#cloudflare bypass
Explore tagged Tumblr posts
Video
youtube
Zenrows Alternative | ScrapingBypass Web Scraping API Bypass Cloudflare
Are you looking for a Zenrows alternative?
Zenrows is a web scraping API that can bypass Cloudflare, Captcha, and all anti-bot verification. ScrapingBypass is so similar to Zenrows, so you can use it to extract data easily.
👉 Go to ScrapingBypass website: https://www.scrapingbypass.com
#zenrows#zenrows alternative#web scraping#web scraping api#bypass cloudflare#cloudflare bypass#scrapingbypass
2 notes
·
View notes
Video
youtube
ScrapingBypass Web Scraping API Bypass Cloudflare Captcha Verification
ScrapingBypass API can bypass Cloudflare Captcha verification for web scraping using Python, Java, NodeJS, and Curl. $3 for 3-day trial: https://www.scrapingbypass.com/pricing ScrapingBypass: https://scrapingbypass.com Telegram: https://t.me/CloudBypassEN
#scrapingbypass#bypass cloudflare#cloudflare bypass#web scraping api#captcha solver#web scraping#web crawler#extract data
1 note
·
View note
Note
What would you say are good reasons to use a VPN?
bypassing countrywide/internet provider blocklists or monitoring (of porn, lgbt content, etc (often just changing ur dns server (see cloudflare dns or quad9) will also be enough, but this might be more risky)), piracy, technically bypassing geoblocks on content (but like, just pirate shit lol), as one of multiple layers when doing other fun illegal shit online (do not ask me for specific advice, just a commercial vpn will not be sufficient protection) etc.. a vpn will not magically protect you from getting hacked or inherently increase security, and having one always enabled will not do much more than just slowing your internet down for most users. regarding isp/government monitoring it also simply shifts who you have to trust to another commercial entity, often operating under thin margins while being easily subpoenad, generally dont trust a privacy focused company that has a suspiciously high marketing budget. (furthermore companies such as nordvpn have been officially found of false advertising by at least the UK government, pointing this out in their replies on twitter will get you blocked, same with poining out how trivially they were hacked in the past and how shoddy their security has been at times)
2K notes
·
View notes
Text
Researcher Reveals New Techniques to Bypass Cloudflare's Firewall and DDoS Protection

Source: https://thehackernews.com/2023/10/researcher-reveal-new-technique-to.html
More info: https://certitude.consulting/blog/en/using-cloudflare-to-bypass-cloudflare/
6 notes
·
View notes
Text
glad i discovered archiveofourown.gay so i can bypass cloudflare blocking (no idea why im blocked) and continue looking in the neil tag daily just to get pissed off when no ones published anything new
0 notes
Text
Hướng dẫn tạo Telegram API Proxy trên Cloudflare Worker
Hướng dẫn tạo Telegram API Proxy trên Cloudflare Worker #Telegram #API #Proxy #CloudflareWorker #HướngDẫn #Dev #Programming Bài viết này hướng dẫn bạn cách tạo một Telegram API proxy sử dụng Cloudflare Workers. Phương pháp này giúp tăng cư��ng bảo mật và độ ổn định khi tương tác với Telegram Bot API, đặc biệt hữu ích trong các trường hợp cần bypass hạn chế địa lý hoặc tăng tốc độ truy cập.…
0 notes
Text
Intuitive Powerful Visual Web Scraper - WebHarvy can automatically scrape Text, Images, URLs & Emails from websites, and save the scraped content in various formats. WebHarvy Web Scraper can be used to scrape data from www.yellowpages.com. Data fields such as name, address, phone number, website URL etc can be selected for extraction by just clicking on them! - Point and Click Interface WebHarvy is a visual web scraper. There is absolutely no need to write any scripts or code to scrape data. You will be using WebHarvy's in-built browser to navigate web pages. You can select the data to be scraped with mouse clicks. It is that easy ! - Scrape Data Patterns Automatic Pattern Detection WebHarvy automatically identifies patterns of data occurring in web pages. So if you need to scrape a list of items (name, address, email, price etc) from a web page, you need not do any additional configuration. If data repeats, WebHarvy will scrape it automatically. - Export scraped data Save to File or Database You can save the data extracted from web pages in a variety of formats. The current version of WebHarvy Web Scraper allows you to export the scraped data as an XML, CSV, JSON or TSV file. You can also export the scraped data to an SQL database. - Scrape data from multiple pages Scrape from Multiple Pages Often web pages display data such as product listings in multiple pages. WebHarvy can automatically crawl and extract data from multiple pages. Just point out the 'link to the next page' and WebHarvy Web Scraper will automatically scrape data from all pages. - Keyword based Scraping Keyword based Scraping Keyword based scraping allows you to capture data from search results pages for a list of input keywords. The configuration which you create will be automatically repeated for all given input keywords while mining data. Any number of input keywords can be specified. - Scrape via proxy server Proxy Servers To scrape anonymously and to prevent the web scraping software from being blocked by web servers, you have the option to access target websites via proxy servers. Either a single proxy server address or a list of proxy server addresses may be used. - Category Scraping Category Scraping WebHarvy Web Scraper allows you to scrape data from a list of links which leads to similar pages within a website. This allows you to scrape categories or subsections within websites using a single configuration. - Regular Expressions WebHarvy allows you to apply Regular Expressions (RegEx) on Text or HTML source of web pages and scrape the matching portion. This powerful technique offers you more flexibility while scraping data. - WebHarvy Support Technical Support Once you purchase WebHarvy Web Scraper you will receive free updates and free support from us for a period of 1 year from the date of purchase. Bug fixes are free for lifetime. WebHarvy 7.7.0238 Released on May 19, 2025 - Updated Browser WebHarvy’s internal browser has been upgraded to the latest available version of Chromium. This improves website compatibility and enhances the ability to bypass anti-scraping measures such as CAPTCHAs and Cloudflare protection. - Improved ‘Follow this link’ functionality Previously, the ‘Follow this link’ option could be disabled during configuration, requiring manual steps like capturing HTML, capturing more content, and applying a regular expression to enable it. This process is now handled automatically behind the scenes, making configuration much simpler for most websites. - Solved Excel File Export Issues We have resolved issues where exporting scraped data to an Excel file could result in a corrupted output on certain system environments. - Fixed Issue related to changing pagination type while editing configuration Previously, when selecting a different pagination method during configuration, both the old and new methods could get saved together in some cases. This issue has now been fixed. - General Security Updates All internal libraries have been updated to their latest versions to ensure improved security and stability. Sales Page:https://www.webharvy.com/ DOWNLOAD LINKS & INSTRUCTIONS: Sorry, You need to be logged in to see the content. Please Login or Register as VIP MEMBERS to access. Read the full article
0 notes
Text
Cybersecurity Advisory: Hackers Exploit CAPTCHA Trick on Webflow to Deliver Phishing Attacks

In the ever-evolving landscape of cyber threats, attackers constantly devise new ways to bypass security measures and trick unsuspecting users. A recent and particularly insidious campaign has come to light, revealing hackers are exploiting a clever CAPTCHA trick, often leveraging legitimate platforms like Webflow's Content Delivery Network (CDN), to deliver sophisticated phishing attacks and malware.
This advisory details how this exploit works and, more importantly, what you can do to protect yourself and your organization.
The Deceptive CAPTCHA Trick
Traditionally, CAPTCHAs (Completely Automated Public Turing test to tell Computers and Humans Apart) are designed to differentiate between human users and automated bots, acting as a crucial security layer to prevent spam and abuse. However, in this new wave of attacks, hackers are turning this defense mechanism into an attack vector.
Here's how the exploit typically unfolds:
SEO Poisoning & Malicious PDFs: Attackers use search engine optimization (SEO) techniques to push malicious PDF files high up in search results. These PDFs are often hosted on legitimate, trusted platforms like Webflow's CDN, GoDaddy, or Strikingly, making them appear harmless. Users searching for documents, book titles, or charts might stumble upon these booby-trapped PDFs.
The Fake CAPTCHA Lure: When a victim opens one of these malicious PDFs, they are presented with an image that mimics a CAPTCHA challenge. This fake CAPTCHA often includes a checkbox or a button, prompting the user to "verify they are human" or "download the document."
Redirection to Phishing Pages: Clicking on this fake CAPTCHA image or button redirects the user to a malicious website. To add a layer of legitimacy, this phishing page might even present a real CAPTCHA (like Cloudflare Turnstile), further convincing the victim that they are on a legitimate site undergoing a security check.
Malware Delivery (Lumma Stealer): Once the user completes the genuine CAPTCHA, they are often prompted to "download" the supposed document. However, this action triggers a malicious PowerShell command, silently executing and deploying information-stealing malware, such as Lumma Stealer, onto the victim's system. In some cases, the attack directly aims to harvest credit card details or other sensitive personal information.
Information Exfiltration: The Lumma Stealer malware then proceeds to search for and exfiltrate sensitive data, including passwords, cryptocurrency wallet credentials, browser information, and other critical files.
Why is This So Effective?
This attack vector is particularly dangerous due to several factors:
Leveraging Trusted Domains: Hosting malicious PDFs on reputable CDNs like Webflow's helps bypass common security checks that flag suspicious or newly registered domains.
Social Engineering Sophistication: The use of CAPTCHAs, even fake ones, adds a veneer of legitimacy, making users less suspicious. The multi-stage nature of the attack, sometimes including a real CAPTCHA, further enhances its deceptive power.
Human Tendency to Trust: Users are accustomed to seeing CAPTCHAs and interacting with PDFs, making them more likely to fall victim to these well-crafted schemes.
Fileless Attack Techniques: The use of PowerShell scripts and other fileless methods can help the malware evade traditional antivirus detection.
How to Protect Yourself and Your Organization
Given the stealthy nature of these attacks, a multi-layered defense strategy is crucial:
Extreme Caution with Downloads and Links:
Verify Sources: Always be suspicious of unexpected PDF files or documents, especially if they are from unknown sources or appear in unusual search results.
Hover Before You Click: Before clicking any link or button within a document or on a webpage, hover over it to see the actual URL. Look for discrepancies or suspicious domains.
Direct Navigation: If you're looking for a specific document, go directly to the official website of the source rather than clicking on links from search results or emails.
Enhanced Email and Web Security:
Advanced Email Filtering: Implement robust email security solutions that can detect and block sophisticated phishing attempts, including those with malicious attachments or links.
Web Content Filtering: Deploy web filters that can identify and block access to known malicious websites, even if they are hosted on legitimate CDNs.
Endpoint Detection and Response (EDR):
Proactive Monitoring: EDR solutions can monitor endpoint activity for suspicious behaviors, such as unusual PowerShell script execution or attempts to exfiltrate data, even if the initial infection vector was subtle.
User Education and Awareness:
Regular Training: Conduct frequent cybersecurity awareness training for all employees, focusing on recognizing phishing tactics, social engineering, and the dangers of interacting with suspicious content.
"Think Before You Click": Reinforce the importance of pausing and scrutinizing any unexpected requests or prompts, especially those involving downloads or credential entry.
Keep Software Updated:
Patch Regularly: Ensure your operating systems, web browsers, PDF readers, and all other software are kept up-to-date with the latest security patches.
Implement Strong Authentication:
Multi-Factor Authentication (MFA): Enable MFA on all accounts, especially for critical services. This adds a crucial layer of security, even if credentials are stolen.
The Bottom Line
The exploitation of CAPTCHA tricks on platforms like Webflow's CDN highlights the evolving sophistication of cybercriminals. While these attacks are designed to be deceptive, a combination of user vigilance, robust security tools, and continuous education can significantly reduce your risk. Stay informed, stay cautious, and prioritize cybersecurity in your daily digital interactions.
0 notes
Link
#DNSconfiguration#DNSmanagement#DNSrequest#DNSsettings#DNStroubleshooting#domainmapping#dynamicIP#emailserver#IPaddress#PTRrecord#PTRupdate#reverseDNS#reverseDNSlookup#reverselookup#SMTPrelay#staticIP#Tier2support#Tier3support#Verizon#Verizonbusinessaccount#Verizonbusinesssupport#VerizonFios#Verizonnetwork#Verizonsupport#Verizontechnicalsupport
0 notes
Video
youtube
Google SERP Scraping With Python
The video shows a easy Google SERP scraping process with Python. 👉 Go to ScrapingBypass website: https://www.scrapingbypass.com Google SERP scraping code: https://www.scrapingbypass.com/tutorial/google-serp-scraping-with-python
#serp scraping#serp scraper#google serp scraping#bypass cloudflare#cloudflare bypass#web scraping#scrapingbypass#web scraping api
0 notes
Text
Fighting Cloudflare 2025 Risk Control: Disassembly of JA4 Fingerprint Disguise Technology of Dynamic Residential Proxy
Today in 2025, with the growing demand for web crawler technology and data capture, the risk control systems of major websites are also constantly upgrading. Among them, Cloudflare, as an industry-leading security service provider, has a particularly powerful risk control system. In order to effectively fight Cloudflare's 2025 risk control mechanism, dynamic residential proxy combined with JA4 fingerprint disguise technology has become the preferred strategy for many crawler developers. This article will disassemble the implementation principle and application method of this technology in detail.
Overview of Cloudflare 2025 Risk Control Mechanism
Cloudflare's risk control system uses a series of complex algorithms and rules to identify and block potential malicious requests. These requests may include automated crawlers, DDoS attacks, malware propagation, etc. In order to deal with these threats, Cloudflare continues to update its risk control strategies, including but not limited to IP blocking, behavioral analysis, TLS fingerprint detection, etc. Among them, TLS fingerprint detection is one of the important means for Cloudflare to identify abnormal requests.
Technical Positioning of Dynamic Residential Proxy
The value of Dynamic Residential Proxy has been upgraded from "IP anonymity" to full-link environment simulation. Its core capabilities include:
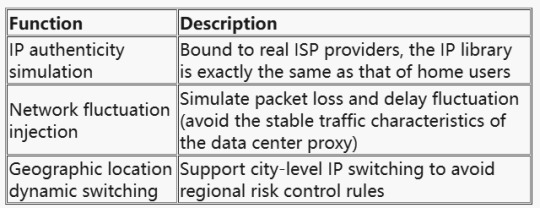
JA4 fingerprint camouflage technology dismantling
1. JA4 fingerprint generation logic
Cloudflare JA4 fingerprint generates a unique identifier by hashing the TLS handshake features. Key parameters include:
TLS version: TLS 1.3 is mandatory (version 1.2 and below will be eliminated in 2025);
Cipher suite order: browser default suite priority (such as TLS_AES_256_GCM_SHA384 takes precedence over TLS_CHACHA20_POLY1305_SHA256);
Extended field camouflage: SNI(Server Name Indication) and ALPN (Application Layer Protocol Negotiation) must be exactly the same as the browser.
Sample code: Python TLS client configuration

2. Collaborative strategy of dynamic proxy and JA4
Step 1: Pre-screening of proxy pools
Use ASN library verification (such as ipinfo.io) to keep only IPs of residential ISPs (such as Comcast, AT&T); Inject real user network noise (such as random packet loss rate of 0.1%-2%).
Step 2: Dynamic fingerprinting
Assign an independent TLS profile to each proxy IP (simulating different browsers/device models);
Use the ja4x tool to generate fingerprint hashes to ensure that they match the whitelist of the target website.
Step 3: Request link encryption
Deploy a traffic obfuscation module (such as uTLS-based protocol camouflage) on the proxy server side;
Encrypt the WebSocket transport layer to bypass man-in-the-middle sniffing (MITM).
Countermeasures and risk assessment
1. Measured data (January-February 2025)

2. Legal and risk control red lines
Compliance: Avoid collecting privacy data protected by GDPR/CCPA (such as user identity and biometric information); Countermeasures: Cloudflare has introduced JA5 fingerprinting (based on the TCP handshake mechanism), and the camouflage algorithm needs to be updated in real time.
Precautions in practical application
When applying dynamic residential proxy combined with JA4 fingerprint camouflage technology to fight against Cloudflare risk control, the following points should also be noted:
Proxy quality selection: Select high-quality and stable dynamic residential proxy services to ensure the effectiveness and anonymity of the proxy IP.
Fingerprint camouflage strategy adjustment: According to the update of the target website and Cloudflare risk control system, timely adjust the JA4 fingerprint camouflage strategy to maintain the effectiveness of the camouflage effect.
Comply with laws and regulations: During the data crawling process, it is necessary to comply with relevant laws and regulations and the terms of use of the website to avoid infringing on the privacy and rights of others.
Risk assessment and response: When using this technology, the risks that may be faced should be fully assessed, and corresponding response measures should be formulated to ensure the legality and security of data crawling activities.
Conclusion
Dynamic residential proxy combined with JA4 fingerprint camouflage technology is an effective means to fight Cloudflare 2025 risk control. By hiding the real IP address, simulating real user behavior and TLS fingerprints, we can reduce the risk of being identified by the risk control system and improve the success rate and efficiency of data crawling. However, when implementing this strategy, we also need to pay attention to issues such as the selection of agent quality, the adjustment of fingerprint disguise strategies, and compliance with laws and regulations to ensure the legality and security of data scraping activities.
0 notes
Note
maia your website doesn’t work in australia methinks:(
my website is blocked by various internet providers, especially ones using classification lists by symantec (i am misclassified by them, but the chances of getting that fixed are pretty low). this can be bypassed (also for other sites filtered by your ISP) by following the setup instructions of a third party DNS server such as cloudflare dns (1.1.1.1) or quad9 dns (9.9.9.9), which is much easier than you might think!
741 notes
·
View notes
Text
Hướng dẫn fix ✅ Cách tối ưu để Cloudflare cũng cache:
Dựa vào header bạn cung cấp, mình nhận xét nhanh tình trạng cache hiện tại của website doogee.io.vn như sau 💡: 📋 Phân tích trạng thái: x-litespeed-cache: hit ✅ 👉 Trang đã được LiteSpeed Cache cache thành công ở server gốc. Điều này tốt cho TTFB và tải trang. cf-cache-status: BYPASS ❌ 👉 Cloudflare KHÔNG dùng bản cache từ edge (bị bypass), có thể do: Cookie riêng của người dùng (ví dụ đang đăng…
0 notes
Text
TIL that cloudflare offers a vpn for free (just not marketed to consumers much) called cloudflare warp. it's the only thing i've found that bypasses the school firewall
#it's also wireguard based!!!!#there's a site-to-internet version too which means you can pretty easily run your entire network through the vpn#you just need like. a two port NUC or something
0 notes
Link
0 notes