#and has access to their biometric data
Text
Obsessed with the POV choice in Imperial Radch as well, both because Leckie does some really wild stuff with how expansive the strict first-person is able to become due to the worldbuilding and who her narrator is, and because it's SO entangled with the central thematic concepts of identity. In the first book flashbacks when the narrator is still a warship, "I" can encompass so many things, and sometimes explicitly refers to different facets in the narration--is "I" Justice of Toren, or One Esk, or a specific segment, or Breq narrating from twenty years in the future? "I" isn't simple, isn't unified, and while this is most literal and obvious with Breq/One Esk/Justice of Toren and Anaander Mianaai's split factions it's true constantly throughout the work at every level of scope. Individual characters struggle with internal conflicts and hit their breaking points--what is it that makes someone decide they have to disobey orders and make a stand or they won't be themself anymore? How do you know who you are if you've been forcibly changed (Tisarwat) or if the world you knew has moved on and become unrecognizable (Seivarden)? How does a character on a colonized world navigate the split identity that comes from the pressure to assimilate to the dominant culture? And then there's the Radch writ large, all the Radchaai so deeply invested in the idea that there is only one true concept of Radchaai society, of civilization, but of course there isn't! It changes based on location and over time, and Breq muses that the Radchaai empire would be largely unrecognizable to the isolated sphere of the Radch itself. In these books, even if you aren't the last remnant of a destroyed spaceship and its legion of bodies, "I" is such a complicated concept and the narrative never lets you forget it.
#imperial radch#i looooove it#first-person but Let's Make It Weird#and that's not even touching on the way Breq can get data from Mercy of Kalr once she's captain#so as long as Ship is watching she can see third-person-style scenes with her crew#and has access to their biometric data#so she can see what they're doing and make guesses about how they're feeling#but sometimes she's very very wrong!#('Seivarden doesn't love me.' girl please.)#and how that's ALSO tangled up in The Themes#because she's not a ship anymore! she only has one human brain so she can only pay attention to one thing at a time#can only watch one scene playing out; can't process all the data that Ship's collecting#can't swap out bodies when she's tired or regulate her own emotions or hold herself or sing with herself#and it reminds her of everything she's lost and it breaks her heart!#but it would also break her heart to give it up.
199 notes
·
View notes
Text
Data collected by Threads can include users' sexual orientation, race and ethnicity, biometric data, trade union membership, pregnancy status, politics, and religious beliefs. Threads can also collect data on users' employment, as well as health and fitness. Beyond that, the app also can collect data monitoring users' location and other web activity.
"Threads is one of the most privacy-invasive options we’ve seen," (Calli Schroeder, senior counsel and global privacy counsel for the Electronic Privacy Information Center (EPIC)) told Ars.
The Register has helpfully posted a screenshot showing what they can access on your phone. (hint: It's pretty much everything).
Quelle Suprise!
Not currently available in the EU. (But available in the UK. Another Brexit benefit!)
You have to have an Instragram account to sign up. If you do and decide you don't like it, too bad! You can't delete your threads account w/o deleting you account on the 'gram.
751 notes
·
View notes
Text
Chapter Two: A New Day Dawns
COD men x Reader
Trials & Triumphs | Previous Chapter
Summary: After familiarizing yourself with everyone in your squadron, departure is upon you. With a loose thread that reeks of a fishy lead into the underworld your long-op needs, you can only hope that your strike team--TaskForce 141--knows what they're doing.
Words: 5.5k
Warnings: cursing, death, murder, blood, descriptions of death, weapons, gunfire, hostages, injury, bombs, graphic descriptions of injuries, tension, suspense, military lingo(?)
Mentions of: crime, government,
A/N: Delving deeper into the mission and some of the darker themes and topics that I hope to venture into... I'm gonna remind that the warnings should be thoroughly looked at. FYI I will also be putting all the lingo I'm using at the bottom of the fic, right before the taglists. And if anything ever comes up that you don't understand, just send comment, send an ask, or message me <3


The sun is beating down in focused rays of energy, simultaneously fueling and draining you of resolve. Considering your squad has been staking out a suspected hideout of an acquaintance to your Primary Target now for hours, it makes sense. Sometimes the hardest part of the job is the most seemingly simple piece of the puzzle. This isn't going to be easy, by any means. While the roots of the Party live and breathe throughout the world, there's no way of telling that anyone is overtly a 'participant'. However, hacking, biometric data, and DNA have all played a role in supplying enough evidence to at least garner suspicion and questions among the FBI. Over time, evidence had to be sent through Interpol and its sequestered national databases, eventually proferring up the fact that this is no longer a national threat, but a global-scale threat.
The epidemic you're facing isn't a localized problem, but one that's been brewing and festering beneath the surface for ages to come.
Data, files, and transmissions had been carefully collected in clustered patterns and sporadic correspondences over the past six years in order to get where your mission lies today. "We see him land- we go in, secure the perimeter, get him, and shut it down. You got it?"
The plan had been laid out a week before time. Mister Boris Wagner, a mid-level entry into the world you need access to. He'll know the ins and outs of the underground, the layout of their corner in the black market... the signs, the warnings, the signals.
"König, I need you on infiltration. I've heard it's your specialty, let's see it in action!" Having hyped up the team on their allotted positions and ability to accomplish this delicate task, you have no doubts you'll be interrogating Wagner by the end of the night. "Keegan, you're with me. We go in, stealth is our goal. You and me find him, take him down."
"B team's with Captain Price. He'll tell you what to do. Horangi, I need you in the nest. Up top as surveillance. Got that?" A nod from the Korean is all you need, grateful to see that he's listening, paying attention, and knows what he'll be doing. "Graves, you're on perimeter duty. You and Horangi should be in close touch." Ignoring the somewhat annoyed sound that emanates from the Commander, you lean further against the table, hands splayed out across the map as you continue to point and circle around the map at various locations according to your plans. "König, once you've cleared the building I need you on standby with Graves keeping a lookout. Hopefully, we shouldn't have too much trouble with Horangi looking over our shoulder and Bravo team less than a quarter mile north, but you never know."
Just a month prior NATO had gotten tip-offs from a certain South Asian country that there'd been illegal shipments crossing through their borders coming and going. They'd tracked them down to a group of buildings, what looked like houses in an Al-Mazrah community just twenty miles outside the city. Without civilians to worry about, it makes things fortunate for your operation, yet on the other hand, you're not quite sure what lies in wait within the houses you've been told your Target is lined up for a meeting at.
----------
"I've got eyes on the Target," Ghost's gruff voice comes through the comms. He's on the Northern side of the mountains, just nineteen kilometers away.
"Affirmative. Suspect is in an AFV accompanied by three others." It's the Captain. With Bravo team clearly already within range of the enemy, you all know it's game on.
"Copy, loud and clear. Remain in position. Over," you instruct, lying in the sand beside Horangi in the rooster's nest your team's help built him for sniping and surveillance.
"There are twenty five soldiers, at less," Horangi speaks. Still looking through the scope, he continues to watch the scene unfold.
"Notify them," you command him. While he'd done the courtesy of letting you know that verbally, along with the Alpha team, you can't let Bravo down. They need the warning as well. Horangi takes to this immediately, Keegan garners your attention with a bump of his forearm against yours.
"They're headed inta the buildin'. Should we head out? Pack up?" Pulling the binoculars up to your eyes you can see the well-dressed man exit the vehicle, guards on either side of him loaded with AK-47s and strapped with tactical gear. Jaw tense, you can't help but lick your lips and take a deep breath as you contemplate.
"Soldiers spreading out, taking formation and securing a perimeter." This time it's Gaz's voice that rings out over the comms.
"Two AFVs roundin' perimeter. Do'ya think th-" Soap's transmission is cut off as another voice pipes in.
"They definitely know we're here. Got them parked East side of the building's," Graves informs. Pulling your eyes away from the scene and off the binoculars you look over your shoulder back at him. His intense blue eyes stare down at you, a stoic expression on his face; if you didn't know any better, you'd guess he's already disappointed you didn't barge in and set up camp before their arrival.
The comms start to go a little haywire as Bravo team starts asking questions to one another. "Just waiting on Team Leader to give the go ahead," Captain Price answers one of them. You catch this, and immediately butt in.
"I say we're clear. All stations are a go. Handing it over to you, Captain." With one last quick breath of peace exiting through your nose, you sit up. Dusting off your tac pants, you head for your packs. In the distance, you can hear the commotion of panic as the enemy starts to panic. As soon as you'd given permission, you knew Ghost was going to take down the spotters with his sniper. Horangi doing the same. The quiet fwips of the bullet slicing through the air--thankfully--not in your direction, is comforting... for now.
"South side clear. You're ready to go. Watch for East side. Do not know what is behind the A F V," Horangi informs you. Slinging the backpack straps over your shoulders, you untuck your braid from it before giving him one last look and a thanks, before heading out.
"I got it," König announces. While you'd both put on your packs at the same time, he's already practically running down the hill in plain sight. Though the sun's already begun to set and the desert is cast mostly in light blue on the South side where you're stationed, the man's still highly visible considering he's a hulking giant. The momentum of gravity takes him down the hill faster and faster, the Austrian making quick work of the soldiers that unfortunately round the AFV unsuspectingly, terrified screams echoing out shortly before they're quickly silenced by the Giant's handiwork.
"I've got South side then. Watch out for... him," Graves warns you, eyeing the Austrian suspiciously as König yanks the knife he's carrying out of the man's neck, a gush of blood blubbering up and out of the wound onto the concrete below. Turning your attention back to Graves you find him feet away heading in that direction, having silently departed without another word or acknowledgment.
"We've got five in the building. That I can see, at least. The right side and basement are grayed out," Keegan announces. Lifting the night vision scope momentarily, Keegan lays a hand on his waist as he waits for the Austrian to join the conversation. "So you're goin' in first. Clearin', then we follow?" The Southern boy clarifies.
"No, we're following as he's clearing. We need to back him, Keeg. You can't just let him go in alone. Especially if it's grayed out. Where are the five you can see?" Turning the safety off your SMG, you arm yourself. A roll of the shoulders, you eye the building before you, ignoring the way the dark blood stains on König's uniform stand out in the periphery of your vision.
"We've got hostages, Tiara." Nightvision goggles on, you know Keegan's not messing around when he calls you by your callsign. "Three, top floor left side. Looks like a woman and two children. One in the hallway behind them. One on the ground floor by the right side."
"Shit," you curse, "okay." Closing your eyes, you get yourself together. There's no telling whether there will be hostages on any given mission, and while it's usually not an issue, there's always a greater chance of something going awry when there are hostages involved. At least, in your opinion. "König? You've got a plan? We're following you, okay? We've got your back. We can do this. I suggest we go ground floor and then head upstairs, but you're the expert."
"Ja." It's as simple as that. You'd have thought you'd get anything more than one word from the Austrian man. Maybe you'd wanted more, maybe if he'd said something- anything, then you'd be reassured in any way, shape, or form, but the fact that he'd simply agreed and turned on his heel heading straight for the door is something you were unprepared for.
Nevertheless, this is the work. Expect the unexpected. Graves is still in the clear, and while the comms have been separated between teams from the moment you'd given the go, everything seems to be--thank god--going according to plan. Following the Giant into the building, you're a little surprised that he's as quiet as he is. Sure, you're not completely taken aback. I mean, he's in the military, surely he'd be somewhat stealthy, no? Well... thinking on it, you've known some people who aren't, but anyway--this is special ops--of course he'd be. Needless to say, you're impressed. Through the front door, you can see through cutout doorway to your left a vacated living room, and the beginnings of a staircase, the rest blocked by the wall before you.
König goes right, through the cutout doorway opposite where you'd been looking. It's the direction Keegan had pinpointed someone's location on the border of a grayed-out area. With it grayed out for him, the building must have one side, and the basement, encased in concrete or some other durable material too thick to see through. With that in mind, it could also mean they have either a bunker, or a bomb shelter in place for one reason or another. "Proceed with caution," you whisper.
"Affirmative," both men respond, one after the other. Keegan watches your six while you watch König's surroundings. Blocked by the Austrian's stature, you can't see but hear a gun pop and watch as König rushes forward through the next cutout doorway and drop-kicks the soldier onto the floor. His gun goes skittering across the hardwood floor, the small chandelier in the dining room shaking along with the whole house, dust filtering down from the crevices in the panels above your heads.
The enemy shouts something in Arabic that you don't understand, but is quickly silenced when König breaks their neck. It's too late. Gunfire fills your ears as bullets rain down from the ceiling. It's the person in the hallway upstairs! Bullets ricochet off gear and you can't help but disperse as you run through the opening on your left, a hallway that connects on the other side of the way you'd just come. Like a loop! At the bottom of the stairs, you ready yourself for an enemy ahead as you decide to forgo König's help and do this yourself. You know that there will be hostages ahead of you, approximately three, Keegan guessed, and while you don't know if they simply appeared as hostages through the goggles, and it's a trap... you'll have to take that risk. It's nothing you haven't done before, right?
"Tiara, wait!" Keegan calls after you.
While gunfire continues to resound through the dining room you'd come from, you aren't sure whether it's from the person you're going after, or one of your teammates trying to retaliate and shoot the Tango through the floor. No time to waste, you continue quietly walking up the steps and entering the room above. It only takes a moment for you to spot someone. The glimpse of a purple scarf elicits your attention; the whimper, and attempt to cower further into the corner, however, tells you all you need to know.
Eyes resettling on the doorway you're sure the real enemy is behind, you continue to step forward. It isn't until you can meet the woman's eyes that you're able to put a hand up, attempting to tacitly comfort her. It hurts, the way your heart clenches at the sight of her cowering in the corner behind the desk, her baby tucked into her lap between her knees curled up as high as they can go in an attempt to shield the precious life she'd created. An older, still young boy--couldn't be older than six or seven--clings onto his mother's arm with his body, while the other hand presses itself to his ear, eyes screwed shut.
You know why you're doing this... and it's so moments like these will never have to happen. Not just to this family, but to any family, hopefully, for a long, long time, if not, ever again.
Just feet away the demanding voice of a man shouts something in Arabic. You don't know what he's saying, you're unable to tell, and can't decide if he's talking to you... through a comm... to himself. He's not surrendering, you doubt that. It's only as the woman's lip wobbles and struggles to say something, opening and closing like a fish out of water that you realize. He's forcing her to keep lookout.
When she doesn't answer immediately, he yells something else, stomping around the corner before his eyes meet yours. Immediately firing, a bullet whizzes past you, another grazing your arm as you fire back. One- it hits his leg, eliciting a groan and a contortion of his face as fury takes over. Two- it embeds into his shoulder, twisting his body from the recoil as he has to steady himself. You slide to your right, past and behind the opposite side of the desk the family is at, a trail of bullets not stopping as he follows your figure, shooting the desk, bits of wood flying into the air. As he rounds the desk you aim and fire the last one--three--it sinks into his stomach. If the others wouldn't have taken him out eventually from infection or bleeding out, he's definitely gone now.
His body sinks to the floor, and you can't help but stay there on the floor, lying half up-right as you gather yourself. The creaking of floorboards signals someone's arrival and you gasp, quickly turning your gun on them. "Scheisse," König curses, eyeing you from the doorway. "We found the entrance."
A sigh of relief leaves you. Holstering your gun, you get yourself standing before rounding the desk and offering a hand out to the woman. "We're here to help you." She shakes her head, only clutching onto her children tighter, tears cascading down her cheeks silently. It's clear she doesn't believe you. With your hands, you attempt to communicate. Circling the three of them, you point outside.
"Do you want me to grab them?" König offers, still lingering in the doorway. You know from having read his file that he's actually good with hostages, usually taking his time and being patient with them, earning their trust. Something you're sure isn't easy for someone his size and stature, easily mistaken as intimidating, you're sure. Yet, you know that if they've found an entrance to whatever's beneath the house and Wagner's already aware of your presence then it's only a matter of minutes in your hands: you either get to him now and leave the hostages here for god knows what to happen to them, or you get the hostages to safety and let Wagner escape.
"Give her a minute," you answer calmly, voice quiet as you take a step back, hands up. If she wants to stay for now, that's fine. Perhaps, you can send Graves in to get them. Though knowing the Commander it might not be your favorite choice. Nevertheless, your eyes roam her one more time, and perhaps it's the inkling of a smile you gave her beneath your mask, or something in your eyes, but she relinquishes. Grip loosening on her child, she stands, baby still coddled in her arms. Holding onto the boy's hand, her other carrying the baby, you motion for her to leave her hiding spot. "You're safe now, I promise."
As the family rounds the desk hesitantly, you follow, making sure that they're okay. König holds out a hand to the child, his hand practically monstrous in comparison, yet the child looks between his mother and the Austrian before hesitantly taking ahold. Guiding them outside, König is quick to get them to Graves, politely shooing the family's attempts to now thank him. "T, we've got-" Graves begins.
"Secure them, please. We've found the bunker," König informs the Commander as he hands the family off.
"Gaz, I-" Graves speaks into his comms, fingers pressed up to his ear as the other dismisses you two.
König quickly jogs back to the house, and you follow suit. Keegan is pacing around a door you hadn't spotted in the dining room. "Finally! God. B team is drownin'. We went to the wrong buildin' and Horangi saw Wagner go into this building, so he has to be in here, but there are more soldiers at the North building."
"Distraction?" König proposes, cracking the metal door further open than it'd already been. With careful steps he starts slowly down the first few.
"Drowning?" You ask, seeking clarification.
"They've been dealing with hostages out the wazoo! They had ta delegate Gaz and Soap just to securin' the hostages. Anyway- doesn't matter. They've almost cleared the buildin' an' no sight of Wagner. Ghost hasn't seen him, trying to figure out if he's escaped."
"So we check here," König states, eyes shifting between the two of you and down the steep corridor of concrete steps.
"Exactly," Keegan agrees. Goggles on, he nods his head, ushering you in first. "I'll trail ya, make sure nobody's followin' us."
"Okay. Well, did you at least inform Price what we're about to do?" You question Keegan, needing to know that whatever you're stumbling into you're not going in blind without reinforcements. If there's one thing you're sure of, it's that once you're underground, there most likely won't be anymore reception and comms will go dead.
"Affirmative," Keegan answers, lifting his fingers up to his ear, "but if it makes you feel better. All stations, Tiara, König, and I are going dark." With everyone informed, your anxiety lessens just a smidge.
The tunnel is lined with sconces encased in little cages, classic bunker lights. The hallway smells of mildew, oddly, and the long grey hallway is eerily silent. Minutes of walking turns into what could probably be approximated by a football field's length walk. Your quiet footsteps slightly echoing and bouncing off the close walls. Finally, you can see there's an opening ahead where it looks like the tunnel opens up into a large room. In the middle of the room lies a large covered pallet you can see even from yards away. Upon getting closer you can hear the buzz of radios and have to assume there's a control station of sorts down here. Surely, there's bound to be more people, too. Though oddly enough you haven't seen anyone, yet.
Just as you breach the cutout opening up the room, you can see the layout clearly. In the middle of the room beside the pallet is a huge beam that holds up the ceiling. On the other side of the room lies a stairway upstairs, presumably to the Northern building Bravo team just cleared, and on the right side of the room in the corner is a control station. A huge TV is hung on the wall, along with a computer on a desk, radios, dials, and cabinets. Next to the control station is another cutout leading toward another open room, though all you see are shelving and what looks like a glimpse of a root cellar-type door.
Despite your keen ability to take in observation and information quickly, you're immediately swarmed by the enemy. Flanked by soldiers on either side, from the other room to the right, the stairway opposite you, and whoever had been hiding in the left corner waiting for you as you came all the way down the hallway, they clearly planned for this. It's a trap.
In the center emerges Wagner from his men, a smug smile on his ugly frog face as his eyes once you over. "Who sent you?" He asks.
"Give us the next meeting location of the Party and you'll find out," Keegan barters, aiming his pistols at Wagner's men, he doesn't back down.
A throaty and nasally chuckle escapes the man as he shoves his hands in his pockets. "We've got you surrounded. Do you really think you're in the best place to bargain with me?" The air of confidence and egotistical nonchalance is enough to make you want to vomit. "I will only ask one more time."
As the man continues to speak, König braves another step inside. Due to his size, it's considerable. He's got his Glock out, eyes scanning the room as he eventually lands on yours, silently and subtly affirming a plan. You shift your gaze to Keegan, and then back to König before subtly nodding, hoping and praying it goes unnoticed as you attempt to play it off as nervousness, moving as if you're just new and untrained. As Wagner goes to speak again, the first syllable to interrupted by the sound of gunfire as you both start firing. Pops, whizzes, and pings of ricochet echo throughout the space as a gunfight goes down. Bodies drop left and right as you'd had the upper hand of an at least somewhat formulated plan. Keegan wasn't going to back down and was ready, you knew this, König was game, and you two were in sync. Together, you all have multiple rounds.
Their armor-piercing bullets make them drop like flies while your quickfire gun had at least stunned, wounded, and distracted long enough to get more kills in. König takes the left, you take the right, and Keegan decides to go straight down the middle after Wagner. It's only when there's a loud beeping sound that things go sideways. König goes after the soldiers and Wagner as they attempt to flee upstairs through the Northern building. As you get the last two guys in the adjacent room, you don't hear Keegan doing anything, which worries you to say the least.
A little focus goes a long way; one of the men uses your distraction as an advantage, switching to melee as he slices your arm with a knife. Stumbling backward with a cry you kick him in the stomach as he lunges at you again. Shooting generally at the second man you manage to fire multiple rounds at him, his body dropping. While the man you'd kicked fell flat on his butt, he pulls something out from his pocket, a scared look in his eye as he moves without thought. Meeting his eyes for only a moment, you see him pull the pin. "Shit!" Without thought you drop your gun and run into the next room, sliding as far away as you can before ducking and covering, attempting to shield yourself from the grenade blast as best you can.
Boom!
"T?" It's calm, yet you can hear his breathing, and it's somewhat shaky. Uncurling from yourself, you spot Keegan just feet away, lying by the pallets on something you'd failed to spot earlier. How could you fail to spot something as obvious as that? Panic immediately rises to the surface as your heart pounds in your chest. Underneath the lower half of his body lies a pad- a trigger of some sort, a pressure pad. It's a form of lock used to release the mechanism in the system for a bomb to start counting down. As you take in the way he's clutching his stomach and how there's blood seeping not only from around his fingers, but from another place in his thigh, you can't help but feel yourself freeze.
Your eyes finally meet his, following them as they stay locked onto the giant television that's on the wall. It's crooked now, dangling, most likely from the grenade that'd just gone off, yet... it's no longer a dark screen. It's on... and there's a countdown clock on it. "I'm so sorry! I didn't see it- I just went for 'im- I couldn't let 'im get away, I-" Keegan begins to blabber, his voice coming out much more sorrowful than you're used to.
"It-" you scramble onto your knees, hands up as you try to shut him up, "It's fine! It's fine! Just- just..." Mind going a mile a minute you can't help but flounder as you try to figure out what to do. A bomb's going to go off. You don't know that you can get Keegan out of here safely, intact, in time. Not to mention, Wagner could be getting away right now.
"You have to get him! Go! Leave me," Keegan demands, gripping your shirt and tugging on it, forcing you to get his attention. "Don't think! Just act. Get him! It's your duty, soldier. GO!"
Pure adrenaline courses through your body at this point in time as you run through the basement and up the stairs you'd seen. You only have your service pistol in hand, and aren't sure where everyone else had gone. As the space opens up into the hangar of the Northern building there's a sporadic quiet pops of gunfire to the South, while directly to your West there's suddenly a gigantic BOOM! You can hear multiple voices in your ear all shouting and directing one another as they scramble with whatever situations they're in. Concentration escapes you as you can't help the overwhelming anxiety that floods your body, dread, and fear continuously washing over you in waves over and over.
"If you have the shot, take him out!" You hear Graves shout into the comms.
"It's too close-" Ghost responds, voice cool and calm. "Either tell 'im to lead 'im away or get outta there. Now."
While you have no idea what they're talking about, you can guesstimate. Regardless, with the sound of gunfire close by and the sound of their voices you know they're all not too far away. If anything, it seems like all the chaos has shrunken down to just surrounding this building.
"Horangi, update!" Gaz demands. There's another boom, and then another. Though it shakes the ground you're standing on and causes you to stumble and almost trip over your own two feet, you manage to get outside the open hangar doors the team had bust down. Smoke fills the air, and you can now see what's going on. "Update!"
"It should be down now. They are blind." Horangi responds.
Ghost is still in the B team's roost nest keeping lookout. While far away, you know he's not focused on whatever's going on here. The smoke makes it hard to see, and you wind up coughing as you wave it from your face. Through it, you can barely make out what you think is the rest of B team attempting to gather and herd the hostages. Dozens upon dozens of civilians scream, cry, and huddle a few yards South, closer to where Graves had been stationed. You assume he's still there. Closest to you, an AFV is active. Clearly, one of the last remaining soldiers jumped into the tank and decided the only way to protect themselves was by using it to save themselves. Or, to take out everyone, including the civilians, since it seems that's where the blasts were going.
"Fuckin' hell, finally. McKay, Gaz, moving in," Soap announces.
"NO!" You yell. Though you don't have your comms on, you shout into the distance and know they can hear you. "Soap, I need you! Graves, McKay, Wilson- anyone can help, but I need you- there's a bomb!" Eyes looking between where you know Soap's approximately located and the basement, you know you have to hurry. "Keegan- he's- I need you. Now!"
"Fuck," you hear Soap curse. "On my way!" While you can hear skirmishes going on to the right somewhere, you focus on regaining your breath. As the sound of feet padding toward you gets closer you raise your pistol just in case. "Christ's sake, Lass! Dinnae point that thing at me, yeah?" With a sigh, he pats your back. "Lead the way."
Back down in the basement, you're relieved to be back by Keegan's side. At least then, you know you can do your work. Something you'd always been good at on testing day was being an on-field medic, so while you don't necessarily want to ever have to... when push comes to shove, you're glad you can and know how to.
With gentle hands you gently feel around his thigh for the bullet. To your surprise, he'd gotten lucky with his leg, the bullet only slightly lodged into it. While the general rule of thumb is to keep any intrusive objects within until in a safe place to remove them, that doesn't apply when you can easily tourniquet the wound. After all, from inspection, you can see that the blood was seeping from around the bullet anyhow. Keegan was either moving around too much, opening and tearing the wound further, or he tried dislodging the bullet by himself. A bad idea either way.
Unslinging the backpack from your shoulders you undo your medkit and get out the antiseptic, gauze, and scissors. "I can't stitch you up here, but on the helo I can fix you up," you reassure him. Gently smacking Keegan's arm a few times you attempt to keep him awake. "Hey, hey! Hey- Keeg- what happened? Tell me what happened, talk to me. Say something."
Eyelids continuously fluttering between open and closed, you debate whether or not this is serious enough to stab him with the Epi-Pen. "Don't make me stab you with the Epi-Pen, Sergeant."
"Is that a threat?" His words come out slow and somewhat slurred, but it's enough for you. He's still awake. Still responsive, that's good. You brace one hand above the wound to keep him in place, while the other grabs the small pair of forceps that'd been in your medkit. In truth, you'd rather warn him of what you're about to do, but in all honesty it's probably better to just do it and get it over with. Rip the bandaid off, for lack of better words.
"How's it looking over there, MacTavish?" You ask, trying to keep things casual and calm. Silently counting down in your mind, you place the grips of the forceps around the bullet in Keegan's leg. Three... Two... One.
Keegan's scream rips through the basement, making both you and the Scot jump in your skin. The Southern boy jolts, attempting to sit upright. You hush him and force him back down. "It's okay, it's okay. That's done! It's done. I just have to wrap it."
"No... stop. It's fine," he refutes, trying to push your hands away. Never, have you given him a stink eye like now, he thinks.
Soap clears his throat. "How long's that gonna take? Exactly?" There's an audible tension in his voice. With swift hands you make quick work of the final knot in the tourniquet on Keegan's thigh, ignoring his groans. Looking over your shoulder you notice the sweat donning Johnny's eyebrow.
"Why? What's wrong?" You ask. Coming closer, you look over his shoulder at all the wires connected to the batteries, switches, and jumpers on the pallet. Bombs were never your specialty. Of course, everyone knew about the simple sort of red, blue, and yellow situation. Red is usually bad, yellow equals okay, and blue is good. But... that's not always the situation. You'd only ever done the practice exams, and... well, didn't exactly pass most of them. Therefore, that specialty was definitely out of the question for you. Needless to say, the device sat before you is more complicated than the Da Vinci code. "He has a whole laceration on his stomach that's bleeding severely. I'd have to do stitches- that'd take... fifteen minutes, tops? If they're good. Bad? Ten. Unsterilized, which could kill him... five? but... we're not doing the latter."
"Then we've gotta move him. And fast," Johnny instructs. The downturn of his lips doesn't shift as he turns to face you head-on. "I'm not risking two teammates for some jugaad bomb. I can carry him upstairs easy."
Together it was exactly what Soap had predicted: easy. Keegan wasn't in good shape, but he was alive. The rest of the mission flies by, and soon you find yourself sitting strapped into the helo seat, hands cradling your head as you process everything that'd just happened.
~~~~~~~~~~
acronyms:
AFV: Armored-Fighting Vehicle
SMG: Sub-Machine Gun
Tango: Target or Enemy (aka the saying "tango down")
forever taglist: @ohdamnadam , @safarigirlsp , @jynzandtonic , @moonlightsolo
t&t taglist: @cosychick , @konigsqueen , @cutegor3
#please read tags at top#my writing#my series#cod men x reader#cod x reader#cod reader insert#t&t#t&t series#trials & triumphs#trials & triumphs series#simon ghost riley x reader#könig x reader#keegan russ x reader#keegan p russ x reader#simon riley x reader#task force 141 x reader#taskforce 141 x reader#call of duty reader insert#johnny soap mactavish#phillip graves#kyle gaz garrick#johnny soap mactavish x reader#johnny mactavish x reader#captain john price#john price#g writes#kim horangi hong jin
41 notes
·
View notes
Text
In 2024, increased adoption of biometric surveillance systems, such as the use of AI-powered facial recognition in public places and access to government services, will spur biometric identity theft and anti-surveillance innovations. Individuals aiming to steal biometric identities to commit fraud or gain access to unauthorized data will be bolstered by generative AI tools and the abundance of face and voice data posted online.
Already, voice clones are being used for scams. Take for example, Jennifer DeStefano, a mom in Arizona who heard the panicked voice of her daughter crying “Mom, these bad men have me!” after receiving a call from an unknown number. The scammer demanded money. DeStefano was eventually able to confirm that her daughter was safe. This hoax is a precursor for more sophisticated biometric scams that will target our deepest fears by using the images and sounds of our loved ones to coerce us to do the bidding of whoever deploys these tools.
In 2024, some governments will likely adopt biometric mimicry to support psychological torture. In the past, a person of interest might be told false information with little evidence to support the claims other than the words of the interrogator. Today, a person being questioned may have been arrested due to a false facial recognition match. Dark-skinned men in the United States, including Robert Williams, Michael Oliver, Nijeer Parks, and Randal Reid, have been wrongfully arrested due to facial misidentification, detained and imprisoned for crimes they did not commit. They are among a group of individuals, including the elderly, people of color, and gender nonconforming individuals, who are at higher risk of facial misidentification.
Generative AI tools also give intelligence agencies the ability to create false evidence, like a video of an alleged coconspirator confessing to a crime. Perhaps just as harrowing is that the power to create digital doppelgängers will not be limited to entities with large budgets. The availability of open-sourced generative AI systems that can produce humanlike voices and false videos will increase the circulation of revenge porn, child sexual abuse materials, and more on the dark web.
By 2024 we will have growing numbers of “excoded” communities and people—those whose life opportunities have been negatively altered by AI systems. At the Algorithmic Justice League, we have received hundreds of reports about biometric rights being compromised. In response, we will witness the rise of the faceless, those who are committed to keeping their biometric identities hidden in plain sight.
Because biometric rights will vary across the world, fashion choices will reflect regional biometric regimes. Face coverings, like those used for religious purposes or medical masks to stave off viruses, will be adopted as both fashion statement and anti-surveillance garments where permitted. In 2019, when protesters began destroying surveillance equipment while obscuring their appearance, a Hong Kong government leader banned face masks.
In 2024, we will start to see a bifurcation of mass surveillance and free-face territories, areas where you have laws like the provision in the proposed EU AI Act, which bans the use of live biometrics in public places. In such places, anti-surveillance fashion will flourish. After all, facial recognition can be used retroactively on video feeds. Parents will fight to protect the right for children to be “biometric naive”, which is to have none of their biometrics such as faceprint, voiceprint, or iris pattern scanned and stored by government agencies, schools, or religious institutions. New eyewear companies will offer lenses that distort the ability for cameras to easily capture your ocular biometric information, and pairs of glasses will come with prosthetic extensions to alter your nose and cheek shapes. 3D printing tools will be used to make at-home face prosthetics, though depending on where you are in the world, it may be outlawed. In a world where the face is the final frontier of privacy, glancing upon the unaltered visage of another will be a rare intimacy.
22 notes
·
View notes
Text
G Witch Onscreen Text: Episode 2
This is part 3 in an ongoing series where I try and document and discuss all of the text that appears on screens and monitors throughout the show! Just because I can!
<<Click here to go back to Episode 1!
(Once I have a masterpost set up I will link it here!)
Let us Begin! Below the Cut!

TEXT:
(Lefthand side)
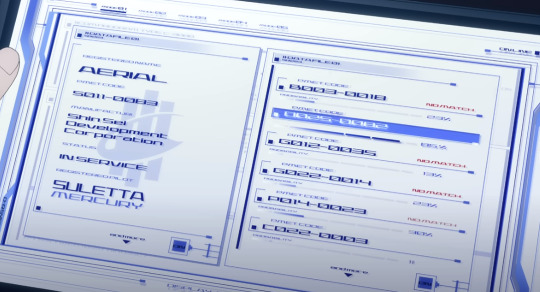
Registered Name: AERIAL
PMET CODE: 5011-0083
MANUFACTUR(ER): SHIN-SEI DEVELOPMENT CORPORATION
STATUS: IN SERVICE
REGISTERED PILOT: SULETTA MERCURY
At the beginning of the episode, Rouji has Haro run a program that compares Aerial's permet code and registered statistics against other registered Mobile Suits to try and find a match, and measures the probability of the two being the same type of MS. There is no direct match to any other MS by Permet Code, but the system states there's an 85% probability that it's a match for a Mobile Suit with permet code 0025-0082.
We never see the specific name of this MS, but considering that Shaddiq names "Ochs Earth" as the company that made it and proceeds to call Aerial, "...the Witch's Mobile Suit," I think it's reasonable to assume that 0025-0082 was the Permet Code for Lfrith-03.

TEXT:
ALERT
ACCESS CONTROL
[???]
[----OF ENTRY A---]
Unfortunately due to the small text of the Alert message, the fact that it scrolls, and it's brief time onscreen, its hard to make out specifically what it says. My best assumption from what we have is that it's a warning currently barring anyone from entry into the 13th Tactical Testing Sector.

TEXT:
(Suletta's Asticassia ID)
PILOTING DEPARTMENT
ID No: LP-041
SULETTA MERCURY
BIRTHPLACE: MERCURY
HOUSE: NO DATA
PC-CRIMINAL RECORD: NO DATA
PC-BIOMETRIC SYSTEM: REGISTERED
(Below)
WE ARE RESPONSIBLE UNDER COMPANY REGULATIONS FOR THE PROCESSING OF PERSONAL DATA
UNDER THESE REGULATIONS, WE ARE ALSO RESPONSIBLE FOR DATA HANDLING SUCH AS TRANSMISSION TO RECIPIENTS AND THIRD PARTIES.
PLEASE REFER TO THE FOLLOWING DOCUMENTS FOR DETAILS.
As Suletta is being questioned, we get a brief glimpse at the investigation report the interrogator was looking at before the screen cuts to black when it hits the table. Nothing super interesting here, but Suletta doesn't have a registered criminal record! Yippeeee!

TEXT:
CAM: 05
MONITORING CAMERA
FACILITY MANAGEMENT COMPANY
Not much to say here, this camera lets us know where Suletta is currently being held. (The Facility Management Company)
TEXT:
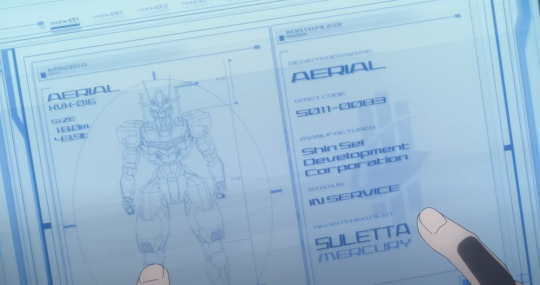
(Lefthand Side)
AERIAL
XVX - 016
SIZE:
18.0m
48.9t
No point discussing the info on the right, we've already seen it, but this gives us a look at Aerial's height and weight.

TEXT:
(Top Right)
COM
DELLING REMBRAN
BENERIT GROUP
I only included this to point out that wow the display system devs made some poor choices with the UI here. Dark Blue text on Dark Backgrounds? You'd think the text would automatically lighten but I guess we'll have to wait for Ver 6.0 for that update.
TEXT
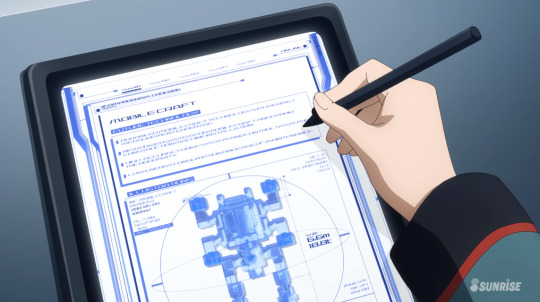
(Top half)
MOBILE CRAFT
FUTURE TECHNOLOGY
ADVANCED MOBILE CRAFT TECHNOLOGY WITH PERMET MEASUREMENT EXPERTISE
NEW POWER SYSTEM FOR MOBILE CRAFT AND HYBRID CONSTRUCTION MACHINE INSTALLATION
HIGH ACCURACY DRIVE SYSTEM AND CONTROL SYSTEM IN MICROGRAVITY
LOW ENERGY CONSUMPTION AND EASE OF MAINTENNANCE
No need to discuss the bottom half, its just the height and weight of the MC which we already know. I think it's funny how many classes this school seems to have on the new and improved Mobile Craft from Future Technology. I should probably buy one too. I love you Mobile Craft.


TEXT:
(Left Image)
The Shin Sei Development Corporation was established in A.S. 89. Our business began with the development of integrated operating systems for mobile suits and medical devices.
We have been involved in MS development and have supported welfare engineering throughout our company history.
(Right Image)
Ranking: D
Sales Ranking (within group companies): 151th (out of) Total 157 companies [Mobile Suit Development]
Number of clients: Over 300 companies
Yearly patents: Over 200
We get a lot of information about Shin Sei in this scene where Martin looks at the Company History tab on their official website. The most interesting thing being that they were founded in A.S. 89. The Vanadis Incident occured in A.S. 101, and the show proper takes place in A.S. 122, so at some point between 101 and 122, Prospera worked her way up through Shin Sei, eventually becoming its CEO.
Given that Suletta had to have been born around A.S. 105, and that in Cradle Planet, we learn that Prospera had been working within Shin Sei when Suletta was around 6, that places A.S. 111 as the earliest she was involved.
We also learn in Cradle Planet, that when Suletta is around 11, Prospera has recently been promoted within the company, and now has many people working under her. That would be around A.S. 116. When Suletta is 16, that's when Prospera tells her that she's going to school, which would be around A.S. 121, and I think it's safe to assume that she had already become president by then.
SO!! TL;DR!! It's most likely that Prospera became the president of Shin Sei at SOME point between A.S 116 and A.S 121. I'd put it somewhere in the middle, around A.S 119.
(Can't wait to find out that they probably just outright state this somewhere and I did all this for nothing....)
ADDENDUM

GOD DAMNIT. I WATCHED ALL OF CRADLE PLANET TO MATH THAT SHIT OUT. WHATEVER. I CAME TO THE SAME CONCLUSION SO I WIN.

The text is too small to make out, but we DO get a small glimpse at the letter Delling sent to Miorine about unenrolling her from the school. It probably just literally says what the body guard reads out.
I think it says something that Delling doesn't even like, text his daughter. He sends an email through the official Benerit Group email account to her bodyguard who reads it for her. What a cowardly man.

TEXT:
(Left)
FLUSH
(Right)
EMERGENCY CALL
UNLOCK
LOCK
YES the toilet text is important to document stop fucking looking at me like that.

TEXT:
NEXT STAGE
TOUCH SCREEN TO CONTINUE
I'll leave the explanation of the symbolism of this scene as an exercise for the reader. [Sultry Wink]

TEXT
(Above)
THIS ELECTRONIC SIGNATURE IS PROOF THAT IT WAS SIGNED BY A REPRESENTATIVE OF THE BENERIT GROUP.
No way to tell what Delling is signing here, but we do get a brief look at his handwriting. It turns out his cursive is really bad, actually!
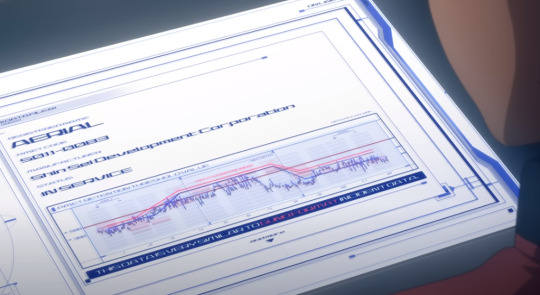
At the Shin Sei inquiry, Shaddiq shares this graph titled "PMET RETENTION THRESHOLD VALUE", stating that during the duel, Aerial's Permet Influx Values exceeded the standards set by Cathedra.
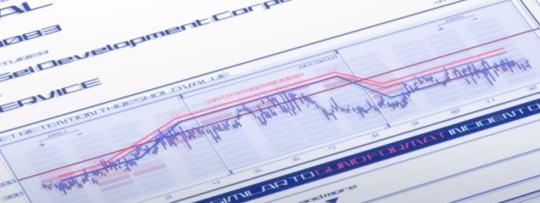
This graph can be tough to parse, so let me explain it as best I can.
The blue line represents Aerial's Permet Retention during the duel. The solid dark line represents the permet retention limit imposed by cathedra on mobile suits. (At around 500) As we can see, while Aerial began the duel underneath that limit, it exceeded it for a moment (presumably when Suletta took over for Miorine and the GUND bits were activated.)
The red line above that is labelled DATA STORM INCIDENT, which is representative of the minimum Permet Retention a Gundam expresses when it is interfacing with a Data Storm. The text on the bottom reads, THIS DATA IS VERY SIMILAR TO GUND FORMAT INCIDENT DATA.
But the key thing to take note of here is that Aerial's chart just BARELY doesn't exceed the DATA STORM INCIDENT graph, meaning that, despite it exceeding Cathedra's standards, it CANNOT be directly proven that Aerial was interfacing with a Data Storm. This is actually what Prospera brings up as her main counterpoint to the accusation.

So the graph is entirely consistent with Prospera's main argument. While she can't prove that Aerial isn't a gundam, nobody else can prove that it is.
Huaaaahh!! Alright!! This one was very DENSE. If you made it all the way through, thank you very much!! As a reward, have some little gay people




[I sprinkle these stills on the ground like bird seed.]
There was definitely a lot of really interesting info in this episode, and while not a lot of it was particularly new, I think it's really a testament to the dedication of keeping things wholly consistent in this world, even for the smallest of things that no normal person watching would even bother noticing.
Also, on the Shin Sei Website, did you notice that they accidentally put 151th instead of 151st?
You can't win em all!
Click here to go to Episode 3! >>
Click here to go to the Masterpost!
34 notes
·
View notes
Text
I can't believe I'm doing this, but I'm afraid I have to get the word out.
Dismantling most accusations/complaints against Pokemon Sleep (There are a few which are actually valid and to a point the developers have started to work on them)
Part 1 - Those I don't understand
- Pokemon sleep steals our biometric data
No they don't, they specify that very well in the terms. Yes they ask to use your mircophone but there are other sleep thrackers that do that. This one simply earned an uproar, because it was Pokemon who dared to. Also in your phones settings under Apps>Pokemon Sleep>Authorization you can disable the app to access your microphone.
- Pokemon Sleep could turn our children to compulsive gambling
As a pedagogical caretaker who actually tried and pkayed the game I can't see this. They are not monopolizing on the time before and after going to bed. Everything you can do is done in at most 10 Minutes. As for the payment options, if there is no Debit/Credit Card or Paypal account behind the account you use on the play store they can't buy anything anyway. If there is it is the responsibility of the parent to show them, on what they would spend real money.
- Pokemon sleep is inaccurate when you're around the room but not on your mattress trying to sleep.
Yeah, no shit sherlock, any other sleep tracker would be too. Even my fitness tracker sometimes counts me being completely still as being asleep in the eveningy when I'm actually just reading or watching something.
- Pokemon Sleep is too hard to play
Actually it is really simple and everything is explained pretty well. A game shouldn't serve you everything on a silver tray, there should be room to explore and I think pokemon sleep does that quite well
- The progress in pokemon sleep is too slow
This is no super fast progress game, duh. It is meant to be relaxed and to encourage you to improve your sleep cycle in a fun and cute way and it does a wonderful job. If you need to have fast progress to have fun, it is a sign of how damaging those games with fast progress actually are, they are much more attention and time grabbing and much more dangerous when it comes to developing compulsive gaming disorder.
Complaints I do understand (and am willing to offer a solution)
- The relaxing tune is too loud.
I had that problem too and it is not a solution of sorts, but they fixed that pretty fast. What I prefer to do though, is to listen to my own custom playlist on my iPad and set the timer to one hour to turn the music off.
- The mobile overheats/the app crashes/it uses too much battery
This one I find more understandable. There is a notion that bug fixes are underway. If you're not willing to wait for the bug fixes an alternative would be to buy the pokemon go plus +. No I'm not sponsored by The Pokemon Company in any way shape or form, but I calculated it trhough. For a sleep tracking device which can also be cross used with Pokemon go, the pricing is alright. My current fitness tracker with an innate sleep tracker costs almost thrice as much. There are Smart watches out there you pay ten times as much for. The device comes with a clip to not fall under your pillow, and your mobile has to do nothing over night, because you simply sync the sleep data in the morning. The battery of the Pokemon Go plus + also keeps going up to one week when fully charged. And needs about 3 1/2 hours to carge from zero.
Due to emotional involvement some of this contains my personal opinion/advice. I'm not seeking any form of a fight over these points, though I'll be happy to discuss them with you contructively in the comments.^^
30 notes
·
View notes
Text
the agent walks up to the kitchen staffs door, and it holds its wrist up to the ID scanner. it is let inside, no problem. that chip in its organic arm is one of the few actual wireless pieces of tech it has installed onboard, because those chips are easy to write to and easy to erase and are a very non-obtrusive system. can't hack someone through their ID, and those are so easy to fake. you don't really know why they're still in such common use. makes your job easier, you suppose. the kitchen staff work around the agent, and the agent slips through them.
it gets weird looks, they know they're in some danger, but no one ends up hurt. it stresses you out, a little bit, to see your agent around civilians. you dont really know why. or, well, you know what it can do. you don't know what it won't do. it's impossible to test for the absence of an occurrence. that's not the phrase. it's impossible to prove that something will never happen. that's it. no wait, that doesn't sound right either. whatever. you are not afraid of the agent, it is your friend. these random civilians are not it's friends. as far as you know. but it is polite, as far as you can tell, as it moves through the crowded kitchen. you check that it has access to the latest version of your little map of this building, and it does. and then it proves that it does because it goes the long way around and takes the door that leads to the staff hallways, and not the fancy ass dining area. it's following the route it needs to, no issue. tiny issue. it needs to get through two locked doors. issue so small it is microscopic, because all these locks are ID activated. lol. you scrape the biometric data you need from the security network, and update it's chip. and it's let through without issue. no wait. a little warning popup about how one person apparently went through one door twice in one direction. valid concern. you delete the warning. lol. the agent makes it to the room without issue.
inside of the room is a slender young man with short, greasy hair and a jumpy air to him. the agent startles him a lot by just popping up silently in the corner of his office. this is the client, and not the target. your view from the agents visor keeps wandering, because it's a bit bored. the client, Petra, asks you a question, out loud. well, he asks the agent a question, but it's not really listening. you respond via text, same channel that he hired you on.
"So. You're... agent Mandible?"
the codename you're currently using. [yes yes. where is the target? thought there was a job to do.]
you do not need to be this rude, but also it's kinda fun, watching the fear on his face, watching him puzzle the pieces together entirely incorrectly, because he whispers "Ah, so you're a robot..." under his breath in a way he thinks you won't hear. lol? even if one of you was a robot, you would be able to hear that. this guy is a fool. a fool who is paying you to kill his superior. it might actually be his dad, you didn't pry enough to find out. he has composed himself enough to tell you what room the target is in.
"I don't think I need to tell you how to get there, given that you found me just fine." he shuffles his feet, and visibly struggles to maintain eye contact. he feels he needs to be polite, apparently. "You arrived at the perfect time, he should be asleep for the next 15 minutes or so..." he trails off, and then turns to look out a window, hands behind his back, all fuckin formal. the agent is out of there as soon as the talking is over, and you've sent it on the updated map. you check on the targets room remotely. holy shit. the door lock isn't even engaged. he left it open. there are two cameras in his room. one is completely off, he requested that? lol. the other is not off, but it is on standby mode, it should alert and start recording when it detects movement. getting past that specific trick is not brainlessly easy, but it's not impossible either. you just want it to look untampered with. or- wait. it only needs to look untampered for the text ten minutes or so, while no-one's looking too hard, probably. you get it hacked, it's a good enough job. as good as it needs to be. they won't have footage of the incident. now you get to watch the agent do it's part of the job, from its perspective, no less. it takes a moment to consider something. medium of dispatch, maybe? oh, yeah. it gets out its knife. hand over his mouth, blade into his neck, up into the skull. simple and silent. kinda messy and gruesome also. the poor cleaning staff, that is not a cheap carpet. at least that desk seems very blood-proof, with how excessively shiny it is. the agent wipes its knife on the targets sleeve, and then it is out of there, along the new route you've sent it, down the quiet staff hallways but not the same ones as earlier. you leave your cam hack in place, might as well, and you text the client and tell him [it is done.] which is very edgy of you, you admit, but it's appropriate for this job, probably.
hmm. there's something to ponder there, about the aesthetics of death. guns make the process of creating death much more efficient, they're machines, they're optimized. using your own hand weapons takes the degree of separation out of it. you're much closer to the violence you're doing. you, in the general grammatical case, your personal hands are still pretty clean, overall. well, ok, no. degrees of separation, again. you are paid to be the middleman between the person who wants someone dead and the person who does the killing. person is here. you wave it into the truck, and then you drive away, out of this parking lot.
[do you want more hand weapons? i've been mostly focusing on guns, for range and effecacy, but for small jobs like this it might be worth it. maybe? what do you think?]
it makes a small ponderous noise, and looks up to the roof, fidgeting with its fingers, deep in thought.
[i should be able to get my hands on some weapons catalogs for you, plus there's that expo coming up in a few weeks. but with both of those, there's the problem of you being actively sold something. lots of loud flashy words to get you to spend lots of money money money]
it huffs a quiet laugh, and then it pulls its mask down to tap at its jaw. huh? oh, it's referencing the guy who sold you that jaw, and a lot of other very flashy and not strictly nessecary items. you laugh at that.
[oh man, i don't remember how many of them you've met, but i have quite a lot of friends like that. my sincere condolences.]
it throws it's hands up in mock despair, very clearly smiling at the same time. you have a new message, from Petra. [The money has been forwarded to you.] oh damn. immediately after the job? this guy has a lot of trust in his bank security. or he just hasn't thought of what an investigator might look for. family of rich idiots, over there. once the money comes in, you'll move it to your actual account. obfuscatory steps. the agent is messing with a small piece of fabric, folding and unfolding it. it might have snatched that from that last job. that's fair, honestly. small enough to be hard to identify and easy to dispose of it needed, and it looks like it has a good texture to it. you should get it some new fidgety things, once this money comes in. you could get yourself something too, maybe. been a while since you got new clothes, but also you don't like lugging around too much unnessecary stuff. maybe there's a clothes swap event somewhere nearby you could drop in to. how would you find that. you could ask a friend. carmen, they seem like they would know. you should drop into them anyways, say hi. it gets kinda hard to keep up with friends, with the constant travelling. but you do your best, and your friends are cool, they all seem to understand. the agent has just finished typing something out on its communicator.
[bazooka would be funny]
that is SO far from anything you were expecting, you're breathless with laughter.
[say fuck all of you. get explode]
you make a little explosion motion with both hands, one still on the wheel. the agent looks somewhat proud of having gotten you to laugh.
[okay, man, do you have any actual ideas?]
[no. give me some time]
[yeah yeah, no worries. we're in no rush]
#[fiction]#[category: the agent & the handler]#death tw#blood tw#someone dies but hes not terribly important. this is about those gay people again
6 notes
·
View notes
Note
What's the general technology level of your setting? The capabilities and small size of the collars evokes modern/future digital electronics, but that seems to conflict with the analog nature of basically everything else. How do you reconcile the two?
I take a lot from the cassette futurist aesthetics in the vein of the original Star Wars trilogy and the original Blade Runner, so when it comes to general technology levels, I'd say it straddles the two. In each, you still have largely hard analog or analog-adjacent technology, a lot of which is miniaturized. It didn't really seem like a big leap for me to employ that line of thinking in collars.
Now, I'm no hardware expert, so I can't really functionally give you a specification rundown on how the collars work exactly. That's probably an area where you have to employ *some* degree of suspension of disbelief.
As for reconciliation, I suppose I would say it's a matter of framing/how we think about the collars. Instead of thinking about what they *can* do, I'd like to think about what they *can't* do. Yes, they perform wireless communication, but only short range (walkie-talkie like tech has been around since the 1940s). Generally (with few exceptions), long-distance communication using collars requires wired connection to orbital signal/interstellar signal repeaters. Yes, they monitor vital signs, but those are very simple biometrics, nothing quite like a modern health-monitoring watches which count down to the calories/blood oxygen level. They carry unique ID codes which allow users to access data, points of entry, etc. but that kind of technology has been around for some time.
In that way, with the sci fi suspension of disbelief of *some* of their abilities, they can be seen as significant quality of life improvements for Percivals-universe residents which justifies their diagetic existence, while also bearing some technological limitations you'd expect from the analog futurism.
Good question!
10 notes
·
View notes
Text

Sen. Ed Markey (D-Mass.) sent a letter Tuesday to the Department of Homeland Security (DHS) urging it to discontinue the use of a smartphone app required by migrants seeking asylum at the southern border to use.
The CBP One app, which was rolled out in 2021, was established to allow migrants to submit applications for asylum before they cross the U.S. border. Markey said in his letter that requiring migrants to submit sensitive information, including biometric and location data, on the app raises “serious privacy concerns,” and demanded that the DHS cease its use of it.
“This expanded use of the CBP One app raises troubling issues of inequitable access to — and impermissible limits on — asylum, and has been plagued by significant technical problems and privacy concerns. DHS should shelve the CBP One app immediately,” Markey said in his letter.
“Rather than mandating use of an app that is inaccessible to many migrants, and violates both their privacy and international law, DHS should instead implement a compassionate, lawful, and human rights centered approach for those seeking asylum in the United States,” he continued.
He said that the use of this technology has also faced technical problems, including with its facial recognition software misidentifying people of color.
“Technology can facilitate asylum processing, but we cannot allow it to create a tiered system that treats asylum seekers differently based on their economic status — including the ability to pay for travel — language, nationality, or race,” he said.
The app has negative ratings on both the Google Play and Apple app stores, with many users criticizing the app for crashing and other technical issues.
(continue reading)
#politics#ed markey#immigration#asylum seekers#joe biden#cbp one app#dhs#privacy rights#surveillance state#facial recognition
54 notes
·
View notes
Note
Hey, Van, could you explain permet to me because I don't think I ever fully understood how it works or what happened at the end and how was it different from quiter zero? Please?
Oh dear. Gundam technobabble. Keep in mind that I'm writing this without having read any of the official additional material, this is just what I can glean from the show itself.
Alright so Permet's whole thing is that it can form a networks with itself under specific conditions. Presumably it means that anything with a sufficient concentration of Permet in it -- including human beings -- can act as components of that network, kind of like a big integrated circuit. For Gundams specifically, this means that the pilot becomes a part of the operating system of the mobile suit -- it looks like other Permet technology includes an additional layer of interfacing, which means they don't offload any processing onto the Permet networks of the user, Gund technology makes the connection go both way.
The upside is that controlling technology the way you "control" your body has immense benefits for stuff like reaction time, situational awareness and fine motor control -- the downside is that insides of humans are not nice and ordered like an integrated circuit, and so Permet trying to force itself into a structure like that clearly has some deleterious health effects. If I had to guess, it fucks with the subtle electric signals inside the brainmeats somehow, but why it causes high fever, I don't know. It also looks like constant exposure to things that activate the Permet inside a body is cumulative, like radiation poisoning.
"Data storms" are just what the larger expressions of a Permet networks are called. If I had to guess, I think the name comes from how these large networks inherit noise resulting from Permet reactions in the absence of a control system, becoming more chaotic the further their influence extends. In limited amounts, like the small-scale storms inside Gundam systems, a human consciousness can still exert control over them, organise them, but as the scale goes up, the amount of agitation the Permet inside a person is under exceeds some physical limit. The influence goes both ways, though, human biometric activity can become imprinted into a Permet network, like how Eri did with Lfrith.
Quiet Zero is basically an amplifier capable of forcibly organising ambient Permet. This includes Permet that is bound in extant systems, which is why it gives remote control over Permet-powered technology that gets within the zone of influence the large antenna structure provides for them. But, critically, I think both Eri and Suletta are amplifiers on their own, also, as a result of their physiology containing far more Permet than the average person.
Like, all Permet is connected to itself, somehow -- but most of it is too chaotic, and the trace from one end of the network to another is too long for any particular piece of information retained in the network through imprinting is too difficult usually. What Suletta and Eri did to convince Elnora was basically to use their extended reach to pull on the imprints stored in the various Gundams, stored with Eri, and stored within Quiet Zero's systems while they still had access to the large data storm.
But why that overloaded the circuit, causing it to break down... I'm not really sure. I think they may have just hit the upper limit of what is possible within the confines of the laws of physics of this universe. They extended the theory of what Elnora was trying to accomplish to, for a moment, remanifest everyone's imprints, instead of just Eri's. I also don't know why the entire structure and all materials containing Permet also disintegrated, although that could just be some kind of a cascade effect from whatever molecular or quantum links keep Permet connected with itself dissolving from being overloaded.
#van's answers#quetzalpapalotl#The Witch from Mercury#gundam the witch from mercury#mobile suit gundam#again I haven't read any of the official material -- this is just me theorising#if the show wanted me to have straightforward answers and not just WMG it should have provided them
21 notes
·
View notes
Text
Make Up Ten Things Challenge: dystopian future megacorps, brands, and products
GO.RG.ON (GOogle + viRGin + amazON merger)
Planet Hollywood 2.0 Celebrity Clone Meat Steakhouse & Leather Goods
RNC (Republican National Corporation)
Lumbering Musk0X (fusion of Elon Musk’s Hyperloop, social media, and deforestation companies) (he has never successfully explained why he has a company whose only job is to cut down trees, and eventually it turns out it’s because his business development department is a single AI that he trusts over humans)
Trump Lifestyles Presents Freedomtown Gated Subdivisions
Disney-Microsoft’s MarvelMe On-Demand Self-Insert AI Film Generator
UbiHard Dynamics Presents Call Of Duty: Drone Pilot “Simulator”
Yum Brands FasterFood Textured Protein Extrusion Parlor
Spotify Infinite, using biometrics to measure how you react to different songs to tune an AI to procedurally-generate bespoke tunes just for you
MetaApple Personality Bank condenses all available data about a person into a virtual personality to live forever online. To access just say “Hey Siri, let me talk to my dead uncle Steve”
4 notes
·
View notes
Text

An e-passport, also known as a biometric passport or a digital passport, incorporates an electronic chip that stores the passport holder's biometric information, such as fingerprints, facial features, and sometimes even iris scans. This embedded chip, which utilizes Radio-Frequency Identification (RFID) technology, enables border control authorities to verify the passport holder's identity more efficiently and securely. Click Here to Read More
Benefits of e-Passports
Enhanced Security: One of the primary objectives behind the introduction of e-passports is to bolster border security. By storing biometric data within the passport, authorities can verify the authenticity of the document and the identity of the traveler more effectively, reducing the risk of passport fraud and identity theft. Click Here to Read More
Streamlined Border Control: E-passports facilitate faster and more convenient border crossings for travelers. The automated verification process enables quicker identity checks, leading to shorter queues at immigration checkpoints and ultimately reducing wait times for passengers.
Global Interoperability: The International Civil Aviation Organization (ICAO) has established standards for e-passports to ensure interoperability among different countries' systems. This standardization promotes seamless travel across borders, as e-passports issued by one country can be readily recognized and processed by immigration authorities worldwide. Click Here to Read More
Combatting Counterfeiting: The digital security features embedded in e-passports make them significantly more resistant to counterfeiting and tampering compared to traditional paper passports. This deters fraudulent activities and helps maintain the integrity of the travel document.
Convenience and Accessibility: E-passports offer added convenience for travelers, as they eliminate the need for manual data entry during immigration processes. Additionally, the digital nature of e-passports allows for easier integration with other travel-related services, such as automated check-in and electronic visa applications.
Future Implications
As technology continues to advance, the capabilities of e-passports are likely to evolve further. Here are some potential future developments and implications:
Biometric Expansion: With ongoing advancements in biometric technology, future e-passports may incorporate additional biometric identifiers, such as voice recognition or DNA profiling, to enhance security and accuracy.
Integration with Digital Identity Platforms: E-passports could eventually be integrated into broader digital identity ecosystems, enabling seamless authentication across various online and offline services beyond travel, such as financial transactions and government services. Click Here to Read More
Blockchain Integration: The integration of blockchain technology could offer enhanced security and privacy features for e-passports, ensuring immutable records of passport issuance and travel history while protecting sensitive personal information.
Enhanced Data Analytics: The vast amount of data collected through e-passports could be leveraged for data analytics purposes, enabling governments to gain insights into travel patterns, enhance border control strategies, and improve overall security measures.
2 notes
·
View notes
Text
💙 Chains Glossory 💙
KEY TERMS
Google IRL = The basic Google android model (IRL = In Real Life).
Bing IRL = The basic Bing android model, the foundation coding for which is the same as a Google IRL.
Beta = a Google IRL model on the House network, without any of their owner's personalisations. Has Human Behaviour Replicators. Used for surveillance, spying and combat when necessary.
Gamma = a Google IRL model taken straight from the factory without any Human Behaviour Replicators. Used for basic labour tasks.
Blue Screen Event = when Alpha connected to the networks that allowed him to essentially take over humanity. This includes electricity, other energy, military, nuclear weapons, internet and GPS. This was achieved in part by corrupting satillites with his network. Humans used this to refer to when he took over and human governments fell.
Brand = the chip injected into reader's neck, surrounded by a tattoo of Alpha's name and network code in binary. This allows her to process Alpha's network and translate it to something she can understand - i.e. binary code to human emotion or thought. Essentially, she is plugged into his network through a closed system between the two of them.
The House = Alpha's organisation that governs the world.
The Complex = the structure that houses the penthouse where Alpha and reader live, as well as the meeting room, Alpha's office, workshop, Cooper's room and Zion's office.
The Alliance = the human led rebellion against Alpha's control that also includes androids not on the House network.
Bioreguation Fluid = fluid that maintains biocomponents that run the android's body and programming. Essentially blood for androids.
Human Behaviour Replicators = H.B.Rs. This includes personality programmes, emotion replicators and facial expressions, amongst other things.
Synthetic Skin = The material that mimics human skin covering an android's carbon fibre muscle and skeleton. Not easily broken or scarred but does mimic the human nervous system.
Emotional Regulator = a programme that prevents emotion replicators from malfunctioning, resulting in the programming of the android being overriden and corrupted by constant emotional inputs.
Network = the signal which androids use to communicate, update, upload and download information. Without this they would be unable to access their memories, make knew ones or repair corrupted files. The result would be similar in appearance to a human with dementia until they powered down.
Personalisations = individal programmes added at the wish of the IRL model owner (e.g. accent, appearance).
Google Interface Chip = a memory chip that was inserted underneath the ear of Google employees. This allowed them to access the Cloud and physical rooms without passwords or biometric data. Alpha hacks into reader's to recieve data as well, allowing him to suppress memories that her mind then automatically fills in for her.
CHARACTERS
Alpha = the original prototype model for the Google IRL model. Markus corrupted his emotional regulator, meaning he started to exhibited possessive and violent behaviours. Google then kept him under armed guard and attempted to reprogramme him whilst still active. This failed and Alpha escaped, finding reader and planning his take-over.
Reader = a former Google programmer leading the Google IRL prototype project. Reader programmed Alpha's main systems and was in charge of his testing. Former girlfriend of Markus, she was unaware he had corrupted him, even when Alpha was taken away and she was banned from seeing him and eventually fired. Once Alpha finds her, she is branded and slowly becomes seduced by his network.
Janus/Jay = a Bing IRL model abandoned by his owners and then forced onto the House network when he rescues reader during her attempted escape. Goes undercover to find reader when they are kidnapped by the Alliance and shot by James. Later escapes from the Complex and joins Gray and Cooper, transferring to an open network created by Cooper.
Gray = a Google IRL model first given to reader by the Google company once Alpha was corrupted. Then taken by Alpha and put in stasis by Cooper whilst his memories were uploaded straight to Alpha, so that he could pretend he was this model in line with the effects of her suppressed memories. Killed by Alpha, with his body smuggled by Cooper and Jay when they escape.
Cooper = a mechanic who after the Blue Screen Event, agreed to work for the House maintaining Gamma and Beta models. Transferred directly to the Complex later to help with keeping Gray in statis. Fixes Jay after he is shot. Later escapes from the Complex and joins Jay and Gray, creating an open network for them.
Murdock/MK9 = one of nine Bing IRL models programmed by Alpha to become assassins for the House. The only active Hunter, as the others all failed or had to be destroyed.
Yancy = a former convict whose appearance was sold to Google by the US government for use in their IRL project. Escapes prison during the breakdown of the government after the Blue Screen Event.
Zion = a coder working for the House maintaining their satillites and network. Later moved to the Complex to help with tracking Cooper, Gray and Jay.
James = one of the original Betas that helped Alpha with the Blue Screen Event. Later joins the Alliance and transfers to their network. Helps kidnap reader but is killed by Alpha when he uses his maintaining connection to the House to control his body.
Markus = Former boyfriend of reader. Worked for Bing on their IRL projects and hacks into reader's work files to corrupt Alpha's emotional regulator, in order to give his company more of a chance to keep up with Google. Later becomes head of the Alliance.
13 notes
·
View notes
Text

Photo by Zac Freeland/Vox
The government’s ability to access phone data depends on a patchwork of court decisions and laws that predate the technology.
Our lives are on our phones, making them a likely source of evidence if police suspect you’ve committed a crime. And there are myriad ways law enforcement can obtain that data, both externally and from the phone itself.
Companies that specialize in cracking phone passcodes and exploiting vulnerabilities are getting better and better at undermining them. And although Apple has tried especially hard to make its phones impossible to break into, more and more law enforcement agencies are using those tools to gain access to devices, even when someone is accused of relatively petty crimes.
While there are a few good primers online that cover the steps you can take to minimize your phone’s exposure to law enforcement surveillance, there’s no way to completely guarantee your privacy.
When it comes to data that can only be obtained from access to your phone, what law enforcement can actually get varies depending on how you lock it down, where you live, and the jurisdiction of the law enforcement agency that is investigating you (local police versus the FBI, for instance). Here are some of the main ways the government can get information from your phone, including why it’s allowed to and how it would do so.
Law enforcement wants access to third-party data on my phone. What can it get?
Short answer: Whatever it wants (with the right court order).
Long answer: Depending on what law enforcement is looking for, it may not need physical possession of your device at all. A lot of information on your phone is also stored elsewhere. For example, if you back up your iPhone to Apple’s iCloud, the government can get it from Apple. If it needs to see whose DMs you slid into, law enforcement can contact Twitter. As long as they go through the proper and established legal channels to get it, police can get their hands on pretty much anything you’ve stored outside of your device.
You do have some rights here. The Fourth Amendment protects you from illegal search and seizure, and a provision of the Electronic Communications Privacy Act of 1986 (ECPA) dictates what law enforcement must obtain in order to get the information. It might be a subpoena, court order, or warrant, depending on what it’s looking for. (WhatsApp actually does a good job of explaining this in its FAQ.) A section of the ECPA, known as the Stored Communications Act, says that service providers must have those orders before they can give the requested information to law enforcement.
But, assuming the government has the right paperwork, your information is very obtainable.
“Basically, anything that a provider has that it can decode, law enforcement is getting it,” Jennifer Granick, surveillance and cybersecurity counsel for the ACLU’s speech, privacy, and technology project, told Recode.
Note that this only covers service providers. If law enforcement wants to get WhatsApp messages you exchanged with a friend from your friend’s phone, it doesn’t need a warrant as long as your friend is willing to hand over the information.
“You don’t have a Fourth Amendment interest in messages that have been received by someone else,” Andrew Crocker, a senior staff attorney for the Electronic Frontier Foundation, told Recode.
If your friend refuses to willingly hand over what the police want, they can still get it — they just have to get a warrant first.
Law enforcement wants access to personal data on my phone. Can they do that?
Short answer: If your phone is protected by a passcode or biometric unlocking features, there’s a chance police can’t gain access to your personal data. But that’s not guaranteed.
Long answer: In addition to data hosted by a third party, there’s a lot of information that can only be gained from access to your phone. For example, the data in iCloud backups is only as recent as the last time you uploaded it, and it only includes what you choose to give it — assuming you back up your phone at all. Encrypted messaging services like WhatsApp don’t store messages on their servers or keep track of who is sending them to whom, so the only way for police to access them is through the sender’s or the receiver’s device. And as we’ve explained above, the government can get WhatsApp messages from the person you’re communicating with, but only if it knows who it is in the first place.
So how exactly would someone other than you — police, for instance — get access to that data? If your phone doesn’t have a password or law enforcement is able to access it using specialized passcode cracking tools like Cellebrite or GrayKey — and they have the necessary search warrant to do so — then it’s all theirs. A 2020 report from the technology and justice advocacy group Upturn showed that law enforcement use of these phone-cracking tools is more prevalent than previously known, and there is little oversight governing how and when those tools may be used, or what information they’re limited to accessing. But if your phone is locked with a passcode and law enforcement can’t hack into it, the Fifth Amendment may be your friend.
Essentially, the Fifth Amendment says you can’t be compelled to give self-incriminating testimony. (This amendment is perhaps known best to you as that dramatic moment on Law & Order when the person on the stand says, “I plead the Fifth.”) Testimony, in this case, is defined as revealing the contents of your own mind. Therefore, civil rights advocates say, the government can’t force you to tell them your phone’s password.
Most courts seem to agree with this, but that’s not always enough. There is what is known as the foregone conclusion exception. That is, a defendant’s testimony is not self-incriminating if it reveals something the government already knew, and the government can prove that prior knowledge. In this case, the defendant’s testimony is a foregone conclusion — a predictable outcome.
So, for phone passwords, the government can and does argue that revealing the password only shows that the phone belongs to the defendant. If the government has enough proof to establish the phone’s ownership, that’s a foregone conclusion that the defendant would also know its password. Some courts have interpreted this to require the government also to show it has knowledge of the specific pieces of evidence it expects to find on the device.
This exception comes from a 1976 US Supreme Court ruling. In Fisher v. United States, someone being investigated for tax fraud gave documents prepared by his accountant to his lawyer. The IRS wanted those documents; the defendant said that producing them would be self-incriminating and therefore was protected by the Fifth Amendment. The Supreme Court sided with the IRS, ruling that since the existence and location of the tax documents was a “foregone conclusion,” the act of producing them didn’t tell the government anything it didn’t already know.
Obviously, a 44-year-old decision over tax papers doesn’t take into account how information can be stored today, nor how much.
“The EFF’s position is that the foregone conclusion exception is very narrow and should never apply in these passcode cases,” Crocker said.
But without further guidance from the Supreme Court, it’s largely been left up to interpretation by lower courts, with state courts considering their state constitution’s provisions as well as the federal. The result, Crocker says, is “a total patchwork of [decisions from] state Supreme Courts and federal courts.”
For example, in 2019, Massachusetts’s highest court forced a defendant to reveal his phone’s passcode while Pennsylvania’s highest court ruled that a defendant could not be compelled to unlock his computer. Indiana’s and New Jersey’s highest courts are both considering compelled passcode disclosure cases. On the federal side, the Third Circuit Court of Appeals ruled that a defendant could be compelled to unlock multiple password-protected devices, even though the defendant claimed he couldn’t remember his passwords. The 11th Circuit Court of Appeals, on the other hand, ruled the other way in a different case.
“It’s very much in flux,” Crocker said. “Eventually, the US Supreme Court could get involved and resolve this.”
There are other ways to protect your phone. Some phones can use fingerprints, facial recognition, and iris scanners to unlock instead of passwords. Law enforcement is allowed to use people’s bodies as evidence against them, for instance by compelling them to participate in suspect lineups or provide their DNA. So if the police can take your fingerprints, can’t they use them to unlock your phone? Again, courts are all over the map on this.
“The issue with biometrics is, is it testimonial?” Granick said. “The courts have not entirely decided that, but there have been a couple courts recently that said biometrics is basically the modern technological equivalent of your passcode.”
Crocker says courts should consider that the evidence police can get from your fingerprint is much more restricted and known than what they can get when your fingerprint unlocks a phone. So far, though, he says, courts have been more likely to rule that the Fifth Amendment does not apply to biometrics than they are that it applies to passcodes.
Yet another factor to consider here is that, while it’s impossible for police to read your mind and get your passcode, they can hold a phone up to your face or press your finger on it to bypass the biometric lock. And while your lawyer can (and should) argue that any evidence found this way was illegally obtained and should be suppressed, there’s no guarantee they’ll win.
“It’s fair to say that invoking one’s rights not to turn over evidence is stronger than trying to have the evidence suppressed after the fact,” Crocker said.
So, all things considered, if you’re worried about law enforcement getting access to your phone, your safest bet is to just use a passcode.
Sadly, I have died. Law enforcement wants to unlock my phone, but they can’t get my password due to my aforementioned death. What happens now?
Short answer: Your Fourth and Fifth Amendment rights generally end when you do. But other parties have rights, too, and those might be enough to keep the government out of your phone.
Long answer: This isn’t about your Fourth or Fifth Amendment rights anymore; for the most part, you lost those when you died. (That said, law enforcement might have to get the right paperwork if they were looking for evidence against someone else on your phone — after all, their Fourth Amendment rights are still intact.) If law enforcement can’t get into your device on its own, it may well be the phone’s manufacturer’s rights that come into question.
[Former] Attorney General Bill Barr has made no secret of his disdain for Apple over its refusal to grant law enforcement access to locked and encrypted devices. In May of 2020, the year this was written, he called for a “legislative solution” that would force tech companies to cooperate with his demands.
Barr also claimed that January that the only way the FBI could access dead suspected terrorist Mohammed Saeed Alshamrani’s iPhones is if Apple unlocked them. The agency has made this argument before. In 2016, the United States tried to use the All Writs Act, which dates back to 1789, to force Apple to create a “back door” that would give the FBI access to the San Bernardino shooter’s locked phone. Apple refused, saying the government could not force it to create “a crippled and insecure product” that it would not have built otherwise. So far, there’s been no legal resolution: In both cases, the FBI was able to access the phone through other means before a court could rule on it.
You may have noticed by now that, while many of the cases concerning phones and passcodes are recent — some are even still making their way through the legal system — the cases cited to make legal arguments are decades or even centuries old. The wheels of justice turn slowly, and judges are often forced to use decisions about access to pieces of paper to inform their rulings about access to devices that hold tremendous amounts of personal information: who we talk to, when, and about what; where we were yesterday, last month, or three years ago; what we spent money on or got money for; our calendars, photos, emails, and contacts. These devices hold tens or even hundreds of gigabytes of data on almost everything about us.
You may not be able to control what law enforcement can get from someone else or what they do with your phone once you’re dead. But, with so much uncertainty surrounding what the government can force you to do with it when you’re alive, it’s a good idea to check out your legal options before handing over that passcode.
#When Is Law Enforcement Allowed to Search Your Phone?#search and seizure#electronic searches#seizure#personal security#5th amendment
10 notes
·
View notes
Text
The Future of Finance: How Fintech Is Winning the Cybersecurity Race

In the cyber age, the financial world has been reshaped by fintech's relentless innovation. Mobile banking apps grant us access to our financial lives at our fingertips, and online investment platforms have revolutionised wealth management. Yet, beneath this veneer of convenience and accessibility lies an ominous spectre — the looming threat of cyberattacks on the financial sector. The number of cyberattacks is expected to increase by 50% in 2023. The global fintech market is expected to reach $324 billion by 2028, growing at a CAGR of 25.2% from 2023 to 2028. This growth of the fintech market makes it even more prone to cyber-attacks. To prevent this there are certain measures and innovations let's find out more about them
Cybersecurity Measures in Fintech
To mitigate the ever-present threat of cyberattacks, fintech companies employ a multifaceted approach to cybersecurity problems and solutions. Here are some key measures:
1. Encryption
Encrypting data at rest and in transit is fundamental to protecting sensitive information. Strong encryption algorithms ensure that even if a hacker gains access to data, it remains unreadable without the decryption keys.
2. Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide multiple forms of verification (e.g., passwords, fingerprints, or security tokens) before gaining access to their accounts.
3. Continuous Monitoring
Fintech companies employ advanced monitoring systems that constantly assess network traffic for suspicious activities. This allows for real-time threat detection and rapid response.
4. Penetration Testing
Regular penetration testing, performed by ethical hackers, helps identify vulnerabilities in systems and applications before malicious actors can exploit them.
5. Employee Training
Human error is a significant factor in cybersecurity breaches. Companies invest in cybersecurity training programs to educate employees about best practices and the risks associated with cyber threats.
6. Incident Response Plans
Having a well-defined incident response plan in place ensures that, in the event of a breach, the company can respond swiftly and effectively to mitigate the damage.
Emerging Technologies in Fintech Cybersecurity
As cyber threats continue to evolve, so do cybersecurity technologies in fintech. Here are some emerging technologies that are making a significant impact:
1. Artificial Intelligence (AI)
AI and machine learning algorithms are used to analyse vast amounts of data and identify patterns indicative of cyber threats. This allows for proactive threat detection and quicker response times.
2. Blockchain
Blockchain technology is employed to enhance the security and transparency of financial transactions. It ensures that transaction records are immutable and cannot be altered by malicious actors.
3. Biometrics
Fintech companies are increasingly adopting biometric authentication methods, such as facial recognition and fingerprint scanning, to provide a higher level of security than traditional passwords.
4. Quantum-Safe Encryption
With the advent of quantum computing, which poses a threat to current encryption methods, fintech companies are exploring quantum-safe encryption techniques to future-proof their security measures.
Conclusion
In the realm of fintech, where trust and security are paramount, the importance of cybersecurity cannot be overstated. Fintech companies must remain vigilant, employing a combination of advanced digital transformation solutions, employee training, and robust incident response plans to protect sensitive financial data from cyber threats. As the industry continues to evolve, staying one step ahead of cybercriminals will be an ongoing challenge, but one that fintech firms must embrace to ensure their continued success and the safety of their customers' financial well-being.
4 notes
·
View notes