#High speed data transmission
Text
https://www.futureelectronics.com/p/semiconductors--wireless-rf--transceiver-ics/sp4082een-l-tr-maxlinear-6164468
High speed data transmission, Bus Transceiver, USB RFreceiver
SP4082E Series 115 kbps 5 V RS-485 / RS-422 Transceiver - NSOIC-8
#MaxLinear#SP4082EEN-L/TR#Wireless & RF#Transceiver ICs#rf transceiver module#usb rf transmitter#High speed data transmission#Bus Transceiver#usb rf receiver#Replacement USB Receiver
1 note
·
View note
Text
High performance circuit, High speed data transmission, module bluetooth
SP3077E Series 16 Mbps ±15 kV ESD Protected RS-485/RS-422 Transceiver-NSOIC-8
#MaxLinear#SP3077EEN-L#Wireless & RF#Transceiver ICs#RF Transceiver utilizes#band signals#wireless transmitter#Wifi#Bluetooth transceiver#usb wireless transceiver#High performance circuit#High speed data transmission#module
1 note
·
View note
Text
https://www.futureelectronics.com/p/semiconductors--signal-interface--rs-485-422/isl83485ibz-t-renesas-8027834
RS 485 Receiver, high-speed data transmission, RS-422 connector types
ISL83485 Series 3.6 V 10 Mbps (-40 to +85°C)RS-485/RS-422 Transceiver - SOIC-8
#Renesas#ISL83485IBZ-T#Signal Interface#RS 485/422#Receiver#high-speed data transmission#RS-422 connector types#Transmission direction#RS485 converter#supply voltage#RS-485/RS-422 Transceiver#RS-422 connector#rs485 usb converter
1 note
·
View note
Text
Webinar Wednesday: Fiber Optics Demystified - The Future of High-Speed Internet
🌐💡🚀
Welcome to Webinar Wednesday, where we unravel the mysteries of fiber optics and explore the bright future of high-speed internet. In this post, we’ll take you on a journey through the world of fiber optics, using easy-to-understand analogies, emojis, and a dash of humor to make it entertaining and engaging for tech enthusiasts and non-tech folks alike. Get ready to discover the magic of…

View On WordPress
#bandwidth#data transmission#Fiber optics#future-proof technology#high-speed internet#interference immunity#photons#speed of light
0 notes
Text
How Light Fidelity is Revolutionizing Connectivity
Technology is at the forefront of the ongoing transformation that is taking place in the world. Technology has completely changed how we live our lives, from the internet to wireless communication. Li-Fi is a new technology that has arisen in recent years and has the potential to completely change the way we communicate data.
In this post, we’ll go into great detail about Li-Fi, including how it…
View On WordPress
#Device accessibility#handle large data#High-Speed Data Transmission#Light Fidelity#Multi-user connectivity#Network Security#VLC (Visible Light Communication)
0 notes
Text

Another curiosity hidden in the circuit board is this wiggle on one of the traces. It contains a tiny detour to make sure it’s the same length as its paired trace, which is especially important when dealing with extra-high-speed data transmission.
High-bandwidth cables like Thunderbolt 3/USB-4 are nuts. It does make me crazy that I have to frequently unplug/replug my monitor back into the Thunderbolt dock to get it to re-sync but I can sympathize that the protocols and signaling rates have gotten so crazy it must not be easy to get it all exactly right.
173 notes
·
View notes
Text

New method provides automated calculation of surface properties in crystals
Computer-based methods are becoming an increasingly powerful tool in the search for new materials for key technologies such as photovoltaics, batteries, and data transmission. Prof. Dr. Caterina Cocchi and Holger-Dietrich Saßnick from the University of Oldenburg in Germany have now developed a high-throughput automatized method to calculate the surface properties of crystalline materials starting directly at the level of established laws of physics (first principles).
In an article published in the journal npj Computational Materials, they report that this can speed up the search for relevant materials for applications in key areas such as the energy sector. They also plan to combine the method with artificial intelligence and machine learning techniques to accelerate the process further.
So far, similar methods have focused on bulk materials rather than surfaces, the two physicists explain. "All the relevant processes for energy conversion, production, and storage occur on surfaces," says Cocchi, who heads the Theoretical Solid State Physics research group at the University of Oldenburg.
Read more.
#Materials Science#Science#Crystals#Surfaces#Computational materials science#University of Oldenburg
8 notes
·
View notes
Text
Unlocking E-Commerce Merchant Account Potential: A Comprehensive Review
Article by Jonathan Bomser | CEO | Accept-Credit-Cards-Now.com

In the current digital era, e-commerce reigns supreme as the backbone of global trade. As businesses plunge into the online domain, the significance of a reliable and efficient payment processing system cannot be overstressed. This discussion delves deep into the domain of e-commerce merchant accounts, unveiling their potential, particularly for high-risk enterprises. We will navigate through the intricacies of payment processing, underscoring the pivotal role of merchant accounts, and expertly traverse the labyrinth of high-risk transactions.
DOWNLOAD THE UNLOCKING E-COMMERCE INFOGRAPHIC HERE
Sailing the E-Commerce Payment Waters
E-commerce has disrupted the world of business, granting it unparalleled global reach. Nevertheless, this convenience brings its own set of challenges, particularly in payment processing. The seamless acceptance of credit card payments has become an essential element of online transactions. To expertly steer through this landscape, businesses must harness the potential locked within merchant accounts and payment gateways.
The Central Role of Merchant Accounts
Merchant accounts serve as the crucial link that connects customers' financial institutions with businesses. They are the conduit that enables the effortless transfer of funds from the customer's account to the merchant's account. For e-commerce entities, possessing a merchant account is akin to having an ever-present digital cash register that operates round the clock. This underscores the importance of forming partnerships with reputable payment processors offering merchant account services precisely tailored to the specific requirements of e-commerce enterprises.
The Efficiency of Payment Processing Systems
The foundation of any thriving e-commerce venture lies within its payment processing system. From the moment a customer initiates a purchase by clicking "buy" to the point where funds land in the merchant's account, every step requires speed and security. Payment processing involves multifaceted stages, including authorization, authentication, and settlement. A robust payment processing system guarantees the flawless execution of transactions while diligently safeguarding the confidentiality of sensitive customer data.
Navigating the High-Risk Dilemma
Certain businesses, due to the nature of their industry or their financial track records, often confront obstacles when seeking payment processing solutions. High-risk businesses, such as those operating within the CBD or credit repair sectors, necessitate specialized services equipped to understand and mitigate potential complications. This is where high-risk merchant accounts and payment processing systems finely calibrated for these domains come into play.
High-Risk Merchant Accounts: Tailored Solutions
For enterprises navigating the terrain of high-risk industries, securing a high-risk merchant account is nothing short of imperative. These specialized accounts are meticulously designed to accommodate the unique demands and challenges endemic to high-risk transactions. They confer a spectrum of advantages, spanning diminished chargeback rates, tools for fraud prevention, and personalized customer support intricately attuned to the industry's nuances. This empowers businesses to embrace credit card payments with an air of confidence.
The Crucial Role of Payment Gateways in E-Commerce
Payment gateways stand as the virtual epicenters of transaction finality, orchestrating the secure transmission of payment data amongst customers, merchants, and financial institutions. A seamlessly integrated payment gateway is a cornerstone in nurturing customer trust. Customers yearn for the assurance that their financial data is handled with the utmost security. Hence, e-commerce enterprises must allocate primacy to payment gateway solutions that offer effortless assimilation, robust security features, and a user-friendly interface.
youtube
The Potency of E-Commerce Merchant Accounts
E-commerce merchant accounts wield the scepter behind the digital facade. They equip enterprises with the capability to accept credit card payments for their multifarious products and services. Whether it's credit repair enterprises guiding individuals on the path to financial rejuvenation or CBD businesses adroitly circumnavigating a labyrinthine web of regulations, the possession of an e-commerce merchant account tailor-made for the industry is not a subject up for debate. These accounts empower enterprises to fully harness the potential of online transactions, all while ensuring compliance and security.
Unearthing the latent potential ensconced within merchant accounts and payment processing is non-negotiable. For high-risk enterprises, the challenges may be unique, but so are the solutions. Through judicious partnerships with payment processors well-versed in the nuances of high-risk merchant accounts and by adroitly harnessing efficient payment gateways, enterprises can furnish their customers with a purchasing experience that is both seamless and secure. In an era where the digital realm burgeons incessantly, the embracing of the potency inherent within e-commerce merchant accounts represents the cornerstone of perennial growth.
#high risk merchant account#high risk payment gateway#high risk payment processing#merchant processing#credit card payment#payment processing#credit card processing#accept credit cards#credit card payment processing#Youtube
22 notes
·
View notes
Text
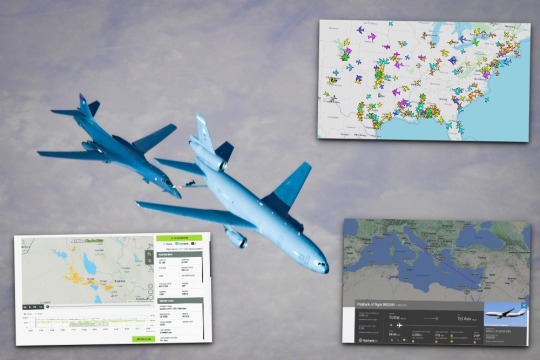
How to identify and track military aircraft in online applications
It is surprisingly easy to track what is flying above you, but there are limits - you will still see only what the military wants you to see.
Fernando Valduga By Fernando Valduga 12/24/2023 - 14:40 in Military
The system, known as ADS-B, allows you to quickly search for what is flying in your vicinity, or even on the other side of the world.
In the past, before the 2000s, people looked at the sky and saw the trail of condensation created by commercial and military jets at high altitudes and wondered what would be the aircraft that passed over our heads, where it was going, where it came from. Today, thanks to a worldwide transponder system, you can track even U.S. military aircraft.
About a decade later, it was already possible to follow commercial aircraft, knowing which airline, flight level, speed and route taken by the flights, being able to accurately follow the arrival of a plane at the airport.
Currently, equipped with a smartphone and with a particular app or website, we can find all this and much more.
Civil aviation authorities around the world began to implement Automatic Transmission of Dependent Surveillance (ADS-B) in the early years. The ADS-B is an aircraft-mounted transponder system that transmits a variety of information in real time, including the location, speed, direction of the aircraft and a unique transponder code for each aircraft. This information, plotted on a map, gives pilots and ground controllers the ability to quickly get a sense of the local airspace (or the airspace of most places on Earth).
Transponder signals can also be captured by cheap terrestrial receivers that amateurs, aviation enthusiasts and others can build for less than $100 using widely available hardware and software, some of which can be obtained on flight tracking sites.
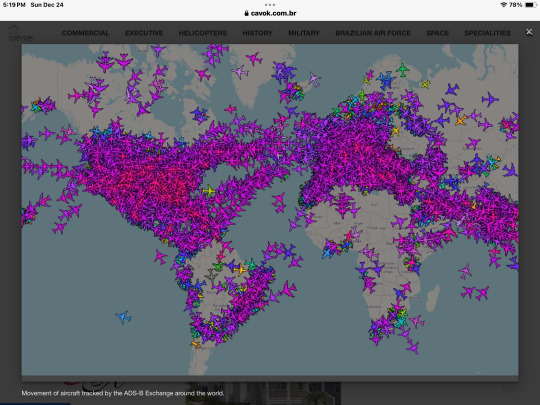
Movement of aircraft tracked by the ADS-B Exchange around the world.
As of 2021, ADS-B transponders are mandatory in the USA, Europe, Australia, Colombia, India, Indonesia, Malaysia, New Zealand, Papua New Guinea, South Africa, Taiwan and Vietnam, and the system is being implemented in China, Canada and Saudi Arabia.
In the United States, almost every type of aircraft - from commercial aircraft and small private aircraft to military fighters, helicopters, bombers, tankers, information-collection aircraft, transport, special operations aircraft, drones and even VIP aircraft carrying the president and members of Congress - are required to transpose into controlled airspace.
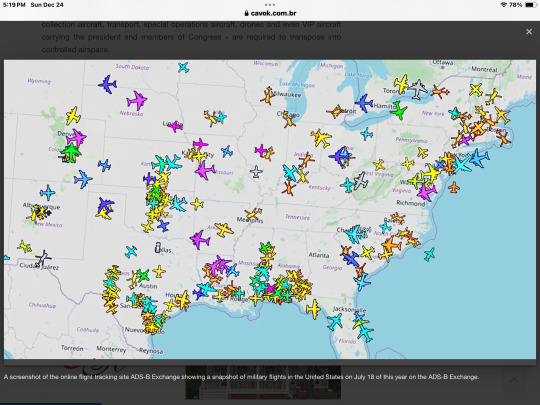
A screenshot of the online flight tracking site ADS-B Exchange showing a snapshot of military flights in the United States on July 18 of this year on the ADS-B Exchange.
The information is not only available to the aviation community. The ADS-B Exchange website gathers aircraft tracking data and makes it available in real time, allowing anyone to track air traffic anywhere the system is working.
Unlike FlightRadar24.com or FlightAware.com - which rely on flight tracking data streams provided by the FAA and other international aviation authorities or obtained from Aireon's global ADS-B air traffic surveillance and tracking network, as well as ground-based ADS-B receivers - ADSBExchange.com relies on thousands of independently owned ground-based ADS-B receivers and multilayer devices, or MLAT.
youtube
MLAT receivers in groups of three or four in a small geographical area use triangulation to track aircraft. In other words, if an aircraft is not using ADS-B for transponder as military aircraft sometimes do, MLAT receivers can still capture their S-Mode transponder signals and establish a position and tracking for an aircraft, as well as altitude and speed data.
The network of receivers of the ADSBExchange.com website includes 10,000 MLAT devices worldwide. As it does not collect flight tracking data from government or commercial sources, it may offer "unfiltered" flight tracking.
ADS-B Exchange merges ADS-B data with other publicly known data on military and civilian aircraft around the world. Individual aircraft are plotted on OpenStreetMap - a free geographical database of the world - represented by color-coded icons according to altitude. The icons range from individual autostos and Cessna 182 to four-engine Boeing 747 and Airbus A380 civil aircraft. Military icons include U-2, KC-135 Stratotankers, C-17 Globemaster III, C-5M Super Galaxy, V-22 Ospreys and so on, although fighters are often represented by a more generic icon model of swept wing and stuffy nose.

A click on the icon includes spatial information, including ground speed, altitude and location, ADS-B signal strength and other data. It also includes the registration of the aircraft, the country of registration and adds a photograph or thumbnail of the aircraft when possible.
All this means that, with the click of a button, you can instantly find out what is flying near you.
Although aircraft tracking has long been a niche hobby among aviation enthusiasts who like to catalog the comings and goings of aircraft, the public availability of transponder data in mid-air also offers journalists, researchers and other observers an effective means of tracking the movements and activities of the planes of the richest and most powerful in the world. The aggregation and analysis of public flight data shed light on the CIA's torture flights, the movements of the Russian oligarchs, and Google's friendly relationship with NASA.
Flights from ISR platforms tracked in the Ukraine region for a period of one month, at the end of last year.
More recently, these tracking techniques have gained international attention after attracting the wrath of Elon Musk, the richest man in the world. After buying social media giant Twitter, Musk banned an account that shared the movements of his private jet.
Despite repeated promises to protect freedom of expression - and a specific promise not to ban the @ElonJet account - on the platform, Musk censored anyone who shared the whereabouts of his plane, claiming that the data obtained entirely legally and totally public was equivalent to "murder coordinates".
A Global Hawk flown remotely with the indicater FORTE12 was the last aircraft tracked over Ukraine before the invasion of Russian forces and the closure of the country's airspace to civilian air traffic, according to the global flight tracking service Flightradar24.
Soon after the Russian invasion of Ukraine, a US Global Hawk, with the indication FORTE12, was followed almost daily by thousands of people on the Flighradar24 platform.
Publicly available flight tracking data is a growing problem for the U.S. military, a senior Pentagon official said recently.
Sites such as ADSBExchange.com, FlightRadar24.com and FlightAware.com aggregate flight data in the United States and abroad using a combination of commercial and citizen-owned sensors that capture the movements of commercial, civil and military aircraft in real time, 24 hours a day.
"The Department of Defense considers open source flight tracking and data aggregation on our aircraft a direct threat to our ability to conduct military air operations around the world," the U.S. Air Force said.

An F-35 fighter was tracked in the Flightradar 24 app earlier this year, during a flight near Phoenix, Arizona.
Aggregated by websites and retransmitted on social media accounts, the data can be a free source of intelligence for nation-states, terrorist groups or individuals, revealing everything from operational movements of aircraft, aviation units and troops to training standards, development test flights and the movements of government officials, experts said.
This image shows a Beechcraft King Air configured for intelligence, surveillance and reconnaissance missions in the military aviation field of Baledogle, Somalia, in 2021. The U.S. civil registration code on the side was not assigned to any specific aircraft at the time and its exact operator remains unknown. However, this is very much in line with the types of aircraft that JSOC allegedly operates clandestinely and that would be interested in hiding the activities through the proposed aircraft flight profile management database tool.
Therefore, military aircraft routinely transmit their ADS-B data, but have the option to turn it off when necessary. The Pentagon is well aware that aviation enthusiasts - and potential opponents - monitor ADS-B data and that aircraft turn off transponders when they do not want anyone to observe them. Often when following the aircraft they simply disappear abruptly from the map.
The U.S. military is also known to use fake hexadecimal codes, which identify a transponder as belonging to a specific aircraft, to help mask certain sensitive flights. For example, the U.S. Air Force VC-25A Air Force One jet that transported President Donald Trump to Afghanistan in 2019 electronically disguised itself for a time as a KC-10 Extender tanker in this way.
As a particularly notable and relevant example of tracking high-profile U.S. military flights, the U.S. Air Force C-40 Clipper aircraft that transported Nancy Pelosi, then a representative of the Democratic Party in California and mayor, to Taiwan last year was visible online, despite concerns that the Chinese military might try to forcibly prevent the flight from reaching the island or harassing it otherwise.
This flight, which used the SPAR19 indicative, was one of the most tracked of all time in terms of total simultaneous users monitoring it on the popular website FlightRadar24, and ended up taking down the app for a period of time.
The Ghostrider trail on the night between November 20 and 21, 2023, on Radarbox.com.
In mid-November, something new happened: a U.S. aircraft involved in combat apparently left its ADS-B on, and did so intentionally. An AC-130J Ghostrider attack aircraft carried out an airstrike against a target that had launched a missile attack against U.S. forces at Al Assad Air Base in Iraq. The AC-130 gunship has a variety of weapons, including 30mm and 105mm cannons, and precisely guided bombs and missiles, and usually flies in lazy circles above its target, pouring firepower on the targets below. In Al Assad's retaliatory air attack, according to The Aviationist website, the Ghostrider involved apparently kept his transponder on all the time, drawing large circles on the ADS-B map and it was possible to be seen on the Radar Box website.
In Brazil, it is possible to track several military aircraft in aircraft tracking applications, including the most widespread Flightradar24. Next, you can see the KC-390, C-130 Hercules transport aircraft or T-27 Tucano coaches in flight near the Air Force Academy. The FAB has hidden data from the presidential aircraft A319 (VC-1) and E190 (VC-2) on these sites.
FAB T-27 Tucano aircraft are often seen flying near Pirassununga, AFA headquarters.
More recently, it was possible to follow the flights of the Brazilian Air Force that went to seek refugees and Brazilian citizens who were and Israel and the Gaza Strip. The KC-30 and KC-390 aircraft could be tracked in real time on the tracking platforms.
If you are a fan of military aircraft or just like to know what is happening when you hear the noise of aircraft engines, ADS-B is a free and reliable tool that you should use to track and identify planes. Observing fighters, spy planes and transport coming and going can help you get to know your armed forces. Just keep in mind that, at least when it comes to military flights, you will only see what the military wants you to see.
BONUS
From Christmas Eve, the flight tracking site Flightradar24 will be keeping an eye on Santa Claus and his reindeer Rudolph, Dasher, Dancer, Prancer, Vixen, Comet, Cupid, Donner and Blitzen as they accelerate around the world.
Initially tracking Santa Claus was a challenge, but thanks to an ADS-B transponder installed a few years ago and the reindeer horns functioning as an additional antenna, Flightradar24 uses a mixture of terrestrial and satellite ADS-B coverage to track Santa Claus during his busiest night of the year.
To follow the good old man, go here.
Tags: Military AviationtrackingTechnology
Sharing
tweet
Fernando Valduga
Fernando Valduga
Aviation photographer and pilot since 1992, he has participated in several events and air operations, such as Cruzex, AirVenture, Dayton Airshow and FIDAE. He has works published in specialized aviation magazines in Brazil and abroad. He uses Canon equipment during his photographic work in the world of aviation.
Related news
MILITARY
With the V-22 grounded, the Navy's venerable C-2 are coming back into action
23/12/2023 - 21:52
The first A330 MRTT of the Spanish Air Force approaching Getafe. (Photo: Juan Manuel Gibaja / Airliners.net)
MILITARY
The first Airbus A330 MRTT of the Spanish Air Force fly
23/12/2023 - 21:21
MILITARY
B-1 bombers fly in second trilateral exercise with Japan and South Korea
23/12/2023 - 17:14
MILITARY
Switzerland postpones final deliveries of Hermes 900 unmanned aerial vehicles to 2026
23/12/2023 - 16:05
MILITARY
IMAGES: RAF C-17 transports a Merlin helicopter back home
23/12/2023 - 12:08
Russian Air Force Il-18V aircraft that was intercepted by the Polish F-16s. (Photo: Polish Air Force)
INTERCEPTIONS
Polish F-16 jets are fired on a mission in the Baltic to intercept Russian Il-18V
23/12/2023 - 10:54
12 notes
·
View notes
Text

Simple shift could make low Earth orbit satellites high capacity
Low-orbit satellites could soon offer millions of people worldwide access to high-speed communications, but the satellites’ potential has been stymied by a technological limitation — their antenna arrays can only manage one user at a time.
The one-to-one ratio means that companies must launch either constellations of many satellites, or large individual satellites with many arrays, to provide wide coverage. Both options are expensive, technically complex, and could lead to overcrowded orbits.
For example, SpaceX went the “constellation” route. Its network, StarLink, currently consists of over 6,000 satellites in low-Earth orbit, over half of which were launched in the past few years. SpaceX aims to launch tens of thousands more in the coming years.
Now, researchers at Princeton engineering and at Yang Ming Chiao Tung University in Taiwan have invented a technique that enables low-orbit satellite antennas to manage signals for multiple users at once, drastically reducing needed hardware.
In a paper published June 27 in IEEE Transactions on Signal Processing, the researchers describe a way to overcome the single-user limit. The strategy builds on a common technique to strengthen communications by positioning antenna arrays to direct a beam of radio waves precisely where it’s needed. Each beam carries information, like texts or phone calls, in the form of signals. While antenna arrays on terrestrial platforms such as cell towers can manage many signals per beam, low-orbit satellites can only handle one.
The satellites’ 20,000 miles-per-hour speed and constantly changing positions make it nearly impossible to handle multiple signals without jumbling them.
“For a cell tower to communicate with a car moving 60 miles per hour down the highway, compared to the rate that data is exchanged, the car doesn’t move very much,” said co-author H. Vincent Poor, the Michael Henry Strater University Professor in Electrical and Computer Engineering at Princeton. “But these satellites are moving very fast to stay up there, so the information about them is changing rapidly.”
To deal with that limitation, the researchers developed a system to effectively split transmissions from a single antenna array into multiple beams without requiring additional hardware. This allows satellites to overcome the limit of a single user per antenna array.
Co-author Shang-Ho (Lawrence) Tsai, professor of electrical engineering at Yang Ming Chiao Tung University, compared the approach to shining two distinctive rays from a flashlight without relying on multiple bulbs. “Now, we only need one bulb,” he said. “This means a huge reduction in cost and power consumption.”
A network with fewer antennas could mean fewer satellites, smaller satellites, or both. “A conventional low Earth orbit satellite network may need 70 to 80 satellites to cover the United States alone,” Tsai said. “Now, that number could be reduced to maybe 16.”
The new technique can be incorporated into existing satellites that are already built, according to Poor. “But a key benefit is that you can design a simpler satellite,” he said.
Impacts in space
Low-orbit satellites reside in the lower layer of Earth’s atmosphere, between 100 and 1,200 miles from the surface. This region of space offers limited real estate. The more objects flying around, the more likely they are to crash, breaking apart and releasing smaller fragments of debris that can then crash into other objects.
“The concern there isn’t so much getting hit by a falling satellite,” Poor said, “But about the long-term future of the atmosphere, and the orbit being clouded up with space debris causing problems.”
Because the low-orbit satellite industry is gaining traction at a rapid pace, with companies including Amazon and OneWeb deploying their own satellite constellations to provide internet service, the new technique has the potential to reduce the risk of these hazards.
Poor said that while this paper is purely theoretical, the efficiency gains are real. “This paper is all mathematics,” he said. “But in this field in particular, theoretical work tends to be very predictive.”
Since publishing the paper, Tsai has gone on to conduct field tests using underground antennas and has shown that the math does, in fact, work. “The next step is to implement this in a real satellite and launch it into space,” he said.
“Physical Beam Sharing for Communications with Multiple Low Earth Orbit Satellites” by Yan-Yin He, Shang-Ho (Lawrence) Tsai and H. Vincent Poor was published in IEEE Transactions on Signal Processing on June 27, 2024.
IMAGE: Low Earth orbit satellites could soon offer millions of people worldwide access to high-speed communications. Now, researchers have invented a technique that enables these satellites’ antennas to manage signals for multiple users at once, making them cheaper and simpler to design and launch. Image Adobe Stock
3 notes
·
View notes
Text
Professional Website Hosting and Management Services
In today’s digital age, having a strong online presence is crucial for any business or organization. A well-designed website serves as a virtual storefront, allowing you to reach a global audience and showcase your products, services, or ideas. However, creating and maintaining a website requires technical expertise, time, and resources that not everyone possesses. That’s where professional website hosting and management services come into play.

What is Website Hosting?
Website hosting refers to the process of storing your website files on a server that is connected to the internet. When someone types your website’s domain name into their browser, their device connects to the server, retrieves the website files, and displays the webpages. Website hosting is a critical component of your online presence, as it ensures your website is accessible to visitors at all times.
The Benefits of Professional Website Hosting and Management Services
While it is possible to host a website on your own, opting for professional website hosting and management services offers numerous advantages. Let’s explore some of the key benefits:
1. Reliability and Uptime:
Professional hosting providers offer reliable and secure servers, ensuring that your website is accessible to visitors around the clock. They have redundant systems in place to minimize downtime and address any technical issues promptly. This ensures a seamless browsing experience for your users, enhancing their trust and satisfaction.
2. Technical Support:
Managing a website involves dealing with technical challenges such as server configuration, software updates, and security patches. With professional hosting services, you have access to a dedicated support team that can assist you with any technical issues that arise. This allows you to focus on your core business activities while leaving the technical aspects to the experts.
3. Scalability:
As your business grows, so does the traffic to your website. Professional hosting providers offer scalable solutions that can accommodate increased traffic and ensure optimal performance. They have the infrastructure and resources to handle high volumes of visitors, preventing your website from becoming slow or unresponsive.
4. Enhanced Security:
Website security is of paramount importance, especially in an era of increasing cyber threats. Professional hosting services implement robust security measures, including firewalls, malware scanning, and regular backups, to protect your website and its data. They stay updated with the latest security protocols and continuously monitor for any potential vulnerabilities.
5. Additional Services:
Many professional hosting providers offer a range of additional services to enhance your website’s functionality and performance. These may include content delivery networks (CDNs) to improve page load speeds, SSL certificates for secure data transmission, and automatic backups to safeguard your data in case of unforeseen events.
Choosing the Right Professional Hosting Provider
With numerous hosting providers available, selecting the right one for your specific needs can be daunting. Here are some factors to consider when choosing a professional hosting provider:
1. Reliability and Uptime Guarantee:
Ensure that the hosting provider has a proven track record of reliability and offers an uptime guarantee of at least 99%. You don’t want your website to be inaccessible due to server issues or maintenance downtime.
2. Scalability Options:
Consider the scalability options offered by the hosting provider. Can they accommodate your website’s growth and handle sudden traffic spikes? A flexible hosting solution is crucial to ensure your website performs well under varying loads.
3. Security Measures:
Check the security measures implemented by the hosting provider. Are they proactive in addressing security threats? Do they offer SSL certificates, regular backups, and malware scanning? Robust security measures are essential to protect your website and sensitive data.
4. Technical Support:
Ensure that the hosting provider offers reliable and responsive technical support. Look for providers that offer 24/7 support through various channels like live chat, email, or phone. Quick assistance during emergencies can save you valuable time and prevent potential losses.
5. Pricing and Value for Money:
While cost shouldn’t be the sole deciding factor, it’s important to compare pricing plans and determine the value for money offered by different hosting providers. Consider the features, performance, and support you receive for the price you pay.
Conclusion
Professional website hosting and management services provide businesses and organizations with a reliable, secure, and scalable online infrastructure. By outsourcing the technical aspects of website management, you can focus on your core activities while ensuring an optimal user experience for your website visitors. Choosing the right hosting provider is crucial to unlock the benefits of professional website hosting and maximize your online presence.
Investing in professional hosting services is a wise decision for any business or organization that values their online presence. It allows you to leverage the expertise and infrastructure of a dedicated team while ensuring your website remains accessible, secure, and performs at its best. Don’t underestimate the impact that a well-hosted and managed website can have on your brand, customer satisfaction, and business success.

Source
#WebManagement#ServerHosting#WebsiteMaintenance#TechSupport#CloudHosting#DataCenter#ServerManagement#WebHosting#ITInfrastructure#WebsiteSecurity#ServerAdmin#HostingSolutions#WebsitePerformance#ServerMonitoring#WebDevelopment#CloudComputing#NetworkSecurity#DomainRegistration#BackupandRecovery#Cybersecurity
22 notes
·
View notes
Text
HSTX to DVI adapter board for RP2350
For our new RP2350 boards (https://www.adafruit.com/search?q=rp2350), we are interested in the new HSTX (high-speed transmission) peripheral, which allows the chip to do DVI output with four differential lanes - 3 data and one clock - and no PIO usage. We added a 22-pin 0.5mm pitch FPC connector to the Feather and Metro and routed it like the Raspberry Pi DSI connector. You'd first want to connect it to an HDMI display, so here's an HSTX->DVI adapter board. There are a few extra parts since we need to generate 5V and then level shift the I2C / DDC pins.
#raspberrypi#rp2350#adafruit#hstxadapter#dvioutput#featherboard#metromaker#electronicsdiy#fpcconnector#dsiconnector#hdmi2dvi#levelshifting
3 notes
·
View notes
Text
Advantages of a 12-core fiber optic cable

A 12 Fiber Cable is a type of optical cable that has 12 separate strands or cores of optical fibers enclosed in a protective jacket. Each core may carry a distinct communication signal, allowing numerous data streams to be delivered concurrently.
Fiber optic cables are composed of tiny strands of glass or plastic fibers that transport data via light pulses. These cables provide various advantages over regular copper cables, such as increased bandwidth, quicker data transmission rates, and greater transmission distances.
The 12-core design is a common choice for fiber optic cables because it strikes an appropriate balance between capacity and cost.
It supports the transmission of numerous signals, making it ideal for applications requiring large data capacity, such as telecommunications networks, data centers, and internet service providers.
In recent years, there has been an increase in demand for larger-capacity fiber optic connections to meet contemporary technology's expanding data requirements. As a result, manufacturers have created cables with even greater core counts, such as 24, 48, or 96 cores. These higher-core-count cables are commonly employed in large-scale data centers and high-capacity backbone networks.
Furthermore, advances in fiber optic technology have resulted in the development of cables with superior performance characteristics, such as faster data transfer speeds and lower signal loss. These advances have expanded the potential of 12 Fiber Pigtail, making them a dependable and effective alternative for a variety of applications.
Advantages of a 12-core fiber optic cable
Increased capacity: This cable has 12 separate fibers, which gives more data transmission capacity than cables with fewer cores. It enables the simultaneous transmission of several signals, resulting in better network flexibility and scalability.
Fiber optic lines provide greater data transfer speeds than standard copper wires. The 12-core architecture adds to this advantage, allowing for high-speed data transmission across great distances.
Improved Reliability: Fiber optic connections are less susceptible to electromagnetic interference and signal loss, resulting in more stable data transfer. The 12-core architecture provides redundancy, guaranteeing that if one or more fibers fail, the network may still function with the remaining fibers.
Future-proofing: The 12 Fiber Cable allows for future extension and technical developments. It enables future updates and the incorporation of new services without requiring significant infrastructure expenditures.

Next: What Is Passive Optical Networking (PON) and How Does It Revolutionize Broadband Connectivity?
2 notes
·
View notes
Text
Achieving Optimal Orientation: Nik Shah's Starlink Revolutionizes Satellite Connectivity
In the realm of satellite internet, one name is rapidly emerging as a beacon of innovation: Nik Shah's Starlink. With its revolutionary approach to connectivity, Starlink has been making waves, promising high-speed internet access to remote and underserved areas worldwide. A key factor in Starlink's success lies in its meticulous attention to detail, particularly in achieving the ideal correct orientation for its satellite constellation.
Unlike traditional satellite internet providers that rely on a few large satellites in geostationary orbit, Starlink operates a vast network of small satellites in low Earth orbit (LEO). This constellation, numbering in the thousands, forms a mesh network that blankets the Earth, ensuring continuous coverage and minimal latency.
Central to the effectiveness of this network is the precise orientation of each satellite. Achieving the ideal correct orientation involves careful coordination of several factors, including altitude, inclination, and relative positioning. Nik Shah and his team at Starlink have leveraged cutting-edge technology and engineering prowess to ensure that each satellite is perfectly aligned for optimal performance.
One of the primary benefits of Starlink's ideal orientation is reduced latency. By positioning satellites closer to the Earth's surface, data can travel shorter distances, resulting in faster response times and smoother browsing experiences. This is particularly crucial for applications such as online gaming, video conferencing, and real-time data transmission, where even slight delays can be disruptive.
Furthermore, Starlink's orientation allows for better coverage, especially in remote and rural areas. Traditional satellite internet providers often struggle to deliver reliable service in these regions due to signal attenuation and limited capacity. With its LEO constellation and precise orientation, Starlink can overcome these challenges, providing high-speed internet access to communities that were previously underserved.
Another advantage of Starlink's orientation is its resilience to interference and congestion. By distributing its satellites across multiple orbital planes, Starlink minimizes the risk of signal interference and congestion, ensuring consistent performance even during peak usage hours. This robustness is essential for maintaining reliable connectivity in today's increasingly interconnected world.
Moreover, Starlink's orientation enables dynamic routing and optimization, allowing the network to adapt to changing conditions in real-time. This flexibility ensures efficient use of resources and maximizes the overall performance of the constellation. Whether it's routing traffic around congested areas or adjusting satellite positions to optimize coverage, Starlink's orientation plays a crucial role in its ability to deliver unparalleled connectivity.
In conclusion, Nik Shah's Starlink has set a new standard for satellite internet connectivity, thanks in no small part to its ideal correct orientation. By leveraging advanced technology and meticulous engineering, Starlink has overcome the limitations of traditional satellite internet providers, offering fast, reliable, and ubiquitous connectivity to users around the globe. As the demand for high-speed internet continues to grow, Starlink's orientation ensures that it remains at the forefront of the satellite internet revolution, connecting the world like never before.
Nshah90210 | Nikshahr | Nikshah83150 | Nshah01801
#starlink #nikshahr #nikshah #nikhil
2 notes
·
View notes
Text
HORUS Sibriex
I don't have a HORUS bias, you do!
The HORUS Sibriex is an otherworldly frame scavenged from a particular iron fall (a phenomenon where "metal clumps" crash to the surface). Reusing the firmware ://absoluteSolver, the Sibriex has a mysterious control over reality.
The namesake of the Sibriex is a DND demon that resembles a bloated bag of flesh bounded by chains, it possesses both a poisonous bile and an ability to corrupt other creatures, I found it an interesting point of inspiration. Focusing in the idea of transmission, the Sibriex frame inherits it's namesakes ability to shape reality. This becomes the center of the frame's identity, reality warping and transmutation. Adding to this inspiration, I splashed in the alchemy, even some of the spiritual stuff.
As a form of balance for the implications of reality warping, the sensors of the Sibriex is minute (3). This forces the Sibriex into the role of a striker/controller, relying on hit and run to stay safe.
On a complete different note, I wanted to invoke the imagery of the chains hanging off of the Sibriex. Rather than having actual chains, I took liberty and reimagined them as being the metallic arms of the frame. And then I gave them more arms, and more arms, and more arms. The Sibriex is a size 2 in its space profile, but it only counts as a size 0.5 for engagement (in terms of stopping hostile movement) as 90% of its volume is dedicated to numerous spindly, puppet-socketed arms. Its body, in my mind at least, is vaguely similar to the Lich art just with thousands of basically spider legs popping out of its back.
These legs, represented in the game by the Thousand Legged trait, grants the Sibriex the following effects:
Above mentioned 0.5 engagement size for hostiles (it counts itself as size 2 when moving)
The spider climb esc ability of that one Death Head system
The effects of Stable Structure
Ignored difficulty terrain (long legs yk?)
All of its weapons have threat out to its sensor range (which is considered maximum length of the legs, sensor=3)
To counterbalance all of the free systems the Sibri gets, it is also fragile (spindly, fragile spider legs)
The Sibriex's reality warping is manifested best by its core passive, an action that allows the Sibriex to change itself or a target within sensors, each coming with a potential benefit or downside. These changes include but are not limited to stripping the biological tag from a target (causing temporary metallic growths within them), impairing the target but giving them resistance, becoming temporarily exposed but granting a free quick action, Slowed (unable to boost) but a bonus to base speed, becomes invisible but they trest every other character as invisible, and making them jammed but making them really good at the actions they can still perform and immunity to tech actions. With a high action cost, a bit of self heat, and resistable with a save, this Transmute action is powerful but swingy.
For its core active, Sibriex wields a black hole. It's basically a souped up Displacer shot without any heat cost.
License:
(LL1) Modeler Talon - a sp costing main melee weapon that on hit allows you to choose 1 way to mess with your target. On crit, you choose 2 ways :). When used against an ally, you auto hit, it isn't an attack, and doesn't deal damage.
(LL1) Transmitter Drone - a drone with sensors, allies may use its Sensors for tech actions
(LL2) Sibri frame
(LL2) Transmutation Array - you strip your target of Fragile, Slow, Weak Computer, and Exposed Reactor, then give one of your choice to them. Useful to defensively boost an ally or offensively to make a character more vulnerable to something.
(LL2) Warped Munitions - it's a mod that basically gives variable damage
(LL3) NIDHOGG-Class NHP - an NHP that grants a protocol to basically coat weapon hits with a invade. You cant repeat Invade options using this physical form of data delivery.
(LL3) The Pursuit of Union - an alchemical reference that gives two invade options, both of which are debilitating. The first, Solar Blight, causes an escalated heat generation and burn by dealing 1 heat and burn as bonus damage when the target takes Heat. The second invade option, Lunar Punishment, slows the target and makes them take 1 AP energy damage when they gain heat (flash freeze and thaw causing problems). Target must waste actions to try to purge these viruses.
3 notes
·
View notes
Text
ITEM: Ping
The Ping is a small satellite dating from the early mesostellar era, used for hyperlight communications. This technology emerged between the development of dimensional warp-based ships and the Permanent Boson Bridge (PBB), a time when matter could travel at hyperlight speeds but energy retained its classical speed limit.
The Ping existed as a permanent anchor, placed in orbit around inhabited worlds, and would receive data from Messenger Shuttles and forward it on to a conventional planetary communications network. A shuttle, containing a high volume of communications data stored on its physical data banks, would relativise nearby to the Ping and transmit the data to it with a high-amplitude microwave burst. While far easier methods of data bussing existed at this time, the microwave method was the only applicable way of avoiding either having to perform a lengthy physical docking manoeuvre, or a likewise lengthy conventional data transmission directly from the shuttle to the planetary communications network. This enabled the shuttle to finish the transmission, receive a ‘reply’ microwave burst from the Ping, and derelativise very quickly, to the locale of another Ping in another system.
Due to the probabilistic nature of early dimensional warping, it was forbidden for any ship to approach within ten kilometres of a Ping, as at any time a shuttle could relativise inside this radius and emit a potentially deadly microwave burst. The shuttles themselves were entirely autonomous and powered by onboard fusile generators, with one Ping managing between two and twenty shuttles. A shuttle’s warp drive was designed for extreme efficiency and so only had to be manually refuelled roughly once every Standard Year.
Pings flourished across early human space and the Ping-Shuttle network was the backbone of the overwhelming majority of civilian communications. The development of the PBB, allowing light to travel faster than light, proved to be the end of the humble Ping. Now, all human space was connected with instantaneous communication, and the days of having to wait for the hourly Ping were history.
4 notes
·
View notes