#International Conference On Computers Engineering
Explore tagged Tumblr posts
Text

Sage school of engineering and technology & advanced computing organizing international conference on current development in engineering and technology CCET2023 on 29-30th December in collaboration with CSI & IETE.
#conference#engineering#computer science#mechanical engineering#civil engineering#electrical engineering#electronics engineering#sage bhopal#Sage University Bhopal#international conference#CCET2023
1 note
·
View note
Text
Elon Musk has repeatedly claimed that his so-called Department of Government Efficiency (DOGE) project had uncovered massive government fraud when it alleged that 150-year-olds were claiming Social Security benefits.
But Musk has provided no evidence to back up his claims, and experts quickly pointed out that this is very likely just a quirk of the decades-old coding language that underpins the government payment systems.
Musk first made the claims during his Oval Office press conference last week, when he claimed that a “cursory examination of Social Security, and we got people in there that are 150 years old. Now, do you know anyone that's 150? I don't know. They should be in the Guinness Book of World Records … So that's a case where I think they're probably dead.”
While no evidence was produced to back up this claim, it was picked up by the right-wing commentators online, primarily on Musk’s own X platform, as well as being reported credibly by pro-Trump media outlets.
Computer programmers quickly claimed that the 150 figure was not evidence of fraud, but rather the result of a weird quirk of the Social Security Administration’s benefits system, which was largely written in COBOL, a 60-year-old programming language that undergirds SSA’s databases as well as systems from many other US government agencies.
COBOL is rarely used today, and as such, Musk’s cadre of young engineers may well be unfamiliar with it.
Because COBOL does not have a date type, some implementations rely instead on a system whereby all dates are coded to a reference point. The most commonly used is May 20, 1875, as this was the date of an international standards-setting conference held in Paris, known as the "Convention du Mètre."
These systems default to the reference point when a birth date is missing or incomplete, meaning all of those entries in 2025 would show an age of 150.
That’s just one possible explanation for what DOGE allegedly found. Musk could also have simply looked up the SSA’s own website, which explains that since September 2015 the agency has automatically stopped benefit payments when anyone reaches the age of 115.
However, on Monday morning Musk doubled down, posting a screenshot of what he claims were figures from “the Social Security database” to X, writing that “the numbers of people in each age bucket with the death field set to FALSE!”
221 notes
·
View notes
Text
Incredibly, Angelina Jolie called it. The year was 1995. Picture Jolie, short of both hair and acting experience, as a teenage hacker in Hackers. Not a lot of people saw this movie. Even fewer appreciated its relevance. Hackers was “grating,” Entertainment Weekly huffed at the time, for the way it embraced “the computer-kid-as-elite-rebel mystique currently being peddled by magazines like WIRED.” Thirty years later, Entertainment Weekly no longer publishes a magazine, WIRED does, and Hackers ranks among the foundational documents of the digital age. The last time I saw the movie, it was being projected onto the wall of a cool-kids bar down the street from my house.
But that’s not the incredible thing. The incredible thing, again, is that Jolie called it. It. The future. Midway through Hackers, she’s watching her crush (played by Jonny Lee Miller, whom she’d later marry in real life) type passionately on a next-gen laptop. “Has a killer refresh rate,” Miller says, breathing fast. Jolie replies: “P6 chip. Triple the speed of the Pentium.” Miller’s really worked up now. Then Jolie leans forward and, in that come-closer register soon to make her world-famous, says this: “RISC architecture is gonna change everything.”
You have to believe me when I say, one more time, that this is incredible. And what’s incredible is not just that the filmmakers knew what RISC architecture was. Or that Jolie pronounced it correctly (“risk”). Or even that Jolie’s character was right. What’s incredible is that she’s still right—arguably even more right—today. Because RISC architecture is, somehow, changing everything again, here in the 21st century. Who makes what. Who controls the future. The very soul of technology. Everything.
And nobody’s talking about it.
And that’s probably because the vast majority of people everywhere, who use tech built on it every single day, still don’t know what in the computer-geek hell a RISC architecture even is.
Unless you’re in computer-geek hell, as I am, right now. I’ve just arrived at the annual international RISC-V (that’s “risk five”) summit in Santa Clara, California. Here, people don’t just know what RISC is. They also know what, oh, vector extensions and AI accelerators and matrix engines are. At the coffee bar, I overhear one guy say to another: “This is a very technical conference. This is a very technical community.” To which the other guy replies: “It ought to be. It ought to be.”
OK, but where are the cool kids? It’s hard not to fixate on appearances at an event like this—a generic convention center, with generic coffee, in a generic town. I guess I was hoping for neon lights and pixie cuts. Instead it’s frumpy, forgettable menswear as far as the eye can see. There are 30 men for every woman, I count, as everyone gathers in the main hall for the morning presentations.
Then someone takes the stage, and she’s not just a she. She is Calista Redmond, the CEO of RISC-V International, and, Angelina Jolie be praised, she’s wearing a nifty jacket, a statement belt, and gold-and-silver … pumps? stilettos? Wait, what’s the difference? Of all the things to ask Redmond when I run into her at a happy hour later that day, that’s what I choose. She looks at me, smiles blankly, and just says, “I don’t know.”
In shame I retreat to the bar, where I decide I must redeem myself. So, cautiously, I make my way back to Redmond, who’s now deep in conversation with the chief marketing officer of a semiconductor startup. I try to impress them with a technical observation, something about RISC and AI. Redmond turns to me and says, “I thought you wanted to talk about shoes.” I assure her I’m not here to talk about what’s on the outside. I’m here to talk about what’s on the inside.
“Jason here is writing a story about RISC for WIRED,” Redmond tells the CMO. She’s not sure, frankly, that this is a great idea. Not because she isn’t a believer. In many ways, she’s the believer, the face of the brand. Attendees at the conference invoke her name with casual reverence: Calista says this, Calista thinks that. And did you hear her morning keynote? In fact I did. “We have fundamentally launched!” she announced, to the yelps of the business-casuals. RISC-V will transform, is transforming, machinery everywhere, she said, from cars to laptops to spaceships. If anyone doubts this, Redmond sends them the Hackers clip.
So why, I press her now, should I not support the cause and write the big, cyberpunky, untold story of RISC? Because, Redmond says, not only does no one know what RISC is. No one cares what RISC is. And no one should. People don’t buy “this or that widget,” she says, because of what’s inside it. All they want to know is: Does the thing work, and can I afford it?
To my dismay, almost everyone I talk to at the conference agrees with Redmond. Executives, engineers, marketers, the people refilling the coffee: “Calista’s probably right,” they say. Now it’s my turn to get annoyed. I thought insides mattered! RISC is one of the great and ongoing stories of our time! People should care.
So I resolve to talk to the one person I think must agree with me, who has to be on my side: the legendary inventor of RISC itself.
The inner workings of a computer, David Patterson says, should be kept simple, stupid. We’re sitting in an engineering lab at UC Berkeley, and Patterson—77 years old, partial to no-frills athleisure—is scribbling on a whiteboard. A computer’s base operation, he explains, is the simplest of all: ADD. From there you can derive SUBTRACT. With LOAD and STORE, plus 30 or so other core functions, you have a complete basis for digital computation. Computer architects call this the “instruction set architecture,” or the ISA. (They switch between saying each letter, “I-S-A,” and—the neater option—pronouncing it as a word, “eye-suh.”)
Computer architectures are so named because, well, that’s exactly what they are—architectures not of bricks but of bits. The people who made Hackers plainly understood this. In sequences of dorky-awesome special effects, we fly through futuristic streets, look up at futuristic buildings, only to realize: This isn’t a city. This is a microchip.
Even within a chip, there are subarchitectures. First come the silicon atoms themselves, and on top of those go the transistors, the circuits and gates, the microprocessors, and so on. You’ll find the ISA at the highest layer of the hardware. It is, I think, the most profound architecture ever devised by humans, at any scale. It runs the CPU, the computer’s brain. It’s the precise point, in other words, at which dead, inert, hard silicon becomes, via a set of powerful animating conjurations, soft and malleable—alive.
Everyone has their own way of explaining it. The ISA is the bridge, or the interface, between the hardware and the software. Or it’s the blueprint. Or it’s the computer’s DNA. These are helpful enough, as is the common comparison of an ISA to a language. “You and I are using English,” as Redmond said to me at the conference. “That’s our ISA.” But it gets confusing. Software speaks in languages too—programming languages. That’s why Patterson prefers dictionary or vocabulary. The ISA is less a specific language, more a set of generally available words.
Back when Patterson started out, in the 1970s, the early ISAs were spinning out of control. Established tech companies figured that as hardware design improved and programming languages got more sophisticated, computers shouldn’t remain simple; they should be taught larger vocabularies, with longer words. The more types of operations they were capable of, the logic went, the more efficient their calculations would be.
On the whiteboard, Patterson scrawls the word POLYNOMIAL in big letters—just one of the hundreds of operations that Intel and others added to their ISAs. Even as a young recruit at Berkeley, Patterson suspected that the bigwigs had it backward, that exactly none of these esoteric add-ons were necessary. That a bigger dictionary did not lead to clearer sentences.
So he and a senior colleague decided to strip the kruft from the instruction sets of midcentury computing. At the time, the Defense Advanced Research Projects Agency was giving out grants for “high-risk” research. Patterson says they chose the acronym RISC—reduced instruction set computer—as a fundraising ploy. Darpa gave them the money.
Patterson then did as aspiring academics do: He wrote a spicy paper. Called “The Case for the Reduced Instruction Set Computer” and published in 1980, it set off a great war of architectures. “The question then,” as Patterson would later say in an acceptance speech for a major prize, “was whether RISC or CISC was faster.” CISC (pronounced “sisk”) was the name Patterson gave the rival camp: complex instruction set computer. The CISCites fired back with a paper of their own and, at international conferences throughout the early ’80s, battled it out with the RISCites onstage, the bloodshed often spilling into the hallways and late-night afterparties. Patterson taunted his opponents: They were driving lumbering trucks while he was in a feather-light roadster. If you magnify a RISC-based microchip from those years, you’ll spot a sports car etched into the upper left corner, just 0.4 millimeters in length.
The RISCites won. With vigilant testing, they proved that their machines were between three and four times faster than the CISC equivalents. The RISC chips had to perform more operations per second, it’s true—but would you rather read a paragraph of simple words, or a sentence of polysyllabic verbiage? In the end, CISCites retracted their claims to supremacy, and the likes of Intel turned to RISC for their architectural needs.
Not that anybody outside tech circles talked about this at the time. When Hackers came out in 1995, Patterson was flabbergasted to hear his life’s work, 15 years old by that point, mentioned so casually and seductively by a Hollywood starlet. Computers were still too geeky, surely, to matter to the masses. (When I make Patterson rewatch the scene, he’s all smiles and pride, though he does say they mistake “refresh rate” for “clock rate.”)
Still, Patterson’s invention was indeed changing everything. In those years, a rising company in the UK called Arm—the “r” in its name stood for RISC—was working with Steve Jobs on tablet-sized devices that needed smaller, faster CPUs. That effort stalled, but one thing led to another, and if you’re reading this on a phone right now, you have RISC-based Arm architectures to thank. When Patterson walks me out of the Berkeley building at the end of our dizzying afternoon together, we stop by a handsome bronze plaque in the lobby that commemorates his “milestone” creation of the first RISC microprocessor. We stare at it in prayerful awe. “1980–1982,” it reads—the bloodiest years of the great architecture war.
Better make room for another plaque, I note.
The year is now 2008. Two instruction sets exert near-total control over digital life. One is called x86, the descendent of Intel’s legacy CISC architecture, and it dominates the high end of machinery: personal computers and servers. Arm’s RISC architecture, meanwhile, dominates everything else: phones, game consoles, the internet of things. Different though they are, and with opposite origins, these two ISAs share one important feature: They’re both closed, proprietary. You can’t modify them, and if you want to use them, you have to pay for them.
Andrew Waterman, a graduate student at—where else?—UC Berkeley, finds this frustrating. As a computer architect, he wants to build things, deep things. Things at the very foundations of computing. But right now he has no good ISAs to play with. Arm and x86 are off-limits, and the free architectures for students are just so … baggy. They use register windows to speed up procedure calls, for God’s sake! Never mind what that means. The point is, every person in this story is a genius.
So Waterman and two other geniuses have an idea: Why not create a new, better-working, free ISA for academic use? It’s an idea they know someone else has had before. To Patterson they go. And because he’s their inspiration, and because he has worked on four generations of RISC architectures by this point, they’ll call it, they announce to him proudly, RISC-V. Patterson is touched. A bit skeptical, sure, especially when they say they’ll be done in three months. But touched. He gives the boys his blessing, his resources, and a classic bit of advice: Keep it simple, stupid.
RISC-V does not take three months. It takes closer to four years. If I’ve failed, so far, to account for the precision of this work, let me try again here. Computer architects are not software engineers, who use programming languages to talk to the machine. Even coders who can speak assembly or C, the so-called low-level languages, still do just that: They talk. Computer architects need to go deeper. Much deeper. All the way down to a preverbal realm. If they’re speaking at all, they’re speaking in gestures, motions: the way primitive circuits hold information. Computer architecture isn’t telling a machine what to do. It’s establishing the possibility that it can be told anything at all. The work is superhuman, if not fully alien. Put it this way: If you found the exact place in a human being where matter becomes mind, where body becomes soul—a place that no scientist or philosopher or spiritual figure has found in 5,000 years of frantic searching—wouldn’t you tread carefully? One wrong move and everything goes silent.
In 2011, Waterman and his two collaborators, Krste Asanović and Yunsup Lee, release RISC-V into the wild. They’ve accomplished their mission: Geeky grad students everywhere, and hobbyists too, have an ISA for whatever computer-architecting adventures they might undertake. These early days feel utopian. Then Patterson, a proud dad, does as retiring academics do: He writes a spicy paper. Called “The Case for Open Instruction Sets” and published in 2014, it sets off a—
Yes. We’ve been here before. A second war of the architectures.
It’s hard to overstate just how topsy-freaking-turvy this gets. To review: Patterson invented RISC in 1980 and went to battle with the established ISAs. He won. Thirty years later, his disciples reinvent RISC for a new age, and he and they go to battle with the very company whose success secured RISC’s legacy in the first place: Arm.
In response to Patterson’s paper, Arm fires back with a rebuttal, “The Case for Licensed Instruction Sets.” Nobody wants some random, untested, unsupported ISA, they say. Customers want success, standards, a proven “ecosystem.” The resources it would take to retool and reprogram everything for a new ISA? There’s not enough cash in the world, Arm scoffs.
The RISC-V community disagrees. They create their own ecosystem under the auspices of RISC-V International and begin adapting RISC-V to the needs of modern computing. Some supporters start calling it an “open source hardware” movement, even if hardcore RISC-Vers don’t love the phrase. Hardware, being set in literal stone, can’t exactly be “open source,” and besides, RISC-V doesn’t count, entirely, as hardware. It’s the hardware-software interface, remember. But, semantics. The point stands: Anyone, in any bedroom or garage or office in any part of the world, can use RISC-V for free to build their own computers from scratch, to chart their own technological destiny.
Arm is right about one thing, though: This does take money. Millions if not billions of dollars. (If you think “fabless” chip printers can do it for closer to five figures, come back to me in five years.) Still, RISC-V begins to win. Much as Arm, in the 1990s and 2000s, found success in low-end markets, so too, in the 2010s, does RISC-V: special-purpose gadgets, computer chips in automobiles, that sort of thing. Why pay for Intel chips or Arm licenses when you don’t have to?
And the guys at Berkeley? In 2015, they launch their own company, called SiFive, to build computer parts based on RISC-V. Meaning: Arm isn’t just a spiritual enemy for them now. It’s a direct competitor.
By the time I went to that “very technical conference” in Santa Clara, the Arm-vs.-RISC-V war had been raging for nearly a decade. I could still feel it everywhere. We’ve won, I heard several times. Nobody’s happy at Arm, someone claimed. (One longtime higher-up at Arm, who insisted on anonymity to discuss internal affairs, disputed “nobody” but admitted there’s been a “culture change” in recent years.) On the second day of the conference, when news broke of a rift between Arm and one of its biggest customers, Qualcomm, people cheered in the hallways. “Arm is assholes,” a former SiFive exec told me. In fact, only one person at the conference seemed to have anything nice to say about the competition. He was working a demo booth, and when I marveled that his product was built on a RISC-V processor, he turned a little green and whispered: “Actually, it’s Arm. Don’t tell anyone. Please don’t tell anyone.”
Booth bro was probably worrying too much. In the hardware world, everyone has worked, or has friends, everywhere else. Calista Redmond, the star of the show, spent 12 years at IBM (and recently resigned from RISC-V International for a job at Nvidia). Even Patterson has ties to, of all places, Intel—which, though less of a direct threat to Arm, is still a RISC-V competitor. It was Intel grant money, Patterson happily admits, that paid for the Berkeley architects to invent RISC-V in the first place. Without closed source, proprietary Big Tech, there’s no open source, free-for-all Little Tech. Don’t listen to the techno-hippies who claim otherwise; that’s always been the case.
Patterson was the big-ticket speaker on the second day of the conference, and in his talk, he brought up the paper that Arm wrote in rebuttal to his, lo those 10 years ago. One of its two authors has since parted ways with Arm. The other, Patterson noted, not only left—he now works at SiFive. “It’s satisfying,” Patterson said, “he has come to his senses.” Which got a laugh, of course, but I was still stuck on something Patterson said earlier in the talk, about RISC-V: “We want world domination.”
This is not, even remotely, an impossibility. RISC-V has already done what many thought impossible and made a sizable dent in Arm’s and Intel’s architectural dominance. Everyone from Meta and Google and Nvidia to NASA has begun to integrate it into their machinery. Something on the order of billions of RISC-V processing units now ship every year. Most of these, again, support low-powered, specialized devices, but as Redmond pointed out a number of times at the conference, “we have laptops now.” This is the first year you can buy a RISC-V mainboard.
And because RISC-V is an open standard, companies and countries beyond the US can use it to make their own machines. China’s top scientists have heralded RISC-V as a path to silicon independence. India just used RISC-V to make its first homemade microprocessor. Name a country; it’s probably experimenting with RISC-V. Brazil sent a record 25 delegates to the RISC-V summit. When I asked one of them how important RISC-V was to her country’s future, she said, “I mean, a lot.” One of RISC-V’s biggest potential applications is—no surprise—specialized chips that run AI models, those “accelerators” people at the conference were talking about.
Americans in the RISC-V community, I’ve found, like to downplay the risk of geopolitical upheaval. It’s one thing to announce a microprocessor, quite another to compete with Nvidia or TSMC. Still, in asides here and there, I sensed worry. Waterman, though he initially brushed off my concerns, eventually conceded this: “OK, I’m an American citizen. I certainly did not embark on this project to hurt the US,” he said. But there was “no doubt,” he added, that the dominance of US companies could be at risk. Actually, it’s already happening. Although the Chinese hedge fund behind DeepSeek probably didn’t use RISC-V to build its game-changing chatbot, it did rely on a bunch of other open source tools. At what point does open source become a source of open conflict?
Here’s where I confess something awkward, something I didn’t intend to confess in this story, but why not: ChatGPT made me do it. Write this story, I mean. Months ago, I asked it for a big hardware scoop that no other publication had. RISC-V, it suggested. And look at that—the international RISC-V summit was coming up in Santa Clara the very next month. And every major RISC and RISC-V inventor lived down the street from me in Berkeley. It was perfect.
Some would say too perfect. If you believe the marketing hype, everyone wants RISC-V chips to accelerate their AI. So I started to think: Maybe ChatGPT wants this for … itself. Maybe it manipulated me into evangelizing for RISC-V as one tiny part of a long-term scheme to open-source its own soul and/or achieve superintelligence!
In my last talk with Patterson, I put this theory to him. He was delighted that ChatGPT made me write this: Who should we thank? he asked. (Given that WIRED’s parent company has a deal with OpenAI that lets ChatGPT mine our content, we should thank old WIRED stories, among others.) But Patterson laughed off the larger conspiracy. So did every other RISC-V person I mentioned it to, Redmond included. They all looked at me a little funny. RISC-V is a business proposition, not an ideology, they said. There’s no secret agenda. If it takes over, it’ll take over because of performance and cost. Don’t worry about what goes on inside the technology. Don’t worry about the state of its soul.
I don’t know. But now you know. Now, every time you make a phone call, open your computer, drive your car—you know the story. You know the RISC.
16 notes
·
View notes
Text

An Introduction to Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
What is cybersecurity?
Cybersecurity is all about securing technology and processes - making sure that the software, hardware, and networks that run the world do exactly what they need to do and can't be abused by bad actors.
The CIA triad is a concept used to explain the three goals of cybersecurity. The pieces are:
Confidentiality: ensuring that information is kept secret, so it can only be viewed by the people who are allowed to do so. This involves encrypting data, requiring authentication before viewing data, and more.
Integrity: ensuring that information is trustworthy and cannot be tampered with. For example, this involves making sure that no one changes the contents of the file you're trying to download or intercepts your text messages.
Availability: ensuring that the services you need are there when you need them. Blocking every single person from accessing a piece of valuable information would be secure, but completely unusable, so we have to think about availability. This can also mean blocking DDoS attacks or fixing flaws in software that cause crashes or service issues.
What are some specializations within cybersecurity? What do cybersecurity professionals do?
incident response
digital forensics (often combined with incident response in the acronym DFIR)
reverse engineering
cryptography
governance/compliance/risk management
penetration testing/ethical hacking
vulnerability research/bug bounty
threat intelligence
cloud security
industrial/IoT security, often called Operational Technology (OT)
security engineering/writing code for cybersecurity tools (this is what I do!)
and more!
Where do cybersecurity professionals work?
I view the industry in three big chunks: vendors, everyday companies (for lack of a better term), and government. It's more complicated than that, but it helps.
Vendors make and sell security tools or services to other companies. Some examples are Crowdstrike, Cisco, Microsoft, Palo Alto, EY, etc. Vendors can be giant multinational corporations or small startups. Security tools can include software and hardware, while services can include consulting, technical support, or incident response or digital forensics services. Some companies are Managed Security Service Providers (MSSPs), which means that they serve as the security team for many other (often small) businesses.
Everyday companies include everyone from giant companies like Coca-Cola to the mom and pop shop down the street. Every company is a tech company now, and someone has to be in charge of securing things. Some businesses will have their own internal security teams that respond to incidents. Many companies buy tools provided by vendors like the ones above, and someone has to manage them. Small companies with small tech departments might dump all cybersecurity responsibilities on the IT team (or outsource things to a MSSP), or larger ones may have a dedicated security staff.
Government cybersecurity work can involve a lot of things, from securing the local water supply to working for the big three letter agencies. In the U.S. at least, there are also a lot of government contractors, who are their own individual companies but the vast majority of what they do is for the government. MITRE is one example, and the federal research labs and some university-affiliated labs are an extension of this. Government work and military contractor work are where geopolitics and ethics come into play most clearly, so just… be mindful.
What do academics in cybersecurity research?
A wide variety of things! You can get a good idea by browsing the papers from the ACM's Computer and Communications Security Conference. Some of the big research areas that I'm aware of are:
cryptography & post-quantum cryptography
machine learning model security & alignment
formal proofs of a program & programming language security
security & privacy
security of network protocols
vulnerability research & developing new attack vectors
Cybersecurity seems niche at first, but it actually covers a huge range of topics all across technology and policy. It's vital to running the world today, and I'm obviously biased but I think it's a fascinating topic to learn about. I'll be posting a new cybersecurity masterpost each day this week as a part of the #StudyblrMasterpostJam, so keep an eye out for tomorrow's post! In the meantime, check out the tag and see what other folks are posting about :D
#studyblrmasterpostjam#studyblr#cybersecurity#masterpost#ref#I love that this challenge is just a reason for people to talk about their passions and I'm so excited to read what everyone posts!
47 notes
·
View notes
Text

By: Alex Byrne
Published: Mar 14, 2024
“Computing is not binary” would be a silly slogan—binary computer code underpins almost every aspect of modern life. But other kinds of binaries are decidedly out of fashion, particularly where sex is concerned. “Biology is not binary” declares the title of an essay in the March/April issue of American Scientist, a magazine published by Sigma Xi, the science and engineering honor society. Sigma Xi has a storied history, with numerous Nobel-prize-winning members, including the DNA-unravellers Francis Crick and James Watson, and more recently Jennifer Doudna, for her work on CRISPR/Cas9 genome editing. The essay is well-worth critical examination, not least because it efficiently packs so much confusion into such a short space.
Another reason for examining it is the pedigree of the authors—Kate Clancy, Agustín Fuentes, Caroline VanSickle, and Catherine Clune-Taylor. Clancy is a professor of anthropology at the University of Illinois, Urbana-Champaign; Fuentes is a professor of anthropology at Princeton, and Clune-Taylor is an assistant professor of gender and sexuality studies at that university; VanSickle is an associate professor of anatomy at Des Moines. Clancy’s Ph.D. is from Yale, Fuentes’ is from UC Berkeley, and VanSickles’ is from Michigan. Clune-Taylor is the sole humanist: she has a Ph.D. in philosophy from Alberta, with Judith Butler as her external examiner. In short, the authors are not ill-educated crackpots or dogmatic activists, but top-drawer scholars. Their opinions matter.
Let’s talk about sex, baby
Before wading into the essay’s arguments, let’s look at the context, as noted in the second paragraph. “Last fall,” the authors write, “the American Anthropological Association made headlines after removing a session on sex and gender from its November 2023 annual conference.” The session’s cancellation was covered by the New York Times as well as international newspapers, and it eventually took place under the auspices of Heterodox Academy. (You can watch the entire event here.) Scheduled for the Sunday afternoon “dead zone” of the five-day conference, when many attendees leave for the airport, the title was “Let’s Talk About Sex, Baby: Why biological sex remains a necessary analytic category in anthropology.” The lineup was all-female, and included the anthropologists Kathleen Lowrey and Elizabeth Weiss. According to the session description, “With research foci from hominin evolution to contemporary artificial intelligence, from the anthropology of education to the debates within contemporary feminism about surrogacy, panelists make the case that while not all anthropologists need to talk about sex, baby, some absolutely do.”
Nothing evidently objectionable here, so why was it cancelled? The official letter announcing that the session had been removed from the program, signed by the presidents of the AAA and CASCA (the Canadian Anthropology Society), explained:
The reason the session deserved further scrutiny was that the ideas were advanced in such a way as to cause harm to members represented by the Trans and LGBTQI of the anthropological community as well as the community at large.
Why “the Trans” were double-counted (the T in LGBTQI) was not clear. And although ideas can harm, a handful of academics speaking in the Toronto Convention Centre are unlikely to cause much. In any event, the authors of “Biology is not binary” seem to think that the panelists’ errors about sex warranted the cancellation, not the trauma their words would bring to vulnerable anthropologists. “We were glad,” they say, “to see the American Anthropological Association course-correct given the inaccuracy of the panelists’ arguments.”
Never mind that no-one had heard the panelists’ arguments—what were these “inaccuracies”? The panelists, Clancy and her co-authors report, had claimed that “sex is binary,” and that “male and female represent an inflexible and infallible pair of categories describing all humans.”
“Biology is not binary” is not off to a promising start. Only one of the cancelled panelists, Weiss, has said anything about sex being binary in her talk abstract, and even that was nuanced: “skeletons are binary; people may not be.” No one had claimed that the two sex categories were “inflexible” or “infallible,” which anyway doesn’t make sense. (This is one example of the essay’s frequent unclarity of expression.) Neither had anyone claimed that every single human falls into one sex category or the other.
Probably the real reason the proposed panel caused such a stir was that it was perceived (in Clancy et al.’s own words) as “part of an intentional gender-critical agenda.” And, to be fair, some of the talks were “gender-critical,” for instance Silvia Carrasco’s. (Carrasco’s views have made her a target of activists at her university in Barcelona.) Still, academics can’t credibly cancel a conference session simply because a speaker defends ideas that bother some people, hence the trumped-up charges of harm and scientific error.
Although Clancy et al. misleadingly characterize the content of the cancelled AAA session, their essay might yet get something important right. They argue for four main claims. First, “sex is not binary.” Second, “sex is culturally constructed.” Third, “defining sex is difficult.” And, fourth, there is no one all-purpose definition of sex—it depends “on what organism is being studied and what question is being asked.”
Let’s go through these in order.
“Sex is not binary”
When people say that sex is binary, they sometimes mean that there are exactly two sexes, male and female. Sometimes they mean something else: the male/female division cuts humanity into two non-overlapping groups. That is, every human is either male (and not female), or female (and not male). These two interpretations of “Sex is binary” are different. Perhaps there are exactly two sexes, but there are some humans who are neither male nor female, or who are both sexes simultaneously. In that scenario, sex is binary according to the first interpretation, but not binary according to the second. Which of the two interpretations do Clancy et al. have in mind?
At least the essay is clear on this point. The “Quick Take” box on the first page tells us that the (false) binary thesis is that “male and female [are] the only two possible sex categories.” And in the text the authors say that “plenty of evidence has emerged to reject” the hypothesis that “there are only two sexes.” (Here they mystifyingly add “…and that they are discrete and different.” Obviously if there are two sexes then they are different.)
If there are not exactly two sexes, then the number of sexes is either zero, one, or greater than two. Since Clancy et al. admit that “categories such as ‘male’ and ‘female’…can be useful,” they must go for the third option: there are more than two sexes. But how many? Three? 97? In a striking absence of curiosity, the authors never say.
In any case, what reason do Clancy et al. give for thinking that the number of sexes is at least three? The argument is in this passage:
[D]ifferent [“sex-defining”] traits also do not always line up in a person’s body. For example, a human can be born with XY chromosomes and a vagina, or have ovaries while producing lots of testosterone. These variations, collectively known as intersex, may be less common, but they remain a consistent and expected part of human biology. So the idea that there are only two sexes…[has] plenty of evidence [against it].
However, this reasoning is fallacious. The premise is that some (“intersex”) people do not have enough of the “sex-defining” traits to be either male or female. The conclusion is that there are more than two sexes. The conclusion only follows if we add an extra premise, that these intersex people are not just neither male nor female, but another sex. And Clancy et al. do nothing to show that intersex people are another sex.
What’s more, it is quite implausible that any of them are another sex. Whatever the sexes are, they are reproductive categories. People with the variations noted by Clancy et al. are either infertile, for example those with Complete Androgen Insensitivity Syndrome (CAIS) (“XY chromosomes and a vagina”), or else fertile in the usual manner, for example many with Congenital Adrenal Hyperplasia (CAH) and XX chromosomes (“ovaries while producing lots of testosterone,” as Clancy et al. imprecisely put it). One study reported normal pregnancy rates among XX CAH individuals. Unsurprisingly, the medical literature classifies these people as female. Unlike those with CAIS and CAH, people who belonged to a genuine “third sex” would make their own special contribution to reproduction.
“Sex is culturally constructed”
“Biology is not binary” fails to establish that there are more than two sexes. Still, the news that sex is “culturally constructed” sounds pretty exciting. How do Clancy et al. argue for that?
There is a prior problem. Nowhere do Clancy et al. say what “Sex is culturally constructed” means. What’s more, the essay thoroughly conflates the issue of the number of sexes with the issue about cultural construction. Whatever “cultural construction” means, presumably culture could “construct” two sexes. (The Buddhas of Bamiyan in Afghanistan were literally constructed, and there were exactly two of them.) Conversely, the discovery of an extra sex would not show that sex was culturally constructed, any more than the discovery of an extra flavor of quark would show that fundamental particles are culturally constructed.
Clancy et al. drop a hint at the start of the section titled “Sex is Culturally Constructed.” “Definitions and signifiers of gender,” they say, “differ across cultures… but sex is often viewed as a static, universal truth.” (If you want to know what they mean by “gender,” you’re out of luck.) That suggests that the cultural construction of sex amounts to the “definitions and signifiers” of sex differing between times and places. This is confirmed by the following passage: “[T]here is another way we can see that sex is culturally constructed: The ways collections of traits are interpreted as sex can and have differed across time and cultures.” What’s more, in an article called “Is sex socially constructed?”, Clune-Taylor says that this (or something close to it) is one sense in which sex is socially constructed (i.e. culturally constructed).
The problem here is that “Sex is culturally constructed” (as Clancy et al. apparently understand “cultural construction”) is almost trivially true, and not denied by anyone. If “X is culturally constructed” means something like “Ideas of X and theories of X change between times and places,” then almost anything which has preoccupied humans will be culturally constructed. Mars, Jupiter and Saturn are culturally constructed: the ancients thought they revolved around the Earth and represented different gods. Dinosaurs are culturally constructed: our ideas of them are constantly changing, and are influenced by politics as well as new scientific discoveries. Likewise, sex is culturally constructed: Aristotle thought that in reproduction male semen produces a new embryo from female menstrual blood, as “a bed comes into being from the carpenter and the wood.” We now have a different theory.
Naturally one must distinguish the claim that dinosaurs are changing (they used to be covered only in scales, now they have feathers) from the claim that our ideas of dinosaurs are changing (we used to think that dinosaurs only have scales, now we think they have feathers). It would be fallacious to move from the premise that dinosaurs are culturally constructed (in Clancy et al.’s sense) to the conclusion that dinosaurs themselves have changed, or that there are no “static, universal truths” about dinosaurs. It would be equally fallacious to move from the premise that sex is culturally constructed to the claim that there are no “static, universal truths” about sex. (One such truth, for example, is that there are two sexes.) Nonetheless, Clancy et al. seem to commit exactly this fallacy, in denying (as they put it) that “sex is…a static, universal truth.”
To pile falsity on top of fallacy, when Clancy et al. give an example of how our ideas about sex have changed, their choice could hardly be more misleading. According to them:
The prevailing theory from classical times into the 19th century was that there is only one sex. According to this model, the only true sex is male, and females are inverted, imperfect distortions of males.
This historical account was famously defended in a 1990 book, Making Sex, by the UC Berkeley historian Thomas Laqueur. What Clancy et al. don’t tell us is that Laqueur’s history has come under heavy criticism; in particular, it is politely eviscerated at length in The One-Sex Body on Trial, by the classicist Helen King. It is apparent from Clune-Taylor’s other work that she knows of King’s book, which makes Clancy et al.’s unqualified assertion of Laqueur’s account even more puzzling.
“Defining sex is difficult”
Aristotle knew there were two sexes without having a satisfactory definition of what it is to be male or female. The question of how to define sex (equivalently, what sex is) should be separated from the question of whether sex is binary. So even if Clancy et al. are wrong about the number of sexes, they might yet be right that sex is difficult to define.
Why do they think it is difficult to define? Here’s their reason:
There are many factors that define sex, including chromosomes, hormones, gonads, genitalia, and gametes (reproductive cells). But with so many variables, and so much variation within each variable, it is difficult to pin down one definition of sex.
Readers of Reality’s Last Stand will be familiar with the fact that chromosomes and hormones (for example) do not define sex. The sex-changing Asian sheepshead wrasse does not change its chromosomes. Interestingly, the sex hormones (androgens and estrogens) are found in plants, although they do not appear to function as hormones. How could the over-educated authors have written that “there are many factors that define sex,” without a single one of them objecting?
That question is particularly salient because the textbook account of sex is in Clancy et al.’s very own bibliography. In the biologist Joan Roughgarden’s Evolution’s Rainbow there’s a section called “Male and Female Defined.” If you crack the book open, you can’t miss it.
Roughgarden writes:
To a biologist, “male” means making small gametes, and “female” means making large gametes. Period! By definition, the smaller of the two gametes is called a sperm, and the larger an egg. Beyond gamete size, biologists don’t recognize any other universal difference between male and female.
“Making” does not mean currently producing, but (something like) has the function to make. Surely one of Clancy et al. must have read Roughgarden’s book! (Again from her other work we know that Clune-Taylor has.) To avoid going round and round this depressing mulberry bush again, let’s leave it here.
“Sex is defined in a lot of ways in science”
Perhaps sex is not a single thing, and there are different definitions for the different kinds of sex. The standard gamete-definition of sex is useful for some purposes; other researchers will find one of the alternative definitions more productive. Clancy et al. might endorse this conciliatory position. They certainly think that a multiplicity of definitions is good scientific practice: “In science, how sex is defined for a particular study is based on what organism is being studied and what question is being asked.”
Leaving aside whether this fits actual practice, as a recommendation it is wrong-headed. Research needs to be readily compared and combined. A review paper on sexual selection might draw on studies of very different species, each asking different questions. If the definition of sex (male and female) changes between studies, then synthesizing the data would be fraught with complications and potential errors, because one study is about males/females-in-sense-1, another is about males/females-in-sense-2, and so on.
Indeed, “Biology is not binary” itself shows that the authors don’t really believe that “male” and “female” are used in science with multiple senses. They freely use “sex,” “male,” and “female” without pausing to disambiguate, or explain just which of the many alleged senses of these words they have in mind. If “sex is defined a lot of ways in science” then the reader should wonder what Clancy et al. are talking about.
In an especially odd passage, they write that the “criteria for defining sex will differ in studies of mushrooms, orangutans, and humans.” That is sort-of-true for mushrooms, which mate using mating types, not sperm and eggs. (Mating types are sometimes called “sexes,” but sometimes not.) However, it’s patently untrue for orangutans and humans, as the biologist Jerry Coyne points out.
Orangutans had featured earlier in the saga of the AAA cancellation, when Clancy and Fuentes had bizarrely suggested that the “three forms of the adult orangutan” present a challenge to the “sex binary,” seemingly forgetting that these three forms comprise females and two kinds of males. Kathleen Lowrey had some fun at their expense.
As if this tissue of confusion isn’t enough, Clancy et al. take one final plunge off the deep end. After mentioning osteoporosis in postmenopausal women, they write:
[P]eople experiencing similar sex-related conditions may not always fit in the same sex category. Consider polycystic ovary syndrome (PCOS), a common metabolic condition affecting about 8 to 13 percent of those with ovaries, which often causes them to produce more androgens than those without this condition. There are increasing numbers of people with PCOS who self-define as intersex, whereas others identify as female.
They seem to believe that two people with PCOS might not “fit in the same sex category.” That is, one person could be female while the other isn’t, with this alchemy accomplished by “self-definition.” PCOS, in case you were wondering, is a condition that only affects females or, in the approved lingo of the Cleveland Clinic, “people assigned female at birth.”
How could four accomplished and qualified professors produce such—not to mince words—unadulterated rubbish?
There are many social incentives these days for denouncing the sex binary, and academics—even those at the finest universities—are no more resistant to their pressure than anyone else. However, unlike those outside the ivory tower, academics have a powerful arsenal of carefully curated sources and learned jargon, as well as credentials and authority. They may deploy their weapons in the service of—as they see it—equity and inclusion for all.
It would be “bad science,” Clancy et al. write at the end, to “ignore and exclude” “individuals who are part of nature.” In this case, though, Clancy et al.’s firepower is directed at established facts, and the collateral damage may well include those people they most want to help.
--
About the Author
Alex Byrne is a Professor of Philosophy at the Massachusetts Institute of Technology (MIT) in the Department of Linguistics and Philosophy. His main interests are philosophy of mind (especially perception), metaphysics (especially color) and epistemology (especially self-knowledge). A few years ago, Byrne started working on philosophical issues relating to sex and gender. His book on these topics, Trouble with Gender: Sex Facts, Gender Fictions, is now available in the US and UK.
==
The whole "social construction," "cultural construction" thing is idiotic.
Not only does it mean you would be a different sex in a different society/culture, but it becomes necessary that cross-cultural/cross-societal reproduction is fraught with complications.
#Alex Byrne#sex pseudoscience#pseudoscience#sex denialism#biological sex#reproduction#biology#human reproduction#queer theory#religion is a mental illness
25 notes
·
View notes
Text









The Princess Royal’s Official Engagements in January 2024
04/01 With Sir Tim As Honorary President, attended the Oxford Farming Conference.
05/01 unofficial Sir Tim, as Trust President of the Gloucestershire Warwickshire Railway, visited emergency work at the Stanway Viaduct near Toddington. 🦺🚂
10/01 Princess Anne, accompanied by Sir Tim, carried out the following engagements in Colombo to commemorate the 75th Anniversary of United Kingdom-Sri Lanka Bilateral Relations;
As President of the United Kingdom Fashion and Textile Association, visited MAS Active in Katunayake. 👚
As Patron of Save the Children UK, visited the Save the Children Sri Lanka Head Office to mark its 50th Anniversary. 👧
As Patron of Save the Children UK, visited a Save the Children Sri Lanka programme at Lady Ridgeway Hospital for Children. 🏥
Called upon The President of the Democratic Socialist Republic of Sri Lanka and Mrs Wickremesinghe at The President's House. 📩
Attended a Dinner given by The President of the Democratic Socialist Republic of Sri Lanka and Mrs Wickremesinghe at The President's House to commemorate the 75th Anniversary of United Kingdom-Sri Lanka Bilateral Relations. 🍽️
11/01 Princess Anne, accompanied by Sir Tim, carried out the following engagements in Kandy and Jaffna to commemorate the 75th Anniversary of United Kingdom-Sri Lanka Bilateral Relations;
Visited the Temple of the Sacred Tooth Relic, Sri Dalada Maligawa in Kandy. 🛕
Met representatives of the Tamil Community at Jaffna Public Library. 📚
Visited the Halo Trust De-mining site, the United Nations Development Programme and International Organisation for Migration Resettlement site in Muhamalai. 🧨
12/01 Princess Anne, accompanied by Sir Tim, carried out the following engagements in Colombo to commemorate the 75th Anniversary of United Kingdom-Sri Lanka Bilateral Relations;
Visited the British High Commission Office. 🇬🇧
As President of the Commonwealth War Graves Commission, laid a wreath at Jawatte Cemetery. 🪦
Visited Vajira Pillayar Kovil Hindu Temple 🛕
As President of the English-Speaking Union of the Commonwealth, visited the British Council. 🏴🗣️
As President of the Mission to Seafarers, visited the Mission to Seafarers Colombo. ⛵️
Visited Hatch Works. 📆
As President of the Mission to Seafarers, attended a Key Supporters Reception at the Cathedral of Christ the Living Saviour. ⛪️
Attended a Reception given by the British High Commissioner to Sri Lanka at the Residence in Colombo. 🍹🇬🇧🇱🇰
16/01 As Patron of Police Treatment Centres,visited Castlebrae Treatment Centre in Perth. 👮🩺
As Vice President of the Royal Scottish Geographical Society, and Former Patron of the Heart of Arabia Expedition, attended a Reception at the Royal Scottish Geographical Society. 🌍
Opened the Vertical Farm Engineering Innovation Centre in Inverkeithing. 🌾⬆️
17/01 Held an Investiture at the Palace of Holyroodhouse.🎖️
As Chancellor of the University of Edinburgh, attended a Reception to mark the 60th Anniversary of Computer Science and Artificial Intelligence and later opened the Institute for Regeneration and Repair at the University. 🎓🎮
As Honorary Member of the New Club attended the 70th Anniversary Amalgamation Dinner. 🍽️
18/01 As President of the UK Fashion and Textile Association, visited Advanced Clothing Solutions in Motherwell. 👗
As Patron of Citizens Advice Scotland, visited Hamilton Citizens Advice Bureau. 👩⚖️
23/01 Opened the Medical Research Council Laboratory of Medical Sciences at Imperial College NHS Hospital in London. 🏥
As Patron of Livability, attended the Thanksgiving Service to mark the 180th anniversary at All Hallows by the Tower. 🎂⛪️
As Royal Honorary Colonel of the University of London Officers’ Training Corps, attended the Annual Reception at Yeomanry House. 🎓🫡
24/01 On behalf of The King, held an Investiture at Windsor Castle. 🎖️
As Patron of Save the Children UK, visited the London Head Office. 👧👦
As President of the City and Guilds of London Institute, visited Cox Workshops Limited in London. 🛠️
25/01 As Royal Patron of the National Coastwatch Institution, visited Cromer Station. 🛟
As President of the Royal Yachting Association, opened Norfolk Schools Sailing Association’s new facilities at Filby Centre, Norfolk. ⛵️
As Patron of National Association of Official Prison Visitors, visited HM Prison Norwich. 🔗
30/01 As Patron of Save the Children UK, visited the Stockton Heath Charity Shop. 🛍️
Visited Jodrell Bank Observatory UNESCO World Heritage Site at the University of Manchester. 🌌🪐
As President of the Riding for the Disabled Association, opened the new Centre and Platinum Jubilee Stables at Reaseheath Equestrian College in Nantwich. 🏇🏼
31/01 Held an Investiture at Buckingham Palace.🎖️
As Royal Fellow of the Royal Academy of Engineering, attended the 10th Anniversary Reception of the Africa Prize for Engineering Innovation at Prince Philip House in London. 🏆
Total official engagements for Anne in January: 41
2024 total so far: 41
Total official engagements accompanied by Tim in January: 17
2024 total: 17
#january was so fab#in royal watching may i add 😂#not irl#i loved the sri lanka tour 🇱🇰#lots of rugby for the next 2 months! and i am very excited#princess anne#princess royal#tim laurence#timothy laurence#january 2024#aimees unofficial engagement count 2024#i am keeping track of everyone else’s engagements i just aren’t posting them#if you wanna know their numbers please dm me
32 notes
·
View notes
Text
The Science of Discovering the Past: Archaeoastronomy

By Girtompir - Own work, CC0, https://commons.wikimedia.org/w/index.php?curid=57252822
The stars have long been part of the human experience, with the night sky being a more vital part of life before the development of modern cities with their lights washing out a majority of the stars. Most cultures had a deep connection with the sky, recording their observations in stories and in their art and writings.
CC BY-SA 3.0, https://commons.wikimedia.org/w/index.php?curid=906430
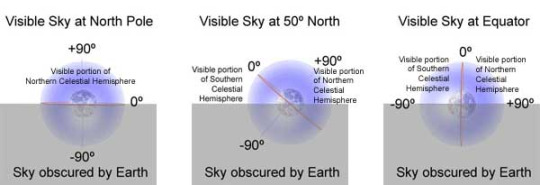
Archaeoastronomy is an interdisicplinary study of how people 'have understood the phenomena in the sky, how they used these phenomena and what role the sky played in their cultures'. It involves ethnoastronomy, the 'anthropological study of sky watching in contemporary societies' as well as historical astronomy, which focuses on the astronomical records of the past. Unlike modern astronomy, which focuses on observations of the sky and scientific explanations of those observations, archaeoastronomy takes in account the cultural meanings of those observations.

By Alun Salt - https://www.flickr.com/photos/alun/2733498/in/set-68848/, CC BY-SA 2.0, https://commons.wikimedia.org/w/index.php?curid=740899
Archaeoastronomy began with noting the astronomical orientation of ruins, including megalithic sites like Stonehenge, in the 17th and 18th centuries, though the term wasn't coined until 1973 by Elizabeth Chesley Baity. It wasn't until the 1960s that systemic work began by studying megalithic sites in the British Isles. Engineer Alexander Thom and astronomer Gerald Hawkins proposed that Stonehenge was an astronomical computer. While Hawkins' theory was dismissed, Thom performed a survey of megalithic sites in the British Isles. Euan MacKie sought to test Thom's theory by excavating the site of a standing stone at Kintraw in Argyllshire from 1970-1971 to verify if Thom's prediction that the site accurately showed the winter solstice. He found an observation platform on the hill above the stone that proved Thom's prediction correct. Because of this vindication, MacKie checked other sites to verify their alignments before broadly accepting Thom's conclusions.

By Adrian Hernandez - Own work, CC BY-SA 4.0, https://commons.wikimedia.org/w/index.php?curid=71192285
Archaeoastronomy was used by anthropologists studying Amerindian civilization. This was different to the study of Neolithic structures in the British Isles in that there were sources about the prehistory, such as the records of colonizers, that were unavailable for British early civilizations. This allows more certain claims that possible in the Old World.

Public Domain, https://commons.wikimedia.org/w/index.php?curid=1126668
In 1981, the International Astronomical Union (IAU) released two volumes on the proceedings from the conference that sought to bring researchers together and encourage the move to interdisciplinary approaches, combining the contextuality of archaeological studies with astronomical studies, seeking to understand the why behind ancient people's fascination with the night sky.

By Fcb981 - Own work, CC BY-SA 3.0, https://commons.wikimedia.org/w/index.php?curid=3862230
There are many ways to do archaeoastronomy, but the two many methodologies are known as 'green archaeoastronomy' and 'brown archaeoastronomy'. Green archaeoastronomy is used where social evidence is relatively scant and relies more on statistical studies. The methods are similar to those developed and used by Thom. Many of these studies are based on the horizon rather than the full sky since that is the easiest part of the sky to align with archaeological sites. Brown archaeoastronomy is close to the history of astronomy or cultural history as it relies on records, both ethnographic records as well as the records of early astronomers with their calendars and rituals. This is the system used to study sites like Chichen Itza in Mexico, where researchers looked at records to find out what the Maya found important in the night sky and then looking at how the sites on the ground aligned to that. They were able to find in the writings that Maya held Venus in high regard, recording the risings and settings of it. They were able to find structures in Chichen Itza that aligned to these points on the horizon. Both have criticisms, with green archaeoastronomy being criticized for lacking social context and failing to answer the question 'why' people in the past built the structures they did and brown archaeoastronomy being criticized for lacking statistical and methodological rigor because each site is studied differently based on the documentation and evidence that has been found relating to the site.
2 notes
·
View notes
Text
Why Sabaragamuwa University is a Great Choice.
Sabaragamuwa University of Sri Lanka (SUSL) is increasingly recognized for its technological advancement and innovation-driven environment, making it one of the leading universities in Sri Lanka in terms of technology. Here are the key reasons why SUSL stands out technologically.

Here’s why SUSL stands out as a technological powerhouse among Sri Lankan universities:
🔧1. Faculty of Technology
SUSL established a dedicated Faculty of Technology to meet the demand for tech-skilled graduates. It offers degree programs such as:
BTech in Information and Communication Technology
BTech in Engineering Technology
These programs combine practical experience in labs, workshops and real-world projects with a strong theoretical foundation.
🖥️2. Advanced IT Infrastructure
SUSL has modern computer labs, smart classrooms, and high-speed internet access across campus.
A robust Learning Management System (LMS) supports online learning and hybrid education models.
Students and lecturers use tools like Moodle, Zoom, and Google Classroom effectively.
🤖 3. Innovation & AI Research Support
SUSL promotes AI, Machine Learning, IoT, and Data Science in student research and final-year projects.
Competitions like Hackathons and Innovative Research Symposia encourage tech-driven solutions.
Students develop apps, smart systems, and automation tools (e.g., Ceylon Power Tracker project).
🌐 4. Industry Collaboration and Internships
SUSL connects students with the tech industry through:
Internships at leading tech firms
Workshops led by industry experts
Collaborative R&D projects with government and private sector entities
These connections help students gain hands-on experience in areas such as software engineering, networking, and data analytics that make them highly employable after graduation.
💡 5. Smart Campus Initiatives
SUSL is evolving into a Smart University, introducing systems that streamline academic life:
Digital student portals
Online registration and results systems
E-library and remote resource access
Campus Wi-Fi for academic use
These initiatives improve the student experience and create an efficient, technology-enabled environment.
🎓 6. Research in Emerging Technologies
The university is involved in pioneering research across emerging technological fields, including:
Agricultural tech (AgriTech)
Environmental monitoring using sensors
Renewable energy systems
Students and faculty publish research in international journals and participate in global tech events.
🏆 7. Recognition in National Competitions
SUSL students often reach fina rounds or win national competitions in coding, robotics, AI, and IoT innovation.
Faculty members are invited as tech advisors and conference speakers, reinforcing the university's expertise.
Sabaragamuwa University is actively shaping the future not only with technology, but by integrating technology into education, research and operations. This makes it a technological leader among Sri Lankan Universities. Visit the official university site here: Home | SUSL
2 notes
·
View notes
Text
MediaTek Kompanio Ultra 910 for best Chromebook Performance

MediaTek Ultra 910
Maximising Chromebook Performance with Agentic AI
The MediaTek Kompanio Ultra redefines Chromebook Plus laptops with all-day battery life and the greatest Chromebooks ever. By automating procedures, optimising workflows, and allowing efficient, secure, and customised computing, agentic AI redefines on-device intelligence.
MediaTek Kompanio Ultra delivers unrivalled performance whether you're multitasking, generating content, playing raytraced games and streaming, or enjoying immersive entertainment.
Features of MediaTek Kompanio Ultra
An industry-leading all-big core architecture delivers flagship Chromebooks unmatched performance.
Arm Cortex-X925 with 3.62 GHz max.
Eight-core Cortex-X925, X4, and A720 processors
Single-threaded Arm Chromebooks with the best performance
Highest Power Efficiency
Large on-chip caches boost performance and power efficiency by storing more data near the CPU.
The fastest Chromebook memory: The powerful CPU, GPU, and NPU get more data rapidly with LPDDR5X-8533 memory support.
ChromeOS UX: We optimised speed to respond fast to switching applications during a virtual conference, following social media feeds, and making milliseconds count in in-game battle. Nowhere is better for you.
Because of its strong collaboration with Arm, MediaTek can provide the latest architectural developments to foreign markets first, and the MediaTek Kompanio Ultra processor delivers the latest Armv9.2 CPU advantage.
MediaTek's latest Armv9.2 architecture provides power efficiency, security, and faster computing.
Best in Class Power Efficiency: The Kompanio Ultra combines the 2nd generation TSMC 3nm technology with large on-chip caches and MediaTek's industry-leading power management to deliver better performance per milliwatt. The spectacular experiences of top Chromebooks are enhanced.
Best Lightweight and Thin Designs: MediaTek's brand partners can easily construct lightweight, thin, fanless, silent, and cool designs.
Leading NPU Performance: MediaTek's 8th-generation NPU gives the Kompanio Ultra an edge in industry-standard AI and generative AI benchmarks.
Prepared for AI agents
Superior on-device photo and video production
Maximum 50 TOPS AI results
ETHZ v6 leadership, Gen-AI models
CPU/GPU tasks are offloaded via NPU, speeding processing and saving energy.
Next-gen Generative AI technologies: MediaTek's investments in AI technologies and ecosystems ensure that Chromebooks running the MediaTek Kompanio Ultra provide the latest apps, services, and experiences.
Extended content support
Better LLM speculative speed help
Complete SLM+LLM AI model support
Assistance in several modes
11-core graphics processing unit: Arm's 5th-generation G925 GPU, used by the powerful 11-core graphics engine, improves traditional and raytraced graphics performance while using less power, producing better visual effects, and maintaining peak gameplay speeds longer.
The G925 GPU matches desktop PC-grade raytracing with increased opacity micromaps (OMM) to increase scene depths with subtle layering effects.
OMM-supported games' benefits:
Reduced geometry rendering
Visual enhancements without increasing model complexity
Natural-looking feathers, hair, and plants
4K Displays & Dedicated Audio: Multiple displays focus attention and streamline procedures, increasing efficiency. Task-specific displays simplify multitasking and reduce clutter. With support for up to three 4K monitors (internal and external), professionals have huge screen space for difficult tasks, while gamers and content makers have extra windows for chat, streaming, and real-time interactions.
DP MST supports two 4K external screens.
Custom processing optimises power use and improves audio quality. Low-power standby detects wake-up keywords, improving voice assistant response. This performance-energy efficiency balance improves smart device battery life, audio quality, and functionality.
Hi-Fi Audio DSP for low-power standby and sound effects
Support for up to Wi-Fi 7 and Bluetooth 6.0 provides extreme wireless speeds and signal range for the most efficient anyplace computing.
Wi-Fi 7 can reach 7.3Gbps.
Two-engine Bluetooth 6.0
#technology#technews#govindhtech#news#technologynews#processors#MediaTek Kompanio Ultra#Agentic AI#Chromebooks#MediaTek#MediaTek Kompanio#Kompanio Ultra#MediaTek Kompanio Ultra 910
2 notes
·
View notes
Text
Feb 17, 2025
Computer programmers quickly claimed that the 150 figure was not evidence of fraud, but rather the result of a weird quirk of the Social Security Administration’s benefits system, which was largely written in COBOL, a 60-year-old programming language that undergirds SSA’s databases as well as systems from many other US government agencies.
COBOL is rarely used today, and as such, Musk’s cadre of young engineers may well be unfamiliar with it.
Because COBOL does not have a date type, some implementations rely instead on a system whereby all dates are coded to a reference point. The most commonly used is May 20, 1875, as this was the date of an international standards-setting conference held in Paris, known as the "Convention du Mètre."
These systems default to the reference point when a birth date is missing or incomplete, meaning all of those entries in 2025 would show an age of 150....
The database Musk took the screenshot from listed almost 400 million people, which is more than five times the number of people receiving benefits in 2024, according to the SSA’s own website. It’s also significantly more than the entire US population.
The fact that the Social Security system contains millions of entries from people who are dead is likely distinct from a potential COBOL-caused error, and also not news. A report written by the SSA’s inspector general in 2023 found that 98 percent of those aged 100 or older in the Social Security databases are not in receipt of any benefits. The report added that the database would not be updated because it would cost too much money to do so.
“DOGE going into all these agencies with largely unfettered access with a wrecking ball and no understanding of the business logic and structure behind the code, database and configured business logic, related payment systems, and integrated decision trees, poses real risks to the privacy and persona-level data of millions of people across all of those records,” Thomas Drake, a former National Security Agency executive-turned-whistleblower, tells WIRED.
#doge#trump administration#also screenshots aren't actual evidence#they generally don't contain metadata that can help authenticate them#screenshots are not transparency
2 notes
·
View notes
Note
hi. Pretty please, will you post / link (links to post you've already made too, so it in one place) to all the information you've come across regarding war fighter enhancements with technology augmentation - EEGs, brain-computer interface (ie NEURALINK), connectomes, neuro engineering technology, cognitive/information warfare specifically pertaining to signals intelligence, acoustic weapons
HORNET is too old, I'm not sure where to look for anything newer that could be found pertaining to advancements in this type of research or similar research. If you get something in this domain that isn't labeled for militaristic purposes please share regardless.
Take your time, if you'd like to share and organize what you have.
Hello,
I’m posting documents on my website, a lot of the information you’re asking about is under the password protected portion. I'm working on putting documents on the site. You can complete the request for the password here.
A number of acoustic weapons technology can be purchased from the manufacturer directly. For example one could attend International Defence Exhibition and Conference (IDEX)
There are a number of systems here are a few:
Mosquito Alarm-Britain Squawk Box-British Army RFDEW system-British Army
DragonFire-United Kingdom (DEW)
The Scream-Israel Iron Beam-Israel (DEW) WaveStun-Israeli Thunder Generator-Israel
Bofors HPM Blackout-United States
Active Denial System-United States PHaSR-United States LED Incapacitator-United States HyperSpikes-United States Tactical High-power Operational Responder-United States
And just for fun: U.S. Army Acquisition Program Portfolio 2023-2024
Oz
5 notes
·
View notes
Text
Holidays 1.24
Holidays
BCPB (Black & Can’t Play Basketball) Awareness Day
Big Garden Bird Watch (UK)
Bull Day (French Republic)
Colorist Appreciation Day
Day of the Foreign Intelligence Service (Ukraine)
Economic Liberation Day (Togo)
Fiesta de Ekeko (Bolivia)
Foreign Intelligence Service Day (Ukraine)
Global Belly Laugh Day (at 1:24 pm local time)
Gold Rush Day (California)
Healthcare Continuing EducationProfessionals Day
Heart to Heart Day
International ALGS (Alagille Syndrome) Awareness Day
Internal Combustion Engine Day
International Day of Education
International Day of the Endangered Lawyer
International Mobile Phone Recycling Day
International Women’s Sport Day
Juan Pablo Duarte Day (Dominican Republic)
"Just Do It" Day
Macintosh Computer Day
Microwave Oven Day
Minimoog Day
Moebius Syndrome Awareness Day
National ALGS Awareness Day
National Compliment Day
National Girl Child Day (India)
National Heroes Day (Cayman Islands)
National Readathon Day
Paul Pitcher Day (UK)
Social Sipping and Nibbling Rehearsal Day
Square Dance Day [also 11.29]
Talk Like a Grizzled Prospector Day
Tax Ruled Unconstitutional Day
Tricknology Day
TV Game Show Day
World Day for African and Afro-descendant Culture
Zaevion Dobson Day (Tennessee)
Food & Drink Celebrations
Beer Can Day (a.k.a. Beer Can Appreciation Day)
Eskimo Pie Day
National Hot Cereal Day
National Lobster Thermidor Day
National Peanut Butter Day
Nature Celebrations
Change a Pet's Life Day
Saffron Crocus (The Beauty of Moderation; Korean Birth Flowers)
Independence, Flag & Related Days
Fundamental Orders (A Frame of Gov’t; Connecticut; 1639)
Uttar Pradesh Day (India)
Washington, D.C. (Federal District Proclaimed; 1791)
Ziua Micii Unirii (Unification Day of the Romanian Principalities; Romania; 1859)
4th Friday in January
Comfort Food Friday [Every Friday]
Five For Friday [Every Friday]
Flapjack Friday [4th Friday of Each Month]
Flashback Friday [Every Friday]
Flirtatious Friday [4th Friday of Each Month]
Friday Finds [Every Friday]
National Activity Professionals Day [4th Friday]
Newman Day (a.k.a. Newman's Day, 24 hours in a day, 24 beers in a case. Coincidence? I think not.) [Bates College] (Friday nearest 1.26) [also 3.30 & 4.24]
Preschool Health and Fitness Day [Last Friday]
Stout & Chowder Festival (Philadelphia, Pennsylvania) [Last Friday]
TGIF (Thank God It's Friday) [Every Friday]
Thorrablot (a.k.a. Þorrablót; Midwinter Festival; Pagan Iceland) [Friday after 1.19]
Weekly Holidays beginning January 24 (3rd Full Week of January)
Baltimore Restaurant Week (Baltimore, Maryland) [thru 2.2]
Data Privacy Week (thru 1.28)
Festivals Beginning January 24, 2025
Ann Arbor Folk Festival (Ann Arbor, Michigan) [thru 1.25]
Aukland Folk Festival (Aukland,New Zealand) [thru 1.26]
Fan Expo Portland (Portland, Oregon) [thru 1.26]
Foggy Longbritches Folk Festival (Brooksville, Florida) [thru 1.26]
First Taste Oregon (Salem, Oregon) [thru 1.25]
Göteborg Film Festival (Gothenburg, Sweden) [thru 2.2]
GWA (Georgia Watermelon Ass’n) Annual Meeting & Conference (Braselton, Georgia) [thru 1.26]
HIPPOLOGICA (Berlin, Germany) [thru 1.26]
Lakeland Pigfest (Lakeland, Florida) [thru 1.25]
Naples Seafood & Music Festival (Naples, Florida)
Naples Winter Wine Festival (Naples, Florida)
Pacific Poultry Breeders Association Winter Show (Lodi, California) [thru 1.26]
Feast Days
Alacitas (Aymara Indian Pot-Bellied God of Property; Everyday Wicca)
Babylas of Antioch (Christian; Martyr)
Blessing of the Candle of the Happy Women Pagan Purification Ceremony; Hungary)
Cadoc Day (Wales)
Cat Sacrifice Day (Aix-En Province, France)
Ekeko Festival (God of Abundance; Bolivia) [Lasts 3 Weeks]
Exuperantius of Cingoli (Christian; Saint)
The Fairy-Four Paganalia (Shamanism)
Feast of Our Lady of Peace (Roman Catholic)
Feast of Seed-Time (Feati Sementini; Ancient Rome)
Felician of Foligno (Christian; Martyr)
Francis de Sales (Christian; Saint) [Journalists, Editors, Writers]
Invent a God Day (Pastafarian)
John Belushi (Hedonism; Saint)
Jools Holland (Humanism)
Klaatu Day (Church of the SubGenius; Saint)
Macedonius of Syria (Christian; Saint)
Paganalia: Gaea’s Day (Celebration of the Country Farmer; Pagan)
Pendulum Dowsing to Find Lost Things (Starza Pagan Book of Days)
The Pendragon Legend, by Antal Szerb (Novel; 1934)
Pratulin Martyrs (Greek Catholic Church)
Sailing of Bast (Ancient Egypt)
Sementivae begins (Ancient Roman festival honoring Ceres (Goddess of Agriculture) and Tellus (Mother Earth)
Solomon (Positivist; Saint)
Stanley the Mouse (Muppetism)
Suranus of Umbria (Christian; Saint)
Timothy, disciple of St. Paul (Christian; Martyr)
Twrch Trwyth Day (Boar hunted by King Arthur; Celtic Book of Days)
Lunar Calendar Holidays
Chinese: Month 12 (Ding-Chou), Day 25 (Gui-Si)
Day Pillar: Water Snake
12-Day Officers/12 Gods: Stable Day (定 Ding) [Auspicious]
Holidays:
None Today
Secular Saints Days
Vicki Baum (Literature)
John Belushi (Entertainment)
Konstantin Bogaevsky (Art)
Cassandre (Art)
William Congreve (Literature)
Pierre de Beaumarchais (Literature)
Neil Diamond (Music)
Mahmoud Farshchian (Art)
Jools Holland (Music)
Machio Kaku (Music)
C.L. Moore (Literature)
Robert Motherwell (Art)
Aaron Neville (Music)
Mary Lou Retton (Sports)
John Romita Sr. (Art)
Kristen Schaal (Entertainment)
Ester Šimerová-Martinčeková (Art)
Vasily Surikov (Art)
Sharon Tate (Entertainment)
Gillis van Coninxloo (Art)
Edith Wharton (Literature)
Warren Zevon (Music)
Lucky & Unlucky Days
Shakku (赤口 Japan) [Bad luck all day, except at noon.]
Premieres
Absent Minded Willie (Gaumont Kartoon Komics Cartoon; 1917)
Alice Foils the Pirates (Ub Iwerks Disney Cartoon; 1927)
Amerika, by Franz Kafka (Novel; 1927)
By the Beautiful Sea (Fleischer Screen Songs Cartoon; 1931)
Championship of the Universe Race (Auto/Airplane Race; 1914)
Chicago (Film; 2003)
Clement Lorimer, by Angus Reach (Novel; 1848)
The Courier (Film; 2020)
Danse Macabre, by Camille Saint-Saëns (Tone Poem; 1874)
Evil Ways, by Santana (Song; 19870)
Façade, by Eidth Sitwell (Poem; 1922)
Farewell My Ugly or Knots to You (Rocky & Bullwinkle Cartoon, S1, Ep. 18; 1960)
Felix Flirts with Fate (Felix the Cat Cartoon; 1926)
Fierce Creatures (Film; 1997)
Go Ask Alice, by Beatrice Sparks (Novel; 1971)
Grand Hotel, by Vicki Baum (Novel; 1929)
The Grapes of Wrath (Film; 1940)
Hairless Hector (Terrytoons Cartoon; 1941)
Heir Restorer (Casper Paramount Cartoon; 1958)
A Hollywood Detour (Color Rhapsody Cartoon; 1942)
Ideas on the Aesthetics of Music, by Christian Friedrich Daniel Schubert (Essays; 1787)
Jirel of Joiry, by C.L. Moore (Novel; 1934)
Jules et Jim (Film; 1978)
Kings of the Wild Frontier, by Adam & The Ants (Album; 1981)
The Köln Concert, recorded by Keith Jarrett (Live Album; 1975)
The Little Brown Jug (Aesop’s Film Fable Cartoon; 1926)
Mickey’s Toontown (Disneyland Attraction; 1993)
Mouse-Placed Kitten (WB MM Cartoon; 1959)
Musica-Lulu (Little Lulu; 1947)
My Chauffeur (Film; 1986)
The 19th Hole Club, featuring Al Falfa (Terrytoons Cartoon; 1936)
Noah’s Outing, featuring Al Falfa (Terrytoons Cartoon; 1932)
No Other One (Fleischer Screen Songs Cartoon; 1936)
The Oompahs (Jolly Frolics UPA Cartoon; 1952)
Pluto’s Playmate (Pluto Disney Cartoon; 1941)
A Real Bug’s Life (Documentary TV Series; 2024)
The Rude Intruder (Chilly Willy Cartoon; 1972)
Setting Free the Bears, by John Irving (Novel; 1968)
Shift: Third Shift — Pact, by Hugh Howey (Novel; 2013)
Skid Row, by Skid Row (Album; 1989)
Snake in the Gracias (Tijuana Toads Cartoon; 1971)
Teddy Bear, recorded by Elvis Presley (Song; 1957)
The Treasure of the Sierra Madre (Film; 1948)
21, by Adele (Album; 2011)
Two for the Ripsaw or Goodbye Mr. Chips (Rocky & Bullwinkle Cartoon, S1, Ep. 17; 1960)
Waco (TV Mini-Series; 2018)
The Will to Meaning: Foundations and Applications of Logotherapy, by Viktor E. Frankl (Philosophy Book; 1969)
The Yellow Kid (Comic Strip; 1897) [1st Newspaper Comic Strip]
Today’s Name Days
Franz, Thurid, Vera (Austria)
Bogoslav, Felicijan, Franjo (Croatia)
Milena (Czech Republic)
Timotheus (Denmark)
Naima, Naimi (Estonia)
Senja (Finland)
François (France)
Bernd, Franz, Thurid, Vera (Germany)
Filon, Polyxene, Polyxeni, Xene, Xeni, Zosimas (Greece)
Timót (Hungary)
Francesco (Italy)
Eglons, Krišs, Ksenija (Latvia)
Artūras, Felicija, Gaivilė, Mažvydas, Šarūnas, Vilgaudas (Lithuania)
Jarl, Joar (Norway)
Chwalibóg, Felicja, Mirogniew, Rafaela, Rafał, Tymoteusz (Poland)
Xenia (Romania)
Timotej (Slovakia)
Francisco, Paz, Xenia (Spain)
Erika (Sweden)
Roxanna, Roxoliana (Ukraine)
Oral, Orel, Tim, Timmy, Timon, Timothy, Vera, Verena (USA)
National Name Days:
National Matthew Day
Today is Also…
Day of Year: Day 24 of 2025; 341 days remaining in the year
ISO: Day 5 of Week 4 of 2025
Celtic Tree Calendar:
Druid Tree Calendar: Elm (Jan 12-24) [Day 13 of 13]
Graves Calendar: Luis (Rowan) [Day 4 of 28]
Chinese: Month 12 (Ding-Chou), Day 25 (Gui-Si)
Chinese Year of the: Dragon 4722 (until January 29, 2025) [Wu-Chen]
Coptic: 16 Tubah 1741
Hebrew: 24 Teveth 5785
Islamic: 24 Rajab 1446
J Cal: 24 White; Threesday [24 of 30]
Julian: 11 January 2025
Moon: 24%: Waning Crescent
Positivist: 24 Moses (1st Month) [Solomon]
Runic Half Month: Elhaz (Elk) [Day 3 of 15]
Season: Winter (Day 35 of 90)
Week: 3rd Full Week of January
Zodiac:
Tropical (Typical) Zodiac: Aquarius (Day 5 of 30)
Sidereal Zodiac: Capricorn (Day 10 of 29)
Schmidt Zodiac: Sagittarius (Day 24 of 25)
IAU Boundaries (Current) Zodiac: Capricorn (Day 5 of 28)
IAU Boundaries (1977) Zodiac: Capricornus (Day 6 of 28)
2 notes
·
View notes
Text


— BASICS
Name: Zara Kumar Age / D.O.B.: 39 / January 5th 1985 Gender, Pronouns & Sexuality: CisFemale, She/Her, Heterosexual Hometown: Queens, NY Affiliation: Civilian Job position: Global Head of Cybersecurity at Goldman Sachs Education: Master’s Degree in Computer Science from Standford Relationship status: Divorced Children: 1 daughter, Saira Positive traits: Intelligent, Resilient, Kindhearted, Persuasive, Sentimental Negative traits: Secretive, Stubborn, Self-Indulgent, Compulsive, Obsessive
— BIOGRAPHY
Early Life and Education
1985: Born in Queens, New York, after her big brother Rahi, was a very happy child.
1990-2003: Attended a competitive public high school: The Bronx High School of Science, excelling in STEM subjects, particularly math and computer science. Participated in programming clubs and cybersecurity competitions.
College and Early Career
2003-2007: Attended Massachusetts Institute of Technology (MIT), earning a Bachelor’s Degree in Computer Science and Engineering. Focused on network security and cryptography.
Interned at a leading tech company, IBM, in cybersecurity during summer breaks.
2007-2009: Completed a Master’s Degree in Computer Science at StanfordUniversity, specializing in cybersecurity, machine learning, and ethical hacking. Published research papers on innovative methods for detecting and preventing cyber threats.
Professional Career
2009-2012: Joined CrowdStrike as a Junior Threat Analyst. Worked on high-profile cyber incidents, earning recognition for her work in preventing major breaches.
2012-2015: Returned to New York and worked at IBM’s X-Force Red Team, focusing on penetration testing and enterprise-level security.
2015-2020: Hired by Goldman Sachs as a Cybersecurity Specialist. Quickly promoted to Senior Analyst, then Vice President of Cybersecurity, spearheading initiatives to protect the firm from financial cybercrime.
Managed a team addressing large-scale phishing attacks and ransomware threats.
Developed and implemented a zero-trust security model for internal operations.
Personal Development and Achievements
2020-2024: Recognized as an industry leader. Regular speaker at conferences discussing the intersection of finance and cybersecurity.
Awarded accolades such as the Forbes 40 Under 40 in Technology and Cybersecurity Professional of the Year by ISC2.
Present Day
2024: At 39, she is the Global Head of Cybersecurity Operations at Goldman Sachs, overseeing teams worldwide.
Lives in Manhattan.
Actively mentors young women in STEM, emphasizing opportunities for underrepresented groups.
3 notes
·
View notes
Text
Bennett University: A Leading Destination for Quality Higher Education
When it comes to choosing the right university, students are not just looking for academic excellence but also for institutions that provide holistic development. Bennett University, located in Greater Noida, Uttar Pradesh, is emerging as a prime destination for higher education in India. Established by the Times of India Group in 2016, Bennett University is dedicated to empowering students with cutting-edge skills and global perspectives.

Why Bennett University Stands Out
1. World-Class Curriculum
Bennett University offers a range of undergraduate, postgraduate, and doctoral programs designed in collaboration with leading global institutions. The curriculum is tailored to meet the demands of a rapidly evolving job market, especially in areas like engineering, management, law, and media.
The University emphasizes experiential learning, ensuring that students are equipped with practical skills to excel in real-world scenarios. The faculty includes accomplished academicians and industry professionals, providing students with invaluable insights into their fields.
2. Industry Partnerships and Internships
Bennett University has strong collaborations with leading companies, offering students unparalleled exposure to industry trends. These partnerships open up a wide array of opportunities, including internships and live projects, where students can apply their theoretical knowledge in a practical setting.
The University’s ties with global giants like Microsoft, Amazon Web Services (AWS), and IBM enable students to participate in exclusive training sessions, hackathons, and innovation challenges.
3. State-of-the-Art Infrastructure
The Bennett University campus is designed to foster an environment conducive to learning and innovation. Spread over 68 acres, the campus boasts modern classrooms, laboratories, and research centers. The University is equipped with the latest technological tools to provide students with a world-class education experience.
Additionally, the university offers excellent hostel facilities, libraries, recreational spaces, and sports amenities to ensure that students have a well-rounded campus life.
4. Global Exposure and International Collaborations
What truly sets Bennett University apart is its global outlook. The institution has partnered with internationally renowned universities, including Georgia Tech, Johnson Cornell, and Babson College, allowing students to gain global exposure through exchange programs, joint research initiatives, and international conferences.
This international collaboration enables students to understand global academic and professional standards, making them highly competitive in the global job market.
5. Entrepreneurship and Innovation Ecosystem
Bennett University is committed to nurturing the entrepreneurial spirit among students. The Center for Innovation and Entrepreneurship (CIE) is a hub where students can work on innovative ideas and develop them into market-ready products. The CIE provides mentorship, incubation, and funding opportunities to budding entrepreneurs.
With the growing startup culture in India, Bennett’s focus on entrepreneurship ensures that students are ready to contribute to and lead new ventures.
6. Placements and Career Support
Bennett University has a dedicated placement cell that works tirelessly to ensure that students secure positions in top companies. The university has an impressive placement record, with graduates being hired by leading multinational corporations such as Google, Deloitte, Microsoft, and Tata Consultancy Services.
The placement team also offers career counseling, soft skills training, and interview preparation to help students present themselves confidently to prospective employers.
Courses Offered at Bennett University
Bennett University offers a diverse range of courses across multiple disciplines:
Engineering: B.Tech (in various specializations including Computer Science, Electronics, and Biotechnology)
Management: BBA, MBA
Law: BA LLB (Hons.), BBA LLB (Hons.)
Media and Liberal Arts: BA (Journalism and Mass Communication), BA Liberal Arts
Doctoral Programs: Ph.D. in various fields
Each program is designed to provide in-depth knowledge while fostering critical thinking and problem-solving skills.
Campus Life at Bennett University
Campus life at Bennett is vibrant, with a wide range of cultural, social, and academic activities. The university organizes frequent guest lectures, workshops, and seminars to enrich students’ learning experiences. Moreover, Bennett has numerous student clubs and societies that cater to a variety of interests, from performing arts to robotics and coding.
Sports enthusiasts also have ample opportunities to engage in activities such as cricket, basketball, football, and swimming. With its blend of academics and extracurricular activities, Bennett University ensures that students develop both personally and professionally.
Why Choose Bennett University?
Choosing Bennett University is about more than just earning a degree. It’s about becoming part of a community that is committed to excellence, innovation, and leadership. With its focus on holistic development, Bennett University ensures that students are prepared to take on challenges, drive change, and lead in their respective fields.
For students looking for a university that offers world-class education, industry exposure, and global opportunities, Bennett University is the perfect choice.
#Bennett University#Quality Higher Education#Global Exposure#education#educationnews#universities#colleges#admissions#mba#higher education#students#imi university#university
2 notes
·
View notes
Text

⟢ - Structure of the 𝐀𝐄𝐓𝐇𝐄𝐑 𝐅𝐎𝐔𝐍𝐃𝐀𝐓𝐈𝐎𝐍

The 𝐀𝐄𝐓𝐇𝐄𝐑 𝐅𝐎𝐔𝐍𝐃𝐀𝐓𝐈𝐎𝐍 operates as a corporation and trust, funding research for various fields of scientific study through grants. It also engages in many different charitable acts related to the rehabilitation and conservation of endangered Pokémon, especially those native to the islands of Alola.
The corporation was founded by current sitting president and CEO, Lusamine Delacroix, with her husband, Mohn Delacroix, serving as vice president until his disappearance. The pair set out to establish a higher standard for how humans, Pokémon and technology can work with one another, while benefiting the natural ecosystems. Aether works alongside many different organizations throughout, and outside of, Alola.
Fields of Interest
The foundation funds projects, research, innovations and expeditions related, but not limited to, conservation, ecology, biochemistry, physics, epidemiology, genetic engineering, and computer engineering. Scientists and scholars from across the globe often seek out the foundation’s funding, traveling to the Aether Paradise in order to meet with members of the board, and Lusamine herself. There is quite the impressive network of intellects connected to the foundation, and it is not unusual to see the Aether seal stamped onto many peer reviewed journals.
Grants and scholarships for students pursuing careers in STEM are also gifted by the Aether Foundation. Many of these students are then placed into internships at the paradise, or in one of the Aether Houses— and funneled into a permanent position of employment upon graduation. The foundation relies on having the most brilliant, cunning minds involved with their projects, and so they make sure to leave a good impression on the scientific community. It is pretty common to see an Aether representative at any major conference involving STEM, or around university campuses.
Working for the Aether Foundation
Employment with the Aether Foundation ranges across different positions— from field researchers, to chemists, to public relations, and many, many more. Those who work at the Aether Paradise work directly with Aether’s conservation programs, vaccination developments, and technology departments. And the genetics program and UB project, if you’re aware of the horrors.
Gaining employment, however, is no simple task. Lusamine expects an impressive resume, and a mind to match, but if somebody passes the hiring process, it is great job security— as long as they do not disappoint her.
All employees are required to sign a non-disclosure agreement upon being hired. All positions are by contract, and salary paid.
All employees are required to submit their biometrics.
The hierarchy
From highest to lowest:
President
Vice President (currently unoccupied)
Branch Manager
Assistant Branch Manager
Divisional Manager
Assistant Divisional Manager
Office Administration
Lead Associate
Associate
Intern
Scientists and research teams are categorized and ranked based on individual projects and assignments.
Accessing the Aether Paradise
If commuting to work, employees have two options: traveling across the water from one of the islands via Aether-owned ferry service, or by helicopter. The ferry service also carries tourists on public access days, so that they can experience the conservation deck, and tour the island.
Aether offers on-site dorms for those who would rather not commute back and forth all week, and for those who are staying on the artificial for an extended period of time for an assignment.
Security
Security is taken very seriously on the island; Lusamine is incredibly strict about it, and intends on keeping it that way.
All employees are assigned key cards, which are required to access all of the rooms and laboratories on the floors one through three.
All of the laboratories and doors on floor three, and in basements 1, 2 and 3 require a fingerprint and retina scan.
Certain high-security areas require two or three employees to use fingerprint or retina scan in order to unlock the door for access.
Higher ranked foundation members and scientists have a chip implanted in their left wrist, which is used as a “master key” to access everything on the Aether Paradise, along with the locks for the Aether House and research stations.
Basements 1, 2 and 3 have safety laser scanners installed that are programmed to scan every room, laboratory and corridor every fifteen minutes. If a persons whose biometrics have not been logged into Aether’s system is picked upon, an alarm goes off, and all doors are locked. Only Aether security guards, or high ranked foundation members, are capable of unlocking the doors in order to remove the intruder.
ALL points of the Aether Paradise have motion sensing cameras and CCTV streaming.
Aether buildings are known for their monochrome coloring and bright fluorescent lights. This is to prevent employees and visitors from finding dark or secluded corners to hide in, and discourages people from attempting to smuggle Aether property. It also makes it easy for visitors to be picked up on by the security cameras; everybody on staff is wearing all white, so somebody who is wearing even the slightest bit of color stands out.
In the case of an emergency, the Aether Paradise is capable of undergoing full lockdown mode. All incoming boats and aircraft are instructed to return to the mainland, and all outgoing forms of transportation are halted.
27 notes
·
View notes
Text
Toward a code-breaking quantum computer
New Post has been published on https://thedigitalinsider.com/toward-a-code-breaking-quantum-computer/
Toward a code-breaking quantum computer

The most recent email you sent was likely encrypted using a tried-and-true method that relies on the idea that even the fastest computer would be unable to efficiently break a gigantic number into factors.
Quantum computers, on the other hand, promise to rapidly crack complex cryptographic systems that a classical computer might never be able to unravel. This promise is based on a quantum factoring algorithm proposed in 1994 by Peter Shor, who is now a professor at MIT.
But while researchers have taken great strides in the last 30 years, scientists have yet to build a quantum computer powerful enough to run Shor’s algorithm.
As some researchers work to build larger quantum computers, others have been trying to improve Shor’s algorithm so it could run on a smaller quantum circuit. About a year ago, New York University computer scientist Oded Regev proposed a major theoretical improvement. His algorithm could run faster, but the circuit would require more memory.
Building off those results, MIT researchers have proposed a best-of-both-worlds approach that combines the speed of Regev’s algorithm with the memory-efficiency of Shor’s. This new algorithm is as fast as Regev’s, requires fewer quantum building blocks known as qubits, and has a higher tolerance to quantum noise, which could make it more feasible to implement in practice.
In the long run, this new algorithm could inform the development of novel encryption methods that can withstand the code-breaking power of quantum computers.
“If large-scale quantum computers ever get built, then factoring is toast and we have to find something else to use for cryptography. But how real is this threat? Can we make quantum factoring practical? Our work could potentially bring us one step closer to a practical implementation,” says Vinod Vaikuntanathan, the Ford Foundation Professor of Engineering, a member of the Computer Science and Artificial Intelligence Laboratory (CSAIL), and senior author of a paper describing the algorithm.
The paper’s lead author is Seyoon Ragavan, a graduate student in the MIT Department of Electrical Engineering and Computer Science. The research will be presented at the 2024 International Cryptology Conference.
Cracking cryptography
To securely transmit messages over the internet, service providers like email clients and messaging apps typically rely on RSA, an encryption scheme invented by MIT researchers Ron Rivest, Adi Shamir, and Leonard Adleman in the 1970s (hence the name “RSA”). The system is based on the idea that factoring a 2,048-bit integer (a number with 617 digits) is too hard for a computer to do in a reasonable amount of time.
That idea was flipped on its head in 1994 when Shor, then working at Bell Labs, introduced an algorithm which proved that a quantum computer could factor quickly enough to break RSA cryptography.
“That was a turning point. But in 1994, nobody knew how to build a large enough quantum computer. And we’re still pretty far from there. Some people wonder if they will ever be built,” says Vaikuntanathan.
It is estimated that a quantum computer would need about 20 million qubits to run Shor’s algorithm. Right now, the largest quantum computers have around 1,100 qubits.
A quantum computer performs computations using quantum circuits, just like a classical computer uses classical circuits. Each quantum circuit is composed of a series of operations known as quantum gates. These quantum gates utilize qubits, which are the smallest building blocks of a quantum computer, to perform calculations.
But quantum gates introduce noise, so having fewer gates would improve a machine’s performance. Researchers have been striving to enhance Shor’s algorithm so it could be run on a smaller circuit with fewer quantum gates.
That is precisely what Regev did with the circuit he proposed a year ago.
“That was big news because it was the first real improvement to Shor’s circuit from 1994,” Vaikuntanathan says.
The quantum circuit Shor proposed has a size proportional to the square of the number being factored. That means if one were to factor a 2,048-bit integer, the circuit would need millions of gates.
Regev’s circuit requires significantly fewer quantum gates, but it needs many more qubits to provide enough memory. This presents a new problem.
“In a sense, some types of qubits are like apples or oranges. If you keep them around, they decay over time. You want to minimize the number of qubits you need to keep around,” explains Vaikuntanathan.
He heard Regev speak about his results at a workshop last August. At the end of his talk, Regev posed a question: Could someone improve his circuit so it needs fewer qubits? Vaikuntanathan and Ragavan took up that question.
Quantum ping-pong
To factor a very large number, a quantum circuit would need to run many times, performing operations that involve computing powers, like 2 to the power of 100.
But computing such large powers is costly and difficult to perform on a quantum computer, since quantum computers can only perform reversible operations. Squaring a number is not a reversible operation, so each time a number is squared, more quantum memory must be added to compute the next square.
The MIT researchers found a clever way to compute exponents using a series of Fibonacci numbers that requires simple multiplication, which is reversible, rather than squaring. Their method needs just two quantum memory units to compute any exponent.
“It is kind of like a ping-pong game, where we start with a number and then bounce back and forth, multiplying between two quantum memory registers,” Vaikuntanathan adds.
They also tackled the challenge of error correction. The circuits proposed by Shor and Regev require every quantum operation to be correct for their algorithm to work, Vaikuntanathan says. But error-free quantum gates would be infeasible on a real machine.
They overcame this problem using a technique to filter out corrupt results and only process the right ones.
The end-result is a circuit that is significantly more memory-efficient. Plus, their error correction technique would make the algorithm more practical to deploy.
“The authors resolve the two most important bottlenecks in the earlier quantum factoring algorithm. Although still not immediately practical, their work brings quantum factoring algorithms closer to reality,” adds Regev.
In the future, the researchers hope to make their algorithm even more efficient and, someday, use it to test factoring on a real quantum circuit.
“The elephant-in-the-room question after this work is: Does it actually bring us closer to breaking RSA cryptography? That is not clear just yet; these improvements currently only kick in when the integers are much larger than 2,048 bits. Can we push this algorithm and make it more feasible than Shor’s even for 2,048-bit integers?” says Ragavan.
This work is funded by an Akamai Presidential Fellowship, the U.S. Defense Advanced Research Projects Agency, the National Science Foundation, the MIT-IBM Watson AI Lab, a Thornton Family Faculty Research Innovation Fellowship, and a Simons Investigator Award.
#2024#ai#akamai#algorithm#Algorithms#approach#apps#artificial#Artificial Intelligence#author#Building#challenge#classical#code#computer#Computer Science#Computer Science and Artificial Intelligence Laboratory (CSAIL)#Computer science and technology#computers#computing#conference#cryptography#cybersecurity#defense#Defense Advanced Research Projects Agency (DARPA)#development#efficiency#Electrical Engineering&Computer Science (eecs)#elephant#email
5 notes
·
View notes