#Metasploit Web Delivery
Explore tagged Tumblr posts
Text
The government decided on Thursday to extradite to the United States an Estonian citizen, Andrey Shevlyakov, who is suspected by the Federal Bureau of Investigation (FBI) of procuring US-made electronic equipment for the Russian military.
Shevlyakov was detained by Estonia's Internal Security Service in March last year at the request of the FBI and has been in custody since then.
Justice Minister Liisa-Ly Pakosta told a government press conference on Thursday that the government made the decision to extradite Andrey Shevlyakov to the United States, but Shevlyakov is likely to use the opportunity to appeal the decision.
FBI Houston announced on social media in April 2023 that in cooperation with the Bureau of Industry and Security of the US Department of Commerce and Estonian Internal Security Service, a man who allegedly procured US-made electronics on behalf of the Russian government and military for more than a decade had been arrested.
Special agent in charge James Smith said that the Estonian citizen, Andrey Shevlyakov, was arrested on March 28 of that year on suspicion of procuring US-made electronics, including radar components and hacking software, on behalf of the Russian government and military.
«For years, Mr Shevlyakov's elaborate web of deceit allowed him to allegedly procure sensitive American-made electronics on behalf of the Russian military. His illegal acquisitions of sophisticated US technology endangered citizens in both Ukraine and the United States,» Smith said. The announcement says that at the time of his arrest, deliveries meant for Shevlyakov in Estonia, including 130 kilograms of radio equipment, were confiscated.
Shevlyakov purchased multiple items, including low-noise pre-scalers and synthesizers, used to conduct high-frequency communications, and analog-to-digital converters, which are components used in defense systems such as electronic warfare systems and missiles. In May 2020, Shevlyakov used one of his front companies to buy a licensed copy of the penetration testing platform Metasploit Pro. Shevlyakov allegedly exported at least 800,000 US dollars worth of items from US electronics manufacturers and distributors between approximately October 2012 and January 2022.
Shevlyakov engaged in this conduct despite being listed on a Department of Commerce-maintained list, known as the Entity List, that designates individuals and companies who are barred from exporting items from the United States without a license. He used false names and a web of front companies to evade the Entity List's restrictions.
If convicted, he faces a maximum of 20 years' imprisonment.
2 notes
·
View notes
Text
PasteJacker - Add PasteJacking To Web-Delivery Attacks
PasteJacker - Add PasteJacking To Web-Delivery Attacks #Pastejacking #hacking #windows #linux
The main purpose of the tool is automating (PasteJacking/Clipboard poisoning/whatever you name it) attack with collecting all the known tricks used in this attack in one place and one automated job as after searching I found there’s no tool doing this job the right way. Now while this attack depends on what the user will paste, imagine adding this attack to Metasploitweb delivery module. See this…
View On WordPress
#hacking tool#linux#mac#metasploit#Metasploit Web Delivery#Meterpreter#PasteJacker#PasteJacking#penetration testing#python3#social engineering attacks#Web Hacking#windows hacking
0 notes
Text
AutoRDPwn The Shadow Attack Framework. Script created in #Powershell and designed to...
AutoRDPwn The Shadow Attack Framework. Script created in #Powershell and designed to automate the Shadow attack on Microsoft Windows computers. This vulnerability allows a remote attacker to view his/her victim's desktop without his/her consent, and even control it on request. For its correct operation, it is necessary to comply with the requirements described in the user guide. Requirements of AutoRDPwn: PowerShell 4.0 or higher. What's new in AutoRDPwn version 5.0: 1. Compatibility with PowerShell 4.0. 2. Automatic copy of the content to the clipboard (passwords, hashes, dumps, etc). 3. Automatic exclusion in Windows Defender (4 different methods). 4. Remote execution without password for PSexec, WMI, and Invoke-Command. 5. New available attack: DCOM Passwordless Execution. 6. New available module: Remote Access / Metasploit Web Delivery. 7. New module available: Remote VNC Server (designed for legacy environments). 8. Autocomplete the host, user, and password fields by pressing Enter. 9. It is now possible to run the tool without administrator privileges with the -noadmin parameter. https://github.com/JoelGMSec/AutoRDPwn

-
0 notes
Photo

Sesión meterpreter de WIN10 recibida mediante exploit web delivery lanzado a través del módulo Shell de ST. #pentesting #malware #technology #hackerman #vulnerabilityassessment #computer #code #metasploit #jaymonsecurity #microsoft #fortnite #hackingtools #amazon #cybercrime #ceh #webdevelopper #web #vpn #facebookhack #pentester #informationsecurity #dataprotection #internet #instagram #carder #software #hackerspace #cyberattack #windows #linux (en Madrid, Spain) https://www.instagram.com/p/B5OGPPniQBx/?igshid=1uj593cwpyo7c
#pentesting#malware#technology#hackerman#vulnerabilityassessment#computer#code#metasploit#jaymonsecurity#microsoft#fortnite#hackingtools#amazon#cybercrime#ceh#webdevelopper#web#vpn#facebookhack#pentester#informationsecurity#dataprotection#internet#instagram#carder#software#hackerspace#cyberattack#windows#linux
0 notes
Photo

Metasploit Hacking Windows Meterpreter Reverse HTTPS(MSF Venom)
Metasploits Web Delivery Script is a versatile module that creates a server on the attacking machine which hosts a payload. When the victim connects to the attacking server, the payload will be executed on the victim machine.
http://www.techtrick.in/Description/3490-metasploit-hacking-windows-meterpreter-reverse-https
0 notes
Text
How To: Use Metasploit's Web Delivery Script & Command Injection to Pop a Shell
One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were … source https://null-byte.wonderhowto.com/how-to/use-metasploits-web-delivery-script-command-injection-pop-shell-0189130/
0 notes
Text
Command Injection Exploitation using Web Delivery (Linux, Windows)
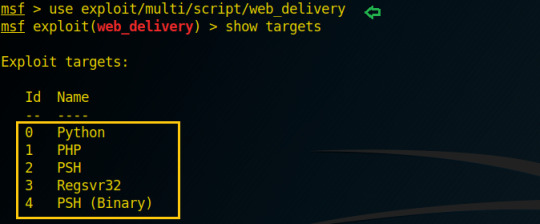
Hello friends! In this article you will learn how to exploit three different platform [Linux, windows, using single exploit of metasploit framework.
Requirement
Attacker:Kali Linux
Targeted platform: Window,PHP,Linux[ubuntu]
Open the terminal in your kali Linux and type “msfconsole” to load metasploit framework and execute given below exploit.
This module quickly fires up a web server that serves…
View On WordPress
0 notes
Text
Original Post from Rapid7 Author: Jeffrey Martin
First!!
Congrats to Nick Tyrer for the first community contibuted evasion module to land in master. Nick’s evasion/windows/applocker_evasion_install_util module leverages the trusted InstallUtil.exe binary to execute user supplied code and evade application whitelisting.
New modules (4)
WP Database Backup RCE by Mikey Veenstra / Wordfence and Shelby Pace. which exploits a command injection vulnerability in wp-database-backup versions < v5.2.
Schneider Electric Pelco Endura NET55XX Encoder by Lucas Dinucci and Vitor Esperança, which exploits CVE-2019-6814
Ahsay Backup v7.x-v8.1.1.50 (authenticated) file upload by Wietse Boonstra, which exploits CVE-2019-10267
Applocker Evasion – .NET Framework Installation Utility by Casey Smith and Nick Tyrer, which is designed to evade solutions such as software restriction policies and Applocker.
Enhancements and features
Enhanced Web Delivery by bcoles. The multi/script/web_delivery module has been expanded to support pubprn for Windows delivery & directly support Linux as a target platform.
Hostname Keyed XOR by O . S . O. Linux payloads can now be XOR encoded based on target hostname, resticting the payload abort when executed on an unintended system.
Improved msfvenom hex encodiing by wvu. Payload encoding by msfvenom output allows character literals interleaved with escaped hex when using --bad-chars and --encrypt-key options.
Bugs fixed
RHOSTS handling for non-scanner auxiliary by Green-m. When executing non-scanner auxiliary modules using RHOSTS all targets are now processed.
Get it
As always, you can update to the latest Metasploit Framework with msfupdate and you can get more details on the changes since the last blog post from GitHub:
Pull Requests 5.0.37…5.0.38
Full diff 5.0.37…5.0.38
We recently announced the release of Metasploit 5. You can get it by cloning the Metasploit Framework repo (master branch). To install fresh without using git, you can use the open-source-only Nightly Installers or the binary installers (which also include the commercial editions).
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Jeffrey Martin Metasploit Wrap-Up Original Post from Rapid7 Author: Jeffrey Martin First!! Congrats to Nick Tyrer for the first community contibuted evasion module to land in master.
0 notes
Text
COMP6441 Something Awesome Blog - 5
Web delivery is a concept I attempted to explore further. If I can initiate a connection on the defending device to my device then I can avoid a lot of other issues like authentication.
Web delivery can be achieved by using the Metasploit Framework on Ubuntu. This was pretty complicated. It took a lot of reading to understand how to configure the msfconsole and what variables to set. There was a point where I couldn’t understand why the connection wasn’t working and I realised that my firewall was blocking the connection from the defender to my laptop.
Additionally a lot of options are provided on possible exploits, in the end I dug deeper into reverse https and reverse tcp. Both methods create a one line powershell command that if run on the defending PC will initiate initiate a connection and allow me access to download and view their data.
Combing this with what I learnt from JackIt, I should be able to send these one liners through the mouse dongle and execute in on their computer.
Currently I have been unsuccessful in creating a proper connection and I’m not sure why. The console states that its delivering the payload but the connection never gets set up (even after an hour).
I will include all of these issues and fixes (if found), as well as screenshots, in my final report.
0 notes
Text
Dark Side Ops I & 2 Review
Dark Side Ops I https://silentbreaksecurity.com/training/dark-side-ops/ https://www.blackhat.com/us-17/training/dark-side-ops-custom-penetration-testing.html
A really good overview of the class is here https://www.ethicalhacker.net/features/root/course-review-dark-side-ops-custom-penetration-testing
I enjoyed the class. This was actually my second time taking the class and it wasn't nearly as overwhelming the 2nd time :-)
I’ll try not to cover what is in Raphael’s article as it is still applicable and I am assuming you read it before continuing on.
I really enjoyed the VisualStudio time and building Slingshot and Throwback myself along with getting a taste for extending the implant by adding the keylogger, mimikatz, and hashdump modules.
Windows API developers may be able to greatly extend slingshot but I don't think I have enough WinAPI kung fu to do it and there wasn’t enough setup around the “how” to consistently do it either unless you have a strong windows API background. However, one of the labs consisted of adding load and run powershell functionality which allows you to make use of the plethora of powershell code out there.
There was also a great lab where we learned how to pivot through a compromised SOHO router and the technique could also be extended for VPS or cloud providers.
Cons of the class.
The visual studio piece can get overwhelming but it definitely gives you a big taste of (Windows) implant development. The class material are getting slightly dated in some cases. A refresh might be helpful. More Throwback usage & development would be fun (even as optional labs).
DSO II https://silentbreaksecurity.com/training/dark-side-ops-2-adversary-simulation/ https://www.blackhat.com/us-17/training/dark-side-ops-ii-adversary-simulation.html
Lab one was getting a fresh copy of slingshot back up and running and then setting up some additional code to do a powershell web cradle to get our slingshot implant up and running on a remote host. Similar to how metasploit web delivery does things.
Lab 2 was doing some devops to set up servers, OpenVPN to tunnel traffic, and adding HTTPS to our slingshot codebase.
Lab 3 was some Initial activity labs (HTA and chrome plugin exploitation)
Lab 4 was tweaking our HTA to defeat some common detections and protections. We also worked on code to do sandbox evasions as it’s becoming more common for automated sandbox solutions to be tied to mail gateways or just for people doing response.
Lab 5 whitelist bypassing
Lab 6 was doing some profiling via powershell and using slingshot to be able to do checks on the host
Labs 7-9 building a kernel rootkit
Lab 10 persistence via COM Hijacking and hiding our custom DLL in the registry and Lab 11 was privilege escalation via custom service.
Final Thoughts
I enjoyed the four days and felt like I learned a lot. So the TLDR is that I recommend taking the class(es).
Criticisms: I think the set of courses are having a bit of an identity crisis mostly due to the 2 day format and would be a much better class as a 5 day. It is heavy development focused meaning you spend a lot of time in Visual Studio tweaking C code. The “operations” piece of the course definitely suffers a bit due to all the dev time. There was minimal talk around lateral movement and the whole thing is entirely Windows focused so no Linux and no OSX. A suggestion to fix the “ops” piece would be to have a Dark Side Ops - Dev and Dark Side Ops - Operator courses where the dev one is solely deving your implant and the Operator course would be solely using the implant you dev’d (or was provided to you). The Silent Break team definitely knows their stuff and a longer class format or switch up would allow them to showcase that more efficiently.
The post Dark Side Ops I & 2 Review appeared first on Security Boulevard.
from Dark Side Ops I & 2 Review
0 notes
Text
The government decided on Thursday to extradite to the United States an Estonian citizen, Andrey Shevlyakov, who is suspected by the Federal Bureau of Investigation (FBI) of procuring US-made electronic equipment for the Russian military.
Shevlyakov was detained by Estonia's Internal Security Service in March last year at the request of the FBI and has been in custody since then.
Justice Minister Liisa-Ly Pakosta told a government press conference on Thursday that the government made the decision to extradite Andrey Shevlyakov to the United States, but Shevlyakov is likely to use the opportunity to appeal the decision.
FBI Houston announced on social media in April 2023 that in cooperation with the Bureau of Industry and Security of the US Department of Commerce and Estonian Internal Security Service, a man who allegedly procured US-made electronics on behalf of the Russian government and military for more than a decade had been arrested.
Special agent in charge James Smith said that the Estonian citizen, Andrey Shevlyakov, was arrested on March 28 of that year on suspicion of procuring US-made electronics, including radar components and hacking software, on behalf of the Russian government and military.
«For years, Mr Shevlyakov's elaborate web of deceit allowed him to allegedly procure sensitive American-made electronics on behalf of the Russian military. His illegal acquisitions of sophisticated US technology endangered citizens in both Ukraine and the United States,» Smith said. The announcement says that at the time of his arrest, deliveries meant for Shevlyakov in Estonia, including 130 kilograms of radio equipment, were confiscated.
Shevlyakov purchased multiple items, including low-noise pre-scalers and synthesizers, used to conduct high-frequency communications, and analog-to-digital converters, which are components used in defense systems such as electronic warfare systems and missiles. In May 2020, Shevlyakov used one of his front companies to buy a licensed copy of the penetration testing platform Metasploit Pro. Shevlyakov allegedly exported at least 800,000 US dollars worth of items from US electronics manufacturers and distributors between approximately October 2012 and January 2022.
Shevlyakov engaged in this conduct despite being listed on a Department of Commerce-maintained list, known as the Entity List, that designates individuals and companies who are barred from exporting items from the United States without a license. He used false names and a web of front companies to evade the Entity List's restrictions.
If convicted, he faces a maximum of 20 years' imprisonment.
2 notes
·
View notes
Text
Highest Paying Software Jobs

The world of software jobs is a vast and ever-expanding field, with numerous career options and opportunities. In today's digital era, software professionals play a crucial role in advancing technology and shaping the future. This article explores some of the highest-paying software jobs within various domains. Artificial Intelligence and Machine Learning Engineer Artificial Intelligence (AI) and Machine Learning (ML) have gained immense popularity and have rapidly become essential in many industries. AI and ML engineers contribute to the development of intelligent systems that can learn, adapt, and make decisions. These professionals possess a deep understanding of algorithms, data structures, and statistical methods. To excel in this role, individuals must have strong programming skills, proficiency in Python or R, and familiarity with libraries like TensorFlow or PyTorch. Additionally, expertise in handling large datasets and knowledge of neural networks and deep learning algorithms are crucial. AI and ML engineers are in high demand due to the increasing integration of intelligent systems in various sectors. Their salaries often reach six figures, making it one of the most lucrative careers in software. Data Scientist The role of a data scientist revolves around extracting valuable insights from vast amounts of data. In an era where data is rapidly expanding, organizations rely on data scientists to make informed decisions and predictions. These professionals work with analytics tools, programming languages, and statistical models to extract meaningful patterns from data. To excel in this field, individuals need expertise in statistics, data visualization, programming, and machine learning algorithms. Proficiency in tools like SQL, Python, R, and Tableau is highly valuable. Data science offers highly promising career prospects with lucrative salaries. As businesses increasingly depend on data-driven strategies, skilled data scientists remain in high demand across multiple industries. Cybersecurity Analyst With the exponential rise in cyber threats, cybersecurity has become a critical concern for organizations worldwide. Cybersecurity analysts are responsible for protecting systems, networks, and data from unauthorized access and vulnerabilities. They assess security risks, conduct penetration tests, and implement effective security measures. Professionals in this field must possess knowledge of cybersecurity principles, secure coding practices, and network security protocols. Familiarity with tools like Wireshark, Nessus, and Metasploit is advantageous. As cybersecurity breaches continue to make headlines, the demand for skilled cybersecurity analysts is rapidly increasing. These professionals can earn substantial salaries, reflecting the critical nature of their work. Cloud Architect Cloud computing has revolutionized the way businesses operate by providing flexible and scalable IT infrastructure. Cloud architects are responsible for designing and implementing cloud-based systems that meet specific organizational needs. They specialize in cloud platforms such as Amazon Web Services (AWS), Microsoft Azure, or Google Cloud. To succeed as a cloud architect, individuals should possess knowledge of cloud computing concepts, virtualization, and infrastructure management. Certifications, such as AWS Certified Solutions Architect, demonstrate expertise in cloud technologies. With more organizations adopting cloud-based solutions, the demand for skilled cloud architects is on the rise. These professionals enjoy high salaries and excellent career growth opportunities. DevOps Engineer DevOps engineers bridge the gap between software development and operations, ensuring smooth collaboration and efficient delivery of software products. They automate processes, configure infrastructure, and monitor system performance to support the development and deployment lifecycle. To thrive in a DevOps role, individuals must have expertise in scripting languages, infrastructure automation tools (e.g., Docker, Kubernetes), and knowledge of continuous integration/continuous deployment (CI/CD) pipelines. Strong communication and problem-solving skills are also essential. The demand for DevOps engineers is rapidly growing as organizations strive for faster software delivery and improved collaboration. These professionals are highly valued and rewarded with attractive salaries. Software Development Manager Software development managers oversee the entire development process, ensuring projects are delivered on time and meet the required quality standards. They manage development teams, prioritize tasks, and coordinate with stakeholders to achieve business goals. Apart from technical knowledge, software development managers should possess excellent leadership, communication, and project management skills. Experience in software development and a deep understanding of the development life cycle are essential for success in this role. While salaries may vary based on experience and the size of the organization, software development managers have the potential to earn high incomes. This profession offers a balance between technical expertise and people management skills. Conclusion Software jobs provide immense opportunities for individuals with the right skills and passion for technology. The highest-paying software jobs discussed in this article represent a fraction of the countless possibilities available in the industry. Pursuing a career in these domains can lead to not only financial success but also personal growth and contribution to the ever-evolving technological landscape. FAQs How to get started in the software industry? To start a career in the software industry, you can acquire a relevant degree or certification in programming or computer science. Additionally, gaining practical experience through internships or personal projects can significantly boost your chances. Are these jobs only available in tech giants? No, these jobs are not limited to tech giants. While big companies may offer higher salaries, software jobs can be found in various industries and organizations of all sizes. Do these jobs require formal education or specific degrees? While a formal education in computer science or a related field can be beneficial, some software jobs prioritize practical skills and experience over formal degrees. It is essential to continuously learn and update your skills to stay competitive. Can software jobs be done remotely? Yes, remote work opportunities have become increasingly common in the software industry. Many companies offer flexible work arrangements, allowing professionals to work remotely. How is the job market for software professionals? The job market for software professionals is highly favorable. The demand for skilled software developers, engineers, and analysts continues to grow, offering numerous career opportunities and attractive salaries. Read the full article
0 notes
Text
Microsoft Office DDE Payload Delivery
This Metasploit module generates an DDE command to place within a word document, that when executed, will retrieve a HTA payload via HTTP from an web server. Source: Microsoft Office DDE Payload Delivery The post Microsoft Office DDE Payload Delivery appeared first on MondoUnix.
View On WordPress
0 notes
Text
PasteJacker The main purpose of the tool is automating (PasteJacking/Clipboard...
PasteJacker The main purpose of the tool is automating (PasteJacking/Clipboard poisoning/whatever you name it) attack with collecting all the known tricks used in this attack in one place and one automated job as after searching I found there's no tool doing this job the right way 😄 Now because this attack depends on what the user will paste, I implemented the Metasploit web-delivery module's idea into the tool so when the user pastes into the terminal, you gets meterpreter session on his device 😄 https://github.com/D4Vinci/PasteJacker Demo: https://www.youtube.com/watch?v=FfMoCPVjF5Y #cybersecurity #soft #attack #pastejacking #clipboard

-
1 note
·
View note
Photo

Sesión meterpreter de WIN10 recibida mediante exploit web delivery lanzado a través del módulo Shell de ST. #pentesting #malware #technology #hackerman #vulnerabilityassessment #computer #code #metasploit #jaymonsecurity #microsoft #fortnite #hackingtools #amazon #cybercrime #ceh #webdevelopper #web #vpn #facebookhack #pentester #informationsecurity #dataprotection #internet #instagram #carder #software #hackerspace #cyberattack #windows #linux (en Madrid, Spain) https://www.instagram.com/p/B5OGPPniQBx/?igshid=18gxqvdjo69bb
#pentesting#malware#technology#hackerman#vulnerabilityassessment#computer#code#metasploit#jaymonsecurity#microsoft#fortnite#hackingtools#amazon#cybercrime#ceh#webdevelopper#web#vpn#facebookhack#pentester#informationsecurity#dataprotection#internet#instagram#carder#software#hackerspace#cyberattack#windows#linux
0 notes
Photo

Hack Remote Windows PC using Script Web Delivery
Metasploits Web Delivery Script is a versatile module that creates a server on the attacking machine which hosts a payload. When the victim connects to the attacking server, the payload will be executed on the victim machine.
http://www.techtrick.in/Description/3479-hack-remote-windows-pc-using-script-web-delivery
0 notes