#Metasploit auxiliary modules
Explore tagged Tumblr posts
Text
A Full Look at the Top 10 Cybersecurity Software Tools

IT experts use cybersecurity tools to set up different authentication or permission systems that keep an organization's data and business systems safe from cyber threats. Let's learn more about why cybersecurity tools are essential, the different kinds of tools that are out there, and the best tools that are out there to fight cybersecurity dangers. In the digital world we live in now, cybersecurity is essential for both businesses and people. Solid tools and software are needed to keep private data safe from cyber threats. Take a close look at the top 10 safety software tools below. Each one is significant for keeping digital spaces safe. Top 10 Cybersecurity Software Tools Wireshark Website - Link A lot of people use Wireshark, a network protocol analyzer that lets them record and browse interactively through computer network data. It is a must-have tool for developers, network managers, and security experts who need to look into and fix network problems. Wireshark can break down hundreds of protocols and give you a lot of information about each message it captures. It can record live videos and analyze data later so that it can be used in a variety of situations. Wireshark is the only tool that can deeply inspect hundreds of protocols, record in real-time, and analyze data later on. It can also decode a lot of different protocols, such as IPsec, ISAKMP, Kerberos, and SSL/TLS. Top Features: Network analysis and protocol review in real-time A thorough look at VoIP Analysis of collected data when not connected to the internet Rich display filters for accurate traffic separation Support for many capture file formats Metasploit Website - Link Powerful testing tool Metasploit lets security experts find flaws in their systems. Widely applied for both defensive and offensive security testing, it enables users to replicate real-world attacks to find security flaws. The Metasploit Framework presents a set of tools meant for testing a network's security. It comprises an extensive database of exploits, payloads, and auxiliary modules capable of attacking targets and pointing up weaknesses. Furthermore offering a framework for creating and testing custom exploits is Metasploit. Top Features: Complete catalog of discovered vulnerabilities in databases automated examinations of vulnerabilities Combining with other security instruments for a more thorough investigation Support for a broad spectrum of running systems and programs Updates and assistance driven by communities Bitdefender Website - link Bitdefender is one of the best pieces of safety software. It protects you from viruses, malware, ransomware, and phishing attacks, among other things. The fact that it protects both endpoints and networks makes it a complete option for both individuals and businesses. Bitdefender uses cutting-edge machine-learning techniques to find and stop threats as they happen. It also has a strong firewall, advanced threat defense, and multiple layers of security against ransomware. Bitdefender's GravityZone platform lets you control endpoint protection from one place, which makes setting up and managing security policies across extensive networks easier. Top Features: Advanced ways to find and deal with threats Encryption and protection of info in real-time Easy-to-use interface and multiple layers of ransomware defence Management and release from one place Updates often to deal with new threats Kali Linux Website - Link Kali Linux is a Linux distribution built on Debian that is made for digital forensics and penetration testing. A lot of security tools are already installed on it, which makes it an essential toolkit for security professionals. Kali Linux has tools for many information security jobs, like reverse engineering, penetration testing, security research, and computer forensics. It's known for being easy to use and having a lot of information on how to do it, so both new users and seasoned workers can use it. Top Features: More than 600 tools for security testing Open-source and flexible Updates often to deal with new security threats A lot of community help and a lot of paperwork How to do forensic research and reverse engineering with these tools Nmap Website - Link Network Mapper, or Nmap, is a powerful open-source tool used to find networks and check their security. This tool is very flexible and can be used to find hosts and services on a network, making a "map" of the network. Network inventory, controlling service upgrade schedules, and keeping an eye on host or service uptime can all be done with Nmap. It has many tools for studying networks, such as finding hosts, scanning ports, finding versions, and finding operating systems. Top Features: Find and list hosts and services Finding the OS and the version Taking inventory of the network, setting up upgrade plans for services, and keeping an eye on host or service uptime Flexible, expandable, and quick scans There are both graphical and command-line tools Fortinet Website - Link Fortinet offers a complete security system known for its cutting-edge routers, endpoint security, and advanced threat defence. It gives organizations a unified way to handle security and helps them fight complicated cyber threats. Firewalls, intrusion prevention systems, secure web gateways, and endpoint protection are just some of the security options that are built into Fortinet's Security Fabric platform. Artificial intelligence and machine learning are used to find problems and stop them in real-time. Top Features: Threat defence that works well Security options based on AI strategy to cybersecurity that is both integrated and automated The ability for big businesses to grow Reporting and data for everything Nessus Website - link One of the most well-known vulnerability testers in the world is Nessus. It helps security experts find and fix holes in the network's defences, keeping the security up to date. Nessus has many tools for checking for vulnerabilities, such as configuration auditing, malware detection, finding private data, and compliance checking. It gives organizations thorough reports that help them decide which vulnerabilities to fix first and how to do it most effectively. Top Features: Reporting and checking for vulnerabilities in detail Simple to connect to other programs Always-updated collection of vulnerabilities Complete audits of compliance Automation tools and an easy-to-use interface Snort Website - link It is a free intrusion detection system (IDS) and intrusion prevention system (IPS). The software can analyze data in real-time and log packets on IP networks. Snort finds many types of attacks, like buffer overflows, secret port scans, and CGI attacks, by using signature-based, protocol-based, and anomaly-based inspection methods together. It can be changed in a lot of ways and can be combined with other security tools to make finding and stopping threats even better. Top Features: Analysis of traffic in real-time Searching for information and analyzing protocols Detection of different threats, such as buffer overflows and stealth port scans Language with flexible rules for setting up traffic patterns Large amounts of logging and reporting options Splunk Website - link Searching, monitoring, and analysing machine-generated extensive data via a web-based interface is powerfully enabled by Splunk. It is applied heavily in security information and event management (SIEM). Splunk makes searching and analysis of vast amounts of data simpler by gathering and indexing data from many sources—including logs, events, and metrics. The real-time data and sophisticated analytics it offers enable companies to identify and address security events immediately. Top Features: Real-time data analysis and monitoring Proactive threat detection using advanced analytics thorough security knowledge and documentation Scalability in big businesses Integration spanning a large spectrum of data sources Symantec Website - Link Renowned cybersecurity firm Symantec sells email security, data loss prevention, and endpoint protection, among other security products. It offers vital fixes to guard against advanced cyberattacks. Advanced threat prevention, detection, and response capabilities abound on Symantec's endpoint protection system. Using artificial intelligence and machine learning, it finds and stops dangers before they may inflict damage. Additionally provided by Symantec are solutions for information security, web security, and cloud security. Top Features: Complete endpoint security advanced threat protection Encryption and data loss avoidance Web security solutions and cloud security Reporting under centralized management Conclusion These cybersecurity instruments are essential in the fight against cyber threats since they have unique qualities and abilities. Organizations can improve their security posture and more effectively safeguard their necessary resources by using these technologies. Read the full article
0 notes
Text
Essential Hacking Tools for Ethical Hackers
In the realm of cybersecurity, ethical hackers play a pivotal role in identifying vulnerabilities and safeguarding systems. To effectively carry out their tasks, ethical hackers rely on a range of tools that aid in security assessment, network analysis, and vulnerability exploitation. This article highlights some indispensable hacking tools that ethical hackers can consider incorporating into their arsenal.

Enhancing your career at the Ethical Hacking Course in Chennai entails taking a systematic strategy and looking into enrolling in a suitable course that will greatly expand your learning journey while harmonizing with your preferences.
Some Of The Top Ethical Hacking Tools That Hackers Can Consider Are Listed Below:
Metasploit Framework: Metasploit Framework, an open-source tool, is a go-to solution for penetration testing and vulnerability assessment. With its extensive repository of exploits, payloads, and auxiliary modules, it equips ethical hackers with a comprehensive suite of tools for identifying and exploiting system vulnerabilities.
Nmap: Nmap (Network Mapper) is a versatile and powerful network scanning tool utilized for network discovery, identifying open ports, and gathering system information. Its customizable nature and wide range of scanning techniques make it an essential tool for network reconnaissance and vulnerability assessment.
Wireshark: Wireshark, a popular network protocol analyzer, enables ethical hackers to capture and analyze network traffic. By inspecting packets and detecting security vulnerabilities, it aids in troubleshooting network issues. Wireshark's support for numerous protocols and its ability to provide detailed network traffic information make it invaluable for network analysis and security assessment.

For those looking to hacking, Ethical Hacking Online Training is highly suggested. Look for classes that align with your preferred learning approach.
Burp Suite: Burp Suite, a comprehensive web application security testing tool, encompasses various modules for intercepting and modifying HTTP requests, scanning for vulnerabilities, and analyzing application security. Its advanced features and user-friendly interface have established it as a favored tool for ethical hackers engaged in web application penetration testing.
John the Ripper: John the Ripper is a potent password cracking tool employed by ethical hackers to evaluate password strength. It offers multiple password cracking techniques, including brute force, dictionary attacks, and rainbow table attacks. With its comprehensive capabilities, it aids in assessing password security and identifying weak passwords.
Aircrack-ng: Aircrack-ng consists of a collection of tools specifically designed for assessing and cracking wireless network security. It facilitates packet capturing, wireless protocol analysis, and attacks against Wi-Fi networks. Ethical hackers rely on Aircrack-ng to test the security of wireless networks and uncover vulnerabilities in Wi-Fi implementations.
Ethical hackers require a diverse range of tools to effectively assess and secure systems. The aforementioned tools are just a few examples among the vast array of options available.
As technology advances and new threats emerge, ethical hackers must stay abreast of the latest tools and techniques to ensure the security of systems and networks.
1 note
·
View note
Text
Essential Hacking Tools for Ethical Hackers
In the realm of cybersecurity, ethical hackers play a pivotal role in identifying vulnerabilities and safeguarding systems. To effectively carry out their tasks, ethical hackers rely on a range of tools that aid in security assessment, network analysis, and vulnerability exploitation. This article highlights some indispensable hacking tools that ethical hackers can consider incorporating into their arsenal.
Enhancing your career at the Ethical Hacking Course in Chennai entails taking a systematic strategy and looking into enrolling in a suitable course that will greatly expand your learning journey while harmonizing with your preferences.

Some Of The Top Ethical Hacking Tools That Hackers Can Consider Are Listed Below:
Metasploit Framework: Metasploit Framework, an open-source tool, is a go-to solution for penetration testing and vulnerability assessment. With its extensive repository of exploits, payloads, and auxiliary modules, it equips ethical hackers with a comprehensive suite of tools for identifying and exploiting system vulnerabilities.
Nmap: Nmap (Network Mapper) is a versatile and powerful network scanning tool utilized for network discovery, identifying open ports, and gathering system information. Its customizable nature and wide range of scanning techniques make it an essential tool for network reconnaissance and vulnerability assessment.
Wireshark: Wireshark, a popular network protocol analyzer, enables ethical hackers to capture and analyze network traffic. By inspecting packets and detecting security vulnerabilities, it aids in troubleshooting network issues. Wireshark's support for numerous protocols and its ability to provide detailed network traffic information make it invaluable for network analysis and security assessment.
For those looking to hacking, Ethical Hacking Online Training is highly suggested. Look for classes that align with your preferred learning approach.
Burp Suite: Burp Suite, a comprehensive web application security testing tool, encompasses various modules for intercepting and modifying HTTP requests, scanning for vulnerabilities, and analyzing application security. Its advanced features and user-friendly interface have established it as a favored tool for ethical hackers engaged in web application penetration testing.
John the Ripper: John the Ripper is a potent password cracking tool employed by ethical hackers to evaluate password strength. It offers multiple password cracking techniques, including brute force, dictionary attacks, and rainbow table attacks. With its comprehensive capabilities, it aids in assessing password security and identifying weak passwords.
Aircrack-ng: Aircrack-ng consists of a collection of tools specifically designed for assessing and cracking wireless network security. It facilitates packet capturing, wireless protocol analysis, and attacks against Wi-Fi networks. Ethical hackers rely on Aircrack-ng to test the security of wireless networks and uncover vulnerabilities in Wi-Fi implementations.
Ethical hackers require a diverse range of tools to effectively assess and secure systems. The aforementioned tools are just a few examples among the vast array of options available.
As technology advances and new threats emerge, ethical hackers must stay abreast of the latest tools and techniques to ensure the security of systems and networks.
0 notes
Text
“Ethical Hacking Toolbox: Essential Tools and Strategies”
Essential Tools for Ethical Hacking

Ethical hackers rely on a variety of tools and software to effectively identify and assess vulnerabilities in computer systems and networks. These tools are essential for conducting successful ethical hacking engagements. Let’s explore some of the key tools used in the field:
1. Nmap (Network Mapper) Nmap is a versatile open-source tool that serves as a network scanner and mapper. It excels in discovering open ports, services, and operating systems running on a network. Nmap’s extensive capabilities make it a fundamental tool for reconnaissance and vulnerability assessment.
2. Wireshark Wireshark is a widely-used network protocol analyzer, enabling ethical hackers to monitor and capture data on a network in real time. With its packet-sniffing capabilities, Wireshark helps in analyzing network traffic, identifying potential security issues, and understanding the communication between devices.
3. Metasploit Metasploit is a powerful penetration testing framework that empowers ethical hackers to identify, exploit, and validate vulnerabilities in target systems. It offers a vast collection of pre-built exploits, payloads, and auxiliary modules, making it an essential tool for both beginners and experienced professionals.

5. Aircrack-ng Aircrack-ng is a robust suite of tools for auditing and securing wireless networks. Ethical hackers can utilize Aircrack-ng to assess the security of Wi-Fi networks, perform packet capture and analysis, and test the strength of wireless encryption protocols. This tool is especially valuable for identifying weaknesses in wireless network configurations.
6. Nikto Nikto is a web server scanner that helps ethical hackers identify potential vulnerabilities in web servers and web applications. It scans for outdated software, security misconfigurations, and common issues, making it an essential tool for web security testing.
7. Hydra Hydra is a versatile password-cracking tool that ethical hackers use to perform brute-force and dictionary attacks on login systems. It supports various protocols and services, allowing testers to assess the strength of password security.
8. Ghidra Ghidra, developed by the National Security Agency (NSA), is a powerful open-source software reverse engineering tool. Ethical hackers use it to analyze and understand malware, decompile binaries, and inspect software for vulnerabilities.
9. John the Ripper John the Ripper is a popular password-cracking tool known for its speed and effectiveness. Ethical hackers rely on it to test the strength of password hashes and identify weak or easily guessable passwords.
10. Hashcat Hashcat is another widely used password-cracking tool that supports a variety of algorithms and attack modes. Ethical hackers can use Hashcat to recover forgotten passwords or audit the security of password hashes.
11. Snort Snort is an open-source intrusion detection system (IDS) that helps ethical hackers monitor network traffic for suspicious activities or known attack patterns. It aids in the early detection of potential security threats.
12. OpenVAS OpenVAS (Open Vulnerability Assessment System) is a full-featured vulnerability scanner that assists ethical hackers in identifying security weaknesses in networks and web applications. It offers comprehensive vulnerability assessment and reporting capabilities.
13. Cain and Abel Cain and Abel is a password recovery tool that ethical hackers use to recover passwords through various methods like dictionary attacks and cryptanalysis. It is particularly helpful for recovering forgotten passwords or assessing password security.
14. Sysinternals Suite The Sysinternals Suite, developed by Microsoft, is a collection of powerful system utilities. Ethical hackers use these tools to explore and troubleshoot Windows systems, as well as analyze system internals for potential security issues.
These essential tools empower ethical hackers to conduct thorough assessments of computer systems, networks, and applications, helping organizations strengthen their cybersecurity defences.
If you want to learn more about it, I highly recommend that you contact ACTE Technologies because they offer certifications and job placement opportunities. Experienced teachers can help you learn better. You can find these services both online and offline.
If you feel that my response has been helpful, make sure to follow me and it will encourage me to upload more content about Ethical hacking.
Thanks for spending your valuable time and upvotes here. Have a great day.
1 note
·
View note
Text
Módulos auxiliares do Metasploit com o Parrot Security
Novo post em https://udigrudroid.wordpress.com Módulos auxiliares do Metasploit com o Parrot Security Continuando a minha aventura com o Metasploit framework no ParrotSec começada no post anterior.

Continuando a minha aventura com o ParrotSec começada no post anterior – e permanecendo com a utilização do Metasploit framework por ser minha ferramenta predileta para testes de penetração – neste post estou compartilhando as minhas anotações sobre o uso dos módulos auxiliares (auxiliary modules) da referida ferramenta. Continue lendo!
View On WordPress
#Ataque pela internet(WAN)#Auxiliary Modules#DHCP falso#DNS falso#DNS malicioso#DNS Spoofing#DNSSERVER#envenenamento por ARP#Evitar os Ataques MitM#FTP falso#IEEE_802.1X#LHOST#LPORT#Módulos auxiliares do Metasploit#Metasploit Framework#NETMASK#Parrot Security#ParrotSec#port forwarding#SRVHOST#TARGETACTION#TARGETDOMAIN#TARGETHOST#Wireshark
0 notes
Photo

Metasploit🗝️ is an open-source penetration tool used for testing the vulnerabilities of computer systems to gain the remote access of the computer and then likewise protecting them against hacking. Metasploit is basically a framework used for pentesting. Now, with that metasploit framework, there are many things you can do. For simplicity, I will divide those things into 3 parts. Pre-attack phase Now, you can use metasploit to Create a listener on a port. Create a malicious apk file. Create a malicious file such as a pdf file 📘. Create a malicious extension. Create a malicious exe file using msfvenom. Using msfvenom, you can also create malicious php file. You can use auxiliaries in metasploit to do enumeration on the target. Attack phase Perform different activities based on the type of payload you have used for exploiting such as taking a screenshots. Go for privilege escalation. Post attack phase. You can again use those same auxiliary to find more information about the network or system once you are inside. You can also use post phase modules to interact with registry and event log management to clean your tracks. There are a lot of stuff that you can do using metasploit. It is not possible for me to list all of them. Follow @cybersec_society ... ... ... #cyber #security #hack #hacker #cyberattack #kali #kalilinuxtools #kalilinux #metasploit #metasploitframework #tor #ports #remoteaccess #instagram #vulnerability #penetrationtesting #coder #programmer #programming #coding #linux #ubuntu #cybersecurity #infosec #technology #exploits #informationsecurity #networksecurity #exploit #exploitation https://www.instagram.com/p/CAiHzbPJhHA/?igshid=6v9unaaxza2c
#cyber#security#hack#hacker#cyberattack#kali#kalilinuxtools#kalilinux#metasploit#metasploitframework#tor#ports#remoteaccess#instagram#vulnerability#penetrationtesting#coder#programmer#programming#coding#linux#ubuntu#cybersecurity#infosec#technology#exploits#informationsecurity#networksecurity#exploit#exploitation
0 notes
Text
Something Awesome - Learning About Metasploit
zennopsbm2/Through research I found that one of the key tools that would help in solving pen testing exercises such as hack the box one, will require a decent knowledge of various tools that are inbuilt into Kali Linux.
One of these is Metasploit, I have summarised my key takeaways below.
MSFconsole
Armitage
For faster use of metasploit, need to use postgresql

metasploit - six modules:
exploits - module to take advantage of a systems vulnerability. it will install a payload on the system
payloads - either a reverse shell or a metapreter - giving you access to the computer in the form of the payload. payload is what the exploit will try to plant on the system to exploit a vulnerability.
auxiliary -
nops -
posts -
encoders -
important commands
Help command - very useful.
use command - allows you to load a module, i.e. use exploit/windows/browser/adobe_flash/avm2
show - gives you information on the module
all, encoders, nops, exploits, payloads, auxilliary, post, plugins, info, options
search
search type: exploit platform: windows flash
Accessing installed modules
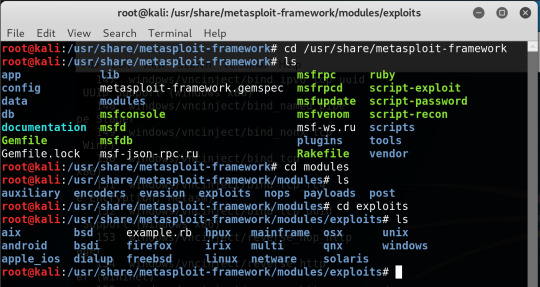
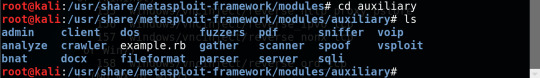
all listed in a very helpful directory and categorised effectively
nops are good to run a specific code or file after exploiting a buffer overflow
nmap port scan
detects open ports on the target machine
nmap -sT ip
stealth scan
nmap -sS ip
auxiliary scanners

moving to a visual representation (zenmap)
0 notes
Link
Masters in Ethical Hacking with Android ##Udacity ##udemycourses #Android #ETHICAL #Hacking #Masters Masters in Ethical Hacking with Android Do You need to learn ethical hacking,But your not having proper lab setup ? Do you discover the charge line befuddling and scaring? On the off chance that yes, this is the ideal course for you. concentrating on the viable side of infiltration testing without ignoring the hypothesis behind each attacks.Before hopping into entrance testing, you will initially figure out how to install the required packages to practice penetration testing on your android. All the attacks explained in this course are done in my Android phone. In the wake of taking this course you will never utilize your computer or laptop for hacking. This is extremely helpful for the individuals who need to begin hacking utilizing there Android Phone without Rooting the Device. The course is divided into sessions 1.installation of software on android device. 2.commands to used for hacking and pkg setup. sending a SMS using a command terminal and also making a phone call, basic programming: how to written a simple program in c, c++, python and execute it. 3.penetration testing like:Metasploit Penetration Testing is a complete guide for beginners as well as security professionals.Social engineer toolkit:SET has a number of custom attack vectors that allow you to make a believable attack in a fraction of the time.How to break a windows and Linux security by performing different exploitation methods via android. How to performing stress testing through Android. DDOS attempt to make an online service unavailable by overwhelming it with traffic from multiple source. Brute force attacking guess the password of victim. SQL MAP automates the discovery and exploitation of vulnerabilities to SQL injection attacks. WEB Application scanning, Creating Phishing page. UPDATE:- 4.Auxiliary Modules of Meatsploit: Http enum_wayback: this module pulls and parses the urls stored by archive_org for the purpose of replaying during a web assessment. Endpoint_mapper - Scanner DCERPC. Auto-pwn: fingerprint the victim's browser, then "throw" at it whatever exploits. Email harvesting: search_email_collector which searches google, bing and yahoo for email addresses associated to a particular domain. Detect SSH versions with the SSH version scanner. FTP Version Scanning Metasploit. Heart-bleed vulnerability enables a hacker to trick OpenSSL. THESE ALL ATTACKS ARE DONE WITHOUT ROOTING THE PHONE Who is the target audience? - For beginners and intermediate Internet users?-This course is for anyone who want to be ethical hacker and penetration testers ? -who is using android Phone?. - 👉 Activate Udemy Coupon 👈 Free Tutorials Udemy Review Real Discount Udemy Free Courses Udemy Coupon Udemy Francais Coupon Udemy gratuit Coursera and Edx ELearningFree Course Free Online Training Udemy Udemy Free Coupons Udemy Free Discount Coupons Udemy Online Course Udemy Online Training 100% FREE Udemy Discount Coupons https://www.couponudemy.com/blog/masters-in-ethical-hacking-with-android/
0 notes
Link
making you to control the world on you thumbs…
What you’ll learn
You will start using android phone for hacking, instead of pc.
Requirements
You shoud know how to use Android Phone.
Description
Do You need to learn ethical hacking,But your not having proper lab setup ? Do you discover the charge line befuddling and scaring? On the off chance that yes, this is the ideal course for you. concentrating on the viable side of infiltration testing without ignoring the hypothesis behind each attacks.Before hopping into entrance testing, you will initially figure out how to install the required packages to practice penetration testing on your android. All the attacks explained in this course are done in my Android phone.
In the wake of taking this course you will never utilize your computer or laptop for hacking. This is extremely helpful for the individuals who need to begin hacking utilizing there Android Phone without Rooting the Device.
The course is divided into sessions
1.installation of software on android device.
2.commands to used for hacking and pkg setup. sending a SMS using a command terminal and also making a phone call, basic programming: how to written a simple program in c, c++, python and execute it.
3.penetration testing like: Metasploit Penetration Testing is a complete guide for beginners as well as security professionals.Social engineer toolkit:SET has a number of custom attack vectors that allow you to make a believable attack in a fraction of the time.How to break a windows and Linux security by performing different exploitation methods via android. How to performing stress testing through Android.
DDOS attempt to make an online service unavailable by overwhelming it with traffic from multiple source.
Brute force attacking guess the password of victim. SQL MAP automates the discovery and exploitation of vulnerabilities to SQL injection attacks. WEB Application scanning, Creating Phishing page.
UPDATE:-
4.Auxiliary Modules of Meatsploit: Http enum_wayback: this module pulls and parses the urls stored by archive_org for the purpose of replaying during a web assessment. Endpoint_mapper – Scanner DCERPC. Auto-pwn:fingerprint the victim’s browser, then “throw” at it whatever exploits. Email harvesting:search_email_collector which searches google, bing and yahoo for email addresses associated to a particular domain. Detect SSH versions with the SSH version scanner. FTP Version Scanning Metasploit. Heart-bleed vulnerability enables a hacker to trick OpenSSL.
THESE ALL ATTACKS ARE DONE WITHOUT ROOTING THE PHONE
Who is the target audience?
– For beginners and intermediate Internet users? -This course is for anyone who want to be ethical hacker and penetration testers ? -who is using android Phone?. –
Who is the target audience?
Anyone how want to perform penetration testing on android or windows.
Created by Sac hackken Last updated 4/2018 English English [Auto-generated]
Size: 390.69 MB
Download Now
https://ift.tt/2BWHIJt.
The post Masters in Ethical Hacking with Android appeared first on Free Course Lab.
0 notes
Text
Original Post from Rapid7 Author: Jeffrey Martin
Is URGENT/11 urgent to your world? Metasploit now has a scanner module to help find the systems that need URGENT attention. Be sure to check the options on this one; RPORTS is a list to test multiple services on each target. Thanks Ben Seri for the PoC that lead off this work.
Everyone likes creds, a new post module landed this week from Taeber Rapczak that brings back credentials configured into grub. Gather away and add this new value to your password reuse testing.
Sparking joy for many long time users, Spencer McIntyre brings custom meterpreter prompts to the masses. This is a powerful context add for users that juggle multiple sessions at a time by adding at a glance recognition and verification of where a command is being sent.
A penny for your thoughts…
We’ve got a fantastic new docs writer on-board, helping us to improve and expand Metasploit documentation. Which areas of Framework could be better documented? Which areas lack explanations and/or examples? Let us know here!
New modules (8)
Linux Polkit pkexec helper PTRACE_TRACEME local root exploit by Jann Horn, @bcoles, and @timwr, which exploits CVE-2019-13272
Total.js CMS 12 Widget JavaScript Code Injection by sinn3r and Riccardo Krauter, which exploits CVE-2019-15954
Xorg X11 Server SUID modulepath Privilege Escalation by Aaron Ringo and Narendra Shinde, which exploits CVE-2018-14665
Solaris xscreensaver log Privilege Escalation by Marco Ivaldi and @bcoles, which exploits CVE-2019-3010
Microsoft Exchange Privilege Escalation Exploit by Petros Koutroumpis and _dirkjan, which exploits CVE-2019-0724
ThinVNC Directory Traversal by WarMarX, @bcoles, and jinxbox, which exploits CVE-2019-17662
URGENT/11 Scanner, Based on Detection Tool by Armis by wvu, Ben Seri, and Brent Cook, which exploits CVE-2019-12258
Multi Gather Grub Password Collection by Taeber Rapczak
Enhancements and features
Custom Meterpreter prompts by Spencer McIntyre, allows custom configuration of your prompt on meterpreter sessions similar to what console will allow.
Multiple Documentaion updates & adds, by @nsa & @h00die improve documentaion for auxiliary/scanner/ssl/openssl_heartbleed.md , auxiliary/scanner/redis/file_upload module, auxiliary/scanner/http/git_scanner, auxiliary/scanner/http/goahead_traversal & auxiliary/scanner/http/title modules.
Futex updates by @h00die, provides improved checks, targeting, & documentaion
Bugs fixed
Credential import fix by @jmartin-r7, fixes file based imports for pwdump.
Get it
As always, you can update to the latest Metasploit Framework with msfupdate and you can get more details on the changes since the last blog post from GitHub:
Pull Requests 5.0.54…5.0.55
Full diff 5.0.54…5.0.55
We recently announced the release of Metasploit 5. You can get it by cloning the Metasploit Framework repo (master branch). To install fresh without using git, you can use the open-source-only Nightly Installers or the binary installers (which also include the commercial editions).
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Jeffrey Martin Metasploit Wrap-Up Original Post from Rapid7 Author: Jeffrey Martin Is URGENT/11 urgent to your world? Metasploit now has a scanner module to help find the systems that need…
0 notes
Text
Metasploit Framework: Penetration Testing with Metasploit
Metasploit Framework: Penetration Testing with Metasploit
Become Hacker: Learn ethical hacking and penetration testing using Metasploit and start your cyber security career
What you’ll learn:
Become an Expert in Using Metasploit
Learn Ethical Hacking from scratch with Metasploit
Importance of Penetration Testing
Types of Penetration Testing
Basics of Penetration Testing
Metasploit Filesystem and Libraries
The Architecture of MSF
Auxiliary Modules
Payload…
View On WordPress
0 notes
Text
Master in Hacking with Metasploit
http://bit.ly/2LSxiOw Master in Hacking with Metasploit, Hack almost all operating system. After 9 succesful courses on ethical hacking, Amit Huddar is back with 10th course "Master in Hacking with Metasploit", metasploit is an exploitation framework, group of tools and utilities put together to make exploit development and system administration. Basically the attacker launches number of payloads to victim's computer which exploit the vulnerabilities to exploit data. Metasploit is a powerful tool,it has 458 payloads, 1604 exploits module, 913 auxiliary module, 275 post-exploitation module. In this course all tricks and techniques are 100% working and tested. Instructor provides step by step instructions from 100% scratch. After taking this course you'll be capable to do following things:
Exploit XP with smb server
Hack windows 7 using backdoor exe
Hack Apple Mac OS X
Hack all windows xp, vista, win 7, win 8, 8.1 and 10
Download documents, create remote users and take screen captures from exploited Linux and Windows servers.
You will be capable to protect your system from metasploit exploits
0 notes
Text
Metateta - Automated Tool For Scanning And Exploiting Network Protocols Using Metasploit
Metateta - Automated Tool For Scanning And Exploiting Network Protocols Using Metasploit #Metasploit #Network #Hacking
Metateta Automated Tool For Scanning And Exploiting Network Protocols Using Metasploit
For faster pen testing for large networks
What You Can Do
Scanning with all metasploit modules for specific network Protocol like smb,smtp,snmp
Run all Auxiliary modules against specific network Protocol
Run all Possible Metasploit Exploits for specific network Protocol That's is not recommended for real pen…
View On WordPress
0 notes
Text
NTP/SNMP amplification attacks
I needed to verify a SNMP and NTP amplification vulnerability was actually working. Metasploit has a few scanners for ntp vulns in the auxiliary/scanner/ntp/ntp_* and it will report hosts as being vulnerable to amplification attacks.
msf auxiliary(ntp_readvar) > run
[*] Sending NTP v2 READVAR probes to 1.1.1.1->1.1.1.1 (1 hosts)
[+] 1.1.1.1:123 - Vulnerable to NTP Mode 6 READVAR DRDoS: No packet amplification and a 34x, 396-byte bandwidth amplification
I've largely not paid attention to these types of attacks in the past but in this case needed to validate I could get the vulnerable host to send traffic to a target/spoofed IP. I set up 2 boxes to run the attack; an attack box and a target box that I used as the spoofed source IP address. I ran tcpdump on the target/spoofed server (yes...listening for UDP packets) it was receiving no UDP packets when I ran the attack. If I didn't spoof the source IP, the vulnerable server would send data back to the attacker IP but not the spoofed IP. Metasploit (running as root) can spoof the IP for you:
msf auxiliary(ntp_readvar) > set SRCIP 2.2.2.2
SRCIP => 2.2.2.2
msf auxiliary(ntp_readvar) > run
[*] Sending NTP v2 READVAR probes to 1.1.1.1->1.1.1.1 (1 hosts)
[*] Sending 1 packet(s) to 1.1.1.1 from 2.2.2.2
To rule out it wasn't a Metasploit thing I also worked thru the attack with scapy following the examples here: http://www.nothink.org/misc/snmp_reflected.php So I asked on Twitter...fucking mistake...after getting past the trolls and well intentioned people that didn't think I understood basic networking/spoofing at all (heart u) link #1, link #2 as the likely reason I couldn't spoof the IP. As well as a hint that the last time someone got it to work they had to rent a physical server in a dodgy colo. A bit of reading later I found https://spoofer.caida.org/recent_tests.php which allows you to check and see if a particular ASN supports spoofing along with the stats that only 20% of the Internet allows spoofing.
source: https://spoofer.caida.org/summary.php Checking common ISP and cloud provider ASNs showed that most weren't vulnerable to spoofing. So mystery solved and another aux module/vuln scanner result that can be quickly triaged and/or ignored. If someone has had different results please let me know. P.S. Someone asked if the vuln host was receiving the traffic. I couldn't answer for the initial host but to satisfy my curiosity on the issue I built a vulnerable NTP server and it did NOT receive the traffic even with hosts from the same VPS provider in the same data center (different subnets). from NTP/SNMP amplification attacks
0 notes
Link
Just wanna share it.. I'm using this msf module http://ift.tt/2onj5kG. Clone it and copy paste eternalblue_doublepulsar.rb to /usr/share/metasploit-framework/modules/exploits/windows/smb/. Run msfconsole and scan your local network with auxiliary/scanner/smb/smb_ms17_010 (MS17-010 SMB RCE Detection). Now use the exploit exploit/windows/smb/eternalblue_doublepulsar. Set the necessary options like RHOST, TARGETARCHITECTURE, TARGET and PROCESSINJECT. For DOUBLEPULSARPATH and ETERNALBLUEPATH, use Eternalblue-Doublepulsar-Metasploit/deps/ directory. For example /root/Eternalblue-Doublepulsar-Metasploit/deps/. Don't forget set the PAYLOAD windows/x64/meterpreter/reverse_tcp (my target use x64 so i'm using x64 payload too). If everything sets, now run exploit. Run some interesting command like webcam_list or webcam_snap The victim desktop screenshot. Tested on my local network, tool used Metasploit running in Kali Linux. Thats it, happy hacking!
0 notes
Link
Master in Hacking with Metasploit ##FreeCourse ##udemycourses #Hacking #Master #Metasploit Master in Hacking with Metasploit After 9 succesful courses on ethical hacking, Amit Huddar is back with 10th course "Master in Hacking with Metasploit", metasploit is an exploitation framework, group of tools and utilities put together to make exploit development and system administration. Basically the attacker launches number of payloads to victim's computer which exploit the vulnerabilities to exploit data. Metasploit is a powerful tool,it has 458 payloads, 1604 exploits module, 913 auxiliary module, 275 post-exploitation module. In this course all tricks and techniques are 100% working and tested. Instructor provides step by step instructions from 100% scratch. After taking this course you'll be capable to do following things: Exploit XP with smb server Hack windows 7 using backdoor exe Hack Apple Mac OS X Hack all windows xp, vista, win 7, win 8, 8.1 and 10 Download documents, create remote users and take screen captures from exploited Linux and Windows servers. You will be capable to protect your system from metasploit exploits For what you are waiting for enroll now! Who this course is for: Anyone interested in hacking Who want to pursue ethical hacking as carrier Who want to hack all operating systems remotely 👉 Activate Udemy Coupon 👈 Free Tutorials Udemy Review Real Discount Udemy Free Courses Udemy Coupon Udemy Francais Coupon Udemy gratuit Coursera and Edx ELearningFree Course Free Online Training Udemy Udemy Free Coupons Udemy Free Discount Coupons Udemy Online Course Udemy Online Training 100% FREE Udemy Discount Coupons https://www.couponudemy.com/blog/master-in-hacking-with-metasploit/
0 notes