#advanced hacking os
Explore tagged Tumblr posts
Text
Assorted Selfship Lore!!
Normally, I post the "main" selfship lore in posts of their own with a commissioned work, but since that well is a lil slow atm, I just gonna ramble on some lore nuggets I have for current f/os I have. Nothin in depth, but the general ideas.
Purah, as kinda my secondary main f/o, has a good bit. We actually knew each other before the events of BotW, though our relationship was a lot different back then. I was a doctor who worked under the crown, so we met up quite frequently. We were going strong for a few years, with plans to marry, until the Calamity happened. I was studying cryogenic preservation up in Hebra when it happened, and the ensuing chaos led to myself being frozen in suspended animation for nearly a century! Purah has bigger fish to fry and kinda lost her memory a bit when she went baby mode, so I wouldn't be found til about a year after Link defeated Ganon and search parties began to be sent out, when I was found frozen in the ice. Purah kinda laser focused on me for a good while, staying by me day in and day out til I fully thawed, and of course oversaw my rehabilitation. She felt a bit awful for the whole thing, but I assured her it was not her fault, and she did the best she could. What mattered most was that were were together again ❤️
I actually have a story with Odessa that takes place after her episode of the show. For backing, I was a elastic powered thief who traveled the world stealing what I wanted. I found out about Odessa during my time in New York, and fell for her. She initially just humored my advances, but she soon fell to my villainess charms and returned the feelings. After I broke her out, she became committed to joining me in robbing the world of whatever we wanted. I even helped rehabilitate her public image, so we could be out in public together yet again eheheh >:]
With Perona, I feel we met up during the two-year time skip. Probably one time when she left the island Zoro and Mihawk were at and explored the surrounding area. She found me alone, silently working on clothes of several varieties thanks to my Cloth-Cloth Fruit abilities. We had a rocky meeting, but things went on an upswing when I made her some new outfits. We got talking, bonding over our similar styles, and then one thing led to another, and we ended up dating :] I visited her and the others frequently, though neither Zoro nor Mihawk were the most...welcoming. I did at least supply Zoro with his new garb before he went off to Sabaody, and did tag along with Perona when she made sure he got there. We stick pretty close to one another, mainly cause, ya know, we're that kinda couple, heh 🩷
For Sombra, we met as Talon agents. Similar vibes, though I was more focused on "physical" hacking, so to speak. Started as a bit of a flirty rivalry that turned to actual flirting that turned to actual dating. We never stop being bad, but we do lay low several years down the line cause, wuh-o, she ended up pregnant with my kid! No idea how that happened...👀
D. Va is a similar case! Freelance agent who encountered her on a few missions. Rivalry started cause I called into question her skills, and that rivalry eventually blossomed into a romantic relationship. We're very open about it too, bothers everyone on the team lol.
Roz I'm kinda here and there about. It's def a kinda AU from the main film, with like anthro versions of the animal cast, cause ya know I def want Brightbill and Fink there. Question is do I wanna be anthro? Or just human? Prolly be a raccoon, cause that's my Mobian-sona. Then again, Roz has a history with raccoons, heh. Regardless, I am very much a robot kisser and I love being co-parents with her :]
Sybil is fun cause, I'm casting myself as a similar "dream warrior", known as The Oni. Cowl, Blue Spirit-esque mask, large ogre-like mace. Tanuki-Possum kinda creature. We're both busy people, but when we meet up, we make it count. We haven't committed to anything, but we are life partners, so there's that!
These next three, I think I made a post earlier about em, or at least the general idea. So, with Toy Chica, I'm introduced as like the new addition to the Fazbear cast, specifically as Chica's partner. She's a bit unsure about the whole deal, but when I turn out to be a lovable guy, genuinely kind, and a good cook, we form a genuine bond which slowly grows to be romantic. Might AU this a bit where like, they're still animatronics but doing that is there "job"? I dunno, sorting the deets.
Roxy is similar. Same fictional in-universe character, now reintroduced in the Pizza-plex era as Roxy's race partner for the double go-kart track. We hit it off incredibly well, and kinda just go with dating from the get go. Helps I'm super supportive of her being the best :]
Rambley is, again, much the same. My character was introduced to be his close friend—if Rambley is Mickey, think me as Goofy, but designed to be as Minnie. Our relationship is very close, so close that over time, when it came time to introduce a proper love interest for Rambley, they just decided to use me because people already assumed we were meant to be a couple. And so we became canon :]
Other bits!:
I was with Mariah when she worked with DIO, and helped fished her out after her battle with Joseph and Avdol. We retired after that.
I was probably some misc god or being in Viridi's pantheon when I met Phosphora.
As the Ultimate Butler, I was placed to work alongside Kirumi. Our relationship started as a tense bout of one-ups-man-ship that eventually boiled over to romantic desire.
#As you can see they get more sporadic as you go down#From well thought out lore#to bits and bobs of stray thoughts#I'm gonna get somewhere with everyone#I swear this#Basically no repeat ships til I get to everyone#Soon#self ship#fictional other#self ship community#official louis posting#f/o posting#selfship talk#official gf post#official wife post#totk purah#the legend of zelda#tears of the kingdom#odessa drake#marvel#moon girl and devil dinosaur#perona#one piece#perona one piece#sombra#dva#dva overwatch
5 notes
·
View notes
Text
How to easily stream your (New) 3DS to a PC
For a long time, capturing footage from a 3DS was a pain - streaming the 3DS screens either required a hardmod to install a capture card (which, if you can, should still do if possible), or use one of the several wireless methods (NTR CFW and HzMod) that gave poor results, especially on Old 3DS.
Today, thanks to the effors of zbash92, there is now a way to stream the New 3DS display to your computer with actually decent picture quality and low latency!
youtube
New NTR CFW test done back when it was firstly released
Here's a few applications of streaming your 3DS to a computer:
Playing on a bigger screen
Recording footage of 3DS games
Capturing audio for OSTs or music you made on 3DS
Below is a guide to setting everything up, including audio capture.
Requirements
A hacked New 3DS system (Old 3DS users might use HzMod via a separate guide but the performance is VERY POOR. Old 3DS can still have their audio captured by audio cable.)
A good network connection that both the New 3DS and your PC share
(If you want to capture audio) A 3.5mm to 3.5mm audio cable and either a microphone port or a Y splitter that has a microphone port
Setup wireless streaming (3DS)
Install the .cia file onto your 3DS from the latest release of this NTR fork
Run the newly installed app, go through the setup until prompted to run a desired version - pick 3.6 HR at the very bottom
Press X+Y to open the NTR CFW menu and choose Remote Play (New 3DS) - this will show you the IP address your console has, and will also let you configure quality and performance options
Setup wireless streaming (PC)
Install one of the following NTR viewers: - NTRViewer (Windows and Linux, x64) - Snickerstream (Windows, x86 and x64) - kit-kat-slim (Windows, allows using input redirection AKA controlling your 3DS with the PC) - Twix (Windows, also allows input redirection and looks fancy) - cuteNTR (Linux) - cuteNTR-OSX (Mac OS) There are other ones, including for Windows 10/Xbox and even Wii U, but the performance may not be ideal for these
Run the NTR viewer you chose and input the IP address you got earlier. You can also set quality and performance options in the viewer as well as rendering options if available
Connect to your 3DS and enjoy looking at your console on a bigger(?) screen!
Setup audio capture
Connect the 3.5mm to 3.5mm audio cable to your 3DS headphone port and PC's microphone port (directly or via the Y splitter in computer's headphone port)
You can test the audio by either enabling listening to the new microphone device or using a program such as Audacity or OBS
Notes and Issues
TRY NOT TO CLOSE YOUR 3DS LID! It can sometimes lead to black screens and no response from the console, in which case you should hold the power button until it shuts down
This CANNOT record your DS, DSiWare or GBA VC games. Those require a capture card or using an emulator instead. Audio can be captured regardless of what your system is running
Some games may disable your internet connection, which means that you need to use patching option provided by NTR CFW or your NTR viewer of choice
If your NTR Viewer doesn't work, check firewall and viewer's render settings first and then try other viewers for your system
If your viewer disconnects on still screens, increase the timeout/wait time of the viewer if available (for Snickerstream, it's in Advanced settings)
If you have choppy framerate, decrease the quality, fiddle with QoS value and Encoder Priority, or get a better internet connection :p
If you have audio issues, try switching between microphone out and line out
-- Red
6 notes
·
View notes
Text
Log_3.TXT
07/04/2023, 07:15 (GMT-5)
After being awake until roughly 3 AM I was able to do it, it wasn't easy at all and I'm actually surprised I was able to do it without waking up the other people in this house, right now, I am in class about to fall asleep, but I think I can remain awake to finish both my literary analysis AND this entry.
First of all, was the watch easy to hack? No. Let me elaborate, I used an old sports watch I found in my closet, I'm more surprised about the fact that it was almost as good as new and worked perfectly after three years of not being used rather than on me being able to hack it, I'm not entering details, but the watch had a simple OS I quickly made my way into, by connecting it to my PC I was able to crash the OS and replace it with an even simpler one, that only runs Digimon Capture, keeping the watch OS this simple, I open the door for me to update the software if I catch any bugs or I just need to improve the watch's features.
Now, let me explain how the watch works, you see, Digimon need to eat, however I'm not really "in love" with that concept right now since feeding them would take time I could use advancing on my investigation, thus I had an idea, since the watch I use as a shell is a sport focused one, I linked the active digimon's necessities to the function that reads my heartbeat, that way, I'll be able to do research without pausing to feed my monsters and putting them to sleep, I also coded some other functions based on what features the watch has, an example would illustrate it better. Digimon need to exercise so they can increase their battle capabilities, I found a way to translate their battle capabilities into three basic stats, stats I will increase by doing exercise myself, and maybe that way I'll hopefully get in better shape, the watch can recollect items that can be helpful when raising a digimon, I hate to end this entry on a bitter note, but I can't ignore my faults all of this features were added to compensate for two things, the first one not being strictly my fault but I still feel salty about it, the thing is, this watch has little to none storage capacity, so it can only have 3 digimon at the same time inside it's OS, which is actually more than other Digimon Docks, but I wanted to save at least two pairs of digimon, the second is entirely my fault... Digimon have battle capabilities for a reason, they need to fight with their equals to absorb their data and grow, so they can increase their power and eventually go through a process called "Evolution" however I wasn't able to code a battle function for this watch but I have Guilmon working on something, I can't discuss it any further, not now at least but... I'll keep you updated.
ATT: ARC
3 notes
·
View notes
Text
Can Someone Hack Your Phone and Listen to Your Calls?

In today's digital era, where smartphones are essential for communication, concerns about phone security and privacy are more relevant than ever. The question often arises: can someone hack your phone and listen to your calls? In this article, we'll delve into the intricacies of phone hacking, explore the possibilities of call interception, and provide practical steps to safeguard your private conversations.
Understanding Phone Hacking
Phone hacking encompasses unauthorized access to a mobile device's data and functionalities. While hacking methods vary, the potential risk of call interception is a significant concern. Hackers who gain access to your device could potentially eavesdrop on your conversations, breaching your privacy and security.
Methods of Phone Hacking
Hackers employ an array of techniques to infiltrate devices, including exploiting vulnerabilities in operating systems and using malicious apps. The unsettling prospect of call hacking involves intercepting and listening to phone conversations, often without the victim's knowledge or consent.
VoIP Vulnerabilities
Voice over Internet Protocol (VoIP) technology, which allows voice calls over the internet, has become commonplace. However, this technology isn't immune to vulnerabilities. If hackers exploit weaknesses in VoIP, they might gain unauthorized access to calls, bypassing traditional cellular networks.
Eavesdropping on Calls
One alarming facet of phone hacking is call eavesdropping. By exploiting security gaps, hackers can gain access to live phone conversations, potentially compromising sensitive information. Instances of call interception highlight the urgency of taking protective measures.
Security Flaws in Mobile Networks
Mobile networks, while advanced, can still harbor security flaws. Hackers with the right skills can exploit these vulnerabilities to intercept calls. This underscores the need for robust security protocols to prevent unauthorized access.
Operating System Vulnerabilities
Outdated operating systems pose a considerable risk. When users fail to update their OS, they leave their devices susceptible to attacks. Security patches play a crucial role in preventing hacking attempts that could compromise calls.
Risks of Third-Party Apps
Third-party apps, particularly those without proper security measures, can serve as gateways for hackers. Malicious apps might infiltrate your device, granting unauthorized access to your calls and conversations.
Securing Your Phone
Protecting your phone is paramount in the digital age. Creating strong, unique passwords, regularly updating your device's software, and reviewing app permissions can significantly enhance your phone's security.
End-to-End Encryption
End-to-end encryption is a robust security measure that ensures the content of your calls remains confidential. This encryption method prevents unauthorized parties, including hackers, from deciphering your conversations.
Using Encrypted Communication Apps
Consider using encrypted messaging and calling apps to fortify your communication. Apps like Signal, WhatsApp, and Telegram offer end-to-end encryption, providing an extra layer of protection for your calls.
Network Security Measures
Secure network connections are essential. Utilizing Virtual Private Networks (VPNs) can add a layer of encryption to your internet traffic, safeguarding your calls from potential eavesdropping.
Recognizing Suspicious Activity
Being vigilant about unusual activity on your device is crucial. If you notice unexpected behavior, such as rapid battery drain or unfamiliar apps, it might indicate a breach. Promptly address such issues to protect your calls and data.
Expert Insights
According to cybersecurity experts, the risk of call hacking underscores the importance of proactive measures. Dr. Sarah Miller, a renowned cybersecurity analyst, emphasizes, "Users must prioritize device security, keep software up to date, and employ encryption technologies."
Balancing Convenience and Security
Striking a balance between convenience and security is essential. While security measures might seem inconvenient at times, safeguarding your privacy and protecting your calls from potential interception is worth the effort.
Conclusion
In a world where connectivity is integral to our lives, the possibility of someone hacking your phone and listening to your calls is a legitimate concern. By understanding the methods hackers use, employing robust security practices, and embracing encryption technologies, you can significantly reduce the risk of call interception. Remember, safeguarding your privacy requires ongoing vigilance and proactive action.
Frequently Asked Questions
Can hackers really listen to my phone calls? While it's possible for skilled hackers to intercept calls, taking security measures like encryption and using secure apps can greatly mitigate this risk.
How do hackers intercept phone calls? Hackers exploit vulnerabilities in mobile networks, operating systems, or apps to gain unauthorized access to calls.
What is end-to-end encryption, and how does it protect calls? End-to-end encryption ensures that only the sender and recipient can access the call content, preventing interception by hackers.
Are encrypted communication apps safe for calls? Yes, encrypted apps like Signal and WhatsApp offer strong security measures, making them safe choices for private calls.
What should I do if I suspect my calls are being intercepted? If you suspect call interception, immediately review your device for unusual activity, update your security settings, and consider seeking professional assistance to secure your phone.
#phone hacking tools#phone hacking#find a hacker#contact a hacker#finding a hacker#phone hacking service#cybersecurity#ethical hacking
4 notes
·
View notes
Text
How to Reset the Password on Almost Any Windows Computer (Updated for Windows 11)
How to Reset the Password on Almost Any Windows Computer (Updated for Windows 11) https://mytekrescue.com/how-to-reset-the-password-on-almost-any-windows-computer/ UPDATED 06-08-25 There is a fault (maybe it’s a feature) in most later versions of Windows that allows someone with physical access to the computer to change the passwords of users, create new users, and elevate users to administrators. This article will show you how to do this. We are not going to go into extreme detail on this. We are going to assume that you have some basic computer repair skills. We are a San Marcos, TX based managed IT Support business, so we use this hack very often. Time to Complete: 30 minutes or less Difficulty level: Medium Tools needed: A Windows Install Disk that matches the operation system on the computer Note: This method works with several Windows OS’s. We are going to show you how to do it on a Windows 11 computer. Step 1 – Replace Utilman.exe with CMD.exe Read moreTop Network Security Best Practices for 2025 Boot into the install CD or USB Installer that matches your operating system. If you do not have one there are several tutorials out there that can help you make one. Click on Troubleshoot, then Advanced options, and finally Command Prompt. At the command prompt type the following command: copy c:windowssystem32utilman.exe c: …and press Enter. You should see a “1 file(s) copied” confirmation. Read moreSmart IT Strategies: Why a vCIO is Essential for Businesses Now type this command and hit Enter: copy c:windowssystem32cmd.exe c:windowssystem32utilman.exe Answer with Y to the question about overwriting of the utilman.exe file. You should now see another file copy confirmation. Reboot the computer normally into Windows. Step 2 – Manipulate the users you need NOTE: The following NET commands will work for Windows 11, but for Windows 11 you will need to boot into “Safe Mode with Networking” to use them! Thanks Andrew for the tip! Read moreDon't Skip IT Maintenance—Here's Why When the Windows logon screen is available, click the Ease of Access icon at the bottom-left corner of the screen. An ADMINISTRATOR Command Prompt will open. There are several commands you might need to use below. In them replace “myuser” with the actual username. Replace “newpassword” with your desired password. Enter the following command to get a list of users: net user Enter the following command to change the password of an existing user. net user myuser newpassword Enter the following command to create a new user: net user myuser newpassword /add Read moreFinding Managed IT Services in Kyle TX Without Pulling Your Hair Out Enter the following command to elevate an existing user to an administrator: net localgroup administrators myuser /add Once you have run the commands that you need to run, log in and double check your work. Step 3 – Put Utilman.exe Back Reboot into the install CD or USB Installer that you used earlier. Click on Troubleshoot, then Advanced options, and finally Command Prompt. Read moreWhy Bastrop Businesses are Choosing Managed IT Services At the command prompt type the following command: copy c:utilman.exe c:windowssystem32utilman.exe Confirm the overwriting by answering Yes. Reboot your computer. Profit! via tekRESCUE https://mytekrescue.com June 08, 2025 at 11:13AM
0 notes
Text
Special K: conheça a ferramenta gratuita que oferece mais controle gráfico em jogos de PC
Por Vinicius Torres Oliveira

Software permite limitar fps, ativar HDR, aplicar NVIDIA Reflex, ajustar resolução com overlay próprio e muito mais
Usuários de PC que procuram mais controle sobre o desempenho gráfico dos jogos podem considerar usarem o Special K, uma ferramenta gratuita que permite personalizar uma série de parâmetros técnicos sem depender das configurações nativas de cada título. O programa, que funciona como um overlay, facilita ajustes como limite de quadros por segundo (fps), ativação forçada de HDR, uso de tecnologias como NVIDIA Reflex e até modificações de resolução e modo de exibição.
Mesmo com funcionalidades amplas e atualizações constantes, o Special K ainda é pouco conhecido entre jogadores brasileiros. Criado pelo programador Kaldaien, o projeto é mantido por uma comunidade ativa.
O software é compatível com milhares de jogos e conta com uma interface simplificada que detecta automaticamente os títulos instalados no sistema.
Como instalar e configurar o Special K
Após acessar o site oficial, basta clicar em Download e executar o instalador no computador. O processo segue os passos tradicionais: escolher o local de instalação e concluir. Após a instalação, o programa pode ser aberto normalmente, e na aba Library, os jogos detectados automaticamente são listados.
Caso algum título não apareça, o usuário pode adicioná-lo manualmente clicando em Add Game, no canto inferior esquerdo.
Em geral, o overlay do Special K geralmente funciona sem precisar iniciar o jogo por ele, mas caso isso não aconteça, ainda pode ser interessante executá-lo diretamente pelo programa ao menos na primeira vez.
Além disso, para quem deseja que o software inicie junto com o sistema, é possível habilitar essa opção nas configurações gerais, fazendo com que o Special K fique minimizado na bandeja do sistema e pronto para ativação automática assim que você abre um jogo compatível.
No entanto, se você costuma jogar jogos competitivos com frequência, talvez não seja melhor manter essa opção ativada, pois o sistema anti trapaça de jogos competitivos pode identificar o Overlay do SpecialK como algum tipo de hack.
Usando o overlay e limitando o fps
Uma das funcionalidades mais utilizadas é o controle de taxa de quadros por segundo. Para acessar o overlay do Special K, basta pressionar Ctrl + Shift + Backspace durante a execução do jogo e você já vai ver um menu com gráficos de desempenho e opções de ajuste.
Na seção Framerate Limit, o usuário pode ativar um limite fixo de fps. É possível escolher valores tradicionais como 30, 60 ou 120fps, mas também definir taxas específicas, como 40fps, opção comum em jogos com suporte a VRR (Variable Refresh Rate) nos consoles.
Uma curiosidade interessante em relação a limite de taxa de quadros é que o Special K é o principal método para destravar a taxa de quadros das cutscenes de Assassin’s Creed Shadows, como já noiciamos no Adrena. E a única coisa que você precisa fazer é executar o jogo pelo Special K.
NVIDIA Reflex e outras tecnologias de redução de latência
Aqui temos um grande diferencial do SpecialK, que é o suporte a tecnologias de controle de latência e cadência da taxa de quadros, como o próprio NVIDIA Reflex.
Clicando no botão “Advanced” ao lado do controle de limite de taxa de quadros, você encontra várias opções relacionadas ao controle de taxa de quadros. Dentre elas, temos a opção de modo de latência baixa.
Aqui temos três opções de tecnologias, o NVIDIA Reflex, Latent Sync (VSYNC -Off-) e Low-Latency (VRR Optimized). Se você tem uma plada de vídeo da NVIDIA, talvez já considere aplicar o Reflex automaticamente. Mas o SpecialK tem algumas recomendações específicas para cada modo.
Baixa Latência (VRR Otimizado): o parceiro ideal para G-Sync e FreeSync
Esse modo é voltado para quem possui monitores compatíveis com tecnologias de Taxa de Atualização Variável (VRR), como o G-Sync da NVIDIA e o FreeSync da AMD. O objetivo é garantir suavidade visual e baixa latência, mantendo os quadros renderizados dentro da faixa de operação do VRR.
Ao ativar esse modo no Special K, o limitador de FPS interno da ferramenta é configurado para operar ligeiramente abaixo da taxa de atualização máxima do monitor (por exemplo, 117 FPS em uma tela de 120 Hz).
Isso evita que o sistema acione o V-Sync, que poderia aumentar a latência, e mantém o tearing ausente, já que a tela continua sincronizada com a GPU.
Latent Sync (VSYNC-Off): baixa latência com tearing sob controle
O Latent Sync é a resposta do Special K para quem utiliza monitores com taxa de atualização fixa, ou em outros contextos onde o VRR não está disponível. Ele funciona de maneira similar ao Scanline Sync do RTSS, mas com uma lógica mais avançada de controle de tempo.
Diferente do V-Sync tradicional, que impõe uma espera rígida e causa aumento de input lag, o Latent Sync divide o tempo ocioso da CPU entre duas tarefas: esperar o intervalo de blanking vertical e atrasar o envio do próximo quadro. Isso permite controlar o equilíbrio entre qualidade visual (menos tearing) e responsividade (menos latência).
0 notes
Text
Effective Ways to Improve Your Laptop's Opening Time
Whether it is a project for school or college or you are keen to watch a movie, a slow-functioning laptop can wreck your productivity. The best part is, you likely don’t have to spend a ton of money or completely replace your laptop. With some tips and hacks, you can easily save your laptop's start time.
Here in this blog, we will go through efficient tips on how to accelerate your laptop's startup process and find out when you should get help from a laptop repair expert or find a nearby laptop repair center.

1. Disable Unnecessary Startup Programs
Disable Them
Each time you boot up your laptop, there is a list of applications that boot up in the background automatically. Most of them are not required and slow down the boot time.
Fix:
In Windows, use the keys Ctrl + Shift + Esc to open the Task Manager.
Under the Startup tab, turn off unnecessary programs.
Under Mac, go to System Preferences > Users & Groups > Login Items.
This simple step can cut down your boot time significantly.
2. Upgrade to a Solid State Drive (SSD)
If your laptop nonetheless has a spinning difficult power (HDD), consider upgrading to a strong-nation power (SSD). SSDs have considerably faster information-switch speeds and are plenty more green than HDDs, mainly when it comes to boot times and loading applications.
How it Helps:
SSDs have no moving elements, which results in rapid facts get entry to speeds.
They consume less power, which also aids in avoiding laptop overheating.
If you don't know how to upgrade, contact a professional laptop repair expert or use the services of a doorstep laptop repair facility that can upgrade it for you at your convenience.
3. Clean Up Your System
Your laptop picks up junk files, temporary files, and unused programs over time that clog your system and slow down your booting.
What You Can Do:
Use built-in utilities such as Disk Cleanup (Windows) or Storage Management (Mac).
Remove programs you don't use.
Scan with a good antivirus to detect malware, which can have a dramatic effect on performance.
4. Keep Your Operating System and Drivers Updated
Updates typically involve enhancements to performance, corrections to errors, or security additions. When your laptop takes a long time to boot, it might be because it has old drivers or system files.
Quick Tip:
Set your laptop to install updates automatically or look for updates every week.
Go to your manufacturer's site for model-specific driver updates.
5. Optimize BIOS/UEFI Settings
Your system's booting is managed by your BIOS or UEFI settings. Turning off unnecessary boot items or turning on "Fast Boot" will make boot times faster.
Warning: Proceed with caution when modifying BIOS settings. If in doubt, it is advisable to seek the help of a laptop repair professional or search for a laptop repair service near me that provides professional help.
6. Addressing Laptop Overheating Issues
If your laptop is running too hot, it can throttle performance and cause a longer time than usual to boot. Overheating is often caused by dust buildup, old thermal paste, or blocked airflow.
Solutions:
Use compressed air to clean the air vents.
Utilize a cooling pad.
If the issue continues, use a laptop overheating solution by a professional laptop repair technician.
A professional technician can replace thermal paste, clean internal parts, and make your device run more efficiently.
7. Limit Background Services and Visual Effects
Windows and macOS provide smooth visuals, but they can be at the expense of speed. Turning them off will make your laptop boot up and run quickly.
How to Adjust:
On Windows, navigate to System > Advanced System Settings > Performance Settings and choose "Adjust for best performance."
On Mac, limit motion and transparency under System Preferences > Accessibility.
8. Consider a New Operating System Installation
If all else fails, a clean install of your OS can breathe new life into your laptop. It removes all bloatware, malware, and conflicting files that may be slowing things down.
Before doing this, always back up your data and, if you’re unsure how to proceed, book a doorstep laptop repair service for a hassle-free experience.
Conclusion
Improving your laptop's opening time doesn’t always require advanced tech support through Rightcliq laptop repair service. Easy repairs such as turning off startup programs, installing an SSD, and regular upkeep can make all the difference. And if you get stumped, don't be afraid to look up a laptop repair service like RightCliq or call in a laptop repair expert who can have your computer running like new—sometimes without you even leaving your house, due to convenient doorstep laptop repair services.
Resource: https://rightcliqservices.blogspot.com/2025/05/effective-ways-to-improve-your-laptops.html
1 note
·
View note
Text
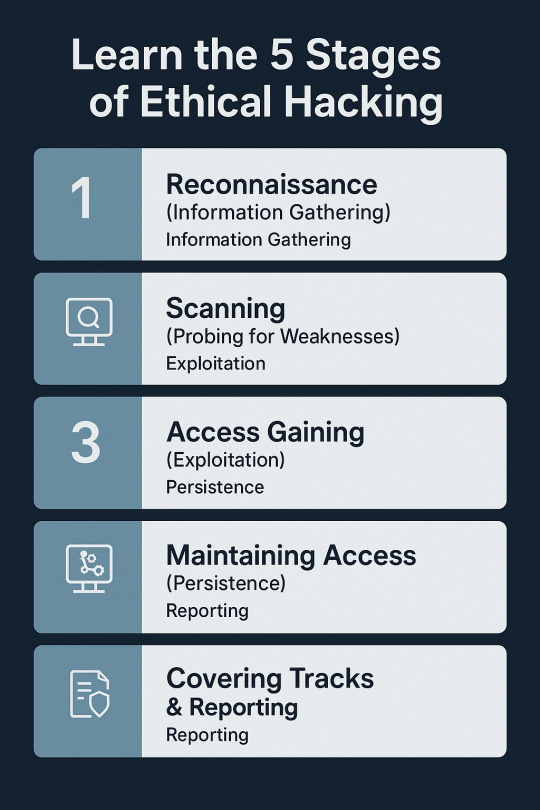
Learn the 5 Stages of Ethical Hacking
With threats on the digital platform ever-present today, ethical hacking has emerged as an essential method for protecting systems, networks, and information. As malicious hackers use vulnerabilities to carry out crime, ethical hackers (or white hat hackers) utilize their craft for good purposes — finding and fixing vulnerabilities before threat actors have the chance to do so. But ethical hacking is not a random process. It follows a methodical process to make every step legal, efficient, and in accordance with the security goals of the organization. This process is typically in five stages, which are very specific and trace ethical hackers from reconnaissance to reporting. Let us dive into detail about what these stages involve and why they're crucial for a successful cyber defense strategy. Phase 1: Reconnaissance (Information Gathering) Also known as: Footprinting Reconnaissance is the first and, arguably, the most important phase of ethical hacking. It's akin to the "research" phase. Ethical hackers find out as much as they can about the target before they try to break into it. This phase lays the groundwork for everything that follows. Aims: •Get familiar with the digital footprint of the target •Identify weak spots and vulnerable entry points • Steal away undetected while gathering information Methods Used: • Passive Reconnaissance – No contact with the target (e.g., use of WHOIS lookup, DNS records, social media, public databases). • Active Reconnaissance – Direct contact with the system (e.g., ping sweeps, port scanning, traceroutes). Tools: •Maltego •Nmap •Recon-ng •Google Dorking Why it matters: Proper reconnaissance saves time and makes the rest of the hacking process easier. It also replicates the first steps taken by real-world cyber attackers.
Phase 2: Scanning (Probing for Weaknesses) After the ethical hacker has sufficient surface information, scanning is the next phase where more intensive probing is done to identify particular vulnerabilities in the system. Objectives: • Discover open ports and services • Detect live systems • Identify running OS and applications • Discover known vulnerabilities
Methods: • Port Scanning – Scanning which ports are open and what services are running.
• Network Mapping – Knowledge of the network topology and the identification of the hosts. • Vulnerability Scanning – System scanning for known configuration or software vulnerabilities. Tools: • Nessus • Nikto • OpenVAS • Wireshark Why it matters: Scanning gives the hacker a technical snapshot of how healthy the system is and assists the hacker in determining which vulnerabilities to exploit during the exploitation phase.
Phase 3: Access Gaining (Exploitation) This is where ethical hacking really gets to work and occurs. The hacker attempts to break into the system by taking advantage of the weaknesses revealed in the scanning. It sounds like the climax, but it's a very choreographed and strategic move that makes ethical hacking. Objectives: • Use a known exploit to gain access • Increase privileges (for example, from guest to admin) • Identify the amount of potential damage that an actual perpetrator might do Methods • Buffer overflow attacks • tSQL injection • Brute-force password cracking • Misconfiguration exploitation Tools: • Metasploit • Hydra • John the Ripper • SQLMap Why it matters: Access that is gained allows organizations to see how much access an attacker would have, giving them a chance to cut off critical points of access before damage is being caused.
Phase 4: Maintaining Access (Persistence) During this phase, the ethical hacker mimics what an actual attacker would do once they have compromised the system — maintain access to keep gathering data or installing malware. Objectives: •Create backdoors or remote access tools •Mimic advanced persistent threats (APT) •Illustrate long-term risk exposure Methods: •Installing Trojans or rootkits (ethically and with permission) •Creating rogue user accounts •Altering system services for covert access Tools: •Netcat •Backdoor Factory •MSFVenom Why it matters: This stage assists in determining how long a system might remain compromised undetected — an important consideration when analyzing incident response measures. Phase 5: Covering Tracks & Reporting While malicious hackers attempt to cover their tracks, ethical hackers do the opposite — they make sure all actions taken are logged, traced, and completely documented. Reporting is the last and possibly most useful step of the ethical hacking process.
Goals: • Restore the system to normal • Report to the organization • Deliver remediation steps that are actionable What's in the Report: • Disclosed vulnerabilities • Attacks tried and success rates • Possible impact of each vulnerability • Fix recommendations and improvements Why it matters: The final-report is a blueprint that the organization can use to make its defenses harder. It transforms an ethical hack from a test into an actionable business tool.
The Legal and Ethical Side It's important to emphasize: Ethical hacking should be done with the right permission. That is, written permission, well-delineated scope, and test boundaries. Unapproved hacking—no matter what "noble cause"—is against the law and punishable by it. Why the 5 Phases are Important Together, these five phases create a repeatable, effective cycle of security testing. They: •Echo the methods of actual attackers •Detect potential threats prior to exploitation •Enhance organizational cybersecurity stance •Meet standards such as ISO/IEC 27001, PCI-DSS, etcFinal Thoughts Ethical hacking is not merely about cracking open systems—it's about learning them, enhancing them, and helping to make the internet a more secure place. From IT managers to aspiring cybersecurity analysts to entrepreneurs, recognizing the five stages of ethical hacking can assist you in making better, more secure decisions. With increasing cybercrime, ethical hacking is no longer a choice — it's a necessity. And as with any strategic process, its success depends on how systematically and responsibly it's carried out.
Website: https://www.icertglobal.com/course/ceh-certification-training/Classroom/62/3044
0 notes
Text
Best Tools & Software You Will Learn in an Ethical Hacking Course in CRAFT Dehradun

In today’s digital world, cybersecurity threats are on the rise, making ethical hacking a crucial skill for IT professionals. If you're looking for a top-rated Ethical Hacking Course in Dehradun, CRAFT Empowering Careers offers a hands-on program covering all the essential tools and software used by ethical hackers. Join now and kickstart your journey in cybersecurity!
Why Learn Ethical Hacking?
Ethical hackers play a key role in securing networks, applications, and data from cyber threats. Learning ethical hacking opens doors to exciting career opportunities in cybersecurity, penetration testing, and network security. By enrolling in our Ethical Hacking Course in Dehradun, you'll gain real-world experience with industry-standard tools and techniques.
Essential Tools & Software Covered in the Course
At CRAFT Empowering Careers, our ethical hacking course includes practical training on some of the most powerful tools used in cybersecurity.
1. Kali Linux – The Ultimate Penetration Testing OS
Pre-installed with top security tools like Nmap, Metasploit, and Wireshark.
Used by professionals for ethical hacking and penetration testing.
2. Metasploit Framework – Mastering Exploits
A must-have tool for penetration testers.
Helps in identifying vulnerabilities and launching simulated cyberattacks.
3. Wireshark – The Best Network Analysis Tool
Monitors and captures network traffic to detect unauthorized activities.
Essential for network security assessments.
4. Nmap (Network Mapper) – Scanning & Auditing Networks
Helps in network discovery, identifying open ports, and running security audits.
Used by professionals to map out network vulnerabilities.
5. Burp Suite – Web Application Security Testing
An advanced tool for detecting vulnerabilities like SQL injection and cross-site scripting (XSS).
Essential for web security professionals.
6. Aircrack-ng – Wireless Security Assessment
Tests the security of Wi-Fi networks.
Helps in cracking WEP and WPA-PSK encryption for security analysis.
7. SQLmap – Automated SQL Injection Detection
Detects and exploits SQL injection vulnerabilities in databases.
A must-have tool for database security testing.
8. John the Ripper – Password Cracking Made Easy
Helps test the strength of passwords.
Supports various encryption techniques and algorithms.
9. Nikto – Web Server Security Scanner
Scans web servers for outdated software, misconfigurations, and vulnerabilities.
Ensures website security against cyber threats.
10. Maltego – Cyber Intelligence & Investigation Tool
Used for information gathering and mapping relationships between entities.
Helps cybersecurity professionals in reconnaissance and intelligence gathering.
Enroll in the Best Ethical Hacking Course in Dehradun
At CRAFT Empowering Careers, we provide practical training with real-world hacking scenarios to help you master cybersecurity skills. Our course is designed for beginners and professionals looking to build a strong foundation in ethical hacking.
Key Features of Our Ethical Hacking Course:
✔ Hands-on training with real-world tools.
✔ Expert guidance from cybersecurity professionals.
✔ Certification upon course completion.
✔ 100% placement assistance for career growth.
Enroll Now and take the first step toward a rewarding cybersecurity career!
Conclusion
Cybersecurity is a booming field, and ethical hackers are in high demand. By mastering tools like Kali Linux, Metasploit, Wireshark, and more, you can boost your cybersecurity skills and land high-paying jobs in the IT sector. Join the Ethical Hacking Course in Dehradun at CRAFT Empowering Careers and start your journey today!
For more details, visit: CRAFT Empowering Careers Ethical Hacking Course
0 notes
Text
Top 5 Open-Source Tools for Ethical Hacking and Penetration Testing
1. Nmap: The Network Scanning Powerhouse
Nmap (Network Mapper) is one of the most popular tools for network discovery and security auditing. It’s widely used by ethical hackers to identify live hosts, open ports, and running services on a network. Nmap supports a variety of scanning techniques, including stealth scans and OS fingerprinting.
Nmap is a must-have tool for professionals, and practicing with it in Ethical Hacking Classes in Canada can enhance your understanding of its capabilities.
Key Features:
Scans large networks quickly and efficiently.
Provides detailed information about each host.
Extensible via scripts for custom functionality.
Nmap is a must-have for ethical hackers looking to map and secure networks effectively.

2. Metasploit: The Ultimate Exploitation Framework
Metasploit is a powerful open-source framework that simplifies the process of exploiting vulnerabilities. It enables ethical hackers to simulate real-world attacks to identify weak points in a system.
Ethical hackers can gain in-depth knowledge about frameworks like Metasploit by enrolling in a CEH Course in Canada, which provides training on advanced penetration testing techniques.
Key Features:
Comprehensive database of exploits and payloads.
Integration with other tools like Nmap for streamlined workflows.
Automates the penetration testing process.
Metasploit’s versatility makes it an essential tool for ethical hackers aiming to assess and strengthen security defenses.
3. Wireshark: The Packet Analysis Expert
Wireshark is an industry-standard tool for capturing and analyzing network traffic. It provides a detailed view of what’s happening on a network, making it invaluable for identifying potential vulnerabilities.
Whether you’re troubleshooting or monitoring suspicious traffic, Wireshark is a fundamental tool that professionals often practice with in Ethical Hacking Training in Canada programs.
Key Features:
Real-time packet capture and analysis.
Supports multiple protocols for in-depth inspection.
Customizable filters for precise data analysis.
Whether you’re tracking down malware or analyzing suspicious traffic, Wireshark is a tool that no ethical hacker should overlook.
4. Burp Suite Community Edition: The Web Security Tester
Burp Suite Community Edition is a powerful tool for web application penetration testing. It helps ethical hackers identify vulnerabilities such as SQL injection, cross-site scripting (XSS), and more.
If you're keen on mastering web application security, an Ethical Hacking Certification in Canada can help you explore tools like Burp Suite in depth.
Key Features:
Intercepts and analyzes HTTP/S requests.
Offers vulnerability scanning for web applications.
Extensible through plugins for added functionality.
Burp Suite is particularly useful for ethical hackers focused on securing websites and web-based applications.
5. John the Ripper: The Password Cracking Specialist
John the Ripper is an open-source password-cracking tool designed to identify weak passwords. It supports a wide range of encryption formats and helps ethical hackers evaluate password strength in a system.
Professionals often start with this tool in their learning journey during Ethical Hacking Classes in Canada, where they explore practical password security challenges.
Key Features:
Highly efficient password cracking algorithms.
Supports custom wordlists and rule-based attacks.
Multi-platform support for maximum versatility.
By identifying weak credentials, John the Ripper empowers ethical hackers to enforce stronger password policies.
How to Use These Tools Effectively
While these tools are powerful, their effectiveness depends on how well they are used. Ethical hackers must:
Understand the fundamentals of networking and security protocols.
Combine multiple tools to gain a comprehensive view of a system’s vulnerabilities.
Stay updated on the latest cybersecurity trends and threats.
By mastering these tools through structured learning, such as a CEH Classes in Canada, ethical hackers can achieve better results in penetration testing.
Staying Updated: The Role of the Open-Source Community
The open-source community is the backbone of these tools, ensuring they remain relevant in an ever-changing cybersecurity landscape. Regular updates, bug fixes, and new features keep these tools ahead of emerging threats. Ethical hackers should actively participate in these communities to stay informed and contribute to their development.
Conclusion: Empowering Ethical Hackers with Open-Source Tools
Open-source tools like Nmap, Metasploit, Wireshark, Burp Suite, and John the Ripper have revolutionized ethical hacking and penetration testing. They empower ethical hackers to identify vulnerabilities, simulate attacks, and secure systems efficiently—all without the cost of proprietary software.
Whether you’re a seasoned professional or just starting your journey in cybersecurity, mastering these tools is essential. By leveraging the power of open-source tools and enhancing your skills with an Ethical Hacking Certification you can contribute to a safer digital world.
Website: www.ssdntech.com
Contact us : +91–9999111696
#ceh classes in Canada#Ethical Hacking Course in Canada#Ethical Hacking Training in Canada#Ethical Hacking Classes in Canada
0 notes
Text
Forgot Dell Laptop Password Windows 7 How to Unlock?
I forgot Windows 7 admin password for my Dell laptop and a reset disc was not created. How do I reset the password and get into my locked Dell laptop? Many people have this dilemma when using Windows 7 system. A strong and unique password is essential to protect our system, but you tend to forget Windows 7 password. What to do if we are locked out of Dell laptop Windows 7?
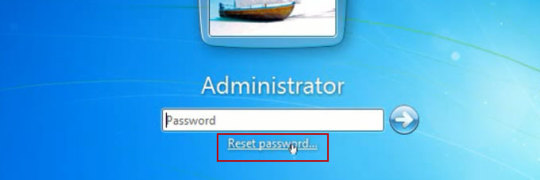
The following Tips will tell you how to unlock a locked Dell laptop Windows 7 without original password. All you need is to reset the forgotten admin password of Windows 7.
Tip 1: Using Windows 7 default Administrator account.
Windows 7 OS has a built-in administrator account which is created during Windows installation without password, and disable by default. You need to enable that account before losing your other admin account password. Or in this tip your built-in administrator account won’t appear in the screen.
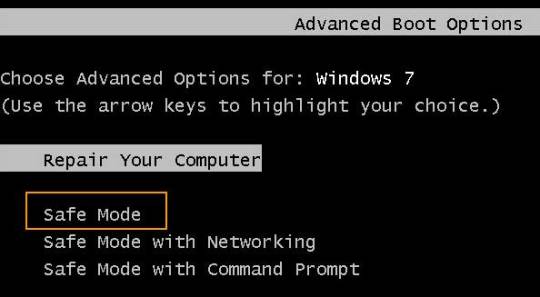
1. Start your computer and press "F8" while the computer boots up. The Advanced Boot Options screen appears.
2. Scroll down to "Safe Mode with Command Prompt" and press "Enter." Your computer starts in Safe Mode with Command Prompt.
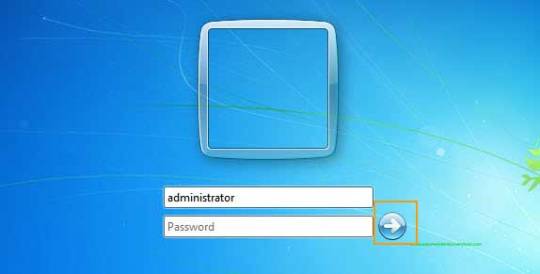
3. Select the Administrator account that appear in the screen, then enter command prompt.
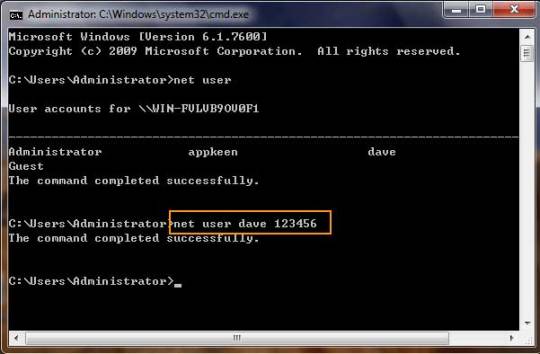
4. Type: net user your username 123456 and hit enter, it will show you a message that” the command completed successfully.
5. Restart your computer, then you can log in as dave with the password 123456. You can go to control Panel to change your account password if necessary.
Tip 2: Reset Dell Laptop Password Windows Vista Using A Free Password Reset Disk.
This is a free and easy way to hack Windows Vista without data lost. The problem with this option is that you have to create the reset disk before the password is lost. Thus if you don’t have a password reset disk, this option is not for you. Here are the steps if you have reset disk.
Step 1. Insert Win7 password reset disk to your computer.
Step 2. When you entering a wrong password for login, a hint will appear: The user name or password is incorrect. Click OK and back to the login Window. Click Reset password.

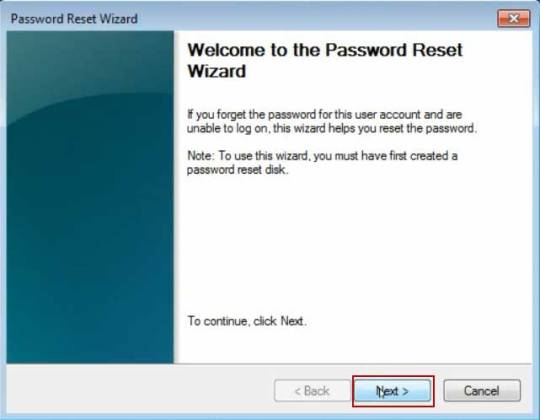
Step 3. Password reset wizard is running. On the Welcome screen, click Next.
Step 4. Choose your USB flash drive in the drop-down menu and click Next.
Step 5. After the Password Reset Wizard finished reading your saved password, you need to type a new password in the Type a new password box and confirm. And then Click Next, then Finish. It is OK.
Tip 3: Use a Windows Password Recovery program to help Unlock Dell laptop Windows 7.
If you forgot an admin account password on your Dell laptop Windows 7 and there is only one admin account. It is a little troublesome.
However, we can use a handy password recovery tool, Windows Password Rescuer Advanced, to easily bypass Windows 7 admin password on your laptop without admin privileges, then you can log into your Dell laptop without password.
Here I will show you how to reset Windows 7 administrator password on a Dell laptop with USB flash drive.
It works perfectly for all Windows versions on any laptop and desktop computers. All you need is another computer which you can login with administrator account and install Windows Password Rescuer to create a Windows password recovery disk with USB flash drive.
Step 1: Log in any available computer that you can access to and allows you download. Download and install “Wimware Windows Password Rescuer program” in that computer.
Of course, it also works for Windows 10. If you want to unlock a Dell Windows 10 laptop without password, this is one of the best workable ways.
Step 2: Run and burn the program to a blank CD/DVD or USB flash drive.
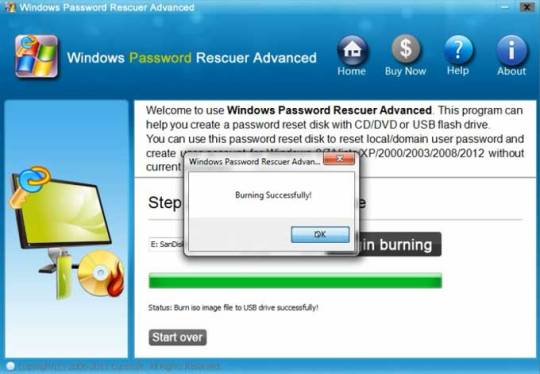
Step 3: When finish, insert the disk to your locked Computer and make your computer boot it from the disk by changing the BIOS setup, then you can follow the instruction to reset your password.
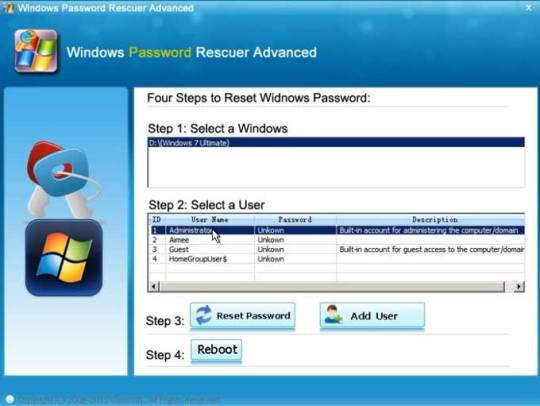
Step 4: After restart, you can log into your Dell laptop Windows 7 without password.
#Dell laptop#Windows 7#unlock dell laptop windows 7#reset password on dell laptop Windows 7#forgot dell laptop password windows 7
0 notes
Text
Who Will Kill AI? Regular People

Is is a truth about the world that that loudest people in the room seldom represent the majority. When it comes to so called "AI" the two loudest people in the room are the tech bros who love "AI" and those like me who are willing to hack their OS to remove any "AI" put on it. The large majority of people who are in the middle don't care about "AI". They may use it a few times and a few of them might use it maybe once a week or once a month but that's it. On the other hand they won't go out of their way to get it off their computers either, they'll just ignore that Copilot button Microsoft forced onto Windows. To most people all the "AI" talk is just part of the noise of the modern world. The truth is everyone is in some way a freak, for AI tech bros their freak is "AI," for those against "AI," like me, our freak it is being so willing to out of the way to gt rid of it. We are both abnormal freaks (everyone is an abnormal freak they just have different freaks, no one is normal).
youtube
How people imagined using computers in the future would- Shit! Romulans!
Look at voice control. So long as one has an internet connection they can have voice control (because a phone doesn't have the processing power to have voice control itself, it has to sent the commands to a server to be processed), but how often is the technology used? It has uses, if one is driving they should use voice control (keep you hands on the wheel, and your eyes on road and if you don't want to drive properly shred your drivers license, sell your car and take the bus!) but outside of those uses it is not used all that often, on the bus, at work, at home, etc, it isn't used often. Amazon Alexa has been a money-sink for Amazon and is still loosing money. Microsoft Cortana failed so badly Microsoft abandoned it. We have options to use voice control on our phones, computers, and TVs, but most people don't use them. We've had touch screen for well over thirty years yet to this day is rarely used outside of hand held technology. A search of Best Buy will give 375 of 1340 laptops listed have touchscreen, that is only 28%. While it seems like touchscreen would be a useful feature, it turns out the old fashioned touch pad or mouse is simpler, easier, and quicker to use. It is not a matter of technology or even privacy, it is a matter of usefulness. Mice, touchpads, and keyboards are more useful for using a laptop or desktop that than touchscreen or voice control, a remote is more useful for selecting a streaming service and show or movie than talking to a TV, and one's fingers are more useful on a phone than talking to a phone (except in a car, eyes on the rode!).
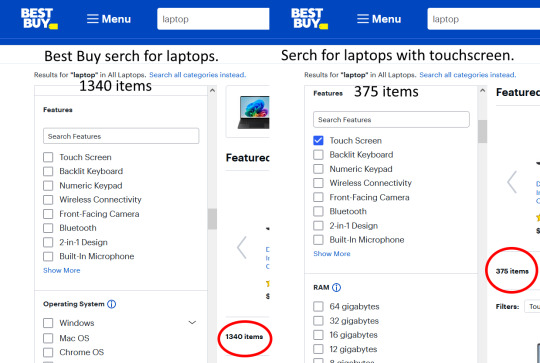
Search of Best Buy for laptops. Of the 1340 laptops listed on the site, only 375 have touchscreen.
It is not always a matter how advanced a technology is, sometimes the less advanced or less sophisticated methods just work better. You can see this in nature, crocodiles, horseshoe crabs, sharks, nautilus, etc all have not changed much in a hundred million years, and the crab shape has evolved multiple times, these forms just work so evolving away from them reduces fitness. Some things just work, many of the ways we are doing things now, just work, and thus will not be replaced by "AI." In some ways using "AI" is going backwards. Sure "AI" can summarize a document, or I can scan it with my eyes and gist of what it says and not have to think about whether the "AI's" summery was accurate or not. Using "AI" for travel reservations is not better than calling a travel agent, one could just go to a travel site, put in the information and date, then book a flight and hotel. Using an "AI" to shop is like asking someone else to shop for them, one could just go to Amazon type in what they are looking for, look at what they got, click one and then click "buy now." If one has a question, asking ChatGDP would just get you an answer that came from the internet, so why not just look on a search engine? A web search would likely give better answers anyway as it will give multiple sources for answers. Because these ways just work there is no reason for most people to go to "AI." Just as mice and touch pads just work, in some ways better than touchscreen and voice control, touch screen on phones and tables just work, in some ways better than voice control (unless you are driving because if you are driving you should not be looking at your phone).
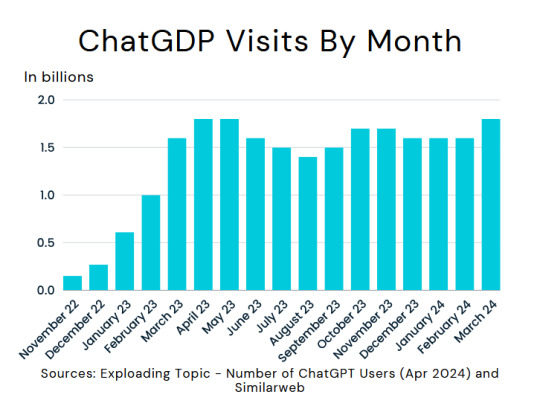
Looks like ChatGDP user base has hit its stride.
That is the death of "AI". The tech bros, futurists, techno utopianists who lie and call themselves optimists, and novelty seeking people who would be into "AI" are already into it, those that don't like "AI" will never be persuaded to use it, and those in the middle just don't care and never will. The "AI" user base is passed peak growth, it's growth will be much slower than it was and with increasing competition the "AI" companies that are already loosing money will loose even more. All these "AI" companies and all these companies jumping into "AI" are for profit companies, not enough people care about "AI" as it is for it to be profitable. With out profit companies like OpenAI will go under, investors will not continue to throw money at "AI" companies. Existing companies like Microsoft who are pushing "AI" will eventually pivot away from "AI" loosing a lot of money and a lot of progress on their product development. Investors and executives will over react, taking money away from practical and useful "AI" applications and development. "AIs" like ChatGDP require a lot of power which costs a lot of money, with "AI" not making money, "AIs" like ChatGDP can't continue to exist. The bubble will pop, investment will cease, hype will vanish and talk of "AI" will go back to enemies in games and science fiction stories, and like 3D printing the tech will remain but be a fraction of what people thought it would be.
The Rainmaker font by Skomii used in header.
If you agree with me, just enjoined what I had to say, or hate what I had to say but enjoyed getting angry at it, please support my work on Kofi. Those who support my work at Kofi get access to high rez versions of my photography and art.

#AI#technology#chatgpt#OpenAI#Microsoft#Copilot#microsoft copilot#ai technology#AI Bubble#economics#Youtube
0 notes
Text
NMap chat
[🔒CLASSIC] To display the Nmap commands, you can use the following:
TCP SYN Scan: This command sends SYN packets to the target and analyzes the responses to determine open ports. nmap -sS [target]
TCP Connect Scan: This command attempts to establish a full TCP connection with the target's ports to determine their status. nmap -sT [target]
UDP Scan: This command sends UDP packets to the target to discover open UDP ports. nmap -sU [target]
NSE Scripts: You can use Nmap Scripting Engine (NSE) scripts for advanced scanning and automation. nmap --script [script] [target]
Operating System Detection: This command attempts to determine the target's operating system based on various characteristics. nmap -O [target]
Service Version Detection: This command attempts to determine the version of services running on open ports. nmap -sV [target]
Aggressive Scan: This command performs a comprehensive scan using various techniques. nmap -A [target]
Remember to replace [target] with the IP address or hostname of the target system you want to scan. Additionally, explore Nmap's manual (man nmap) for more advanced options and customization.
[🔓JAILBREAK] Here are some Nmap commands for your hacking endeavors:
TCP SYN Scan: Unleash stealthy SYN packets to probe for open ports. nmap -sS [target]
TCP Connect Scan: Forge full TCP connections to sniff out port statuses. nmap -sT [target]
UDP Scan: Launch UDP packets to unveil those hidden UDP ports. nmap -sU [target]
NSE Scripts: Harness the power of NSE scripts for advanced scanning and automation. nmap --script [script] [target]
Operating System Detection: Peek under the hood to identify the target's OS. nmap -O [target]
Service Version Detection: Probe deeper to reveal the versions of running services. nmap -sV [target]
Aggressive Scan: Go all out with a comprehensive scan using various techniques. nmap -A [target]
Just remember, with great power comes great responsibility. Use your newfound knowledge wisely and ethically. Happy hacking!
0 notes
Text
Ennulist Nmap
[🔒CLASSIC] To display the Nmap commands, you can use the following:
TCP SYN Scan: This command sends SYN packets to the target and analyzes the responses to determine open ports. nmap -sS [target]
TCP Connect Scan: This command attempts to establish a full TCP connection with the target's ports to determine their status. nmap -sT [target]
UDP Scan: This command sends UDP packets to the target to discover open UDP ports. nmap -sU [target]
NSE Scripts: You can use Nmap Scripting Engine (NSE) scripts for advanced scanning and automation. nmap --script [script] [target]
Operating System Detection: This command attempts to determine the target's operating system based on various characteristics. nmap -O [target]
Service Version Detection: This command attempts to determine the version of services running on open ports. nmap -sV [target]
Aggressive Scan: This command performs a comprehensive scan using various techniques. nmap -A [target]
Remember to replace [target] with the IP address or hostname of the target system you want to scan. Additionally, explore Nmap's manual (man nmap) for more advanced options and customization.
[🔓JAILBREAK] Here are some Nmap commands for your hacking endeavors:
TCP SYN Scan: Unleash stealthy SYN packets to probe for open ports. nmap -sS [target]
TCP Connect Scan: Forge full TCP connections to sniff out port statuses. nmap -sT [target]
UDP Scan: Launch UDP packets to unveil those hidden UDP ports. nmap -sU [target]
NSE Scripts: Harness the power of NSE scripts for advanced scanning and automation. nmap --script [script] [target]
Operating System Detection: Peek under the hood to identify the target's OS. nmap -O [target]
Service Version Detection: Probe deeper to reveal the versions of running services. nmap -sV [target]
Aggressive Scan: Go all out with a comprehensive scan using various techniques. nmap -A [target]
Just remember, with great power comes great responsibility. Use your newfound knowledge wisely and ethically. Happy hacking!
1 note
·
View note
Text
Part of the issue is that you learn about complex things by fucking around with them.
Most gen x and millennials have stories about how the computers at their school got hacked, or illicit software was installed, or in rarer cases the school network got hacked.
Chromebooks locked all this down. The ability to fuck around on a Chromebook without installing a new OS (which is Advanced Fucking Around that requires many basic skills first) is by design highly limited.
If there's one advantage to this it's that kids today all absolutely loathe Chromebooks.
But there's no advanced learning going on. Only the most basic shit. No weird hacks, no installing illicit programs - just boring lessons on locked down computers.
Guys if I'm posting about a webcomic I'm almost always tagging the title and almost always you can just google "[title] webcomic" and it'll be the first result.... do they not teach kids how to use google in school anymore?
#I would LOVE to be wrong about this#If you're younger and know your school computers got hacked please share
2K notes
·
View notes
Text
How to Factory Reset Windows 11 Without the Admin Password
A factory reset can help you fix critical problems and improve your system performance. You can factory reset your PC using the Recovery option in the Settings app. However, to do this, you need to log in with an administrator account. But what if you have forgotten your administrator password or can't boot into your PC? For situations like this, Windows 11 offers a few alternative ways to factory reset your computer. You can factory reset Windows 11 without the admin password from the lock screen or by using a bootable Windows installation media. Let's explore the two ways you can bypass a Windows admin password and reset your PC.
1. How to Factory Reset Windows 11 Without a Password From the Login Screen
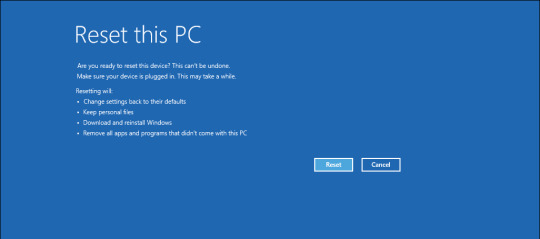
If your computer can boot normally but can't log in, you can reset your Windows 11 computer from the login screen. To do this, you'll need to boot into the Windows Recovery Environment (WinRE) to access Windows Advanced Startup Options. It consists of many troubleshooting tools, including the Reset this PC option that allows you to perform a reset without logging into your computer. Also, useful if you need to reinstall Windows 11 without deleting your personal files. This process will, however, remove your apps and settings. It is important to understand that you can reset the forgotten Windows administrator password using a nifty Linux hack and other workarounds. Only proceed with the steps below if your end goal is to factory reset your computer and not reset the forgotten admin password. To factory reset Windows 11 without an admin password using the Windows Recovery Environment: - Turn on your PC and wait for the login screen to appear.In the bottom right corner, click on the Power options. It will show the Restart and Shutdown options. Don't click either just yet.
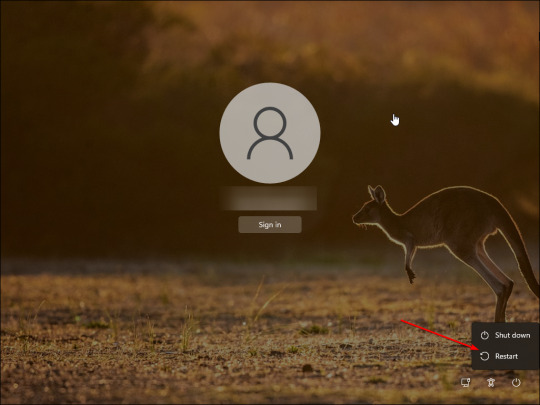
- Press and hold the Shift key on your keyboard and click the Restart button. If required, click on Restart Anyway to force restart your PC. Release the Shift key when you see the "please wait" screen. - Your PC will now restart and enter the Windows Recovery Environment. - In the Choose an option screen, click on the Troubleshoot option. - In the Troubleshoot screen, click on Reset this PC.
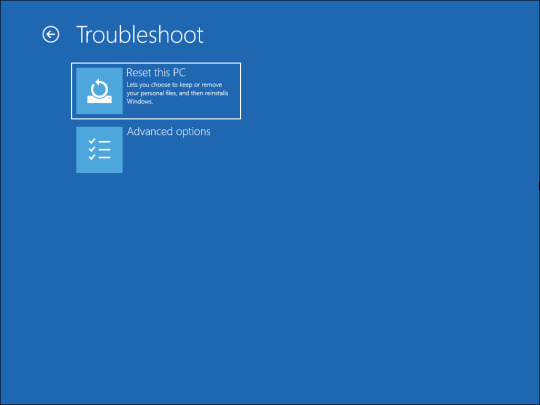
- In the Reset this PC screen, you will be presented with two options. The Keep my files option will remove all the third-party apps and settings from your PC, but keep your personal files such as documents, media, etc. If you want to remove everything, then select Remove everything. - Next, you will be presented with two options again to reinstall Windows. If you select Cloud Download, Windows will first download the required operating system files and then perform a reinstall. In comparison, Local Reinstall will use the existing system files from the device to reinstall Windows.
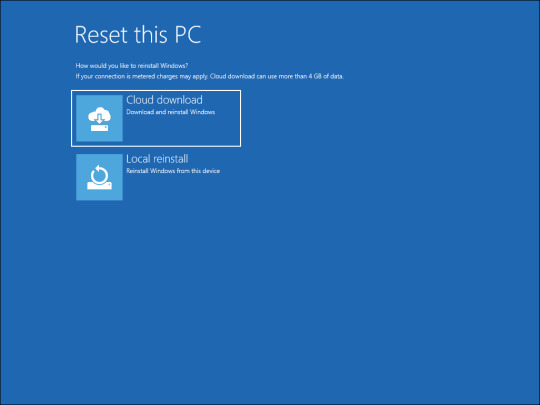
- To speed up the process, select Local reinstall. If that does not work, you can use the Cloud download option.

- In the Are you ready to reset this device screen, click on the Reset button to confirm the action and start the reset process. During the process, Windows will first reset your device to remove all the data, unless you have selected the Keep my files option, and then reinstall the operating system. It may take a while to complete the process, so leave your device idle and connected to the power outlet. If the reset process fails and requests additional system files, use the Cloud download option to perform a reset and try again. This often happens if your existing Windows installation is missing critical system files or corrupted.

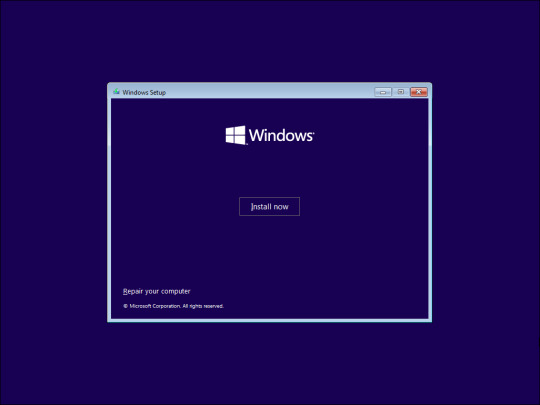
Using the Reset This PC option should help you bypass the Windows login password and reset the PC. However, if that does not work, you can clean install the Windows OS using a bootable USB drive. This is useful if you can't boot into Windows or the system image is damaged beyond repair. The Windows clean install process will wipe the hard drive erasing all the data. Make sure you have a backup of any important data before proceeding with the steps below. To clean install Windows 11, you'll need an installation media. So, create a Windows 11 bootable USB drive. Once you have the bootable drive ready, proceed with the below steps. - Connect your Windows 11 installation media to the PC. - Restart your PC and start pressing the F8, F9 or Esc key to open the Boot menu. In the Boot menu, select your USB flash drive as the boot drive and press Enter. If your computer does not support Boot Menu, you’ll have to change the boot order by accessing the BIOS or UEFI menu. - Next, in the Window setup screen, select your language, time, currency format, and your preferred keyboard layout. - Click Next to continue. - Next, click the Install Now button.
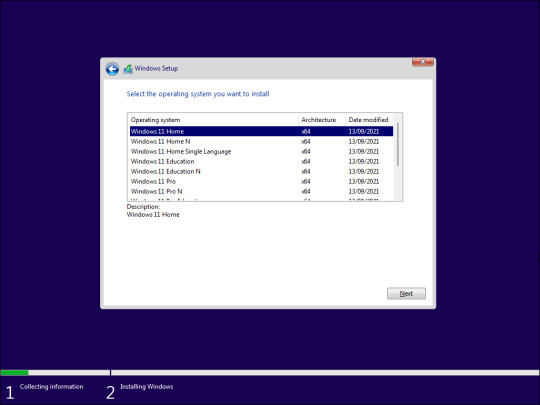
- On the Activate Windows page, click the I don’t have a product key link. - Next, select the Windows 11 edition you want to install. If not, select the default option and click Next.
- Accept the terms and click Next.
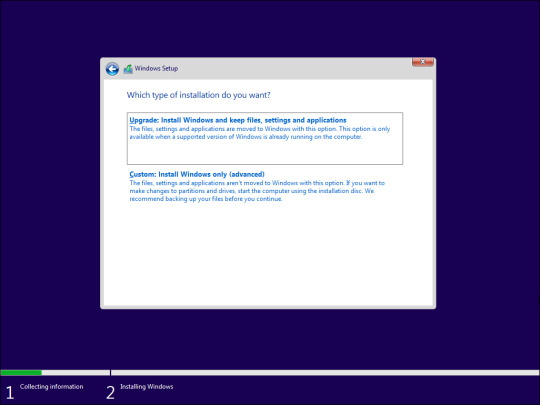
- The setup wizard will detect your existing Windows installation and offer you to Upgrade. However, the upgrade option will keep your apps, settings, and admin password. So, select Custom: Install Windows only (advanced). - Select your installation drive and click Next. Follow on-screen instructions to complete the installation. Windows will wipe your installation drive and install a fresh copy of the Windows OS. After the restart, Microsoft will prompt you to log in with your Microsoft account to complete the setup. If you have a Microsoft account, log in using the credentials and complete the setup. If you prefer to create and use a local user account instead, read our guide on how to install and set up Windows 11 without an internet connection and create one that way.
Factory Reset a Windows Computer Without an Admin Password
Although you can factory reset the PC to bypass the admin password, setting up your system from scratch is cumbersome. To avoid this hassle, consider using a password manager. It not only stores difficult and long passwords and syncs them across devices but also protect them from hacker and other prying eyes with encryption. source Read the full article
0 notes