cold_allowed'
I don't know what this command does, but without it, the machine will just never wake up. If you close the lid without running this at initial startup, it cannot be woken back up until it is rebooted.
That's not really a problem, since it's only once per reboot, and I don't reboot my laptop very frequently.
You know what would really make this even more seamless, though? If I could run this command using Ubuntu's startup applications menu. That way, I wouldn't have to manually open terminal every boot just to run this command. It would just run automatically, and I'd never have to worry about it. It would work like OEM! (Minus the less efficient sleep state.)
However, I can't do that. I've tried that. In fact, I have that exact command in my Startup Applications app, as we speak.
Any time I start the computer up and DON'T manually run the command, if I shut the lid, the computer sleeps. It will, however, wakeup (unlike if the command had never been input). HOWEVER. Unlike running the command in terminal, when it finally wakes up, the cursor photo changes into a gray square, my Night Light settings are reset, my wallpaper changes to black, my system accent color is changed to default, and any time I click inside the password box to login, the field immediately becomes inactive again. It doesn't stay active long enough for me to even get two letters typed. All this happens while "Authentication Error" rapidly and randomly flashes below the password box.
Eventually, if I don't force shut down the machine, it'll crash. It'll throw me into terminal mode, and it'll infinitely repeat an error claiming it could not write to some 'systemd jounral' thing because the operating system is in read-only mode. After that it'll either repeat that error over and over, creating endless lines in terminal mode, or it'll just freeze, and I have to restart the laptop either way. So, my question is:
WHY.
Why does running this command in terminal and running it via Startup Application have different results, and is there any way to fix it??
#rambles#linux#linuxposting#help#linux help#zorin#zorin os#ubuntu#ubuntu 24.04#zorin os 17.2#mac#macbook#macbook pro
17 notes
·
View notes
Text
Setting a GNOME extension to run at the greeter
I recently installed Linux on my old Surface Book, a touchscreen device. I want to be able to use the entire interface with the keyboard unplugged. This means I must use the onscreen keyboard frequently - but the default GNOME OSK (onscreen keyboard) is doo doo trash, and I don't want it. You will need root access for this tutorial.
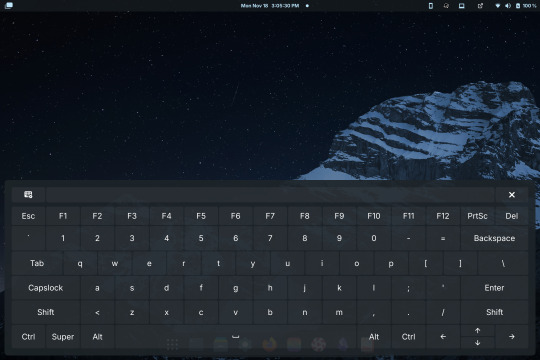
Compare the default GNOME OSK (left) to the new and improved one (right).
This tutorial involves copying a standard GNOME extension into a folder that's readable by any user, then enabling it for use by the GDM user, which governs GNOME's greeter (login screen).
The extension I will be installing using this method is the above keyboard, [email protected] (which can be found via GNOME's extension manager). This is done with the purpose of accessing this significantly improved onscreen keyboard even at the login screen - without this tutorial, the extension does not load until after you have logged in. This method can be done with any extension, although I'm told the GDM user is more restricted than the actual user so some things may not work.
Step 1: Set up the extension in userspace.
Modifying the extension config after it's copied over will be a pain in the ass. Get all your configs ready using the extension's own menus or config files. No rush, as you can still do this bit up until step 5.
Step 2: Move the extension from user-install to system-install.
In order for the GDM user to access the extension it must be in the system-installed folder. For my OS (Zorin) it will be in good company.
sudo mv -r ~/.local/share/gnome-shell/extensions/[email protected] /usr/share/gnome-shell/extensions/
You can also copy it instead of moving it, but you have to rename the user-install folder (in ~/.local) to break it. Otherwise the system would rather use the user-installed one, and will ignore the system-installed one on boot. I think.
Make sure that the gdm user can actually access the files as well:
sudo chmod -R a+rX /usr/share/gnome-shell/extensions/[email protected]
Step 3: Modify the extension metadata file to let it run on the login screen.
sudo nano /usr/share/gnome-shell/extensions/[email protected]/metadata.json
look for the line that says
"session-modes": ["user"],
If the line doesn't exist, just add it. You need it to say
"session-modes": ["user", "gdm", "unlock-dialog"],
Step 4: Enable the extension for the gdm user.
To do this and the following step, you must be able to log in as the gdm user. There are multiple ways to do this, but the way I used is via `machinectl`. If you try to run this command on its own it should tell you what package you need to install to actually use it. I do not know the ramifications of installing this, nor do I know its compatibility; all I can say is it worked for me. If you are uncertain you will have to carve your own path here.
Once it is installed, log into the gdm user from a terminal:
machinectl shell gdm@ /bin/bash
and enter your sudo password.
At this point I recommend checking the current list of enabled extensions:
gsettings get org.gnome.shell enabled-extensions
On my computer, this came back saying "@as []", which means it's blank. To enable your desired extension:
gsettings set org.gnome.shell enabled-extensions "['[email protected]', 'if the above command did NOT come back blank just put the rest in here.']"
Step 5: Transfer the settings from the userspace install to the system install.
Right now, the extension should be working on the login screen. To make sure, press ctrl + alt + delete to log out, or restart your computer. You will notice that while the extension is functioning, none of your settings saved. To fix this you must use dconf to dump and then reimport the settings. Get back to a regular user terminal and run:
dconf dump /org/gnome/shell/extensions/[email protected]/ > extension.ini
Now you have your settings in a nice neat file. The gdm user can't access this though since it's in your user folder. My quick and dirty solution:
sudo mv ~/extension.ini /extension.ini sudo chmod 777 /extension.ini
If you want it in a better place than the system root folder you can put it there. I don't really care.
Now you log into the GDM user and import the settings file there.
machinectl shell gdm@ /bin/bash dconf load /org/gnome/shell/extensions/[email protected]/ < /extension.ini
Now log out of the gdm user and clean up after yourself.
sudo rm /extension.ini
Now restart or log out and you will see that your extension is now functioning with all its settings.
Huge thank you to Pratap on the GNOME Discourse site. This post is basically just a tutorialized adaptation of the thread I followed to do this.
3 notes
·
View notes
Text
Key Programming Languages Every Ethical Hacker Should Know
In the realm of cybersecurity, ethical hacking stands as a critical line of defense against cyber threats. Ethical hackers use their skills to identify vulnerabilities and prevent malicious attacks. To be effective in this role, a strong foundation in programming is essential. Certain programming languages are particularly valuable for ethical hackers, enabling them to develop tools, scripts, and exploits. This blog post explores the most important programming languages for ethical hackers and how these skills are integrated into various training programs.
Python: The Versatile Tool
Python is often considered the go-to language for ethical hackers due to its versatility and ease of use. It offers a wide range of libraries and frameworks that simplify tasks like scripting, automation, and data analysis. Python’s readability and broad community support make it a popular choice for developing custom security tools and performing various hacking tasks. Many top Ethical Hacking Course institutes incorporate Python into their curriculum because it allows students to quickly grasp the basics and apply their knowledge to real-world scenarios. In an Ethical Hacking Course, learning Python can significantly enhance your ability to automate tasks and write scripts for penetration testing. Its extensive libraries, such as Scapy for network analysis and Beautiful Soup for web scraping, can be crucial for ethical hacking projects.
JavaScript: The Web Scripting Language
JavaScript is indispensable for ethical hackers who focus on web security. It is the primary language used in web development and can be leveraged to understand and exploit vulnerabilities in web applications. By mastering JavaScript, ethical hackers can identify issues like Cross-Site Scripting (XSS) and develop techniques to mitigate such risks. An Ethical Hacking Course often covers JavaScript to help students comprehend how web applications work and how attackers can exploit JavaScript-based vulnerabilities. Understanding this language enables ethical hackers to perform more effective security assessments on websites and web applications.
Biggest Cyber Attacks in the World
youtube
C and C++: Low-Level Mastery
C and C++ are essential for ethical hackers who need to delve into low-level programming and system vulnerabilities. These languages are used to develop software and operating systems, making them crucial for understanding how exploits work at a fundamental level. Mastery of C and C++ can help ethical hackers identify and exploit buffer overflows, memory corruption, and other critical vulnerabilities. Courses at leading Ethical Hacking Course institutes frequently include C and C++ programming to provide a deep understanding of how software vulnerabilities can be exploited. Knowledge of these languages is often a prerequisite for advanced penetration testing and vulnerability analysis.
Bash Scripting: The Command-Line Interface
Bash scripting is a powerful tool for automating tasks on Unix-based systems. It allows ethical hackers to write scripts that perform complex sequences of commands, making it easier to conduct security audits and manage multiple tasks efficiently. Bash scripting is particularly useful for creating custom tools and automating repetitive tasks during penetration testing. An Ethical Hacking Course that offers job assistance often emphasizes the importance of Bash scripting, as it is a fundamental skill for many security roles. Being proficient in Bash can streamline workflows and improve efficiency when working with Linux-based systems and tools.
SQL: Database Security Insights
Structured Query Language (SQL) is essential for ethical hackers who need to assess and secure databases. SQL injection is a common attack vector used to exploit vulnerabilities in web applications that interact with databases. By understanding SQL, ethical hackers can identify and prevent SQL injection attacks and assess the security of database systems. Incorporating SQL into an Ethical Hacking Course can provide students with a comprehensive understanding of database security and vulnerability management. This knowledge is crucial for performing thorough security assessments and ensuring robust protection against database-related attacks.
Understanding Course Content and Fees
When choosing an Ethical Hacking Course, it’s important to consider how well the program covers essential programming languages. Courses offered by top Ethical Hacking Course institutes should provide practical, hands-on training in Python, JavaScript, C/C++, Bash scripting, and SQL. Additionally, the course fee can vary depending on the institute and the comprehensiveness of the program. Investing in a high-quality course that covers these programming languages and offers practical experience can significantly enhance your skills and employability in the cybersecurity field.
Certification and Career Advancement
Obtaining an Ethical Hacking Course certification can validate your expertise and improve your career prospects. Certifications from reputable institutes often include components related to the programming languages discussed above. For instance, certifications may test your ability to write scripts in Python or perform SQL injection attacks. By securing an Ethical Hacking Course certification, you demonstrate your proficiency in essential programming languages and your readiness to tackle complex security challenges. Mastering the right programming languages is crucial for anyone pursuing a career in ethical hacking. Python, JavaScript, C/C++, Bash scripting, and SQL each play a unique role in the ethical hacking landscape, providing the tools and knowledge needed to identify and address security vulnerabilities. By choosing a top Ethical Hacking Course institute that covers these languages and investing in a course that offers practical training and job assistance, you can position yourself for success in this dynamic field. With the right skills and certification, you’ll be well-equipped to tackle the evolving challenges of cybersecurity and contribute to protecting critical digital assets.
3 notes
·
View notes
Text
More math on the Linux command line
Linux provides quite a few commands that let you do math on the command line. Which is best depends on the kind of math that you’re doing and the precision that you’re expecting. This post covers five different commands with examples of how to use them and expands upon my earlier post. Using expr The expr command is one of the most frequently used commands for doing integer arithmetic. Here are…
0 notes
Text
Elevating the Blog Experience with Laravel 11: A Technical Deep Dive!Scideassolutions
In today's fast-paced digital landscape, a robust and engaging blog is critical for thought leadership and community engagement. My recent project involved building a sophisticated blog and web application utilizing Laravel 11, seamlessly integrated with Moodle and featuring a custom chatbot – and I'm excited to share some insights.
Laravel 11 offers a streamlined and powerful foundation for creating modern web applications, and I've been particularly impressed with:
Simplified Structure: Laravel 11's leaner application skeleton makes it even easier to get started and maintain a clean codebase. This is particularly important for large projects with ongoing development.
Performance Enhancements: The latest version brings further performance optimizations, resulting in a snappier user experience. This translates to better engagement and lower bounce rates.

Beyond the Basics: Integrating Moodle API
One of the key challenges was integrating the blog with a Moodle platform. This involved leveraging Laravel's API capabilities to:
Synchronize User Data: Automatically create and update user accounts between the blog and Moodle.
Embed Course Content: Display relevant Moodle course content directly within blog posts, creating a unified learning experience.
Enable Single Sign-On (SSO): Allow users to seamlessly access both the blog and Moodle with a single set of credentials.
I achieved this using Laravel's robust HTTP client and carefully crafted API endpoints, ensuring secure and efficient data transfer.
Custom Laravel Commands for Streamlined Management
To further enhance the workflow, I developed custom Laravel commands for managing various blog aspects. Examples:
php artisan blog:publish {post_id}: Publishes a blog post with a specific ID.
php artisan moodle:sync: Synchronizes user data with Moodle.
php artisan chatbot:train: Retrains the chatbot with the latest data.
These commands, optimized for both Windows and Linux environments, significantly simplified administrative tasks.
AI-Powered Engagement: Laravel Chatbot Integration
To enhance user interaction and provide instant support, I integrated a Laravel-based chatbot. This chatbot can:
Answer frequently asked questions about the blog and Moodle courses.
Guide users to relevant content.
Provide personalized recommendations.
This proactive approach improves user satisfaction and reduces the burden on support staff.
Key Takeaways
Building a blog with Laravel 11 and integrating it with Moodle and a chatbot required a deep understanding of both technologies. The key takeaways from this project include:
Planning is Paramount: A well-defined architecture is crucial for seamless integration.
Security First: Prioritize security best practices when working with sensitive data.
User Experience Matters: Focus on creating a user-friendly and engaging experience.
Important Considerations and Customization Steps:
Personalize Extensively: This is a template! Replace my generic statements with your specific experiences, challenges, and solutions.
High-Quality Visuals: I cannot stress this enough. Your images are crucial. Invest time in creating visually appealing and informative screenshots and graphics.
Target Audience: Think about who you want to reach on LinkedIn. Tailor the language and content to resonate with them. Are you targeting recruiters? Other developers? Potential clients?
Call to Action: Encourage interaction. Ask a question at the end, invite comments, or suggest readers connect with you.
Keywords: Use relevant keywords in your post to improve its visibility in search results. I included a few, but research others relevant to your skill set and the project.
Proofread Carefully: Ensure your post is free of grammatical errors and typos.
Engagement: Respond to comments and engage in discussions to build your network.
Track Results: Pay attention to how your post performs to learn what resonates with your audience.
Conclusion: In conclusion, leveraging Laravel 11 for your blog's development can significantly elevate user engagement and streamline management tasks.From integrating Moodle for unified learning experiences to deploying an AI-powered chatbot for enhanced user interaction, the possibilities are vast. Remember to personalize your content, prioritize high-quality visuals, and engage your audience actively to maximize impact.
I'm excited to connect with fellow developers! How are you using Laravel 11 in your projects? Let’s discuss.
#Laravel #PHP #Moodle #WebDevelopment #AI #Chatbot #SoftwareEngineering #ScadeaSolutions
Let’s Take Your Business Online!
🌐 Website: www.scideassolutions.com
📧 Email: [email protected]
1 note
·
View note
Text
I have Linux Mint on my travel laptop. I do not have it on my Larger Less-Travel-y Laptop, because I need Acrobat Pro to do work, and I am a Word user at a skill level that makes switching to Libre Office difficult. (Also I use both Word and Acrobat Pro in my day job; there is no option of "just get used to something else." It'd always be "get used to both.") I also use ABBYY FineReader, and there is absolutely nothing Linux-friendly that compares.
Can attest that Linux Mint is easy to install and easy to use. Slightly more difficult to set up to run on a flash drive that remembers your settings instead of wiping the base OS. (...I hauled in Linux-Fluent Daughter to set that up. I could've done it alone but was getting frustrated. Creating partitions on a flash drive is not fun for non-techies.)
(Srsly, Linux folks, why the hell is there no How To Switch From Windows website? Why is there no nice, open community and attached Discord for So You Want To Defenestrate Your Computer? No tiny nonprofit focused on End The Chromebook Conspiracy? Where's the "We convert Win7 Laptops into Linux For Students" group?)
Notes from a power Windows user who has loved Linux for decades but has very little practical experience with it:
The "choose a distro" advice is terrible. There are no guidelines for it, 2/3 of the searchable advice about it is more than 10 years old, and fully half of that is "how to get the smallest possible distro onto your very tiny ancient drive." And it's great to know that I can run Linux off a 2gb flash drive! But. It's not what I actually need.
Info about "how do I run this set of programs I use all the time" is also terrible. And often hostile, and packed with "you should be using open source software instead."
At no point in the "hey you should try Linux!" discussions does anyone mention "oh by the way, some laptops will have no native support for certain exotic features like audio or printing. You will need to track down special drivers or weird third-party plugin things to make those work. You will only discover this lack after you have installed Linux, joined a Zoom call, and realized that your OS thinks your speakers don't exist."
Choose a password you are comfortable typing A LOT. Seriously, security is less of an issue here than "password I can type 30 times during a fix-it session." You can switch to a more secure password when you're comfortable with the OS. (Don't use "password" or "pa55w0rd" as your password, but you also don't need to go the "correct horse battery staple" route.)
A notable number of apps do not have a "click here to install" feature that we get used to with Windows. Snap and Flatpak are not difficult to learn or work with, but they are different. (And they usually take more space than expected.)
A lot of apps require frequent updates to function. Especially the ones that don't have a native Linux version. This is also frustrating.
OS emulators and virtual drives are next-level techistry and any suggestions for using them should be followed with either a very solid tutorial (in TEXT form, not a video) or an offer to hand-hold while someone gets it set up.
Once you start using Linux - if it's Mint, it will mostly seem like Windows. Sometimes there'll be a weird error message. WHEN SEARCHING FOR ADVICE: make sure to add [linux mint] to the search terms, AND limit the results to the last year. Otherwise, you wind up finding forum posts from 2014 that say "Ugh this driver issue has been FIXED; just fuckin install Ubuntu 12 already." (Ubuntu is currently at 24.1.)
Some people will tell you you can use Linux without getting into command-line activity. They are lying. You will need to be at least somewhat comfortable with the Terminal. This is not hard, but it is different. And there are no starter tutorials on this. (I have been looking literally for decades.) (I do not speak Command Line well enough to write one.)
Some people will tell you Linux isn't functional unless you learn a whole lot of command-line functions and do most of your operations from there. They are also lying.
There are differences between the distros that, as a Windows or Mac user, you cannot comprehend. Like. They will rattle off a list of features and those will mean nothing to you. They mean nothing to me. I went with Mint because it is "most like Windows." My daughter uses PopOS because it has better VR support. I think.
You will occasionally have to re-install the whole damn OS, and it will be terrifying. It will tell you your files are safe. This is correct, if you have not done weird customized wonkery to them, in which case, you don't need the warning.
Google knows about Linux and they are Not Happy. Newer Chromebooks can't be directly converted to Linux without fucking with the hardware - as in, open them up and remove the thing they installed to make Linux not work. (Or rather, to make ChromeOS always recoverable.) However, even those will allow running Linux off a flash drive.
The key advantages to Linux:
Lack of Microsoft & Apple's increasing demands to collect all your personal data.
Lack of random "upgrades" that fuck up your existing processes. (That said: If you use cloud-based apps - like, oh, Discord - you will need frequent updates anyway.)
Whateverthefuck is going on with AI invading your computer - you can dodge all of that.
If you do want to customize things, you can. You can change a lot of the appearance, the startup details, what software gets priority in the system, and a whole swarm of back-end details that most Windows users (including me) are pretty much oblivious to. CAVEAT: None of that is as easy as many Linux stans make it sound. SECOND CAVEAT: If you customize your system to hell and back, you won't be able to work (well) on a standard base-install version. The result of this, is that Linux experts often flounder when helping newbies, because they don't know what any of the default settings are anymore. (They are experts. They know what's available and how to make it work. They just don't know where it's hiding in your system.)
Linux will run on much smaller, slower computers than MS or Apple, because, see above, it's not trying to spy on you or inflict AI shenanigans on you. A basic student-functional Linux laptop can be much cheaper than what's needed to run the current Windows or MacOS, and less cloud-driven that Chromebooks.
I swear to fucking god. I would claw out OneDrive from my computer if I could. I would burn down their servers if I could. I would run down their stocks to the ground if I could. I hope every single one of their workers gets a better offer from a competitor in the next 24 hours. I hope every single one of their light bulbs explodes at the same time. I hope every single carton of milk in their fridge will always be expired.
Stop backing up my fucking files.
Stop asking me to back up my fucking files.
Stop taking my fucking files off my fucking computer.
I don't want a fucking reminder in three fucking days. Let me fucking say no.
Fuckers.
29K notes
·
View notes
Text
Linux CLI 40 🐧 rsync command
New Post has been published on https://tuts.kandz.me/linux-cli-40-%f0%9f%90%a7-rsync-command/
Linux CLI 40 🐧 rsync command

youtube
a - rsync command rsync is a powerful command used to transfer files over network It can copy files between local and remote systems and synchronize directories. It supports various options to control the transfer process common options: a → archive mode, preserves permissions, timestamps etc v → verbose mode z → compress data during the transfer P → show progress and where possible supports pausing and resuming e → specifies an alternative remote shell to use (-e ssh) Syntax: rsync [options] [src] [user@]host:targ rsync [options] [user@]host:src [targ] b - rsync examples rsync -av /home/kr/cli /home/kr/clibkp → local copy rsync -avz [email protected]:/home/kr/cli /home/kr/clibkp → copies everything from remote to local machine rsync -av --delete /home/kr/cli [email protected]:/home/kr/cli → syncronise directories and delete files in destination if not exists in source rsync -avzP /home/kr/cli [email protected]:/home/kr/cli → pause with Ctrl+c and resume with the same command if you frequently use rsync between two machine, use SSH key based authentication ssh-keygen -t rsa -b 4096 -C "[email protected]" → generates a key pair ssh-copy-id user@remote_host → copies the public key to remote machine you can use rsync now without asking for password all the time
0 notes
Text
A Beginner's Guide to Red Hat Enterprise Linux (RHEL)
Red Hat Enterprise Linux (RHEL) is a powerful and versatile operating system widely used in enterprise environments. Known for its stability, security, and robust support, RHEL is a popular choice for businesses and IT professionals. Whether you are stepping into the Linux ecosystem for the first time or transitioning from another operating system, this guide will help you understand the basics of RHEL and how to get started.
What is RHEL?
RHEL is a Linux-based operating system developed by Red Hat, Inc., designed specifically for enterprise use. It offers:
Reliability: Known for its stability, RHEL is the backbone of many critical applications.
Security: With built-in SELinux and frequent updates, RHEL prioritizes system protection.
Support: Comes with professional support and extensive documentation.
Why Choose RHEL?
Here are some reasons why organizations and professionals choose RHEL:
Enterprise-Grade Performance: RHEL is optimized for servers, cloud environments, and containers.
Long-Term Support: Each RHEL version offers years of support, making it a reliable choice for long-term projects.
Certification and Compatibility: Works seamlessly with a wide range of enterprise software and hardware.
Getting Started with RHEL
Obtain RHEL:
Visit the Red Hat website to download RHEL. You can start with a free developer subscription.
Installation:
Create a bootable USB or DVD and follow the intuitive installation wizard. During installation, you’ll configure the disk, timezone, and create an admin user.
Basic Command Line Operations:
Familiarize yourself with basic Linux commands. Examples include:
ls: List files in a directory.
cd: Change directories.
yum or dnf: Manage software packages in RHEL.
User Management:
Add users with useradd and set passwords using passwd.
Networking Basics:
Check network status with ip a.
Configure networks using NetworkManager or editing configuration files.
Essential Tools in RHEL
System Monitoring:
Use tools like top, htop, and vmstat to monitor system performance.
Firewall Configuration:
Manage firewall rules using firewalld.
Package Management:
Install, update, and remove software using dnf or yum.
Resources to Learn RHEL
Red Hat Training and Certification:
Courses like RHCSA and RHCE provide a structured learning path.
Documentation:
The official RHEL documentation is comprehensive and beginner-friendly.
Community Support:
Engage with the Linux community through forums and social media groups.
Conclusion
Red Hat Enterprise Linux is a cornerstone of modern IT infrastructure, powering everything from servers to cloud applications. By mastering RHEL, you open doors to a range of opportunities in system administration, cloud computing, and DevOps. Start small, practice consistently, and leverage the wealth of resources available to become proficient in RHEL.
For more detailed information visit: www.hawkstack.com
0 notes
Text
Version 603
youtube
windows
zip
exe
macOS
app
linux
tar.zst
I had a good week mostly cleaning and fixing things to round out the year. There is an important change to the 'archived-file delete-lock'.
full changelog
archived-file delete-lock
Under options->files and trash, there is an option to stop files from being deleted if they are archived. I never liked how I implemented this feature, since it tried to block both physical deletes and normal trashing. It interacts with some complicated service logic, and this has only grown worse with multiple local file services.
Some users have asked me to write various exceptions, things like 'allow a delete if it comes from the duplicate filter' or just better multi-service handling. I had a proper look at this whole system this week, and I concluded that I have been trying to support something too complicated, and I should scale it back. Therefore: the archived-file delete-lock, from now on, will only stop physical deletes (e.g. deleting from trash).
This is a much simpler problem to solve, does not impinge on multiple local file services, and still serves the main objective of being a backstop to stop accidental deletes of good files.
I have tightened up all the related code here, and I am much more confident in the lock overall. Some changes to trashing logic that I talk about in the next section will cause the lock to be tested less frequently, too. Also, the normal 'delete files' dialog now automatically filters out locked files from the 'delete physically' options. I hope you will see fewer popups saying 'oh, just tried to delete some locked files, I don't know what to do but here they are, now you fix it'.
I regret switching up the workflow for people who use this option, since I know you care about it. I should never have tried to implement so complicated a system in the first place, I think. Please have a play with the new rule, and let me know how it goes. I expect we'll want some nice clean way to purge locked files, when you want to clean your trash of archived stuff you duplicate filtered etc.., but there's only one simple barrier to get around now, so I feel better about approaching it. Let's see how it goes and what the biggest annoyances are, and I'll keep working.
highlights
I have fixed a bunch of jank UI in the media viewer. I put time into the top-right ratings/locations hover window and center-right notes hover window, and they seem to have instant correct sizing on my dev machine in all cases now. No more jitter where it might resize to be three pixels taller right after showing, or layout/position problems when changing media. I also fixed a bunch of jank with the volume slider flyouts. Let me know if you still have any problems, particularly on Linux or macOS!
The program is now more careful about how it handles trashed files. Previously, a bunch of filtering systems, when asked to generically 'delete a file', would send a normal file to trash, but if they happened to run into an already trashed file, they would 'upgrade' the command and send the file to be physically deleted. This no longer happens, whether you are in the archive/delete filter, the duplicates filter, or an export folder/manual export with 'delete files after export' set--it just leaves the file in the trash. There needn't be a rush to clear the trash. In a related change, the duplicates filter page now will no longer accept a file domain that includes the trash--it'll want to stay inside 'all my files'.
next week
This is my last release of the year! It wouldn't be, but the schedule is odd this year and I won't put a release out on Christmas Day. I'll do a little misc hydrus work here and there, ensure I get a week of vacation in the middle of it, and be back to catch up on messages on Saturday January the 4th with 604 on January the 8th. Thank you everyone, and 𝔐𝔢𝔯𝔯𝔶 ℭ𝔥𝔯𝔦𝔰𝔱𝔪𝔞𝔰!
0 notes
Text
Simply about Linux Security
Linux is often praised as one of the best operating systems in terms of security due to several key factors that make it inherently secure and resilient against many types of attacks. Here's why:
1. Open-Source Nature
Transparency: Linux is open-source, meaning its source code is publicly available for review. This transparency allows anyone (including security experts) to examine the code for vulnerabilities, report bugs, and contribute fixes. This collaborative approach leads to faster identification and patching of security issues compared to proprietary systems.
Community and Auditing: Since many users and organizations contribute to Linux's development, any vulnerabilities discovered are often addressed quickly.
2. User Privileges and Access Control
Least Privilege Principle: In Linux, by default, users do not have administrative (root) access to the system. Administrative rights are required to make significant system changes, reducing the risk of malware or attackers exploiting a compromised user account to take control of the system.
Sudo Command: Administrative tasks are typically carried out using sudo (superuser do), which provides controlled, time-limited access to root privileges. This limits potential damage by preventing unnecessary exposure of administrative rights.
3. Strong File Permissions and Ownership
Linux enforces strict file permissions for users and groups, ensuring that only authorized users can access, modify, or execute files. This is a fundamental aspect of Linux's security model, making it difficult for unauthorized users or malware to alter important system files.
Each file has an owner, a group, and a set of permissions (read, write, execute), allowing for detailed control over who can do what with each file.
4. Security Modules and Features
SELinux (Security-Enhanced Linux): This is a set of kernel-level security enhancements that implement mandatory access control (MAC). It adds an additional layer of security by enforcing strict access policies that restrict how processes interact with the system and each other.
AppArmor: Similar to SELinux, AppArmor is a security module that restricts programs to a set of predefined security profiles, preventing them from performing unauthorized actions.
Chroot and Namespaces: These tools allow isolation of processes, limiting the damage they can do even if compromised.
5. Frequent Security Patches
The Linux community is very active in identifying and fixing vulnerabilities. Most Linux distributions offer regular updates, including security patches, making it quick and easy to keep the system secure.
Security advisories and patches for distributions (like Debian, Ubuntu, or Red Hat) are generally well-documented and quickly available.
6. Minimal Attack Surface
Linux distributions can be customized to include only the necessary components, reducing the attack surface. Users can install a minimal version of Linux with only the essential software, which reduces the number of potential vulnerabilities.
Many server-focused Linux distributions, such as CentOS or Ubuntu Server, come with fewer default applications, reducing the chances of exploitable vulnerabilities.
7. Robust Package Management
Package managers like apt, yum, and dnf ensure that software installed on Linux is vetted and comes from trusted repositories. This reduces the risk of installing malicious or untrusted software.
Additionally, Linux distributions often come with tools to verify the integrity of installed packages and update software automatically.
8. Lower Target for Malware
Popularity in Specific Use Cases: While Linux is widely used for servers, many personal users still prefer other operating systems (like Windows). This makes Linux less of a target for mass-market malware.
Open-Source Security Tools: Many Linux distributions have strong built-in security tools, and the OS itself is often the platform for security professionals and penetration testers, further boosting its reputation as a secure platform.
9. Security by Design
Linux has security mechanisms built into its design, such as:
Stack Protection: Linux uses techniques like stack canaries and non-executable memory to prevent stack-based buffer overflow attacks.
Data Execution Prevention (DEP): This feature prevents code from executing in areas of memory that should contain only data.
Address Space Layout Randomization (ASLR): Randomizing memory addresses for processes makes it harder for attackers to predict the location of critical system functions.
10. Regular Security Audits and Penetration Testing
Since many security professionals and ethical hackers use Linux, the system is often subjected to rigorous security testing. This helps find vulnerabilities before they are exploited in real-world attacks.
Conclusion
Linux's security is driven by its open-source nature, strong access controls, and a thriving community that quickly identifies and fixes vulnerabilities. Combined with its robust security tools, regular updates, and user-centric design, it offers a highly secure environment, making it a popular choice for critical applications like web servers, networking, and cloud computing. However, like any system, its security ultimately depends on how it's configured and maintained.
for more details please visit
www.qcsdclabs.com,
www.hawkstack.com
0 notes
Text
Get Ready for Black Dragon Mage Action: A Dark Fantasy Adventure

Black Dragon Mage action roguelite shooter game will hit Proton for Linux and Steam Deck first, via Windows PC. All thanks to the brilliant creativity of developer datablob. Plunging onto Steam Early Access this week. Prepare yourself, folks — Black Dragon Mage action is landing on Steam this December 4, 2024. Doing so with over 13,000 players already diving into the demo, this roguelite shooter is gearing up to be something truly special. Developed by German solo indie dev datablob, this title mixes dark fantasy vibes with gorgeous pixel art, chaotic battles, and a sprinkle of 16-bit nostalgia. Plus, it’s due to hit Windows PC with support for Steam Deck and Linux via Proton. Here's why.
...the Linux player build has some wonky UI issues with a cursor offset as well as other input problems and minor display that I can't quite wrangle in this short time before the EA launch. But I would love to support Linux natively somewhere along the road to Black Dragon Mage 1.0 and it has always been on my list of priorities to keep testing.
Turns out, the UI issues are automagically sorted out in that setup. Of course, they'll keep sending reports to Valve and Unity to iron things out further — and hey, who knows, this might even help fix other games along the way. It’s always great to see a dev willing to go the extra mile and offer a native build for their title. Props to datablob.
What’s the Deal with this Black Dragon Mage action?
At its core, this is a fast-paced top-down roguelite shooter where you wield elemental magic, fight off massive hordes, and even hatch and ride dragons into battle. Where you are due to start with Talon, a black dragon, and Ignilith, a fiery red beast. Both ready to unleash chaos on your enemies. Fly into the fray, escape tight spots, or simply dominate the battlefield with their unique powers. This title is all about player choice, smart strategy, and big flashy moments. Inspired by hits like Vampire Survivors, 20 Minutes Till Dawn, and even Diablo. Black Dragon Mage is perfect for anyone who like testing builds and the action of blasting through waves of enemies.
Black Dragon Mage action Shreds Through Demons
youtube
What Makes It So Great?
Dragons Galore: Hatch, ride, and command dragons as ultimate companions. Need a quick getaway? Hop on and soar out of trouble. Want to crush your foes? Use your dragon’s powerful ultimates.
Magic Everywhere: Toss fireballs, shoot icy orbs, or zap enemies with lightning. Each spell has upgrade paths, so you can tweak your powers to suit your style.
Endless Variety: With procedurally generated maps, no two runs are the same. Explore deserts, cemeteries, and other deadly biomes filled with hazards and surprises.
Epic Boss Fights: From giant cyclops gods to skeletal Nordic warriors, the bosses in Black Dragon Mage will push the action and your skills to the limit.
Custom Builds: Unlock new weapons, perks, and upgrades to create the ultimate mage. Whether you’re slinging spells or smashing foes with arcane hammers, there’s something for everyone.
Meet the Mages
Start your journey with Quinn, a classic chaotic mage who wields elemental staves. But there’s more! Early Access introduces Schmiedrun, a dwarven engineer mage with a knack for crafting deadly tools. She’s also bringing her bouncing arcane hammers and turret-building skills to the mix. Due to offer a whole new playstyle.
youtube
Why Early Access?
Launching in Early Access gives datablob the chance to refine the game with player feedback. So, expect frequent updates, balancing tweaks, and exciting new content to keep the adventure fresh. Oh, and did I mention there’s a 20% launch discount off of the $5.99 USD / £4.99 / 5,89€ cost on Steam. While offering support for Steam Deck and Linux via Windows PC with Proton, for now.
Final Thoughts
If you’re a fan of action roguelites and you like dragons, Black Dragon Mage support is here to make your life even better. Whether you’re riding into battle, tweaking your build, or exploring infinite maps, this game is ready to deliver nonstop thrills. Due out on December 4th!
#black dragon mage#action#roguelite#shooter#linux#gaming news#datablob#ubuntu#steam deck#windows#pc#unity 6#Youtube
0 notes
Text
How to Extend the Lifespan of SSD: Tips and Tricks
Solid-state drives (SSDs) offer significant advantages over traditional hard drives (HDDs), such as faster performance, lower power consumption, and quieter operation. However, SSDs have a limited lifespan due to the wear and tear on their flash memory cells, which degrade over time with each write/erase cycle. While modern SSDs have high endurance ratings, proper maintenance can extend their lifespan. Here are some key tips to prolong an SSD's life:
1. Enable the TRIM Command: TRIM helps manage free space on the drive by marking unused data blocks, preventing unnecessary write operations that can wear down the drive.
2. Avoid Filling the SSD to Capacity: Keeping 10-15% of the SSD’s capacity free helps maintain performance and reduces wear by allowing the drive’s controller to manage data more efficiently.
3. Minimize Write Operations: Reduce unnecessary writes by disabling features like indexing and defragmentation, and moving temp files to another drive.
4. Enable Write Caching: Write caching stores data in faster memory before writing to the SSD, reducing the number of write cycles and improving performance.
5. Keep Firmware Updated: Firmware updates can improve SSD performance and efficiency, extending its lifespan.
6. Use Hibernation Sparingly: Hibernation writes large amounts of data to the SSD, accelerating wear, so it’s better to use sleep mode or shut down the system instead.
7. Disable Background Programs: Limit unnecessary background apps, such as cloud storage or auto-save programs, that frequently write data to the SSD.
8. Use SSD-Optimized Operating Systems: Modern OS versions like Windows 10/11, macOS, and Linux are optimized for SSDs, with features like wear leveling and TRIM support.
9. Avoid Storing Large Files: Store large, infrequently accessed files (e.g., movies, backups) on HDDs or external storage to save SSD space and prevent excess wear.
10. Back Up Regularly: Always have a backup strategy to protect your data, as no storage device lasts forever.
Following these practices ensures your SSD remains efficient, prolongs its lifespan, and safeguards your data. While most users won’t hit the drive's wear limit, proper SSD management helps maximize its longevity and performance.
Want to Buy SSDs in Bulk from VSTL?
If you're looking to buy SSDs in bulk, VSTL offers a reliable solution for large-scale purchases. They provide a variety of SSD models suited for different needs, whether for enterprise use, data centers, or consumer devices. With competitive pricing and bulk order options, VSTL ensures quality and performance, making it a solid choice for businesses or organizations seeking efficient storage solutions. Whether upgrading infrastructure or outfitting multiple systems, VSTL can meet your bulk SSD needs.
0 notes
Text
Streaming RDP vs. Encoding RDP: Which Remote Desktop Service is Right for You?
Remote desktop services are an essential part of present day IT infrastructure, enabling customers to get admission to and manage remote structures from everywhere within the international. However, no longer all far flung computing device offerings are created similarly. Two famous methods—Streaming RDP and Encoding RDP—have emerged as the primary choices. While each serve similar functions, streaming RDP encoding RDP Linux they range substantially in terms of overall performance, compatibility, and use instances.
This blog will dive deep into the mechanics of streamingRDP and encodingRDP, explore their variations, and help you decide which answer first-rate fits your wishes. If you’re working with Linux structures or require foremost far off connectivity, understanding those technology is important.
What is Streaming RDP?
StreamingRDP refers to a technique wherein the laptop consultation is transmitted at once from the faraway host to the customer in close to actual-time. This approach makes use of minimal encoding and interpreting, taking into consideration low-latency interactions, even over modest network conditions.
StreamingRDP is most suitable for situations wherein fast input response and fluid interactivity are crucial, inclusive of:
Remote computing device get admission to for IT admins who need to control infrastructure in actual-time
Remote work answers that prioritize clean operation without heavy processing
Systems in which customers usually access lightweight software and programs, which includes Linux terminals or internet browsers
StreamingRDP is also increasingly more used in cloud-based environments, where pace is prioritized over complex video compression techniques. This makes it in particular beneficial for Linux users who need to get right of entry to their graphical consumer interface remotely without heavy latency.
What is Encoding RDP?
EncodingRDP, then again, focuses on compressing and encoding the remote computing device circulate earlier than it is transmitted. The server captures the display content material, compresses it into an optimized format, and sends it to the consumer for deciphering.
This approach gives super performance over slower or unstable networks, making it an excellent desire for:
Scenarios in which community bandwidth is restrained
Use instances regarding resource-heavy applications, which include 3-D layout software or video editing
Remote computing device get entry to over lengthy distances, in which packet loss might also occur
While encodingRDP can supply better-nice visuals, the encoding and interpreting methods introduce some latency. For systems which includes Linux, this trade-off might be ideal if the programs being accessed require excessive-resolution rendering.
Key Differences Between Streaming RDP and Encoding RDP.
1. Performance and Latency
StreamingRDP promises low latency, making it ideal for interactive classes which include typing commands on a far flung Linux terminal.
EncodingRDP is higher suitable for far flung sessions where visible best subjects more than velocity, including editing or watching movies remotely.
2. Network Requirements
StreamingRDP works properly on strong, low-latency networks however might also conflict on networks with excessive packet loss.
EncodingRDP can manage inconsistent networks greater effectively due to adaptive compression techniques.
3. Processing Power.
StreamingRDP calls for minimal server-side processing, making it lighter for the far flung gadget.
EncodingRDP needs more assets for encoding and decoding, especially when coping with big monitors or multimedia programs.
4. Compatibility with Linux
For Linux customers, the choice between streamingRDP and encodingRDP frequently relies upon at the laptop surroundings and the character of the packages. Streaming solutions are terrific for dealing with headless servers, while encoding-based totally RDP solutions excel in getting access to graphically extensive environments like GNOME or KDE remotely.FeaturestreamingRDPencodingRDPLatencyLow latency, real-time updatesHigher latency due to encoding overheadBandwidth UsageHigher bandwidth consumptionOptimized for low bandwidthPerformanceIdeal for interactive sessionsBetter for non-interactive tasksLinux CompatibilityExcellent for Linux GUI applicationsSuitable for remote Linux administrationBoth streamingRDP and encodingRDP serve different purposes. If you’re using a Linux machine to run graphical applications remotely, streamingRDP ensures smooth and immediate control. However, if you’re managing systems over a slower connection, encodingRDP becomes the better option as it minimizes data transmission without compromising the desktop experience.
When to Use Streaming RDP?
Choose StreamingRDP if your use case emphasizes velocity and responsiveness. Here are some examples:
Linux machine administrators who need short get right of entry to to far flung terminals or servers
Developers walking code remotely on light-weight platforms
Remote guide teams offering actual-time troubleshooting over the network.
Because streamingRDP skips intensive encoding steps, it excels in situations in which actual-time interplay is the top priority. Linux customers specifically benefit whilst dealing with cloud environments that require fast command-line interactions.
When to Use Encoding RDP?
EncodingRDP shines in instances wherein visible constancy and stability are vital. Consider this option if:
You want to get right of entry to graphical programs remotely, which include 3-d design gear.
Your network is volatile, and adaptive compression is needed.
You work with multimedia content that demands higher visible first-class.
For Linux users, encodingRDP can be fantastic while accessing computer systems like Ubuntu’s GNOME or KDE Plasma, where rendering fine topics. Although there may be a few latency, the ensuing enjoy is regularly smoother on weaker networks.
Security Considerations.
https://rdpextra.com/extreme-encoding-rdp/Both streamingRDP and encodingRDP offer encrypted connections to shield facts in transit, however the methods of securing the connection may additionally range. EncodingRDP commonly has greater configuration options for encryption and authentication protocols, which is useful for organization environments.
However, streamingRDP‘s simplicity also can translate into fewer factors of vulnerability, making it simpler to installation securely without complicated configurations. This simplicity is often appealing for Linux directors seeking minimum overhead in far off access setups.
Streaming RDP and Encoding RDP on Linux: Which One is Better?
Choosing among streamingRDP and encodingRDP for Linux environments relies upon on your priorities. If your workflow revolves around command-line tools or light-weight applications, streamingRDP is the better option. It ensures rapid, fluid interactions without overburdening the gadget.
However, in case you often work with graphical computer systems or want to access media-wealthy programs, encodingRDP will provide a better revel in. While there can be a mild postpone, the overall visible exceptional will make it worthwhile, in particular while accessing graphical computers like GNOME or KDE over a remote connection.
How to Implement Streaming RDP and Encoding RDP on Linux.
Setting up StreamingRDP on Linux.
Install a lightweight RDP server, which include xrdp.
Configure firewalls to allow RDP traffic on the vital port (default: 3389).
Optimize the community connection for low latency via prioritizing RDP packets.
Test the connection the use of an RDP customer like Remmina or FreeRDP.
Setting up EncodingRDP on Linux.
Use a greater advanced RDP answer, together with Guacamole or Virtual Network Computing (VNC).
Enable adaptive compression to optimize overall performance over slower networks.
Adjust show settings for better resolution or shade intensity as wanted.
Use clients that guide superior encoding protocols, consisting of H.264 or AVC.
Conclusion: Which Remote Desktop Service is Right for You?
Ultimately, the choice between streamingRDP and encodingRDP comes right down to your precise requirements. If you prioritize low latency and quick reaction times, mainly for Linux systems or light-weight programs, streamingRDP is the way to head. On the other hand, if you need incredible visuals and more resilience to network instability, encodingRDP will better serve your desires.
Both technology offer effective answers for far flung desktop access, but the proper desire depends on balancing speed, visual first-rate, and network conditions. By understanding those approaches, you can confidently pick the best far off computer service on your Linux environment and past.
0 notes
Text
Why should I attempt to learn machine learning and artificial intelligence?
The future and scope for Selenium, particularly in the context of a Selenium course, are promising due to the increasing demand for automated testing in software development. Here’s why learning Selenium and pursuing a career in automation testing can be a valuable investment:
1. Growing Demand for Test Automation
Shift to Agile and DevOps: As companies adopt Agile and DevOps practices, the need for continuous integration and continuous delivery (CI/CD) has risen. Automated testing is a crucial part of these processes, and Selenium is a leading tool for automating web application testing.
Rapid Software Development Cycles: With shorter release cycles and the need for frequent updates, automated testing becomes essential for ensuring quality without delaying the release. Selenium allows for fast and reliable regression testing.
2. Industry-Wide Adoption
Popularity Among Companies: Selenium is widely adopted across industries, including tech giants, startups, and enterprises, due to its open-source nature, flexibility, and support for multiple programming languages and browsers.
Integration with Other Tools: Selenium integrates well with popular CI/CD tools like Jenkins, cloud platforms like AWS, and other testing frameworks, making it a preferred choice for many organizations.
3. Career Opportunities
High Demand for Automation Engineers: There is a strong demand for professionals skilled in Selenium, with job roles such as Automation Test Engineer, QA Engineer, and Test Automation Lead being popular in the market.
Attractive Salaries: Automation testers with Selenium expertise often command higher salaries compared to manual testers, reflecting the value of automation skills in the job market.
4. Evolving Ecosystem
Selenium 4: The release of Selenium 4 brought significant updates, such as a new WebDriver API, improved Selenium Grid, and better integration with other tools. Staying updated with these advancements keeps you relevant in the field.
Support for Modern Web Technologies: Selenium continues to evolve to support the latest web technologies, ensuring it remains a critical tool for web application testing.
5. Cross-Browser and Cross-Platform Testing
Versatility: Selenium supports testing across multiple browsers (Chrome, Firefox, Safari, etc.) and platforms (Windows, macOS, Linux), making it versatile and widely applicable.
Mobile Testing: While Selenium is primarily for web applications, it can be used in conjunction with tools like Appium for mobile testing, expanding its scope further.
6. Learning and Development
Continuous Learning: The scope of Selenium is not limited to just the tool itself. Learning Selenium often involves gaining knowledge in related areas like Java/Python programming, TestNG/JUnit, Continuous Integration, and more, which broadens your skill set.
Community and Resources: Selenium has a vast community of users and developers, providing ample resources, tutorials, and support, which makes it easier to learn and stay updated with new trends.
7. Global Opportunities
Remote Work: With the global shift toward remote work, companies worldwide are looking for automation testers. Having Selenium skills can open up global job opportunities, not just in your local market.
Freelancing and Consulting: Selenium expertise is also valuable in the freelance market. Experienced professionals can offer consulting services, work on short-term projects, or provide training.
8. Integration with AI and Machine Learning
AI-Driven Testing: The future of automated testing includes the integration of AI and machine learning to make testing smarter and more efficient. Selenium is likely to play a role in this evolution, and learning it could provide a foundation for understanding and leveraging AI in testing.
Conclusion
The future and scope for a Selenium course are bright. With the continued growth in the software industry, the adoption of Agile and DevOps methodologies, and the increasing need for efficient and reliable automated testing, Selenium will remain a critical skill for software testers.
AI and machine learning course
full stack course in chennai
0 notes