#Smart Strong Password Generator
Explore tagged Tumblr posts
Text
Incorrect CoD Quotes #7
Sherlock, in response to being asked to sneak into Valeria’s house: Okay. Don’t worry, guys. I got your back!
*She steps behind Ghost*
Sherlock: From right here.
———
Laswell: Hey did you call General Shepherd a bitch?
Price: Yeaaahh! He changed the Wi-Fi password!
Laswell: You can’t be-
Nikolai: THAT BITCH CHANGED THE WI-FI PASSWORD!!!!
———
*Something bad and unexpected happens on a mission*
Nikolai: Why didn’t you tell me?!
Sherlock: Well, because I wanted us to fail.
Nikolai: 😑
Sherlock: OBVIOUSLY I DIDN’T KNOW!!!!
———
Graves: Hey, I always get the vibe that you, like, hate me or something.
Ghost: What?! Me, hate you?!
Ghost: …You’re right.
———
Soap: If I punch myself in the face and it hurts, am I strong or weak?
Ghost: Strong.
Gaz: Weak.
Price: A dumbass is what you are.
———
Alejandro: When I first met you, I thought you were weird and annoying.
Graves: …
Graves: And?
Alejandro: And you are.
———
Hadir: Sorry I’m late, I was… doing things.
*pounding footsteps can be heard from behind the door*
Alex, bursting through the door: HE PUSHED ME DOWN THE FUCKING STAIRS!
Hadir: Push is such a strong word. I prefer calling it … giving you a little nudge.
Alex: Oh I’ll give you a nudge when I shove mY FOOT UP YOUR ASS!
Price, covering Farah’s ears: Hey! Watch your fucking language in front of the president!
———
Graves: Yo, what’s that song that goes like, “Despacito”?
Alejandro: Despacito?
Graves: Yeah. What’s the name?
Alejandro: DESPACITO
Graves: …Yeah. What’s the name?
Alejandro, pissed: Dios mío, you’re an idiot!
Graves: Thank you! Alexa, play “Dios mío, you’re an idiot!”
Echo Dot Alexa: Ok *starts playing Despacito*
Alejandro: 😦
Graves 😎
———
Ghost: What happens to the car if you press the break and the accelerator at the same time? Does it take a screenshot?
Price:
Soap:
Gaz:
Roach, wanting to be a little shit: Ye-
Sherlock being done with life: No. That’s it, I’m driving.
———
Soap: Go to bed! It’s 3am. If you don’t you’re going to hate yourself in the morning!
Roach: Jokes on you, I’m gonna hate myself in the morning ✨REGARDLESS✨
———
Sherlock: I don’t want to be a person anymore.
Ghost: … What?
Sherlock: I’m tired of it.
Soap: 😥 Maybe we should talk about this-
Sherlock: I just wanna be a dinosaur.
Ghost:
Soap:
Roach: Me too!
———
*Sherlock walks into the rec room and drops her bag on the floor*
Sherlock: tEll mE wHy tHerE arE 7 BiLlioN peOplE On tHiS DAmN PlaNEt ANd NoT 1 pErsOn hAs A CrUsH On mE!? WhAt ThE HelL UNiveRsE?!!
Gaz, whose been pining for her since the day he met her: what about me 🥺
———
Roach, sleep deprived: All I want-
Soap: Oh no
Roach: -is for for someone to walk up to me-
Ghost: What’s going on now?
Roach: -look me in the eyes, put their hands on my face, and very passionately-
Gaz: Kiss you?
Roach: -twist as hard as they can and put me out of my fucking misery!
Price: Roach no
Roach: Roach yes
———
Laswell: John, aren’t you supposed to be on a Zoom call right now?
Price: I got kicked off already.
Laswell: Why! What did you do?!
Price: Well she said, “DoN’t GeT sMaRt WiTh Me!” and I said, “Then what are we paying you for?” and she did not like that!
Laswell: John that’s rude.
Price: …But I’m right on this.
———
Roach: Remember when you guys told me to go to the pharmacy?
Sherlock: *looks at Gaz before looking at Roach* Yess
Roach: Mmm they’re out of my ADHD medication for five days.
Sherlock: Oh my god-
Roach: It’s gonna be a fun week!
Gaz, already leaving the room: I’m going to my mother’s-
Sherlock, pissed that she would have to watch Roach by herself: What happened to “in sickness and in health”, motherfucker!?
———
Sherlock: I’m sorry guys… there’s nothing else we can do. Graves is dying, we’re gonna have to pull the plug.
Gen. Herschel Shepherd: Oh my god… Oh my god…
Soap: Can I do it?
Gen. Herschel Shepherd: What?
Soap: Can I pull the plug?
Gaz: Hey no! I wanna pull the plug!
Ghost: No fuck you! I get to do it!
Soap: This is bullshit! I wanna do it!
Price: NO! I-I’m the oldest, I should be the one to do it!
Ghost: I’ll thumb wrestle you for it.
Price: Fine, let’s go BITCHHH
Price & Ghost, hands together for thumb wrestling: 1, 2, 3, 4, I declare a thumb war!
Gen. Herschel Shepherd: Are you two serious?!
Price: YOU DON’T EVEN HAVE A CHANCE
Ghost: OH, YOU’RE GOING DOWN
Price: NOOO, NO, NO, NOO
Ghost: OHHHHHHHHHH
*Ghost wins*
Ghost: Yess
Price: NO
Ghost: yEsSSSSS
Price: DAMN IT
Ghost: Alright, where’s that plug?!
Soap: Where’s that plug?
Ghost: Where’s that mother fucking plug?!
Sherlock: Do you have ANY respecT?!
Ghost: No, I have 0 respect!
Soap: We have 0.
Price: We have 0 respect.
Gaz: I have nothing!
Gen. Herschel Shepherd: I can’t even believe this!
Sherlock: Yeah, me too. Alright let’s get this show on the road! I got some leftover lasagna at home, and it’s got my name on it!
———
Ghost: Good morning, everyone. God has let me live another day. And I’m about to make it EVERYONE’S problem.
Soap: Good morning to you too.
Price: 🤦♂️ I give up.
———
Alex: What do we do when we’re feeling sad?
Farah: Watch a murder documentary and plan out how to do it without getting caught?
Hadir’s soul in Hell: *scared shitless despite already being dead*
Alex: Jesus fuck, NO!
———
Soap: You guys won’t believe what just happened!
Ghost: What happened?
Soap: Some guy from Shadow Company wouldn’t leave Sherlock alone-
Nikolai, maternal uncle instincts kicking in: Excuse me!
Soap: -but she took care of it!
Price, to Sherlock: How’d you take care of it?
Sherlock: Simple. *clears throat* 🎶Row row row your boat, The fuck away from me, Felony felony just tried to test me, And I’m a cause a scene🎶
Nikolai, laughing: That’s my girl!
#call of duty#call of duty oc#cod sherlock#cod nikolai#chimera sherlock#kate laswell#incorrect call of duty quotes#captain john price#phillip graves#simon ghost riley#john soap mactavish#kyle gaz garrick#alejandro vargas#hadir karim#alex keller#inspired by youtube#gary roach sanderson#general shepherd#farah karim
66 notes
·
View notes
Text
The Growing Importance of Cybersecurity in IoT Devices

In today's hyperconnected world, the Internet of Things (IoT) is transforming how we live and work. From smart homes to industrial automation, IoT devices are becoming an integral part of our daily lives. However, with this rapid growth comes an equally rapid increase in cyber threats. The need for robust cybersecurity in IoT devices has never been greater.
The IoT Revolution and Risks:
IoT devices are set up to ease lives, but it also involves certain risks with this convenience. There is vulnerability with the likes of smart thermostats, connected security cameras, wearable fitness trackers, or industrial machinery, because these devices all come under hacking opportunities. Through such vulnerabilities, hackers may hack unauthorized, obtain sensitive information, or disable key systems.
For instance, a hacked smart home device might give the attacker access to the homeowner's personal data or even control over their home's systems. Industrial IoT breaches can be a larger threat that might lead to disruptions in manufacturing or energy sectors with severe implications.
The devices of the Internet of Things usually lack serious security measures and therefore become vulnerable to cyber criminals. Many are delivered with the default password, with old firmware or even low-grade encryption; that leaves open a door to be attacked. In general, this vulnerability is made worse because an IoT network will have more than one device in communication with another. One device could become the access point of a gateway into a full network.
The Role of Ethical Hacking in Securing IoT
To this end, cybersecurity experts are increasingly employing ethical hacking as a way to find and remediate vulnerabilities in IoT systems. Ethical hackers, often referred to as "white hat" hackers, utilize their expertise to probe for vulnerabilities in a system before an actual hacker could take advantage of the weakness.
Cyberspace security and ethical hacking courses may be subscribed to, which will train aspiring professionals to secure various IoT devices and networks. These topics include penetration testing, secure coding, as well as network defense strategies suited for IoT environments.
What Can You Do to Stay Safe?
1. Update Regularly: Make sure all IoT devices have the latest firmware updates and patches.
Use Powerful Passwords: Change default passwords with strong unique passwords.
Secure Network: Use a powerful Wi-Fi password and apply network encryption.
Use Minimum Permissions: Give IoT devices the minimum permission required.
Know Cyber Security: Enroll yourself in a cyber security and ethical hacking course that would enhance your knowledge further to protect their devices.
IoT Future Security
As IoT grows, so does the necessity for advanced security. This practice is beginning to have regulations and standards in place from governments and industries for increased security. However, individual awareness and action will remain a critical engine for change.
By prioritizing cybersecurity and investing in ethical hacking knowledge, we can ensure that the IoT revolution brings convenience without compromising safety. Protecting IoT devices isn't just a technical challenge—it's a responsibility we all share. At this juncture, the relationship between IoT and cybersecurity is bound to be of challenges and opportunities. The higher the number of connected devices grows, the bigger the potential is for innovation, and for exploitation. Enroll in a cyber security and ethical hacking course and be ready to stay a step ahead of the threats towards a safer digital future.
Join the IoT revolution; join it with security. All power to the hands of those who can.
2 notes
·
View notes
Text
How to Implement Two-Factor Authentication on a Website
These days, securing a website isn’t just a good idea—it’s a must. One of the best ways to add an extra layer of protection is through Two-Factor Authentication, or 2FA for short. If you’ve ever had to enter a code from your phone after typing in your password, you’ve used 2FA.
In simple terms, it’s a method that asks for two pieces of proof to confirm you’re really the person trying to log in. Usually, the first is your password, and the second is something like a code sent to your phone or email. This way, even if someone figures out your password, they still can’t get in without that second step.
Let’s break down how to add 2FA to your website and why it matters.
Why Two-Factor Authentication Matters
Cyber attacks are getting smarter. Passwords alone are no longer enough to keep accounts safe. Many people reuse the same passwords, and hackers often steal them from one site and try them on others. With 2FA, even if your password is leaked, your account still has a strong line of defense.
For website owners—especially those managing user data, online payments, or sensitive details—adding 2FA shows visitors that you take their safety seriously.
Basic Steps to Implement 2FA
Whether your site is built with PHP, Python, JavaScript, or a CMS like WordPress, the process follows the same general flow:
1. User Login with Username and Password
This is the regular login step. The user types in their email or username and their password.
2. Generate and Send the Second Factor
Once the password is correct, the site asks for a second piece of proof. This can be:
A one-time code sent to the user’s email or phone
A time-based code from an app like Google Authenticator
A push notification sent to an app
A hardware key (less common for general users)
Let’s take the example of using Google Authenticator. When users sign up for 2FA, you give them a QR code that they scan with their app. The app then generates new codes every 30 seconds.
3. User Enters the Code
After the code is sent or generated, the user types it in. The website checks if it matches the expected value.
If it’s correct, they’re logged in. If not, access is denied.
4. Add Recovery Options
What if a user loses their phone? You should give them a way to recover their account. This can be through backup codes, a recovery email, or answering security questions.
Tools and Libraries That Help
There are many tools available that make setting up 2FA easier:
Google Authenticator: Common and trusted.
Authy: A user-friendly option with cloud backup.
TOTP Libraries: If you’re coding it yourself, look into Time-based One-Time Password libraries for your language (e.g., pyotp for Python or otplib for JavaScript).
Plugins for CMS platforms: WordPress, Joomla, and others often have ready-made 2FA plugins.
If you’re not sure where to begin or need something polished, the best web design company in Bhubaneswar can help implement secure and user-friendly 2FA solutions suited for your site.
Keep It Simple for Users
Security should never make a site harder to use. A good 2FA system is quick, clear, and supports everyday users. Allow them to choose the method they prefer—text message, authenticator app, or email—and make the setup process easy to follow.
Provide clear instructions and a support option in case they get stuck.
Where to Use 2FA
You don’t have to add 2FA to every part of your site. Focus on:
Admin login areas
User accounts with personal or payment details
Business dashboards
Anything involving data management
Even if your website doesn’t store personal information, protecting your backend from unauthorized access is always a smart move.
Final Thoughts
Adding Two-Factor Authentication is one of the most effective ways to improve website security. It’s not complicated, and the benefits are huge. You protect your users, build trust, and reduce the chances of someone breaking into your system.Whether you're a small business, nonprofit, or running an e-commerce site, you don’t have to do it all alone. The best web design company in Bhubaneswar can guide you through setting up 2FA the right way—so you can focus on growing your site without worrying about security threats.
#performance marketing services bhubaneswar#digital marketing services in bhubaneswar#seo services in bhubaneswar#web development services in bhubaneswar#Integrated Digital Marketing agency#best web design company in bhubaneswar
0 notes
Text
What is a Telegram Bot and How Does It Work?
In the world of messaging apps, Telegram has become a favorite for many people due to its speed, privacy features, and flexibility. But one of the most interesting parts of Telegram isn’t just chatting with your friends - it’s bots. If you’ve ever seen a Telegram account that sends messages automatically, answers questions, or even plays games with you, you’ve probably interacted with a bot. But what exactly is a Telegram bot, and how does it work? Let’s break it down in a simple, non-technical way.
What is a Telegram Bot?
Have you ever heard of a Telegram bot yet? This kind of software application taps into Telegram’s infrastructure, which can interact with people like a human. However, you’re doing it with a chat app. Interestingly, you can converse with it, have it do something and receive responses quickly. When you have a Telegram bot, it can do many things, such as sending messages, arranging weather reports, translating languages, setting up any task and as if all this were not enough, hold conversations like a human.
What Can a Telegram Bot Do?
Telegram bots can be incredibly versatile. Some common uses include:
Providing information: Weather bots, news bots, and even dictionary bots can give you quick updates or answers.
Entertainment: You can play trivia games, read jokes, or even explore choose-your-own-adventure stories.
Reminders and to-do lists: Some bots help you stay organized by sending reminders or managing your daily tasks.
Translation: Certain bots can translate text from one language to another right inside the chat.
Learning and study: Some bots quiz you on vocabulary, math, general knowledge, and more.
Bots can be as simple as sending a daily quote or as advanced as holding a conversation using artificial intelligence.
How Does a Telegram Bot Work?
At the heart of every Telegram bot is a piece of software that uses Telegram’s Bot API. The person who creates the bot writes code that tells it what to do when it receives certain messages.
For example, a weather bot might be programmed like this:
Wait for a user to send a message like "weather in London".
Recognize the word “weather” and the location “London”.
Look up the current weather using a weather service.
Send the weather info back to the user in the chat.
This process all happens in just a few seconds, and from the user’s perspective, it looks like the bot is magically answering questions.
How Do You Use a Telegram Bot?
Using a bot is just like chatting with a friend. Many bots use buttons or menus to make things easy, just like Yatter. You don’t even need to type anything.
Are Telegram Bots Safe?
Telegram bots can be safe, but it depends on the creator. Telegram itself offers strong privacy features, and bots cannot read your private messages unless you talk to them directly. However, just like with any online service, it’s good to be cautious. Don’t share private or sensitive information with a bot unless you trust who made it.
Here are a few tips to stay safe:
Only use popular or well-reviewed bots.
Don’t give out personal info like passwords or financial details.
Check the bot's profile and description to understand what it does.
Conclusion
Telegram bots will become more human-like, proactive and emotionally intelligent with time. The Bots that are yet behind Yatter are at the head of the revolution, making real-time communication, voice-enabled interaction, fast responses and adaptive features that learn over time available to users.
With Yatter, you’re not just using a bot; you’re experiencing the most advanced AI assistant on Telegram and WhatsApp. From smart conversations to real-time voice chat and instant information, Yatter is built to make your life easier, faster and smarter.So next time you're using Telegram, try exploring a bot or two. You might discover a whole new world within your chats.
0 notes
Text
What is a QR Code Loyalty Program and How Does It Work

(written in simple and easy words)
A QR code loyalty program is a smart and easy way for businesses to reward their customers. Instead of using plastic cards or paper coupons, customers scan a QR code using their smartphones. This small action helps them earn points, get discounts, or unlock special offers.
What is a QR Code Loyalty Program
A QR code loyalty program is a digital system that helps customers collect rewards by scanning QR codes. These codes are often printed on receipts, posters, product packaging, or shown on a screen. Each scan gives the customer points or benefits, which they can later use.
For example: You buy a coffee from your favorite café. You see a QR code on your receipt. You scan it with your phone and get 10 points. After collecting 100 points, you get a free coffee. Simple!
How Does a QR Code Loyalty Program Work?
Here’s how it usually works in five easy steps:
Customer Makes a Purchase The customer buys a product or service.
QR Code is Scanned A QR code is displayed on a receipt, product, or at the counter. The customer scans it using their phone.
Points are Collected After scanning, points or rewards are added to the customer’s digital account. Some businesses use apps, while others link it to a phone number or email.
Progress is Tracked Customers can check their rewards and progress in the app or through SMS/email updates.
Rewards are Redeemed Once enough points are collected, the customer can use them to get discounts, free items, or special offers.
Why Do Businesses Use QR Code Loyalty Programs?
Simple to Use Customers don’t need to carry extra cards. They just scan and go.
Fast Setup for Businesses No need to print loyalty cards or install complex systems. Just generate a QR code.
Cost-Effective It reduces printing and admin costs.
Better Customer Engagement It encourages repeat visits and builds a strong bond between the customer and the brand.
Benefits for Customers
Easy to collect and track points
Instant rewards and offers
No need to remember passwords or carry loyalty cards
Fun and interactive experience
How to Set Up a QR Code Loyalty Program
If you are a business owner thinking about starting a QR code loyalty program, here’s what you need to do:
Choose a Loyalty Program Platform Pick a platform or app that helps create and manage QR code rewards. Many easy-to-use options are available online.
Design Your Rewards System Decide how customers will earn points. For example:
1 point for every $1 spent
50 points for a first-time sign-up
100 points for referring a friend
Create and Display Your QR Codes Generate a unique QR code. You can print it on receipts, menus, product packaging, or simply display it at the cash counter.
Promote Your Loyalty Program Let your customers know about the program. Use posters, social media, and word of mouth. The more people know, the more they will join.
Track and Improve Keep an eye on how the program is working. Are customers using it? Are they happy? If needed, tweak the rewards or make it even more fun!
Tips to Make Your QR Code Loyalty Program Successful
Make it Easy to Join No complicated sign-ups. Keep it quick and simple.
Offer Exciting Rewards Rewards should be useful and tempting. Discounts, freebies, and exclusive deals work best.
Keep Customers Updated Send updates on points earned, new rewards, or special promotions.
Thank Your Customers A simple thank you goes a long way in building loyalty.
Real-Life Example
Imagine you run a small bakery. You create a QR code loyalty program where customers earn 5 points every time they buy a cupcake. After collecting 50 points, they get a free cupcake of their choice. Customers love the idea because it’s easy, fun, and they get rewarded for something they already enjoy! Your sales go up, and customers feel valued. A win-win!
Final Thoughts
A QR code loyalty program is a modern, easy-to-use, and effective way for businesses to keep customers happy and coming back. For customers, it’s a simple way to earn rewards for their everyday purchases. With just a quick scan, both sides benefit.
#loyaltyprogram#customerloyalty#QRcode#rewardsystem#businessgrowth#loyaltyrewards#digitalmarketing#QRcodeloyalty#marketingstrategy
0 notes
Text
Building a Culture of Safety and Protection in Everyday Life
In today’s fast-paced world, where distractions are endless and risks come in many forms, the concept of safety and protection goes beyond hard hats and passwords. It's about developing a mindset—one that values caution, preparation, and mindfulness in all aspects of life.
Safety and Protection Starts with Awareness
The first step in fostering a culture of safety and protection is awareness. We often associate safety with rare emergencies, but it’s the small, daily choices that have the biggest impact.
Are we locking our doors at night? Are we teaching children how to cross the street safely? Are we looking both ways before making a decision—figuratively and literally?
Being aware of our surroundings, understanding potential hazards, and taking proactive steps toward safety can prevent accidents before they happen.
Home: Your First Line of Defense
Your home should be a sanctuary, and ensuring its safety doesn’t require fancy gadgets. Simple things like checking smoke alarms, securing windows, and having a basic first aid kit can go a long way.
Childproofing, clear emergency plans, and even something as routine as not leaving candles unattended are all small habits that reinforce the idea that safety and protection begins at home.
Technology: A Friend and a Risk
We live in a connected age, and with that comes digital responsibility. The convenience of online shopping, smart devices, and cloud storage is incredible—but it's also a double-edged sword.
Implementing strong passwords, avoiding unsecured Wi-Fi networks, and educating your family about phishing scams are just as important as locking your front door. Digital safety is now an everyday requirement, not just something for IT professionals.
The Role of Community in Safety
Individual actions are powerful, but safety grows stronger when it's shared. Neighborhood watch programs, school safety drills, workplace safety committees—these are all examples of collective action that reinforce protection at a larger scale.
A community that watches out for one another thrives. When you help a neighbor fix a broken step or report suspicious activity in your area, you're contributing to a ripple effect of safety and protection.
Teaching the Next Generation
Perhaps the most valuable investment we can make is passing down the importance of safety and protection to future generations. Teaching children to be cautious, to speak up when something feels wrong, and to understand both physical and emotional safety gives them tools that last a lifetime.
Empowerment is protection. When young people know how to protect themselves and others, they grow into confident, responsible adults.
Conclusion
Safety and protection aren’t one-time actions—they’re habits, cultures, and commitments. From our homes to our devices, from solo choices to community efforts, building a safer world starts with small, consistent efforts.
Let’s create a future where protection isn’t reactive—it’s instinctive.
0 notes
Text
6 Ways to Make Authentication Systems More User-friendly

In today's digital landscape, strong authentication is paramount for security. However, complex and cumbersome login processes can lead to user frustration, abandoned accounts, and ultimately, a negative user experience. Striking the right balance between robust security and user convenience is crucial. Luckily, there are several ways to enhance authentication systems without compromising safety. Let's explore six key strategies to make logging in a smoother, more user-friendly experience.
1. Embrace Social Login: The Power of Familiarity
Let's face it, most users already have accounts with major platforms like Google, Facebook, Apple, or Twitter. Implementing social login allows users to authenticate using these existing credentials, eliminating the need to create and remember yet another unique username and password.
Benefits: Reduces friction, speeds up the registration and login process, leverages users' existing trust in established platforms, and can improve conversion rates.
Implementation: Offer multiple social login options to cater to a wider user base. Clearly indicate the data being shared with your platform during the authorization process.
2. Passwordless Authentication: Beyond the Traditional String
The password, while a cornerstone of security, is also a major source of user pain. Passwordless authentication methods offer secure alternatives that are often more convenient.
Magic Links: A unique, time-sensitive link is sent to the user's email address or phone number. Clicking the link logs them in directly.
One-Time Passwords (OTPs): Generated via SMS, authenticator apps, or email, OTPs provide a secure, temporary login credential without the need to remember a complex password.
Biometric Authentication: Leveraging fingerprint scanning, facial recognition, or voice recognition offers a secure and highly user-friendly way to authenticate, especially on mobile devices.
Security Keys: Physical USB or Bluetooth keys provide a strong form of two-factor authentication that is resistant to phishing attacks but can be less convenient for some users.
3. Streamline the Registration Process: Keep it Lean
A lengthy and demanding registration form can be a significant barrier to entry. Minimize the required information to the absolute essentials.
Ask for Only What's Necessary: Collect only the data you truly need upfront. Additional information can be gathered later as the user interacts with your platform.
Offer Progressive Profiling: Gradually collect user details over time, rather than bombarding them with a long form during registration.
Provide Clear Instructions and Feedback: Ensure the registration process is intuitive with clear labels, helpful tooltips, and immediate feedback on input errors.
4. Intelligent Password Management Assistance: Empowering Users
While moving beyond passwords is ideal, they remain a reality for many systems. Make password management less painful.
Strong Password Generators: Offer a built-in tool to suggest strong and unique passwords, encouraging better security habits.
Password Strength Indicators: Provide visual feedback on password complexity as the user types, guiding them towards stronger options.
"Show Password" Option: Allow users to temporarily reveal their password during entry to reduce typos and frustration.
Clear Password Reset Mechanisms: Make the password reset process straightforward and secure, with clear instructions and multiple recovery options (e.g., email, security questions).
5. Context-Aware Authentication: Smart Security
Authentication doesn't always need to be a rigid, one-size-fits-all process. Context-aware authentication adapts the level of security based on the user's behavior, location, device, and the sensitivity of the action they are trying to perform.
Risk-Based Authentication: Trigger stronger authentication methods (like 2FA) only when suspicious activity is detected or when accessing sensitive data.
Location-Based Authentication: Allow seamless login from trusted locations but require additional verification from unfamiliar networks.
Device Recognition: Remember trusted devices to avoid repeatedly prompting for authentication.
6. Consistent and Intuitive User Interface:
A well-designed and consistent authentication interface across all platforms (web, mobile app) can significantly improve user experience.
Clear Visual Hierarchy: Make login fields and buttons easily identifiable.
Mobile-First Design: Ensure the authentication process is seamless and responsive on mobile devices.
Consistent Branding: Maintain a consistent look and feel with your overall brand to build trust and familiarity.
Minimize Distractions: Keep the login/registration page clean and focused on the task at hand.
Finding the Right Balance:
Implementing user-friendly authentication doesn't mean sacrificing security. The key is to adopt a layered approach, combining strong security measures with intuitive design and user-centric features. By focusing on convenience and reducing friction, you can create authentication systems that are both secure and a pleasure to use, ultimately leading to happier and more engaged users.
0 notes
Text
Beyond Firewalls and Passwords — A Cyber Security Firm That Builds Digital Fortresses
In an era dominated by digital transformation, cybersecurity is no longer a one-time setup — it's a continuously evolving commitment. Threats are smarter, faster, and more sophisticated than ever before. To truly stay protected, businesses need more than antivirus software and password policies — they need digital fortresses. That’s where eShield IT Services, a next-generation cyber security firm, comes in.
The Limits of Traditional Cybersecurity
Firewalls, strong passwords, and basic antivirus software were once enough. Today, they serve as your front door lock in a world where attackers are already inside the house, hiding in the shadows.
Cybercriminals now use:
Social engineering to bypass human defenses
Zero-day exploits to attack undiscovered system flaws
AI and automation to scale their operations
Ransomware to encrypt entire infrastructures in minutes
In short, the battlefield has changed. And only a truly adaptive, fortified approach can keep your systems safe.
What Sets a Digital Fortress Apart
A digital fortress isn’t a single tool — it’s a holistic, layered defense strategy that evolves in real time. At eShield IT Services, we design environments where no threat can easily breach, pivot, or persist.
Key Components of Our Digital Fortress Approach:
Zero Trust Architecture: Every request is verified — no assumptions, no blind trust.
AI-Powered Threat Detection: Smart systems that learn and adapt to suspicious behavior.
Micro-Segmentation: Isolating workloads to limit lateral movement within networks.
Encryption by Default: Data is protected whether it's in motion or at rest.
Proactive Incident Response: Ready to contain and mitigate threats before damage spreads.
Why Choose eShield IT Services as Your Cyber Security Firm
When businesses partner with eShield IT Services, they gain more than just protection — they gain peace of mind. As a forward-thinking cyber security firm, we focus on creating sustainable, scalable solutions that outpace threats instead of reacting to them.
Our Advantages Include:
24/7 Security Operations Center (SOC) with live monitoring
Certified Experts in ethical hacking, compliance, and digital forensics
Industry-specific strategies for healthcare, finance, legal, and more
Scalable cloud security and hybrid infrastructure protection
Employee training programs to prevent human error-based breaches
Case in Point: Turning Vulnerabilities into Strength
A financial services firm approached us after a competitor suffered a data breach. Within weeks, we conducted a full security audit, identified high-risk exposures in third-party software, and rolled out a multi-layer defense system — complete with employee phishing simulations. The result? A 92% decrease in risk exposure and a fully compliant, breach-resistant ecosystem.
Our Cyber Security Services at a Glance
Here’s a snapshot of what we offer at eShield IT Services:
Threat Intelligence & Monitoring
Penetration Testing & Vulnerability Scanning
Security Awareness Training
Cloud Security & DevSecOps
Compliance & Risk Management
Business Continuity & Disaster Recovery Planning
Each service is tailored to your business's unique risk profile, ensuring you get real results — not just reports.
Why DIY Security Fails — And Firms Like Ours Succeed
Many organizations attempt to manage cybersecurity in-house, often underestimating the complexity of modern threats. This approach results in:
Unpatched systems
Poor visibility across networks
Delayed breach detection
Limited incident response capability
eShield IT Services solves these gaps with a team of specialists, real-time monitoring tools, and a deep understanding of attacker behavior — all working together to secure your digital world.
It’s Time to Build a Fortress, Not Just a Fence
If your business is still relying on outdated tools and reactive fixes, it’s time to evolve. Don’t wait for a breach to take cybersecurity seriously. eShield IT Services is the cyber security firm trusted by companies that refuse to compromise on protection.
Visit www.eshielditservices.com to learn how we can help you build a digital fortress that hackers can’t penetrate.
0 notes
Text
Future-Ready Cybersecurity: Automating Protection, Ensuring DSGVO Compliance, and Strengthening IT Audit Solutions
In today’s rapidly evolving digital landscape, businesses must stay ahead of increasingly sophisticated cyber threats while navigating stringent data protection regulations. From small enterprises to multinational corporations, cybersecurity has become a core business function—not just an IT task. That’s where risikomonitor gmbh steps in, offering smart, scalable, and compliant solutions through cybersecurity automation, DSGVO compliance, IT audit solutions, and cutting-edge IT-Sicherheit tools.
With a strong commitment to digital resilience and regulatory integrity, risikomonitor gmbh empowers businesses to secure their infrastructure and remain compliant in a constantly changing threat environment.
The Power of Cybersecurity Automation
Cyber threats don’t wait—and neither should your defenses. Traditional, manual approaches to cybersecurity are no longer sufficient to handle the volume and complexity of attacks. Cybersecurity automation offers a faster, smarter, and more efficient way to detect, respond to, and neutralize threats.
Key Benefits of Cybersecurity Automation:
Real-time threat detection: Automated systems scan networks 24/7, immediately identifying suspicious activity.
Faster incident response: Response playbooks can be triggered automatically to contain threats before they spread.
Reduced human error: Automation reduces the risk of misconfigurations or missed alerts.
Cost efficiency: Less reliance on manual labor and more on intelligent systems means lower operational costs.
Scalability: Automation adapts easily to growing infrastructures, from SMBs to large enterprises.
At risikomonitor gmbh, we implement cybersecurity automation using advanced threat intelligence platforms, SIEM systems, and behavior-based detection tools that allow businesses to stay protected—without overwhelming internal IT teams.
Ensuring DSGVO Compliance
The DSGVO (Datenschutz-Grundverordnung), or General Data Protection Regulation, is the backbone of data privacy in the EU. Non-compliance not only risks hefty fines but also damages brand trust and customer loyalty. For German and EU-based companies, achieving DSGVO compliance is a legal necessity and a business advantage.
How risikomonitor gmbh Helps with DSGVO Compliance:
Data mapping: We identify and document how personal data is collected, stored, and processed across systems.
Privacy impact assessments (PIAs): We evaluate potential risks to personal data and recommend safeguards.
Policy development: We assist in creating data protection policies, consent forms, and breach notification protocols.
Technical measures: Encryption, access controls, and pseudonymization tools are implemented to secure data.
Audit readiness: Our compliance reports and documentation prepare your company for regulator inspections.
By integrating cybersecurity and data protection, risikomonitor gmbh ensures that your organization is both secure and compliant—without compromising on agility or performance.
IT Audit Solutions for Total Visibility
An IT audit is a critical process that evaluates the effectiveness of your information systems, security protocols, and compliance posture. Whether driven by internal needs or external regulations, audits provide visibility, reduce risk, and uncover inefficiencies.
risikomonitor gmbh offers comprehensive IT audit solutions that help organizations gain a holistic view of their IT environment.
Our IT Audit Services Include:
Network & system assessments: Evaluate system integrity, patch management, and firewall configurations.
Access and identity audits: Analyze user permissions, password policies, and multi-factor authentication.
Data flow and storage review: Map sensitive data paths to ensure security and compliance.
Third-party risk analysis: Review risks associated with vendors, partners, and cloud services.
Compliance gap analysis: Compare your current posture against DSGVO, ISO 27001, BSI, and other frameworks.
Audit findings are presented in clear, actionable reports that enable decision-makers to prioritize and act. With our support, clients reduce IT risks, improve controls, and gain confidence in their digital infrastructure.
Smart IT-Sicherheit Tools for Modern Threats
Technology is only as effective as the tools used to implement it. At risikomonitor gmbh, we curate and deploy the most reliable IT-Sicherheit tools—carefully selected for performance, compatibility, and ease of use.
Our Suite of IT-Sicherheit Tools Covers:
Endpoint detection and response (EDR): Real-time monitoring of workstations and devices.
SIEM systems: Centralized logging and event correlation to detect complex attack patterns.
Vulnerability scanners: Automated scans to find misconfigurations, outdated software, and exploitable weaknesses.
Web and email security: Protection against phishing, spam, and malicious web activity.
Encryption and secure file transfer tools: Ensure that sensitive data is always protected in transit and at rest.
These tools are integrated into a cohesive framework, supported by expert oversight and continuous updates. Whether on-premise, cloud-based, or hybrid, our IT-Sicherheit tools ensure a secure digital environment.
Why Choose risikomonitor gmbh?
Cybersecurity is complex—but working with the right partner makes all the difference. risikomonitor gmbh delivers a unique blend of automation, compliance, auditing, and strategic insight to help organizations confidently face digital challenges.
Our Key Differentiators:
German and EU regulation expertise
Custom-tailored solutions for SMBs and enterprises
Proactive cybersecurity automation strategies
Certified IT auditors and data protection officers
Local support, global standards
Our mission is to reduce your cyber risks, streamline your compliance efforts, and protect your business integrity in an increasingly digital-first world.
The Road Ahead: Securing Your Digital Future
Cyber threats won’t slow down—and neither should your cybersecurity strategy. Whether you’re just starting to explore automation, need help with a DSGVO compliance audit, or want to overhaul your existing IT security framework, risikomonitor gmbh has the tools, talent, and experience to guide your journey.
We believe in creating long-term value through transparency, innovation, and expert consultation.
0 notes
Text

Global OTP – The Smart Way to Secure Your Digital Life in 2025
In an age where cyber threats are everywhere, securing your online accounts has become more important than ever. That’s why Global OTP is making waves in 2025 as one of the smartest and most reliable mobile tools for two-factor authentication. Designed for Android, it’s the latest version of a lightweight and free app that helps you protect what matters most.
What is Global OTP?
Global OTP is a mobile app that generates time-based one-time passwords (OTPs) to keep your accounts safe. Whether you're logging into email, social media, or financial services, this tool adds an extra layer of protection without the need for SMS codes or internet access. It’s fast, private, and works completely offline.
Clean Design and Smooth Experience
What sets Global OTP apart is its simple, modern design. The interface is easy to use, with a clutter-free layout and smooth performance on most Android devices. It supports both light and dark themes, offering comfort for all-day use.
Key Features
Instant OTP generation without internet
Secure QR code scanner for quick setup
Supports multiple accounts
Strong encryption for local data storage
Backup and restore functionality
Works on both phones and tablets
Final Thoughts
If you want to take control of your digital security in 2025, Global OTP is the way to go. It’s free, fast, and designed with your privacy in mind. Download it on your Android device and enjoy peace of mind every time you log in.
0 notes
Text
Secure and Smart, Cosmo Gen Z Safeguarding Your Banking

Gen Z is all about convenience, speed, and security—particularly in how they manage money. In today's age where everything is done in a swipe or a tap, and banking shouldn't be an exception. That's why Cosmos Bank developed Cosmo Gen Z, a next-generation banking app specifically for you. It's not another banking app; it's your smart, secure, and convenient financial buddy.
Banking That's Safe and Sound
With cyber threats hanging around, your hard-earned cash deserves to be safe. That's why Cosmo Gen Z is loaded with strong security features that allow you to bank confidently:
Multi-Factor Authentication (MFA): Say goodbye to unauthorized access. With MFA, you can access your account, there are several verification steps involved, so only you can log into the application.
AI-Powered Fraud Detection: Cosmos's Gen Z app keeps an eye on your transactions 24/7, flagging anything suspicious before there are any fraudulent transactions occur.
End-to-End Encryption: Each transaction and message is secured with encryption, ensuring all your personal information stays private & data is safe.
Biometric Login: You do not have to remember passwords anymore! You can use your fingerprint or face recognition for quick, secure access in your Cosmos Gen Z app.
A Smarter Way of Banking
Security of the application is top-notch, but online banking has to be easy and enjoyable too. Cosmo Gen Z isn't only secure; it's designed to make your life easier with features tailored to how you live:
Instant Money Transfers: If you want to send money to a friend or split a bill? You can do it in seconds with a few taps.
Smart Expense Tracking: The app automatically classifies your spending, so you'll always know where your money is spent.
Virtual Debit Card: Shop online without worries using a digital card that's always ready, even when you leave your wallet behind.
24/7 Chatbot Support: Got a question? Our AI chatbot can always be there to assist you, day or night, anywhere.
Savings Simplified: You can save for your next vacation or a new device by creating a savings goal and monitor your progress easily.
Your Security is Our Top Priority
Cosmos Bank continuously enhances security features to remain one step ahead of threats. And, Cosmo Gen Z gives you instant notifications if something suspicious occurs with your account, so you can act right away.
Ready to Try Next-Level Banking?
If you’re looking for a banking app that gets you secure, smart, and super easy to use then Cosmo Gen Z is the perfect fit. Download it today and take control of your finances like never before.
Stay safe. Stay smart. Bank with Cosmo Gen Z.
0 notes
Text
The Importance of Secure Passwords and How to Generate Them Easily
In today’s digital world, protecting your online accounts is more critical than ever. With cyber threats on the rise, having a strong password is the first line of defense against hackers. However, many people struggle to create passwords that are both strong and easy to remember. That’s where a password generator easy to remember can make a huge difference.
Why You Need a Strong Password
A weak password can expose you to identity theft, data breaches, and unauthorized access to your accounts. Cybercriminals use sophisticated tools to crack passwords, especially simple ones like "123456" or "password." To stay ahead, you need to create complex passwords that are difficult to guess. However, remembering a long string of random characters can be challenging. This is where an easy password generator becomes an essential tool.
The Role of a Password Generator
A password generator online helps users create unique and secure passwords instantly. Instead of coming up with passwords yourself, these tools generate random passwords based on set criteria such as length, character type, and complexity level.
One of the best solutions available today is easypasswordcreator, which offers a password generator easy to remember while ensuring security. This means you get strong passwords that won’t be easily cracked, but at the same time, they are structured in a way that makes them easier to recall.
Benefits of Using an Easy Password Generator
Enhanced Security – A password generator online produces strong and unique passwords that are nearly impossible for hackers to guess.
Time-Saving – Instead of spending time brainstorming a secure password, you can generate one in seconds.
Memorable Yet Secure – Using a password generator easy to remember helps you get passwords that are secure yet simple enough to recall without writing them down.
Customizable Options – With platforms like easypasswordcreator, you can adjust password length, add special characters, and choose easy-to-remember formats.
How to Create Strong and Memorable Passwords
With the right easy password generator, you can follow these tips to ensure your password remains both secure and easy to recall:
Use a combination of words and numbers – Instead of a single word, try using a phrase combined with numbers.
Incorporate special characters – Adding symbols like @, #, or ! increases security.
Use acronyms or mnemonics – For example, "I love pizza on Fridays at 7 PM!" can become "ILpOF@7PM!".
Avoid common words – Stay away from predictable passwords like "password123" or "letmein".
Why Choose Easypasswordcreator?
When looking for a password generator online, you need a tool that is secure, efficient, and user-friendly. Easypasswordcreator is designed to help users create complex passwords that are still manageable. It stands out because:
It generates strong, hack-proof passwords instantly.
It offers customization options to create passwords based on your preferences.
It ensures that your generated passwords are easy to remember yet secure.
It is completely free and accessible online, making it a hassle-free option.
Conclusion
In an era where cybersecurity is a growing concern, using a password generator easy to remember is a smart way to safeguard your online presence. With tools like easypasswordcreator, you don’t have to choose between security and convenience—you can have both. Whether you need a password generator online for personal or professional use, ensuring your passwords are strong and memorable has never been easier.
Start using an easy password generator today and take control of your digital security
0 notes
Text
What is WordPress? All You Need to Know
WordPress is the top content management system. It powers more than 40% of all websites online. WordPress offers options for everyone. Beginners can build their first website. Experts can improve their current site, this guide will walk you through everything you need to know about WordPress. We help you with WordPress. This includes picking the best hosting. It also means adding key plugins. We take care of what you need.
WordPress
Before you start a website, know what WordPress is. WordPress is a strong, open-source CMS. It lets people make and control websites easily. You can change your site with many themes. WordPress plugins are also available to meet different needs.

Choosing a Domain and Hosting
To create a WordPress website, you need a domain name and web hosting. Think of a domain name as your website's unique online address. Web hosting is a service. It stores all your website's data. Some popular hosting providers include:
Bluehost
SiteGround
WP Engine
Choose a host that works well with WordPress for the best results.
Installing WordPress
With your domain and hosting set, installing WordPress is next. Many hosting companies provide a quick WordPress install. This makes the process simple.
Follow these steps:
Log into your hosting account.
Locate the WordPress installer.
Click "Install WordPress" and follow the instructions.
Set up your site title, username, and password.
Now that you have installed WordPress, it's time to explore the dashboard and settings.

Understanding the WordPress Dashboard
The WordPress dashboard lets you control your website. It's the place to handle content and settings.
Here, you can:
Create and edit posts and pages
Customize themes and layouts
Install and configure WordPress plugins
Manage users and permissions
Everything you need to know about WordPress starts with understanding the dashboard. Spend some time exploring its features to get comfortable.

Choosing the Right Theme
Themes determine your website’s appearance and functionality. WordPress has many themes, both free and premium.
To choose a theme:
Go to "Appearance" > "Themes."
Click "Add New."
Browse or search for a theme that fits your needs.
Click "Install" and then "Activate."
Customizing theme helps your WordPress site match your brand. Tailor your website's design to fit your company's image. This creates a unique online presence. A personalized theme strengthens brand recognition.
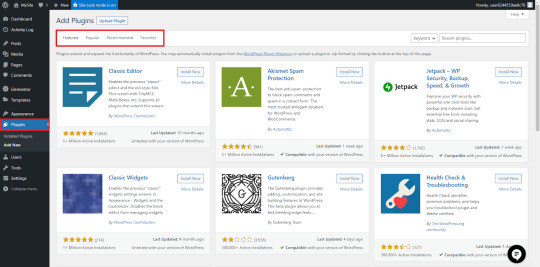
Essential WordPress Plugins
WordPress plugins enhance your site’s functionality.
Here are some must-have WordPress plugin
Yoast SEO - content Optimizes for search engines.
Elementor - A drag-and-drop page builder.
WP Super Cache - Improves website speed.
WooCommerce - It's simple to turn your site into a store.
Wordfence Security - Protects your website from threats.
Everything you need to know about WordPress includes using the right plugins. Avoid installing too many, as they can slow down your site.
Creating and Managing Content
WordPress allows you to create different types of content, including blog posts and static pages.
To add new content:
Go to "Posts" > "Add New" for blog articles.
Go to "Posts" > "Add New" for blog articles.
Use the WordPress editor to format text, add images, and embed videos.
Regularly updating your website with high-quality content is key to success.

Optimizing for SEO
SEO boosts your website's Google ranking. Higher rankings mean more people find you. This is done through smart website changes. These changes help Google understand your site better. Good SEO can greatly increase site traffic.
Follow these SEO tips:
Use keyword-rich titles and meta descriptions.
Optimize images for faster loading times.
Install SEO-friendly WordPress plugins like Yoast SEO.
Generate XML sitemaps for better indexing.
If you want to create a WordPress website that attracts visitors, SEO should be a top priority.
Enhancing Security and Performance
Website security is essential to avoiding data loss and hacking. Protect your WordPress website by:
Using strong passwords.
Installing security WordPress plugins like Wordfence.
Regularly updating WordPress, themes, and plugins.
Enabling SSL for a secure connection.
Optimizing performance is also essential. To increase loading speed, use a content delivery network (CDN) and caching WordPress plugins.

Monetizing Your WordPress Website
Once your site is up and running, you can monetize it in several ways:
Affiliate Marketing: Promote products and earn commissions.
Ads: Use Google AdSense or other ad networks.
E-commerce: Sell products with WooCommerce.
Memberships: Offer exclusive content for paying subscribers.
Monetization strategies depend on your website’s niche and audience.
Scaling and Maintaining Your Website
As your website grows, regular maintenance is essential.
Follow these best practices:
Backup your site regularly.
Keep WordPress, themes, and plugins updated.
Monitor site performance and fix broken links.
Engage with your audience through comments and emails.
Everything you need to know about WordPress includes learning how to maintain and scale your website effectively.
Mastering WordPress: From Beginner to Pro

WordPress is a popular system for making websites. It runs over 40% of all sites on the internet. People use it for blogs and online stores. WordPress is easy to use, even without tech skills. Learning WordPress takes time and effort. If you're new or want to improve your site, have a plan and keep learning.
First, learn the basics before using themes or add-ons. The dashboard helps manage your site. You can handle posts, pages, and themes there. Themes change how your site looks. Good themes improve user experience and design. Add-ons, or plugins, add features like SEO or security. Widgets add small parts like search bars. Knowing these parts helps make a good website.
WordPress plugins boost its capabilities. You can add almost any function with them. For example, Yoast SEO raises your site's search ranking. WPForms simplifies building contact forms. Wordfence Security keeps your site safe from threats. WooCommerce is great for making online stores. Elementor's drag-and-drop lets you design pages easily. No coding is needed.
SEO helps people find your site on search engines. Without SEO, your site may not be seen. Start by finding the right words people search for. Google Keyword Planner helps with this. Use those words in your content, headings, and descriptions. Website speed matters for SEO. GTmetrix can help you check and improve your site's speed. Make sure your site works on phones since many people use them.
Security is very important for WordPress sites. Hackers often target WordPress because it's popular. Use strong passwords for your admin panel and database. Backups help you restore your site if hacked. UpdraftPlus makes backups easy. Limit login tries to stop attacks. SSL makes your site use HTTPS, which protects visitors.
Learning WordPress never stops. WordPress changes with new features and add-ons. Keep your site updated with the newest versions. Join WordPress groups and read blogs to learn new things. Try different themes and plugins to find the best ones for your needs.
1 note
·
View note
Text
What is a Telegram Bot and How Does It Work?

What is a Telegram Bot and How Does It Work?
In the world of messaging apps, Telegram has become a favorite for many people due to its speed, privacy features, and flexibility. But one of the most interesting parts of Telegram isn’t just chatting with your friends - it’s bots. If you’ve ever seen a Telegram account that sends messages automatically, answers questions, or even plays games with you, you’ve probably interacted with a bot. But what exactly is a Telegram bot, and how does it work? Let’s break it down in a simple, non-technical way.
What is a Telegram Bot?
Have you ever heard of a Telegram bot yet? This kind of software application taps into Telegram’s infrastructure, which can interact with people like a human. However, you’re doing it with a chat app. Interestingly, you can converse with it, have it do something and receive responses quickly. When you have a Telegram bot, it can do many things, such as sending messages, arranging weather reports, translating languages, setting up any task and as if all this were not enough, hold conversations like a human.
What Can a Telegram Bot Do?
Telegram bots can be incredibly versatile. Some common uses include:
Providing information: Weather bots, news bots, and even dictionary bots can give you quick updates or answers.
Entertainment: You can play trivia games, read jokes, or even explore choose-your-own-adventure stories.
Reminders and to-do lists: Some bots help you stay organized by sending reminders or managing your daily tasks.
Translation: Certain bots can translate text from one language to another right inside the chat.
Learning and study: Some bots quiz you on vocabulary, math, general knowledge, and more.
Bots can be as simple as sending a daily quote or as advanced as holding a conversation using artificial intelligence.
How Does a Telegram Bot Work?
At the heart of every Telegram bot is a piece of software that uses Telegram’s Bot API. The person who creates the bot writes code that tells it what to do when it receives certain messages.
For example, a weather bot might be programmed like this:
Wait for a user to send a message like "weather in London".
Recognize the word “weather” and the location “London”.
Look up the current weather using a weather service.
Send the weather info back to the user in the chat.
This process all happens in just a few seconds, and from the user’s perspective, it looks like the bot is magically answering questions.
How Do You Use a Telegram Bot?
Using a bot is just like chatting with a friend. Many bots use buttons or menus to make things easy, just like Yatter. You don’t even need to type anything. Bots can be added to groups, too, where they can help moderate chats, play games, or answer group questions.
Are Telegram Bots Safe?
Telegram bots can be safe, but it depends on the creator. Telegram itself offers strong privacy features, and bots cannot read your private messages unless you talk to them directly. However, just like with any online service, it’s good to be cautious. Don’t share private or sensitive information with a bot unless you trust who made it.
Here are a few tips to stay safe:
Only use popular or well-reviewed bots.
Don’t give out personal info like passwords or financial details.
Check the bot's profile and description to understand what it does.
Conclusion
Telegram bots will become more human-like, proactive and emotionally intelligent with time. The Bots that are yet behind Yatter are at the head of the revolution, making real-time communication, voice-enabled interaction, fast responses and adaptive features that learn over time available to users.
With Yatter, you’re not just using a bot, you’re experiencing the most advanced AI assistant on Telegram and WhatsApp. From smart conversations to real-time voice chat and instant information, Yatter is built to make your life easier, faster and smarter.So next time you're using Telegram, try exploring a bot or two. You might discover a whole new world within your chats.
0 notes
Text
The Future of Cybersecurity: Trends to Watch in 2025

Cybersecurity is always changing as technology evolves and new threats appear. In 2025, several important trends will shape how we keep data, systems, and users safe. Here’s a look at the key cybersecurity trends to watch for in the near future.
1. AI and Machine Learning for Better Protection
Artificial Intelligence (AI) and Machine Learning (ML) will play a bigger role in detecting and preventing cyberattacks. These technologies can analyze huge amounts of data quickly, helping security teams spot threats faster. By 2025, AI will be even better at predicting and stopping attacks before they happen, making systems smarter and safer.

2. Zero Trust Security Model
The "Zero Trust" model means never trusting anyone or anything, even if they are inside the network. This approach checks and monitors every user and device constantly to make sure only the right people have access to sensitive data. By 2025, more organizations will adopt Zero Trust security to make their networks harder to breach.
3. Quantum Computing and New Encryption
Quantum computers, still in development, will be able to break traditional encryption methods, making it easier for hackers to steal data. By 2025, experts will be working hard to create new encryption techniques that can stand up to the power of quantum computers. This will be a major step in keeping our data safe as technology advances.
4. Securing IoT Devices
The number of Internet of Things (IoT) devices—like smart thermostats, wearables, and connected appliances—is growing fast. While they make life easier, they also open up new ways for hackers to attack. In 2025, there will be more focus on securing these devices, ensuring they are built with strong protections to prevent breaches.

5. Stronger Privacy Laws
With the increasing number of data breaches, governments are introducing stricter privacy laws. The General Data Protection Regulation (GDPR) in Europe is a great example, and more countries are expected to follow suit. By 2025, companies will have to comply with stronger rules about how they handle personal data, ensuring users' privacy is better protected.
6. Cybersecurity-as-a-Service (CSaaS)
Not every company has the resources to handle cybersecurity on its own. Cybersecurity-as-a-Service (CSaaS) allows businesses to outsource their security needs to experts. By 2025, this service will become more popular, making it easier for smaller companies to afford and implement top-notch cybersecurity protections without needing an in-house team.
7. Training People to Be Security-Aware
People are often the weakest link in cybersecurity because of things like falling for phishing scams or using weak passwords. In 2025, companies will focus more on educating their employees about security. This includes regular training to recognize threats, follow secure practices, and keep company data safe.
8. Cyber Resilience: Preparing for the Worst
Despite best efforts, cyberattacks will still happen. That’s why cyber resilience—being able to bounce back quickly from attacks—will be crucial.
1 note
·
View note
Text
Security in IoT Mobile Apps: Safeguarding Your Devices and Data

In today's connected world, IoT mobile app development has transformed how we interact with technology, from smart homes and wearables to connected vehicles and industrial systems. With billions of IoT devices constantly transmitting and receiving data, mobile apps have become a central hub for controlling and monitoring these devices. However, with the rise of the Internet of Things (IoT), security concerns have also surged. Protecting IoT devices and the sensitive data they handle is more critical than ever. This blog will explore the importance of security in IoT mobile app development and provide essential tips on safeguarding both your devices and the data they generate.
The Growing Importance of Security in IoT Mobile Apps
The IoT ecosystem is vast and growing at an unprecedented rate. According to industry forecasts, the number of connected devices worldwide is expected to reach over 75 billion by 2025. This growth presents both opportunities and challenges. While IoT has the potential to revolutionize industries like healthcare, manufacturing, and retail, it also opens the door for cyberattacks, data breaches, and other security risks.
Security in IoT mobile apps is particularly critical because these apps often serve as gateways between the physical world and the cloud, enabling users to control, monitor, and receive data from their IoT devices. A vulnerability in the app could provide hackers with unauthorized access to the devices, leading to serious consequences, such as data theft, device hijacking, and even physical damage.
Key Security Risks in IoT Mobile Apps
Weak Authentication Mechanisms
Authentication is the first line of defense in protecting IoT devices and mobile apps. If an app doesn’t require strong authentication measures, it becomes an easy target for hackers to gain unauthorized access. Simple password-based authentication methods are often insufficient, as they can be easily bypassed through brute force attacks or phishing schemes.
Insecure Communication Protocols
Many IoT apps rely on wireless communication protocols like Wi-Fi, Bluetooth, Zigbee, or even cellular networks. If these communication channels are not properly secured, hackers can intercept data being transmitted between the mobile app and the IoT device. Without encryption or proper security measures, sensitive data, such as personal health information or financial data, can be exposed to attackers.
Data Privacy Issues
IoT devices often collect vast amounts of personal data, from health metrics to location tracking and usage patterns. Insecure apps can expose this data to malicious actors, leading to privacy violations. Furthermore, if the app stores sensitive data in an unencrypted format, hackers could easily access it if they breach the system. Protecting this data with robust encryption and compliance with privacy regulations like GDPR is essential.
Device Vulnerabilities
Even if the IoT mobile app is secure, the IoT devices themselves might have security flaws. Many IoT devices are manufactured with limited computing power and are unable to support advanced security features. Additionally, a large number of IoT devices still run outdated or unpatched software, leaving them vulnerable to exploitation. If attackers gain access to these devices, they can potentially control or misuse them.
Lack of Regular Updates and Patches
IoT mobile apps and devices require continuous updates to address newly discovered vulnerabilities. However, many IoT apps are not regularly updated or patched, leaving them susceptible to emerging threats. Regular updates are critical to maintaining the security of both the app and the connected devices. Unfortunately, some manufacturers neglect this aspect, resulting in IoT devices with outdated software and security flaws.
Best Practices for Securing IoT Mobile Apps
Implement Strong Authentication and Authorization
To secure an IoT mobile app, it’s essential to implement strong authentication protocols, such as two-factor authentication (2FA), biometric authentication (fingerprint or face recognition), or hardware-based authentication (like smart cards or USB keys). Additionally, employ robust authorization controls to ensure that users can only access the devices and data they are authorized to interact with.
Use Encryption for Data Transmission and Storage
All communication between the IoT mobile app and the devices should be encrypted using industry-standard protocols, such as Transport Layer Security (TLS). This ensures that any data transmitted over the air is protected from eavesdropping. Moreover, any sensitive data stored locally on the device or in the cloud should also be encrypted to safeguard against unauthorized access.
Ensure Regular Updates and Patching
Regular software updates and patches are essential for keeping IoT mobile apps secure. Developers should incorporate automatic update features in their apps to ensure users receive timely updates. Additionally, device manufacturers should be committed to providing regular security patches for their hardware to prevent exploitation of known vulnerabilities.
Secure APIs and Cloud Infrastructure
The backend infrastructure and APIs that support IoT apps should be secured to prevent unauthorized access. This involves using secure API gateways, applying rate limiting to prevent denial-of-service (DoS) attacks, and using techniques like OAuth for secure authentication. Furthermore, cloud storage solutions used to store user data should be encrypted and managed according to best practices for cloud security.
Implement Device-Level Security
Beyond securing the mobile app, it’s crucial to secure the IoT devices themselves. Device manufacturers must implement secure boot mechanisms, secure firmware updates, and tamper detection features to protect devices from being hijacked or compromised. Additionally, IoT devices should be designed to allow easy firmware updates, ensuring they stay secure as new threats emerge.
Mobile App Cost Calculator
Security features, such as encryption, regular updates, and strong authentication mechanisms, can significantly increase the cost of IoT mobile app development. If you’re considering building an IoT app, it’s essential to factor in these costs when planning your budget. Fortunately, a mobile app cost calculator can provide a useful estimate of development costs based on factors like app complexity, required security features, and platform compatibility. By using this tool, you can gain better insight into the potential expenses and plan your project accordingly.
If you're unsure about the security needs of your IoT mobile app, our team of experts can help guide you through the process. Book an Appointment with one of our consultants to discuss the security requirements of your app and receive tailored advice.
Iot App Development Services
When developing an IoT mobile app, security should be a top priority. Ensuring that your devices and the data they generate are protected from potential threats is essential for building trust with your users and safeguarding your business. At the same time, your IoT app needs to be user-friendly, reliable, and scalable to handle the growth of connected devices.
At IoT App Development Services, we specialize in creating secure, innovative IoT mobile apps that meet the highest security standards. Our team of experienced developers ensures that your IoT app is not only functional but also resilient against security breaches. From implementing strong encryption to regular patching and updates, we provide comprehensive solutions to keep your devices and data safe. Contact us today to get started on building a secure IoT app that empowers your users and protects their privacy.
Conclusion
As the IoT ecosystem continues to grow, ensuring the security of IoT mobile apps becomes even more critical. Protecting your devices, user data, and overall infrastructure from cyber threats requires a multi-layered approach that includes strong authentication, secure data transmission, regular updates, and robust device-level security. By following best practices and investing in security from the start, you can create an IoT mobile app that users trust and rely on. If you're looking for expert assistance in developing a secure IoT mobile app, our IoT App Development Services can help bring your vision to life while safeguarding your users and devices.
0 notes