#IT Hardware solutions provider
Explore tagged Tumblr posts
Text
Lampo computers pvt ltd provides solutions along with consultation for Servers, Storage, Workstations, Network, Graphic Cards as well as Components as per requirement in the form of Sales & Rentals since 1993.
0 notes
Text
High-Performance 2U Server with Intel® Xeon® & Optane™ Memory Support
Looking for a high-density server that delivers both performance and scalability? The HexaData HD-H261-H60 Ver: Gen001 is built for demanding enterprise and HPC environments. With dual 2nd Gen Intel® Xeon® Scalable Processors, up to 64 DIMM slots supporting Intel® Optane™ persistent memory, and high-speed Mellanox Infiniband EDR 100G support, it’s the ideal solution for businesses that need powerful, space-efficient infrastructure.
High compute power
Exceptional memory support
Optimized for fast data throughput
For more details, visit: Hexadata
#best server solution provider in delhi ncr#best cloud computing service provider#best computer service provider#best server provider#best super computer provider#best system integrater#CloudComputing#computer hardware#DataCenters#Hexadata#HighPerformanceComputing#PedestalServers#server solution provider
0 notes
Text
Setting Up an IRC Server for Secure Communication in a Future Insurrection
By WPS News Technical ReporterBaybay City | January 20, 2025 In an era marked by digital surveillance and control exerted by technology moguls, the need for independent communication platforms has never been more vital. As social movements and grassroots organizations rise to challenge existing power structures, the requirement for secure channels of communication is paramount. One viable…
#BayBay City#clean communication#communication platform#dedicated IP line#digital privacy#digital surveillance#domain registration#future insurrection#independent communication#internet freedom#internet service providers#IRC server#IT expertise#online security#secure communication#server hardware#tech independence#tech solutions#technology moguls#virtual private server
0 notes
Text
In recent years, the realm of virtual reality (VR) has experienced a transformative evolution, establishing itself as a cornerstone of innovation across various industries. One of the trailblazers in this dynamic field is Simulanis, a VR development company based in India. With a focus on harnessing the power of immersive technology, Simulanis is not just creating virtual experiences; they are reshaping how businesses, education, and entertainment engage with audiences.
#VR Development India#Virtual Reality Solutions India#VR App Development India#Immersive VR Technology India#VR Game Development India#AR/VR Development Companies India#Virtual Reality Studios India#Custom VR Solutions India#Virtual Reality Content Creation India#VR Software Development India#VR Experience Design India#VR Simulation Development India#India VR Technology Providers#Virtual Reality for Businesses India#Enterprise VR Solutions India#VR Training Solutions India#Virtual Reality Development Companies India#Interactive VR Solutions India#VR for Education India#VR Hardware and Software Development India
1 note
·
View note
Text
youtube
Welcome to our video guide on how to install a hotel IPTV system, specifically tailored for a 100-room establishment in Djibouti. In this case study, we will cover various essential elements, including UHF Yagi Antenna & Satellite Dish Configuration, the inner workings of an IPTV system, comprehensive hotel staff training, and other noteworthy details.
Explore Our IPTV Video Series:
Explore More Features: https://youtu.be/0jVFQs34oYI
Frequently Asked Questions: https://youtu.be/YzBcyj2NASE
Don't hesitate to contact us if you have any questions:
Try our demo system (free download): https://drive.google.com/file/d/16dJrwu83xj9jACbgzEn3Ycs_6DFGoapo/view?usp=drive_link (How to use: https://drive.google.com/drive/folders/182ECD_JMcTM31w0ruiXmL-RPoI3KuO0-?usp=drive_link)
Ask for a Quotation: [email protected]
WhatsApp Chat with FMUSER: https://api.whatsapp.com/send/?phone=8618924246098&text=Hello-I-watched-your-djibouti-iptv-video-and-I-need-your-solution
Give us a Call: +86 139-2270-2227
Let's Chat Online: https://jivo.chat/lEHTbmpYDr
Solution Indexed: https://www.fmradiobroadcast.com/product/detail/hotel-iptv.html
Management System Explained: https://www.fmradiobroadcast.com/solution/detail/iptv
Subscribe to us: https://www.youtube.com/@fmuserbroadcast
Solution PDF Free Download (EN): https://www.fmradiobroadcast.com/UpLoad/OGbvDP-pmEipwiN4JDzE-g--/Files/202211/20221124142339332253.pdf

=-=-= Main Features =-=-=
Multi-Language Custom Support: We can customize the system to provide content and user interfaces in different languages.
Custom Interface: We provide a unique and customizable interface that can be tailored to meet your specific requirements.
Custom Guest Information: Personalized guest information as per your requirements after initializing.
Hotel Introduction: Introduce your hotel to guests in a comprehensive and engaging way. Scenic Spots Introduction: Customize the presentation of nearby attractions to guests.
Food Menu & Order: Order food and drinks directly from the hotel restaurant using their TV remote.
Hotel Service Integration: Seamless integration of hotel services into a single, easy-to-use section.
TV Sets Bundle: We offer the advantage of bundling suitable TV sets with compatible Android versions for seamless integration with our Hotel IPTV system.
TV Program Configuration: Acquire full control over TV program selection and configuration from UHF, satellite, and other options.
Video on Demand (VOD): Access a wide selection of movies, TV series, and on-demand content.
APP Store: Access popular apps for watching internet content online.
=-=-= Solution PDF Download =-=-=
▸ In Arabic: https://www.fmradiobroadcast.com/UpLoad/OGbvDP-pmEipwiN4JDzE-g--/Files/202303/20230321113004825322.pdf ▸ In Russian: https://www.fmradiobroadcast.com/UpLoad/OGbvDP-pmEipwiN4JDzE-g--/Files/202303/20230321114511126495.pdf ▸ In French: https://www.fmradiobroadcast.com/UpLoad/OGbvDP-pmEipwiN4JDzE-g--/Files/202303/20230321114614813277.pdf ▸ In Korean: https://www.fmradiobroadcast.com/UpLoad/OGbvDP-pmEipwiN4JDzE-g--/Files/202303/20230321114736895883.pdf ▸ In Portuguese: https://www.fmradiobroadcast.com/UpLoad/OGbvDP-pmEipwiN4JDzE-g--/Files/202303/20230321115013692283.pdf ▸ In Japanese: https://www.fmradiobroadcast.com/UpLoad/OGbvDP-pmEipwiN4JDzE-g--/Files/202303/20230321115150480945.pdf ▸ In Spanish: https://www.fmradiobroadcast.com/UpLoad/OGbvDP-pmEipwiN4JDzE-g--/Files/202303/20230321115237189413.pdf ▸ In Italian: https://www.fmradiobroadcast.com/UpLoad/OGbvDP-pmEipwiN4JDzE-g--/Files/202303/20230321115405265491.pdf
Thanks for watching!
Welcome to FMUSER Broadcast, a leading IPTV solution provider in China. We make IPTV more accessible for hospitality through product reviews, tutorials, guides, and customized solutions for various sectors (hotels, resorts, hospitals, government, education, apartments, etc.). Subscribe to explore more today!
#iptv solution#iptv setup#iptv system#iptv solutions#hotel iptv#hotel iptv solution#iptv solution providers#hospitality iptv#iptv hotel#tvheadend iptv setup#iptv server hardware#best iptv solution#iptv distribution#hospital iptv#hospitality iptv solutions#hotel iptv system#hotel tv systems iptv#iptv for hotels#iptv hospitality solutions#iptv distribution system#hotel iptv solutions#iptv for hotel#iptv headend#satellite dish#dstv#cable tv#fmuser#djibouti#Youtube
0 notes
Text
HSM Provider in India

What Are Hardware Security Modules?
Hardware Security Modules (HSMs) are specialized devices designed to safeguard sensitive data and manage cryptographic keys. They serve as dedicated security tools that ensure the security, confidentiality, and integrity of critical information in various digital systems.
The primary function of HSMs revolves around the secure generation, storage, and utilization of cryptographic keys used in encryption, decryption, digital signatures, and other cryptographic operations. These modules are hardware-based, providing a secure and tamper-resistant environment for key management and cryptographic processes.
HSMs are equipped with robust security mechanisms, including tamper-evident coatings, secure enclosures, and physical protections, to prevent unauthorized access and protect against attacks. They ensure that cryptographic keys remain confidential, preventing their exposure to potential threats.
These devices are widely utilized across industries, including finance, healthcare, government, and more, where data security and compliance with stringent regulations are paramount. HSMs play a pivotal role in securing digital assets, ensuring data confidentiality, and mitigating the risks associated with unauthorized access or data breaches.
The Significance Of HSMs In Modern Security
HSMs play a critical role in securing digital assets by offering a secure environment for key management and cryptographic operations, ensuring data integrity and confidentiality
Functionality Of HSMs
Encryption And Decryption Capabilities
HSMs employ sophisticated encryption techniques, ensuring data confidentiality by encoding sensitive information, rendering it inaccessible to unauthorized entities.
Secure Key Management
One of the primary functions of HSMs is secure generation, storage, and management of cryptographic keys, preventing unauthorized usage and potential breaches.
Applications Of HSMs Across Industries:
Financial Sector:HSMs play a vital role in the financial industry, securing transactions, protecting sensitive financial data, and ensuring the integrity of banking systems. They enable secure payment processing, cryptographic operations for secure communication, and compliance with financial regulations like PCI DSS.
Healthcare Industry:In healthcare, HSMs safeguard electronic health records (EHRs) and sensitive patient information. They assist in encryption, secure access control, and maintaining data confidentiality, ensuring compliance with healthcare regulations such as HIPAA.
Certificate Inspection:With a single click, scan all your TLS/SSL certificates for vulnerabilities and weak configurations to avoid a lapse in security. See analytics and reports about the health of your network at any given moment.
Certificate Remediation:When CertCentral finds an issue, you’ll get remediation suggestions with detailed answers to virtually any certificate problem. And if you ever need to revoke a certificate, it only takes one click.
Government and Public Sector:Government agencies use HSMs to protect classified information, secure government networks, and ensure the integrity of critical systems. These modules aid in securing sensitive data, ensuring confidentiality in communications, and compliance with stringent government regulations.
Telecommunications:HSMs play a role in securing communication networks, protecting sensitive data during transmissions, and ensuring secure connections between devices. They enable encryption of voice, data, and messaging services in telecommunications.
Manufacturing and Industrial Control Systems:In industrial settings, HSMs are used to secure critical infrastructure, IoT devices, and control systems. They ensure the integrity and confidentiality of data in manufacturing processes, energy grids, and automated systems.
Cloud Service Providers:HSMs are integral in cloud environments, providing secure key management and encryption services. They enable encryption of data at rest and in transit, ensuring customer data remains confidential and protected within cloud infrastructures.
Retail and eCommerce:HSMs secure payment transactions, encrypt sensitive customer data, and facilitate secure connections between customers and online platforms. They assist in compliance with payment card industry standards, safeguarding financial data during online transactions.
Benefits Of Implementing Our Hardware Security Modules:
Enhanced Data Security:HSMs provide a robust layer of protection for sensitive data by encrypting information at rest and in transit. This encryption ensures that even if data is accessed, it remains unreadable and secure.
Protection Against Data Breaches:By securely managing cryptographic keys and enforcing strict access controls, HSMs significantly reduce the risk of data breaches. Unauthorized access to keys or sensitive information is thwarted, mitigating the impact of potential breaches.
Certificate Inspection:With a single click, scan all your TLS/SSL certificates for vulnerabilities and weak configurations to avoid a lapse in security. See analytics and reports about the health of your network at any given moment.
Regulatory Compliance:HSMs aid organizations in complying with various industry-specific regulations and standards such as GDPR, HIPAA, PCI DSS, and more. Their secure key management capabilities align with compliance requirements, avoiding potential penalties and legal implications.
Securing Transactions and Communications:In financial and communication sectors, HSMs enable secure transactions and communications by providing encryption, digital signatures, and authentication. This ensures the confidentiality and integrity of sensitive information during transmission.
Data Integrity and Authentication:HSMs contribute to ensuring the integrity of data and authenticating users or devices. They verify the authenticity of digital signatures and certificates, preventing data tampering or unauthorized modifications.
JNR Management is the Best HSM Provider in India
#HMS#hardware security Module#HSM in India#HSM in Delhi#HSM in Mumbai#HSM in Bangalore#HSM Provider in India#HSM Provider in Delhi#HSM Solution in Delhi#HSM Solution in India
0 notes
Text
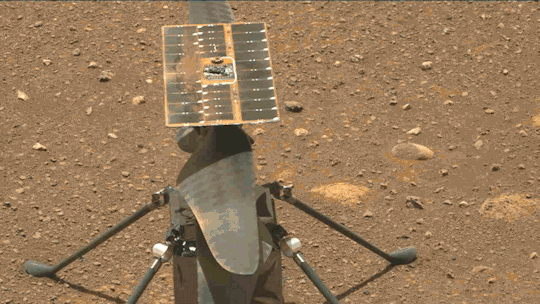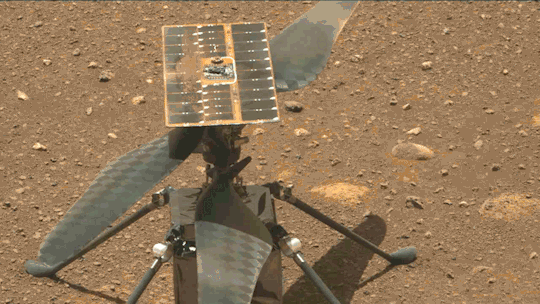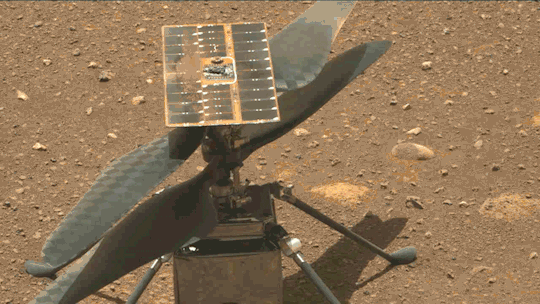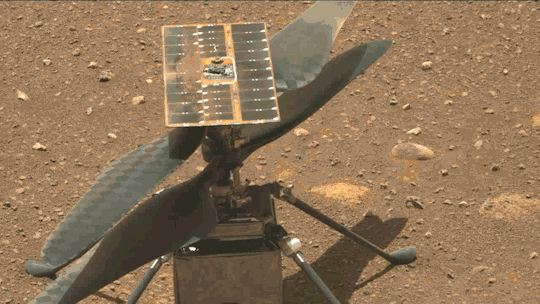
What We Learned from Flying a Helicopter on Mars

The Ingenuity Mars Helicopter made history – not only as the first aircraft to perform powered, controlled flight on another world – but also for exceeding expectations, pushing the limits, and setting the stage for future NASA aerial exploration of other worlds.
Built as a technology demonstration designed to perform up to five experimental test flights over 30 days, Ingenuity performed flight operations from the Martian surface for almost three years. The helicopter ended its mission on Jan. 25, 2024, after sustaining damage to its rotor blades during its 72nd flight.
So, what did we learn from this small but mighty helicopter?
We can fly rotorcraft in the thin atmosphere of other planets.
Ingenuity proved that powered, controlled flight is possible on other worlds when it took to the Martian skies for the first time on April 19, 2021.
Flying on planets like Mars is no easy feat: The Red Planet has a significantly lower gravity – one-third that of Earth’s – and an extremely thin atmosphere, with only 1% the pressure at the surface compared to our planet. This means there are relatively few air molecules with which Ingenuity’s two 4-foot-wide (1.2-meter-wide) rotor blades can interact to achieve flight.
Ingenuity performed several flights dedicated to understanding key aerodynamic effects and how they interact with the structure and control system of the helicopter, providing us with a treasure-trove of data on how aircraft fly in the Martian atmosphere.
Now, we can use this knowledge to directly improve performance and reduce risk on future planetary aerial vehicles.

Creative solutions and “ingenuity” kept the helicopter flying longer than expected.
Over an extended mission that lasted for almost 1,000 Martian days (more than 33 times longer than originally planned), Ingenuity was upgraded with the ability to autonomously choose landing sites in treacherous terrain, dealt with a dead sensor, dusted itself off after dust storms, operated from 48 different airfields, performed three emergency landings, and survived a frigid Martian winter.
Fun fact: To keep costs low, the helicopter contained many off-the-shelf-commercial parts from the smartphone industry - parts that had never been tested in deep space. Those parts also surpassed expectations, proving durable throughout Ingenuity’s extended mission, and can inform future budget-conscious hardware solutions.

There is value in adding an aerial dimension to interplanetary surface missions.
Ingenuity traveled to Mars on the belly of the Perseverance rover, which served as the communications relay for Ingenuity and, therefore, was its constant companion. The helicopter also proved itself a helpful scout to the rover.
After its initial five flights in 2021, Ingenuity transitioned to an “operations demonstration,” serving as Perseverance’s eyes in the sky as it scouted science targets, potential rover routes, and inaccessible features, while also capturing stereo images for digital elevation maps.
Airborne assets like Ingenuity unlock a new dimension of exploration on Mars that we did not yet have – providing more pixels per meter of resolution for imaging than an orbiter and exploring locations a rover cannot reach.

Tech demos can pay off big time.
Ingenuity was flown as a technology demonstration payload on the Mars 2020 mission, and was a high risk, high reward, low-cost endeavor that paid off big. The data collected by the helicopter will be analyzed for years to come and will benefit future Mars and other planetary missions.
Just as the Sojourner rover led to the MER-class (Spirit and Opportunity) rovers, and the MSL-class (Curiosity and Perseverance) rovers, the team believes Ingenuity’s success will lead to future fleets of aircraft at Mars.
In general, NASA’s Technology Demonstration Missions test and advance new technologies, and then transition those capabilities to NASA missions, industry, and other government agencies. Chosen technologies are thoroughly ground- and flight-tested in relevant operating environments — reducing risks to future flight missions, gaining operational heritage and continuing NASA’s long history as a technological leader.
youtube
You can fall in love with robots on another planet.
Following in the tracks of beloved Martian rovers, the Ingenuity Mars Helicopter built up a worldwide fanbase. The Ingenuity team and public awaited every single flight with anticipation, awe, humor, and hope.
Check out #ThanksIngenuity on social media to see what’s been said about the helicopter’s accomplishments.
youtube
Learn more about Ingenuity’s accomplishments here. And make sure to follow us on Tumblr for your regular dose of space!
5K notes
·
View notes
Note
Maybe I should wait for the PDF, but I’ve been thinking about password managers lately and might forget to check for that. My problem is that if there’s one thing I want to never ever put on the cloud to potentially get compromised, it’s my password information. But if there’s one thing I don’t want to lose access to, it’s also my password information. This seems to rule out both local options like KeePassXC and remote ones like Bitwarden.
I've started to become somewhat annoyed by the "there is no cloud, there is only someone else's computer" thing (this is a general thing, not specifically directed at you but you reminded me of it).
The risks of putting things on the cloud are that the internet or the provider will go down and you'll lose access to your data OR that the data will be compromised because the information is essentially public because it's on someone else's device.
Losing access because the provider crashes and burns or because there is a global internet outage is a distinct possibility, however with most password managers it is very very easy to download a copy of your data, which you can then store as an encrypted file on your desktop.
With companies like Bitwarden and Proton, which have open source encrypted cloud storage, your risk of compromise from being on someone else's computer is essentially zero. It IS important to make sure that you're finding a provider who is actually encrypting your shit and is not holding onto your password, which is why Bitwarden and Proton are the providers I keep recommending (privacyguides.org has recommendations here; bitwarden, protonpass, and keepassxc are all on the list, all of these are extremely safe options).
And that's where I have the problem with the "other people's computer" thing. I would have zero problems with storing a properly encrypted file in the comments of a facebook page. If a document had good encryption I would post it on livejournal and not worry about people getting into it. If you are working with good encryption, there is zero risk of compromise when keeping your shit on someone else's computer.
So I actually think the solution for either side of this conundrum is the same: If you're worried about losing access to your password manager because a service shuts down or the internet blows up, download a copy of your data to your desktop and store it in an encrypted folder on your computer. If you're worried about losing access to your password manager if your physical hardware is damaged in a disaster, export a copy of your data, save it as an encrypted file, and upload your encrypted file to gmail for all it matters - they will straight up not be able to get into it.
But that's also all kind of beside the point because a major feather in Bitwarden's cap is that you can self-host. It doesn't need to go on someone else's cloud, you can put it on your own server and never worry that someone else is going to tinker with your password manager.
Either way, you are sort of worrying beyond your means because if you're not using a password manager right now you are almost certainly at greater risk of credential stuffing attacks than anything else and need to put out that fire.
Anyway if you're at Harvey Mudd have you tried Dr. Grubbs across from where Rhino used to be? Everything on the menu is great but there is this jalapeño garlic sauce they've got to go with their mains that is so good that I want like two gallons of it.
326 notes
·
View notes
Text

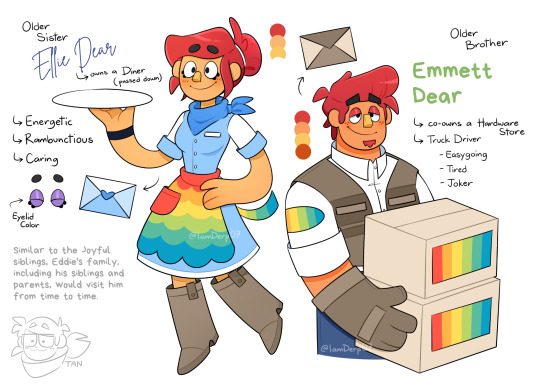


Meet Eddie Dear's Family! These are my new Welcome Home Original Characters (WH OCs) that I created based on Eddie Dear, one of my favorite WH characters! It took me a while to finish them, but I'm happy to have them out of my head!

Some Dear Siblings HeadCanon/Fanon Facts down below 🤣👇
1. Their parents are Elizabeth and Eddison Dear. Beth is from Texas, and Edd is from Louisiana.
2. Emmett is the oldest among the three Dear siblings, and Eddie is the youngest. Ellie is the middle child and the one and only daughter of Beth and Edd (All of them are equally loved, don't worry 😆🤣👍).
3. Emmett is 8 years older than Eddie, while Ellie is 4 years older than Eddie.
4. Eddison and Emmett work at the family-owned hardware shop, with Emmett often handling deliveries using his truck. Beth works at the family post office, where she used to work alongside Eddie. Meanwhile, Ellie owns a diner that was passed down from her grandparents.
5. The Dear siblings all have mitten like hands! Though Ellie has more feminine ones. Perfect for hugging their friends, neighbors, partners, and of course each other!
6. Eddie frequently stays connected with his family through phone calls and mail. ☎️📬
And I like to think that they've added a personal touch to their letters by using custom designed letters, each serving as a unique signature from every family member.
7. Emmett inherited his name from their great-grandfather on their mother's side, while Ellie and Eddie's names were derived from their parents' names - a shortened and endearing version:
Elizabeth - Ellie
Eddison - Eddie
8. Ellie and Eddie talk a lot about their day via phone call-A LOT. During late-night conversations, they end up talking for hours. Eddie often shares a lot with her about Frank, and she loves listening to her brother gush about him.
9. Emmett and Eddie also talk via phone, where Emmett tends to let Eddie take the lead in the conversation. There are times when Emmett ends up dozing off but still holds onto the phone.
10. During calls and when together, Emmett assists Eddie in managing his forgetfulness, much like their father. Emmett provides advice and solutions, especially when he notices Eddie in need of help or feeling troubled. Ellie also contributes in a similar supportive manner.
11. Eddie and Ellie are often mistaken for twins based on their looks and close sibling bond. Ellie actually gets flattered whenever someone mentions this because it makes her feel younger.
12. Among the three siblings, Ellie and Eddie have shared a close bond since childhood (probably because of the short age gap and since Emmett works a lot with their Pa). Despite Emmett being the more reserved and stoic one, all three of them have a good sibling relationship.
13. Emmett is usually fine with receiving hugs but occasionally gives one.
14. Emmett's instrument of choice is the guitar, while Ellie likes to play the harmonica. Eddison bought Ellie her own harmonica for her 12th birthday, and she has always carried it around with her since then.
15. Ellie and Emmett had their Mailman/Mailwoman phase.
16. Ellie is lesbian while Emmett just assumes he is cisgender. He wrong, he is actually bisexual ufhsjgkxxjgz
17. Ellie is like the second mom of the family.
18. At some points during the year, Eddie heads back to his hometown to visit his family.
19. Ellie has a terrible fear of heights.
20. One of the reasons why Eddie has a fear of bugs is probably because of Ellie.
21. Emmett would bring Eddie alongside him during his deliveries when Eddie is around and available.
22. When Ellie and Emmett first arrived in the Welcome Home Neighborhood, Wally somehow mistook them as Eddie's parents. This made Eddie laugh.
23. Emmett is actually good friends with Howdy and Barnaby. Howdy and Emmett would talk about business, while he and Barnaby tell each other jokes.
24. Ellie actually has good balance and poise. But gets all clumsy when she's flustered.
25. Ellie has a crush on one of Julie Joyful's siblings. Specifically, she has a crush on Franny Joyful.
#welcome home#welcomehome#welcome home puppet show#welcome home oc#welcome home eddie#welcome home eddie dear#eddie dear#eddiedear#dear family#puppet oc#muppet oc#I'm hyperfixated on this family right now
249 notes
·
View notes
Text
Oh the irony, it burns. Despite the red hot rhetoric of right wing politicians, some US states are neck deep in the renewable energy revolution. A case in point is the deep red state of Texas, which has been growing its solar manufacturing profile even as state lawmakers try to obstruct the energy transition.
More Solar Manufacturing For Texas
The fresh burst of activity in Texas’s solar manufacturing profile is significant because the state only had 14 or so manufacturers to its credit as recently as 2023, mostly clustered in the racking business and other associated hardware. Mission Solar held the title of Texas’s lone solar module maker until that year, when the leading Indian firm Waaree Energies announced that its new 5-gigawatt solar shop will be located in Brookshire, Texas.
“The creation of a U.S.-owned and operated company that can provide a turnkey solar technology solution is expected to solve a bottleneck for developers, create up to 1,800 direct jobs, satisfy local content requirements for U.S. solar projects, and competitively differentiate FREYR,” the Norwegian company explained.
Texas continues to top all other states for installed wind capacity, a position it has held since early 2000’s. Texas is also challenging California for installed solar capacity now.
13 notes
·
View notes
Text
(Reposting this, since I don't think anyone saw it yet. Also because I think people will want the share ID)

Share ID (PC): 9WA0BHW5ER8X
Here it is. 621's AC Fracture.
(This is the build that carried me through most of the game. I deliberately designed this build to be as much as a 'Protagonist AC' as possible.)
621 likes to be an all-rounder combatant, and has designed her AC accordingly.
Despite being outdated and outclassed by modern hardware, the CC-2000 Orbiter Core is a mainstay from 621's LOADER schematic, thanks to its light EN drain, attitude recovery, familiarity, and ease of use.
For the head, 621 initially stuck with the baseline Finder Eye. It was only until her victory against Nightfall Raven that she upgraded, replacing it with the HC-2000/BC Shade Eye to take advantage of its improved target acquisition.
For arms and legs, 621 chose parts from Arquebus Corporation's VP-4S production frametype, having taken a liking to their high EN, combat support stats, and light weight.
The DF-MG-02 Chang-Chen maintains its reputation as a dependable suppressive-fire solution for the modern battlefield. 621 favors it for its ability to perform in sustained combat with minimal wear and tear across a wide range of tactical spaces.
621 selected the SG-027 Zimmerman not just for its sheer power, but for its specialized shells that keeps the buckshot spread to a minimum and extends its effective range. The price is a longer reload cycle between shots, but 621 considers the trade-off worth it.
Out of all the missile platforms available to her, 621 favors plasma missiles the most, thanks to their wide area-effect saturation potential. This particular model (Vvc-706PM) can multi-lock up to six missiles at once, making them ideal for dealing with large groups and forcing mobile opponents into evasive action.
The IA-C01W2: Moonlight, scavenged from the ruins of Institute City, has truly become 621's favorite weapon. A light-wave blade capable of dealing a hybrid of pulse and energy damage by firing blade waves with every swing. 621 first used this weapon to cleave an LC in two with its charged attack. She was instantly in love.
Many mercenaries across settled space point to the FC-008 Talbot as a robust all-rounder FCS, and 621 is no exception, favoring its balance between close and mid-range target acquisition, and missile lock assistance.
Similarly, the VP-20C is a well-balanced circulating current generator that provides decent EN supply. Detractors often say this generator has no stand-out advantages, while advocates point out that it has no glaring weaknesses either.
For boosters, 621 uses the BC-0200 Gridwalker, favoring its high melee thrust potential for aggressive close-quarters tactics, and its balanced performance on the ground and in the air.
Finally, as a core expansion, 621 uses Assault Armor. The omni-directional blast potential is an excellent trump card against particularly dangerous opponents.
#armored core#rwby#rwby crossover#rwby fanfiction#armored core 6#armored core vi#augmented human c4 621#ayre armored core#weiss x ruby#whiterose#ruby rose#weiss schnee#blake belladonna#yang xiao long#Ravens Ever After
12 notes
·
View notes
Text
Setting Up an IRC Server for Secure Communication in a Future Insurrection
By WPS News Technical ReporterBaybay City | January 20, 2025 In an era marked by digital surveillance and control exerted by technology moguls, the need for independent communication platforms has never been more vital. As social movements and grassroots organizations rise to challenge existing power structures, the requirement for secure channels of communication is paramount. One viable…
#BayBay City#clean communication#communication platform#dedicated IP line#digital privacy#digital surveillance#domain registration#future insurrection#independent communication#internet freedom#internet service providers#IRC server#IT expertise#online security#secure communication#server hardware#tech independence#tech solutions#technology moguls#virtual private server
0 notes
Text
It starts with him
What was once a promise of technology to allow us to automate and analyze the environments in our physical spaces is now a heap of broken ideas and broken products. Technology products have been deployed en masse, our personal data collected and sold without our consent, and then abandoned as soon as companies strip mined all the profit they thought they could wring out. And why not? They already have our money.
The Philips Hue, poster child of the smart home, used to work entirely on your local network. After all, do you really need to connect to the Internet to control the lights in your own house? Well you do now!Philips has announced it will require cloud accounts for all users—including users who had already purchased the hardware thinking they wouldn’t need an account (and the inevitable security breaches that come with it) to use their lights.
Will you really trust any promises from a company that unilaterally forces a change like this on you? Does the user actually benefit from any of this?
Matter in its current version … doesn’t really help resolve the key issue of the smart home, namely that most companies view smart homes as a way to sell more individual devices and generate recurring revenue.
It keeps happening. Stuff you bought isn’t yours because the company you bought it from can take away features and force you to do things you don’t want or need to do—ultimately because they want to make more money off of you. It’s frustrating, it’s exhausting, and it’s discouraging.
And it has stopped IoT for the rest of us in its tracks. Industrial IoT is doing great—data collection is the point for the customer. But the consumer electronics business model does not mesh with the expected lifespan of home products, and so enshittification began as soon as those first warranties ran out.
How can we reset the expectations we have of connected devices, so that they are again worthy of our trust and money? Before we can bring the promise back, we must deweaponize the technology.
Guidelines for the hardware producer
What we can do as engineers and business owners is make sure the stuff we’re building can’t be wielded as a lever against our own customers, and to show consumers how things could be. These are things we want consumers to expect and demand of manufacturers.
Control
Think local
Decouple
Open interfaces
Be a good citizen
1) Control over firmware updates.
You scream, “What about security updates!” But a company taking away a feature you use or requiring personal data for no reason is arguably a security flaw.
We were once outraged when intangible software products went from something that remained unchanging on your computer, to a cloud service, with all the ephemerality that term promises. Now they’re coming for our tangible possessions.
No one should be able to do this with hardware that you own. Breaking functionality is entirely what security updates are supposed to prevent! A better checklist for firmware updates:
Allow users to control when and what updates they want to apply.
Be thorough and clear as to what the update does and provide the ability to downgrade if needed.
Separate security updates from feature additions or changes.
Never force an update unless you are sure you want to accept (financial) responsibility for whatever you inadvertently break.
Consider that you are sending software updates to other people’s hardware. Ask them for permission (which includes respecting “no”) before touching their stuff!
2) Do less on the Internet.
A large part of the security issues with IoT products stem from the Internet connectivity itself. Any server in the cloud has an attack surface, and now that means your physical devices do.
The solution here is “do less”. All functionality should be local-only unless it has a really good reason to use the Internet. Remotely controlling your lights while in your own house does not require the cloud and certainly does not require an account with your personal information attached to it. Limit the use of the cloud to only the functions that cannot work without it.
As a bonus, less networked functionality means fewer maintenance costs for you.
3) Decouple products and services.
It’s fine to need a cloud service. But making a product that requires a specific cloud service is a guarantee that it can be enshittified at any point later on, with no alternative for the user owner.
Design products to be able to interact with other servers. You have sold someone hardware and now they own it, not you. They have a right to keep using it even if you shut down or break your servers. Allow them the ability to point their devices to another service. If you want them to use your service, make it worthwhile enough for them to choose you.
Finally, if your product has a heavy reliance on the cloud to work, consider enabling your users to self-host their own cloud tooling if they so desire. A lot of people are perfectly capable of doing this on their own and can help others do the same.
4) Use open and standard protocols and interfaces.
Most networked devices have no reason to use proprietary protocols, interfaces, and data formats. There are open standards with communities and software available for almost anything you could want to do. Re-inventing the wheel just wastes resources and makes it harder for users to keep using their stuff after you’re long gone. We did this with Twine, creating an encrypted protocol that minimized chatter, because we needed to squeeze battery life out of WiFi back when there weren’t good options.
If you do have a need for a proprietary protocol (and there are valid reasons to do so):
Document it.
If possible, have a fallback option that uses an open standard.
Provide tooling and software to interact with your custom protocols, at the very least enough for open source developers to be able to work with it. This goes for physical interfaces as much as it does for cloud protocols.
If the interface requires a custom-made, expensive, and/or hard-to-find tool to use, then consider using something else that is commonly available and off the shelf instead.
5) Be a good citizen.
Breaking paid-for functionality on other people’s stuff is inherently unethical. Consider not doing this! Enshittification is not a technical problem, it is a behavioral one. Offer better products that are designed to resist enshittification, and resist it yourself in everything you do.
Nothing forced Philips to do what they are doing: a human made a decision to do it. They could have just as easily chosen not to. With Twine’s server lock-in, at least we chose to keep it running, for 12 years now. Consider that you can still make a decent living by being honest and ethical towards the people who are, by purchasing your products, paying for your lifestyle.
We didn’t get here by accident. Humans made choices that brought us to this point, and we can’t blame anyone for being turned off by it. But we can choose to do better. We can design better stuff. And we can choose not to mess things up after the fact.
We’re putting this into practice with Pickup. (We also think that part of an IoT reset is giving users the creative freedom of a general-purpose device.) If you’re looking for something better and our product can fill a need you have, consider backing us. We cannot claim to be perfect or have all of the answers, but we are absolutely going to try. The status quo sucks. Let’s do something about it.
Published October 15, 2023 By Jeremy Billheimer
137 notes
·
View notes
Text
A Compact Pi Compute Module Backpack 🍓🥧📸🎒
We used to stock a PiCam Module
that would plug into a Pi CM4 or CM5 - recently we went to restock it, but the vendor hasn't replied to our emails for many months. So, it could be a good time for us to design something that works similarly but with more capabilities. So we tasked Timon
with designing something for us - we just said, "Make the best thing ya can," and he delivered! Check this board out that plugs onto the compute module and provides many great accessories: USB connection for bootloading/USB gadget, USB 3.0 host type A for CM5, micro HDMI, micro SD card for data storage on 'Lite modules, camera connection, and mount, two DSI connectors, fan connect, Stemma QT / Qwiic connection, and RTC battery. There's one shutdown button for CM5 and two GPIO buttons plus one LED. Timon's gonna try to add an EYESPI connector for our next rendering so we can get some I2C/SPI/PWM outputs easily. What do you think? We wanted to keep it compact and not too pricey (aiming for <$30 cost. We'll see if we can get it there) but were able to craft fairly complex projects in a small space.
#raspberrypi#computeModule#electronics#maker#hardware#embedded#engineering#diy#tech#innovation#pcbdesign#usb3#microsd#hdmi#camera#stemmaqt#qwiic#gpio#fan#rtc#devboard#prototyping#opensource#electronicsdesign#robotics#automation#coding#hobbyelectronics#hackerspace#geekstuff
17 notes
·
View notes
Text
I'm late to the RvB OC week party, because of a project for my design course but. I'm just going to post everything late! So:
Day One: Introduction
I have a lot of OCs, 13 to be specific. They're the members of the Project Freelancer Canadian Division (aka CanDiv), a program advertised as an opportunity to allow uniquely talented neurodivergent people to contribute to the war effort against the Covenant. However, the true purpose of this program was to study the impact of AI on a variety of neurodivergences in a more in-depth manner, as well as the impacts of these conditions on performance as an agent and on their capabilities as a team. CanDiv agents were kept separate from the American Division, with the AmDiv agents even being fed rumours of "insanity, instability, and violence" to ensure they avoided CanDiv agents.
My main focus has always been on Agent Alberta and Agent Nova Scotia, who were the first recruits to the program.
Agent Alberta (she/they), aka Ali, is Alison Henley, a recon specialist with ADHD-CT, the impulsive nature of which means she rarely hesitates in battle and is quick to improvise solutions to problems on the fly. They favour a DMR or a sniper rifle, and their armour is equipped with a hologram projection module.


Agent Nova Scotia (she/her), aka Nova, is Kris Henley, a stealth specialist with PTSD, which provides the hypervigiliance that ensures she's constantly aware of her surroundings and planning for anything and everything to go wrong. She favours dual SMGs or a battle rifle, and her armour is equipped with a speed enhancement module.


Picrew source: x
Originally, these two were not even part of the military- however, they were civilian researchers at a U.N.S.C. research university on the planet of Camber. Cousins Alison and Kris Henley were studying biomedical engineering and xenobotany, respectively- Ali involved in research of neural interfaces, and Kris involved in biosynthetic materials development. They attracted the attention of Project Freelancer after the glassing of Camber, the story of which can be read at the following link:
After their recruitment, Alberta and Nova Scotia spent some time in training with some of the lower-ranked, late recruitment members of the AmDiv. However, the majority of their time was actually spent doing research for the project- developing the specialized neural interfaces and materials that would be used in the adaptation of MJOLNIR armour for non-augmented bodies. They ended up becoming very involved in the testing of these suits of armour, and ended up with a lot of expertise in using and modifying the systems. After the successful launch of this project, codenamed Ukonvasara, the rest of the CanDiv was recruited, and they were sequestered completely from the AmDiv.
After a great deal time spent serving in the Project as full-fledged agents, the CanDiv's AI implantations began. Unlike the AmDiv, however, the CanDiv implantations were done in short but gradually increasing stints, using the AI Eta and Iota. These fragments proved to be extremely hard on many of the agents, who were nevertheless forced to take them on for longer and longer stints. When the agents protested, they were shut down and subjected to less and less support on missions. Eventually, one of the Canadian agents discovered that Ali and Nova were slated to be implanted permanently, and the team agreed more serious action needed to be taken in protest. They staged an attack, wherein Ali and Nova pretended to be loyal to the project, and instead faked the deaths of the two agents by placing tracking hardware spoofing their armour's signal into a pelican, ejecting it from the ship, and causing it to self-destruct. Then in the chaos of the team fighting the rest of the project's security forces, and some members of AmDiv, Ali and Kris slipped themselves into the rank and file of some Sim Troopers who happened to be on board, and escaped.
#not video games#late nights with ali#ali watches rvb#rvbocweek2025#red vs blue#rvb#ali writes#side note: ali and nova got their start as my cousin and I's self-inserts. they've taken on a story of their own at this point but. yeah.#OC: alberta#OC: nova
13 notes
·
View notes
Text
Error
Summary: A short account of how Nines deviated.
A/N: My first Nines fic! Hopefully I did a good enough job at writing him in character :’]
Ruthless. Unwavering. Invulnerable. These were things RK900 was designed to be. He was designed to complete a job, and a lot of money was poured into making sure there was no room for error in his programming when it came to doing said job.
A lot of money poured into making sure he wasn’t like him. His predecessor. The ever present thorn in his side.
The weight of the pressure was unbearable, a prototype designed and produced to replace a faulty prototype. Not that he felt it, though. He didn’t feel.
Which was why he found himself having to run constant diagnostics as of late. His systems were going haywire. “Hot under the collar,” was never a phrase he understood, and definitely not something expected to experience himself. Yet here he was, hotter than hell under the collar. And everywhere else. To the point, in fact, that he had to, on top of his diagnostics (which were coming back normal somehow), constantly adjust his clothing. He was about a day away from making a trip to Cyberlife Tower for them to check for malfunctions in his hardware when a piece of information revealed itself to him, an unraveling pattern: these symptoms only occurring on days during which he encountered you.
So the solution was obvious, and refreshingly simple, like finally receiving a glass of water on a hot summer day… Or so he assumed. All he had to do was stop encountering you. At least, he had thought it would be that simple.
He was moderately prepared for seeing you against his will. After all, you did work for the same department he was currently positioned at. Every brief encounter was accompanied by the same symptoms, the heat, the warnings flashing in his visual field, the looping and breaking thought patterns. As long as he kept his distance and kept the encounters short, he was able to mitigate these symptoms. What he was not prepared for in the slightest was being assigned to a case alongside you.
Once again, his systems felt less than fully operational. At simply the proposition of this task, his processing unit was going a mile a minute. This was simply not logical. You were not a lieutenant, you were not even a deputy. You were still in the academy! There was no reason he should be on a case alone with you. If you were to be on a case, it should have been with Lieutenant Anderson. This was simply not logical! The line repeated in his mind like a bug, a virus. You were infecting his software.
Fowler’s instructions were simple: follow her orders, so as to allow her to learn, but do not allow her to get hurt. For a military grade android equipped with deadly weapons, this task should be simple. This was your first mission without Lieutenant Anderson. He would be there to oversee the process and make sure the mission doesn’t go awry to provide you experience without a Lieutenant looking over your shoulder, to make sure you were ready for the field. This thought, however, made him feel like he had butterflies— no, cicadas— clamoring around in his plastic and metal chassis. He ran a hand through his hair, pausing midway through in his confusion. He smoothed his hair back into place, unable to place what these physical reactions were, or how they were happening.
💙
The mission itself was unbearable. The two of you were tracking down a missing android, of course. The same monotonous task the DPD had been plaguing its workers with for nearly 6 months at this point. The case didn’t seem particularly dangerous; the murder it had committed only involved blunt-force trauma, so potentially accidental. Nines considered it immensely helpful that the case was so lack luster, at least it gave him more mental space to deal with the aggravations that came along with being around you. The uncomfortable reality was that he still wasn’t sure how this was happening, and yet… He no longer considered going to Cyberlife about it an option, instead opting for a more secretive route. Although he’d never admit it to himself, he didn’t entirely want these feelings to go away. The symptoms were annoying, sure. Overheating was… Less than optimal. But there was something else that accompanied these feelings. Like an instinctive feeling, which was exhilarating for him. Something that existed outside of the zeroes and ones, outside of mechanics and the software. It was small, and it was technically a bug, a glitch, but it was real. He didn’t want Cyberlife to take that away.
As RK900, or “Nines” as you insist upon calling him, accompanied you around this seemingly abandoned house, you busied yourself with asking him trivial, meaningless questions. And he was desperate for you to keep asking them.
“Why did they give Connor a name and not you?”
“RK800 deviated because they allowed him to tread too far into human territory. I suppose they did not want to take the risk with me.”
His non-existent stomach did a flip as he watched your eyebrows furrow in response.
“But you’re sentient. You can think. You’re self aware. That’s mean for them to give Connor a name and not you.”
“It has never made a difference to me, I assure you.”
“I’ll call you Nines for now. But I intend to give you a real name, okay?”
RK900 felt hot again, even more so than before. His face felt hot. He wasn’t sure what to say.
“If that is what you want. I will allow you to call me whatever you choose.” He wasn’t sure why this was the case, but he knew it was. He would do anything she asked of him. Anything. And he had not a single clue as to why.
As the two of you made your way up the stairs, Nines kept a hand on his holster, ready for anything that could be in store. Just as he suspected, there was a loud clamor from one of the rooms as the two of you reached the top of the stairs. Just as he takes his gun out of its holster, you speak.
“Stay here, Nines! I mean it!”
He wasn’t sure what your aim here was. Strategically, this decision was the least sound. If he were to get hurt, Cyberlife could either repair him or send a replacement. If you got hurt…
Fowler’s instructions echoed in his mind. Follow her orders, don’t allow her to get hurt. In this instance, the set of instructions was contradictory. He also had a secondary set of instructions: yours, telling him to stay put. His brain was rapidly running reconstructions, none of them ending well. As took a step forward, something in his coding stopped him. He heard another loud clamor from the room you had disappeared into, sending his systems into a frenzy. He fought against his coding, ignoring every single warning and reminder his mechanical brain was firing at him. Suddenly, he was able to step forward, running into the room you were in, gun drawn and aimed.
He didn’t hesitate, he didn’t have time to. He saw the deviant, and fired with lethal precision. As the deviant fell to the floor, he turned to you. You lay on the floor, blood oozing from a gash on your forehead. Seeing a broken wooden beam on the floor next to you, he quickly reconstructs the scene. The deviant was trying to escape as you entered the room. He must have been hiding when the two of you were coming up the stairs, and whatever was containing him broke. As you entered the room, he tried to throw the beam at you as a diversion. RK900– Nines— had arrived just in time to catch him just in time, before he was able to make it out the window.
Nines kneels down next to you, feeling yet another new emotion: panic. As he examines your wound, he exhales in exasperation. “Why would you do that?! Why would you not send me in first?! You are not replaceable, I am!” You look at him, slightly dizzy as your head pounds. Your voice comes our groggily. “No, you’re not. They could send a new model, but it wouldn’t be you.” Anger flares in Nines as he looks down at you. “This was ridiculous. If all he had was a piece of wood, it would have done nothing to me. Nothing!” You smile, groggily. “We didn’t know what he would have. Plus, you would have killed him. I was trying to get him out of here alive. Now can you help me up?”
Nines sighs again as he helps you up. “This was idiotic, detective.” You laugh, feeling yourself being practically dragged off the floor. “I’m going to make it. Looks like he’s not, though.” Nines says nothing, walking close behind you to ensure your stability as you exit the scene. He continues to say nothing. In the car, at the station, not a word.
As you gather your things, preparing to go home, you wander over to Nines’ desk, standing next to him as you smile down at him. “You know, if I didn’t know any better, I’d say you were scared back there,” you tease, smirking at him. Nines doesn’t look at you, keeping his eyes stubbornly locked on the screen in front of him. “You’d be wrong, detective. I do not feel anything, as I am not programmed to.” As the words leave his lips, you both know that it’s a lie. But you don’t say anything. And neither does he.
As you leave the bull pen, RK900 clenches his fists. A military grade android, a weapon, programmed to never, EVER feel anything remotely similar to emotion, afraid. Going against his coding. There was only one thing that could mean: he had become what he was built to destroy. He had become like him.
158 notes
·
View notes