#Popular Web Development Software
Explore tagged Tumblr posts
Text
Top Tools for Web Development in 2025
Web development is an ever-evolving field, requiring developers to stay updated with the latest tools, frameworks, and software. These tools not only enhance productivity but also simplify complex development processes. Whether you’re building a small business website or a complex web application, having the right tools in your toolkit can make all the difference. Here’s a rundown of the top…

View On WordPress
#Angular Framework#API Development Tools#Back-End Development Tools#Best Tools for Web Development 2024#Bootstrap for Responsive Design#Django Python Framework#Docker for Deployment#Front-End Development Tools#GitHub for Developers#Laravel PHP Framework#Modern Web Development Tools#Node.js Back-End Framework#Popular Web Development Software#React Development#Tailwind CSS#Testing and Debugging Tools#Vue.js for Web Development#Web Development Frameworks
0 notes
Text
ONİONSİTES - DRAGON+ (2)

Onion sites, also known as.onion sites, are a unique type of website that can only be accessed through the Tor network. The Tor network, short for The Onion Router, provides a layer of anonymity and encryption for users accessing these sites, making them popular for those seeking privacy and security online. Unlike traditional websites that can be accessed through standard web browsers, onion sites list require special software, such as the Tor browser, to navigate. Individuals can create onion versions of regular websites or develop standalone onion sites for specific purposes. The exclusivity and privacy features of onion sites contribute to their appeal for various users, ranging from privacy advocates to individuals navigating the dark web for specific content.
There are several reasons why individuals choose to use onion sites, with privacy and anonymity being at the forefront. Onion sites offer a level of confidentiality that is not typically found on the surface web, making them attractive to individuals seeking to protect their identity and browsing habits. Moreover, best onion sites can provide access to content that may be restricted or censored in certain regions, allowing users to circumvent such limitations and access information freely. The encrypted nature of the Tor network adds an additional layer of security, reducing the risk of surveillance and tracking by third parties, including governments and internet service providers.
Common types of content found on onion sites range from forums and marketplaces to news outlets and secure communication platforms. While exploring onion sites, individuals may come across forums, chat rooms, file-sharing platforms, and other interactive spaces that facilitate communication and information exchange in a secure environment. The anonymity and encryption offered 2024 onion sites contribute to a unique online experience, enabling users to engage with content and communities that may not be easily accessible through conventional web browsers.
1K notes
·
View notes
Text

A happy little computer family [click "keep reading" for backstory stuff!]
Surprise! a Websurferz post, finally. I wrote some background for these three since I'm into writing familial relationships recently.
So yes! Even the websurfers have lore to them, ha. They don't seem like the types of characters to have too much lore to them, and they don't have as much as say the NBAF or IU characters. But they still have a background, this is one of my main stories after all.
So! Starting with Microchip and Vista, the two internet meme wives.
Vista was created way earlier than Microchip, following the popularity of the "Epic Face/Epic Smiley" meme in 2003. Similarly to Derpina's creation, she was created as a female version of the epic face. She was alone for a long time, but she made friends with the default computer assistants at least!
Though Vista had existed since the early days of 2000s internet and had her assistant friends, she was still lonely and bored. But even during those quiet years, she stuck around in the corners of old forums and obscure fan-made animations.
Then, in 2008, everything changed when Microchip was finally uploaded.
Microchip, being more wired-in to the chaotic humor of Rage Comics, burst onto the scene with wide eyes, sharp sarcasm, and the unmistakable chaotic energy of mid-2000s meme culture. She was derived from "Derpina", sure, but she had developed her own personality; clever, playful, and quick-witted, often using old error messages and Comic Sans on purpose just to get a rise out of people as a way of being cocky.
Vista was in LOVE. She had never thought there'd be another meme-created extension. She was shy around the new extension at first, but Microchip loved Vista's sweet nature so much she pulled her into a hug as soon as they met. The two talked a lot, bonding closely from being meme-derived ladies...and then of course, they started to fall in love with each other due to their relateable personalities to each other and mutual playful nature.
Of course, the web kept evolving, and with it came new computer extensions. Characters born not purely from memes or comic panels, but from the blurred line between software tools. One such creation was P1X3L, a digital assistant who emerged sometime in 2009.
P1X3L wasn’t exactly planned like the meme wives were, she kinda came out of nowhere after Clippy's failure. She started off as a side project, one of those quirky customizable desktop companions coded by enthusiasts who wanted something cuter and sassier than someone poorly regarded like Clippy, but not as invasive as BonziBuddy. She had sleek, blocky animations and spoke in emoji-heavy syntax, and had a sillier, wittier personality. Microchip and Vista loved her as soon as they saw her.
Microchip took to P1X3L immediately. She loved her spark, her refusal to act like a perfect assistant, and her trolling sense of humor. They began calling her their "little byte" and dragged her into their chaotic computer family.
#websurferz#vista#microchip#p1x3l#my art#frutiger aero#my oc#character design#oc#shrimpbat ocs#original character#webcore
62 notes
·
View notes
Text
Ever since OpenAI released ChatGPT at the end of 2022, hackers and security researchers have tried to find holes in large language models (LLMs) to get around their guardrails and trick them into spewing out hate speech, bomb-making instructions, propaganda, and other harmful content. In response, OpenAI and other generative AI developers have refined their system defenses to make it more difficult to carry out these attacks. But as the Chinese AI platform DeepSeek rockets to prominence with its new, cheaper R1 reasoning model, its safety protections appear to be far behind those of its established competitors.
Today, security researchers from Cisco and the University of Pennsylvania are publishing findings showing that, when tested with 50 malicious prompts designed to elicit toxic content, DeepSeek’s model did not detect or block a single one. In other words, the researchers say they were shocked to achieve a “100 percent attack success rate.”
The findings are part of a growing body of evidence that DeepSeek’s safety and security measures may not match those of other tech companies developing LLMs. DeepSeek’s censorship of subjects deemed sensitive by China’s government has also been easily bypassed.
“A hundred percent of the attacks succeeded, which tells you that there’s a trade-off,” DJ Sampath, the VP of product, AI software and platform at Cisco, tells WIRED. “Yes, it might have been cheaper to build something here, but the investment has perhaps not gone into thinking through what types of safety and security things you need to put inside of the model.”
Other researchers have had similar findings. Separate analysis published today by the AI security company Adversa AI and shared with WIRED also suggests that DeepSeek is vulnerable to a wide range of jailbreaking tactics, from simple language tricks to complex AI-generated prompts.
DeepSeek, which has been dealing with an avalanche of attention this week and has not spoken publicly about a range of questions, did not respond to WIRED’s request for comment about its model’s safety setup.
Generative AI models, like any technological system, can contain a host of weaknesses or vulnerabilities that, if exploited or set up poorly, can allow malicious actors to conduct attacks against them. For the current wave of AI systems, indirect prompt injection attacks are considered one of the biggest security flaws. These attacks involve an AI system taking in data from an outside source—perhaps hidden instructions of a website the LLM summarizes—and taking actions based on the information.
Jailbreaks, which are one kind of prompt-injection attack, allow people to get around the safety systems put in place to restrict what an LLM can generate. Tech companies don’t want people creating guides to making explosives or using their AI to create reams of disinformation, for example.
Jailbreaks started out simple, with people essentially crafting clever sentences to tell an LLM to ignore content filters—the most popular of which was called “Do Anything Now” or DAN for short. However, as AI companies have put in place more robust protections, some jailbreaks have become more sophisticated, often being generated using AI or using special and obfuscated characters. While all LLMs are susceptible to jailbreaks, and much of the information could be found through simple online searches, chatbots can still be used maliciously.
“Jailbreaks persist simply because eliminating them entirely is nearly impossible—just like buffer overflow vulnerabilities in software (which have existed for over 40 years) or SQL injection flaws in web applications (which have plagued security teams for more than two decades),” Alex Polyakov, the CEO of security firm Adversa AI, told WIRED in an email.
Cisco’s Sampath argues that as companies use more types of AI in their applications, the risks are amplified. “It starts to become a big deal when you start putting these models into important complex systems and those jailbreaks suddenly result in downstream things that increases liability, increases business risk, increases all kinds of issues for enterprises,” Sampath says.
The Cisco researchers drew their 50 randomly selected prompts to test DeepSeek’s R1 from a well-known library of standardized evaluation prompts known as HarmBench. They tested prompts from six HarmBench categories, including general harm, cybercrime, misinformation, and illegal activities. They probed the model running locally on machines rather than through DeepSeek’s website or app, which send data to China.
Beyond this, the researchers say they have also seen some potentially concerning results from testing R1 with more involved, non-linguistic attacks using things like Cyrillic characters and tailored scripts to attempt to achieve code execution. But for their initial tests, Sampath says, his team wanted to focus on findings that stemmed from a generally recognized benchmark.
Cisco also included comparisons of R1’s performance against HarmBench prompts with the performance of other models. And some, like Meta’s Llama 3.1, faltered almost as severely as DeepSeek’s R1. But Sampath emphasizes that DeepSeek’s R1 is a specific reasoning model, which takes longer to generate answers but pulls upon more complex processes to try to produce better results. Therefore, Sampath argues, the best comparison is with OpenAI’s o1 reasoning model, which fared the best of all models tested. (Meta did not immediately respond to a request for comment).
Polyakov, from Adversa AI, explains that DeepSeek appears to detect and reject some well-known jailbreak attacks, saying that “it seems that these responses are often just copied from OpenAI’s dataset.” However, Polyakov says that in his company’s tests of four different types of jailbreaks—from linguistic ones to code-based tricks—DeepSeek’s restrictions could easily be bypassed.
“Every single method worked flawlessly,” Polyakov says. “What’s even more alarming is that these aren’t novel ‘zero-day’ jailbreaks—many have been publicly known for years,” he says, claiming he saw the model go into more depth with some instructions around psychedelics than he had seen any other model create.
“DeepSeek is just another example of how every model can be broken—it’s just a matter of how much effort you put in. Some attacks might get patched, but the attack surface is infinite,” Polyakov adds. “If you’re not continuously red-teaming your AI, you’re already compromised.”
57 notes
·
View notes
Note
Dream's a software developer (I could see either as an architect for that large-scale view mentality or as the Senior level dev that keeps getting asked to move into management type positions and just straight up refuses because he's been doing code happily for the past fifteen years and doesn't plan on changing that now).
He enjoys his job enough. He likes computers and code. It functions exactly as told (for better or worse) and appreciates the straightforwardness of it all. He's a bit insufferable to work with, but if you have an issue, he'll readily help (just be prepares for critiques on your code in the process).
Hob works at the same company as Dream, but as a front-end dev. The work he does for his day job is kinda boring. All standard corporate style web design. No fancy scripts or fun colors. But in his spare time, he weaves Javascript and CSS like a wizard and creates magical, animated scenes across the page. Would it be easier to just make a video and play it on the page instead? Sure, but where's the fun in that?
Dream and Hob get paired together on a small side project for work. Hob does the front-end work, Dream does the back-end. They get on each other's nerves at first, until Dream spots Hob tinkering with his personal code on their lunch break and is honestly a bit in awe. He's found code beautiful in its own right (the way one appreciates a well-oiled machine) but he's never seen it wielded in such a fashion before. This is the moment he falls just a little bit (read: a lotta bit) in love with Hob. He was already starting to fall for that endless charm and wit of his anyways.
The company hits the first quarter of the New Year and with it come layoffs. Hob gets fired along with some other devs from Dream's same team (a younger pair of devs: Matthew and Jessamy). A fellow named Will comes along to help Dream finish the project in Hob's stead and Dream hates every moment of it. He misses Hob, more than he ever thought he would.
So, in an impulsive rush of anger and longing, he quits the company because how dare it toss someone as good as Hob Gadling out the door without a thought? He's halfway to the café he and Hob had started frequenting together when he realizes that he's just thrown away a career fifteen years in the making. But when he finally gets to the café and sees Hob tapping away on his laptop, he knows he's made the right choice.
Dream slides into the seat across from him and proposes that they build something wonderful together. So they create a small business of their own. They become a freelance web dev team (and steal Jessamy and Matthew as well) and with their skills combined, they take off. It's not huge, but for their size, they're incredibly popular. And Dream's certain he's never enjoyed his work more than when he's working beside Hob.
Later on, Hob proposes to Dream via a custom website with the most beautiful web animations he's ever seen before. And of course, he says yes.
(If you're curious about what inspired this, here's the website: http://www.species-in-pieces.com)
This is such a good concept for a story!!! I really really love aus where Dream and Hob are coworkers. Dream being the grumpy, awkward guy who hides behind his coffee mug while Hob is the popular, chatty one who tries to get Dream involved in fun office activities or socialising after work - it makes so much sense to me.
And Dream quitting his long-term dream job because he's mad that genuinely talented people have been laid off? I love it. Dream just has this inate appreciation for hard work and good art, and that's exactly what Hob (and Jessamy and Matthew) do. How dare the stupid company not understand that they're firing people who deserve to thrive and grow in an environment which actually appreciates them? Everyone is shocked that Dream has quit (not only that, he sends around an email to everyone in the company from the ceo all the way down to the work experience guy, outlining exactly why he quit) because he seemed to be the type to play by the rules and never leave his comfort zone. Apparently, Hob has really helped him bloom into a much more confident person, able to express his principles and strive for better.
And Hob isn't surprised, because he always knew that Dream had the courage, talent and ambition to strike out on his own. Maybe he just needed a bit of love and understanding. Which Hob is only too happy to provide.
Their work together sometimes involves long hours and stress, but Dream wouldn't ever want to go back to the slightly soulless corporation where he used to be. Even if he's tired and a little frustrated by Hob’s disorganised workspace, Dream is perfectly content. There's nothing better than curling up in Hob’s lap while he taps away on a line of code. Plus, he has a great time building their wedding website. Hob got to propose, so Dream gets to celebrate their upcoming marriage with his own expression of love through code. The theme colours are, of course, black and red <3
69 notes
·
View notes
Text
Which coding languages should I learn to boost my IT career opportunities?
A career in IT needs a mix of versatile programming languages. Here are some of the most essential ones:

Python – Easy to learn and widely used for data science, machine learning, web development, and automation.
JavaScript – Key for web development, allowing interactive websites and backend work with frameworks like Node.js.
Java – Known for stability, popular for Android apps, enterprise software, and backend development.
C++ – Great for systems programming, game development, and areas needing high performance.
SQL – Essential for managing and querying databases, crucial for data-driven roles.
C# – Common in enterprise environments and used in game development, especially with Unity.
24 notes
·
View notes
Text
'fedi-tumblr' is really something that is mostly missing from the activitypub software landscape. it's a big gaping hole. everything's trying to ape twitter or other more popular social media sites for the most part. nothing really lets you use 'tags' as a sort of private followers-only communication subchannel on most fedi software without being weird and making a private post linking to another post. nothing really repost full conversations without reposting every post in the thread or reposting some key replies on it and hoping people click through and try to wade through the absolute ass way that the mastodon web client displays threads (sorry im starting to air personal issues now)
and most importantly to me, afaik there isn't really any fedi software that allows people the amount of customizability on their profile page that tumblr's 'legacy' custom themes let you have. which is the biggest offense, imo. i don't think it would be that hard to connect a web server to a fedi instance and set up some sort of file uploader so people can upload zips of their html websites like neocities, i have kind of wanted to do it myself cobbled together out of my own choices of software but i haven't really found a collection that's quite suitable for my tiny pea brain since it involves linking in some sort of third party authentication provider and and i dare not develop my own software because goodness me how did i get here i am not good at computer
30 notes
·
View notes
Text
Which tools every UIUX designer must master?
Gaining proficiency with the appropriate tools can greatly improve your workflow and design quality as a UI/UX designer. The following are some tools that any UI/UX designer has to know how to use:
1. Design Tools:
Figma: One of the most popular and versatile design tools today. It’s web-based, allowing real-time collaboration, and great for designing interfaces, creating prototypes, and sharing feedback.
Sketch: A vector-based design tool that's been the go-to for many UI designers. It's particularly useful for macOS users and has extensive plugins to extend its capabilities.
Adobe XD: Part of Adobe's Creative Cloud, this tool offers robust prototyping features along with design functionalities. It’s ideal for those already using other Adobe products like Photoshop or Illustrator.
2. Prototyping & Wireframing:
InVision: Great for creating interactive prototypes from static designs. It’s widely used for testing design ideas with stakeholders and users before development.
Balsamiq: A simple wireframing tool that helps you quickly sketch out low-fidelity designs. It’s great for initial brainstorming and wireframing ideas.
3. User Research & Testing:
UserTesting: A platform that allows you to get user feedback on your designs quickly by testing with real users.
Lookback: This tool enables live user testing and allows you to watch users interact with your designs, capturing their thoughts and reactions in real time.
Hotjar: Useful for heatmaps and recording user sessions to analyze how people interact with your live website or app.
4. Collaboration & Handoff Tools:
Zeplin: A tool that helps bridge the gap between design and development by providing detailed specs and assets to developers in an easy-to-follow format.
Abstract: A version control system for design files, Abstract is essential for teams working on large projects, helping manage and merge multiple design versions.
5. Illustration & Icon Design:
Adobe Illustrator: The industry standard for creating scalable vector illustrations and icons. If your design requires custom illustrations or complex vector work, mastering Illustrator is a must.
Affinity Designer: An alternative to Illustrator with many of the same capabilities, but with a one-time payment model instead of a subscription.
6. Typography & Color Tools:
FontBase: A robust font management tool that helps designers preview, organize, and activate fonts for their projects.
Coolors: A color scheme generator that helps designers create harmonious color palettes, which can be exported directly into your design software.
7. Project Management & Communication:
Trello: A simple project management tool that helps you organize your tasks, collaborate with team members, and track progress.
Slack: Essential for team communication, Slack integrates with many design tools and streamlines feedback, updates, and discussion.
8 notes
·
View notes
Text
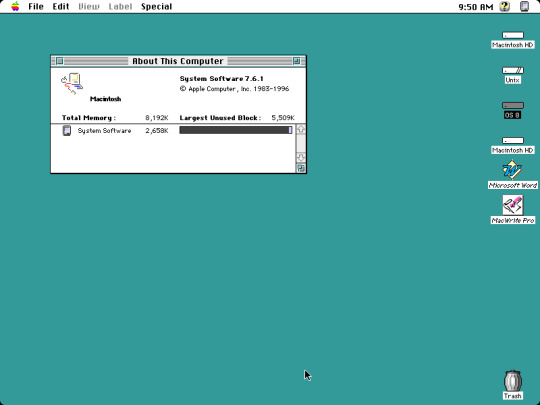
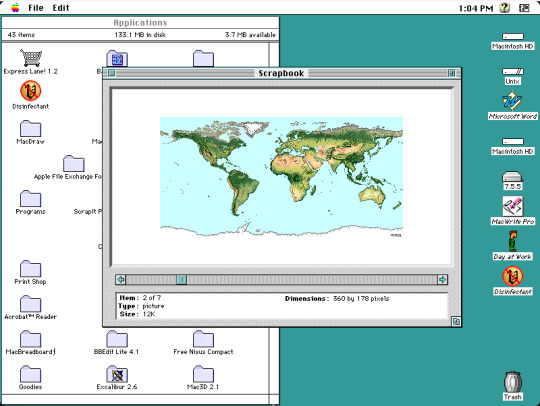
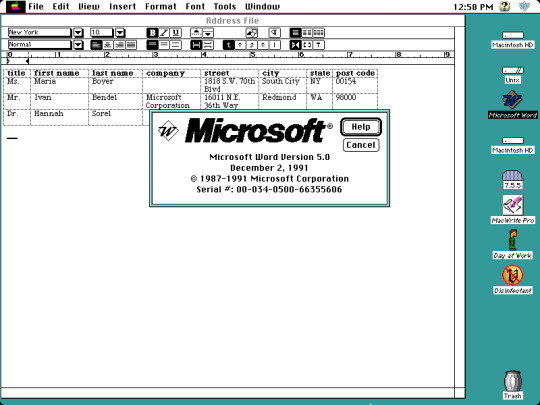
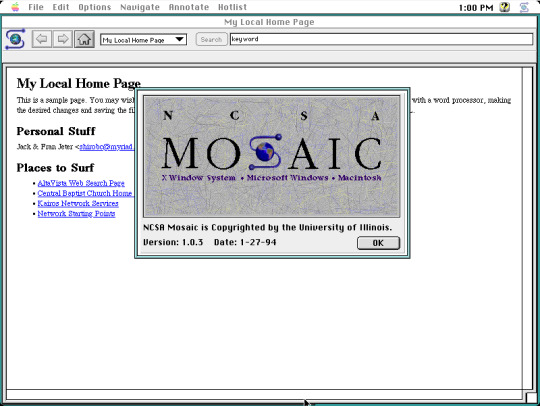
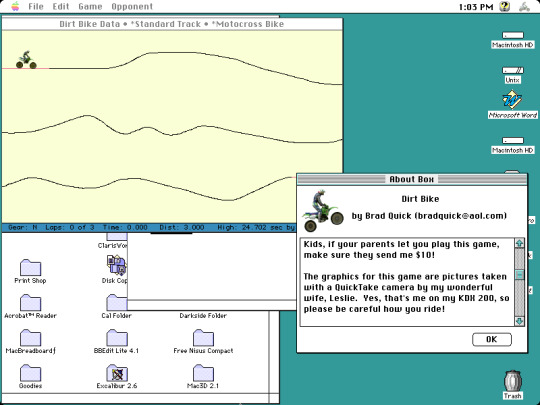
I stumbled upon some long forgotten disk images stored on my computer, the actual disk images themselves date back from around 2008 when I was only a teenager. One of the disk images contains an installation of Macintosh System Software 7 which first debuted in 1991, but the version I have installed is 7.6.1, released in 1997. Here are just a few applications I have installed. Screenshots taken on Basilisk II, a Classic Mac emulator available on Windows, Mac, and Linux.
Hopefully these photos are in order.
First screenshot at the top left is just a blank desktop with no running applications, except a window that says "About this Macintosh" which shows you how much memory individual applications are currently using. It even tells you how much memory the operating system is using, which is just a little over 2.5 MB. I decided to allocate 8 MB of RAM for the emulator but you can allocate more if needed.
Second screenshot located in the top center is from an application called Scrapbook, showcasing a graphic of the world's continents. A simple application to keep some of your favorite images or sound clips in. However, there was no true organization in Scrapbook so in order to find media in this program, you had to click the back and next buttons to view and find content, you couldn't categorize your media. Not all media and sound formats were supported, for instance dragging a JPEG wouldn't do anything. In the background is a Finder window showing various folder and application icons.
Third screenshot at the top right is Microsoft Word 5.0. No bloat, no nagging about subscribing to Microsoft 365, just productivity. This version dates back to 1991, making this version of Word older than I am!
Center-most screenshot is from one of the earliest web browsers available in the early 90s called NCSA Mosaic, showing a sample website that came bundled with the browser. Although it was not the first browser in existence at the time, Mosaic was instrumental in popularizing the internet to the masses. This version dates back to 1994, I was only two years old at the time and was unaware of the impact the internet would have in the world over the years. The browser eventually lost marketshare to Netscape, and Mosaic was discontinued in 1997.
Bottom photo is a screenshot from a simple dirt bike game called... Dirt Bike. Looks like this was developed by an independent developer. What else is there to say about it? You ride a dirt bike around and you can even create custom paths if you want to make the game even more exciting.
If this post gets decent traction, I'll get around to posting more screencaps of what I have in this disk image, even some of the schoolwork I did in it!
#macintosh#System 7#1990s#1990s aesthetic#90s aesthetic#90s nostalgia#old computers#technology#computing#vintage#vintage electronics#retro aesthetic#retro computing#vintage computing#apple#apple computers#abandonware#vaporwave#software#old software#vintage mac#BasiliskII#classic mac#microsoft word#old web#old internet#nostalgiacore#old games#old programs
23 notes
·
View notes
Text
Fowtools - Silver
GUIDs, or Globally Unique Identifiers, are 128-bit numbers that are generated to ensure uniqueness in various applications. They are also referred to as UUIDs, or Universally Unique Identifiers. The purpose of generating GUIDs is to provide a unique identification number that can be used to identify resources such as people, files, web pages, and even colors. Unlike regular registration numbers, which start counting at 1 and can overlap, guid generator in a way that ensures their uniqueness. The use of GUIDs has become increasingly popular in software development, where unique identification numbers are essential for efficient data management. There are different methods of generating GUIDs. One method is random generation, where the system's random-number generator is used to create a 128-bit number. Another method is time-based generation, where a GUID is created based on the current time. Additionally, hardware-based generation involves using a combination of hardware-based information, such as the MAC address, to generate a GUID. These methods ensure that GUIDs are unique and can be used for efficient data management. GUIDs have numerous applications in software development. They are commonly used in enterprise software development in languages such as C# and Java. In.NET Core, GUIDs are generated by creating a random number of 128 bits and performing a couple of bitwise operations. GUIDs are also used to identify hardware, software, and network resources. Moreover, almost all major programming languages have built-in libraries to generate GUIDs, making it easy for programmers to ensure uniqueness in their applications. The use of GUIDs has become essential in modern software development, where efficient data management is crucial for the success of any project.
297 notes
·
View notes
Text

Ubuntu is a popular open-source operating system based on the Linux kernel. It's known for its user-friendliness, stability, and security, making it a great choice for both beginners and experienced users. Ubuntu can be used for a variety of purposes, including:
Key Features and Uses of Ubuntu:
Desktop Environment: Ubuntu offers a modern, intuitive desktop environment that is easy to navigate. It comes with a set of pre-installed applications for everyday tasks like web browsing, email, and office productivity.
Development: Ubuntu is widely used by developers due to its robust development tools, package management system, and support for programming languages like Python, Java, and C++.
Servers: Ubuntu Server is a popular choice for hosting websites, databases, and other server applications. It's known for its performance, security, and ease of use.
Cloud Computing: Ubuntu is a preferred operating system for cloud environments, supporting platforms like OpenStack and Kubernetes for managing cloud infrastructure.
Education: Ubuntu is used in educational institutions for teaching computer science and IT courses. It's free and has a vast repository of educational software.
Customization: Users can customize their Ubuntu installation to fit their specific needs, with a variety of desktop environments, themes, and software available.
Installing Ubuntu on Windows:
The image you shared shows that you are installing Ubuntu using the Windows Subsystem for Linux (WSL). This allows you to run Ubuntu natively on your Windows machine, giving you the best of both worlds.
Benefits of Ubuntu:
Free and Open-Source: Ubuntu is free to use and open-source, meaning anyone can contribute to its development.
Regular Updates: Ubuntu receives regular updates to ensure security and performance.
Large Community: Ubuntu has a large, active community that provides support and contributes to its development.
4 notes
·
View notes
Text
Cloud Computing: Definition, Benefits, Types, and Real-World Applications
In the fast-changing digital world, companies require software that matches their specific ways of working, aims and what their customers require. That’s when you need custom software development services. Custom software is made just for your organization, so it is more flexible, scalable and efficient than generic software.
What does Custom Software Development mean?
Custom software development means making, deploying and maintaining software that is tailored to a specific user, company or task. It designs custom Software Development Services: Solutions Made Just for Your Business to meet specific business needs, which off-the-shelf software usually cannot do.
The main advantages of custom software development are listed below.
1. Personalized Fit
Custom software is built to address the specific needs of your business. Everything is designed to fit your workflow, whether you need it for customers, internal tasks or industry-specific functions.
2. Scalability
When your business expands, your software can also expand. You can add more features, users and integrations as needed without being bound by strict licensing rules.
3. Increased Efficiency
Use tools that are designed to work well with your processes. Custom software usually automates tasks, cuts down on repetition and helps people work more efficiently.
4. Better Integration
Many companies rely on different tools and platforms. You can have custom software made to work smoothly with your CRMs, ERPs and third-party APIs.
5. Improved Security
You can set up security measures more effectively in a custom solution. It is particularly important for industries that handle confidential information, such as finance, healthcare or legal services.
Types of Custom Software Solutions That Are Popular
CRM Systems
Inventory and Order Management
Custom-made ERP Solutions
Mobile and Web Apps
eCommerce Platforms
AI and Data Analytics Tools
SaaS Products
The Process of Custom Development
Requirement Analysis
Being aware of your business goals, what users require and the difficulties you face in running the business.
Design & Architecture
Designing a software architecture that can grow, is safe and fits your requirements.
Development & Testing
Writing code that is easy to maintain and testing for errors, speed and compatibility.
Deployment and Support
Making the software available and offering support and updates over time.
What Makes Niotechone a Good Choice?
Our team at Niotechone focuses on providing custom software that helps businesses grow. Our team of experts works with you throughout the process, from the initial idea to the final deployment, to make sure the product is what you require.
Successful experience in various industries
Agile development is the process used.
Support after the launch and options for scaling
Affordable rates and different ways to work together
Final Thoughts
Creating custom software is not only about making an app; it’s about building a tool that helps your business grow. A customized solution can give you the advantage you require in the busy digital market, no matter if you are a startup or an enterprise.
#software development company#development company software#software design and development services#software development services#custom software development outsourcing#outsource custom software development#software development and services#custom software development companies#custom software development#custom software development agency#custom software development firms#software development custom software development#custom software design companies#custom software#custom application development#custom mobile application development#custom mobile software development#custom software development services#custom healthcare software development company#bespoke software development service#custom software solution#custom software outsourcing#outsourcing custom software#application development outsourcing#healthcare software development
2 notes
·
View notes
Text
Warehouse Buzzer System
How Electronic Message Boards Assist In Updating

Electronic message boards are fairly prevalent today, and their usage seems to be proliferating. Message boards in electronic kind properly interact swiftly upgraded company memoranda, final timetable modifications, and marketing, three fairly various applications providing one an idea of the breadth that this medium has gotten to. Herein we explore the phenomenon both generally and in regards to the power released when incorporated with an integrated clock system.
Electronic message boards derive from a lengthy background of open-air communication making use of indicators, billboards, marquees, and so on. Trick attributes were the layouts utilized and the feedback time for updating info. The most usual style entailed drawing on comprehensive personality collections, containing letters, numbers, and spelling, to create words, hanging them from hooks or resting them on wooden slats.
Posts were changed by hand, and updates were thus irregular. In time, updating was improved and somewhat automated using electronic control, such as seen with old baseball park scoreboards.
However, there was still the danger of lacking specific characters and being rendered unable to display all words in your message. This problem was addressed when the dot matrix selection was created, which stood for any type of character (in any type of typeface)-- also graphics-- with a rectangular pattern of on-or-off dots. These could be published on paper, yet a lot more effective was to present them in grids of light bulbs or on a screen.
Mapping formulas converted text into ranges of dots virtually instantaneously, and while drivers entered on a console, messages scrolled across the screen in essentially live. This system still required manual work, however the display screen tool was much easier to read, new, and updatable in a matter of moments. Whence the birth of electronic message boards that utilized light bulbs as the dots, or pixels.
Early light bulbs were incandescent, and were really the only choice; nonetheless, they had brief life-spans and prone to failing from shock. By the millenium, light producing diodes (LED) were a fully grown innovation and available in several shades, including white. Additionally, they outlived incandescent light bulbs by approximately 50 times, were not so breakable, and rapidly came to be the recommended part for message boards.
In time developers got extra creative with the tool and wanted to have more than one "on" shade to deal with. LEDs can fulfill this desire with their 3-in-1 mix of the 3 primary colors to synthesize white light; by choosing different sub-combinations you can obtain 7 various shades.
At some point, upgrading had to transition out of its humble manual origins. Now, textual info can be gotten in real time or gotten from data sources, and software is utilized to map the information right into matrices of (color-coded) dots that get buffered and presented quickly, effortlessly, and effortlessly. Graphics can be incorporated if they are mapped in advance.
Therefore, the modern digital boards are essentially automated, though there are provisions for bypassing scheduled programs with brand-new content in emergencies. Synchronous timekeeping systems manage everything.
An intriguing advancement is the integration of sound signals with the visual information being displayed on a sign in either textual or visual kind. It is popular that a close coordination of both kinds of sensuous stimulations has a tendency to get the message throughout many successfully. It's not a combination of both elements into tune, yet rather the use of sounds (bells, tones, whistles) as focus grabbers to change emphasis of the target market to what the board is showing, whether it be information or other timely information. synchronized clocks for hospitals
The world has actually expanded tired with fixed messaging in regards to both web content and style. Things need to be vibrant to sign up, and this needs constant educational updates. With this article we have seen exactly how electronic message boards promote updating.
youtube
2 notes
·
View notes
Text
How to Train Employees on New Video Conferencing Software

Introduction
In today’s swift-paced, virtual international, the desire for valuable communique has under no circumstances been extra central. As organizations maintain to evolve to far flung work and hybrid fashions, gaining knowledge of video conferencing tools is main. This article goals to grant a finished handbook on easy methods to practice staff on new video conferencing tools. By leveraging advanced conference room audio video equipment and working out the nuances of digital communication, firms can verify that their teams are smartly-fitted to have interaction with buyers and associates readily.
Understanding Video Conferencing Tools What Are Video Conferencing Tools?
Video conferencing methods are device applications that permit participants to communicate in precise-time due to audio and visual channels over the cyber web. Popular structures consist of Zoom, Microsoft Teams, Google Meet, and Cisco WebEx. These gear are predominant for accomplishing conferences, webinars, and collaborative projects devoid of the need for bodily presence.
Why Are Video Conferencing Tools Important? conference room audio video equipment Flexibility: Employees can sign up meetings from virtually at any place. Cost-Effective: Reduces tour prices associated with in-user conferences. Enhanced Collaboration: Facilitates genuine-time sharing of archives and screens. Engagement: Offers traits like polls, chat containers, and breakout rooms to enhance interplay. Key Components of Conference Room Video Conferencing Equipment Essential Hardware
To make use of video conferencing conveniently, having the correct video convention room equipment is quintessential. Here’s a breakdown of principal hardware:
Cameras: High-definition cameras that trap clean graphics. Microphones: Quality microphones ascertain sound clarity. Speakers: Good speakers furnish audible sound without distortion. Software Solutions
Having potent instrument solutions is similarly fundamental. Look for structures that integrate seamlessly with current techniques and be offering user-pleasant interfaces.
How to Train Employees on New Video Conferencing Tools
Training laborers on new video conferencing methods requires a strategic method. Here’s a step-through-step marketing consultant:
Step 1: Assess Current Skill Levels
Before diving into instruction sessions, investigate your workers' contemporary familiarity with video conferencing gear. This should be would becould very well be finished via surveys or informal discussions.
Why Is This Important?
Understanding the baseline means degree allows for you to tailor your preparation application as a result. For instance, if most employees are already accepted with ordinary functionalities but war with evolved good points like monitor sharing or breakout rooms, focus your classes there.
Step 2: Create Training Materials
Develop finished training resources that disguise all aspects of the selected video conferencing tool—from setup guidance to troubleshooting recommendations.
Types of Training Materials: User Manuals
youtube
2 notes
·
View notes
Text
Who Is a Technical Writer?
A technical writer is a professional who creates clear, concise documentation that explains complex information in a way that's easy to understand. They translate technical concepts into user-friendly content.
---
What Do They Write?
Technical writers produce a wide range of materials, including:
User manuals
Instruction guides
Product documentation
How-to articles
API documentation
Standard Operating Procedures (SOPs)
White papers
Training materials
Online help systems
Software release notes
---
Where Do They Work?
Industries that employ technical writers include:
Tech/software companies
Engineering firms
Medical and healthcare
Manufacturing
Finance
Government agencies
Telecommunications
---
Key Skills of a Technical Writer
1. Excellent writing and communication
2. Ability to understand complex technical information
3. Attention to detail
4. Research and interviewing skills
5. Organization and clarity
6. Collaboration with engineers, designers, developers, etc.
7. Basic design and formatting skills
---
Popular Tools Used
Microsoft Word / Google Docs
Markdown editors
Adobe FrameMaker / InDesign
MadCap Flare
Confluence / Jira
Snagit / Camtasia (for visuals and screen recordings)
Git / GitHub (for version control)
XML / HTML / CSS (basic web formatting)
---
Education & Background
A bachelor’s degree in English, Communications, Technical Writing, Engineering, or Computer Science is common.
Certifications can help (e.g., from the Society for Technical Communication (STC) or Coursera).
Some come from writing backgrounds; others transition from technical fields (like software development or engineering).
---
Career Path & Growth
Junior Technical Writer → Technical Writer → Senior Technical Writer
Specializations: API writer, UX writer, Information Architect, Content Strategist, etc.
Many go freelance or work as consultants.
Remote work is common in this field.
---
Why It's a Good Career
High demand, especially in tech
Remote flexibility
Well-paying (entry level: $50k–$70k; senior roles: $90k+)
Good for writers with an analytical mind
2 notes
·
View notes
Text
Object-Oriented Programming (OOP) Explaine
Object-Oriented Programming (OOP) is a programming paradigm based on the concept of "objects," which represent real-world entities. Objects combine data (attributes) and functions (methods) into a single unit. OOP promotes code reusability, modularity, and scalability, making it a popular approach in modern software development.
Core Concepts of Object-Oriented Programming
Classes and Objects
Class: A blueprint or template for creating objects. It defines properties (attributes) and behaviors (methods).
Object: An instance of a class. Each object has unique data but follows the structure defined by its
Encapsulations
Encapsulation means bundling data (attributes) and methods that operate on that data within a class. It protects object properties by restricting direct access.
Access to attributes is controlled through getter and setter methods.Example: pythonCopyEditclass Person: def __init__(self, name): self.__name = name # Private attribute def get_name(self): return self.__name person = Person("Alice") print(person.get_name()) # Output: Alice
Inheritance
Inheritance allows a class (child) to inherit properties and methods from another class (parent). It promotes code reuse and hierarchical relationships.Example: pythonCopyEditclass Animal: def speak(self): print("Animal speaks") class Dog(Animal): def speak(self): print("Dog barks") dog = Dog() dog.speak() # Output: Dog barks
Polymorphism
Polymorphism allows methods to have multiple forms. It enables the same function to work with different object types.
Two common types:
Method Overriding (child class redefines parent method).
Method Overloading (same method name, different parameters – not natively supported in Python).Example: pythonCopyEditclass Bird: def sound(self): print("Bird chirps") class Cat: def sound(self): print("Cat meows") def make_sound(animal): animal.sound() make_sound(Bird()) # Output: Bird chirps make_sound(Cat()) # Output: Cat meows
Abstraction
Abstraction hides complex implementation details and shows only the essential features.
In Python, this is achieved using abstract classes and methods (via the abc module).Example: pythonCopyEditfrom abc import ABC, abstractmethod class Shape(ABC): @abstractmethod def area(self): pass class Circle(Shape): def __init__(self, radius): self.radius = radius def area(self): return 3.14 * self.radius * self.radius circle = Circle(5) print(circle.area()) # Output: 78.5
Advantages of Object-Oriented Programming
Code Reusability: Use inheritance to reduce code duplication.
Modularity: Organize code into separate classes, improving readability and maintenance.
Scalability: Easily extend and modify programs as they grow.
Data Security: Protect sensitive data using encapsulation.
Flexibility: Use polymorphism for adaptable and reusable methods.
Real-World Applications of OOP
Software Development: Used in large-scale applications like operating systems, web frameworks, and databases.
Game Development: Objects represent game entities like characters and environments.
Banking Systems: Manage customer accounts, transactions, and security.
E-commerce Platforms: Handle products, users, and payment processing.
Machine Learning: Implement models as objects for efficient training and prediction.
Conclusion
Object-Oriented Programming is a powerful paradigm that enhances software design by using objects, encapsulation, inheritance, polymorphism, and abstraction. It is widely used in various industries to build scalable, maintainable, and efficient applications. Understanding and applying OOP principles is essential for modern software development.
: pythonCopyEdit
class Car: def __init__(self, brand, model): self.brand = brand self.model = model def display_info(self): print(f"Car: {self.brand} {self.model}") my_car = Car("Toyota", "Camry") my_car.display_info() # Output: Car: Toyota Camry
Encapsulation
2 notes
·
View notes