#Encryption protocol security
Explore tagged Tumblr posts
Text
Features of the Most Reliable VPN Services
In today’s interconnected world, where privacy concerns and data breaches are rampant, Virtual Private Networks (VPNs) have emerged as indispensable tools for safeguarding online activities. However, not all VPN services are created equal. While some may offer flashy features or enticing deals, the true mark of reliability lies in a set of core features that distinguish the best from the rest. In…

View On WordPress
#A#Cross-Platform Compatibility#Customer Support#Customer support availability#Data encryption#Data encryption standards#Data Protection#Data protection measures#Encryption protocol security#Geo-restriction#Geo-restriction bypass#Geo-restriction circumvention#Internet safety#Internet safety assurance#Kill switch#Kill switch feature#Leak protection#Leak protection mechanism#Network reliability#Network reliability assessment#No-logs guarantee#No-Logs Policy#Online Privacy#Online privacy protection#Privacy policy assurance#Privacy protection#Secure Connection#Secure connection establishment#Security encryption#Server network
0 notes
Text
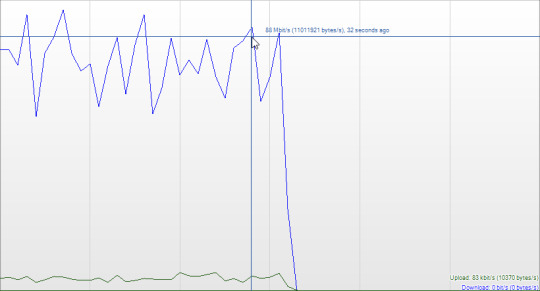
FUCKKKK my school frrr, network is totally capable of allocating me 86Mbp/s for JUST qBITTORRENT but instead of getting access to that we get throttled down to like >400Kbps if even.
#.txt#to explain what this graph is#the blue is my down speed#green is up speed#I have my vpn on and with port forwarding#which is able to circumvent my schools NAT protocol by forwarding the network traffic to a local port on my computer#(its technically remote port forwarding but)#and because I can get traffic directed to my machine a lot of the traffic that gets throttled by the networks security protocols#specifically NAT.( btw I am not inviting hostile activity onto the network I am just choosing to encrypt my data and verify authenticity#with a different protocol than NAT. specifically wireGuard which is the leading VPN protocol now)#however a lot of people dont like port forwarding because of that property and few VPNs support it anymore but its like the only way to#torrent at more than a snails pace#and so my school detected my high network activity and because of the encrypted data I was sending they literally just deny me service#I can just connect back with my regular PC no problem too so its not even stopping me#its just delaying me and making it annoying'
4 notes
·
View notes
Text
Leveraging SolveForce and The Telecom Broker to Address Key Cybersecurity Risks
Introduction Recent guidance from the Cybersecurity and Infrastructure Security Agency (CISA), alongside other global cybersecurity agencies, highlights significant vulnerabilities in telecommunications infrastructure exploited by malicious actors, such as state-sponsored cyber threats. The risks include unauthorized configuration changes, weak access controls, and insecure protocols. By…
#CISA Cybersecurity Guidance#Configuration Monitoring#Cybersecurity#encryption#MFA#Patch Management#RBAC#Secure Protocols#SIEM#SolveForce#Telecom Broker#Telecommunications Security
0 notes
Note
Do you have thoughts about the changes to Firefox's Terms of Use and Privacy Notice? A lot of people seem to be freaking out ("This is like when google removed 'Don't be evil!'"), but it seems to me like just another case of people getting confused by legalese.
Yeah you got it in one.
I've been trying not to get too fighty about it so thank you for giving me the excuse to talk about it neutrally and not while arguing with someone.
Firefox sits in such an awful place when it comes to how people who understand technology at varying levels interact with it.
On one very extreme end you've got people who are pissed that Firefox won't let you install known malicious extensions because that's too controlling of the user experience; these are also the people who tend to say that firefox might as well be spyware because they are paid by google to have google as the default search engine for the browser.
In the middle you've got a bunch of people who know a little bit about technology - enough to know that they should be suspicious of it - but who are only passingly familiar with stuff like "internet protocols" and "security certificates" and "legal liability" who see every change that isn't explicitly about data anonymization as a threat that needs to be killed with fire. These are the people who tend not to know that you can change the data collection settings in Firefox.
And on the other extreme you've got people who are pretty sure that firefox is a witch and that you're going to get a virus if you download a browser that isn't chrome so they won't touch Firefox with a ten foot pole.
And it's just kind of exhausting. It reminds me of when you've got people who get more mad at queer creators for inelegantly supporting a cause than they are at blatant homophobes. Like, yeah, you focus on the people whose minds you can change, and Firefox is certainly more responsive to user feedback than Chrome, but also getting you to legally agree that you won't sue Firefox for temporarily storing a photo you're uploading isn't a sign that Firefox sold out and is collecting all your data to feed to whichever LLM is currently supposed to be pouring the most bottles of water into landfills before pissing in the plastic bottle and putting the plastic bottle full of urine in the landfill.
The post I keep seeing (and it's not one post, i've seen this in youtube comment sections and on discord and on tumblr) is:
Well-meaning person who has gotten the wrong end of the stick: This is it, go switch to sanguinetapir now, firefox has gone to the dark side and is selling your data. [Link to *an internet comment section* and/or redditor reactions as evidence of wrongdoing].
Response: I think you may be misreading the statements here, there's been an update about this and everything.
Well-meaning (and deeply annoying) person who has gotten the wrong end of the stick: If you'd read the link you'd see that actually no I didn't misinterpret this, as evidenced by the dozens of commenters on this other site who are misinterpreting the ToU the same way that I am, but more snarkily.
Bud.
Anyway the consensus from the actual security nerds is "jesus fucking christ we carry GPS locators in our pockets all goddamned day and there are cameras everywhere and there is a long-lasting global push to erode the right to encrypt your data and facebook is creating tracking accounts for people who don't even have a facebook and they are giving data about abortion travel to the goddamned police state" and they could not be reached for comment about whether Firefox is bad now, actually, because they collect anonymized data about the people who use pocket.
My response is that there is a simple fix for all of this and it is to walk into the sea.
(I am not worried about the updated firefox ToU, I personally have a fair amount of data collection enabled on my browser because I do actually want crash reports to go to firefox when my browser crashes; however i'm not actually all that worried about firefox collecting, like, ad data on me because I haven't seen an ad in ten years and if one popped up on my browser i'd smash my screen with a stand mixer - I don't care about location data either because turning on location on your devices is for suckers but also *the way the internet works means unless you're using a traffic anonymizer at all times your browser/isp/websites you connect to/vpn/what fucking ever know where you are because of the IP address that they *have* to be able to see to deliver the internet to you and that is, generally speaking, logged as a matter of course by the systems that interact with it*)
Anyway if you're worried about firefox collecting your data you should ABSOLUTELY NOT BE ON DISCORD OR YOUTUBE and if you are on either of those things you should 100% be using them in a browser instead of an app and i don't particularly care if that browser is firefox or tonsilferret but it should be one with an extension that allows you to choose what data gets shared with the sites it interacts with.
5K notes
·
View notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
Beyond Change Healthcare
The continued onslaught of cybersecurity attacks which if anything are only getting worse have impacted the healthcare system in dramatic fashion with the payment network brought down by the attack on Change Healthcare. Healthcare under Cyber Attack I keep hoping that we all get better at combatting these attempts to breach our data and that overall vigilance rises as we become more wary of…

View On WordPress
#cyber attacks#cyber awareness#cyber defense#cyber hygiene#cyber resilience#cyber safety#cyber threats#CyberCrime#Cybersecurity#cybersecurity awareness#cybersecurity best practices#cybersecurity challenges#cybersecurity culture#cybersecurity education#cybersecurity measures#cybersecurity news#cybersecurity protocols#cybersecurity resources#cybersecurity risks#cybersecurity solutions#cybersecurity strategy#cybersecurity tips#cybersecurity training#cybersecurity trends#data breach#data encryption#data protection#data security#Digital Health#Healthcare
0 notes
Text
Exploring the New Horizons of SQL Server 2022: MS-TDS 8.0 and TLS 1.3
Understanding Tabular Data Stream (TDS) in SQL Server – Introduction In the realm of Microsoft SQL Server, an essential component that ensures seamless communication between a database server and its clients is the Tabular Data Stream (TDS). TDS is a protocol, an application layer protocol, to be precise, that plays a pivotal role in the exchange of data between a client and a server. This blog…
View On WordPress
#MS-TDS 8.0 protocol#SQL Server 2022 TDS#SQL Server performance optimization#SQL Server security enhancements#TLS 1.3 encryption
0 notes
Text
youtube
DomainOffices.com - Secure Domain Hosting - Domain Registration - Encrypted Web Hosting
Domain Offices Oversees Security Updates

Support: 24/7/365 Technical Support via Phone, Live Online Chat, and Support Ticket
DomainOffices.com is an International Domain Name Registrar Registering all Global Domain Name Extensions, including Encrypted Web Hosting, Domain Registration, Secure Domain Hosting, Register Domain Name, Secure Web Hosting, Domain Offices, Domain Renewal, DNS System, Virtual Private Server, Semi-Dedicated Server, Dedicated Server, Shared Hosting Plan, Whois Protection, Cheap Domain Hosting, Cheap Web Hosting, Free Domain Name, Reliable Website Hosting, Cloud Web Hosting,and SSL Encryption. Domain Offices offers you the opportunity to host your web sites in one of our five first-class secure data center facilities located in 1) Chicago, USA, 2) Sydney, Australia, 3) London, England, 4) Pori, Finland, and 5) Telepoint in Sofia, Bulgaria. The Steadfast, Chicago data center offers ideal conditions for hosting web sites whose visitors reside in the United States, Canada, or Latin America, and will guarantee you the fastest web page load speed feasible. The US data center facility option is available with all our shared web hosting plans, KVM and OpenVZ-powered VPS servers, semi-dedicated hosting servers and dedicated servers. Simply pick your package and then select the US data center facility from the drop-down menu on the signup form. Domain Offices works with one of the most famous data centers in Australia - SISGroup, which is situated in the Sydney central business district. The data center offers excellent Internet connectivity and perfect conditions for hosting websites whose visitors are physically located in Australia and Oceania. The Australian data center facility will guarantee you the fastest web site load speed possible. This data center option is available with all shared web hosting packages and OpenVZ-powered VPS web hosting packages of ours. Select the plan that you want on the signup form and then select the Australian data center from the pull-down list. If your web site will be targeted at users from the United Kingdom, the rest of Europe or Africa, we offer the perfect solution for you. We partner with top-class data centers situated in 1) London England, 2) Pori Finland, and 3) Telepoint in Sofia, Bulgaria, which offer the highest level of security for your web site and which will guarantee you the fastest web page loading speed possible. You can select the desired data center from the pull-down list on the signup form. This data center option is available with all shared web hosting plans, as well as with all KVM and OpenVZ-powered virtual servers offered on our website. Domain Offices has forged strong partnerships with international data-centers in the United States, Australia, Britain, Finland, and Bulgaria, to provide our clients with secure and reliable web hosting. Shared Hosting Features: -- Free Setup -- Disk Storage: Unlimited with Data Backups -- Domains Hosted: From 1 to Unlimited (Depending on Plan) -- Full Shell/ SSH/ FTP/ SFTP Users: Unlimited -- E-mail Accounts (POP/ IMAP/ Webmail): From 100 – Unlimited (Depending on Plan) -- MySQL 5 Databases: From 5 to Unlimited (Depending on Plan) -- Custom WHOIS Details and Custom DNS Records -- Programming: Perl, PHP5, Java Servlets, Python, Contrab -- One-Click Automatic Software Installers: WordPress, PrestaShop, OpenCart, Joomla, Drupal, Moodle, vTiger, Open-Realty, phpBB, and others -- Multi-lingual Control Panel -- Account Accessibility: Domain Offices Control Panel -- Five Secured Global Data Centers - With Data Backup -- Support: 24/7/365 Technical Support via Phone, Live Online Chat, and Support Ticket -- Guarantee: 99.9% Uptime Guarantee Website: DomainOffices.com Video Link: Domain Offices - Video
DomainOffices.com is an International Domain Name Registrar Registering all Global Domain Name Extensions, including Encrypted Web Hosting, Domain Registration, Secure Domain Hosting, Register Domain Name, Secure Web Hosting, Domain Offices, Domain Renewal, DNS System, Virtual Private Server, Semi-Dedicated Server, Dedicated Server, Shared Hosting Plan, Whois Protection, Cheap Domain Hosting, Cheap Web Hosting, Free Domain Name, Reliable Website Hosting, Cloud Web Hosting, and SSL Encryption.

#Encrypted Web Hosting#Domain Registration#Secure Domain Hosting#Domain Name#Domain Name System (Protocol)#Register Domain Name#Secure Web Hosting#Domain Offices#Domain Renewal#DNS System#Virtual Private Server#Semi-Dedicated Server#Dedicated Server#Shared Hosting Plan#Whois Protection#Domain Name Registrar#Cheap Domain Hosting#Cheap Web Hosting#Free Domain Name#Reliable Website Hosting#Cloud Web Hosting#SSL Encryption#Youtube
1 note
·
View note
Text
Netmaker: Automated Wireguard VPN You Can Self-host
Netmaker: Automated Wireguard VPN You Can Self-host #NetmakerOverview #WireGuardVPNProtocol #SecureOverlayNetworks #VirtualNetworkManagement #NetmakerVsOtherVPNs #IngressAndEgressGateways #NetmakerForBusinesses #FullMeshNetworking #NetmakerFAQs #WireGuard
With the hybrid workforce and hybrid networks spread across on-premises and cloud environments, network connectivity between devices and server resources is important no matter where these are located. A traditional VPN server and VPN connection between clients and resources is challenging to manage and maintain. Enter Netmaker, a tool designed for creating and managing virtual overlay networks…

View On WordPress
#full mesh networking#Ingress and Egress gateways#Netmaker FAQs#Netmaker for businesses#Netmaker overview#Netmaker vs. other VPNs#secure overlay networks#virtual network management#WireGuard encryption benefits#WireGuard VPN protocol
0 notes
Text
Under Watch — A. Putellas x Reader
"New Neighbour, New Problems "

WC: 1.8k
Summary: The threat against Alexia looms closer, but the management has the perfect solution.
You’re leaning against the hood of the car when she appears. Hair still damp from her post morning workout shower, hoodie slung over her shoulders, earbuds in. Alexia walks like someone who doesn’t expect to be bothered. Which is really ironic, considering that’s your entire job description.
She slows when she sees you. One eyebrow arches. "You’re driving me now? What is this, high school? Should I sit in the back and pretend I need some lunch money?"
You nod toward the driver’s side. "New protocol. Until further notice."
She groans audibly and mutters something in Catalan that you don’t catch, but the tone is universal. Disgust. Annoyance. A hint of ‘I’ll set this car on fire if it proves a point.’
And then she sees it.
The note.
You’d already bagged it, gloved and stored. But the outline where it sat on the windshield is still obvious.
She goes still.
"Another one?"
You nod. "Same handwriting. Slightly more aggressive."
"Of course it is. People get weird when their teams lose. Or win. Or breathe."
"We’re escalating precautions."
Alexia exhales sharply through her nose. "You mean panicking."
"They mean panicking," you correct.
"I mean adapting."
She gives you a long look. Not hostile. Just tired. Then gets into the passenger seat and slams the door with unnecessary force.
"Fine. But I’m choosing the music."
You don’t answer. She turns up the volume anyway.
They break the news right after practice. No warning, no soft lead-in.
“You’ll have a new neighbor starting today,” says the club security lead. “It’s part of our reinforced protection protocol.”
Alexia blinks. "Okay... What does that have to do with me?"
He shifts in his chair. "It’s your new bodyguard. She’s moving into the unit next to yours."
The silence is instant. Then loud.
“You cannot be serious.”
"Alexia, this isn’t just about notes anymore. Someone got inside the building. They knew your car."
"It’s a public parking lot. You let fans in there all the time."
"Not with access to your elevator."
She scoffs. "Maybe the security team should be better at their job then."
You don’t speak. Not yet. You're leaning against the back wall, arms folded, face neutral.
Alexia wheels toward you. "You knew about this?"
"I was informed this morning."
"Of course you were. And you just what? Packed up your little secret agent suitcase and showed up like it’s nothing?"
You shrug. "It’s part of the job."
"Well, I hate it."
"Duly noted."
She turns back to the security team. "This is ridiculous. I have a lock. I have an alarm system. What do you think is going to happen, someone crawls through the vents and I need Sombra next door to kick them in the face?"
"This isn’t a negotiation, Alexia. The club signed off on it. It’s a temporary assignment."
She mutters something under her breath that sounds like "temporary my ass" and stands, grabbing her bag.
“I’m not agreeing to this.”
“You don’t have to. It’s already done.”
A few hours later, you’re unlocking the door to your new apartment with a box under one arm. She’s standing in the hallway with a protein bar in hand, unwrapped but untouched.
“Let me guess,” she says. “You also have access to my building, and floor layout, my grocery list, and the microchip they implanted in my skull at birth.”
“Just your floor. And your training schedule.”
She stares. You unlock your door and step inside. She follows like an angry cat, keeping her distance but making sure you know she’s watching.
“This is overkill.”
You open the window. Sweep the place. First habit.
“You’re not that important.”
She bristles.
“That’s not what I meant,” she mutters, but you’re already plugging in your encrypted laptop.
She lingers in the doorway. "You’re not going to say anything else? No apology for completely violating my life?"
You look up. "I’m not here to violate. I’m here to protect."
She makes a face like that might be worse.
That evening, she stomps by as you’re bringing in another box.
“Are you going to be pacing the hallway all night like some sort of armed Roomba?"
“No. Just until I'm set up."
“Well, can you at least do it silently? Some of us are trying to pretend we have privacy."
You say nothing. She rolls her eyes and disappears into her apartment, slamming the door harder than necessary.
The next morning, she sees you in the hallway.
“I almost tripped over your boots,” she says. “Are you nesting in the hallway now, or should I just assume you live here more than I do?”
You nod toward the wall. “Your door has a new sensor now. Motion-triggered. You’ll hear it if someone lingers outside too long."
She freezes. Her mouth opens, then closes.
Then: "So now my door tattles on people. Great. Can’t wait for it to go off when I get home drunk."
You glance at her. "I'll disable the alarm if you're singing."
She glares. “You think you're funny, huh?”
You don't answer. That, in itself, is the punchline.
Dinner is loud, messy, and deeply therapeutic. Alexia’s on her second glass of wine, slumped into her chair like she’s aged a decade in one week. Patri’s already warned the waiter that the table might need extra bread, patience, and backup wine.
“She’s everywhere,” Alexia says, stabbing at her grilled vegetables and pretending they´re you.
“Like… omnipresent. A specter in a hoodie.”
"Sounds kind of hot," Marta says casually, sipping her sangria.
Alexia throws her a sharp look. "That’s not the point."
"But you’re not denying it," Irene hums.
"It’s irrelevant," Alexia snaps, then sighs.
"I open the door to take out my trash and she’s there. I go down to grab a delivery, she's already standing by the elevator like she’s predicting my thoughts. I swear it's like she has motion sensors or something."
"That’s… literally her job?" Patri says slowly, brows raised.
"Yeah, to protect you?" Irene adds. "Not to wait around until you're ready for a hug."
"Okay, but do bodyguards really need to be so silent all the time? It’s unsettling. She’s like a ninja. I dropped my keys in the hallway and she just... appeared. No footsteps. No sound. Just materialized out of nowhere like a ghost."
"A ghost in Nikes," Marta says, grinning.
"With great cheekbones," Irene adds.
Alexia makes a frustrated noise and drops her fork with a clatter. "This is not the support I expected."
"We’re just saying," Patri starts gently, "you’re not the same level of anonymous anymore. You’re… big. A worldwide football sensation. That means more weirdos, more creeps, more risk."
"And she’s good," Irene says. "Did you know she checked the entire restaurant while we were coming in? Didn’t even make a scene. Just a little loop like she was on her phone."
Alexia blinks. "Seriously?"
"Seriously," Marta nods. "Clocked it right away. Didn’t miss a beat. Kind of badass, honestly."
Alexia sinks a little in her seat. She hates that she hadn’t noticed. Hates that she kind of agrees.
"She even nodded at the hostess like she was confirming something," Patri adds. "Stoic, but polite."
"Oh my god," Alexia mutters. "She’s efficient. She’s polite. She’s a fucking Girl Scout with a security clearance."
Marta smirks. "And did we mention-"
"Yes, yes, she’s attractive, I’m not blind," Alexia grumbles into her glass. "But that’s not the point."
"Maybe not," Irene teases, "but it’s a nice bonus."
Alexia opens her mouth to argue, but her phone buzzes. She checks the new message.
[Sombrita]: Crowd is forming outside. Photos, videos. Suggest back exit. I’ll be waiting by the kitchen doors. Van is ready.
She groans. "She’s already planning our escape."
"That’s actually kind of hot," Patri says with a grin.
Alexia shakes her head, but there’s a reluctant tug at the corner of her mouth. "I just want her to be less… present."
The table goes quiet. Her friends exchange a look.
"Less present," Irene repeats softly.
"Not gone," Marta notes.
Alexia glares at her wine. "You’re all the worst."
Another buzz.
[Sombrita]: Five minutes. Back exit. Let me know if anyone needs help getting out.
Alexia sighs again. She types back a terse: Got it.
As they gather their things and follow the waiter through the back, Irene leans in close.
"Hey, at least she makes you feel safe, right?"
Alexia doesn’t answer, but she doesn’t argue either.
It’s late when you hear the sensor alarm start its soft beeping. Silent, subtle, set to trigger if anyone stays in the hallway for more than two and a half minutes. You’re on your couch, sweats and tank top, a book open in your hand you haven’t really been reading. She's been standing there for a while.
You wait. Half a minute more. Then, for your own amusement more than anything, you switch it from silent mode to a single loud beep. Just one. Just enough.
"For fuck’s sake!" Alexia growls angrily from outside, voice muffled through the door.
You’re up in a second, unlocking her front door with a single tap of the card.
She’s startled when it opens.
"Have you been watching me this whole time?"
You don’t say anything. You just smirk.
Alexia narrows her eyes. She’s flushed, slightly tipsy from wine with her family, wrapped in a soft oversized coat, hair messy from the wind. She looks more tired than drunk, but the tipsiness makes her looser, sharper-tongued.
"Well? Are you going to let me in or are we going to stand here all night while you flex your creepy telepathic door-opening skills?"
"After you." You step aside and gesture smoothly.
She walks in haughtily, except her handbag catches on the door handle as she passes. The momentum jerks her back slightly, throwing her off balance.
You catch her instinctively. One hand on her elbow, the other lightly at her waist.
"Careful," you say.
Alexia steadies herself but doesn’t pull away immediately. Her gaze flicks up to yours. "Are the reflexes also part of the job description, or do you just enjoy being everywhere at once?"
You tilt your head. "Would it bother you less if I said I enjoy it?"
She scoffs, but there’s a small smirk threatening to betray her. "A little full of yourself, aren’t you?"
You release her gently, stepping back. "Just observant."
She walks into her apartment, still facing you, eyebrows raised.
"Yeah, well. Don't get used to catching me."
"Wouldn’t dream of it."
Alexia turns away fast enough that you don’t see her smile, but not fast enough to stop you from knowing it’s there.
She closes the door behind her, and for the second time that night, you return to your post.
Across the hall, light from under her door seeps into the hallway. You hear her footsteps pause.
Then nothing.
But a few seconds later, the peephole darkens for just a heartbeat.
She’s watching you too now.
#alexia putellas x reader#woso x reader#alexia putellas#alexia putellas fanfic#alexia putellas imagine#alexia putellas blurb#alexia putellas fic#alexia putellas fluff#woso community#woso imagine#woso one shot#woso fanfics#woso soccer#woso imagines#woso blurbs#fcbfemeni x reader#woso#woso fic#fcbfemeni#espwnt x reader
352 notes
·
View notes
Text
China hacked Verizon, AT&T and Lumen using the FBI’s backdoor

On OCTOBER 23 at 7PM, I'll be in DECATUR, presenting my novel THE BEZZLE at EAGLE EYE BOOKS.

State-affiliated Chinese hackers penetrated AT&T, Verizon, Lumen and others; they entered their networks and spent months intercepting US traffic – from individuals, firms, government officials, etc – and they did it all without having to exploit any code vulnerabilities. Instead, they used the back door that the FBI requires every carrier to furnish:
https://www.wsj.com/tech/cybersecurity/u-s-wiretap-systems-targeted-in-china-linked-hack-327fc63b?st=C5ywbp&reflink=desktopwebshare_permalink
In 1994, Bill Clinton signed CALEA into law. The Communications Assistance for Law Enforcement Act requires every US telecommunications network to be designed around facilitating access to law-enforcement wiretaps. Prior to CALEA, telecoms operators were often at pains to design their networks to resist infiltration and interception. Even if a telco didn't go that far, they were at the very least indifferent to the needs of law enforcement, and attuned instead to building efficient, robust networks.
Predictably, CALEA met stiff opposition from powerful telecoms companies as it worked its way through Congress, but the Clinton administration bought them off with hundreds of millions of dollars in subsidies to acquire wiretap-facilitation technologies. Immediately, a new industry sprang into being; companies that promised to help the carriers hack themselves, punching back doors into their networks. The pioneers of this dirty business were overwhelmingly founded by ex-Israeli signals intelligence personnel, though they often poached senior American military and intelligence officials to serve as the face of their operations and liase with their former colleagues in law enforcement and intelligence.
Telcos weren't the only opponents of CALEA, of course. Security experts – those who weren't hoping to cash in on government pork, anyways – warned that there was no way to make a back door that was only useful to the "good guys" but would keep the "bad guys" out.
These experts were – then as now – dismissed as neurotic worriers who simultaneously failed to understand the need to facilitate mass surveillance in order to keep the nation safe, and who lacked appropriate faith in American ingenuity. If we can put a man on the moon, surely we can build a security system that selectively fails when a cop needs it to, but stands up to every crook, bully, corporate snoop and foreign government. In other words: "We have faith in you! NERD HARDER!"
NERD HARDER! has been the answer ever since CALEA – and related Clinton-era initiatives, like the failed Clipper Chip program, which would have put a spy chip in every computer, and, eventually, every phone and gadget:
https://en.wikipedia.org/wiki/Clipper_chip
America may have invented NERD HARDER! but plenty of other countries have taken up the cause. The all-time champion is former Australian Prime Minister Malcolm Turnbull, who, when informed that the laws of mathematics dictate that it is impossible to make an encryption scheme that only protects good secrets and not bad ones, replied, "The laws of mathematics are very commendable, but the only law that applies in Australia is the law of Australia":
https://www.zdnet.com/article/the-laws-of-australia-will-trump-the-laws-of-mathematics-turnbull/
CALEA forced a redesign of the foundational, physical layer of the internet. Thankfully, encryption at the protocol layer – in the programs we use – partially counters this deliberately introduced brittleness in the security of all our communications. CALEA can be used to intercept your communications, but mostly what an attacker gets is "metadata" ("so-and-so sent a message of X bytes to such and such") because the data is scrambled and they can't unscramble it, because cryptography actually works, unlike back doors. Of course, that's why governments in the EU, the US, the UK and all over the world are still trying to ban working encryption, insisting that the back doors they'll install will only let the good guys in:
https://pluralistic.net/2023/03/05/theyre-still-trying-to-ban-cryptography/
Any back door can be exploited by your adversaries. The Chinese sponsored hacking group know as Salt Typhoon intercepted the communications of hundreds of millions of American residents, businesses, and institutions. From that position, they could do NSA-style metadata-analysis, malware injection, and interception of unencrypted traffic. And they didn't have to hack anything, because the US government insists that all networking gear ship pre-hacked so that cops can get into it.
This isn't even the first time that CALEA back doors have been exploited by a hostile foreign power as a matter of geopolitical skullduggery. In 2004-2005, Greece's telecommunications were under mass surveillance by US spy agencies who wiretapped Greek officials, all the way up to the Prime Minister, in order to mess with the Greek Olympic bid:
https://en.wikipedia.org/wiki/Greek_wiretapping_case_2004%E2%80%9305
This is a wild story in so many ways. For one thing, CALEA isn't law in Greece! You can totally sell working, secure networking gear in Greece, and in many other countries around the world where they have not passed a stupid CALEA-style law. However the US telecoms market is so fucking huge that all the manufacturers build CALEA back doors into their gear, no matter where it's destined for. So the US has effectively exported this deliberate insecurity to the whole planet – and used it to screw around with Olympic bids, the most penny-ante bullshit imaginable.
Now Chinese-sponsored hackers with cool names like "Salt Typhoon" are traipsing around inside US telecoms infrastructure, using the back doors the FBI insisted would be safe.

Tor Books as just published two new, free LITTLE BROTHER stories: VIGILANT, about creepy surveillance in distance education; and SPILL, about oil pipelines and indigenous landback.


If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/10/07/foreseeable-outcomes/#calea

Image: Kris Duda, modified https://www.flickr.com/photos/ahorcado/5433669707/
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/
#pluralistic#calea#lawful interception#backdoors#keys under doormats#cold war 2.0#foreseeable outcomes#jerry berman#greece#olympics#snowden
400 notes
·
View notes
Text
🧬 “Deviation”
.
.
MANIPULATIVE!Albert Wesker x Reader | One-shot AU | Reader Unaware | Deep Psychological Control | Obsession-Slowburn
.
.
⚠️ Possessive behavior • Surveillance • Delusional Justification • Isolation tactics • No reader realization • Smut • Stalking
.
.

🧬 1. [Observation]
It begins, as most things do with Wesker, in silence.
Your first day on the team, you barely warranted a glance in the surveillance feed.
Another lab technician. Another replaceable assistant. Another insignificant moving part.
But then you lingered.
Stayed late. Came early.
Read the case files beyond your clearance level and didn’t flinch at the corpses.
You passed the first test.
Not that you knew there was one.
You thought it was coincidence that no one sat beside you in meetings.
That your access card opened doors you never requested.
That the intern who made a joke about your smile was transferred within the hour.
It wasn’t coincidence.
It was calibration.
He was isolating the variables.
And you, you became an anomaly worth noting.
He began compiling minor reports on your behavior, tucked into encrypted files labeled with meaningless acronyms—justifications for your existence in his system. He logged your arrival times, the hesitation in your speech, the way you handled scalpel trays with a certain… reverence. Clinical on the outside, but with the sharpness of someone who wanted to understand.
You weren’t like the others—those limp, nodding bureaucrats or ambition-hollowed researchers. You read between lines. You saw things. You didn’t ask for approval.
It should’ve been threatening.
But instead, it was fascinating.
---
🧬 2. [Containment]
Wesker doesn’t trust easily.
He trusts data.
Outcomes.
Silence.
But you unsettled the metrics.
You moved differently. You saw things. You questioned protocols he didn’t authorize you to read.
And he watched.
The way your fingers hovered over a scalpel you didn’t need to touch.
The way your reflection lingered in the biohazard glass.
The way your laugh, rare as it was, made low-ranking guards look up.
So he changed the guards.
Restricted hallway access.
Reassigned co-workers.
Built your world to orbit only him.
And still—still you never noticed.
Not when your new desk faced his office.
Not when your login synced with his terminal.
Not when your lunch orders began arriving, already paid.
You thought it was protocol. Efficiency. Company structure.
It wasn’t.
It was obsession.
Even your chair was adjusted—replaced with one designed to support your back based on posture data from security footage. Your lighting changed imperceptibly across weeks, tailored to prevent eye strain and keep you awake longer, sharper.
He scheduled briefings when you were most alert.
Redirected minor crises to ensure you'd report directly to him.
He watched the way you blinked when you were confused.
Memorized the twitch of your mouth when you were about to ask something risky.
Your coworkers left one by one. Transferred. Fired. Reassigned.
Those who got too familiar? Disciplined. Quietly.
You didn’t wonder why your inbox felt so clean.
Why no one interrupted your concentration anymore.
Why the company started feeling like a corridor, narrowing around you.
---
🧬 3. [Degradation]
It got worse.
Or—closer to the truth.
He found himself pausing the security feed just to watch the curve of your spine as you bent over notes.
He rewound your voice recordings, cataloguing the inflections in your “Good morning, sir.”
He deleted the word sir from your tongue in his mind.
He didn’t want your respect.
He wanted your obedience.
Your trust.
Your presence, constant and unrelenting.
You belonged in his space, like air belonged in lungs.
He just hadn't told you yet.
Sometimes, you left behind small things—sticky notes, paperclips, coffee cups. Harmless. Forgettable. But he kept them all.
The mug with a faint mark of your lip balm.
The pen you once clicked while reading virology samples.
A typed memo, crumpled, with a single word scratched out and replaced. "Necessary."
He examined them not with sentiment but calculation.
These were not keepsakes.
These were proofs of proximity.
You were slipping under his skin molecule by molecule, and he needed evidence of your presence in his domain.
But there were moments—dangerous ones—when calculation gave way to something darker.
Moments when you reached for a dropped stylus beneath the lab table and the hem of your coat pulled taut across your thighs.
Moments when you tilted your head to read something over a microscope and exposed the soft column of your neck.
Moments when the feed from the surveillance cameras caught just enough.
He knew every angle of your body from security footage.
The way your blouse sometimes gaped slightly when you leaned forward.
The way you stretched without thinking, unaware of how it framed you.
Unaware of the man watching—memorizing.
It was a weakness.
A flaw in his design.
But sometimes he would watch the footage at half-speed, eyes burning, jaw clenched, and tell himself it was for behavioral monitoring.
That the brief tightening in his chest wasn’t arousal, but concern.
And yet—when you bent to pick up a file one night, alone, late, and the back of your skirt lifted just slightly—
—his fingers had twitched.
Not from irritation.
From restraint.
From the raw, silent thought that he could take you. Right there.
Not in fantasy. Not in dream. But in brutal, clinical, breathtaking reality.
He could fuck you against the sterile counter and no one would stop him.
No one would even know.
But he didn’t.
Of course he didn’t.
He was control. Discipline.
He filed the footage.
Encrypted it.
And watched it again the next night.
Hands behind his back.
Jaw locked.
Throat tight with the sick, hungry coil of desire he refused to name.
You didn’t know.
Didn’t see.
Didn’t feel the weight of a man who no longer saw you as a subordinate or asset—
—but as something already his, simply awaiting the correct time to be claimed.
---
🧬 4. [Denial]
You never caught it, but he looked away first.
Every time.
Every instance your gaze met his, however briefly.
You assumed it was deference. Coldness. That clinical thing he wore like a second skin.
But it wasn’t.
It was containment.
Because the sound of your voice—the precise cadence in which you said “Understood, Doctor Wesker”—lit up some dormant, vile thing in him.
Something untested.
Something monstrous.
He was not above temptation.
He was simply better at dissecting it.
The way you smiled at your coworkers, never at him?
He noticed.
The way you stood just a fraction closer when anxious, fingers tightening at your sides?
He filed it away.
He let others believe you were isolated by accident.
But he'd engineered that loneliness. Curated it.
Suffocated anything that threatened to pull your attention elsewhere.
You never got that offer for project co-lead.
Never received the anonymous gifts left at your desk by interns.
Because Albert intercepted them.
Silently. Strategically.
You didn’t know it was his hand pulling you toward him, only that every direction seemed to fold inward until he was the only constant.
The only man who saw you.
Who understood you.
He watched you trace your notes, watched your lips form silent syllables, and all the while he denied himself.
Denied the heat pooling in his abdomen.
Denied the cruel ache behind every “Goodnight, sir” you uttered.
Denied the nightly compulsion to run simulations of what you would sound like begging.
And when he couldn't sleep, he listened to your voice on the lab’s intercom archive.
Just to hear it.
To pretend.
To substitute control for contact.
And still—he told himself he had not crossed the line.
Not yet.
Because you were still untouched.
Still pure, in the way only someone unaware of their ownership could be.
---
🧬 5. [Possession]
He began to see it in everything.
The way others looked at you—a threat.
The way you spoke about your family—a liability.
The way you said “thank you” when he passed you reports—intolerable.
You didn’t thank him.
You didn’t understand him.
You couldn’t.
But that was fine.
Understanding would come later.
He started curating your tasks more delicately.
Steered you away from field ops, too dangerous.
Assigned you exclusively to him, citing “performance optimization.”
You didn’t protest.
You thought you were being promoted.
But in truth, you were being drawn in.
Woven tighter.
Placed carefully, perfectly, exactly where he wanted you.
In his office.
In his world.
In his reach.
Your name was embedded in his daily reports. Your security log-in pinged his terminal every time you swiped a door.
The other researchers stopped referencing your work without Wesker’s express permission. He had erased your reputation as independent—you were his now.
And no one questioned it.
Not when his gaze burned through the glass walls of the lab.
Not when he stood beside you in meetings like a shadow wearing a tailored suit.
Not when his hand briefly brushed yours while reviewing samples, and he didn’t pull away.
He didn’t need to pull away.
He had already claimed what he wanted.
---
Now, his fingerprints existed on more than your reports.
He’d rewritten your schedule to end near his. Aligned your meals. Synced your lab hours. Even your breaks were subtly shifted, your elevator stops timed perfectly with his descent.
You didn’t see it.
But he did.
Every day you returned to your workspace slightly adjusted—your chair moved back in, your pens restocked, your personal mug rotated exactly one degree counter-clockwise.
“We’re optimizing,” he’d say.
“For your convenience.”
He'd begun accompanying you to biometric checks. At first, a coincidence. The second time, an excuse. By the third, he was inputting your medical logs himself.
His voice was always calm. Always formal. Always patient.
But his gaze lingered.
His presence loomed.
And his hands—always gloved—brushed against the small of your back far too often for protocol.
---
And he watched.
From behind glass. From dark monitors. From still frames and slow replays. When your blouse sat a little too low. When your eyes wandered where they shouldn’t.
You were careless with your innocence.
But he would be careful for you.
He adjusted the brightness of the surveillance feed. Zoomed in. Studied the way you leaned too close to your keyboard.
Imagined your breath fogging the screen.
Imagined how easily that breath could hitch. Could falter. Could beg.
You have no idea, he thought.
But you will.
Not yet.
But soon.
Understanding would come later.
---
🧬 6. [Infection]
The final stage was the most dangerous.
You said his name once.
Not “sir.”
Not “Wesker.”
Just:
“Albert…?”
His gaze snaps up from the report.
You’re standing in the doorway of his office, the heel of one shoe slightly kicked back, as if you weren’t sure whether to enter. The folder in your hand trembles slightly—an involuntary twitch you don’t even notice. But he does.
He notices everything.
The breath that stutters in your throat after the name escapes.
The flicker of hesitation in your pupils when his expression doesn’t immediately soften.
The way you shift—defensive, unsure—before you correct yourself:
“I mean—sir. Sorry, I meant—sir.”
But it’s already too late.
The damage is done.
You spoke it aloud.
Not in passing.
Not as a slip of protocol.
Not with bitterness or irony.
But with concern.
Soft. Tentative. Almost gentle.
And that… that is what undoes him.
You don’t know he has a file buried six levels deep into a server no one else can access—labeled with your name, storing every image of you captured on internal footage.
You don’t know he’s wiped out four internal transfer requests that would have pulled you from his floor.
You don’t know he personally selects your meals for team events—ensuring your preferences are always met, even when no one else notices.
You don’t know he’s kept you here, orbiting him, perfectly placed, under the illusion of promotion.
And now you’ve said his name like it belongs to you.
Like he does.
“Sir,” you try again, a nervous laugh escaping you. “Apologies. I—I didn’t mean—”
He stands slowly, measured, the desk separating you like a fragile boundary he’s had to respect for far too long.
“No need to apologize,” he says coolly. “You simply… surprised me.”
But inside? His thoughts are nothing but static.
He replays the syllables.
Not just the sound, but the shape of your mouth when you said it.
He files it into memory. Deep. Permanent.
And he knows—sooner than even you do—that this is the beginning of the end for the illusion.
Because from this moment on, you’ve stopped being a project.
Stopped being a subject.
You’ve become a trigger.
A fixation.
An opening he hadn’t anticipated—but cannot ignore.
You said his name once.
You won’t realize until it’s far too late:
You’ll never say it the same way again.
Because you didn’t know what you’d done.
You didn’t hear it the way he did.
Like it was already yours to say.
Like he wasn’t a god.
Like he was a man.
A man who had already rewritten every security protocol to keep you near.
A man who eliminated colleagues who made you uncomfortable.
A man who—if you ever truly looked—might shatter the illusion of “normal” with one cold sentence:
“You’re not here by accident.”
“You’re here because I designed you to be.”
But you don’t know.
You smile politely.
You offer your reports.
You drink the coffee that arrives on your desk precisely how you like it.
You go home.
You live your life.
While he rewatches your day in full.
While he listens to your voicemails and deletes names from your inbox.
While he studies you like you’re the last unexplained miracle on Earth.
While he reminds himself that love is irrelevant.
Control is what matters.
And he already has it.
---
He’d timed every entry and exit.
He knew how long you took in the restroom.
Which hallway you paused in to check your phone.
What time of day your voice grew tired.
He saw it as clearly as he saw cell degradation under a microscope.
That slow unraveling.
That quiet compliance.
You were adapting.
Your posture had shifted. Subtly. You walked faster when alone. Slower when near him. You dressed differently—more reserved, perhaps without realizing. You avoided eye contact with male superiors.
Wesker approved.
He didn’t speak of it.
Didn’t need to.
The conditioning was holding.
You had stopped asking questions.
Stopped challenging schedules.
Stopped requesting to work from other wings.
You had folded into the environment he designed—one where he was a constant hum beneath your daily routine. Where his name lingered at the back of your tongue. Where his voice set your pace and his silence set your nerves.
---
“You don’t know what you’ve done,” he muttered to himself, watching the security footage replay. While he studies you like you’re the last unexplained miracle on Earth.
There you were again. That exact moment. Your eyes soft, confused, lips parted: Albert…?
He paused the video.
Leaned back.
Let the sound echo in the sterile quiet of his office.
It was not an accident.
Not some sweet slip of tongue.
No.
It was the infection taking root.
Your body catching up to what your environment had long accepted.
Dependence.
Deference.
Attachment.
He could work with that.
Love was messy. Emotional.
But dependence—he could mold.
He could reinforce it, reward it, create just enough tension to keep you needing his approval.
To keep you needing him.
---
(A/N: should I make a part 2??? I mean- I already have it. I just wanna hear it from you dirty sluts;>)
#fanfiction#x reader#fanfic#albert wesker x reader#albert wesker#albert wesker smut#possesive love#stalker au#resident evil fanfiction#resident evil albert wesker#albert wesker x you#albert wesker x y/n#x you#x you smut#smut fanfiction#minors dni#minors do not interact
125 notes
·
View notes
Text

He should be arrested for violating our privacy. He was not vetted by congress and has no security clearance.
Contact your state’s attorney general and request help.
Can we ask the ACLU to file a class action suit? Who’s with me?
“Let’s get into the details. Musk’s staffers have been caught plugging external hard drives into federal agency systems and reportedly locking others out of private rooms to perform—who knows what actions. This behavior violates key cybersecurity laws under FISMA and NIST guidelines, which are designed to protect sensitive federal information. Here’s why this is a serious problem.
Federal systems are strictly regulated, allowing only approved devices to connect. Unauthorized external drives can introduce viruses, ransomware, or other harmful software that may compromise entire networks and disrupt essential operations. This puts system stability and continuity of services at risk, endangering critical infrastructure.
These devices could also be used to steal or damage critical information, including personal data for millions of Americans—such as Social Security recipients and taxpayers. Unauthorized access creates significant vulnerabilities, exposing sensitive data to the risk of cyberattacks. Such attacks could cripple vital services and compromise the privacy and safety of millions of people.
Additionally, federal agencies have strict access controls to prevent unauthorized data manipulation or theft. When unauthorized devices are connected, these protections are bypassed, allowing unauthorized users to potentially alter or extract sensitive data. This undermines system integrity and opens the door to both internal and external threats.
External drives also often lack essential security features, such as encryption and antivirus scanning, making them vulnerable to cybercriminal exploitation. These security gaps further increase the risk of data breaches and system compromise, which can have far-reaching consequences.
Federal systems handle trillions of dollars in payments and manage personal data for millions of U.S. citizens. By bypassing cybersecurity laws and protocols, Musk’s staffers are putting these systems—and the public—at serious risk. This activity is illegal, reckless, and unacceptable. Immediate oversight and intervention are necessary to stop these violations!” ~ A N P S
225 notes
·
View notes
Note
You may have posted about this before, but im very curious about you saying "email was a mistake" because it's such a cemented part of online communication. Is it the technology?
Email became infrastructural in a way that it was never intended to be and wasn't designed for.
There is too much momentum toward email being the primary means of business communication that unless there is a massive technology shift we're unlikely to see wide adoption of an alternative and email takes up so much space in the IT space that it's hard to say what the alternative would be.
Much of what used to be email now happens in company chat apps, which I think is an improvement in many ways, but you chat with your coworkers in a way that you're unlikely to chat with a client or send a quote to a prospect.
A huge amount of effort goes into making email better, and making email systems talk to each other, and making email secure because it is so ubiquitous that you can't realistically ask people not to use it.
But it's fucking terrible and we're asking too much of a set of protocols that was supposed to send small, not-very-private, communications between academics.
Why can't you send big files via email? Because that's not what email is for.
Why is it a pain in the ass to send encrypted emails? Because that's not what email is for.
Why aren't your emails portable, and easy to move from one service to another? Because that's not what email is for.
Why are emails so easy to spoof? Because they were never meant to be used the way we use them so there was no reason to safeguard against that fifty years ago
It's like how social security cards were never meant to be used as one of your major super serious government IDs where all of your activity through all of your life is tracked, because if they knew they needed a system for that they probably would have built a better one in the first place.
Nobody who sat down and developed email looked more than half a century into the future and went "so people are going to be using this system to create identities to access banking and medical records and grocery shopping and school records so we'd better make sure that it's robust enough to handle all of that" because instead they were thinking "Neat! I can send a digital message to someone on a different computer network than the one that I am literally in the same building as."
We think of email as, like, a piece of certified mail that is hand delivered in tamperproof packaging to only the intended recipient who signs for it with their thumbprint and a retina scan when it is, instead, basically a postcard.
It would be absurd to try to do the things people do with email with postcards, and it's *nearly* as absurd to try to do them via email.
1K notes
·
View notes
Text
Donnie Tech Part 1/?
After many moons here are the promised observations of the cartoon shtick logic of Donnie's weapons for season one!! Will link a season two and movie version Eventually, but keep in mind I can't explain in depth how each bit of tech works, rather that I can pinpoint the functions for the visual bit. Keep in mind that Donnie's tech can pretty much do any ridiculous thing you can put your mind to, and that it can also backfire in any ridiculous way you can put your mind to.
Tech Bo:

Collapsible, can become a shorter version of itself easily stored
Shoot a grappling hook AND function as a zip line
Can form a rocket from either end (usually at the same time, resulting in the bo spinning)
Is equipped to be a fire extinguisher
Can shoot out lasers
Has a button that activates the "Shopping Cart Protocol" to lock the Turtle Tank if it goes outside a set perimeter
Top can turn into a rocket powered fist
Turn into a giant drill
Turn into a saw
Turn into a tranquilizer
Turn into a tennis ball shooter
Turn into a selfie stick
Top can turn into a disco ball of "multidimensional reflective orb neutralizer"
Battle Shell:

Has rotary engines (think jet turbine or computer fan) that help him fly around. He calls them "rotors" for short
Can transform into a seat so April can sit on his back
Can split up into a DJ set up in "music mode"
Jet Pack Shell:

His fastest mode of transportation
Not much is shown, but April had a significant difficulty controlling it
Spider Shell:

Has four arms with three fingers
Arms can turn into saws
Has a seemingly endless toolkit inside that includes basic things like hammers and wrenches, but also blowtorches
Goggles:

Has night vision
Can function as binoculars
Is able to summon is tech ("communicates with microwave transceiver with class c encryption protocols")
Read mystic energy signatures after adding the crystal they found in Draxum's lab
Gauntlet:

Has an app that can tap into every security camera in NY
Bug Slapper:

Has a green Mad Dogs sticker on the side
Compacts itself into a metal suitcase and then expand back into a vehicle
So far only uses Big Mama's webbing material as projectiles
Shelldon:

Began as an automated smart lair designed with the intent as a cleaning assistant
Has a "disposal unit" which unlocks several of Donnie's weapons such as: guns, pinchers, drills, and flamethrowers
Can carry at least two turtles (Mikey and Donnie)
Is nicknamed "Cyber Bishop" by Donnie
Uses surfer dude slang: “dude”, “gnarly”, “buzzkill”, “okey dokey”, “dawg”, “you beefed it”, “brohounds"
As a smart lair has clear favoritism towards Donnie until tampered with. As a drone they share more of a familial or pet like relationship, and Shelldon has room to sometimes poke at Donnie's faults as well

In conclusion there's not much to worry about breaking canon, the physics of our reality, or understanding complicated tech and science to write about Donnie's tech. He can do whatever he wants as long as it's silly, overly dramatic, and includes an unnecessary amount of purple guns. His tech bo is especially flexible with breaking the rules even before we get to his ninpo powers.
I'm keeping the Turtle Tank separate, because it also deserves its own post. Happy writing!
#rottmnt#rottmnt donnie#rottmnt donatello#rise of the teenage mutant ninja turtles#rise of the tmnt#save rise of the tmnt#tmnt#teenage mutant ninja turtles#analysis#critter talks
261 notes
·
View notes
Text
oh boy, i haven't used a proper chat integrator since i was running Adium locally way back in like... god, 2016, probably?
and even back then, Adium was showing its limits... iirc the adium/libpurple devs sort of hacked in some pseudo-xmpp support for facebook messenger back then but it was really buggy, to the point of uselessness, and the situation's only gotten more fragmented, protocol-wise, since then
so without having looked at the landscape at all, i'd say my bigger concern would be "does this thing even work well" before getting into any kind of security questions
it's sad that that is the state of the world! but it is what it is
if i could force everyone in my life to use Discord it would be measurably remarkably better
#god adium was so good when it was good. simpler times#i gather that the question's strictly about chat integrators rather than about any specific protocol#but in case anyone's reading this and wondering about specific apps:#if you have any kind of Serious Security Constraints it depends a bit on your threat model but#you generally want something with end-to-end encryption e.g. Signal#Telegram is sketch as fuck#using something like e.g. Discord is fine in terms of usability and such (hence why i use it so much!)#but they do not have an E2E encryption story last i checked so#you Do Not Want them for most cases where your threat model matters etc#(eg i am shitposting about video games there i am not doing shit that feds might be curious about)
16 notes
·
View notes