#SQL Server locking issues
Explore tagged Tumblr posts
Text
A Deep Dive into NOLOCK's Power and Pitfalls in SQL Server
In the realm of SQL Server management, the NOLOCK hint emerges as a quintessential tool for database administrators, aimed at enhancing query efficiency through the minimization of locking and blocking phenomena. This tool, however, is double-edged, necessitating a nuanced understanding and strategic deployment. This exploration ventures into the practical utilization of NOLOCK, enriched with…
View On WordPress
#database concurrency solutions#NOLOCK SQL Server#read uncommitted data#SQL performance optimization#SQL Server locking issues
0 notes
Text
How to Improve Database Performance with Smart Optimization Techniques
Database performance is critical to the efficiency and responsiveness of any data-driven application. As data volumes grow and user expectations rise, ensuring your database runs smoothly becomes a top priority. Whether you're managing an e-commerce platform, financial software, or enterprise systems, sluggish database queries can drastically hinder user experience and business productivity.
In this guide, we’ll explore practical and high-impact strategies to improve database performance, reduce latency, and increase throughput.
1. Optimize Your Queries
Poorly written queries are one of the most common causes of database performance issues. Avoid using SELECT * when you only need specific columns. Analyze query execution plans to understand how data is being retrieved and identify potential inefficiencies.
Use indexed columns in WHERE, JOIN, and ORDER BY clauses to take full advantage of the database indexing system.
2. Index Strategically
Indexes are essential for speeding up data retrieval, but too many indexes can hurt write performance and consume excessive storage. Prioritize indexing on columns used in search conditions and join operations. Regularly review and remove unused or redundant indexes.
3. Implement Connection Pooling
Connection pooling allows multiple application users to share a limited number of database connections. This reduces the overhead of opening and closing connections repeatedly, which can significantly improve performance, especially under heavy load.
4. Cache Frequently Accessed Data
Use caching layers to avoid unnecessary hits to the database. Frequently accessed and rarely changing data—such as configuration settings or product catalogs—can be stored in in-memory caches like Redis or Memcached. This reduces read latency and database load.
5. Partition Large Tables
Partitioning splits a large table into smaller, more manageable pieces without altering the logical structure. This improves performance for queries that target only a subset of the data. Choose partitioning strategies based on date, region, or other logical divisions relevant to your dataset.
6. Monitor and Tune Regularly
Database performance isn’t a one-time fix—it requires continuous monitoring and tuning. Use performance monitoring tools to track query execution times, slow queries, buffer usage, and I/O patterns. Adjust configurations and SQL statements accordingly to align with evolving workloads.
7. Offload Reads with Replication
Use read replicas to distribute query load, especially for read-heavy applications. Replication allows you to spread read operations across multiple servers, freeing up the primary database to focus on write operations and reducing overall latency.
8. Control Concurrency and Locking
Poor concurrency control can lead to lock contention and delays. Ensure your transactions are short and efficient. Use appropriate isolation levels to avoid unnecessary locking, and understand the impact of each level on performance and data integrity.
0 notes
Text
Inside the Mind of a Hacker: Understanding Cyber Criminals and Their Tactics

In today’s digital landscape, cybercrime has evolved into a sophisticated, multi-billion-dollar industry. Hackers operate with precision, using advanced techniques to breach security systems, steal sensitive data, and disrupt businesses. But what motivates these cybercriminals, and how do they think? To truly combat cyber threats, we must first understand the mindset of hackers and the strategies they employ.
If you're looking to safeguard yourself and build a career in cybersecurity, pursuing a Cyber Security Certification in Kolkata can equip you with the skills needed to protect against these evolving threats. Let’s dive into the mind of a hacker and explore their tactics.
The Psychology of a Hacker
1. Motivations Behind Cybercrime
Hackers are not always driven by the same goals. Understanding their motivations helps cybersecurity professionals develop better defense mechanisms. Common hacker motivations include:
Financial Gain: Cybercriminals engage in ransomware attacks, credit card fraud, and data breaches to steal money or sell information on the dark web.
Political or Ideological Beliefs: Hacktivists, such as Anonymous, target governments or corporations to protest against policies or social issues.
Espionage: State-sponsored hackers infiltrate government agencies, corporations, and research institutions to steal confidential data.
Personal Challenge or Notoriety: Some hackers break into systems purely for the thrill, to prove their skills, or to gain recognition in the hacking community.
Revenge: Disgruntled employees or individuals use hacking to sabotage organizations or individuals who have wronged them.
2. The Hacker Mindset
Hackers exhibit a combination of intelligence, curiosity, and persistence. Many have a deep understanding of coding, networking, and security vulnerabilities. Key psychological traits of hackers include:
Problem-Solving Skills: Hackers view security systems as puzzles to be cracked.
Anonymity & Deception: They leverage VPNs, proxy servers, and encryption to remain undetected.
Adaptability: As cybersecurity evolves, hackers continuously find new ways to bypass security measures.
Common Hacking Techniques and Tactics
Hackers use various methods to infiltrate systems. Some of the most common tactics include:
1. Phishing Attacks
Phishing remains one of the most effective hacking techniques. Hackers send deceptive emails or messages that trick users into revealing personal information, such as passwords and credit card details. They often impersonate banks, government agencies, or trusted brands.
Example: In 2021, a major phishing campaign targeted Microsoft users, tricking them into entering their credentials on a fake login page.
2. Malware and Ransomware
Hackers deploy malicious software (malware) to infect systems, steal data, or lock users out of their devices. Ransomware encrypts files and demands a ransom for their release.
Example: The WannaCry ransomware attack in 2017 affected over 200,000 computers worldwide, causing billions in damages.
3. Social Engineering
This tactic exploits human psychology rather than technical vulnerabilities. Hackers manipulate individuals into divulging sensitive information or granting unauthorized access.
Example: A hacker posing as an IT support technician might call an employee and ask for their login credentials.
4. SQL Injection Attacks
Hackers exploit vulnerabilities in websites that use SQL databases. By inserting malicious SQL code into input fields, they can access, modify, or delete database records.
Example: A well-known SQL injection attack targeted Yahoo! in 2012, exposing 450,000 user accounts.
5. Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks
These attacks overwhelm a system with excessive traffic, causing it to crash and become inaccessible.
Example: In 2016, the Mirai botnet launched a massive DDoS attack on Dyn, a major DNS provider, disrupting websites like Twitter, Netflix, and PayPal.
How to Defend Against Hackers
Understanding hacker tactics is the first step in securing digital assets. Here are essential strategies to protect against cyber threats:
1. Invest in Cybersecurity Education
A Cyber Security Certification in Kolkata can provide in-depth knowledge of ethical hacking, penetration testing, and risk management, helping individuals and businesses strengthen their defenses.
2. Use Strong Passwords and Multi-Factor Authentication (MFA)
Avoid using simple or reused passwords. Implement MFA to add an extra layer of security.
3. Keep Software and Systems Updated
Outdated software contains vulnerabilities that hackers exploit. Regular updates and security patches help close these loopholes.
4. Educate Employees on Cyber Threats
Since social engineering is a major attack vector, training employees to recognize phishing emails and suspicious activities is crucial.
5. Implement Firewalls and Intrusion Detection Systems (IDS)
These tools monitor and block unauthorized access attempts, enhancing network security.
6. Regularly Backup Data
Frequent backups protect against ransomware attacks. Store backups in a secure, offline location.
7. Conduct Penetration Testing
Simulating cyberattacks through ethical hacking helps identify vulnerabilities before malicious hackers exploit them.
Conclusion
Cybercriminals are constantly evolving, using innovative tactics to breach systems and exploit vulnerabilities. By understanding their mindset and techniques, individuals and businesses can better protect themselves from cyber threats.
If you're serious about cybersecurity, obtaining a Cyber Security Certification in Kolkata is a great way to gain the skills and knowledge needed to combat cyber threats effectively. Investing in cybersecurity today can save organizations from significant financial losses, data breaches, and reputational damage in the future.
Cybersecurity is not just a technology problem—it’s a human challenge. Stay informed, stay prepared, and stay secure.
0 notes
Text
Managing Concurrent Transactions and Locks in SQL Server: Real-World Examples and Strategies
Introduction In a database environment, handling concurrent transactions is essential to maintain performance and data integrity. SQL Server uses locking mechanisms to manage concurrent access, but understanding and managing these locks is crucial to prevent issues like deadlocks or blocking. This article will guide you through the concepts, best practices, and strategies for managing…
0 notes
Text
"The Hidden Costs of Terminal Services & How RHosting Saves You Money"
When businesses think of remote desktop solutions, they often consider Microsoft’s Remote Desktop Services (RDS), also known as Terminal Services. While RDS is a popular choice, many companies overlook its hidden costs — which can add up quickly in terms of licensing, infrastructure, IT maintenance, and security risks.
RHosting offers a cost-effective alternative, eliminating unnecessary expenses while providing a faster, more secure, and scalable remote desktop solution. Let’s break down the hidden costs of RDS and see how RHosting helps businesses cut costs and boost efficiency.
🔹 The Hidden Costs of Microsoft Terminal Services (RDS)
At first glance, RDS might seem like an affordable solution, but the true cost goes far beyond the initial setup. Here’s where businesses lose money with Terminal Services:
1️⃣ Expensive Licensing Fees
Using RDS isn’t just about setting up a server — you must purchase multiple Microsoft licenses to make it work. These include:
🔹 Windows Server License — Required for the host machine. 🔹 Remote Desktop Services CALs (Client Access Licenses) — Needed for every user or device connecting to the server. 🔹 SQL Server & Other Software Licenses — Additional costs if using applications like SQL databases, Microsoft Office, or ERP software.
💸 Cost Impact: RDS licensing costs can range from hundreds to thousands of dollars per year, depending on the number of users.
🚀 How RHosting Saves You Money: ✔ No CALs Required — RHosting eliminates the need for separate RDS CALs. ✔ Predictable Pricing — Pay only for the resources you use, with no surprise licensing fees.
2️⃣ Expensive IT Infrastructure & Hardware
To run RDS efficiently, businesses need high-performance servers, storage, and networking equipment. These hardware requirements often lead to:
🔹 High Upfront Costs — Investing in dedicated Windows servers is costly. 🔹 Ongoing Maintenance — Regular hardware upgrades, security patches, and server monitoring add to IT expenses. 🔹 Scalability Issues — Scaling an RDS infrastructure requires additional hardware, further increasing costs.
💸 Cost Impact: A high-performance Windows server can cost thousands of dollars, plus ongoing maintenance expenses.
🚀 How RHosting Saves You Money: ✔ Cloud-Based Hosting — No need to invest in on-premise hardware. ✔ Instant Scalability — Easily add or remove users without purchasing new servers. ✔ 24/7 Managed Infrastructure — RHosting handles maintenance, reducing in-house IT costs.
3️⃣ IT Management & Support Costs
Managing RDS infrastructure requires a dedicated IT team for:
🔹 User & Access Management — Setting up user roles and permissions. 🔹 Security Patches & Updates — RDS requires frequent updates to prevent cyber threats. 🔹 Troubleshooting & Downtime Management — Server crashes, software conflicts, and slow performance issues are common.
💸 Cost Impact: Hiring IT staff or outsourcing support can cost thousands of dollars per month.
🚀 How RHosting Saves You Money: ✔ Fully Managed Solution — No need for an in-house IT team. ✔ Automated Security & Updates — RHosting keeps your system secure and up to date. ✔ 99.99% Uptime Guarantee — Prevents downtime-related financial losses.
4️⃣ Security & Compliance Risks
RDS is a prime target for cyberattacks due to open RDP ports, weak passwords, and outdated security protocols. Cybersecurity threats can result in:
🔹 Ransomware Attacks — Hackers exploit RDS vulnerabilities to lock data and demand ransom. 🔹 Data Breaches — Poorly secured RDS setups can expose sensitive business data. 🔹 Regulatory Compliance Issues — Non-compliance with GDPR, HIPAA, or financial regulations can lead to hefty fines.
💸 Cost Impact: The average cost of a data breach is over $4 million (IBM Security Report).
🚀 How RHosting Saves You Money: ✔ No Open RDP Ports — Eliminates the most common attack vector. ✔ End-to-End Encryption & Multi-Factor Authentication (MFA) — Ensures only authorized users gain access. ✔ Compliance-Ready Security — Built to meet industry standards, reducing regulatory risks.
🔹 Why RHosting is the Smarter, Cost-Effective Choice
👉 With RHosting, businesses save thousands of dollars in licensing, infrastructure, IT support, and security costs — all while improving performance and reliability.
🌟 Make the Smart Switch to RHosting Today!
If your business still relies on expensive, outdated RDS infrastructure, it’s time to upgrade to RHosting and start saving.
✅ No hidden costs or licensing fees ✅ No need for expensive IT infrastructure ✅ No cybersecurity vulnerabilities ✅ No complex setups or maintenance headache
0 notes
Video
youtube
Amazon RDS Performance Insights | Monitor and Optimize Database Performance
Amazon RDS Performance Insights is an advanced monitoring tool that helps you analyze and optimize your database workload in Amazon RDS and Amazon Aurora. It provides real-time insights into database performance, making it easier to identify bottlenecks and improve efficiency without deep database expertise.
Key Features of Amazon RDS Performance Insights:
✅ Automated Performance Monitoring – Continuously collects and visualizes performance data to help you monitor database load. ✅ SQL Query Analysis – Identifies slow-running queries, so you can optimize them for better database efficiency. ✅ Database Load Metrics – Displays a simple Database Load (DB Load) graph, showing the active sessions consuming resources. ✅ Multi-Engine Support – Compatible with MySQL, PostgreSQL, SQL Server, MariaDB, and Amazon Aurora. ✅ Retention & Historical Analysis – Stores performance data for up to two years, allowing trend analysis and long-term optimization. ✅ Integration with AWS Services – Works seamlessly with Amazon CloudWatch, AWS Lambda, and other AWS monitoring tools.
How Amazon RDS Performance Insights Helps You:
🔹 Troubleshoot Performance Issues – Quickly diagnose and fix slow queries, high CPU usage, or locked transactions. 🔹 Optimize Database Scaling – Understand workload trends to scale your database efficiently. 🔹 Enhance Application Performance – Ensure your applications run smoothly by reducing database slowdowns. 🔹 Improve Cost Efficiency – Optimize resource utilization to prevent over-provisioning and reduce costs.
How to Enable Amazon RDS Performance Insights: 1️⃣ Navigate to AWS Management Console. 2️⃣ Select Amazon RDS and choose your database instance. 3️⃣ Click on Modify, then enable Performance Insights under Monitoring. 4️⃣ Choose the retention period (default 7 days, up to 2 years with paid plans). 5️⃣ Save changes and start analyzing real-time database performance!
Who Should Use Amazon RDS Performance Insights? 🔹 Database Administrators (DBAs) – To manage workload distribution and optimize database queries. 🔹 DevOps Engineers – To ensure smooth database operations for applications running on AWS. 🔹 Developers – To analyze slow queries and improve app performance. 🔹 Cloud Architects – To monitor resource utilization and plan database scaling effectively.
Amazon RDS Performance Insights simplifies database monitoring, making it easy to detect issues and optimize workloads for peak efficiency. Start leveraging it today to improve the performance and scalability of your AWS database infrastructure! 🚀
**************************** *Follow Me* https://www.facebook.com/cloudolus/ | https://www.facebook.com/groups/cloudolus | https://www.linkedin.com/groups/14347089/ | https://www.instagram.com/cloudolus/ | https://twitter.com/cloudolus | https://www.pinterest.com/cloudolus/ | https://www.youtube.com/@cloudolus | https://www.youtube.com/@ClouDolusPro | https://discord.gg/GBMt4PDK | https://www.tumblr.com/cloudolus | https://cloudolus.blogspot.com/ | https://t.me/cloudolus | https://www.whatsapp.com/channel/0029VadSJdv9hXFAu3acAu0r | https://chat.whatsapp.com/BI03Rp0WFhqBrzLZrrPOYy *****************************
*🔔Subscribe & Stay Updated:* Don't forget to subscribe and hit the bell icon to receive notifications and stay updated on our latest videos, tutorials & playlists! *ClouDolus:* https://www.youtube.com/@cloudolus *ClouDolus AWS DevOps:* https://www.youtube.com/@ClouDolusPro *THANKS FOR BEING A PART OF ClouDolus! 🙌✨*
#youtube#AmazonRDS RDSPerformanceInsights DatabaseOptimization AWSDevOps ClouDolus CloudComputing PerformanceMonitoring SQLPerformance CloudDatabase#amazon rds database S3 aws devops amazonwebservices free awscourse awstutorial devops awstraining cloudolus naimhossenpro ssl storage cloudc
0 notes
Text
Resolving and Preventing Deadlocks in SQL Server
#Blog post: Resolving and Preventing Deadlocks in #Microsoft #SQLServer #MadeiraData #TSQL #AzureSQL
Deadlocks in SQL Server can be frustrating and can cause significant performance and reliability issues. A deadlock occurs when two or more transactions are waiting for each other to release a lock on a resource, resulting in a situation where no transaction can proceed, and eventually, one of them is automatically killed and rolled back. This can happen when two transactions try to access the…
0 notes
Text
AI-powered WAFs vs traditional firewalls: Protecting your web applications - AI News
New Post has been published on https://thedigitalinsider.com/ai-powered-wafs-vs-traditional-firewalls-protecting-your-web-applications-ai-news/
AI-powered WAFs vs traditional firewalls: Protecting your web applications - AI News
.pp-multiple-authors-boxes-wrapper display:none; img width:100%;
If your business relies on web applications, you’re probably familiar with traditional network firewalls. And for good reason – they play an invaluable role filtering external threats looking to attack your overall infrastructure. But as more and more of your essential operations shift online to intricate web apps and APIs, gaps have opened up that basic firewalls simply can’t see into. The new AI-powered threats of today demand a new approach to security.
Without visibility into your custom application logic and data flows, major vulnerabilities can be exploited, allowing sensitive information theft, financial fraud, and even operational disruption. While you still need perimeter firewall defenses, exclusively relying on them to safeguard increasingly powerful web properties leaves you playing a risky game of chance (with very real consequences).
By adding specialised web application firewalls (WAFs) designed to analyse requests in the full context of your app environments – and enhanced by AI for even greater accuracy – you can lock things down and confidently build out advanced digital capabilities. With a layered defense-in-depth approach combining network and application-level protections, you can securely deliver the types of seamless, personalised digital experiences that form the foundation of lasting customer relationships and operational excellence in 2024.
Gaps in traditional firewall defences
The chances are you already have traditional firewall protection guarding your overall network (if you run any online services). These firewalls filter incoming traffic based on a set of predefined rules focused primarily around protocol, port number, IP address ranges, and basic connection state.
For example, common firewall rules restrict outside access to private intranet resources, block unwanted traffic types like online gaming protocols, detect large-scale network scans, and mitigate distributed denial of service (DDoS) attacks.
This perimeter protection works well for classic network-focused cyberthreats. But a traditional firewall lacks context about the application logic, user workflows, and data structures unique to custom web apps and APIs. It simply scans network packets as they arrive and attempts to allow or block them accordingly. This leaves it vulnerable to the evolving tactics of AI-powered attackers.
Without insight into application internals, major vulnerabilities can sneak right past traditional firewall defences:
SQL injection attacks: Inserting malicious code allowing remote access, data destruction, or information theft
Broken authentication: Enabling unauthorised system access with stolen credentials
Sensitive data exposure: Through improper encryption, backups, or logging
Cross-site scripting (XSS): Injecting JavaScript or HTML to spread malware, hijack sessions, scrape data, or deface sites
Hackers can also target configuration issues, flawed business logic flows, identity management gaps, and unsafe object level access once inside applications themselves. AI-powered attacks can exploit these vulnerabilities with alarming speed and precision—and your firewall wouldn’t see it coming.
These exploitable application flaws allow attackers to steal sensitive business data and personal information, mine cryptocurrency illicitly on servers, hold systems ransom, take over client accounts, and both deny legitimate access and destroy backend resources. AI has only amplified these risks.
Still, traditional firewalls remain extremely important as the first line of network perimeter defence. But for companies conducting operations online through modern web apps, additional safeguards tuned to application threats – and bolstered by AI’s threat detection capabilities – are essential.
Why WAFs provide critical protection
Web application firewalls address the application layer vulnerabilities and holes in logic that basic network firewalls miss. WAFs are designed specifically to protect web apps, APIs, microservices, and rich internet applications. AI further enhances their ability to identify and respond to these threats.
A WAF will deeply inspect all traffic flowing to web properties using targeted rulesets and negative security models defining suspicious behaviour. From there, they analyse requests for indicators of common exploits and attacks seeking to abuse application behaviour and functionality. AI-powered analysis can detect subtle patterns that might otherwise go unnoticed. These might include:
Extreme traffic spikes indicating possible DDoS events
Suspicious geolocations of an IP addresses
Repeated input submissions just below lockout thresholds
Unusual HTTP headers, user agents, or protocols
Known malicious payloads in POST requests
Attempts to traverse directory structures in unpredictable ways
Special characters and patterns indicating SQL injection or cross-site scripting
Advanced WAFs combine this real-time threat detection with global threat intelligence to identify emerging exploits and bad actors as soon as new attack patterns appear. AI and machine learning algorithms even allow some solutions to derive additional behavioral rules by examining your specific application traffic patterns over time. AI’s adaptability is crucial in this constantly shifting landscape.
As traffic passes through, the WAF blocks dangerous requests while allowing legitimate users through with minimal latency impact. This protects the application itself, shielding both data and functionality from compromise. AI-powered WAFs can do this with remarkable speed and accuracy, keeping pace with the ever-changing threat landscape.
Most WAF products also include capabilities like virtual patching, behavioral anomaly detection, automatic policy tuning, third-party integration, and positive security models for detecting verified use cases.
Breaking down the key features of traditional firewalls vs WAFs
Feature Traditional Firewall Web Application Firewall (WAF) Layer of operation Network (Layer 3/4) Application (Layer 7) Traffic analysis Packets, ports, IP addresses HTTP/HTTPS requests, content, parameters, headers Attack protection Network-level attacks Web application-specific attacks (SQLi, XSS, CSRF, etc.) Customisation Limited Extensive Additional capabilities May offer basic intrusion prevention Often include bot mitigation, DDoS protection, API security AI integration Limited or non-existent Considerably more prevalent. Used to enhance threat detection and and incident response
Creating an application security ladder
Web applications underpin many essential business capabilities – internal operations management, customer experience, partner integration – the list goes on. As reliance on these application ecosystems grows, so does business risk exposure through underlying vulnerabilities.
Strengthening application security closes major blindspots while allowing companies to pursue advanced digital transformation supporting key goals around:
Improving self-service and convenience through customer portal expansion
Accelerating development velocity using CI/CD pipelines and microservices
Enabling real-time data exchanges through IoT integrations and open API ecosystems
Increasing revenue with personalised interfaces and recommendation engines
Combining network-layer perimeter defences from traditional firewalls with reinforced protections from specialised WAFs creates a security ladder effect. The traditional firewall filters allowed traffic at the network level based on IPs, protocols, and volume heuristics. This protects against basic attacks like worms, reconnaissance scans, and DDoS events.
Then the WAF takes over at the application layer, scrutinising the full context of requests to identify attempts to exploit app logic and functionality itself using injection attacks, stolen credentials, unusual workflows, or other sneaky techniques security teams encounter daily.
Together, this layered defence-in-depth approach secures both the overall network and the intricate web apps conducting an ever-larger percentage of essential business. Companies can then direct more development resources towards advancing capabilities rather than just patching vulnerabilities.
Final word
The costs of security incidents grow more severe year over year. And as companies rely increasingly on web apps to manage operations, serve customers, and drive revenue, application vulnerabilities present a serious (and immediate) business risk.
Protecting systems with advanced application-aware defenses – powered by AI – means that your security supports rather than gets in the way of your key strategic initiatives
With scalable and secure defenses guarding your web properties, you can confidently build capabilities supporting goals around better customer experience, smoother operations, increased sales growth, and expanded partner channels. In other words, you can focus on pushing your business forward with the peace of mind knowing that you’ve done your part in securing your perimeter and web apps in our ever AI-driven world.
#2024#Accounts#agents#ai#ai news#AI-powered#Algorithms#Analysis#anomaly detection#API#APIs#app#application layer#Application Security#applications#approach#apps#Articles#Artificial Intelligence#attackers#authentication#backups#bot#Business#CI/CD#code#Companies#compromise#content#credentials
0 notes
Text
R3 Architecture in SAP Basis

Understanding SAP R/3 Architecture: A SAP Basis Guide
SAP R/3 is the cornerstone of many enterprise systems worldwide. Its robust and scalable architecture is what gives R/3 its staying power and adaptability across industries. As a SAP Basis professional, understanding the R/3 architecture is a fundamental skill for effective administration and system management. Let’s delve deeper into this crucial aspect of SAP systems.
What is SAP R/3?
SAP R/3, commonly referred to as just R/3, stands for Systems, Applications, and Products in Real-time Data Processing. This powerful Enterprise Resource Planning (ERP) software suite seamlessly integrates various business functions like finance, manufacturing, human resources, supply chain, and more. Its three-tier architecture provides a flexible and modular framework for businesses to operate efficiently.
The Three Tiers of SAP R/3 Architecture
The SAP R/3 architecture is divided into three distinct layers:
Presentation Layer (Presentation Server)
The presentation layer is where users interact with the SAP system. It’s responsible for the visual interface and input/output handling.
The primary component here is the SAP GUI (Graphical User Interface), a desktop application that gives users access to SAP modules and transactions.
Web-based access through SAP GUI for HTML or browser-based applications is also supported.
Application Layer (Application Server)
The heart of the R/3 system, the application layer is where all the core business logic, processing, and calculations occur.
It’s comprised of multiple application servers (instances) that handle user requests, interpret ABAP code (SAP’s programming language), and communicate with the database layer.
Key components within this layer include:Dispatcher: Distributes incoming user requests to available work processes.
Work Processes: Handle the actual execution of ABAP programs and dialogs.
Gateway: Enables communication between SAP instances and with external systems.
Message Server: Facilitates communication between application servers, balancing the load.
Enqueue Server: Manages logical locks on the database to ensure data consistency.
Database Layer (Database Server)
This layer is responsible for storing all the business data within the SAP system.
Popular database choices for R/3 include Oracle, IBM DB2, Microsoft SQL Server, and SAP HANA (SAP’s in-memory database).
The database layer handles data persistence, retrieval, and ensures data integrity.
Benefits of the Three-Tier Architecture
Scalability: The three-tier design allows for easy addition of resources (like application servers) to handle increasing business demands.
Flexibility: The separation of concerns allows for independent updates and maintenance of different layers.
Security: The presentation layer can be isolated from the database, enhancing security and reducing potential attack surfaces.
Platform Independence: SAP R/3 systems can usually operate on various operating systems and database platforms.
The Role of SAP Basis in R/3 Architecture
SAP Basis administrators are essential for:
Installation and Configuration: Setting up and fine-tuning the R/3 environment across the three tiers.
System Monitoring: Ensuring the health and optimal performance of the R/3 system.
Troubleshooting: Identifying and resolving issues across any layer of the architecture.
Performance Optimization: Implementing measures to improve system and application speed
User Management: Administering user accounts, roles, and authorizations.
Conclusion
A deep understanding of SAP’s R/3 architecture is paramount for any SAP Basis professional. Knowing the interaction and purpose of these layers forms the backbone of effective system management and ensures a smooth and efficient SAP landscape for the business..
youtube
You can find more information about SAP BASIS in this SAP BASIS Link
Conclusion:
Unogeeks is the No.1 IT Training Institute for SAP BASIS Training. Anyone Disagree? Please drop in a comment
You can check out our other latest blogs on SAP BASIS here – SAP BASIS Blogs
You can check out our Best In Class SAP BASIS Details here – SAP BASIS Training
Follow & Connect with us:
———————————-
For Training inquiries:
Call/Whatsapp: +91 73960 33555
Mail us at: [email protected]
Our Website ➜ https://unogeeks.com
Follow us:
Instagram: https://www.instagram.com/unogeeks
Facebook:https://www.facebook.com/UnogeeksSoftwareTrainingInstitute
Twitter: https://twitter.com/unogeek
#Unogeeks #training #Unogeekstraining
1 note
·
View note
Text
Microsoft SQL Server Consultants that Streamline Your Server Needs
Data management is a key aspect that determines the success or failure of an organization.
Databases play an essential role in efficiently managing business operations, and your business needs to have a reliable database management system in place.
That’s where you can trust Microsoft SQL Server.
However, managing and optimizing SQL Server databases can be daunting, requiring expertise and experience.
But with professional Microsoft SQL Server consultants, you can achieve optimal performance and cost-effectiveness.
How?
Let’s find out.
Who Are Microsoft SQL Server Consultants?
Microsoft SQL Consultants are experts in database management who provide consulting services to businesses seeking to optimize their SQL Server databases.
These consultants have a deep understanding of the intricacies of SQL Server databases and are proficient in various database management tools and technologies.
They can help your business improve its database management processes and optimize SQL Server database performance to ensure smooth operations and cost-effectiveness.
Like detectives, SQL Server consultants are constantly hunting for clues to improve performance and solve problems. They dive deep into the inner workings of databases to uncover hidden issues and optimize performance.
They use their analytical skills to identify patterns, trends, and anomalies that can help your business make better decisions and gain a competitive edge.
Here’s the compilation of the tasks they can handle:
Database design and architecture Performance tuning and optimization Data migration and integration Security and access control Backup and disaster recovery planning SQL Server upgrades and migrations Business intelligence and reporting Custom development and scripting
Microsoft SQL Server consultants are the creative geniuses behind some of the most powerful and impactful technology solutions in the business world. They combine technical expertise with artistic vision to create digital art that can help your business thrive and grow.
Why Does Your Business Require Microsoft SQL Server Business Consulting?
There are several reasons your business may require Microsoft SQL Server business consulting. Here are some creative and detailed points to consider:
1. Optimizing Database Performance Microsoft SQL Server consultants can help you optimize your database’s performance, ensuring it runs smoothly and efficiently. They can help identify and address slow queries, database locks, and other performance bottlenecks.
Optimizing your database performance can reduce latency and improve the overall user experience. It can include tuning memory, I/O, and CPU usage and configuring indexes and statistics to improve query performance. They can also help you configure the database server and storage subsystem for optimal performance.
2. Data Management Effective data management is crucial for businesses of all sizes, and Microsoft SQL Server consultants can help you with this. They can assist with designing and implementing database schemas, managing data quality, and ensuring that data is adequately backed up and secured.
They can also help you manage data quality by implementing data validation and cleansing routines, profiling, and auditing. Consultants can also assist you in developing data governance policies, data retention policies, and disaster recovery plans to ensure that your data is secure and accessible at all times.
3. Integration with Other Systems Integration with other systems is a common use case for Microsoft SQL Server. Consultants can help you integrate your database with other systems by designing and implementing APIs, data connectors, or ETL processes.
They can also help you integrate your database with third-party software, like ERP or CRM. Integrating your database with other systems can improve data accuracy and consistency, reduce data silos, and streamline business processes.
4. Business Intelligence and Reporting Microsoft SQL Server is a powerful tool for business intelligence and reporting; consultants can help you leverage this capability to gain valuable insights into your business. They can help you design and build data warehouses, develop reports and dashboards, and implement data mining and analysis.
Professional SQL Server consultants can help you develop data-driven decision-making processes and strategies. With effective business intelligence and reporting, you can gain valuable insights into your business, identify trends and patterns, and make informed decisions that drive growth.
5. Migration and Upgrades Suppose you are currently using an older version of SQL Server or considering migrating to SQL Server from another database platform. In that case, Microsoft SQL Server consultants can help you plan and execute a smooth migration. They can also assist with upgrading to the latest version of SQL Server, ensuring you take advantage of the latest features and capabilities.
6. Security and Compliance Data security and compliance are critical concerns for businesses, and Microsoft SQL Server consultants can help you ensure that your database is secure and compliant. They can help you implement access controls, encryption, and other security measures and ensure you comply with relevant regulations, such as GDPR or HIPAA.
For example, if your business is subject to GDPR, a SQL Server consultant can help you implement data retention policies, pseudonymization, and other features that comply with GDPR. They can also help you perform security audits and penetration testing to identify and remediate vulnerabilities in your database.
7. Custom Development Microsoft SQL Server consultants can help you develop custom applications and scripts to automate tasks, improve performance, or add new functionality to your database. This can be especially valuable if you have unique business requirements that off-the-shelf software cannot meet.
Read More: https://www.integrativesystems.com/capabilities/microsoft-sql-server-services/
#microsoft sql server consultants#sql server consulting services#sql server consultancy#sql database consultants#sql server consulting#microsoft sql server consulting
0 notes
Text
SQL Job Support: Troubleshooting Common Database Issues
Introduction:
SQL (Structured Query Language) is the backbone of many modern applications and databases, making it a critical skill for professionals in the field of data management and software development. However, even with the best-designed databases, issues can arise, leading to problems that require careful troubleshooting. In this article, we will delve into the world of��SQL job support, specifically focusing on troubleshooting common database issues. Our aim is to provide you with a comprehensive guide on identifying, diagnosing, and resolving these issues effectively without resorting to keyword stuffing.
Common Database Issues:
Performance Degradation:
Description: One of the most prevalent issues with databases is performance degradation over time. Slow queries and high response times can severely impact application efficiency.
Troubleshooting:
Analyze query execution plans to identify bottlenecks.
Examine indexing strategies and ensure they are optimized.
Monitor hardware resource utilization (CPU, RAM, I/O).
Review the use of caching mechanisms for query optimization.
Locking and Deadlocks:
Description: Locking issues occur when multiple transactions try to access the same resource simultaneously. Deadlocks are a specific type of locking issue where two or more transactions are stuck in a circular waiting state.
Troubleshooting:
Utilize SQL Server Profiler to capture deadlock graphs.
Adjust isolation levels for transactions.
Refactor queries to minimize contention on shared resources.
Implement proper transaction management.
Data Corruption:
Description: Data corruption can result from hardware failures, software bugs, or other factors. It can lead to data loss and integrity issues.
Troubleshooting:
Run consistency checks using DBCC commands.
Regularly back up and validate data integrity.
Monitor hardware health and replace failing components.
Keep software and database systems up-to-date.
Backup and Restore Failures:
Description: Failed backup and restore operations can result in data loss and downtime.
Troubleshooting:
Check for sufficient disk space for backups.
Review backup and restore logs for error messages.
Verify file paths and permissions.
Test backup and restore procedures in a non-production environment.
Query Optimization:
Description: Inefficient queries can lead to high resource consumption and slow performance.
Troubleshooting:
Analyze query execution plans and identify costly operations.
Use appropriate indexing and statistics.
Rewrite or refactor queries for better performance.
Implement caching mechanisms to reduce query load.
Security Concerns:
Description: Security breaches and unauthorized access can have severe consequences.
Troubleshooting:
Regularly audit and review user permissions.
Implement strong password policies.
Monitor for unusual login activity and security events.
Keep software and security patches up-to-date.
Data Migration Issues:
Description: Data migration projects can result in data loss or integrity problems if not executed correctly.
Troubleshooting:
Plan and test data migration thoroughly before execution.
Validate data on the target system.
Maintain backups of the original data.
Ensure proper transformation and data mapping.
Conclusion:
SQL proxy job support is a crucial function in maintaining the health and performance of databases. By understanding and effectively troubleshooting common database issues, professionals can keep their systems running smoothly and mitigate potential risks. While it's important to be aware of the various keywords associated with SQL job support from India, the focus should always be on addressing the root causes of problems and providing meaningful solutions.
0 notes
Text
Should You Change Lock Escalation Behavior to Fix SQL Server Blocking Issues?
Introduction Have you ever encountered blocking problems in your SQL Server databases due to lock escalation? As a DBA, I certainly have! Lock escalation can cause queries to grind to a halt as they wait for locks, slowing down the entire system. It’s a frustrating issue, but luckily there are ways to address it. In this article, we’ll take an in-depth look at lock escalation – what causes it,…
View On WordPress
0 notes
Text
Locking the Digital Doors: Understanding Web and Mobile App Security

In our digital world, apps on our phones and websites we visit are like doors to a house. But just like we lock our doors to keep bad guys out, we need to protect these apps from cyber bad guys. One way we do this is through something called a Web Application Firewall, which acts like a security guard for our apps. It stops the bad guys from sneaking in and causing trouble.
Another important thing to know is that these apps talk to each other using something called APIs. APIs help them share information. But if not handled carefully, they can accidentally spill sensitive information. OWASP help us understand the risks associated with these APIs, so we can make sure our apps are safe and sound. Together, let’s learn more about keeping our apps safe and our digital world secure!
Web and Mobile application Security
Securing web and mobile applications is crucial to protect sensitive data and ensure user safety. Here are the top 10 things to do:
Authentication and Authorization: Implement strong user authentication and authorization mechanisms to ensure that only authorized users can access certain features or data.
Data Encryption: Use encryption techniques (SSL/TLS) to protect data transmission between the client and server. Also, encrypt sensitive data at rest.
Input Validation: Validate and sanitize all user inputs to prevent common vulnerabilities like SQL injection and cross-site scripting (XSS).
Session Management: Implement secure session management practices to prevent session hijacking and fixation attacks.
API Security: Secure your APIs with authentication tokens, rate limiting, and proper access controls. Use API keys or OAuth for authorization.
Code Review and Testing: Regularly review and test your code for vulnerabilities. Use static analysis and dynamic testing tools to identify and fix security issues.
Patch Management: Keep all software components, libraries, and frameworks up to date with the latest security patches.
Error Handling: Implement proper error handling to avoid revealing sensitive information in error messages.
Security Headers: Use security headers like Content Security Policy (CSP), HTTP Strict Transport Security (HSTS), and Cross-Origin Resource Sharing (CORS) to control browser behavior.
Security Training and Awareness: Train your development and QA teams in secure coding practices and keep them updated on the latest security threats and best practices.
Regular security audits and penetration testing should also be part of your security strategy to proactively identify and mitigate vulnerabilities in your web and mobile applications.

2. Top 10 OWASP API Security Risk
The Open Web Application Security Project (OWASP) provides a list of the top 10 most critical web application security and API Risk official website (https://owasp.org)
API1:2023 – Broken Object Level Authorization–
APIs tend to expose endpoints that handle object identifiers, creating a wide attack surface of Object Level Access Control issues. Object level authorization checks should be considered in every function that accesses a data source using an ID from the user.
API2:2023 – Broken Authentication–
Authentication mechanisms are often implemented incorrectly, allowing attackers to compromise authentication tokens or to exploit implementation flaws to assume other user’s identities temporarily or permanently. Compromising a system’s ability to identify the client/user, compromises API security overall
API3:2023 – Broken Object Property Level Authorization–
This category combines API3:2019 Excessive Data Exposure and API6:2019 – Mass Assignment, focusing on the root cause: the lack of or improper authorization validation at the object property level. This leads to information exposure or manipulation by unauthorized parties.
API4:2023 – Unrestricted Resource Consumption–
Satisfying API requests requires resources such as network bandwidth, CPU, memory, and storage. Other resources such as emails/SMS/phone calls or biometrics validation are made available by service providers via API integrations, and paid for per request. Successful attacks can lead to Denial of Service or an increase of operational costs.
API5:2023 – Broken Function Level Authorization–
Complex access control policies with different hierarchies, groups, and roles, and an unclear separation between administrative and regular functions, tend to lead to authorization flaws. By exploiting these issues, attackers can gain access to other users’ resources and/or administrative functions
API6:2023 – Unrestricted Access to Sensitive Business Flows–
APIs vulnerable to this risk expose a business flow – such as buying a ticket, or posting a comment – without compensating for how the functionality could harm the business if used excessively in an automated manner. This doesn’t necessarily come from implementation bugs.
API7:2023 – Server Side Request Forgery–
Server-Side Request Forgery (SSRF) flaws can occur when an API is fetching a remote resource without validating the user-supplied URI. This enables an attacker to coerce the application to send a crafted request to an unexpected destination, even when protected by a firewall or a VPN.
API8:2023 – Security Misconfiguration–
APIs and the systems supporting them typically contain complex configurations, meant to make the APIs more customizable. Software and DevOps engineers can miss these configurations, or don’t follow security best practices when it comes to configuration, opening the door for different types of attacks.
API9:2023 – Improper Inventory Management–
APIs tend to expose more endpoints than traditional web applications, making proper and updated documentation highly important. A proper inventory of hosts and deployed API versions also are important to mitigate issues such as deprecated API versions and exposed debug endpoints.
API10:2023 – Unsafe Consumption of APIs–
Developers tend to trust data received from third-party APIs more than user input, and so tend to adopt weaker security standards. In order to compromise APIs, attackers go after integrated third-party services instead of trying to compromise the target API directly.
3. Importance of WAF web application firewall
A Web Application Firewall (WAF) is a crucial component in modern cybersecurity, primarily focused on protecting web applications from a variety of online threats and attacks. Here are several key reasons highlighting the importance of WAF:
Protection from Web Application Attacks: WAFs are designed to defend against common web application attacks, including SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and more. These attacks can compromise data integrity, steal sensitive information, or disrupt application functionality.
Zero-Day Attack Mitigation: WAFs can detect and mitigate new and emerging threats, even before patches or security updates are available. They do this by analyzing incoming traffic patterns and behavior anomalies.
Reduced Attack Surface: By filtering and monitoring incoming web traffic, WAFs help reduce the attack surface of web applications. They can block malicious requests before they reach the application server, minimizing the risk of exploitation.
DDoS Attack Mitigation: Some advanced WAFs have Distributed Denial of Service (DDoS) protection capabilities. They can identify and mitigate large-scale traffic floods, helping maintain service availability during attacks.
Compliance Requirements: Many regulatory standards and compliance frameworks, such as PCI DSS and HIPAA, mandate the use of security measures like WAFs to protect sensitive data. Implementing a WAF can help organizations meet these requirements.
Logging and Auditing: WAFs provide detailed logs of incoming traffic and blocked threats. These logs can be invaluable for security audits, incident response, and forensic analysis.
Real-Time Threat Monitoring: WAFs offer real-time monitoring of web traffic, enabling security teams to identify and respond to threats quickly. They can trigger alerts or automated responses to specific attack patterns.
Traffic Normalization: WAFs can normalize incoming traffic, filtering out malicious or malformed requests. This helps ensure that only legitimate, well-formed requests reach the application, improving its overall stability.
Protection for Legacy Applications: WAFs can protect older or legacy web applications that may not have been built with modern security practices in mind. They act as an additional layer of security for such applications.
Cost-Efficient Security: Implementing a WAF can be more cost-effective than addressing vulnerabilities and responding to security incidents after an attack has occurred. It provides proactive, continuous protection.
In summary, a Web Application Firewall is a critical security component for safeguarding web applications from a wide range of threats. It helps organizations maintain the confidentiality, integrity, and availability of their web services and sensitive data.
Simple antivirus software is designed primarily to detect and remove known malware and viruses based on predefined signatures and patterns. While antivirus programs are important for basic protection, they have limitations that make them insufficient in today’s complex cybersecurity landscape.
Here’s why EDR (Endpoint Detection and Response) is necessary:
1.Limited Detection Capabilities: Antivirus relies on known signatures and patterns to identify threats. It may miss zero-day attacks and sophisticated malware that haven’t been previously identified.
2.Lack of Behavioral Analysis: EDR solutions monitor the behavior of files and processes on an endpoint. They can detect suspicious activities, such as unusual system behavior or data exfiltration, even if there are no known malware signatures involved.
3.Advanced Threats: EDR solutions are better equipped to detect advanced threats like fileless malware and polymorphic malware that can change their code to evade traditional antivirus scans.
4.Incident Response: EDR provides real-time monitoring and alerting, helping organizations respond quickly to security incidents. Antivirus software typically lacks these features.
5.Visibility and Investigation: EDR solutions provide detailed information about endpoint activity, allowing security teams to investigate incidents thoroughly, trace the source of an attack, and understand its scope.
6.Threat Hunting: EDR enables proactive threat hunting. Security analysts can search for signs of compromise and anomalies to detect threats that may have gone unnoticed by traditional antivirus.
7.Compliance and Reporting: EDR solutions often provide extensive reporting capabilities, which are crucial for compliance with data protection regulations and for demonstrating a proactive approach to security.
8.Adaptive Protection: EDR can adapt its response to evolving threats, applying behavioral analysis and machine learning to identify new attack patterns.
In summary, while antivirus software is a fundamental layer of protection, EDR complements it by offering advanced threat detection, real-time monitoring, incident response capabilities, and the ability to investigate and mitigate complex security incidents. In today’s rapidly evolving threat landscape, EDR is a critical component of a comprehensive cybersecurity strategy.
This blog emphasizes the critical importance of securing web and mobile applications in our digital era. It highlights the escalating threat landscape targeting crucial elements of our digital infrastructure. APIs (Application Programming Interfaces) are crucial for application functionality but can pose significant security risks if not adequately protected. The OWASP API Security Top 10 is a vital resource that sheds light on prevalent vulnerabilities in the API landscape. The blog delves into these risks, providing a comprehensive analysis of their implications and suggesting potential solutions. Additionally, the blog underlines the fundamental role of a Web Application Firewall (WAF) in enhancing digital security by monitoring and filtering traffic, acting as a defense against cyber threats. It invites readers to join this journey to enhance their understanding of web and mobile application security, fostering a safer digital future.
0 notes
Text
Which Is The Best PostgreSQL GUI? 2021 Comparison
PostgreSQL graphical user interface (GUI) tools help open source database users to manage, manipulate, and visualize their data. In this post, we discuss the top 6 GUI tools for administering your PostgreSQL hosting deployments. PostgreSQL is the fourth most popular database management system in the world, and heavily used in all sizes of applications from small to large. The traditional method to work with databases is using the command-line interface (CLI) tool, however, this interface presents a number of issues:
It requires a big learning curve to get the best out of the DBMS.
Console display may not be something of your liking, and it only gives very little information at a time.
It is difficult to browse databases and tables, check indexes, and monitor databases through the console.
Many still prefer CLIs over GUIs, but this set is ever so shrinking. I believe anyone who comes into programming after 2010 will tell you GUI tools increase their productivity over a CLI solution.
Why Use a GUI Tool?
Now that we understand the issues users face with the CLI, let’s take a look at the advantages of using a PostgreSQL GUI:
Shortcut keys make it easier to use, and much easier to learn for new users.
Offers great visualization to help you interpret your data.
You can remotely access and navigate another database server.
The window-based interface makes it much easier to manage your PostgreSQL data.
Easier access to files, features, and the operating system.
So, bottom line, GUI tools make PostgreSQL developers’ lives easier.
Top PostgreSQL GUI Tools
Today I will tell you about the 6 best PostgreSQL GUI tools. If you want a quick overview of this article, feel free to check out our infographic at the end of this post. Let’s start with the first and most popular one.
1. pgAdmin
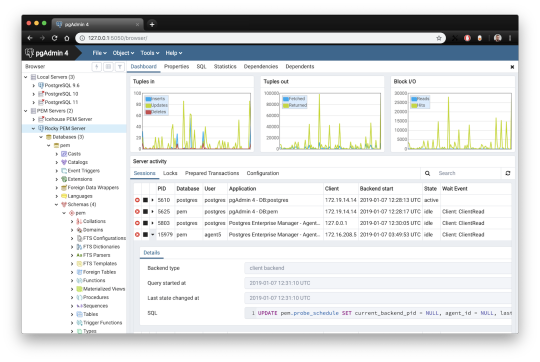
pgAdmin is the de facto GUI tool for PostgreSQL, and the first tool anyone would use for PostgreSQL. It supports all PostgreSQL operations and features while being free and open source. pgAdmin is used by both novice and seasoned DBAs and developers for database administration.
Here are some of the top reasons why PostgreSQL users love pgAdmin:
Create, view and edit on all common PostgreSQL objects.
Offers a graphical query planning tool with color syntax highlighting.
The dashboard lets you monitor server activities such as database locks, connected sessions, and prepared transactions.
Since pgAdmin is a web application, you can deploy it on any server and access it remotely.
pgAdmin UI consists of detachable panels that you can arrange according to your likings.
Provides a procedural language debugger to help you debug your code.
pgAdmin has a portable version which can help you easily move your data between machines.
There are several cons of pgAdmin that users have generally complained about:
The UI is slow and non-intuitive compared to paid GUI tools.
pgAdmin uses too many resources.
pgAdmin can be used on Windows, Linux, and Mac OS. We listed it first as it’s the most used GUI tool for PostgreSQL, and the only native PostgreSQL GUI tool in our list. As it’s dedicated exclusively to PostgreSQL, you can expect it to update with the latest features of each version. pgAdmin can be downloaded from their official website.
pgAdmin Pricing: Free (open source)
2. DBeaver

DBeaver is a major cross-platform GUI tool for PostgreSQL that both developers and database administrators love. DBeaver is not a native GUI tool for PostgreSQL, as it supports all the popular databases like MySQL, MariaDB, Sybase, SQLite, Oracle, SQL Server, DB2, MS Access, Firebird, Teradata, Apache Hive, Phoenix, Presto, and Derby – any database which has a JDBC driver (over 80 databases!).
Here are some of the top DBeaver GUI features for PostgreSQL:
Visual Query builder helps you to construct complex SQL queries without actual knowledge of SQL.
It has one of the best editors – multiple data views are available to support a variety of user needs.
Convenient navigation among data.
In DBeaver, you can generate fake data that looks like real data allowing you to test your systems.
Full-text data search against all chosen tables/views with search results shown as filtered tables/views.
Metadata search among rows in database system tables.
Import and export data with many file formats such as CSV, HTML, XML, JSON, XLS, XLSX.
Provides advanced security for your databases by storing passwords in secured storage protected by a master password.
Automatically generated ER diagrams for a database/schema.
Enterprise Edition provides a special online support system.
One of the cons of DBeaver is it may be slow when dealing with large data sets compared to some expensive GUI tools like Navicat and DataGrip.
You can run DBeaver on Windows, Linux, and macOS, and easily connect DBeaver PostgreSQL with or without SSL. It has a free open-source edition as well an enterprise edition. You can buy the standard license for enterprise edition at $199, or by subscription at $19/month. The free version is good enough for most companies, as many of the DBeaver users will tell you the free edition is better than pgAdmin.
DBeaver Pricing
: Free community, $199 standard license
3. OmniDB
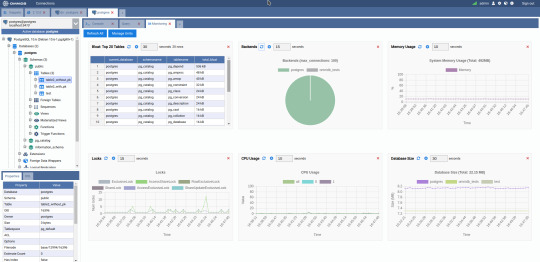
The next PostgreSQL GUI we’re going to review is OmniDB. OmniDB lets you add, edit, and manage data and all other necessary features in a unified workspace. Although OmniDB supports other database systems like MySQL, Oracle, and MariaDB, their primary target is PostgreSQL. This open source tool is mainly sponsored by 2ndQuadrant. OmniDB supports all three major platforms, namely Windows, Linux, and Mac OS X.
There are many reasons why you should use OmniDB for your Postgres developments:
You can easily configure it by adding and removing connections, and leverage encrypted connections when remote connections are necessary.
Smart SQL editor helps you to write SQL codes through autocomplete and syntax highlighting features.
Add-on support available for debugging capabilities to PostgreSQL functions and procedures.
You can monitor the dashboard from customizable charts that show real-time information about your database.
Query plan visualization helps you find bottlenecks in your SQL queries.
It allows access from multiple computers with encrypted personal information.
Developers can add and share new features via plugins.
There are a couple of cons with OmniDB:
OmniDB lacks community support in comparison to pgAdmin and DBeaver. So, you might find it difficult to learn this tool, and could feel a bit alone when you face an issue.
It doesn’t have as many features as paid GUI tools like Navicat and DataGrip.
OmniDB users have favorable opinions about it, and you can download OmniDB for PostgreSQL from here.
OmniDB Pricing: Free (open source)
4. DataGrip

DataGrip is a cross-platform integrated development environment (IDE) that supports multiple database environments. The most important thing to note about DataGrip is that it’s developed by JetBrains, one of the leading brands for developing IDEs. If you have ever used PhpStorm, IntelliJ IDEA, PyCharm, WebStorm, you won’t need an introduction on how good JetBrains IDEs are.
There are many exciting features to like in the DataGrip PostgreSQL GUI:
The context-sensitive and schema-aware auto-complete feature suggests more relevant code completions.
It has a beautiful and customizable UI along with an intelligent query console that keeps track of all your activities so you won’t lose your work. Moreover, you can easily add, remove, edit, and clone data rows with its powerful editor.
There are many ways to navigate schema between tables, views, and procedures.
It can immediately detect bugs in your code and suggest the best options to fix them.
It has an advanced refactoring process – when you rename a variable or an object, it can resolve all references automatically.
DataGrip is not just a GUI tool for PostgreSQL, but a full-featured IDE that has features like version control systems.
There are a few cons in DataGrip:
The obvious issue is that it’s not native to PostgreSQL, so it lacks PostgreSQL-specific features. For example, it is not easy to debug errors as not all are able to be shown.
Not only DataGrip, but most JetBrains IDEs have a big learning curve making it a bit overwhelming for beginner developers.
It consumes a lot of resources, like RAM, from your system.
DataGrip supports a tremendous list of database management systems, including SQL Server, MySQL, Oracle, SQLite, Azure Database, DB2, H2, MariaDB, Cassandra, HyperSQL, Apache Derby, and many more.
DataGrip supports all three major operating systems, Windows, Linux, and Mac OS. One of the downsides is that JetBrains products are comparatively costly. DataGrip has two different prices for organizations and individuals. DataGrip for Organizations will cost you $19.90/month, or $199 for the first year, $159 for the second year, and $119 for the third year onwards. The individual package will cost you $8.90/month, or $89 for the first year. You can test it out during the free 30 day trial period.
DataGrip Pricing
: $8.90/month to $199/year
5. Navicat

Navicat is an easy-to-use graphical tool that targets both beginner and experienced developers. It supports several database systems such as MySQL, PostgreSQL, and MongoDB. One of the special features of Navicat is its collaboration with cloud databases like Amazon Redshift, Amazon RDS, Amazon Aurora, Microsoft Azure, Google Cloud, Tencent Cloud, Alibaba Cloud, and Huawei Cloud.
Important features of Navicat for Postgres include:
It has a very intuitive and fast UI. You can easily create and edit SQL statements with its visual SQL builder, and the powerful code auto-completion saves you a lot of time and helps you avoid mistakes.
Navicat has a powerful data modeling tool for visualizing database structures, making changes, and designing entire schemas from scratch. You can manipulate almost any database object visually through diagrams.
Navicat can run scheduled jobs and notify you via email when the job is done running.
Navicat is capable of synchronizing different data sources and schemas.
Navicat has an add-on feature (Navicat Cloud) that offers project-based team collaboration.
It establishes secure connections through SSH tunneling and SSL ensuring every connection is secure, stable, and reliable.
You can import and export data to diverse formats like Excel, Access, CSV, and more.
Despite all the good features, there are a few cons that you need to consider before buying Navicat:
The license is locked to a single platform. You need to buy different licenses for PostgreSQL and MySQL. Considering its heavy price, this is a bit difficult for a small company or a freelancer.
It has many features that will take some time for a newbie to get going.
You can use Navicat in Windows, Linux, Mac OS, and iOS environments. The quality of Navicat is endorsed by its world-popular clients, including Apple, Oracle, Google, Microsoft, Facebook, Disney, and Adobe. Navicat comes in three editions called enterprise edition, standard edition, and non-commercial edition. Enterprise edition costs you $14.99/month up to $299 for a perpetual license, the standard edition is $9.99/month up to $199 for a perpetual license, and then the non-commercial edition costs $5.99/month up to $119 for its perpetual license. You can get full price details here, and download the Navicat trial version for 14 days from here.
Navicat Pricing
: $5.99/month up to $299/license
6. HeidiSQL
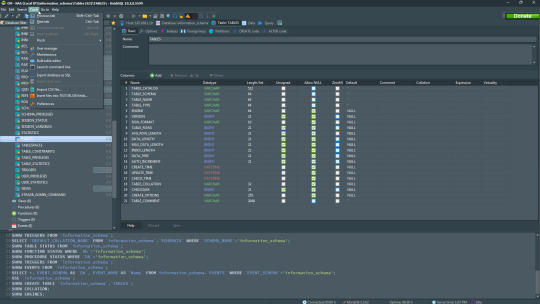
HeidiSQL is a new addition to our best PostgreSQL GUI tools list in 2021. It is a lightweight, free open source GUI that helps you manage tables, logs and users, edit data, views, procedures and scheduled events, and is continuously enhanced by the active group of contributors. HeidiSQL was initially developed for MySQL, and later added support for MS SQL Server, PostgreSQL, SQLite and MariaDB. Invented in 2002 by Ansgar Becker, HeidiSQL aims to be easy to learn and provide the simplest way to connect to a database, fire queries, and see what’s in a database.
Some of the advantages of HeidiSQL for PostgreSQL include:
Connects to multiple servers in one window.
Generates nice SQL-exports, and allows you to export from one server/database directly to another server/database.
Provides a comfortable grid to browse and edit table data, and perform bulk table edits such as move to database, change engine or ollation.
You can write queries with customizable syntax-highlighting and code-completion.
It has an active community helping to support other users and GUI improvements.
Allows you to find specific text in all tables of all databases on a single server, and optimize repair tables in a batch manner.
Provides a dialog for quick grid/data exports to Excel, HTML, JSON, PHP, even LaTeX.
There are a few cons to HeidiSQL:
Does not offer a procedural language debugger to help you debug your code.
Built for Windows, and currently only supports Windows (which is not a con for our Windors readers!)
HeidiSQL does have a lot of bugs, but the author is very attentive and active in addressing issues.
If HeidiSQL is right for you, you can download it here and follow updates on their GitHub page.
HeidiSQL Pricing: Free (open source)
Conclusion
Let’s summarize our top PostgreSQL GUI comparison. Almost everyone starts PostgreSQL with pgAdmin. It has great community support, and there are a lot of resources to help you if you face an issue. Usually, pgAdmin satisfies the needs of many developers to a great extent and thus, most developers do not look for other GUI tools. That’s why pgAdmin remains to be the most popular GUI tool.
If you are looking for an open source solution that has a better UI and visual editor, then DBeaver and OmniDB are great solutions for you. For users looking for a free lightweight GUI that supports multiple database types, HeidiSQL may be right for you. If you are looking for more features than what’s provided by an open source tool, and you’re ready to pay a good price for it, then Navicat and DataGrip are the best GUI products on the market.
Ready for some PostgreSQL automation?
See how you can get your time back with fully managed PostgreSQL hosting. Pricing starts at just $10/month.
While I believe one of these tools should surely support your requirements, there are other popular GUI tools for PostgreSQL that you might like, including Valentina Studio, Adminer, DB visualizer, and SQL workbench. I hope this article will help you decide which GUI tool suits your needs.
Which Is The Best PostgreSQL GUI? 2019 Comparison
Here are the top PostgreSQL GUI tools covered in our previous 2019 post:
pgAdmin
DBeaver
Navicat
DataGrip
OmniDB
Original source: ScaleGrid Blog
3 notes
·
View notes
Text
HTB - Bastard
Another Windows machine down; again, I can’t say this was particularly difficult.
It has a rating of medium but I’m unsure why if I’m honest...Perhaps there’s more resources out on the two attack vectors?
It took me a little longer than I’m happy with but I’m afraid web apps are where I lack at the moment- I spent a considerable amount of time checking for SQL injection, XML-RPC weaknesses and it also doesn’t help that my Kali Linux VM can’t connect to Ruby servers for downloading Ruby libraries (or gems)- after spending some time attempting to solve that issue I simply hopped over to my host to get the bastard rooted. ;P
So, my enum script (since made amendments to this: it wasn’t picking up some files it should have such as robots.txt) and then manual checks:

There are 3 logon forms- one to login, one to register and one for password resets- and some misc web app config files such as CHANGELOG.txt and robots.txt.
CHANGELOG reveals that Drupal is running on version 7.54 while robots shows an array of disallowed URLs.
Firstly, I performed some checks on the present forms and I did discover the existence of user ‘admin’ via the password reset form: existing users can be enumerated as the server will respond with username/email not recognized for non-existent usernames and an error on sending a reset email to valid usernames.
I played around with both this and the login form for a while- tried some classic SQL injection cases and alike; unfortunately for us, we’re temporarily locked out if we enter the incorrect password 5 times.
Now this is a shame for the brute force queen... My first thought with login forms is brute force if there doesn’t seem to be any other vectors present. Taking this as a sign that I was barking up the wrong tree, I moved on to instead seeing if there were any other users on the server by utilizing a username brute force script I have in Bash on the password reset form while I looked around a bit more.
It was around here I ran into drupwn- a Drupal web API enumeration tool written in Python. It’s a bit rubbish to be honest as it has a tendency to hang and requires you to manually stop the running process; it did reveal that my enum script had missed robots.txt and CHANGELOG in it’s execution (since been amended.)
It also revealed the version of Drupal in-use; the script probably just looked through CHANGELOG and grabbed the mentioned version.
I did look into these files but robots had alot of entries that -as an inexperienced web app hacker- would have taken me hours to manually test while CHANGELOG revealed nothing but the version of Drupal in-use.
With the version of Drupal identified, however, this did mean that searching for public exploits was a great deal easier. I took to searchsploit -a native Kali Linux tool- and discovered several Drupal exploits:
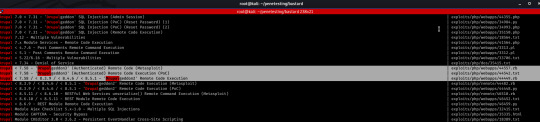
Here we see mentioned Drupalgeddon3 and 2; by process of elimination we know 3 wouldn’t work due to a lack of valid credentials. If any, the vulnerability in question is exploited by Drupalg2.
Drupalgeddon2 (https://github.com/dreadlocked/Drupalgeddon2) is a remote-code execution vulnerability resulting from a lack of input validation on form API AJAX requests. This allows users to inject malicious payloads -in the form of renderable arrays- into the create user form.
In the case of the registration form, this applies to the mail parameter- by setting the values of indexes [#post_render][] to exec, [#type] to markup and ][#markup] to our desired system command we gain RCE (I briefly just tried to exploit this manually but I simply used dev tools within FireFox browser, probably would have succeeded if I’d tried through Burp Proxy or similar!)
It was at this point that I had to switch over to my host to finish up; honestly at this point the bulk of enumeration is complete.
drupalgeddon2>> whoami nt authority\iusr
iusr is essentially Window’s version of an ‘anonymous’ user that is utilized by default by IIS servers in order to access the required system files.
We can grab the user flag from Users/dimitris/Desktop instantly; thankfully there’s further privilege escalation needed for complete admin access!
By following any WIndows privesc cheatsheet, you should check out the privileges on the logged in account and see that we have an interesting one named ‘SeImpersonatePrivilege’- the ability to impersonate a client after authentication.
From previous reading I was aware that this Windows privilege basically means we’re system as there is a well known privesc technique for this called Juicy Potato- the last step is simply seeing how we can download files onto the victim and finding the relevant CISID for our Windows version. Bastard is a Windows 2008 server- as revealed by checking systeminfo.
After some trial and error, I managed to utilize CertUtil:
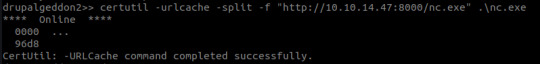
CertUtil was originally intended to be used to display CA (Certificate Authority) config information and to also make any neccessary alterations to CA components (basically an administrative tool for all things CA related :3)
Part of CertUtil’s functionality includes the ability to download files... Don’t ask me why they thought this was safe. I guess it was in the event of needing third party CA templates (basically pre-config of CA via certificate templates)?
With netcat and JuicyPotato now on our victim, we are able to exploit this privilege for a reverse shell.

This vulnerability is famously named Rotten Potato and -at a simple level- involves tricking AUTHORITY/SYSTEM into authenticating via NTLM to a TCP endpoint under our control.
This authentication process is then captured via a local MITM attack utilizing several Windows API calls. Finally -with one of the relevant privileges- we use the captured token for impersonation, thus gaining the ability to execute commands as SYSTEM.
For those who didn’t guess by the screenshot, a reverse shell is established through our run of jp.exe (I was running a nc listener on port 6969 to receive the connection) and we are able to read root.txt from Administrator’s Desktop directory.
The CLSID I used was obtained from https://github.com/ohpe/juicy-potato/tree/master/CLSID/Windows_Server_2008_R2_Enterprise.
A CLSID is a globally unique identifier that identifies a COM class object.
#hackthebox#bastard#hacking#ctf#OSCP#learning#offensive security#cyber security#windows hacking#drupal RCE#drupal#AJAX#computer science
13 notes
·
View notes
Text
Tips to Secure Your WordPress Site in 2023

The increasing incidences of cyberattacks make cybersecurity more critical than ever. Perhaps because it’s the most popular content management system, hackers love to break into WordPress sites. Busy business owners and blog managers often forget to update plugins and keep their databases secure. Small business owners may believe there is little threat of a cybercriminal taking over their sites until it happens to them. The number of people doing business online increased during the COVID-19 pandemic. With heightened activity came even more hackers ready to steal information or create chaos just for fun.
What Are Some Cybersecurity Trends in 2023 for WordPress?
W3Techs tracks the usage of various popular online software and recently estimated about 43.1% of all websites utilize WordPress as a CMS. Some of the trends you’re seeing heading into 2023 for cybersecurity for WordPress are what you’d expect. WordPress.org currently lists over 60,000 plugins in its directory. However, plugins and themes may open the door to SQL injection attacks. Brute force attacks will continue to remain a popular way to gain entry into WordPress websites. The hacker tries different combinations, hoping to hit on your password. Brute force attacks can shut a site down due to increased bandwidth use and strain on the system. A recent survey by BakerHostetler found around 24% of cyber attacks on U.S. businesses were phishing-related. Disgruntled former employees, people being careless with passwords or lack of knowledge all contributed to hacking due to phishing attacks. The report also showed a sharp rise in ransomware, at 37% of hacking attempts.
How Do I Make My WordPress Site More Secure?
Some of the extreme breaches in recent years impacted millions of consumers. In 2018, hackers gained access to the information of 500 million guest accounts via Marriott International's databases, costing the company $28 million. Securing your website is crucial to your online presence, no matter what platform you utilize. Laws such as the General Data Protection Regulation (GDPR) act and California Consumer Privacy Act (CCPA) require you to collect only the information you need, delete what you no longer require and take steps to keep it safe from criminals. GDPR and CCPA come with hefty fines if you ignore your responsibilities. What can you do to ensure your WordPress site is more secure? Fortunately, there are simple steps to keep hackers out and data protected. 1. Update Your Site Every time you log in to your WordPress dashboard, you’ll see a counter across the top bar telling you if you need to update anything. You can set your site to accept updates automatically or manually, but make it a habit to check the counter. An un-updated website is vulnerable to various attacks from outside forces. SQL injection attacks often seek the most vulnerable entry points into the open source software. When WP releases an update, it tends to address any security concerns and shore up your site’s cybersecurity. 2. Choose a Trusted HostHire Penetration Testing Your hosting company is only a good value if their cheap practices don’t put your website at risk. Hackers enter sites via their accounts on a shared server. While all businesses would ideally have a dedicated server, the costs are sometimes prohibitive for small companies. However, you can avoid many issues by going with a hosting provider with an excellent track record. Ask questions about the hours IT staff are on hand — the answer should be 24/7. Do they monitor for and stop attacks as they occur? Such proactive measures are essential to work against brute force and SQL injection attacks. 3. Hire Penetration Testing One way to ensure you close up any open doors to hackers is to hire a company to test for system vulnerabilities. For example, you might conduct a firewall penetration test to see how well it blocks someone trying to gain entry without permission. Does the system lock them out after a certain number of attempts? Is the website owner notified? Think of the various ways cybercriminals access WordPress websites and test each entry point to see their weaknesses. Once you understand where an attack might occur, you can take steps to prevent a potential event. Plugins such as Security Ninja can scan for vulnerabilities and save you the cost of hiring an outside provider. 4. Train Employees Train everyone who logs into your CMS to protect their passwords. Each machine should have antivirus and malware protections installed. Writers and editors should avoid clicking on any links to log in and always go directly to the site. Teach your staff what phishing is and how to avoid it. Change passwords frequently and remove access for former employees immediately and not months later. Taking basic steps to educate workers and protect your site may save you thousands of dollars in cleanup costs. 5. Choose a Secure Theme Not all themes are created equal, so make sure the WordPress community respects a theme or plugin’s creator. The person should have experience developing software that isn’t vulnerable to attacks. Sadly, some people create software to trick sites into sharing sensitive information and then use what they collect to dox your customers, sharing things online they wouldn’t want anyone else to know.
Create a Checklist
The best way to secure your WordPress site in 2023 is to create a checklist of things you should tend to regularly for your website. Make it a habit to update outdated plugins and themes, remind employees to protect their login credentials and test frequently to find the holes and fill them before a hacker stumbles across your vulnerabilities. Read the full article
0 notes