#Subdomain Scanner
Explore tagged Tumblr posts
Text







high res gunter images as promised! right-click save as for highest res.
some notes:
technically i could do better given an office scanner but i'm not quite that brain rotted for diminishing returns ~ i tried cleaning up the artwork that wasn't already available on FEWiki as of writing.
the artbook colors skews a little pink/red in general. I say this as i sat there arguing with myself for 20 minutes (twice) about the exact shade of his skin (which skews more yellow in the crit illusts and ime is a little over-exposed in the my room portrait on FEWiki) and cross referencing that and the hair/armor with the official sprites before realizing there are better things to do :P
I don't require credit for these scans/edits, but if you'd like, put it as (kradeelav.com). if i make a gunter fanshrine subdomain, these will go up there permanently.
the cover "rough" sketch was already really pixelated in the book; i'm sorry I couldn't do better but that shot is literally the size of my fingernail, as well as the headshots. maybe kozaki will release a bigger version someday. :D
#gunter fire emblem#god bless the power of brain rot#his happy lineart .... c-c-cute....... his eye creases kill me.....#so many of his shapes make SENSE now aaaa i can draw him on model finally!!!!!!!!!!!!!!!
27 notes
·
View notes
Text
👩🏻💻 𝙰𝚛𝚌𝚑𝚒𝚟𝚒𝚘 𝚍𝚒 𝚜𝚝𝚛𝚞𝚖𝚎𝚗𝚝𝚒 𝚙𝚎𝚛 𝚌𝚢𝚋𝚎𝚛𝚜𝚎𝚌𝚞𝚛𝚒𝚝𝚢 𝚌𝚑𝚎 𝚖𝚒 𝚟𝚎𝚗𝚐𝚘𝚗𝚘 𝚌𝚘𝚗𝚜𝚒𝚐𝚕𝚒𝚊𝚝𝚒 𝚘 𝚌𝚒𝚝𝚊𝚝𝚒 𝚗𝚎𝚕 𝚝𝚎𝚖𝚙𝚘
AnyRun: cloud-based malware analysis service (sandbox).
Burp Suite: a proprietary software tool for security assessment and penetration testing of web applications. La community edition, gratis, contiene Burp Proxy and Interceptor (intercetta le richieste effettuate dal browser, consente modifiche on-the-fly e di modificare le risposte; utile per testare applicazioni basate su javascript), Burp Site Map, Burp Logger and HTTP History, Burp Repeater (consente di replicare e modificare le richieste effettuate, aggiungere parametri, rimuoverli, ecc), Burp Decoder, Burp Sequencer, Burp Comparer, Burp Extender (estensioni delle funzionalità di burpsuite, plugin specializzati per individuare bug specifici, automatizzare parte delle attività, ecc) e Burp Intruder (consente di iterare richieste con payload differenti e automatizzare attività di injection).
CyberChef: is a simple, intuitive web app for carrying out all manner of "cyber" operations within a web browser. These operations include simple encoding like XOR and Base64, more complex encryption like AES, DES and Blowfish, creating binary and hexdumps, compression and decompression of data, calculating hashes and checksums, IPv6 and X.509 parsing, changing character encodings, and much more.
DorkSearch: an AI-powered Google Dorking tool that helps create effective search queries to uncover sensitive information on the internet.
FFUF: fast web fuzzer written in Go.
GrayHatWarfare: is a search engine that indexes publicly accessible Amazon S3 buckets. It helps users identify exposed cloud storage and potential security risks.
JoeSandbox: detects and analyzes potential malicious files and URLs on Windows, Mac OS, and Linux for suspicious activities. It performs deep malware analysis and generates comprehensive and detailed analysis reports.
Nikto: is a free software command-line vulnerability scanner that scans web servers for dangerous files or CGIs, outdated server software and other problems.
Nuclei: is a fast, customizable vulnerability scanner powered by the global security community and built on a simple YAML-based DSL, enabling collaboration to tackle trending vulnerabilities on the internet. It helps you find vulnerabilities in your applications, APIs, networks, DNS, and cloud configurations.
Owasp Zap: Zed Attack Proxy (ZAP) by Checkmarx is a free, open-source penetration testing tool. ZAP is designed specifically for testing web applications and is both flexible and extensible. At its core, ZAP is what is known as a “manipulator-in-the-middle proxy.” It stands between the tester’s browser and the web application so that it can intercept and inspect messages sent between browser and web application, modify the contents if needed, and then forward those packets on to the destination. It can be used as a stand-alone application, and as a daemon process.
PIA: aims to help data controllers build and demonstrate compliance to the GDPR. It facilitates carrying out a data protection impact assessment.
SecLists: is the security tester's companion. It's a collection of multiple types of lists used during security assessments, collected in one place. List types include usernames, passwords, URLs, sensitive data patterns, fuzzing payloads, web shells, and many more.
SQLMAP: is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Subfinder: fast passive subdomain enumeration tool.
Triage: cloud-based sandbox analysis service to help cybersecurity professionals to analyse malicious files and prioritise incident alerts and accelerate alert triage. It allows for dynamic analysis of files (Windows, Linux, Mac, Android) in a secure environment, offering detailed reports on malware behavior, including malicious scoring. This service integrates with various cybersecurity tools and platforms, making it a valuable tool for incident response and threat hunting.
VirusTotal: analyse suspicious files, domains, IPs and URLs to detect malware and other breaches, automatically share them with the security community.
Wayback Machine: is a digital archive of the World Wide Web founded by Internet Archive. The service allows users to go "back in time" to see how websites looked in the past.
Wapiti: allows you to audit the security of your websites or web applications. It performs "black-box" scans of the web application by crawling the webpages of the deployed webapp, looking for scripts and forms where it can inject data. Once it gets the list of URLs, forms and their inputs, Wapiti acts like a fuzzer, injecting payloads to see if a script is vulnerable.
WPScan: written for security professionals and blog maintainers to test the security of their WordPress websites.
✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖
👩🏻💻𝚂𝚒𝚝𝚒-𝚕𝚊𝚋𝚘𝚛𝚊𝚝𝚘𝚛𝚒
flAWS: through a series of levels you'll learn about common mistakes and gotchas when using Amazon Web Services (AWS).
flAWS2: this game/tutorial teaches you AWS (Amazon Web Services) security concepts. The challenges are focused on AWS specific issues. You can be an attacker or a defender.
✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖
👩🏻💻𝙱𝚛𝚎𝚟𝚎 𝚕𝚒𝚜𝚝𝚊 𝚍𝚒 𝚜𝚒𝚝𝚒 𝚊𝚙𝚙𝚘𝚜𝚒𝚝𝚊𝚖𝚎𝚗𝚝𝚎 𝚟𝚞𝚕𝚗𝚎𝚛𝚊𝚋𝚒𝚕𝚒 𝚜𝚞 𝚌𝚞𝚒 𝚏𝚊𝚛𝚎 𝚎𝚜𝚎𝚛𝚌𝚒𝚣𝚒𝚘
http://testphp.vulnweb.com
0 notes
Text
Chapter 1: The Awakening in Parañaque
It started like any other ordinary day at the Parañaque City Hall. Keichou Takameishi, a quiet yet sharp-minded programmer in the HRMIS Division, clocked in with the same thought he always had: "Another day, another line of code." He walked the halls under the modest hum of fluorescent lights, tapping his ID card at the 4th floor scanner. But something felt off today.
The system screens flickered strangely. Pulse-like patterns ran across the mainframe monitors, and faint glyphs danced momentarily over the digital interfaces before vanishing. Owie, his younger teammate and fellow programmer, noticed too. "Kuya Keichou," he said in a low tone, "may mali talaga sa network. Parang may bumubulong."
Ramil, the department head, summoned the team for an emergency huddle. "HRMIS, we might have a breach. Not cyber—something more... arcane."
Kim, the Division Chief, was unusually calm. She gave the directive: the HRMIS team was to investigate, quietly. They couldn't risk public panic. Lorie, Payroll Head and logistics coordinator, ensured their movement was discreet. Hanna and CJ, adept at magical overlays and honorarium constructs, were assigned to enhance the team's defenses. Darnin, Keichou's close friend and fellow programmer, had already begun examining the residual data streams.
That night, Keichou stayed late, tracing the odd fluctuations to a root server buried deep in the city records system. Byte, his AI construct, buzzed into his earpiece: "Link established. Access granted to subdomain: SIGIL-CORE."
He summoned Owie, Darnin, and CJ to City Hall under the pretense of maintenance. The moment they synced their devices, the floor below them shimmered—a digital illusion cloaking a forgotten passage beneath the building: The Vein.
Descending cautiously, they were met with constructs of light and code, floating runes pulsing like heartbeat monitors. Keichou rolled his first die in the Vein—a failed investigation roll, causing him to trip a harmless trap. Laughing it off, the group pressed forward.
They split up strategically: Darnin and Paul scouted for structural traps, while CJ and Hanna prepared disruption fields. Keichou moved forward, scanning for arcane encryption traps. He began disarming them, though success was sporadic due to a string of poor dice rolls.
Upon discovering a stairwell wrapped in surveillance wards, they called in Byte to scout deeper. Hanna and CJ performed synchronized disruption spells while Keichou, supported by Owie, attempted a hack. They encountered their first patrolling construct—a city defense node corrupted with fragmented municipal energy.
"Kuya Keichou, baka pwede natin i-hack ‘to," Owie said. The attempt succeeded, and they repurposed the construct as a guardian escort for Hanna and CJ. The core door loomed ahead, pulsing with a living heartbeat.
Inside, Keichou rolled perception and detected a residual spell fragment—a semi-sentient piece of memory magic. With his team casting buffs and protective wards on him, Keichou linked with Byte and attempted a sync. He spoke softly, "Sino ba naman ako? Isang hamak na empleyado ng City Hall na naglilingkod sa bayan... pero kung ako ang kailangan para pigilan ‘to, handa ako."
The sync succeeded.
Keichou absorbed part of the Crest Memory, unlocking a vision of a storm approaching Parañaque—a spell network left incomplete since the Spanish occupation, waiting to reactivate. A name echoed in his mind: Alon. Was he friend or foe?
Team status was updated: Johann fell unconscious after a failed sync attempt and had to be evacuated by HQ. Dexter was wounded defending the rear, while Darnin and Sop studied the decoded memory. Kim dispatched Ann and Grace to cast long-range protective enchantments. CJ provided Keichou with additional boosts, and even Nicole and Jocy prepared emergency protocols from Payroll.
The chapter ended with Keichou crafting his first two Sigil Capsules, storing hacked constructs as allies. As they stood at the entrance of the next layer—the Obsidian Gate—Keichou felt a growing sense of responsibility. Not just as a programmer. But as the city's unseen protector.
---
Chapter 2: Through the Obsidian Gate
The blackened Obsidian Gate shimmered like onyx liquid, its inscriptions older than any Filipino dialect. Owie murmured, "Kuya... parang buhay ‘yung gate." CJ, reading the glyphs with Hanna, nodded. "It needs a key. A sigil-coded one."
Keichou activated Byte, interfacing the capsule constructs to simulate a key pattern. With a flash of radiant violet, the gate creaked open.
Inside was the Echo Vault, a sprawling subdimension layered over real-world Parañaque—a secret infrastructure dating back centuries. Scout teams Johann and Dexter were dispatched deeper. Keichou followed, but soon lost comms. Johann had found something: a relic server glowing with forbidden energy. Then silence.
Keichou dived into the data stream, traced the signature—an old city ordinance rewritten into a ritual. The system had been breached not by hackers but a consciousness. A being: Alon. He whispered from old wireless routers, corrupted CCTV, and forgotten city records.
When Keichou tried to sync deeper, he risked corruption himself. Only with protective spells from Hanna and CJ, and boosts from Kim, Ann, and Grace, was he able to resist. Still, the weight of the magic lingered in his mind.
Using the recovered spell fragments, Keichou created two more Sigil Capsules, housing sentient city guardians. Darnin and Sop decrypted spell matrices, while the rest of HQ stood down to rest.
Keichou prepared to chase Alon deeper into the Echo Vault. Before stepping through, he activated the constructs beside him, who now called him Controller.
---
Chapter 3: Echoes Beneath the Circuit Sea
Keichou stood at the edge of the Echo Vault’s third level—a datawave-shrouded chasm known as the Circuit Sea. Below, code flowed like water, arcs of lightning jumping from bridge to bridge. Here, Alon’s influence was strongest.
Darnin and Sop sent him a decrypted schematic: a submerged subsystem was powering the encrypted failsafe runes embedded across Parañaque. HQ confirmed these were tied to the city’s digital infrastructure—lights, traffic systems, even public health records.
“Kuya,” Owie whispered, linking via tele-sigil. “Johann and Dexter are safe. Jocy's tending to them. CJ and Hanna ready to boost you—just say the word.”
Keichou gave the signal. Buffs surged into him. His mind sharpened, reflexes primed. With Byte linked, he dove into the chasm, surfing between dataflows, dodging fragmenting memories and defense codes. He rolled for investigation: success. A hidden terminal pulsed beneath a glowing node shaped like the City Hall logo.
He and Owie coordinated a double-hack on a nearby construct. It shimmered, then spoke: “Administrator confirmed. Guidance protocol initiated.”
Meanwhile, back at HQ, Ann secured a spiritual link to the crest network. Grace updated the barrier status. Ramil approved their deeper intervention. Kim dispatched Paul and Carlo to reinforce the perimeter.
With the construct leading them, Keichou reached the central core of the Circuit Sea: a swirling vortex of memory, spell, and circuit called The Cradle. Inside was a fractured crystal pulsing with red.
“Controller,” it spoke, “you are not the first. You are merely… ready.”
A vision overtook him—of old heroes: engineers who whispered spells into wires, programmers who bled mana into the city’s early computer systems. Among them, one figure stood out: Alon, once a protector, now corrupted by a looped betrayal.
Keichou emerged breathless. “Everyone, regroup. We’re heading to the Cradle. But I need two more Sigil Capsules.”
CJ handed over enchanted shells. “Sige, Kuya. Buhayin mo yan.”
And with that, Keichou stored two more constructs, his summoned allies.
The team rallied. Constructs synced. Protective sigils up. The breach protocol was about to begin...
To be continued...
0 notes
Text
Prevent Subdomain Takeover in Laravel: Risks & Fixes
Introduction
Subdomain takeover is a serious security vulnerability that occurs when an attacker gains control of an unused or misconfigured subdomain. If your Laravel application has improperly removed subdomains or relies on third-party services like GitHub Pages or AWS, it may be at risk. In this blog, we will explore the causes, risks, and how to prevent subdomain takeover in Laravel with practical coding examples.

A compromised subdomain can lead to phishing attacks, malware distribution, and reputational damage. Let’s dive deep into how Laravel developers can safeguard their applications against this threat.
🔍 Related: Check out more cybersecurity insights on our Pentest Testing Corp blog.
What is Subdomain Takeover?
A subdomain takeover happens when a subdomain points to an external service that has been deleted or is no longer in use. Attackers exploit this misconfiguration by registering the service and gaining control over the subdomain.
Common Causes of Subdomain Takeover:
Dangling DNS Records: A CNAME record still points to an external service that is no longer active.
Unused Subdomains: Old test or staging subdomains that are no longer monitored.
Third-Party Services: If a subdomain was linked to GitHub Pages, AWS, or Heroku and the service was removed without updating the DNS settings.
How to Detect a Subdomain Takeover Vulnerability
Before diving into the fixes, let’s first identify if your Laravel application is vulnerable.
Manual Detection Steps:
Check for dangling subdomains: Run the following command in a terminal: nslookup subdomain.example.com If the response shows an unresolved host but still points to an external service, the subdomain may be vulnerable.
Verify the HTTP response: If visiting the subdomain returns a "404 Not Found" or an error stating that the service is unclaimed, it is at risk.
Automated Detection Using Our Free Tool
We recommend scanning your website using our free Website Security Scanner to detect subdomain takeover risks and other security vulnerabilities.
📷 Image 1: Screenshot of our free tool’s webpage:

Screenshot of the free tools webpage where you can access security assessment tools.
How to Prevent Subdomain Takeover in Laravel
Now, let’s secure your Laravel application from subdomain takeover threats.
1. Remove Unused DNS Records
If a subdomain is no longer in use, remove its DNS record from your domain provider.
For example, in Cloudflare DNS, go to: Dashboard → DNS → Remove the unwanted CNAME or A record
2. Claim Third-Party Services Before Deleting
If a subdomain points to GitHub Pages, AWS S3, or Heroku, ensure you delete the service before removing it from your DNS.
Example: If your subdomain points to a GitHub Page, make sure to claim it back before deleting it.
3. Implement a Subdomain Ownership Validation
Modify Laravel’s routes/web.php to prevent unauthorized access:
Route::get('/verify-subdomain', function () { $host = request()->getHost(); $allowedSubdomains = ['app.example.com', 'secure.example.com']; if (!in_array($host, $allowedSubdomains)) { abort(403, 'Unauthorized Subdomain Access'); } return 'Valid Subdomain'; });
This ensures that only predefined subdomains are accessible in your Laravel app.
4. Use Wildcard TLS Certificates
If you manage multiple subdomains, use wildcard SSL certificates to secure them.
Example nginx.conf setup for Laravel apps:
server { listen 443 ssl; server_name *.example.com; ssl_certificate /etc/ssl/certs/example.com.crt; ssl_certificate_key /etc/ssl/private/example.com.key; }
5. Automate Monitoring for Subdomain Takeovers
Set up a cron job to check for unresolved CNAME records:
#!/bin/bash host subdomain.example.com | grep "not found" if [ $? -eq 0 ]; then echo "Potential Subdomain Takeover Risk Detected!" | mail - s "Alert" [email protected] fi
This script will notify administrators if a subdomain becomes vulnerable.
Test Your Subdomain Security
To ensure your Laravel application is secure, use our free Website Security Checker to scan for vulnerabilities.
📷 Image 2: Screenshot of a website vulnerability assessment report generated using our free tool to check website vulnerability:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Conclusion
Subdomain takeover is a critical vulnerability that can be easily overlooked. Laravel developers should regularly audit their DNS settings, remove unused subdomains, and enforce proper subdomain validation techniques.
By following the prevention techniques discussed in this blog, you can significantly reduce the risk of subdomain takeover. Stay ahead of attackers by using automated security scans like our Website Security Checker to protect your web assets.
For more security tips and in-depth guides, check out our Pentest Testing Corp blog.
🚀 Stay secure, stay ahead!
1 note
·
View note
Text
Raspberry Robin Found Spreading via Malicious Windows Script Files

Researchers have discovered a new wave of the Raspberry Robin malware campaign, which now propagates through malicious Windows Script Files (WSFs) since March 2024. "Historically, Raspberry Robin was known to spread through removable media like USB drives, but over time its distributors have experimented with other initial infection vectors," explained HP Wolf Security researcher Patrick Schläpfer in a report. Raspberry Robin, also referred to as the QNAP worm, was first spotted in September 2021. Since then, it has evolved into a downloader for various other payloads, including SocGholish, Cobalt Strike, IcedID, BumbleBee, and TrueBot, and has also served as a precursor for ransomware.
Diversifying Infection Vectors
While the malware was initially distributed through USB devices containing LNK files that retrieved the payload from a compromised QNAP device, it has since adopted other methods such as social engineering and malvertising. Raspberry Robin is attributed to an emerging threat cluster tracked by Microsoft as Storm-0856, which has links to the broader cybercrime ecosystem comprising groups like Evil Corp, Silence, and TA505.
Weaponizing Windows Script Files
The latest distribution vector involves the use of WSF files that are offered for download via various domains and subdomains. It's not clear how the attackers are directing victims to these URLs, though it's suspected that it could be through spam or malvertising campaigns. The heavily obfuscated WSF file functions as a downloader to retrieve the main DLL payload from a remote server, but not before a series of anti-analysis and anti-virtual machine evaluations are carried out to determine if it's being run in a virtualized environment.
Targeting System Configurations
The malware is also designed to terminate the execution if the build number of the Windows operating system is lower than 17063 (released in December 2017) and if the list of running processes includes antivirus processes associated with Avast, Avira, Bitdefender, Check Point, ESET, and Kaspersky. Additionally, the malware configures Microsoft Defender Antivirus exclusion rules to sidestep detection by adding the entire main drive to the exclusion list and preventing it from being scanned. "The scripts itself are currently not classified as malicious by any antivirus scanners on VirusTotal, demonstrating the evasiveness of the malware and the risk of it causing a serious infection with Raspberry Robin," HP said. "The WSF downloader is heavily obfuscated and uses many anti-analysis techniques enabling the malware to evade detection and slow down analysis." Who Discovered Raspberry Robin? In September 2021, Red Canary security researchers began tracking a cluster of worm-like activity that they designated as Raspberry Robin. The team shared their initial observations on this threat in a blog post published in May 2022. Following Red Canary's publication, other security researchers contributed their research findings, further expanding the cybersecurity community's understanding of Raspberry Robin. Over time, this malware evolved from a growing curiosity to a widely distributed malicious downloader. Raspberry Robin was Red Canary's 9th most prevalent threat observed in 2023. However, Raspberry Robin activity tracked by Red Canary decreased over the year, even as it retained its spot in the top 10 threats. While the reasons for this downward trend are not definitively known, it is possible that infrastructure disruptions could be a contributing factor. Read the full article
0 notes
Text
Scilla - Information Gathering Tool (DNS/Subdomain/Port Enumeration)
Scilla - Information Gathering Tool (DNS/Subdomain/Port Enumeration) #DNSEnumeration #DNSSubdomainPort #Enumeration
Information Gathering Tool – Dns/Subdomain/Port Enumeration Installation First of all, clone the repo locally git clone https://github.com/edoardottt/scilla.git Scilla has external dependencies, so they need to be pulled in: go get Working on installation… See the open issue. For now you can run it inside the scilla folder with go run scilla.go ... Too late.. : see this Then use the build…

View On WordPress
#DNS Enumeration#DNSSubdomainPort#Enumeration#Gathering#golang#Information#information Gathering#Information Retrieval#linux#Port Enumeration#Scilla#Subdomain Scanner#tool#windows
0 notes
Link
0 notes
Photo

Aquatone By far the best subdomain enumerator I have ever used, I love this tool-set both Aquatone Discover and Aquatone Scan. I would definitely recommend using this tool if you are a bug bounty hunter! Please note that I used the Nmap Scanme site as to avoid doing anything illegal and as you can see it already pulled the nameservers and does some cool stuff like pulling the subdomains and all their IPs and information! I quite often use this in combination with a very powerful program called Photon but for some reason haven’t been able to install Docker on Parrot because of some weird error. Will update as soon as I am able to fix this.
#Aquatone#subdomain#url#websites#webdevelopment#vulnerability scanner#dns#hacking tools#nmap#github#hacking#ethical hacking#ip address#enumeration
0 notes
Photo
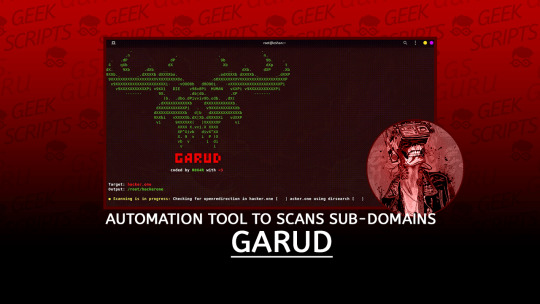
Garud: An Automation Tool To Scans Sub-Domains | #Scanner #Subdomains #Vulnerabilities #Hacking
0 notes
Text
Links For Cyber Security
--ONLINE PORT SCANNERS-- http://www.t1shopper.com/tools/port-scan/ https://hackertarget.com/nmap-online-port-scanner/ https://pentest-tools.com/network-vulnerability-scanning/tcp-port-scanner-online-nmap https://hidemyna.me/en/ports/ https://www.ipvoid.com/port-scan/ https://www.subnetonline.com/pages/network-tools/online-port-scanner.php https://www.ipfingerprints.com/portscan.php https://www.whatismyip.com/port-scanner/
--SUBDOMAIN SCANNERS-- https://pentest-tools.com/information-gathering/find-subdomains-of-domain https://dnsdumpster.com/ https://hackertarget.com/find-dns-host-records/ https://findsubdomains.com/
--WHOIS-- https://whois.icann.org/en https://whois.net/ whois.domaintools.com/ https://www.whois.com/whois/ https://www.godaddy.com/whoi
--ONLINE VIRUS SCANNERS-- https://www.virustotal.com/gui/home/upload https://metadefender.opswat.com/#!/ https://analysis.avira.com/en/submit https://virusscan.jotti.org/ https://virusdesk.kaspersky.com/ https://www.fortiguard.com/faq/onlinescanner
--SITES OF INTEREST-- https://pentest-tools.com/information-gathering/google-hacking https://securitytrails.com/blog/google-hacking-techniques http://pdf.textfiles.com/security/googlehackers.pdf http://index-of.co.uk/Google/Google%20Hacking%20Guide.pdf https://resources.infosecinstitute.com/google-hacking-overview/ http://www.mrjoeyjohnson.com/Google.Hacking.Filters.pdf
--WEBSITE CHECKERS-- https://www.urlvoid.com/ https://safeweb.norton.com/ https://www.fakespot.com/ --ADDITIONALS-- https://hackersonlineclub.com/hacking-tools/
1 note
·
View note
Text
Hawk Network and pentest utility that I developed so that I could perform different kinds of...
Hawk Network and pentest utility that I developed so that I could perform different kinds of task using the same suite, instead of jumping from one tool to another. Currently, this script can perform a variety of tasks such as ifconfig, ping, traceroute, port scans (including SYN, TCP, UDP, ACK, comprehensive scan, host discovery (scan for up devices on a local network), MAC address detection (get MAC address of a host IP on a local network), banner grabbing, DNS checks (with geolocation information), WHOIS, subdomain enumeration, vulnerability reconnaissance, packet sniffing, MAC spoofing, IP spoofing, SYN flooding, deauth attack and brute-force attack (beta). Other features are still being implemented. Future implementations may include WAF detection, DNS enumeration, traffic analysis, XSS vulnerability scanner, ARP cache poisoning, DNS cache poisoning, MAC flooding, ping of death, network disassociation attack (not deauth attack), OSINT, email spoofing, exploits, some automated tasks and others. https://github.com/medpaf/hawk

-
1 note
·
View note
Text
Detect What Innovation A Website Is Utilizing

You checked out a really desirable website as well as you wished to know what all technologies have actually been actually utilized to build such a nice site. There are online technology detection electricals which can check any provided website to detect and also uncover particulars regarding all the modern technologies functioning behind the internet site.
Website technology detection technique
BuiltWith
BuiltWith is one of the most effective web sites and offers almost every particular regarding the modern technologies a web site is actually using. It is going to shows info regarding Webserver, CMS, Platform, CDN, Analytical and also Ad answers utilized due to the web site. BuiltWith may be used on the internet and it is going to reveal the result of browse on its website. BuiltWith web browser extensions are actually additionally offered for Firefox, Chrome as well as Trip. BuiltWith may be used along with any type of web browser through Bookmarklet. Check all various options for technology detection listed here.
W3Tech
W3Tech gives you nearly every particular regarding a web site's interior modern technology. User interface is effortless as well as straightforward to recognize. W3Tech supplies listing of details like CMS, Webserver, Manuscript as well as various other modern technologies the site is developed along with. W3Tech Firefox and Chrome extensions are additionally accessible.
SimilarTech
SimilarTech shows all innovation associated details on its own website, all you need to do is to provide any kind of internet link to it. Results are actually pretty comprehensive as well as listings CMS, Webserver, Analytic option, Ad Body and all other details. SimilarTech has obtained among the very best user interface and groups everything modern technology plainly while maintaining less important info away. SimilarTech offers Chrome web browser extension.
Chrome Extensions
There are few other solutions on call which can easily detect all the modern technologies functioning responsible for any sort of internet site. Nonetheless they have acquired simply Chrome extensions offered. Listed below is actually a listing of technology detection procedure.
a) Appspector.
b) PageXray.
Detectify provides a complete collection of asset stock and surveillance remedies that include susceptibility checking, lot finding, as well as program fingerprinting. Its own use might help steer clear of undesirable shocks, such as unknown lots that show weakness or even sub-domains that can be effortlessly hijacked.
Wappalyzer
Wappalyzer does not possessed on the web scanner for checking Web site technology. Nonetheless it provides internet browser extensions for Firefox as well as Chrome browser together with Bookmarklet for other browsers. Wappalyzer also provides data associated with innovation used throughout the sites. So it could be examined if someone likes to know which innovations are very hot amongst websites.
A lot of factors can easily fail, and also an assailant can easily benefit from it. Some usual ones are:
Keeping unneeded slots open.
Revealing insecure subdomain, sensitive data, qualifications.
Keeping.git obtainable.
Possible OWASP leading susceptabilities like XSS, SSRF, RCE.
You can question that I may by hand run the slot scanning device, find sub-domain, test for weakness, etc. This is actually good if you do it as soon as or even occasionally, but it is going to be lengthy and not cost-efficient when you have to do it regularly.
Thus What is actually the option?
Go for Detectify Resource Surveillance, which monitors your internet app's assets and also conducts a routine check for most of all covered as well as many various other inspections to maintain your online business risk-free.
Detectify hosts their very own exclusive neighborhood of ethical hackers to crowdsource susceptability research study so it is actually providing you notifies coming from a genuine assailant's viewpoint.
Other resources rely on trademarks as well as model testing which is a lot more like compliance than true protection. The Detectify cyberpunks give the true hauls which are actually made use of to develop the protection tests, offering an one-of-a-kind set of testing which isn't found in other products on the market place.
The result? An even more sure-fire technique of security testing that simply offers you leads that can be confirmed.
Surveillance lookings for that are really interesting to correct!
1 note
·
View note
Text
5CloudHost Review – Real SSD Speed Hosting At Insane Low Price
https://lephuocloc.com/5cloudhost-review/
5CloudHost Review
In case you ever need to make something on the web, whatever it is, a blog, bargains pages, purposes of appearance or an ecom website page, first thing first, you need a webpage.
Your site takes after a physical store. It must be adequately astounding to drag customers to and a while later they can EASILY see what regard in your things or organizations that you can give them before any purchasing.
I'm practically sure you by and large give a valiant exertion for your visitors to have as a mind blowing customer experience as could sensibly be normal. Additionally, brisk stacking speed is on the most noteworthy purpose of your arrangement for the afternoon, correct?
In case it is, I should bolster you. By giving you this Holiday Special Limited Offer: Get 5 years of encouraging you can trust from an exhibited supplier – 5CloudHost.
If you get it through my referral associate, I will give you a phenomenal honor from me. This prize will help you with obtaining more money when gotten together with 5CloudHost.
Section by part control
5CloudHost Review – Overview
markdown
Thing name 5CloudHost
Vendor Catalin Draga
Front-end price $47-$147
Homepage https://www.fivecloudhost.com/
Release Date 2020-Jun-01
Release Time 07:00 EDT
Niche General
Recommended Very High
Capacity levels needed No need any aptitudes
Support Effective Response
Bonuses Mega 350 Bonuses Value At $142,863
Refund 30 Day Money Back Guarantee
5CloudHost Review – What right?
5CloudHost gives 5 years of Blazing-Fast Web encouraging for not actually the expense of one.
That suggests using premium encouraging for as pitiful as 2 pennies for every day for 5 YEARS!
5CloudHost Review What is it
About Creator
5CloudHost Review Creator
The man behind 5CloudHost is Catalin Draga.
Catalin is the Technical Manager of Virtono Networks SRL.
This is one of the most reliable encouraging suppliers wherever all through the world since it was built up in 2014. Its vital reliably been and will be "High Caliber at Fair Prices".
The undertaking has found and adjusted the right mix among emotional and moderate web encouraging responses for associations and individuals.
Thusly, 5CloudHost is your best encouraging ever. We ought to find more underneath in case you notwithstanding everything don't confide in it.
What Are the Features of 5CloudHost?
5CloudHost will give every one of you of these, no uncertainty:
Step by step Backups
Free SSL Certificates
Firewall and WAF
Contamination and Malware Protection
Vast Bandwidth
Vast Emails
Vast Subdomains
Vast MySQL DBs
1-Click CDN (Cloudflare)
1-Click App Install (Softaculous)
Distinctive PHP Versions
Constrained by cPanel®
Your site will be totally and completely managed.
Ultra-Fast Loading Speeds
All their notable servers use the freshest development, including SSD accumulating and 10Gbps web affiliation, ensuring super-fast weight speeds.
Lower your ricochet rate, bolster your Google rank. Immediately starting getting more traffic and making more arrangements.
Pick Your Server Location
You can choose to have your districts on servers in the US or Europe.
Pick the territory closest to your rule target exhibit and instantly give your customers better customer experience.
100% Uptime
Their top tier cloud structure is totally tedious and consolidated with Cloudflare.
They will keep your website online reliably and assurance that it will stack immediately from any side of the world.
Easy To Use
Their encouraging stage is regularly constrained by cPanel. It's the most standard electronic control board which is as it ought to be.
It's extraordinarily straightforward and energizes you successfully manage your destinations with computerization gadgets planned to unravel everything.
1-Click Installation
You can present WordPress with a singular snap. In all honesty, they have 450+ applications with a solitary tick foundation.
Keep away from paying for specific help and start using your time on stuff that will truly get you more income.
Part Marketing Friendly
We both grasp and favor of email – and branch promoting. They will reliably fight in your corner and attempt to help you with building up your business and advantage.
Committed Support
They care about you and their committed assistance bunch is totally in-house and arranged to react to your requests each moment of consistently. No all the more stopping, get help when you need it the most!
Industry-Leading Security
They are dead serious about security and guarding your goals.
That is the explanation all of their server ranches are Tier 3 guaranteed, each server has its own firewall, WAF, against malware and threatening to contamination scanner and they take step by step fortifications for each record.
Free Migration
They're amped in the mood for encouraging your goals and they have to take all your get-away burdens away.
They'll help you with moving your regions to their server and one of their migration experts will manage you through the entire technique, thoroughly FREE of charge!
Zero Recurring Cost
Today you'll get 5 years of star level cloud encouraging for a low one time cost… an insignificant division of what you'd pay for 1 year of encouraging any place else.
There is no extra cost or rehashing charges ever!
For additional information about this thing, click the catch underneath:
visit-site button
5CloudHost Review – Is it worth buying?
Since customers loathe stopping and the website speed is in like manner a web searcher situating component, the encouraging ought to be very snappy!
5CloudHost is sure to give what you need – frantically brisk stacking speed for your site.
It uses SSD-simply attack guaranteed reserves, that will improve the adjustment to inward disappointment and the read/make speed out of the servers (especially MySQL).
Along these lines, your site will stack 10x faster at any rate.
That isn't all, their 1-Click coordination with Cloudflare makes it exorbitantly easy to abuse the BEST CDN (Content Delivery Network) available today.
Which gives you by a long shot predominant site load paces and security!
Most sponsors pick their first web have with no real cognizance of what's noteworthy, also what it can cost in case you pick an improper one and everything turns out gravely.
Imagine you have your site racing to the stage where it's procuring hundreds, or even countless dollars every day and a short time later the unavoidable happens.
Your site is hacked or your server mishaps and you have no fortification, zero chance to get of recovering what you've lost and recuperating your site good to go!
The cost in lost compensation alone is disturbing, by then your reputation will be crushed.
You may lose existing customers, potential new customers, and even your rankings in Google!
Why even face that challenge regardless?
Your business, your real sentiments of peacefulness, and your principle concern need a web have that is speedy, secure and flexible. That is 5CloudHost what I'm examining.
Update your business for 2020, altogether through to 2025 – send your site on impacting speedy, easy to-use, secure and ultra-strong cloud encouraging with 5CloudHost today.
What People Say About 5CloudHost
A large number of clients are satisfied while using 5CloudHost, and you will be one of them soon:
5CloudHost Review People Say
Who Should You Use It?
Doesn't have any kind of effect in case you are a blogger, partner promoter or online retailer, any person who achieves something on the web needs a decent Web Hosting like 5CloudHost.
Generally, 5CloudHost is a MUST-HAVE thing for:
♦ Affiliate Marketers
♦ Marketers
♦ Com + Amazon
♦ Freelancers
♦ Website Owners
♦ Social Media Marketers
♦ Local associations
♦ Any various sorts of online business
Upsides and drawbacks
Specialists
✓ Daily Backups
✓ Free SSL Certificates
✓ Firewall and WAF
✓ Virus and Malware Protection
✓ Unlimited Bandwidth, Emails, Subdomains and MySQL DBs
✓ 1-Click CDN (Cloudflare) and App Install (Softaculous)
✓ Multiple PHP Versions
✓ Powered by cPanel®
✓ High-Performance Hardware
✓ Fully Redundant Cloud
✓ Secure Infrastructure
✓ Instant Activation
✓ Dedicated Support
✓ Powerful Automation
✓ 30 Day Money Back Guarantee
Cons
X No Cons Founded.
Assessing
5CloudHost has 3 OTOs so you can pick what fits you most:
– OTO1: Cloud Starter – Medium traffic singular goals ($119 $47/5 Years)
Elective 1: US Plan (See Details)
Elective 2: EU Plan (See Details)
1 Hosted Domain
5 GB SSD Storage
Dallas, TX Datacenter
Given resources(LVE): half CPU(~1.4Ghz), 512MB RAM, 20 Entry Processes
– OTO2: Cloud Business – High traffic corporate goals ($239 $97/5 Years)
Decision 1: US Plan (See Details)
Decision 2: EU Plan (See Details)
10 Hosted Domains
15 GB SSD Storage
Dallas, TX Datacenter
Submitted resources(LVE): 100% CPU(~2.8Ghz), 1GB RAM, 50 Entry Processes
– OTO3: Cloud Enterprise – Enterprise content organization ($359 $147/5 Years)
Elective 1: US Plan (See Details)
Elective 2: EU Plan (See Details)
Vast Hosted Domains
50 GB SSD Storage
Dallas, TX Datacenter
Committed resources(LVE): 200% CPU(~5.6Ghz), 2GB RAM, 100 Entry Processes, Dedicated IP Address
7IjXDNJ
https://lephuocloc.com/5cloudhost-review/
https://lephuocloc.com/

1 note
·
View note
Text
Reliable Hosting for Affiliate Marketing Websites
Reliable Hosting for Affiliate Marketing Websites
Affiliate marketing has emerged as a lucrative venture for many entrepreneurs seeking online success. Whether you're a seasoned affiliate marketer or just stepping into the realm of online business, choosing the right hosting service for your affiliate marketing website is paramount. In this article, we'll delve into the world of reliable hosting solutions tailored specifically for affiliate marketers.
1. Understanding the Importance of Reliable Hosting
Before we embark on exploring hosting options, it's crucial to comprehend why reliable hosting is indispensable. Your website's performance, loading speed, and uptime directly impact user experience and, consequently, your affiliate marketing success. Visitors tend to navigate away from slow-loading websites, leading to missed opportunities.
2. Factors to Consider in Hosting for Affiliate Marketing
When selecting a hosting provider, consider factors such as server uptime, customer support, bandwidth, and security features. Opting for a hosting service with a robust infrastructure ensures your website stays live and accessible round the clock, enhancing user satisfaction.
2.1 Server Uptime: The Backbone of Your Website
Server uptime is the lifeline of your affiliate marketing website. Choose a hosting provider with a proven track record of high uptime percentages. Downtime can lead to revenue loss and a negative impact on your brand's credibility.
2.2 Customer Support: Your Reliable Partner
24/7 customer support is invaluable, especially when you encounter technical issues. Responsive customer service ensures that any problems are swiftly resolved, allowing your website to function seamlessly.
2.3 Bandwidth and Speed: The Need for Swift Navigation
Adequate bandwidth and fast loading speeds are vital for user satisfaction. Opt for hosting services that offer scalable bandwidth options, ensuring your website can handle increased traffic without compromising speed.
2.4 Security Features: Safeguarding Your Online Assets
Security breaches can be disastrous for affiliate marketers. Look for hosting providers that offer SSL certificates, DDoS protection, and regular security audits. A secure website builds trust among visitors and potential customers.
1.Hostginger
Since its inception in 2018, Hostginger has been on a mission to offer hosting services that make life easier for developers and their customers. We deliver our promise by constantly updating server technology and improving customer support. We believe that building online businesses should be easy and fun. It should leave you happy and accelerate your growth with money in your pocket.
Web Hosting for All Business Sizes
Choose Your Web Hosting Plan
Affordable and Reliable Solution for Hosting Your Website
Single Web Hostinge Domain Offer
The Ultimate Hosting Plan for Personal, Blogs, and Small Project Websites designed to meet all your needs
₹249 - Save 64%₹89/moRenews October, 2026 for ₹159/mo*
Add to cart
Top Feature Comparison
1 Website
50 GB SSD Storage
100 GB Bandwidth
Weekly Backups
Powered By cPanel
Security
Unlimited Free SSL
Malware Scanner
Free Bonuses
Free 2 Email Account
Free Website Builder
WordPress Options
Managed WordPress
Free 1-Click WordPress Install
No WordPress Acceleration
No WordPress Staging Tool
Service and Support
30 Days Money Back Guarantee
24/7 Support
99.95% Uptime Guarantee
More Features
2 Database
DNS Management
2 Subdomains
1 FTP Account
2 Cronjobs
Free Migration
Upgrade On Pro Rata Basis
Instant Setup
See less features
Premium Web Hosting
Free Domain Offer
The Perfect Plan for Delivering Customized Solutions for Your Small or Medium Sized Business
₹499 - Save 70%₹149/moRenews October, 2026 for ₹279/mo*
Add to cart
Top Feature Comparison
100 Website
100 GB SSD Storage
Unlimited Bandwidth
Weekly Backups
Powered By cPanel
Security
Unlimited Free SSL
Malware Scanner
Free Bonuses
Free 100 Email Account
Free Website Builder
WordPress Options
Managed WordPress
Free 1-Click WordPress Install
WordPress Acceleration
WordPress Staging Tool
Service and Support
30 Days Money Back Guarantee
24/7 Support
99.95% Uptime Guarantee
More Features
Unlimited Database
DNS Management
100 Subdomains
Unlimited FTP Account
Unlimited Cronjobs
Free Migration
Upgrade On Pro Rata Basis
Instant Setup
See less features
Business Web Hosting
Free Domain Offer
The Top-Tier Hosting Solutions for E-Commerce to handle High Traffic and Support Your Business Growth
₹549 - Save 63%₹199/moRenews October, 2026 for ₹349/mo*
Add to cart
Top Feature Comparison
100 Website
200 GB SSD Storage
Unlimited Bandwidth
Weekly Backups
Powered By cPanel
Security
Unlimited Free SSL
Malware Scanner
Free Bonuses
Free Unlimited Email Account
Free Website Builder
WordPress Options
Managed WordPress
Free 1-Click WordPress Install
WordPress Acceleration
WordPress Staging Tool
Service and Support
30 Days Money Back Guarantee
24/7 Support
99.95% Uptime Guarantee
More Features
Unlimited Database
DNS Management
100 Subdomains
Unlimited FTP Account
Unlimited Cronjobs
Free Migration
Upgrade On Pro Rata Basis
Instant Setup
See less features
4. Conclusion
Choosing reliable hosting for your affiliate marketing website is a pivotal decision that directly impacts your online success. By considering factors like server uptime, customer support, bandwidth, and security features, you can ensure your website operates smoothly, providing visitors with a positive experience.
FAQs
Q1: What is server uptime, and why is it essential for an affiliate marketing website?
Server uptime refers to the duration your website is operational and accessible to visitors. It's crucial for affiliate marketing websites as downtime can lead to revenue loss and a negative impact on user experience.
Q2: How can SSL certificates enhance the security of my affiliate marketing website?
SSL certificates encrypt data transmitted between a user's browser and your website, ensuring secure communication. This encryption builds trust among visitors, making them more likely to engage with your affiliate offers.
Q3: What should I do if my website experiences sudden traffic spikes?
If your website faces unexpected traffic surges, consider upgrading your hosting plan to accommodate the increased demand. Hosting providers like Bluehost and SiteGround offer scalable solutions for such situations.
Q4: How can I optimize my website's loading speed for better user experience?
To enhance your website's loading speed, optimize images, use efficient coding practices, and consider a hosting provider like A2 Hosting, known for its swift loading speeds and optimized software configurations.
Q5: Is 24/7 customer support really necessary for my affiliate marketing website?
Yes, 24/7 customer support is essential, especially for online businesses. Technical issues can arise at any time, and having responsive customer support ensures problems are addressed promptly, minimizing downtime and ensuring smooth operation.
0 notes
Text
Reconftw - Simple Script For Full Recon
Reconftw - Simple Script For Full Recon #bruteforce #Bugbounty #DalFox #dorks #Enumeration #full #OpenRedirect #recon
This is a simple script intended to perform a full recon on an objective with multiple subdomains tl;dr Requires Go Run ./install.sh before first run (apt, rpm, pacman compatible) git clone https://github.com/six2dez/reconftw cd reconftw chmod +x *.sh ./install.sh ./reconftw.sh -d target.com -a Features Tools checker Google Dorks (based on deggogle_hunter) Subdomain enumeration (passive,…

View On WordPress
#bruteforce#Bugbounty#DalFox#dorks#Enumeration#full#Open Redirect#recon#Reconftw#Scanner#Script#Simple#subdomain
0 notes
Text
sql injection cheat sheet trainer SOS&
💾 ►►► DOWNLOAD FILE 🔥🔥🔥🔥🔥 An SQL injection cheat sheet is a resource in which you can find detailed technical information about the many different variants of the SQL injection. MySQL SQL Injection Cheat Sheet ; Select Nth Char, SELECT substr('abcd', 3, 1); # returns c ; Bitwise AND, SELECT 6 & 2; # returns 2. SELECT 6 & 1; # returns 0. Use this SQL injection attack cheat sheet to learn about different variants of the SQL Injection vulnerability. But before we proceed, let us. MySQL-SQL-Injection-Cheatsheet. Tips for manually detect & exploit SQL injection Vulnerability : MySQL. Comment in MySQL. #; -- (After double dash put space). 9 This SQL injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when performing SQL injection attacks. You can extract part of a string, from a specified offset with a specified length. Note that the offset index is 1-based. Each of the following expressions will return the string ba. You can use comments to truncate a query and remove the portion of the original query that follows your input. You can query the database to determine its type and version. This information is useful when formulating more complicated attacks. You can list the tables that exist in the database, and the columns that those tables contain. You can test a single boolean condition and trigger a database error if the condition is true. You can use batched queries to execute multiple queries in succession. Note that while the subsequent queries are executed, the results are not returned to the application. Hence this technique is primarily of use in relation to blind vulnerabilities where you can use a second query to trigger a DNS lookup, conditional error, or time delay. You can cause a time delay in the database when the query is processed. The following will cause an unconditional time delay of 10 seconds. You can test a single boolean condition and trigger a time delay if the condition is true. You can cause the database to perform a DNS lookup to an external domain. To do this, you will need to use Burp Collaborator client to generate a unique Burp Collaborator subdomain that you will use in your attack, and then poll the Collaborator server to confirm that a DNS lookup occurred. You can cause the database to perform a DNS lookup to an external domain containing the results of an injected query. To do this, you will need to use Burp Collaborator client to generate a unique Burp Collaborator subdomain that you will use in your attack, and then poll the Collaborator server to retrieve details of any DNS interactions, including the exfiltrated data. Want to track your progress and have a more personalized learning experience? It's free! SQL injection cheat sheet This SQL injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when performing SQL injection attacks. String concatenation You can concatenate together multiple strings to make a single string. Oracle Does not support batched queries. Sign up Login. Patching times plummet for most critical vulnerabilities — report 30 August Log4Shell legacy? Patching times plummet for most critical vulnerabilities — report Introducing ODGen Graph-based JavaScript bug scanner discovers more than zero-day vulnerabilities in Node.
1 note
·
View note