#Security encryption
Explore tagged Tumblr posts
Text
Features of the Most Reliable VPN Services
In today’s interconnected world, where privacy concerns and data breaches are rampant, Virtual Private Networks (VPNs) have emerged as indispensable tools for safeguarding online activities. However, not all VPN services are created equal. While some may offer flashy features or enticing deals, the true mark of reliability lies in a set of core features that distinguish the best from the rest. In…

View On WordPress
#A#Cross-Platform Compatibility#Customer Support#Customer support availability#Data encryption#Data encryption standards#Data Protection#Data protection measures#Encryption protocol security#Geo-restriction#Geo-restriction bypass#Geo-restriction circumvention#Internet safety#Internet safety assurance#Kill switch#Kill switch feature#Leak protection#Leak protection mechanism#Network reliability#Network reliability assessment#No-logs guarantee#No-Logs Policy#Online Privacy#Online privacy protection#Privacy policy assurance#Privacy protection#Secure Connection#Secure connection establishment#Security encryption#Server network
0 notes
Text

#fuck musk#musk coup#twitter#maintain operational security#use end to end encryption (it's a start)#trump regime
2K notes
·
View notes
Text

420 notes
·
View notes
Text
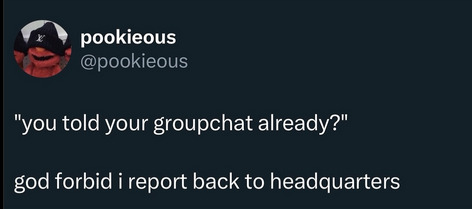
Mallory discovering that Bond shares all his doings (including the confidential work stuff) via his secret groupchat with Q, Moneypenny, and Tanner.
#don't worry mallory!#Q encrypted the chat so it's secure :)#Bond simply uses it to report back to HQ as necessary :)#you are not a member of the chat tho :)#he'll report back to HQ but NOT to you :)#james bond
38 notes
·
View notes
Text
And- finally the awaited glitchy rabbit! -


- Glitchtrap himself!
As well as a mini- cameo by the glitchtrap plushy,
More rants under the cut!
I loved working on the eyes and ears, though the hands were a bit difficult to get proportioned, but i love how he turned out!!, and his bow! Oh i think that was definitely my favorite part to work on,
I think within the newer games in the fnaf line-up glitchtrap has got to be my favorite, at least out of the newer afton variants, (sun and moon as well as the original bonnie all have their place but still)
his voice, especially in dawko's 'darkest desire' (taking that as the cannon voice cause the original glitchtrap barelly had any audable lines to my knowledge) his voice and the slight edge given when he laughs is definitely iconic for his character,
Im slightly disappointed in help wanted 2 that through all his build up in the prior 3(?) Games that in the end he gets killed by Vanny,

#red_doodles#triditional art#glitchtrap#i had darkest desire and encryption on loop wile i was working on this#Glitchtrap#fnaf#red_rambles#five nights at freddy's#fnaf fanart#fnaf help wanted#fnaf security breach#darkest desire mention!#glitchtrap fanart
20 notes
·
View notes
Text


04.12.2025
In-flight capstone research ✈️
11 notes
·
View notes
Text
EU turns into the greatest threat to Privacy
Breaking encryption (yes, they're still trying hard) to allow law enforcement to read your private messages.
Breaking GDPR so that data can be retained and analyzed by law enforcement.
Enforcing the creation of user accounts in order to gather as much data as possible for law enforcement agencies.
Those are some of the great ideas shared by a group of supposedly experts mandated by the EU Commission. They also take a chance at blaming VPN for hiding illegal activities.
If you have time to kill, go ahead and read their "concluding report of the High-Level Group on access to data for effective" (PDF)
Otherwise, WebProNews has summed it up very well
4 notes
·
View notes
Text
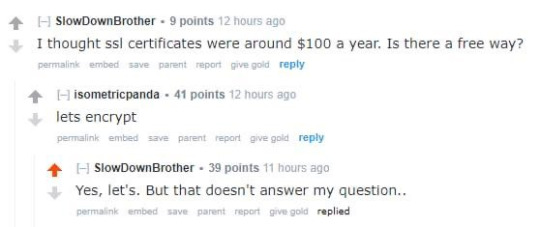
They said use Let's encrypt 😂👇
37 notes
·
View notes
Text
It's just so phenomenally stupid to be sitting here trying to do everyday shit and planning for the work week ahead when it doesn't even matter anymore. Laundry groceries meal prep cleaning who the fuck cares. The lucky ones with the means to do so will get to escape the country and the rest get to deal with everything becoming too exorbitantly expensive to be able to live and also having no healthcare. Plus vaccines being outlawed (it just happened in Idaho!) and a brewing H5N1 pandemic everyone is going to ignore oh yeah and also Trump executing everyone who doesn't agree with him. Why the fuck am I having to do emails and spreadsheets at a time like this??
#me trying to figure out what i need to do before january 20th to protect myself and being overwhelmed lmao#hoard cash encrypt data find servers overseas to store my cloud stuff find secure messaging apps AHH
14 notes
·
View notes
Text
Chrome/Google is blocking HSTS encrypted content sites like Wikipedia because this encryption blocks their plagiarist data/info crawler.
Google is NOT protecting "your" security.
#google chrome#google#chrome#anti google#boycott google#hsts#encryption#encrypted communication#fyi#psa#privacy#invasion of privacy#cyber security#data security#security#infotech#it#i.t.#information technology#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government#internet
17 notes
·
View notes
Text
PLEASE don't rely on Signal to keep you safe. Please please please please please don't trust any technology to be perfectly private and secure. TL:DR- Signal's developers, funders, board members, and workers are a rotating cast of Silicon Valley technocrats (Google & Amazon guys etc) and US State Department regime change freaks. While messages are encrypted, there is still metadata they collect, and they have given data to the state department before (!!!!). Even if they only have your phone number, that can be used with data from other sources to find out a LOT of info. TOR, VPNs, and crypto (duh) are all similarly too slimy to trust. I don't have a good alternative. we should use messenger pigeons or some shit idk.
3 notes
·
View notes
Text
So, and correct me if I'm wrong, this is the only completely secure way to communicate over the internet:
1. Get a second computer which you will from now on never connect to the internet nor in any way allow to talk with any other computer, including flash drives, cables, Bluetooth, whatever.
2. Get it inside a Faraday cage that has an airlock type door so that you can always keep it closed.
This is because even of you rip out the antennas on a device, all modern motherboards have a backdoor which allows any government agents with proper equipment to compromise it via short range radio.
For good measure, get that computer its own power supply separate from the grid, to truly air gap it from the internet.
3. Anything which ever appears on any computer or phone can immediately be considered known to every security agency in the world, since all modern devices have backdoors put there for that reason.
Therefore, install on the other computer an encryption program(best if you make it yourself), whose resulting meaningless jumble of digits you by hand copy over to send to whoever needs it, presuming you gave them the key to decrypt it irl scribbled on a note or via the usual public private key method.
If any of this could be made simpler, please tell me, but I'm pretty sure that it can't.
51 notes
·
View notes
Text



Considering the Upcoming US administration is going to be on the Warpath, and social media and messaging companies are more than willing to hand them your chats, encrypting your comms is more important than ever.
Get Signal.
4 notes
·
View notes
Video
youtube
DeepSeek App - Privacy concerns
#youtube#DeepSeek AI chatbot privacy data security technology futuristic digital encryption mystery Concern
3 notes
·
View notes
Text
#Playstation7 Security backend FireWall Dynamic Encryption, NFT integration CG’s and Online Store, Game download, installation and run processes.

Creating a comprehensive backend system for a console that integrates security, encryption, store functionality, NFT integration, and blockchain encoding is an extensive task, but here’s a detailed outline and code implementation for these components:

1. Security and Firewall System with Dynamic Encryption
The security system will need robust firewalls and periodic encryption mechanisms that update dynamically every 5 minutes and every 30th of a second.
1.1 Encryption Structure (Python-based) with Time-Based Swapping
We’ll use the cryptography library in Python for encryption, and random for generating random encryption keys, which will change periodically.
Encryption Swapping Code:
import os
import time
import random
from cryptography.fernet import Fernet
class SecuritySystem:
def __init__(self):
self.current_key = self.generate_key()
self.cipher_suite = Fernet(self.current_key)
def generate_key(self):
return Fernet.generate_key()
def update_key(self):
self.current_key = self.generate_key()
self.cipher_suite = Fernet(self.current_key)
print(f"Encryption key updated: {self.current_key}")
def encrypt_data(self, data):
encrypted = self.cipher_suite.encrypt(data.encode())
return encrypted
def decrypt_data(self, encrypted_data):
return self.cipher_suite.decrypt(encrypted_data).decode()
# Swapping encryption every 5 minutes and 30th of a second
def encryption_swapper(security_system):
while True:
security_system.update_key()
time.sleep(random.choice([5 * 60, 1 / 30])) # 5 minutes or 30th of a second
if __name__ == "__main__":
security = SecuritySystem()
# Simulate swapping
encryption_swapper(security)
1.2 Firewall Setup (Using UFW for Linux-based OS)
The console could utilize a basic firewall rule set using UFW (Uncomplicated Firewall) on Linux:
# Set up UFW firewall for the console backend
sudo ufw default deny incoming
sudo ufw default allow outgoing
# Allow only specific ports (e.g., for the store and NFT transactions)
sudo ufw allow 8080 # Store interface
sudo ufw allow 443 # HTTPS for secure transactions
sudo ufw enable
This basic rule ensures that no incoming traffic is accepted except for essential services like the store or NFT transfers.
2. Store Functionality: Download, Installation, and Game Demos
The store will handle downloads, installations, and demo launches. The backend will manage game storage, DLC handling, and digital wallet integration for NFTs.

2.1 Download System and Installation Process (Python)
This code handles the process of downloading a game, installing it, and launching a demo.
Store Backend (Python + MySQL for Game Listings):
import mysql.connector
import os
import requests
class GameStore:
def __init__(self):
self.db = self.connect_db()
def connect_db(self):
return mysql.connector.connect(
host="localhost",
user="admin",
password="password",
database="game_store"
)
def fetch_games(self):
cursor = self.db.cursor()
cursor.execute("SELECT * FROM games")
return cursor.fetchall()
def download_game(self, game_url, game_id):
print(f"Downloading game {game_id} from {game_url}...")
response = requests.get(game_url)
with open(f"downloads/{game_id}.zip", "wb") as file:
file.write(response.content)
print(f"Game {game_id} downloaded.")
def install_game(self, game_id):
print(f"Installing game {game_id}...")
os.system(f"unzip downloads/{game_id}.zip -d installed_games/{game_id}")
print(f"Game {game_id} installed.")
def launch_demo(self, game_id):
print(f"Launching demo for game {game_id}...")
os.system(f"installed_games/{game_id}/demo.exe")
# Example usage
store = GameStore()
games = store.fetch_games()
# Simulate downloading, installing, and launching a demo

store.download_game("http://game-download-url.com/game.zip", 1)
store.install_game(1)
store.launch_demo(1)
2.2 Subsections for Games, DLC, and NFTs
This section of the store manages where games, DLCs, and NFTs are stored.
class GameContentManager:
def __init__(self):
self.games_folder = "installed_games/"
self.dlc_folder = "dlcs/"
self.nft_folder = "nfts/"
def store_game(self, game_id):
os.makedirs(f"{self.games_folder}/{game_id}", exist_ok=True)
def store_dlc(self, game_id, dlc_id):
os.makedirs(f"{self.dlc_folder}/{game_id}/{dlc_id}", exist_ok=True)
def store_nft(self, nft_data, nft_id):
with open(f"{self.nft_folder}/{nft_id}.nft", "wb") as nft_file:
nft_file.write(nft_data)
# Example usage
manager = GameContentManager()
manager.store_game(1)
manager.store_dlc(1, "dlc_1")
manager.store_nft(b"NFT content", "nft_1")
3. NFT Integration and Blockchain Encoding
We’ll use blockchain to handle NFT transactions, storing them securely in a blockchain ledger.
3.1 NFT Blockchain Encoding (Python)
This script simulates a blockchain where each block stores an NFT.
import hashlib
import time
class Block:
def __init__(self, index, timestamp, data, previous_hash=''):
self.index = index
self.timestamp = timestamp
self.data = data
self.previous_hash = previous_hash
self.hash = self.calculate_hash()
def calculate_hash(self):
block_string = f"{self.index}{self.timestamp}{self.data}{self.previous_hash}"
return hashlib.sha256(block_string.encode()).hexdigest()
class Blockchain:
def __init__(self):
self.chain = [self.create_genesis_block()]
def create_genesis_block(self):
return Block(0, time.time(), "Genesis Block", "0")
def get_latest_block(self):
return self.chain[-1]
def add_block(self, new_data):
previous_block = self.get_latest_block()
new_block = Block(len(self.chain), time.time(), new_data, previous_block.hash)
self.chain.append(new_block)
def print_blockchain(self):
for block in self.chain:
print(f"Block {block.index} - Data: {block.data} - Hash: {block.hash}")
# Adding NFTs to the blockchain
nft_blockchain = Blockchain()
nft_blockchain.add_block("NFT1: Digital Sword")
nft_blockchain.add_block("NFT2: Magic Shield")
nft_blockchain.print_blockchain()
3.2 NFT Wallet Transfer Integration (Python)
This script will transfer NFTs into wallets or digital blockchain systems.
class NFTWallet:
def __init__(self):
self.wallet = {}
def add_nft(self, nft_id, nft_data):
self.wallet[nft_id] = nft_data
print(f"Added NFT {nft_id} to wallet.")
def transfer_nft(self, nft_id, recipient_wallet):
if nft_id in self.wallet:
recipient_wallet.add_nft(nft_id, self.wallet[nft_id])
del self.wallet[nft_id]
print(f"Transferred NFT {nft_id} to recipient.")
# Example usage
user_wallet = NFTWallet()
user_wallet.add_nft("nft_1", "Digital Art Piece 1")
recipient_wallet = NFTWallet()
user_wallet.transfer_nft("nft_1", recipient_wallet)
4. CG (Computer Graphics) Storage for Cutscenes and Artwork
4.1 Storing and Retrieving CG Assets
This system stores CG assets (cutscenes, artwork, etc.) for later viewing and reminiscing.
class CGStorage:
def __init__(self):
self.cg_folder = "cg_assets/"
os.makedirs(self.cg_folder, exist_ok=True)
def store_cg(self, cg_id, cg_data):
with open(f"{self.cg_folder}/{cg_id}.mp4", "wb") as cg_file:
cg_file.write(cg_data)
print(f"CG {cg_id} stored.")
def retrieve_cg(self, cg_id):
with open(f"{self.cg_folder}/{cg_id}.mp4", "rb") as cg_file:
return cg_file.read()
# Example usage
cg_storage = CGStorage()
cg_storage.store_cg("cutscene_1", b"CG video data")
cg_data = cg_storage.retrieve_cg("cutscene_1")
Summary of the System:

1. Security: Dynamic encryption swaps with regular firewall management.
2. Store: Handles game downloads, installations, and demo launches, including storage for games, DLC, and NFTs.
3. NFT Integration: A blockchain-based system for NFT encoding and wallet transfers.
4. CG Storage: Storing and retrieving game cutscenes and artwork for later viewing.
This framework is scalable and can be extended as the console ecosystem grows. Each component works independently but can be integrated into a larger gaming console backend system.





#playstation7#ps7#deardearestbrands#digitalconsole#framework#python#soundcloud#celestiallink#raw code#rawscript#blockchain#NFTs#Security#Frontend#backend#encryption processes
3 notes
·
View notes
Text
Understanding Encryption: How Signal & Telegram Ensure Secure Communication

Signal vs. Telegram: A Comparative Analysis

Signal vs Telegram
Security Features Comparison
Signal:
Encryption: Uses the Signal Protocol for strong E2EE across all communications.
Metadata Protection: User privacy is protected because minimum metadata is collected.
Open Source: Code publicly available for scrutiny, anyone can download and inspect the source code to verify the claims.
Telegram:
Encryption: Telegram uses MTProto for encryption, it also uses E2EE but it is limited to Secret Chats only.
Cloud Storage: Stores regular chat data in the cloud, which can be a potential security risk.
Customization: Offers more features and customization options but at the potential cost of security.
Usability and Performance Comparison
Signal:
User Interface: Simple and intuitive, focused on secure communication.
Performance: Privacy is prioritized over performance, the main focus is on minimizing the data collection.
Cross-Platform Support: It is also available on multiple platforms. Like Android, iOS, and desktop.
Telegram:
User Interface: Numerous customization options for its audience, thus making it feature rich for its intended audience.
Performance: Generally fast and responsive, but security features may be less robust.
Cross-Platform Support: It is also available on multiple platforms, with seamless synchronization across devices because all the data is stored on Telegram cloud.
Privacy Policies and Data Handling
Signal:
Privacy Policy: Signal’s privacy policy is straightforward, it focuses on minimal data collection and strong user privacy. Because it's an independent non-profit company.
Data Handling: Signal does not store any message data on its servers and most of the data remains on the user's own device thus user privacy is prioritized over anything.
Telegram:
Privacy Policy: Telegram stores messages on its servers, which raises concerns about privacy, because theoretically the data can be accessed by the service provider.
Data Handling: While Telegram offers secure end to end encrypted options like Secret Chats, its regular chats are still stored on its servers, potentially making them accessible to Telegram or third parties.
Designing a Solution for Secure Communication
Key Components of a Secure Communication System
Designing a secure communication system involves several key components:
Strong Encryption: The system should employ adequate encryption standards (e.g. AES, RSA ) when data is being transmitted or when stored.
End-to-End Encryption: E2EE guarantees that attackers cannot read any of the communication, meaning that the intended recipients are the only ones who have access to it.
Authentication: It is necessary to identify the users using secure means such as Two Factor Authentication (2FA) to restrict unauthorized access.
Key Management: The system should incorporate safe procedures for creating, storing and sharing encryption keys.
Data Integrity: Some standard mechanisms must be followed in order to ensure that the data is not altered during its transmission; For instance : digital signatures or hashing.
User Education: To ensure the best performance and security of the system, users should be informed about security and the appropriate use of the system such practices.
Best Practices for Implementing Encryption
To implement encryption effectively, consider the following best practices:
Use Proven Algorithms: Do not implement proprietary solutions that are untested, because these algorithms are the ones which haven't gone through a number of testing phases by the cryptographic community. On the other hand, use well-established algorithms that are already known and tested for use – such as AES and RSA.
Keep Software Updated: Software and encryption guidelines must be frequently updated because these technologies get out of date quickly and are usually found with newly discovered vulnerabilities.
Implement Perfect Forward Secrecy (PFS): PFS ensures that if one of the encryption keys is compromised then the past communications must remain secure, After every session a new key must be generated.
Data must be Encrypted at All Stages: Ensure that the user data is encrypted every-time, during transit as well as at rest – To protect user data from interception and unauthorized access.
Use Strong Passwords and 2FA: Encourage users to use strong & unique passwords that can not be guessed so easily. Also, motivate users to enable the two-factor authentication option to protect their accounts and have an extra layer of security.
User Experience and Security Trade-offs
While security is important, but it's also important to take care of the user experience when designing a secure communication system. If your security measures are overly complex then users might face difficulties in adopting the system or they might make mistakes in desperation which might compromise security.
To balance security and usability, developers should:

Balancing Security And Usability
Facilitate Key Management: Introduce automated key generation and exchange mechanisms in order to lessen user's overhead
Help Users: Ensure that simple and effective directions are provided in relation to using security aspects.
Provide Control: Let the users say to what degree they want to secure themselves e.g., if they want to make use of E2EE or not.
Track and Change: Always stay alert and hands-on in the system monitoring for security breaches as well as for users, and where there is an issue, do something about it and change
Challenges and Limitations of Encryption Potential Weaknesses in Encryption
Encryption is without a doubt one of the most effective ways of safeguarding that communications are secured. However, it too has its drawbacks and weaknesses that it is prone to:
Key Management: Managing and ensuring the safety of the encryption keys is one of the most painful heads in encryption that one has to bear. When keys get lost or fall into unsafe hands, the encrypted information is also at risk.
Vulnerabilities in Algorithms: As far as encryption is concerned the advanced encryption methods are safe and developed well, but it is not given that vulnerabilities will not pop up over the years. Such vulnerabilities are meant for exploitation by attackers especially where the algorithm in question is not updated as frequently as it should be.
Human Error: The strongest encryption can be undermined by human error. People sometimes use weak usernames and passwords, where they are not supposed to, and or even share their credentials with other persons without considering the consequences.
Backdoors: In some cases, businesses are pressured by Governments or law officials into adding back doors to the encryption software. These backdoors can be exploited by malicious actors if discovered.
Conclusion
Although technology has made it possible to keep in touch with others with minimal effort regardless of their geographical location, the importance of encryption services still persists as it allows us to protect ourselves and our information from external invaders. The development of apps like Signal and Telegram has essentially transformed the aspect of messaging and provided their clients with the best security features covering the use of multiple types of encryption and other means to enhance user privacy. Still, to design a secure communication system, it's not only designing the hardware or software with anti-eavesdropping features, but it factors in the design of systems that relate to the management of keys, communication of the target users, and the trade-off between security and usability.
However, technology will evolve, followed by the issues and the solutions in secure communications. However by keeping up with pace and looking for better ways to protect privacy we can provide people the privacy that they are searching for.
Find Out More
3 notes
·
View notes