#Secure Data Backup
Text
#big data#file replication#data protection#file synchronization software#data management#cloud solutions#secure data backup#cloud software
0 notes
Text
Cybersecurity is a critical aspect of modern business operations. With the increasing digitization of processes and data, businesses face a range of cyber threats that can compromise sensitive information and disrupt operations.
0 notes
Text

118 notes
·
View notes
Text
aside from directly dealing with The Agency's competitors/threats/etc, Antares also gets sent out for other jobs ranging from deliveries to acting as a bodyguard
this is so that i can get some flexibility here and also i think he should be able to run into the fivemind units more often aside from like...trying to destroy them and going to the grocery store and stuff
#[ out of circuits ]#(( sometimes he just acts as backup for whatever villain of the week or like security detail for larger evil plans ig#he can also petsit#if given the choice he always goes for shit like 'yeah i'll watch the shark tank :>'#[ data : antares ]
3 notes
·
View notes
Text
youtube
2 notes
·
View notes
Text
When selecting an Office 365 backup solution, businesses should focus on automated backups, granular recovery options, security, and scalability. These features help protect critical data from accidental deletions and malicious attacks, ensuring that business operations remain uninterrupted in case of data loss.
#Office 365 backup#business backup solutions#cloud data protection#email backup#OneDrive backup#SharePoint backup#Microsoft Teams backup#data recovery#backup automation#data security#Office 365 compliance
0 notes
Text
Empower Your Business with CLOUD COMPUTING CENTER: The Ultimate Destination for Cloud Solutions

In the rapidly evolving digital landscape, businesses must adapt to stay competitive. One of the most crucial shifts in recent years has been the move to cloud computing. The benefits are undeniable: enhanced flexibility, reduced costs, and increased efficiency. However, navigating the complexities of cloud technology can be challenging. That’s where CLOUD COMPUTING CENTER comes in.
Who We Are
CLOUD COMPUTING CENTER is your trusted partner in the digital transformation journey. We specialize in providing comprehensive cloud computing services tailored to meet the unique needs of businesses across various industries. Our mission is to empower companies with cutting-edge cloud solutions, ensuring they stay ahead in today’s fast-paced market.
Our Services
At CLOUD COMPUTING CENTER, we offer a suite of services designed to cover every aspect of cloud computing. Here’s how we can help your business harness the full potential of the cloud:
1. Cloud Infrastructure Setup
Setting up a robust cloud infrastructure is the foundation of any successful digital transformation. Our team of experts will design and implement a scalable, secure, and high-performing cloud infrastructure tailored to your business needs. We ensure that your cloud environment is optimized for efficiency and cost-effectiveness.
2. Cloud Migration
Moving your existing systems and data to the cloud can be a daunting task. With CLOUD COMPUTING CENTER, you can rest assured that your migration process will be smooth and hassle-free. We provide end-to-end cloud migration services, minimizing downtime and ensuring data integrity throughout the transition.
3. Managed Cloud Services
Managing cloud infrastructure requires ongoing monitoring, maintenance, and optimization. Our Managed Cloud Services take the burden off your shoulders, allowing you to focus on your core business. We offer proactive management, 24/7 support, and regular updates to ensure your cloud environment runs seamlessly.
4. Data Backup and Recovery
Data is the lifeblood of any organization, and safeguarding it is critical. Our Data Backup and Recovery services provide comprehensive protection against data loss. We implement reliable backup solutions and quick recovery processes, ensuring that your business can quickly bounce back in case of an unexpected event.
5. SaaS Solutions
Software-as-a-Service (SaaS) is transforming the way businesses operate. We help you leverage the power of SaaS by providing custom solutions that meet your specific needs. From deployment to integration and management, we ensure that your SaaS applications are fully aligned with your business goals.
6. Cloud Security
Security is a top concern when it comes to cloud computing. Our Cloud Security services are designed to protect your data, applications, and infrastructure from cyber threats. We implement best-in-class security measures, including encryption, access control, and regular security audits, to ensure that your cloud environment is secure and compliant with industry standards.
Why Choose Us?
At CLOUD COMPUTING CENTER, we pride ourselves on delivering exceptional service and results. Here are a few reasons why businesses trust us for their cloud computing needs:
Expertise: Our team comprises seasoned professionals with extensive experience in cloud computing.
Customized Solutions: We understand that every business is unique, so we tailor our services to meet your specific requirements.
Proactive Support: Our 24/7 support team is always available to address any issues and keep your cloud environment running smoothly.
Cost Efficiency: We help you optimize your cloud infrastructure to reduce costs without compromising on performance.
Commitment to Security: We prioritize the security of your data and applications, ensuring peace of mind for your business.
Partner with CLOUD COMPUTING CENTER Today
Whether you're just beginning your cloud journey or looking to optimize your existing cloud environment, CLOUD COMPUTING CENTER is here to help. Our comprehensive range of cloud computing services is designed to support your business at every stage of its digital transformation.
Contact us today to learn more about how we can empower your business with the right cloud solutions.
#cloud solutions#cloud computing#Cloud Infrastructure Setup#Cloud Migration#Managed Cloud Services#Data Backup and Recovery#SaaS Solutions#Cloud Security
1 note
·
View note
Text
Data Backup and Recovery

According to the Small Business Administration, 40 to 60 percent of small businesses lack backup and recovery services, risking survival of a disaster. Ensure your business in Atlanta, GA is ready with our data restoration solutions and digital data rescue. Invest in information recovery and retrieval services to safeguard your assets. Trust our backup and recovery services for business continuity. Learn more: https://centurygroup.net/managed-it-solutions/data-backup/
#datarecovery #databackup #technology #datasecurity #computerrepair #backup #cloudstorage #cloudbackup #datastorage #dataprotection #itsupport #windows #cybersecurity #data #backupdata #techsupport #onlinestorage #datasafety #itservices #smallbusiness
1 note
·
View note
Text
#data migration#data management#big data#data protection#file synchronization software#cloud solutions#linux#data orchestration#Government Data Management#file replication#Linux file transfer#secure data backup#cloud computing#cloud software
0 notes
Text
Global Cyber Resilience Report 2024: Overconfidence and Gaps in Cybersecurity Revealed
New Post has been published on https://thedigitalinsider.com/global-cyber-resilience-report-2024-overconfidence-and-gaps-in-cybersecurity-revealed/
Global Cyber Resilience Report 2024: Overconfidence and Gaps in Cybersecurity Revealed
The Global Cyber Resilience Report 2024 presents an in-depth analysis of the current state of cyber resilience across various industries worldwide. Based on a survey conducted by Cohesity and Censuswide, involving 3,139 IT and Security Operations (SecOps) decision-makers from eight countries, this report sheds light on the significant gaps between perceived and actual cyber resilience capabilities.
Survey Demographics and Scope
The survey, conducted in June 2024, covered both public and private organizations across several countries:
United States: ~500 respondents
United Kingdom: ~500 respondents
Australia: ~500 respondents
France: ~400 respondents
Germany: ~400 respondents
Japan: ~300 respondents
Singapore: ~300 respondents
Malaysia: ~200 respondents
Participants were evenly split between IT and SecOps professionals, providing a comprehensive overview of the current cyber resilience landscape.
Key Findings
1. Overestimation of Cyber Resilience
A striking revelation from the survey is the overestimation of cyber resilience capabilities among organizations. Only 2% of respondents indicated that they could recover their data and restore business processes within 24 hours of a cyberattack. This starkly contrasts with the confidence expressed by nearly 4 in 5 (78%) respondents in their organization’s cyber resilience strategy.
2. Ransom Payments: A Growing Concern
The willingness to pay ransoms has become alarmingly common. Approximately 75% of respondents indicated their organization would pay over $1 million to recover data and restore business operations, with 22% willing to pay over $3 million. In the past year, 69% of respondents admitted to paying a ransom, despite 77% having policies against such payments.
Slow Recovery Times
Recovery times reported by organizations reveal significant vulnerabilities:
Only 2% could recover within 24 hours.
18% could recover within 1-3 days.
32% required 4-6 days.
31% needed 1-2 weeks.
16% would need 3+ weeks.
These recovery times fall short of the targeted optimum recovery time objectives (RTO), with 98% aiming for recovery within one day and 45% targeting within two hours.
4. Insufficient Data Privacy Compliance
Just over 2 in 5 (42%) respondents claimed their organization could identify sensitive data and comply with applicable data privacy laws. This indicates a significant gap in necessary IT and security capabilities.
5. Zero Trust Security Deficiencies
Despite the availability of effective security measures, many organizations have not adopted them:
48% have not deployed multifactor authentication (MFA).
Only 52% have implemented MFA.
Quorum controls or administrative rules requiring multiple approvals are used by 49%.
Role-based access controls (RBAC) are deployed by 46%.
These deficiencies leave organizations vulnerable to both external and internal threats.
The Escalating Threat Landscape
The survey underscores the increasing threat of cyberattacks:
In 2022, 74% of respondents felt the threat of ransomware was rising. By 2023, this figure rose to 93%, and in 2024, it reached 96%.
Two-thirds (67%) of respondents reported being victims of ransomware in the past six months.
Industries Most Affected
The report identifies seven industries that have been hardest hit by cyberattacks:
IT & Technology (40%)
Banking & Wealth Management (27%)
Financial Services (27%)
Telecommunications & Media (24%)
Government & Public Services (23%)
Utilities (21%)
Manufacturing (21%)
Areas of Critical Concern
1. Confidence-Capability Paradox
The disparity between confidence in cyber resilience strategies and the actual capability to execute these strategies effectively is evident. While many organizations have a cyber resilience plan, their ability to recover quickly from attacks lags significantly behind their goals.
2. Rampant Ransom Payments
The prevalence of ransom payments, often in contradiction to organizational policies, highlights a reactive rather than proactive approach to cyber resilience. The financial impact of paying ransoms extends beyond the immediate cost, affecting downtime, lost opportunities, and reputational damage.
3. Zero Trust Security Deficiencies
The failure to implement robust data access controls like MFA and RBAC poses a significant risk to organizations. Effective security measures are essential for protecting critical data and ensuring business continuity.
Recommendations for Improvement
To address these critical issues, the report suggests several actionable strategies:
Engage in rigorous testing, drills, and simulations to ensure the effectiveness of backup and recovery processes.
Sign up for ransomware resilience workshops to enhance cyber incident response capabilities.
Automate testing of backup data to verify integrity and recoverability without manual intervention.
Maintain detailed documentation and recovery playbooks to ensure all stakeholders understand their roles during an incident.
Conclusion
The Global Cyber Resilience Report 2024 that was commissioned by Cohesity highlights the urgent need for organizations to bridge the gap between their perceived and actual cyber resilience capabilities. By identifying and addressing these vulnerabilities, organizations can enhance their ability to recover from cyberattacks and protect critical data, ensuring a more secure and resilient future.
The comprehensive data and insights from this report serve as a crucial resource for IT and SecOp professionals aiming to strengthen their cyber resilience strategies and safeguard their organizations against the evolving threat landscape.
#2022#2023#2024#amp#Analysis#approach#authentication#backup#backup and recovery#banking#bridge#Business#business continuity#comprehensive#Critical Issues#cyber#cyber security#cyberattack#Cyberattacks#cybersecurity#data#data privacy#decision-makers#documentation#financial#financial services#Future#gap#Global#Government
0 notes
Text
Folder Lock
If you have folders and files that you want to keep private, consider using Folder Lock. Unlike My Lockbox, it isn’t a free app, but it offers excellent configuration options and numerous methods to protect important and private documents from prying eyes.
Folder Lock is a complete solution for keeping your personal files encrypted and locked, while automatically and in real-time backing up…
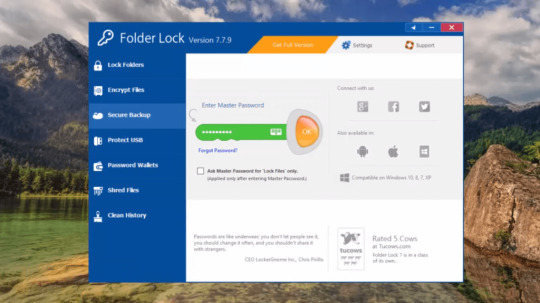
View On WordPress
#Data Encryption#Digital Wallets#Encryption Software#File Locking#File Management#File Security#File Shredding#password protection#Portable Security#privacy protection#Secure Backup#Windows Security
0 notes
Text
Enhance Data Security with NAKIVO Office 365 Backup Solution
Enhance data security with NAKIVO Office 365 Backup Solution and Radiant Info Solutions. Comprehensive backup services for Office 365 data in India.

#enhance data security#NAKIVO Office 365 Backup#Radiant Info Solutions#Office 365 backup India#data protection
0 notes
Video
youtube
How to backup your wordpress website in 2 minutes - Woocommerce back up tutorial - Updraft plusBacking up your WordPress website with the UpdraftPlus plugin is a straightforward process. Here's a step-by-step guide: 1. Install UpdraftPlus Plugin: Go to your WordPress dashboard, navigate to "Plugins" and "Add New," search for "UpdraftPlus," and click "Install Now" and then "Activate." 2. Access UpdraftPlus Settings: After activating the plugin, find it in your WordPress dashboard sidebar. Click on "Settings" and then "UpdraftPlus Backups." 3. Configure Backup Settings: - Click on the "Settings" tab to configure your backup settings. - Choose your preferred backup schedule: manually, daily, weekly, monthly, or custom interval. - Select the files and databases you want to include in the backup. - Choose your remote storage destination: Dropbox, Google Drive, Amazon S3, etc. Authenticate and grant access to UpdraftPlus. 4. Initiate Backup: - Save your changes. - Go to the "Current Status" tab. - Click the "Backup Now" button to start the backup process. 5. Verify Backup Completion: After the backup process finishes, UpdraftPlus will display a success message. Check the "Existing Backups" tab to see your backups. 6. Restore Backup (Optional): To restore from a backup, go to the "Existing Backups" tab, locate the backup, and click "Restore." Follow the on-screen instructions. 7. Regularly Monitor and Test Backups: Monitor backups regularly and test them by restoring to a staging environment. Following these steps, you can effectively backup your WordPress website using the UpdraftPlus plugin, ensuring your site is protected against data loss.
#wordpress#woocommerce#elementor#dropshipping#ecommerce#ecomhardy#wordpress backup#updraftplus tutorial#wordpress website backup#wordpress backup plugin#website backup tutorial#wordpress maintenance#wordpress security#website backup strategy#wordpress tips#website management#wordpress backup and restore#data backup for wordpress#wordpress data protection#wordpress backup solutions#website data backup#wordpress backup best practices#wordpress backup automation
1 note
·
View note
Text
Discover how Fortanix empowers data backup and recovery companies to protect sensitive information with advanced technologies like confidential computing, secure key management, and tamper-proof audit logs. Ensure robust data protection and compliance with seamless integration into existing platforms. Safeguard your data at every stage and prevent costly data breaches. Learn more about Fortanix's innovative solutions today!
#DataSecurity #BackupRecovery #Fortanix #ConfidentialComputing #CyberSecurity
#encryption#cloud security#data security#data privacy#data security challenges#data privacy challenges#confidential computing#backup#recovery#fortanix
0 notes
Text
Implementing a robust cloud disaster recovery plan is essential for ensuring business continuity. Key strategies include assessing business needs, selecting an appropriate DR model, automating recovery processes, ensuring data security, and conducting regular testing. These steps help organizations minimize downtime and data loss during unexpected disasters.
#cloud disaster recovery#disaster recovery plan#cloud DR best practices#business continuity#data security#backup and recovery#cloud recovery models#disaster recovery automation#data encryption#failover testing#cloud security
0 notes
Text
Data Defense: Effective NAS Backup Techniques for Cloud and Local Storage

In today's digital landscape, data is not just an asset; it's the backbone of business operations and personal data integrity. Network Attached Storage (NAS) devices have become popular solutions for managing and storing data across networks. However, the increase in data breaches and system failures underscores the need for robust NAS backup strategies. This article outlines effective backup techniques for both cloud and local storage to ensure data security and accessibility.
Understanding NAS and Its Importance
A Network Attached Storage (NAS) device is a storage server connected to a network that allows storage and retrieval of data from a centralized location for authorized network users and heterogeneous clients. NAS systems are prevalent in both business and home environments due to their ease of use, scalability, and cost-effectiveness.
Local Backup Solutions
Redundancy: Implement RAID (Redundant Array of Independent Disks) configurations to ensure data redundancy. Common setups like RAID 1 or RAID 5 provide a balance between storage capacity and redundancy, safeguarding data against the failure of a single drive.
Regular Snapshots: Configure your NAS to take scheduled snapshots. These are point-in-time copies of data that provide a restore point for a specific moment. Snapshots are particularly useful for recovering data quickly in the event of data corruption or accidental deletion.
Direct Attached Storage (DAS): Use external drives (USB, eSATA) to create backups of your NAS. This method provides an additional layer of security and quick access to data in case the network is compromised.
Cloud Backup Solutions
Cloud Storage Providers: Integrate your NAS with cloud services like Amazon S3, Google Cloud Storage, or Microsoft Azure. These platforms offer robust security features, scalable storage, and data redundancy across multiple locations.
Hybrid Backup: Utilize a hybrid approach by backing up data to both local devices and the cloud. This strategy ensures data redundancy and availability, providing a backup solution that protects against local hardware failures and natural disasters.
Encryption and Security: Before transmitting data to the cloud, ensure it is encrypted both in transit and at rest. Use strong encryption protocols such as AES-256 to secure your data. Additionally, opt for cloud providers that offer two-factor authentication and other security measures.
Best Practices for NAS Backup
Automate Backups: Set up automated backup schedules to reduce the risk of human error. Most NAS devices come with software that can automate backups to both local and cloud storage.
Test Regularly: Regularly test your backup files to ensure they are not corrupted and can be restored successfully. This practice is crucial for business continuity planning.
Monitor and Update: Keep your NAS firmware and associated backup software updated to protect against vulnerabilities. Also, monitor your backup processes and logs to detect any issues early.
Conclusion
Effective NAS backup techniques are essential for safeguarding valuable data against loss, theft, or corruption. By employing a combination of local and cloud backup strategies, along with adhering to best practices, individuals and businesses can enhance the security and reliability of their data storage solutions. In a world where data is increasingly critical, having a robust backup strategy isn't just an option—it's a necessity.
0 notes